#how to test for a dns leak
Explore tagged Tumblr posts
Text
Best VPNs for Protecting Against DNS Hijacking and Phishing Attacks
Are you tired of feeling like a fish swimming in dangerous waters, constantly at risk of falling victim to DNS hijacking and phishing attacks? Look no further! We’ve compiled a list of the best VPNs that will act as your impenetrable shield, protecting you from these malicious online threats. With these VPNs, it’s as if you have a virtual bodyguard standing by your side, ensuring your online…

View On WordPress
#best vpn for custom dns#check for dns leaks#dns hijacking#domain name system hijacking#how to protect yourself from dns hijacking#how to test for a dns leak#is there a free vpn for torrenting?#is there completely free vpn for pc#is vpn needed for torrenting#prevention tips for dns hijacking#what is dns hijacking
0 notes
Text
Please for the love of all that is holy STOP USING FREE VPNS. You know that adage about how, "If a service is free, you're the product?" It's extremely true, particularly when it comes to free VPNs.
A 2016 study of Android VPNs found that:
75% of free VPNs use 3rd-party tracking software
38% of free VPNs contain code flagged as malware
19% tunnel your data through FULLY UNENCRYPTED CONNECTIONS
84% of all VPNs were leaking IPv6 traffic
66% of all VPNs were leaking DNS traffic
4 of the VPNs tested were ACTIVELY DOING TLS INJECTIONS
You are straight up better off trusting your ISP with your traffic data than some random VPN you found and downloaded from the internet. Using no VPN is far far safer than using a free VPN whose whole profit model is built off selling your information.
57 notes
·
View notes
Text
How to Flange Out a Stainless Steel Pipe: 5 Best Tips to Use Steel Pipe Flanges
A pipe flange is a mechanical device that serves the purpose of joining the pipes together. It can be in the form of a welding neck where it is welded to a pipe or other butt-weld fittings.
The threaded flange or flange collar is screwed to the flange with a companion pipe. Other methods include using a lap joint to make connections using a stub end, as well as the common slip-on and socket weld connections.

Here are five tips for using the steel pipe flange for the first time:
Slip-on flanges for low-pressure services
The preference of slip-on flanges is mainly by the users who prefer flanges that are easy to use, have less installation time, and have low cost.
In addition, they are helpful for non-critical low-pressure services like firewater, cooling water, and other non-challenging pipework owing to their strength being approximately 1/3 lower than that of a weld neck flange, depending on the assembly. The pipe gets welded to the flange hub and bore.
If you want to check on the integrity of the slip-on connection, a magnetic particle, a simple visual test, or even a PT test are the approaches you can follow. You can use the slip-on flanges, which come in a variety of sizes greater than NPS ½ (DN 15).
Socket weld flanges in high-pressure pipe works
If you do high-pressure pipework below 2 inches (DN50), a socket weld flange is preferable when space is constrained. It would help if you filleted weld the pipe to the socket weld flange hub.
A good welding flange experience is crucial to make the connection, since a radiographic examination on the fillet weld is not easy to execute.
If, however, the connection is visual and critical, examination alone will not be enough if it carries out the magnetic failure or penetrates particle tests to check the connection strength.
Lap joint flange in high-cost material pipelines
The working of lap joint connections is good for pipelines that are in high-cost materials such as stainless steel and nickel alloys. It dramatically reduces the total cost of all flanged connections, which is required. The stub end, which has been welded to the pipe, and the backing or lapped flanges are used to make a lap joint connection.
You may, for instance, use the stainless steel stub end combined with a carbon steel lap joint flange for a good welded connection at lower costs. This is becoming an increasingly common alternative as the volatility of steel prices becomes an issue.
Connecting weld neck flanges to the butt weld for good performance
There is a tapered hub on the weld-neck flanges. It comes with an end that’s finished as a butt weld and can be connected to butt weld pipe and fittings.
You can examine the weld’s quality with ultrasound radiography or visually do it.
The welded connection of weld neck flange or pipe flange features good fatigue as well as mechanical stress performance.
Skilled professionals execute the pipe flange joint process
Trained personnel must be the ones to execute flange joint seals. It helps to prevent dangerous leaks from happening in the pipeline.
With the first time use of steel pipes, a properly trained engineer must be the one to execute flange ring joint connections and reference the correct bolt torque data.

Conclusion
Steel pipe flanges are often the best solutions to your multi-stage pipe assemblies, but the material grade is also of concern.
Stainless steel is a corrosion-resistant, durable, strong metal, making it an excellent choice for flange fittings in the gas and oil industry when carbon steel will not suffice.
If you want more information on steel pipe flanges, contact Texas Flange.
0 notes
Text
How To Secure Your Privacy with VPN?

A VPN is a tool that encrypts your internet connection and masks your IP address, making your online activities private and secure. It routes your internet traffic through a server in a location of your choice, ensuring your real identity and location remain hidden.
Steps to Secure Your Privacy with a VPN
1. Choose a Reliable VPN Provider
Select a VPN service known for strong privacy policies, no-logs practices, and robust encryption. Trusted providers like Vipiyan, NordVPN, ExpressVPN, or Surfshark offer excellent security features.
2. Install the VPN on Your Devices
Download and install the VPN app on all your devices, including laptops, smartphones, and tablets. Most VPN providers support multiple devices under a single subscription.
3. Connect to a Secure Server
Once installed, open the app and connect to a server. For maximum privacy, choose a server outside your country or one in a privacy-friendly region.
4. Enable Kill Switch and Leak Protection
Activate features like the Kill Switch, which cuts off internet access if the VPN disconnects, and DNS/IPv6 leak protection to prevent accidental exposure of your data.
5. Use Strong Encryption Protocols
Ensure the VPN is set to use secure encryption protocols like OpenVPN or WireGuard for optimal security.
6. Avoid Free VPNs
Free VPNs often log your data or inject ads, which can compromise your privacy. Opt for paid VPN services for better protection.
7. Combine with Secure Browsing Practices
Use incognito mode or privacy-focused browsers like Brave or Tor.
Clear cookies and cache regularly to avoid tracking.
Avoid logging into personal accounts when using public Wi-Fi.
8. Regularly Update the VPN Software
Keep your VPN app up to date to benefit from the latest security patches and features.
9. Test Your VPN
Use online tools like DNS leak test or IP leak test to ensure your VPN is functioning properly and your IP address is hidden.
Benefits of Using a VPN for Privacy
Data Encryption: Safeguards your sensitive data like passwords and financial information.
Anonymity: Prevents tracking by hiding your real IP address.
Access Restricted Content: Helps bypass geographical restrictions.
Secure Public Wi-Fi: Protects your data on unsecured public networks.
Conclusion
Using a VPN is one of the most effective ways to protect your privacy online. By following these steps and integrating secure browsing habits, you can shield your personal information from hackers, trackers, and unauthorized entities. Invest in a reliable VPN service today to ensure a safer and more private internet experience.
Let me know if you'd like me to tailor this further!
1 note
·
View note
Text
You have invested in a proxy server because you know the advantages of having one. The proxy provides anonymity and privacy while browsing. You get security because it sieves content from remote websites. The proxy also allows you to access content from sites with geographical restrictions. Data encryption also seals any areas of vulnerability hackers can use to access your site. However, sometimes you may not be getting all the benefits of your proxy. This happens when your proxy is leaking your IP address. But, how will you know if this is happening? Our article will teach you seven ways to check if your proxy is leaking your IP address. Let's dive into it. How Proxies Hide Your IP Address A proxy is an internet computer that has its IP address. It becomes a gateway between you and the internet. All requests from your server go through the proxy. The remote server will see the proxy IP address and not yours. Different proxies work in different ways to hide your IP address. A SOCKS proxy forms a shield that covers your address. It does not interfere with Your IP in any way because it continues to exist but underneath the surface. What Happens When There Is An IP Address Leak? Think about your home address is accessible to anyone at any time. You cannot be sure of security and privacy. The same happens when your IP or online address is visible to everyone. You will no longer enjoy that anonymity or privacy. You become an easy target for content and ads that are annoying. You also lose the advantage of being able to bypass website restrictions. You also lose the benefits proxies have for your business. If you start to notice some of the things we have highlighted, your IP address may be leaking. Here is What you Need to Do to Confirm the Same. Checking For IP Address Proxy Leaks You can run some very simple tests that will tell you whether your IP address is leaking. Let's dive into it. Use browserleaks.com To Check for IP Address Leaks You only need to login to browserleaks.com to get all the information. You will get this page. It carries out different tests, including WebRTC leak tests, DNS leak test, and flash leak tests. Check for IP Address Leaks with Windows You can use Windows to check for IP address leaks. You will need to know your IP address and the proxy server one as well. Now follow the steps below. Launch the command prompt on your computer Type in pingtestservername.com-n1 on the search bar This screen will come up Now confirm that the IP address that comes up is not the same as the original one. Search For IP Address Leaks With Google.Com Your favorite search engine will allow you to search for IP address leaks. You follow the same process as you would if you are searching. You must first disable your proxy. Now go to the search bar and type in what is my IP address. The first results on the page will show your IP address. Please take note of it by jotting it down somewhere. Now enable your proxy and run the search again. If you get a different IP address, then you are safe. It shows that your proxy is shielding your original IP. Identify DNS Leaks with dnsleaktest.com Your online phone book is the domain name system or DNS. Your ISP assigns you a DNS when you sign up. If your proxy bypasses the Proxy DNS and goes to the default, your IP address becomes visible to anyone on the online platform. Follow the Steps Below Log in to the website; you will get this screen. Now decide on the test you want to run, whether standard or extended. By clicking on the former, this is what you will get. Use whatismyip.com to check for IP address Leaks Many online resources will help you run IP leak tests. One such tool is whatsmyip.com. Simply log onto the platform, and you will get a screen like this. The platform gives exact details, including your country, region, and city. The next step is to log in to a proxy from a different country from yours.
