#botnet.1
Explore tagged Tumblr posts
Text
Recently there has been a fall in engagement with Palestinian content on tumblr, and for those of us who are helping Palestinians fundraise it is very obvious that this has happened directly after the very public smear campaigns, carried out by some racist users with significant followings.
It seems half the site somehow found it easier to believe in the horseshit about “belgian scam rings” and “russian botnets” in an effort to justify their apathy towards genocide victims, and the other half seems to think that everything is over and that the evil was defeated just because some racist bloggers got run off the site after giving half-hearted apologies that did nothing to mitigate the damage they had done.
THERE ARE PEOPLE STILL IN DIRE NEED OF HELP !! There are people who are still getting death threats from zionists every day and have to stay on this godforsaken website because their gofundmes haven't reached their endgoals yet...
I'm going to keep this brief:
Siraj's ( @siraj2024 ) family including his parents, and his five siblings and their families were displaced during the recent attacks by IOF on deir al balah
This means there are now 23 family members that Siraj is the sole provider for at the moment.
10 of those members are young children.
Siraj's wife, Halima, is having a terrible flareup of eczema and his children are suffering from skin infections and badly need medical attention.
This whole family has been living in unhygienic conditions in 2 tents, packed like sardines during this heatwave, leading to spread of infections between them as well– all during a time where hygiene products have become unaffordable due to the israeli blockade, and when water has become scarce, and kids cant even receive life saving vaccinations during polio epidemic.
All this while everyday siraj risks his life trying to reach out to us from an internet point amidst violence and shelling from the IOF in what once was a “humanitarian safe zone”, even more desperately than before because–
THIS FUNDRAISER IS NOW THE ONLY LIFELINE FOR FIVE FAMILIES INSTEAD OF JUST ONE !!
Currently at $55,614/ $82,000 CAD
TIME IS RUNNING OUT!! We have to get to 60k by thursday i.e WITHIN THE NEXT THREE DAYS!! DONATE AND BOOST
Vetting link #219
If you want additional incentive to donate, pls check out:
Art raffle here (ending in 4 days!!!) - where you get to win this zine as a prize as well for as low as $5 for 1 entry, please dont miss it !!


16K notes
·
View notes
Text
Masterpost of informational posts
All posts are written for everyone, including those with no prior computer science education. If you know how to write an email and have used a computer at least sparingly, you are qualified for understanding these posts. :)
What is a DDoS
What are the types of malware
Vulnerabilities and Exploits (old and somewhat outdated)
Example of how malware can enter your computer
What are botnets and sinkholes
How does passwords work
Guide for getting a safer password
Here are various malware-related posts you may find interesting:
Stuxnet
The North Korean bank heist
5 vintage famous malware
Trickbot the Trickster malware (old and not up to date)
jRAT the spy and controller (old and not up to date)
Evil malware
New to Linux? Here's a quick guide for using the terminal:
Part 1: Introduction
Part 2: Commands
Part 3: Flags
Part 4: Shortcuts
If you have any questions, request for a topic I should write about, or if there is something in these posts that you don't understand, please send me a message/ask and I'll try my best to help you. :)

- unichrome
Bonus: RGB terminal
#datatag#masterpost#malware#cybersecurity#infosec#security#hacking#linux#information#informative#computer science
352 notes
·
View notes
Text
From the beginning | Previously | Coin standings | 60/70 | 37/37
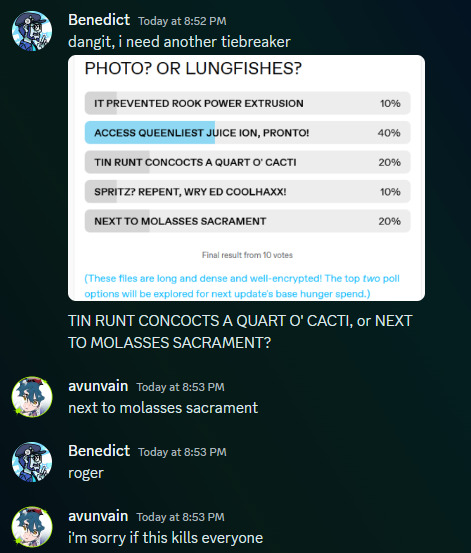
Once again, some kind strangers have left you some supplies. You get another WIFI ACCESS POINT, to replace the one you're about to use, plus another NOBLE BELT TUT BOTNET BULLET (bringing you back up to 4) and a spare SOFTWARE PATCH (bringing you to 2). Wait, 2? Walter says yeah, I've had this one lying around since before I fell down in the sparkling abyss. Adea says well why didn't you SAY so?!
You're both distracted by the priciest purchase yet, though: a BIONIC MINTER BIT COIN MINER. This device- although someone appears to have briefly gnawed on its casing- can be installed anywhere you can find a power outlet, and it'll just spit out free money! Five Coin in the amount of time it takes for you to lose 1 hunger! Or... free minus the electricity it consumes, but it's not like it's your electricity you'd be using in this otherworld. Just leave it to run, then come back later, and you've got a massive pile of cash to spend! And there's power outlets all over this tower, so setting it up should be no problem.
Yep, there's definitely no downsides to using this machine!
So that's very convenient. Satisfied, you dig into ACCESS QUEENLIEST JUICE ION, PRONTO! "JOCQUES NINELITE PROSECUTION CASE".
Jocques Ninelite, apparently, is a local entrepreneur, who recently quit his government job as a HAZARD WICK to found the Ninelite RECEDING NEST, a technology startup. His new company has developed and is distributing EDEN SNAKE, and this has Governor Thinrar extremely mad at him for some reason. This document details dozens of attempts to come up with charges that'll stick to him so he can be arrested and his DECADE'S CHOICES confiscated, but most of them have run aground on insufficient evidence.
There's reams of legal jargon attempting to find obscure laws and bylaws under which selling EDEN SNAKE is illegal, but he apparently knew the law and meticulously avoided any of the various traps- Thinrar's legal advisors don't think they can make any of these stick in court.
Ninelite was found snooping around the scene of an apparent terrorist bombing in the MR. SQUEAK TABLEWARE 15 years ago, and is suspected of having tampered with the crime scene- but no physical evidence exists.
There's a half-finished case for an antitrust suit in here, alleging anticompetitive hiring practices where he attempts to poach talent from other companies. Nothing he's done has technically been illegal, though, but they're working on drafting new legislation that might be able to get him retroactively.
The RECEDING NEST's R&D experiments are under investigation for workplace safety violations, but they haven't been able to get an inspector on-site without alerting them ahead of time- everything they've done under surveillance has been free of occupational safety hazards.
They're even trying to get the corporate campus written up for landscaping code violations. This city has a landscaping code?! What kind of HOA nonsense is this?
You'd think a rich tech CEO would have mountains of dirty laundry, but a concerted effort by the local government has been totally unable to pin anything on him, which is odd. No one's record is this clean unless someone's put effort into cleaning it. How has he been covering his tracks?

The NEXT TO MOLASSES SACRAMENT CORONAMELT TAX ASSESSMENT reveals a similar battle involving Thinrar's legal team trying to pin something on a local business owner. This time, though, it's looking a lot less flimsy. RANDOM SEED, owner of the mountainside casino-resort MONTE CARLO, is very plainly guilty of dozens of counts of felony tax evasion, and HAZARD WICK specialist ONE-TIME PAD has volunteered to go retrieve the last pieces of evidence needed to bring him down.
...The emails between Thinrar and his legal team, though, reveal there's more going on here. Apparently, none of this tax evasion is new- rather, it's been tolerated for decades as part of some kind of under-the-table deal with the casino. Not even tolerated, exactly- it'd just be redundant to pay taxes when RANDOM SEED has been paying such humongous bribes to Thinrar in exchange for exemption from the city's gambling laws.
