#cybercriminal attacks
Explore tagged Tumblr posts
Text
Hospitals Are the Target in a New Kind of Cyberwar
New Post has been published on https://thedigitalinsider.com/hospitals-are-the-target-in-a-new-kind-of-cyberwar/
Hospitals Are the Target in a New Kind of Cyberwar


Since the earliest days of cybercrime, healthcare data has been a prime target. Until recently, most cyberattacks on hospitals followed a familiar pattern: ransomware groups would encrypt patient records and demand payment. The motive was clear – and it was all about the money.
But cybersecurity experts are now warning of a shift. A growing number of attacks on health sector systems appear to be driven not by profit, but by politics. These incidents, often traced back to nation state-backed groups, aim to disrupt hospital operations, steal sensitive medical data, and undermine public trust. The United Nations has called cyberattacks on healthcare “a direct and systemic risk to global public health and security.”
This evolution comes at a vulnerable time, as trust in health institutions remains fragile. Cyberattacks deepen that mistrust, strain critical infrastructure, and blur the line between criminal enterprise and geopolitical strategy. As someone working at the intersection of healthcare security and intelligence sharing, I believe this is no longer just a criminal problem – it’s a threat to national security.
The challenge of attribution
As the motives behind cyberattacks on the health sector shift, so too does the complexity of understanding who is behind them – and why.
Unlike the straightforward financial motives of traditional ransomware groups, state-backed campaigns are often hidden behind layers of sophisticated proxies, hacktivist fronts, or loosely affiliated cybercriminals. What may initially appear to be a routine ransomware incident could, upon deeper investigation, reveal signs of a coordinated strategy: targeting critical healthcare infrastructure, maximizing operational disruption, and carefully avoiding attribution to any nation-state.
This pattern has already been seen in high-profile cases. During the COVID-19 pandemic, several European healthcare institutions suffered cyberattacks that officials later suspected were linked to foreign intelligence operations. Although the attacks initially resembled criminal ransomware campaigns, deeper analysis pointed to broader aims – such as stealing vaccine research, disrupting care during a public health emergency, or sowing mistrust in the healthcare system.
This deliberate ambiguity serves the attackers well. By masking strategic sabotage as criminal activity, they sidestep direct political consequences while still inflicting serious harm on institutions providing patient care. For defenders, this blurred line between crime and geopolitics complicates the response at every level: technical, operational, and diplomatic.
In the health sector, patient safety is at immediate risk during a cyber incident, and there is little time or capacity for in-depth forensic analysis. Without a clear understanding of the nature and purpose of an attack, hospitals and healthcare providers may misjudge the threat, miss broader patterns, and fail to coordinate an appropriate defensive strategy.
Importance of intelligence sharing
The key to building an effective defense is collective action, which depends on the free exchange of information. Critical infrastructure organizations are coming together to form Information Sharing and Analysis Centers, or ISACs. Health-ISAC brings together more than 14,000 people through anon-profit industry association designed to facilitate trusted exchanges of cybersecurity threat intelligence, enabling faster, more coordinated responses to emerging risks. Health-ISAC connects hospitals, pharmaceutical companies, insurers, and other stakeholders, creating an ecosystem where knowledge flows more freely and early warnings can be amplified across the global health community.
By sharing indicators of compromise, attack techniques, suspicious behaviors, and lessons learned, organizations can turn isolated observations into industry-wide intelligence. A malware signature spotted in a single hospital today could be the early warning that prevents a wave of attacks across the entire globe tomorrow. In this way, intelligence sharing transforms defense from a series of isolated struggles into a coordinated, proactive effort.
However, building and sustaining this kind of collaboration is not without its challenges. Effective sharing depends on trust: trust that sensitive information will be handled responsibly, and trust that participants are committed to mutual defense. Health sector organizations must be willing to report incidents transparently. Fostering this culture of openness remains one of the sector’s greatest challenges, but also one of its most powerful opportunities to strengthen the industry against increasingly sophisticated threats.
