#hexadecimal software
Explore tagged Tumblr posts
Text
🚨 Triumph Thruxton 400: A Modern Café Racer You Can’t Miss! 🏍️✨
🏁 Rev up your engines, riders! Triumph Motorcycles is set to unleash its latest masterpiece—the Thruxton 400—in July 2025! 🎉 A stunning blend of retro café racer vibes and modern performance, this bike is the perfect match for:
🔥 New riders looking for an approachable thrill 🔥 Café racer enthusiasts craving classic style 🔥 Urban explorers needing agility 🔥 Weekend adventurers ready for spirited rides
💸 Price? Only around ₹2.60 lakh—style, performance, and value all rolled into one! 🙌
🕶️ Retro Meets Tech
The Thruxton 400 screams old-school cool with: 🎨 Teardrop fuel tank 🔧 Clip-on handlebars 🪞 Bar-end mirrors
But don’t let the looks fool you—this baby’s packed with tech: ⚡ Ride-by-Wire for smooth throttle response 📟 Digital display for all your stats 💨 Liquid-cooled 398cc engine pumping 40 PS of pure adrenaline
🚦 Why Pick Thruxton 400?
This bike isn’t just a looker—it’s a performer! With: ✅ Lightweight build for nimble city riding ✅ 43mm inverted forks and gas-charged monoshock for smooth handling ✅ Dual disc brakes for reliable stopping power
🔥 Battle of the Retro Titans 🔥
Can the Thruxton 400 stand up to the mighty Royal Enfield Continental GT 650? 🤔 Here’s a quick comparison: ⚙️ Feature 🏍️ Thruxton 400 🏍️ Continental GT 650 Engine 💨 398cc 648cc Power ⚡ 40 PS @ 8000 rpm 47 PS @ 7250 rpm Weight 🪶 Lighter! ~214 kg Price 💸 ₹2.60 lakh ₹3.19-3.45 lakh
📅 Get Ready to Ride!
Mark your calendars! 🗓️ This stunning café racer hits showrooms in July 2025. Test rides await, so gear up to experience the perfect combo of style, performance, and tech.
❤️ Brought to You By Experts
This post is powered by Hexadecimal Software—your go-to experts in software development and IT services. From web design to custom solutions, they bring innovation to life. 💻✨
For more awesome updates, explore Hexahome—your hub for all things tech, automobiles, and lifestyle. 🌐🚀
Let the countdown begin! ⏳ Who’s ready to hit the road on a Triumph Thruxton 400? Drop a 🏍️ in the comments if you are!
0 notes
Text
re:amy and software/hardware
i think amy is an incredibly good hacker. no idea how she figured that stuff out but shes good enough to step in where and when tails cant. shes great at guessing and finding passwords also. plus just generally rlly good at coding (no idea which languages specifically but id say. uh. if tails can code in binary she can code in hexadecimal lmao)
also i think shes great at repairing cars. your car breaks down and she diagnoses the problem immediately and then Fixes It (even if it means spindashing and hammerbouncing back and forth for an hour or so)
but like. if ur pc has a problem and she cant find anything weird on it shes just like....have you tried turning it off and on again.
she absolutely could learn how to work w Gadgets:tm: and stuff but she just doesnt. shes got her lane and shes gonna stick w it, and tails is more than good enough for their entire conjoined friend groups.
#amy rose#sth#sonic series#sonic 4 episode talks#cherrypickers au#episode 2 headcanon bogaloo#since she doesnt meet tekno in our au until presumably after forces i bet theyd be able to bond over that#similar skill levels in slightly different directions...:]#she gets more used to repairing neo specifically but since neos so. Unique. she cant rlly use that knowledge anywhere else
9 notes
·
View notes
Text
not my usual kind of post but i think this is really cool
i stumbled upon this ARG on tiktok lately that poses itself as an investigation into a cancelled Wii peripheral called the Wii Reaffirmation System, and it's included software, Mind Master.
doing things like putting the videos into spectrograms and translating hexadecimal code into plain text, you can find various youtube and google drive links that explain what the system does and how it got scrapped.
currently we are on episode six, and just cracked a puzzle that produced a full report of how the device functions.
if you'd like to watch the series, check out the original creator's page: https://www.tiktok.com/@nebula_animated
and if you'd like to help solve the series, check out this google document that explains how all of the puzzles were solved, and where you can help us continue to research: https://docs.google.com/document/d/1RTU5oP2jAH2ajU5ZsHZFrh7O-UtvwVEtkgS-pkYqvbQ/edit?usp=sharing
#arg#alternate reality game#unfiction#unreality#wii#mind master#wii arg#mind master arg#tiktok#nebula_animated#alternate reality#nintendo
26 notes
·
View notes
Text
Manually Decoding DTMF Through A Spectrogram
While working on a recent CTF, I came across a challenge that required participants to extract a credit card number from a recording of a touch-tone telephone. If you pull your phone out now, turn on your ringer (because it’s almost definitely off), and click on some random numbers on the phone app keypad, you’ll hear the product of what’s known as DTMF, which stands for dual-tone multi-frequency.
I won’t go into the specifics of DTMF and why it exists — the important thing to know is DTMF uses a combination of two distinct tones to create one sound. There is a low tone and a high tone. Today, I’ll be showing you how to decode DTMF by sight through a spectrogram. There are decoders available for free online, so if you come across a problem like this in a CTF, or otherwise, I highly recommend using one of those, purely for speed and convenience. All that being said, this is an interesting process, and just generally a cool thing to know about. It’s the equivalent of converting binary to hexadecimal by hand instead of using an online converter — basically useless — but a great party trick (in the event of attending one, which I highly doubt given you’re reading this — so yeah, basically useless… on that note (or should I say tone (my musically inclined friend has informed me that I should not)), on with the article!)
Note — Standard DTMF — two tones, four levels per tone.
As of iOS 15.7, this tutorial is still relevant. I am looking for more samples (other phone brands and software models) to determine how accurate this is cross-platform. If you’re interested in contributing, there will be some information at the end explaining how.
