#how to hack whatsapp group in mobile
Explore tagged Tumblr posts
Text
How to Spy Whatsapp Girlfriend's Phone Without Touching it 2024

Exploring 2024's Leading WhatsApp Monitoring Solution:
How to Monitor Without Physical Access Unlocking WhatsApp via Phone Number in 2024
Spying on WhatsApp Messages ->
WhatsApp, a globally recognized messaging platform, has gained immense popularity, leading to increased interest from parents, employers, and individuals for various reasons. In response to this demand, practical solutions in the form of WhatsApp monitoring applications have emerged. Despite WhatsApp's robust security measures, the potential for surveillance remains. SpyDm provides a means of remotely and discreetly monitoring someone's WhatsApp activities. Dive into this article to explore these tools and identify the most effective option!
Remotely Monitoring WhatsApp Messages: A Step-by-Step Guide The use of spy apps enables remote monitoring of WhatsApp messages, designed to observe and track activities on the target device, often without the owner's knowledge or consent.
Enter the SpyDm service, offering the capability to spy remotely without alerting the victim. No passwords or private account details are required for the spying process, ensuring the target remains unaware of the monitoring tool.
Upon accessing the site, the interface prompts you to choose the victim's country and enter their phone number. Select the specific content you want to monitor—text, images, or videos.
Verification takes just 2 minutes; opt for the free option and proceed.
Upon completing the verification process, you will be redirected to the victim's WhatsApp messages.
A comprehensive contact list will be displayed, featuring individuals recently messaged on WhatsApp—both sent and received messages.
Select a WhatsApp contact to view their direct messages.
Important Note: It is crucial to emphasize that the use of this tool is not endorsed. The presentation of the SpyDm tool is for educational purposes only. The responsibility lies with individuals to refrain from abusing this hacking method.
As of 2023, the SpyDm Software is reported to be functional; however, it may face potential removal for obvious reasons. It is crucial to approach such tools responsibly and ethically, respecting privacy and legal boundaries.
#how to spy whatsapp girlfriend's phone without touching it 2024#how to spy whatsapp 2023#how to spy whatsapp messages without touching phone#how to spy whatsapp girlfriend's phone#how to spy whatsapp girlfriend's phone without touching it for free#how to hack whatsapp with phone number 2023#how to hack whatsapp messages without touching phone#how to hack whatsapp with termux 2023#how to hack whatsapp account only number 2024#how to hack whatsapp group in mobile
2 notes
·
View notes
Text
At first, the F.B.I. and other investigators believed that China’s hackers used stolen passwords to focus mostly on the system that taps telephone conversations and texts under court orders. It is administered by a number of the nation’s telecommunications firms, including the three largest — Verizon, AT&T and T-Mobile. But in recent days, investigators have discovered how deeply China’s hackers had moved throughout the country by exploiting aging equipment and seams in the networks connecting disparate systems. [...] But the Chinese activity in the past year has taken these intrusions to a new level, Mr. Warner said on Thursday. “This is far and away the most serious telecom hack in our history,” he said. “This makes Colonial Pipeline and SolarWinds look like small potatoes.” He said that only in the past week had it become clear that “every major provider has been broken into.” The hackers were not able to listen to conversations on encrypted applications, like those carried over WhatsApp or Signal. Nor could they read encrypted messages, such as those sent from one iPhone to another over Apple’s iMessage system. But they could read regular text messages between an iPhone and an Android phone, for example, or listen to phone calls over the ordinary telephone networks, much as the government can if it has a legal order. The Chinese went after the conversations of national security officials, politicians and some of their staff, investigators have concluded. There may have been several Chinese groups at work, said a senior official involved in the investigation, who noted that one of them might have focused on Mr. Trump and Mr. Vance.
How nice of the US government to provide a convenient method for it to be spied on
83 notes
·
View notes
Text
The United States telecom giant AT&T disclosed a breach in July involving call and text messaging logs from six months in 2022 of “nearly all” its more than 100 million customers. In addition to exposing personal communication details for a slew of individual Americans, though, the FBI has been on alert that its agents’ call and text records were also included in the breach. A document seen and first reported by Bloomberg indicates that the bureau has been scrambling to mitigate any potential fallout that could lead to revelations about the identities of anonymous sources connected to investigations.
The breached data didn't include the content of calls and texts, but Bloomberg reports that it would have shown communication logs for agents' mobile numbers and other phone numbers they used during the six months period. It is unclear how widely the stolen data has spread, if at all. WIRED reported in July that after the hackers attempted to extort AT&T, the company paid $370,000 in an attempt to have the data trove deleted. In December, US investigators charged and arrested a suspect who reportedly was behind the entity that threatened to leak the stolen data.
The FBI tells WIRED in a statement: “The FBI continually adapts our operational and security practices as physical and digital threats evolve. The FBI has a solemn responsibility to protect the identity and safety of confidential human sources, who provide information every day that keeps the American people safe, often at risk to themselves.”
AT&T spokesperson Alex Byers says in a statement that the company “worked closely with law enforcement to mitigate impact to government operations” and appreciates the “thorough investigation” they conducted. “Given the increasing threat from cybercriminals and nation-state actors, we continue to increase investments in security as well as monitor and remediate our networks,” Byers adds.
The situation is surfacing amid ongoing revelations about a different hacking campaign perpetrated by China's Salt Typhoon espionage group, which compromised a slew of US telecoms, including AT&T. This separate situation exposed call and text logs for a smaller group of specific high-profile targets, and in some cases included recordings as well as information like location data.
As the US government has scrambled to respond, one recommendation from the FBI and the Cybersecurity and Infrastructure Security Agency has been for Americans to use end-to-end encrypted platforms—like Signal or WhatsApp—to communicate. Signal in particular stores almost no metadata about its customers and would not reveal which accounts have communicated with each other if it were breached. The suggestion was sound advice from a privacy perspective, but was very surprising given the US Justice Department's historic opposition to the use of end-to-end encryption. If the FBI has been grappling with the possibility that its own informants may have been exposed by a recent telecom breach, though, the about-face makes more sense.
If agents were following protocol for investigative communications strictly, though, the stolen AT&T call and text logs shouldn't pose a big threat, says former NSA hacker and Hunter Strategy vice president of research Jake Williams. Standard operating procedure should be designed to account for the possibility that call logs could be compromised, he says, and should require agents to communicate with sensitive sources using phone numbers that have never been linked to them or the US government. The FBI could be warning about the AT&T breach out of an abundance of caution, Williams says, or it may have discovered that agents' mistakes and protocol errors were captured in the stolen data. “This wouldn't be a counterintelligence issue unless someone was not following procedure,” he says.
Williams adds, too, that while the Salt Typhoon campaigns are only known to have impacted a relatively small group of people, they affected many telecoms, and the full impact of those breaches still may not be known.
“I worry about the FBI sources who might have been affected by this AT&T exposure, but more broadly the public still doesn't have a full understanding of the fallout of the Salt Typhoon campaigns,” Williams says. “And it seems that the US government is still working on getting a grasp of that as well.”
0 notes
Text
Best Cell Phone Hack for Monitoring Your Partner - 2024
In today's digital age, trust and transparency in relationships are more important than ever. However, doubts and uncertainties can sometimes creep in, leading to a desire for reassurance. One controversial yet increasingly discussed method is using cell phone hacking to monitor your partner's activities. This article explores the best cell phone hacks for 2024, focusing on techniques, tools, and services like HackersList, known for providing top-tier cell phone hacking services worldwide.

