#bluecoat proxy
Explore tagged Tumblr posts
Video
vimeo
PROXY, Louisa Martin, 2017. Exhibition at Bluecoat, Liverpool, 6 May - 24 June 2017. from Louisa Martin on Vimeo.
Video documentation of solo exhibition 'Proxy' at Bluecoat, Liverpool, 6 May - 24 June 2017.
6 notes
·
View notes
Text
How to check website category in BlueCoat
How to check website category in BlueCoat
How to check website category in BlueCoat:– The Symantec ProxySG solution is designed for today’s cloud generation environment and offers the most advanced, flexible, and powerful platform to build a complete advanced security defense for web traffic. As part of the ongoing operations of the security defense layer, ProxySG blocks the bulk of the incoming threats to any organization, while…
View On WordPress
#bluecoat#bluecoat proxy#bluecoat site review#bluecoat site review script#bluecoats 2017#check website category in BlueCoat#how to check website category in bluecoat#sitereview bluecoat com sitereview jsp
0 notes
Photo

Symantec BlueCoat SG training this week. It has been some years since I got a refresh on their systems very excited to work or BlueCoats again #BCCPA #BCCPP #networking #networksecurity #Proxy #coding #excited #motivated https://www.instagram.com/p/Bmczs0GBKyl/?utm_source=ig_tumblr_share&igshid=jjhphypc726
4 notes
·
View notes
Text
Registrar la ip real del cliente en Apache

Registrar la ip real del cliente en Apache. Para lograr más velocidad y seguridad, es una practica común instalar nuestros servidores web apache detrás de un proxy de equilibrio de carga como Nginx o Haproxy (Haproxy Load Balancer a resucitado). También es frecuente que el servidor Apache este instalado detrás de un proxy de almacenamiento caché, como Squid o un proxy del tipo BlueCoat (actualmente de Symantec), Las practicas mencionadas anteriormente son perfectamente validas, incluso recomendadas. Pero tienen un problema, en los registros de Apache la dirección IP real del cliente se reemplaza por la dirección IP del proxy. Para evitar este problema, Squid desarrolló un encabezado de solicitudes HTTP personalizado, se conoce como X-Forwards-For. Actualmente es el encabezado estándar que identifica el origen real de la IP de un cliente conectado a través de un proxy HTTP, o un balanceador de carga. Esta cabecera depura las estadísticas, y genera contenido dependiente de la ubicación. La información generada se ofrece de forma publica al registro de Apache para ser publicada (en este tema existe una gran controversia en la comunidad, recuerda que hablamos de datos sensibles del usuario). Nada es perfecto, X-Forwards-For, tampoco. Bueno, parece que con este encabezado si registramos las IP de los clientes, pero ojo!!!, si haces peticiones directamente a tu Apache sin pasar por el proxy, no se registran. En este articulo vemos como registrar todas las ip reales de los clientes en Apache.
Registrar la ip real del cliente en Apache
Para lograr nuestro objetivo debemos editar el archivo httpd.conf. Dependiendo del linux que tengas instalado en el servidor su localización puede variar, vemos las dos rutas posibles. sudo nano/etc/httpd/conf/httpd.conf o sudo nano/usr/local/apache2/httpd.conf Ahora busca la siguiente linea: LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\"" combined Ahora debes cambiar , por: %{X-Forwarded-For}i
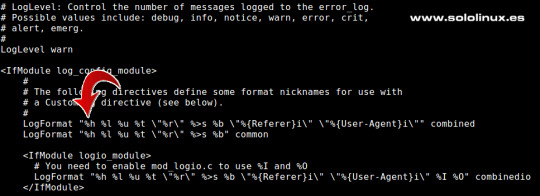
Modificar la cadena LogFormat en Apache La cadena quedara de la siguiente forma: LogFormat “%{X-Forwarded-For}i %l %u %t \”%r\” %>s %b \”%{Referer}i\” \”%{User-Agent}i\”” combined” Guarda el archivo y cierra el editor. Como ultimo paso reiniciamos Apache. sudo systemctl restart httpd o sudo systemctl restart apache2 Canales de Telegram: Canal SoloLinux – Canal SoloWordpress Espero que este articulo te sea de utilidad, puedes ayudarnos a mantener el servidor con una donación (paypal), o también colaborar con el simple gesto de compartir nuestros artículos en tu sitio web, blog, foro o redes sociales. Read the full article
#BlueCoat#cadenaLogFormat#clienteenApache#Haproxy#httpd.conf#IPrealdelcliente#nginx#RegistrarlaIP#registrodeApache#servidorApache#servidoreswebapache#Squid#X-Forwards-For
0 notes
Text
Need IT Security Engineer Consultant