Building resilience
While robust cybersecurity controls remain essential, the reality is that preventing every attack is impossible. Therefore, health sector institutions must invest in resilience: the ability to maintain or quickly restore critical services under attack.
That starts with preparation. Organizations should develop and regularly rehearse detailed incident response plans tailored to their specific workflows, facilities, and patient care requirements. These exercises help staff know what to do when systems go down and ensure that decision-making isn’t delayed by confusion or uncertainty during a crisis.
Segmented network architectures are another critical defense. By isolating systems – such as separating medical devices from administrative tools or confining lab networks to their own segment – organizations can prevent malware from moving laterally and causing widespread disruption. This kind of compartmentalization limits damage and buys valuable time for response teams.
Equally important is the strength and accessibility of backup and recovery systems. Backups should be stored securely, tested regularly, and maintained in offline or immutable formats to prevent them from being manipulatedduring an attack. The faster an organization can restore patient records, scheduling tools, and communication systems, the sooner it can return to safe and effective care.
Final thoughts
Too often, cyberattacks reveal that resilience was treated as an afterthought. But in the health sector – in which lives are on the line – it must be a foundational priority. Planning, practice, and coordination are no longer optional. They are the frontline defenses in a cyberwar hospitals can no longer afford to ignore.
What’s needed now is a shift in mindset. Health sectorleaders must view cybersecurity not as an IT issue, but as a core part of patient safety and institutional trust. That means allocating resources, engaging staff at every level, and collaborating beyond organizational boundaries.
No single hospital can stand alone against the forces reshaping the threat landscape. But together – through shared intelligence, coordinated response, and a renewed focus on resilience – the health sector can push back against this rising tide and protect the critical systems millions rely on every day.
#000#Accessibility#Analysis#attackers#backup#backup and recovery#backups#blur#Building#challenge#Collaboration#Collective#communication#Community#Companies#complexity#compromise#covid#crime#critical infrastructure#cyber#Cyberattacks#cybercrime#cybercriminals#cybersecurity#cybersecurity experts#data#defenders#defense#defenses
1 note
·
View note
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
Fortinet: Cybercriminals Exploit Vulnerabilities 43% Faster, Urgent Action
Fortinet’s 2H 2023 Global Threat Landscape Report reveals that cybercriminals are exploiting industry vulnerabilities 43% faster than in the first half of 2023. Key findings highlight the need for better cyber hygiene, faster patch management, and adherence to vulnerability disclosure best practices. Notably, 44% of ransomware and wiper attacks targeted the industrial sector, and botnets showed…

View On WordPress
0 notes
Text
Beware Of These Techniques That Cybercriminals Use To Steal Cryptocurrency
While the rise of cryptocurrency has brought about revolutionary changes in the financial landscape, it has also opened doors to new forms of cybercrime. The decentralized and anonymous nature of cryptocurrencies has made them attractive targets for cybercriminals.
Understanding the techniques that cybercriminals use to steal these digital assets is crucial for protecting oneself in the evolving landscape of cybersecurity. It is important that you stay vigilant, and informed, and prioritize security to protect yourself against these evolving threats.
Check out this list of techniques that cybercriminals use to steal cryptocurrency.
1. Phishing Attacks

One of the most common techniques used by cybercriminals is phishing. They employ misleading emails, websites, or messages that look similar to legitimate platforms or communication from trusted entities. Unsuspecting users are tricked into revealing their private keys, passwords, or wallet information which allows the criminals to gain access to their cryptocurrency holdings.
To Read More Click here...