What is Cell Phone Hacking?
Cell phone hacking refers to the process of gaining unauthorized access to someone’s mobile device. This can involve extracting data, intercepting communications, and even manipulating the device's functionalities without the owner's knowledge. While hacking has a notorious reputation, it's worth noting that it can be used for various purposes, including cybersecurity, parental control, and, as discussed here, monitoring a partner.
How Mobile Phone Hacking
Mobile phone hacking involves exploiting vulnerabilities in the phone’s operating system or installed applications. Hackers can gain access to personal information, track location, and even listen to conversations. Popular methods include:
Phishing: Deceptive emails or messages tricking users into revealing their passwords.
Spyware: Malicious software installed on a device to monitor activities.
Network Attacks: Intercepting data over unsecured networks.
How to Mobile to Mobile Hack
Mobile-to-mobile hacking refers to accessing one mobile device through another. This often involves using specialized software that can be installed on the target device through a text message, email, or direct physical access. Here’s a basic outline of how it works:
Choose the Right Software: There are various software options available, like mSpy and FlexiSPY, designed for mobile monitoring.
Install the Software: The software needs to be installed on the target device, which might require temporary physical access.
Monitor the Device: Once installed, you can monitor the target device remotely from your own phone.
Hacking Mobile Networks
Mobile network hacking involves intercepting data as it is transmitted over cellular networks. This can be done through techniques like:
Man-in-the-Middle Attacks: Intercepting communications between two parties.
Rogue Access Points: Setting up fake Wi-Fi hotspots to capture data.
SS7 Exploitation: Exploiting vulnerabilities in the Signaling System 7 (SS7) protocol used in cellular networks.
These methods require a higher level of technical expertise and are often used by more advanced hackers.
Best Cell Phone Hackers
Cell Phone hackers are individuals or groups with the skills to infiltrate mobile devices. While some work independently, others might be part of larger organizations or offer their services through platforms like HackersList. HackersList is renowned for providing top-tier cell phone hacking services, connecting clients with professional hackers capable of discreetly monitoring mobile devices. Connect with expert by posting new job
Cell Phone Hack Help to SMS Hack
Related: Cheating Husband Cell Phone Spy App for Read Secret Message
One of the most sought-after features in mobile hacking is the ability to intercept and read SMS messages. This can provide insights into the target’s communications. Tools like HackersList are popular for SMS hacking, allowing users to:
Read Sent and Received Messages: View all SMS communications.
Access Deleted Messages: Retrieve messages that have been deleted.
Monitor Messaging Apps: Track messages from apps like WhatsApp, Facebook Messenger, and more.
Hacking Someone’s Cell Phone
Hacking someone's cell phone involves several steps and considerations. Here’s a simplified guide:
Choose a Reliable Service or Tool: Services like HackersList offer professional hacking services that ensure discretion and efficiency.
Install Monitoring Software: Physical access to the target phone is often required for initial installation.
Monitor Activities: Once installed, you can remotely monitor calls, messages, location, and other activities.
Hack Cell Phone Number
Hacking a cell phone number can provide access to various forms of communication and personal information. Techniques include:
SIM Swapping: Gaining control of the target’s phone number by manipulating the mobile carrier.
Phishing: Tricking the user into revealing their number and associated accounts.
Social Engineering: Using psychological manipulation to gain information.
Hack Mobile Camera
Hacking a mobile camera can provide visual access to the target’s surroundings. This is typically done through spyware that activates the camera without the user’s knowledge. Tools like FlexiSPY offer this functionality, allowing the hacker to:
Take Photos Remotely: Capture images from the target’s camera.
Record Videos: Activate the video recording feature.
Stream Live Video: View live footage from the target’s camera.
Android Cell Phone Hacks
Android devices are particularly susceptible to certain types of hacks due to their open-source nature. Popular hacks include:
Rooting: Gaining superuser access to the device, allowing for extensive control.
Spyware: Installing apps that monitor activities without the user’s knowledge.
Exploiting Vulnerabilities: Taking advantage of security flaws in the Android OS.
Cell Phone Cloned
Cloning a cell phone involves creating an exact replica of the target phone’s data on another device. This allows the hacker to intercept calls, messages, and other communications. Methods include:
SIM Cloning: Duplicating the SIM card to intercept communications.
Phone Cloning Software: Using software to copy the phone’s data.
All Mobile Hack
“All mobile hack” refers to tools and techniques that can be used across different mobile platforms, including Android and iOS. Universal hacking tools like HackersList are designed to work on multiple devices, providing comprehensive monitoring capabilities regardless of the operating system.
Conclusion
Cell phone hacking, while controversial, offers a means to gain insights and reassurance in relationships. With advances in technology, methods have become more sophisticated and accessible. Services like HackersList provide professional hacking solutions, ensuring discretion and effectiveness. Whether it's intercepting SMS messages, hacking mobile networks, or accessing the mobile camera, these tools and techniques offer a comprehensive way to monitor your partner's activities. However, it's crucial to weigh the ethical implications and legal considerations before embarking on this path.
#best cell phone hack#cell phone hacks#cell phone hack#cell phone hacker#cell phone hacking#mobile hacker#mobile hacks#hackerslist
0 notes
Text
Best Cell Phone Hack for Monitoring Your Partner - 2024
In today's digital age, trust and transparency in relationships are more important than ever. However, doubts and uncertainties can sometimes creep in, leading to a desire for reassurance. One controversial yet increasingly discussed method is using cell phone hacking to monitor your partner's activities. This article explores the best cell phone hacks for 2024, focusing on techniques, tools, and services like HackersList, known for providing top-tier cell phone hacking services worldwide.

What is Cell Phone Hacking?
Cell phone hacking refers to the process of gaining unauthorized access to someone’s mobile device. This can involve extracting data, intercepting communications, and even manipulating the device's functionalities without the owner's knowledge. While hacking has a notorious reputation, it's worth noting that it can be used for various purposes, including cybersecurity, parental control, and, as discussed here, monitoring a partner.
How Mobile Phone Hacking
Mobile phone hacking involves exploiting vulnerabilities in the phone’s operating system or installed applications. Hackers can gain access to personal information, track location, and even listen to conversations. Popular methods include:
Phishing: Deceptive emails or messages tricking users into revealing their passwords.
Spyware: Malicious software installed on a device to monitor activities.
Network Attacks: Intercepting data over unsecured networks.
How to Mobile to Mobile Hack
Mobile-to-mobile hacking refers to accessing one mobile device through another. This often involves using specialized software that can be installed on the target device through a text message, email, or direct physical access. Here’s a basic outline of how it works:
Choose the Right Software: There are various software options available, like mSpy and FlexiSPY, designed for mobile monitoring.
Install the Software: The software needs to be installed on the target device, which might require temporary physical access.
Monitor the Device: Once installed, you can monitor the target device remotely from your own phone.
Hacking Mobile Networks
Mobile network hacking involves intercepting data as it is transmitted over cellular networks. This can be done through techniques like:
Man-in-the-Middle Attacks: Intercepting communications between two parties.
Rogue Access Points: Setting up fake Wi-Fi hotspots to capture data.
SS7 Exploitation: Exploiting vulnerabilities in the Signaling System 7 (SS7) protocol used in cellular networks.
These methods require a higher level of technical expertise and are often used by more advanced hackers.
Best Cell Phone Hackers
Cell Phone hackers are individuals or groups with the skills to infiltrate mobile devices. While some work independently, others might be part of larger organizations or offer their services through platforms like HackersList. HackersList is renowned for providing top-tier cell phone hacking services, connecting clients with professional hackers capable of discreetly monitoring mobile devices. Connect with expert by posting new job
Cell Phone Hack Help to SMS Hack
Related: Cheating Husband Cell Phone Spy App for Read Secret Message
One of the most sought-after features in mobile hacking is the ability to intercept and read SMS messages. This can provide insights into the target’s communications. Tools like HackersList are popular for SMS hacking, allowing users to:
Read Sent and Received Messages: View all SMS communications.
Access Deleted Messages: Retrieve messages that have been deleted.
Monitor Messaging Apps: Track messages from apps like WhatsApp, Facebook Messenger, and more.
Hacking Someone’s Cell Phone
Hacking someone's cell phone involves several steps and considerations. Here’s a simplified guide:
Choose a Reliable Service or Tool: Services like HackersList offer professional hacking services that ensure discretion and efficiency.
Install Monitoring Software: Physical access to the target phone is often required for initial installation.
Monitor Activities: Once installed, you can remotely monitor calls, messages, location, and other activities.
Hack Cell Phone Number
Hacking a cell phone number can provide access to various forms of communication and personal information. Techniques include:
SIM Swapping: Gaining control of the target’s phone number by manipulating the mobile carrier.
Phishing: Tricking the user into revealing their number and associated accounts.
Social Engineering: Using psychological manipulation to gain information.
Hack Mobile Camera
Hacking a mobile camera can provide visual access to the target’s surroundings. This is typically done through spyware that activates the camera without the user’s knowledge. Tools like FlexiSPY offer this functionality, allowing the hacker to:
Take Photos Remotely: Capture images from the target’s camera.
Record Videos: Activate the video recording feature.
Stream Live Video: View live footage from the target’s camera.
Android Cell Phone Hacks
Android devices are particularly susceptible to certain types of hacks due to their open-source nature. Popular hacks include:
Rooting: Gaining superuser access to the device, allowing for extensive control.
Spyware: Installing apps that monitor activities without the user’s knowledge.
Exploiting Vulnerabilities: Taking advantage of security flaws in the Android OS.
Cell Phone Cloned
Cloning a cell phone involves creating an exact replica of the target phone’s data on another device. This allows the hacker to intercept calls, messages, and other communications. Methods include:
SIM Cloning: Duplicating the SIM card to intercept communications.
Phone Cloning Software: Using software to copy the phone’s data.
All Mobile Hack
“All mobile hack” refers to tools and techniques that can be used across different mobile platforms, including Android and iOS. Universal hacking tools like HackersList are designed to work on multiple devices, providing comprehensive monitoring capabilities regardless of the operating system.
Conclusion
Cell phone hacking, while controversial, offers a means to gain insights and reassurance in relationships. With advances in technology, methods have become more sophisticated and accessible. Services like HackersList provide professional hacking solutions, ensuring discretion and effectiveness. Whether it's intercepting SMS messages, hacking mobile networks, or accessing the mobile camera, these tools and techniques offer a comprehensive way to monitor your partner's activities. However, it's crucial to weigh the ethical implications and legal considerations before embarking on this path.
#cell phone hack#cell phone hacker#cell phone hacking#cell phone hacked#mobile hacker#mobile hacking#hackerslist
0 notes
Text
Cyberbullying and Mental Health: Protecting Loved Ones in the Digital Age

