#decrypt .your_last_chance files
Explore tagged Tumblr posts
Text
How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files
What’s CryptON Ransomware
Word: Some versions of CryptON Ransomware are decryptable. You’ll be able to attempt free decryptors provided under and attempt to restore encrypted information. In any other case, hold your information till effective decryptor can be launched.
Notice: In July 2019 new variation of Nemesis Ransomware was discovered. It appends .YOUR_LAST_CHANCE extension to encrypted information. Ransom observe file is known as: _RESTORE FILES_.txt. Victims are provided to contact malefactors by way of e-mails: [email protected], [email protected] or [email protected].
CryptON Ransomware or Nemesis Ransomware or X3M Ransomware is among the most dangerous and wide-spread ransomware households. At present, there are multiple successors of initial virus and a number of other deviations constructed on one other platforms. Cry9, Cry36 and Cry128 Ransomware came from this collection. Virus makes use of mixture of AES-256, RSA-2048 and SHA-256 encryption algorithms. Newest discovered version is definitely referred to as CryptON Ransomware and makes use of [email protected] extension for affected information. Other used suffixes are:
.YOUR_LAST_CHANCE, _x3m, _locked, _crypt, .encrptd, _locked_by_krec, _locked_by_perfect, _r9oj, .nemesis, .v8dp, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_, .-juccy[a]protonmail.ch, _[[email protected]].xj5v2, .-sofia_lobster[a]protonmail.ch, _[wqfhdgpdelcgww4g.onion.to].r2vy6, _[qg6m5wo7h3id55ym.onion.to].63vc4, _2irbar3mjvbap6gt.onion.to._, _gebdp3k7bolalnd4.onion._, .fgb45ft3pqamyji7.onion.to._, .losers, .damoclis
Ransomware calls for from zero.2 to 1 BitCoin for decryption. It isn’t really helpful to pay the ransom as there are not any guarantee malefactors will send decryption key. Depending on version, after encryption CryptON Ransomware creates totally different text information with directions to pay the ransom. Current model makes use of HOWTODECRYPTFILES.html and it incorporates following info:
CryptON Ransomware
All information are encrypted! CryptON Ransomware To decrypt the information, you want to purchase special software program «CryptON decryptor» Restore the info, comply with the instructions! You possibly can study extra / request e-mail: [email protected] You’ll be able to study extra/questions within the chat: https://cryptxf3zamy5kfz.tor2web.link (not need Tor) https://cryptxf3zamy5kfz.onion.plus (not need Tor) http://cryptxf3zamy5kfz.onion/ (need Tor) You possibly can study extra drawback out bitmessage: https://bitmsg.me/ BM-2cWzhoNFbjQ3X8pULiWSyKhc6dedQ54zQ1 – If the resource is unavailable for a long time to put in and use the terms of reference of the browser: 1. + Begin the Internet browser 2. + Sort or copy the tackle https://www.torproject.org/download/download-easy.html within the tackle bar of your browser and press key ENTER three. + On the website you may be prompted to obtain the Tor browser, download and install it. To work. four. + Connection, click on “join” (utilizing English model) 5. + After connecting, open a traditional window Tor-browser 6. + Sort or copy the handle http://cryptxf3zamy5kfz.onion/ within the handle bar of Tor-browser and press key ENTER 7. + Watch for the download website // + When you’ve got any problems with set up or utilization, please go to the video: https://www.youtube.com/watch?v=gOgh3ABju6Q Your personal identification ID:-
YOUR_LAST_CHANCE Ransomware
*** ALL YOUR WORK AND PERSONAL FILES HAVE BEEN ENCRYPTED ***
To decrypt your information that you must purchase the particular software program ñ “Nemesis decryptor” You’ll find out the small print/buy decryptor + key/ask questions by e-mail: [email protected], [email protected] OR [email protected] IMPORTANT! DON’T TRY TO RESTORE YOU FILES BY YOUR SELF, YOU CAN DAMAGE FILES! If inside 24 hours you did not receive an answer by e mail, make sure to write to Jabber: [email protected] Your private ID: –
Different potential filenames for ransom notes information are: COMO_ABRIR_ARQUIVOS.txt, ###DECRYPT-MY-FILES###.txt, HOW_OPEN_FILES.html, DECRYPT MY FILE.txt. On this article we collected, consolidated and structured obtainable details about this malware and potential ways of decryption. Use directions on this web page to take away CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked information in Home windows 10, Windows 8 or Home windows 7.
How CryptON Ransomware infected your PC
Could be distributed by hacking by means of an unprotected RDP configuration, using e-mail spam and malicious attachments, fraudulent downloads, exploits, net injections, pretend updates, repackaged and infected installers. After infection and encryption, Scarab deletes shadow copies of information, system restore points, disables the Windows Boot Repair, using sure command immediate commands. Virus assigns certain ID with the victims, that is used to call these information and supposedly to ship decryption key. In an effort to forestall an infection with such a threats in future we advocate you to make use of SpyHunter and BitDefender Anti-Ransomware.
Download CryptON Ransomware Removing Software
Obtain Removing Software
To take away CryptON Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of CryptON Ransomware.
Learn how to remove CryptON Ransomware manually
It isn’t really helpful to take away CryptON Ransomware manually, for safer answer use Removing Tools as an alternative.
