#having also sent them the powerpoint file itself
Explore tagged Tumblr posts
Note
A character who is thematically green coded, with tech and/or nature motifs as a character that I would say of course you would say that if you said you liked their archetype
what is it about slapping a green palette on literally anybody that makes me immediately love them
#i recorded a voice note like a year or two ago where i was walking a friend through that favorite characters powerpoint#having also sent them the powerpoint file itself#and the voice note was like. forty minutes long? something like that?#partly because i cant shut up but also partly because i put WAY too much data into it
7 notes
·
View notes
Text
I am fully convinced that if some of my students didn't have their heads attached to their shoulders and it was instead sitting next to them, they would have an entire meltdown and not be able it (or even try).
Went over expectations for a homework assignment very. clearly. in class. Emphasized that they must insert a photo into the Excel spreadsheet that we provided (and set up) for them and not into any other spreadsheet, and definitely not by itself. Got multiple photo-only submissions. Also multiple random-Excel-sheet submissions. Two people sending me messages, wanting to know what the instructions were again (....they're literally in the same place that you submit the document; also, I uploaded the parts of the PowerPoint presentation that explained this step-by-step). They've also sent messages to the course coordinator instead of me, uploaded the wrong Excel file altogether, and most managed to skip a very clear instruction that I gave and spent a good three minutes talking about.
....I am fully looking forward to not ever teaching again once I finish grad school, because this is insane.
#teaching#several have been corrected re: sending messages to the wrong person multiple. times.#I think there should be a rule that freshmen be distributed evenly between classes so that no one has to deal with a whole clueless cohort#also. like. college is not for everyone. and that's okay
19 notes
·
View notes
Text
...
So, working on a project and one aspect of it is making a really simple scientific poster. I'm the design guy, I do the front nd design since I'm the only person who knows basic html and css, the only person who has taken art and design classes, and I do this stuff for fun so I go ahead and take charge of the poster. Plus they really just don't have the intuition for design at all, even when I or the professors give clear instructions on How To Do Things Right. We have to make tons of drafts and get feedback on them, and its kind of a dripfeed because staff would make comments on some things, neglect to comment on the other things, and make us turn in another draft based on those missed comments.
Every single fucking time my teammates would work on it, I would have to go back and fix allllllll of the margins and padding they neglected, and I would have to remake every image of a diagram into a simplified, vectorized. Every time we had to change text or images based on the feedback, I would have to go back and change those as well. Today, while I was working on this, one of my teammates was literally trying to edit the same thing at the same time (using figma and diagrams.net). I was going to lose my mind because I was just trying to fix all of the issues, like I had to do multiple times, that my teammates would neglect from the feedback, and so this was actively happening while I was trying to fix them.
I had everything in their own groups, so that it would be easy to change things out. My teammates didn't know how to work with that. Earlier teammate literally did not understand that a file cannot have two different file extensions, and sent me a rasterized image of a diagram instead of the actual editable file, because diagrams.net just lets you have an "editable (so like, able to move around the individual elements) png" saved to your google docs, exported it as a plain png and posted it in the project chat. When I couldn't open it they then tried to tell me like, well it worked for me and well it has the other extension too so it should work. It was only the filename that had the 'extension' of the proper file format. (this is the big csc senior class btw)
The fact that we went back and forth so much on that diagram to begin with was frustrating because they could've given me access to the editable file at any time, and would constantly ignore or forget feedback which meant having to fix it many, many more times, and most of those fixes were still missing the core design feedback like 'make the text size bigger' and 'eliminate unnecessary whitespace'. If anything, it would've been much better if I went through with porting it to figma instead of relying on them, but I'm over here not wanting to be a total control freak so I'm like... whatever.
So when I get access to that diagram I fix issues from all of the feedback, but at the end of our final feedback they go and try to edit at the same fucking time as I am editing, and I had been fixing the diagram all day up to that point. Then the same thing happened on the figma document, and of course they deleted my group for the section the diagram was supposed to go in, so I had to make it again, fix the margins, fix the padding, fix the sizing.
They also completely trashed my design for a page I worked on for the project itself like waay earlier in the semester, so I was like. Okay. You guys do your thing, I can put in all my junk later. I would like to avoid wasting my time as much as possible, considering how mentally ill and exhausted I already am.
oh yeah and also the examples the professors put in the powerpoint for posters had the same (margins and spacing or text inconsistencies, bad looking screenshots, that kind of thing) or worse issues (think black impact font on a busy patterned background, for fucks sake) that they kept nitpicking us for, so its kinda like. please actually showcase something that's relevant thanks.
At least it's finally(?) over.
1 note
·
View note
Text
ILOVEYOU is a VBS email worm found in the wild in 2000 that used social engineering tactics and a quirk of Windows OS to spread *very* quickly.
VBS stands for Visual Basic script. It’s a programming language still used today, in macros and such, and it’s *very* easy to edit. It’s kinda made to be user friendly. My mom used to get magazines with instructions to code simple games in VBS; it was more intuitive to an inexperienced user than something like C or Assembly.
In 2000, Windows OS were designed to hide the appended letters after a file name which denote file type, if it recognized the type of file and trusted it. For example, if you had a file called “diary.txt”, by default it would show up on your desktop or in your email as “diary”, and the .txt would be hidden. Notably, .vbs files were a trusted file type.
ILOVEYOU took advantage of this; when it sent itself in an email as an attachment, it called the file “LOVE-LETTER-FOR-YOU.txt.vbs”. So, to the end user opening their email, it would appear as “LOVE-LETTER-FOR-YOU.txt”. Since .txt files can’t run code, people would see the attachment and assume it was safe, and might click on it to see what it was. When that happened, the worm would run, replacing several different types of files with copies of itself. It wouldn’t brick your system (the original variant didn’t replace .com or .exe files), but it would make you lose a lot of files and software (it did replace any .doc and .jpg files, for example). It would also find everyone in your Outlook mailing list and mail a copy of itself, posing as you.
ILOVEYOU was also problematic because it was written in VBS specifically, meaning anyone who got a copy could modify the code very easily. Some variants of ILOVEYOU are even more destructive, or credit a different author than the original worm credited, or remove credits entirely.
The original author of the worm lived in the Philippines, and this worm was a modified version of his thesis project at university, which was originally intended to steal passwords used for internet access. Because there were no laws in the Philippines at the time about using computer worms maliciously, he wasn’t able to be charged with anything, but the incident caused the Philippines to pass new laws to prevent destructive code from spreading this way again. ILOVEYOU almost certainly caused strained relations between Filipino companies and their foreign partners; the worm primarily spread outside of the Philippines through business computers, which had foreign partners’ emails on their mailing lists. Likely with some calls to action from large businesses, the government responded quickly; those new anti-malware laws were passed mere months after the incident.
Disinfecting a computer with ILOVEYOU on it didn’t restore your damaged files; even after it was removed, you’d have lost all your documents and photos and such. The expense of having to replace those, as well as the expense of disinfecting computers, made ILOVEYOU one of the most destructive worms up to that point, even though the computers themselves still functioned.
Nowadays, there are some safety features Windows OS has to prevent this from happening again, but this incident still teaches us an important lesson; if you’re getting an email, even from someone you trust, that’s out of character for them, don’t click on *anything* until you’ve double checked with them first. VBS still is used to write malicious code, primarily as macroviruses, which can infect Office software and spread to others every time you share Word, Excel, or PowerPoint files. Modern Office products differentiate between Office files with macros and without macros, and will automatically put unfamiliar files in Protected Mode, but these safety features aren’t infallible. It’s important to be vigilant. Furthermore, VBS script still works on NT systems; just because the virus is old doesn’t mean someone can’t edit it to work on your Windows 11 system.
Thank you so much for asking! I love talking about old computer malware.
Happy St Valentine’s/Ash Wednesday. I’m inflicting my special interests on all of you.

60 notes
·
View notes
Note
OK buckle up this is gonna be a LONG ask *pulls out PowerPoint presentation*
So Virgil I have some possible solutions to your MC- dying- to- soon dilemma, assuming the MC is human in this case. Now if I remember correctly Virgil is trapped in a digital reality that he can manipulate somewhat to his liking with the downside being that he can't leave for long periods of time. So if he somehow manages to keep MC in that reality (whether through kidnapping or persuasion) for long that they basically become one with the code, he could, in theory, be able to manipulate the MC's code. Which can give them a longer lifespan as well as other perks. There are different ways you could do this, all of it requires the consent of the MC of course.
First up: Slowing their perception of time
Now we know that the average human lifespan 75-80 yrs we can assume the average elven lifespan is around x1.5-3 that amount. If we are able to slow down only MC's perception of time due to them being part of the game they should also age slower due to their perception syncing to how time works in-game. For example the game could say that they have been there for year but to a person outside the game looking in the MC would have been there for 3 years.
Now some things to consider are:
Will the MC lag behind the rest of the world? Would Virgil be able to notice the delay? Would the day&night cycle in-game differ between MC&Virgil enough to be noticeable? Would the change in time perception affect Virgil, making this entire process void? Will this perception stick if the MC decides to go dimension jumping with Virgil?
Next up: Straight up changing the species of MC
It has already been answered in a previous ask that Virgil cannot do anything the MC's species through magic. But if able to take his ability to manipulate the code of his world then that answer might change. In theory he would be able to pop in the MC's code and shift them from human to whatever species the MC wanted.
Some things to consider are:
The nature of the creature being shifted to. How will this affect the MC? What will they gain from this transformation? What will they lose? Will they gain the instincts of the creature? What is the weaknesses of the creature being shifted to? What is the average lifespan of the creature?
Finally: Adjusting the lifespan and the speed of physical/mental aging of the MC while still keeping them human.
This is most likely your safest option because you have more control in case things go wrong. Just to clarify I meant mental aging as the aging of the brain as an organ not the mental state of the MC. You will be able to extend their lifetime for as long as you want while slowing down their aging speed in order to match yours. It was answered in a previous ask that elves such yourself stop aging in their 50s. So when the MC reaches that age you could cut off the aging process of both their body&brain entirely.
Things to consider:
Nothing really comes to mind to be honest except for dimension jumping, might want to them out of it just to be sure.
Thanks for your time goodbye 👋
Virgil took a deep breathe as his fingers play with his necklace. “These are not bad suggestions I can tell you that. However… they’re just a vessel to you my dear. A placeholder character that their actions and words are controlled by you.”
He summons a file, “I definitely can use some coding to get my beloved to age slowly like me. But…” He sent the file away. He rubs his neck, “It can only work for the vessel and not well… the player itself. And if I bring someone in that reality, it can possibly work for suggestion one...”
“But…” Virgil looks conflicted. He shook his head. “Never mind… I’m just overthinking again.”
#virgil evans#would you stay game#wouldyoustay?#yandere virgil#would you stay?#wysvn#virgil#would you stay visual novel#ask yan virgil
34 notes
·
View notes
Text
Gigaleak, preservation, emulation and content dissemination

(la version française de cet article est disponible ici)
On November 21, 1992, the sequel to the most widespread Mega Drive title was released in both Japan and South Korea, then in the rest of the world. In spite of itself, this game made many people want to find out what had happened to all those elements that had been cut during development. A few months earlier, when Sega started to show its future hit to the press, the public got a glimpse of levels such as Hidden Palace, an area absent from the final version. This wasn't the first time such an event had occurred; other sometimes equally popular titles such as Super Mario Bros. 3 have encountered the same fate, either through press coverage or via screenshots featured on the game's box. But Sonic 2 has one point that sets it apart from most other titles, in addition to its popularity: a development version was stolen a few months before the game hit the shelves. According to Yuji Naka, programmer and figurehead of the license at the time, a cartridge was stolen at a trade show in New York. His former colleague Akinori Nishiyama, meanwhile, says Sega had been hacked. In any case, this version was marketed in markets where cartridges produced without an official license were common, before being found in 1999 on a Chinese website as a ROM. Named after the person who found the ROM, the Simon Wai prototype features an unfinished version of a level that was thought to be never playable: Hidden Palace. The popularity of the license helping, amateurs started to collect documents of all types in order to identify all the differences between the versions marketed by Sega and the numerous screenshots and other development versions found over the years.

