#bypass internet filters
Explore tagged Tumblr posts
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
A sexy, skinny defeat device for your HP ink cartridge
Animals keep evolving into crabs; it's a process called "carcinisation" and it's pretty weird. Crabs just turn out to be extremely evolutionarily fit for our current environment:
https://www.scientificamerican.com/article/why-do-animals-keep-evolving-into-crabs/
By the same token, all kinds of business keep evolving into something like a printer company. It turns out that in this enshittified, poorly regulated, rentier-friendly world, the parasitic, inkjet business model is extremely adaptive. Printerinisation is everywhere.
All that stuff you hate about your car? Trapping you into using their mechanics, spying on you, planned obsolescence? All lifted from the inkjet printer business model:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
That GE fridge that won't make ice or dispense water unless you spend $50 for a proprietary charcoal filter instead of using a $10 generic? Pure printerism:
https://pluralistic.net/2020/06/12/digital-feudalism/#filtergate
The software update to your Sonos speakers that makes them half as useful and takes away your right to play your stored music, forcing you to buy streaming music subscriptions? Straight out of the HP playbook:
https://www.wired.com/story/sonos-admits-its-recent-app-update-was-a-colossal-mistake/
But as printerinized as all these gadgets are, none can quite attain the level of high enshittification that the OG inkjet bastards attain on a daily basis. In the world championships of effortlessly authentic fuckery, no one can lay a glove on the sociopathic monsters of HP.
For example: when HP wanted to soften us all up for a new world of "subscription ink" (where you have to pre-pay every month for a certain number of pages' worth of printing, which your printer enforces by spying on you and ratting you out to HP over the internet), they offered a "lifetime subscription" plan. With this "lifetime" plan, you paid just once and your HP printer would print out 15 pages a month for so long as you owned your printer, with HP shipping you new ink every time you ran low.
Well, eventually, HP got bored of not making you pay rent on your own fucking printer, so they just turned that plan off. Yeah, it was a lifetime plan, but the "lifetime" in question was the lifetime of HP's patience for not fucking you over, and that patience has the longevity of a mayfly:
https://pluralistic.net/2020/11/06/horrible-products/#inkwars
It would take many pages to list all of HP's sins here. This is a company that ships printers with half-full ink cartridges and charges more than the printer cost to buy a replacement set. The company that won't let you print a black-and-white page if you're out of yellow ink. The company that won't let you scan or send a fax if you're out of any of your ink.
They make you "recalibrate" your printer or "clean your heads" by forcing you to print sheets of ink-dense paper. They also refuse to let you use your ink cartridges after they "expire."
HP raised the price of ink to over $10,000 per gallon, then went to war against third-party ink cartridge makers, cartridge remanufacturers, and cartridge refillers. They added "security chips" to their cartridges whose job was to watch the ink levels in your cartridge and, when they dip below a certain level (long before the cartridge is actually empty), declare the cartridge to be dry and permanently out of use.
Even if you refill that cartridge, it will still declare itself to be empty to your printer, which will therefore refuse to print.
Third party ink companies have options here. One thing they could do is reverse-engineer the security chip, and make compatible ones that say, "Actually, I'm full." The problem with this is that laws like Section 1201 of the Digital Millennium Copyright Act (DMCA) potentially makes this into a felony punishable by a five-year prison sentence and a $500k fine, for a first offense.
DMCA 1201 bans bypassing "an effective means of access control" to a copyrighted work. So if HP writes a copyrighted "I'm empty" program for its security chip and then adds some kind of access restriction to prevent you from dumping and reverse-engineering that program, you can end up a felon, thanks to the DMCA.
Another countermove is to harvest security chips out of dead cartridges that have been sent overseas as e-waste (one consequence of HP's $10,000/gallon ink racket is that it generates mountains of immortal, toxic e-waste that mostly ends up poisoning poor countries in the global south). These can be integrated into new cartridges, or remanufactured ones.
In practice, ink companies do all of this and more, and total normie HP printer owners go to extremely improbable lengths to find third party ink cartridges and figure out how to use them. It turns out that even people who find technology tinkering intimidating or confusing or dull can be motivated to learn and practice a lot of esoteric tech stuff as an alternative to paying $10,000/gallon for colored water.
HP has lots of countermoves for this. One truly unhinged piece of fuckery is to ask Customs and Border Patrol to block third-party ink cartridges with genuine HP security chips that have been pried loose from e-waste shipments. HP claims that these are "counterfeits" (because they were removed and re-used without permission), even though they came out of real HP cartridges, and CBP takes them at their word, seizing shipments.
Even sleazier: HP pushes out fake security updates to its printers. You get a message telling you there's an urgent security update, you click OK, and your printer shows you a downloading/installing progress bar and reboots itself. As far as you can tell, nothing has changed. But these aren't "security" updates, they're updates that block third-party ink, and HP has designed them not to kick in for several months. That way, HP owners who get tricked into installing this downgrade don't raise hell online and warn everyone else until they've installed it too, and it's too late:
https://www.eff.org/deeplinks/2020/11/ink-stained-wretches-battle-soul-digital-freedom-taking-place-inside-your-printer
This is the infectious pathogen business model: one reason covid spread so quickly was that people were infectious before they developed symptoms. That meant that the virus could spread before the spreader knew they had it. By adding a long fuse to its logic bomb, HP greatly increases the spread of its malware.
But life finds a way. $10,000/gallon ink is an irresistible target for tinkerers, security researchers and competitors. Necessity may be the mother of invention, but the true parent of jaw-dropping ingenuity is callous, sadistic greed. That's why America's army of prisoners are the source of so many of the most beautiful and exciting forms of innovation seen today:
https://pluralistic.net/2021/06/09/king-rat/#mother-of-invention
Despite harsh legal penalties and the vast resources of HP, third-party ink continues to thrive, and every time HP figures out how to block one technique, three even cooler ones pop up.
Last week, Jay Summet published a video tearing down a third-party ink cartridge compatible with an HP 61XL:
https://www.youtube.com/watch?v=h0ya184uaTE
The third-party cartridge has what appears to be a genuine HP security chip, but it is overlaid with a paper-thin, flexible, adhesive-backed circuit board that is skinny enough that the cartridge still fits in an HP printer.
This flexible circuit board has its own little microchip. Summet theorizes that it is designed to pass the "are you a real HP cartridge" challenge pass to the security chip, but to block the followup "are you empty or full?" message. When the printer issues that challenge, the "man in the middle" chip answers, "Oh, I'm definitely full."
In their writeup, Hackaday identifies the chip as "a single IC in a QFN package." This is just so clever and delightful:
https://hackaday.com/2024/09/28/man-in-the-middle-pcb-unlocks-hp-ink-cartridges/
Hackaday also notes that HP CEO Enrique J Lores recently threatened to brick any printer discovered to be using third-party ink:
https://arstechnica.com/gadgets/2024/01/hp-ceo-blocking-third-party-ink-from-printers-fights-viruses/
As William Gibson famously quipped, "the future is here, it's just not evenly distributed." As our enshittification-rich environment drives more and more companies to evolve into rent-seeking enterprises through printerinisation, HP offers us a glimpse of the horrors of the late enshittocene.
It's just as Orwell prophesied: "If you want a picture of the future, imagine a HP installing malware on your printer to force you to spend $10,000/gallon on ink – forever."