#business#business blog#new updates#trending topic#cryptocurrency#Phishing Attacks#Cybercriminals#new techniques#revolutionary#evolving threats
0 notes
Text
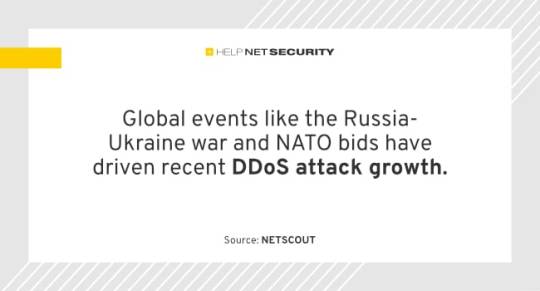
Global events fuel DDoS attack campaigns - Help Net Security
Cybercriminals launched approximately 7.9 million DDoS attacks in 1H 2023, representing a 31% year-over-year increase, according to NETSCOUT. Global events like the Russia-Ukraine war and NATO bids have driven recent DDoS attack growth. Finland was targeted by pro-Russian hacktivists in 2022 during its bid to join NATO. Turkey and Hungary were targeted with DDoS attacks for opposing Finland’s…
View On WordPress
0 notes
Text
The child sextortion group 764 and the global collective of loosely associated groups known as “The Com” are using tools and techniques normally used for financially motivated cybercrime tactics — such as SIM swapping, IP grabbing and social engineering — to commit violent crimes, according to exclusive law enforcement and intelligence reports reviewed by CyberScoop. The reports offer insight into the underbelly of the global network, showing how they are using traditional cybercriminal tools to identify, target, groom, extort, and cause physical and psychological harm to victims as young as 10. They were shared with police nationwide and in some cases, with foreign-allied governments. [...] The group “appears to be situated at the nexus of communities of users who share gore material, [Racially or Ethnically Motivated Violent Extremist-White Supremacist] adherents such as M.K.U. and child exploitation actors like 764.” M.K.U., it says, is a neo-Nazi group with a presence in Russia and Ukraine. [...] The groups use methods to trick children into sending sexually explicit photos of themselves, threaten to make the photos public unless they harm themselves, and kill or harm animals, among other crimes. The group’s members have coerced children into attempting suicide, harming themselves, siblings and animals. (x)
///
Wired reported this week that a 19-year-old working for Elon Musk‘s so-called Department of Government Efficiency (DOGE) was given access to sensitive US government systems even though his past association with cybercrime communities should have precluded him from gaining the necessary security clearances to do so. As today’s story explores, the DOGE teen is a former denizen of ‘The Com,’ an archipelago of Discord and Telegram chat channels that function as a kind of distributed cybercriminal social network for facilitating instant collaboration. [...] Internet routing records show that Coristine runs an Internet service provider called Packetware (AS400495). Also known as “DiamondCDN,” Packetware currently hosts tesla[.]sexy and diamondcdn[.]com, among other domains. DiamondCDN was advertised and claimed by someone who used the nickname “Rivage” on several Com-based Discord channels over the years. A review of chat logs from some of those channels show other members frequently referred to Rivage as “Edward.” From late 2020 to late 2024, Rivage’s conversations would show up in multiple Com chat servers that are closely monitored by security companies. In November 2022, Rivage could be seen requesting recommendations for a reliable and powerful DDoS-for-hire service. Rivage made that request in the cybercrime channel “Dstat,” a core Com hub where users could buy and sell attack services. Dstat’s website dstat[.]cc was seized in 2024 as part of “Operation PowerOFF,” an international law enforcement action against DDoS services. (x)
DOGE teen is a pedophile cybercriminal involved in a neonazi CSA-producing cybergang. and he has access to your SSN.
680 notes
·
View notes
Text

He should be arrested for violating our privacy. He was not vetted by congress and has no security clearance.
Contact your state’s attorney general and request help.
Can we ask the ACLU to file a class action suit? Who’s with me?
“Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!” ~ A N P S
225 notes
·
View notes
Text
alt text under cut
Alt National Park Service·
Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!
64 notes
·
View notes
Text

Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!
