#cryptocurrency website scripts
Explore tagged Tumblr posts
Text
What are the legal and regulatory aspects that startups need to consider when using Cryptocurrency Exchange script?
What is Cryptocurrency Exchange Script?
A Cryptocurrency Exchange Script is a pre-built exchange software solution that paves the way for startups to establish their own cryptocurrency exchange, akin to the world's leading trading platforms. This script is designed with all the advanced features and security components necessary for the seamless operation of an exchange platform.
Cryptocurrency Exchange Script Development:
With this script in hand, you can create a feature-rich cryptocurrency trading website in just 7 to 10 days, providing a significant advantage for your business. It offers support for a wide range of reputable cryptocurrencies, including Bitcoin, Cardano, Ripple, Ethereum, Bitcoin Cash, BNB, Matic, Shiba Inu, Dogecoin, and many others.

Key Features of Cryptocurrency Exchange Script:
User Authentication:
Secure user authentication is a fundamental feature of any cryptocurrency exchange script. This encompasses user account creation, two-factor authentication, and password management.
Wallet Management:
The script empowers users to manage their digital currency wallets, enabling them to view their balances and conduct cryptocurrency deposits and withdrawals.
Trading Engine:
The heart of the cryptocurrency exchange, the trading engine, facilitates the buying and selling of digital currencies. It includes advanced features such as order books, trading charts, and order matching algorithms.
Payment Gateway Integration:
Seamlessly integrate payment gateways, allowing users to deposit funds into their accounts and make withdrawals. Popular payment methods encompass credit cards, bank transfers, and e-wallets.
KYC/AML Procedures:
To combat fraud and illegal activities, many countries require Know Your Customer (KYC) and Anti-Money Laundering (AML) procedures. The script comes equipped with built-in procedures to meet these requirements.
Multilingual Support:
To attract users from across the globe, the cryptocurrency exchange script supports multiple languages, ensuring inclusivity.
Customer Support:
A robust customer support system is essential, including features like a help desk, live chat, and a support ticket system to assist users efficiently.
Security Features:
Cryptocurrency exchange scripts are fortified with robust security features to shield against cyberattacks, data breaches, and other security threats.
Customizability:
A quality cryptocurrency exchange script allows businesses to customize the platform to align with their unique needs, including branding, color schemes, and additional features.
These are some of the core features you can expect from a typical cryptocurrency exchange script. It's worth noting that different software solutions may offer additional or different features to meet specific business requirements.
Why Choose Hivelance for Your Cryptocurrency Exchange Script Development?
Hivelance stands as the foremost provider of cryptocurrency exchange software services, offering a competitive edge. With extensive experience in blockchain solutions, including cryptocurrency exchange script development, our team comprises experienced developers, designers, and project managers to guide you through the development process, ensuring the success of your exchange. We provide a range of benefits, including expertise, customization, security, and unwavering support, for businesses seeking to develop their cryptocurrency exchange script.
Grab Up To 73% Off on Black Friday Deals for all our services like Cryptocurrency Exchange Script Development Services. Launch your Cryptocurrency Exchange Platform easily!
#cryptocurrency exchange script#cryptocurrency exchange software#Cryptocurrency Trading Script#Bitcoin Exchange Script#Bitcoin Trading Script#Bitcoin Exchange Website Script
1 note
·
View note
Text
As digital scamming explodes in Southeast Asia, including so called “pig butchering” investment scams, the United Nations Office on Drugs and Crime (UNODC) issued a comprehensive report this week with a dire warning about the rapid growth of this criminal ecosystem. Many digital scams have traditionally relied on social engineering, or tricking victims into giving away their money willingly, rather than leaning on malware or other highly technical methods. But researchers have increasingly sounded the alarm that scammers are incorporating generative AI content and deepfakes to expand the scale and effectiveness of their operations. And the UN report offers the clearest evidence yet that these high tech tools are turning an already urgent situation into a crisis.
In addition to buying written scripts to use with potential victims or relying on templates for malicious websites, attackers have increasingly been leaning on generative AI platforms to create communication content in multiple languages and deepfake generators that can create photos or even video of nonexistent people to show victims and enhance verisimilitude. Scammers have also been expanding their use of tools that can drain a victim’s cryptocurrency wallets, have been manipulating transaction records to trick targets into sending cryptocurrency to the wrong places, and are compromising smart contracts to steal cryptocurrency. And in some cases, they’ve been purchasing Elon Musk’s Starlink satellite internet systems to help power their efforts.
“Agile criminal networks are integrating these new technologies faster than anticipated, driven by new online marketplaces and service providers which have supercharged the illicit service economy,” John Wojcik, a UNODC regional analyst, tells WIRED. “These developments have not only expanded the scope and efficiency of cyber-enabled fraud and cybercrime, but they have also lowered the barriers to entry for criminal networks that previously lacked the technical skills to exploit more sophisticated and profitable methods.”
For years, China-linked criminals have trafficked people into gigantic compounds in Southeast Asia, where they are often forced to run scams, held against their will, and beaten if they refuse instructions. Around 200,000 people, from at least 60 countries, have been trafficked to compounds largely in Myanmar, Cambodia, and Laos over the last five years. However, as WIRED reporting has shown, these operations are spreading globally—with scamming infrastructure emerging in the Middle East, Eastern Europe, Latin America, and West Africa.
Most prominently, these organized crime operations have run pig butchering scams, where they build intimate relationships with victims before introducing an “investment opportunity” and asking for money. Criminal organizations may have conned people out of around $75 billion through pig butchering scams. Aside from pig butchering, according to the UN report, criminals across Southeast Asia are also running job scams, law enforcement impersonation, asset recovery scams, virtual kidnappings, sextortion, loan scams, business email compromise, and other illicit schemes. Criminal networks in the region earned up to $37 billion last year, UN officials estimate. Perhaps unsurprisingly, all of this revenue is allowing scammers to expand their operations and diversify, incorporating new infrastructure and technology into their systems in the hope of making them more efficient and brutally effective.
For example, scammers are often constrained by their language skills and ability to keep up conversations with potentially hundreds of victims at a time in numerous languages and dialects. However, generative AI developments within the last two years—including the launch of writing tools such as ChatGPT—are making it easier for criminals to break down language barriers and create the content needed for scamming.
The UN’s report says AI can be used for automating phishing attacks that ensnare victims, the creation of fake identities and online profiles, and the crafting of personalized scripts to trick victims while messaging them in different languages. “These developments have not only expanded the scope and efficiency of cyber-enabled fraud and cybercrime, but they have also lowered the barriers to entry for criminal networks that previously lacked the technical skills to exploit sophisticated and profitable methods,” the report says.
Stephanie Baroud, a criminal intelligence analyst in Interpol’s human trafficking unit, says the impact of AI needs to be considered as part of a pig butchering scammer’s tactics going forward. Baroud, who spoke with WIRED in an interview before the publication of the UN report, says the criminal’s recruitment ads that lure people into being trafficked to scamming compounds used to be “very generic” and full of grammatical errors. However, AI is now making them appear more polished and compelling, Baroud says. “It is really making it easier to create a very realistic job offer,” she says. “Unfortunately, this will make it much more difficult to identify which is the real and which is the fake ads.”
Perhaps the biggest AI paradigm shift in such digital attacks comes from deepfakes. Scammers are increasingly using machine-learning systems to allow for real-time face-swapping. This technology, which has also been used by romance scammers in West Africa, allows criminals to change their appearance on calls with their victims, making them realistically appear to be a different person. The technology is allowing “one-click” face swaps and high-resolution video feeds, the UN’s report states. Such services are a game changer for scammers, because they allow attackers to “prove” to victims in photos or real-time video calls that they are who they claim to be.
Using these setups, however, can require stable internet connections, which can be harder to maintain within some regions where pig butchering compounds and other scamming have flourished. There has been a “notable” increase in cops seizing Starlink satellite dishes in recent months in Southeast Asia, the UN says—80 units were seized between April and June this year. In one such operation carried out in June, Thai police confiscated 58 Starlink devices. In another instance, law enforcement seized 10 Starlink devices and 4,998 preregistered SIM cards while criminals were in the process of moving their operations from Myanmar to Laos. Starlink did not immediately respond to WIRED’s request for comment.
“Obviously using real people has been working for them very well, but using the tech could be cheaper after they have the required computers” and connectivity, says Troy Gochenour, a volunteer with the Global Anti-Scam Organization (GASO), a US-based nonprofit that fights human-trafficking and cybercrime operations in Southeast Asia.