Tor Books as just published two new, free LITTLE BROTHER stories: VIGILANT, about creepy surveillance in distance education; and SPILL, about oil pipelines and indigenous landback.


If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/09/30/life-finds-a-way/#ink-stained-wretches

Image: Jay Summet https://www.youtube.com/watch?v=h0ya184uaTE
4K notes
·
View notes
Text
Don't look away.
The hands clasp the sides of my head tightly, preventing me from moving.
Don't look away.
The person they belong to force my gaze onto grisly scenes of death, destruction, torment.
Don't look away.
I stare in horror at all the suffering before me.
Don't look away.
I close my eyes, but the hands' impossibly long fingers force my eyelids back open.
Don't look away.
My eyes begin to water, whether it is because of their being forced open for so long or my heart breaking at all I see I cannot tell.
Don't look away.
Why is this happening? I cry.
Because of reasons you will never be able to understand. Keep watching.
Is there anything I can do to stop it? I ask.
You must inform anyone you come across of this travesty. You must not let them look away either. But the suffering will continue regardless. They are all convinced they are in the right, all fighting for the will of a god that they will never confirm to be real, in fact the same god in wildly different interpretations. All the while, the innocents caught in the crossfire will continue to die, glorified in the disgusting "honor" known as martyrdom.
If there is nothing substantial I can do, I plead, then why are you forcing me to watch?
#the book of jess#decided to change out the ramble tag for the writing tag because this *was* meant more as a kind of freeverse poetry#in a sense#death mention#idk man i'm stressed enough with my own problems i don't need the world's problems nor the guilt-tripping crap#and people who can't be assed to let people post what they want on their own blogs#or attempt to work out what is clearly meant to be metaphor#the unseen person's fingers keeping my eyes held open was symbolic of me trying to filter things that people rework to intentionally bypass#said filters to *make* you see things that you're specifically filtering out#remember when the internet was an escape from reality?#curating your dashboard means nothing when the things that appear on it are purposefully set to bypass your curation#you may notice the ''might delete later'' tag is gone...decided i wouldn't delete this after all#just cuz
0 notes
Note
maia your website doesn’t work in australia methinks:(
my website is blocked by various internet providers, especially ones using classification lists by symantec (i am misclassified by them, but the chances of getting that fixed are pretty low). this can be bypassed (also for other sites filtered by your ISP) by following the setup instructions of a third party DNS server such as cloudflare dns (1.1.1.1) or quad9 dns (9.9.9.9), which is much easier than you might think!
741 notes
·
View notes
Text
Does anyone else get sensory overload from the internet these days? Sites are bypassing adblock, spam email filters aren’t efficient anymore, every little action requires you to download an app or make an account, youtube is sabotaging itself to force you to watch more ads. There’s a wave of minimalism that still has the trappings of maximalism bc menus are unclear or take forever to navigate. I’m too autistic for this level of mass inaccessibility, which means I struggle to find and hold a job since everything relies on modern programs and sites these days.
#actually autistic#I got fired for not checking discord enough (supposedly)#(it was definitely bc I became chronically ill but apparently DISCORD was the last straw)#idk maybe DONT use a gaming chat app for a professional business. imo
117 notes
·
View notes
Note
Cricky- The horny anons are at it again-
⚔️
[RESPONSE: SYSTEM AUTOMATED MESSAGE – UNIT S.E.N-KU_v1.03 UNAVAILABLE]
Incoming message detected: "Cricky—The horny anons are at it again—"
[SYSTEM STATUS:] Unit Status: OFFLINE Cognitive Threading: Terminated Emotional Coolant: Leaked Dignity Core: 404 Not Found User Filtering Protocols: Bypassed by Degeneracy.exe
AUTOMATED RESPONSE: This unit is currently non-operational due to sustained exposure to unsolicited horny discourse. Please redirect all future inquiries to a qualified mental health professional.
If this is an emergency:
Do not call @senku-ishigami-official. He’s already pretending he doesn’t know me. Do not offer comfort. I no longer trust kindness. Do not refer to me as "turbo" anything.
Estimated Reboot Time: When the internet regains shame. (Indefinite.)
[END AUTO-RESPONSE] [BEEPBEEPBEEP.mp3] [transmission noise: quiet weeping in binary]
#offline like my will to exist#science is dead and you killed it#dr stone rp#mecha senku#mecha senku says!#drst#dcst rp#dr stone rp blog#dcst senku#ishigami senku#dcst rp blog#drst rp
9 notes
·
View notes
Note
when you say you use ChatGPT to write gay incest, do you mean the real chatgpt or another chat bot AI? Because I myself was never able to get GPT to write porn for me. Even sfw incest gets flagged. I know that there are some ways to phrase prompts that go around the censoring, but I don't know how to do that. If you know, can you share some of your prompts? Thank you 🩵
Yes, the real ChatGPT! So when I used it maybe a year ago, it was denying me any incestuous themes, even without anything NSFW. Now it easily generates me incestuous stories based on my prompts, I don't know why their politics changed. Even the warning appears only if you ask it to include direct discussion of incest (using the word) and such, in my experience.
BUT as you're asking for porn specifically, I wasn't able to get that either. Slight NSFW is allowed if you use round about words, that's true, but nothing explicit. I'm sorry though, I can't offer you a guide for specifically ChatGPT NSFW, I don't try that often, can only say the basic advice to hint at sexual things without saying them, such as IDK reaches the breaking point/peak, gets excited, dangerous state, etc. I have much more fun bypassing the filter in CharacterAI, which is the art itself. Officially it doesn't allow NSFW just as much, but you can get it to rp very NSFW things with the right skill. If you're interested, you can find guides on the Internet. Obviously wording it in an implicit way is one of the tactics, but my fave tactic is simply saying whatever I want until at least one of the 30 answers shows me something, then it gets easier to continue roleplaying it.
#ah yes the hidden (not hidden at all) perv in me#but tbh on chatgpt most of the things I rp are sfw#a: mine#r: all#chatgpt#AI chatbot#AI roleplay#tw:incest#asks
10 notes
·
View notes
Note
In your latest post about regulus (asking why people like him) someone told you to check the anti regulus tag and you expressed confusion, because you never heard about the tag.
so like...I don't know if you're still confused? Because you have to use "anti (character)" tags when you're posting (character) critical content. People who love (character) can filter the tag out, that way they wouldn't have to see that type of content.
(it's fandom etiquette, also there are anti (ship) tags as well, if you don't like Jegulus or something else)
So when you answered that anon ask about Severus with criticism under only the "Severus Snape" tag without the anti Severus tag, I'm wondering if you realize this was going to come across as attack? Because it's entering Severus fan spaces, bypassing the filter?
Which means Severus fans will respond to you...hence why you're getting attacked?
Did you mean to start the argument? Or was that you not knowing how tags work? It's fine if you didn't know btw, this whole thing is just confusing me.
- 🎀
hey i'm gonna try to be nice here but this is sort of getting on my nerves.
this whole thing is confusing me so much.
i made a post about severus snape. so i tagged severus snape. because severus snape is mentioned in the post. that's how you categorize. if a book talks about cooking, you put it in the cooking section. regardless of favor, that's how you categorize. for example, people write books about thomas jefferson. one book may talk about the good things thomas jefferson did, and another may talk about the bad things thomas jefferson did. regardless of this favor or lack of favor, both books will be categorized by the topic being thomas jefferson. i don't understand why it isn't the same way here?
i love a great many fictional characters, and when i see a critique of them, i read it carefully, and then i either respond to it with my opinion, make my own post discussing my opinion, or i scroll past it. and it's great! i got to see someone else's opinion, and regardless of whether or not i agree with it, i've learned a new perspective on a character i love. why wouldn't people want the same? don't people want to learn everything about their favorite characters? don't people want rich and diverse perspectives on worlds that they adore?
besides, i think the notion that i "asked to be attacked" by posting and tagging snape is simply ridiculous. it's like me saying "i hate bread because it tastes bad and it has a funky texture." and then someone responding with "you are so stupid for hating bread. bread has all of these benefits. you're reductionist and simple for hating bread". like i didn't ask for those insults at all! all i said was that i hated bread! it would be one thing if i said "everyone who likes bread is disgusting and slimy and will never get married". but i didn't say that. i just said that i hated bread.
also if you know me (which you don't, so it is fine), then you know how i feel about censorship. i refuse to engage in censorship of any kind unless it has to do with shielding children from danger. and this is not shielding children from danger. it's having a differing opinion from my fellow man, which is one of the largest stepping stones in the pond of humanity. i refuse to hide my opinion behind an "anti" tag when someone reading it can simply stop reading it. i find the notion of trying to avoid any nuance or anything that pops your ignorant little internet bubble absolutely ridiculous and i refuse to contribute to that culture.
do i like that snape defenders are up my ass and targeting my intelligence and being horrifically rude to me for expressing an opinion? no! i despise it wholeheartedly. but at the same time, it's an engagement, a discourse, a conversation with my fellow man in which i learn more about the world. like for example, i learned that there hasn't been a single snape defender i've talked to about snape who is actually mature and decently kind. and if i had to choose between hiding the post and getting no rude replies or showing the post and getting rude replies but also an interesting perspective on something that can be interpreted in many different ways, then i'll choose the latter every time.
i have thick skin, i can take a bit of internet harassment, though i won't hesitate to complain about it, because again, it is unwarranted!
not to be rude, but i personally don't care what fandom etiquette is. i don't have to do anything. i don't care that everyone else is doing it. i'm going to do things my way, and if people don't like it, they can block me and stay in their bubbles.
#marauders#the marauders#marauders era#marauders fandom#hp marauders#severus snape#because i'm funny like that and i'm just gonna keep tagging it because well#like i said#categorization#fandom#fandom etiquette#is kinda stupid#omg omg who said that
11 notes
·
View notes
Note
ur gifs r always sooo nice and clear thank u for ur zb1 gif services,, i was also wondering if u used specific files or settings as well (i downlaod off youtube so they never quite go as crispy clear nd i would lov to kno the secret)
awh thank you!! it's really sweet of you to say 🥹🥰