I’ll be using this audio file - https://voca.ro/1dr1J1gbyw5B
(This is from the CyberSoc Wales “personalbanker” challenge)
The first thing I did was put the recording through a spectrogram program. There are plenty available for free online; personally, I like using Academo, because it includes lines that will help with quick sight-reading later on. (https://academo.org/articles/spectrogram/).
You may be better off downloading software (Audacity is fantastic), should you require a spectrogram for a longer recording. Academo is not scalable beyond 10 seconds, so you can use it, but you’re going to be taking quite a few screenshots.
The first thing I did was drop the recording from the challenge into Academo.
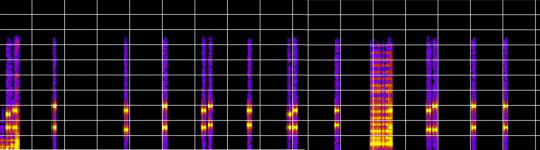
A spectrogram is a visual representation of the frequency content of an audio signal as it changes over time. In the image above, I’ve isolated the beeps produced by the clicking of the phone keypad. This section of the recording is longer than 10 seconds, so I also spliced together two screenshots. Any discrepancies you may notice in the image above are a product of that.
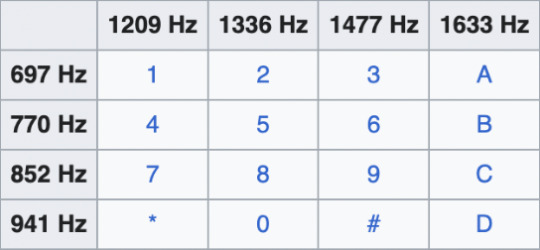
Each vertical line of dots represents one beep, and thus, one number. You’ll notice that there are two horizontal rows per beep, this is the magic of DTMF. There are 8 total frequencies involved in the DTMF system. The original DTMF keypad was laid out in a 4x4 format (below). The letter keys (A, B, C, and D) are no longer used for personal telecommunication. For digital decoding purposes, you will almost certainly not come across the letter keys, although they are still used by amateur radio operators, payphones, and the occasional equipment control system.

I was starting from scratch, with no knowledge of how a spectrogram worked with DTMF, so the first thing I did was create two recordings of myself clicking each number in my phone app (I am using iOS 15.7 on my iPhone XR).
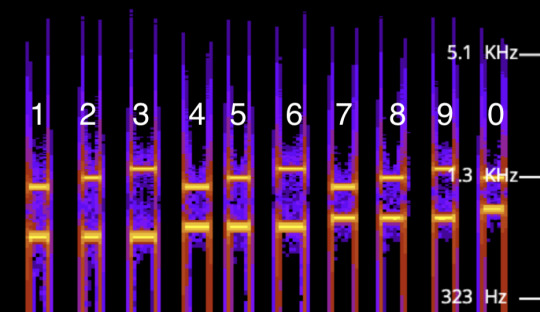

What you’ll begin to notice is that each number has its own combination of low and high tones. If you want to try to figure out the system on your own, now is the time.
Each variation in height represents a tone at a specific Hz. In order to decode this manually, you do not need to know the specific Hz of each number, you just need to understand the relational position of each tone, informed by its Hz.
I ended up throwing the original audio into Audacity so that I could create my own lines on the spectrogram for demonstration purposes.
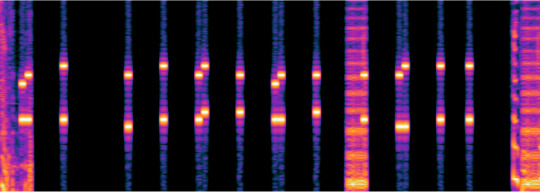
First, I’m going to turn down the contrast to make it a little easier to see.

Now, I’m going to add some lines to match up the similar tones.
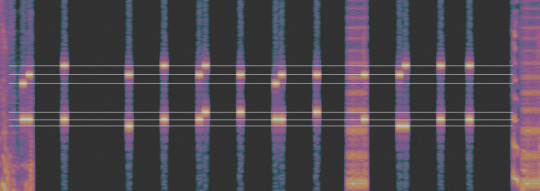
At this point, we have 6 layers of lines, there are no 0s present in this recording, if there were, we would have another line just above the bottom three. The use of the original DTMF structure with the ABCD keys would give us another line above the top three.
The simplest way to proceed is to categorize each set into Low, Medium, and High. You could choose any system — 1, 2, 3; a, b, c; whatever works for you. I recommend the LMH system because it’s visual and easy to keep track of.
I filled out the table below to show each numerical combination.

Two letters per number, each representing Low, Medium, or High (ultra High in the case of 0).
The first letter represents the top layer, and the second letter represents the bottom.
The corresponding Hz are listed in the third row for your reference.
I’ll walk you through the decoding process for the first two and then you can try the third.
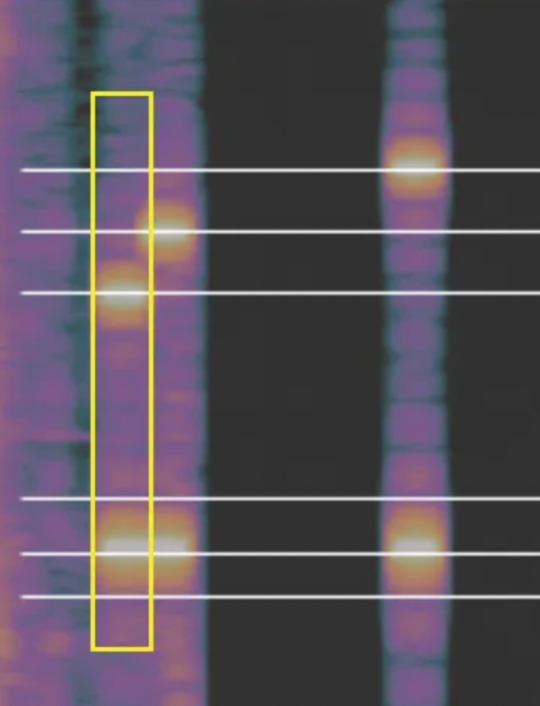
We’re going to look at the first column of tones (boxed in yellow).
