#ey hashtag
Explore tagged Tumblr posts
Text
Cyber Resilience: Embracing Tomorrow’s Security
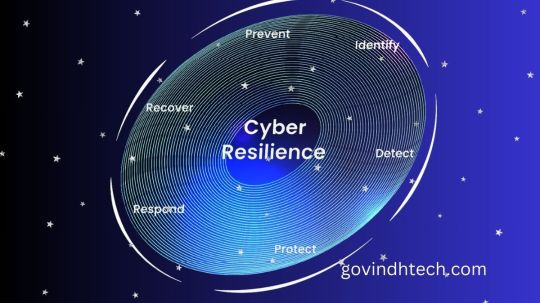
What is cyber resilience?
Business continuity, information systems security, and organizational resilience are all included under the idea of cyber resilience.
Cyber resilience framework
The harsh reality for leaders in cybersecurity is that they must protect a growing number of attack surfaces while dealing with persistently aggressive, constantly changing hostile actors. The data indicates that conventional security techniques and instruments are insufficient to ensure the safety of organizations. Organizations face 44 major cyber events annually on average, according to the EY 2023 Global Cybersecurity Leadership Insights Study, and ransomware expenses are expected to hit $265 billion by 2031. Only one in five chief information security officers (CISOs) said their firms’ current methods were successful against contemporary threats, indicating that the majority of CISOs already know what their organizations are doing is inadequate.
Cyber resilience plan
According to the EY 2023 Global Cybersecurity Leadership Insights Study, C-suite executives are battling a variety of known and unknown threats. However, it also provides comfort in knowing that diverse results are experienced by enterprises, some of which may be attributed to their cybersecurity approach. Businesses may improve their cybersecurity by taking a cue from the best and focusing on integration of cybersecurity concerns across the whole business, simplicity, and holistic thinking. Prone Enterprises has the ability to get all of these. Important takeaways from the survey are as follows:
Simplify the cyber technology stack to make it more visible and lower risk. By clearing up the technological environment via automation and orchestration, you can identify signals more quickly and take action more skillfully.
Reduce supply chain access points for hackers, increase cyber alertness, and continually evaluate performance by using automation and standardization without introducing needless bureaucracy. This guarantees early vendor selection involvement for security teams as well.
Convert your tale into a narrative that speaks to the company in terms of value generation, business impact, and risk buydown.
To make the workforce cyber-secure by design, combine automation and preventive technologies with well-planned, gradual training.
Integrate cybersecurity into your company’s operations rather than seeing it as a hindrance. It creates value, gives people the self-assurance they need to innovate, and creates new income streams and market prospects.
Even the most experienced cybersecurity professionals face novel and unanticipated problems as a result of the ever-changing threat environment. In addition to moving beyond reactive technology adoption and disaster recovery, organizations must constantly improve their security procedures and embrace an approach that centers cyber resilience inside an end-to-end organizational strategy.
Cyber resilience is a holistic strategy to defending enterprises that includes business continuity, information systems security, and organizational resilience. It goes well beyond just anticipating and reacting to threats and assaults. Cyber resilient firms must integrate security into every element of their operations and iterate to improve their posture. Innovators are helping achieve cyber resilience, which is difficult.
Cyber resilience vs cyber security
The first issue that gives rise to the requirement for cyber resilience is the extreme complexity that security executives are now facing in their enterprise’s technology and security ecosystems. The use of many technological solutions by IT and security professionals to counter attacks has resulted in significant complexity in their tech stacks and security plans. According to EY study, the most often mentioned internal obstacle to an organization’s cybersecurity strategy is “too many attack surfaces.” Additionally, 75% of respondents identified cloud and Internet of Things (IoT) as the top technological concerns for the next five years. Emerging technologies and generative AI (GenAI) provide additional complexity and dangers to the enterprise.