Somehow, MONTE CARLO has been producing more Coin than it could possibly be extracting from the pockets of desperate gamblers, and it's been keeping the city's municipal budget (and Thinrar's gubernatorial campaign) afloat for years. They're only prosecuting him now because the money is starting to dry up, and they think they can finally get better election odds by making a show of rooting out corruption. (Y'know, rather than by taking kickbacks from that same corruption.) Most of these emails are discussing how to prevent retaliation, and prosecute the case without exposing their own illegal dealings.
These files are like something out of an Ayn Rand novel- corrupt bureaucracy trying to keep down poor innocent captains of industry. The naked corruption on display is pretty flabbergasting- is it all like this?
You've been at this a while- do you want to keep digging, or has your governorship's REIGN PEAKED and you'd like to go somewhere else?
Continued | 60/70 | 36/36
#lost in hearts#if you continue decrypting files i'll just take 2 hunger and give you all three remaining#the bit coin miner notably produces Coin directly rather than giving it to a player to spend#so what controls how it's spent? a question that probably doesn't matter‚ i bet.
9 notes
·
View notes
Text
About three years ago, some of Google’s security engineers came to company attorneys with a gigantic mess.
The security team had discovered that Google unwittingly was enabling the spread of malicious software known as Glupteba. The malware had corrupted more than 1 million Windows computers, turning them into vehicles to mine cryptocurrency and spy on users. By hijacking Google accounts, purchasing Google ads to lure in users, and misusing Google cloud tools, the hackers behind the operation were on their way to infecting even more computers.
Tech giants such as Google long have had a playbook for destroying botnets like Glupteba. They call up fellow companies and US authorities and together coordinate a massive takedown operation. Sometimes, the cops file criminal charges. But this time around, Google’s legal team recommended an approach that the company hadn’t pursued in years: Sue the hackers for money.
The eventual lawsuit against two Russian men and a dozen unnamed individuals allegedly behind Glupteba would be the first of a run of at least eight cases that Google has filed against various hackers and scammers, adding to a sporadic few filings in the past. The tactic, which Google calls affirmative litigation, is meant to scare off would-be fraudsters and generate public awareness about scams. Now, for the first time, Google is opening up about this strategy.
Leaders of Google’s security and legal teams tell WIRED they believe going after people in court has paid off. Google hasn’t yet lost a case; it has collected almost all of the more than $2 million that it has won through the legal process, and forced hundreds of companies or websites to shut down. The awards are trivial to Google and its parent Alphabet, a $2 trillion company, but can be devastating for the defendants.
“We’re disrupting bad actors and deterring future activity, because it’s clear that the consequences and the costs are high,” says Chester Day, lead of the three-person “litigation advance” team at Google that’s focused on taking people to court. Google, he adds, is “making it clear that we’re willing to invest our resources into taking action to protect our users.”
Google blog posts and similar content about the lawsuits and the underlying scams have drawn more than 1 billion views, according to the company. Google representatives say that the awareness increases vigilance among consumers and shrinks the pool of vulnerable targets. “Educating people about how these crimes work may be the best thing we can do to stop the crime,” says Harold Chun, director of Google’s security legal team.
Several Big Tech companies have pursued affirmative litigation, though not necessarily under that name and with varying strategies. Microsoft has filed more than two dozen lawsuits since 2008 with a focus on securing court permission to dismantle botnets and other hacking tools. Amazon has been a prolific complainant since 2018, filing at least 42 cases over counterfeit products, 38 for reviews fraud, three for copyright abuse, and, recently, two for bogus product returns. Amazon has been filing so many counterfeit cases, in fact, that the federal court in western Washington assigned three magistrate judges to focus on them.
Since 2019, Meta has filed at least seven counterfeiting or data theft cases, with settlements or default judgments in four so far, including one in which it won nearly $300,000 in damages. Like Meta, Apple has sued Israeli spyware developer NSO Group for alleged hacking. (NSO is fighting the lawsuits. Trials are scheduled for next year.)
Some attorneys who’ve studied how the private sector uses litigation to enforce the law are skeptical about the payoff for the plaintiffs. David Noll, a Rutgers University law professor and author of a forthcoming book on state-supported private enforcement, Vigilante Nation, says it’s difficult to imagine that companies could bring the volume of cases needed to significantly stop abuse. “The fact that there is a small chance you might be named in a suit isn’t really going to deter you,” he says.
Noll believes the big risk is that Google and other tech companies could be burdening the court system with cases that ultimately secure some favorable headlines but do less to make the internet safer than the companies could achieve through investing in better antifraud measures.
Still, of the six outside legal experts who spoke to WIRED, all of them say that overall Google deserves credit for complementing the work of underfunded government agencies that are struggling to rein in online abuse. At an estimated hundreds of thousands of dollars per case, it’s a low-risk endeavor for the tech giant, former prosecutors say.
“Reliable and regular enforcement when folks step outside the law brings us closer to a society where less of us are harmed,” says Kathleen Morris, resident scholar of law at UC Berkeley’s Institute of Governmental Studies. “This is healthy and robust collaboration on law enforcement by the public and private sectors.”
Google’s general counsel, Halimah DeLaine Prado, tells WIRED she wants to send a message to other companies that the corporate legal department can do more than be the team that says “no” to wild ideas. “Legal can be a proactive protector,” she says.
Marketing Scams
DeLaine Prado says that from its earliest days, Google has considered pursuing litigation against people abusing its platforms and intellectual property. But the first case she and other leaders within Google recall filing was in 2015. Google accused Local Lighthouse, a California marketing company, of placing robocalls to dupe small businesses into paying to improve their ranking in search results. Google alleged trademark infringement, unfair competition, and false advertising. As part of a settlement, Lighthouse stopped the problematic calls.
Since then, Google has filed complaints against five similar allegedly scammy marketers, with three of them ending in settlements so far. A Florida business and its owners agreed to pay Google $850,000, and a Los Angeles man who allegedly posted 14,000 fake reviews on Google Maps agreed to stop. Terms of the third deal, with an Illinois company, were not disclosed in court files, but Google spokesperson José Castañeda says it involved a seven-figure payment to Google.
Castañeda says Google has donated all the money it has collected to recipients such as the Better Business Bureau Institute, the National Consumers League, Partnership to End Addiction, Cybercrime Support Network, and various US chambers of commerce.
Another genre of cases has targeted individuals submitting false copyright complaints to Google to get content removed from the company’s services. A man in Omaha, Nebraska, whom Google accused of falsely claiming ownership of YouTube videos to extort money from their real owners, agreed to pay $25,000 to Google. Two individuals in Vietnam sued by Google never responded—a common issue.
In 2022, Google won default judgment against an individual in Cameroon who never responded to charges that he was using Gmail to scam people into paying for fake puppies, including a $700 basset hound. After the lawsuit, complaints about the scammer dried up, according to Google.
But legal experts say the most fascinating cases of Google’s affirmative litigation are four that it filed against alleged computer hackers. The suits emerged after months of investigation into Glupteba.
Security engineers at Google realized that eradicating Glupteba through the typical approach of taking down associated servers would be difficult. The hackers behind it had designed a backup system involving a blockchain that enabled Glupteba to resurrect itself and keep pilfering away.
That’s in part why Google’s attorneys suggested suing. Chun, the security legal director, had pursued cases against botnets as a federal prosecutor. “I thought this would be something good to do from a civil angle for a company as well,” he says. “Law enforcement agencies have limits on what they can do. And Google has a large voice and the litigation capacity.”
Chun and other attorneys cautioned their bosses that the hackers might use the lawsuit to reverse engineer Google’s investigation methods and make Glupteba more evasive and resilient. But ultimately, DeLaine Prado, who has final say over lawsuits, signed off. Chun says his former colleagues from the government applauded the complaint.