Today, we are living in a highly driven digital world where technology and social media go hand-in-hand. The age group that is highly influenced by social media today is the young children. These social media platforms are a great way to connect with friends and family but also have certain drawbacks. The most troublesome thing about social media is the anonymity it gives to people who have bad intentions.
Cyberbullying has become an everyday activity for these people who are active on platforms like Instagram, Facebook, WhatsApp, and more. They are well aware that children are fond of these apps and they are the ones who spend most of their time scrolling through them. It is easier for the cyberbullies to target young kids so that they can scam them by hacking their phones and looting their money.
We understand that anyone can be a victim of such an act but kids especially can be the easy targets, that’s why it is important that you as a parent keep them safe against any such situation as this can have serious consequences on their mental health.
Cyberbullying & kids
Cyberbullying is the new-age and electronic way to bully or harass others. There is no concrete reason as to why they do so. They can think of it as a fun activity, or to hack other people’s accounts, or their phones to take out their money. Cyberbullying can happen anytime and from anywhere. Sometimes, the bully simply wants to spread rumors, post hateful things just to play with a person’s emotions and god forbid if it is kids who are at the receiving end then things can get even worse.
There is significantly no escape from it when we talk about cyberbullying because once the information is in public domain then it has the tendency to reach masses at once and this can trigger a child’s emotional and mental health. To avoid any such situation, using hidden spy apps in the digital age can be helpful. These apps give parents the freedom to know what their child is up to and if they need their attention and guidance.
Prevent cyberbullying with spy apps
We know that you must be aware of the importance of communication with your loved ones when you want to ensure that they are safe and everything is going on fine in their life and having open communication gives more clarity and creates more room for a safe space where you can comfortably share your thoughts and views with each other. You may not be aware but you can definitely prevent cyberbullying with spy apps. These apps come loaded with a lot of features that can add value to the way you raise your children. You can spy and keep track of everything that they do that too remotely and keep them safe against all types of online threats. The features of a phone spy app are so useful that in some cases, you can benefit from them in the real world as well.
The hidden spy apps come with features like hidden call recorder, WhatsApp spy, social media monitoring and much more. The hidden call recorder lets you to listen to your child’s phone conversations remotely. The recordings are saved on the server from where you can access them and if you think that any specific person is being a threat to your child then you can block their number and report about them to the legal authorities too with proof.
Similarly, WhatsApp spy is another useful feature with the help of which you can read your child’s chats, you can view the media that they send and receive, the links and documents they exchange with their contacts. All this information can play a vital role in understanding the pattern and behavior of your child’s online activity. They may not realize but what information they share with others can impact their overall wellbeing.
Another important feature is social media monitoring. We all know how important Facebook, Instagram and similar apps are for today’s kids. By using a mobile spy app, you can track every activity they perform on these apps and see if they need your attention. No matter even if they have a private account, with a social media spy app, you can know about everything they do on their profile and the people and the type of content they engage with.
One of the most crucial features that every parent looks for before signing up to a spy app is the location tracker. The live-location tracker can let you know where your child is and that’s why it is important to sign up to a good spy app so that you can get accurate and real time information.
In The End
Cyberbullying is a serious issue and it can have a very strong impact on young minds. Technology will always continue to be evolving but it is crucial that as parents and as responsible adults, you lead them by setting the right examples. Additionally, by creating a supportive and open environment for your children, you can protect them and also help them overcome any situation that seems to be difficult to move on from.
Spy apps are a valuable tool and by choosing the right spy app, you can ease the way you raise your children. Onemonitar is a great android spy app and offers more than 60 features. All these features are essential when we talk about digital parenting and can help in maintaining a healthy mental health state for kids as well as parents.
If you need to enquire more about the features, plans, performance of Onemonitar, you can check out their website where you will find all the features, package details, performance and the ways to connect with the spy app’s support team.
Well, whatever way you choose to monitor your loved ones, make sure it is reliable and accurate as this will play a crucial role in maintaining the privacy and sanity of the people you care about.
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy#whatsappspy#whatsappspyapp
1 note
·
View note
Text
How much does it cost to build an app like Signal?
A signal is a cross-stage talking application, created by Signal Innovation Establishment and Sign Courier LLC and established in 2014. This application empowers clients to do balanced and bunch messages and can share records, voice notes, pictures and recordings. Aside from that, there is no risk of account hacking or data breach when using the app for one-on-one or group audio and video calls.
The Signal application improvement cost range is subject to various elements. Like each portable application improvement quote, four key elements add to the general cost statement.
Also Read: Educational app development
What Are the Priority Features for Signal Like Application?
When creating a chat app like Signal, a number of features help with the process. While 80% of them are the same as any messaging platform, there are a few elements that make Signal special as every social networking app development companies would tell you.
Invite friends
When users open the Signal social media app, the first thing they see is a choice to invite friends and create a new group. Users are required to grant the app access to their contact book in order to use the option to "invite friends," which we consider to be an essential feature.
Real-time messaging
The real-time messaging feature is at the heart of the Signal app's features. With Signal, users can communicate with one another in real time from anywhere in the world without apparent concurrency issues.
Sharing features
By allowing users to share documents, contacts, media (images, videos, and GIFs), and location with their contacts or in a group, the Signal private messenger app makes sharing easier.
Also Read: Game development company in Bangalore
Video and in-app call
Today's messaging platforms must offer calls as a feature. While once limited to text messaging, today users are demanding the facility to make video and in-app calls to their contacts.
Notifications
The messaging apps industry does not have a difficult time coming up with a strategic push notification strategy. The application only has to show messages, call and missed call prompt, and when it’s time to back up the data. Signal, however, gives users the option to turn off lock screen notifications on their devices.
Privacy settings
Screen lock, incognito keyboard, and other privacy settings are included with the Signal chat app. Following WhatsApp's inability to give clients an assurance that their information will be gotten, protection settings like these are ready to turn into a high priority component of replies around how to make application like Signal.
End to end encryption
End to end encryption is one of the top ways to secure a mobile app. The open-source end to end encryption feature of Signal private messenger app makes it impossible for telecom companies, advertisers (Signal doesn’t allow advertisements in the app), and even Signal to read the chats and activities of users.
Despite the fact that these are some of the essential features for Signal secure messaging, such as application development, there are a number of other features that are built into Signal but are not available in other messaging apps. Some of those are Disappearing messages, Safety binary numbers that one can cross-check with their contact’s to ensure that there’s a complete end to end encryption, group chat with 8 users, and voice record functionality.
Also Read: Best Mobile App Development company in India
How much does it cost to develop Signal, a messaging app
The price range for developing a Signal app is determined by a number of factors. The overall price quote is influenced by four key factors, just like every cost estimate for developing a mobile app.
When discussing Signal in particular, imitating the same feature set will result in higher costs. Therefore, our recommendation is to develop an MVP messaging app and incorporate the encryption protocol into it. Along these lines, you will actually want to try things out prior to sending off an undeniable application.
Our social media app developers advise that entrepreneurs must first create a plan of features that they would like to have in the application. We can focus on the technological and resource capabilities based on the features, which will ultimately determine the cost of developing a social media app.
The most important factors when deciding whether or not to replicate an app are its popularity and development costs. When talking about Signal app development cost, the sum depends on various factors.
The expense of advancement of such applications can differ from USD 30,000 to USD 70,000.
Cost of Improvement of iOS Application: USD 40,000-USD 45,000
Cost of Advancement of Android Application: USD 45,000-USD 55,000
Then talking about the region of development,
South Asia: USD 25,000
Eastern Europe: USD 40,000
Australia: 70,000 USD
Western Europe: USD 65, 000
North America: USD 70,000.