CryptON Ransomware information:
Crypton.exe FileSpy.exe invoice-0071350.js svchost.exe
CryptON Ransomware registry keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun”crypton” = “%AppDatapercentCrypton.exe” HKEY_CURRENT_USERSoftwareCrypton”mail” = “.exe”
How one can decrypt and restore .YOUR_LAST_CHANCE, _x3m or _locked information
Use automated decryptors
Obtain CryptON Decryptor
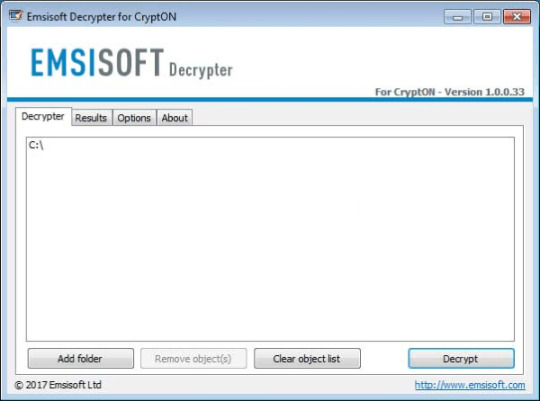
Use following software from Emsisoft referred to as Decryptor for CryptON, that may decrypt information with following extensions:
.id-_locked, .id-_locked_by_krec, .id-_locked_by_perfect, .id-_x3m, .id-_r9oj, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_
Obtain it right here:
Obtain Emsisoft CryptON Decryptor
Download Cry9 Decryptor
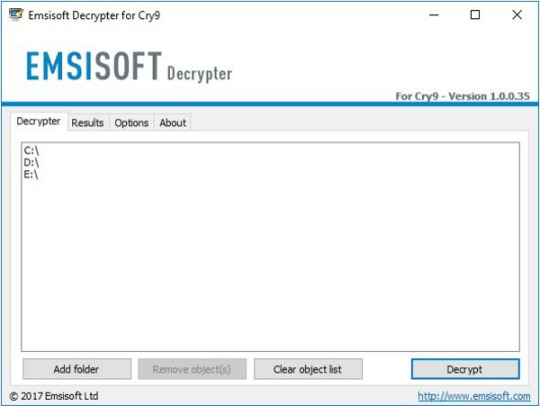
Use following device from Emsisoft referred to as Decryptor for Cry9, that can decrypt information with following extensions:
.-juccy[a]protonmail.ch, .id-, .id-_[[email protected]].xj5v2, .id-_r9oj, .id-_x3m, .id-_[[email protected]]_[[email protected]].x3m, “.”, .-sofia_lobster[a]protonmail.ch and ._[wqfhdgpdelcgww4g.onion.to].r2vy6
Obtain it here:
Obtain Emsisoft Cry9 Decryptor
Obtain Cry128 Decryptor
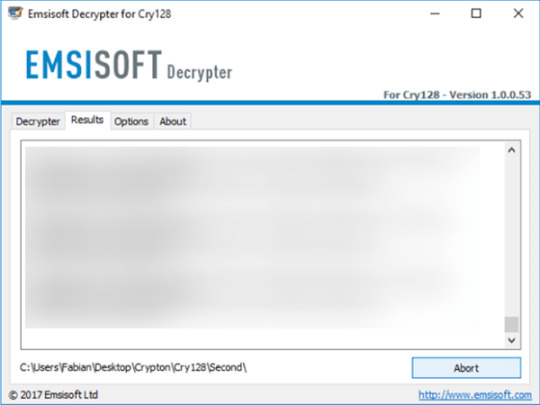
Use following software from Emsisoft referred to as Decryptor for Cry128, that may decrypt information with following extensions:
.fgb45ft3pqamyji7.onion.to._, .id__gebdp3k7bolalnd4.onion._, .id__2irbar3mjvbap6gt.onion.to._ and .id-_[qg6m5wo7h3id55ym.onion.to].63vc4
Download it here:
Download Emsisoft Cry128 Decryptor
There isn’t a function to pay the ransom because there isn’t a guarantee you’ll obtain the key, however you’ll put your financial institution credentials in danger.
In case you are contaminated with CryptON Ransomware and removed it out of your pc you’ll be able to try to decrypt your information. Antivirus distributors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you are able to do the following:
Use Stellar Knowledge Restoration Professional to revive .YOUR_LAST_CHANCE, _x3m or _locked information
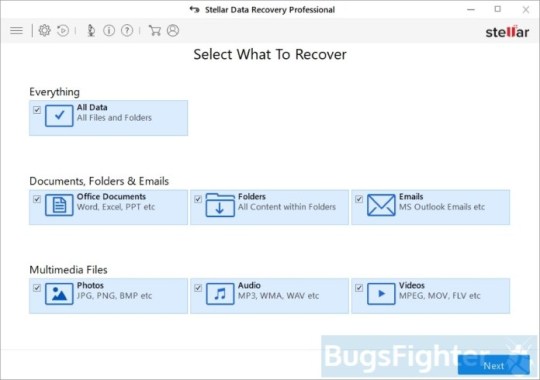
Download Stellar Knowledge Recovery Skilled.
Click Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview found information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Recovery Skilled
Utilizing Home windows Previous Versions choice:
Right-click on infected file and choose Properties.
Select Previous Versions tab.
Select specific model of the file and click Copy.
To restore the selected file and substitute the prevailing one, click on the Restore button.
In case there isn’t a gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Obtain Shadow Explorer program.
Run it and you will notice display itemizing of all of the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Right-click on a folder identify and select Export.
In case there are not any other dates within the listing, choose various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that incorporates encrypted information.
Right-click on the encrypted file and choose Earlier Versions.
Choose the model of the file you wish to restore and click on the Restore button.
Learn how to shield pc from viruses like CryptON Ransomware in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may aid you with lively anti-ransomware protection, as further defend to your present protection. It won’t conflict with greater safety purposes. In case you are looking complete internet security answer contemplate upgrading to full version of BitDefender Internet Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information utilizing easy online backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating bodily drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Home windows 10 and eight/eight.1 users can discover pre-installed OneDrive backup answer from Microsoft. It’s truly the most effective backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it right here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Using spam filters and creating anti-spam guidelines is sweet apply. One of many world leaders in anti-spam safety is SpamFighter. It works with numerous desktop purposes, and supplies very excessive degree of anti-spam protection.
Download SPAMFighter 5/5 (3)
The post How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files appeared first on Spouting-Tech.
#decrypt _crypt files#decrypt _locked files#decrypt _r9oj files#decrypt .damoclis files#decrypt .losers files#decrypt .nemesis files#decrypt [email protected] files#decrypt .x3m files#decrypt .your_last_chance files#Ransomware#remove cry128 ransomware#remove cry9 ransomware#remove crypton ransomware#remove losers ransomware#remove nemesis ransomware#remove x3m ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files
What’s CryptON Ransomware
Word: Some versions of CryptON Ransomware are decryptable. You’ll be able to attempt free decryptors provided under and attempt to restore encrypted information. In any other case, hold your information till effective decryptor can be launched.
Notice: In July 2019 new variation of Nemesis Ransomware was discovered. It appends .YOUR_LAST_CHANCE extension to encrypted information. Ransom observe file is known as: _RESTORE FILES_.txt. Victims are provided to contact malefactors by way of e-mails: [email protected], [email protected] or [email protected].
