#fidonet
Explore tagged Tumblr posts
Text
I am pre-internet.
(By trope-specific i mean for example all the slash fics hosting websites, or the nsfw-only ones, etc)
11K notes
·
View notes
Text
Fidonet (or FidoNet as a WikiName) was/is a world-wide hobbyist communications network that was started by an anarchist (TomJennings) who specified only two rules for behavior.
Don't be excessively annoying.
Don't be easily annoyed.
There were lots of other operational and organizational rules that came along afterward, but these two rules formed the base of much of everything else. The ambiguity of these rules (what is "annoying") is actually a strength, because it recognizes that not everyone has the same threshold for annoyance. The first rule is one most people don't have a problem with. Telling others not to be annoying is easy. It's the second rule where things get interesting. Telling people not to be "excessively annoyed" recognizes that in any public exchange of ideas, there is likely going to be something that annoys you. Maybe you should increase your threshold of annoyance.
0 notes
Text
Erinnerung aus der #Vergangenheit:
Vor der Zeit des #Internet gab es das System mit #Mailbox die dann teilweise in Netzen wie #MausNet oder #FidoNet untereinander kommuniziert hatten. Als #Point hatte man im Regelfall ein #Pointprogramm (bei mir war das #CrossPoint | ich habe es geliebt) und holte mit einem #Modem (erst 2400er dann 9600 Baud, die ganz flotten hatten etwas mit 16k) meist einmal am Tag seine Nachrichten ab (Flatrate etc. gab es nicht)
Es gab damals schon Gruppen so das man sich ungestört zu Themenbereichen unterhalten konnte.
Es gab aber auch damals schon das Problem, das so manch #Kommunikation dann aus den Ruder lief. Irgendwann gab es dann die geniale Einrichtung einer Gruppe in der man sich frei von der Leber weg beschimpfen und beleidigen konnte. Alle Beiträge die an diese Gruppe gesendet wurden, wurden automatisch vom System anonymisiert, so das niemand wusste wer steckt denn nun wirklich hinter welcher Schimpftriade. Es gab nur eine Regel: Es gibt keine Regel.
Manchmal frage ich mich, warum gibt es das nicht im #Fediverse. Eine Gruppe in der die Leute ihre Wut abbauen können ...
#Fediverse#internet#Kommunikation#Mailbox#Fidonet#Mausnet#Vergangenheit#modem#Point#Pointprogramm#CrossPoint
0 notes
Text
Shamir Secret Sharing
It’s 3am. Paul, the head of PayPal database administration carefully enters his elaborate passphrase at a keyboard in a darkened cubicle of 1840 Embarcadero Road in East Palo Alto, for the fifth time. He hits Return. The green-on-black console window instantly displays one line of text: “Sorry, one or more wrong passphrases. Can’t reconstruct the key. Goodbye.”
There is nerd pandemonium all around us. James, our recently promoted VP of Engineering, just climbed the desk at a nearby cubicle, screaming: “Guys, if we can’t get this key the right way, we gotta start brute-forcing it ASAP!” It’s gallows humor – he knows very well that brute-forcing such a key will take millions of years, and it’s already 6am on the East Coast – the first of many “Why is PayPal down today?” articles is undoubtedly going to hit CNET shortly. Our single-story cubicle-maze office is buzzing with nervous activity of PayPalians who know they can’t help but want to do something anyway. I poke my head up above the cubicle wall to catch a glimpse of someone trying to stay inside a giant otherwise empty recycling bin on wheels while a couple of Senior Software Engineers are attempting to accelerate the bin up to dangerous speeds in the front lobby. I lower my head and try to stay focused. “Let’s try it again, this time with three different people” is the best idea I can come up with, even though I am quite sure it will not work.
It doesn’t.
The key in question decrypts PayPal’s master payment credential table – also known as the giant store of credit card and bank account numbers. Without access to payment credentials, PayPal doesn’t really have a business per se, seeing how we are supposed to facilitate payments, and that’s really hard to do if we no longer have access to the 100+ million credit card numbers our users added over the last year of insane growth.
This is the story of a catastrophic software bug I briefly introduced into the PayPal codebase that almost cost us the company (or so it seemed, in the moment.) I’ve told this story a handful of times, always swearing the listeners to secrecy, and surprisingly it does not appear to have ever been written down before. 20+ years since the incident, it now appears instructive and a little funny, rather than merely extremely embarrassing.
Before we get back to that fateful night, we have to go back another decade. In the summer of 1991, my family and I moved to Chicago from Kyiv, Ukraine. While we had just a few hundred dollars between the five of us, we did have one secret advantage: science fiction fans.
My dad was a highly active member of Zoryaniy Shlyah – Kyiv’s possibly first (and possibly only, at the time) sci-fi fan club – the name means “Star Trek” in Ukrainian, unsurprisingly. He translated some Stansilaw Lem (of Solaris and Futurological Congress fame) from Polish to Russian in the early 80s and was generally considered a coryphaeus at ZSh.
While USSR was more or less informationally isolated behind the digital Iron Curtain until the late ‘80s, by 1990 or so, things like FidoNet wriggled their way into the Soviet computing world, and some members of ZSh were now exchanging electronic mail with sci-fi fans of the free world.
The vaguely exotic news of two Soviet refugee sci-fi fans arriving in Chicago was transmitted to the local fandom before we had even boarded the PanAm flight that took us across the Atlantic [1]. My dad (and I, by extension) was soon adopted by some kind Chicago science fiction geeks, a few of whom became close friends over the years, though that’s a story for another time.
A year or so after the move to Chicago, our new sci-fi friends invited my dad to a birthday party for a rising star of the local fandom, one Bruce Schneier. We certainly did not know Bruce or really anyone at the party, but it promised good food, friendly people, and probably filk. My role was to translate, as my dad spoke limited English at the time.
I had fallen desperately in love with secret codes and cryptography about a year before we left Ukraine. Walking into Bruce’s library during the house tour (this was a couple years before Applied Cryptography was published and he must have been deep in research) felt like walking into Narnia.
I promptly abandoned my dad to fend for himself as far as small talk and canapés were concerned, and proceeded to make a complete ass out of myself by brazenly asking the host for a few sheets of paper and a pencil. Having been obliged, I pulled a half dozen cryptography books from the shelves and went to work trying to copy down some answers to a few long-held questions on the library floor. After about two hours of scribbling alone like a man possessed, I ran out of paper and decided to temporarily rejoin the party.
On the living room table, Bruce had stacks of copies of his fanzine Ramblings. Thinking I could use the blank sides of the pages to take more notes, I grabbed a printout and was about to quietly return to copying the original S-box values for DES when my dad spotted me from across the room and demanded I help him socialize. The party wrapped soon, and our friends drove us home.
The printout I grabbed was not a Ramblings issue. It was a short essay by Bruce titled Sharing Secrets Among Friends, essentially a humorous explanation of Shamir Secret Sharing.
Say you want to make sure that something really really important and secret (a nuclear weapon launch code, a database encryption key, etc) cannot be known or used by a single (friendly) actor, but becomes available, if at least n people from a group of m choose to do it. Think two on-duty officers (from a cadre of say 5) turning keys together to get ready for a nuke launch.
The idea (proposed by Adi Shamir – the S of RSA! – in 1979) is as simple as it is beautiful.
Let’s call the secret we are trying to split among m people K.
First, create a totally random polynomial that looks like: y(x) = C0 * x^(n-1) + C1 * x^(n-2) + C2 * x^(n-3) ….+ K. “Create” here just means generate random coefficients C. Now, for every person in your trusted group of m, evaluate the polynomial for some randomly chosen Xm and hand them their corresponding (Xm,Ym) each.
If we have n of these points together, we can use Lagrange interpolating polynomial to reconstruct the coefficients – and evaluate the original polynomial at x=0, which conveniently gives us y(0) = K, the secret. Beautiful. I still had the printout with me, years later, in Palo Alto.
It should come as no surprise that during my time as CTO PayPal engineering had an absolute obsession with security. No firewall was one too many, no multi-factor authentication scheme too onerous, etc. Anything that was worth anything at all was encrypted at rest.
To decrypt, a service would get the needed data from its database table, transmit it to a special service named cryptoserv (an original SUN hardware running Solaris sitting on its own, especially tightly locked-down network) and a special service running only there would perform the decryption and send back the result.
Decryption request rate was monitored externally and on cryptoserv, and if there were too many requests, the whole thing was to shut down and purge any sensitive data and keys from its memory until manually restarted.
It was this manual restart that gnawed at me. At launch, a bunch of configuration files containing various critical decryption keys were read (decrypted by another key derived from one manually-entered passphrase) and loaded into the memory to perform future cryptographic services.