If the IP address that comes up is the same as what you have on whatsmyip.com, you have a problem. It means that your proxy server is not concealing your address. Check Torrent Leaks Online You probably use torrents to access content for entertainment, software, or even music. To check for torrent leaks, search for private checkers online. IPMagnet, for example, will require you to download the software. When you log in, you will get a page like this . Click on the magnet link to download the tool. Open it with the torrent you normally use. Once it completes the scan, you will get two IP addresses. One should be for the torrent client, the other your original one. If your results show your IP address for both, you have a proxy IP address leak. WebTRC Leak Tests with ipleak.org WerbRTC is important for push notifications. You have the option of disabling it in your browser. It may, however, compromise some of the default settings. The other option is to keep up with testing your website to avoid IP address leaks. ipleak.org is easy to use. Simply log in, and you will get a page like this. Final Thoughts A proxy server will give you privacy and anonymity while online. You also get to excess contents that may not be available within your graphical location. However, you may get an IP address leak, which you need to correct immediately. If not, your address will be visible to everyone using the internet. We have shared 6 Ways you can use to check for IP address leaks. The steps are simple to follow. It allows you to take the necessary measures to restore your privacy.
0 notes
Text
Best VPN Services in Canada: Comparison Between Audit Insider and Market Insider
When looking for the best VPN services in Canada, it's important to evaluate them based on a variety of factors including privacy, speed, security, user experience, and cost. Two platforms that can offer valuable insights into this are Audit Insider and Market Insider. Both provide in-depth information on VPN services, but they approach the topic in different ways, helping consumers make more informed choices.
Audit Insider focuses on offering reviews and audits of VPN services, evaluating them based on privacy policies, data security measures, and how well they adhere to their claims. One of the key things Audit Insider often highlights is the transparency of VPN providers. They dig deep into whether these services log user data, their history with data leaks or breaches, and how they protect users against government surveillance or hackers. This is particularly important in Canada, where privacy and security concerns are high. If a VPN provider claims to have a no-logs policy, Audit Insider often goes a step further to confirm that they do not store any personally identifiable information.
Additionally, Audit Insider pays close attention to the technical side of VPN services. They look at whether the VPN offers robust encryption protocols like OpenVPN or WireGuard, both of which are recognized for their strength and security. Other features that Audit Insider may evaluate include kill-switch functionality (which disconnects your internet if the VPN connection drops), DNS leak protection, and the VPN’s ability to bypass geo-blocking. Since users in Canada often seek access to content from other countries, the ability to easily bypass geo-restrictions becomes an important factor.
Market Insider, on the other hand, takes a broader approach by providing comparisons of VPN services across different price ranges and offering recommendations based on budget, location, and intended use. They provide helpful breakdowns of VPN service packages, including subscription plans, free trials, and any hidden costs that might surprise customers later on. They also compare VPNs in terms of their performance metrics, such as speed, server locations, and ease of use. This is beneficial for Canadian users who might prioritize a smooth streaming experience or need a fast connection for gaming or downloading large files.
Market Insider also focuses on the overall customer experience, such as the quality of customer support, ease of setup, and whether the VPN service is compatible with popular operating systems like Windows, macOS, Android, and iOS. For those who are not tech-savvy, the availability of easy-to-follow installation guides or helpful customer service teams can make a big difference when choosing a VPN.
Both Audit Insider and Market Insider assess VPN services based on their compatibility with Canadian law and the unique online challenges that Canadians might face. Canada has strong privacy laws, but some VPN providers may not be able to guarantee the same level of protection as others. Some providers based outside of Canada might be subject to different laws, including those in countries with less stringent privacy protections. For example, a VPN provider based in the US might be part of the Five Eyes intelligence alliance, which could affect its data retention practices. This is a point that both Audit Insider and Market Insider frequently address when making their comparisons.
Performance is another area where both Audit Insider and Market Insider offer valuable insights. Speed is often a key concern for VPN users, especially for those in Canada who may need to connect to distant servers. If a VPN service is too slow, it can significantly affect the quality of activities like streaming, gaming, or video conferencing. Both platforms will typically test VPN services across different server locations to give users a clear picture of how the service will perform under real-world conditions.
Price is also a critical factor when evaluating VPN services. Some VPN providers in Canada may have subscription plans that are more affordable than others, and both Audit Insider and Market Insider will compare these costs to help users choose the best value for their money. Sometimes a lower-priced VPN might have fewer features or slower speeds, but it may still work well for users with basic needs. For those willing to pay a bit more, there are premium VPN services that offer faster speeds, more servers, and additional features such as double encryption or dedicated IP addresses.
Both Audit Insider and Market Insider tend to recommend VPN providers with strong track records, solid reputations, and an emphasis on user privacy. For instance, services like ExpressVPN, NordVPN, and Surfshark are often mentioned on these platforms due to their strong performance and commitment to privacy. However, Audit Insider might offer more detailed insights into how each provider stacks up when it comes to actual security practices, while Market Insider will give a clearer understanding of pricing and performance comparisons. This means that together, both platforms offer a well-rounded picture of what to look for when choosing a VPN in Canada.
While both platforms provide helpful comparisons, they also recognize that the "best" VPN will ultimately depend on individual needs. For example, if you're a Canadian user who only wants a VPN for streaming geo-blocked content, you might prioritize a VPN with fast speeds and servers in many countries. On the other hand, if you're concerned with privacy and data security, you might choose a service that offers stronger encryption, a zero-logs policy, and legal protections.
Both Audit Insider and Market Insider frequently update their reviews and comparisons to keep up with the ever-changing landscape of VPN services. This is particularly important because the VPN industry evolves rapidly, with new features, servers, and security protocols being introduced regularly. As VPN technology improves and regulations around data privacy change, both platforms will continue to provide the latest information to help Canadian users make informed decisions.
Ultimately, choosing the best VPN service in Canada requires careful consideration of both personal preferences and the technical aspects of each provider. Audit Insider and Market Insider are both excellent resources for Canadian users who want to explore their options in depth and find a service that best suits their needs. Whether you're concerned about security, streaming performance, or cost, both platforms can help guide you toward the VPN that will offer the most value for your online activities.
0 notes
Text
How to effectively test proxy servers
When using a proxy server, speed, stability and security are key factors that affect the user experience. To ensure that your proxy server is meeting user needs, it's crucial to have a comprehensive testing strategy in place. This article will provide you with a guide to an effective strategy for testing the impact of proxy servers to help you optimize proxy performance.

1. Speed Testing
Use an online tool or software to test the speed of the proxy. The following steps can help you measure the speed performance of your proxy server:
·Ping Test: The Ping test measures the response time of the proxy server and thus assesses the latency. You can use a command line tool or a Ping test website to do this.
·Download Speed and Upload Speed Test: Test the download and upload speeds of the proxy at different bandwidths with a speed test tool such as Speedtest.
· Multi-threading test: Test the performance of the proxy under high concurrency by issuing multiple requests at the same time to evaluate its ability to handle large-scale tasks.
2. Stability test
Stability testing can be realized by connecting to the proxy server for a long time and observing whether its connection is interrupted. The following two methods are usually used:
· Long-time connection: Continuously use the proxy server for network access and observe whether the connection is stable and whether there are frequent drops or disconnections.
· Load test: Simulate multiple users connecting to the proxy server at the same time and observe its performance under high load.
3. Security Test
In order to ensure the security of the proxy, the following methods can be used:
· DNS Leakage Test: Detect whether the proxy server leaks real DNS requests through a specialized DNS leakage test tool.
· IP Leakage Test: Check if the proxy leaks the user's real IP address through IP leakage test, especially when using encrypted protocols such as HTTPS.
· Encryption Test: Ensure that the proxy supports encryption protocols such as HTTPS, verify the encryption quality of the data it transmits, and prevent the data from being intercepted during transmission.
4. Compatibility Test
Test whether the proxy supports the protocols required by the user (such as HTTP, HTTPS, SOCKS5, etc.) and whether it is compatible with various types of operating systems and devices. Compatibility can be ensured by configuring different types of proxy settings.