Job Position : IT Security Engineer Consultant Job Location : Atlanta, GA Job Duration : 6 months Job Description The IT Security Engineer will provide engineering, consulting, and implementation of security controls and processes for client. This position will be responsible for a variety of security functions including network security, Windows and Linux security, vulnerability management, incident response, and security monitoring. Day to day responsibilities: ? Design and engineering of new and enhanced security capabilities including documentation, metrics, roles and responsibilities, process, and technology ? Provide consulting and advisory to IT and business unit constituents on security threats, risks, and mitigations ? Support investigation and response to cyber security events and incidents ? Perform firewall and web proxy request risk analysis ? Manage vulnerability management platform including scans, reporting, and remediation lifecycle Skills and experience: ? 5 years of experience with Windows and Active Directory security ? 5 years of experience with firewall and web proxy technology ? 5 years of experience with network IDS/IPS technology ? 3 years of experience with network vulnerability scanning and remediation lifecycle ? Strong knowledge of network protocols such as HTTP, DNS, SMTP, SSH, DHCP, CIFS, and LDAP ? Knowledge of PKI and Certificate Authority templates and operations ? Knowledge of database security including RBAC, encryption, masking, and other features ? Scripting languages such as Powershell, Bash, Perl, or Python ? Check Point, SourceFire and/or TippingPoint IPS ? Check Point and/or Cisco firewalls ? BlueCoat and/or ForcePoint web proxy ? Microsoft Windows Server 2008R2, 2012, 2016 ? Microsoft SCCM ? ArcSight Logger ? Rapid7 Nexpose ? MobileIron MDM ? Windows Certificate Services Reference : Need IT Security Engineer Consultant jobs from Latest listings added - JobsAggregation http://jobsaggregation.com/jobs/technology/need-it-security-engineer-consultant_i7187
0 notes
Text
Need IT Security Engineer Consultant
Job Position : IT Security Engineer Consultant Job Location : Atlanta, GA Job Duration : 6 months Job Description The IT Security Engineer will provide engineering, consulting, and implementation of security controls and processes for client. This position will be responsible for a variety of security functions including network security, Windows and Linux security, vulnerability management, incident response, and security monitoring. Day to day responsibilities: ? Design and engineering of new and enhanced security capabilities including documentation, metrics, roles and responsibilities, process, and technology ? Provide consulting and advisory to IT and business unit constituents on security threats, risks, and mitigations ? Support investigation and response to cyber security events and incidents ? Perform firewall and web proxy request risk analysis ? Manage vulnerability management platform including scans, reporting, and remediation lifecycle Skills and experience: ? 5 years of experience with Windows and Active Directory security ? 5 years of experience with firewall and web proxy technology ? 5 years of experience with network IDS/IPS technology ? 3 years of experience with network vulnerability scanning and remediation lifecycle ? Strong knowledge of network protocols such as HTTP, DNS, SMTP, SSH, DHCP, CIFS, and LDAP ? Knowledge of PKI and Certificate Authority templates and operations ? Knowledge of database security including RBAC, encryption, masking, and other features ? Scripting languages such as Powershell, Bash, Perl, or Python ? Check Point, SourceFire and/or TippingPoint IPS ? Check Point and/or Cisco firewalls ? BlueCoat and/or ForcePoint web proxy ? Microsoft Windows Server 2008R2, 2012, 2016 ? Microsoft SCCM ? ArcSight Logger ? Rapid7 Nexpose ? MobileIron MDM ? Windows Certificate Services Reference : Need IT Security Engineer Consultant jobs Source: http://jobrealtime.com/jobs/technology/need-it-security-engineer-consultant_i7607
0 notes
Text
I’m finally caught up in The Adventure Zone and just started a re-listen of my favorite arc.
Which is great, because now I get to “see” these stories with more fleshed out versions of the NPC characters instead of the proxies pulled from other media franchises that I’m only half familiar with through tumblr cultural osmosis that my brain tends to offer up when it’s pressed for time and doesn’t have energy to headcannon, which is how I ended up with white robot dude from Big Hero Six as Roswell, yellow lizard scientist and blue fish girlfriend from Undertale as Hurley and Sloane, and bluecoat big-ear mcfurry lady from Treasure Planet as the Director.