42 notes
·
View notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes
Text
My leverage redemption s3 wishlist:
Flashback episode about a job the team pulled between the old and the new series; so eliot-parker-hardison only. Alternatively i accept an episode in which sophie is incapacited for whatever reason and parker steps up as the one calling the shots (bonus points if it's actually parker and eliot making the plans together, extra bonus points if they somehow pull hardison into it too)
An episode when they team up with another leverage international team; but like properly. Not just 'these background randos are actually leverage-people and on their side'
Eliot blatantly being sophie's attack/guard dog
Sterling
A completely new kind of bonkers narrative framing in one single episode. Can coincide with the first item
Maggie cameo, preferably via sophie inviting her because they are Very Good Friends
During a job, someone recognises Breanna('s name) as a known and famed cybercriminal
Robot bodies mention
12 notes
·
View notes
Text
A study of over 19 billion exposed passwords has revealed that only 6 percent of the leaked passwords were unique. The vast majority, 94 percent, were reused or duplicated, making them prime targets for cybercriminals.
Common keyboard patterns and easily guessed strings remain prevalent. The "123456" sequence still dominates, appearing in 338 million passwords, according to the Cybernews study.
Why It Matters
The scale of password breaches and the continued reliance on weak passwords have heightened concerns about "credential stuffing," a tactic in which attackers use automated tools to test stolen credentials across multiple platforms.
Even breach success rates between 0.2 percent and 2 percent can still yield thousands of compromised accounts, according to Cybernews.
The most common password length is eight to 10 characters, and a significant portion contains only lowercase letters and digits, making passwords vulnerable to brute-force attacks.
Compared to just 1 percent in 2022, 19 percent of passwords now mix uppercase, lowercase, numbers, and symbols.
What To Know
The dataset analyzed included 19,030,305,929 passwords sourced from 200 cybersecurity incidents. These came from leaked databases, stealer logs, and combolists.
Paul Walsh, CEO of MetaCert, has emphasized another growing risk vector: phishing attacks targeting phones. He has urged cybersecurity companies to tackle SMS phishing with the same intensity as email security to help mitigate password leaks and breaches.
In an article published on Monday, Walsh told Forbes that MetaCert's latest national SMS phishing test, carried out in March and including carriers such as AT&T, Verizon, T-Mobile and Boost Mobile, was concerning.
"Every phishing message was still delivered," Walsh said. "None were blocked, flagged, or rewritten."
Walsh has written an open letter to the cybersecurity industry asking why the SMS phishing problem wasn't solved long ago.
What Are the Most Common Passwords?
Predictable patterns continue to dominate password choices. "123456" alone appears in 338 million of the passwords in the Cybernews study, while "password" and "admin" were used over 100 million times combined.
Users also often rely on names, with "Ana" appearing in 178.8 million instances. Positive words like "love," "freedom," and pop culture references such as "Batman" are also prevalent. Profanity, surprisingly, is common as well; "ass" alone shows up in 165 million passwords.
Some of the most frequently used pop culture terms in passwords included "Mario" (9.6 million), "Joker" (3.1 million), "Batman" (3.9 million), and "Thor" (6.2 million).
Additionally, seasonal words, food items, and cities frequently feature in password choices, leaving accounts vulnerable to attackers who exploit such predictability. Over 10 million of the passwords featured "apple," 4.9 million "rice," and 3.6 million "orange," while 3.3 million opted for "pizza."
The most popular city for passwords was "Rome" (13 million), while "summer" (3.8 million) was the most popular season.
What People Are Saying
Neringa Macijauskaitė, information security researcher at Cybernews: "We're facing a widespread epidemic of weak password reuse. If you reuse passwords across multiple platforms, a breach in one system can compromise the security of other accounts."
MetaCert CEO Paul Walsh told Forbes: "Criminals have already moved in full force, and the industry is failing to respond."
"The cybersecurity industry has no shortage of experts in email security, endpoint protection, or network defense, but when it comes to SMS infrastructure and security, there is a distinct lack of deep expertise."
What Happens Next
Researchers have urged individuals and organizations to boost password security by using password managers, enforcing minimum length and complexity standards, and enabling multi-factor authentication. Organizations are advised to regularly audit access controls, monitor for credential leaks, and adopt real-time detection solutions.