5. IP Distribution and Availability Testing
· IP address check: Test whether the proxy server can provide stable and diversified IP choices by using IP addresses from different regions for access, and IPinfo is recommended for the test.
· IP Quality Test: Use the IP Quality Check tool to assess whether the IP provided by the proxy server is flagged as suspicious or blocked by the target website to ensure the availability of the IP.
Testing the impact of a proxy server is critical to ensure its performance, stability and security. Through detailed testing of speed, stability, security, compatibility and IP distribution, you can better understand the performance of your proxy server and optimize it for your business needs.
711Proxy has worldwide IP resources, supports multiple protocols, and is highly stable and secure.
0 notes
Text

DNS Leak Test: How to Secure Your Online Privacy http://dlvr.it/TD48nc
0 notes
Text
absolutely no ill will to the person above me, but here's a bunch of piracy sites to use and other resources directly added onto the post because it being immediately available to the public is much more effective.
BEFORE YOU EVEN START PIRATING:
read this beginner's guide: https://rentry.org/Piracy-BG
sign up for a REPUTABLE paid vpn service. avoid express vpn, they happily sponsor alt-right, bigoted shitbags like matt walsh, steven crowder, ben shapiro, etc
download qbittorrent (https://www.qbittorrent.org). do NOT use bittorrent or utorrent. they're known to download malware/crypto miners onto your pc
bind qbittorrent to your vpn (https://reddit.com/r/VPNTorrents/comments/ssy8vv/guide_bind_vpn_network_interface_to_torrent/). do NOT rely on the vpn's built in "kill switch." they are not reliable and can easily lead to your isp seeing that you're torrenting
test that you've successfully bound qbittorrent to your vpn. instructions for this are in the above reddit link
check for possible dns leaks before torrenting ANYTHING (https://ipleak.net/ and https://dnsleaktest.com/)
stay AWAY from the pirate bay. it sucks, it's slow as hell, and full of viruses
CHECK PROGRAMS YOU DOWNLOAD WITH VIRUS TOTAL (https://www.virustotal.com/gui/home/upload) BEFORE INSTALLING
install ublock origin on your pc browser. download adguard for mobile devices
read through this list of untrustworthy sites: https://www.reddit.com/comments/10bh0h9
REPUTABLE PLACES TO TORRENT/DOWNLOAD THINGS (but mostly torrent):
basic/most popular ones:
movies and tv:
https://1337x.to/top-100-movies (don't download games from here unless they're from verified repackers and don't download software from here)
https://rutracker.org/forum/index.php
subtitles:
https://www.opensubtitles.org/en/search/subs
anime/manga:
https://nyaa.si/
wiki for all things anime/manga piracy: https://thewiki.moe/
current-day games:
https://fitgirl-repacks.site/ (this is the ONLY official site. WATCH OUT FOR FALSE LINKS)
retro games:
https://vimm.net/
https://archive.org/details/softwarelibrary_msdos_games
https://myrient.erista.me/files/No-Intro/
adobe software:
https://w14.monkrus.ws/
how to disable adobe's "genuine software integrity service: https://www.reddit.com/r/GenP/comments/ue47y6/possible_solution_to_unlicensed_app_popup_no/
audiobooks:
currently not working as of 6:23am est on october 28th, 2023 (however it usually does work): https://audiobookbay.li/ or https://audiobookbay.se/ (avoid fake download links, use torrents/magnets: https://i.ibb.co/8sV2061/0fa8159b11bb.png)
https://tokybook.com/ (definitely use an adblocker for this one)
ebooks:
https://zlibrary-africa.se/ (no, tiktok did not get this taken down)
archive.org
misc resources:
an entire wiki dedicated to piracy: https://www.reddit.com/r/FREEMEDIAHECKYEAH/wiki/index/ (backup link: https://notabug.org/nbatman/freemediaheckyeah/wiki/_pages)
https://reddit.com/r/Piracy
https://reddit.com/r/torrents
https://reddit.com/r/CrackWatch
https://www.reddit.com/r/movieleaks/
https://reddit.com/r/DataHoarder
https://reddit.com/r/sideloaded
https://www.reddit.com/r/ApksApps/
https://wiki.ds-homebrew.com/
https://reddit.com/r/3dshacks
https://wii.guide/
rarbg backup: https://web.archive.org/web/20230611112609/https://github.com/2004content/rarbg or https://rarbglite.github.io/
IMPORTANT
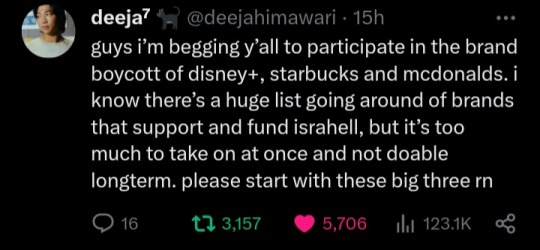
Boycott:
McDonald's
Starbucks
Disney+
Plz you can always watch the shows on pirated sites and find better alternatives for burgers & coffee, nothing is more important than stopping a genocide. It's a global boycott.
24K notes
·
View notes
Text
how to check a vpn connection
🔒🌍✨ Ganhe 3 Meses de VPN GRÁTIS - Acesso à Internet Seguro e Privado em Todo o Mundo! Clique Aqui ✨🌍🔒
how to check a vpn connection
Como testar a conexão VPN
Uma conexão VPN, ou Rede Virtual Privada, é uma ferramenta importante para proteger sua privacidade e segurança online. No entanto, é fundamental garantir que a conexão VPN esteja funcionando corretamente para obter os benefícios esperados.
Para testar a conexão VPN, existem algumas etapas simples que você pode seguir. Em primeiro lugar, verifique se a VPN está ativa e conectada. Isso geralmente é indicado por um ícone na barra de tarefas ou configurações do dispositivo. Em seguida, confira o endereço IP fornecido pela VPN para garantir que corresponda à localização esperada. Você pode fazer isso pesquisando "qual é o meu IP" em um mecanismo de busca.
Além disso, teste a velocidade da conexão VPN para garantir que não haja queda significativa no desempenho. Existem diversas ferramentas online gratuitas que permitem medir a velocidade da Internet, como o SpeedTest. Certifique-se de testar a velocidade com a VPN habilitada e desabilitada para comparar os resultados.
Outro aspecto importante a verificar é se a conexão VPN está vazando seu endereço IP real. Existem sites específicos que ajudam a identificar vazamentos de IP, como o DNS Leak Test. Caso seja identificada alguma falha de privacidade, é recomendável revisar as configurações da VPN ou procurar suporte técnico especializado.
Ao realizar esses testes de conexão VPN, você pode garantir uma navegação mais segura e protegida na Internet, preservando sua privacidade e mantendo seus dados pessoais seguros. É essencial incorporar essas práticas de verificação regularmente para garantir que sua VPN esteja funcionando adequadamente.
Verificar a estabilidade da VPN
Ao utilizar uma VPN (Virtual Private Network) para se conectar à internet, é essencial verificar a estabilidade da conexão a fim de garantir uma experiência segura e eficiente. Uma VPN é uma ferramenta muito útil para proteger sua privacidade online, criptografando seus dados e mascarando seu endereço IP, impedindo que terceiros monitorem suas atividades na web.
Para verificar a estabilidade da VPN, é importante considerar alguns pontos. Em primeiro lugar, verifique a velocidade da conexão ao utilizar a VPN. Uma queda significativa na velocidade da internet pode indicar instabilidade na VPN ou uma sobrecarga nos servidores. Testar a conexão em diferentes horários e servidores pode ajudar a identificar problemas de velocidade.
Além disso, é fundamental checar se há desconexões frequentes ao utilizar a VPN. Interrupções constantes na conexão podem comprometer a segurança de seus dados e interferir na qualidade da navegação.
Outro aspecto a ser considerado é a compatibilidade da VPN com diferentes dispositivos e sistemas operacionais. Verifique se a VPN é compatível com todos os dispositivos que você pretende usar para se conectar à internet.
Por fim, lembre-se de atualizar regularmente o software da VPN para garantir a estabilidade e segurança da conexão. Mantendo essas boas práticas, você poderá desfrutar de todos os benefícios de uma VPN de forma segura e estável.
Testar a segurança da conexão VPN
Testar a segurança da conexão VPN é fundamental para garantir a proteção dos dados e a privacidade dos usuários ao navegar na Internet. Uma VPN (Virtual Private Network) é uma ferramenta utilizada para criptografar o tráfego de dados, tornando-o mais seguro e garantindo a privacidade dos usuários, especialmente em redes públicas.
Existem várias maneiras de testar a segurança de uma conexão VPN. Uma delas é verificar o protocolo de segurança que está sendo utilizado pela VPN, como o OpenVPN, L2TP/IPsec ou IKEv2, e garantir que está atualizado e configurado corretamente. Além disso, é importante verificar se não há vazamentos de IP, DNS ou WebRTC que possam comprometer a privacidade do usuário.
