#cisco log analysis
Explore tagged Tumblr posts
Text
Cisco Exposes State-Sponsored Hackers Exploiting Cisco Firewall Zero-Days CVE-2024-20359

Cisco has uncovered a sophisticated state-backed hacking group exploiting two previously unknown vulnerabilities in Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) firewalls since November 2023. The malicious cyber espionage campaign, dubbed "ArcaneDoor," has successfully infiltrated government networks worldwide, compromising crucial security infrastructure.
Weaponizing Zero-Day Exploits for Cyber Espionage
The threat actors, identified as UAT4356 by Cisco Talos and STORM-1849 by Microsoft, leveraged two zero-day vulnerabilities—CVE-2024-20353 (denial of service) and CVE-2024-20359 (persistent local code execution)—to breach Cisco firewalls. These previously undisclosed security flaws allowed cybercriminals to deploy sophisticated malware implants, granting them persistent access and remote control over compromised devices. One implant, dubbed "Line Dancer," is an in-memory shellcode loader capable of executing arbitrary payloads, disabling logging mechanisms, and exfiltrating captured network traffic. The second implant, a persistent backdoor named "Line Runner," incorporates multiple defense evasion techniques to evade detection while enabling the attackers to execute arbitrary Lua code on the hacked systems. Hallmarks of State-Sponsored Cyber Threats Cisco's analysis reveals that the threat actor's bespoke tooling, espionage focus, and in-depth knowledge of targeted devices are hallmarks of a sophisticated state-sponsored actor. The malicious actors exploited their access to exfiltrate device configurations, control logging services, and modify authentication mechanisms for lateral movement within compromised environments.
Urgent Call for Mitigation and Enhanced Security
In response to this severe cyber threat, Cisco has released security updates to address the two zero-day vulnerabilities and strongly recommends that customers promptly upgrade their ASA and FTD devices to the latest patched software versions. Administrators are also urged to monitor system logs for suspicious activity, implement strong multi-factor authentication, and ensure devices are securely configured and logged to a centralized location. As state-sponsored cyber threats continue to escalate, organizations must prioritize proactive security measures, regular patching, and robust incident response strategies to safeguard critical infrastructure and sensitive data. Complacency in the face of such advanced cyber espionage campaigns can devastate national security and organizational resilience. Read the full article
2 notes
·
View notes
Text
Step-by-Step Guide to AIOps Platform Development for Enterprises
As IT infrastructures become more complex, enterprises are increasingly turning to AIOps (Artificial Intelligence for IT Operations) platforms to streamline operations, enhance efficiency, and proactively manage incidents. A well-developed AIOps platform can automate troubleshooting, reduce downtime, and optimize IT performance using AI and machine learning.

In this blog, we’ll take you through a step-by-step guide to AIOps platform development for enterprises, covering everything from planning and data integration to model deployment and continuous optimization.
Step 1: Define Business Goals and Requirements
Before starting AIOps platform development, enterprises must clearly define objectives and align them with business needs. Key considerations include:
What IT challenges need to be solved? (e.g., downtime reduction, anomaly detection, performance optimization)
What metrics will define success? (e.g., Mean Time to Resolution (MTTR), system uptime, cost savings)
What existing IT tools and processes need integration?
A collaborative approach involving IT teams, data scientists, and business stakeholders ensures alignment between AIOps capabilities and enterprise goals.
Step 2: Choose the Right AIOps Architecture
The AIOps platform should be designed with scalability, flexibility, and real-time processing in mind. A typical AIOps architecture consists of:
1. Data Collection Layer
Collects data from logs, metrics, traces, and event streams
Integrates with IT monitoring tools (e.g., Splunk, Datadog, Prometheus)
2. Data Processing & Normalization
Cleans and structures raw data to prepare it for analysis
Eliminates redundant, outdated, and irrelevant data
3. AI & Machine Learning Models
Uses anomaly detection, predictive analytics, and event correlation algorithms
Applies natural language processing (NLP) for automated log analysis
4. Automation & Remediation Layer
Implements self-healing capabilities through automation scripts
Provides recommendations or auto-remediation for IT incidents
5. Visualization & Reporting
Dashboards and reports for monitoring insights
Custom alerts for proactive issue resolution
By selecting the right cloud-based, on-premises, or hybrid architecture, enterprises ensure scalability and flexibility.
Step 3: Data Integration & Collection
AIOps thrives on real-time, high-quality data from multiple sources. The platform should ingest data from:
IT infrastructure monitoring tools (Nagios, Zabbix)
Application performance monitoring (APM) tools (New Relic, AppDynamics)
Network monitoring tools (SolarWinds, Cisco DNA)
Cloud services (AWS CloudWatch, Azure Monitor)
💡 Best Practice: Use streaming data pipelines (Kafka, Apache Flink) for real-time event processing.
Step 4: Implement AI/ML Models for Analysis
The core of an AIOps platform is its AI-driven analysis. Enterprises should develop and deploy models for:
1. Anomaly Detection
Identifies abnormal patterns in system behavior using unsupervised learning
Helps detect issues before they escalate
2. Event Correlation & Noise Reduction
Uses graph-based analysis to correlate alerts from different sources
Filters out noise and reduces alert fatigue
3. Predictive Analytics
Forecasts potential failures using time-series forecasting models
Helps IT teams take preventive action
4. Incident Root Cause Analysis (RCA)
Uses AI-based pattern recognition to identify root causes
Reduces mean time to detect (MTTD) and mean time to resolve (MTTR)
💡 Best Practice: Continuously train and refine models using historical and real-time data for higher accuracy.
Step 5: Implement Automation & Self-Healing Capabilities
The true power of AIOps comes from its ability to automate responses and remediation. Enterprises should:
Automate routine IT tasks like server restarts, patch updates, and log cleanup
Use AI-driven playbooks for common incident resolution
Implement closed-loop automation where AI detects issues and applies fixes automatically
💡 Example: If an AIOps system detects high memory usage on a server, it can automatically restart specific processes without human intervention.
Step 6: Develop Dashboards & Alerts for Monitoring
To provide IT teams with real-time insights, enterprises must develop intuitive dashboards and alerting systems:
Use Grafana, Kibana, or Power BI for visualization
Set up dynamic alert thresholds using AI to prevent false positives
Enable multi-channel notifications (Slack, Teams, email, SMS)
💡 Best Practice: Implement explainable AI (XAI) to provide transparent insights into why alerts are triggered.
Step 7: Test, Deploy, and Optimize
After development, the AIOps platform should be rigorously tested for:
Scalability: Can it handle large data volumes?
Accuracy: Are AI models correctly identifying anomalies?
Latency: Is the system responding in real-time?
After successful testing, deploy the platform in stages (pilot → phased rollout → full deployment) to minimize risks.
💡 Best Practice: Implement a feedback loop where IT teams validate AI recommendations and continuously improve models.
Step 8: Continuous Learning and Improvement
AIOps is not a one-time setup—it requires continuous monitoring and optimization:
Retrain AI models regularly with new datasets
Refine automation workflows based on performance feedback
Incorporate user feedback to improve accuracy and usability
💡 Best Practice: Schedule quarterly AIOps audits to ensure efficiency and alignment with business goals.
Conclusion
Developing an AIOps platform for enterprises requires a structured, step-by-step approach—from goal setting and data integration to AI model deployment and automation. When implemented correctly, AIOps can enhance IT efficiency, reduce downtime, and enable proactive incident management.
0 notes
Text
Antenna Market Size, Share, Trends, Growth and Competitive Analysis
"Global Antenna Market – Industry Trends and Forecast to 2029
Global Antenna Market, By Antenna Type (External, Internal), Frequency Range (Ultra-High, Very High, High), Technology (MIMO (Multi Input Multi Output), SIMO (Single Input Multi Output), MISO (Multi Input Single Output), SISO (Single Input Single Output)), Application (Cellular Systems, Radar, Wi-Fi Systems, WiMAX, Others), End Use Sector (Networking/ Communications, Consumer Electronics, Military/Defense, Automotive, Industrial, Health/Medical, IoT, 5G, Others) – Industry Trends and Forecast to 2029
Access Full 350 Pages PDF Report @
**Segments**
- **Type** - **Parabolic Dish Antenna** - **Flat Panel Antenna** - **Yagi Antenna** - **Log-Periodic Antenna** - **Horn Antenna** - **Others** - **Frequency** - **High frequency** - **Ultra-high frequency** - **Very high frequency** - **Super high frequency** - **Others** - **Application** - **Telecommunication** - **Consumer Electronics** - **Defense and Military** - **Automotive** - **Broadcasting** - **Others**
Antennas are essential components in various industries, ranging from telecommunications to consumer electronics. In terms of type, the antenna market is segmented into Parabolic Dish Antenna, Flat Panel Antenna, Yagi Antenna, Log-Periodic Antenna, Horn Antenna, and others. Each type serves different purposes based on the requirements of the industry. Additionally, the frequency segment includes high frequency, ultra-high frequency, very high frequency, super high frequency, and other categories based on the signal strength and range needed. Moreover, the application segment covers telecommunications, consumer electronics, defense and military, automotive, broadcasting, and other sectors where antennas are crucial for connectivity and communication purposes.