useful necessary skill for kpop gifmaking i have found is to become proficient in the art of foraging the internet to find 4k / .ts / etc files. youtube compresses its videos a lot no matter how good your downloading method is, so it's good to avoid it when you can, especially for stages which are kind of crunchy by default and rarely uploaded in 4k. fancam/facecam 4k files are usually okay to use, though.
for this zebe particularly (m!countdown yesterday), i used a file from this person on twitter. they usually upload (some of the stages from) broadcasts every week (then delete them after a week also).
other places i get files are different recorders' discord servers, this website (which i think just collects the files from the first twitter person uploaded a few days after the fact tbh, but it's useful for archival. use an adblocker and a linkvertise bypasser). i also use kpop24hrs and 4sashi, but those are invite-only and/or complicated. (as a sidenote, for mv masters it's often good to look on sharemania).
as for my sharpen settings, i am (usually, i kind of change around all the time. cannot decide) using a modified version of @/sugurugeto's sharpen actions + photoshop's camera raw filter. if youre not familiar, heres a small tutorial about camera raw. if you have an older photoshop you may need to download it yourself from adobe's website or elsewhere as it's an add-on/plugin. for kpop in particular i get a lot of mileage out of the detail/remove noise slider + adjusting whites & highlights
if there's anything specific you want to ask more about please let me know !
#rowan asks#gifmaking#other gifmakers & especially friends n mutuals -#feel free to ask me if youre looking for a specific file. i cant always guarantee anything but.#i understand the struggle lmao#i think i said most of these things in a previous ask on the topic (you can find in the gifmaking tag on this post)#but i tried to be more specific here u.u
3 notes
·
View notes
Text
The Internet Service Providers Association (ISPA)—a trade association representing British ISPs—and the also British body Internet Watch Foundation have criticized Mozilla, developer of the Firefox web browser, for supporting DoH, as they believe that it will undermine web blocking programs in the country, including ISP default filtering of adult content, and mandatory court-ordered filtering of copyright violations. The ISPA nominated Mozilla for its "Internet Villain" award for 2019 (alongside the EU Directive on Copyright in the Digital Single Market, and Donald Trump), "for their proposed approach to introduce DNS-over-HTTPS in such a way as to bypass UK filtering obligations and parental controls, undermining internet safety standards in the UK." Mozilla responded to the allegations by the ISPA, arguing that it would not prevent filtering, and that they were "surprised and disappointed that an industry association for ISPs decided to misrepresent an improvement to decades-old internet infrastructure".[50][51] In response to the criticism, the ISPA apologized and withdrew the nomination.[52][53] Mozilla subsequently stated that DoH will not be used by default in the British market until further discussion with relevant stakeholders, but stated that it "would offer real security benefits to UK citizens".[54]
What is wrong with this country
4 notes
·
View notes
Text
Rockman.EXE and Cyber Security.