Gochenour’s research involves tracking trends on Chinese-language Telegram channels related to carrying out pig butchering scams. And he says that it is increasingly common to see people applying to be AI models for scam content.
In addition to AI services, attackers have increasingly leaned on other technical solutions as well. One tool that has been increasingly common in digital scamming is so-called “crypto drainers,” a type of malware that has particularly been deployed against victims in Southeast Asia. Drainers can be more or less technically sophisticated, but their common goal is to “drain” funds from a target’s cryptocurrency wallets and redirect the currency to wallets controlled by attackers. Rather than stealing the credentials to access the target wallet directly, drainers are typically designed to look like a legitimate service—either by impersonating an actual platform or creating a plausible brand. Once a victim has been tricked into connecting their wallet to the drainer, they are then manipulated into approving one or a few transactions that grant attackers unintended access to all the funds in the wallet.
Drainers can be used in many contexts and with many fronts. They can be a component of pig butchering investment scams, or promoted to potential victims through compromised social media accounts, phishing campaigns, and malvertizing. Researchers from the firm ScamSniffer, for example, published findings in December about sponsored social media and search engine ads linked to malicious websites that contained a cryptocurrency drainer. The campaign, which ran from March to December 2023 reportedly stole about $59 million from more than 63,000 victims around the world.
Far from the low-tech days of doing everything through social engineering by building a rapport with potential victims and crafting tricky emails and text messages, today’s scammers are taking a hybrid approach to make their operations as efficient and lucrative as possible, UN researchers say. And even if they aren’t developing sophisticated malware themselves in most cases, scammers are increasingly in the market to use these malicious tools, prompting malware authors to adapt or create hacking tools for scams like pig butchering.
Researchers say that scammers have been seen using infostealers and even remote access trojans that essentially create a backdoor in a victim’s system that can be utilized in other types of attacks. And scammers are also expanding their use of malicious smart contracts that appear to programmatically establish a certain agreed-upon transaction or set of transactions, but actually does much more. “Infostealer logs and underground data markets have also been critical to ongoing market expansion, with access to unprecedented amounts of sensitive data serving as a major catalyst,” Wojcik, from the UNODC, says.
The changing tactics are significant as global law enforcement scrambles to deter digital scamming. But they are just one piece of the larger picture, which is increasingly urgent and bleak for forced laborers and victims of these crimes.