Google sued Dmitry Starovikov and Alexander Filippov, alleging that they were the Russia-based masterminds behind Glupteba after linking websites associated with the virus to Google accounts in their name. The search giant accused the duo (and unknown co-conspirators) of violating the Racketeer Influenced and Corrupt Organizations Act (RICO), the Computer Fraud and Abuse Act, and the Electronic Communications Privacy Act. The lawsuit also alleged a trademark law violation for hiding Glupteba in a tool that claimed to download videos from YouTube.
Google argued that it had suffered substantial harm, having never received payment for ads it had sold to the hackers, who allegedly were using fraudulent credit cards. Users also had their experiences with Google services degraded, putting them at risk and impairing the value of the company’s brand, according to the lawsuit.
In court papers, Starovikov and Filippov stated they learned of the lawsuit only through friends and then decided to hire a New York attorney, Igor Litvak, to fight on their behalf. The defendants initially offered innocent explanations for their software related to Glupteba and said that their projects had not targeted the US market. At one point, they countersued Google for $10 million, and at another, they allegedly demanded $1 million each to hand over the keys to shut down the botnet. They eventually denied the allegations against them.
Following an ordeal over whether the defendants could obtain Russian passports, sit for depositions in Europe, and turn over work files, Google’s attorneys and Litvak traded accusations of lying. In 2022, US district judge Denise Cote sided with Google. She found in a 48-page ruling that the defendants “intentionally withheld information” and “misrepresented their willingness and ability” to disclose it to “avoid liability and further profit” from Glupteba. “The record here is sufficient to find a willful attempt to defraud the Court,” Cote wrote.
Cote sanctioned Litvak, and he agreed to pay Google $250,000 in total through 2027 to settle. The jurist also ordered Starovikov and Filippov to pay nearly $526,000 combined to cover Google’s attorneys fees. Castañeda says Google has received payment from all three.
Litvak tells WIRED that he still disagrees with the judge's findings and that Russia’s strained relationship with the US may have weighed on whom the judge trusted. “It’s telling that after I filed a motion to reconsider, pointing out serious issues with the court’s decision, the court went back on its original decision and referred [the] case to mediation, which ended with … me not having to admit to doing anything wrong,” he says in an email.
Google’s Castañeda says the case achieved the intended effect: The Russian hackers stopped misusing Google services and shut down their marketplace for stolen logins, while the number of Glupteba-infected computers fell 78 percent.
Not every case delivers measurable results. Defendants in Google’s other three hacking cases haven’t responded to the accusations. That led to Google last year winning default judgment against three individuals in Pakistan accused of infecting more than 672,000 computers by masquerading malware as downloads of Google’s Chrome browser. Unopposed victories are also expected in the remaining cases, including one in which overseas app developers allegedly stole money through bogus investment apps and are being sued for violating YouTube Community Guidelines.
Royal Hansen, Google’s vice president for privacy, safety, and security engineering, says lawsuits that don’t result in defendants paying up or agreeing to stop the alleged misuse still can make alleged perpetrators’ lives more difficult. Google uses the rulings as evidence to persuade businesses such as banks and cloud providers to cut off the defendants. Other hackers might not want to work with them knowing they have been outed. Defendants also could be more cautious about crossing international borders and becoming newly subject to scrutiny from local authorities. “That’s a win as well,” Hansen says.
More to Come
These days, Google’s small litigation advance team meets about twice a week with other units across the company to discuss potential lawsuits. They weigh whether a case could set a helpful precedent to give extra teeth to Google’s policies or draw awareness to an emerging threat.
Team leader Day says that as Google has honed its process, filing cases has become more affordable. That should lead to more lawsuits each year, including some for the first time potentially filed outside the US or representing specific users who have been harmed, he says.
The tech giants' ever-sprawling empires leave no shortage of novel cases to pursue. Google’s sibling company Waymo recently adopted the affirmative litigation approach and sued two people who allegedly smashed and slashed its self-driving taxis. Microsoft, meanwhile, is weighing cases against people using generative AI technology for malicious or fraudulent purposes, says Steven Masada, assistant general counsel of the company’s Digital Crimes Unit.
The questions remain whether the increasing cadence of litigation has left cybercriminals any bit deterred and whether a broader range of internet companies will go on the legal offense.
Erin Bernstein, who runs the California office of Bradley Bernstein Sands, a law firm that helps governments pursue civil lawsuits, says she recently pitched a handful of companies across industries on doing their own affirmative litigation. Though none have accepted her offer, she’s optimistic. “It will be a growing area,” Bernstein says.
But Google’s DeLaine Prado hopes affirmative litigation eventually slows. “In a perfect world, this work would disappear over time if it’s successful,” she says. “I actually want to make sure that our success kind of makes us almost obsolete, at least as it relates to this type of work.”
10 notes
·
View notes
Text

#cyberpunk#detailed#futuristic#moody#gritty#urban#decay#reflective#high-tech#dystopia#atmospheric#digital art#cyberpunk 2077
10 notes
·
View notes
Text
FBI joint operation takes down massive Chinese botnet

Source: https://cyberscoop.com/fbi-operation-china-botnet-flax-typhoon/
More info:
https://media.defense.gov/2024/Sep/18/2003547016/-1/-1/0/CSA-PRC-LINKED-ACTORS-BOTNET.PDF
https://blog.lumen.com/derailing-the-raptor-train/
4 notes
·
View notes
Text
So, Anonymous Sudan, the group of probably Russian hackers whose intended goal is division in the West, is the group attacking Ao3 at the moment. They’ve issued a $30,000 dollar ransom demand, which is stupid because 1) the OTW isn’t gonna pay that, and 2) the OTW can’t pay that.
Ao3 and the OTW are run by donations. They don’t have the money to pay this even if they wanted to, and all indications are they’re not inclined to give money to Anonymous Sudan that they’ll just use to buy more additions to their botnets and bring down more websites
19 notes
·
View notes
Text
This day in history

Tonight (December 5), I'm at Flyleaf Books in Chapel Hill, NC, with my new solarpunk novel The Lost Cause, which 350.org's Bill McKibben called "The first great YIMBY novel: perceptive, scientifically sound, and extraordinarily hopeful."

#20yrsago Walt Disney’s FBI files https://memex.craphound.com/2003/12/06/walt-disneys-fbi-files/
#20yrsago Ska-anthem about duct tape https://web.archive.org/web/20031209020640/http://www.ducktapeclub.com/contests/roll/lyrics.asp?entryid=131
#15yrsago Britain’s “Great Firewall” set to restrict access to Wikipedia https://en.wikinews.org/wiki/British_ISPs_restrict_access_to_Wikipedia_amid_child_pornography_allegations
#15yrsago Workers in Argentina taking over dead factories and running them democratically https://www.newstatesman.com/long-reads/2007/08/argentina-workers-movement
#10yrsago https://memex.craphound.com/2013/12/06/what-nelson-mandelas-life-tells-us-about-the-legitimacy-of-democratic-nations/
#10yrsago Medieval kids’ birch-bark doodles https://erikkwakkel.tumblr.com/post/67681966023/medieval-kids-doodles-on-birch-bark-heres
#10yrsago Botnet of 20,000 point-of-sale machines https://arstechnica.com/information-technology/2013/12/credit-card-fraud-comes-of-age-with-first-known-point-of-sale-botnet/
#5yrsago Jamie Dimon is getting fed up with the protesters who “occupy” him everywhere he goes https://www.bloomberg.com/news/articles/2018-12-03/wherever-dimon-goes-activists-turn-his-speeches-into-spectacles
#5yrsago Wells Fargo blames “computer glitch” for its improper foreclosure on 545 homes https://www.cbsnews.com/news/wells-fargo-loan-modification-error-homeowners-who-went-into-foreclosure-seek-answers/
#5yrsago The third annual AI Now report: 10 more ways to make AI safe for human flourishing https://web.archive.org/web/20181206184028/https://ainowinstitute.org/AI_Now_2018_Report.pdf
#5yrsago Europe’s biggest sports leagues and movie studios disavow #Article13, say it will give #BigTech even more control https://www.eff.org/deeplinks/2018/12/letter-eu-european-film-companies-and-sports-leagues-disavow-article-13-say-it
#5yrsago On January 1, America gets its public domain back: join us at the Internet Archive on Jan 25 to celebrate https://creativecommons.org/2018/12/05/join-us-for-a-grand-re-opening-of-the-public-domain/


It's EFF's Power Up Your Donation Week: this week, donations to the Electronic Frontier Foundation are matched 1:1, meaning your money goes twice as far. I've worked with EFF for 22 years now and I have always been - and remain - a major donor, because I've seen firsthand how effective, responsible and brilliant this organization is. Please join me in helping EFF continue its work!