A preview published in the October 1992 issue of the British magazine Mega. 2 of the 3 levels shown here do not appear in the final version of the game.
Since Sonic 2, a lot of development versions and design documents have found their way on the net with more or less echo and communities of amateur researchers have gathered around sites such as The Cutting Room Floor, Unseen64 or Hidden Palace. On February 23, 2008, the latter put online a thousand development versions of games produced by Sega or released on Sega consoles after buying archives disks containing the games in question, sometimes with several dozen versions per title. However, the data leakage that Nintendo is experiencing in recent months seems unparalleled in terms of volume and variety of content.
In April 2020, development versions of various episodes of Pokémon, as well as source code, development tools and graphics from intermediate versions were released. Before that, in 2018 and 2019, a development version of Pokémon Gold and Silver (the "Spaceworld 1997 demo", named after the show where it was presented), assets of Pokémon Red and Green then Pokémon Diamond and Pearl had leaked on the net. In the days that followed, other types of content appeared on 4chan: official documentation relating to a number of Nintendo consoles including the Wii, the Nintendo 64, the 64DD, the iQue Player, a technical demo produced for the Nintendo 64, source code written for Super Mario 64, Powerpoints and internal correspondence from several companies for a total of about 29,000 documents. A second batch of data began to appear on July 24th and found an echo that goes far beyond technical enthusiasts and console clone producers. A large amount of content relating to some of the most popular titles and licenses in the history of video games (Mario, Zelda, Animal Crossing, StarFox) has been put online, linked on 4chan then distributed on the rest of the Internet. Development versions of Super NES, Nintendo 64, Game Boy, Game Boy Color, Game Boy Advance games, as well as source codes, graphic assets, 3D animation tests, sound effects and uncompressed music, 2D and 3D illustrations, logos, level editors, conversations between developers, visuals for a website, documents relating to the Wii, etc.
The origins of the leak Nintendo has been the subject of several attacks in recent years. Of those that have come to light, one resulted in the leakage of information about the Switch prior to its release, another involved source codes obtained from dozens of companies, but the one that most closely corresponds to the present case - generally called the Gigaleak - was carried out in 2018 by a man named Zammis Clark, a British security researcher and former Malwarebytes employee, a company specialised in detecting and removing malicious software. In 2015, he hacked VTech's servers, revealing that the company had illegally collected the data of nearly 200,000 children. He also revealed vulnerabilities in apps from manufacturers such as Dell, Lenovo and Toshiba as well as in a tool used in UK schools and developed by Impero. In 2017, he hacked some of the Microsoft servers and stole tens of thousands of files before sharing access to these servers with others. After being arrested and released on bail, he hacked Nintendo's internal network in March 2018. In its official communication, the Japanese company only mentioned the theft of a few thousand IDs and passwords as well as access to data relating to games in development at the time. However, Ganix, the man who released the Pokémon Diamond and Pearl sprites in December 2019, explained in an interview he gave to LavaCutContent a few days later that the various leaked content relating to Pokémon (including the Spaceworld 1997 demo released in May 2018, the month Nintendo realised it had been hacked by Clark) all came from a hack done in March 2018 by a man who goes by the pseudonym "Wack0". We know since the Impero affair that Wack0 is none other than Clark's pseudonym - a letter written by Impero and addressed to Clark in 2015 links the two names. Clark had shared these files with Ganix, who decided on his own initiative to leak them in December 2019, thus betraying Clark's confidence in him. The 4chan thread with which the Gigaleak started in July 2020 seems to refer to this event by its title: "ppg leak time: fuck ganix".
Because of his profile - Clark has a form of autism and suffers from prosopagnosia, the inability to recognize and identify faces - the judge felt that he would be at too great a risk if sent to prison. He was sentenced in 2019 to a 15-month suspended prison sentence and subject to a 5-year judicial review.
The presence of files relating to the iQue Player and the BroadOn company among the leaked documents suggests that the hacker accessed BroadOn’s servers, a company founded by Wei Yen who also co-founded iQue with Nintendo. Due to the legal restrictions in effect in China from 2000 to 2015, Nintendo had to make a joint venture to enter this market and develop a variant of the Nintendo 64 - the iQue Player. BroadOn is one of Nintendo's collaborators and has developed software for the Wii as well as for the iQue Brand (which includes game consoles such as the Game Boy Advance, the DS and the 3DS).

The iQue Player (picture by Evan Amos)
While Nintendo is the main target of this leak, other companies have also been affected by the ripple effect. Among them are Capcom, Konami and M2 (which is the current holder of the rights to the Aleste series). Assets and development versions of some of their games released on Super Famicom are now in the wild. Among them are Megaman X, Super Ghouls'n Ghosts, Super Castlevania IV, Axelay, Parodius Da!, Ganbare Goemon and Super Aleste. Since the release of Collection of Mana, it is public knowledge that Nintendo keep content produced by other companies in its archives. Masaru Oyamada, producer of the Mana series, said that this compilation was made possible by Nintendo, which allowed Square-Enix to recover the various source codes of these games.
In the wake of the Gigaleak, the source code for the Xbox Unreal Championship 2 game has been put online, along with numerous design documents. Epic Games' servers had been hacked in 2011 without the identity of the visitor being revealed; it cannot be excluded that the files in question originated from this attack and that the author of the hack kept them until that day on July 30, 2020. The link between this leak and the Gigaleak is not yet certain. In such a case, it is unlikely that anyone would publicly claim responsibility for the leak.
On the authenticity of the leaked content When a console prototype, a development version of a popular game or from a major license surfaces, it is customary to take it with a pinch of salt, in case someone came up with the idea of pulling a hoax or to replenish his bank account by trying to sell a fake. In the case of the contents leaked in 2020, since Nintendo hasn't officially commented on the case despite the requests made by Vice.com and LeMonde.fr, the doubt persists and the volume of data is such that it will be difficult to authenticate everything file by file. Nevertheless, Dylan Cuthbert, former developer of Argonaut who later joined Nintendo, recognised one of the tools developed for Starfox 2. In addition, in a number of cases, developers at the company have in the past provided clues suggesting that at least some of the content is authentic. This includes some rejected designs for Yoshi from Super Mario World, already unveiled in 2017.