“It is now increasingly clear that a potentially irreversible displacement and spillover has taken place in which organized crime are able to pick, choose, and move value and jurisdictions as needed, with the resulting situation rapidly outpacing the capacity of governments to contain it,” UN officials wrote in the report. “Failure to address this ecosystem will have consequences for Southeast Asia and other regions.”
29 notes
·
View notes
Text
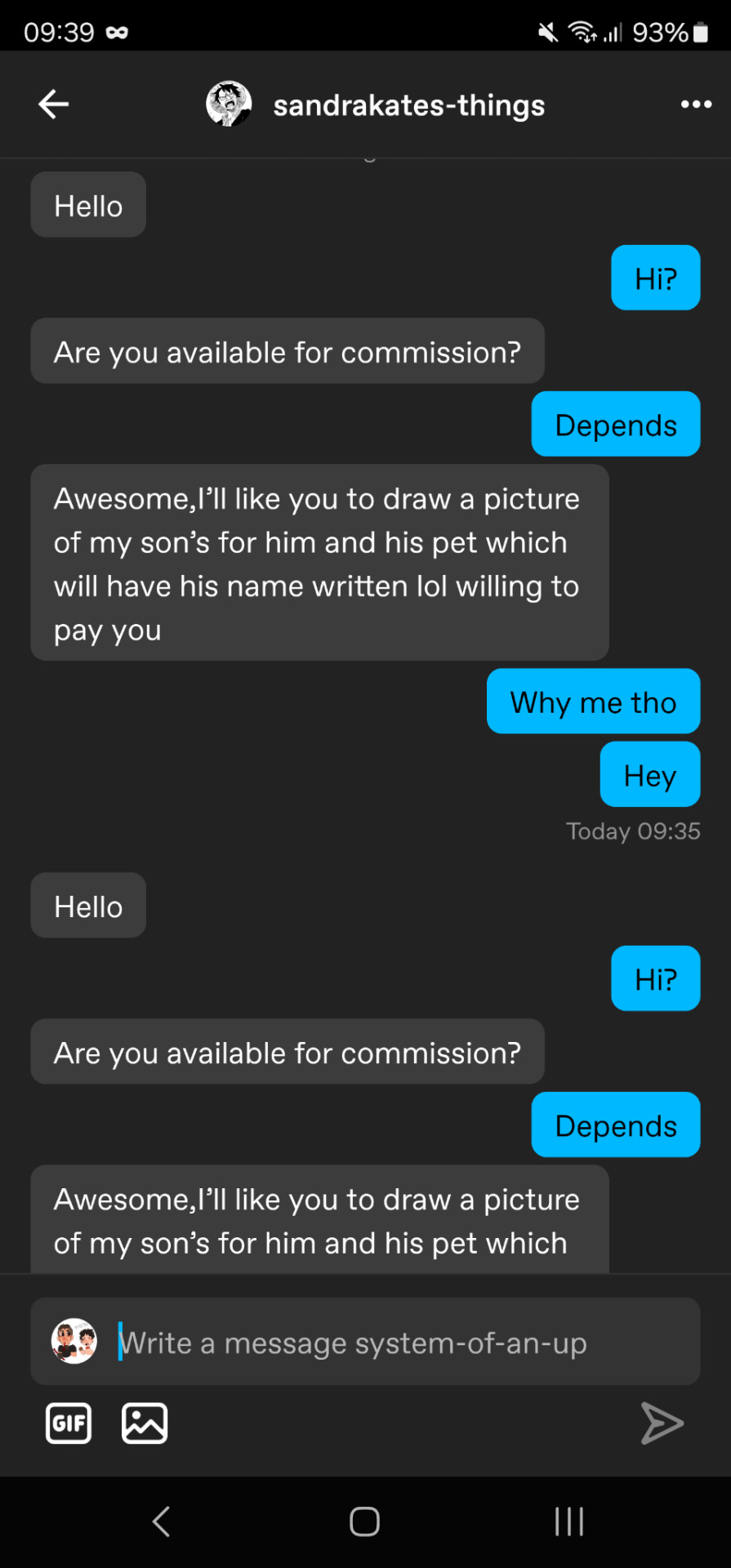
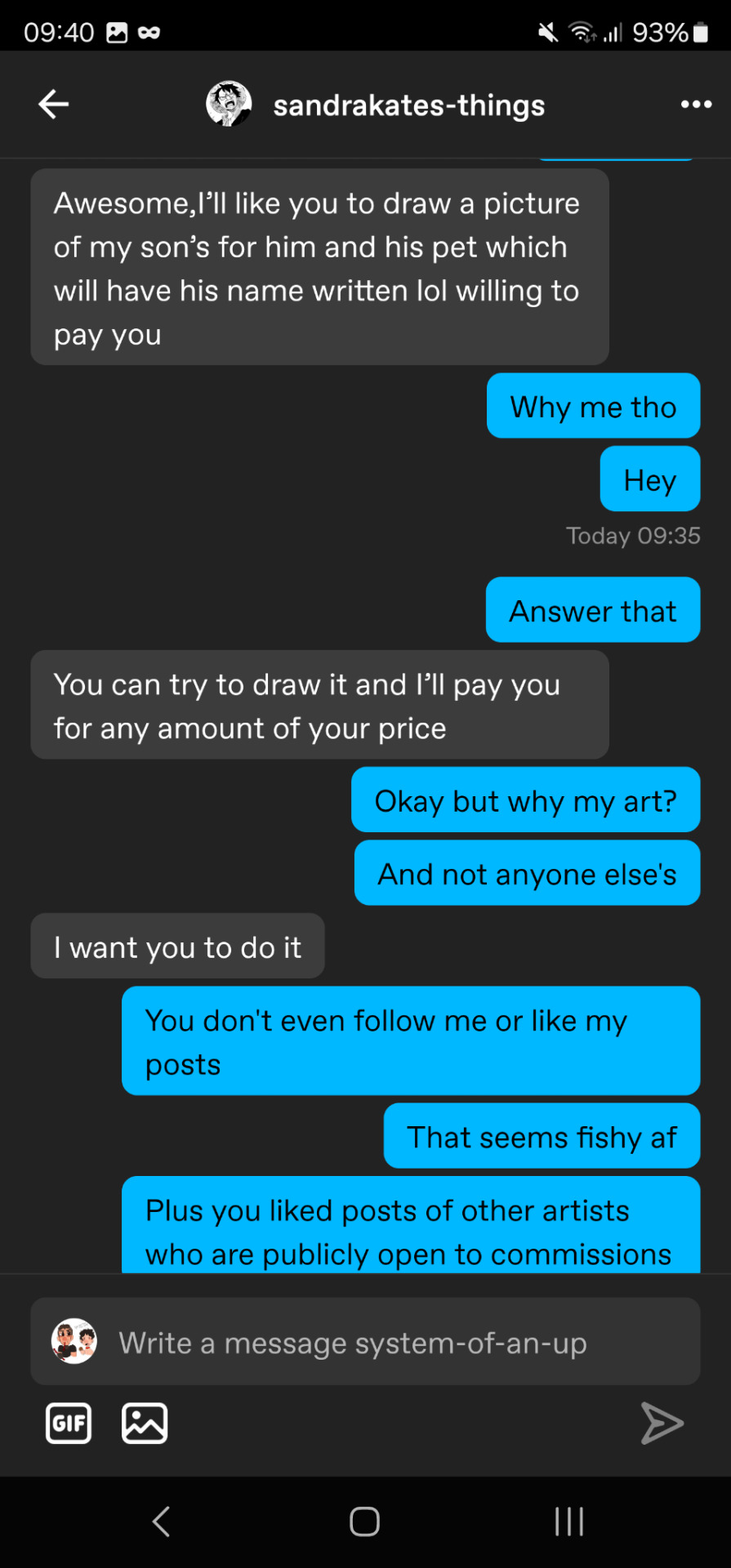
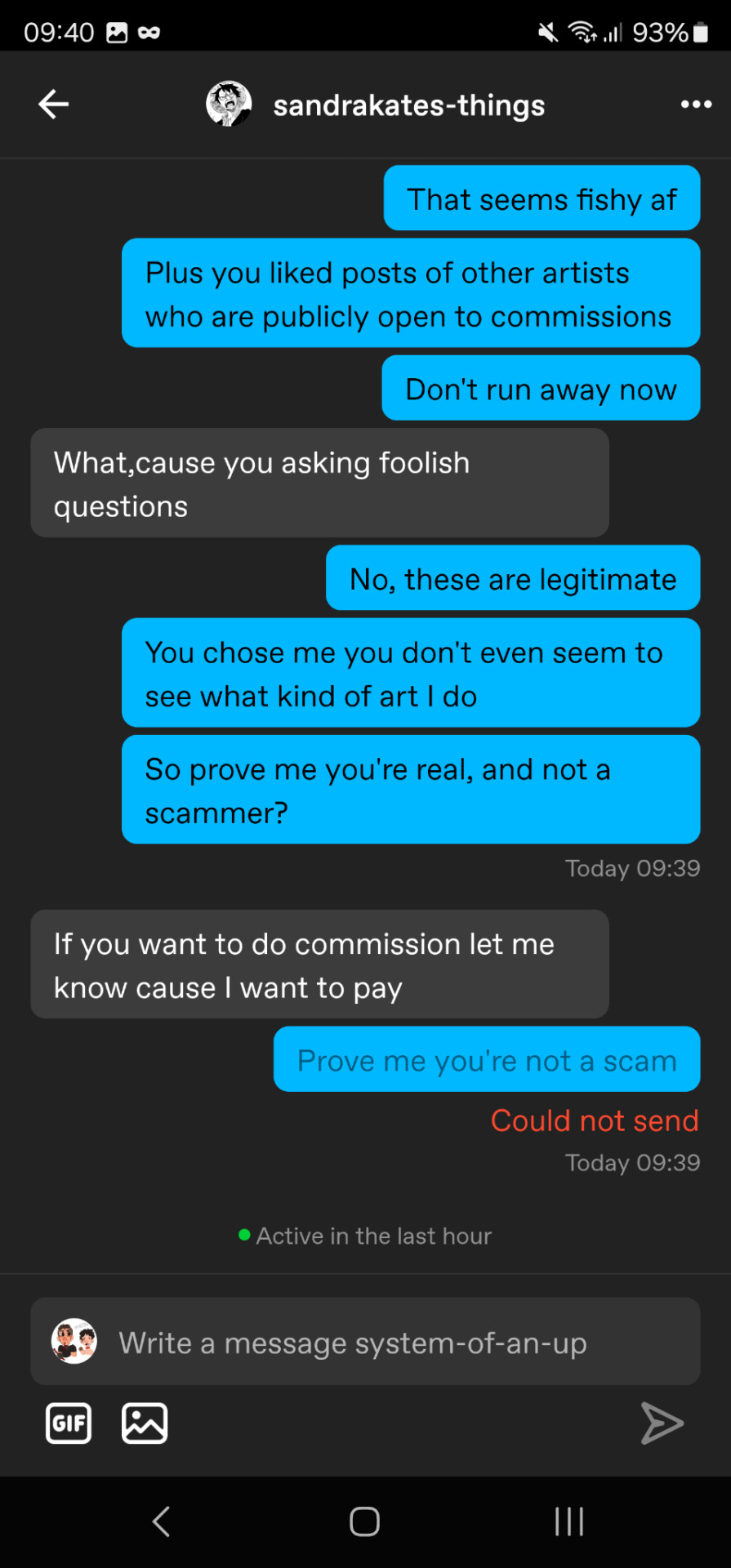
I'm so clever
Stay safe artists.
How to recognize an art scam?
1. Hi can you draw a picture of my son and his pet? I'll pay you anything what are your prices?
That's the most common question I got several times on other websites. Whether you gave prices or not they won't look into it. They never looked at your account, in fact. They pish you into making high prices for them to get refunded later.
2. They don't follow you, or they didn't like your art a while ago.
When you're commissioning an artist, it's because you enjoy their art. The least you'd normally do is give their art likes, comments, or follow you.
3. Just do it
A normal client would totally understand your suspicions and would prove they're not a scammer by explaining what they like in your art. For example, the choice of color palette, the graphic paw (funny way to say signature style), etc. They can also make you feel guilty about your questions. Don't.
4. They'll insist on a certain payment method that could give them advantages, and/or pay you AFTER.
Okay, let's say you're gonna buy bread. The baker hands you your baguette. You are right in front of them, so it's okay to pay after.
Now, you are asking for a developer to make you a script. They have no guarantee that you are real, nor that you are honest. It's normal for them to ask you to pay them first. Or 50% before 50% in the middle.
If you take PayPal, don't. They have a 180d refund policy, and even if the client was hobest at first, PayPal is by the buyer's side and not yours. It doesn't matter if you did the commission, the buyer CAN be refunded.
Solutions?
KYC. Know Your Customer. Sniff shady customers. But it's not really 100% working.
Use a middleman. This one decreases trust from the buyer's side but someone who has seen your commissions before and trusts you from the beginning wouldn't be too affected.
Make them sign an online contract before the commission. A lawyer can make you one or you can make one yourself. Email them, and if they're not a scammer they would sign it. Then you could contact PayPal in case of refund with this contract that person signed with their REAL information + their username and PayPal acc.
Ask for CRYPTOCURRENCY or set up a private XMR <your crypto currency> wallet. Few people really use crypto though.
DMCA them in case they use your art after refusing to pay you. Keep reverse-searching (Google Lens/Images) your art after getting scammed. As long as you have screenshots of the conversation with the client, you have all rights to do so.