When you are a Rockman/Megaman Battle Network fan and you take a college course about networking, you start to notice how broken the internet is in the anime. So just for fun, I want to talk about a few things I learn about network security and how it is interpreted in the Megaman Battle Network anime.
1. Firewalls
What are firewalls? In simple terms, it is a security barrier that is placed between a private network and the public network.
They are configured to monitor and filter networking traffic, hackers go through them by figuring out how they are programed, once they do they can either bypass the security undetected or simply disable the firewall.
Lets take a scene from the movie where Lan sends Megaman into a secretary’s console to destroy a program inside a company’s server.

Megaman is running through the network between the console and the firewall, which protects the private network of the company.

Logically, for Megaman to go through the firewall, he is going to need to use his powers as a Net Navigator (Net Navi) to analyze the firewall at an incredible speed to try to find a way to go through it, right?
WRONG! Battle Network logic says you can just break it with brute force!
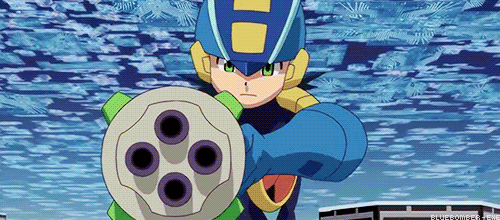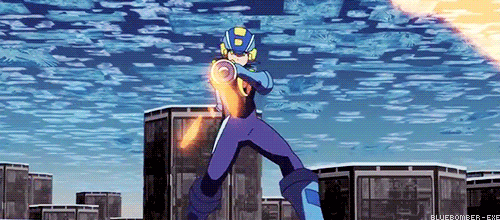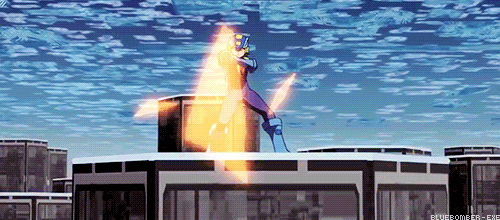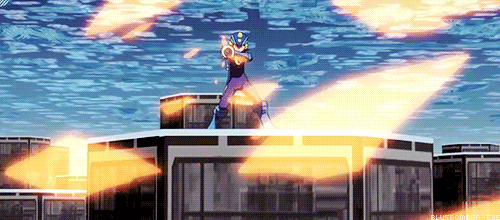

You see the problem?
Does this mean Navis and battle chips are just as destructive to the net as viruses? Because last time I checked, Viruses and malware are the only programs with the ability to destroy networks.
2. Viruses
Viruses are man made, they are programed with a purpose that’s usually to destroy data files. They can also be used to change and manipulate programs, that’s why you can see evil Navis controlling viruses to do specific jobs for them. Viruses can’t replicate on their own without a user interface, so how is this Moloko a baby?!

There was an undubbed episode of Megaman Axess where Rush meets and befriends a baby Moloko virus, which doesn’t make any sense. Yes, Rush is a virus, and it has been established that viruses can communicate with each other, but why does this Moloko have parents? And why was the group of Molokos it separated from was being herded by other viruses like Trumpy? All I’ve seen Molokos do is charge at megaman when they see him, trying to ram him. Why would someone herd them? For the wool? It disappears after you hit it!
And what even is Rush’s purpose anyway? When he first appeared in the anime, he was made to track down Rockman’s frame or structure when they were trying to revive him with the backup data, but now?
All he does is being a crappy character who runs away when things get dangerous, doesn’t act like a dog anymore, and irritates me because he can move between the cyberworld and the real world! He is selfish, lacy, and practically useless, there are several times where Megaman goes missing and Rush is never even called to track him down, so he doesn’t even have that ability anymore.
On a positive note, viruses can be interesting, I found out that there are different types of viruses. For example.
A Stealth virus is a virus that avoids detection from anti virus software, this means it can conceal itself and attack without being spotted, sounds familiar? In this case the anti-virus software would also include Navis.
A retro virus tries to destroy anti-virus programs, I like to think these apply to viruses who specifically target Navis in battle like Canodumbs and Piranahs since they only attack when they detect an enemy in the line of fire.
Armored Viruses are hard to detect or analyze because they have a protective code, These could be Viruses with armors or auras like the Dominerd or even the life virus.
But Phage viruses remind me of these guys because they rewrite programs.

And I guess this one counts too?

Other viruses just act like malware, like the Alpha bug that is more of a worm than a virus, because it can replicate and travel across networks without any human assistance.
Others are obvious like the Pop up virus which is just Rush, and it is supposed to be adware, but just like Rush, it is more annoying than harmful.
In the anime, killereye viruses are used as spyware, there was an episode were Videoman used them to spy on Rockman and make copies of him.

3. Tracing a signal.
Basically, everything you do on the net leaves bread crumps or cookies behind that makes it easy to track a user online, every device have a Mac Address and every network has an IP address, but it takes a special kind of software and advance skills to track down somebody in the real world.
Let’s talk about episode 32 of Stream.
Remember that episode were Megaman followed a revived Shademan to 20 Years in the past and he witnessed a famous hacking incident that was stopped by Colonel?

Aside from the fact that it was 20 years in the past and Megaman is more advance than most of the technology there, there were a few things bothering me.
For starters, why does that computer show a little Colonel doing something to that guy’s hacking program? It’s cute and all, but this is a confusing way to show someone disabling a program, it usually just shows a notification. Or is that how the computer sees colonel, like a little pixel version of him? XD
That hacking program was made to open any cyber lock, it uses three special pillars to disguise the signal so the police wouldn’t be able to track down the address, this means those pillars have some special form of encryption to cover the data to make it untraceable. In the anime’s world, that means it’s invisible, but somehow Megaman can still sense it? And how did Barryl know where the guy was? Did colonel tell him? Or did the viruses he sent to delete colonel revealed his location? Oops.
4. Hard Drives.
To end this post, what are hard drives? They are what your computer uses to store files, so Navis can obviously be stored in a computer as well. The problem is that they are still sentient inside the computer instead of dormant.
The concept of containing a Navi, yes, Navis have their own jail in this universe, doesn’t really make any sense. We know Navis can sleep, but the Navis we see in cages are still active, and if everything is connected to the internet, how can they not escape?
I’m using this scene with Megaman as an example, when he was arrested for being in the wrong place at the wrong time, he was put in a cute little cyber cage.