This represents one number.
The first tone is crossed by the lowest of the top lines, it is marked L.
The second tone is crossed by the medium bottom line, it is marked M.
Together, they are LM — which, upon referencing the chart, is 4.
The second one is MM, which is 5.
Now try the third. (full answer at the end, scroll up now if you’d like to try it on your own — try it with lines or without!)
Once you get a feel for this, the process becomes much faster. The lines are purely for demonstrative purposes, with a little practice you’ll be able to quickly do this without lines.
And that’s how to decode DTMF manually through a spectrogram! Is it useless? Yes! Is it fun? That’s debatable!
If you’d like to help me compare cross-platform DTMF signaling, take a screen recording that captures you pressing 1234567890 on your phone keypad. Send the file to me through one of the methods outlined below. Please include your phone model and its latest software.
Discord — Adler#7210
Email me — [email protected]
If you’re seeing this on Tumblr, send me a DM!
Medium link - https://medium.com/@adler7210/manually-decoding-dtmf-through-spectrogram-562e4b0b99c3
The final answer to the CTF challenge — 4562 6598 4585 2366
Anyway, thanks for reading, enjoy decoding!
38 notes
·
View notes
Text
Pseudo-historical project about 1912 unit record equipment computation aka the "Symbolic Analyst Processor" full stack!


(above pictures emulate the looks of what this tech stack documentation and actual use may look like, still very early in the process though)
It is still coming together by my head as I write infodump notes and research various aspects of the whole time, (including the WIMP & MERN/MEAN stack) but yk, things are coming together nicely to give some milestone project mid-way between my current phase in life and the next where I go develop a fully alternative INTJ lively stack of tools. Explanations, history dives, lively reaction studies and a couple more content suggestions related to it are on the way.
Behold, the infodumps
"Top-bottom and back up workflow" 1910 / 1912 Unit Record Equipment Tabulator Computation "Bundle" Project (Pflaumen & Utalics' SymbolicAnalystProcessor)
Information Processing Language / LISP 1.5 / Bel, A-BASIC / DIBOL, Spreadsheets, Cellular Automaton, COS-310, magnetic tape storage too, TECO / VIM, Assembly, Wirebox, Tabulator, Alphanumeric Interpreter, Printer, RTTY device, Data Recording, Bulk Data Processing Indexed Cards, 60-64 entries Deque, 4K Direct-use RAM, 12K * 24 storage devices, Phonebook, Timeclock, DateTime Calendar, Programmable, Statistics, Demographics, Voting, Ledger, Journal, Logging, Rolodex, 12 Generic-use Registers & 4 Special Registers, Catalog, ~16 Keys Pad, Customized Hexadecimal Numeric Representation for "MachineCode" Hexdumps, 4*12 bits per page of data, Macros, Paracosm, may be useful for Military & Civilian Uses, Electrical Energy (and possibly incorporates some mechanical energy too), Nouns & Verbs, "Vector" XY plotter, Lambda Calculus / Panini Grammar / Universal Turing Machine Thesis, Rotors, Ural TriodeVaccumTube "Mainframe", Interactive-Use, Hypertext Interactive Video Terminal, Memex, Modem, Electric + Radio Telegraphy, Document-processing, Word-processing, Orange Plasma Touchscreen Terminal, Time-sharing, Cash Register, Bank, Automatic Teller Machine, Vending Machine, Oracle, Typewriter / Selectric, IBM 701, IBM 1440, IBM 403, IBM System/360, OpenPOWER, F#, IBM Tellum, MUD, TextWorld, solo text-adventures, Email, AIX, z/OS, Linux for IBM mainframes, Symbolic Processing System, Autocoder, modular, IBM Lotus Suite, interface with KDE or CDE, paper handling equipment, Addventure, 12-bit basic data unit as designated word, Distributed Interactive System, VeneraFS (cladogram Parade+DolDoc), GNU Hurd / MINIX3-style Microkernel, either permissive FLOSS license or public domain waiver, extensive documentation, printed illustrated booklets, music-playback, emulator / compiler / bytecode / interpreter, analog media-friendly, mostly for didactic tinkering educational uses, multilingual reconfigurable programming, HTML+CSS, Markdown, Argdown, DMA, hardware-friendly, software development environment for direct-access programmers and aesthetic designers, sub-version control system like Git, various hardware & software implementations, museum / observatory Toymaker story, constructed languages / imaginative paracosm influences around the immersive in-world lore of the "16^12" pseudo-historical setting…
Back to the point
The list is far from exhaustive or finished, as life is so much more than meets the eye. But this should be a good start to remind myself what I am working towards, a full revamp of the last ~120 years of history with much attention and care put into making it as satisfying to me as possible, despite the very probable scenario where people take the ideas and incorporate only some of such "modules" in their own workflows. Which is fine but not taking the whole package (and only specific modules) is eventually gonna be a major learning experience for me considering the reason I revamp it all beyond control freak stuff is literally to provide less exclusive / less invasive tools that anyone can learn and customize despite being very... idiosyncratic yk.
Still welcoming suggestions and constructive criticism for such big time, I hope those textual infodumps I do every so often don't bother you too much... Cya soon!
5 notes
·
View notes
Text
Why Progressive Web Apps (PWAs) Are the Future of Mobile Experience
Sure! Here's a fresh 500-word blog on another interesting tech topic: "Why Progressive Web Apps (PWAs) Are the Future of Mobile
In a world where users demand fast, reliable, and engaging mobile experiences, businesses are constantly seeking better ways to connect with customers. One solution that is gaining traction is the use of Progressive Web Apps (PWAs). These apps combine the best of websites and mobile apps to deliver a smooth experience across all devices.