A sprite sheet created by Shigefumi Hino during the development of Super Mario World, one year before the game’s release.
There are also quotes from developers about the presence of Luigi in Super Mario 64 and adult Mario in Yoshi's Island (both of which were set aside during development), characters in overalls in Super Mario Kart before it was decided to set the game in the Mario universe and a circuit from Mario Kart 64 located in a city but deemed too big. The same goes for the Zelda license: Yoshiaki Koizumi said he made a polygonal version of Link as part of a prototype adaptation of Zelda II for the Super Famicom, Eiji Aonuma explained that the cycle of Majora's Mask originally lasted not three days but a week and Link's Awakening was originally thought to be an adaptation of A Link to the Past - the world map of the latter made with the engine of the former has been found. Regarding Dragonfly, one of the very first Super Famicom titles shown to the public in 1988 before being renamed Pilotwings, the different screenshots published in magazines correspond to the version that leaked. While this is not an absolute proof of its authenticity - in 2012, a fan recreated an early version of Sonic 1 using screenshots as references -, the sum of clues previously cited and the large amount of documents posted online make the hoax thesis unlikely.
This leak also contains a lot of files that are difficult to identify, mainly because the names used for the files and directories are not always very explicit and some titles had never been publicly shown before or in another form. Examples include Sleep, an unfinished mouse-playable Super Famicom game (which may have been announced under the title "Black Out" in 1992), Super Donkey, another unfinished title with a number of visual similarities to Yoshi's Island, or Link's profile sprites for which we can only make guesses. Plunging into this maze of repertories requires patience as well as certain skills. Let's take the case of a game: each game has its own CVS file (named after the software used by Nintendo). A CVS file may contain several versions of a game, like a log of its evolution: an early version, a more advanced version with some elements that differ from the final version, the final version, etc. These files are not ROMs that could be launched in an emulator in 3 clicks. You have to compile the source code of the game you want to launch first, if there is source code.
Private conversations There is one point on which the leak doesn't seem to have been publicly praised: the posting of private conversations. Since April 2020, conversations between employees from various companies (Nintendo, BroadOn, then Argonaut in July) have been circulating on the net, in particular exchanges between Argonaut employees that took place in the early 90s, when some of them came to work at Nintendo in Japan. In addition to the fact that these are private correspondence - which already poses legal and moral issues - some of the excerpts shared online highlight issues that echo recent cases involving other companies, particularly on the subject of sexism and sexual harassment. In this case, the problem is twofold: there is, of course, the harassment itself (unsolicited pornographic images), but also the fact that the subject has come up without the victims having chosen to deal with it themselves.
This case illustrates the fact that video game preservation requires a minimum of methodology and should not necessarily result in the unregulated dissemination of any content relating to the development of a game or the history of a society. On the rest of the leak, opinions are very divided. Some people welcome it unreservedly; others have a mixed or even negative opinion, with the question of preservation and its modalities itself being debated.
Preservation Video game preservation is a race against time that began years ago, but the rules to be applied are still being discussed. A part of the public considers that everything that is not yet available as a ROM or ISO on the net should be dumped and shared. In 2019, a notorious collector, owner of one of the 3 knonw copies of the arcade game Akka Arrh, claimed that someone came to his home to unknowingly dump the ROM of the game in question and put it online. This is one of the most extreme cases known (if true), but it raises another issue: does preservation necessarily have to be illegal? The ROMs of commercial games you can find on the net (excluding the official websites such as the Nintendo eShop) are copies that contravene intellectual property law, whether they are final or intermediate versions, marketed or not. As early as 1993-94, consoles such as the NES, Super NES and Mega Drive had their dedicated emulator and with them ROMs that could be found via BBS. Already at that time, there were ROMs of development versions, some of which seem to have disappeared from the net because of their low distribution. These generally come either from developers who kept cartridges, CDs or files on hard disk, or from journalists who did the same with preview versions. In both cases, it is likely that they were not supposed to keep possession of them, let alone resell them years later to individuals. The amount of money exchanged for these copies has skyrocketed over the last 20 years. What might have been worth a hundred dollars in the early 2000s is now steadily rising to over a thousand. The illegal nature of the Gigaleak is nothing new in this field, but it may have been shocking in terms of its scale and the fact that the content was not obtained through a transaction (even if what made it possible is of questionable legality).
In 1979, while Namco was conducting a location test of Galaxian in a coffee shop, the game's PCB was swapped and duplicated, making it one of the first commercial titles with a beta version that ended up in the wild even before the final (and official) version was released.
Legislation in countries such as Japan, France or the United States is not so much a hindrance to the preservation as it is to the dissemination of ROMs and ISOs. We can certainly deplore the inadequacy of state initiatives as well as the meagre budgets allocated to the preservation of video games - in 2017, during a symposium on the preservation of video game preservation held at the BNF (National Library of France), its audiovisual department confessed that the budget allocated for video games was much lower than that obtained by the film sector with an average of 5,000 to 6,000 euros per year, going up to 8,000 euros in good years. It covers the acquisition of missing games (those who fell through the cracks of legal deposit), storage costs (the room where the games and machines are kept must remain at a constant temperature), etc. But the current legislation is an obstacle to preservation mainly in special cases such as video games with child pornographic content, games that companies such as Enix sometimes published in the early 1980s in Japan.
The Game Preservation Society, an entity based in Japan, does not have the task of putting online copies of the (sometimes very rare) games that it keeps in its archives, but of preserving them. Private individuals can also call on it to make backups of titles from their collection, the purpose of a private backup being to prevent damage to the programme's storage medium (cassettes, floppy disks, CDs, etc.). This policy is sometimes met with incomprehension or even disapproval from a certain fringe of the public who tirelessly demand the games' ROMs. OK, but which games? Websites that share ROMs without the agreement of their rights holders have a definite advantage over game publishers: almost all the games released on some of the most popular consoles can be found on the net. Few publishers are able to exploit their entire catalogue on a continuous basis for reasons as diverse as lack of resources, rights problems in the event of third-party licenses, or lack of commercial interest. If you want to try out the entire Mega Drive library, either you buy the 900 or so cartridges published in the past, or you download an emulator and the corresponding ROMset, thus breaking the law. It gets even more complicated with games that were playable online or available for sale in digital form only if the relevant service has closed. Abandonware-France, a website created in 2000 where you can find thousands of PC games and video game-related magazines, has adopted a clear line excluding games that are still commercially exploited as well as those released after 2000. It's less an ideal solution than a default solution - it doesn't solve the legality issue, since the games haven't yet fallen into the public domain - but it has no impact on publishers' sales, which is still one of the surest ways to get through the bullets. Other websites have been less cautious on this point by making available content that is still commercially exploited. Due to its special status, Internet Archives makes it possible to play (but not download) thousands of old games online, including titles that are still commercially exploited (Sonic 1 for example) but with the notable exception of Nintendo games or games released on Nintendo systems. In 2016, the Japanese company took down the Nintendo Power issues that were available for download at the digital library, stating that "The unapproved use of Nintendo's intellectual property can weaken our ability to protect and preserve it, or to possibly use it for new projects”. On June 1, 2020, four book publishers sued the Internet Archive after its National Emergency Library project went online, a project with which the library lent out digitized versions of books that are still commercially available. The outcome of this lawsuit could have an impact on the fate of the site and the different types of content that can be found there.
If you're interested in development versions, having a well-stocked wallet won't be of much help as legally accessible versions are rare. Sega provided us with a few exceptions by including both the final and an intermediate version of Gunstar Heroes in "Sega Ages 2500 Series Vol. 25: Gunstar Heroes Treasure Box". Probably unintentionally, the version of Revenge of Shinobi featured in "Sega Smash Pack Volume 1" on PC is a development version. As for “Silent Hill HD Collection”, the choice to base these adaptations of Silent Hill 2 and 3 on intermediate versions (retouched for the occasion) was made by default.
Finally, there is the question of making the design documents available, which again relies largely on the good will of the publishers. In addition to the interviews and documents published on specialized sites and magazines, many artbooks including illustrations, concept art and/or excerpts from design documents have been released in Japan since the end of the 1980s, followed by the US market in the early 2000s and more recently by France. Although it is not the first representative of its category, Sonic Jam has long been a reference in terms of compilation by offering galleries of documents, information and sometimes previously unseen videos in addition to the first Mega Drive episodes. In 2002, Final Fantasy X came bundled with a making of, following in the footsteps of the movie industry Square was looking towards at the time. For the past few years, some of the games produced by Sony have been the subject of making of accompanying their release and many independent developers regularly communicate on the progress of their games, both on social networks and through their blogs. However, not all games have their own journal or post-mortem. This is where initiatives such as the one launched by the Conservatoire National du Jeu Vidéo in France take over. The latter meets with developers and development companies and requests that part of their archives be made available to the public, with varying degrees of success. Other organizations such as the Musée Bolo in Switzerland (which was given archives by former Infogrames CEO Bruno Bonnell) and Internet Archive have hosted documents of this type.
The issue of preservation is not only a public issue, as companies are (or should be) concerned as well. Apart from exceptional cases such as the Great Hanshin earthquake that destroyed part of the Konami Archives in 1995, development companies rarely communicate about the loss of documents. One of the reasons for this is that in many cases they have disposed of all or part of their archives themselves. In 2016, 2 Namco employees started the Archive Project to save 350 boxes of documents from the dumpster. The two men had to convince their company to release a budget for this project even though the latter was planning to dispose of the boxes to avoid incurring new storage costs. At Square Enix, on the other hand, some files could not be saved in time and some games' source codes were lost. In addition to the Mana series previously mentioned, we know that the source code of the PlayStation version of Final Fantasy VIII has disappeared, forcing the developers of the HD version to fall back on the code of the PC version whose music is slightly different. Same with the first episode of Kingdom Hearts; the developers of the 1.5 HD Remix version had to analyze in depth a commercial copy and recreate many assets. An example that echoes the story a developer posted in 2010 in which he explained that, as part of a port of various Midway arcade games, the editor in charge of the project was unable to get his hands on the source code of Spy Hunter, so he had to download the game's ROM in order to extract the graphics via MAME and retrieve the sound files from a fan site, among other things.
---- Interlude: source code----- Having the ROM of a game does not mean you have the source code of that game. While there are thousands of ROMs of commercial games on the net, source codes are much rarer. In 2012, Jordan Mechner released the source code for the Apple II version of Prince of Persia, which he wrote alone and for which he is the owner, even though the licensing rights now belong to Ubisoft. More unexpectedly, it was discovered in 2014 that a large part of the source code for the NeoGeo version of Art of Fighting was in a file from its adaptation on PC Engine CD. In all likelihood, the developers of this version had access to the source code of the original version, which was mistakenly included in all copies of the game. In theory, having the source code of a game facilitates its adaptation on another support since, from one version to another, one can reuse a more or less important part of it, thus reducing the workload and the development costs. The loss of a game's source code therefore greatly reduces the chances of seeing a remastered version of the game. The fallback solution when it is an old game originally released on console or arcade is to use a ROM and an emulator, as it has been done on many compilations or re-releases of arcade games since the early 2000s.
The Nintendo case The source code for several Nintendo games and systems is now available on the net. Some might see this as a public backup, but the various leaks that happened since 2018 tend to prove that Nintendo knows how to preserve its data (at least for some time) and doesn't necessarily need outside help. There are several rumours about Nintendo that have not yet been confirmed. One of them is that the source code for The Legend of Zelda: Link's Awakening has been lost, a hypothesis that arose after studying the source code for the DX version of the game, released five years later for Game Boy Color. Another rumour claims that Nintendo is downloading the ROMs for its own NES games, a rumour that found an echo in 2016 after a lecture on emulation was given at the Game Developer Conference. However, if the NES game ROMs used by Nintendo for its Virtual Console look like the ones circulating on the rest of the net, maybe it's because at least one of the persons hired by the Japanese manufacturer to dump the ROMs of its games - Tomohiro Kawase - contributed to the group (iNES) that was dumping ROMs of those same games before joining the company.
The argument that Nintendo is a temple from which nothing comes out seems somewhat exaggerated. The company's games may not have been the subject of as many artbooks as Square Enix's, which, when it doesn't lose its source codes, knows how to showcase its heritage, but it has published many documents in the past relating to series such as Mario and Zelda (which was recently the subject of a series of artbooks), has released new games or versions of new games (Starfox 2 on the Super NES Mini, the European version of Drill Dozer on the Wii U Virtual Console), not to mention the "Iwata Asks" series, which we'd like to see an equivalent in all other development companies. The sense of secrecy that some people might see in Nintendo is probably due in part to the fact that the public is more interested in it than in most of its competitors. The popularity of some of its licenses has few equivalents in the world of video games and pop culture in general. The fact that we still discover old, unreleased Nintendo games nowadays is nothing unusual; tons of games are cancelled without having had a chance to be officially announced.
On the age of the content put online Two arguments are regularly put forward to minimize the significance of the Gigaleak. According to the first one, the content in question is old and therefore less sensitive or of lesser value than if it were recent documents. This is forgetting that Nintendo has more than once taken ideas or concepts that are sometimes decades old out of its boxes. During the 2007 Game Developers Conference, Shigeru Miyamoto went back over the concept of Miis and explained that it had undergone several changes over the years, starting as a demo on the Famicom Disk System, then reappearing on Super Famicom and 64DD before finally finding its way to the Wii in 2006. The Mario series has also had its share of ideas that have been put aside then used in later episodes. The idea of straddling a mount, for example, was first suggested during the development of Super Mario Bros. 3 (1988) before being adopted in Super Mario World (1990) with Yoshi. Miyamoto had originally envisioned a horse, but he kept the idea for The Legend of Zelda: Ocarina of Time (1998). A simultaneous multiplayer mode was experimented with at the time of Super Mario Bros. 3 (1988) and will only be included in the series starting with New Super Mario Bros. Wii (2009). Finally, one of the sprites from Super Donkey bears some resemblance with one of those appearing in Super Mario Maker, by its concept.
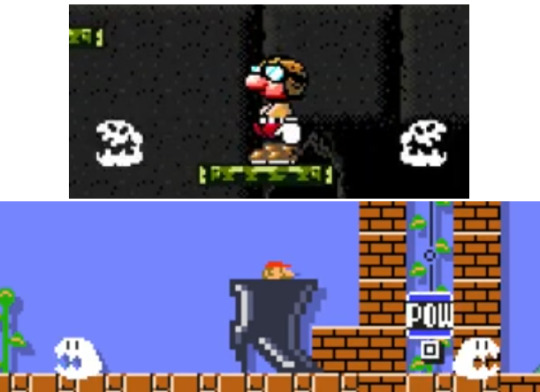
Top: Super Donkey. Bottom: Super Mario Maker.
The second argument concerns the damage suffered by Nintendo and reveals a difference in treatment with what happened in April 2020 when a development version of The Last of Us 2 leaked a few weeks before the game's release. Messages of disapproval and support for the developers seem to have been more popular than those welcoming the leak. In the case of the Gigaleak, Nintendo has often been perceived as a big company, an abstract entity, thus obscuring the fact that its games are also the sum of the work of a group of individuals. In legal terms, unless otherwise stated, the fruit of the work produced within a company is the property of the company. On a personal level, it often happens that a developer has a particular attachment to what he produces.
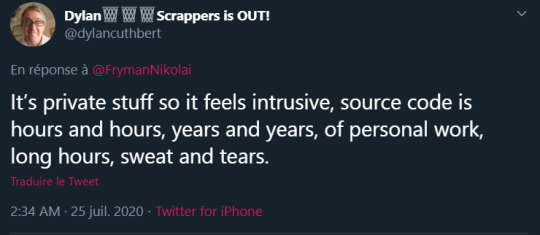
Dylan Cuthbert, in response to a person asking him how he felt, a few hours after the July 24th leak.
While some developers may have been in favour of releasing development versions - Yuji Naka tried to find the prototype of the first Sonic publicly shown in June 1990 to include it in Sonic Mega Collection - or even production documents - Jordan Mechner published the journals he kept during the development of Karateka and Prince of Persia - others are less enthusiastic about making such files available. By definition, a development version is not a finished product, and while it is natural for a finished product to be made public, this is not necessarily the case with everything relating to the development process. This is not exclusive to video games: many illustrators are reluctant to show their sketches, works in progress or unfinished drawings, no matter how old theirs works are, and the same is true of writers and musicians. As with private conversations, there is the question of respect for developers and their consent. This is obviously not a small obstacle for anyone who wants to preserve and share all the documents relating to the history of video games, but it seems difficult to me to do the work of an archivist or historian (who relies on the work of developers) if it means harming some of these developers even slightly. Of course, you have to hope that as much information as possible will come out and you can work on it in different ways, but you also have to set limits on the methods you can use and not just reason in legal and/or material terms.
Consequences It is difficult to measure how much will come out of this case, as other elements may be added in the coming days or weeks. Now that the leaked content is circulating, Nintendo will have a hard time getting it off the net and can expect clones of consoles using its own source codes to be produced and marketed in certain countries.
Regarding the emulation scene, it's a bit more complicated. In 1999, source code and documents relating to the Nintendo 64 leaked from Silicon Graphic Inc, a company that produced processors for the Nintendo 64. Known as the Oman Archive, this content was used in the early days of Nintendo's system emulation, which led to quick results. But this use of an illegally obtained code subject to intellectual property law was also a liability for the emulation scene of this machine, which took years to get rid of. Most of the other emulators available online are legal since they were developed with their own code. It's to avoid breaking the law that console BIOSes often have to be downloaded separately (like the source code, BIOS are copyrighted). The appearance of the Wii source code is therefore a poisoned gift for developers of amateur emulators. It may allow them to understand how Nintendo has done this or that, but they can't reuse it even partially without breaking the law.
Nintendo has probably already apologised to Capcom, Konami and M2 whose files have also ended up on the web. As for the rest, we can only speculate. Will publishers become aware of the interest of a part of their audience in the making of their games and offer more content to satisfy this curiosity (videos from their archives, books, making of, etc.) or, on the contrary, will they lock the doors of their archives by throwing the key into a well? Will security and control on the net increase, further restricting the distribution of certain types of content, be it fan games, ROMs - two categories that Nintendo has been fighting hard against in recent years - or Youtube videos showing things that publishers would prefer not to see on the net (like, say, glitches from Animal Crossing: New Horizons)? Or maybe nothing will change.
Sources : Sonic 2 https://web.archive.org/web/20051104100754/http://xbox.gamespy.com/articles/654/654750p4.html https://info.sonicretro.org/Sonic_Team_interview_by_Kikizo_(November_30,_2005) Hidden Palace http://info.sonicretro.org/February_23,_2008_Proto_Release Pokémon Gold 1997 prototype (2018) https://twitter.com/sanquii/status/1002107775651057664 Pokémon 2019 leak https://lavacutcontent.com/pokemon-beta-leaker-statement/ https://helixchamber.com/2019/02/16/what-dreams-may-come/ April-May 2020 leak https://resetera.com/threads/the-nintendo-leak-saga-continues-biggest-nintendo-leak-in-history-full-source-code-design-files-for-wii-released-online.196683/ https://www.resetera.com/threads/the-nintendo-leak-saga-continues-biggest-nintendo-leak-in-history-full-source-code-design-files-for-wii-released-online.196683/post-32917584 https://nintendoeverything.com/nintendo-suffers-huge-leak-source-code-and-design-files-for-wii-appearing-online/ https://twitter.com/Zetsuboushitta/status/1256320740527239168 https://twitter.com/LuigiBlood/status/1256543745794879488 recent leaks: 1 Ryan Hernandez https://www.thegamer.com/man-leaked-nintendo-switch-prison-charges/ https://www.justice.gov/usao-wdwa/pr/california-man-who-hacked-nintendo-servers-steal-video-games-and-other-proprietary 2 Tillie Kottmann https://www.bleepingcomputer.com/news/security/source-code-from-dozens-of-companies-leaked-online/ 3 Zammis Clark https://www.theverge.com/2019/3/28/18286027/microsoft-nintendo-vtech-security-hack-breach-researcher-guilty https://lavacutcontent.com/pokemon-beta-leaker-statement/ Mail sent by Impero to Zammis Clark - Wack0 https://archive.org/stream/pdfy-fRcZ1TWHaDkwz-Ea/Letter%20to%20Mr%20Zammis%20A%20Clark%20dated%2013%20July%202015_djvu.txt BroadOn + iQue https://wiki.mariocube.com/index.php/IQue#BroadOn July 2020 leak https://boards.4channel.org/vp/thread/44305551/ppg-leak-time-fuck-ganix https://www.resetera.com/threads/update-super-mario-64-and-oot-source-leaked-massive-nintendo-data-leak-source-code-to-yoshis-island-a-link-to-the-past-f-zero-and-more.254724/page-62 Aleste and M2 https://twitter.com/M2_STG/status/1014031712672571393 Collection of Mana https://gameinformer.com/preview/2019/06/11/decades-in-the-making Vice, Lemonde.fr and Nintendo https://www.vice.com/en_us/article/7kp7bx/a-massive-leak-of-nintendo-source-code-is-causing-chaos-in-video-games https://www.lemonde.fr/pixels/article/2020/07/31/nintendo-ce-que-l-on-sait-de-la-fuite-supposee-de-documents-lies-aux-jeux-video_6047809_4408996.html Cuthbert and Starfox 2 https://twitter.com/dylancuthbert/status/1286789583061934080 Mario World sprite sheet https://topics.nintendo.co.jp/article/cb34ab17-9135-11e7-8cda-063b7ac45a6d Luigi in Super Mario 64 https://shmuplations.com/mario64/ Adult Mario in Yoshi's island http://shmuplations.com/yoshi/ Super Mario Kart before Mario https://twitter.com/toruzz/status/1287400639165861888 http://iwataasks.nintendo.com/interviews/#/wii/mariokart/0/0 Mario Kart 64 circuit http://shmuplations.com/mariokart64/ https://twitter.com/AeroArtwork/status/1288299965954088966?s=19 Zelda II SFC in 3D http://iwataasks.nintendo.com/interviews/#/3ds/zelda-ocarina-of-time/1/1 Zelda OOT in Ganondorf's Castle https://twitter.com/AeroArtwork/status/1287524648222105607 7 day cycle in Zelda: Majora's Mask https://twitter.com/Zen64_/status/1287582698085777408 http://iwataasks.nintendo.com/interviews/#/3ds/majoras-mask-3d/0/0 https://www.polygon.com/2015/2/18/8064257/majoras-mask-three-day-timer-week DragonFly https://www.unseen64.net/2008/04/14/pilotwings-snes-proto/ Sonic 1 fan recreation https://www.youtube.com/watch?v=oHtzXzu2BDA Argonaut https://twitter.com/corentin_lamy/status/1286932458173276161 https://www.resetera.com/threads/update-super-mario-64-and-oot-source-leaked-massive-nintendo-data-leak-source-code-to-yoshis-island-a-link-to-the-past-f-zero-and-more.254724/post-40826655 Unreal Championship 2 https://twitter.com/Sinoc229/status/1288680503801860096 https://www.ign.com/articles/2011/06/11/epic-games-website-forums-hacked Akka Arrh https://arstechnica.com/gaming/2019/04/after-a-lost-atari-rom-leaks-retro-fans-ask-was-it-stolen/ Galaxian https://www.4gamer.net/games/999/G999905/20180313040/ Firsts emulators https://emulation.miraheze.org/wiki/History_of_emulation Namco's Archive Project https://game.watch.impress.co.jp/docs/news/1205387.html Spy Hunter http://web.archive.org/web/20110925185703/http://www.ppl-pilot.com.nyud.net/mame.aspx Prince of Persia https://github.com/jmechner/Prince-of-Persia-Apple-II On the CNJV, Musée Bolo and BNF : "colloque: la conservation du patrimoine vidéoludique" (2017). Nintendo Power, Internet Archive https://www.polygon.com/2016/8/8/12405278/nintendo-power-issues-disappear-from-free-online-archive http://blog.archive.org/2020/06/01/four-commercial-publishers-filed-a-complaint-about-the-internet-archives-lending-of-digitized-books/ Nintendo ROMs https://www.resetera.com/threads/tomohiro-kawase-mightve-been-hired-by-nintendo-to-put-rom-headers-into-vc-updated-dec-1-2018.64755/ https://twitter.com/LuigiBlood/status/1045348387174977536?s=19 https://www.reddit.com/r/emulation/comments/9msl9j/update_did_nintendo_actually_download_roms_for/e7iemhb/ GDC 2016 https://www.gdcvault.com/play/1023470/-It-s-Just-Emulation The Legend of Zelda: Link's Awakening source code https://www.neogaf.com/threads/it-bothers-me-that-nintendo-keeps-ignoring-links-awakening.931702/page-2 Mii https://unseen64.net/2008/04/14/mii-nes-prototype/ https://www.nintendo.fr/Iwata-demande/Iwata-Demande-Nintendo-3DS/Vol-5-Interview-de-Miyamoto-san-a-la-veille-de-la-sortie-de-la-console/2-Faire-des-personnages-Mii-un-standard-international/2-Faire-des-personnages-Mii-un-standard-international-210297.html Yoshi and a horse https://www.nintendo.co.uk/News/2017/October/Nintendo-Classic-Mini-SNES-developer-interview-Volume-5-Super-Mario-World-and-Super-Mario-World-2-Yoshi-s-Island-1290850.html Multiplayer mode in SMB3 http://iwataasks.nintendo.com/interviews/#/wii/mario25th/2/3 Super Donkey - Mario Maker https://twitter.com/dbMisadventure/status/1286751468293414912 Dylan Cuthbert https://twitter.com/dylancuthbert/status/1286822093703622656 Sonic 1 prototype https://www.gamesradar.com/super-rare-1990-sonic-the-hedgehog-prototype-is-missing/ Oman Archive https://sm64-conspiracies.fandom.com/wiki/Oman_Archive Animal Crossing: New Horizons vidéo https://www.vice.com/en_us/article/m7j7yb/nintendo-takes-down-youtube-video-of-fan-showing-animal-crossing-glitches
89 notes
·
View notes
Text
“I don’t like it.”