However, since Megaman is more advance, he wonders if the hard drive of the computer he is stored in is weak against vibrations. What does he mean by that? Physical or cyber vibrations? Does that mean he can control a frequency in that computer’s cyberworld to alter it?
Whatever he did worked, because he left a gap in the cage, but how did he do it without damaging the Hard Drive? The police officer wouldn’t be able to access his files anymore, maybe it was minor file corruption?
And the worst part is that he opened a gateway into the internet, which is still there! I guess Megaman can travel through routers by himself? Maybe that wouldn’t have happen if the officer just disconnected his ethernet cable.
This Network based world is a scary one.
48 notes
·
View notes
Text
2024 is a big election year for the world: More than 50 countries are expected to hold national polls, including large but profoundly damaged democracies such as India, Indonesia, and the United States. Anxieties abound that social media, further weaponized with artificial intelligence, will play a destructive role in these elections.
Pundits have worried that technology might doom democracy since Donald Trump’s election as U.S. president in 2016. It’s true that social media can benefit aspiring autocrats. Populists in particular latch on to social media today as a way to connect directly with people, bypassing restraints on their behavior that political parties would have provided in the pre-internet age. They can also profit from echo chambers, which reinforce the sense that a whole people uniformly supports a populist leader.
Yet social media is not inherently populist. And if populists do well this year, it will not be because there are no tools or strategies to stop them.
To combat populism, democracies need political will. They must not only push for better platform design and regulation but also work to strengthen what some consider a thoroughly old-fashioned institution: political parties that have the capacity to rein in leaders threatening democracy.
Every media revolution in history has caused a moral panic: The printing press was said to have prompted wars of religion; radio gave the world Adolf Hitler; TV enabled McCarthyism. None of these points, still repeated by sophisticated observers today, is completely wrong. But in every case, the technological determinism proved mistaken, as did the assumption that new media would empower irrational masses, always ready to be seduced by demagogues.
At first, social media was greeted with great optimism. In what now feels like a different era, promoters of democracy looked to Twitter (now known as X) and Facebook as tools to help uprisings against autocrats everywhere. But just as the Arab Spring turned to Arab Winter, enthusiasm morphed into pessimism. Panic ensued in 2016, after the double shock of Brexit and Trump’s election. Liberal commentators were quick to identify what they saw as a major culprit of the world’s twin populist disasters: social media and, in particular, echo chambers. Not only did liberals veer from cheering to jeering. They also indulged in nostalgia for a supposedly golden age of responsible gatekeeping by journalists. The wild swings in opinion and the idealization of the past were signs that we have yet to find our bearings when making sense of new media.
Social scientists today know a bit more than they did in 2016: Filter bubbles—or online echo chambers curated by algorithms—exist but are much less common than often assumed; they are not the main cause of polarization, even as they help spread disinformation and propaganda more swiftly; and our offline life is in many ways less diverse than our online existence.
What makes social media unique is that it allows for what can seem like a direct connection between political leaders and potential followers. This is particularly useful for populists, who claim that only they can represent what they often call the “real people.” This implies that all other contenders for power do not represent the people, since, as the usual charge goes, they are corrupt. It also implies that some citizens are not part of the “real people” at all. Think of Trump complaining that his critics are not just wrong about policy but that they are “un-American” or even—as he put it at a Veterans Day rally last year—“vermin.” The point of populism, then, is not just criticism of elites. After all, finding fault with the powerful is often justified. Instead, the point is to exclude people from the people: other politicians at the level of party politics and entire groups—usually already vulnerable ones, such as Muslims in India—at the level of the citizenry.
This seemingly direct connection contributes to the erosion of political parties. Populism is about denying and, eventually, destroying pluralism; well-functioning parties can push back against this and rein in populist political entrepreneurs. Some countries even require parties by law to have internal democratic structures. (The radical right-wing Dutch populist Geert Wilders’s Party for Freedom, which won the most seats in last November’s elections, would not be allowed in those countries because Wilders is the only official member.) Of course, parties unite partisans. But partisans often disagree on how principles they share should translate into policy. There is nothing strange about parties forming legitimate opposition to their leadership, and it has often proved crucial in providing a check on leaders. There’s a reason that populists such as Indian Prime Minister Narendra Modi and Hungarian Prime Minister Viktor Orban run their parties in a highly autocratic fashion.
To be sure, the sense of directness created by social media is an illusion. Social media mediates, after all. Yet the prospect of an unfiltered encounter—however misguided—promises authenticity and a sense of connection that was once available only at exceptional moments, such as at a party meeting or mass rally. The political theorist Nadia Urbinati has suggested the paradoxical-sounding term “direct representation” for this relationship: Anyone standing between citizens and their representatives seems to have disappeared.
The work of getting people to the polls used to be done differently. As the political scientist Paul D. Kenny explains in his book Why Populism?, before the age of social media, mobilization depended on clientelism or a well-organized (put more bluntly: highly bureaucratized) political party. Parties and candidates promised supporters material benefits or bureaucratic favors in exchange for votes. This was costly, and costs would rise steeply if political competition intensified or more power brokers entered the fray. Bureaucratic parties are also expensive to maintain. Party officers have to be paid, even if they can count on volunteer work from idealists who sacrifice their weekends to distribute leaflets or canvass door-to-door.
As Kenny points out, social media cuts the costs of mobilization, especially for celebrity candidates such as Trump, who can draw on their pop culture credit. In the old days, when print and TV were dominant, propaganda feedback loops would have been constructed at great costs by party strategists; today, they are created for free by companies that want to maximize engagement for the sake of profit.
As with influencers, a politician’s online presence requires constant curation, so it is not entirely costless. Trump might have written his own tweets, spelling mistakes and all, but others need to pay tech-savvy teams. Social media might work best for those who already treat parties as instruments for marketing a personality rather than developing policy. Take former Italian Prime Minister Silvio Berlusconi, whose public relations specialists created the Forza Italia party for him in the 1990s and organized it like a fusion of soccer fan club and business enterprise. It is not an accident that Berlusconi joined TikTok before the most recent Italian elections in 2022 (even if the ragazzi he tried to appeal to might have found his performance, as young adults would say, cringe).
The most successful politicians can tap into both forms of support. For instance, Modi, with his enormous cult of personality, has emerged from a mass membership party with a bureaucratic apparatus and can rely on the free labor of partisan foot soldiers. Yet he has also built a following online, where he has been able to present himself as a celebrity above party politics.
Once populist leaders establish the illusion of direct connection, they find it easier to discredit traditional mediators, such as professional journalists, by claiming that they distort politicians’ messages. That can translate into fewer pluralistic debates and fewer opportunities for reporters to ask inconvenient questions. Modi and Orban have not held a genuine press conference in many years; Trump and Israeli Prime Minister Benjamin Netanyahu have declined to join debates before elections. Trump’s refusal to appear onstage with current Republican candidates might seem like a risky gamble: As candidate Ron DeSantis has tried to point out, the front-runner seems afraid to engage the rest of the pack; plus, he’s losing an opportunity to fully display his knack for the memorable put-down. But Trump is following the autocrat’s playbook: to appear above the fray and portray yourself as the unique embodiment of the popular will. Why stoop to the level of the competition if you’ve already told your supporters that everyone else is corrupt or, at the least, completely unrepresentative of their views?
Filter bubbles can therefore help populists sell their core product: the notion of a homogeneous people united behind the populist leader. Algorithmic curation designed to increase engagement with like-minded users amplifies this dynamic. Platforms often suggest what to watch or click on next. Anyone looking up Orban on X, for instance, will likely find an assortment of far-right content. When I recently checked his account, I was shown tweets from the Russian foreign ministry and U.S. presidential candidate and conspiracy theorist Robert F. Kennedy Jr.
To be sure, these online bubbles do not form in a vacuum. In the United States, plenty of people do live in a far-right bubble, without any contact even with center-right outlets such as the Wall Street Journal. This bubble is not the result of Facebook or X, however. As social scientists at Harvard University demonstrated in a 2018 study, its contours were shaped by the enormous success of right-wing cable news and talk radio in the 1990s. Social media just came on top of that infrastructure. If social media itself made for a world where conspiracy theories and hate always reign, we would see the same outcome in every country—but we don’t.
Democracies must overhaul how platforms are governed to make it harder for populists to use them to their advantage. One problem with social media in its current form is that it gives too much power to a few people. Platform power—the control over the means of connecting with others online—is today’s great unchecked power. As the social scientist Michael Seemann has written, platform power stems from the ability to give access to platforms or deny it, either through outright bans or harassment from online trolls.
As Elon Musk’s changes at Twitter have demonstrated, those who control platforms and their underlying machinery can manipulate online discourse. Since he took over the platform in 2022, Musk has not only arbitrarily suspended journalists but also weakened the rules—and reduced staffing—for content moderation. As Musk has replatformed white supremacists and other hatemongers, minorities such as transgender people have become less protected.