8 notes
·
View notes
Note
sometimes i get so mad about online advertising being so lawless compared to other mediums (ex. television ads occupying specific spots in programming or a small fraction of the screen while online ads can sprawl wherever the hell they want And bog down computer performance) i find myself wishing for someone to enact legislation leading to their regulation, but how likely of a possibility do you think that actually is?
it depends tbh. we do have related stuff like CCPA and GDPR (obligatory meme that I have saved on my phone:)

...so it's not impossible for further laws/regulations to crop up down the line. my main thoughts here are that (1) adtech changes so rapidly that I think any specific legislation is almost certainly doomed to become obsolete before long (compounded further by the fact that most lawmakers barely seem to understand the internet, let alone a fucking RTB supply chain lol), (2) enforcement would be a nightmare considering there are literally several hundred billion bid requests generated EVERY SINGLE DAY (googled this stat to make sure I wasn't misremembering and got another dr. fou link lol. can't escape this guy) and (3) believe it or not, the online advertising industry is largely self-governing... or at least tries to be.
an organization called the IAB (interactive advertising bureau) sets a ton of standards around not only the logistics of buying and selling ads (they are, for example, the creators of the OpenRTB protocol for real-time auctions), but also the quality of the ads and ad space being sold. there are tons of initiatives they've proposed that have widespread buy-in among the industry, like ads.txt, which everybody who's anybody uses these days.
you do, of course, have to buy in to what the IAB is metaphorically selling, but their decrees hold a lot of weight among all sections of the ads supply chain—both reputable buyers and reputable sellers regularly adjust their behavior based on IAB guidelines. for example, two of the things you mentioned:
"ads can sprawl wherever they want": the IAB has about a million guidelines for where ads can physically go on a page, how they can run (e.g., video ads must be muted by default or they aren't IAB compliant), and what percentage of the visual real estate they can use up. publishers obviously can and do violate these guidelines, but third-party tools exist to make sure your ads aren't running on pages that pull that shit. and as a rule, advertisers actively dislike buying ad space on awful cluttered pages because they know the pages are shitty and the impressions are less valuable.
"big down computer performance": people call those heavy ads! the IAB sets standards around ad performance (the lighter the better, basically) and google chrome even implemented a feature that automatically kills heavy ads before they eat up your whole CPU. some performance based-issues are also caused by malvertising which is uhhh a whole other thing but no one likes it and everyone who matters is trying to stop it.
which isn't to be naive here or an industry shill or whatever because Fucking Obviously these problems persist. I actually had to email the advertising division at conde nast recently because I kept getting malicious redirect ads on their mobile site (they haven't responded yet... return my calls bitch!) so clearly even well-meaning reputable websites and ad platforms and advertisers continue to have issues with IVT and whatnot. the struggle is eternal.
but arguably so is the struggle against basically anything that's legislated, like property crime or whatever. I'm admittedly not optimistic that formal laws would fix digital advertising, only put a slightly hotter fire under people's asses to clean up their respective acts better. which is certainly a good thing, it's just a rapidly evolving game where the bad actors are always coming up with new tactics.
fun and related example: I read a recent retrospective about the kids behind the mirai botnet, which originally started out as a DDoS-for-hire scheme but pivoted to ad fraud when it turned out that was way more profitable. possibly the largest botnet ever (don't quote me on that though) and it was spun up by three teenagers!!!
11 notes
·
View notes
Text
Note to Self: DON'T USE UNITY ENGINE
Take FEE from Developers for Every copy for every game installed.
FREE GAMES the fees still apply estimate more than $25,000,000
Declare bankruptcy to the bank, loaner's and users. (??? Does Unity apply the same charges to Casino machines,slot websites, jackpot party, it's legally a gaming ain't it?)
I get FREE GAME, while DEVELOPER is CHARGED for that MY FREE COPY
So if I a Gamer become a Developer will be CHARGED for FREE GAMES even by multiple copies from one user
" That's bad " I feel bad for studio's situation :(
*Edit UPDATES (September 13 2023)
- Unity "regrouped" and now says ONLY the initial installation of a game triggers a fee (0.20$ per install){I hope there no glitches concerning installation}
- Demos mostly won't trigger fees (Keyword: MOSTLY what does that mean)
- Devs not charged fee for Game Pass, Thank God for the Indie Developers
- Charity games/bundles exempted from fees
Xbox is on the hook, for Gamepass?
*Edit Updates (September 13 2023)
Unity:
-Who is impacted by this price increase: The price increase is very targeted. In fact, more than 90% of our customers will not be affected by this change. Customers who will be impacted are generally those who have found a substantial scale in downloads and revenue and have reached both our install and revenue thresholds. This means a low (or no) fee for creators who have not found scale success yet and a modest one-time fee for those who have. (How big of scale of success before your charged?)
-Fee on new installs only: Once you meet the two install and revenue thresholds, you only pay the runtime fee on new installs after Jan 1, 2024. It’s not perpetual: You only pay once for an install, not an ongoing perpetual license royalty like a revenue share model. (???)(How do they know that from device)
-How we define and count installs: Assuming the install and revenue thresholds are met, we will only count net new installs on any device starting Jan 1, 2024. Additionally, developers are not responsible for paying a runtime fee on: • Re-install charges - we are not going to charge a fee for re-installs. •Fraudulent installs charges - we are not going to charge a fee for fraudulent installs. We will work directly with you on cases where fraud or botnets are suspected of malicious intent.
- Trials, partial play demos, & automation installs (devops) charges - we are not going to count these toward your install count. Early access games are not considered demos.
- Web and streaming games - we are not going to count web and streaming games toward your install count either.
- Charity-related installs - the pricing change and install count will not be applied to your charity bundles/initiatives.(Good)
•If I make a expansion pack does count as install, what if I made sequel?
•Fee apply to$200,000 USD (How does work for other countries)
So I charge $60 per ONE Videogame I will be charged fees once I sell about 3400 copies ($204000)
I then sell say 10,000copies(New Sequels as well)
(If I download game onto my computer twice they get charged 0.20, how ever if I redownload onto another device say Xbox, would they get charged again, charges may vary depending on how many games.)
OVERALL
Seems to force companies to charge customers higher prices on videogames to avoid a loss of profit.
*Edit Updates as of (September 22.2023)
- Your Game is made using a Unity Pro or Unity Enterprise plan.
- Your Game is created or will be upgraded to the next major Unity version releasing in 2024.
- Your Game meets BOTH thresholds of $1,000,000 (USD) gross revenue (GROSS= Before Deductions & Taxes) on a trailing 12 month basis(?) AND 1,000,000 *lifetime initial engagements.
As for counting the number of *initial engagements, it will depend on your game and distribution platforms.
Some example metrics that we recommend are number of units sold or first-time user downloads.