Let’s dive into what PWAs are, how they work, and why they’re becoming a smart choice for modern businesses.
What is a Progressive Web App?
A Progressive Web App (PWA) is a website that behaves like a mobile app. You can open it in a browser just like any other website, but it can also be installed on your phone, work offline, send push notifications, and load quickly—even with a poor internet connection.
PWAs are built using web technologies like HTML, CSS, and JavaScript but offer app-like features without needing to be published on app stores like Google Play or Apple App Store.
Key Features of PWAs
Responsive Design PWAs work on phones, tablets, laptops, and desktops with the same ease.
Offline Support Thanks to service workers (scripts running in the background), users can access content even without an internet connection.
App-Like Feel Once installed, a PWA opens in its own window like a regular app, not inside a browser tab.
Push Notifications Businesses can send updates directly to users’ devices, just like mobile apps do.
No App Store Needed Users can install a PWA directly from the browser, saving time and avoiding lengthy app store approvals.
Why PWAs Matter
1. Faster Loading Times
PWAs are optimized for performance and can load content instantly using caching, which improves user experience and keeps people engaged.
2. Lower Development Costs
Instead of building separate apps for iOS, Android, and the web, you can build one PWA that works everywhere. This saves both time and money.
3. Better User Engagement
Features like offline access, home screen icons, and push notifications keep users coming back.
4. Easy to Update
Since PWAs are websites, updates are applied automatically without needing users to download a new version.
Examples of Popular PWAs
Twitter Lite: Loads quickly, even on 2G networks
Pinterest: Increased user engagement after switching to a PWA
Flipkart Lite: Saw a significant rise in conversions using their PWA
Is a PWA Right for Your Business?
If your goal is to reach more users, especially in areas with slow internet or limited storage space, PWAs can be a smart solution. They're great for e-commerce platforms, news portals, booking systems, and even real estate websites.
Final Thoughts
Progressive Web Apps are changing the way businesses think about mobile experiences. They offer speed, flexibility, and a native app feel—all from a single codebase. As more companies shift toward PWAs, it’s clear they are an important part of the future of web development.
About Hexadecimal Software Hexadecimal Software (https://www.hexadecimalsoftware.com/) develops high-performance Progressive Web Apps tailored to your business needs. From design to deployment, we ensure your app is fast, secure, and user-friendly on every device.
Explore More Tech Blogs on Hexahome Stay updated with the latest in web technology and digital innovation by visiting https://www.hexahome.in. Simple reads for tech lovers and business owners alike.
0 notes
Text
ED issues notice to Mahesh Babu in money laundering case
Superstar Mahesh Babu recently returned to Hyderabad from Rome after a brief family trip. He is set to resume shooting for his much-anticipated film, tentatively titled SSMB29, directed by the globally acclaimed SS Rajamouli.
However, a fresh update has emerged: the Enforcement Directorate (ED) has sent a notice to Mahesh Babu, summoning him to appear before them on April 27, 2025. The issue at hand involves his remuneration from Surana Group and Sai Surya Developers, related to his involvement in promoting their real estate projects.
Reports suggest that Mahesh Babu was paid a total of Rs. 5.9 crore – Rs. 3.4 crore via cheque and Rs. 2.5 crore in cash. The cash payment is now under investigation, with suspicions of it being linked to a money laundering network.
It is also known that both Surana Group and Sai Surya Developers were recently raided by the ED. The outcome of the investigation remains unclear, and further developments are awaited.
WRITTEN BY:-HEXAHOME,HEXADECIMAL SOFTWARE
0 notes
Text
The Rise of Neuromorphic Computing: Mimicking the Human Brain for Advanced AI
Neuromorphic computing is an innovative approach to computing that emulates the structure and function of the human brain. This technology utilizes artificial neurons and synapses to process information, offering a paradigm shift from traditional computing architectures, such as the von Neumann model, which relies on separate processing and memory units.
Key Features of Neuromorphic Computing
Parallel Processing: Neuromorphic systems can handle multiple tasks simultaneously, akin to how biological neurons operate. This allows for more efficient data processing and real-time learning capabilities.
Energy Efficiency: The human brain operates on approximately 20 watts while achieving extraordinary computational power. Neuromorphic chips aim to replicate this efficiency, making them suitable for high-performance applications without excessive energy consumption.
Scalability: Neuromorphic architectures are inherently scalable; adding more chips increases the number of active neurons without traditional bottlenecks.
Applications and Future Potential
Neuromorphic computing has significant implications for artificial intelligence (AI), enabling advancements in machine learning, sensory processing, and autonomous systems. Companies like IBM have developed neuromorphic chips, such as TrueNorth, which demonstrate the potential for complex computations in real-world applications. As research progresses, neuromorphic computing is expected to play a crucial role in developing artificial superintelligence and enhancing AI capabilities beyond current limitations .
Conclusion
The rise of neuromorphic computing represents a promising frontier in technology, merging insights from neuroscience with advanced engineering. By mimicking the human brain's efficiency and adaptability, this approach could revolutionize how we develop and implement AI systems, paving the way for smarter, more responsive technologies in the future.
Written By :- Hexahome and Hexadecimal Software
0 notes
Text
David Lynch: The Visionary of Surrealism and Dreamlike Cinema

Early Life and Artistic Beginnings
David Lynch, an iconic figure in the world of cinema, passed away on January 16, 2025, leaving behind a legacy that has profoundly influenced the art of filmmaking. Born on January 20, 1946, in Missoula, Montana, Lynch's journey began in the realm of painting before he transitioned to filmmaking in the late 1960s. His unique blend of surrealism and dreamlike narratives has captivated audiences for over five decades.
Breakthrough with Eraserhead
Lynch's first feature film, Eraserhead (1977), became a cult classic and set the tone for his career. The film’s unsettling imagery and themes of anxiety resonated deeply with viewers, establishing Lynch as a distinctive voice in cinema. Following this success, he directed The Elephant Man (1980), a biographical drama that garnered critical acclaim and multiple Academy Award nominations. This film marked Lynch's entry into mainstream cinema while retaining his signature surrealist style.