CryptON Ransomware or Nemesis Ransomware or X3M Ransomware is among the most dangerous and wide-spread ransomware households. At present, there are multiple successors of initial virus and a number of other deviations constructed on one other platforms. Cry9, Cry36 and Cry128 Ransomware came from this collection. Virus makes use of mixture of AES-256, RSA-2048 and SHA-256 encryption algorithms. Newest discovered version is definitely referred to as CryptON Ransomware and makes use of [email protected] extension for affected information. Other used suffixes are:
.YOUR_LAST_CHANCE, _x3m, _locked, _crypt, .encrptd, _locked_by_krec, _locked_by_perfect, _r9oj, .nemesis, .v8dp, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_, .-juccy[a]protonmail.ch, _[[email protected]].xj5v2, .-sofia_lobster[a]protonmail.ch, _[wqfhdgpdelcgww4g.onion.to].r2vy6, _[qg6m5wo7h3id55ym.onion.to].63vc4, _2irbar3mjvbap6gt.onion.to._, _gebdp3k7bolalnd4.onion._, .fgb45ft3pqamyji7.onion.to._, .losers, .damoclis
Ransomware calls for from zero.2 to 1 BitCoin for decryption. It isn’t really helpful to pay the ransom as there are not any guarantee malefactors will send decryption key. Depending on version, after encryption CryptON Ransomware creates totally different text information with directions to pay the ransom. Current model makes use of HOWTODECRYPTFILES.html and it incorporates following info:
CryptON Ransomware
All information are encrypted! CryptON Ransomware To decrypt the information, you want to purchase special software program «CryptON decryptor» Restore the info, comply with the instructions! You possibly can study extra / request e-mail: [email protected] You’ll be able to study extra/questions within the chat: https://cryptxf3zamy5kfz.tor2web.link (not need Tor) https://cryptxf3zamy5kfz.onion.plus (not need Tor) http://cryptxf3zamy5kfz.onion/ (need Tor) You possibly can study extra drawback out bitmessage: https://bitmsg.me/ BM-2cWzhoNFbjQ3X8pULiWSyKhc6dedQ54zQ1 – If the resource is unavailable for a long time to put in and use the terms of reference of the browser: 1. + Begin the Internet browser 2. + Sort or copy the tackle https://www.torproject.org/download/download-easy.html within the tackle bar of your browser and press key ENTER three. + On the website you may be prompted to obtain the Tor browser, download and install it. To work. four. + Connection, click on “join” (utilizing English model) 5. + After connecting, open a traditional window Tor-browser 6. + Sort or copy the handle http://cryptxf3zamy5kfz.onion/ within the handle bar of Tor-browser and press key ENTER 7. + Watch for the download website // + When you’ve got any problems with set up or utilization, please go to the video: https://www.youtube.com/watch?v=gOgh3ABju6Q Your personal identification ID:-
YOUR_LAST_CHANCE Ransomware
*** ALL YOUR WORK AND PERSONAL FILES HAVE BEEN ENCRYPTED ***
To decrypt your information that you must purchase the particular software program ñ “Nemesis decryptor” You’ll find out the small print/buy decryptor + key/ask questions by e-mail: [email protected], [email protected] OR [email protected] IMPORTANT! DON’T TRY TO RESTORE YOU FILES BY YOUR SELF, YOU CAN DAMAGE FILES! If inside 24 hours you did not receive an answer by e mail, make sure to write to Jabber: [email protected] Your private ID: –
Different potential filenames for ransom notes information are: COMO_ABRIR_ARQUIVOS.txt, ###DECRYPT-MY-FILES###.txt, HOW_OPEN_FILES.html, DECRYPT MY FILE.txt. On this article we collected, consolidated and structured obtainable details about this malware and potential ways of decryption. Use directions on this web page to take away CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked information in Home windows 10, Windows 8 or Home windows 7.
How CryptON Ransomware infected your PC
Could be distributed by hacking by means of an unprotected RDP configuration, using e-mail spam and malicious attachments, fraudulent downloads, exploits, net injections, pretend updates, repackaged and infected installers. After infection and encryption, Scarab deletes shadow copies of information, system restore points, disables the Windows Boot Repair, using sure command immediate commands. Virus assigns certain ID with the victims, that is used to call these information and supposedly to ship decryption key. In an effort to forestall an infection with such a threats in future we advocate you to make use of SpyHunter and BitDefender Anti-Ransomware.
Download CryptON Ransomware Removing Software
Obtain Removing Software
To take away CryptON Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of CryptON Ransomware.
Learn how to remove CryptON Ransomware manually
It isn’t really helpful to take away CryptON Ransomware manually, for safer answer use Removing Tools as an alternative.
CryptON Ransomware information:
Crypton.exe FileSpy.exe invoice-0071350.js svchost.exe
CryptON Ransomware registry keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun”crypton” = “%AppDatapercentCrypton.exe” HKEY_CURRENT_USERSoftwareCrypton”mail” = “.exe”
How one can decrypt and restore .YOUR_LAST_CHANCE, _x3m or _locked information
Use automated decryptors
Obtain CryptON Decryptor
Use following software from Emsisoft referred to as Decryptor for CryptON, that may decrypt information with following extensions:
.id-_locked, .id-_locked_by_krec, .id-_locked_by_perfect, .id-_x3m, .id-_r9oj, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_
Obtain it right here:
Obtain Emsisoft CryptON Decryptor
Download Cry9 Decryptor
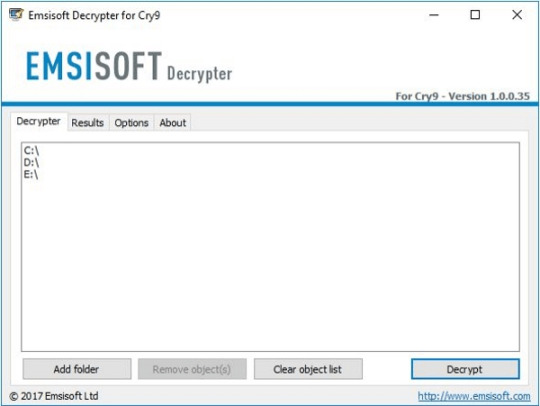
Use following device from Emsisoft referred to as Decryptor for Cry9, that can decrypt information with following extensions:
.-juccy[a]protonmail.ch, .id-, .id-_[[email protected]].xj5v2, .id-_r9oj, .id-_x3m, .id-_[[email protected]]_[[email protected]].x3m, “.”, .-sofia_lobster[a]protonmail.ch and ._[wqfhdgpdelcgww4g.onion.to].r2vy6
Obtain it here:
Obtain Emsisoft Cry9 Decryptor
Obtain Cry128 Decryptor
Use following software from Emsisoft referred to as Decryptor for Cry128, that may decrypt information with following extensions:
.fgb45ft3pqamyji7.onion.to._, .id__gebdp3k7bolalnd4.onion._, .id__2irbar3mjvbap6gt.onion.to._ and .id-_[qg6m5wo7h3id55ym.onion.to].63vc4
Download it here:
Download Emsisoft Cry128 Decryptor
There isn’t a function to pay the ransom because there isn’t a guarantee you’ll obtain the key, however you’ll put your financial institution credentials in danger.