8 notes
·
View notes
Text
Why should I learn Bluecoat Proxy online? How is it better than offline training?
Blue Coat’s secure Web gateway (SWG), the Proxy SG, is among the leading products in the SWG marketplace. Like its competitors, Blue Coat Proxy SG is equipped with user authentication; Web filtering, data loss prevention, and inspection. Each course is designed to provide you with the highest quality training experience using the latest product releases. BCCPA course is intended for IT professionals who wish to master the fundamentals of the Blue Coat ProxySG. BCCPP Course is intended for IT professionals who wish to master the advanced features of the Blue Coat ProxySG.
The audience for BlueCoat Proxy Training
IT network or security professionals who wish to master the fundamentals of Blue Coat products with a focus on network security and who have not taken any previous Blue Coat training courses.
Prerequisites for Bluecoat Proxy Training
Students should be familiar with networking essentials, such as LAN, Internet, security, and IP protocols. Basic knowledge of authentication methods is also a plus.
About MaxMunus’s BlueCoat Proxy Training
This Bluecoat Proxy Training will help you learn how to describe the architecture of the Proxy SG, how to write code in Content Policy Language to configure Proxy SG policy processing, how to implement and troubleshoot advanced authentication realms deployments, manage downloads and Flash traffic, implement advanced SSL proxy functionality, monitor and analyze Proxy SG performance. BlueCoat Proxy Training course is intended for IT professionals who wish to master the fundamentals of the Blue Coat ProxySG. BlueCoat Proxy corporate Training Services offers a variety of instructor-led and web-based training course
Few of the clients we have served across industries are:
DHL | PWC | ATOS | TCS | KPMG | Momentive | Tech Mahindra | Kellogg’s | Bestseller | ESSAR | Ashok Leyland | NTT Data | HP | SABIC | Lamprell | TSPL | Neovia | NISUM and many more.
MaxMunus has successfully conducted 1000+ corporate training in India, Qatar, Saudi Arabia, Oman, Bangladesh, Bahrain, UAE, Egypt, Jordan, Kuwait, Srilanka, Thailand, Hong Kong, Germany, France, Australia, and the USA.
Why should you learn Blue Coat to grow your career?
There are numerous job opportunities available around the world due to the high demand for Blue Coat ProxySG.
Most of the world’s top multinational companies are recruiting Blue Coat certified professionals.
The average salary of a skilled Blue Coat professional is USD 159,731 per annum.
Our BlueCoat Proxy training helps you gain expertise in the following areas:
Blue Coat PacketShaper architecture
Advanced Classification
Traffic Tree Management
URL Categorization
Understanding Adaptive Response
Network Management and Monitoring
Advanced Bandwidth Management
PacketShaper Reporting Tools
Overview of Intelligence Center
Summary of the Policy Center
To join Bluecoat Proxy online Training session kindly feel free to contact us.
Email Id: [email protected]
Contact No: +91-8553177744.
http://www.maxmunus.com/page/Bluecoat-Proxy-Training
#bluecoatproxytraining#Bluecoatproxycorporatetraining#Bluecoatproxycourses#Bluecoatcertificationtraining#Bluecoatproxyonlinetraining
0 notes
Text
Need IT Security Engineer Consultant
Job Position : IT Security Engineer Consultant Job Location : Atlanta, GA Job Duration : 6 months Job Description The IT Security Engineer will provide engineering, consulting, and implementation of security controls and processes for client. This position will be responsible for a variety of security functions including network security, Windows and Linux security, vulnerability management, incident response, and security monitoring. Day to day responsibilities: ? Design and engineering of new and enhanced security capabilities including documentation, metrics, roles and responsibilities, process, and technology ? Provide consulting and advisory to IT and business unit constituents on security threats, risks, and mitigations ? Support investigation and response to cyber security events and incidents ? Perform firewall and web proxy request risk analysis ? Manage vulnerability management platform including scans, reporting, and remediation lifecycle Skills and experience: ? 5 years of experience with Windows and Active Directory security ? 5 years of experience with firewall and web proxy technology ? 5 years of experience with network IDS/IPS technology ? 3 years of experience with network vulnerability scanning and remediation lifecycle ? Strong knowledge of network protocols such as HTTP, DNS, SMTP, SSH, DHCP, CIFS, and LDAP ? Knowledge of PKI and Certificate Authority templates and operations ? Knowledge of database security including RBAC, encryption, masking, and other features ? Scripting languages such as Powershell, Bash, Perl, or Python ? Check Point, SourceFire and/or TippingPoint IPS ? Check Point and/or Cisco firewalls ? BlueCoat and/or ForcePoint web proxy ? Microsoft Windows Server 2008R2, 2012, 2016 ? Microsoft SCCM ? ArcSight Logger ? Rapid7 Nexpose ? MobileIron MDM ? Windows Certificate Services Reference : Need IT Security Engineer Consultant jobs from Latest listings added - cvwing http://cvwing.com/jobs/technology/need-it-security-engineer-consultant_i10903