Masterpieces of Surrealism
Throughout his career, Lynch continued to explore the darker sides of human nature through films like Blue Velvet (1986) and Mulholland Drive (2001). Blue Velvet is often regarded as one of his masterpieces, delving into the underbelly of suburban America with its unsettling narrative and complex characters. Mulholland Drive, initially conceived as a television pilot, evolved into a critically acclaimed film that won him an Academy Award for Best Director. Its non-linear storytelling and exploration of Hollywood’s dark side solidified Lynch's reputation as a master storyteller.
Groundbreaking Television: Twin Peaks
In addition to his film work, Lynch gained widespread recognition for creating the groundbreaking television series Twin Peaks (1990-1991). The show combined elements of mystery and soap opera, captivating audiences with its quirky characters and intricate plotlines. Its success not only solidified Lynch's status as a cultural icon but also paved the way for future television dramas that embraced unconventional storytelling.
Artistic Exploration Beyond Film
Lynch’s artistic vision extended beyond film and television; he was also a musician and visual artist. His exploration of sound design has been integral to his films' atmospheres, enhancing their surreal qualities. In recent years, he utilized digital platforms to release short films and series, demonstrating his adaptability in an ever-changing media landscape.-Powered By Hexadecimal Software Pvt Ltd.
0 notes
Text
A Grand Slam Like No Other: The Australian Open
The Australian Open, fondly known as the "Happy Slam," is a tournament that epitomizes the essence of tennis. Held annually in the vibrant city of Melbourne, Australia, this Grand Slam event brings together the world's top tennis players and a legion of passionate fans. Over the years, the Australian Open has grown to become one of the most anticipated sporting events globally, offering electrifying matches, record-breaking performances, and an unmatched atmosphere. Let’s explore what makes this iconic event so special!
A Journey Through History
The Australian Open began in 1905 as the Australasian Championships, evolving to gain its Grand Slam status in 1924 and becoming the Australian Open in 1969. Originally held at various locations, it found its permanent home at Melbourne Park in 1988, transitioning from grass courts to hard courts and introducing retractable roofs—a game-changer for tennis.
Iconic Moments and Legendary Players
This event has hosted tennis legends and unforgettable matches:
Rod Laver's Double Slam: Achieving all four Grand Slam titles in a calendar year twice (1962 & 1969) is the stuff of legends.
Margaret Court’s Dominance: With 11 singles titles, Margaret Court’s legacy inspires players worldwide.
Serena & Venus Williams: Redefining power and style, Serena claimed seven Australian Open titles.
Novak Djokovic: Known as the "King of Melbourne," Djokovic’s 10 titles showcase his unparalleled dominance.
Why It’s a Fan Favorite
The tournament’s festival vibe is unbeatable! From live music and gourmet food to the kid-friendly AO Ballpark and the laid-back Beach House, Melbourne Park transforms into a celebration hub for sports and culture.
Tech & Sustainability
The Australian Open leads with innovation. Think electronic line-calling, Hawk-Eye systems, and sustainability initiatives—proving that sports can be cutting-edge and eco-conscious.
Memorable Matches
Who can forget epic clashes like Djokovic vs. Nadal in 2012 or Federer’s emotional 2017 comeback against Nadal? These matches are more than just games; they’re moments etched in history.
Shoutout to Hexadecimal Software
Just as the Australian Open sets the gold standard, Hexadecimal Software delivers unparalleled software development services. Need innovative solutions for your business? Hexadecimal Software has got you covered!
Make Your House a Home with HexaHome
Transform your living space with HexaHome. From smart home automation to stunning interiors, they’ll turn your dream home into reality.
Game. Set. Match.
The Australian Open isn’t just a tournament—it’s a global spectacle. And just like this event, Hexadecimal Software and HexaHome bring excellence and innovation to their fields. Enjoy the game and elevate your life with their expert services. 🌟
0 notes
Text
The Essence of Christmas

Christmas celebrates the birth of Jesus Christ, a figure whose life and teachings have inspired billions across the globe. Born in Bethlehem over 2,000 years ago, Jesus is revered as the Son of God in Christianity. His messages of love, compassion, forgiveness, and hope resonate deeply during this festive season, reminding us to embrace these values in our daily lives.
The joy of Christmas is encapsulated in gatherings with family and friends, sharing meals, and spreading kindness to those in need. It’s a time for reflection on our blessings and an opportunity to give back to our communities. The tradition of singing carols, lighting candles, and sharing stories further enriches this festive atmosphere.
Embracing the Spirit of Giving
In the spirit of giving, many people engage in charitable activities during this time. Whether it's donating to local shelters, volunteering at food banks, or simply reaching out to loved ones, these acts of kindness embody the true essence of Christmas.
Additionally, businesses often participate by organizing events that contribute to their communities, showcasing how corporate responsibility can align with the values celebrated during this season.
Technology and Christmas
As we celebrate Christmas in a digital age, technology plays a significant role in how we connect with one another. From virtual gatherings to online shopping, technology has made it easier than ever to share the joy of the season with loved ones near and far.
At Hexadecimal Software, we understand the importance of innovation in enhancing experiences during such special times. As a leading software development company, we specialize in creating tailored solutions that help businesses thrive in today’s digital landscape.
About Hexadecimal Software
Hexadecimal Software is dedicated to transforming your vision into reality through cutting-edge software development services. Our expertise spans various domains including mobile app development, web app development, DevOps & cloud computing, UI/UX design, and more. We are committed to delivering scalable solutions that grow with your business needs while ensuring high-quality outcomes.
For more insights into our services and industry trends, be sure to check out our blog at Hexadecimal Software Blog, where we share valuable information about software development and technology innovations.
This Christmas season, let us all embrace the spirit of love and generosity while leveraging technology to enhance our connections. Wishing you a Merry Christmas filled with joy and peace!