In case you are contaminated with CryptON Ransomware and removed it out of your pc you’ll be able to try to decrypt your information. Antivirus distributors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you are able to do the following:
Use Stellar Knowledge Restoration Professional to revive .YOUR_LAST_CHANCE, _x3m or _locked information
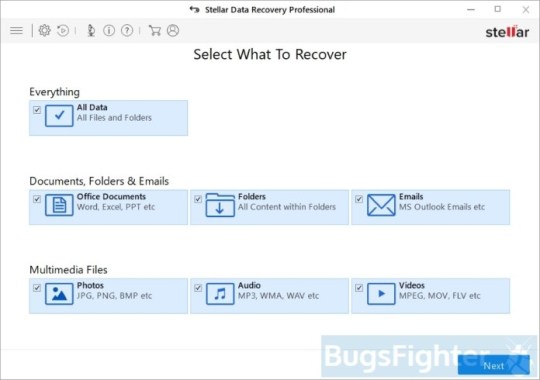
Download Stellar Knowledge Recovery Skilled.
Click Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview found information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Recovery Skilled
Utilizing Home windows Previous Versions choice:
Right-click on infected file and choose Properties.
Select Previous Versions tab.
Select specific model of the file and click Copy.
To restore the selected file and substitute the prevailing one, click on the Restore button.
In case there isn’t a gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Obtain Shadow Explorer program.
Run it and you will notice display itemizing of all of the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Right-click on a folder identify and select Export.
In case there are not any other dates within the listing, choose various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that incorporates encrypted information.
Right-click on the encrypted file and choose Earlier Versions.
Choose the model of the file you wish to restore and click on the Restore button.
Learn how to shield pc from viruses like CryptON Ransomware in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may aid you with lively anti-ransomware protection, as further defend to your present protection. It won’t conflict with greater safety purposes. In case you are looking complete internet security answer contemplate upgrading to full version of BitDefender Internet Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information utilizing easy online backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating bodily drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Home windows 10 and eight/eight.1 users can discover pre-installed OneDrive backup answer from Microsoft. It’s truly the most effective backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it right here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Using spam filters and creating anti-spam guidelines is sweet apply. One of many world leaders in anti-spam safety is SpamFighter. It works with numerous desktop purposes, and supplies very excessive degree of anti-spam protection.
Download SPAMFighter 5/5 (3)
The post How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files appeared first on Spouting-Tech.
#decrypt _crypt files#decrypt _locked files#decrypt _r9oj files#decrypt .damoclis files#decrypt .losers files#decrypt .nemesis files#decrypt [email protected] files#decrypt .x3m files#decrypt .your_last_chance files#Ransomware#remove cry128 ransomware#remove cry9 ransomware#remove crypton ransomware#remove losers ransomware#remove nemesis ransomware#remove x3m ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files
What’s CryptON Ransomware
Word: Some versions of CryptON Ransomware are decryptable. You’ll be able to attempt free decryptors provided under and attempt to restore encrypted information. In any other case, hold your information till effective decryptor can be launched.
Notice: In July 2019 new variation of Nemesis Ransomware was discovered. It appends .YOUR_LAST_CHANCE extension to encrypted information. Ransom observe file is known as: _RESTORE FILES_.txt. Victims are provided to contact malefactors by way of e-mails: [email protected], [email protected] or [email protected].
CryptON Ransomware or Nemesis Ransomware or X3M Ransomware is among the most dangerous and wide-spread ransomware households. At present, there are multiple successors of initial virus and a number of other deviations constructed on one other platforms. Cry9, Cry36 and Cry128 Ransomware came from this collection. Virus makes use of mixture of AES-256, RSA-2048 and SHA-256 encryption algorithms. Newest discovered version is definitely referred to as CryptON Ransomware and makes use of [email protected] extension for affected information. Other used suffixes are:
.YOUR_LAST_CHANCE, _x3m, _locked, _crypt, .encrptd, _locked_by_krec, _locked_by_perfect, _r9oj, .nemesis, .v8dp, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_, .-juccy[a]protonmail.ch, _[[email protected]].xj5v2, .-sofia_lobster[a]protonmail.ch, _[wqfhdgpdelcgww4g.onion.to].r2vy6, _[qg6m5wo7h3id55ym.onion.to].63vc4, _2irbar3mjvbap6gt.onion.to._, _gebdp3k7bolalnd4.onion._, .fgb45ft3pqamyji7.onion.to._, .losers, .damoclis
Ransomware calls for from zero.2 to 1 BitCoin for decryption. It isn’t really helpful to pay the ransom as there are not any guarantee malefactors will send decryption key. Depending on version, after encryption CryptON Ransomware creates totally different text information with directions to pay the ransom. Current model makes use of HOWTODECRYPTFILES.html and it incorporates following info:
CryptON Ransomware
All information are encrypted! CryptON Ransomware To decrypt the information, you want to purchase special software program «CryptON decryptor» Restore the info, comply with the instructions! You possibly can study extra / request e-mail: [email protected] You’ll be able to study extra/questions within the chat: https://cryptxf3zamy5kfz.tor2web.link (not need Tor) https://cryptxf3zamy5kfz.onion.plus (not need Tor) http://cryptxf3zamy5kfz.onion/ (need Tor) You possibly can study extra drawback out bitmessage: https://bitmsg.me/ BM-2cWzhoNFbjQ3X8pULiWSyKhc6dedQ54zQ1 – If the resource is unavailable for a long time to put in and use the terms of reference of the browser: 1. + Begin the Internet browser 2. + Sort or copy the tackle https://www.torproject.org/download/download-easy.html within the tackle bar of your browser and press key ENTER three. + On the website you may be prompted to obtain the Tor browser, download and install it. To work. four. + Connection, click on “join” (utilizing English model) 5. + After connecting, open a traditional window Tor-browser 6. + Sort or copy the handle http://cryptxf3zamy5kfz.onion/ within the handle bar of Tor-browser and press key ENTER 7. + Watch for the download website // + When you’ve got any problems with set up or utilization, please go to the video: https://www.youtube.com/watch?v=gOgh3ABju6Q Your personal identification ID:-
YOUR_LAST_CHANCE Ransomware
*** ALL YOUR WORK AND PERSONAL FILES HAVE BEEN ENCRYPTED ***
To decrypt your information that you must purchase the particular software program ñ “Nemesis decryptor” You’ll find out the small print/buy decryptor + key/ask questions by e-mail: [email protected], [email protected] OR [email protected] IMPORTANT! DON’T TRY TO RESTORE YOU FILES BY YOUR SELF, YOU CAN DAMAGE FILES! If inside 24 hours you did not receive an answer by e mail, make sure to write to Jabber: [email protected] Your private ID: –
Different potential filenames for ransom notes information are: COMO_ABRIR_ARQUIVOS.txt, ###DECRYPT-MY-FILES###.txt, HOW_OPEN_FILES.html, DECRYPT MY FILE.txt. On this article we collected, consolidated and structured obtainable details about this malware and potential ways of decryption. Use directions on this web page to take away CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked information in Home windows 10, Windows 8 or Home windows 7.