0 notes
Text
Need IT Security Engineer Consultant
Job Position : IT Security Engineer Consultant Job Location : Atlanta, GA Job Duration : 6 months Job Description The IT Security Engineer will provide engineering, consulting, and implementation of security controls and processes for client. This position will be responsible for a variety of security functions including network security, Windows and Linux security, vulnerability management, incident response, and security monitoring. Day to day responsibilities: ? Design and engineering of new and enhanced security capabilities including documentation, metrics, roles and responsibilities, process, and technology ? Provide consulting and advisory to IT and business unit constituents on security threats, risks, and mitigations ? Support investigation and response to cyber security events and incidents ? Perform firewall and web proxy request risk analysis ? Manage vulnerability management platform including scans, reporting, and remediation lifecycle Skills and experience: ? 5 years of experience with Windows and Active Directory security ? 5 years of experience with firewall and web proxy technology ? 5 years of experience with network IDS/IPS technology ? 3 years of experience with network vulnerability scanning and remediation lifecycle ? Strong knowledge of network protocols such as HTTP, DNS, SMTP, SSH, DHCP, CIFS, and LDAP ? Knowledge of PKI and Certificate Authority templates and operations ? Knowledge of database security including RBAC, encryption, masking, and other features ? Scripting languages such as Powershell, Bash, Perl, or Python ? Check Point, SourceFire and/or TippingPoint IPS ? Check Point and/or Cisco firewalls ? BlueCoat and/or ForcePoint web proxy ? Microsoft Windows Server 2008R2, 2012, 2016 ? Microsoft SCCM ? ArcSight Logger ? Rapid7 Nexpose ? MobileIron MDM ? Windows Certificate Services Reference : Need IT Security Engineer Consultant jobs from Latest listings added - LinkHello http://linkhello.com/jobs/technology/need-it-security-engineer-consultant_i7772
0 notes
Text
Need IT Security Engineer Consultant
Job Position : IT Security Engineer Consultant Job Location : Atlanta, GA Job Duration : 6 months Job Description The IT Security Engineer will provide engineering, consulting, and implementation of security controls and processes for client. This position will be responsible for a variety of security functions including network security, Windows and Linux security, vulnerability management, incident response, and security monitoring. Day to day responsibilities: ? Design and engineering of new and enhanced security capabilities including documentation, metrics, roles and responsibilities, process, and technology ? Provide consulting and advisory to IT and business unit constituents on security threats, risks, and mitigations ? Support investigation and response to cyber security events and incidents ? Perform firewall and web proxy request risk analysis ? Manage vulnerability management platform including scans, reporting, and remediation lifecycle Skills and experience: ? 5 years of experience with Windows and Active Directory security ? 5 years of experience with firewall and web proxy technology ? 5 years of experience with network IDS/IPS technology ? 3 years of experience with network vulnerability scanning and remediation lifecycle ? Strong knowledge of network protocols such as HTTP, DNS, SMTP, SSH, DHCP, CIFS, and LDAP ? Knowledge of PKI and Certificate Authority templates and operations ? Knowledge of database security including RBAC, encryption, masking, and other features ? Scripting languages such as Powershell, Bash, Perl, or Python ? Check Point, SourceFire and/or TippingPoint IPS ? Check Point and/or Cisco firewalls ? BlueCoat and/or ForcePoint web proxy ? Microsoft Windows Server 2008R2, 2012, 2016 ? Microsoft SCCM ? ArcSight Logger ? Rapid7 Nexpose ? MobileIron MDM ? Windows Certificate Services Reference : Need IT Security Engineer Consultant jobs from Latest listings added - LinkHello http://linkhello.com/jobs/technology/need-it-security-engineer-consultant_i7772
0 notes
Text
Project Remote Support on Bluecoat proxy By MaxMunus
Blue Coat's secure Web gateway (SWG), the Proxy SG, is among the leading products in the SWG marketplace. Like its competitors, Blue Coat Proxy SG is equipped with user authentication; Web filtering, data loss prevention and inspection.