0 notes
Text
Christmas Eve: Traditions, Celebrations, and Global Customs
Christmas Eve, celebrated on December 24th, is a night filled with anticipation and joy as families around the world prepare for the arrival of Christmas Day. This special evening is rich in traditions, customs, and cultural practices that vary from region to region, creating a unique tapestry of celebrations.
The Significance of Christmas Eve
Christmas Eve marks the culmination of the Advent season, a time of preparation for Christians leading up to the birth of Jesus Christ. It is traditionally observed with various religious services, the most notable being Midnight Mass, which holds great significance in many Christian denominations. This service typically begins at midnight and celebrates the Nativity of Jesus with hymns, prayers, and communion, allowing congregants to reflect on the spiritual meaning of Christmas.
Global Traditions
Across the globe, Christmas Eve is celebrated in diverse ways:
United States: Families often set out cookies and milk for Santa Claus, a beloved tradition that adds a magical touch for children eagerly awaiting his arrival. Many also attend church services or enjoy festive meals together.
Italy: Known for the Feast of the Seven Fishes, Italian families gather to enjoy a seafood feast on Christmas Eve. This meal reflects the Catholic tradition of abstaining from meat before Christmas Day.
Spain: Families come together for a grand feast known as La Nochebuena, which includes various traditional dishes. After dinner, it’s common to attend a late-night Mass.
Germany: In Germany, it is customary to exchange gifts on Christmas Eve rather than Christmas Day. Families often celebrate with festive meals and decorate their homes with candles and ornaments.
Iceland: The Jólabókaflóð, or "Christmas Book Flood," is a cherished tradition where families give each other books on Christmas Eve. They spend the evening reading together, fostering a cozy atmosphere.
Family Gatherings and Festive Activities
Christmas Eve is also a time for family gatherings and festive activities. Many families engage in rituals such as:
Decorating the Christmas Tree: In numerous cultures, decorating the tree is an essential part of Christmas Eve celebrations. Families often hang ornaments that hold sentimental value or symbolize their heritage.
Singing Carols: Caroling remains a popular tradition, where groups sing festive songs door-to-door or at community events, spreading cheer throughout neighborhoods.
Storytelling: Sharing stories about past Christmases or reading classic tales like The Night Before Christmas helps create lasting memories and fosters family bonds.
Culinary Traditions
Food plays a central role in Christmas Eve celebrations. Many cultures have specific dishes that are prepared:
Poland: The traditional meal often features twelve dishes representing the twelve apostles, including fish, beet soup, and various pastries.
Mexico: Families celebrate with a festive dinner that may include tamales and ponche (a warm fruit punch), followed by attending Misa de Gallo, or Rooster’s Mass.
Conclusion
Christmas Eve serves as a bridge between anticipation and celebration. It is a night filled with cherished traditions that bring families together in joy and reflection. Whether through religious observances, festive meals, or simple family gatherings, this magical evening sets the tone for Christmas Day itself. As people around the world engage in their unique customs, they share in the universal spirit of love, giving, and togetherness that defines this special time of year.
Written By- Hexadecimal Software
0 notes
Text
Backend Software Development
Backend software development is a critical aspect of building robust applications that power the digital experiences we encounter daily. It involves creating the server-side logic, databases, APIs, and architecture that ensure an application runs smoothly and efficiently.
Basically,five components are used in backend software development which are server-side logic,API development,Database Management,security measures and cloud integration.
Hexadecimal Software excels in backend software development by focusing on creating scalable, secure, and efficient web applications tailored to meet client needs.
Hexadecimal Software has recently developed HexaHome, a platform that encompasses both a website and a mobile application, focusing on enhancing the real estate experience for users.The frontend of HexaHome is designed to be user-friendly and visually appealing, focusing on delivering an intuitive interface that enhances user engagement.The website and app are built to be responsive,clear menus and search functionalities are implemented to enhance usability.
The backend of HexaHome is robust and secure, designed to handle complex data processing and storage needs efficiently.Hexadecimal Software implemented RESTful APIs to facilitate communication between the frontend and backend.The backend server is responsible for processing requests from the HexaHome website and app. It handles everything from user authentication to transaction processing, ensuring that all operations are secure and reliable.
1 note
·
View note
Text
Understanding Hex Color Codes: How They Work and Why They Matter

In the world of digital design and web development, colors serve not only to enhance visual appeal but also to convey meaning, brand identity, and user experience. They play a pivotal role in shaping how information is perceived and interacted with online. Behind every vibrant website or engaging digital interface lies a sophisticated system of color representation: hex color codes.
These codes are indispensable tools that empower designers and developers to define precise color choices across diverse platforms and devices, ensuring consistency and fidelity to creative intent. This article explores the nuanced workings of hex color codes, shedding light on their intricacies, practical applications, and significance in modern digital media.
Hexadecimal Notation Explained
Hexadecimal, or "hex" for short, is a base-16 numbering system widely used in computing. Unlike our familiar decimal system (base-10), which uses ten digits (0-9), hexadecimal incorporates six additional symbols: A, B, C, D, E, and F, representing values 10 to 15. This system's utility stems from its direct correlation with binary, the fundamental language of computers. Each hexadecimal digit corresponds precisely to a grouping of four binary digits (bits), making it a convenient shorthand for representing binary values in a more manageable and human-readable format.
Components of Color: RGB Model
Colors displayed on digital screens are synthesized using the RGB (Red, Green, Blue) color model. This model operates on the principle of additive color mixing, where different intensities of red, green, and blue light combine to create a vast spectrum of colors. In RGB, each color component can independently vary from 0 (minimum intensity) to 255 (maximum intensity), allowing for precise control over the hue, saturation, and brightness of displayed colors.
Encoding Colors with Hex Color Codes
Hex color codes are a compact and efficient method of specifying colors in digital environments. Represented by a hash symbol (#) followed by six hexadecimal digits (e.g., #RRGGBB), these codes succinctly convey the intensity levels of red, green, and blue that compose a particular color. For instance, the hex code #FF0000 signifies pure red, with the red component at its maximum intensity (FF in hexadecimal) and no green or blue present (00 in hexadecimal).