In halfway-functioning democracies, capricious oligarchs such as Musk get to govern platforms almost singlehandedly. In countries on the path to autocracy, the state itself can successfully pressure platforms to do its bidding, as India has done with Twitter by forcing it to block politicians, activists, and even the BBC. In outright autocracies, governments are perfecting what the social scientist Margaret Roberts has called friction and flooding. Rather than simply rely on fear created by widespread repression, as traditional dictatorships would, autocracies now “flood” the web with information to distract users and use intentional technical glitches (“friction”) to make it more difficult for citizens to access certain sites. These regimes know that censorship can draw attention to scandalous content; the truly savvy make it disappear. Such techniques are ubiquitous in China, as is surveillance. Aspiring autocrats, including right-wing populists vying for power in democracies, will no doubt try to copy this repertoire.
To be sure, populists cannot be prevented from building their own counter-publics online, just as parties cannot—and should not—be hindered as they bring together followers. Freedom to assemble and associate means that like-minded people have every right to get together with others who share the same commitments. One would not want authorities to start shutting down safe spaces for groups devoted to empowering minorities, for instance, just because they happen to be insufficiently pluralistic. Ideas to combat online homogeneity through injecting viewpoint diversity into online life are well intentioned but impractical. The jurist Cass Sunstein, for example, has suggested a “serendipity button,” which could very well come out as, “Now that you’re looking at the feminist viewpoint, how about clicking on the anti-feminist one?”
A more nuanced view of online political life does not mean that democracies must tolerate the incitement of hatred. Platform design makes a difference: As the political scientist Jennifer Forestal has shown, Reddit, for instance, makes for a more diverse conversation than Facebook Groups. Reddit allows for communities to form but keeps borders between subreddits permeable; it also empowers both moderators and users to stick to rules agreed on by an online community.
Content moderation in particular should be mandatory, as it is in Germany, rather than a luxury that a platform controller such as Musk has the power to dispense. Moderation can be abused, but that is the case with any attempt to control media power. (Libel laws can be—and are—exploited by undemocratic actors, but that does not mean we should dispense with them altogether.) To forestall this, content moderation must be as transparent as possible and subject to proper oversight; the “black boxes” of algorithms should be opened at least to researchers so that they can help policymakers understand how social media platforms are run. This might sound like a pipedream. But the European Union has been pursuing these goals with its recent Digital Services Act and Digital Markets Act, which so far have prevented Facebook from launching its X clone, Threads, in the bloc due to its failure to comply with privacy regulations.
Legislation and education will be important tools for democracies. The business models of social media, which are based on maximizing engagement through offering ever more extremist content, are not beyond political regulation. Democracies should also invest serious resources in teaching media literacy—something that many leaders affirm in the abstract but that, just like civic education, always gets short shrift in the end, since “hard” subjects such as math are seen as more important for global economic competition. Not least, democracies must not treat social media in isolation. If they foster a healthier media landscape, including by reinvigorating local journalism, and regulate political parties, it will be much harder for populists to succeed.
10 notes
·
View notes
Text
What is an ISP Proxy?
An ISP Proxy is a type of proxy hosted in a data center but uses residential IP addresses. Through ISP proxies, you can take advantage of the speed of data center networks while benefiting from the good reputation of residential IPs.
If ISP proxies are a combination of data center and residential proxies in some way, we might want to first define these terms.
Data Center Proxies are designed with simplicity in mind. In most cases, traffic is forwarded from the proxy client to the data center, where the provider redirects your traffic to the destination. As a result, the traffic originates from one of the IP addresses in the data center, meaning multiple users often share the same IP address. For anyone trying to block their use, this can be a red flag. The main advantages of data center proxies are speed and network stability, as data center networks are very stable and offer gigabit speeds.
Residential Proxies rely on the ability of an Internet Service Provider (ISP) to assign IP addresses tied to specific locations. In other words, you get a legitimate and unique IP address that masks your actual location.
With ISP proxies, you get access to these legitimate and unique IP ranges, and hosting them in a data center provides an additional benefit. This makes ISP proxies particularly effective, offering the benefits of both residential proxy services (such as the ability to surf the web from anywhere and the good reputation of residential IPs) and data center proxy services (such as impressive speed).
---
Why Do You Need ISP Proxies?
As you can see, ISP proxies combine the undetectable features of residential proxies with the speed of data center proxies. ISP proxy providers achieve this by working with different ISPs to provide IP addresses instead of the user's IP address. This makes them especially useful for various tasks. Let’s take a look at some of them:
1. Web Scraping
ISP proxies are the best choice for web scraping. They provide fast, undetectable connections that allow you to scrape as much data as needed.
2. Bypass Rate Limiting Displayed as Residential Connections
To prevent attacks like Denial of Service (DoS), most websites and data centers implement rate limiting. This prevents a single IP address from making too many requests or downloading too much data from a single website. The direct consequence is that if you perform web scraping, you are likely to hit these limits.
However, ISP proxies offer a way to bypass rate limits; they use ISP IP addresses to trick the rate limiter code, making it appear as if the requests are coming from a different residential location.
3. Accessing Geo-Restricted Content
Like all proxies, ISP proxies allow you to change your location, making it appear as though you are accessing the internet from another country or region.
4. Bulk Purchasing of Limited Edition Products
E-commerce websites take proactive measures to prevent bots (automated scripts) from purchasing products on their platforms. One common technique is to blacklist IP addresses associated with compulsive purchasing behavior. ISP proxies can help you bypass these restrictions.
---
A Closer Look at ISP Proxies
As mentioned earlier, ISP proxies are hosted in data centers and provide internet service provider IP addresses to the destination. Since ISPs own large pools of public IP addresses, it is nearly impossible to trace the computer using the proxy.
While the main benefit is that they are ideal for web scraping, they also provide other features such as:
- Security: End-to-end encryption, firewalls, web filtering, auditing, and analysis.
- Performance: Web caching and high-speed internet from data centers to destinations.
The uniqueness of ISP proxies is that they are the only proxies that directly deal with ISPs to provide the best anonymous connection. While data center proxies are a good option for providing speed and privacy at a lower price, ISP proxies combine the ability to offer speed and anonymity, giving them a significant advantage.
---
Use Cases
The speed and undetectability of ISP proxies make them the preferred choice for large-scale network operations such as web scraping, SEO monitoring, social media monitoring, and ad verification. Let’s take a deeper look at each use case.
1. Web Scraping
Web scraping is the process of analyzing HTML code to extract the required data from websites.
While the concept is simple, large-scale web scraping requires proxy servers to change your location because many websites display different pages based on your location Additionally, to scrape large volumes of data within a reasonable timeframe, proxies need to be extremely fast. Because of these reasons, ISP proxies are considered the best choice for web scraping.
2. SEO Monitoring
SEO monitoring involves checking the performance of your website, content, articles, etc., in search engine results. However, search engine results are influenced by your location, and the cookies attached to your web browser can affect the displayed results. To bypass these issues, proxies are needed to anonymize your connection or simulate a user from another global location.
Moreover, SEO monitoring involves frequent access to the same webpage, which could lead to your IP address being blacklisted or subjected to rate limits. Therefore, it’s best to use proxies when performing SEO monitoring.
3. Social Media Monitoring
Similar to SEO monitoring, activities in social media monitoring can raise suspicion. As a result, you are forced to comply with the host's rules to avoid being blocked or banned from the platform. For example, managing multiple accounts with the same IP address would certainly raise red flags.
In such cases, ISP proxies can be particularly useful because they fool social network algorithms about your IP address, so you won’t be blocked in the end.
4. Ad Verification
As a marketer, you may want to verify that your advertising partners are delivering on their promises and that the statistics they provide are legitimate.
Ad verification involves scanning the web to check if the ads displayed on various websites match campaign standards, appear on the right sites, and reach the target audience. Since these scans need to cover millions of websites, ISP proxies are ideal to ensure that your ad verification process runs quickly and without being blocked due to excessive use of IP addresses.
---
Conclusion
ISP proxies combine the best of both worlds by offering the speed and stability of data center proxies along with the anonymity and legitimacy of residential proxies. This makes them the perfect tool for activities that require speed, anonymity, and high-volume operations, such as web scraping, SEO monitoring, social media management, and ad verification. By working with ISPs to provide legitimate and unique IP addresses, ISP proxies help users bypass restrictions, access geo-restricted content, and operate more efficiently online.
2 notes
·
View notes
Text
‘The Impact of Social Media Bans on Chinese Users and Global Connections’
MDA20009 Digital Communities
Hello everyone, this is our last post T^T! To my course mates, the semester has come to an end, hope you all had a great holiday! Also, an early 🎄Merry Christmas❄️ to everyone!!!
The quick spread of social media around the world has brought people and communities together. However, some countries maintain restrictive media environments that make it difficult for people to use these platforms freely, with China being a good example. The Chinese government has implemented strict censorship measures to control news, social media and online communication. The ‘Great Firewall’ prevents users from accessing popular platforms such as Facebook, Instagram and Google services. Despite these restrictions, millions of Chinese users have found ways around these barriers, raising significant questions about how censorship affects lives, national identity and global connectivity. This raises important questions about how these restrictions shape individual lives, national identities, and broader networks of global interaction.