This list is not comprehensive, but you can submit an estimate based on these metrics. Hope this helps! You can also find more information here: https://unity.com/pricing-updates
I'm sorry, Did that User say runtime fee is still tied to the number of installations (WTF Runtime Fee)
•Qualify(Ew) for the run-time fee:
1) are on Pro and Enterprise plans
2) have upgraded to the Long Term Support (LTS) version releasing in 2024 (or later)
3) You have crossed the $1,000,000 (USD) in gross revenue (GROSS= Before Deductions & Taxes)(trailing 12 months)
4) 1,000,000 initial engagements
( I noticed that it doesn't seem to mention International Revenue. Only the USD)
•Delete Unity
•Deletes Game before they make million
•Make $900,000 then make Game Free
•Make Game Free and implore people for their generosity
•Change Game Engine
Too tired to do the math...
8 notes
·
View notes
Text
Leverage Redemption Log: The Turkish Prisoner Job
So that name feels like a reference to the "Spanish Prisoner" (the original form of what is now known as the "Nigerian Prince" con). --- 2 crooked cops sitting in a car, complaining that there isnt enough crime for them to hit a quota. One of them is playing hexagordle or whatever its called. Guy name Delgado is leaving the house (that was the cartel from the OG series wasnt it?) Rodrigo is walking to his car like he's got shit in his pants. Cops plant a gun. And Rodrigo is about to be sent to prison cause crooked cops. --- Harry is at a courthouse trying to talk to a runaway prosecutor. Harry is already working Rodrigo's case. Its Golf Job Girl! (i dont remember your name, thats not an insult im just shit with names)
Its Harry's turn to run a con. (he still doesnt know how to steal a catchphrase) --- Parker is clicking a pen in a car. Parker is right, surveilance is boring. Operation Bigger Fish is a go!
Parker has stolen the free smoothie (come on man, not cool. This guy is only trying to prevent himself from getting framed by the cops.) Cops have taken the bait, Sophie is playing the "criminal" to be targeted. Harry is playing himself. (Sophie has brought on 2 understudies as bodyguards), also Breanna, why are you putting so many cuts into your camerafootage. Jumping from cam 1 to cam 3 every other sentence. --- Ok so the plan is to leave the cops alone around a bunch of cash and cocaine and let them "help themselves" while hidden cameras roll. Simple plan.
Oh Romero's family problems just chased him down in prison. Time for an improvised jailbreak! --- Plan has changed, tell the two stooges that the drug deal has been postponed, then kidnap Rodrigo in court. We can get the stooges vengeance for their victims can wait until after we ensure their victims dont die in prison.
Breanna has set up a botnet to astroturf up an anti-hotsauce factory protest. (probably based on the Irwindale Sriracha lawsuit. Yes i had to google the city.)
Quick read of the signs, prop department should be proud of the simple Jalapeno sign. Good work!
GolfGirl catches onto it pretty quickly that Harry is about to do a thing. (DAQ protocol engaged) Elliot is in a shared holding with Rodrigo.
The coffee is smoking. Cops are walking down the staircase, Beardy boy has a concious. Or at least is worried this might bite them in the behind. Woman is clearly the mastermind. "i did it by the book for years, it got me nowhere". Ah, so thats how we're playing this episode. The instruments of state-sponsored violence cant be evil only misguided cause what if the government wont give our production company their subsidies no more. (even the "evil cops" episode is copaganda nowadays)
And we frame the protesters for a chemical attack. Because the solution to innocent people getting their lives ruined by cops framing them for crimes they didnt commit is to frame a bunch more innocents for crimes they didnt commit. --- And the team enters in hazmat suits. Romero is having a panic attack/asthma thing.
Turns out the cops, while evil, are actually good at their job and now we have our victim charged with attempted jailbreak.
Harry has to make a tough call, cant get into a high-speed chase with the foodtruck (not only does it compromise elliots entire food-based Lucille army, the Lucille Legion is also not meant for stealth not speed) --- Sophie shows Harry her Eiffel Tower Salesman Trunk, mentions her mentor. (we're seeding more Sophie Lore) Harry has homework.
Covers arent blown, they're recyclable. (Narco in town on mysterious business, Federal officer in jail.) --- Did these bodies get buried in a tic-tac-toe formation normally, or did Breanna make this entire setpiece from scratch in an actual graveyard?
Sophie arrives to let Breanna and Parker "die" in character now that our cops are hooked. Elliot warns us that another hit is coming in the morning. (we're gonna have to kill this guy and set him up with the Leverage Witness Protection Division) --- Elliot reminds Rodrigo that the real bad-guy here is still theoretically the as-of-yet unidentified housing corpo that is bribing a congressman into presuring the cops. (if these people dont get rounded up at the end of episode, it'll all feel sort of hollow)
Elliot pretends to be a fellow gang-member/hitman angry that Rodrigo isnt actually a delgado.
Huh, using a key as a hilt on a shiv. Creative.
Cops are here to break out Elliot and Rodrigo. --- Old gator-zoo abandoned after Katrina. (turns out you dont need ghosts when you have Gators)
"im not a moron i just have a lot of concussions", His constant references to sportsball. Are we really weaving in a CTE storyline in the middle of this Evil Cops story? If so, its a verry nuanced characterdetail to give our crook of the week.
Billy Brainbash is starting to recognise Elliot from somewhere. --- The un-tied boat (untied as in "was never tied" not as in "has had the tie-ing undone") buys us enough time to fake a gator attack without needing to blank their guns.
Ok even if the guns werent blanks we just unloaded them on the "gators" so Sophie is safe.
Flashback shows Breanna making Gatordroids (i mean didnt even need a flashback. The gators were pretty clearly props by the way Elliot dropped them. Or maybe im just getting too familiar with the show) --- Meanwhile our crooked cops are at (presumeably the prosecutor's) stashhouse. Yup its the Prosecutor (McShane really was the smart one.) --- Harry presures the judge to pressure the prosecutor to investigate the Quota's.
Breanna found the Bagmans house. (turns out, cash money takes up a lot of space and only some houses built in the story-apropriate era have enough space between their walls. Add in his area of operation and it narrows down to 1) --- Harry Wilson, Law Criminal. Has a ring to it. (also the "con artist" line gets a 10/10)
#leverage#leverage redemption#leverage redemtion season 2#the turkish prisoner job#trigger warning CTE#Chronic Traumatic Encephalopathy#CTE mention#TW CTE
2 notes
·
View notes
Text
concepts designed to ruin youtubes metrics
1: botnet that just clicks on every reccomended video, watches the ad, then clicks away after 1 second of video [attacked metric: watch time = quality. attack method: financial & metric ruining]
2. botnet that targets shortform content snipers in longform & video essay categories [manual list composition required] upon watching 5 second of video, clicks dislike [attack metric: watch % = quality. attack method: targeted content developer ruination. fuck those content snipers]
3 notes
·
View notes
Text
Speaking as fellow old person, a couple of corrections:
You can definitely still get new, non-smart TVs. I don’t know about how the picture and audio quality stacks up against smart ones, because I don’t really care all that much about either one (and I don’t play the kinds of console games where latency matters very much), but B*st B*y not only has them but has a store brand of them (Ins*gnia, in sizes from 19 inches to 40), and you can find them on Am*zon if you look. (Asterisks because this post already has enough brands in it.)
Also, you can plug in headphones to an iPhone, even an iPhone 15. (If you insist on Apple-branded stuff, look for “EarPods” instead of “AirPods”, choose your connector type, and pay ~$20 plus tax, or just search Google for the connector type you want and “headphones”… or you can get an adaptor and plug in anything to anything.) (Those brand names already appeared so I’m not bothering to censor them.) You don’t have to use Bluetooth, and really since Bluetooth audio has always sucked for some reason — I’ve been trying it at intervals since Bluetooth was the Shiny New Feature, and it has always been noticeably worse than plain old wired audio, which suggests that the defects are built into the standard — you never should, on anything.