Understanding Hexadecimal Conversion
Converting RGB values to hex color codes involves translating each decimal (base-10) value of the RGB components into its hexadecimal equivalent. This conversion simplifies the process of specifying colors in web design and graphic editing software, ensuring consistency across different platforms and devices. For example, the RGB value (255, 0, 0) converts directly to the hex code #FF0000, reflecting its pure red composition.
Efficiency and Range of Hex Codes
Hexadecimal notation offers significant advantages in terms of both efficiency and range. By condensing complex RGB values into a concise six-digit format, hex color codes facilitate streamlined communication and implementation of color specifications in digital media. With 16,777,216 possible combinations (16^6), hex codes encompass a comprehensive palette of colors that can be accurately reproduced on various digital screens, ensuring fidelity to designers' creative intentions.
Hex Code Abbreviations
In addition to full six-digit hex codes, abbreviated versions can be used for common colors. This shorthand notation offers several benefits:
Compactness: Reduces the code length to three digits, enhancing readability and efficiency in coding.
Performance Optimization: Helps optimize web page performance by reducing file sizes in CSS and HTML documents.
Ease of Use: Simplifies color specification and editing, particularly in large-scale web projects.
Compatibility: Widely supported across browsers and digital platforms, ensuring consistent color rendering.
For example:
#F00: Represents pure red (#FF0000).
#0F0: Represents pure green (#00FF00).
Practical Applications in Web Design
Hex color codes serve as foundational tools in web design, providing designers with a precise means to specify and manipulate colors across different digital platforms. By incorporating hex codes directly into CSS stylesheets or HTML attributes, designers ensure uniformity and coherence in color schemes, regardless of the viewing device or browser. This approach facilitates seamless adjustments and updates to color palettes throughout the development lifecycle, enhancing both aesthetic appeal and user experience.
Learning and Skill Development
Understanding hex color codes extends beyond practical application in web design, encompassing broader implications for digital media production and software development. Mastery of hex codes equips designers and developers with enhanced control over color manipulation and presentation, fostering creativity and technical proficiency across various digital disciplines. By grasping the nuances of hexadecimal notation and its relationship to RGB color encoding, professionals can elevate their capabilities in graphic design, image editing, and interface development.
Conclusion
In conclusion, hex color codes represent a cornerstone of modern digital design, enabling precise color representation and consistency in an increasingly digital world. By leveraging hexadecimal notation and its applications in the RGB color model, designers empower themselves to articulate visual concepts effectively and create compelling digital experiences. Mastery of hex color codes not only enhances technical proficiency but also enriches creative expression, underscoring their significance as essential tools for contemporary digital professionals.
0 notes
Text
What is Edge Computing and How is it Changing the Future?
Technology is growing fast. From smart homes to self-driving cars, everything is becoming connected. To make these devices faster and smarter, a new technology called edge computing is playing an important role.
Let’s understand what edge computing is, how it works, and why it is becoming popular.
What is Edge Computing?
Edge computing is a method where data is processed closer to where it is created, instead of sending it all the way to a central server or cloud. The “edge” means the edge of the network — where the devices like cameras, sensors, or smartphones are located.
In simple words, instead of sending information far away to be processed, edge computing lets nearby devices do the job.
A Simple Example
Imagine you're using a smart camera in your home to detect motion. In traditional cloud computing, the camera sends video data to a cloud server, which checks for motion and then alerts you.
With edge computing, the camera itself (or a nearby device) checks for motion and sends the alert immediately. This saves time and reduces internet usage.
Why is Edge Computing Important?
Faster Response Time Processing data locally means things happen quicker. This is important for real-time tasks like traffic control, healthcare devices, or gaming.
Less Internet Usage Since not all data is sent to the cloud, it reduces the amount of internet bandwidth used.
Better Privacy and Security Sensitive data can be processed locally without sending it to other servers, reducing the risk of data leaks.
Works Offline Some edge systems can still work even without an internet connection. This is helpful in remote areas or during network outages.
Where is Edge Computing Used?
Self-Driving Cars: They need to make fast decisions. Edge computing helps them process sensor data instantly.
Smart Cities: Traffic lights, cameras, and sensors use edge computing to manage traffic and safety in real-time.
Healthcare: Devices like heart monitors can alert doctors instantly using edge processing.
Manufacturing: Factories use edge devices to detect problems in machines before they break down.
Edge vs Cloud Computing
Cloud computing stores and processes data in remote data centers. It’s great for storing large amounts of data and doing complex tasks.
Edge computing handles tasks that need quick action and happen often. Many modern systems use both — edge for real-time tasks and cloud for heavy processing.
Final Thoughts
Edge computing is helping devices become smarter and faster. As technology grows, we’ll see more systems using edge computing to deliver better performance, lower delays, and improved security. It is a big step towards the future of connected devices and smart environments.
About Hexadecimal Software Hexadecimal Software (https://www.hexadecimalsoftware.com/) provides modern software solutions including edge computing architecture, IoT development, and cloud integration. Our team builds intelligent and scalable tech systems for the future.
Read More at Hexahome Blogs Explore more easy-to-read blogs on technology trends, development tools, and cloud systems at https://www.hexahome.in/. Stay updated and informed with simple explanations.
0 notes
Text
127.0.0.1:62893: Understanding the Meaning and How to Fix It?