Four or five of us on the engineering team knew the passphrase and could restart cryptoserv if it crashed or simply had to have an upgrade. What if someone performed a little old-fashioned rubber-hose cryptanalysis and literally beat the passphrase out of one of us? The attacker could theoretically get access to these all-important master keys. Then stealing the encrypted-at-rest database of all our users’ secrets could prove useful – they could decrypt them in the comfort of their underground supervillain lair.
I needed to eliminate this threat.
Shamir Secret Sharing was the obvious choice – beautiful, simple, perfect (you can in fact prove that if done right, it offers perfect secrecy.) I decided on a 3-of-8 scheme and implemented it in pure POSIX C for portability over a few days, and tested it for several weeks on my Linux desktop with other engineers.
Step 1: generate the polynomial coefficients for 8 shard-holders.
Step 2: compute the key shards (x0, y0) through (x7, y7)
Step 3: get each shard-holder to enter a long, secure passphrase to encrypt the shard
Step 4: write out the 8 shard files, encrypted with their respective passphrases.
And to reconstruct:
Step 1: pick any 3 shard files.
Step 2: ask each of the respective owners to enter their passphrases.
Step 3: decrypt the shard files.
Step 4: reconstruct the polynomial, evaluate it for x=0 to get the key.
Step 5: launch cryptoserv with the key.
One design detail here is that each shard file also stored a message authentication code (a keyed hash) of its passphrase to make sure we could identify when someone mistyped their passphrase. These tests ran hundreds and hundreds of times, on both Linux and Solaris, to make sure I did not screw up some big/little-endianness issue, etc. It all worked perfectly.
A month or so later, the night of the key splitting party was upon us. We were finally going to close out the last vulnerability and be secure. Feeling as if I was about to turn my fellow shard-holders into cymeks, I gathered them around my desktop as PayPal’s front page began sporting the “We are down for maintenance and will be back soon” message around midnight.
The night before, I solemnly generated the new master key and securely copied it to cryptoserv. Now, while “Push It” by Salt-n-Pepa blared from someone’s desktop speakers, the automated deployment script copied shard files to their destination.
While each of us took turns carefully entering our elaborate passphrases at a specially selected keyboard, Paul shut down the main database and decrypted the payment credentials table, then ran the script to re-encrypt with the new key. Some minutes later, the database was running smoothly again, with the newly encrypted table, without incident.
All that was left was to restore the master key from its shards and launch the new, even more secure cryptographic service.
The three of us entered our passphrases… to be met with the error message I haven’t seen in weeks: “Sorry, one or more wrong passphrases. Can’t reconstruct the key. Goodbye.” Surely one of us screwed up typing, no big deal, we’ll do it again. No dice. No dice – again and again, even after we tried numerous combinations of the three people necessary to decrypt.
Minutes passed, confusion grew, tension rose rapidly.
There was nothing to do, except to hit rewind – to grab the master key from the file still sitting on cryptoserv, split it again, generate new shards, choose passphrases, and get it done. Not a great feeling to have your first launch go wrong, but not a huge deal either. It will all be OK in a minute or two.
A cursory look at the master key file date told me that no, it wouldn’t be OK at all. The file sitting on cryptoserv wasn’t from last night, it was created just a few minutes ago. During the Salt-n-Pepa-themed push from stage, we overwrote the master key file with the stage version. Whatever key that was, it wasn’t the one I generated the day before: only one copy existed, the one I copied to cryptoserv from my computer the night before. Zero copies existed now. Not only that, the push script appears to have also wiped out the backup of the old key, so the database backups we have encrypted with the old key are likely useless.
Sitrep: we have 8 shard files that we apparently cannot use to restore the master key and zero master key backups. The database is running but its secret data cannot be accessed.
I will leave it to your imagination to conjure up what was going through my head that night as I stared into the black screen willing the shards to work. After half a decade of trying to make something of myself (instead of just going to work for Microsoft or IBM after graduation) I had just destroyed my first successful startup in the most spectacular fashion.
Still, the idea of “what if we all just continuously screwed up our passphrases” swirled around my brain. It was an easy check to perform, thanks to the included MACs. I added a single printf() debug statement into the shard reconstruction code and instead of printing out a summary error of “one or more…” the code now showed if the passphrase entered matched the authentication code stored in the shard file.
I compiled the new code directly on cryptoserv in direct contravention of all reasonable security practices – what did I have to lose? Entering my own passphrase, I promptly got “bad passphrase” error I just added to the code. Well, that’s just great – I knew my passphrase was correct, I had it written down on a post-it note I had planned to rip up hours ago.
Another person, same error. Finally, the last person, JK, entered his passphrase. No error. The key still did not reconstruct correctly, I got the “Goodbye”, but something worked. I turned to the engineer and said, “what did you just type in that worked?”
After a second of embarrassed mumbling, he admitted to choosing “a$$word” as his passphrase. The gall! I asked everyone entrusted with the grave task of relaunching crytposerv to pick really hard to guess passphrases, and this guy…?! Still, this was something -- it worked. But why?!
I sprinted around the half-lit office grabbing the rest of the shard-holders demanding they tell me their passphrases. Everyone else had picked much lengthier passages of text and numbers. I manually tested each and none decrypted correctly. Except for the a$$word. What was it…
A lightning bolt hit me and I sprinted back to my own cubicle in the far corner, unlocked the screen and typed in “man getpass” on the command line, while logging into cryptoserv in another window and doing exactly the same thing there. I saw exactly what I needed to see.
Today, should you try to read up the programmer’s manual (AKA the man page) on getpass, you will find it has been long declared obsolete and replaced with a more intelligent alternative in nearly all flavors of modern Unix.
But back then, if you wanted to collect some information from the keyboard without printing what is being typed in onto the screen and remain POSIX-compliant, getpass did the trick. Other than a few standard file manipulation system calls, getpass was the only operating system service call I used, to ensure clean portability between Linux and Solaris.
Except it wasn’t completely clean.
Plain as day, there it was: the manual pages were identical, except Solaris had a “special feature”: any passphrase entered that was longer than 8 characters long was automatically reduced to that length anyway. (Who needs long passwords, amiright?!)
I screamed like a wounded animal. We generated the key on my Linux desktop and entered our novel-length passphrases right here. Attempting to restore them on a Solaris machine where they were being clipped down to 8 characters long would never work. Except, of course, for a$$word. That one was fine.
The rest was an exercise in high-speed coding and some entirely off-protocol file moving. We reconstructed the master key on my machine (all of our passphrases worked fine), copied the file to the Solaris-running cryptoserv, re-split it there (with very short passphrases), reconstructed it successfully, and PayPal was up and running again like nothing ever happened.
By the time our unsuspecting colleagues rolled back into the office I was starting to doze on the floor of my cubicle and that was that. When someone asked me later that day why we took so long to bring the site back up, I’d simply respond with “eh, shoulda RTFM.”
RTFM indeed.
P.S. A few hours later, John, our General Counsel, stopped by my cubicle to ask me something. The day before I apparently gave him a sealed envelope and asked him to store it in his safe for 24 hours without explaining myself. He wanted to know what to do with it now that 24 hours have passed.
Ha. I forgot all about it, but in a bout of “what if it doesn’t work” paranoia, I printed out the base64-encoded master key when we had generated it the night before, stuffed it into an envelope, and gave it to John for safekeeping. We shredded it together without opening and laughed about what would have never actually been a company-ending event.
P.P.S. If you are thinking of all the ways this whole SSS design is horribly insecure (it had some real flaws for sure) and plan to poke around PayPal to see if it might still be there, don’t. While it served us well for a few years, this was the very first thing eBay required us to turn off after the acquisition. Pretty sure it’s back to a single passphrase now.
Notes:
1: a member of Chicagoland sci-fi fan community let me know that the original news of our move to the US was delivered to them via a posted letter, snail mail, not FidoNet email!
522 notes
·
View notes
Text
Twinkfrump Linkdump