**Market Players**
- **Comba Telecom Systems Holdings Ltd.** - **Huawei Technologies Co. Ltd.** - **ZTE Corporation** - **CommScope** - **Kathrein SE** - **Laird Connectivity** - **Harada Industry Co. Ltd.** - **Antenna Products Corporation** - **Comprod Inc.** - **MP Antenna** - **Panasonic Corporation** - **Motorola Solutions Inc.** - **Cisco Systems Inc.** - **Cobham PLC** - **Amphenol Corporation** - **ARRIS International plc**
The global antenna market is competitive, with several key playersThe global antenna market is highly competitive, with several key players vying for market share and striving to innovate and stay ahead of the competition. Companies such as Comba Telecom Systems Holdings Ltd., Huawei Technologies Co. Ltd., ZTE Corporation, CommScope, Kathrein SE, and Laird Connectivity are prominent players in the market, known for their cutting-edge technology and quality products. These companies invest heavily in research and development to introduce new and advanced antennas that cater to the evolving needs of different industries. With the increasing demand for connectivity and communication solutions across various sectors, the competition among these market players is fierce, driving them to continuously improve their offerings and expand their market presence globally.
Moreover, companies like Harada Industry Co. Ltd., Antenna Products Corporation, Comprod Inc., MP Antenna, Panasonic Corporation, and Motorola Solutions Inc. also play a significant role in the antenna market, offering a wide range of antennas for different applications. These companies have a strong manufacturing base and distribution network, enabling them to reach a broad customer base and provide solutions tailored to specific industry requirements. Additionally, companies such as Cisco Systems Inc., Cobham PLC, Amphenol Corporation, and ARRIS International plc are key players known for their expertise in providing advanced antenna solutions for telecommunications, defense, consumer electronics, and other sectors.
The market players in the antenna industry are focusing on strategic collaborations, partnerships, and acquisitions to strengthen their market position and expand their product portfolio. By leveraging the latest technologies such as 5G, Internet of Things (IoT), and artificial intelligence (AI), these companies are able to offer innovative antenna solutions that enhance connectivity, coverage, and performance. Furthermore, with the increasing demand for high-speed internet and seamless connectivity, the market players are investing in developing antennas that meet the requirements of next-generation communication networks.
The growing adoption of advanced antenna technologies such as Massive MIMO (Multiple Input Multiple Output) and beamforming is driving the market players to invest in R&D to improve the**Global Antenna Market Analysis**
Antennas play a crucial role in various industries, especially with the rising demand for connectivity and communication solutions. The global antenna market is segmented based on type, frequency, and application, catering to the diverse needs of industries like telecommunications, consumer electronics, defense and military, automotive, and broadcasting. The market is highly competitive, with key players like Comba Telecom Systems Holdings Ltd., Huawei Technologies Co. Ltd., and ZTE Corporation leading the innovation and technology advancements in the antenna industry. These companies invest significantly in R&D to introduce cutting-edge antenna solutions that meet the evolving requirements of different sectors.
Strategic collaborations, partnerships, and acquisitions are common strategies employed by market players to strengthen their market position and expand their product portfolio. By leveraging technologies such as 5G, IoT, and AI, companies aim to offer innovative antenna solutions that enhance connectivity, coverage, and performance in next-generation networks. The adoption of advanced technologies like Massive MIMO and beamforming is also driving investment in R&D to improve antenna capabilities and provide more efficient communication solutions.
The global antenna market is further categorized by antenna type, frequency range, technology, application, and end-use sector, reflecting the diverse uses of antennas across industries. The market trends indicate a growing demand for high-speed internet and seamless connectivity, prompting market players to develop antennas that align with the requirements of modern communication networks. With a focus on technological advancements and product innovation, the antenna market is expected to witness continued growth in the
The report provides insights on the following pointers:
Market Penetration: Comprehensive information on the product portfolios of the top players in the Antenna Market.
Product Development/Innovation: Detailed insights on the upcoming technologies, R&D activities, and product launches in the market.
Competitive Assessment: In-depth assessment of the market strategies, geographic and business segments of the leading players in the market.
Market Development: Comprehensive information about emerging markets. This report analyzes the market for various segments across geographies.
Market Diversification: Exhaustive information about new products, untapped geographies, recent developments, and investments in the Antenna Market.
Highlights of TOC:
Chapter 1: Market overview
Chapter 2: Global Antenna Market
Chapter 3: Regional analysis of the Global Antenna Market industry
Chapter 4: Antenna Market segmentation based on types and applications
Chapter 5: Revenue analysis based on types and applications
Chapter 6: Market share
Chapter 7: Competitive Landscape
Chapter 8: Drivers, Restraints, Challenges, and Opportunities
Chapter 9: Gross Margin and Price Analysis
Objectives of the Report
To carefully analyze and forecast the size of the Antenna market by value and volume.
To estimate the market shares of major segments of the Antenna
To showcase the development of the Antenna market in different parts of the world.
To analyze and study micro-markets in terms of their contributions to the Antenna market, their prospects, and individual growth trends.
To offer precise and useful details about factors affecting the growth of the Antenna
To provide a meticulous assessment of crucial business strategies used by leading companies operating in the Antenna market, which include research and development, collaborations, agreements, partnerships, acquisitions, mergers, new developments, and product launches.
Browse Trending Reports:
Oil Shale Market Cyclin Dependent Kinase Inhibitor Market Agammaglobulinemia Treatment Market Infantile Systemic Hyalinosis Market Continuous Bioprocessing Market Automated Harvesting System Market Capillary Blood Collection Devices Market Automotive Lead Acid Batteries Market 4d Laser Scanner Market Polyurethane Composites Market Interactive Whiteboard Market Botnet Detection Market High Temperature Composite Resin Market Low Profile Additives Market Form Fill Seal Equipment Market Ophthalmic Knives Market Aluminium Nitride Market Tapping Sleeves Market Astaxanthin Market
About Data Bridge Market Research:
Data Bridge set forth itself as an unconventional and neoteric Market research and consulting firm with unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market. Data Bridge endeavors to provide appropriate solutions to the complex business challenges and initiates an effortless decision-making process.
Contact Us:
Data Bridge Market Research
US: +1 614 591 3140
UK: +44 845 154 9652
APAC : +653 1251 975
Email: [email protected]"

0 notes
Text
Snort: Understanding The Network Intrusion Detection & Prevention System

Snort is a powerful and lightweight open-source IDS/IPS that analyses network traffic and records packets in real time. SNORT is a strong open-source Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) that analyzes and logs data packets in real-time network traffic. It uses a rule-based language with methods for anomaly detection, protocol analysis, and signature inspection to find actions that might be harmful. Denial-of-service (DoS) attacks, Distributed DoS (DDoS) attacks, Common Gateway Interface (CGI) attacks, buffer overflows, and stealth port scans are some of the cyber threats that network managers use SNORT to find. SNORT sets up rules that describe bad network behavior, find harmful packets, and send users warnings. SNORT is an open-source solution, which means it is free and can be used by both people and businesses. The SNORT rule language tells the computer what network data to watch and what to do when it finds malicious packets. With this feature, SNORT can spot malicious packets like sniffers and traditional network intrusion detection systems, or it can be used as a full IPS solution that watches network activity, finds threats, and blocks them. Snort Network Intrusion Detection & Prevention System Specifications Specification Description Type IDS/IPS License Open-source Platform Cross-platform Detection Signature Performance High-speed Configuration Flexible Protocols Multiple Alerts Real-time Rules Customizable Community Active Logging Detailed Integration Versatile Updates Regular Analysis Comprehensive Deployment Easy Introducing Snort Martin Roesch created the C-based network intrusion detection system Snort in 1998, and Cisco is currently responsible for maintaining it. Protocol analysis, content matching, OS fingerprinting, real-time traffic monitoring, and packet logging are some of its features. It is both free and open-source. In addition to being deployable over a wide range of Network Intrusion Detection & Prevention Systems, it is extremely customizable. Why Do People Like Snort? A Network Intrusion Detection System (IDS) called Snort is widely used and known as one of the best tools for finding cyber threats in the cybersecurity field. It effectively keeps an eye on network traffic in real-time, carefully checking each packet for payloads that could be dangerous. The fact that Snort can analyze protocols, look for content, and match patterns is a big part of its popularity. It can find many types of threats, like port scans and buffer spills, making it very useful for finding them. Snort is widely used because it is easy to move around and works with many other programs. It works with all major BSD operating systems, Windows, Linux, and many versions of UNIX. Notably, Snort doesn't need the kernel to be recompiled or any extra software or hardware to be installed. It only needs to be installed and run with root capabilities. Built to work like a normal network intrusion detection system, Snort checks network data against rules already set. It then tells system administrators about any suspicious activity so they can fix it. Finally, Snort is a good choice for organizations with limited funds because it is open source and doesn't cost anything. This includes educational institutions, small and medium-sized businesses, and even home users who need an Intrusion Detection and Prevention System (IDPS) solution. How Snort Is Used? Brief Synopsis Companies looking for a flexible Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) to protect their networks from new hazards often embrace Snort. Snort is mainly used for: Real-time network traffic analysis Analyzing protocols Content matching is arranged according to protocol, ports, and content Operating Systems (OS) fingerprinting Interference with platforms Logging and packet sniffing Snort efficiently captures and analyses network traffic as a packet sniffer and logger. In: Track local network traffic on an interface. Save captured packets for troubleshooting on the disc. Real-time network traffic monitoring lets you check every packet for potentially dangerous content. Guidelines and Alerts Based on preset criteria, snort can create alarms for odd packets found in network traffic. This capacity facilitates the identification of network vulnerabilities and their mitigating action. Using the versatile Snort rule language lets consumers: Establish specific guidelines to differentiate regular network behavior from anomalies. Create additional rules to track particular actions and stop possible assaults. Finding attacks Because Snort is flexible and works with many operating systems, it can find many types of network attacks as long as there are rules that match how the attacks behave. Some examples are: DoS and DDoS Attacks These hacks send many fake service requests through the network, which stops things from working. DoS attacks come from a single system, while DDoS attacks are planned by many systems working together. Too Much Buffer Attackers send too much data to a network address, which uses up the system's bandwidth. Spoofing Hackers pretend to be authorized users or systems to get into target networks and do bad things. Common Gateway Interface Hackers can use input validation attacks to exploit common CGI script flaws. Stealth Port Scans Hackers get around firewalls by using stealth port scans to find open ports on the network without making full links. Can Snort Find Attacks That Don't Exist Yet? Yes. Hannes Holm from the Royal Institute of Technology (KTH), Sweden, wrote a study called "Signature Based Intrusion Detection for Zero-Day Attacks: (Not) A Closed Chapter?" that says Snort can find zero-day attacks. The study looked at 356 serious attacks on Snort that used old government rules. It found that Snort can find zero-day exploits about 17% of the time. The average detection rate for known attacks is higher (54%), but Snort can find zero-day flaws at an impressive rate of 8.2%, showing that it can work even against threats that aren't known yet. Snort Installation Steps On Linux wget https://www.snort.org/downloads/snort/snort-2.9.15.tar.gz tar xvzf snort-2.9.15.tar.gz cd snort-2.9.15 ./configure –enable-sourcefire && make && sudo make install On Windows Get the Snort installation from the Snort Download Page. Handle the installer. Different Snort Modes Sniffer Mode: Use./snort -v to output TCP/IP headers or./snort -vd to include IP addresses. Packet Logging: Store packets on the disc under./snort -dev - l./SnortLogs. Network IDS Mode: Activate with ./snort -dev -l ./SnortLogs -h 192.127.1.0/24 -c snort.conf. How does Snort detect an Attack? Snort uses the Misuse Detection Engine BASE to look at real-time network data. It checks both coming and going data packets against signatures in its rule set. The following are some of Snort's most important features for finding intrusions: Watch the traffic on the network: Snort finds malicious packets and setup problems by looking at traffic that has been recorded. Find Strange Things in the Network: Snort rules let network managers tell the difference between normal and strange traffic to spot malicious activity in real time. Packet Sniffing: Snort gathers all data bits sent within a network, which lets you look at traffic in great detail. Set Up Alerts: Snort lets users know when it finds strange or harmful packets, possible uses of security holes, or policy violations based on how it is set up. Create New Standards: Snort lets admins make their own rules, which lets them set criteria for finding new threats like backdoor attacks or certain packet content. Network managers can quickly separate normal, expected internet activity from anything deviating from the norm by applying SNORT principles. SNORT creates notifications to users after real-time analysis of network activity to identify hostile activities. FAQs How is Snort different from other systems that look for intrusions? Snort is special because it is open source, meaning it can be changed and added in many ways. It uses signature-based and anomaly-based detection algorithms to give you a flexible and all-around way to find intrusions. Snort can be used in small networks, right? Yes, Snort is good for small networks because it can identify and stop intrusions well, is scalable, and has features that can be customized. It meets the security needs of smaller networks without needing a lot of resources. What does Snort do with data that is encrypted? Snort has trouble checking encrypted traffic because it can't look at encrypted text directly. To fix this problem, businesses often combine SSL/TLS decryption proxies with Snort. This lets them look at material decrypted for possible security threats. Read the full article
0 notes
Link
0 notes
Text
Harnessing AI for IT Operations: Revolutionizing Efficiency and Reliability
In the dynamic landscape of IT operations, where businesses rely heavily on seamless functioning and optimal performance, Artificial Intelligence (AI) is emerging as a transformative force. AI for IT Operations (AIOps) platforms are revolutionizing how enterprises manage, monitor, and optimize their IT environments. Let's delve into how this technology is reshaping the IT Operations platform market and what it means for businesses worldwide.
𝐆𝐞𝐭 𝐅𝐫𝐞𝐞 𝐏𝐃𝐅 𝐒𝐚𝐦𝐩𝐥𝐞 𝐂𝐨𝐩𝐲 𝐨𝐟 𝐑𝐞𝐩𝐨𝐫𝐭 (𝐈𝐧𝐜𝐥𝐮𝐝𝐢𝐧𝐠 𝐅𝐮𝐥𝐥 𝐓𝐎𝐂, 𝐋𝐢𝐬𝐭 𝐨𝐟 𝐓𝐚𝐛𝐥𝐞𝐬 & 𝐅𝐢𝐠𝐮𝐫𝐞𝐬, 𝐂𝐡𝐚𝐫𝐭)@ https://www.infinitivedataexpert.com/industry-report/artificial-intelligence-for-it-operations-platform-market#sample

The Rise of AIOps Platforms
Traditional IT operations management often involves manual processes, reactive issue resolution, and siloed data analysis. This approach can lead to inefficiencies, delays in problem resolution, and missed opportunities for proactive management. AIOps platforms, powered by AI and machine learning (ML), bring a paradigm shift by automating and enhancing various aspects of IT operations:
Automated Monitoring and Analysis: AIOps platforms aggregate and analyze vast amounts of data from disparate sources in real-time. By leveraging ML algorithms, these platforms can detect anomalies, identify patterns, and predict potential issues before they impact operations.
Root Cause Analysis: One of the significant challenges in IT operations is identifying the root cause of problems amidst complex and interconnected systems. AIOps platforms use advanced analytics to trace issues back to their origin, facilitating quicker resolution and minimizing downtime.
Predictive Insights: By analyzing historical data and real-time metrics, AIOps platforms can provide predictive insights into future performance trends and potential bottlenecks. This proactive approach enables IT teams to preemptively address issues and optimize resource allocation.
Automation of Routine Tasks: Routine IT tasks such as system monitoring, log management, and incident response can be automated through AI-driven workflows. This automation not only reduces manual effort but also frees up IT personnel to focus on more strategic initiatives.
List of Major Market Participants - IBM Corporation, Sumo Logic Inc., Splunk Inc., Evolven Software, AppDynamics (Cisco), ScienceLogic Inc., Broadcom Inc., Zenoss Inc., New Relic Inc., LogicMonitor Inc., Resolve Systems LLC, OpsRamp Inc., Ayehu Software Technologies Ltd., Loom Systems, BigPanda Inc., Dynatrace LLC, CloudFabrix Software Inc., Micro Focus International, Moogsoft Inc., Nexthink S.A.
𝐆𝐞𝐭 𝐅𝐫𝐞𝐞 𝐏𝐃𝐅 𝐒𝐚𝐦𝐩𝐥𝐞 𝐑𝐞𝐩𝐨𝐫𝐭@ https://www.infinitivedataexpert.com/industry-report/artificial-intelligence-for-it-operations-platform-market#sample
Market Segment:
Global Artificial Intelligence for IT Operations Platform Market, By Offering - Platform, Service Global Artificial Intelligence for IT Operations Platform market, By Application - Infrastructure Management, Application Performance Analysis, Real-Time Analytics, Network & Security Management, Others
Market Dynamics and Adoption
The AI for IT Operations platform market is experiencing rapid growth, driven by the increasing complexity of IT environments, the growing volume of data generated, and the demand for operational efficiency. Key factors contributing to the adoption of AIOps platforms include:
Scalability: AIOps platforms can scale to accommodate large and diverse IT infrastructures, making them suitable for enterprises of all sizes.
Integration Capabilities: These platforms integrate seamlessly with existing IT tools and infrastructure, ensuring compatibility and minimal disruption during deployment.
Cost Savings: By streamlining operations, reducing downtime, and optimizing resource utilization, AIOps platforms deliver significant cost savings over time.
Future Outlook
Looking ahead, the future of AIOps holds immense promise. As AI and ML technologies continue to evolve, AIOps platforms will become more sophisticated, capable of handling even greater volumes of data and providing deeper insights. Key trends shaping the future of AIOps include:
Enhanced Cognitive Capabilities: AI algorithms will become more adept at learning from data and making complex decisions autonomously.
Expanded Use Cases: Beyond traditional IT operations, AIOps will find applications in cybersecurity, customer experience management, and more.
Ethical Considerations: As AI adoption grows, addressing ethical concerns such as data privacy, bias mitigation, and algorithmic transparency will become increasingly important.
𝐆𝐞𝐭 𝐅𝐫𝐞𝐞 𝐏𝐃𝐅 𝐒𝐚𝐦𝐩𝐥𝐞 𝐂𝐨𝐩𝐲 𝐨𝐟 𝐑𝐞𝐩𝐨𝐫𝐭 (𝐈𝐧𝐜𝐥𝐮𝐝𝐢𝐧𝐠 𝐅𝐮𝐥𝐥 𝐓𝐎𝐂, 𝐋𝐢𝐬𝐭 𝐨𝐟 𝐓𝐚𝐛𝐥𝐞𝐬 & 𝐅𝐢𝐠𝐮𝐫𝐞𝐬, 𝐂𝐡𝐚𝐫𝐭)@ https://www.infinitivedataexpert.com/industry-report/artificial-intelligence-for-it-operations-platform-market#sample
In conclusion, AI for IT Operations platforms are not just a technological advancement but a strategic imperative for modern businesses seeking to stay competitive in a digitally-driven world. By harnessing the power of AI, organizations can achieve greater operational efficiency, improve reliability, and deliver enhanced user experiences. As the market continues to evolve, embracing AIOps will undoubtedly be a pivotal decision for businesses looking to thrive in the digital age.
For enterprises considering adopting AIOps, staying informed about industry trends, evaluating vendor capabilities, and planning for seamless integration are essential steps towards leveraging this transformative technology effectively. As we move forward, the synergy between AI and IT operations will continue to drive innovation and redefine the future of enterprise IT management.