Outro teste importante é verificar se a conexão VPN está realmente criptografando o tráfego de dados, usando ferramentas online específicas para isso. Também é recomendado testar a velocidade da conexão VPN, pois uma velocidade muito baixa pode indicar problemas de segurança ou de configuração.
É fundamental escolher uma VPN confiável e segura, de preferência paga, que ofereça políticas claras de privacidade e não registre atividades dos usuários. Testar regularmente a segurança da conexão VPN é essencial para garantir a proteção dos dados e a privacidade online. Assim, os usuários podem navegar na Internet com tranquilidade, sabendo que estão protegidos contra ameaças cibernéticas e violações de privacidade.
Avaliar a velocidade da VPN
Avaliar a velocidade da VPN é uma etapa crucial para garantir uma conexão segura e eficiente. Quando utilizamos uma VPN, nossos dados trafegam por servidores remotos, o que pode resultar em uma redução na velocidade da internet. Por isso, é importante testar a velocidade da VPN periodicamente para garantir que ela atenda às suas necessidades.
Existem diversas ferramentas disponíveis online que permitem medir a velocidade da VPN. Uma das métricas mais importantes a se observar é a velocidade de download, que impacta diretamente na rapidez com que você pode acessar conteúdos na internet. Além disso, a velocidade de upload também é relevante, especialmente se você realiza videochamadas ou envia grandes arquivos com frequência.
Ao avaliar a velocidade da VPN, é importante levar em consideração o servidor utilizado. Quanto mais distante o servidor, maior a probabilidade de haver uma queda na velocidade da conexão. Por isso, escolher um servidor próximo à sua localização pode resultar em uma experiência mais satisfatória.
Em resumo, avaliar a velocidade da VPN é essencial para garantir uma navegação segura e sem interrupções. Utilize ferramentas de medição disponíveis online, verifique tanto a velocidade de download quanto a de upload e escolha servidores próximos para obter o melhor desempenho possível. Dessa forma, você poderá aproveitar todos os benefícios de uma conexão VPN sem comprometer a velocidade da sua internet.
Garantir a privacidade na VPN
Ao utilizar uma Rede Privada Virtual (VPN), é essencial garantir a privacidade dos dados e da conexão. Uma VPN cria um túnel criptografado que protege as informações contra possíveis interceptações ou ataques cibernéticos, proporcionando maior segurança durante a navegação online.
Para garantir a privacidade na VPN, é importante seguir algumas medidas de segurança. Em primeiro lugar, é fundamental escolher uma VPN confiável e segura, de preferência uma que não mantenha registros das atividades dos usuários. Além disso, é recomendável utilizar uma combinação de protocolos de segurança, como o OpenVPN, L2TP/IPsec ou IKEv2, para reforçar a proteção dos dados.
Outro ponto a considerar é a localização dos servidores da VPN. Optar por servidores localizados em países com leis rígidas de proteção de dados contribui para a preservação da privacidade. Também é aconselhável ativar a função de desconexão automática (kill switch) para interromper a conexão à internet caso a VPN apresente falhas, evitando assim que os dados fiquem expostos.
É importante ainda manter o software da VPN sempre atualizado, pois as atualizações frequentes garantem a correção de possíveis vulnerabilidades de segurança. Por fim, é aconselhável utilizar senhas fortes e autenticação de dois fatores para proteger o acesso à VPN contra possíveis invasões.
Seguindo essas medidas de segurança, é possível desfrutar dos benefícios de uma VPN sem comprometer a privacidade dos dados. Garantir a privacidade na VPN é essencial para navegar na internet com tranquilidade e segurança.
0 notes
Text
how to check if my vpn is leaking
🔒🌍✨ Ganhe 3 Meses de VPN GRÁTIS - Acesso à Internet Seguro e Privado em Todo o Mundo! Clique Aqui ✨🌍🔒
how to check if my vpn is leaking
O que é um vazamento de VPN
Um vazamento de VPN ocorre quando ocorre uma falha na conexão segura fornecida por uma Rede Privada Virtual (VPN). Uma VPN é projetada para proteger a privacidade e a segurança dos dados durante a transmissão pela internet, criptografando o tráfego entre o dispositivo do usuário e o servidor da VPN. No entanto, um vazamento de VPN pode expor informações confidenciais, como endereço IP real, localização geográfica, atividades online e dados pessoais.
Existem vários tipos de vazamentos de VPN, incluindo vazamento de IP, vazamento de DNS e vazamento de WebRTC. Um vazamento de IP revela o endereço IP real do usuário, comprometendo sua privacidade online. Um vazamento de DNS expõe os servidores DNS que o usuário está utilizando, enquanto um vazamento de WebRTC revela endereços IP locais mesmo quando uma VPN está ativada.
Para evitar vazamentos de VPN, os usuários devem garantir que estão usando um provedor de VPN confiável que ofereça recursos de segurança avançados, como proteção contra vazamentos. Além disso, é importante manter o software da VPN atualizado e realizar testes regulares para identificar possíveis vazamentos.
Em resumo, um vazamento de VPN representa uma vulnerabilidade significativa na segurança online de um usuário, comprometendo a eficácia da criptografia e expondo informações privadas. Portanto, é fundamental estar ciente dos riscos associados aos vazamentos de VPN e adotar medidas proativas para proteger a privacidade e a segurança dos dados durante a utilização de uma conexão VPN.
Teste de vazamento de VPN
Um teste de vazamento de VPN é uma ferramenta importante para garantir a segurança e privacidade dos usuários ao navegar na internet. Uma rede privada virtual (VPN) é uma tecnologia que cria uma conexão segura e criptografada entre o dispositivo do usuário e a internet, protegendo seus dados de possíveis invasores.
O teste de vazamento de VPN verifica se há algum vazamento de informações do usuário durante a conexão. Isso pode ocorrer devido a configurações incorretas da VPN ou falhas no seu funcionamento. Os vazamentos podem expor o endereço IP real do usuário, sua localização e até mesmo suas atividades online, comprometendo assim sua privacidade e segurança.
Ao realizar um teste de vazamento de VPN, o usuário pode identificar e corrigir possíveis falhas na sua conexão. Existem várias ferramentas online disponíveis gratuitamente que permitem realizar esse tipo de teste e obter informações detalhadas sobre a segurança da sua VPN.
É fundamental que os usuários de VPN, especialmente aqueles que utilizam a rede para atividades sensíveis, realizem regularmente testes de vazamento para garantir a eficácia da sua proteção. Dessa forma, é possível desfrutar dos benefícios da privacidade e segurança oferecidos pela VPN, sem correr o risco de ter suas informações pessoais expostas.
Como verificar se há vazamento de VPN
Se você usa uma VPN para proteger sua privacidade online, é importante garantir que sua conexão esteja segura e que não haja vazamentos de informações confidenciais. Um vazamento de VPN pode expor seu endereço IP real, sua localização e atividades online, comprometendo assim a eficácia da VPN.
Existem várias maneiras de verificar se há vazamento de VPN. Uma maneira simples é acessar um site que verifica vazamentos de IP, como o "ipleak.net". Esse site mostrará seu endereço IP real e se há vazamentos de DNS ou WebRTC.
Além disso, você pode realizar testes adicionais, como verificar se seu endereço IP coincide com a localização fornecida pela VPN, garantir que seu tráfego esteja protegido por criptografia e testar se há vazamentos de IPv6.
Para prevenir vazamentos de VPN, certifique-se de utilizar uma VPN confiável e atualizada, que ofereça proteção contra vazamentos de IP. Além disso, desative a detecção de vazamentos de WebRTC em seu navegador e fique atento a avisos de vazamentos de DNS.
Verificar regularmente se há vazamentos de VPN é essencial para manter sua privacidade e segurança online. Ao adotar essas práticas, você pode desfrutar de uma experiência de VPN mais segura e protegida.
Ferramentas para detectar vazamento de VPN
As VPNs tornaram-se essenciais para garantir a privacidade e segurança online, mas vazamentos de VPN podem comprometer esses benefícios. Por isso, é fundamental contar com ferramentas especializadas para detectar e corrigir possíveis vazamentos.
Uma das maneiras mais eficazes de identificar vazamentos de VPN é por meio de testes de vazamento de DNS. Esses testes verificam se o tráfego de DNS está vazando para o servidor do provedor de serviços de Internet, expondo as suas atividades online. Ferramentas como o DNS Leak Test e o DNSleak.com são amplamente utilizadas para realizar esse tipo de verificação.
Além disso, é importante contar com ferramentas que verifiquem vazamentos de IP e WebRTC para garantir uma proteção abrangente. O WebRTC Leak Test e o IPLeak.net são exemplos de ferramentas que auxiliam na identificação desses tipos de vazamentos, garantindo que sua conexão VPN esteja realmente protegendo sua privacidade.
Por fim, é recomendável utilizar um kill switch, uma funcionalidade presente em muitos serviços de VPN, que interrompe a conexão com a internet caso haja algum vazamento detectado. Essa medida adicional evita que suas informações fiquem expostas em caso de falha na VPN.