I'm touring my new, nationally bestselling novel The Bezzle! Catch me in CHICAGO (Apr 17), Torino (Apr 21) Marin County (Apr 27), Winnipeg (May 2), Calgary (May 3), Vancouver (May 4), and beyond!

Welcome to the seventeenth Pluralistic linkdump, a collection of all the miscellany that didn't make it into the week's newsletter, cunningly wrought together in a single edition that ranges from the first ISP to AI nonsense to labor organizing victories to the obituary of a brilliant scientist you should know a lot more about! Here's the other 16 dumps:
https://pluralistic.net/tag/linkdump/
If you're reading this (and you are!), it was delivered to you by an internet service provider. Today, the ISP industry is calcified, controlled by a handful of telcos and cable companies. But the idea of an "ISP" didn't come out of a giant telecommunications firm – it was created, in living memory, by excellent nerds who are still around.
Depending on how you reckon, The Little Garden was either the first or the second ISP in America. It was named after a Palo Alto Chinese restaurant frequented by its founders. To get a sense of that founding, read these excellent recollections by Tom Jennings, whose contributions include the seminal zine Homocore, the seminal networking protocol Fidonet, and the seminal third-party PC ROM, whence came Dell, Gateway, Compaq, and every other "PC clone" company.
The first installment describes how an informal co-op to network a few friends turned into a business almost by accident, with thousands of dollars flowing in and out of Jennings' bank account:
https://www.sensitiveresearch.com/Archive/TLG/TLG.html
And it describes how that ISP set a standard for neutrality, boldly declaring that "TLGnet exercises no control whatsoever over the content of the information." They introduced an idea of radical transparency, documenting their router configurations and other technical details and making them available to the public. They hired unskilled punk and queer kids from their communities and trained them to operate the network equipment they'd invented, customized or improvised.
In part two, Jennings talks about the evolution of TLG's radical business-plan: to offer unrestricted service, encouraging their customers to resell that service to people in their communities, having no lock-in, unbundling extra services including installation charges – the whole anti-enshittification enchilada:
https://www.sensitiveresearch.com/Archive/TLG/
I love Jennings and his work. I even gave him a little cameo in Picks and Shovels, the third Martin Hench novel, which will be out next winter. He's as lyrical a writer about technology as you could ask for, and he's also a brilliant engineer and thinker.
The Little Garden's founders and early power-users have all fleshed out Jennings' account of the birth of ISPs. Writing on his blog, David "DSHR" Rosenthal rounds up other histories from the likes of EFF co-founder John Gilmore and Tim Pozar:
https://blog.dshr.org/2024/04/the-little-garden.html
Rosenthal describes some of the more exotic shenanigans TLG got up to in order to do end-runs around the Bell system's onerous policies, hacking in the purest sense of the word, for example, by daisy-chaining together modems in regions with free local calling and then making "permanent local calls," with the modems staying online 24/7.
Enshittification came to the ISP business early and hit it hard. The cartel that controls your access to the internet today is a billion light-years away from the principled technologists who invented the industry with an ethos of care, access and fairness. Today's ISPs are bitterly opposed to Net Neutrality, the straightforward proposition that if you request some data, your ISP should send it to you as quickly and reliably as it can.
Instead, ISPs want to offer "slow-lanes" where they will relegate the whole internet, except for those companies that bribe the ISP to be delivered at normal speed. ISPs have a laughably transparent way of describing this: they say that they're allowing services to pay for "fast lanes" with priority access. This is the same as the giant grocery store that charges you extra unless you surrender your privacy with a "loyalty card" – and then says that they're offering a "discount" for loyal customers, rather than charging a premium to customers who don't want to be spied on.
The American business lobby loves this arrangement, and hates Net Neutrality. Having monopolized every sector of our economy, they are extremely fond of "winner take all" dynamics, and that's what a non-neutral ISP delivers: the biggest services with the deepest pockets get the most reliable delivery, which means that smaller services don't just have to be better than the big guys, they also have to be able to outbid them for "priority carriage."
If everything you get from your ISP is slow and janky, except for the dominant services, then the dominant services can skimp on quality and pocket the difference. That's the goal of every monopolist – not just to be too big to fail, but also too big to care.
Under the Trump administration, FCC chair Ajit Pai dismantled the Net Neutrality rule, colluding with American big business to rig the process. They accepted millions of obviously fake anti-Net Neutrality comments (one million identical comments from @pornhub.com addresses, comments from dead people, comments from sitting US Senators who support Net Neutrality) and declared open season on American internet users:
https://ag.ny.gov/press-release/2021/attorney-general-james-issues-report-detailing-millions-fake-comments-revealing
Now, Biden's FCC is set to reinstate Net Neutrality – but with a "compromise" that will make mobile internet (which nearly all of use sometimes, and the poorest of us are reliant on) a swamp of anticompetitive practices:
https://cyberlaw.stanford.edu/blog/2024/04/harmful-5g-fast-lanes-are-coming-fcc-needs-stop-them
Under the proposed rule, mobile carriers will be able to put traffic to and from apps in the slow lane, and then extort bribes from preferred apps for normal speed and delivery. They'll rely on parts of the 5G standard to pull off this trick.
The ISP cartel and the FCC insist that this is fine because web traffic won't be degraded, but of course, every service is hellbent on pushing you into using apps instead of the web. That's because the web is an open platform, which means you can install ad- and privacy-blockers. More than half of web users have installed a blocker, making it the largest boycott in human history:
https://doc.searls.com/2023/11/11/how-is-the-worlds-biggest-boycott-doing/
But reverse-engineering and modding an app is a legal minefield. Just removing the encryption from an app can trigger criminal penalties under Section 1201 of the DMCA, carrying a five-year prison sentence and a $500k fine. An app is just a web-page skinned in enough IP that it's a felony to mod it.
Apps are enshittification's vanguard, and the fact that the FCC has found a way to make them even worse is perversely impressive. They're voting on this on April 25, and they have until April 24 to fix this. They should. They really should:
https://docs.fcc.gov/public/attachments/DOC-401676A1.pdf
In a just world, cheating ripoff ISPs would the top tech policy story. The operational practices of ISPs effect every single one us. We literally can't talk about tech policy without ISPs in the middle. But Net Neutrality is an also-ran in tech policy discourse, while AI – ugh ugh ugh – is the thing none of us can shut up about.
This, despite the fact that the most consequential AI applications sum up to serving as a kind of moral crumple-zone for shitty business practices. The point of AI isn't to replace customer service and other low-paid workers who have taken to demanding higher wages and better conditions – it's to fire those workers and replace them with chatbots that can't do their jobs. An AI salesdroid can't sell your boss a bot that can replace you, but they don't need to. They only have to convince your boss that the bot can do your job, even if it can't.
SF writer Karl Schroeder is one of the rare sf practitioners who grapples seriously with the future, a "strategic foresight" guy who somehow skirts the bullshit that is the field's hallmark:
https://pluralistic.net/2024/03/07/the-gernsback-continuum/#wheres-my-jetpack
Writing on his blog, Schroeder describes the AI debates roiling the Association of Professional Futurists, and how it's sucking him into being an unwilling participant in the AI hype cycle:
https://kschroeder.substack.com/p/dragged-into-the-ai-hype-cycle
Schroeder's piece is a thoughtful meditation on the relationship of SF's thought-experiments and parables about AI to the promises of AI hucksters, who promise that a) "general artificial intelligence" is just around the corner and that b) it will be worth trillions of dollars.
Schroeder – like other sf writers including Ted Chiang and Charlie Stross (and me) – comes to the conclusion that AI panic isn't about AI, it's about power. The artificial life-form devouring the planet and murdering our species is the limited liability corporation, and its substrate isn't silicon, it's us, human bodies:
What’s lying underneath all our anxieties about AGI is an anxiety that has nothing to do with Artificial Intelligence. Instead, it’s a manifestation of our growing awareness that our world is being stolen from under us. Last year’s estimate put the amount of wealth currently being transferred from the people who made it to an idle billionaire class at $5.2 trillion. Artificial General Intelligence whose environment is the server farms and sweatshops of this class is frightening only because of its capacity to accelerate this greatest of all heists.
After all, the business-case for AI is so very thin that the industry can only survive on a torrent of hype and nonsense – like claims that Amazon's "Grab and Go" stores used "AI" to monitor shoppers and automatically bill them for their purchases. In reality, the stores used thousands of low-paid Indian workers to monitor cameras and manually charge your card. This happens so often that Indian technologists joke that "AI" stands for "absent Indians":
https://pluralistic.net/2024/01/29/pay-no-attention/#to-the-little-man-behind-the-curtain
Isn't it funny how all the really promising AI applications are in domains that most of us aren't qualified to assess? Like the claim that Google's AI was producing millions of novel materials that will shortly revolutionize all forms of production, from construction to electronics to medical implants:
https://deepmind.google/discover/blog/millions-of-new-materials-discovered-with-deep-learning/
That's what Google's press-release claimed, anyway. But when two groups of experts actually pulled a representative sample of these "new materials" from the Deep Mind database, they found that none of these materials qualified as "credible, useful and novel":
https://pubs.acs.org/doi/10.1021/acs.chemmater.4c00643
Writing about the researchers' findings for 404 Media, Jason Koebler cites Berkeley researchers who concluded that "no new materials have been discovered":
https://www.404media.co/google-says-it-discovered-millions-of-new-materials-with-ai-human-researchers/
The researchers say that AI data-mining for new materials is promising, but falls well short of Google's claim to be so transformative that it constitutes the "equivalent to nearly 800 years’ worth of knowledge" and "an order-of-magnitude expansion in stable materials known to humanity."
AI hype keeps the bubble inflating, and for so long as it keeps blowing up, all those investors who've sunk their money into AI can tell themselves that they're rich. This is the essence of "a bezzle": "The magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it":
https://pluralistic.net/2023/03/09/autocomplete-worshippers/#the-real-ai-was-the-corporations-that-we-fought-along-the-way
Among the best debezzlers of AI are the Princeton Center for Information Technology Policy's Arvind Narayanan and Sayash Kapoor, who edit the "AI Snake Oil" blog. Now, they've sold a book with the same title:
https://www.aisnakeoil.com/p/ai-snake-oil-is-now-available-to
Obviously, books move a lot more slowly than blogs, and so Narayanan and Kapoor say their book will focus on the timeless elements of identifying and understanding AI snake oil:
In the book, we explain the crucial differences between types of AI, why people, companies, and governments are falling for AI snake oil, why AI can’t fix social media, and why we should be far more worried about what people will do with AI than about anything AI will do on its own. While generative AI is what drives press, predictive AI used in criminal justice, finance, healthcare, and other domains remains far more consequential in people’s lives. We discuss in depth how predictive AI can go wrong. We also warn of the dangers of a world where AI continues to be controlled by largely unaccountable big tech companies.
The book's out in September and it's up for pre-order now:
https://bookshop.org/p/books/ai-snake-oil-what-artificial-intelligence-can-do-what-it-can-t-and-how-to-tell-the-difference-arvind-narayanan/21324674
One of the weirder and worst side-effects of the AI hype bubble is that it has revived the belief that it's somehow possible for giant platforms to monitor all their users' speech and remove "harmful" speech. We've tried this for years, and when humans do it, it always ends with disfavored groups being censored, while dedicated trolls, harassers and monsters evade punishment:
https://pluralistic.net/2022/08/07/como-is-infosec/
AI hype has led policy-makers to believe that we can deputize online services to spy on all their customers and block the bad ones without falling into this trap. Canada is on the verge of adopting Bill C-63, a "harmful content" regulation modeled on examples from the UK and Australia.
Writing on his blog, Canadian lawyer/activist/journalist Dimitri Lascaris describes the dire speech implications for C-63:
https://dimitrilascaris.org/2024/04/08/trudeaus-online-harms-bill-threatens-free-speech/
It's an excellent legal breakdown of the bill's provisions, but also a excellent analysis of how those provisions are likely to play out in the lives of Canadians, especially those advocating against genocide and taking other positions the that oppose the agenda of the government of the day.
Even if you like the Trudeau government and its policies, these powers will accrue to every Canadian government, including the presumptive (and inevitably, totally unhinged) near-future Conservative majority government of Pierre Poilievre.
It's been ten years since Martin Gilens and Benjamin I Page published their paper that concluded that governments make policies that are popular among elites, no matter how unpopular they are among the public:
https://www.cambridge.org/core/journals/perspectives-on-politics/article/testing-theories-of-american-politics-elites-interest-groups-and-average-citizens/62327F513959D0A304D4893B382B992B
Now, this is obviously depressing, but when you see it in action, it's kind of wild. The Biden administration has declared war on junk fees, from "resort fees" charged by hotels to the dozens of line-items added to your plane ticket, rental car, or even your rent check. In response, Republican politicians are climbing to their rear haunches and, using their actual human mouths, defending junk fees:
https://prospect.org/politics/2024-04-12-republicans-objectively-pro-junk-fee/
Congressional Republicans are hell-bent on destroying the Consumer Finance Protection Bureau's $8 cap on credit-card late-fees. Trump's presumptive running-mate Tim Scott is making this a campaign plank: "Vote for me and I will protect your credit-card company's right to screw you on fees!" He boasts about the lobbyists who asked him to take this position: champions of the public interest from the Consumer Bankers Association to the US Chamber of Commerce.
Banks stand to lose $10b/year from this rule (which means Americans stand to gain $10b/year from this rule). What's more, Scott's attempt to kill the rule is doomed to fail – there's just no procedural way it will fly. As David Dayen writes, "Not only does this vote put Republicans on the spot over junk fees, it’s a doomed vote, completely initiated by their own possible VP nominee."
This is an hilarious own-goal, one that only brings attention to a largely ignored – but extremely good – aspect of the Biden administration. As Adam Green of Bold Progressives told Dayen, "What’s been missing is opponents smoking themselves out and raising the volume of this fight so the public knows who is on their side."
The CFPB is a major bright spot in the Biden administration's record. They're doing all kind of innovative things, like making it easy for you to figure out which bank will give you the best deal and then letting you transfer your account and all its associated data, records and payments with a single click:
https://pluralistic.net/2023/10/21/let-my-dollars-go/#personal-financial-data-rights
And now, CFPB chair Rohit Chopra has given a speech laying out the agency's plan to outlaw data-brokers:
https://www.consumerfinance.gov/about-us/newsroom/prepared-remarks-of-cfpb-director-rohit-chopra-at-the-white-house-on-data-protection-and-national-security/
Yes, this is some good news! There is, in fact, good news in the world, bright spots amidst all the misery and terror. One of those bright spots? Labor.
Unions are back, baby. Not only do the vast majority of Americans favor unions, not only are new shops being unionized at rates not seen in generations, but also the largest unions are undergoing revolutions, with control being wrestled away from corrupt union bosses and given to the rank-and-file.
Many of us have heard about the high-profile victories to take back the UAW and Teamsters, but I hadn't heard about the internal struggles at the United Food and Commercial Workers, not until I read Hamilton Nolan's gripping account for In These Times:
https://inthesetimes.com/article/revolt-aisle-5-ufcw-grocery-workers-union
Nolan profiles Faye Guenther, president of UFCW Local 3000 and her successful and effective fight to bring a militant spirit back to the union, which represents a million grocery workers. Nolan describes the fight as "every bit as dramatic as any episode of Game of Thrones," and he's not wrong. This is an inspiring tale of working people taking power away from scumbag monopoly bosses and sellout fatcat leaders – and, in so doing, creating a institution that gets better wages, better working conditions, and a better economy, by helping to block giant grocery mergers like Kroger/Albertsons.
I like to end these linkdumps on an up note, so it feels weird to be closing out with an obituary, but I'd argue that any celebration of the long life and many accomplishments of my friend and mentor Anne Innis Dagg is an "up note."
I last wrote about Anne in 2020, on the release of a documentary about her work, "The Woman Who Loved Giraffes":
https://pluralistic.net/2020/02/19/pluralist-19-feb-2020/#annedagg
As you might have guessed from the title of that doc, Anne was a biologist. She was the first woman scientist to do field-work on giraffes, and that work was so brilliant and fascinating that it kicked off the modern field of giraffology, which remains a woman-dominated specialty thanks to her tireless mentoring and support for the scientists that followed her.
Anne was also the world's most fearsome slayer of junk-science "evolutionary psychology," in which "scientists" invent unfalsifiable just-so stories that prove that some odious human characteristic is actually "natural" because it can be found somewhere in the animal kingdom (i.e., "Darling, please, it's not my fault that I'm fucking my grad students, it's the bonobos!").
Anne wrote a classic – and sadly out of print – book about this that I absolutely adore, not least for having one of the best titles I've ever encountered: "Love of Shopping" Is Not a Gene:
https://memex.craphound.com/2009/11/04/love-of-shopping-is-not-a-gene-exposing-junk-science-and-ideology-in-darwinian-psychology/
Anne was my advisor at the University of Waterloo, an institution that denied her tenure for fifty years, despite a brilliant academic career that rivaled that of her storied father, Harold Innis ("the thinking person's Marshall McLuhan"). The fact that Waterloo never recognized Anne is doubly shameful when you consider that she was awarded the Order of Canada:
https://nationalpost.com/news/canada/queen-of-giraffes-among-new-order-of-canada-recipients-with-global-influence
Anne lived a brilliant live, struggling through adversity, never compromising on her principles, inspiring a vast number of students and colleagues. She lived to ninety one, and died earlier this month. Her ashes will be spread "on the breeding grounds of her beloved giraffes" in South Africa this summer:
https://obituaries.therecord.com/obituary/anne-innis-dagg-1089534658