Cost and cross-functional work provide the second challenge. In the past, the majority of companies have provided strong support for cybersecurity expenditures. However, if threats increase in strength and number, businesses could start to doubt their financial commitments. Security has to be a company-wide endeavor, not only the domain of the IT department and cybersecurity teams, in order to decide where to allocate their money for security and implement top-down initiatives.
More than ever, companies need to integrate security into their technology instead of depending only on security personnel to safeguard all facets of their operations. Improved communication across organizational layers is necessary to transform cybersecurity from a compartmentalized endeavor into a cross-functional operation, which is a feature of the most successful security programs.
Finally, leaders need a mentality change. Strong cybersecurity is no longer a game of cat and mouse with unique solutions to address unique assaults because the rules have changed. In the current threat environment, a firm must contend with skilled attackers and not rely just on disaster recovery or business continuity plans. The ultimate answer, cyber resilience, can only be achieved by a company-wide integration of security policies, procedures, and technologies, which calls on leadership to adopt a more comprehensive and intrinsic security strategy.
Resilience cyber insurance solutions
To assist provide enterprises an advantage over contemporary cyber threats, the EY organization and Dell technology have collaborated with industry experts to develop an intelligent cyber resilience platform driven by AI/ML technology. The two innovators combine Dell’s data security technologies and cyber resilience tactics with the comprehensive industry knowledge and vision of the EY team. Together, they bring a wealth of technology and experience to the table. With the help of this potent combination, businesses can transform a complicated environment into a multilayered defensive system that can endure both changing risk and severe digital upheaval.
The alliance excels at using these technologies with the appropriate setup and procedures. The correct operational approach and the latest technology advances work together to create true cyber resilience, and each firm has a distinct optimal approach. Teams from EY and Dell are excellent at providing cybersecurity solutions that work as well as a tried-and-true process for operationalizing them to increase resilience, flexibility, and overall security posture. In order to understand an organization’s data challenges and vulnerabilities and to customize a solution to meet their needs, the EY organization and Dell collaborate closely with leaders in the industry. This allows the organization to secure its critical data from cyber threats��while maintaining accessibility for daily operations.
Strengthen Your Cybersecurity Hardiness with Dell and EY
The partnership between EY and Dell Technologies gives progressive companies the adaptability they need to use advanced cybersecurity to fend off attackers and withstand changing threats. When together, they support organizations by:
Utilize an integrated, unified cyber resilience solution to handle the ever-increasing complexity of the technological and security environments.
Using a cross-functional collaborative strategy, bring all aspects of your firm under the cyber resilience umbrella.
Change the way you think about security in your firm and adopt a comprehensive strategy to cyber resilience that integrates procedures, policies, and resources across the whole enterprise.
Read more on govindhtech.com
#cyberresilience hashtag#cybersecurity hashtag#ey hashtag#dell hashtag#cyberthreats hashtag#genai hashtag#ml hashtag#ai hashtag#technology hashtag#technews hashtag#govindhtech
0 notes
Text