(Incidentally: one of the tech things we need, particularly now that USB has significant power transmission, is a new generation of reasonably high-quality, bus-powered USB speakers. Unlike Bluetooth, USB speakers are actually pretty good, and there’s a device class for them so they can be no-specific-driver-needed plug-and-play devices. For a while, it was possible to get USB 1 powered speakers, but the low power delivery meant they could never get as loud as cheap externally-powered computer speakers with a 3.5mm jack… which meant having to have an extra power cable to plug in, usually with a brick to waste space on the surge protector. With USB 2 or 3, that restriction should be liftable… but somebody has to make and market them and nobody seems to be interested in doing that. But I digress.)
There are so many whole categories of ways “smart” things can go wrong that it’s a little scary, particularly given how many engineers seem to be unable to predict the problems in advance. We’ve already reached the point where “smart devices no longer receiving software updates are trivially hackable from outside and are being used by criminals to form botnets and DDOS the Internet” is A Thing. Also “your car’s internal computer can be hacked from another vehicle while the car is moving and the hacker can interfere with the engine or potentially even the steering”, that’s another good one. My favorite, though, would have to be “this smart device has outlived the company which made it but it was hard-coded to store all its settings on a remote server so now it’s a piece of expensive junk”.
Really, one would think that the EU would be passing some laws about it to require non-smart controls… and maybe to require (at a minimum) companies to put both the internal programming and the controlling apps for all smart devices into some sort of public trust, so that if the company goes out of business it is possible to resurrect the software and keep using the device.
123K notes
·
View notes
Text
An indictment from the US Department of Justice may have solved the mystery of how disgraced cryptocurrency exchange FTX lost over $400 million in crypto. The indictment, filed last week, alleges that three individuals used a SIM-swapping attack to steal hundreds of millions in virtual currency from an unnamed company. The timing and the amount stolen coincides with FTX's theft. Meanwhile, in a letter obtained by WIRED this week, seven lawmakers have demanded the DOJ stop funding biased and inaccurate predictive policing tools until the agency has a way to ensure law enforcement won’t use them in a way that has a “discriminatory impact.”
In Florida, prosecutors say a 17-year-old named Alan Winston Filion is responsible for hundreds of swatting attacks around the United States. The news of his arrest was first reported by WIRED days before law enforcement made it public. It was the culmination of a multi-agency manhunt to piece together a trail of digital breadcrumbs left by the teenager. In Ukraine, unmanned aerial vehicles have been powerful tools since the Russian invasion began in February 2022. But as the war rages on, another kind of unmanned robot has increasingly appeared on the front-lines: the unmanned ground vehicle, or UGV.
For months lawyers affiliated with an India based hacker-for-hire firm called Appin Technology have used legal threats to censor reporting about the company’s alleged cyber mercenary past. The EFF, Techdirt, MuckRock, and DDoSecrets are now pushing back, publicly sharing details for the first time about the firm's efforts to remove content from the web. It’s a dangerous world out there, so we’ve also got a list of some major patches issued in January that you can use to update your devices to keep them secure.
And there’s more. Each week, we highlight the news we didn’t cover in-depth ourselves. Click on the headlines below to read the full stories. And stay safe out there.
China’s Hackers Keep Targeting US Water and Electricity Supplies
For years Western security officials have warned about the threat of China collecting data about millions of people and the country’s hackers infiltrating sensitive systems. This week, Federal Bureau of Investigation director Christopher Wray said hackers affiliated with the Chinese Communist Party are constantly targeting US critical infrastructure, such as water treatment plants, the electrical grid, and oil and gas pipelines. Wray’s testimony, at a House subcommittee on China, came as the FBI also revealed it removed malware from hundreds of routers in people’s homes and offices that had been planted by the Chinese hacking group Volt Typhoon.
“China’s hackers are positioning on American infrastructure in preparation to wreak havoc and cause real-world harm to American citizens and communities,” Wray said in the public appearance. “Low blows against civilians are part of China’s plan.” The FBI director added that China has a bigger hacking operation than “every other major nation combined,” and claimed that if all of the FBI’s cyber-focused agents were assigned to work on issues related to China, they would still be outnumbered “by at least 50 to 1.”
While concerns about the scale of China’s espionage and cyber operations aren’t new, the US intelligence community has been increasingly vocal and worried about critical infrastructure being targeted by Volt Typhoon and other groups. “The threat is extremely sophisticated and pervasive,” NSA officials warned in November. In May 2023, Microsoft revealed it had been tracking Volt Typhoon intrusions at communications and transportation infrastructure, among other critical infrastructure, in US states and Guam.
The FBI and DOJ, also revealed this week that they remotely removed the KV Botnet malware from hundreds of routers infected by Volt Typhoon. The impacted routers, from Cisco and Netgear, were mostly at the end of their life, but were being used as part of wider operations. “The Volt Typhoon malware enabled China to hide, among other things, pre-operational reconnaissance and network exploitation against critical infrastructure like our communications, energy, transportation, and water sectors,” Wray said. It isn’t the first time US officials have obtained a court order to remotely wipe devices infected by hackers, but the move is still rare.
‘Untraceable’ Monero Transactions Have Been Traced, Police Claim
Since the first cryptocurrencies emerged more than a decade ago, there has been the assumption that the blockchain-based digital currencies are anonymous and untraceable. They are, in fact, very traceable. Researchers have shown how people can be linked to the transactions they make and law enforcement have used the techniques to help bust illicit dark web markets and catch pedophiles. There are, however, still some privacy-focused cryptocurrencies that appear to be less traceable than Bitcoin. This includes Monero, which is increasingly being adopted by sellers of child sexual abuse materials.
This week investigators in Finland said Moreno-tracing helped reveal the identity of a hacker who allegedly attacked psychotherapy company Vastaamo in 2020, stealing thousands of patient records and threatening to leak them unless people paid a ransom. Investigators from the Finnish National Bureau of Investigation claim they used heuristic analysis to infer where funds were moved to. The investigators did not reveal the full methods of how they allegedly traced the Monero payments, however, they add to the growing body of evidence that cryptocurrency tracing firms and investigators may be able to track the currency.
Russia Likely Behind a Spike in GPS Interference, Officials Say
Planes flying over Europe have faced a spike in accuracy issues with GPS systems used for navigation in recent months. The head of Estonia’s Defense Forces has claimed that Russia is likely the source of this interference, according to an interview with Bloomberg. “Someone is causing it, and we think it’s Russia,” Martin Herem told the publication, adding that Russia may be testing its electronic warfare capabilities and “learning” the most effective tactics. Across Europe, and particularly the Baltics region, there has been a reported increase in GPS jamming, with Finland reporting large interferences in December and pilots repeatedly reporting issues with their navigation systems.
Vault 7 Hacking Tools Leaker Joshua Schulte Sentenced to 40 Years
In 2017, the Vault 7 leaks exposed some of the CIA’s most sophisticated hacking tools, including how the agency could compromise routers, phones, PC, and TVs. Joshua Schulte, a former CIA engineer in the agency’s Operations Support Branch who prosecutors identified as being behind the data breach and responsible for leaking the materials to Wikileaks, was convicted in numerous trials in recent years. Schulte, who denied the allegations, has been sentenced to 40 years in prison for the espionage and also for possessing thousands of child abuse images. Judge Jesse Furman, sentencing Schulte, said he had caused “untold damage to national security.” In June 2022, The New Yorker published this comprehensive investigation into the data breach and Schulte’s troubled history working at the agency.
2 notes
·
View notes
Text
Understanding DDoS Attacks
Understanding DDoS Attacks What is a DDoS Attack? How Do DDoS Attacks Work? Types of DDoS Attacks Consequences of DDoS Attacks Prevention and Mitigation Laws and Regulations
Understanding DDoS Attacks
What are DDoS attacks? As the world becomes increasingly reliant on the internet, the threat of cyberattacks continues to grow. One of the most common and devastating types of cyberattacks is the Distributed Denial of Service (DDoS) attack. In this article, we will delve into the world of DDoS attacks, exploring what they are, how they work, and the consequences of such attacks.