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/04/13/goulash/#material-misstatement

Image: Valeva1010 https://commons.wikimedia.org/wiki/File:Hungarian_Goulash_Recipe.png
CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#linkdump#linkdumps#junk fees#fcc#ai#ai hype#labor#unions#hamilton nolan#history#cfpb#privacy#online harms#ai snake oil#anne dagg#anne innis dagg#obits#rip#mobile#net neutrality#5g
88 notes
·
View notes
Text

Got this in a comic swap with an old friend from my FidoNet Comics days: The Jungle Twins 15. Cover by George Wilson.
5 notes
·
View notes
Text

Revisited: Classic GVP & Amiga Hardware - Robert Miranda
"We, Robert Miranda & Pete Keretz, were in the trenches of Great Valley Products’ Technical Support from ~1989-1994 (combined). We were regular maintainers of the GVP BBS, and we frequented the online FidoNet discussion groups for the Commodore Amiga and GVP Tech Support. We tested many 3rd party hardware and software offerings as part of our day job. That fed our growing passion for computer technology. Stop by to see some of our collection of Amiga expansion gear, and feel free to engage us in the technical memories from the classic Amiga era."
VCF East XIX
10 notes
·
View notes
Photo



CAMELOT.WAD: Camelot (CAMELOT.WAD) E1M1 (-2296, 1886, 60) Author: Joe - Joe's Garage BBS (206) 639-4370 FIDOnet - 1:343/254 (shameless plug) (I'll always have the lat Date: 2010-11-01 Description:
11 notes
·
View notes
Text

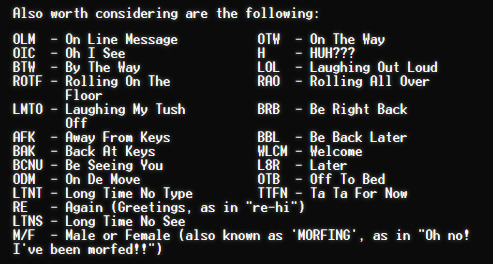
i was scrolling through this neat little game of internet artifacts and loved this one from 1989, featuring compilations of early internet emoticons and acronyms. notably this was the first appearance of "lol" on the internet, but i love some of the other ones that haven't really caught on- i especially think we should bring back ]:> for "devil/guilty" and 0:) for "angel/innocent"; [% for a mug is pretty cute too tbh
here's the explainer text that accompanied this section:
Earliest LOL The acronym "LOL" made its first documented appearance on the internet in a FidoNet newsletter. FidoNet was a network of BBSs - or bulletin board systems. Messages were transferred over phone calls during off-peak hours to minimize toll costs. This edition of the FidoNet newsletter attempts to catalog the increasing number of emoticons and acronyms that were spreading on the network at the time. It also contained conventions that never really caught on - like ODM for "On De Move".
image descriptions under the cut!
[image 1 description: white text in a simple font on a black background. the text is split into two columns. column one reads:
:) - smile/happy
:D - big smile or laugh
:> - mischievous smile
;) - wink
:* - kiss
:0 - shout/yawn
]:> - devil/guilty
:# - grimace/frustrated
:P - sticking out tongue
:d - tastes good :9
B) - glasses
c% - coffee cup
u - shot glass
---<--<-@ long-stemmed rose
----==== drink sliding down bar
column two reads:
:( - frown/sad
:c - pout
: '( - cry
:> - sly wink
[ ] - hug
0:) - angel/innocent
:I - content
:/ - disfavor/baffled
:X - not talking
8) - wide-eyed surprise
[% - mug
U - glass
Y - wine/cocktail glass
/end image 1 description.]
[image two description: white text in a simple font on a black background. the text at the top reads "Also worth considering are the following:" and the rest of the text below it is split into two columns. column one reads:
OLM - On Line Message
OIC - Oh I See
BTW - By The Way
ROTF - Rolling On The Floor
LMTO - Laughing My Tush Off
AFK - Away From Keys
BAK - Back At Keys
BCNU - Be Seeing You
ODM - On De Move
LTNT - Long Time No Type
RE - Again (Greetings, as in "re-hi")
LTNS - Long Time No See
M/F - Male or Female (also known as 'MORFING', as in "Oh no! I've been morfed!!")
column two reads:
OTW - On The Way
H - HUH???
LOL - Laughing Out Loud
RAO - Rolling All Over
BRB - Be Right Back
BBL - Be Back Later
WLCM - Welcome
L8R - Later
OTB - Off To Bed
TTFN - Ta Ta For Now
/end image two description.]
#mine#early internet#internet history#tell me in the tags which is your fave on here/ what you would bring back!
2 notes
·
View notes
Text

Mistigram: in this #BBCMicro high resolution graphics animation, titled "Download", @blippypixel demonstrates the traditional underground BBS "regional hub and distro site" warez distribution technique -- but abstracting out the BBSes entirely, instead more efficiently disseminating the pirated software via the bodies of the pirates themselves. Progress! (If it went both ways, you'd have walking, talking FidoNet zone hosts.) This piece was included in last month's science fiction-themed MIST0523 artpack collection.
3 notes
·
View notes
Text
FidoNet. Back in the 80s. Using a 1200/75 dial-up modem.
*for our purposes, a youtube account only counts if you’ve used it to post videos.
reblog for reach/bigger sample size!!
26K notes
·
View notes
Text
Da ich immer mal wieder gefragt werde warum ich #betamax + 65 als Pseudo nutze. Nein es hat nichts mit dem #Videoformat von #Sony aus der 70ern zu tun.
Erklärung: In der PreInternetZeit als man sich per Modem in #Mailbox eingewählt hat und ggf. über #Fidonet bzw. #Mausnet dann weltweit kommuniziert hat, war ich immer max ... das bewährte sich, mit der Öffnung des #Internet für die Allgemeinheit, nicht wirklich. Zur damaligen Zeit wurde ich dann irgendwann Tester einer (nicht mehr existierenden) #Linux Distribution. Wir haben damals hauptsächlich über #IRC kommuniziert. Damit die anderen sehen konnten ob ich gerade stable oder beta unterwegs war, war ich mit der Betaversion dann als Betamax im Channel. Und schon war der neue #Nick geboren.
0 notes
Text
Enshitternet

Going to Burning Man? Catch me on Tuesday at 2:40pm on the Center Camp Stage for a talk about enshittification and how to reverse it; on Wednesday at noon, I'm hosting Dr Patrick Ball at Liminal Labs (6:15/F) for a talk on using statistics to prove high-level culpability in the recruitment of child soldiers.
On September 6 at 7pm, I'll be hosting Naomi Klein at the LA Public Library for the launch of Doppelganger.
On September 12 at 7pm, I'll be at Toronto's Another Story Bookshop with my new book The Internet Con: How to Seize the Means of Computation.