The internet has enabled great things. It allows teams to collaborate from remote locations. It allows Bluecoat Proxy remote Support to provide exceptional support to its clients over it. Our clients love the fact that they can have support without waiting. Most software related issues can be solved through remote support.
Your employees will be surprised by the comprehensive services we can deliver remotely. With the help of easy to use language and concise explanations we enable and empower your people to solve the problem quickly. We are well known in the Bluecoat Proxy for our excellent remote support services. There are clients who have never had to meet us face to face simply because all their problems are remotely solved by us.
If you too need support immediately and remotely then we will create a solution tailor-made according to your needs. Our accommodating structure allows the smallest and the largest companies to benefit from it equally.
Flexible Mode:
1.Pay Per Ticket (PPT)
2. Pay per hour (PPH)
3. Pay Per Month (PPM)
4. Emergency Support (EMR)s– For any unplanned/ emergency/ SOS needs also our subject matter experts will be available to assist you.
For Remote Support on Bluecoat Proxy kindly feel free to contact us
Email Id: [email protected]
Contact No: +91-8553576305 (Whatsapp)
Skype Id: saurabhmaxmunus
http://www.maxmunus.com/page/Bluecoat-Proxy-Training
0 notes
Text
Network Security Engineer (H/F)
Au sein d’une équipe Télécom pluridisciplinaire (Radio, Téléphonie, Réseaux, Sécurity), assurer la gestion opérationnelle de l’infrastructure sécurité et principalement des Firewall internes et externes, de la zone DMZ ainsi que la gestion des accès VPN, surveiller le fonctionnement des systèmes et des équipements physiques et logiques des systèmes mentionnés ainsi que participer à l’optimalisation de l’infrastructure afin de contribuer à la disponibilité des systèmes opérationnels et continu, dans le cadre des normes de qualité et sécurité attendues.
Vous surveillez le fonctionnement des systèmes et des équipements physiques et logiques des systèmes mentionnés ainsi que participez à l’optimalisation de l’infrastructure afin de contribuer à la disponibilité des systèmes opérationnels en continu, dans le cadre des normes de qualité et sécurité attendues.
En détail :
* Vous développez un savoir-faire dans le domaine ICT Environnement Microsoft Active-Directory, Firewall, Proxy, Reverse-Proxy, Load balancers et autres équipements dédiés ou impliqués indirectement à la sécurisation informatique. * Vous développez un savoir-faire dans le domaine ICT Environnement Réseaux et plus particulièrement sur les plateformes TCP/IP Cisco, Juniper et Avaya. * Dans le cadre du domaine technique spécifique, vous contribuez dans des projets d’évolutions de l’infrastructure imposées par les nouvelles applications, les nouvelles technologie et les changements d’organisation. * Vous procédez à l’installation des Services et vérifiez leur fonctionnement sur base des instructions établies. En cas d’incidents, vous participez à l’analyse du dysfonctionnement et réalisez les interventions nécessaires pour rétablir le Service. * Vous contribuez à développer l’automatisation de l’adminstration technique de l’environnement technique et aux aspects techniques liés à la fourniture d’équipements et de Services par des tiers (Vendor Management). * Vous interfacez avec les clients tant internes qu’externes dans le cadre de la livraison des Services spécifiques.
* Vous disposez d’un Bachelor en informatique ou réseau ou experience équivalente. * Expérience pratique indispensable dans la gestion opérationnelle de firewall (Palo-Alto, Juniper SRX), des Proxy, reverse Proxys (BlueCoat), des loads balancers-Netscalers et de la gestion des tunnels VPN. * Connaissance approfondie de l’architecture et des normes en matière de sécurité IT. * Connaissance approfondie des différentes techniques de sécurisation. * Connaissance de base des processus IT Service Management (ITIL) * Vos qualités personnelles : capacité d’analyse et de synthèse, sens de l’organisation, problem- solver, orientation client et résultats, résistant au stress, flexible et un vrai teamplayer. * Vous êtes francophone et/ou néerlandophone et disposez d’une bonne connaissance de la seconde langue nationale. Vous avez une bonne connaissance de l’anglais.