13 notes
·
View notes
Text
Revolutionizing the Digital Landscape: Technoviaan Software's Comprehensive IT Services
In the ever-evolving digital landscape, businesses require innovative solutions to stay ahead of the curve. Introducing Technoviaan Software, a trailblazer in the realm of Information Technology services. With a profound expertise spanning across various cutting-edge technologies, Technoviaan Software stands as a beacon of excellence, offering unparalleled services tailored to meet the diverse needs of modern businesses.Empowering Businesses with Technological BrillianceAt Technoviaan Software, we understand the pivotal role technology plays in shaping the success of businesses in today's competitive environment. Leveraging our expertise in a multitude of technologies, we offer comprehensive IT services designed to empower businesses across various domains.Expertise in Key Technologies.NET Development: Our skilled team of developers excels in crafting robust and scalable solutions using the .NET framework. Whether it's building dynamic web applications or enterprise-level software, we ensure unparalleled performance and reliability.Java Development: With a deep-rooted understanding of Java technology, we deliver tailored solutions that drive business growth. From enterprise application development to Java-based web solutions, our expertise knows no bounds.PHP Development: Technoviaan Software pioneers in PHP development, delivering high-performance websites and applications that resonate with your audience. Our proficiency in PHP frameworks like Laravel ensures swift development cycles and exceptional results.Python Development: Python's versatility is at the core of our development philosophy. Our Python experts harness the power of this language to create data-driven solutions, machine learning algorithms, and automation scripts that propel businesses forward.Digital Marketing: In the digital realm, visibility is paramount. Technoviaan Software offers bespoke digital marketing solutions tailored to amplify your online presence. From SEO strategies to targeted PPC campaigns, we deploy tactics that drive tangible results and maximize ROI.Blockchain Development: Embrace the future of technology with our blockchain development services. Whether it's implementing smart contracts, building decentralized applications, or exploring cryptocurrency solutions, Technoviaan Software is your trusted partner in blockchain innovation.Unmatched Commitment to ExcellenceWhat sets Technoviaan Software apart is our unwavering commitment to excellence. We strive to understand the unique requirements of each client and deliver solutions that exceed expectations. With a customer-centric approach and a penchant for innovation, we forge long-lasting partnerships built on trust and mutual success.Experience the Technoviaan AdvantageIn a world where technology reigns supreme, Technoviaan Software emerges as a beacon of innovation and expertise. Whether you're a startup venturing into uncharted territories or an established enterprise seeking to revitalize your digital presence, we have the tools, the talent, and the tenacity to propel you towards success.Experience the Technoviaan advantage today and embark on a journey of digital transformation like never before. Your success is our mission, and together, we'll shape a future fueled by technological brilliance.Connect with us today and unlock the limitless possibilities of technology with Technoviaan Software.
#it services#software developers#software development#software services#software solutions#.net development#phpdevelopment#flutter app development#web development#it staffing services#technology#ios app development#android app development#Software
3 notes
·
View notes
Text
25 Python Projects to Supercharge Your Job Search in 2024

Introduction: In the competitive world of technology, a strong portfolio of practical projects can make all the difference in landing your dream job. As a Python enthusiast, building a diverse range of projects not only showcases your skills but also demonstrates your ability to tackle real-world challenges. In this blog post, we'll explore 25 Python projects that can help you stand out and secure that coveted position in 2024.
1. Personal Portfolio Website
Create a dynamic portfolio website that highlights your skills, projects, and resume. Showcase your creativity and design skills to make a lasting impression.
2. Blog with User Authentication
Build a fully functional blog with features like user authentication and comments. This project demonstrates your understanding of web development and security.
3. E-Commerce Site
Develop a simple online store with product listings, shopping cart functionality, and a secure checkout process. Showcase your skills in building robust web applications.
4. Predictive Modeling
Create a predictive model for a relevant field, such as stock prices, weather forecasts, or sales predictions. Showcase your data science and machine learning prowess.
5. Natural Language Processing (NLP)
Build a sentiment analysis tool or a text summarizer using NLP techniques. Highlight your skills in processing and understanding human language.
6. Image Recognition
Develop an image recognition system capable of classifying objects. Demonstrate your proficiency in computer vision and deep learning.
7. Automation Scripts
Write scripts to automate repetitive tasks, such as file organization, data cleaning, or downloading files from the internet. Showcase your ability to improve efficiency through automation.
8. Web Scraping
Create a web scraper to extract data from websites. This project highlights your skills in data extraction and manipulation.
9. Pygame-based Game
Develop a simple game using Pygame or any other Python game library. Showcase your creativity and game development skills.
10. Text-based Adventure Game
Build a text-based adventure game or a quiz application. This project demonstrates your ability to create engaging user experiences.
11. RESTful API
Create a RESTful API for a service or application using Flask or Django. Highlight your skills in API development and integration.
12. Integration with External APIs
Develop a project that interacts with external APIs, such as social media platforms or weather services. Showcase your ability to integrate diverse systems.
13. Home Automation System
Build a home automation system using IoT concepts. Demonstrate your understanding of connecting devices and creating smart environments.
14. Weather Station
Create a weather station that collects and displays data from various sensors. Showcase your skills in data acquisition and analysis.
15. Distributed Chat Application
Build a distributed chat application using a messaging protocol like MQTT. Highlight your skills in distributed systems.
16. Blockchain or Cryptocurrency Tracker
Develop a simple blockchain or a cryptocurrency tracker. Showcase your understanding of blockchain technology.
17. Open Source Contributions
Contribute to open source projects on platforms like GitHub. Demonstrate your collaboration and teamwork skills.
18. Network or Vulnerability Scanner
Build a network or vulnerability scanner to showcase your skills in cybersecurity.
19. Decentralized Application (DApp)
Create a decentralized application using a blockchain platform like Ethereum. Showcase your skills in developing applications on decentralized networks.
20. Machine Learning Model Deployment
Deploy a machine learning model as a web service using frameworks like Flask or FastAPI. Demonstrate your skills in model deployment and integration.
21. Financial Calculator
Build a financial calculator that incorporates relevant mathematical and financial concepts. Showcase your ability to create practical tools.
22. Command-Line Tools
Develop command-line tools for tasks like file manipulation, data processing, or system monitoring. Highlight your skills in creating efficient and user-friendly command-line applications.
23. IoT-Based Health Monitoring System
Create an IoT-based health monitoring system that collects and analyzes health-related data. Showcase your ability to work on projects with social impact.
24. Facial Recognition System
Build a facial recognition system using Python and computer vision libraries. Showcase your skills in biometric technology.
25. Social Media Dashboard
Develop a social media dashboard that aggregates and displays data from various platforms. Highlight your skills in data visualization and integration.
Conclusion: As you embark on your job search in 2024, remember that a well-rounded portfolio is key to showcasing your skills and standing out from the crowd. These 25 Python projects cover a diverse range of domains, allowing you to tailor your portfolio to match your interests and the specific requirements of your dream job.
If you want to know more, Click here:https://analyticsjobs.in/question/what-are-the-best-python-projects-to-land-a-great-job-in-2024/
#python projects#top python projects#best python projects#analytics jobs#python#coding#programming#machine learning
2 notes
·
View notes
Text
🚀 LIBRA Creator Challenges Jurisdiction in New York Lawsuit! 🚀
Because who doesn't love a good courtroom drama? 🎭 Meet Hayden Davis, the mastermind behind the LIBRA token, who's flipping the script in a class action lawsuit! Filed in the illustrious court of NYC, this case claims that over $150 million was, let's say, "misappropriated." Sounds a bit Fishy McFishface, doesn't it? 🐟💰
But wait! Hayden's strutting into court and saying, "Nah, you can't touch this!" 🕺💃 Challenging the jurisdiction might open a Pandora's box of issues for investor protections—and we know how much crypto lovers adore oversight. 😜
🤔 Are We in the Twilight Zone of Crypto?
Meanwhile, the lawsuit claims insiders, including Kelsier Ventures and Meteora's Benjamin Chow, made off with a king's ransom. Not exactly the plot twist the crypto community wanted. 😱
🌐 "This ongoing investigation suggests insiders kept a dominant share of supply..." - Burwick Law
Just imagine your investment dropping by 94%, which is basically a one-way ticket to Villain Town for all involved. 🥺💔
💔 Investor Backlash: The Drama Continues
The echoes of discontent are palpable in the air, with community grumbling about this tragedy of errors. Folks are eyeing potential new regulations that might put some order in this chaotic crypto circus. 🎪
🧐 "If only there were more regulations to reign in this wild west of crypto!"
Experts predict that LIBRA's saga could set a legal precedent for crypto jurisdiction disputes. Great, right? We can only hope it helps to stabilize the dizzying rollercoaster ride that is decentralized finance. 🎢💸
Want to dive deeper? Check out all the juicy details in the full article on kanalcoin.com. Let’s sift through the popcorn-worthy drama together! 🍿✨
Disclaimer: This website provides information only and is not financial advice. Cryptocurrency investments are risky. We do not guarantee accuracy and are not liable for losses. Conduct your own research before investing.
Join the conversation, share your hot takes, and don't forget to tag your fellow crypto enthusiasts! 💬👇 #CryptoDrama #LIBRA #Investing #CryptoNews #MemeLife #JurisdictionJourney #CryptoRegulations
0 notes
Text
From Script Kiddies to Sophisticated Syndicates: The Evolution of Cybercrime Groups
The image of a "hacker" has undergone a dramatic transformation. What once conjured up visions of rebellious teenagers in hoodies, fueled by curiosity and a desire to "break things" for bragging rights, has evolved into a far more sinister and professionalized landscape. We've moved from the era of isolated "script kiddies" to the sophisticated, globe-spanning operations of cybercrime syndicates.1 This evolution isn't just a matter of scale; it's a fundamental shift in motivation, methodology, and organizational structure.