How CryptON Ransomware infected your PC
Could be distributed by hacking by means of an unprotected RDP configuration, using e-mail spam and malicious attachments, fraudulent downloads, exploits, net injections, pretend updates, repackaged and infected installers. After infection and encryption, Scarab deletes shadow copies of information, system restore points, disables the Windows Boot Repair, using sure command immediate commands. Virus assigns certain ID with the victims, that is used to call these information and supposedly to ship decryption key. In an effort to forestall an infection with such a threats in future we advocate you to make use of SpyHunter and BitDefender Anti-Ransomware.
Download CryptON Ransomware Removing Software
Obtain Removing Software
To take away CryptON Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of CryptON Ransomware.
Learn how to remove CryptON Ransomware manually
It isn’t really helpful to take away CryptON Ransomware manually, for safer answer use Removing Tools as an alternative.
CryptON Ransomware information:
Crypton.exe FileSpy.exe invoice-0071350.js svchost.exe
CryptON Ransomware registry keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun”crypton” = “%AppDatapercentCrypton.exe” HKEY_CURRENT_USERSoftwareCrypton”mail” = “.exe”
How one can decrypt and restore .YOUR_LAST_CHANCE, _x3m or _locked information
Use automated decryptors
Obtain CryptON Decryptor
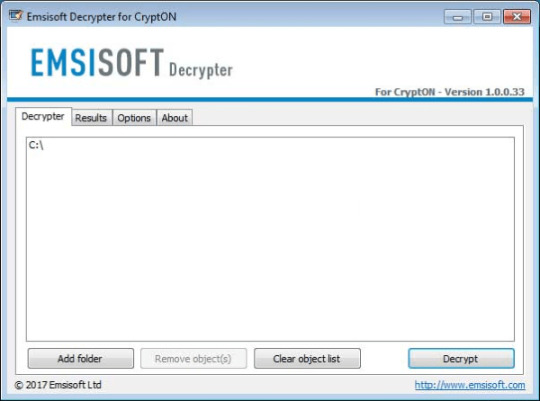
Use following software from Emsisoft referred to as Decryptor for CryptON, that may decrypt information with following extensions:
.id-_locked, .id-_locked_by_krec, .id-_locked_by_perfect, .id-_x3m, .id-_r9oj, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_
Obtain it right here:
Obtain Emsisoft CryptON Decryptor
Download Cry9 Decryptor
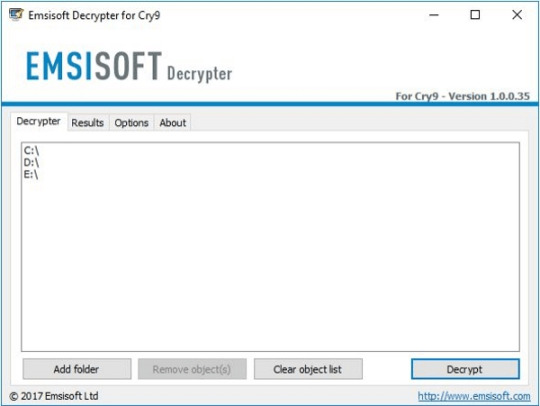
Use following device from Emsisoft referred to as Decryptor for Cry9, that can decrypt information with following extensions:
.-juccy[a]protonmail.ch, .id-, .id-_[[email protected]].xj5v2, .id-_r9oj, .id-_x3m, .id-_[[email protected]]_[[email protected]].x3m, “.”, .-sofia_lobster[a]protonmail.ch and ._[wqfhdgpdelcgww4g.onion.to].r2vy6
Obtain it here:
Obtain Emsisoft Cry9 Decryptor
Obtain Cry128 Decryptor
Use following software from Emsisoft referred to as Decryptor for Cry128, that may decrypt information with following extensions:
.fgb45ft3pqamyji7.onion.to._, .id__gebdp3k7bolalnd4.onion._, .id__2irbar3mjvbap6gt.onion.to._ and .id-_[qg6m5wo7h3id55ym.onion.to].63vc4
Download it here:
Download Emsisoft Cry128 Decryptor
There isn’t a function to pay the ransom because there isn’t a guarantee you’ll obtain the key, however you’ll put your financial institution credentials in danger.
In case you are contaminated with CryptON Ransomware and removed it out of your pc you’ll be able to try to decrypt your information. Antivirus distributors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you are able to do the following:
Use Stellar Knowledge Restoration Professional to revive .YOUR_LAST_CHANCE, _x3m or _locked information
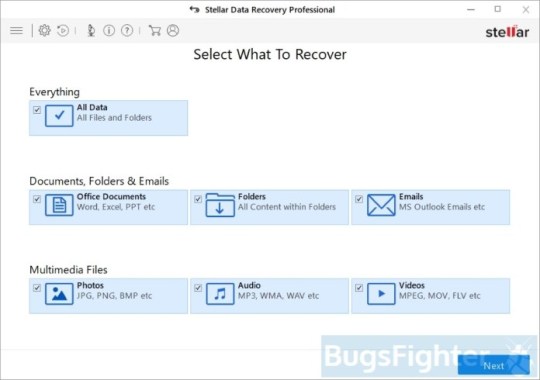
Download Stellar Knowledge Recovery Skilled.
Click Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview found information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Recovery Skilled
Utilizing Home windows Previous Versions choice:
Right-click on infected file and choose Properties.
Select Previous Versions tab.
Select specific model of the file and click Copy.
To restore the selected file and substitute the prevailing one, click on the Restore button.
In case there isn’t a gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Obtain Shadow Explorer program.
Run it and you will notice display itemizing of all of the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Right-click on a folder identify and select Export.
In case there are not any other dates within the listing, choose various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that incorporates encrypted information.
Right-click on the encrypted file and choose Earlier Versions.
Choose the model of the file you wish to restore and click on the Restore button.
Learn how to shield pc from viruses like CryptON Ransomware in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may aid you with lively anti-ransomware protection, as further defend to your present protection. It won’t conflict with greater safety purposes. In case you are looking complete internet security answer contemplate upgrading to full version of BitDefender Internet Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information utilizing easy online backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating bodily drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Home windows 10 and eight/eight.1 users can discover pre-installed OneDrive backup answer from Microsoft. It’s truly the most effective backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it right here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Using spam filters and creating anti-spam guidelines is sweet apply. One of many world leaders in anti-spam safety is SpamFighter. It works with numerous desktop purposes, and supplies very excessive degree of anti-spam protection.
Download SPAMFighter 5/5 (3)
The post How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files appeared first on Spouting-Tech.