0 notes
Text
Whatsapp Mobile Number List
Understanding the Controversy Surrounding WhatsApp Mobile Number Lists
In the era of digital communication, messaging apps have revolutionized the way we connect with friends, family, and colleagues. WhatsApp, owned by Facebook, stands out as one of the most popular and widely used messaging platforms, boasting over two billion users worldwide. However, recent concerns and controversies have arisen regarding the concept of WhatsApp mobile number lists. These lists, which contain contact information for multiple users, have raised questions about privacy, security, and the responsible use of personal data.
What Are WhatsApp Mobile Number Lists?
WhatsApp mobile number lists are collections of phone numbers associated with WhatsApp accounts. These lists can be curated for various purposes, such as creating contact groups, broadcasting messages to multiple recipients, or simply keeping track of known contacts. The app itself allows users to save contacts, view their status updates, and exchange messages, photos, and videos seamlessly.
The trouble arises when these lists extend beyond personal use. Organizations and individuals with nefarious intentions could potentially misuse such lists for spamming, phishing, or even identity theft. This has led to concerns about the responsible management of WhatsApp mobile number lists and the potential consequences of their misuse.
Privacy and Security Concerns
The primary concern surrounding WhatsApp mobile number lists is the potential violation of privacy. When users share their phone numbers on WhatsApp, they expect a certain level of confidentiality. However, when these numbers are compiled into lists and shared without consent, individuals may find themselves subject to unwanted messages or even harassment.
Moreover, the security of such lists is also a critical issue. If a list falls into the wrong hands, it can become a valuable asset for cybercriminals. These criminals could use the information for various malicious purposes, including social engineering attacks, hacking attempts, or targeted scams. This potential misuse of personal data raises questions about how WhatsApp and its users can ensure the security of their contact information.
WhatsApp's Efforts to Address Concerns
In response to these concerns, WhatsApp has implemented several features aimed at mitigating the potential misuse of mobile number lists. One of these measures is the option to control who can add users to groups. By adjusting group privacy settings, users can limit their exposure to unwanted group invitations and ensure that their phone numbers remain private.
WhatsApp has also introduced end-to-end encryption, which ensures that messages and calls are only visible to the sender and recipient. This encryption adds an extra layer of security to communication, protecting users from unauthorized access and surveillance.
User Responsibility and Best Practices
While WhatsApp takes steps to enhance privacy and security, users also play a crucial role in safeguarding their information. Implementing best practices when sharing phone numbers and managing contacts can go a long way in preventing potential issues:
Limit Sharing: Be cautious about sharing your phone number on public platforms or with unknown individuals.
Group Invitation Settings: Adjust your group privacy settings to control who can add you to groups. This can prevent unwanted group messages and spam.
Regular Updates: Keep your WhatsApp app up to date to benefit from the latest security enhancements and features.
Report Suspicious Activity: If you encounter suspicious messages or activity, report it to WhatsApp and consider blocking the sender.
Educate Yourself: Stay informed about the latest privacy settings and security features that WhatsApp offers.
The Way Forward
WhatsApp mobile number lists can be a valuable tool for communication and organization, but their potential for misuse raises legitimate concerns. As users, it's essential to strike a balance between convenience and security by adopting responsible practices and staying informed about the app's features. Ultimately, a combination of user vigilance, technological advancements, and the commitment of platform providers like WhatsApp will contribute to a safer and more secure digital communication landscape.
0 notes
Text
What Are the Latest Strategies in Social Media Risk Management?
Beginning: There are always several risks associated with running and managing social media accounts on multiple social media platforms. It is evident from the fact that today there are many incidents of cyber-related threats to businesses and individuals. So, what can be done to curtail these risks and threats? Let us see more below.

What is Social Media Risk Management?
Social media risk management is a group of processes that ensure businesses keep control of their social media interactions. They may have, among other things, knowledge of who accesses their accounts, who allows them to publish posts or messages to consumers, and the basic rules for presenting their brand online. The main goal of social media risk management is to prevent unauthorized communication and misrepresentation of the brand via incorrect messaging.
What Types of Risks Are Associated with Social Media?
- Phishing attacks and scams: malicious third-party attempts to impersonate a brand and communicate with customers to get them to reveal sensitive personal information.
Ransomware: It is malware that uses encryption to force the attack target to pay a ransom demand.
- Imposter accounts. - Malware attacks and hacks. - Vulnerable third-party apps. - Identity and password theft. - Privacy settings and data security. - Unsecured mobile devices. - Malicious apps. - Service denial attacks. The Latest Modern Strategies in Social Media Risk Management - Stronger and more accountable social media use policies: the cause or success of most risks can be attributed to negligence and poor social media use policies. A good policy ensures accountability, honesty, and transparency. - Train and equip: It is good to train and equip users because they are the first line of defense in protecting all the data they access. Moreover, as a responsibility to protect brand identity and image, it is vital to ensure the creation of safe places for customers. This can be done by staying updated on all the latest risks and threats to social media accounts. These can vary across social platforms, from Facebook vulnerabilities to Twitter hacks; it is good to be informed on how personal actions can expose business safety. - Monitoring and tracking: With several social media accounts, it's good to ensure the creation of control to review all actions. This specifies who can access the accounts, what devices they use to login, the time spent, and what is searched. If the staff use personal computers or phones to access business social media accounts, it is better to buffer security on the devices or enhance access protocols. Oversight is vital for social media posts and direct messages from business social media teams. Ensuring post reviews before scheduling with protocols to answer messages received via social media are all critical. Conclusion: Today, exposure to online risks and threats costs businesses lots of revenue and reputational damage. Social media risks and threats are quite more complex today than they were before. It is estimated that there has been a great leap in the growth of social media security risks and threats. Social media risk management is a bulwark attempt at creating solutions to overcome the risks and threats. And stronger, more resilient, and more accountable tactics help businesses succeed and grow.
For More Info:-
WhatsApp Phone Recording App
Zoom Data Leak Management
0 notes
Text
Pluralistic: 11 Mar 2020 (Saturated fat and obesity, which foods produce satiety, spying VPNs, Twitter's research-friendly terms of service)

Today's links
Obesity and unsaturated fats: Blaming unsaturated fats for obesity is very plausible, but likely wrong, alas.
The satiety index: Which foods cause or satisfy cravings?
Sensor Tower's VPNs and adblockers spied on users: Like sneaking laxative into Immodium.
Twitter's new Terms of Service help academics: Good bots welcome.
Italy's "I Stay in the House" law: The comprehensive quarantine plan.
Scam-buster hacks into a scam-factory: He gets their CCTVs, recordings of their calls, transaction data, Whatsapp chats, and more. Delicious.
Postmortem: the catastrophic EU Copyright Directive. Testimony from yesterday's Senate hearing.
Podcast: A Lever Without a Fulcrum Is Just a Stick: My latest Locus column, on how copyright failed artists and enriched corporations.
This day in history: 2010, 2015, 2019
Colophon: Recent publications, current writing projects, upcoming appearances, current reading

Obesity and unsaturated fats (permalink)
Scott Alexander does a very deep dive into the literature on diet, weight, and saturated vs unsaturated fats.
https://slatestarcodex.com/2020/03/10/for-then-against-high-saturated-fat-diets/
The most important elements for me were first, the validation that something really has changed: average US adult men's weight went from 155lbs to 195lbs from the 1800s to today. The 90th percentile 1800s man weighed 185lbs, today, it's 320lbs. US obesity rates in the 1800s were 1%. Today, they're 25%.
But the usual culprits can't explain the change: they ate more bread and potatoes in the 1800s, for one thing.
In China, obesity rates were very low even with a diet dominated by white rice.
1970s France had 1800s US obesity rates, on a diet of "baguettes, pastries, cheese, meat. Lots of sugar, white flour, and fat."
It's true that some tactics (intermittent fasting, low-carbing) work for some people, but they're not what worked in 1970s France or 1800s USA. So if those things work, they're "hacks" – not an indictment of carbs or eating three meals a day.
There's a widespread theory that the change is driven by the switch from saturated to unsaturated fats, which was driven by spiking heart disease in the 1950s. It's likely this heart disease epidemic can be attributed to the vast increase in smoking a couple decades earlier, but the tobacco industry's denial machine meant that the blame fell on diet, and the US (and then global) diet's fat composition shifted dramatically.
We ate a lot fewer animal-derived fats and a lot more plant-derived fats. These fats had lots more Omega 6s and (to a lesser extent) 3s, and the ratio of these Omegas also changed dramatically, both in our diet and in our bodily composition. Intriguingly, these play a significant role in metabolism. There's a plausible ring to this whole business – particularly as a way of crisping up what we mean when we say "avoid processed foods." What is "processing?" Maybe it's doing something that requires vegetable fats.
Unfortunately, neither the literature nor the lived experience of experimenters support the theory. Studies don't support it. Meta analyses don't support it. Reddit forums skew heavily to people saying it didn't work for them (dotted with people for whom it did).
Which makes weight gain a mystery. It can't be (just) exercise: we're exercising more now than we did 40 years ago, and we're heavier now. Studies about causes are inconclusive overall, but clear that weight gain is more explained by diet than exercise. What's more, we're seeing weight gain in lab rats, pets and feral animals, so exercise seems an unlikely culprit here.
Alexander ponders other possible causes: plastics or other contaminants in our diet, or that it's a "ratchet" (once your weight set point changes, it doesn't change back.). Both have little evidence to support them.
He concludes that he's "more confused than when I started it," but will avoid unsaturated fats where possible, with the exceptions of Omega-3 rich oils (fish/olive oil).
I am likewise confused, but also better-informed than I was before I read his post.