10 notes
·
View notes
Text

SILLY GUAYYYYYYYYYYYYYYYYYYYY <3 closeups, human form, and ✨document✨under cut!




i have been putting him off for way too long tbh Transcript of doc:
Z-256 - Codename: "The Technician", real name "Hade Parabellum", is to be shot on sight by the EXR-P teams and any personnel without hesitation. Z-256 is a high-level threat in Urbanshade; caution is required if encountered. Given his partnership with Z-779, extreme caution should be taken when in a room equipped with turrets. It has been reported on multiple occasions that 256 is armed with a long range taser and a .45 ACP revolver. Z-256 was brought in as a LR-P in 2014, after he was found guilty of a worldwide DDOS attack, causing companies big and small to lose over $7.1 trillion USD collectively, as well as mining cryptocurrency for use in illicit trades. He had a natural knack for computers, and had a bachelor's in computer sciences. Given this, Urbanshade swept him away to be held in the Hadal division, and in his wake, created a cover story that he took his own life in his cell. From late 2016 onward, 256 was our lead programmer before the breach, despite his history as a cybercriminal. It was later realized his technological prowess could be put to better use outside Urbanshade's facilities, so the DNA of Penaeidae was spliced into his so he could work under the pressure of the Hadal zone comfortably. However, the changes to his appearance from experimentation left him appearing extremely nonhuman, earning him the classification of Z-256. After several months of planning, Z-256 momentarily formed an alliance with Z-13 and Z-763 to escape, additionally causing a breach in many of the other containment cells holding experiments at the Blacksite. He reportedly handled opening electronic locks with his sentient computer Z-779, who enthusiastically complied and assisted. Afterwards, as revenge, he proceeded to destroy several generators that powered the facility, as well as rip up several cables connected to the main power of the External Repellent System, causing several Vultus Linunaria to gather at the newly safened area around the cannon. At the Blacksite: EXR-P teams should report sightings of 2-256 immediately to HQ. Most commonly reported in proximity to Z-779. (Personnel Note: Look up you dimwits. Z-256 often resides in the control pits of rooms with artillery taken over by Z-779, outside of the action. He will try to turn the machine guns back on after they are disabled on the ground; shoot him so he does not succeed.) Under no circumstances can Z-256 be allowed to leave the Blacksite alive. Abandon previous objectives and, as Mr. Shade himself stated, 'Shred their mags until their trigger-finger bleeds."
#pressure oc#pressure roblox#roblox pressure#hade's eye candy#hade's special babies#any references to a Z-763 is in regard to my friend's pressure oc!!!
14 notes
·
View notes
Text
Every year has its own mix of digital security debacles, from the absurd to the sinister, but 2024 was particularly marked by hacking sprees in which cybercriminals and state-backed espionage groups repeatedly exploited the same weakness or type of target to fuel their frenzy. For attackers, the approach is ruthlessly efficient, but for compromised institutions—and the individuals they serve—the malicious rampages had very real consequences for people's privacy, safety, and security.
As political turmoil and social unrest intensify around the world, 2025 will be a complicated—and potentially explosive—year in cyberspace. But first, here's WIRED's look back on this year's worst breaches, leaks, state-sponsored hacking campaigns, ransomware attacks, and digital extortion cases. Stay alert, and stay safe out there.
China's Salt Typhoon Telecom Breaches
Espionage operations are a fact of life, and relentless Chinese campaigns have been a constant in cyberspace for years now. But the China-linked espionage group Salt Typhoon carried out a particularly noteworthy operation this year, infiltrating a slew of US telecoms including Verizon and AT&T (plus others around the world) for months. And US officials told reporters earlier this month that many victim companies are still actively attempting to remove the hackers from their networks.
The attackers surveilled a small group of people—less than 150 by current count—but they include individuals who were already subject to US wiretap orders as well as state department officials and members of both the Trump and Harris presidential campaigns. Additionally, texts and calls from other people who interacted with the Salt Typhoon targets were inherently also caught up in the espionage scheme.