What is a DDoS Attack?
A DDoS attack is a type of cyberattack where an attacker attempts to make a computer or network resource unavailable by overwhelming it with traffic from multiple sources. This is achieved by flooding the targeted system with a massive amount of traffic, rendering it unable to handle legitimate requests. The goal of a DDoS attack is to disrupt the normal functioning of a website, network, or system, causing it to become slow or even completely inaccessible.
How Do DDoS Attacks Work?
A DDoS attack typically involves the following steps: Recruitment of Botnets: The attacker recruits a network of compromised computers, known as botnets, to carry out the attack. These botnets can be compromised devices such as computers, smartphones, or even IoT devices. Command and Control: The attacker uses a command and control (C2) server to instruct the botnets to launch the attack. Traffic Generation: The botnets generate a massive amount of traffic, which is directed at the targeted system. Overwhelming the System: The targeted system becomes overwhelmed with traffic, causing it to slow down or become completely inaccessible. A Distributed Denial of Service (DDoS) attack is a complex and sophisticated type of cyberattack that involves multiple steps and components. In this section, we will delve into the details of how a DDoS attack works, exploring the recruitment of botnets, command and control, traffic generation, and overwhelming the system. Step 1: Recruitment of Botnets The first step in a DDoS attack is the recruitment of botnets. Botnets are networks of compromised computers, smartphones, or IoT devices that are controlled by the attacker. These devices can be compromised through various means, including: - Malware: Malware is a type of software that is designed to harm or exploit a computer system. Malware can be used to compromise devices and recruit them into a botnet. - Phishing: Phishing is a type of social engineering attack that involves tricking users into revealing sensitive information, such as login credentials. Phishing attacks can be used to compromise devices and recruit them into a botnet. - Exploiting Vulnerabilities: Exploiting vulnerabilities in software or hardware can be used to compromise devices and recruit them into a botnet. Once a device is compromised, it becomes part of the botnet and can be controlled by the attacker. The attacker can then use the botnet to launch a DDoS attack. Step 2: Command and Control The next step in a DDoS attack is the command and control (C2) phase. During this phase, the attacker uses a C2 server to instruct the botnets to launch the attack. The C2 server is typically a compromised device or a server that is controlled by the attacker. The C2 server sends instructions to the botnets, which then carry out the attack. The instructions can include: - Target IP Address: The IP address of the targeted system. - Attack Type: The type of attack to be launched, such as a volumetric attack or an application-layer attack. - Attack Duration: The duration of the attack. The botnets receive the instructions and then launch the attack, generating a massive amount of traffic that is directed at the targeted system. Step 3: Traffic Generation The third step in a DDoS attack is traffic generation. During this phase, the botnets generate a massive amount of traffic that is directed at the targeted system. The traffic can be generated through various means, including: - TCP SYN Floods: A TCP SYN flood is a type of attack that involves sending a large number of TCP SYN packets to the targeted system. - UDP Floods: A UDP flood is a type of attack that involves sending a large number of UDP packets to the targeted system. - HTTP Floods: An HTTP flood is a type of attack that involves sending a large number of HTTP requests to the targeted system. The traffic generated by the botnets can be massive, with some attacks generating over 1 Tbps of traffic. Step 4: Overwhelming the System The final step in a DDoS attack is overwhelming the system. During this phase, the targeted system becomes overwhelmed with traffic, causing it to slow down or become completely inaccessible. The targeted system may experience: - Network Congestion: The network becomes congested, causing delays and packet loss. - System Crashes: The system crashes, causing it to become completely inaccessible. - Service Disruption: The service is disrupted, causing it to become unavailable to users. The goal of a DDoS attack is to overwhelm the system, causing it to become unavailable to users. This can have serious consequences, including financial losses, reputational damage, and data breaches.
Types of DDoS Attacks
Distributed Denial of Service (DDoS) attacks are a type of cyberattack that can be devastating to organizations. There are several types of DDoS attacks, each with its own unique characteristics and goals. In this section, we will explore four common types of DDoS attacks: Volumetric Attacks, Application-Layer Attacks, Protocol Attacks, and Amplification Attacks. Volumetric Attacks Volumetric attacks are a type of DDoS attack that focuses on overwhelming the targeted system with a massive amount of traffic. The goal of a volumetric attack is to consume the bandwidth of the targeted system, making it difficult or impossible for legitimate traffic to reach the system. Volumetric attacks can be further divided into two subcategories: - Flood Attacks: Flood attacks involve sending a large amount of traffic to the targeted system in an attempt to overwhelm it. This can include TCP SYN floods, UDP floods, and ICMP floods. - Amplification Attacks: Amplification attacks involve using third-party services to amplify the traffic, making it more difficult to block. This can include DNS amplification attacks and NTP amplification attacks. How Volumetric Attacks Work Volumetric attacks typically involve the following steps: - Recruitment of Botnets: The attacker recruits a network of compromised computers, known as botnets, to carry out the attack. - Traffic Generation: The botnets generate a massive amount of traffic, which is directed at the targeted system. - Overwhelming the System: The targeted system becomes overwhelmed with traffic, causing it to slow down or become completely inaccessible. Application-Layer Attacks Application-layer attacks are a type of DDoS attack that targets specific applications or services, such as web servers or databases. The goal of an application-layer attack is to disrupt the normal functioning of the targeted application or service. Application-layer attacks can be further divided into two subcategories: - HTTP Floods: HTTP floods involve sending a large number of HTTP requests to the targeted system in an attempt to overwhelm it. - SQL Injection Attacks: SQL injection attacks involve injecting malicious SQL code into the targeted system in an attempt to disrupt its normal functioning. How Application-Layer Attacks Work Application-layer attacks typically involve the following steps: - Identification of Vulnerabilities: The attacker identifies vulnerabilities in the targeted application or service. - Exploitation of Vulnerabilities: The attacker exploits the vulnerabilities to disrupt the normal functioning of the targeted application or service. - Disruption of Service: The targeted application or service becomes disrupted, causing it to become unavailable to users. Protocol Attacks Protocol attacks are a type of DDoS attack that exploits vulnerabilities in network protocols, such as TCP/IP. The goal of a protocol attack is to disrupt the normal functioning of the targeted system by exploiting vulnerabilities in the protocol. Protocol attacks can be further divided into two subcategories: - TCP SYN Floods: TCP SYN floods involve sending a large number of TCP SYN packets to the targeted system in an attempt to overwhelm it. - ICMP Floods: ICMP floods involve sending a large number of ICMP packets to the targeted system in an attempt to overwhelm it. How Protocol Attacks Work Protocol attacks typically involve the following steps: - Identification of Vulnerabilities: The attacker identifies vulnerabilities in the targeted protocol. - Exploitation of Vulnerabilities: The attacker exploits the vulnerabilities to disrupt the normal functioning of the targeted system. - Disruption of Service: The targeted system becomes disrupted, causing it to become unavailable to users. Amplification Attacks Amplification attacks are a type of DDoS attack that uses third-party services to amplify the traffic, making it more difficult to block. The goal of an amplification attack is to overwhelm the targeted system with a massive amount of traffic. Amplification attacks can be further divided into two subcategories: - DNS Amplification Attacks: DNS amplification attacks involve using DNS servers to amplify the traffic. - NTP Amplification Attacks: NTP amplification attacks involve using NTP servers to amplify the traffic. How Amplification Attacks Work Amplification attacks typically involve the following steps: - Identification of Vulnerable Services: The attacker identifies vulnerable services that can be used to amplify the traffic. - Exploitation of Vulnerabilities: The attacker exploits the vulnerabilities to amplify the traffic. - Overwhelming the System: The targeted system becomes overwhelmed with traffic, causing it to slow down or become completely inaccessible.