For some good two seconds, it felt like the earth started crumbling down to its end...
• • • • •
When I was in 3rd year of high school, we had a project for our MAPEH subject. Our class of 44 students was divided into six groups, pre-determined by our professor. In my group, there were seven members and we named ourselves “D’Cookies” because we preferred David Cook over David Archuleta—the good ol’ days of American Idol. My groupmates assigned me to be the leader for this specific project.
When all groups had their leaders, our professor called the six chosen ones to the front for a short discussion on what we were to do.
The project mandated us to report to the class about the music of a specific Southeast Asian country. Other than that, we also had to briefly discuss facts about the country itself—there was a long outline of requirements that we needed to meet.
Our professor then asked us to draw from two sets of paper strips: one set for the country and one set for the order of reporting (only one group shall do the presentation every week). Thailand was the country for my group and we would be the fourth to present—meaning we have at least a month left to prepare. If I remember correctly, the other countries were Singapore, Indonesia, Brunei, Vietnam, and Malaysia.

We were given options on how we could do the presentations. It can be in Powerpoint, traditional Manila paper reporting, videos or movies, a play or some skit, and even puppet shows. I was immediately intrigued by the idea of a puppet show since it’s one thing that I’ve never done before and I thought it would be fun to make for its crafty nature. But I didn’t like the idea of doing a puppet show in front of the class, so I thought it would be better to simply record it then make it a video.
We were also given “bonus instructions” to add a little spice to our projects. One: we don’t only have to please our professor, we have to please our classmates. At the end of each presentation, the non-presenting students shall rate a group’s presentation on a scale of 1–10 with 10 being the highest. The second bonus instruction is that if the group was able to sing a song in the native language of the country they’re reporting about, an additional five points to the final grade will be given.
The six leaders were sent back to their groups to discuss the project internally. To my surprise, my groupmates were down with my idea so we pushed through with it.

I daresay, we took our time even though I didn’t like the idea of cramming stuff up. We had an endless number of school projects and I simply can’t judge how everyone’s availability is limited. And I always wanted to make beautiful projects for the hell of it, not primarily for the sake of grades. Also, I’m more inspired to do better when my I’m grouped with my high school crush (get what I mean?). Don’t know if it’s coincidence or what, but I always do better when I was grouped with her.
Anyway... Two of us wrote the script and searched for animal characters that we can turn into paper bag puppets. We did everything in my house. The following weekends, we made the puppets and colored the forest background that my great-uncle asked a friend of his to draw. When the script was finished, we started recording our voices. We were rarely complete, that’s why we only got to record a few scenes and continued recording once the others were available.
We started shooting the scenes when all the materials were made, even when the audio wasn’t complete yet. We did those for a good two weeks and I was stitching them up using Windows Movie Maker as we went along. We were shooting until the day before our presentation, and while I was combining the scenes altogether, I had them learn the Thai song that we’re going to sing.

It was getting late, so my classmates had to go home—even my mother was concerned about them. Of course, I allowed them even when I knew I had to do everything else on my own until I finish the video.
Rendering of the video took hours—we had a bad PC, technology wasn’t as good then, and I was only using the default Movie Maker. I couldn’t even fathom the problem why the program couldn’t render the entire video as one file which lasted around 30 minutes, so I resorted into splitting them up into four parts: Intro, Thailand’s Culture, Music of Thailand, and Ending. I slept while each part was rendering. It wasn’t even a sound sleep because of the anxiety and the possibility that the video would not render properly due to errors.
Fortunately, everything succeeded. It was 4 o’clock in the morning. I had two hours of anxiety-less sleep before I woke up to ready myself for school.
Presentation time. We were in costumes made to look like the traditional attire of Thailand. We used the sarongs that my father had collected during the time he worked in ASEAN countries. We also brought the puppets—just for fun and as proof that we’re the ones who did our project.
My classmates were watching intently at the video. They laughed at the funny scenes. Some had their notebooks open, jotting down the facts from our video.
By the end, there was applause... And some laughter—I included some BTS bloopers during the end credits.
And we sang our song. It was a very uninspired song performance… but we still did it for the sake of the extra five points.
The bell rang right at the end of our presentation.
Our professor didn’t have time to give a comprehensive review, but before he dismissed the class, he asked everyone to stay for a moment.
He said, in a very serious tone, “I didn’t like it.”
For some good two seconds, it felt like the earth started crumbling down to its end… I could feel the WTF reactions of my groupmates.
“...I LOVE IT,” our professor continued.
And our screams erupted.

1 note
·
View note
Text
Mp3 To Wav, Mp3 To Wave Converter, Mp3 Converter, Mp3 Software, Mp3 Encoder
QQripper is the autoloader software to automate the ripping of a stack of music discs (to transform audio tracks from music CD to digital information) to supported storage devices similar to exhausting disk, iPod or MP3 player. Free obtain the skilled WAV Compression app - iDealshare VideoGo ( for Home windows , for Mac ) , then click the downloaded package and follow the on-screen directions to install and run it, the next interface will pop up. Attempt Zamzar on-line converter for wav to mp3 conversion. I can understand your want to convert to MP3, however am undecided how a lot assist I can be. Perhaps I can do some checking. Within the meantime, have you tried audioshare? I can't bear in mind if it should convert without the cloud, but thought it could convert information. Just don't keep in mind for sure. I'll perform a little googling and get again to you. Submitting a podcast to the iTunes Store is a distinct course of than exporting an Audacity file to an iTunes library. See our Tutorial on Tutorial - Mixing a Narration With Background Music and m4a mp3 converter free mac our Wiki page on Easy methods to publish a Podcast for more assist with creating and publishing a podcast. Link to audio converter product is within the present notes. It additionally helps you change m4a mp3 converter free mac to MP3, AC3, WMA, DTS, CAF, AIFF, FLAC, etc. Similar toWAV recordsdata,AIFF recordsdata could be very massive as a result of the data is uncompressed.
Click on the drop-down button of "Profile". Then, select "MP3 - MPEG Layer-3 Audio (.mp3)" as output audio format from "Common Audio" category. 2Choose WAV (.wav information) as the output format. This MP3 to WAV converter online is a free program that's easy to make use of and permits changing an array of formats to WAV, MP3, WMA, and OGG audio recordsdata. Along with recordsdata, its URL can also be imported. The program additionally permits choosing the output file high quality and facilitates downloading the transformed file from the interface itself. You can use iTunes to convert tune information between compressed and uncompressed codecs. For instance, you might wish to import some uncompressed files into iTunes as compressed recordsdata to save disk space. Examples of compressed formats are MP3 and Apple Lossless Encoder. Examples of uncompressed formats are AIFF or WAV. WAV MP3 Converter converts WAV to MP3 and MP3 to WAV, and resamples WAV and MP3 information. It's an ALL-IN-ONE audio converter that helps more than a hundred and fifty audio and video recordsdata, and retains ID3 tag when changing. The software is full suitable with Vista and Windows 7. With the M4A Converter, you possibly can easily regulate output audio high quality to larger, regular or decrease; alter audio bitrates, sample fee, channels and the volume of audio. Lastly, click on Convert All to start the MP3 to WAV conversion course of. There are a number of benefits to utilizing a compressed format on iPods and iPhones. The 2 primary benefits are you could match many extra songs into the device (for 256 kbps files you may match about 10 occasions as many songs) and compressed files improve battery life, as a result of disk reads are comparatively heavy on battery power. Transfer your cursor to format and choose Widespread Audio" and you'll see an inventory of audio formats, select one from them in line with your devices supported audio codecs which have been listed within the above text. Inform Zamzar the place you need to obtain your converted M4A file. M4A is Microsoft Windows unfriendly audio codecs, in an effort to share music with friends whose laptop are PCs, or to insert the music file to PowerPoint, convert the M4A audio to WAV, WMA, or MP3 is thoughtful deeds. The program can convert FLAC into MP3 in addition to all different audio files, like WAV to MP3 , AAC to MP3, WMA to MP3 , M4A to MP3, OGG to MP3 and vice versa. Moreover, this Free Music Converter additionally lets you exact audio from movies, similar to YouTube, Vimeo, Nicovideo, AVI, MPEG, WMV, MP4, FLV, MKV, and so forth. This is the default setting. When this feature is chosen, Audacity copies the imported file(s) into the mission's audio knowledge. It's essential that files are copied into the undertaking if the Audacity mission is to be moved, opened on another laptop or sent to another person, or if it's worthwhile to to move, rename or delete the unique files. You may't edit M4A audio in audio editors, like Audacity, Wavosaur, and so forth. WAV MP3 Converter presents many more prospects than its easy descriptive identify implies. With an extremely straightforward-to-use structure and impressive list of conversion options, this is a great program that does more than anticipated. Observe that the audio converter is trial-ware which permits you change half of each audio file. To convert full audio, you will need to purchase license code from the purchase hyperlink in the program to finish registration. That is one other decent MP3 to WAV converter that supports an array of formats. In addition to local recordsdata and URL, this system also permits adding files from Dropbox and Google Drive for conversion function. Convertio allows adding multiple files at a time for batch processing. As soon as the information are transformed, they are often saved at PC, Google Drive or Dropbox. Obtain and record music directly to iTunes Library for management. Launch iWisoft Free Video Converter. Click on the Add" icon and browse for the WAV file within the file choice window. Choose the item and click the Open" button to import the audio into the applying. Taking this under consideration, it is clear why MP3 is a great format for distributing, streaming and promoting music. However, this comes at some value. With Total Audio Converter you should use batch mode to transform WAV to MP3. Most attention-grabbing, whether you exchange one file or to hundred information, the velocity is sort of the identical. It takes just a few seconds to render WAV recordsdata within the MP3 format. AIFF (brief for Audio Interchange File Format) is a format developed by Apple Inc. in 1998 and is an audio format standard used for storing sound data for private computers and other digital audio units. The extension for AIFF isaiff oraif, it always used to store uncompressed, so that why it wants extra disk house to store the file. ALAC which is Apple's proprietary lossless format (appropriate with serato) and FLAC (not usable with serato) are knowledge-compressed lossless files which have the same sound high quality as aifs and wavs with about half the space.
1 note
·
View note
Link
MENLO PARK, Calif. — In a glass conference room at its California headquarters, Facebook is taking on the bonfires of hate and misinformation it has helped fuel across the world, one post at a time.
The social network has drawn criticism for undermining democracy and for provoking bloodshed in societies small and large.
But for Facebook, it’s also a business problem.
The company, which makes about $5 billion in profit per quarter, has to show that it is serious about removing dangerous content. It must also continue to attract more users from more countries and try to keep them on the site longer.
How can Facebook monitor billions of posts per day in over 100 languages, all without disturbing the endless expansion that is core to its business? The company’s solution: a network of workers using a maze of PowerPoint slides spelling out what’s forbidden.
Every other Tuesday morning, several dozen Facebook employees gather over breakfast to come up with the rules, hashing out what the site’s two billion users should be allowed to say. The guidelines that emerge from these meetings are sent out to 7,500-plus moderators around the world. (After publication of this article, Facebook said it had increased that number to around 15,000.)
The closely held rules are extensive, and they make the company a far more powerful arbiter of global speech than has been publicly recognized or acknowledged by the company itself, The New York Times has found.
The Times was provided with more than 1,400 pages from the rulebooks by an employee who said he feared that the company was exercising too much power, with too little oversight — and making too many mistakes.
An examination of the files revealed numerous gaps, biases and outright errors. As Facebook employees grope for the right answers, they have allowed extremist language to flourish in some countries while censoring mainstream speech in others.
Moderators were once told, for example, to remove fund-raising appeals for volcano victims in Indonesia because a co-sponsor of the drive was on Facebook’s internal list of banned groups. In Myanmar, a paperwork error allowed a prominent extremist group, accused of fomenting genocide, to stay on the platform for months. In India, moderators were mistakenly told to flag for possible removal comments critical of religion.
The Facebook employees who meet to set the guidelines, mostly young engineers and lawyers, try to distill highly complex issues into simple yes-or-no rules. Then the company outsources much of the actual post-by-post moderation to companies that enlist largely unskilled workers, many hired out of call centers.
Those moderators, at times relying on Google Translate, have mere seconds to recall countless rules and apply them to the hundreds of posts that dash across their screens each day. When is a reference to “jihad,” for example, forbidden? When is a “crying laughter” emoji a warning sign?
Moderators express frustration at rules they say don’t always make sense and sometimes require them to leave up posts they fear could lead to violence. “You feel like you killed someone by not acting,” one said, speaking on the condition of anonymity because he had signed a nondisclosure agreement.
Facebook executives say they are working diligently to rid the platform of dangerous posts.
“It’s not our place to correct people’s speech, but we do want to enforce our community standards on our platform,” said Sara Su, a senior engineer on the News Feed. “When you’re in our community, we want to make sure that we’re balancing freedom of expression and safety.”
Monika Bickert, Facebook’s head of global policy management, said that the primary goal was to prevent harm, and that to a great extent, the company had been successful. But perfection, she said, is not possible.
“We have billions of posts every day, we’re identifying more and more potential violations using our technical systems,” Ms. Bickert said. “At that scale, even if you’re 99 percent accurate, you’re going to have a lot of mistakes.”
It’s a long article. Give it a look.
1 note
·
View note
Text
Pmd To Pdf Converter Free Software