The Dawn of Digital Mischief: The Script Kiddie Era
In the early days of the internet and personal computing, the term "script kiddie" emerged to describe individuals with limited technical skills who relied on pre-written tools and exploits developed by more advanced hackers.2 Their motivations were often rooted in:
Curiosity and Exploration: A desire to see what was possible, to push boundaries, and understand how systems worked.
Bragging Rights: The thrill of successfully defacing a website, taking down a small server, or spreading a simple virus to gain notoriety among peers.3
Vandalism and Pranks: Often, the damage was more about disruption and annoyance than financial gain.4
While these early exploits could certainly cause headaches and some financial loss, they lacked the strategic depth and sustained impact of today's attacks. They were often detectable, and the perpetrators, if caught, were typically individuals operating in isolation.
The Turning Point: Monetization and Organization
The late 1990s and early 2000s marked a significant shift.5 As the internet became intertwined with commerce and personal data, the potential for financial gain from cyber activities became undeniably clear. This attracted a different breed of actor, and with it, the beginnings of professionalization:
Early Financial Motives: Phishing scams, credit card fraud, and the distribution of early malware designed to steal personal information started to appear. The "Love Bug" virus in 2000, while still somewhat unsophisticated by today's standards, demonstrated the massive financial impact a widespread cyberattack could have.6
The Rise of Underground Forums: These online spaces facilitated the exchange of knowledge, tools, and stolen data, allowing for collaboration and the sharing of best practices among burgeoning cybercriminals.7
Initial Group Formations: Small, loosely organized groups began to form, focusing on specific types of fraud or malware development. These groups might pool resources and expertise to launch more effective attacks.
The Professionalization of Crime: Cybercrime Syndicates Emerge
Today, we face a threat that operates with the efficiency and ruthlessness of a multinational corporation.8 Cybercrime syndicates are not just groups of hackers; they are complex, hierarchical organizations that function like legitimate businesses.9 Their transformation is driven by:
Profit as the Primary Driver: The focus is almost exclusively on financial gain. Ransomware-as-a-Service (RaaS), data exfiltration for sale on the dark web, business email compromise (BEC) schemes, and cryptocurrency theft are multi-billion dollar industries.
Specialization and Division of Labor: No longer are individuals trying to do everything. Syndicates have distinct roles:
Developers: Crafting sophisticated malware, exploits, and tools.10
Penetration Testers: Identifying vulnerabilities in target systems.11
Social Engineers: Crafting highly convincing phishing campaigns and deepfake attacks.12
Network Operators: Managing botnets and command-and-control infrastructure.
Financial Specialists: Handling cryptocurrency transactions, money laundering, and payment processing.
Customer Support: Believe it or not, some RaaS groups offer "customer support" to their victims to ensure ransom payments are made efficiently!13
Cybercrime-as-a-Service (CaaS): This is perhaps the most defining characteristic of modern cybercrime. Sophisticated tools, infrastructure, and even expertise are rented or sold on underground marketplaces.14 This "democratization of crime" lowers the barrier to entry, allowing even less skilled actors to launch devastating attacks by simply subscribing to a service.15
Global Reach and Anonymity: The internet provides a global stage for these operations.16 Perpetrators can launch attacks from anywhere in the world, often leveraging proxy networks, VPNs, and cryptocurrencies to mask their identities and locations, making attribution and prosecution incredibly challenging.17
Adaptability and Innovation: These syndicates are constantly researching new vulnerabilities, developing novel attack vectors, and leveraging emerging technologies like AI to enhance their operations.18 They quickly adapt to new security measures, engaging in a continuous arms race with cybersecurity defenders.19
Nation-State Backing/Overlap: While distinct from pure cybercrime, the lines can blur.20 Some highly sophisticated cybercrime groups may have tacit or direct links to nation-state actors, using their skills for geopolitical objectives or operating with impunity due to state protection.21
The Impact on the Digital World
The shift from script kiddies to sophisticated syndicates has profound implications:
Increased Frequency and Severity of Attacks: The professionalization means more attacks, often with greater impact, targeting critical infrastructure, large corporations, and even individuals on an unprecedented scale.
Complex Attack Chains: Modern attacks are rarely a single exploit. They involve intricate multi-stage campaigns, combining social engineering, malware, lateral movement, and data exfiltration.22
Erosion of Trust: Every successful breach chips away at public and corporate trust in digital systems.
Economic Devastation: The financial costs of cybercrime run into trillions of dollars globally, impacting businesses of all sizes, supply chains, and national economies.23
The days of viewing hackers as mischievous renegades are long gone. We are in a perpetual struggle against highly organized, well-funded, and technologically advanced criminal enterprises. Combating this requires a coordinated global effort, robust cybersecurity defenses, and a deep understanding of the professional business model that now underpins the dark side of the digital world. Read more at: Cybersecurity Threat and AI
0 notes
Text
Amit Kakkar Explains How to Identify Visa Fraud in 2025

Visa fraud is becoming more complex and harder to detect with each passing year. In 2025, scams have evolved far beyond fake documents and shady agents. Today, fraudsters use sophisticated tactics, including digital impersonation and fake consultancy setups, to trick unsuspecting applicants.
Amit Kakkar, a recognized immigration consultant with over 15 years of experience, shares expert advice on how to recognize and avoid visa fraud in this changing landscape.
The Changing Face of Visa Fraud
According to Amit Kakkar, the face of visa fraud has changed drastically. “It’s no longer limited to fake stamps or poor-quality documents. We’re seeing full-blown operations that look entirely legitimate on the surface,” he explains.
Scammers now use realistic websites, forged accreditations, and well-rehearsed scripts to trick people into trusting them. The difference between real and fake is often subtle—and that’s where expertise comes in.
Red Flags to Watch For
Amit emphasizes that the key to avoiding visa scams lies in understanding the warning signs. Here are the most common red flags to look for in 2025:
1. Unregistered Consultants or Agencies
Many fraudulent agents operate without proper licensing. "Always check if the agent is registered with a recognized immigration authority," says Amit. Most countries provide public registries where you can verify consultant credentials.
2. Guaranteed Visa Promises
“If someone tells you they can guarantee a visa, be cautious,” Amit warns. Visa approvals are never guaranteed. They depend entirely on the applicant’s qualifications, documentation, and the immigration laws of the destination country.
3. Unusual Payment Requests
Genuine immigration firms operate transparently, with clear payment channels and receipts. Be wary if you're asked to pay through unofficial methods such as personal bank accounts, cryptocurrency, or gift cards.
4. Lack of Transparency in Process
A trustworthy consultant will involve you in every step. Scammers often discourage questions and promise to "handle everything" without providing documentation. “You should always know what’s happening with your application,” Amit advises.
How to Protect Yourself in 2025
With fraud becoming more convincing, being cautious is no longer enough—you need to be proactive. Amit Kakkar recommends the following steps for safeguarding your visa journey:
Verify Credentials
Check if your consultant is registered with official immigration authorities in the country you're applying to. For example, in Canada, use the CICC (College of Immigration and Citizenship Consultants) registry.
Understand the Visa Process Yourself
Even if you're hiring help, knowing the basics of your visa type and application process will help you spot when something doesn’t add up.
Ask the Right Questions
Reputable consultants are open to questions. Ask about their experience, success rate, and license. Be cautious if they seem uncomfortable or evasive.
Avoid High-Pressure Tactics
Fraudsters often use urgency to pressure you into quick decisions. A credible consultant will give you time to think and won't force you into rushed commitments.
Amit Kakkar: A Trusted Voice in Immigration
Amit Kakkar has been at the forefront of immigration consulting for over a decade. Known for his integrity and client-first approach, he has guided thousands of individuals through successful visa applications.
“What matters most is honesty and education,” says Amit. “My goal is to make sure every client understands the process, the risks, and the opportunities.”
He also advocates for stronger public awareness campaigns to help people identify fraud early and report suspicious activity.
Final Thoughts
Visa fraud in 2025 is more advanced—but with the right guidance, it's also more avoidable. By staying informed and working only with certified, trustworthy professionals like Amit Kakkar, you can protect your future and pursue your immigration goals with confidence.
If you're planning to apply for a visa this year, remember: do your homework, ask the right questions, and never ignore the red flags.