#decrypt _crypt files#decrypt _locked files#decrypt _r9oj files#decrypt .damoclis files#decrypt .losers files#decrypt .nemesis files#decrypt [email protected] files#decrypt .x3m files#decrypt .your_last_chance files#Ransomware#remove cry128 ransomware#remove cry9 ransomware#remove crypton ransomware#remove losers ransomware#remove nemesis ransomware#remove x3m ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files
What’s CryptON Ransomware
Word: Some versions of CryptON Ransomware are decryptable. You’ll be able to attempt free decryptors provided under and attempt to restore encrypted information. In any other case, hold your information till effective decryptor can be launched.
Notice: In July 2019 new variation of Nemesis Ransomware was discovered. It appends .YOUR_LAST_CHANCE extension to encrypted information. Ransom observe file is known as: _RESTORE FILES_.txt. Victims are provided to contact malefactors by way of e-mails: [email protected], [email protected] or [email protected].
CryptON Ransomware or Nemesis Ransomware or X3M Ransomware is among the most dangerous and wide-spread ransomware households. At present, there are multiple successors of initial virus and a number of other deviations constructed on one other platforms. Cry9, Cry36 and Cry128 Ransomware came from this collection. Virus makes use of mixture of AES-256, RSA-2048 and SHA-256 encryption algorithms. Newest discovered version is definitely referred to as CryptON Ransomware and makes use of [email protected] extension for affected information. Other used suffixes are:
.YOUR_LAST_CHANCE, _x3m, _locked, _crypt, .encrptd, _locked_by_krec, _locked_by_perfect, _r9oj, .nemesis, .v8dp, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_, .-juccy[a]protonmail.ch, _[[email protected]].xj5v2, .-sofia_lobster[a]protonmail.ch, _[wqfhdgpdelcgww4g.onion.to].r2vy6, _[qg6m5wo7h3id55ym.onion.to].63vc4, _2irbar3mjvbap6gt.onion.to._, _gebdp3k7bolalnd4.onion._, .fgb45ft3pqamyji7.onion.to._, .losers, .damoclis
Ransomware calls for from zero.2 to 1 BitCoin for decryption. It isn’t really helpful to pay the ransom as there are not any guarantee malefactors will send decryption key. Depending on version, after encryption CryptON Ransomware creates totally different text information with directions to pay the ransom. Current model makes use of HOWTODECRYPTFILES.html and it incorporates following info:
CryptON Ransomware
All information are encrypted! CryptON Ransomware To decrypt the information, you want to purchase special software program «CryptON decryptor» Restore the info, comply with the instructions! You possibly can study extra / request e-mail: [email protected] You’ll be able to study extra/questions within the chat: https://cryptxf3zamy5kfz.tor2web.link (not need Tor) https://cryptxf3zamy5kfz.onion.plus (not need Tor) http://cryptxf3zamy5kfz.onion/ (need Tor) You possibly can study extra drawback out bitmessage: https://bitmsg.me/ BM-2cWzhoNFbjQ3X8pULiWSyKhc6dedQ54zQ1 – If the resource is unavailable for a long time to put in and use the terms of reference of the browser: 1. + Begin the Internet browser 2. + Sort or copy the tackle https://www.torproject.org/download/download-easy.html within the tackle bar of your browser and press key ENTER three. + On the website you may be prompted to obtain the Tor browser, download and install it. To work. four. + Connection, click on “join” (utilizing English model) 5. + After connecting, open a traditional window Tor-browser 6. + Sort or copy the handle http://cryptxf3zamy5kfz.onion/ within the handle bar of Tor-browser and press key ENTER 7. + Watch for the download website // + When you’ve got any problems with set up or utilization, please go to the video: https://www.youtube.com/watch?v=gOgh3ABju6Q Your personal identification ID:-
YOUR_LAST_CHANCE Ransomware
*** ALL YOUR WORK AND PERSONAL FILES HAVE BEEN ENCRYPTED ***
To decrypt your information that you must purchase the particular software program ñ “Nemesis decryptor” You’ll find out the small print/buy decryptor + key/ask questions by e-mail: [email protected], [email protected] OR [email protected] IMPORTANT! DON’T TRY TO RESTORE YOU FILES BY YOUR SELF, YOU CAN DAMAGE FILES! If inside 24 hours you did not receive an answer by e mail, make sure to write to Jabber: [email protected] Your private ID: –
Different potential filenames for ransom notes information are: COMO_ABRIR_ARQUIVOS.txt, ###DECRYPT-MY-FILES###.txt, HOW_OPEN_FILES.html, DECRYPT MY FILE.txt. On this article we collected, consolidated and structured obtainable details about this malware and potential ways of decryption. Use directions on this web page to take away CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked information in Home windows 10, Windows 8 or Home windows 7.
How CryptON Ransomware infected your PC
Could be distributed by hacking by means of an unprotected RDP configuration, using e-mail spam and malicious attachments, fraudulent downloads, exploits, net injections, pretend updates, repackaged and infected installers. After infection and encryption, Scarab deletes shadow copies of information, system restore points, disables the Windows Boot Repair, using sure command immediate commands. Virus assigns certain ID with the victims, that is used to call these information and supposedly to ship decryption key. In an effort to forestall an infection with such a threats in future we advocate you to make use of SpyHunter and BitDefender Anti-Ransomware.
Download CryptON Ransomware Removing Software
Obtain Removing Software
To take away CryptON Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of CryptON Ransomware.
Learn how to remove CryptON Ransomware manually
It isn’t really helpful to take away CryptON Ransomware manually, for safer answer use Removing Tools as an alternative.
CryptON Ransomware information:
Crypton.exe FileSpy.exe invoice-0071350.js svchost.exe
CryptON Ransomware registry keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun”crypton” = “%AppDatapercentCrypton.exe” HKEY_CURRENT_USERSoftwareCrypton”mail” = “.exe”
How one can decrypt and restore .YOUR_LAST_CHANCE, _x3m or _locked information
Use automated decryptors
Obtain CryptON Decryptor
Use following software from Emsisoft referred to as Decryptor for CryptON, that may decrypt information with following extensions:
.id-_locked, .id-_locked_by_krec, .id-_locked_by_perfect, .id-_x3m, .id-_r9oj, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_
Obtain it right here:
Obtain Emsisoft CryptON Decryptor
Download Cry9 Decryptor
Use following device from Emsisoft referred to as Decryptor for Cry9, that can decrypt information with following extensions:
.-juccy[a]protonmail.ch, .id-, .id-_[[email protected]].xj5v2, .id-_r9oj, .id-_x3m, .id-_[[email protected]]_[[email protected]].x3m, “.”, .-sofia_lobster[a]protonmail.ch and ._[wqfhdgpdelcgww4g.onion.to].r2vy6
Obtain it here:
Obtain Emsisoft Cry9 Decryptor
Obtain Cry128 Decryptor
Use following software from Emsisoft referred to as Decryptor for Cry128, that may decrypt information with following extensions:
.fgb45ft3pqamyji7.onion.to._, .id__gebdp3k7bolalnd4.onion._, .id__2irbar3mjvbap6gt.onion.to._ and .id-_[qg6m5wo7h3id55ym.onion.to].63vc4
Download it here:
Download Emsisoft Cry128 Decryptor
There isn’t a function to pay the ransom because there isn’t a guarantee you’ll obtain the key, however you’ll put your financial institution credentials in danger.