FREE PDF Converter - not a trial version. Print to PDF from virtually any application. Create PDF output optimized for print, screen, ebook, or press. No annoying pop-up ads, no registration requirement - no catch! High-quality, easy to use PDF creator for all users. Secure PDFs with 40-/128-bit encryption. Add document information. Pagemaker Pmd To Pdf Converter Free Downloads - 2000 Shareware periodically updates software information and pricing of Pagemaker Pmd To Pdf Converter from the publisher, so some information may be slightly out-of-date. You should confirm all information before relying on it.
Formats are supported
pdfPortable Document FormatwordMicrosoft Word DocumentdocMicrosoft Word DocumentdocxMicrosoft Office Open XMLxlsMicrosoft Excel Worksheet Sheet (97-2003)xlsxOffice Open XML Worksheet SheetpptMicrosoft PowerPoint 97/2000/XPpptxMicrosoft PowerPointjpgJoint Photographic Experts GrouptxtPlaintext Text FilepngPortable Network GraphichtmlHyperText Markup LanguagertfRich Text FormatodfODF Text DocumentodpOpenDocument PresentationodsOpenDocument SpreadsheetxpsXML Paper SpecificationcsvComma-Separated ValuesxmlExtensible Markup LanguageepubElectronic PublicationazwKindle Format 8fb2FictionBookmobiMobipocketswfSmall Web FormatbmpMicrosoft Windows bitmapgifGraphics Interchange FormatpsAdobe PostScriptpsdAdobe Photoshop bitmaptiffTagged Image File FormatoxpsOpen XML Paper SpecificationwpsWPS OfficevcfElectronic business cardsmsgOutlook email message formatemlEmail message formatpubMicrosoft PublisherpagesApple PagesvsdMicrosoft Visio FormatmhtMIME Encapsulation of Aggregate HTML DocumentsmppMicrosoft ProjectjsonJavaScript Object NotationpmdAdobe PageMakerodgOpenDocument GraphicskeyApple Keynote FilenumbersApple Numbers filewpdWordPerfect DocumentdjvuDJVU Ebook FormatcbzComic Book ArchivechmMicrosoft Compiled HTML HelpartPFS: 1st PublisherrawCamera raw imageddsMicrosoft Direct Draw SurfacedibMicrosoft Windows Device Independent BitmapdpxSMPTE Digital Moving Picture Exchange 2.0 (SMPTE 268M-2003)emfMicrosoft Enhanced Metafile (32-bit)epsAdobe Encapsulated PostScriptjxrJPEG extended rangesvgScalable Vector GraphicstgaTruevision Targa imagetifTrueType font filewebpWeppy image formatxwdX Windows system window dumpdwgCAD DrawingcdrCorelDraw File FormataiAdobe Illustrator ArtworkdxfDrawing Interchange FormatheifHigh Efficiency Image File FormatheicHigh Efficiency Image File FormaticoMicrosoft iconcurMicrosoft Cursor Icon
2020-11-28 10:23:59 • Filed to: Online PDF Tools • Proven solutions
The current technology has made it easier to convert files freely without purchasing or downloading the software. A variety of free online PDF converters have been established and all is needed is just to upload your file and select the file format that you desire. PDF files can also be converted into texts using online converters. This article discusses some of the best online PDF to Text converter online.
Top 6 Software to Convert PDF to Text Online
1. Hipdf
This is an online software that allows you to make conversions from PDF to TXT online. With this online tool, you do not have to install any software or make any registration as every conversion can be made online using the website. You can convert not only PDF to text but also PDF to ePub, PDF to Excel, PDF to PPT as well as converting these formats to PDF itself. The advantage of this online software is that it is just easy to use. Users need to click on the type of conversion they want to make and it will upload and convert it almost immediately. HiPDF can work perfectly on all devices as well as all the popular browsers like Safari, Internet Explorer and Chrome browsers. With HiPDF, your document security is guaranteed as they are deleted from the server after one hour of conversion. HiPDF has a lot of other amazing features and this is why it is regarded as one of the best PDF to text online converter.
2. Zamzar
Zamzar offers free online file conversion. It supports the conversion of documents into different file formats such as JPEG, CR2, CRW, HTML, doc, ODP, texts, PDF, CSV, DWG, gif, and many more. It has only three simple steps that include, selecting the file to convert, selecting the output format, typing the email to receive the final file, and clicking 'Convert'. The conversion starts immediately and the converted file are sent to the given email. The disadvantage about this converter is that the conversion may delay and one may fail to receive the converted file.
3. PDF to Text
The PDF to Text converter is a free online software that allows an extraction of text from the PDF document. It has simple steps that only requires the user to open the website and then click upload files. After clicking upload files users are able to select the PDF document that they want to convert and then the conversion is done immediately.
4. PDF to TXT
This PDF conversion tool allows the conversion of PDF to texts. It offers a quick text extraction from the PDF. More so, it supports any PDF quality. It offers an immediate conversion and therefore you do not have to take a long time to convert you PDF file. While using this tool, no personal information is required since the output file is returned to the user's Internet browser. The free online PDF to text allows the conversion of Acrobat PDF to texts within a single click.
5. Free Online OCR
The Free online OCR allows conversion of PDF files and image of up to 2MB.the conversion takes a short time after uploading the file to the OCR. It also allows users to select the language of the their document files. It supports a multicolumn text although the recognition result is a plain text meaning that all formatting is lost during the conversion. It also supports the conversion of scanned images and PDF into word and text files.
6. UniPDF
UniPDF offers a high quality PDF conversion. It supports the conversion of PDF files into images such as JPG, PNG, BMP, TIF, GIF, PCF, TGA, word documents such as doc and rtf HTML and text in batches. The conversion preserves the layouts, formats and images of the texts. The converter allows you to select the pages that you wish to convert and the file output format for your final document.
Limitation of Online and Free PDF Signer
There is no doubt that signing your PDF documents online is simple and easy using these online tools. However, it is important to understand that there are limitations to these services especially on the number of documents you can sign at a time. For example, online tools like RightSignature and HelloSign will not allow you to sign more than 5 documents in a month. This means that it may not be suitable for someone with large documents to sign. In addition, you need to have stable and fast network connection.
The size of file that can be converted is limited. The online conversion only supports the conversion of small-sized PDFs and the file exceeding the supported size cannot be converted.
Mostly, the original features of the PDF file are not maintained since the format, the layout of converted texts is corrupted, and mostly the output file is a plain text.
Some of the online converters require users to enter their email address to receive the converted file and sometimes it takes a very long time to receive the file. Some conversion files are very slow and it takes more time to convert a single file.
Best Desktop PDF Signing Tool for Windows and Mac
PDFelement provides the best PDF converter tool. It allows conversion of different file formats into various output files such as texts. The other supported formats include, TXT, RTF, HTML, EBUP, PDF, JPEG, JPG, TIFF, BIM, GIF, Word, Excel and PowerPoint. It supports conversion of PDF documents in batches with a very incredible speed. It maintains the quality of documents since the layout and the format of the original file is maintained.
More so, PDFelement has a variety of editing tools that allows users to edit the PDF files before converting them. The editing options include adding or removing some texts. Merging or splitting some PDF documents, extracting specific PDF pages or permanently redacting sensitive texts and images. More features of the tool include the ability to add notes, create custom stamps, underline, and highlight texts. It also allows password application to PDFs to prevent unauthorized users from accessing them. Besides, it allows users to create a personalized encrypted signature to digitally sign the PDF.
Free Download or Buy PDFelement right now!
Free Download or Buy PDFelement right now!
Pmd To Pdf Converter Online
Dism restore health source files could not be found. Buy PDFelement right now!
Pdf Cube Pro 1.0
Buy PDFelement right now!
Pmd To Pdf Converter Free Software Pdf
0 Comment(s)