Snowflake Customer Breaches
Throughout the summer, attackers were on a tear, breaching prominent companies and organizations that were all customers of the cloud data storage company Snowflake. The spree barely qualifies as hacking, since cybercriminals were simply using stolen passwords to log in to Snowflake accounts that didn't have two-factor authentication turned on. The end result, though, was an extraordinary amount of data stolen from victims including Ticketmaster, Santander Bank, and Neiman Marcus. Another prominent victim, the telecom giant AT&T, said in July that “nearly all” records relating to its customers' calls and texts from a seven-month stretch in 2022 were stolen in a Snowflake-related intrusion. The security firm Mandiant, which is owned by Google, said in June that the rampage impacted roughly 165 victims.
In July, Snowflake added a feature so account administrators could make two-factor authentication mandatory for all of their users. In November, suspect Alexander “Connor” Moucka was arrested by Canadian law enforcement for allegedly leading the hacking spree. He was indicted by the US Department of Justice for the Snowflake tear and faces extradition to the US. John Erin Binns, who was arrested in Turkey for an indictment related to a 2021 breach of the telecom T-Mobile, was also indicted on charges related to the Snowflake customer breaches.
Change Healthcare Ransomware Attack
At the end of February, the medical billing and insurance processing company Change Healthcare was hit with a ransomware attack that caused disruptions at hospitals, doctor's offices, pharmacies, and other health care facilities around the US. The attack is one of the all-time largest breaches of medical data, impacting more than 100 million people. The company, which is owned by UnitedHealth, is a dominant medical billing processor in the US. It said days after the attack started that it believed ALPHV/BlackCat, a notorious Russian-speaking ransomware gang, was behind the assault.
Personal data stolen in the attack included patient phone numbers, addresses, banking and other financial information, and health records including diagnoses, prescriptions, and treatment details. The company paid a $22 million ransom to ALPHV/BlackCat at the beginning of March in an attempt to contain the situation. The payment seemingly emboldened attackers to hit health care targets at an even greater rate than usual. With ongoing, rolling notifications to more than 100 million victims—with more still being discovered—lawsuits and other blowback has been mounting. This month, for example, the state of Nebraska sued Change Healthcare, alleging that “failures to implement basic security protections” made the attack much worse than it should have been.
Russia's Midnight Blizzard Hit Microsoft
Microsoft said in January that it had been breached by Russia's “Midnight Blizzard” hackers in an incident that compromised company executives' email accounts. The group is tied to the Kremlin's SVR foreign intelligence agency and is specifically linked to SVR's APT 29, also known as Cozy Bear. After an initial intrusion in November 2023, the attackers targeted and compromised historic Microsoft system test accounts that then allowed them to access what the company said were “a very small percentage of Microsoft corporate email accounts, including members of our senior leadership team and employees in our cybersecurity, legal, and other functions.” From there, the group exfiltrated “some emails and attached documents.” Microsoft said that the attackers seemed to be looking for information about what the company knew about them—in other words, Midnight Blizzard doing reconnaissance on Microsoft's research into the group. Hewlett-Packard Enterprise (HPE) also said in January that it had suffered a corporate email breach attributed to Midnight Blizzard.
National Public Data
The background check company National Public Data suffered a breach in December 2023, and data from the incident started showing up for sale on cybercriminal forums in April 2024. Different configurations of the data cropped up again and again over the summer, culminating in public confirmation of the breach by the company in August. The stolen data included names, Social Security numbers, phone numbers, addresses, and dates of birth. Since National Public Data didn't confirm the breach until August, speculation about the situation grew for months and included theories that the data included tens or even hundreds of millions of Social Security numbers. Though the breach was significant, the true number of impacted individuals seems to be, mercifully, much lower. The company reported in a filing to officials in Maine that the breach affected 1.3 million people. In October, National Public Data's parent company, Jerico Pictures, filed for Chapter 11 bankruptcy reorganization in the Southern District of Florida, citing state and federal investigations into the breach as well as a number of lawsuits that the company is facing over the incident.