Em resumo, garantir que sua VPN não esteja vazando informações é essencial para manter sua privacidade e segurança online. Utilize as ferramentas mencionadas e verifique regularmente a integridade da sua conexão VPN para desfrutar de uma experiência online protegida e tranquila.
Proteção contra vazamentos de VPN
As VPNs são uma ferramenta crucial para proteger a privacidade e a segurança online dos usuários. No entanto, mesmo usando uma VPN, é importante estar ciente dos vazamentos de informações que podem ocorrer e comprometer a eficácia desse recurso.
Um vazamento de VPN pode ocorrer quando informações pessoais, como endereço IP, localização ou dados de tráfego, são expostos involuntariamente. Existem diferentes tipos de vazamentos de VPN, incluindo vazamentos de IP, DNS e WebRTC, cada um representando uma ameaça à privacidade e a segurança online.
Para proteger-se contra vazamentos de VPN, os usuários podem adotar algumas medidas proativas. Uma das maneiras mais simples de evitar vazamentos de IP é realizar testes periódicos para verificar se a VPN está funcionando corretamente e não expondo o endereço real do usuário. Além disso, é importante escolher um provedor de VPN confiável, que ofereça recursos avançados de segurança e privacidade.
Outra forma de prevenir vazamentos de VPN é desativar serviços como WebRTC, que podem inadvertidamente revelar informações sensíveis. Configurar corretamente as configurações de privacidade do navegador e utilizar extensões especializadas também podem ajudar a fortalecer a proteção contra vazamentos de VPN.
Em resumo, estar ciente dos vazamentos de VPN e implementar medidas de segurança adequadas é essencial para garantir uma experiência online segura e privada. Ao adotar boas práticas e utilizar ferramentas de proteção, os usuários podem desfrutar dos benefícios das VPNs sem comprometer sua privacidade.
0 notes
Text
which vpn server is best
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
which vpn server is best
VPN server speed comparison
Title: Comparing VPN Server Speeds: Finding the Fastest Option
In today's digital landscape, where privacy and security are paramount, Virtual Private Networks (VPNs) have become essential tools. However, not all VPNs are created equal, and one crucial factor to consider is server speed. When choosing a VPN provider, understanding how their servers perform can make a significant difference in your online experience.
The speed of a VPN server can impact various aspects of your internet usage, including browsing, streaming, and downloading. A faster server means quicker loading times for websites, smoother streaming of high-definition content, and faster downloads of files and applications. Therefore, conducting a VPN server speed comparison is essential to ensure you get the best performance for your needs.
Several factors can influence VPN server speed, including server location, network congestion, encryption protocols, and the efficiency of the VPN provider's infrastructure. To accurately compare server speeds, it's essential to conduct tests under similar conditions, such as connecting to servers in the same geographical region and using consistent testing methodologies.
There are several online tools and resources available to help users conduct VPN server speed tests. These tools typically measure metrics such as download/upload speeds, latency, and jitter to provide insights into server performance. Users can also refer to independent reviews and performance benchmarks to gauge the speed and reliability of different VPN providers' servers.
When comparing VPN server speeds, it's crucial to prioritize your specific needs and usage patterns. For example, if you primarily use a VPN for streaming content, you'll want to prioritize servers with high download speeds and low latency. Conversely, if privacy is your primary concern, you may prioritize servers with robust encryption protocols, even if they sacrifice some speed.
In conclusion, conducting a VPN server speed comparison is essential for optimizing your online experience. By choosing a provider with fast and reliable servers, you can enjoy seamless browsing, streaming, and downloading while ensuring your privacy and security remain intact.
Security features of VPN servers
Title: Exploring the Essential Security Features of VPN Servers
In an age where online privacy and security are of paramount concern, Virtual Private Network (VPN) servers play a pivotal role in safeguarding sensitive data and ensuring anonymous browsing experiences. These servers employ a range of security features to fortify connections and shield users from potential threats. Here's a closer look at some of the key security features of VPN servers:
Encryption Protocols: VPN servers utilize robust encryption protocols such as AES (Advanced Encryption Standard) to encode data transmitted between the user's device and the server. This encryption ensures that even if intercepted, the data remains unreadable to unauthorized entities.
Kill Switch: A vital security feature, the kill switch automatically terminates internet connectivity if the VPN connection drops unexpectedly. This prevents sensitive data from being exposed to the unsecured network, maintaining user privacy at all times.
Secure Tunneling: VPN servers create a secure tunnel through which data travels, effectively concealing the user's IP address and browsing activity from prying eyes. This tunneling ensures anonymity and protects against surveillance or tracking attempts.
DNS Leak Protection: DNS (Domain Name System) leak protection prevents the user's DNS queries from being exposed to their Internet Service Provider (ISP) or other third parties. By rerouting DNS requests through the VPN server, this feature enhances privacy and prevents potential data leakage.
Multi-Factor Authentication (MFA): Some VPN servers offer multi-factor authentication, adding an extra layer of security by requiring users to provide multiple forms of verification before accessing the network. This significantly reduces the risk of unauthorized access to sensitive information.
No-Logs Policy: Reputable VPN providers adhere to a strict no-logs policy, meaning they do not store any user activity or connection logs. This ensures that even in the event of a data breach, user information remains inaccessible, maintaining confidentiality.
In conclusion, VPN servers employ a combination of advanced security features to safeguard user data, ensure privacy, and mitigate online threats. By understanding and utilizing these features, individuals can enjoy a safer and more secure browsing experience in an increasingly digital world.
User-friendly interface of VPN servers
A user-friendly interface is essential when it comes to VPN servers. VPNs, or Virtual Private Networks, play a crucial role in safeguarding online privacy and security by creating a secure connection between a user and the internet. A well-designed interface can greatly enhance the user experience, making it easier for individuals to connect to VPN servers and navigate through settings.
One of the key aspects of a user-friendly VPN server interface is simplicity. Users should be able to connect to a server with just a few clicks, without the need for technical expertise. Clear and intuitive options for selecting servers and changing settings can make the process seamless for both beginners and advanced users.
Visual indicators can also enhance the user experience. Status icons that show whether the connection is secure or not can provide users with peace of mind. Additionally, easy-to-understand graphics or maps displaying server locations can help users choose the best server for their needs.
Customization options are another important feature of a user-friendly VPN server interface. Users should have the ability to tailor their settings according to their preferences, such as selecting specific protocols or enabling features like kill switches or split tunneling.
Overall, a user-friendly interface can make the use of VPN servers more accessible and enjoyable for individuals looking to enhance their online security and privacy. By prioritizing simplicity, visual indicators, and customization options, VPN providers can create a more intuitive and efficient user experience for their customers.
Server locations and accessibility
Server locations play a crucial role in determining the accessibility and performance of a website or online service. The physical location of servers directly impacts factors such as latency, loading speed, and overall user experience.
When a user accesses a website or application, their request is routed to the nearest server location that hosts the content they are trying to access. This proximity reduces latency and ensures faster loading times. For example, if a website's servers are located in North America and a user from Europe tries to access it, their request may experience delays due to the longer distance the data needs to travel.
Having server locations strategically distributed across different regions allows websites to cater to a global audience more efficiently. This is particularly important for businesses or organizations with an international presence. By having servers in multiple locations, they can ensure that users from various parts of the world experience optimal performance when accessing their website or services.
Furthermore, server locations also impact factors such as search engine optimization (SEO) and content delivery networks (CDNs). Search engines consider server location when determining the geographical relevance of a website to specific search queries. Additionally, CDNs distribute website content across multiple servers in different locations, further improving accessibility and reliability.
In summary, server locations are critical for ensuring accessibility, performance, and user experience in today's interconnected digital landscape. Businesses and organizations must carefully consider their server infrastructure and strategically choose locations to effectively reach and serve their target audience.
Customer support for VPN servers
Customer support is a critical aspect of any VPN service, ensuring that users have a smooth and secure online experience. When it comes to VPN servers, efficient customer support becomes even more crucial due to the technical nature of the service and the diverse needs of users.
One of the primary roles of customer support for VPN servers is troubleshooting technical issues. Users may encounter problems such as difficulty connecting to servers, slow connection speeds, or compatibility issues with their devices. A knowledgeable and responsive support team can help diagnose these issues and provide timely solutions, minimizing downtime and frustration for users.
Additionally, customer support for VPN servers plays a vital role in addressing security concerns. Users may have questions about encryption protocols, logging policies, or privacy features offered by the VPN service. A reliable support team can offer clear explanations and guidance on how to maximize security and privacy while using the VPN.
Another important aspect of customer support for VPN servers is assisting users with server selection. VPN providers often have servers located in various countries around the world, each offering different levels of performance and accessibility. Customer support agents can help users choose the most suitable servers based on their specific needs, such as streaming content from geo-restricted sites or accessing websites with enhanced privacy protections.