127.0.0.1:62893 is a unique IP address referencing the machine from which you are operating. Working on your computer, have you ever come across the mysterious code 127.0.0.1:62893? Though it seems complicated, knowing its components will be beneficial! The error message "Disconnected from the target VM, address: 127.0.0.1:62893" often shows up on the screen throughout the development process. IPv4 and IPv6 are the two varieties of IP addresses. While IPv6 addresses are 128-bit values written in hexadecimal (e.g., 2001:0b8:85a3:0000:0000:8a2e:0370:7334), IPv4 addresses are 32-bit numbers generally expressed in dotted decimal form (e.g., 192.168.1.1). However, port numbers are used on a device to name particular operations or services. They separate traffic for distinct uses so that several services may run on a single IP address. For HTTP, for instance, online traffic usually uses port 80; for HTTPS, port 443; for SMTP, port 25. This blog post will dissect what 127.0.0.1:62893 represents, how it operates, and how to correct a typical issue. Value In Knowing Network Fundamentals Anyone in IT, networking, or software development needs a strong foundation in network principles. Knowing IP addresses and port numbers enhances security network resource protection, performance optimization, and diagnosis of connectivity problems. Furthermore, it enables experts to set and debug systems properly, guaranteeing seamless connection between devices and services. Summary Of The Subject: 127.0.0.1:62893 An IP address and a port number combine in the address 127.0.0.1:62893. 127.0.0.1 is the loopback address—a special-purpose IP address a host uses to interact with itself. Combined with a port number, it allows local machine testing and development free from system exposure to outside networks. We will examine the details 127.0.0.1:62893 in this blog, including its relevance, typical problems, and recommended methods for diagnosing and maximizing its use. Whether your job is network administrator, developer, or IT enthusiast, knowing this IP can help you to control and fix local network configurations. What Is 127.0.0.1? ( Loopback Address) The most often used loopback address in IPv4 is 127.0.0.1. Reserved for a host to send messages to herself, loopback addresses are a spectrum of IP addresses (127.0.0.0 to 127.255.255). It's a local testing method for network applications without transmitting traffic across the real network. Using 127.0.0.1 causes network traffic to return to the same machine. Because it lets you replicate network environments without impacting other devices, this is very helpful for development, testing, and troubleshooting needs. For instance, if you run a web server on your local computer, you can access it by 127.0.0.1 to guarantee it's operating as it should without letting the internet know. What 127.0.0.1:62893 Can Do for You? There are various benefits to address 127.0.0.1:62893. It gives developers a safe space free from public view by letting them test and troubleshoot programs within. Learning about networking concepts, including TCP/IP systems and client-server communication, benefits one. Early identification and reduction of any security risks depends on local-host traffic monitoring. Debugging helps to identify problems connected to networks, enhancing the stability and performance of applications. Working in a controlled environment, localhost avoids issues with other programs. How to Use 127.0.0.1:62893 The address works as follows in a basic sense: Your device runs an application trying to interact with another process. It wants to interact with a service on the same system, so it uses "localhost," (127.0.0.1). The port number (62893) informs the operating system which service or application should handle incoming traffic. For example, a development tool might utilize this address to interface with a local server for debugging needs. Safety Concerns Although port 62893 and the loopback address are usually safe, there are a few factors to consider: Make sure that your firewall settings allow communication across port 62893 if needed. Blocking this port could stop some programs from operating as they should. If you are unfamiliar with the application or service, be cautious of any software trying to interact with this port. Malicious programs could use this port for illegal correspondence. Now and then, make sure no illegal programs are using any other suspicious port or port 62893 on your machine. Please Note: Even though localhost is designed chiefly for local use, the concepts you gain from experimenting can be used in general networking scenarios. You should now be able to interpret and utilize 127.0.0.1:62893 with ease. The Step-by-Step Troubleshooting Guide STEP 1: Verify whether the service is currently running. Check that the service meant to be listening on 127.0.0.1:62893 is running. Open Command Prompt and run: cmd netstat -an | find "62893". Mac or Linux: Run bash from an open terminal using lsof -i:62893. This command will list the process utilizing port 62893 and indicate whether any service is listening on that port. If no service turns up, start the application or service and try again. STEP 2: Look for port conflicts. Verify no other service makes use of port 62893. If you discover another service, you can stop it or switch the port used for your application. STEP 3: Confirm Firewall Guidelines On particular ports, firewalls can restrict access To be sure port 62893 is permitted, review your firewall settings. Firewall from Windows: Advanced Security Open Windows Defender Firewall Review Inbound and Outbound Rules to find rules blocking Port 62893. Firewall from Apple: Under Security & Privacy, under Firewall Settings in System Preferences STEP 4: Review application settings. To guarantee your program is configured correctly to access 127.0.0.1 and port 62893 Review the configuration files or settings of it. STEP 5: Restart network services Restarts of network services occasionally help to fix underlying problems. Windows: cmd netsh winsock reset Restart the network service using the bash sudo system Linux/Mac. STEP 6: Update or reinstall network drivers Issues can arise from corrupt or antiquated network drivers. Make sure your drivers either reinstall them if needed or are current. Conclusion The combination of a local IP address and a port number utilized by a specific service on your computer is represented as 127.0.0.1:62893, more than simply a string of digits. It is essential for anyone working in web development, networking, or information technology to grasp the significance of port numbers, IP addresses, and local hosts. It is crucial to know how to use localhost and the loopback address 127.0.0.1 while troubleshooting network issues, whether you are a developer testing your latest online application or an IT specialist. If you know what these statistics mean and how to manipulate them, you can keep your local services safe and running efficiently. FAQs Can my browser make an HTTP local request if I am not connected to a network? Indeed, your computer communicates with itself without any network! This is so because your computer connects to a default address—127.0.0.1—which is not particular to any network when it lacks an internet connection. How do IPv6 addresses differ from localhost addresses? Acting as the host entry for any data for a given computer, localhost is the basic IPv4 address stated numerically as 127.0.0.1 together with port 62893. Conversely, IPv6 addresses are a numerical series 127.0.0.1-based internet protocol in the v6 sequence. This is a loopback address, unlike IPv4 addresses, which would not allocate many addresses. Can I block a website using a local host address? If yes, in what manner? Certainly. Just follow a few guidelines as described here: Open Notepad under Administrator; utilize the User Account Control prompt Click File, then Open. View the host file open. Enter 127.0.0.1 in the address bar, then Save and Restart your machine. Read the full article
0 notes