#AIOps#ITOperations#AIinIT#MachineLearning#ITInfrastructure#DigitalTransformation#PredictiveAnalytics#Automation#DataDriven#EnterpriseIT#ITOps#AIinITOps#DataAnalytics#PredictiveOps#DevOpsAI
0 notes
Text
Global Unified Threat Management Market Forecast and Analysis Report (2023-2032)

The global unified threat management market has grown steadily in recent years. It is expected to grow at a CAGR of 15.2% between 2023 and 2030. The market was valued at USD 4.2 Billion in 2022 and is expected to reach USD 11.3 Billion in 2030.
Unified Threat Management (UTM) Market involves integrated security solutions that combine multiple security functions into a single platform to provide comprehensive protection against various network threats. UTM solutions typically include firewall, antivirus, anti-spyware, anti-spam, network intrusion prevention, and content filtering capabilities. This convergence of security tools into one manageable unit simplifies the security management process, making it particularly attractive for small to medium-sized enterprises that may lack extensive IT security resources.
The market for UTM is driven by the increasing complexity and volume of cyber threats, coupled with the growing need for regulatory compliance across industries. The adoption of cloud-based services and the increasing prevalence of remote work environments have further fueled the demand for robust, scalable security solutions like UTM systems. Additionally, the integration of advanced technologies such as machine learning and artificial intelligence to enhance threat detection and response capabilities is a notable trend within this market. Overall, the UTM market is expanding as businesses seek more streamlined and effective ways to secure their networks against a backdrop of ever-evolving cyber risks.
Unified Threat Management (UTM) systems provide a comprehensive security solution by combining multiple security functions into a single platform.
Here are some key points about Unified Threat Management:
All-in-One Solution: UTM integrates various security features such as firewall, antivirus, anti-spyware, anti-spam, VPN, content filtering, and intrusion detection and prevention systems (IDPS) into one device, simplifying network security infrastructure.
Ease of Management: With multiple security features consolidated into one platform, UTMs simplify the management of network security, making it easier to deploy, manage, and update.
Cost-Effective: UTMs can be more cost-effective than purchasing and maintaining multiple separate security devices. This cost efficiency makes UTMs particularly attractive to small and medium-sized enterprises.
Improved Security Posture: By integrating multiple security measures, UTMs provide a more robust defense against a wide range of cyber threats, enhancing an organization's overall security posture.
Scalability: Many UTM solutions offer scalable options, allowing businesses to expand their security as they grow. This scalability includes both physical expansion and the capability to handle increasing amounts of data and transactions.
Real-Time Updates: UTM systems often come with subscriptions to services that provide real-time updates and definitions for antivirus, anti-spyware, and content filtering, ensuring that the protection is always up to date against the latest threats.
Centralized Reporting: UTMs typically include detailed logging and reporting features that allow for a centralized view of security events and traffic across the network, aiding in compliance and auditing processes.
Regulatory Compliance: UTMs help organizations comply with various industry regulations by providing comprehensive security measures and detailed logs required by regulatory bodies.
Remote Management: Many UTMs offer remote management capabilities, which is beneficial for managing network security across multiple locations or for remote workers.
Cloud Integration: With the increase in cloud adoption, many UTM providers have begun offering cloud-based or hybrid solutions, allowing businesses to leverage cloud computing while maintaining robust security measures.
Key Players-
Barracuda Networks, Inc.
Cisco Systems, Inc.
Check Point Software Technologies Ltd.
SonicWall
Fortinet, Inc.
Huawei Technologies Co., Ltd.
Untangle, Inc.
Juniper Networks, Inc.
Sophos Ltd.
WatchGuard Technologies, Inc.
More About Report- https://www.credenceresearch.com/report/unified-threat-management-market
Segmentation
By Component
Hardware
Software
Virtual
By Service
Consulting
Support & Maintenance
Managed UTM
By Deployment
Cloud
On-premise
By Enterprise Size
Large Enterprise
Small & Medium Enterprise (SME)
Unified Threat Management Market Competitive Analysis-
Competitive Strategies-
Product Innovation: Leading companies in the UTM market are continually innovating to integrate advanced technologies such as artificial intelligence and machine learning to improve threat detection and response capabilities.
Market Expansion: Players are expanding their global presence and targeting emerging markets where the adoption of network security solutions is increasing rapidly.
Customer-Focused Solutions: Companies are focusing on providing solutions that are easy to deploy and manage, with scalable options to cater to businesses of different sizes and with varying security needs.
Strategic Partnerships and Collaborations: Many UTM providers engage in partnerships with technology firms, resellers, and managed service providers to expand their reach and enhance their product offerings.
Pricing and Licensing Flexibility: Competitive pricing and flexible licensing models are used to attract and retain a diverse customer base, from small businesses to large enterprises.
Market Challenges-
Integration Complexities: Integrating UTM systems with existing IT infrastructure can be challenging, especially in organizations with complex network environments.
Evolving Cyber Threats: Rapidly evolving cyber threats require continuous updates and upgrades in UTM solutions, posing a challenge for vendors to keep pace.
Customer Education: Educating potential customers about the benefits of a unified security platform versus traditional, siloed security approaches remains a significant challenge.
Future Outlook-
Cloud-Based UTM: There is an increasing trend towards cloud-based UTM solutions, driven by the growing adoption of cloud computing and the need for remote security management.
Regulatory Compliance: As data protection regulations become stricter, UTM systems that help organizations comply with these regulations will likely see increased demand.
Browse the full report – https://www.credenceresearch.com/report/unified-threat-management-market
Browse Our Blog: https://www.linkedin.com/pulse/unified-threat-management-market-outlook-global-trends-forecast-15vsf
Contact Us:
Phone: +91 6232 49 3207
Email: [email protected]
Website: https://www.credenceresearch.com
0 notes
Text
Cloud Firewall Management Market to See Huge Growth by 2028
Latest released the research study on Global Cloud Firewall Management Market, offers a detailed overview of the factors influencing the global business scope. Cloud Firewall Management Market research report shows the latest market insights, current situation analysis with upcoming trends and breakdown of the products and services. The report provides key statistics on the market status, size, share, growth factors of the Cloud Firewall Management The study covers emerging player’s data, including: competitive landscape, sales, revenue and global market share of top manufacturers are McAfee (Intel) (United States), Hewlett Packard Enterprise (HPE) (United States), Cisco (United States), International Business Machines (IBM) Corporation (United States), AT&T (United States), CheckPoint Software Technologies (Israel), NortonLifeLock(United States), DXC Technology (United States), Lumen(United States), Fortinet(United States), Tufin (United States),
Free Sample Report + All Related Graphs & Charts @: https://www.advancemarketanalytics.com/sample-report/2272-global-cloud-firewall-management-market
Cloud Firewall Management Market Definition:
The process of efficiently managing rules associated with cloud firewall, configuration, logs and alerts of firewalls to build infrastructure having network security is known as cloud firewall management. A cloud firewall filter traffic from sources like the internet, virtual networks, tenants, and from virtual data centre. It block cyber-attacks which are directed at these sources. Cloud-based firewalls management creates a virtual barrier around infrastructure, applications and cloud platforms of the organisation’s internal network. The main objective of cloud firewall management is to track the security events and network activities. This cloud firewall management comprises of software and services through which network security is provided. With the use of proper cloud firewall management, an organization can effectively manage logs with ensuring the integrity and it further improved business continuity. The number of management such as vulnerability management, event management and access management is provided by cloud firewall management with the help of different cloud deployment models. Increasing number of cyberattacks and cybercrimes are creating ample amount of opportunities for cloud firewall management. The different types of cybercrimes like ransom is growing rapidly which leads to business interruptions and financial losses. Thus, organisations are focusing on securing their essential data and financial infrastructure. According to recent study, in 2021, approximately USD 6 trillion damage is predicted due to cybercrime. Hence, it is necessary to work on the network security. Geographically, North America is expected to growth with highest growth rate owing to developed security infrastructure, increased technological developments and strong presence of market players across the region.
Market Trend:
Increasing Technical Advancements Due To Involvement of IoT
Preference for Outsourcing the Firewall Development
Market Drivers:
Rising Number Internal and External of Threats Such As Cybercrimes
Inclination of Organisations towards Providing Extended Security to Its Global Branches Offices Demanding Cloud Firewall Management
Unique Features like Unlimited Storage Capacity, Quick Recovery and Effective Collaboration between Different Branches is Responsible for Increasing Demand
Market Opportunities:
Advancement Associated With Virtualization Next-Generation
Demand from the SMEs Creating Opportunities for Cloud Firewall Management
The Global Cloud Firewall Management Market segments and Market Data Break Down are illuminated below:
by Type (Software-as-a-service firewall (SaaS firewall), Security-as-a-service (SECaaS)), Cloud Deployment Model (Hybrid, Multi cloud, Public Cloud), End Use (Government and Defence, BFSI (Banking, Financial Services and Insurance), Telecom and IT, Energy and Utilities, Healthcare and Life Sciences, Retail and Consumer Packaged Goods, Others), Type of Management (Unified Threat Management, Vulnerability Management, Compliance Management, Identity and Access Management, Managed Intrusion Detection, Others)
Region Included are: North America, Europe, Asia Pacific, Oceania, South America, Middle East & Africa
Country Level Break-Up: United States, Canada, Mexico, Brazil, Argentina, Colombia, Chile, South Africa, Nigeria, Tunisia, Morocco, Germany, United Kingdom (UK), the Netherlands, Spain, Italy, Belgium, Austria, Turkey, Russia, France, Poland, Israel, United Arab Emirates, Qatar, Saudi Arabia, China, Japan, Taiwan, South Korea, Singapore, India, Australia and New Zealand etc.
Enquire for customization in Report @: https://www.advancemarketanalytics.com/enquiry-before-buy/2272-global-cloud-firewall-management-market
Strategic Points Covered in Table of Content of Global Cloud Firewall Management Market:
Chapter 1: Introduction, market driving force product Objective of Study and Research Scope the Cloud Firewall Management market
Chapter 2: Exclusive Summary – the basic information of the Cloud Firewall Management Market.