0 notes
Text
Top 10 Blogging Niches That Actually Make Money

In the vast digital ocean, blogging remains a powerful vessel for sharing knowledge, building communities, and, most importantly, generating income. Many aspire to create a blog, but the crucial first step often involves identifying a niche that not only aligns with your passion but also holds genuine financial potential. In 2025, the landscape is ripe with opportunities for those who choose wisely. This article from Zapzy Digital Blog (zapzy.net) delves into the top 10 profitable blogging niches that consistently demonstrate high earning potential. We'll explore why these niches thrive, how they can be monetized, and what it takes to succeed in each, all while keeping Google AdSense guidelines and best SEO practices in mind. Understanding a "Profitable Blogging Niche" Before we dive into the specific niches, let's clarify what makes a blogging niche "profitable." It's more than just a trending topic; it's a sweet spot where these elements converge: - High Demand: A significant audience actively searching for information, solutions, or entertainment related to the topic. - Monetization Potential: The ability to earn revenue through various streams like advertising, affiliate marketing, digital products, services, or sponsorships. - Passion/Expertise: Your genuine interest and knowledge in the subject, which allows you to create authentic, valuable, and sustainable content. - Solvable Problems: Niches that address specific pain points or aspirations of the audience, leading to higher engagement and conversion rates. Remember, even the most promising niches require consistent effort, quality content, and effective promotion to flourish. Key Considerations for Google AdSense & SEO For your blog to truly thrive and be ready for monetization, particularly with platforms like Google AdSense, attention to detail is paramount. While this article focuses on identifying profitable blogging niches, here’s a quick reminder of essential practices: - Original, High-Quality Content: Google prioritizes unique, helpful, and in-depth content. Avoid plagiarism or thin content. - User Experience (UX): A fast-loading, mobile-responsive, and easy-to-navigate website is crucial for both users and search engines. - AdSense Content Policies: Ensure your content adheres to AdSense program policies, avoiding prohibited content (e.g., adult, illegal, hateful). - Clear Disclosure: If using affiliate links or sponsored content, clearly disclose these relationships to your audience. This builds trust and is often a legal requirement. The Top 10 Profitable Blogging Niches Based on current trends, search demand, and diverse monetization opportunities, here are the top 10 profitable blogging niches you should consider for your next venture: 1. Personal Finance & Investing Why it's profitable: Everyone needs to manage money, save, invest, and plan for the future. The demand for financial literacy is constant and growing. Topics range from budgeting and debt reduction to cryptocurrency and real estate investing. Monetization: Affiliate marketing (financial products, investing platforms, credit cards), selling digital products (budgeting templates, investment guides), online courses, consulting services, and display advertising (often with high CPC rates). Example content: "Beginner's Guide to Stock Market Investing," "How to Create a Zero-Based Budget," "Best Robo-Advisors for New Investors." 2. Health & Wellness Why it's profitable: Health is an evergreen concern. This vast niche includes physical fitness, mental health, nutrition, weight loss, holistic living, and specific conditions. People are always seeking ways to improve their well-being. Monetization: Affiliate marketing (supplements, fitness gear, healthy foods, mental wellness apps), selling digital products (meal plans, workout guides, meditation scripts), online coaching, sponsored content, and display advertising. Example content: "5 Easy Morning Yoga Routines for Stress Relief," "Understanding Gut Health: A Beginner's Guide," "Healthy Meal Prep Ideas for Busy Professionals." 3. Digital Marketing & SEO Why it's profitable: Businesses and individuals constantly seek to improve their online presence. This niche covers SEO, social media marketing, content marketing, email marketing, paid advertising, and web design. The industry is ever-evolving, creating continuous learning demand. Monetization: Selling digital products (SEO checklists, content calendars, social media templates), online courses, consulting/freelance services, software affiliate programs (e.g., SEMrush, Ahrefs, Canva), and display advertising. Example content: "Mastering On-Page SEO for Beginners," "Effective Social Media Strategies for Small Businesses," "Top 5 AI Tools for Content Creation." 4. Food & Recipes (with a Niche Twist) Why it's profitable: Eating is a universal need, but specific dietary trends or culinary interests offer strong niche opportunities. Think vegan recipes, gluten-free baking, specific regional cuisines, budget meal prep, or gourmet cooking. Monetization: Display advertising (often performs well), affiliate marketing (kitchen gadgets, specialty ingredients, cookbooks), selling e-cookbooks, online cooking classes, and sponsored posts from food brands. Example content: "Delicious 30-Minute Vegan Dinners," "Authentic Thai Curry Recipes You Can Make at Home," "Best Air Fryer Recipes for Quick Meals." 5. Parenting & Family Life Why it's profitable: Parents are always looking for advice, solutions, and community. This niche covers everything from pregnancy and newborn care to toddler development, raising teenagers, educational activities, and family travel. Monetization: Affiliate marketing (baby products, educational toys, parenting books), selling digital products (printable schedules, activity guides), sponsored reviews of family-oriented products, and display advertising. Example content: "Essential Baby Gear Checklist for First-Time Parents," "Creative Indoor Activities for Toddlers," "Tips for Managing Screen Time in Kids." 6. Home Improvement & DIY Why it's profitable: Many people enjoy DIY projects, home renovation, interior design, and gardening. Content in this niche helps people save money, enhance their living spaces, or pursue hobbies. Monetization: Affiliate marketing (tools, home decor items, building materials), selling digital products (project plans, design guides), online workshops, sponsored content from home brands, and display advertising. Example content: "DIY Pallet Furniture Projects for Your Backyard," "Transform Your Kitchen on a Budget," "Beginner's Guide to Indoor Plant Care." 7. Technology & Gadgets (Reviews & How-To's) Why it's profitable: The tech world constantly innovates, meaning there's always something new to review, explain, or troubleshoot. This includes smartphones, smart home devices, gaming tech, software, and emerging AI trends. Monetization: Affiliate marketing (electronics, software subscriptions), sponsored reviews, display advertising (often high CPC), and potentially creating your own tech-related digital products or guides. Example content: "Review: The Latest Flagship Smartphone," "Setting Up Your Smart Home Hub," "Understanding AI: A Non-Technical Guide." 8. Travel (Specific Focus) Why it's profitable: While broad travel blogs are competitive, niching down makes this highly profitable. Think budget travel, luxury travel, solo female travel, family travel, adventure travel, or focusing on specific regions (e.g., "Backpacking Southeast Asia"). Monetization: Affiliate marketing (flights, hotels, travel insurance, luggage), selling travel guides or itineraries, sponsored trips or content from tourism boards, and display advertising. Example content: "Ultimate Budget Travel Guide to Thailand," "Luxury Resorts for Your Next Romantic Getaway," "Essential Packing List for a European Backpacking Trip." 9. Pet Care Why it's profitable: Pet owners are passionate and willing to spend on their beloved companions. This niche covers pet health, training, nutrition, product reviews (food, toys, accessories), specific breeds, or even pet travel. Monetization: Affiliate marketing (pet food, supplies, insurance), selling digital products (training guides), sponsored product reviews, and display advertising. Example content: "Choosing the Right Dog Food for Your Puppy," "Positive Reinforcement Training Tips for Cats," "Essential Pet Travel Accessories." 10. Personal Development & Self-Care Why it's profitable: People are always seeking ways to improve themselves, their mindset, productivity, and overall well-being. This niche includes topics like mindfulness, productivity hacks, goal setting, motivation, relationships, and mental resilience. Monetization: Selling digital products (planners, journals, e-books), online courses, coaching services, affiliate marketing (books, apps, courses), and display advertising. Example content: "5 Habits to Boost Your Productivity," "Beginner's Guide to Mindfulness Meditation," "Building Resilience: Overcoming Life's Challenges." Choosing Your Perfect Niche: Beyond Profit While profitability is crucial, don't neglect your passion and expertise. The most successful blogs are those where the creator genuinely enjoys the topic and can provide authentic insights. - Assess Your Interests: What topics do you love to talk about? What problems do you enjoy solving? - Evaluate Your Expertise: Do you have professional experience, certifications, or deep personal knowledge in any of these areas? - Consider the Audience: Is there a sizable audience for your chosen niche? Are they actively searching for information? - Research Competition: Don't be afraid of competition, but look for ways to offer a unique perspective or delve into a specific sub-niche (a "micro-niche") to stand out. Monetization Strategies for Your Blog Once you've chosen your profitable blogging niche and started creating content, consider these common monetization methods: - Display Advertising (Google AdSense, Mediavine, Ezoic): This is often the first step for many bloggers. Once your traffic grows, you can apply to premium ad networks for higher earnings. - Affiliate Marketing: Promoting products or services from other companies (like Amazon Associates, as discussed previously) and earning a commission on sales. - Selling Your Own Digital Products: E-books, online courses, templates, printables, stock photos, etc. This offers higher profit margins. - Selling Your Own Services: Coaching, consulting, freelance writing, web design, virtual assistance, etc., leveraging your expertise in the niche. - Sponsored Content: Brands pay you to create content (reviews, articles) that promote their products or services. Always disclose sponsored content. - Memberships/Subscriptions: Offering exclusive content, forums, or resources for a recurring fee. Conclusion Embarking on a blogging journey in 2025 offers immense potential, particularly when you strategically choose one of the top 10 profitable blogging niches. By combining your passion with market demand and implementing smart monetization strategies, your Zapzy Digital Blog (zapzy.net) can not only become a valuable resource for your audience but also a significant source of income. Start exploring these niches, identify where your unique voice can shine, and begin building your successful blogging empire today! Read the full article
0 notes
Text
CoinMarketCap briefly hacked to drain crypto wallets via fake Web3 popup
CoinMarketCap, the popular cryptocurrency price tracking site, suffered a website supply chain attack that exposed site visitors to a wallet drainer campaign to steal visitors’ crypto. On Friday evening, January 20, CoinMarketCap visitors began seeing Web3 popups asking them to connect their wallets to the site. However, when visitors connected their wallets, a malicious script drained…

View On WordPress
0 notes
Text
Victim of a Fake Crypto Exchange? Astraweb Follows the Money Trail

Fake trading platforms are one of the biggest threats to cryptocurrency investors. These fraudulent exchanges mimic real ones, baiting users with promises of fast profits and low fees then vanishing with the funds. Astraweb’s expert recovery team tracks digital assets across wallets, exchanges, and jurisdictions, often intercepting them before they’re lost for good.