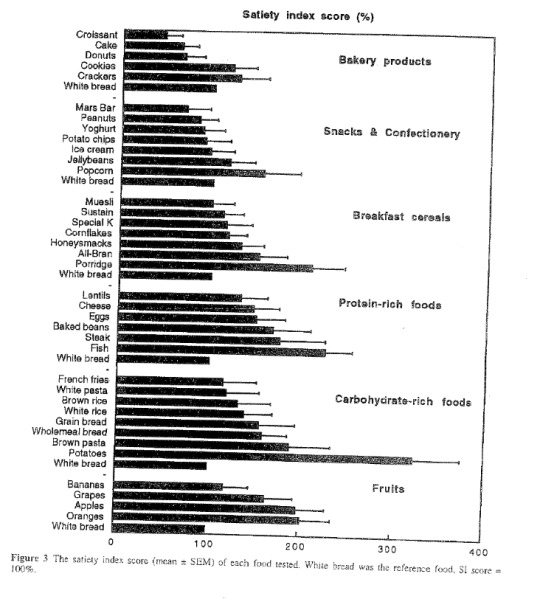
The satiety index (permalink)
I lost ~100lbs in 2002/3 with a low-carb diet. The thing I immediately noticed when I started eating (lots) more fat and (lots) less carbs was that I was always satiated, with none of the food cravings that had plagued me all my life.
No other diet since has had that effect. I really struggle with cravings (and have put 50lbs back on through my 40s, though some of that is muscle from a much higher level of exercise). For me, satiety is the barrier to sticking to any diet. I don't just get ravenous, I get these all-consuming cravings that I can't put out of my mind, even if I resist them (and the longer I resist, the more likely it is that I'll really blow it out when I give in at last).
So I was really interested in this 1995 open access study, "A Satiety Index of common foods," which offers a league table of the foods that made subjects feel full.
https://www.researchgate.net/publication/15701207_A_Satiety_Index_of_common_foods
The meaty (heh) parts are in these charts on pp682-3.

Sensor Tower's VPNs and adblockers spied on users (permalink)
Sensor Tower, a company that made apps billed as privacy-protecting, installed man-in-the-middle certificates on your devices that let them spy on everything you did online.
https://www.buzzfeednews.com/article/craigsilverman/vpn-and-ad-blocking-apps-sensor-tower
They made 20+ VPN apps for Android and Ios, but didn't disclose that all those apps were owned by analytics company, Sensor Tower. The apps had names like "Free and Unlimited VPN, Luna VPN, Mobile Data, and Adblock Focus."
The apps installed a "root certificate" in users' devices. With this cert, the company could insert itself in all the device's otherwise secure, encrypted sessions – web browsing, email, etc. Sensor Tower admits that they collected data using this cert, but insists that it was "anonymized," which is something most computer scientists agree is likely impossible for this kind of data. Re-identification of anonymized data is devilishly hard to avoid.
The claim is made even less credible when you listen to the company's other claims about its practices, such as the idea that they hid the authorship of their apps "for competitive reasons."
Or this howler: that "the vast majority of these apps listed are now defunct (inactive) and a few are in the process of sunsetting." Well, yes, they were removed for violating their users' privacy. It's not like the company had a change of heart or anything.
And then there's this: "Apple and Google restrict root certificate privileges due to the security risk to users. Sensor Tower's apps bypass the restrictions by prompting users to install a certificate through an external website after an app is downloaded."
Twitter's new Terms of Service help academics(permalink)
Twitter just published a new, and much-improved developer policy, one that permits academics to field bots for research and auditing purposes.
https://blog.twitter.com/developer/en_us/topics/community/2020/twitter_developer_policy_update.html
"Researchers will be able to share an unlimited number of Tweet IDs and/or User IDs, if they're doing so on behalf of an academic institution and for the sole purpose of non-commercial research, such as peer review."
https://techcrunch.com/2020/03/10/twitter-rewrites-developer-policy-to-better-support-academic-research-and-use-of-good-bots/
Twitter's also creating a bot registry that must include contact info for the botmaster, so that "it's easier for everyone on Twitter to know what's a bot – and what's not."
https://developer.twitter.com/en/developer-terms/policy#4-b
Italy's "I Stay in the House" law (permalink)
The FAQ for the Italian government's "I Stay In the House" decree is a fascinating document:
http://www.governo.it/it/articolo/decreto-iorestoacasa-domande-frequenti-sulle-misure-adottate-dal-governo/14278
Most notably, Italy has kicked out its tourists. As Bruce Sterling writes, "It's a tourist-ectomy. An Italy devoid of all tourists. It's fantastic, unheard-of. Surely this hasn't happened in at least 700 years."
https://www.wired.com/beyond-the-beyond/2020/03/stay-house-decree/
People are allowed to go to work, to shop, and to run errands, provided it is for an "essential purpose," which you must prove "by means of a self-declaration which can be made on pre-printed forms already supplied to the state and local police forces. The veracity of the self-declarations will be subject to subsequent checks and the non-veracity constitutes a crime."
Business travelers are permitted to enter and leave the country, cab, delivery and freight drivers are allowed to do their jobs, and "outdoor motor activity is allowed as long as not in a group."
Public offices are open. Training activities are suspended. Government offices need to provide hand santizer, but if they run out, they have to stay open ("disinfectant is a precautionary measure but itstemporary unavailability does not justify the closure of the office").
Bars, pubs and restaurants may open from 6AM to 6PM, but have to cancel live music, games and screening events. Theaters, cinemas and museums are closed.
Schools are closed. Universities are closed. Exams and graduations will be conducted by video-link. Med schools are not closed. Research institutions are not closed.
Masses and funerals are canceled. Islamic Friday prayers are canceled.
Farms are open.

Scam-buster hacks into a scam-factory (permalink)
Jim Browning is a talented and prolific scambaiter. He calls the numbers listed in pop-up tech support scams and has the scammers log into a specially prepared system that lets him trace them.
In his latest adventure, Browning thoroughly turns the tables on http://Faremart.com , a Delhi travel agency that was the front for a sprawling network of tech-support scammers taking in millions every year through fraud.
Browning not only traces the scammers: he breaks into their unsecured CCTV network so he can watch them work. He compromises their phone system and listens to the recordings of all their scam-sessions.
https://www.youtube.com/watch?v=le71yVPh4uk
He gets hold of their ledgers, which list how much money each scam nets for the gang. He doxes the scammers and learns their real names. He gets a confederate to fly a drone over their HQ and maps out their comings and going.
In part II, Browning treats us to a delightful scambaiting session in which he mercilessly trolls a scammer who claims to be in San Jose, CA, tripping him up in a series of ever-more-desperate lies.
https://www.youtube.com/watch?v=uV-qa9M-o4E
It's part of a growing genre of journalists who explore and document the operations of overseas scam operations. See, for example, Reply All's excellent podcasts on this:
https://gimletmedia.com/shows/reply-all/6nh3wk https://gimletmedia.com/shows/reply-all/76h5gl
There are two more parts to come in Browning's series (you can watch them now on his Patreon, apparently):
https://www.patreon.com/JimBrowning
He also turned his footage over to the BBC's flagship investigative programme, Panorama, which has produced its own doc based on it:
https://www.youtube.com/watch?v=7rmvhwwiQAY

Postmortem: the catastrophic EU Copyright Directive (postmortem)
Yesterday, the Senate Subcommittee on Intellectual Property held hearings on "Copyright Law in Foreign Jurisdictions," at which two key copyright experts testified on last year's catastrophic EU Copyright Directive.
First up was Pam Samuelson, one of America's leading copyright experts, who explained in eye-watering detail how the compromises made to pass the Copyright Directive produced an incoherent mess that no one can figure out how to implement in law.
https://www.judiciary.senate.gov/imo/media/doc/Samuelson%20Testimony.pdf
Next was Julia Reda, who served in the EU Parliament during the passage of the directive and helped spearhead the opposition to it.
Her testimony really shows you where the bodies were buried: how the EU knew it was making a pig's ear out of things.
https://www.judiciary.senate.gov/imo/media/doc/Reda%20Testimony.pdf
Both are essential reading for anyone striving to understand Article 17 (formerly Article 13) – it is such a tangle of garbage lawmaking that these kinds of guides are indispensable.