Chapter 3: Displayingthe Market Dynamics- Drivers, Trends and Challenges of the Cloud Firewall Management
Chapter 4: Presenting the Cloud Firewall Management Market Factor Analysis Porters Five Forces, Supply/Value Chain, PESTEL analysis, Market Entropy, Patent/Trademark Analysis.
Chapter 5: Displaying market size by Type, End User and Region 2015-2020
Chapter 6: Evaluating the leading manufacturers of the Cloud Firewall Management market which consists of its Competitive Landscape, Peer Group Analysis, BCG Matrix & Company Profile
Chapter 7: To evaluate the market by segments, by countries and by manufacturers with revenue share and sales by key countries (2021-2026).
Chapter 8 & 9: Displaying the Appendix, Methodology and Data Source
Finally, Cloud Firewall Management Market is a valuable source of guidance for individuals and companies in decision framework.
Data Sources & Methodology The primary sources involves the industry experts from the Global Cloud Firewall Management Market including the management organizations, processing organizations, analytics service providers of the industry’s value chain. All primary sources were interviewed to gather and authenticate qualitative & quantitative information and determine the future prospects.
In the extensive primary research process undertaken for this study, the primary sources – Postal Surveys, telephone, Online & Face-to-Face Survey were considered to obtain and verify both qualitative and quantitative aspects of this research study. When it comes to secondary sources Company's Annual reports, press Releases, Websites, Investor Presentation, Conference Call transcripts, Webinar, Journals, Regulators, National Customs and Industry Associations were given primary weight-age.
For Early Buyers | Get Up to 20% Discount on This Premium Report: https://www.advancemarketanalytics.com/request-discount/2272-global-cloud-firewall-management-market
What benefits does AMA research study is going to provide?
Latest industry influencing trends and development scenario
Open up New Markets
To Seize powerful market opportunities
Key decision in planning and to further expand market share
Identify Key Business Segments, Market proposition & Gap Analysis
Assisting in allocating marketing investments
Definitively, this report will give you an unmistakable perspective on every single reality of the market without a need to allude to some other research report or an information source. Our report will give all of you the realities about the past, present, and eventual fate of the concerned Market.
Thanks for reading this article; you can also get individual chapter wise section or region wise report version like North America, Europe or Southeast Asia.
Contact Us:
Craig Francis (PR & Marketing Manager) AMA Research & Media LLP Unit No. 429, Parsonage Road Edison, NJ New Jersey USA – 08837
0 notes
Text
Log Analysis using AI/ML for Broadband

Log Analysis using Artificial Intelligence/Machine Learning [AI/ML] for Broadband
Whenever you hear about “Log analysis”, we picture a developer, going through 1000s of lines of logs to figure out a problem. Does it always have to be like this? Our topic of discussion is what can Artificial Intelligence/Machine Learning [AI/ML]do to help us in Log analysis.
Need for Automated Log Analysis
In large-scale systems, the seemingly obvious way of log analysis is not so scalable. A�� broadband network managed by an operator like Comcast, having 100s of Wi-Fi Access Points and Routers/Switches and 4G/5G small cells, from multiple equipment providers, say Commscope, Aruba, or CISCO. Collection of logs at multiple nodes, there are GBs of data created every minute.
The possible issues are hidden, they may not be something as obvious as a crash. It may be a problem that occurred and went away and could not be detected, other than the fact that there were several complaints received by the Network Operators. These systems are developed by multiple developers (100(0)s), so it is difficult to be analyzed them by a single person. They pull out modules from various third parties and make extensive use of the open source. And then the parts of the systems are on continuous upgrade cycles. So there is a clearly established need for automated log analysis in large-scale networks through the use of smart log analysis techniques.
Mapping Log Analysis problem to Artificial Intelligence/Machine Learning [AI/ML] problem
Machine learning sees the problems in two ways:
supervised
unsupervised.
Supervised learning is applicable if we have a labeled data set i.e. input data, where we know the label (or value). With this data, we can train the model. After Training, the model can take the new input and predict the label (or value).
Unsupervised learning means we do not have labeled data sets. The model classifies data into different classes. When the new data arrives, it finds the correlation with the existing classes and puts it into one of those classes.
For log analysis, we are basically looking for anomalies in the log, something that is not normally expected. We may or may not have labeled data sets, and accordingly, we need to pick supervised or unsupervised learning.
Anomaly Detection algorithms. For supervised algorithms, we will have data sets, where each set is labeled as “normal” or “Anomaly”. For unsupervised algorithms, we need to configure the model for two classes only, “Normal” or “Anomaly”.
A combined approach is good for the broadband use case, where both can be used. For clear anomalous behaviour we can use supervised methods. And when creating an exhaustive labeled data set may not be possible, we can fall back to unsupervised.
These algorithms exist already and there are open-source implementations as well. (refer References)
Mapping Logs to Artificial Intelligence/Machine Learning [AI/ML] input
There are many ongoing online logs coming from various nodes. The only way to make a data set is to time-slice them, into smaller log snippets. Using each snippet we have to convert it into a data set.
Now the logs are distributed, coming from switches, routers, SysLogs and Pcaps, and Others. Do we need different models for each kind of log? No. The logs have to be given to a single Model as only then the correlation between different logs can be harnessed.
The logs are unstructured text, can we use (Natural Language Processing) Models to extract data sets from the logs. The answer is again “No”. For NLP models, the text is preprocessed to get features like the number of times a word is repeated, the different words followed by each other, and other features. There are pre-trained models which can do this and have been trained over the entire Wikipedia text! But these can not be used for logs, as logs have technical context and not the natural language.
Since logs have an underlying structure, we can view the log snippets as a series of predefined events. This way we can retain the information in each log. It also helps aggregate different kinds of logs, as we can consider the logs having different sets of events. The model will be trained by understanding based on events that are happening in a given time window and can then detect anomalies.
Constructing Artificial Intelligence/Machine Learning [AI/ML] Training data set from Logs
Artificial Intelligence/Machine Learning [AI/ML] works on vectors/matrices of numbers and additions and multiplications of these numbers. We can not feed these events directly to the model. They need to be converted into numbers. (Gradient Descent and Logistic Regression works with finding derivatives. Deep learning is Matrix multiplications and lots of it. Decision Trees or Random forests partition the data on numbers.)
For computer vision and image processing use cases, these numbers are the RGB value of each pixel in the image. For tabular data, the text is converted into numbers by assigning ordered or unordered series.
One option is to associate each event with an identifier number and give vectors of these identifiers to the model, along with a timestamp. However, synchronizing/aggregating this will be an issue as we will start getting these vectors from each node. Also one event may happen multiple times, in the snippet, so handling of these vectors will become complex.
So a better method is to collate vectors from each node for a given time slice and then go with the count of each kind of event in a master vector.
We explain the approach below in detail. The approach is derived from this popular paper, for more details please refer https://jiemingzhu.github.io/pub/slhe_issre2016.pdf)
1.Log Collection –
In broadband systems, we have multiple sources of logs (SysLog, Air captures, wired captures, Cloud Logs, Network element i.e. switches/Routers/Access Points logs). We need to first be able to gather logs from each of the sources.
We need to make an exhaustive list of all sources as
[S1, S2, S3.. Sn]
2.Event Definition – For each source, we need to come up with predefined event types. In the networking world, broadly event types in the logs, can be defined as follows
Protocol message
Errors/Alerts
Each Type is one event type
Layer
Management
Each Type is one event type
Control
Each Type is one event type
Data
Each Type is one Event type
State Change
Error Alerts
Each Type is one event type
Module
Each Critical Log Template is an event type
Each State Transitions is an event type
Errors/Alerts
Each type of Error/Alert is one event type each Leaf node corresponds to a different event
With this analysis, for each source, we come up with a list of events, as follows
[S1E1, S1E2, S1E3,.. S1Em,
S2E1, S2E2, S2E3,.. S2En,
… ,
SnE1, SnE2, SnE3,.. SnEp]
3.Log to Event conversion – Each line of the time series log will have a constant part and a variable part. The constant part is what we are interested in. Variable parts like IP addresses, source and destination are variable and need to be ignored. We need to parse logs for the constant parts, to check if the log has any event or not, and record only the event. Then the log snippet taken over a window of time will start looking like something like this for a source.
[T1, E2
T2, Nil
T3, E2
T4, E4]
4.Frequency transform – Invert the parsed log to find event frequency. Basically in a given time window how many times an event happened. So if the window goes from Time 1 to Time 4.

Going for multiple time slices it will look like this

The window can be fixed with timer intervals. These can be non-overlapping or sliding. Sliding windows can give better results, but maybe more computationally intensive.
For balancing computation load, it is advisable to do edge compute i.e. derive the Event Count Matrix separately from each source.
5.Event Frequency Matrix – Once the event count matrix is being fetched from each source, they should be all combined at a central place, before being fed to the ML world.
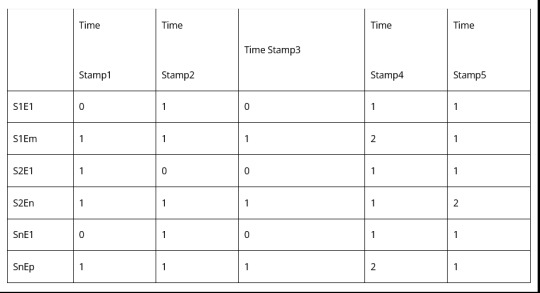
Highlighted Part is the final Matrix that is an input to the ML system. Each window is fed with a timestamp. So it becomes a time series input vector. Set of these vectors will make a data set. So finally now we have the data set for log analysis!