Earthspark Starscream and Megatron yet again
#I think they should hug it out#afterwards they just walk away like nothing happened#and hashtag looks at them with sad puppy eyes asking if they had a fight#megs says yeah but we hugged after#and she’s like 👁👄👁#they make me ill#transformers earthspark#transformers#tf es#megatron#starscream#es starscream#es megatron#once again can be interpreted as ship or not
494 notes
·
View notes
Text

sisterhood of the Well
(this is a piece about parts of a DID system supporting eachother, please dont be weird about it)
#doodle heaven#my ocs#princess rose#personas#im aware i have more eyes on my art than usual and idk im not in the mood to deal with all the hashtag gender on my arts#but since this is positivity for my system it can be for yours too
405 notes
·
View notes
Text
It's always "Kakashi and his mask", the game he played since kindergarten. But he's not the only one, yk.

I present to you Obito and his goggles.
The slight tilt of the head, the right angle where the sun would do its magic at the perfect time and now you could not see his eyes. At all. Not if he doesn't want you to.
Ah and I also have this.
Obito, what are you actually hiding behind those goggles?

(Closeups under the cut)




#naruto#naruto headcanons#didn't know it's a hashtag lol#naruto fanart#Obito#uchiha obito#obito uchiha#minato namikaze#rin nohara#Kakashi hatake#Kakashi fake idgaf-ker#team minato#I just thought its funny that Obito would trick Minato with hia silly goggles game#to the point that the adult had no idea of how he looks like#or if he had eyes at all#український tumblr#укртумбочка
391 notes
·
View notes
Text
“The hands that cradled your face and tilted it upward to kiss your forehead are soaked in unfathomable quantities of blood.”
“But they cradled me, yes?”

I got really into the theory of the apple (from that one image from the beast yeast chapter 7/8 leaks) being the fruit of knowledge. And I thought, what if Pure Vanilla takes a bite out of it? (*^▽^)/★*☆♪
So here’s an artwork where Pure Vanilla is slowly going insane after taking a bite, and all Shadow Milk can do is hold him as he succumbs to the same insanity that claimed him so long ago. Fun stuff, am I right? ((o(^∇^)o))
#pure vanilla crk#shadow milk crk#shadowvanilla#cookie run kingdom#pure vanilla cookie#pureshadow#shadow milk cookie#vanilla milkshake#laughs evilly as I scurry back to my cave to disappear for another month#my fellow Shadowvanilla shippers I have returned#my discord still doesn’t work and I’m still upset about it#how am I supposed to live laugh love if I can’t share my artworks on the vanilla milkshake server?#sad times indeed#anyways I hope nobody mistakes the yellow eyes on my drawing for bill cipher just because they’re yellow#I needed some toe curling angst after being gone for so long#I live off of doomed yaoi#also look at how my art has somewhat improved me is very happy#I should get my pookie to write a fanfic on this don’t you think?#okay this is probably too many hashtags sorgy
359 notes
·
View notes
Text

inari
#may have eye strained too close to the sun w this one#hashtag yolo#eyestrain#cw eyestrain#persona#persona series#persona 5#persona 5 royal#p5#p5r#yusuke kitagawa#p5 yusuke#p5 fanart#persona 5 fanart#p5 fox#my art
356 notes
·
View notes
Text

Nightshade is such a little creature I love their beeg ol' owl optics so much-
I really wanted to draw these two together but the only thing that came in my brain was this meme XD These two goobers are a very underrated combo imo, i need them to interact so bad ewfhwfinwjkf
#tfe starscream#nightshade malto#transformers#tfe#beeg ol eyes meme#thought about rewording it to sound more like something star would say#but thought it'd be more funny to just keep it as is for the silly#could be something he heard from hashtag#never know-#the kiddos will infect the lingo it is inevitable
303 notes
·
View notes
Text



isat stuff. uuuhhhh. kicks rock. the guy i keep under the waters here too for formatting purposes i guess
#cw body horror#kind of???? idk#cw scopophobia#in stars and time spoilers#isat#in stars and time#duuude i drew siffrin holding that candlestick so wrong#no wonder they dropped that shit ... man#loop's eye here is based off 1 of those neighborhood watch signs#looove those sign designs so much#the one im referencing looks like a fish i loves it#not doijg character tags bevause im hashtag sleepy
159 notes
·
View notes
Text

Viktor procrastination sketches ✌️

Golden lashes inspo!

#also yes I did his eyes brown rather than gold cause I'm a firm believer of brown-amber hued natural eyes!au viktor 😌 like honey#noliaert#my art#arcane#arcane fanart#fanart#viktor arcane#the sweater was originally meant to be a moss green lol#people w keen eyes will notice I added 2 more small moles by his mouth + a barely noticable vein by his eye //= hashtag projecting#(I too got one under my eye but i didnt care to add double lmao)
126 notes
·
View notes
Text