Furthermore, customer support teams can provide assistance with account management and billing inquiries. Whether users need help setting up their accounts, updating payment information, or understanding subscription plans, responsive support can ensure a seamless experience throughout the customer lifecycle.
In conclusion, customer support for VPN servers plays a crucial role in ensuring user satisfaction and maintaining the integrity of the service. By offering technical assistance, addressing security concerns, aiding with server selection, and managing account inquiries, support teams contribute to a positive user experience in the increasingly important realm of online privacy and security.
0 notes
Text
why is my norton vpn not working
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
why is my norton vpn not working
Norton VPN troubleshooting
Norton VPN Troubleshooting: Fixing Common Issues
Norton VPN is a popular choice for securing internet connections and ensuring privacy online. However, like any software, it can encounter technical issues that may disrupt its functionality. Here are some common problems users might encounter with Norton VPN and how to troubleshoot them:
Connection Failures: If you're unable to establish a connection with Norton VPN, start by checking your internet connection. Ensure you have a stable internet connection and try connecting to different servers. If the issue persists, restart your device and the VPN application. If that doesn't work, consider reinstalling the VPN software.
Slow Connection Speeds: Slow speeds can be frustrating when using a VPN. To improve performance, try connecting to servers closer to your physical location. Additionally, check for any background processes or downloads that might be consuming bandwidth. Updating the VPN software to the latest version can also optimize performance and fix any bugs causing slowdowns.
DNS Leaks: DNS leaks can compromise your privacy by revealing your browsing activities. To prevent DNS leaks, ensure that the VPN's DNS settings are configured correctly. You can also use third-party tools to test for DNS leaks and adjust your VPN settings accordingly.
Compatibility Issues: Norton VPN may encounter compatibility issues with certain devices or operating systems. Before installing the VPN software, check for compatibility with your device and OS version. If you experience compatibility issues after installation, contact Norton support for assistance or consider using an alternative VPN solution.
Firewall Interference: Firewalls can sometimes block VPN connections, especially in corporate or public network environments. Temporarily disable any firewall or antivirus software and try connecting to Norton VPN again. If successful, adjust your firewall settings to allow VPN traffic.
By troubleshooting these common issues, you can ensure a smooth and secure experience with Norton VPN. If problems persist, don't hesitate to reach out to Norton customer support for further assistance.
Connectivity issues with Norton VPN
Title: Resolving Connectivity Issues with Norton VPN
Norton VPN is a widely used tool for ensuring online privacy and security. However, users may encounter connectivity issues that can disrupt their browsing experience. These problems can range from slow connection speeds to complete inability to connect to the VPN servers. Understanding and troubleshooting these issues can help users regain access to secure browsing.
One common connectivity issue with Norton VPN is slow connection speeds. This can be caused by various factors such as network congestion, distance from the VPN server, or limitations of the user's internet service provider. To address this, users can try connecting to different VPN servers closer to their physical location, or during off-peak hours when network traffic is lower. Additionally, optimizing their internet connection by closing bandwidth-intensive applications or switching to a faster internet plan can improve speeds.
Another issue users may face is difficulty connecting to Norton VPN servers. This can be frustrating, especially when trying to access sensitive information or bypass geo-restrictions. To troubleshoot this problem, users can first ensure that they have the latest version of the Norton VPN software installed. They can also try restarting their device, router, or modem to refresh network settings. If the issue persists, contacting Norton support for further assistance or trying alternative VPN solutions may be necessary.
Furthermore, compatibility issues with other security software or firewall settings can also cause connectivity problems with Norton VPN. Users should ensure that Norton VPN is allowed through their firewall and that it is not being blocked by any other security software installed on their device. Disabling conflicting software temporarily or adjusting firewall settings can often resolve these issues.
In conclusion, while connectivity issues with Norton VPN can be frustrating, they are usually solvable with some troubleshooting steps. By understanding the common causes of these problems and following the appropriate troubleshooting techniques, users can enjoy a seamless and secure browsing experience with Norton VPN.
Norton VPN not connecting
Norton VPN is a popular choice for many users seeking to protect their online privacy and security. However, encountering connectivity issues, such as Norton VPN not connecting, can be frustrating. There are several potential reasons why you may be experiencing this problem, but there are steps you can take to troubleshoot and resolve it.
Firstly, ensure that your internet connection is stable and working properly. A weak or intermittent connection can prevent the VPN from establishing a secure connection. Restarting your router or switching to a different network may help resolve the issue.
Additionally, check if the Norton VPN software is up to date. Outdated software can contain bugs or compatibility issues that may prevent the VPN from connecting. Update the software to the latest version available to ensure optimal performance.
If you are still facing connectivity issues, try switching to a different VPN server location. The server you are trying to connect to may be experiencing high traffic or technical difficulties. Connecting to a different server can help establish a stable connection.
Lastly, if none of the above steps resolve the problem, contact Norton customer support for assistance. They can provide guidance specific to your situation and help troubleshoot any underlying issues causing the VPN connection problem.
By following these steps and being proactive in troubleshooting, you can hopefully resolve the issue of Norton VPN not connecting and continue to enjoy a secure and private online browsing experience.
Norton VPN error messages
Encountering error messages while using Norton VPN can be frustrating, but understanding common issues and their solutions can help alleviate these challenges. Here are some prevalent Norton VPN error messages and their possible causes:
Error 1000: This error typically indicates a problem with the VPN's installation or configuration. Try reinstalling the VPN client or updating it to the latest version to resolve this issue.
Error 1001: Connection issues often trigger this error. Check your internet connection and try reconnecting to the VPN. If the problem persists, restarting your device or router may help.
Error 1002: Authentication failure is the usual culprit behind this error. Ensure that you're entering the correct username and password for your Norton account. If the issue persists, resetting your Norton account password might be necessary.
Error 1003: This error suggests a problem with the VPN server. Switching to a different VPN server location or contacting Norton support for assistance can help resolve this issue.
Error 1004: Firewall or antivirus software may block the VPN connection, leading to this error. Temporarily disabling such software or adding an exception for Norton VPN in your firewall settings could resolve the issue.
Error 1005: Insufficient system resources or conflicting software may trigger this error. Close unnecessary applications and try reconnecting to the VPN. If the problem persists, restarting your device or seeking technical support may be necessary.
In conclusion, encountering Norton VPN error messages is not uncommon, but many issues can be resolved with simple troubleshooting steps. By understanding the underlying causes of these errors and following the recommended solutions, you can enjoy a smoother VPN experience.
Resolving Norton VPN problems
If you're experiencing issues with your Norton VPN, you're not alone. Norton VPN, like any other software, can sometimes encounter problems that prevent it from working as intended. However, with a few troubleshooting steps, you can often resolve these issues and get back to enjoying a secure and private internet connection.
One common problem with Norton VPN is difficulty connecting to servers. If you're having trouble establishing a connection, start by ensuring that your internet connection is stable. Sometimes, a weak or unstable connection can prevent the VPN from connecting properly. Try switching to a different Wi-Fi network or using a wired connection if possible.
If your internet connection is stable but you're still unable to connect to Norton VPN servers, try switching to a different server location. Sometimes, certain server locations may be experiencing high traffic or technical issues, causing connection problems. By selecting a different server, you may be able to establish a connection more easily.
Another potential issue with Norton VPN is slow connection speeds. If you're experiencing slow speeds, try connecting to a server location that's closer to your physical location. Additionally, you can try restarting your device or temporarily disabling other programs or applications that may be consuming bandwidth.
If you've tried these troubleshooting steps and are still experiencing problems with Norton VPN, you may need to contact Norton customer support for further assistance. They can provide personalized troubleshooting advice and help you resolve any underlying issues that may be causing problems with the VPN.
By following these tips, you can often resolve common problems with Norton VPN and enjoy a secure and reliable internet connection once again.