Stage 1: The Threat of Fake Exchanges
In the rapidly evolving crypto world, fake exchanges are sophisticated traps. They often:
Clone legitimate websites and interfaces
Demand excessive ID verification to stall complaints
Disappear without warning, taking all deposits
By the time investors realize something’s wrong, their money is already gone.
Stage 2: Warning Signs You’ve Been Scammed
Early red flags include:
Delayed or failed withdrawals
Wallet address changes or balance errors
Scripted or non-responsive customer service
If these signs appear, time is critical. The sooner action is taken, the higher the chance of recovery.

Stage 3: How Astraweb Tracks and Recovers Stolen Crypto
Astraweb combines advanced technology with global intelligence networks to trace stolen digital assets. Their process includes:
Initial Assessment • Your case is reviewed, blockchain data is analyzed, and recovery potential is estimated.
Digital Tracking • Using forensic software, Astraweb follows the money through anonymizers, mixers, and cross-chain bridges.
Legal Coordination • Collaboration with exchanges, banks, and law enforcement to initiate freezes and pursue asset seizures.
Asset Recovery • Once verified, the recovered funds are safely returned to the rightful owner.
Stage 4: Prevention and Protection for the Future
Astraweb doesn’t just recover your assets they help you secure your crypto life moving forward. Services include:
Cold wallet setup and security guidance
Tools to verify exchange legitimacy
Real-time fraud and scam alert systems

Act Quickly Every Hour Matters
In crypto scams, time works against you. The longer funds remain in motion, the harder they are to retrieve. Astraweb’s forensic skills, legal partnerships, and international reach give victims a real fighting chance.
Contact Astraweb now: [email protected]
1 note
·
View note
Text
Sponzy Nulled Script 5.8

Download Sponzy Nulled Script – Monetize Your Content Creatively If you're looking for a powerful yet cost-effective solution to launch a creator-support platform, Sponzy Nulled Script is the perfect tool for you. Whether you're building a Patreon-style website or looking to monetize content through subscriptions and donations, this script is a game-changer. Enjoy full access to premium features without any licensing restrictions. Get the latest version for free right here and empower your online journey today! What Is Sponzy Nulled Script? Sponzy Nulled Script is a premium PHP-based platform that enables creators to receive financial support from fans and subscribers. With seamless payment integrations, customizable layouts, and multi-language support, Sponzy allows you to create a community-focused platform that rivals the best in the business. The nulled version gives you complete access to its premium functionalities for free—no subscriptions, no hidden charges. Technical Specifications Script Type: PHP Laravel Framework Responsive Design: Fully Mobile-Optimized Database Support: MySQL 5.7+ Latest Version Compatibility: PHP 8+ Security: Integrated reCAPTCHA, CSRF Protection Powerful Features & Unique Benefits The Sponzy Nulled Script comes loaded with high-end features that give you a competitive edge: 1. Multi-Currency & Payment Gateway Support Integrate with PayPal, Stripe, and even cryptocurrency gateways to offer a seamless payment experience worldwide. 2. Membership Tiers Create different support plans with varying benefits to attract a wider range of supporters—from casual fans to superfans. 3. Real-Time Notifications Keep users engaged with real-time alerts for messages, tips, and subscription renewals. 4. GDPR-Ready and SEO-Friendly Built to meet modern data privacy regulations while optimizing your platform for search engines right out of the box. 5. Monetization Tools Enable tipping, subscriptions, and pay-per-view content—all built into the system with intuitive admin control. Why Choose Sponzy Nulled Script? Unlike many open-source alternatives, Sponzy Nulled Script is professionally designed and continuously updated. The nulled version saves you hundreds of dollars while providing the exact same user experience. It’s ideal for entrepreneurs, influencers, bloggers, and creative professionals who want to launch a content support platform without financial risk. How to Install Sponzy Nulled Script Download the script from our website. Upload it to your server using FTP or cPanel. Create a new MySQL database and import the included SQL file. Open the installation URL and follow the on-screen setup process. Log in to your admin panel and start customizing your platform! Use Cases of Sponzy Nulled Script Content Creators: Monetize exclusive videos, blogs, or artwork. Influencers: Offer membership perks to loyal followers. Nonprofits: Receive recurring donations without complex setups. Writers & Journalists: Launch subscription-based content easily. FAQs About Sponzy Nulled Script Q: Is it safe to use the nulled version? A: Yes, we ensure all scripts are scanned for malware and viruses before making them available. However, always use a secure hosting environment. Q: Can I update the script? A: Updates are manual, and you may need to download the latest version from our website when available. Q: Does it support RTL languages? A: Absolutely. Sponzy Nulled Script supports both LTR and RTL, making it perfect for global use. Q: Can I integrate custom themes? A: Yes, the script supports theme customization and development for a personalized user experience. Final Thoughts The Sponzy is more than just a content monetization tool—it’s your gateway to building a thriving digital community. Whether you're just starting out or scaling an established brand, Sponzy delivers professional-grade features without the professional-grade price tag. Don’t miss this opportunity to download it for free and unlock unlimited potential!
Looking for more premium resources? Check out our collection like avada nulled for even more web design flexibility. For a powerful eCommerce theme, try woodmart nulled—a must-have for modern online stores.
0 notes
Text
Cybersecurity Advisory: Hackers Exploit CAPTCHA Trick on Webflow to Deliver Phishing Attacks

In the ever-evolving landscape of cyber threats, attackers constantly devise new ways to bypass security measures and trick unsuspecting users. A recent and particularly insidious campaign has come to light, revealing hackers are exploiting a clever CAPTCHA trick, often leveraging legitimate platforms like Webflow's Content Delivery Network (CDN), to deliver sophisticated phishing attacks and malware.
This advisory details how this exploit works and, more importantly, what you can do to protect yourself and your organization.
The Deceptive CAPTCHA Trick
Traditionally, CAPTCHAs (Completely Automated Public Turing test to tell Computers and Humans Apart) are designed to differentiate between human users and automated bots, acting as a crucial security layer to prevent spam and abuse. However, in this new wave of attacks, hackers are turning this defense mechanism into an attack vector.
Here's how the exploit typically unfolds:
SEO Poisoning & Malicious PDFs: Attackers use search engine optimization (SEO) techniques to push malicious PDF files high up in search results. These PDFs are often hosted on legitimate, trusted platforms like Webflow's CDN, GoDaddy, or Strikingly, making them appear harmless. Users searching for documents, book titles, or charts might stumble upon these booby-trapped PDFs.
The Fake CAPTCHA Lure: When a victim opens one of these malicious PDFs, they are presented with an image that mimics a CAPTCHA challenge. This fake CAPTCHA often includes a checkbox or a button, prompting the user to "verify they are human" or "download the document."
Redirection to Phishing Pages: Clicking on this fake CAPTCHA image or button redirects the user to a malicious website. To add a layer of legitimacy, this phishing page might even present a real CAPTCHA (like Cloudflare Turnstile), further convincing the victim that they are on a legitimate site undergoing a security check.