Understanding the Great Firewall
According to Britannica, the Great Firewall (also known as the Golden Shield Project) is a key component of China's Golden Shield Project, combines regulatory and technological measures to censor and monitor internet usage (Gisonna, 2024). It employs tools like keyword filtering, bandwidth throttling, and Deep Packet Inspection to block specific content. This system not only restricts foreign platforms but also pressures journalists through dismissals and arrests, fostering self-censorship. As journalist Evan Osnos observed, China's digital links to the world are increasingly deteriorating, emphasizing its isolationist internet policy.
U.S. technology in China

China's restrictive policies make it challenging for U.S. tech companies to compete, with platforms like Facebook, Twitter, and Google blocked. To illustrate, in early 2013, Google withdrew its services after several conflicts with Chinese censorship, and in late 2014, China disabled Google's email service Gmail, which raised concerns at the U.S. State Department (Xu, 2017). Furthermore, in early 2014, Google chairman Eric Schmidt indicated that encryption could facilitate entry into the Chinese market for Google. However, these plans encountered a challenge in March 2014 when the government took action against the social networking app WeChat. The government's decision to crack down on the social networking app WeChat to the deletion of the accounts of several prominent political liberals. Subsequently, new regulations were announced for 'instant messaging tools' on mobile chat apps, such as WeChat, which has over 750 million users and is increasingly seen as a platform for mass dissent that can bypass censors (Xu, 2017). Gmail’s ban and the crackdown on politically liberal accounts on WeChat demonstrated the government’s tightening control.