Honorable Mention: North Korean Cryptocurrency Theft
A lot of people steal a lot of cryptocurrency every year, including North Korean cybercriminals who have a mandate to help fund the hermit kingdom. A report from the cryptocurrency tracing firm Chainalysis released this month, though, underscores just how aggressive Pyongyang-backed hackers have become. The researchers found that in 2023, hackers affiliated with North Korea stole more than $660 million across 20 attacks. This year, they stole roughly $1.34 billion across 47 incidents. The 2024 figures represent 20 percent of total incidents Chainalysis tracked for the year and a whopping 61 percent of the total funds stolen by all actors.
The sheer domination is impressive, but the researchers emphasize the seriousness of the crimes. “US and international officials have assessed that Pyongyang uses the crypto it steals to finance its weapons of mass destruction and ballistic missiles programs, endangering international security,” Chainalysis wrote.
10 notes
·
View notes
Text
Unnecessarily compiling sensitive information can be as damaging as actively trying to steal it. For example, the Cybernews research team discovered a plethora of supermassive datasets, housing billions upon billions of login credentials. From social media and corporate platforms to VPNs and developer portals, no stone was left unturned.
Our team has been closely monitoring the web since the beginning of the year. So far, they’ve discovered 30 exposed datasets containing from tens of millions to over 3.5 billion records each. In total, the researchers uncovered an unimaginable 16 billion records.
None of the exposed datasets were reported previously, bar one: in late May, Wired magazine reported a security researcher discovering a “mysterious database” with 184 million records. It barely scratches the top 20 of what the team discovered. Most worryingly, researchers claim new massive datasets emerge every few weeks, signaling how prevalent infostealer malware truly is.
“This is not just a leak – it’s a blueprint for mass exploitation. With over 16 billion login records exposed, cybercriminals now have unprecedented access to personal credentials that can be used for account takeover, identity theft, and highly targeted phishing. What’s especially concerning is the structure and recency of these datasets – these aren’t just old breaches being recycled. This is fresh, weaponizable intelligence at scale,” researchers said.
The only silver lining here is that all of the datasets were exposed only briefly: long enough for researchers to uncover them, but not long enough to find who was controlling vast amounts of data. Most of the datasets were temporarily accessible through unsecured Elasticsearch or object storage instances.
What do the billions of exposed records contain?
Researchers claim that most of the data in the leaked datasets is a mix of details from stealer malware, credential stuffing sets, and repackaged leaks.
There was no way to effectively compare the data between different datasets, but it’s safe to say overlapping records are definitely present. In other words, it’s impossible to tell how many people or accounts were actually exposed.
However, the information that the team managed to gather revealed that most of the information followed a clear structure: URL, followed by login details and a password. Most modern infostealers – malicious software stealing sensitive information – collect data in exactly this way.
Information in the leaked datasets opens the doors to pretty much any online service imaginable, from Apple, Facebook, and Google, to GitHub, Telegram, and various government services. It’s hard to miss something when 16 billion records are on the table.
According to the researchers, credential leaks at this scale are fuel for phishing campaigns, account takeovers, ransomware intrusions, and business email compromise (BEC) attacks.
“The inclusion of both old and recent infostealer logs – often with tokens, cookies, and metadata – makes this data particularly dangerous for organizations lacking multi-factor authentication or credential hygiene practices,” the team said.
What dataset exposed billions of credentials?
The datasets that the team uncovered differ widely. For example, the smallest, named after malicious software, had over 16 million records. Meanwhile, the largest one, most likely related to the Portuguese-speaking population, had over 3.5 billion records. On average, one dataset with exposed credentials had 550 million records.
Some of the datasets were named generically, such as “logins,” “credentials,” and similar terms, preventing the team from getting a better understanding of what’s inside. Others, however, hinted at the services they’re related to.
For example, one dataset with over 455 million records was named to indicate its origins in the Russian Federation. Another dataset, with over 60 million records, was named after Telegram, a cloud-based instant messaging platform.