In case you are contaminated with CryptON Ransomware and removed it out of your pc you’ll be able to try to decrypt your information. Antivirus distributors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you are able to do the following:
Use Stellar Knowledge Restoration Professional to revive .YOUR_LAST_CHANCE, _x3m or _locked information
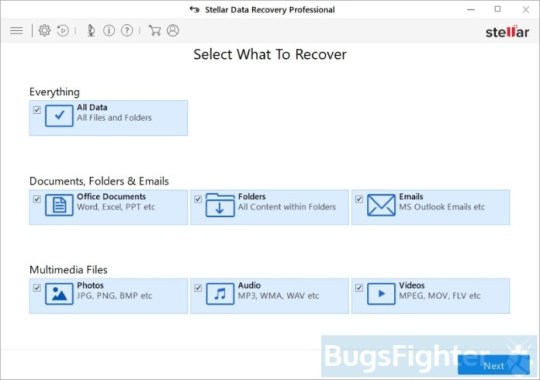
Download Stellar Knowledge Recovery Skilled.
Click Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview found information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Recovery Skilled
Utilizing Home windows Previous Versions choice:
Right-click on infected file and choose Properties.
Select Previous Versions tab.
Select specific model of the file and click Copy.
To restore the selected file and substitute the prevailing one, click on the Restore button.
In case there isn’t a gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Obtain Shadow Explorer program.
Run it and you will notice display itemizing of all of the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Right-click on a folder identify and select Export.
In case there are not any other dates within the listing, choose various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that incorporates encrypted information.
Right-click on the encrypted file and choose Earlier Versions.
Choose the model of the file you wish to restore and click on the Restore button.
Learn how to shield pc from viruses like CryptON Ransomware in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may aid you with lively anti-ransomware protection, as further defend to your present protection. It won’t conflict with greater safety purposes. In case you are looking complete internet security answer contemplate upgrading to full version of BitDefender Internet Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information utilizing easy online backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating bodily drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Home windows 10 and eight/eight.1 users can discover pre-installed OneDrive backup answer from Microsoft. It’s truly the most effective backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it right here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Using spam filters and creating anti-spam guidelines is sweet apply. One of many world leaders in anti-spam safety is SpamFighter. It works with numerous desktop purposes, and supplies very excessive degree of anti-spam protection.
Download SPAMFighter 5/5 (3)
The post How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files appeared first on Spouting-Tech.
#decrypt _crypt files#decrypt _locked files#decrypt _r9oj files#decrypt .damoclis files#decrypt .losers files#decrypt .nemesis files#decrypt [email protected] files#decrypt .x3m files#decrypt .your_last_chance files#Ransomware#remove cry128 ransomware#remove cry9 ransomware#remove crypton ransomware#remove losers ransomware#remove nemesis ransomware#remove x3m ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files
What’s CryptON Ransomware
Word: Some versions of CryptON Ransomware are decryptable. You’ll be able to attempt free decryptors provided under and attempt to restore encrypted information. In any other case, hold your information till effective decryptor can be launched.
Notice: In July 2019 new variation of Nemesis Ransomware was discovered. It appends .YOUR_LAST_CHANCE extension to encrypted information. Ransom observe file is known as: _RESTORE FILES_.txt. Victims are provided to contact malefactors by way of e-mails: [email protected], [email protected] or [email protected].
CryptON Ransomware or Nemesis Ransomware or X3M Ransomware is among the most dangerous and wide-spread ransomware households. At present, there are multiple successors of initial virus and a number of other deviations constructed on one other platforms. Cry9, Cry36 and Cry128 Ransomware came from this collection. Virus makes use of mixture of AES-256, RSA-2048 and SHA-256 encryption algorithms. Newest discovered version is definitely referred to as CryptON Ransomware and makes use of [email protected] extension for affected information. Other used suffixes are:
.YOUR_LAST_CHANCE, _x3m, _locked, _crypt, .encrptd, _locked_by_krec, _locked_by_perfect, _r9oj, .nemesis, .v8dp, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_, .-juccy[a]protonmail.ch, _[[email protected]].xj5v2, .-sofia_lobster[a]protonmail.ch, _[wqfhdgpdelcgww4g.onion.to].r2vy6, _[qg6m5wo7h3id55ym.onion.to].63vc4, _2irbar3mjvbap6gt.onion.to._, _gebdp3k7bolalnd4.onion._, .fgb45ft3pqamyji7.onion.to._, .losers, .damoclis
Ransomware calls for from zero.2 to 1 BitCoin for decryption. It isn’t really helpful to pay the ransom as there are not any guarantee malefactors will send decryption key. Depending on version, after encryption CryptON Ransomware creates totally different text information with directions to pay the ransom. Current model makes use of HOWTODECRYPTFILES.html and it incorporates following info:
CryptON Ransomware
All information are encrypted! CryptON Ransomware To decrypt the information, you want to purchase special software program «CryptON decryptor» Restore the info, comply with the instructions! You possibly can study extra / request e-mail: [email protected] You’ll be able to study extra/questions within the chat: https://cryptxf3zamy5kfz.tor2web.link (not need Tor) https://cryptxf3zamy5kfz.onion.plus (not need Tor) http://cryptxf3zamy5kfz.onion/ (need Tor) You possibly can study extra drawback out bitmessage: https://bitmsg.me/ BM-2cWzhoNFbjQ3X8pULiWSyKhc6dedQ54zQ1 – If the resource is unavailable for a long time to put in and use the terms of reference of the browser: 1. + Begin the Internet browser 2. + Sort or copy the tackle https://www.torproject.org/download/download-easy.html within the tackle bar of your browser and press key ENTER three. + On the website you may be prompted to obtain the Tor browser, download and install it. To work. four. + Connection, click on “join” (utilizing English model) 5. + After connecting, open a traditional window Tor-browser 6. + Sort or copy the handle http://cryptxf3zamy5kfz.onion/ within the handle bar of Tor-browser and press key ENTER 7. + Watch for the download website // + When you’ve got any problems with set up or utilization, please go to the video: https://www.youtube.com/watch?v=gOgh3ABju6Q Your personal identification ID:-
YOUR_LAST_CHANCE Ransomware
*** ALL YOUR WORK AND PERSONAL FILES HAVE BEEN ENCRYPTED ***
To decrypt your information that you must purchase the particular software program ñ “Nemesis decryptor” You’ll find out the small print/buy decryptor + key/ask questions by e-mail: [email protected], [email protected] OR [email protected] IMPORTANT! DON’T TRY TO RESTORE YOU FILES BY YOUR SELF, YOU CAN DAMAGE FILES! If inside 24 hours you did not receive an answer by e mail, make sure to write to Jabber: [email protected] Your private ID: –
Different potential filenames for ransom notes information are: COMO_ABRIR_ARQUIVOS.txt, ###DECRYPT-MY-FILES###.txt, HOW_OPEN_FILES.html, DECRYPT MY FILE.txt. On this article we collected, consolidated and structured obtainable details about this malware and potential ways of decryption. Use directions on this web page to take away CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked information in Home windows 10, Windows 8 or Home windows 7.