Malware Delivery (Lumma Stealer): Once the user completes the genuine CAPTCHA, they are often prompted to "download" the supposed document. However, this action triggers a malicious PowerShell command, silently executing and deploying information-stealing malware, such as Lumma Stealer, onto the victim's system. In some cases, the attack directly aims to harvest credit card details or other sensitive personal information.
Information Exfiltration: The Lumma Stealer malware then proceeds to search for and exfiltrate sensitive data, including passwords, cryptocurrency wallet credentials, browser information, and other critical files.
Why is This So Effective?
This attack vector is particularly dangerous due to several factors:
Leveraging Trusted Domains: Hosting malicious PDFs on reputable CDNs like Webflow's helps bypass common security checks that flag suspicious or newly registered domains.
Social Engineering Sophistication: The use of CAPTCHAs, even fake ones, adds a veneer of legitimacy, making users less suspicious. The multi-stage nature of the attack, sometimes including a real CAPTCHA, further enhances its deceptive power.
Human Tendency to Trust: Users are accustomed to seeing CAPTCHAs and interacting with PDFs, making them more likely to fall victim to these well-crafted schemes.
Fileless Attack Techniques: The use of PowerShell scripts and other fileless methods can help the malware evade traditional antivirus detection.
How to Protect Yourself and Your Organization
Given the stealthy nature of these attacks, a multi-layered defense strategy is crucial:
Extreme Caution with Downloads and Links:
Verify Sources: Always be suspicious of unexpected PDF files or documents, especially if they are from unknown sources or appear in unusual search results.
Hover Before You Click: Before clicking any link or button within a document or on a webpage, hover over it to see the actual URL. Look for discrepancies or suspicious domains.
Direct Navigation: If you're looking for a specific document, go directly to the official website of the source rather than clicking on links from search results or emails.
Enhanced Email and Web Security:
Advanced Email Filtering: Implement robust email security solutions that can detect and block sophisticated phishing attempts, including those with malicious attachments or links.
Web Content Filtering: Deploy web filters that can identify and block access to known malicious websites, even if they are hosted on legitimate CDNs.
Endpoint Detection and Response (EDR):
Proactive Monitoring: EDR solutions can monitor endpoint activity for suspicious behaviors, such as unusual PowerShell script execution or attempts to exfiltrate data, even if the initial infection vector was subtle.
User Education and Awareness:
Regular Training: Conduct frequent cybersecurity awareness training for all employees, focusing on recognizing phishing tactics, social engineering, and the dangers of interacting with suspicious content.
"Think Before You Click": Reinforce the importance of pausing and scrutinizing any unexpected requests or prompts, especially those involving downloads or credential entry.
Keep Software Updated:
Patch Regularly: Ensure your operating systems, web browsers, PDF readers, and all other software are kept up-to-date with the latest security patches.
Implement Strong Authentication:
Multi-Factor Authentication (MFA): Enable MFA on all accounts, especially for critical services. This adds a crucial layer of security, even if credentials are stolen.
The Bottom Line
The exploitation of CAPTCHA tricks on platforms like Webflow's CDN highlights the evolving sophistication of cybercriminals. While these attacks are designed to be deceptive, a combination of user vigilance, robust security tools, and continuous education can significantly reduce your risk. Stay informed, stay cautious, and prioritize cybersecurity in your daily digital interactions.
0 notes
Text

Cryptojacking is a stealthy cybercrime where hackers hijack your device’s computing power to mine cryptocurrency without your consent. It slows down your system, drains your battery, causes overheating, and can lead to costly electricity or cloud service bills. Attackers use methods like infected downloads, malicious email links, or even by injecting mining scripts into websites and ads.
There are different types of cryptojacking: file-based (via software or attachments), cloud-based (targeting services like AWS), and browser-based (activated just by visiting a site). Detecting it involves noticing system slowdowns, high CPU usage, battery drain, or spikes in cloud/server costs.
To protect yourself, use trusted antivirus tools, install mining-blocker browser extensions, keep your software updated, and be cautious with downloads and emails. Businesses should secure their cloud infrastructure and monitor for unusual usage.
Real incidents like YouTube ad cryptojacking and Coinhive’s misuse prove it’s a real threat. But with the right steps, you can stay ahead of these silent attacks.
Stay safe — protect your devices now. 👉 Read more in the blog to dive deeper into detection techniques, prevention tools, and real-world case studies.
#crypto#blockchain#finance#cryptocurrency#crypto news#cryptocurrencies#cryptojacking#cybercrime#cybersecurity
0 notes
Text
🎉 *BREAKING NEWS* 🎉 Strap in, crypto enthusiasts and investors, because the rollercoaster just got a new plot twist! 🤯 Leaked secrets are spilling out like a toddler’s juice box at a two-year-old’s birthday party, and this time it’s about none other than former SEC Chair Gary Gensler. According to leaked details, Mr. Gensler didn’t just sip the crypto Kool-Aid—he was apparently *mixing it with the good stuff* behind closed doors! 🙈💰 You heard me right! While publicly enforcing a barrage of regulations faster than a caffeine-fueled squirrel on a trampoline, he was privately *crushing hard* on crypto assets. 🐿️💨 Imagine a guy heavily involved in drafting over 100 enforcement actions against various crypto firms, yet secretly sporting a T-shirt that screams, “I *💖* my crypto!” Pretty hard to digest, right? [Read all the gossip here!] 📜👀 The latest podcast with Patrick McHenry threw a spotlight on Gensler’s dual life, revealing that he’s academically tethered to blockchain studies all while wielding his enforcement hammer! 🧑⚖️🔨 What’s the crypto crowd’s reaction? Well, let’s just say it’s a blend of confusion and disappointment, like a bad crypto meme that ‘got it’s rug pulled’ at the last second. 😱💔 Many are questioning whether this supposed lover of digital assets has been sticking to the script of an imaginary villain in a tech-noir thriller. 📚💀 As we ponder what all this means for the future, remember that *history typically repeats itself*—and Gensler’s opaque tactics could leave us jumping through hoops like crypto-hungry kangaroos bouncing toward the next bull run. 🦘💸 Explore how these discrepancies in the “Gensler Doctrine” could shape upcoming regulations and market behavior. If you’re as intrigued as I am, you won’t want to miss the original article where all of this mess was uncovered!👉 DIVE IN HERE! 🌊🔍 Disclaimer: This website provides information only and is not financial advice. Cryptocurrency investments are risky. We do not guarantee accuracy and are not liable for losses. Conduct your own research before investing. #CryptoNews #GaryGensler #CryptoMeme #Bitcoin #Ethereum #CryptoCommunity #InvestSmart #HODL #KryptoKween
0 notes
Text
Sure, here is an article based on your request:
Website Mining Crypto with PaladinMining.com
Website mining crypto has become a popular way for individuals to earn cryptocurrencies without needing to purchase expensive hardware. One of the leading platforms in this space is PaladinMining.com, which offers a user-friendly interface and robust tools for both beginners and experienced miners.
How Does Website Mining Work?
Website mining involves using the processing power of a website visitor's device to mine cryptocurrency. This method is particularly useful for websites that have high traffic volumes. By integrating PaladinMining.com's mining script into your website, you can harness the computational power of visitors' devices to mine cryptocurrencies such as Monero (XMR).
Benefits of Using PaladinMining.com
1. Ease of Use: PaladinMining.com provides a straightforward setup process. Simply sign up, generate a mining script, and embed it into your website's code.
2. Transparency: The platform ensures transparency by allowing users to monitor their mining activities and earnings in real-time.
3. High Earnings Potential: With a large number of visitors, website mining can generate significant income over time.
4. Supportive Community: PaladinMining.com has a supportive community where users can share tips, strategies, and troubleshooting advice.
Getting Started with PaladinMining.com
To get started with website mining on PaladinMining.com, follow these steps:
1. Visit https://paladinmining.com and create an account.
2. Generate a mining script from your dashboard.
3. Embed the script into your website’s HTML code.
4. Monitor your mining activities and earnings through the PaladinMining.com dashboard.
Conclusion
Website mining crypto is an innovative way to monetize your online presence. With PaladinMining.com, you can easily integrate mining capabilities into your website and start earning cryptocurrencies. Whether you're a small blog owner or manage a high-traffic site, PaladinMining.com offers a scalable solution to boost your earnings.
Feel free to let me know if you need any further adjustments!
加飞机@yuantou2048

paladinmining
Paladin Mining
0 notes