This week on my podcast, I read "Enshitternet: The old, good internet deserves a new, good internet," my recent Medium column about building a better internet:
https://doctorow.medium.com/enshitternet-c1d4252e5c6b
As John @hodgman is fond of reminding us, "nostalgia is a toxic impulse." It is easy for an old net.hand like me to fall into the trap of shaking his fist at the cloud. Having been on the other side of that dynamic, I can tell you it's no fun.
When I got on BBSes in the early 1980s, there was an omnipresent chorus of grumps insisting that the move from honest acoustic couplers to decadent modems was the end of the Golden Age of telecommunications:
https://en.wikipedia.org/wiki/Acoustic_coupler
When I got on Usenet shortly thereafter, the Unix Greybeard set never passed up an opportunity to tell us newcomers that the Fidonet-Usenet bridge allowed the barbarian hordes to overwhelm their Athenian marketplace of ideas:
https://technicshistory.com/2020/06/25/the-era-of-fragmentation-part-4-the-anarchists/
When I joined The WELL in the late 1980s, I was repeatedly assured that the good times were over, and that we would never see their like again:
https://www.well.com/
Now that I'm 52, I've learned to recognize this dynamic, from the Eternal September:
https://en.wikipedia.org/wiki/Eternal_September
to the moral panic over menuing systems replacing CLIs:
https://www.eff.org/deeplinks/2020/02/gopher-when-adversarial-interoperability-burrowed-under-gatekeepers-fortresses
to the culture wars over what would happen when the net got a normie-friendly GUI:
https://www.dejavu.org/1993win.htm
And yeah, I've done it too, explaining "Why I won’t buy an iPad (and think you shouldn’t, either)":
https://memex.craphound.com/2010/04/01/why-i-wont-buy-an-ipad-and-think-you-shouldnt-either/
But there's a key difference between my own warnings about the enshittification that new "user friendly" technologies would engender and all those other AARP members' complaints: they were wrong, and I was right.
As Tom Eastman reminded us, the internet really was better, back before it became "five giant websites filled with screenshots of text of the other four":
https://twitter.com/tveastman/status/1069674780826071040
The underlying pathology of that enshittification wasn't the UI, or whether it involved an app store. As the Luddites knew, the important thing about a technology isn't what it does, but who it does it for and who it does it to:
https://locusmag.com/2022/01/cory-doctorow-science-fiction-is-a-luddite-literature/
The problem wasn't which technology we used. There is nothing inherent about touchscreens that makes them into prisons that trap users, rather than walled gardens that protect them.
Likewise, the problem wasn't who made that technology. We didn't swap wise UUCP Monks for venal tech bros. The early tech world was full of public-spirited sysops, but it was also full of would-be monopolists who tried – and failed – to get us to "stop talking to each other and start buying things":
https://catvalente.substack.com/p/stop-talking-to-each-other-and-start
If it wasn't the technology that killed the old, good internet, and if it wasn't the people who killed the old, good internet, where did the enshitternet come from?
It wasn't the wrong tech, it wasn't the wrong people: it was the wrong rules. After all, the Apple ][+ went on sale the year Ronald Reagan hit the campaign trail. Consumer tech was the first industry born after antitrust was dismantled, and it created the modern monopoly playbook: buying and merging with competitors. The resulting unity of purpose and anticompetitive profit margins allowed tech to capture its regulators and secure favorable court and legislative outcomes.
The simultaneous drawdown of antitrust enforcement and growth of tech meant that tech's long-standing cycle of renewal was ended. Tech companies that owed their existence to their ability to reverse-engineer incumbent companies' products and make interoperable replacements and add-ons were able to ban anyone else from doing unto them as they did unto the giants that came before them:
https://doctorow.medium.com/let-the-platforms-burn-6fb3e6c0d980
The pirates became admirals, and set about creating a "felony contempt of business model":
https://pluralistic.net/2022/12/03/painful-burning-dribble/#law-of-intended-consequences
They changed the rules to ensure that they could "disrupt" anyone they chose, but could themselves mobilize the full might of the US government to prevent anyone from disrupting them:
https://locusmag.com/2019/01/cory-doctorow-disruption-for-thee-but-not-for-me/
The old, good internet was the internet we we able to make while tech was still realizing the new anticompetitive powers it had at its disposal, and it disappeared because every administration, R and D, from Reagan to Trump, yanked more and more Jenga blocks out of the antitrust tower.
In other words: the old, good internet was always doomed, because it was being frantically built in an ever-contracting zone of freedom to tinker, where technologies could be operated by and for the people who used them.
Today, the Biden administration has ushered in a new era of antitrust renewal, planting the seeds of a disenshittification movement that will tame corporate power rather than nurturing it:
https://www.eff.org/de/deeplinks/2021/08/party-its-1979-og-antitrust-back-baby
In other words, we are living in the first days of a better nation.
In other words, rather than restoring the old, good internet, we should build a new, good internet.
What is a new, good internet? It's an internet where it's legal to:
reverse-engineer the products and services you use, to add interoperability to them so you can leave a social network without leaving your friends:
https://www.eff.org/interoperablefacebook
jailbreak devices to remove antifeatures, like surveillance, ink-locking, or repair-blocking:
https://pluralistic.net/2023/04/17/have-you-tried-not-spying/#coppa
move your media files and apps from any platform to any device or service, even if the company that sold them to you objects:
https://pluralistic.net/2022/09/07/audible-exclusive/#audiblegate
A new, good internet gives powers to users, and takes power away from corporations:
https://doctorow.medium.com/twiddler-1b5c9690cce6
On a new, good internet, companies can't practice algorithmic wage discrimination:
https://pluralistic.net/2023/04/12/algorithmic-wage-discrimination/#fishers-of-men
They can't turn search into an auction between companies that match your query and companies that want to sell you fakes and knockoffs:
https://pluralistic.net/2022/11/28/enshittification/#relentless-payola
They can't charge rent to the people whose feeds you asked to read for the privilege of reaching you:
https://pluralistic.net/2022/12/10/e2e/#the-censors-pen
In fact, a new, good internet is one where we euthanize rentiers:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
On the new good internet, your boss can't use bossware to turn "work from home" into "live at work":
https://pluralistic.net/2021/02/24/gwb-rumsfeld-monsters/#bossware
And on top of that, you have the right to hack that bossware to undetectably disable it (and hackers have the right to sell or give you that hack):
https://www.eff.org/deeplinks/2021/08/tech-rights-are-workers-rights-doordash-edition
On the new, good internet, we stop pretending that tech is stealing content from news companies, and focus on how tech steals money from the news, with app taxes, rigged ad markets, surveillance ads, and payola:
https://www.eff.org/deeplinks/2023/04/saving-news-big-tech
The new, good internet is an internet where we seize the means of computation. It's an internet operated by and for the people who use it.
Hodgman is right. Nostalgia is a toxic impulse. The point of making a new, good internet isn't to revive the old, good internet. There were plenty of problems with the old, good internet. The point is to make a new, good internet that is the worthy successor to the old, good internet – and to consign the enshitternet to the scrapheap of history, an unfortunate transitional stage between one good internet and another.
Here's a link to the podcast episode:
https://craphound.com/news/2023/08/21/enshitternet-the-old-good-internet-deserves-a-new-good-internet/
and here's a direct link to the MP3 (hosting courtesy of the Internet Archive; they'll host your stuff for free, forever):
https://archive.org/download/Cory_Doctorow_Podcast_448/Cory_Doctorow_Podcast_448_-_Enshitternet.mp3
and here's a link to my podcast's RSS feed:
https://feeds.feedburner.com/doctorow_podcast

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/08/22/the-new-good-internet/#the-old-good-internet