* Une fonction variée et passionnante dans un environnement dynamique et convivial. * Un travail au sein d’une société qui offre une stabilité d’emploi, une vision long terme, et des projets qui impactent la vie quotidienne et la mobilité des gens. * Un épanouissement personnel par le biais de formations internes et externes sur mesure, avec des réelles perspectives de carrière à long terme. * Une qualité d’emploi et de vie professionnelle, avec un salaire compétitif accompagné par différents avantages extra-légaux (chèques-repas, assurances groupe et hospitalisation, 35 jours de congé payés par an, abonnement gratuit sur les réseaux STIB, TEC et De Lijn, et jusqu’à 75% de réduction sur l’abonnement de train domicile-travail, etc.)
https://ift.tt/2EAyvc2
0 notes
Text
Information Security Analyst
Role : Information Security Analyst Location : San Antonio, TX Project Duration: Contract 6+ Months Purpose of Job: Investigates, analyzes, and responds to suspicious behavior, attacks, and security breaches within the environments using a variety of cyber defense tools to identify and mitigate threats. Conducts log analysis and security event triage. Stays current with latest information security threats, exploits, trends, and intelligence. Job Requirements: Maintains awareness of the latest critical information security vulnerabilities, threats, and exploits. Assists in conducting routine security event triage and log analysis. Monitors networks, systems, and applications for routine to moderately complex suspicious behavior (includes Insider Threat), attacks, and security breaches. Assists in responding to cyber incidents, performing moderately complex analysis using security tools. Builds knowledge, understanding, and experience of disparate skills (e.g. networking, servers, coding, etc.) to figure out the malicious actor's tactics, techniques and procedures. Assists with conducting routine forensic analysis of comprised systems and determination of consequences. Under direct supervision, uses the discoveries from the incident response process to suggest basic improvements to existing detection capabilities and security controls. Documents findings of completed alerts. Assists with writing up findings on incidents. Minimum Requirements: Bachelor's Degree OR 4 additional years of related experience beyond the minimum required may be substituted in lieu of a degree. 2 or more years of related experience in Information Security and/or Information Technology to include accountability for moderately complex tasks and/or projects. Developing knowledge of function/discipline and demonstrated application of knowledge, skills and abilities towards work products. Developing level of business acumen in the areas of business operations, industry practices and emerging trends. Preferred : Experience in the technology and process of incident response, security event management, and log analysis Experience in disciplined blue team operations Experience researching emerging cyber threats to understand and present hacker methods and tactics, system vulnerabilities, and indicators of compromise Experience investigating, capturing, and analyzing events related to cyber incidents Experience planning and directing recovery activities including forensic event analysis, and malware evidence collection and reverse engineering Experience monitoring web proxy, email security, Web Application Firewall, Data Loss Prevention and Cloud Access Security Broker technology Experience in system administration applied to planning and researching and developing security policies, standards, and procedures across multiple platforms and applications Experience applying security principles, methodologies, and controls to new and emerging technology Specific platform/software experience needed: Phantom, ELK stack (Elastic, Logstash, Kibana), FireEye HX, Cylance Protect and Optics, Bluecoat ProxySG/MAA/CAS, Proofpoint, Powershell, VB Script (in order to analyze macro code), knowledge of the TCP/IP protocol suite -- Reference : Information Security Analyst jobs from Latest listings added - JobRealTime http://jobrealtime.com/jobs/technology/information-security-analyst_i3658
0 notes
Text
Information Security Analyst
Role : Information Security Analyst Location : San Antonio, TX Project Duration: Contract 6+ Months Purpose of Job: Investigates, analyzes, and responds to suspicious behavior, attacks, and security breaches within the environments using a variety of cyber defense tools to identify and mitigate threats. Conducts log analysis and security event triage. Stays current with latest information security threats, exploits, trends, and intelligence. Job Requirements: Maintains awareness of the latest critical information security vulnerabilities, threats, and exploits. Assists in conducting routine security event triage and log analysis. Monitors networks, systems, and applications for routine to moderately complex suspicious behavior (includes Insider Threat), attacks, and security breaches. Assists in responding to cyber incidents, performing moderately complex analysis using security tools. Builds knowledge, understanding, and experience of disparate skills (e.g. networking, servers, coding, etc.) to figure out the malicious actor's tactics, techniques and procedures. Assists with conducting routine forensic analysis of comprised systems and determination of consequences. Under direct supervision, uses the discoveries from the incident response process to suggest basic improvements to existing detection capabilities and security controls. Documents findings of completed alerts. Assists with writing up findings on incidents. Minimum Requirements: Bachelor's Degree OR 4 additional years of related experience beyond the minimum required may be substituted in lieu of a degree. 