Consequences of DDoS Attacks
Distributed Denial of Service (DDoS) attacks can have severe consequences for organizations, including downtime, reputation damage, financial losses, and data breaches. In this section, we will explore the consequences of DDoS attacks in detail, highlighting the potential impact on organizations and their customers. Downtime Downtime is one of the most immediate consequences of a DDoS attack. When a DDoS attack is launched, the targeted system may become completely inaccessible, resulting in lost revenue and productivity. This can have a significant impact on organizations, particularly those that rely on their online presence to conduct business. Types of Downtime There are several types of downtime that can occur as a result of a DDoS attack, including: - Complete Downtime: The targeted system is completely inaccessible, resulting in a complete loss of revenue and productivity. - Partial Downtime: The targeted system is partially inaccessible, resulting in a partial loss of revenue and productivity. - Intermittent Downtime: The targeted system is intermittently inaccessible, resulting in a loss of revenue and productivity during the periods of downtime. Impact of Downtime The impact of downtime can be significant, including: - Lost Revenue: Downtime can result in lost revenue, particularly for organizations that rely on their online presence to conduct business. - Lost Productivity: Downtime can result in lost productivity, particularly for organizations that rely on their online presence to conduct business. - Damage to Reputation: Downtime can damage the reputation of the targeted organization, leading to a loss of customer trust. Reputation Damage A DDoS attack can damage the reputation of the targeted organization, leading to a loss of customer trust. This can have a significant impact on organizations, particularly those that rely on their online presence to conduct business. Types of Reputation Damage There are several types of reputation damage that can occur as a result of a DDoS attack, including: - Loss of Customer Trust: A DDoS attack can damage the reputation of the targeted organization, leading to a loss of customer trust. - Negative Publicity: A DDoS attack can result in negative publicity, particularly if the attack is widely reported in the media. - Damage to Brand: A DDoS attack can damage the brand of the targeted organization, leading to a loss of customer loyalty. Impact of Reputation Damage The impact of reputation damage can be significant, including: - Loss of Revenue: Reputation damage can result in lost revenue, particularly for organizations that rely on their online presence to conduct business. - Loss of Customer Loyalty: Reputation damage can result in lost customer loyalty, particularly if the attack is widely reported in the media. - Difficulty Attracting New Customers: Reputation damage can make it difficult for organizations to attract new customers, particularly if the attack is widely reported in the media. Financial Losses The cost of mitigating a DDoS attack can be significant, including the cost of hiring security experts and purchasing new equipment. This can have a significant impact on organizations, particularly those that have limited resources. Types of Financial Losses There are several types of financial losses that can occur as a result of a DDoS attack, including: - Cost of Hiring Security Experts: The cost of hiring security experts to mitigate the attack can be significant. - Cost of Purchasing New Equipment: The cost of purchasing new equipment to mitigate the attack can be significant. - Loss of Revenue: The loss of revenue as a result of the attack can be significant. Impact of Financial Losses The impact of financial losses can be significant, including: - Difficulty Recovering from the Attack: Financial losses can make it difficult for organizations to recover from the attack. - Difficulty Investing in New Technologies: Financial losses can make it difficult for organizations to invest in new technologies, particularly those that are designed to prevent DDoS attacks. - Difficulty Attracting New Customers: Financial losses can make it difficult for organizations to attract new customers, particularly if the attack is widely reported in the media. Data Breaches In some cases, a DDoS attack may be used as a distraction for a more malicious attack, such as a data breach. This can have a significant impact on organizations, particularly those that store sensitive data. Types of Data Breaches There are several types of data breaches that can occur as a result of a DDoS attack, including: - Unauthorized Access to Sensitive Data: A DDoS attack can be used as a distraction for a more malicious attack, such as unauthorized access to sensitive data. - Theft of Sensitive Data: A DDoS attack can be used as a distraction for a more malicious attack, such as the theft of sensitive data. - Modification of Sensitive Data: A DDoS attack can be used as a distraction for a more malicious attack, such as the modification of sensitive data. Impact of Data Breaches The impact of data breaches can be significant, including: - Loss of Customer Trust: A data breach can damage the reputation of the targeted organization, leading to a loss of customer trust. - Financial Losses: A data breach can result in significant financial losses, particularly if the breach is widely reported in the media. - Difficulty Recovering from the Breach: A data breach can make it difficult for organizations to recover from the breach, particularly if the breach is widely reported in the media.
Prevention and Mitigation
While it is impossible to completely prevent a DDoS attack, there are steps that can be taken to mitigate the risk: - Implementing Firewalls: Firewalls can help block malicious traffic and prevent it from reaching the targeted system. - Using Content Delivery Networks (CDNs): CDNs can help distribute traffic and reduce the load on the targeted system. - Implementing Rate Limiting: Rate limiting can help prevent a large amount of traffic from reaching the targeted system. - Monitoring Traffic: Monitoring traffic can help detect a DDoS attack early, allowing for swift mitigation.
Laws and Regulations
DDoS attacks are illegal under various laws and regulations, including: - Computer Fraud and Abuse Act (CFAA): This US law makes it a crime to access a computer without authorization or to exceed authorized access. - Electronic Communications Privacy Act (ECPA): This US law makes it a crime to intercept or access electronic communications without authorization. - General Data Protection Regulation (GDPR): This EU law requires organizations to implement measures to prevent data breaches, including DDoS attacks. DDoS attacks are a serious threat to the security and integrity of computer systems and networks. Understanding how these attacks work and the consequences of such attacks is crucial in preventing and mitigating them. By implementing security measures and staying informed about the latest threats, organizations can reduce the risk of a DDoS attack and protect their online presence. https://youtu.be/a_r-lzQKMAQ Read the full article
0 notes
Text
Okay, so... tumblr is 'free' right? It costs nothing to create an account and utilize the service. So the startup costs of running a pornbot army is zero, right?
Wrong!
Shady websites sell kits to create/operate pornbot networks. You pay $$$ for an engine and a collection of scripts tuned for various free websites. And apparently (I guess) there is a new tumblr script that comes preloaded with a zillion girlie names + 3 digits, so all the prospective pornbot meister has to do is start the script with some seed values and wait for their bot army to grow.
In order to fly beneath the radar, these scripts operate in stages. First they create the account then follow a few high profile blogs. THAT is why, when they first follow you, they're just a generic stolen cheesecake pic named (randomly generated name) ChestyMoorbutt754 with an otherwise empty profile.
Then after a preset number of days/weeks they start blogging 'content' like bit.ly links to malware or whatever. Along with some legit-looking reblogs to keep up appearances. All these scripted behaviors are configurable.
Their hope is that some certain percentage of idiots will (1) click thru the hosted links to an intermediary landing page (with ads, naturally) that acts as a portal to buy subs for OnlyFans, Sinder etc, or (2) interact with an actual chatbot that eventually convinces the poor schmuck to enter their credit card info so it can be hijacked.
We're seeing a new flood of bots NOW because twitter is floundering and all the talk about twitter alternatives (like tumblr) has caught the attention of the guys who make/sell pornbot tools.
Who are the ones REALLY making profit off all of this. Not the pornbots themselves, but the darkweb dweebs who sell the accounts & kits. Because selling access to pornbot armies is guaranteed income whereas who the hell knows how successful any given pornbot will be in the wild. After awhile, the pornbot army gets detected & shutdown or the customer running the botnet get disillusioned and quits or both... then the cycle begins anew with new sheep to be fleeced.
Just like in the 1840s gold rush era, it wasn't the miners who got rich; it was the guys selling picks & shovels.
Look I know everyone is getting the porn bot follows but like .. what's are they even for? What's the point of them? What are they trying to accomplish?
61K notes
·
View notes