“The inclusion of both old and recent infostealer logs – often with tokens, cookies, and metadata – makes this data particularly dangerous for organizations lacking multi-factor authentication or credential hygiene practices,”
While naming is not the best way to deduce where the data comes from, it seems some of the information relates to cloud services, business-oriented data, and even locked files. Some dataset names likely point to a form of malware that was used to collect the data.
It is unclear who owns the leaked data. While it could be security researchers that compile data to check and monitor data leaks, it’s virtually guaranteed that some of the leaked datasets were owned by cybercriminals. Cybercriminals love massive datasets as aggregated collections allow them to scale up various types of attacks, such as identity theft, phishing schemes, and unauthorized access.
A success rate of less than a percent can open doors to millions of individuals, who can be tricked into revealing more sensitive details, such as financial accounts. Worryingly, since it's unclear who owns the exposed datasets, there’s little impact users can do to protect themselves.
However, basic cyber hygiene is essential. Using a password manager to generate strong, unique passwords, and updating them regularly, can be the difference between a safe account and stolen details. Users should also review their systems for infostealers, to avoid losing their data to attackers.
No, Facebook, Google, and Apple passwords weren’t leaked. Or were they?
With a dataset containing 16 billion passwords, that’s equivalent to two leaked accounts for every person on the planet.
We don’t really know how many duplicate records there are, as the leak comes from multiple datasets. However, some reporting by other media outlets can be quite misleading. Some claim that Facebook, Google, and Apple credentials were leaked. While we can’t completely dismiss such claims, we feel this is somewhat inaccurate.
Bob Diachenko, a Cybernews contributor, cybersecurity researcher, and owner of SecurityDiscovery.com, is behind this recent major discovery.
16-billion-record data breach signals a shift in the underground world
According to Cybernews researcher Aras Nazarovas, this discovery might signal that criminals are abandoning previously popular methods of obtaining stolen data.
"The increased number of exposed infostealer datasets in the form of centralized, traditional databases, like the ones found be the Cybernews research team, may be a sign, that cybercriminals are actively shifting from previously popular alternatives such as Telegram groups, which were previously the go-to place for obtaining data collected by infostealer malware," Nazarovas said.
He regularly works with exposed datasets, ensuring that defenders secure them before threat actors can access them.
Here’s what Nazarovas suggests you should do to protect yourself.
"Some of the exposed datasets included information such as cookies and session tokens, which makes the mitigation of such exposure more difficult. These cookies can often be used to bypass 2FA methods, and not all services reset these cookies after changing the account password. Best bet in this case is to change your passwords, enable 2FA, if it is not yet enabled, closely monitor your accounts, and contact customer support if suspicious activity is detected."
Billions of records exposed online: recent leaks involve WeChat, Alipay
Major data leaks, with billions of exposed records, have become nearly ubiquitous. Last week, Cybernews wrote about what is likely the biggest data leak to ever hit China, billions of documents with financial data, WeChat and Alipay details, as well as other sensitive personal data.
Last summer, the largest password compilation with nearly ten billion unique passwords, RockYou2024, was leaked on a popular hacking forum. In 2021, a similar compilation with over 8 billion records was leaked online.
In early 2024, the Cybernews research team discovered what is likely still the largest data leak ever: the Mother of All Breaches (MOAB), with a mind-boggling 26 billion records.
16 billion passwords exposed: how to protect yourself
Huge datasets of passwords spill onto the dark web all the time, highlighting the need to change them regularly. This also demonstrates just how weak our passwords still are.
Last year, someone leaked the largest password compilation ever, with nearly ten billion unique passwords published online. Such leaks pose severe threats to people who are prone to reusing passwords.
Even if you think you are immune to this or other leaks, go and reset your passwords just in case.
Select strong, unique passwords that are not reused across multiple platforms
Enable multi-factor authentication (MFA) wherever possible
Closely monitor your accounts
Contact customer support in case of any suspicious activity
4 notes
·
View notes
Text
14 notes
·
View notes