2 or more years of related experience in Information Security and/or Information Technology to include accountability for moderately complex tasks and/or projects. Developing knowledge of function/discipline and demonstrated application of knowledge, skills and abilities towards work products. Developing level of business acumen in the areas of business operations, industry practices and emerging trends. Preferred : Experience in the technology and process of incident response, security event management, and log analysis Experience in disciplined blue team operations Experience researching emerging cyber threats to understand and present hacker methods and tactics, system vulnerabilities, and indicators of compromise Experience investigating, capturing, and analyzing events related to cyber incidents Experience planning and directing recovery activities including forensic event analysis, and malware evidence collection and reverse engineering Experience monitoring web proxy, email security, Web Application Firewall, Data Loss Prevention and Cloud Access Security Broker technology Experience in system administration applied to planning and researching and developing security policies, standards, and procedures across multiple platforms and applications Experience applying security principles, methodologies, and controls to new and emerging technology Specific platform/software experience needed: Phantom, ELK stack (Elastic, Logstash, Kibana), FireEye HX, Cylance Protect and Optics, Bluecoat ProxySG/MAA/CAS, Proofpoint, Powershell, VB Script (in order to analyze macro code), knowledge of the TCP/IP protocol suite -- Reference : Information Security Analyst jobs Source: http://cvwing.com/jobs/technology/information-security-analyst_i4709
0 notes
Text
Information Security Analyst
Role : Information Security Analyst Location : San Antonio, TX Project Duration: Contract 6+ Months Purpose of Job: Investigates, analyzes, and responds to suspicious behavior, attacks, and security breaches within the environments using a variety of cyber defense tools to identify and mitigate threats. Conducts log analysis and security event triage. Stays current with latest information security threats, exploits, trends, and intelligence. Job Requirements: Maintains awareness of the latest critical information security vulnerabilities, threats, and exploits. Assists in conducting routine security event triage and log analysis. Monitors networks, systems, and applications for routine to moderately complex suspicious behavior (includes Insider Threat), attacks, and security breaches. Assists in responding to cyber incidents, performing moderately complex analysis using security tools. Builds knowledge, understanding, and experience of disparate skills (e.g. networking, servers, coding, etc.) to figure out the malicious actor's tactics, techniques and procedures. Assists with conducting routine forensic analysis of comprised systems and determination of consequences. Under direct supervision, uses the discoveries from the incident response process to suggest basic improvements to existing detection capabilities and security controls. Documents findings of completed alerts. Assists with writing up findings on incidents. Minimum Requirements: Bachelor's Degree OR 4 additional years of related experience beyond the minimum required may be substituted in lieu of a degree. 2 or more years of related experience in Information Security and/or Information Technology to include accountability for moderately complex tasks and/or projects. Developing knowledge of function/discipline and demonstrated application of knowledge, skills and abilities towards work products. Developing level of business acumen in the areas of business operations, industry practices and emerging trends. Preferred : Experience in the technology and process of incident response, security event management, and log analysis Experience in disciplined blue team operations Experience researching emerging cyber threats to understand and present hacker methods and tactics, system vulnerabilities, and indicators of compromise Experience investigating, capturing, and analyzing events related to cyber incidents Experience planning and directing recovery activities including forensic event analysis, and malware evidence collection and reverse engineering Experience monitoring web proxy, email security, Web Application Firewall, Data Loss Prevention and Cloud Access Security Broker technology Experience in system administration applied to planning and researching and developing security policies, standards, and procedures across multiple platforms and applications Experience applying security principles, methodologies, and controls to new and emerging technology Specific platform/software experience needed: Phantom, ELK stack (Elastic, Logstash, Kibana), FireEye HX, Cylance Protect and Optics, Bluecoat ProxySG/MAA/CAS, Proofpoint, Powershell, VB Script (in order to analyze macro code), knowledge of the TCP/IP protocol suite -- Reference : Information Security Analyst jobs Source: http://jobrealtime.com/jobs/technology/information-security-analyst_i3658
0 notes