0 notes
Text
You have invested in a proxy server because you know the advantages of having one. The proxy provides anonymity and privacy while browsing. You get security because it sieves content from remote websites. The proxy also allows you to access content from sites with geographical restrictions. Data encryption also seals any areas of vulnerability hackers can use to access your site. However, sometimes you may not be getting all the benefits of your proxy. This happens when your proxy is leaking your IP address. But, how will you know if this is happening? Our article will teach you seven ways to check if your proxy is leaking your IP address. Let's dive into it. How Proxies Hide Your IP Address A proxy is an internet computer that has its IP address. It becomes a gateway between you and the internet. All requests from your server go through the proxy. The remote server will see the proxy IP address and not yours. Different proxies work in different ways to hide your IP address. A SOCKS proxy forms a shield that covers your address. It does not interfere with Your IP in any way because it continues to exist but underneath the surface. What Happens When There Is An IP Address Leak? Think about your home address is accessible to anyone at any time. You cannot be sure of security and privacy. The same happens when your IP or online address is visible to everyone. You will no longer enjoy that anonymity or privacy. You become an easy target for content and ads that are annoying. You also lose the advantage of being able to bypass website restrictions. You also lose the benefits proxies have for your business. If you start to notice some of the things we have highlighted, your IP address may be leaking. Here is What you Need to Do to Confirm the Same. Checking For IP Address Proxy Leaks You can run some very simple tests that will tell you whether your IP address is leaking. Let's dive into it. Use browserleaks.com To Check for IP Address Leaks You only need to login to browserleaks.com to get all the information. You will get this page. It carries out different tests, including WebRTC leak tests, DNS leak test, and flash leak tests. Check for IP Address Leaks with Windows You can use Windows to check for IP address leaks. You will need to know your IP address and the proxy server one as well. Now follow the steps below. Launch the command prompt on your computer Type in pingtestservername.com-n1 on the search bar This screen will come up Now confirm that the IP address that comes up is not the same as the original one. Search For IP Address Leaks With Google.Com Your favorite search engine will allow you to search for IP address leaks. You follow the same process as you would if you are searching. You must first disable your proxy. Now go to the search bar and type in what is my IP address. The first results on the page will show your IP address. Please take note of it by jotting it down somewhere. Now enable your proxy and run the search again. If you get a different IP address, then you are safe. It shows that your proxy is shielding your original IP. Identify DNS Leaks with dnsleaktest.com Your online phone book is the domain name system or DNS. Your ISP assigns you a DNS when you sign up. If your proxy bypasses the Proxy DNS and goes to the default, your IP address becomes visible to anyone on the online platform. Follow the Steps Below Log in to the website; you will get this screen. Now decide on the test you want to run, whether standard or extended. By clicking on the former, this is what you will get. Use whatismyip.com to check for IP address Leaks Many online resources will help you run IP leak tests. One such tool is whatsmyip.com. Simply log onto the platform, and you will get a screen like this. The platform gives exact details, including your country, region, and city. The next step is to log in to a proxy from a different country from yours.
If the IP address that comes up is the same as what you have on whatsmyip.com, you have a problem. It means that your proxy server is not concealing your address. Check Torrent Leaks Online You probably use torrents to access content for entertainment, software, or even music. To check for torrent leaks, search for private checkers online. IPMagnet, for example, will require you to download the software. When you log in, you will get a page like this . Click on the magnet link to download the tool. Open it with the torrent you normally use. Once it completes the scan, you will get two IP addresses. One should be for the torrent client, the other your original one. If your results show your IP address for both, you have a proxy IP address leak. WebTRC Leak Tests with ipleak.org WerbRTC is important for push notifications. You have the option of disabling it in your browser. It may, however, compromise some of the default settings. The other option is to keep up with testing your website to avoid IP address leaks. ipleak.org is easy to use. Simply log in, and you will get a page like this. Final Thoughts A proxy server will give you privacy and anonymity while online. You also get to excess contents that may not be available within your graphical location. However, you may get an IP address leak, which you need to correct immediately. If not, your address will be visible to everyone using the internet. We have shared 6 Ways you can use to check for IP address leaks. The steps are simple to follow. It allows you to take the necessary measures to restore your privacy.
0 notes
Text
why vpn are not working
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
why vpn are not working
VPN configuration issues
Title: Troubleshooting Common VPN Configuration Issues
Virtual Private Networks (VPNs) are essential tools for securing online connections, but configuring them correctly can sometimes be challenging. Here are some common VPN configuration issues and how to troubleshoot them:
Connection Failures: One of the most frequent issues is when a VPN fails to connect. This could be due to incorrect login credentials, server overload, or network interference. To troubleshoot, double-check your username and password, try connecting to a different server, or switch to a different network to see if that resolves the issue.
Slow Connection Speeds: If your VPN connection is slow, it may be due to server congestion or network limitations. Try connecting to a different server closer to your physical location, as this can improve speeds. Additionally, closing unnecessary applications and reducing bandwidth-heavy activities can also help optimize your connection speed.
DNS Leaks: A DNS leak occurs when your device uses its default DNS instead of the VPN's encrypted DNS, potentially exposing your browsing activity. To fix this, ensure that your VPN client is configured to use its DNS servers and enable the DNS leak protection feature if available.
IP Address Leaks: Similar to DNS leaks, IP address leaks can compromise your privacy by revealing your true IP address. To prevent this, make sure your VPN is configured to use the VPN-assigned IP address and enable the kill switch feature, which automatically disconnects your internet if the VPN connection drops.
Compatibility Issues: Sometimes, VPNs may not work correctly with certain devices or operating systems. Ensure that your VPN client is compatible with your device and that you have the latest software updates installed. If compatibility issues persist, reach out to the VPN provider's support team for assistance.
By addressing these common VPN configuration issues, you can enjoy a more secure and reliable online experience. Remember to stay informed about best practices and seek assistance from your VPN provider or IT support if needed.
Network connectivity problems
Title: Troubleshooting Network Connectivity Problems: A Comprehensive Guide
Are you experiencing frustrating network connectivity issues? Whether you're at home or in the office, a malfunctioning network can disrupt productivity and cause undue stress. Understanding common network connectivity problems and how to troubleshoot them is essential for maintaining a smooth and efficient workflow.
One of the most common issues users encounter is slow or intermittent internet connectivity. This could be due to various factors such as bandwidth congestion, outdated hardware, or interference from other electronic devices. To address this, start by checking your internet speed using online speed testing tools. If the speed is significantly lower than what you're paying for, contact your internet service provider to investigate further.
Another prevalent issue is limited or no connectivity to the network. This could be caused by a range of issues including misconfigured network settings, faulty cables, or outdated network drivers. Begin troubleshooting by ensuring all cables are securely connected and that there are no visible signs of damage. Then, verify that your device's network settings are correct, including IP address configuration and DNS settings.
Furthermore, wireless network connectivity problems are also common, especially in densely populated areas where multiple networks overlap. To improve wireless connectivity, try relocating your router to a more centralized location, away from potential sources of interference such as microwaves and cordless phones. Additionally, consider upgrading your router to a newer model that supports the latest Wi-Fi standards for faster and more reliable connections.
In some cases, network connectivity issues may be indicative of more complex underlying issues such as network security breaches or hardware failures. If basic troubleshooting steps fail to resolve the problem, consider seeking assistance from a professional network technician who can conduct a thorough diagnosis and implement appropriate solutions.
By familiarizing yourself with common network connectivity problems and their troubleshooting methods, you can minimize downtime and ensure a seamless online experience for yourself and your team. Remember, proactive maintenance and regular updates are key to preventing future connectivity issues.
Firewall or antivirus interference
Firewalls and antivirus software are essential components of modern digital security, serving as the first line of defense against various online threats. However, there are instances where these protective measures can inadvertently interfere with the normal operation of your system or applications.
One common issue users encounter is firewall interference, which occurs when the firewall blocks legitimate network traffic or communication between software applications. This can lead to connectivity issues, preventing users from accessing certain websites or services, or even disrupting online gaming sessions or video calls. In some cases, overly restrictive firewall settings can hinder the functioning of legitimate software or updates, causing frustration for users trying to install or run programs.
Similarly, antivirus programs may also interfere with the normal operation of software applications. This can happen when the antivirus software incorrectly identifies a legitimate program or file as malicious and either quarantines it or blocks its execution. While this is usually done to protect the system from potential threats, it can result in inconvenience for users who rely on the affected software for their daily tasks.
To mitigate firewall or antivirus interference, users can take several steps. First, they should ensure that their security software is properly configured to allow necessary network traffic and whitelist trusted applications to prevent them from being mistakenly blocked. Additionally, keeping firewall and antivirus software up to date with the latest patches and definitions can help reduce the likelihood of false positives and improve compatibility with other software.
Overall, while firewalls and antivirus software are vital for safeguarding against online threats, users should be aware of the potential for interference and take proactive measures to minimize disruptions to their digital experience. By striking the right balance between security and usability, users can enjoy a safer and more seamless computing environment.
Outdated VPN software
Title: The Risks of Outdated VPN Software: Why You Should Update Now
In an era where online security is paramount, virtual private networks (VPNs) serve as a critical tool in safeguarding our digital presence. However, relying on outdated VPN software poses significant risks that can compromise your privacy and security.
Firstly, outdated VPN software lacks the latest security patches and updates, leaving your connection vulnerable to exploits and cyber attacks. Hackers are constantly evolving their tactics, exploiting weaknesses in outdated software to gain unauthorized access to sensitive information.
Moreover, obsolete VPN software may lack support for modern encryption protocols, leaving your data exposed to interception and surveillance. As technology advances, so do encryption standards, and failing to update your VPN means you're missing out on the latest advancements in securing your online communications.
Furthermore, outdated VPNs often suffer from performance issues and compatibility issues with newer operating systems and applications. This can result in slow connection speeds, frequent disconnections, and an overall frustrating user experience.
Additionally, using outdated VPN software may put you at risk of legal and regulatory consequences. Some countries impose strict regulations on VPN usage, and using outdated software may inadvertently violate these laws, exposing you to fines or even legal action.