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#podcasts#mp3s#enshittification#nostalgia#nostalgia is a toxic impulse#spoken word#the old good internet#the new good internet
60 notes
·
View notes
Text
Novel Memory
Well, that was definitely a January. Often considered (in the Northern Hemisphere) the worst winter month, since it's not short like February, not almost-spring like March, and no Christmas. But surely it wasn't longer than 8-10 weeks. I only managed to finish six books, but I am trying to not try to churn through a bunch of novellas for the Goodreads deities any more, so it is what it is.
Possible spoilers within for T. Kingfisher's "Clocktaur Wars", Rachel Caine's "Weather Wardens", and R. Scott Bakker's "Prince of Nothing" series.
Allan Cole & Chris Bunch: Sten, completed January 1
Previous book was a reread, and after it came "trying a new author", male edition. Way back in the 90s, I spent a certain amount of time on BBS systems that connected to Fidonet, and a lot of that on the SF forum, or "echo" as Fidonet called them. A number of people back then were talking about this Sten series, which I knew little about, but I was curious and found the first couple of books in used bookstores (or perhaps I even got them sent to me via FUBS, the Fidonet Used Book Squad, where other users would scour their local second-hand stores for books that other people had trouble finding). All I knew about them was that they were space opera-ish, or possibly military SF, and there were eight books in the series, and that there was an Eternal Emperor.
I thought perhaps I'd end up finishing this book in 2024, but I gave myself extra time for reading the last couple of books because of increased social commitments in the holiday season, so this one ended up getting pushed into January. (Not to worry, to complete the Goodreads Challenge, I finished off Dennis Valdron's ebook about Season 2 of Lexx, which I now realize I forgot to mention in December's column. I'll add a thing here.) I set my goal for this year to a more leisurely 80 books so I won't have to try too hard to polish it off.
Anyway, Sten starts out with a bunch of downtrodden migrant workers ("Migs") on a company-town space station named Vulcan (no relation), who are locked into indenture contracts designed to reduce their chances of ever being able to leave. The Baron who is in charge of the station is working on the secret Project Bravo, and when he is forced to choose between compromising the secrecy of the project and saving the lives of a bunch of Migs, he jettisons the Migs without a second thought. Karl Sten (mostly just called "Sten" throughout the book) narrowly misses joining the rest of his family in death, and swears revenge. He becomes a fugitive for a while, until he's contacted by an agent of the Eternal Emperor to try to find out more about the Baron's secret project. It goes bad, he's extracted off the station and enlisted in the army.
There follows a tedious boot-camp sequence, which ends up with Sten washing out as unsuitable for being a soldier, and instead he becomes a secret agent. This part is sometimes hard to follow because the authors seem to have decided not to do any transitions. You will just abruptly get shifted from one scene to another. (At least they manage to avoid a lot of headhopping this way.) Also, we're only barely introduced to the rest of the agents on Sten's team, because we jump to the middle of a mission, and I kept losing track of them. (Another fifty pages of actually introducing them would not have gone amiss, but perhaps they were trying to keep it under 300 pages.) At the end, Sten and his team have to return to Vulcan and try to deal with the Baron and Project Bravo, fomenting a revolt along the way. The action there is choppy and hard to follow, and I was kind of disappointed in the back half of the book. The first part kind of reminded me of the beginning of Pierce Brown's Red Rising, but better. Sten does not seem to be a particularly engaging character, certainly no Miles Vorkosigan, so I'm divided on whether I'll go on to the next book or not. I may not bother.
2. T. Kingfisher: The Wonder Engine, completed January 5
I am trying not to be concerned about the Goodreads Challenge numbers, and I have set it lower this year, but nonetheless I feel the inclination to get a "head start" with shorter reads. In my head, at least, this was a novella, though given that it took me four days to read, and it was only split into two parts because of length, apparently not.
This novella is the sequel to "Clockwork Boys", which I read last January, and generally a year is the shortest time I like to leave between reading series installments unless I'm really sucked in. I vaguely remembered what happened in the first one, but there's also a synopsis of the first part at the beginning, which is helpful. Our characters are the three freed prisoners sent out (with obedience-ensuring magical tattoos) in Clockwork Boys: forger Slate, disgraced former demon-hunter Caliban, and assassin Brenner, as well as unworldly monk Learned Edmund, and grateful gnole (anthopomorphic-raccoon-type) Grimehug.
I may have mentioned earlier that I was picturing Clockwork Boys as some sort of clockwork youths, rather than hard-to-destroy mechanical centaurs. I also have to say, when they were going into the heart of the city that was sending out these creatures, I was picturing more of a war zone situation; instead, they can mostly move around with impunity, except for the one character who humiliated a local crimelord back when they used to live there. They have to solve a number of mysteries about how to stop the clocktaurs, with a lot of help from the local gnole subculture, and some last-minute plot twists. Plus there's a romance between Slate and Caliban, with some interference from Brenner. Overall I enjoyed it, though some of the plot twists were so heavily foreshadowed that I had to wonder why the characters hadn't figured it out already. Also leavened with plenty of humour, though sometimes it felt forced. The demons in the story kept making me think of Bujold's Five Gods world, but the stakes were more like Curse of Chalion then the cozier Penric series. Overall I liked it and will probably read more of Kingfisher (/Ursula Vernon) in the future.
3. Rachel Caine: Firestorm, completed January 10
I decided that next I felt like an urban fantasy book, but I wasn't really certain which one, so I'd look at the ones where it had been the longest since I'd read a book. Technically the oldest one of those was Sarah Hoyt's, but her series wasn't that long so I didn't feel urgency about it. After that it was down to Rachel Caine and Darynda Jones, and I felt slightly more like the Rachel Caine, so here it is.
To be precise, this is Rachel Caine's Weather Warden series, which is about the group of magically gifted people who try to keep extreme weather under control. That status quo didn't last for long; by this, the fifth book, things seem to have been pretty much upended, with conflict with the djinns and weather getting worse faster than the beleaguered Wardens can deal with it. Our main character, Joanne Baldwin, has been part of the world of the djinns, but now that that's turned hostile she's seeking refuge with the Weather Wardens, what there is of them.
Sometimes it seems like the titles are a little bit figurative, but there's nothing figurative about the firestorm here. There is a big old forest fire (and I'm reading this as southern California is beset by wildfires, yikes) and lightning and demons, and poor Joanne has a hard time of it. By the way, this book came out in 2007, when it seemed like we were just beginning to become aware of extreme weather, after the record-breaking 2005 hurricane season, and now it seems alarmingly prescient.
I found this pretty satisfying all in all, the tension and the stakes staying high all the way through. Even the one subplot which seemed like it had lower stakes, just about saving her sister rather than saving the world, was gripping because it was personal, and so she couldn't leave it to deal with the things threatening the entire world. Then the book ended on a real plot twist which looks like it'll be setting up the next book.
4. Dick Francis: Enquiry, completed January 13
Continuing in my publication-order reread of Dick Francis; I think I'm up to 1969. I had only the vaguest memories of this one, though apparently I first read it in 2006, ninth most recent of all the books of his I read until I started these rereads.
In many ways it's nothing particularly special. Our protagonist is a jockey, which is not unexpected; of Francis's many protagonists, most of them are at least part-time jockeys, even if they have another profession, though of course many just have racing-related jobs and some just have friends/relatives who are in racing. But Kelly Hughes is just a jockey. It starts off with him just having been "warned off", i.e. suspended from being a jockey or horse trainer, for an indefinite period, though we see the enquiry itself in flashbacks over the beginning of the book. Hughes knows he's innocent, but the evidence against him seemed damning, so once he recovers from the blow he starts investigating.
The usual things follow--he finds some clues, he annoys some people, someone tries to kill him, someone beat him up, and eventually he is victorious. There's also a girl, introduced early on, that he ends up in a relationship with. (Hughes was married but his wife died a few years earlier.) I admit that I did not guess (or remember) who the actual culprits were before they were revealed at the end, and I'm not sure I quite bought it. We had friendly-seeming characters who were actually friendly, instead of being the secret mastermind behind the whole thing, which threw me off a bit.
My copy was from the Pan paperback series, where they often have a single object on the cover on a stark white background; in this case it's a leather full-face mask, like a gimp mask. Often this object is something that the protagonist has to deal with as part of the climax, but in this case it's something that was discussed but never actually shown. You see, apparently part of the plot revolves around someone being blackmailed for being in a secret BDSM club, even though they were wearing one of these masks. Scandalous for 1969, I'm sure, though apparently it was still something that you could put into your mystery novel.
5. Liu Cixin: The Three-Body Problem, completed January 18