0 notes
Text
Event organization: How to make the process easier for your client
One of the most stressful occupations in 2017 is the event organizer, and your client must not feel it
Event organization is one of the most stressful parts of public relations. It's a job that requires a high level of concentration, the ability to multitask and a focus on detail that creates the difference between a good event and a top-notch event. Precisely because of the complexity of this work, it is important to make the process as easy as possible for the client – from the initial planning phase to the realization itself.
It all starts with a good brief
Any joint entry of the client and the agency into the event organization process requires a certain range of activities on both sides, all starting with a good brief and predefined goals that are to be achieved. If it is the client who initiates the process of organizing the event, he should know well what he wants to achieve, what goals the event needs to achieve and convey to the agency its idea as specifically as possible. A good brief allows the agency to understand its task fully. So it's very simple – the better the client brief, the better the agency will deliver a better idea.
Characteristics of a quality event organizer
At the project planning stage, it is important that the event organizer shows the client all his expertise and expertise in carrying out the agreed work. This is a priority whether it is a new or permanent client. Once built, a client's trust in the agency must not be undermined. From the very beginning of the project, the client must feel absolutely sure that the agency, i.e. the project manager, will carry out the work responsibly, professionally, in detail and precisely. The Agency must think about how to integrate the event with appropriate communication channels and tools and thereby achieve added value with what has been agreed. This step is more a sign that the agency is thinking proactively and that it does not only want to do the job, but also give one additional nuance that will highlight the event from the others.
How to make it easier for the client?
There are a number of tools used in the event organization process with the aim of quality service delivery and process facilitation:
Regular meetings and reporting on the progress of the project. It is important to always be ready for a "plan B" and have another option if the supplier does not deliver the agreed or the client changes his mind. A detailed forward plan by which the client can follow all phases of the project and everything that has been executed and what has not been done. The term plan also lists the items for which the customer is responsible in order to know in time at what point something more will have to be included in the process Detailed bill of quantities for the entire event Compile a list of items that the customer needs to confirm within specified time frames to make the whole process work smoothly Deliver visual solutions to give the client an insight into what the final product will look like "I'm not going to be a key person in the project," he said. It is desirable for a client to be present at such meetings in order not to omit key information that must be Project Cost Report Final report after the event showing whether the objective has been met Accountability on both sides
While the agency has the main task and responsibility for delivering a top-notch event, the client has an obligation to deliver accurate and timely information to the agency. The necessary things that the client needs to approve are:
Confirmation of creative idea/concept, bill of quantities and event scenarios Participation in the creation of a database of guests Briefing with event moderator, photographers, cameramen Regular meetings with the agency Partnership and feedback as the key to success
With this approach in mind, the agency, together with the client, will organize an event that will achieve a good result and predetermined goals. The partnership between the client and the agency is a formula for success, and upon completion of the project we must not forget about the feedback. Just as a quality brief is an ideal start, high-quality feedback is the ideal end of any collaboration, at least as far as this project is concerned. It is desirable if the client explained as specifically as possible what he was with and what he was not satisfied with so that the agency would better understand his needs and during the next cooperation even better implement the project. With feedback, the agency learns, progresses and grows, and the client gets even better cooperation during the organization of the next event, which he will talk about for a long time to come.
Teams Live Event Organizer Checklist Microsoft Teams Setting up devices (not webcams) If your event requires you to have your own non-Webcam cameras, make sure you have the right equipment:
Cameras
Microphones
Video absorption converter in your computer
Tripod
Drawstrings
Event Information Basic information
Title
Date
Location
Description
Invite anyone who will produce or present (including Q&moderators) as part of the event group. Wait until you create your event and have a link to an attendee.
If someone is going to share PowerPoint, invite them as a producer or presenter.
Event Settings Carefully set up access to your live event. This is very important if you plan to share sensitive information.
Select Q&A if you want to have one.
If you select Q&A,make sure that someone has planned to moderate it (and that you can make it a producer or presenter).
Make sure that the support link points to the correct support information for attendees.
Select a record available to attendees if you want attendees to be able to watch an on-demand event record.
Select a record available to producers and presenters if you want to get an MP4 record file after the event.
Invite participants Send the event link to all participants as you know – Share it on a Teams channel, send an email, share it on a website, or add it to a collaboration group.
Performance test Make sure all facilities work and the connections are solid.
Connect your Madewell (or other converter) to your USB port and try out the audio and video. Make sure your audio and video are set correctly in your device settings.
Make sure you have good illumination. We recommend that you choose a room with natural light.
DO NOT click Start during testing. You cannot stop and restart the event later – you will need to schedule a new document to send to attendees. (If you want to try this out, we recommend that you conduct a live rehearsal a few days before a small group of people.)
Check the participant link wherever you sent it to your audience.
Your link should point to the actual event. If you follow it, you should see a blue screen that says "The live tournament is not started."
Make sure that you and all presenters have content of the event that is ready to share.
Courtesy:event organizer in lahore
0 notes
Text
Your Email Can't Be Sent? Let's Fix It Ourselves
There is limited shortage of autoresponders available for sale. If you do not believe me, just call at your favorite online and have a look. However, there are number of that are good for the average home site owner who searching for to boost their MLM or network marketing business. I might like to review just a few things to be able to for when choosing an autoresponder or bulk email prepare.
When a computer virus or trojan has infected an user's computer, it will likely open a 'backdoor' enable hackers use the infected computer for malicious purpose the actual owner facts. This infected computer is called zombie. Furthermore, the hacker can sell the target computer associated with others and others can use if in relation to own role. If a spammer has gained an access to the target computer, it employs it to send out spam.
I did say video; most digital camera will shoot video. The Exilim, as a little older, shoots AVI (lower resolution) video. Much of the cameras shoot MPEG files which are higher judgment. smtp server gmail
A spyware is software used by hackers and advertisers acquire information a person. When visiting certain websites, you're motivated to install might be the sort of software or updates that will need and the updates you installed turn out to be spyware. Spyware can also install itself in your and it consumes memory usage and often will slow down your internet.
Because seo you check out the Internet, you get yourself a different IP, so quite often you will get a new dynamic IP, the actual reason blocked from your block-lists and you will have no capability to email.
Google Documents has evolved into a real boon. The rii the skill to upload and open Word, Excel and PowerPoint posts. Two key points - again comprise one quite simply can grow to your documents from any computer. But secondly, perform easily collaborate on a document or spreadsheet with simple 'sharing' on coursesmart. You can share a single document or maybe entire folder of credentials. Great for collaboration, bulk email server you can create word processing documents, spreadsheets and presentations.
Have you been on the site, and noticed the sales pitch you are reading never mention Precisely what PRODUCT OR SERVICE was being sold? Then you probably may have. They paint this beautiful picture about fancy cars and mansions; trips to exotic paradise resorts, and the only thing can be yours?! Umm, not quite. This type of person selling you the "Dream" of experiencing a wealthy lifestyle. The domain name of these programs are 'Multi-level Marketing schemes'(MLM), or they may be called 'Pyramid schemes'. Results in to aid recruit individuals want by feeding them the same dream an individual were fed. The only ones making a real income are the creators of the program.
There are in all likelihood hundreds of variations from this theme. I do not claim is actually because perfect on the other hand does allow me to do a thing I do in my office anywhere I venture.
0 notes
Photo

It’s actually probably a little late for this because most people have already bought their laptops. But hey you know what I’m gonna do this anyway.
I was lucky when I bought my laptop. My dad was big into Microsoft and taught me to be very wary and serious about buying a laptop for college. There’s a lot to consider and it’s important to know all of the laptop jargon and everything when you’re looking for a laptop. I never got an honest student-to-student guide on laptops so I wanted to make one.
Preface: Rules for Looking at Laptops
1. Consider what you will use your laptop for first. Almost all college students will use their laptop for these things:
- Typing
- Watching videos
- Reading
- Messaging
If you plan to use your laptop for gaming or video production or photo editing, you need to consider the specs of your computer and the system requirements for the products you want to use. Consider getting a computer that has expandable storage or purchasing an external hard drive. When buying a computer, don’t forget that the operation system and preinstalled programs will take up some of the listed storage.
2. Do your own research.
Write down all the things you think you want to be able to do with your laptop. Read reviews, go to more than one store. Go to the Apple Store on a weekday and ask them questions about the laptop. I’ve found that the Apple employees tend to be kind of vague unless you pester them and it’s easier to do that when the story is less crowded. They assume that if you’re in their for a laptop, you’ll easily buy it just for the logo on the back.
3. Look for student discounts and consider a protection plan. Also consider your school’s tech store and your school’s location to the nearest specialist for your computer. Do not buy a laptop that you would need to send away to get fixed if you can help it. There’s nothing like your harddrive giving out the day before an essay is due. Apple and Microsoft both offer like a 20% student discount if you give them proof or a student email.
4. Check to see if your school will give you the Office Suite for free. Pages and Google Docs are great but Google Docs is kind of painfully unprofessional looking and pages is kind of annoying so I recommend that you get access to Microsoft Office for Word, OneNote, and Powerpoint. Chances are your school may also offer Photoshop CC and Final Cut for free so know what you can get for free from your school and the specs you’ll need to use those if you want to. In some cases you can also get these programs for free to use on library desktop computers.
5. AN IPAD IS NOT ENOUGH. Tablets are great but you’re going to HATE YOURSELF for your first all-nighter. If you want a tablet that bad, consider buying a 2-in-1 or bringing a tablet along with your laptop. I have known people who bring only IPads and they did not have a fun time writing essays.
Now that you know the rules let’ s get on the laptops.
I want to say that I don’t really know that much about laptops. Like I know the basic basics but like you know whatever. I’m gonna do my best so please let me know if there is something I said wrong or something I should add.
Processors and RAM
Processor: Your computer’s brain. How fast can your computer do things? the higher the number the better. i5 or i7 are usually the most common for college students.
RAM= Random Access Memory : How much shit your computer can do at one time. The higher this number, the more things you can run at once. This is why when you have 35 apps open on your phone it gets too hot and slow. It doesn’t really have that kind of RAM. 8 GB of RAM is usually the base but if you do more, you can go up to 16.
College Kid Computers
I’m a big PC gal so I will vouche for that real hard. But I’m trying to be fair.
There are generally five laptops (or laptop adjacents ) you will come across in college: MacBook (including the Pro), SurfaceBook, the Surface, Chromebooks, and Razers. Othe alternatives include Lenovo Yogas (which are cute as shit), Surface Laptops (I don’t believe in these because they have fabric on them but they come in cute colors), and the HP Spectre.
MacBooks are usually best for video and audio editing. They have fantastic displays and you can get great support for them on campus because they are so common. However, they have very little ventilation and even though on campus help is common, due to the way Apple likes to conduct itself, they will need to be sent away if you’re having a serious problem. They can also get expensive so don’t cop out and try to buy a cheap model with low storage because YOU WILL REGRET IT. I had a friend who did that and she had to lug around an external hard drive because she didn’t have enough storage to do projects on her laptop. There are two types: the MacBook and the MacBook Pro. The Pro is probably the better option but it costs a lot more. However, the keyboard is better and it is a little sturdier so it will probably last longer.
Surface Books are really nice. This is the laptop I have. It’s best for photo editing and like design because it has the pen. The Surface Book separates into a tablet and comes with the Surface Pen. They’re windows computers so they come with Office and if you use a windows computer at home, it’s easiest to adjust and transfer over important files. It also separates into a tablet and has a crazy nice battery life because it has two batteries. This computer has pretty decent ventilation and directs all of the heat it generates to the battery on the screen of the computer so it will not burn your thighs! However, these computers are super new so there is no IT support for them on most campuses. These computers are also HELLA ‘spensive because it is a 2-in-1. It start at like $1500 I think. Also, because of the tablet bit, they have a weird hinge that makes the computer gap when closed which is kind of ugly.
Surfaces are often considered to the best college PC. They have an adjustable kick stand and a nice keyboard. They come with the pen and they’re nice and lightweight. Since they aren’t really laptops though they don’t make good computers for lap work and again, because they’re on the more uncommon side, IT support on campus is weak.
Chromebooks are kind of weird. They’re nice and cheap which is cool but that’s really about it. There are my least favorite laptops. If you’re going to bring a desktop to school, this is a great idea because it’s simple and it will get the job done. But it cannot run anything in the Office suite or any other programs you might need for class like statistics software or even Arduino. It can only run web apps and chrome extensions. While Google Drive apps are great for group projects, they aren’t the best for writing papers and making presentations so take that into consideration.
Razer Blades are the most high end of the laptops. They are fucking MONSTERS. These are great for everything from design to video gaming. I haven’t heard anything bad about these computers to be honest. They're gorgeous machines with rainbow keyboards that come with presets for how they light up which is lit as fuck. They can run League of Legends pretty smoothly and I really don’t know anyone who has had a problem with them. I do suggest you have some knowledge of computers before you order one of these though because I think it’s more common to order them online. If you plan on playing a lot of games on your laptop while you’re in college this is probably your best bet. ALSO IF YOU WANT A DANK KEYBOARD OMG THIS WILL CHANGE YOUR LIFE. The click of a Razer Chroma Keyboard is the music of my dreams.
#university#masterpost#guide#laptops#mine#heysareena#emmastudies#elkstudies#scholarcord#studyblr#langblr#computers#college masterposts#college#razer blade#surface book#macbook#chromebook#what else can I tag this with#uh#intellectys#hnnnng#hm I hoep this helps#please don't roast me for knowing only 0 things about laptops#haha#I made that banner in like 1 second#that is the least work I've put into any design ever lol#oops#I hope this is helpful#doing the research for this I want to buy a razer blade so bad
642 notes
·
View notes
Text
TPE 4.8: Use digital tools and learning technologies across learning environments as appropriate to create new content and provide personalized and integrated technology-rich lessons to engage students in learning, promote digital literacy, and offer students multiple means to demonstrate their learning.