In conclusion, the importance of keeping your VPN software up to date cannot be overstated. By regularly updating your VPN, you ensure that you have the latest security features, encryption protocols, and compatibility enhancements, thereby safeguarding your online privacy and security in an ever-evolving digital landscape. Don't let outdated software compromise your protection - update your VPN now.
ISP throttling or blocking
Title: Understanding ISP Throttling and Blocking: What You Need to Know
In the world of internet connectivity, users often encounter the terms "ISP throttling" and "ISP blocking." These practices, employed by Internet Service Providers (ISPs), can significantly affect a user's online experience. Understanding what ISP throttling and blocking entail is crucial for navigating the digital landscape effectively.
ISP throttling refers to the intentional slowing down of internet speeds by an ISP. This practice is often implemented to regulate network traffic and manage bandwidth usage. ISPs may throttle internet speeds for various reasons, including reducing network congestion during peak hours or limiting the bandwidth available to certain types of online activities, such as streaming video or downloading large files.
On the other hand, ISP blocking involves the deliberate prevention of access to certain websites, online services, or content. ISPs may block access to specific websites or online services for reasons such as enforcing copyright laws, complying with government censorship requirements, or mitigating security threats. In some cases, ISPs may also block access to certain types of content, such as adult content or gambling websites, to comply with regulatory standards or corporate policies.
Both ISP throttling and blocking can have significant implications for internet users. Throttling can result in slower internet speeds and degraded performance, particularly for activities that require high bandwidth, such as streaming video or online gaming. Meanwhile, blocking can restrict access to essential online resources and limit users' freedom to access information and services.
To address concerns related to ISP throttling and blocking, users can explore alternative ISPs that offer transparent and unrestricted internet access. Additionally, advocating for net neutrality principles and supporting policies that promote an open and free internet can help protect users' rights to unfettered access to online content and services.
In conclusion, ISP throttling and blocking are practices employed by ISPs that can impact users' internet experience. By understanding these practices and advocating for a free and open internet, users can work towards ensuring fair and unrestricted access to online resources.
0 notes
Text
what is fast vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is fast vpn
VPN Speed Test
A VPN speed test is a crucial way to determine how well your Virtual Private Network (VPN) is performing. VPNs are commonly used for ensuring online privacy and security, but they can sometimes slow down internet connection speeds due to encryption and routing through remote servers. Conducting a VPN speed test allows users to assess their VPN's impact on their browsing experience.
To perform a VPN speed test, start by selecting a reliable online tool or service that specializes in measuring internet speeds. Make sure to choose a server location that is close to your actual physical location for the most accurate results. Next, run a speed test without the VPN enabled to establish a baseline measurement of your internet connection speed. Then, enable your VPN and run the speed test again to compare the results.
Ideally, the difference in speed between the tests should be minimal. A slight decrease in speed is normal when using a VPN, but significant drops in speed could indicate issues with the VPN service provider, server congestion, or suboptimal server locations.
If you are experiencing consistently slow VPN speeds, consider switching to a different VPN server location, upgrading to a higher speed plan, or contacting your VPN provider for troubleshooting assistance. Remember that a fast and reliable VPN connection is essential for maintaining both online security and a seamless browsing experience. By regularly conducting VPN speed tests, you can ensure that your VPN is operating optimally and meeting your performance expectations.
Secure VPN Connection
Title: Ensuring a Secure VPN Connection: Your Ultimate Guide
In today's digital landscape, securing your online activities is paramount. With the rise in cyber threats and surveillance, using a Virtual Private Network (VPN) has become essential for safeguarding your privacy and data. However, not all VPN connections are created equal. Ensuring a secure VPN connection requires attention to several key factors.
First and foremost, choose a reputable VPN provider. Opt for a provider with a proven track record of protecting user privacy and offering robust encryption protocols. Look for features like a no-logs policy, which ensures that your online activities remain private even to the VPN provider.
Next, pay attention to encryption standards. A secure VPN connection employs strong encryption protocols such as AES 256-bit encryption, which is virtually unbreakable. This ensures that your data remains encrypted and secure as it travels between your device and the VPN server.
Moreover, consider the VPN's security features. Look for features like kill switch and DNS leak protection, which prevent your data from being exposed in the event of a VPN connection drop or DNS leak.
Furthermore, always ensure that your VPN software is up to date. VPN providers regularly release updates to patch security vulnerabilities and enhance performance. By keeping your VPN software updated, you can mitigate the risk of exploitation by cyber threats.
Lastly, practice good online hygiene. Even with a secure VPN connection, avoid accessing sensitive information or engaging in risky behavior online. Be cautious of phishing attempts and only visit secure websites with HTTPS encryption.
In conclusion, a secure VPN connection is essential for protecting your privacy and data online. By choosing a reputable VPN provider, employing strong encryption protocols, and practicing good online hygiene, you can enjoy a safe and secure browsing experience.
High-Speed VPN Service
A high-speed VPN service is a valuable tool for individuals and businesses looking to secure their online activities and data. VPN stands for Virtual Private Network, which creates a secure and encrypted connection between your device and the internet. The primary benefit of using a high-speed VPN service is that it provides an extra layer of security and privacy protection, especially when using public Wi-Fi networks.
One of the key features of a high-speed VPN service is its ability to encrypt your internet traffic, making it virtually impossible for hackers or third parties to intercept and access your sensitive information. This is particularly important for individuals who regularly handle confidential data or conduct online transactions.
Furthermore, a high-speed VPN service allows users to bypass geographical restrictions and access region-locked content such as streaming services, websites, and online platforms. By connecting to a server in a different location, users can enjoy unrestricted access to their favorite content, regardless of their physical location.
In addition to security and access benefits, a high-speed VPN service can also improve internet speed and performance for users. By routing your internet traffic through optimized servers, VPN services can help reduce latency and improve connection speeds, resulting in a smoother online experience.
Overall, investing in a high-speed VPN service is a practical decision for anyone looking to enhance their online security, privacy, and browsing experience. With the increasing prevalence of cyber threats and restrictions, a VPN service can provide peace of mind and unrestricted access to the vast online world.
VPN Bandwidth Optimization
Title: Maximizing VPN Bandwidth: Tips for Optimal Performance
In today's digital landscape, VPNs (Virtual Private Networks) have become indispensable tools for ensuring online privacy and security. Whether you're accessing sensitive information or simply browsing the web, a VPN can encrypt your internet connection, safeguarding your data from prying eyes. However, one common concern among VPN users is the potential impact on internet speed and bandwidth. Fortunately, there are several strategies you can employ to optimize your VPN bandwidth and maintain a smooth online experience.
First and foremost, selecting the right VPN provider is crucial. Look for providers with a reputation for high-speed connections and minimal latency. Additionally, choose a server location that's geographically close to your physical location to minimize latency and improve speed.
Another effective way to optimize VPN bandwidth is to use lightweight protocols. While protocols like OpenVPN offer robust security, they can sometimes be resource-intensive, leading to slower speeds. Consider using protocols like WireGuard or IKEv2, which prioritize speed without compromising security.
Furthermore, regularly updating your VPN client can help improve performance. VPN providers often release updates to address bugs, enhance security, and optimize speed. By keeping your client software up to date, you can take advantage of these improvements and ensure optimal performance.
Additionally, limiting background processes and applications can help reduce bandwidth usage and improve VPN speed. Close any unnecessary programs running in the background and prioritize bandwidth-intensive tasks while using the VPN.
Finally, consider upgrading your internet connection if you frequently experience slow VPN speeds. A faster internet connection can significantly improve VPN performance, especially when streaming HD content or downloading large files.
By implementing these strategies, you can maximize your VPN bandwidth and enjoy a seamless online experience without sacrificing security or privacy. With the right approach, you can harness the power of VPNs while maintaining optimal internet speeds.
Fast VPN Protocol
A Fast VPN Protocol is an essential component of any high-performing virtual private network service. A VPN protocol is essentially a set of rules and specifications that dictate how data is transmitted and protected within the VPN network. The protocol plays a crucial role in ensuring the security, speed, and reliability of the VPN connection.
When it comes to fast VPN protocols, there are several options available, each with its strengths and weaknesses. One of the most popular fast VPN protocols is OpenVPN, known for its robust security features and reliable performance. OpenVPN utilizes SSL/TLS protocols to establish an encrypted connection, making it a secure option for users looking to protect their online privacy.
Another fast VPN protocol worth mentioning is WireGuard, which is gaining popularity for its lightning-fast speed and efficiency. WireGuard is known for its simplicity and has been designed with performance in mind, making it an excellent choice for users who prioritize speed without compromising security.
IPSec/IKEv2 is another fast VPN protocol that offers excellent security features and stable performance. This protocol is often used on mobile devices due to its ability to quickly re-establish a connection when switching between networks, making it ideal for users on the go.
In conclusion, choosing the right fast VPN protocol is crucial to ensure a secure and high-speed connection. Whether you prioritize security, speed, or both, there are options available to meet your needs and enhance your online experience. It is recommended to consider your specific requirements and preferences when selecting a VPN protocol to enjoy a fast and secure browsing experience.
0 notes