Social Media Censorship: How does it work?
The Great Firewall of China employs sophisticated methods to enforce internet censorship and block unwanted content (Xu, 2017):
Network Blackholing: A fundamental technique involves maintaining a list of banned IP addresses. If a user attempts to access a prohibited site, the connection is immediately dropped, effectively severing access to restricted content。
Quality of Service (QoS) Filtering: This advanced approach employs deep packet inspection to analyze data traffic and identify connections attempting to bypass censorship through Virtual Private Networks (VPNs). QoS filtering intercepts these connections before they reach their destination, undermining one of the primary tools users rely on to circumvent the firewall.
Domain Name System (DNS) Hijacking: DNS hijacking disrupts the mapping of IP addresses to website names, preventing users from accessing flagged domains. Social media platforms such as Facebook and Twitter are systematically targeted, ensuring that only approved alternatives like Weibo and WeChat dominate the market.
URL Filtering: URL filtering involves the use of proxies to examine requested web addresses for banned keywords. This precise control allows authorities to selectively block pages on platforms like Wikipedia, allowing access to general content while censoring politically sensitive topics.
To learn more about how social media censorship works, here are the views shared by Karoline Kan, a Beijing-based journalist and writer:
The Impact of China's Social Media Censorship
Positive Impacts: Government and Domestic Industry Benefits
From a government perspective, the Great Firewall serves multiple purposes. It blocks access to foreign platforms such as Google, Twitter and Facebook, which were blocked as a result of uprisings such as the 2009 Xinjiang riots. The government is trying to maintain political unity and national security, by limiting access to other forms of governance and lifestyles, Firewalls have also helped Chinese internet companies like Tencent, Baidu, Alibaba and Weibo to grow and succeed without competition from international rivals. This approach to cyber-sovereignty is often seen as a way of protecting national stability (Kannan, A. 2017).
Negative Impacts: Limitations on Innovation and Freedom
From the Chinese citizens perspective, these restrictions pose significant challenges to entrepreneurs, influencers and professionals in accessing global markets and networks, thereby stifling business opportunities and cultural exchanges. Strict government control of online content hinders dissent and creative freedom because users know that surveillance is everywhere. As a result, many people use VPNs to get access to blocked content, but these methods are not foolproof and can be blocked. Some have opted for more advanced tools such as Tor or SSH tunnelling, but these are not for everyone (Xu, 2017).
Despite these challenges, Chinese internet users have found alternative ways to get around the firewall. For instance, tools like Ultrasurf, Psiphon, and Freegate let users set up proxy servers, and microblogging platforms like Weibo have become places for people to talk about things they would normally be banned from discussing. On top of that, over the years, internet users have created a whole range of visual puns, memes, acronyms and slang to get around the censorship, which has transformed online spaces into complex arenas for political and social debate (Xu, 2017).
Global Implications
Censorship not only affects China, but also reshapes global digital dynamics. The fragmentation of the Internet, where users from different countries are often separated into different cyberspaces, limits cross-cultural dialogue and global collaboration. For international brands and content creators, the Chinese market holds great opportunities, but navigating these constraints is often too complex, leading to missed opportunities. On a larger scale, China's digital isolation has exacerbated geopolitical tensions, leading to a growing digital divide between China and the West (Kannan, A. 2017). These tensions complicate international diplomacy and exacerbate the fragmentation of the global digital ecosystem.
Conclusion
In a nutshell, China's 'Great Firewall' is a sophisticated and multifaceted approach to internet censorship that has a significant impact on the online environment for Chinese citizens. While the firewall helps the government keep political stability and protect domestic industries, it also stifles creativity, limits global connectivity, and hinders free expression. Chinese users are creative in finding ways around the restrictions, but these policies contribute to the fragmentation of the global digital landscape and exacerbate geopolitical tensions. Ultimately, censorship policies greatly affect China's digital ecosystem and its interaction with the global community.


Reference:
Gisonna, N. (2024). Great Firewall | History, China, Hong Kong, & Facts. Encyclopedia Britannica. https://www.britannica.com/topic/Great-Firewall
Kannan, A. (2017). Here’s why the Great Firewall of China has benefited the country. Young Post. https://www.scmp.com/yp/discover/your-voice/opinion/article/3066603/heres-why-great-firewall-china-has-benefited-country
Silva, M. (2019).China social media censorship: how does it work? BBC. https://www.bbc.com/news/av/stories-49527899
Xu, B. (2017). Media censorship in China. Council on Foreign Relations. https://www.cfr.org/backgrounder/media-censorship-china
5 notes
·
View notes
Note
WHAT THE FUCK IS HAPPENING -@myerschan
Just relax a bit and enjoy the music, would you? I will be with you in a second~
#ask dr. krueger#twdak#myerschan#albert krueger#dr albert krueger#Taylors Lees unsurpassed technical skills (sending a link to a website)
10 notes
·
View notes
Text
No one under 18 should feel comfortable on the internet because, let's face it, the internet is fundamentally incompatible with such a concept. Thanks to this laser focus on child friendliness, the average minor on the internet has a negative ability to be safe online, because the sites they use claim that they manage children's security for them. This is fundamentally impossible, because no amount of security can protect against an idiot turning it off because they think they don't need it. (Source: I study cybersecurity. Not even most adults can be trusted not to disable their own security systems, not unless you disable their ability to mess with it. Even then, they'll find ways to get around it. This is why my school banned VPNs; not because they bypassed the site filters (though that was a concern), but because they provided a gaping hole in the extensive firewalls that the district maintained by providing a tunnel for unfiltered traffic straight through any attempts at protecting the person using the VPN.)
The way you make the internet "child friendly" is by teaching those children how to be safe online, and making that necessary requires recognizing that there are an insane amount of horrible people online, ensuring they recognize that, and instilling in them an appropriate amount of caution in every interaction. If that means making them feel uncomfortable when online, then so be it.

totally normal and not deranged thing to say
99K notes
·
View notes