Resources
[1] AI/ML Theory Machine Learning by Stanford University
[2] Applied AI/ML Tutorial Deep Learning For Coders—36 hours of lessons for free
[3] Log Analysis AI/ML Research Paper Experience Report: System Log Analysis for Anomaly Detection
[4] LogPai/Loganaly (logpai/loglizer: A log analysis toolkit for automated anomaly detection [ISSRE’16])
[5] AICoE/LAD (AICoE/log-anomaly-detector: Log Anomaly Detection – Machine learning to detect abnormal events logs)
Request a Call
0 notes
Text
Digital Forensics Market to Witness Excellent Revenue Growth Owing to Rapid Increase in Demand
Latest business intelligence report released on Global Digital Forensics Market, covers different industry elements and growth inclinations that helps in predicting market forecast. The report allows complete assessment of current and future scenario scaling top to bottom investigation about the market size, % share of key and emerging segment, major development, and technological advancements. Also, the statistical survey elaborates detailed commentary on changing market dynamics that includes market growth drivers, roadblocks and challenges, future opportunities, and influencing trends to better understand Digital Forensics market outlook. List of Key Players Profiled in the study includes market overview, business strategies, financials, Development activities, Market Share and SWOT analysis are IBM Corporation (United States)
AccessData Group LLC (United States)
FireEye Inc. (United States)
Paraben Corporation (United States)
CISCO (United States)
Guidance Software Inc. (United States)
LogRhythm Inc. (United States)
Micro Systemation AB (Sweden)
NUIX (Australia)
Binary Intelligence LLC (United States)
Digital Forensics is forensic science, which includes identification, recovery, investigation, validation, and presentation of facts regarding digital evidence found on computers. Investigation in digital forensics is carried out in three stages which include exhibit acquisition, investigation, and analysis along with reporting of crime. This is a very big solution for security issues Key Market Trends: Increase Demand of Mobile Devices Forensics and Digital Image Forensics Opportunities: Strong Opportunity In This Field, Which Will Continue To Expand As New Types Of Digital Data Are Created By New Devices Logging People’s Activity Or Electronic Crime. Market Growth Drivers: Increase in Trends of Iot and Cloud Based Solutions
Rise in Use of Multiple Channel
The Global Digital Forensics Market segments and Market Data Break Down by Type (Hardware, Software, Services), Application (Computers, Laptops, Smartphones, Thumb Drives, External Hardware Drives), Services (Computer Forensics, Network Forensics, Mobile Devices Forensics, Digital Image Forensics, Digital Video/Audio Forensics, Memory Forensics)
Presented By
AMA Research & Media LLP
0 notes
Text
North America Log Management Market Status, Analysis Overview, and Industry Insights 2021-2028
“The log management market in North America is expected to grow from US$ 980.06 million in 2021 to US$ 2,300.55 million by 2028; it is estimated to grow at a CAGR of 13.0% from 2021 to 2028.”
The report provides a detailed assessment of the “North America Log Management Market”. This includes enabling technologies, key trends, market drivers, challenges, standardization, regulatory landscape, deployment models, operator case studies, opportunities, future roadmaps, value chains, ecosystem player profiles, and strategies included. The report also presents a SWOT analysis and forecast for North America Log Management investments during the forecast period.
Get a sample copy of this report:
https://www.businessmarketinsights.com/sample/BMIRE00025380
North America Log Management includes Market Analysis Report Top Companies:
Alert Logic
AT&T Inc
Cisco Systems, Inc.
Datadog
IBM Corporation
LogRhythm, Inc.
ManageEngine
Sematext Group Inc.
SolarWinds Worldwide, LLC
Splunk, Inc.
North America Log Management Market Split by Product Type and Applications:
This report segments the North America Log Management Market on the basis of Types are:
Solutions
Services
On the basis of Application, the North America Log Management Market is segmented into:
IT & TELECOM
BFSI
Healthcare
Retail & Ecommerce
Education
Others
Increasing digitalization and cloud usage and subsequently rising data generated create a lucrative outlook for the advanced persistent threats (APTs). APTs hamper the productivity of businesses and damage the infrastructure of critical information technology (IT) and data of organizations. The intent of APTs is often to steal data than to damage the network. Sectors with high-value information, including defense, manufacturing, finance, and telecom, are the most common targets for APT attacks. Increasing social networking trend is also mainly targeted by APT attackers.Important Features that are under Offering and North America Log Management Market Highlights of the Reports:
– Detailed overview of the North America Log Management Market
– Changes in industry market dynamics
– Detailed market segmentation by type, application, etc.
– Historical, current, and projected market size in terms of quantity and value
– Recent industry trends and developments
– Competition situation in North America Log Management Market
– Key companies and product strategies
– Potential niche segment/region showing promising growth.
Finally, the North America Log Management Market Report is the authoritative source for market research that can dramatically accelerate your business. The report shows economic conditions such as major locales, item values, profits, limits, generation, supply, requirements, market development rates, and numbers.
Research Methodology:
North America Log Management Market report includes the estimation of market size for value (million USD) and volume (M Sqm). Both top-down and bottom-up approaches have been used to estimate and validate the market size of North America Log Management Market, and to estimate the size of various other dependent submarkets in the overall market.
Key players in the market have been identified through secondary research, and their market shares have been determined through primary and secondary research. All percentage shares split, and breakdowns have been determined using secondary sources and verified primary sources.
Click here to buy now:
https://www.businessmarketinsights.com/buy/single/BMIRE00025380
Customization of the Report: This report can be customized as per your needs for additional data for up to 3 companies or countries or 40 analyst hours.
How we have factored the effect of Covid-19 in our report:
All the reports that we list have been tracking the impact of COVID-19 on the market. Both upstream and downstream of the entire supply chain have been accounted for while doing this. Also, where possible, we will provide an additional COVID-19 update supplement/report to the report in Q3, please check with the sales team.
About Us:
Business Market Insights is a market research platform that provides subscription services for industry and company reports. Our research team have extensive professional expertise in domains such as Electronics & Semiconductor; Aerospace & Defense; Automotive & Transportation; Energy & Power; Healthcare; Manufacturing & Construction; Food & Beverages; Chemicals & Materials; and Technology, Media, & Telecommunications.
Contact us:
If you have any questions about this report or would like further information, please contact us:
Contact person: Sameer Joshi
Phone: +16467917070
Email: [email protected]
0 notes
Text
APT41 Targets Taiwanese Government Research Institute with ShadowPad and Cobalt Strike

Cisco Talos researchers have reported a significant cyber attack on a Taiwanese government-affiliated research institute, attributing the breach to the China-linked group APT41 with medium confidence. The campaign began as early as July 2023 and involved deploying advanced malware tools including ShadowPad and Cobalt Strike. Attack Overview and Attribution The researchers identified several key aspects of the attack: - The campaign targeted a Taiwanese government-affiliated research institute - APT41, a group allegedly comprised of Chinese nationals, is believed to be responsible - Attribution is based on overlaps in tactics, techniques, and procedures (TTPs), infrastructure, and malware families exclusive to Chinese APT groups ShadowPad Malware Deployment A central component of the attack was the use of ShadowPad, a sophisticated modular remote access trojan (RAT): - ShadowPad is known to be sold exclusively to Chinese hacking groups - The malware exploited an outdated vulnerable version of Microsoft Office IME binary as a loader - A customized second-stage loader was used to launch the payload - Two distinct iterations of ShadowPad were encountered during the investigation Cobalt Strike and Custom Loaders The attackers also leveraged Cobalt Strike and developed custom loaders to evade detection: - A unique Cobalt Strike loader written in GoLang was used to bypass Windows Defender - The loader was derived from an anti-AV tool called CS-Avoid-Killing, found on GitHub - Simplified Chinese file and directory paths suggest the attackers' proficiency in the language - PowerShell commands were used to execute scripts for running ShadowPad directly in memory and fetching Cobalt Strike from command and control (C2) servers

The Github repository of Cobalt Strike loader. Exploitation of CVE-2018-0824 APT41 demonstrated advanced capabilities by exploiting a known vulnerability: - The group created a custom loader to inject a proof-of-concept for CVE-2018-0824 directly into memory - This remote code execution vulnerability was used to achieve local privilege escalation - A tool called UnmarshalPwn was employed in the exploitation process Attack Methodology and Persistence The attackers employed various techniques to maintain access and avoid detection: - Three hosts in the targeted environment were compromised - Documents were exfiltrated from the network - A web shell was used to maintain persistence and drop additional payloads - The "quser" command was executed to monitor for other logged-on users, allowing the attackers to pause activities if detected - After deploying backdoors, the web shell and guest account used for initial access were deleted Broader Implications and Ongoing Investigations Cisco Talos researchers emphasized the potential for further discoveries: - Analysis of artifacts from this campaign led to the identification of samples and infrastructure potentially used in different campaigns - Sharing these findings could help the cybersecurity community make connections and enhance ongoing investigations - Indicators of Compromise (IoCs) for this campaign have been released on Cisco Talos' GitHub repository This sophisticated cyber attack on a Taiwanese government research institute highlights the ongoing threat posed by advanced persistent threat (APT) groups like APT41. Complex malware such as ShadowPad, combined with custom loaders and exploitation of known vulnerabilities, demonstrates the evolving tactics employed by state-sponsored threat actors. Read the full article
0 notes
Text
#ccnp training#ccnp course#ccnp certification#ccnp#cisco ccie#cisco ccna#cisco certification#cisco ramon#cisco log analysis#cisco training center in pune#cisco training boot camp#cisco systems inc#ccna routing and switching#ccie prep#ccie classes#get ccie#ccie sp#ccie lab training
0 notes
Text
How Do I Locate My Router's IP Address
Lookup final results of the search for IP address 192.168.1.11. The Internet Assigned Numbers Authority ( IANA ) is a international organization that manages IP addresses. It initially defined a kind of IP address referred to as IP version four (IPv4). This kind is a 32-bit number usually expressed as 4 numbers separated by a decimal point — for instance, 192.168.0.1. Each decimal should have a worth amongst and 255, which signifies that the IPv4 technique can accommodate about 4 billion unique addresses.