My classroom I am teaching in is a first grade classroom at Bell Avenue Elementary School in the Robla school district. 90.8% of our school demographic is categorized as socioeconomically disadvantaged by the SARC reports. Our students are predominantly Latinx, followed mostly then by Asian and, Caucasian, then other. Our school goes from preschool to 6th grade, and we have a wide variety of support staff, including enrichment teachers, special education teachers and aids, and Hmong outreach liaison. After looking at technology at my school, this is what I saw.
-Shared Vision: I have not seen a shared vision surrounding technology school wide. However, every student at our school get technology class once a week, all classrooms have technology in varying forms in them, and the teachers on my 1st grade team meet and discuss how technology will be used across their lessons.
-Empowered Leaders: The different levels are encouraged to be leaders in different ways. One of the teachers on my team right now is being a leader by powering several different curriculum programs, giving the teachers I work with opportunity to have input on what curriculum they use in the classroom. Students at our school are also involved in student government, which allows them more of a voice in the school, and many classrooms have class representatives for the same reason.
-Implementation Planning: I have seen cooperation between different grade level teachers and the technology teacher. The technology teacher asks grade teams their opinions on programs he should use with their students, and how it should be done, giving both sides input.
-Consistent and Adequate Funding: From what I have seen, all classrooms have chrome books, the technology teacher has enough iPad for a class at a time, and he is able to purchase programs when necessary.
-Equitable Access: My school is in a very underprivileged area; however, all students and staff have great access to technology at almost all times. The school library is also open several days after school, and there are computers in there families could access.
-Skilled Personnel: This one seems to conflict itself a little at my school. Some teachers seem to know some parts of their technology well, for other parts they seem to rely on the technology teacher, and for first year teachers they seem to rely on the help of others because they did not seem to be trained.
-Ongoing Professional Learning: As I noticed for the above, there does not seem to be continuous technology training for teachers that I have seen.
-Technical Support: I have not heard of district wide technology support, however the school’s technology teacher does a lot of technology support for staff. However, this poses an issue if he is teaching a class that makes him unavailable for real time assistance.
-Curriculum Framework: The technology teacher works with each grade level team to make sure what is being taught in technology class is not only building the skills students have surrounding technology, but that the lessons also support what is being taught by the teachers.
-Student-Centered Learning: In the individual classroom I am in, technology is used more so as a way to feed information into the students. However, in technology class the students become much more active in their own learning through technology.
-Assessment and Evaluation: Technology is definitely a positive asset in teaching the academics, and teachers seem overall successful in using the technology in this way. However since I work in first grade, the students do not have a lot of access to technology themselves to aid in their own learning.
-Engaged Communities: Many teachers at the school use communication apps to have constant contact with families, emails are sent out to families, social media is used to connect with families, and a lot of the curriculum programs have stories and games kids can have access to at home to build on their learning in the classroom.
-Support Policies: I have not seen any explicit support policies in place.
-Supportive External Content: Our school makes sure to stay up to date on policies and standards, but I have not seen a direct connection between this and how technology functions in the school setting.
Focusing on my school’s technology usage was very interesting! In the Computers Meet Classroom: Classroom Wins article (Cuban, 1993), he states “the seemingly marginal use of computers and telecommunications in schools and classrooms is due less to inadequate funds, underprepared teachers, and indifferent administrators than to dominant cultural beliefs about what teaching, learning, and proper knowledge are and how schools organize their instruction”. Reflecting on this quote in relation to my school made me think about how a lot of the upper grade classrooms are set up for frequent technology use by students, but now all of the rooms are like that, such as mine. This is relating to how my school organized their instruction. One thing I do see a lot of at my school is using technology as a way to track students’ work and progress, and that is one thing the COSN 2017 report discusses as a benefit. One suggestion I would make for my school’s technology use is having more hands on activities with technology. The way my school uses technology reminds me of the reverse or a flipped classroom, where lectures are pre-done and activities is more about where the learning is done (Educause, 2012). I think that if technology was used as a more hands on activity for my students’ learning, it would benefit them.
Cuban, Larry. Computer Meets Classroom: Classroom Wins. Teachers College Record Volume 95 Number 2, 1993, p. 185-210. http://www.tcrecord.org ID Number: 82, Date Accessed: 10/31/2019
EDUCASE. (2012). 7 Things You Should Know About… Flipped Classrooms. Retrieved October 31, 2019, from https://library.educause.edu/-/media/files/library/2012/2/eli7081-pdf.pdf
(Links to an external site.)
Freeman, A., Adams Becker, S., Cummins, M., Davis, A., and Hall Giesinger, C. (2017). NMC/CoSN Horizon Report: 2017 K–12 Edition. Austin, Texas: The New Media Consortium.
ITSE. (2019). Essential Conditions. ITSE.
Reflection: For this TPE, I provided two pieces of evidence. The first piece that is shown is two screenshots of a lesson I taught over zoom to a group of students that demonstrates different means of expressing their learning. In the screenshots, you can see that the students were able to handwrite their thinking and use Flipgrid to upload their graphic organizers to me. Students were also able to dictate their thoughts to me that I typed into a shared powerpoint to give them another way to demonstrate their knowledge without having to write something. This is evidence of the technology tools closing the equity gap, since students were able to use the tool to have multiple means of expressions (Hwang, 2019). The second piece of evidence is evaluating technology usage at Bell Avenue Elementary, the school I did my student teaching at. This evaluation focuses on technology use in the classroom before distance learning, which enables me to assess technology usage across environments my students are being asked to learn in; both the classroom and school and now their own home online, through the lens of the ISTE standards (ISTE, 2019).
Hwang, K. (2019, April 18). 4 ways to improve digital equity in your classroom. Common Sense Education. https://www.commonsense.org/education/articles/4-ways-to-improve-digital-equity-in-your-classroom
ITSE. (2019). Essential Conditions. ITSE.
0 notes
Text
Profitable Webinars Made Easy
Profitable Webinars Made Easy
Webinars are a profitable and popular way to disseminate information to a lot of people at one time. It's just like an in person seminar except that it's performed over the Internet. You give presentations just like you would in person with slides, handouts, and other companion information. It is essentially a web based seminar. You can teach a class, deliver a lecture, conduct a workshop, and host an interactive Q & A event via webinar.
The technology allows event hosts to deliver their information to multiple locations at the same time because the attendee simply needs to be able to sign on to a computer terminal with Internet access to participate in the event. Usually attendees can participate in a variety of ways from chatting in a chat room, to raising their hand electronically to speech, by using a microphone.
If you have a lot of information you want to disseminate to a number of individuals or groups but don't want to spend a lot of money doing it, a webinar is your answer. Participants can join from anywhere, home, work, any country -- as long as they have a computer and an Internet connection they can join.
They are economically feasible for small or large groups. What's more, they are secure, in that unauthorized people cannot enter the webinar. In most cases the participants only have to download a small program to help them access the event, have ear phones with a microphone, the special link or password to join, and they are in.
Why Have a Webinar?
Many reasons for having webinars were mentioned above, but let's get specific. Hosting a webinar can advance your business to the next level. It can jump start and excite affiliates, and customers alike. Face it, events are fun but they can be expensive and hard to plan. Webinars can be planned from the comfort of your home office, or from any location with computer access and an Internet connection.

Lead Generation
Webinars are an effective way to generate more leads. But you'll need to book speakers that excite your target audience. A targeted topic will also help draw both speakers and attendees. By providing targeted content through a webinar platform with planned speakers you will position yourself to become a thought leader who provides credible, valuable and usable information about your niche.
To generate leads with a webinar you'll need to ask for information at registration. That information should be sent to an email marketing mailing list segmented for potential webinar attendees. In this way you will be collecting leads via your webinar sign up process. By marketing the webinar, you're marketing your email list.

Earn More Money
Another great reason to host a webinar is to make more money. Even if your initial goal is to get more subscribers, with more targeted subscribers you're going to generate more income in the long run. But, if you charge for your webinar you could make more money in an hour than you thought possible. Imagine if you sold the hour for just 10 dollars each. If just 100 people attend the webinar you will have earned 1000 dollars for the hour. Granted you have to spend time developing the event, but imagine if you perfect the event and create a series conducting weekly webinars. How will that add to your bottom line?
Advance Content Marketing
The other thing that webinars do is simply disseminate content in a new way. From one hour long webinar you can create a year's worth of content all from one event if you set it up right. Just get four to six speakers, record the event, then repackage the event in multiple ways to generate almost unlimited content all year long.
Once a webinar is over you can break it down to shorts that you use in your email marketing blurbs or as an eCourse. You can also transcribe it and create an eReport out of the event. Some people are creating Kindle books out of webinar materials. The sky is the limit with the amount of and different forms the content can take from just one webinar event.
Customer Satisfaction
Sometimes your goal is simply to improve customer satisfaction over a product. You might invite only people who have bought your product or service to a webinar that is exclusive to them. Your goal in this case is perhaps to conduct a Q & A to help customers utilize a product or service more fully.

Your objectives for having the webinar can be more than one of the above, but it’s better if you focus on just one or two objectives in order to create marketing materials that work. Determining objectives and setting goals indicates what metrics to study when deciding whether your event was a success or a failure. Having metrics to look at will assist you in perfecting future webinar events by identifying what works and what doesn't work. By doing so, you'll be able to develop a best practices manual for webinars of your own that is fully targeted to your unique market.
Choose Your Technology
Once you've decided your topic, objectives and goals it's important to choose what kind of technology you need to market the webinar, perform the webinar and follow up after the webinar in order to reach your stated goals.
Webinar Technology
You'll need to choose which type of webinar technology you need based on your goals for the event and your budget. Keep in mind that you want it to be user-friendly, look professional from the viewpoint of the customer, and fit into your budget.

To determine what type of webinar technology you want to use think about how you want it to function and what type of presentation you're going to give. Then choose the software that best fits with what you need right now. You can always switch webinar technology later.
Most webinar software offers some or all of the following features:
Break-out Sessions
Enabled to Present Slides (Power Point)
File Transfer
Polls and Surveys
Recording Ability
Screen or Desktop Sharing
Sharing of Hyperlinks
Text Chat
Tracking of attendance
Two Way Audio
Whiteboard
Ability to Charge for Event
There are many inexpensive webinar technologies available such as Zoom, Click Webinar, GoToWebinar. Each of these has various parts if not all of the features listed above. No matter what other people recommend, it's important that any technology you choose works for you.

ü Zoom -- For about $54.99 per month you can host meetings for up to 100 attendees. Broadcast to Facebook Live or YouTube, participant chat and polling, desktop sharing, PowerPoint and multiple file types are supported.
ü Any Meeting -- The non-ad supported cost is about $78.00 a month for up to 100 attendees. This meeting software has basic features such as custom registration forms, email invitations and ticketing when integrated with PayPal. You can record events.
ü Click Webinar -- Touts itself as the "world's easiest webinar software" offers rebranded systems for up to 100 attendees for 55.00 per month. There is moderated and private chat available as well as browser sharing. You can record events.
Which technology you choose will depend on your goals, your budget, and what features you believe that you need. Most of these offer a free trial so that you can try out the technology before you buy. Try the technology out well before the event, buy the technology and have a practice run on the event in advance.
Word of Caution: To perform a profitable webinar, don't try to use free software. You really do need, at a minimum, the ability to avoid advertising during your event, the ability to present slides, two-way and one-way audio choices as well as the ability to record the event for us later. While free can sound good, it's never a good idea when it comes to hosting profitable webinars.
Tip: If you don't want to deal with the technology aspects you can outsource to a Virtual Assistant who specializes in coordinating, planning and hosting webinars on your behalf. With a Webinar VA you'd simply have to give her your materials and agenda and show up while someone else handles the technology.
Shopping Cart Technology
To have a profitable webinar you also will need some form of shopping cart technology. If your webinar software doesn't come with the ability to charge for the event, or you're selling something during the event that you want people to buy due to the event, you'll need to choose a shopping cart technology.
There are many different choices and like the webinar technology, you need to understand your purpose and goals before you choose. This is the only way to know what features that you must have, and what features are optional. In fact, even if your webinar software has the ability to sell tickets to your event, you'll still need an outside shopping cart for attendees to purchase products and services that you are recommending.
Features to look for in your shopping cart technology:
Affiliate Management
Customer Login
Digital Downloads
Discount Coupons
Email Marketing Ability
Great Customer Service
Marketing Ability
Mobile Friendly
Multiple Payment Processing Options
Online Store
PCI Certified
Social Media Integration
Tracking & Metrics
Upsell & Cross Sell Features
You have many choices, but three that you can look at are, Volusion, 1shoppingcart.com, and E-Junkie are very different choices but you can probably find something that you can afford and make work for your business. Again, don't choose the cheapest thing and expect it to work for you long-term.
Word of Caution: Choose the software with the features you need and that can grow with you. Switching shopping cart technology later can be done, but if you pick something that can grow with you now, you will be happier. Choose something that has a track record of providing services long-term and has had recent updates.

Tip: There are professionals who will set up your shopping cart software for you. If you simply do not have time to learn the technology, or just don't want to, look for a Virtual Assistant or service provider who specializes in offering assistance with shopping cart technology. If you know you want a specific type of cart, be sure to check that your service provider works with that particular technology.
Mailing List Technology
You also need some sort of mailing list technology. This will enable you to keep a list of everyone who signed up to attend the webinar so that you can send them information pertaining to the webinar before the webinar, give them reminders about the webinar so they don't miss it, and then follow up after the webinar for an opportunity to upsell and cross-sell other merchandise.
Features to look for in your mailing list technology:
Social Media Integration
Double Opt In Ability
Contact Management
Subscriber Segmentation
Email Templates
Sign up Forms
Autoresponder Features
Tracking Features
Excellent Customer Support
There are a few choices of mailing list technology for you such as Aweber, MailChimp, and iContact. These three give you pretty much all the features you would expect from mailing list software. The best software is cloud based so that you don't have to host it yourself. While sometimes the thought of more monthly fees can get to you, it's more than worth it for peace of mind and easy access to the software.
Word of Caution: Mailing software is difficult to change once you get started. It's hard to get people to switch from one list to another so choose a software that can grow with you and that has a proven track record of longevity.
Tip: At the very least get email software that allows for segmentation, double opt-in, automated subscribe and unsubscribe features, and easy to understand reports and metrics. Like with the other software you can hire experts who will run your entire email campaigns for you, uploading emails, and dealing with the technology for you.