My light. My Claudia. My redemption.
#iwtv#amc iwtv#interview with the vampire#this is from back in November but I still really like them. I drew this with India ink and a twig from the graveyard that I sharpened into a#tiny wooden stake so. thematic hashtag vampire#I probably won’t post more iwtv fanart bc the show makes me feel so ill when I think about it I can’t put it to paper but we’ll see#claudia de pointe du lac#louis de pointe du lac#I like drawing Claudia the most I have a bunch of little drawings of her that look more like her but I’m only posting these bc they have a#nice flow to them. I’m rewatching w my friend and we’ve had to take like a 3 month break before the end of season 1 I can’t wait to#get to Delainey Claudia I like her eyes I can’t draw her well yet it upsets me
136 notes
·
View notes
Text

arson countdown direct to video disney sequel
#tight high boots are not strictly period accurate but let this poor fool plead artistic license.#mizu blue eye samurai#abijah fowler#blue eye samurai#***png#ok bye i’m thawing out the fridge hashtag BOTULISM. much to do. much to see.#in other words making s2 predictions gives me Such Brainworms i can barely function so we will not speak of that.
685 notes
·
View notes
Text

SHRRGFFFF... OUUUUUEUEUUUUUU PROFESSOR BOXLEITNER NOOO DONT CRY WAAHH anyways og under the cut

#wordgirl#dr two brains#steven boxleitner#wordgirl fanart#wordgirl pbs#pbs kids#pastrami sandwiches#fanart#dr. two brains#amazo guy#amazing cheese#NOOO PROFESSOR AAAA#-i say as i make his face redder and deepen the bags under his eyes#do you like making your comfort characters suffer or are you normal#HAHA SORRY FOR BEING GONE GUYS....#I PLAN TO POST MORE#(me making fake promises for the 17th time)WOAH WHO SAID THAT NO CMON CHAT TRUST ME#headcanon they used to make each other cookies often but but now amazo's gone so its just steveAHAHA NORMAL ABOUT THIS#blame user nomoretumbler#didnt know what to do for his apron i gave him wordgirl merch#hashtag what supportive mentor!!😎#i had no other options if you want a good laugh look up 'science apron' and see all the.. awesome options..#ME WHEN AMAZING CHEESE OHHH OH GOD OHHH UHGHGHGJHGHHHR#:(((#I HATE THEM I HATE THEM#OPENS SPOTIFY#ADDS 7 SONGS TO THE AMAZING CHEESE PLAYLIST#I HATE THEM I HATE THEM I HATE THEM#just kidding guys i love them thank you user djsadbean🛐#woah reached tag limit again K BYE GUYS
173 notes
·
View notes
Text


@lewishamilton and @charles_leclerc: dog dads
#i cannot EYE CANNOT believe this is my life the implications of this link up are astronomical#these pics specifically…… they woke up that day and said hashtag family#charles leclerc#lewis hamilton#roscoe#leo#1644#liz.jpg#we need to abolish the capitalist system we live in bc there’s no way i was able to edit these just now
373 notes
·
View notes
Text

uuuyjhhhhhhhh solid snack
#MGS#metal gear solid#solid snake#his eye being obscured kind of makes him look like big boss hashtag agony#my art 🖼️
66 notes
·
View notes
Text

Hamilton slowly trying to get me back in fandom, but I stubbornly resist this temptation
…but as you can see, i cannot fully say no to this… 😤😔
#john laurens#hamilton lams#hamilton#alexander hamilton#hamilton musical#hamilton fanart#hamilton art#fanart#digital#digital aritst#art#my art#artists on tumblr#lams#sketch#gay men#gay#gay love#gay pride#why are you looking at me like that#first time ey?#why are you even looking at hashtags#:0
310 notes
·
View notes
Text
hey guys. I don't normally reblog info on this blog but I do want to remind everybody reading to learn about palestine, sudan and drc, as well as many other peoples currently under genocide.
here are four mastelists with information, sources and donation links and please save them and use them. use the hashtags and read some more. don't buy tech unless necessary and participate in the boycott initiated by the BDS
here's a more recent donation links post
and a post with recommendations for what you can do if you aren't able to donate
tens of millions of people are under genocide and ethnic cleansing. the absolute least we can do is learn and talk about it. if you can, do more than that.

#this is a small community and i want to reach out to you guys#i hope nobody here is a mf enough to complain about this being under the hashtag#extreme ghostbusters#free palestine#keep eyes on sudan#free drc#palestine#sudan#democratic republic of the congo
318 notes
·
View notes