With NetSpot, you can swiftly and painlessly uncover if the region you are connecting from is covered with a robust Wi-Fi signal coming from your router, and you can find out all neighboring Wi-Fi networks that may be interfering with it. To see this IP address, you can connect to it via a cable or wirelessly. 192.168.l.l is frequently utilised to login to router settings, however it is typo. The appropriate IP address is 192.168.1.1.
Alter the password in Network Security Settings and click Next. Step 1: Connect your Cisco Router to Computer employing RJ45 cable. Out of these, the World wide web Engineering Process Force (IETF) has directed the Web Assigned Numbers Authority (IANA) to reserve 17.9 million addresses for private networks, which are normally utilized for nearby region networks (LANs) in residential, workplace, and enterprise environments.
Offered that the login information are correct, you will enter the router's settings web page and make the desired adjustments from there. To access the Router Admin panel, you have to connect it to your Pc with an RJ45 cable. Once connected, open the browser and variety into the address bar. An IPv6 address consists of a series of eight numbers, each and every quantity becoming 4 digits long. Unlike the IPv4 address that is expressed in decimal numbers, an IPv6 address is expressed in hexadecimal numbers.
Properly, your Pc is showing a routable IP address as properly as default gateway so it would seem your router isn't performing significantly of something. To access the RT-N12D1 settings, reconnect to the wireless network and use the updated IP address and port quantity. If you would like to make use of a certain router behind your ISP's router, you have two possibilities: alter your default IP address or keep the current configuration. Nonetheless, if you want to use a router behind your ISP's box, it is not necessary to have the router mode enabled on the existing configuration.
When you want to reach a location in the genuine globe, you ask for its address and put it in your GPS. When you want to attain a destination on the world wide web, you also ask for its address, and you type it into the URL bar of your preferred web browser. Some new Routers have auto setup mode. They permit customers to configure it but if the user doesn't want to Setup a new Router then they automatically setup it for the user. They uncover Default Router Login IP address and Password for you.
These private IPs total about 17.9 million distinct addresses, all reserved for use on private networks. This is why a router's private IP does not require to be unique. The router then assigns a private IP address to each and every device in its network, whether it's a small residence network or an enterprise-level organization. Each device inside the network can connect to one more device in the network utilizing this private IP.
To find your router's IP number, appear subsequent to "Default Gateway" (listed last). Step 1: First of all, connect the Netgear router with your Windows Pc and then open Browser and sort 192.168.1.1 > Enter. Examine whether the LAN wire is properly connected to your router and your computer or not. IP Address 192.168.1.1 belongs to a Private or Reserved variety, most of the IP Address details are not obtainable.
Locate the pinhole reset button. Usually instances this on the back or underside of the router. With the router plugged in, press and hold the reset button for 30 seconds. Soon after releasing the button, wait for the router to energy on, and attempt to login to the router again. IANA has reserved some IP addresses for private networks. We talked about earlier that a private IP address is exclusive within the network it's connected to but the exact same IP address can be assigned to a technique on a various private network.
At the C:> prompt, kind ipconfig and press Enter. In case you do not don't forget the particulars you can use the following strategy to access the IP address. If you cannot access 192.168.0.1, you ought to very first restart your router and attempt once again. If that does not aid, you may want to erase your router's settings. Most routers have a special button just for this objective that you can press with a pointy tool, such as a pen. Simply press and hold the button for at least 10 seconds or till you see the LEDs begin flashing.
Now that you know what the 192.168.1.1 IP address is and how to log into routers that use it as the default gateway, you can explore its admin panel and modify numerous various settings to make your network safer and faster. Now you know a lot of things about IP Addresses, Private and Public IP Address, How to Access 192.168.1.1, What If You Can't Access 192.168.1.1, How To Modify 192.168.1.1 Router Password, Reset Router Settings, How To Locate The Router IP Address and a lot much more.
Now a modest window will appear and ask for username and password. If you don't know the username and password, then you can not log in to the router. Enter username and password and its carried out. You can see the Router homepage exactly where you can see some alternatives for Wireless Settings and Advanced Settings. If your connection issues maintain persisting, you ought to verify that you are in range of your router. NetSpot , an simple-to-use computer software tool for wireless network assessment, scanning, surveys, and Wi-Fi coverage and overall performance analysis, is the best way how to do just that.
1 note
·
View note
Text
192.168.0.1 Admin Login, Password, And IP
Lookup final results of the search for IP address 192.168.1.11. If the IP address 192.168.1.11 is not your router IP you can retrieve the router IP with the Ipconfig command (only Windows, for Mac & Linux use ifconfig). 192.168.1.11 is an IP address in the variety 192.168.1.1 - 192.168.1.255. A really typical default IP address for a router or a modem is 192.168.0.1 — you type this in a browser and you are accessing the router's or modem's interface to make the adjustments you want.
With NetSpot, you can quickly and painlessly find if the location you're connecting from is covered with a robust Wi-Fi signal coming from your router, and you can learn all neighboring Wi-Fi networks that may be interfering with it. To see this IP address, you can connect to it through a cable or wirelessly. 192.168.l.l is frequently used to login to router settings, even so it is typo. The appropriate IP address is 192.168.1.1.
Now a tiny window will seem and ask for username and password. If you do not know the username and password, then you can not log in to the router. Enter username and password and its accomplished. You can see the Router homepage where you can see some alternatives for Wireless Settings and Sophisticated Settings. If your connection troubles maintain persisting, you must confirm that you happen to be in variety of your router. NetSpot , an effortless-to-use software tool for wireless network assessment, scanning, surveys, and Wi-Fi coverage and efficiency analysis, is the greatest way how to do just that.
Step three. Click the Network & Internet” selection. Step 5. Choose how you are connected to your router. If you are hardwired to your router decide on Ethernet. If you are connected to your router by means of WiFi pick Wi-Fi. Please post back right here with the final results of the test and the info on precisely exactly where your Computer network cable connects. But in most cases, the default IP Address for Modems and Routers is 192.168.0.1. Now you also need to Enter Default username and password in order to access its admin web page. The default username and password are diverse for a distinct manufacturer. Right here we are going to share all the attainable Default Username and Password for 192.168.01 IP address.
A public IP address is the IP address assigned to devices that are connected to the web. This address is assigned by your ISP and no other technique on the net can have the identical address. When you connect to the web, you grow to be element of a considerably bigger network that any individual can connect to. Your public IP is usually visible unless you choose to hide it with a VPN service.
You will see the IP address subsequent to IPv4 Default gateway. In some instances, you may possibly locate it not possible to access your router on the 192.168.0.1 IP address even though you know for certain the address is correct. The IP address 192.168.0.1 is one particular of 17.9 million private addresses, and it is utilized as the default router IP address for certain routers, such as some models from Cisco, D-Hyperlink, LevelOne, Linksys, and many other folks.
Nicely, your Computer is showing a routable IP address as effectively as default gateway so it would seem your router is not undertaking considerably of something. To access the RT-N12D1 settings, reconnect to the wireless network and use the updated IP address and port number. If you would like to make use of a certain router behind your ISP's router, you have two options: modify your default IP address or maintain the current configuration. However, if you want to use a router behind your ISP's box, it is not necessary to have the router mode enabled on the existing configuration.
These are commons IP addresses that modems and routers use presently. If you are unable to connect to your modem or wireless router by means of 192.168.1.1, make positive you are connected to it. If everything is right, use the method I described above to discover out the default IP address of your router. In many instances, Web Service Providers (ISPs) set up routers to use an internal network addressing scheme other than 192.168.1.1. To discover out what the default IP address is for a router, use the IPCONFIG command on a pc that is connected to the router by means of a wireless or wired connection.
Your router is a gateway to your network, and you must do whatever you can to defend it from intruders. Whilst it may possibly be hassle-free to stick with the default password, carrying out so compromises your safety and tends to make it a lot less complicated for cybercriminals to infiltrate your network and steal your private details. Equipped with the info from this report, you ought to be able to secure your router without any main difficulties.
There may be some folks in the planet who wouldn't know what an IP address is? To sum what is an IP address, an IP address, or basically an IP,” is a exclusive address that identifies a device on the Internet or a local network. It enables a technique to be recognized by other systems connected by way of the World wide web protocol. There are two major sorts of IP address formats used these days which are the private IP address or IPv4 and the public IP address or IPv6. So let's jump straight into the differences in between the two.
In contrast to us, a pc or smartphone can easily locate the default IP address of your modem or wireless router and then connect to it. You are inside the admin panel and can alter any settings now. Unplug the router, wait a couple of minutes, and then plug it back in. Wait until all the lights on the front of the router have turned on or are blinking prior to attempting to connect once again. Some routers sometimes want a restart right after a power outage, due to improper startup whilst the ISP's own gear was down.
Wait an additional 30 seconds Right after releasing the Reset button for the router to fully reset and energy back on. You must be in a position to inform that the router has completed booting up by the state of its LED indicator lights. Step four: Enter Default username and password (admin-admin) if you haven't changed. Or Enter your username and password. Of course, it is not just routers that can use the 192.168..254 IP address. All electronic devices that can connect to a neighborhood network can identify themselves to other people with the 192.168..254 IP address, which includes webcams, laptops, servers, individual computers, sensible TVs, repeaters, or modems.