How CryptON Ransomware infected your PC
Could be distributed by hacking by means of an unprotected RDP configuration, using e-mail spam and malicious attachments, fraudulent downloads, exploits, net injections, pretend updates, repackaged and infected installers. After infection and encryption, Scarab deletes shadow copies of information, system restore points, disables the Windows Boot Repair, using sure command immediate commands. Virus assigns certain ID with the victims, that is used to call these information and supposedly to ship decryption key. In an effort to forestall an infection with such a threats in future we advocate you to make use of SpyHunter and BitDefender Anti-Ransomware.
Download CryptON Ransomware Removing Software
Obtain Removing Software
To take away CryptON Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of CryptON Ransomware.
Learn how to remove CryptON Ransomware manually
It isn’t really helpful to take away CryptON Ransomware manually, for safer answer use Removing Tools as an alternative.
CryptON Ransomware information:
Crypton.exe FileSpy.exe invoice-0071350.js svchost.exe
CryptON Ransomware registry keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun”crypton” = “%AppDatapercentCrypton.exe” HKEY_CURRENT_USERSoftwareCrypton”mail” = “.exe”
How one can decrypt and restore .YOUR_LAST_CHANCE, _x3m or _locked information
Use automated decryptors
Obtain CryptON Decryptor
Use following software from Emsisoft referred to as Decryptor for CryptON, that may decrypt information with following extensions:
.id-_locked, .id-_locked_by_krec, .id-_locked_by_perfect, .id-_x3m, .id-_r9oj, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_
Obtain it right here:
Obtain Emsisoft CryptON Decryptor
Download Cry9 Decryptor
Use following device from Emsisoft referred to as Decryptor for Cry9, that can decrypt information with following extensions:
.-juccy[a]protonmail.ch, .id-, .id-_[[email protected]].xj5v2, .id-_r9oj, .id-_x3m, .id-_[[email protected]]_[[email protected]].x3m, “.”, .-sofia_lobster[a]protonmail.ch and ._[wqfhdgpdelcgww4g.onion.to].r2vy6
Obtain it here:
Obtain Emsisoft Cry9 Decryptor
Obtain Cry128 Decryptor
Use following software from Emsisoft referred to as Decryptor for Cry128, that may decrypt information with following extensions:
.fgb45ft3pqamyji7.onion.to._, .id__gebdp3k7bolalnd4.onion._, .id__2irbar3mjvbap6gt.onion.to._ and .id-_[qg6m5wo7h3id55ym.onion.to].63vc4
Download it here:
Download Emsisoft Cry128 Decryptor
There isn’t a function to pay the ransom because there isn’t a guarantee you’ll obtain the key, however you’ll put your financial institution credentials in danger.
In case you are contaminated with CryptON Ransomware and removed it out of your pc you’ll be able to try to decrypt your information. Antivirus distributors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you are able to do the following:
Use Stellar Knowledge Restoration Professional to revive .YOUR_LAST_CHANCE, _x3m or _locked information
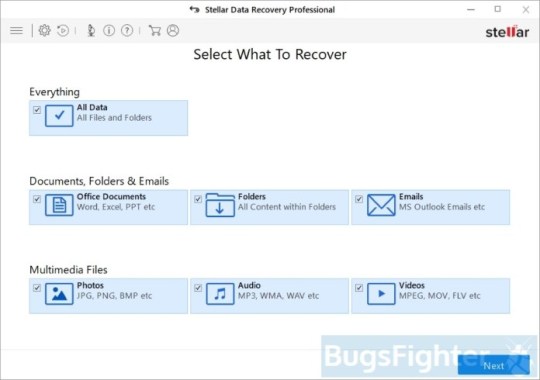
Download Stellar Knowledge Recovery Skilled.
Click Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview found information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Recovery Skilled
Utilizing Home windows Previous Versions choice:
Right-click on infected file and choose Properties.
Select Previous Versions tab.
Select specific model of the file and click Copy.
To restore the selected file and substitute the prevailing one, click on the Restore button.
In case there isn’t a gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Obtain Shadow Explorer program.
Run it and you will notice display itemizing of all of the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Right-click on a folder identify and select Export.
In case there are not any other dates within the listing, choose various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that incorporates encrypted information.
Right-click on the encrypted file and choose Earlier Versions.
Choose the model of the file you wish to restore and click on the Restore button.
Learn how to shield pc from viruses like CryptON Ransomware in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
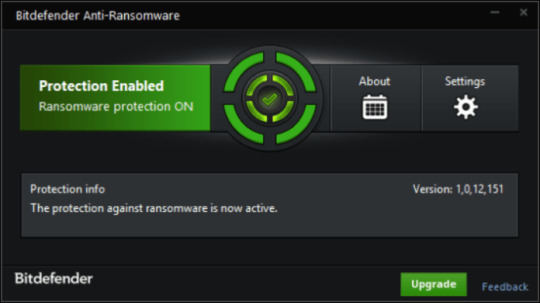
Well-known antivirus vendor BitDefender released free device, that may aid you with lively anti-ransomware protection, as further defend to your present protection. It won’t conflict with greater safety purposes. In case you are looking complete internet security answer contemplate upgrading to full version of BitDefender Internet Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information utilizing easy online backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating bodily drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Home windows 10 and eight/eight.1 users can discover pre-installed OneDrive backup answer from Microsoft. It’s truly the most effective backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it right here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Using spam filters and creating anti-spam guidelines is sweet apply. One of many world leaders in anti-spam safety is SpamFighter. It works with numerous desktop purposes, and supplies very excessive degree of anti-spam protection.
Download SPAMFighter 5/5 (3)
The post How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files appeared first on Spouting-Tech.
#decrypt _crypt files#decrypt _locked files#decrypt _r9oj files#decrypt .damoclis files#decrypt .losers files#decrypt .nemesis files#decrypt [email protected] files#decrypt .x3m files#decrypt .your_last_chance files#Ransomware#remove cry128 ransomware#remove cry9 ransomware#remove crypton ransomware#remove losers ransomware#remove nemesis ransomware#remove x3m ransomware#tech#Tutorials#Viruses
0 notes