Time for the male diversity slot again. Unfortunately I had pretty much run out of stuff; I thought there was another P. Djéli Clark ebook around, but apparently I had already read that one. And I do have the next Wesley Chu book, sequel to The Art of Prophecy, but that was literally the last one I'd read so I didn't want to use it up quite yet. At first I decided to look for the next Ken Liu book at the library, but my wife pointed out I could also try this one. It did win a bunch of awards, after all, even if she hadn't enjoyed it personally herself. In the end, I did put in a request for it, and it even came in on the day I finished Enquiry, so I didn't have to rearrange things to accommodate it.
Interestingly enough, Ken Liu is the translater of this edition, which I'd forgotten. I know little about it going in, having managed to avoid any spoilers so far; I'm just hoping I'm going to be able to keep track of names, since I have had trouble retaining Chinese names in the past.
It's an odd book, but I expected that I would find it so because, you know, it's from China. It started in the Cultural Revolution, which I'm thinking I would not have wanted to have lived through--or perhaps I wouldn't have. I would've been executed for my reactionary beliefs (like "science is real") or something, you know. Most of the book takes place in the "present day" (ca. 2007, I guess, when it was written). Scientists are getting flummoxed (to the point of depression and suicide) by bizarrely inconsistent results in particle physics. And a nanotechnology researcher (our main POV character) starts seeing mysterious floating countdown images--first on his camera images, then on his eyes. He's also trying this VR game called "Three-Body Problem", about trying to come up with some way of solving the habitability problem of a planet with three suns, which orbits around them chaotically. And it all comes down to a woman who survived the Cultural Revolution and ended up working on a remote radar base.
This is very much an idea book, with few well-drawn characters in it, but it says some provocative things. It also dwells on the real-life three-body problem--the fact that it is impossible for a general analytic solution to the motion of three bodies, and even numerical solutions have to deal with sensitivity to initial conditions leading to unpredictable behaviour. The last part of the book gets quite weird and makes me think more of Stanislaw Lem than anything else. There are apparently two sequels, and an adaptation on Netflix; I'm not sure if I will pursue either of them, but given the paucity of my male diversity list I think the odds of my reading the books, at least, is fairly high.
6. R. Scott Bakker: The Judging Eye, completed January 28
Next it was time for another male-author book, and I felt like probably an epic fantasy after that weird SF. There were a few I was considering, and the Bakker was one of them; since I've been avoiding it for a while (perhaps because of its thickness), I decided to go with it.
This is the first book of a series, but it's the sequel series to the "Prince of Nothing" trilogy that I read some time ago. I generally enjoyed it, though it's kind of a bloody series. Our main character, Anasûrimbor Kellhus, is sent from his isolated monastery to respond to a telepathic summons from his father. The only problem is, the place where he has to go is the target of a bloody holy war (heavily based on one or more of the Crusades, as far as I could tell). No problem, Kellhus's training makes manipulating regular people extremely easy, and it doesn't take long before he's basically in charge. He also has to deal with shape-shifters who have infiltrated everywhere and have some nefarious purpose that I can't quite remember right now. There's only a couple of people who realize how much he's manipulating everybody, and rebel against it, and they're cast out as heretics.
It wasn't too hard to pick things back up; partly because there was a "what has gone before" kind of recap, even if it was in the end matter instead of at the beginning, and the first few pages of it were all the underpinnings of the big world problems in ancient history. In this series, it's about twenty years later, and Kellhus is taking a large army to the north to destroy his ancient enemies, while his youngest child (who seems a nice, reliable sort with voices in his head, kind of like Alia "Abomination" Atreides was) prepares to come of age. We also follow Kellhus's wife Esmenet, who is left in charge even though she's a little over her head (though Kellhus is apparently in touch through magical means and can teleport back in if he thinks he needs to); Drusas Achamian, a mage who was one of Kellhus's first friends (and Esmenet's prior lover) until he turned against him, and is trying to find out more about Kellhus's origins; and the king of a freshly-conquered nation (who inherited his throne when Kellhus killed his father) who's being brought along with Kellhus's army. Oh, and a woman who is Esmenet's daughter and maybe Achamian's as well (Esmenet was a prostitute for many years, so Empress is a big step up for her), who's trying to get Achamian to teach her magic. And the high priestess of a cult that has a large following among the downtrodden, and is waiting for the White Luck Warrior (which is the name of the second book, so I'm thinking they'll be significant).
There are some bits which seemed a little too Tolkien-derivative, though. The historical recap talks a lot about the "Nonmen" who preceded the rise of Men, but when we see one of them we realize that these are just basically Elves, with Tolkien Elf-like names. The "Sranc" bad guys who've overrun large chunks of the northern wilderness are very Orc-coded. And when one group has to choose between going over snowy mountains or through ancient Nonmen caverns underneath…and at some point they get trapped and have to fight against not only a bunch of Sranc, but also some large troll-like "Bashrag"…that is extremely Moria-coded. The characters are more Malazan-ish, but still.
But on the whole I enjoyed it, and am somewhat curious where it's headed. I have the next book, but not the two after that, which are probably out of print by now, but what else is new.
Right, so, Dennis Valdron's book on Lexx Season 2. Well, there was a TV series called Lexx, an oddball SF thing that was a German/Canadian coproduction, with a group of ridiculous misfits going around the galaxy in a very powerful dragonfly-shaped ship called the Lexx. Like a hornier Red Dwarf, perhaps. We have Stanley Tweedle, security guard 4th class and accidental traitor; Xev Bellringer, former cage-raised bride turned sex slave, except instead of mental programming she ended up with lizard DNA instead; Kai, long-dead hero of the Brunnen-Ji, reanimated as an emotionless assassin; and 790, the head of an android who got the sex-slave programming intended for Xev. The first season was actually just four TV movies, but the second was full-length and was just all over the place…with a running thread about a guy named Mantrid whose goal was to convert the entire universe into himself. Dennis Valdron, a Canadian SF writer, lawyer, and shit-disturber, wrote some books about the series, with lots of behind-the-scenes info, and I've been enjoying them. I was trying to rewatch the show along with my read, which took me a while because I don't binge-watch, but I did managed to finish it. Probably sometime this year I'll start on Season 3 (which I also have on DVD) and have to pick up the next Valdron book.
I did end up giving up on the Sugar: A Bittersweet History book. A.K.A. Sugar: It's All About Slavery. I kept getting to a point where I could begin to hope that we were done talking about slavery, but nope! Now that we're done talking about slavery in the Caribbean, let's talk about it in Louisiana! Or South Africa! Okay, now let's talk about indentured servitude, and how in the end they were treated basically the same as the slaves, and in fact were pitted against each other! The only bright spot I ran across was on the island of Mauritius, where the African slaves and Indian indentured servants made common cause and things turned out better. I mean, I get that slavery was bad, that sugar plantations were apparently one of the worst offenders, and that entitled rich people attempting to screw the people working for them out of anything they could get away with were not a twentieth-century invention. Probably it's good to be reminded about the horrors of slavery from time to time. And if there had been any mention of slavery on the front of back cover of the book, I might be more forgiving. But there was not. And the book was more about slavery than it was about sugar. It was more about the harvesting of sugar cane, as a crop, than about sugar itself. And I just got tired of it.
I already have several other nonfiction books--just among my recent acquisitions, mind you, not ones that are sitting unread on the shelf from when I got them years ago--waiting to be read. Perhaps I should be leaping immediately to the one I got for Christmas, the new Yuval Noah Harari, but instead I picked one of the bought-on-a-whim-because-it-was-remaindered-and-deeply-discounted hardcovers that represent most of my nonfiction purchases these days. It's a book called Wild And Crazy Guys by Nick de Semlyen, which is about early Saturday Night Live comedians and adjacent--John Belushi, Dan Aykroyd, Eddie Murphy, Steve Martin, John Candy, Rick Moranis, and Bill Murray--and "how they changed the movie industry forever". I found it kind of interesting, and in some cases makes me want to go back and try some of these movies that I missed at the time, or rewatch the ones that I did see back then. (I imagine I'll be rewatching "Groundhog Day" on February 2nd this year, as I often do.)
#T. Kingfisher#Clocktaur Wars#Allan Cole#Chris Bunch#Sten#Rachel Caine#Weather Wardens#Dick Francis#Liu Cixin#R. Scott Bakker#Dennis Valdron#Lexx#Nick de Semlyen#books#reading
0 notes
Photo
34. I will not turn into a snake. It never helps.
--"Things I'll do if I ever become an Evil Overlord", FidoNet, 1990
Has anybody else single-handedly inspired an entry on the evil overlord list?







Thulsa Doom - Conan the Barbarian (1982)
1K notes
·
View notes
Text

SixDegrees is often considered the first social media site, launching in 1997. It allowed users to create profiles, connect with friends, and list their schools.
Explanation
SixDegrees was founded by Andrew Weinreich in 1996.
The site's name comes from the idea that everyone on Earth is separated by no more than six degrees of separation.
SixDegrees combined popular features like profiles, friends lists, and school affiliations.
The site was sold to YouthStream Media Networks in December 2000.
Other early social media platforms include:
PLATO Notes: A conferencing and bulletin board forum system created by Dave Woolley in 1974
Bulletin Board System (BBS): One of the earliest known forms of social media, popular until the late 1990s
FidoNet: Formed in 1984 as BBSs began exchanging email
Blogging and bulletin: The starting point for social media sites in the 1990s
0 notes