Why? Due to the fact 192.168.0.1 is employed in a private IPv4 network address as the router gateway. While other IP addresses could be utilized as nicely, as you can see above, 192.168.0.1 is by far the most typical default router IP address. All routers are accessible through the browser. If your routers IP address is 192.168.1.11, kind in your browser. You will see a login page. Most frequently employed usernames and passwords are: "admin", "1234" or "none". Please refer to your route documentation.
For the security of your network, it really is essential to have a powerful password Never just rely on the default 1. To change your password, login as detailed above and search for the admin tab. Here you will find the choice to alter your password. It will prompt you to sort in the password twice for security motives. To adjust the password of the router, first go to sophisticated settings and from there you should pick an admin password. Then click change it and Save Settings and then it is done. Pressing the reset button of the router for 20 seconds will reset each the username and password to the default ones.
1 note
·
View note
Text
Cisco CCNA Security 210-260 Certification Exam Details
Cisco 210-260 certifications are globally accepted and add significant value to your IT professional. The certification offers you a serious knowledge of each of the workings with the network models and also the devices that are utilized from it. NWexam.com is proud to offer for you the ideal Cisco Exam Guides.
The Cisco 210-260 Exam is challenging, and thorough preparation is important for achievement. This cert guide was created to enable you to plan the CCNA Security certification exam. Its content has an in depth list of the individuals covered around the Professional exam. The following tips for your IINS might help make suggestions with the study process for the certification.
To have Implementing Cisco Network Security certification, you need to pass IINS 210-260 exam. This exam is produced remembering the input of pros in the market and reveals how Cisco products are found in organizations around the globe. 210-260 Implementing Cisco Network Security Exam Summary
? Exam Name: Implementing Cisco Network Security ? Exam Code: 210-260 ? Exam Price: $300 (USD) ? Duration: 90 mins ? Number of Questions: 60-70 ? Passing Score: Variable (750-850 / 1000 Approx.) 210-260 Exam Guide: ? How I pass Cisco 400-201 Certification in first attempt? ? How to arrange for 400-201 exam on CCIE Supplier Topics covered in the CCNA Security 210-260 Exam [1]. Security Concepts (12%)
1 Common security principles a) Describe confidentiality, integrity, availability (CIA) b) Describe SIEM technology c) Identify common security terms d) Identify common network security zones 2 Common security threats a) Identify common network attacks b) Describe social engineering c) Identify malware d) Classify the vectors of internet data loss/exfiltration 3 Cryptography concepts a) Describe key exchange b) Describe hash algorithm c) Assess symmetric and asymmetric encryption d) Describe digital signatures, certificates, and PKI 4 Describe network topologies a) Campus area network (CAN) b) Cloud, wide area network (WAN) c) Data center d) Small office/home office (SOHO) e) Network to protect an on-line environment
[2]. Secure Access (14%) 1 Secure management a) Compare in-band and out-of band b) Configure secure network management c) Configure and verify secure access through SNMP v3 using an ACL d) Configure and verify security for NTP e) Use SCP for file transfer 2 AAA concepts a) Describe RADIUS and TACACS+ technologies b) Configure administrative access on a Cisco router using TACACS+ c) Verify connectivity on a Cisco router to a TACACS+ server d) Explain the combination of Active Directory with AAA e) Describe authentication and authorization using ACS and ISE 3 802.1X authentication a) Identify the functions 802.1X components 4 BYOD a) Describe the BYOD architecture framework b) Describe the function of mobile phone management (MDM)
[3]. VPN (17%)
1 VPN concepts a) Describe IPsec protocols and delivery modes (IKE, ESP, AH, tunnel mode, transport mode) b) Describe hairpinning, split tunneling, always-on, NAT traversal 2 Remote access VPN a) Implement basic clientless SSL VPN using ASDM b) Verify clientless connection c) Implement basic AnyConnect SSL VPN using ASDM d) Verify AnyConnect connection e) Identify endpoint posture assessment 3 Site-to-site VPN a) Implement an IPsec site-to-site VPN with pre-shared key authentication on Cisco routers and ASA firewalls b) Verify an IPsec site-to-site VPN [4]. Secure Routing and Switching (18%)
1 Security on Cisco routers a) Configure multiple privilege levels b) Configure Cisco IOS role-based CLI access c) Implement Cisco IOS resilient configuration 2 Securing routing protocols a) Implement routing update authentication on OSPF 3 Securing the control plane a) Explain the function of control plane policing 4 Common Layer 2 attacks a) Describe STP attacks b) Describe ARP spoofing c) Describe MAC spoofing d) Describe CAM table (MAC address table) overflows e) Describe CDP/LLDP reconnaissance f) Describe VLAN hopping g) Describe DHCP spoofing 5 Mitigation procedures a) Implement DHCP snooping b) Implement Dynamic ARP Inspection c) Implement port security d) Describe BPDU guard, root guard, loop guard e) Verify mitigation procedures 6 VLAN security a) Describe the protection implications of the PVLAN b) Describe the security implications of your native VLAN

[5]. Cisco Firewall Technologies (18%)
1 Describe operational strengths and weaknesses of the different firewall technologies a) Proxy firewalls b) Application firewall c) Personal firewall 2 Compare stateful vs. stateless firewalls a) Operations b) Function of hawaii table 3 Implement NAT on Cisco ASA 9.x a) Static b) Dynamic c) PAT d) Policy NAT e) Verify NAT operations 4 Implement zone-based firewall a) Zone to zone b) Self zone 5 Firewall features on the Cisco Adaptive Security Appliance (ASA) 9.x a) Configure ASA access management b) Configure security access policies c) Configure Cisco ASA interface security levels d) Configure default Cisco Modular Policy Framework (MPF) e) Describe modes of deployment (routed firewall, transparent firewall) f) Describe types of implementing high availability g) Describe security contexts h) Describe firewall services
[6]. IPS (9%)
1 Describe IPS deployment considerations a) Network-based IPS vs. host-based IPS b) Modes of deployment (inline, promiscuous - SPAN, tap) c) Placement (positioning with the IPS inside the network) d) False positives, false negatives, true positives, true negatives 2 Describe IPS technologies a) Rules/signatures b) Detection/signature engines c) Trigger actions/responses (drop, reset, block, alert, monitor/log, shun) d) Blacklist (static and dynamic) [7]. Content and Endpoint Security (12%)
1 Describe mitigation technology for email-based threats a) SPAM filtering, anti-malware filtering, DLP, blacklisting, email encryption 2 Describe mitigation technology for web-based threats a) Local and cloud-based web proxies b) Blacklisting, URL filtering, malware scanning, URL categorization, web application filtering, TLS/SSL decryption 3 Describe mitigation technology for endpoint threats a) Anti-virus/anti-malware b) Personal firewall/HIPS c) Hardware/software encryption of local data
What type of questions is on the Cisco 210-260 exams? ? Single answer multiple choice ? Multiple answer multiple choice ? Drag and Drop (DND) ? Router Simulation ? Testlet CCNA Security 210-260 Practice Exam Questions. Grab an awareness from these Cisco 210-260 sample questions and boost your 210-260 exam preparation towards attaining an Implementing Cisco Network Security Certification. Answering these sample questions is likely to make informed about the types of questions you can anticipate for the actual exam. Doing practice with CCNA Security IINS questions and answers ahead of the exam wherever possible is the key to passing the Cisco 210-260 certification exam.
210-260 Implementing Cisco Network Security Sample Questions:-
01. Which type of traffic inspection uses pattern matching? a) Signature-based inspection b) Statistical anomaly detection c) Protocol verification d) Policy-based inspection Answer: a
02. Which from the following authentication mechanisms can be used with SNMP version 3? (Choose two) a) AES b) MD5 c) 3DES d) SHA Answer: b, d
03. Is there a most typical type of spoofing? a) Application spoofing b) Service spoofing c) DHCP spoofing d) Ip spoofing e) MAC address spoofing Answer: d 04. Which option mitigates VLAN Hopping and Double-tagging VLAN Hopping Attacks? a) Ensuring that the native VLAN in the trunk ports differs from the native VLAN in the user ports b) Making sure that the native VLAN with the trunk ports is the same as the native VLAN from the user ports c) Setting a corner port to “off.” d) Enabling auto trunking negotiations. Answer: a
05. The kind of attack is prevented if you configure Secure Shell (SSH)? a) DoS session spoofing b) Man-in-the-middle attack c) Dictionary attack d) Buffer overflow Answer: b
06. Which in the following is not part of an IKE Phase 2 process? a) Main mode b) Specifying a hash (HMAC) c) Running DH (PFS) d) Negotiating the transform set to utilize Answer: a
07. What are three key features of URL filtering? (Choose three) a) Predefined URL categories b) Malware protection c) Custom URL categories d) Dynamic content analysis Answer: a, c, d 08. What sort of VPN technologies are apt to be employed in a site-to-site VPN? a) SSL b) TLS c) HTTPS d) IPsec Answer: d
09. Which two statements are true of the present threatscape? (Choose two) a) We now have marketplace is the only industry that is certainly exempt from attack. b) The threat landscape is actually evolving. c) Due to recent improvements in security technology, password attacks not play a significant role in the threatscape. d) It is so complex that it must be impossible to catalog in its entirety. Answer: b, d
10. Which three statements are true about firewalls? (Choose three) a) If your system in a security zone is compromised, a firewall can help offer the attack within that zone. b) A firewall can prevent undesired access to a network security zone. c) Modern firewalls give you a complete network security solution. d) Firewalls typically will protect you between and within network security zones. e) A firewall can introduce a performance bottleneck. Answer: a, b, e
For more information about CCNA Security (210-260 IINS) go to see this useful web portal.
1 note
·
View note