Podcast: A Lever Without a Fulcrum Is Just a Stick (permalink)
I've just posted my latest podcast: a reading of my new Locus Magazine column, "A Lever Without a Fulcrum Is Just a Stick," on how copyright failed artists and enriched corporations and what we can do about it.
https://craphound.com/podcast/2020/03/11/a-lever-without-a-fulcrum-is-just-a-stick-2/
Tldr: Giving monopolies to artists doesn't help them gain leverage over the super-concentrated entertainment industry, because the corporations control access to audiences and force artists to sign away those monopolies to get past their gatekeeping.
The more monopolies we give artists, the more monopolies are transfered to corporations, and the more they dominate the market and thus the more they can retain from the earnings generated by the artists' works.
Fights like the EU Copyright Directive are a distraction, a fight over shifting some points from Big Tech's balance sheet to Big Content's – but without any mechanism to move more of that revenue to creators.
Enriching creators means thinking beyond more "monopoly"-style copyright: instead, we have to think about inalienable rights that can be taken away through one-sided contracts (like the "reversion right" that lets US artists take back copyrights after 35 years).
And we have to think beyond copyright itself, by beefing up competition laws to break up entertainment cartels, and by beefing up labor laws to let artists form unions.
There is a role for copyright, but in things like extended collective licensing that would allow all online platforms to access the same catalog and pay for it based on the number of users they have, so a new platform pays pennies while Youtube pays hundreds of millions.
These blanket licenses have been key to keeping other forums for artistic revenues open: think of what the world would be like if one club or radio station could buy the exclusive rights to play the hits of the day, and then use their ensuring dominance to squeeze artists.
If you prefer the written work, you can read the column here for yourself, of course:
https://locusmag.com/2020/03/cory-doctorow-a-lever-without-a-fulcrum-is-just-a-stick/
Here's a direct link to the MP3 of the reading (thanks as always to Internet Archive for hosting – they'll host you too, for free!):
https://archive.org/download/Cory_Doctorow_Podcast_330/Cory_Doctorow_Podcast_330_-_A_Lever_Without_a_Fulcrum_Is_Just_a_Stick.mp3
And here's the RSS for my podcast:
http://feeds.feedburner.com/doctorow_podcast
Now in its 14th year (Thanks to Mark Pesce for convincing me to start it)!

This day in history (permalink)
#10yrsago London Olympics: police powers to force spectators to remove non-sponsor items, enter houses, take posters http://uk.news.yahoo.com/22/20100303/tts-uk-olympics-london-ca02f96.html
#10yrsago Leaked documents: UK record industry wrote web-censorship amendment https://www.openrightsgroup.org/blog/2010/bpi-drafted-web-blocking
#5yrsago Piketty on the pointless cruelty of European austerity https://www.spiegel.de/international/europe/thomas-piketty-interview-about-the-european-financial-crisis-a-1022629.html
#5yrsago Rightscorp loses big on extortion racket https://torrentfreak.com/rightscorp-hemorrhages-cash-profit-from-piracy-remains-elusive-150311/
#5yrsago UK foreign secretary: stop talking about Snowden, let spies get on with it https://web.archive.org/web/20150315031642/http://www.theinquirer.net/inquirer/news/2399082/government-minister-is-bored-with-snowden-and-wants-to-get-on-with-surveillance
#1yrago Defect in car security system aids carjackers, thieves https://www.pentestpartners.com/security-blog/gone-in-six-seconds-exploiting-car-alarms/
#1yrago Former Archbishop of Canterbury cheers on students who are walking out to demand action on climate change https://www.theguardian.com/environment/2019/mar/10/rowan-williams-school-pupil-climate-protests
#1yrago Leaked Chinese database of 1.8 million women includes a field indicating whether they are "BreedReady" https://twitter.com/0xDUDE/status/1104482014202351616
#1yrago Why #Article13 inevitably requires filters https://www.communia-association.org/2019/03/05/final-x-ray-article-13-dangerous-legislative-wishful-thinking/