Determine Your Webinar Topic
To choose an effective topic study your target audience. It's important to understand all the demographics of your audience in order to be able to get the topic right. It also helps to be up-to-date about industry news. You can also survey your current audience to determine topics that they'd choose to attend. To get started thinking of different topics, try brainstorming some ideas by asking these questions.
What are the problems that you can address and solve that might cause them to be interested in your webinar?
Do you already have a blog post or an eReport that involves a numbered list of tips to help solve a particular problem that your target market has?
Do you have some case studies that describe client success following an eCourse or eBook that you've put out previously?
Are you aware of current trends within your industry that you would be comfortable expounding on in a webinar?
Do you have a new product launching soon?
Any topic that fits your niche audience and addresses and solves the problems that they experience will be a success. Remember always, that in anything you do for your audience, it's about them, not you. They want solutions. If you can keep that fact straight as you formulate your topic and the information that you will present, you'll have a very successful webinar.

Find Speakers & Presenters and Keep Them Organized
It's really uncomfortable to do a hour long webinar on your own. Plus, it can get boring to the attendees. So, instead of doing that find speakers and presenters for your webinar. More speakers will mean more information, plus more attendees because each speaker will attract their own audience. This works best if the speakers aren't direct competitors but promote complementary products and services to the same target audience.
Look to Your Network
You can find speakers in a variety of ways depending upon your topic. Some topics are easier to come up with speakers than others. But you can find them through your networks, and plan the event together, or you can plan the event, and the topic, and then invite people whom you've identified as movers & shakers within your target audience community. It is highly suggested that for your first multi-speaker webinar that you plan it in advance and invite the presenters.
Set Expectations in Advance
When you invite anyone to present it's important to set expectations in advance with some kind of formal agreement. It's a good idea for you to have content approval and deadlines for participants to produce. In addition, set dates for and require attendance to practice sessions. If you have open communication and set expectations from the beginning you'll have few problems.
Send Information ASAP
If you are going to use any collaboration software, or any other software that requires special logins it's important to send them to the presenters as soon as you get them. If you've received questions from your target audience from your email marketing campaigns your presenters need to know what they are. Any information that you should share, do it immediately so that the presenters have plenty of time to act on it.
Keep Open Communication
Set up a shared calendar for all speakers for the event. In addition, it will help to have a space for all information, handouts, special offers, and presentations to be uploaded. A shared Dropbox might work, or a project management system like Basecamp will work well too. Add them to an automated email list that will send out reminders and information leading up to the date of the event so that no one forgets to show up or do their part. This is a great way to put on a professionally produced webinar event.
By choosing people that you know, or know about, setting expectations in advance of them even agreeing to participate in the event and keeping communication open throughout you're sure to experience few problems with the presenters for your event.
Develop Webinar Registration Procedures
Do you understand how attendees will register for your webinar and what happens to the information once they register? This part takes great understanding of the technology that you are using to conduct the webinar. You want the process to be simple and easy. If it is too complicated people will not join. Ensure that the system works and is sending confirmations to attendees.
Create and Collect Webinar Presentation Collateral
Every speaker or presenter should be responsible for their own presentation collateral in terms of PowerPoint slides, video that they want to use, and images for all the sales pages. Set up a schedule of when each part is due so that everyone can do their part to ensure that tasks are completed on time. Have a repository such as Dropbox or Basecamp for all the information so that each person can grab what they need to complete their tasks.
Determine Your Webinar Marketing Strategy
When you decide to have a webinar it's important to know why you're having it and what your goals are in having it. You must know who your target audience is. Knowing what they want and need is an important factor in marketing your webinar.
If you don't know who your target market is, you need to figure that out before going further. Ask yourself, "Who has bought from me in the past?" or "Who do I want to buy from me in the future?".
Then, design your marketing to match. Once you've determined your audience and your topic then you'll need to get on with determining your webinar marketing strategy.
Decide Webinar Objective
Is your objective to gather leads, make a specific number of sales, increase customer satisfaction, or something else entirely? Be very specific about the objective of the webinar so that you set up all aspects of the webinar with the objectives in mind. Write down your objectives.
Set Sales Goals
You may actually have zero sales goals in terms of product sales. Your goal might be to get 500 new email subscribers. Whatever your goals set them now based on your webinar objective. Write down your sales goals.
Set the Date & Time
Choose a time and date that most of your target audience will be available. Having the time and date in advance is essential to planning a successful webinar. Try to choose your date six weeks down the line so that you have enough time to plan and market the event. Document the date and time in your event calendar.
Identify Resources
What contacts do you have already? Consider past event attendees, customers, guests and current email list subscribers. Aside from people resources, how much money and time can you spend putting on the webinar? Know in advance what you have, so that you can work within those restrictions. Write down your budget in a small spreadsheet so that you can keep track of your expenditures. Later you'll be able to include your sales from the event to track profit.
Create Your Special Offer
Each speaker should have a special offer for attendees, it needs to be created as soon as possible because it needs to be mentioned in the sales copy. The special offer should be applicable to the event and the target audience and not outside, unrelated products and services.
Write Sales Copy
Sales pages, pay per click ads, social media ads, affiliate marketing ads, etc... all need to be created as soon as you know the topic, speakers and date.
To create a good sales page and emails remember this: Intro, body with bullets, conclusion and call to action such as a registration button. Inside each areas you should have keywords. Test out different CTAs to ensure that everyone who wants to will sign up. Also include social media buttons so that people can share the information.
Create Graphics
All speakers should have headshots, a blurb about them, and information about what part of the even they will be presenting. Plus, if they are giving out any handouts, freebies, or other information graphical representations should be created. Other graphics would be banners and buttons for advertisements and images to use within your own presentation. You can ask that your presenters contribute their own graphics to the event.
Obtain Testimonials
Ask for testimonials from people who have already used your products and services or attended one of your events. Having these testimonials on your sales page with headshots and links back to their own websites will encourage more attendees. After this event is over, send a survey to people who attended the event and ask for testimonials. Do this as soon as possible.
Follow Up
The real value for you in webinars is what happens after the webinar. Whether your goal was to gather more leads, or sale more product and services you will at the very least get sign ups from people who registered for the event. Now, you can market to them via email in a way that can't be done by a one off advertisement.
Planning in advance every aspect of your webinar event from pre-event preparation to post event is an important part of conducting a successful and profitable webinar. You really can't wing it for a webinar event. There are too many things to coordinate from the speakers to the technology, to how you will follow up with the attendees.
Conduct Your Webinar: Best Practices
It's important to understand how to conduct a successful webinar. Your actual tasks will depend on your technology and the help that you have but in general these tips will be important to learn if you want to conduct a profitable webinar. Consider these webinar best practices.
Remember Time Zones
It happens that sometimes people get mixed up with the time zones and miss a webinar even if they're speakers or the organizer. Ensure that you understand the time zones and that your computer is set correctly. You can use Google Local Time Feature to find out what time it is elsewhere. In the search box type "time location".
Remind Everyone
Using the email list software set up reminders that count down to the event for both attendees and speakers. You can even insert reminders to the speakers to "send tease to your list" or "hey today your content is due send it to xyz now please" and so forth. Reminders never hurt anyone and will ensure a better turn out all the way around.
Practice, Practice, Practice
You and the other presenters need to practice with the technology before the event. Do a complete dress rehearsal. You can even invite a special audience for the dress rehearsal to make it even more complete with audience participation.
Test the Technology
Ensure that you have good Internet service and that your speakers understand the Internet requirements. Often, using wireless can mess up VOIP, sometimes it's okay. It depends on what technology you chose. Read their requirements and conduct a test to ensure it works. Test your local tech too, such as your speakers, ear phones, desk top and anything else you plan to use during the presentation.
Choose a Moderator
This can be your webinar specialist, you, or someone else who is good at time management. The moderator is going to be responsible for ensuring that everyone sticks to their time limits and Q & A doesn't get too carried away. Sometimes moderators are also in charge of technology, so be sure that everyone knows what they're doing.

Google My classroom Video training guide
Provide an Agenda
In one of your reminders before the event provide an agenda to the attendees. They'll appreciate seeing what is going to happen during the event and it will get them excited to attend.
Start on Time
All speakers and presenters should arrive early to the event even though it's a webinar so that you can start exactly on time. Guests will not like having to wait on anyone to get started. If someone is late, have a plan in place to switch the order of events. Attendees will get frustrated and leave if you wait around for people who are tardy.
Be Human
One thing that webinars sometimes miss that in person events don't is the humanity. Sometimes people giving a presentation online are more stilted and guarded than they would be in person because they are taking in the audience's reaction. With an online webinar you cannot see anyone's face. A good suggestion is to suggest that each speaker / presenter post a mirror where they can see themselves talking so that they can maintain a human connection. Sounds weird, but it works.
Use Video
Mix up presentations from just PowerPoint to other types of information by adding in some video to your presentation. A lot of webinar software today allows the group to watch and hear YouTube.com videos or to upload video to the system for hearing and viewing. This will create more interest and make the presentations more exciting.
Open Group Chat
Many webinar software offers the ability for the attendees to chat among themselves during the event. The reason this is a great feature is because it offers the social proof that other people are there attending, right now. People will feel part of a group instead of alone. This is one huge way in which webinars different from in person events where talking during the event is discouraged.
Ask for Audience Participation
It can get boring sitting there looking at a screen. If each speaker offers a short Q & A session after their presentation the audience will feel more awake and in tune to the event. Most webinar software also allows for instant surveys and polls to be performed during the event, make use of these at least once per speaker for best results. Plan in advance how many questions, or pick a time limit and stick to it. The moderator should be in charge of ensuring that the time is managed appropriately.
Get Assistance
It can't be said enough but putting on an event, even a webinar can be challenging and time consuming. Depending on your own comfort zone you may want help with the technology, or you may need help getting all the materials prepared to the highest possible quality, or both. There are many virtual assistants who specialize in webinars who are ready and willing to help.
By incorporating these webinar best practices into your planning, you'll create a situation where you cannot have anything but a successful, profitable webinar. After all, you want to succeed with your webinar.
Create an Email Marketing Follow Up Campaign
As you see, the webinar marketing strategy is not over when the webinar is over. You must follow up with both attendees and those who missed it to get the full benefit out of conducting a webinar in the first place. Let's go a little more into following up.
Most of the money making occurs after the event is over, during the follow few weeks and even years later if they remain on your mailing list. Many sales will occur within the first week of the event when the attendees go over the material, look at the special offers, and utilize their coupons. There are ways to increase sales both directly after an event, and in the later weeks and months past the event.
Offer the Recording of the Webinar
Once the event is completed you can offer the recording of the event either for free to attendees or as an up-sell after the event. Whether you offer it free or for a fee will depend on whether the event was a paid event or a free event. If it was a paid event up-selling access to the recording is a good option. If the event was free, it's better to just send the entire recording to all subscribers as well as post it on your website.

Optionally, you can offer another event as a viewing of the recorded webinar with a Q & A session after the recording is shown. This gives you an opportunity to have another quasi live event without having to do the entire thing over again. Any of the speakers could do this on their own with a copy of the recording hosting their own Q & A after.
Send a Survey to Attendees
It was mentioned earlier, but it's important enough to mention it here. Create a survey prior to the event to be sent out automatically a few hours after the event is complete. Ask them questions about the seminar and ask for feedback regarding possible topics they'd like to see in the future.
Offer an additional incentive such as a percents off coupon or an unannounced special offer or freebie to people who complete the survey. A good idea might be to have each speaker create a check list or one page of information such as step-by-step instructions for their topic then package that together as an incentive.
Send a Thank You to Attendees
Within 48 hours of your webinar send an email Thank You message. If you promised any additional information during the webinar this is a good place to include it. For instance, during a live event it's possible that someone asked for information during the Q & A that you needed to send out, do it now. Everyone will be happy that you are sending the information and that you heard them during the live event.
This is also a good place and time to send out a link to or an invite to the recorded event. Some people like watching events over again, especially if they got distracted during the event by something at home or in the office. Being able to see it again will reinforce anything that was taught or brought up.
If you made contact with any one individual that wants a personal follow up, based on the Q & A, or the survey, follow up within 7 days to be most effective. People have short attention spans, the first week after the event is very important so be prepared in advance with the content loaded into your email marketing system in advance as much as possible.
Wrap It All Up
Conducting a profitable webinar takes planning to accomplish. But, once you do one, you'll see for yourself how easy it is to build your mailing list, attract new audiences, and reap the benefits of increased profit. Whether you use webinars for training, product help, list building, or to promote new products is up to you, either way you'll discover that webinars are simple, fun and profitable.
0 notes
Text
June 24: Ships that pass in the night (Chapter Four)
Title: Ships that pass in the night (Chapter Four) Tags: Alternate Timeline, AU, Slow burn, stranger to friends, friends to lovers Words: 2750 Summary: Dan and Phil are YouTubers. The catch? They’ve never met, and Phil doesn’t want them to.
Prompt: this was written on the same day as yesterday’s chapter. I’m in love with this fic and it seems you guys are too… thank you so much for all your kind comments, I really really really love reading them all. My friend is here this weekend so I’ll try and get tomorrow’s up but it might not be possible. I’ll tery for you guys though! FEDIJ Day: June 24 Previous Day | Masterlist of fics so far
#my fics#phanfiction#fanfic#fanfiction#phanfic#phanfic fluff#dan and phil#dnp#fedij#fic#fic a day#fic every day#fic every day in june#fic project#fic prompt#phan#phandom#phanfic au#prompt fic
57 notes
·
View notes