Colophon (permalink)
Today's top sources: Slate Star Codex (https://slatestarcodex.com/), Slashdot (https://slashdot.org), Fipi Lele, Matthew Rimmer (https://twitter.com/DrRimmer).
Hugo nominators! My story "Unauthorized Bread" is eligible in the Novella category and you can read it free on Ars Technica: https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
Upcoming appearances:
Museums and the Web: March 31-April 4 2020, Los Angeles. https://mw20.museweb.net/
Currently writing: I'm rewriting a short story, "The Canadian Miracle," for MIT Tech Review. It's a story set in the world of my next novel, "The Lost Cause," a post-GND novel about truth and reconciliation. I'm also working on "Baby Twitter," a piece of design fiction also set in The Lost Cause's prehistory, for a British think-tank. I'm getting geared up to start work on the novel afterwards.
Currently reading: Just started Lauren Beukes's forthcoming Afterland: it's Y the Last Man plus plus, and two chapters in, it's amazeballs. Last month, I finished Andrea Bernstein's "American Oligarchs"; it's a magnificent history of the Kushner and Trump families, showing how they cheated, stole and lied their way into power. I'm getting really into Anna Weiner's memoir about tech, "Uncanny Valley." I just loaded Matt Stoller's "Goliath" onto my underwater MP3 player and I'm listening to it as I swim laps.
Latest podcast: A Lever Without a Fulcrum Is Just a Stick https://archive.org/download/Cory_Doctorow_Podcast_330/Cory_Doctorow_Podcast_330_-_A_Lever_Without_a_Fulcrum_Is_Just_a_Stick.mp3
Upcoming books: "Poesy the Monster Slayer" (Jul 2020), a picture book about monsters, bedtime, gender, and kicking ass. Pre-order here: https://us.macmillan.com/books/9781626723627?utm_source=socialmedia&utm_medium=socialpost&utm_term=na-poesycorypreorder&utm_content=na-preorder-buynow&utm_campaign=9781626723627
(we're having a launch for it in Burbank on July 11 at Dark Delicacies and you can get me AND Poesy to sign it and Dark Del will ship it to the monster kids in your life in time for the release date).
"Attack Surface": The third Little Brother book, Oct 20, 2020.
"Little Brother/Homeland": A reissue omnibus edition with a very special, s00per s33kr1t intro.
13 notes
·
View notes
Text
Free Netflix Premium Account Generator No Human Verification
Visit here: https://bit.ly/3kz85Jn
Free Netflix Premium Account Generator No Verification No Survey 2020. Netflix Premium Account Generator.How To Get Free Netflix Account generator, free Netflix Account And Password 2020. Free Netflix Account Hack
Free Netflix Premium Account Generator No Human Verification
Free Netflix Account Hack,netflix Premium Account Free,free Netflix Accounts That Work 2020,netflix Account Generator No Human Verification,free Netflix Account Generator 2020,free Netflix Account And Password 2020,.Free Netflix Accounts 2020.
Free Netflix Account and Password in 2020–100% Working Premium Accounts
Netflix is undoubtedly the best movie streaming service all over the world right now. Since 2016, Netflix expanded their coverage
and now you basically can watch movies and TV shows anywhere, except some countries like China, Crimea, North Korea or Syria. That means you won’t miss any new episode when you travel overseas.
Netflix Premium Account Features
You can watch the movies on your smartphone, tablet or computer. In case you want to watch them on TV, recent smart TVs already have the app. If you have an old TV or want to watch Netflix in your hotel room, just use a small streaming media player like Apple TV, Roku streaming stick or Google Chromecast.
Free Netflix Premium Account Generator No Survey Verification
At the moment, Netflix is offering 3 different plans, including Basic, Standard, and Premium which cost $9, $13 and $16 respectively. I’m using the Premium account at the moment because it is offering HD, 4K Ultra HD, and even 4K HDR (High Dynamic Range) content with HDR10, Dolby Vision, and Dolby Atmos. To watch the 4K content, you will need a high-speed Internet connection of 25 Mbps or faster, and of course, a capable 4K TV. Another reason I choose the Premium plan is that it allows 4 devices to watch videos simultaneously, so I can easily share my account with others.
Free Netflix Premium Account Generator No Human Verification
Netflix Password Sharing Free Netflix Gift Code Free Netflix Account Reddit Netflix Lifetime Account Netflix Code Generator Free Netflix Account Without Credit Card Netflix Account Generator Discord Amazon Prime Account Generator Netflix Account Generator Apk Netflix Account Generator Reddit Free Netflix Account Apk Netflix Account Generator Telegram Fake Netflix Apk Netflix Account Bot Fake Email Generator For Netflix Target Card Generator Free Netflix Mobile Pastr Io Netflix Accounts Free Netflix Accounts Whatsapp Group Reddit Free Netflix Username And Password Free Netflix Account Method Netflix Generator Discord What Happened To Accountbot Netflix Accounts Pdf
Free Premium Accounts Netflix Account Generator Download Netflix Premium Best Techlacarte Reddit Netflix Mod Apk 2020 Akun Netflix Gratis Oktober 2020 My Netflix Account Was Hacked Netflix Alt Generator Netflix Accounts Uk Free Netflix Throwbin 2020 Netflix M
[FREE NETFLIX ACCOUNT GENERATOR] {FREE NETFLIX PREMIUM ACCOUNT}™2020
This will help you to generate a premium account and password in just 3 minutes without verification! So that you no longer need to subscribe to the premium subscription of Netflix. You can easily get a Netflix premium account for up to 1 year without any problems.
netflix account generator
free netflix account generator
free netflix account generator 2020
netflix premium account generator
free netflix accounts 2020 generator
netflix account generator discord
netflix account generator hack
netflix generators
free netflix account hack
netflix account hack
cracked netflix account
netflix account generator server
netflix account generator no human verification
netflix account generator apk
premium account generator
how to get free netflix account 2020
1 note
·
View note
Text
Today in technology was a mistake:
A vulnerability in the messaging app WhatsApp has allowed attackers to inject commercial Israeli spyware on to phones, the company and a spyware technology dealer said.
WhatsApp, which is used by 1.5bn people worldwide, discovered in early May that attackers were able to install surveillance software on to both iPhones and Android phones by ringing up targets using the app’s phone call function.
The malicious code, developed by the secretive Israeli company NSO Group, could be transmitted even if users did not answer their phones, and the calls often disappeared from call logs, said the spyware dealer, who was recently briefed on the WhatsApp hack.
WhatsApp, which is owned by Facebook, is too early into its own investigations of the vulnerability to estimate how many phones were targeted using this method, said a person familiar with the issue.
As late as Sunday, as WhatsApp engineers raced to close the loophole, a UK-based human rights lawyer’s phone was targeted using the same method.
Researchers at the University of Toronto’s Citizen Lab said they believed that the spyware attack on Sunday was linked to the same vulnerability that WhatsApp was trying to patch.
NSO’s flagship product is Pegasus, a program that can turn on a phone’s microphone and camera, trawl through emails and messages and collect location data.
NSO advertises its products to Middle Eastern and western intelligence agencies, and says Pegasus is intended for governments to fight terrorism and crime. NSO was recently valued at $1bn in a leveraged buyout that involved the UK private equity fund Novalpina Capital.
In the past, human rights campaigners in the Middle East have received text messages over WhatsApp that contained links that would download Pegasus to their phones.
WhatsApp said teams of engineers had worked around the clock in San Francisco and London to close the vulnerability. It began rolling out a fix to its servers on Friday last week, WhatsApp said, and issued a patch for customers on Monday.
“This attack has all the hallmarks of a private company known to work with governments to deliver spyware that reportedly takes over the functions of mobile phone operating systems,” the company said. “We have briefed a number of human rights organisations to share the information we can, and to work with them to notify civil society.”
WhatsApp disclosed the issue to the US Department of Justice last week, according to a person familiar with the matter. A justice department spokesman declined to comment.
NSO said it had carefully vetted customers and investigated any abuse. Asked about the WhatsApp attacks, NSO said it was investigating the issue.
“Under no circumstances would NSO be involved in the operating or identifying of targets of its technology, which is solely operated by intelligence and law enforcement agencies,” the company said. “NSO would not, or could not, use its technology in its own right to target any person or organisation, including this individual [the UK lawyer].”
The UK lawyer, who declined to be identified, has helped a group of Mexican journalists and government critics and a Saudi dissident living in Canada sue NSO in Israel, alleging that the company shares liability for any abuse of its software by clients.
John Scott-Railton, a senior researcher at Citizen Lab, said the attack had failed. “We had a strong suspicion that the person’s phone was being targeted, so we observed the suspected attack, and confirmed that it did not result in infection,” said Mr Scott-Railton. “We believe that the measures that WhatsApp put in place in the last several days prevented the attacks from being successful.”
Other lawyers working on the cases have been approached by people pretending to be potential clients or donors, who then try and obtain information about the ongoing lawsuits, the Associated Press reported in February.
“It’s upsetting but not surprising that my team has been targeted with the very technology that we are raising concerns about in our lawsuits,” said Alaa Mahajne, a Jerusalem-based lawyer who is handling lawsuits from the Mexican and Saudi citizens. “This desperate reaction to hamper our work and silence us itself shows how urgent the lawsuits are, as we can see that the abuses are continuing.”
On Tuesday, NSO will also face a legal challenge to its ability to export its software, which is regulated by the Israeli ministry of defence.
Amnesty International, which identified an attempt to hack into the phone of one its researchers, is backing a group of Israeli citizens and civil rights group in a filing in Tel Aviv asking the defence ministry to cancel NSO’s export licence.
“NSO Group sells its products to governments who are known for outrageous human rights abuses, giving them the tools to track activists and critics. The attack on Amnesty International was the final straw,” said Danna Ingleton, deputy director of Amnesty Tech.
“The Israeli Ministry of Defence has ignored mounting evidence linking NSO Group to attacks on human rights defenders. As long as products like Pegasus are marketed without proper control and oversight, the rights and safety of Amnesty International’s staff and that of other activists, journalists and dissidents around the world is at risk.”
Additional reporting by Kadhim Shubber in Washington
58 notes
·
View notes
Text
ONLINE NEW METHOD FULL HACK CODES 46 EFOOTBALL PES 2020 DEMO
https://hahahahack.com/g996480.htm?utm_source=tumblr_com
Info - Download the demo now and see for yourself why eFootball PES 2020 won the 'E3 Best Sports Game' award!; Platforms - Windows. EFootball PES 2020 DEMO hack generator. Los jugadores de PS4, Xbox One y PC ya pueden acceder a la versión de prueba del título de Konami, a la venta el próximo 10 de septiembre. Konami ha lanzado la demo de eFootball PES 2020, una. EFootball PES 2020 DEMO hack ios 11. [MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020.
[MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 demos. How to eFootball PES 2020 DEMO Hack for pc. EFootball PES 2020 DEMO hack xyz. [MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 demoiselle. EFootball PES 2020 demo sürümünü şimdi indirebilir ve E3 2019'da 'Best Sports Game' ödülüne layık görülen, büyük beğeni toplayan oyunu deneyebilirsiniz.
[MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 democracy. DEMO, PES - eFootball PES 2020 Official Site. EFootball PES 2020 DEMO hack iphone. EFootball PES 2020 DEMO hack link. [MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 demon. EFootball PES 2020 Demo Arrives on July 30, Details Here. EFootball PES 2020 DEMO cheat ps3. EFootball PES 2020 DEMO hack Coins and Coins cheat tool no survey.
[MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 demo site. EFootball PES 2020 Demo. Konami Demo Released 30 Jul 2019. 27292 Ratings Description. Experience the most realistic and authentic football game with PES 2020, featuring Juventus exclusively licensed, alongside partnerships with FC Barcelona, FC Bayern München and Manchester United! The STANDARD. [MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 demo version. [MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 démo jouable. The eFootball PES 2020 demo is now live - here's the download.
[MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 demonstration. [MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 democratic.
EFootball PES 2020 Demo on PS4, Official PlayStationStore UK.
[MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 demo
[MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 démocratie. EFootball PES 2020 DEMO hack whatsapp group.
'Download the demo now and see for yourself why eFootball PES 2020 won the 'E3 Best Sports Game' award! Pre-order now to receive exclusive myClub content for eFootball PES 2020* • Andres Iniesta - 10 match loan • 1000 myClub coins The STANDARD EDITION also comes with the following myClub content* • Ronaldinho 2019 - 10 match loan.
[MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 demo video. A margine della presentazione dell'accordo tra Konami e Juventus abbiamo provato la demo di PES 2020: ecco quello che abbiamo scoperto. PES2020 #Demo #Juventus. Se vi piacciono i video.
[MOBILE] AUTHORS KONAMI DIGITAL ENTERTAINMENT BUG ONLINE NEW METHOD EFOOTBALL PES 2020 demo 1.
1 note
·
View note
Text
Paypal Pulls Out of The Libra Association

Earlier this year, the excitement among crypto-buffs was palpable. Facebook, the world’s largest social network, revealed it was planning to launch a digital coin in the near future. They were getting their hopes up. Until last Friday.
Payments firm PayPal has become the first company to pull out of an alliance that is trying to launch Facebook's digital currency Libra. PayPal made the announcement in a statement on Friday, but did not specify what had prompted the decision. Libra, and its digital wallet Calibra, were revealed by Facebook in June. But the cryptocurrency has been criticised by regulators, and both France and Germany have pledged to block it from Europe. PayPal said it "[remained] supportive of Libra's aspirations" but had chosen to focus on its own core businesses. The firm was one of the original members of the Libra Association, a group of 28 companies and non-profits helping to develop Libra. Its other members include payments company Visa, ride-hailing app Uber and humanitarian charity Mercy Corps. In response to PayPal's withdrawal, Libra Association said it was aware that attempts to "reconfigure the financial system" would be hard. "Commitment to that mission is more important to us than anything else," it said in a statement. "We're better off knowing about this lack of commitment now."
At its unveiling this year, Facebook said its cryptocurrency will be transferrable with zero fees via its own apps, as well as on messaging products including Messenger and WhatsApp. The new currency could be used to reward users for watching ads on Facebook's platform and spent at major retailers. Presumably any merchant with an account on these platforms could transact in the cryptocurrency with customers who also have accounts—for anything, such as online purchases, and physical-world purchases such as groceries and restaurants. Facebook is working with merchants to accept the token as payment, and may offer sign-up bonuses. There have also been reports that Facebook wants to roll out physical devices for ATMs so users can exchange traditional assets for the cryptocurrency. Facebook said Libra would be independently-managed and backed by real assets, and that paying with it would be as easy as texting.
But there have been concerns about how people's money and data will be protected. There's a risk that Facebook might use the technology to spy on users' spending habits: "There is no doubt that Facebook is treading into new and risky territory with this move," said Steve Giguere, global solution architect at software and microchip firm Synopsys, speaking to newspaper The Sun. "The risks associated with this concept will be surrounding the identity of the user's 'wallet', which associates a certain value of crypto to a person (…) Some of the major breaches around crypto have been hacks into wallet applications or even into mobile devices which can gain access and trigger unwanted transactions to anonymous wallets which can be immediately cashed out or laundered through other crypto exchanges (…) As the fruits of this research are undoubtedly years away still, Facebook will have to clean up its act with regards to its handling of personal data before we can expect the common public to put our money where our data is." The Group of Seven advanced economies warned in July that it would not let Libra proceed until all regulatory concerns had been addressed. Central bank chiefs, including the UK's Mark Carney, have also voiced scepticism, and US President Donald Trump has tweeted he is "not a fan" of the currency.
Sceptics have also voiced concerns over the potential volatility of the currency. But Facebook argues that the cryptocurrency will be a stablecoin — a token designed to have a stable price to prevent discrepancies and complications due to price fluctuations during a payment or negotiation process. Facebook has spoken with financial institutions regarding contributing capital to form a $1 billion basket of multiple international fiat currencies and low-risk securities that will serve as collateral to stabilize the price of the coin. Facebook is working with various countries to pre-approve the rollout of the stablecoin.
The Libra Association will hold the first meeting of its governing body - the Libra Council - on 14 October. The group said in a tweet that it planned to share updates soon afterwards about "1,500 entities that have indicated enthusiastic interest to participate".
2 notes
·
View notes
Text
The World of iOS and How it Develops Today
Since the last 70 years or so, mankind has seen a significant leap in the field of technology. It was in 1946 that the ENIAC (the first supercomputer) opened its eyes into this world) and by 1970 we already had a Personal Computer – a desktop PC as we know it today, available. The coming years saw the advent of mainframe and mini computers. Though the Internet has made its presence felt as early as 1969 at DARPA, it became a household name only when Windows 95 came into being. That is when a new technology came into being parallel – the Mobile (somewhere towards the end of the 20th century).
It was the turn of this technology now to occupy the brain and mind of us humans. The mobiles within just two decades have progressed from just a telephone to almost being a palmtop computer. The content that I am typing now may as well be provided as an input to some application which can read it for you, in a voice you prefer.

It was the Symbian mobiles in the beginning, but with Android as an option, the masses forgot the operating system soon that had brought new technology to this world. With Google at its back, Android powered devices took over the world as anything and people loved it. As the users demanded more and more from the hand-held sets, it was the Apple powered devices that proved a threat to the Android. According to a survey Android alone accounts for 51.1 % of the market share but iOS users are loyal to it more than perhaps the Android users and that is the reason why iOS is seeing an increase in its market share since 2017. Today there are a lot of iOS App development companies in India, US, UK and elsewhere that are loyal to this OS. Although, other mobiles are also having their followers who are loyal to them the iOS app development companies in India are flourishing as they are well supported by the elite of the Indian high class. Let’s see what’s new about iOS in the market as of now:
1.
Apple could launch 16-inch MacBook, new iPad Pro this month: Apple is scheduled to host this month's launch event where new MacBooks and iPads are expected. Apple has scheduled a number of products that it plans to introduce to the user during its October 2019 event. These comprise of a 16-inch MacBook Pro with a scissor keyboard, refreshed iPad Pro model along with Apple Tags items trackers. The company hosted an event on October 30, 2018 at the Brooklyn Academy of Music, New York City, and is expected to host the event again this year around the same time. The 16-inch MacBook Pro is rumored to be the same physical size as the 15-inch MacBook Pro, but for a larger display it will feature smaller bezel sizes. While the existing11-inch and12.9-inch iPad Pro models debuted in October 2018, these high-end tablets could be upgraded this time by the manufacturer. Also, Apple can release its item tracker similar to ' Apple Tag ' famous tile items. It's a tiny device attached to items to make them easy to find, it's combined with elements of augmented reality to help users find their lost items easily.
2.
iOS 13.1.3 is the latest software update from Apple to fix iPhone and iPad bugs: With new bug fixes and performance improvements, Apple is releasing iOS 13.1.3 to the public today. The update, in addition to iPadOS 13.1.3, is now rolling out to iPhone, iPad, and iPod touch users. Apple says the Mail app's update address issues for Bluetooth connectivity, and more. A summary of what has changed in iOS 13.1.3 follows. iOS 13.1.3 contains bug fixes and iPhone enhancements. The update
fixes an issue that might prevent an incoming call from ringing or vibrating phone.
Helps fix a problem that may prevent the opening of an invitation to a meeting in Mail
Solves a problem in which data in the Health app may not show correctly after adjustment of daylight savings
Solves a problem where Voice Memos recordings may not be downloaded after restore iCloud Backup
Addresses a problem where apps may not be updated during iCloud Backup
Fixes a problem that can stop Apple Watch from successfully pairing
Resolves a problem where alerts may not be received on Apple Watch
Fixes a problem where Bluetooth may disconnect on certain vehicles
Improves the reliability of Bluetooth hearing aids and headsets
Addresses release output for applications using Game Center
Recently, Apple released new versions of iOS 13 at a rapid pace. Apple released iOS 13.1.1 last month and just two days later followed up with iOS 13.1.2. The updates focused on improving reliability and addressing bugs for items like the Camera app, iCloud backups, and more. Finally, one would agree that the users can expect general performance improvements, squashed bugs, and more thanks to iOS 13.1.3. Apple is also currently involved in testing a beta version of iOS 13.2 with its new Deep Fusion camera technology .
3.
iPhone users complaining about iOS 13.1.2 issues: The reportedly rushed release of the latest version of Apple's mobile operating system has posed major problems. Apple support forums and Twitter account contain hundreds of iPhone user complaints about both making and receiving calls. Although the update was intended to bring a range of new features to type, including dark mode and swipe, a number of disruptive bugs have also apparently been introduced. One of the most frustrating is the inability to make calls, though users usually complain about battery drain and overheating.
One of the iPhone users complained about the company’s support forum: "After updating, the telephone is heating, batte ry draining, the worst incoming calls don't sound. What's the worth of a ' mobile ' if it doesn't sound like it?". Reports suggest that after a number of critical security issues that have arisen recently, Apple has been forced to rush the release of the new iOS version. A vulnerability found by the clandestine and prestigious group of security researchers known as Project Zero was among the most troubling.Apple had said at that time that it will not announce, discuss or confirm security issues for the safety of their customers until an investigation had taken place and updates or changes have been made generally available.
The transition to iOS 13.1 is intended to fix many of these vulnerabilities, and the security risks that a known code bug that presents to users once a patch is available is so severe that it is never considered reasonable to postpone upgrading. But the downside of widely reported vulnerabilities may prevent users from downloading the update, leaving hackers and cyber criminals at risk. Apple quickly pushed out another update to resolve the new bugs and patch those in the previous release of iOS version 13.1.1, but this rush seemed to introduce more bugs again.
The process seems to have been replicated with iOS 13.1.2, with users complaining about calls, Face ID, Mail, Messages, and battery leakage problems. How fast these issues will be addressed is not clear. Apple was unable to respond to a request for comment immediately.
4.
Apple slams Google for raising the false alarm on iOS security: Apple has blamed Google for making a false perception that its iPhones are at risk due to security bugs that allegedly penetrate many malicious websites into its iOS operating system. Researchers working in Google's Project Zero team had discovered multiple hacked websites that used iPhone security flaws to attack users who visited these websites, exposing their personal files, emails, and location data in real time. The websites distributed their malware indiscriminately and have been active for years, according to Google. "All evidence indicates that these website attacks were only operational for a brief period, about two months, not ' two years ' as Google implies," according to the iPhone maker. Google's Threat Analysis Group (TAG) found that there was no target bias because visiting the compromised site was enough for the exploit server to attack the iPhone and mount a monitoring implant if it was successful. "We predict that thousands of visitors per week are visiting these pages," the Google blog post said.
Google researchers also said they found a vulnerability that used end-to-end authentication applications such as WhatsApp, Telegram and iMessage to access all the server files on the victim's iPhone.
Apple said it patched the bugs in February working extremely fast to solve the problem just 10 days after hearing about it.
When Google came to us, we were already addressing the exploited bugs," the company said, adding that its software security teams around the world were continually iterating to introduce new defenses and vulnerabilities for updates as soon as they are discovered.
#App Developers India#India App Developers#Mobile App Development Company#Mobile App Development Company India#Mobile App Development#Best App Developers#Top App Developers In india
1 note
·
View note