#biometric authentication project
Explore tagged Tumblr posts
Text
Biometrics is the most suitable means of identifying and authenticating individuals in a reliable and fast way through unique biological characteristics. Unlike traditional authentication methods like passwords or PINs, which can be easily forgotten or stolen, biometrics relies on inherent and distinctive attributes of a person. These attributes are difficult to replicate, making biometric authentication a powerful tool for ensuring the integrity and security of sensitive information, physical access control, and various other applications.
#biometricauthentication#biometricstechnology#biometrics#limitlesstech#biometricauthenticationsystem#futureofbiometrics#biometricauthenticationtechnology#facialrecognitiontechnology#biometricdata#biometricdevice#biometricsystem
#biometrics technology#the future of personal security#biometrics authenticaton the future of personal security#LimitLess Tech 888#biometrics#facial recognition#biometric authentication#biometrics authentication#biometric authentication system#the future of biometrics#the future of biometric authentication#biometric#biometric authentication technology#facial recognition technology#biometric authentication project#future tech#biometric device#biometric system
0 notes
Text
Biometrics is the most suitable means of identifying and authenticating individuals in a reliable and fast way through unique biological characteristics. Unlike traditional authentication methods like passwords or PINs, which can be easily forgotten or stolen, biometrics relies on inherent and distinctive attributes of a person. These attributes are difficult to replicate, making biometric authentication a powerful tool for ensuring the integrity and security of sensitive information, physical access control, and various other applications.
However, it also comes with challenges, such as privacy concerns, potential security vulnerabilities, and the need for robust protection of biometric data. As technology continues to advance, biometric authentication is likely to become even more integral to various aspects of our lives, from unlocking smartphones to securing critical infrastructure.
#biometricauthentication#biometricstechnology#biometrics#limitlesstech#biometricauthenticationsystem#futureofbiometrics#biometricauthenticationtechnology#facialrecognitiontechnology#biometricdata#biometricdevice#biometricsystem
#biometrics technology#the future of personal security#biometrics authenticaton the future of personal security#LimitLess Tech 888#biometrics#facial recognition#biometric authentication#biometrics authentication#biometric authentication system#the future of biometrics#the future of biometric authentication#biometric#biometric authentication technology#facial recognition technology#biometric authentication project#future tech#biometric device#biometric system
0 notes
Text
Best Practices for Data Lifecycle Management to Enhance Security
Securing all communication and data transfer channels in your business requires thorough planning, skilled cybersecurity professionals, and long-term risk mitigation strategies. Implementing global data safety standards is crucial for protecting clients’ sensitive information. This post outlines the best practices for data lifecycle management to enhance security and ensure smooth operations.
Understanding Data Lifecycle Management
Data Lifecycle Management (DLM) involves the complete process from data source identification to deletion, including streaming, storage, cleansing, sorting, transforming, loading, analytics, visualization, and security. Regular backups, cloud platforms, and process automation are vital to prevent data loss and database inconsistencies.
While some small and medium-sized businesses may host their data on-site, this approach can expose their business intelligence (BI) assets to physical damages, fire hazards, or theft. Therefore, companies looking for scalability and virtualized computing often turn to data governance consulting services to avoid these risks.
Defining Data Governance
Data governance within DLM involves technologies related to employee identification, user rights management, cybersecurity measures, and robust accountability standards. Effective data governance can combat corporate espionage attempts and streamline database modifications and intel sharing.
Examples of data governance include encryption and biometric authorization interfaces. End-to-end encryption makes unauthorized eavesdropping more difficult, while biometric scans such as retina or thumb impressions enhance security. Firewalls also play a critical role in distinguishing legitimate traffic from malicious visitors.
Best Practices in Data Lifecycle Management Security
Two-Factor Authentication (2FA) Cybercriminals frequently target user entry points, database updates, and data transmission channels. Relying solely on passwords leaves your organization vulnerable. Multiple authorization mechanisms, such as 2FA, significantly reduce these risks. 2FA often requires a one-time password (OTP) for any significant changes, adding an extra layer of security. Various 2FA options can confuse unauthorized individuals, enhancing your organization’s resilience against security threats.
Version Control, Changelog, and File History Version control and changelogs are crucial practices adopted by experienced data lifecycle managers. Changelogs list all significant edits and removals in project documentation, while version control groups these changes, marking milestones in a continuous improvement strategy. These tools help detect conflicts and resolve issues quickly, ensuring data integrity. File history, a faster alternative to full-disk cloning, duplicates files and metadata in separate regions to mitigate localized data corruption risks.
Encryption, Virtual Private Networks (VPNs), and Antimalware VPNs protect employees, IT resources, and business communications from online trackers. They enable secure access to core databases and applications, maintaining privacy even on public WiFi networks. Encrypting communication channels and following safety guidelines such as periodic malware scans are essential for cybersecurity. Encouraging stakeholders to use these measures ensures robust protection.
Security Challenges in Data Lifecycle Management
Employee Education Educating employees about the latest cybersecurity implementations is essential for effective DLM. Regular training programs ensure that new hires and experienced executives understand and adopt best practices.
Voluntary Compliance Balancing convenience and security is a common challenge. While employees may complete security training, consistent daily adoption of guidelines is uncertain. Poorly implemented governance systems can frustrate employees, leading to resistance.
Productivity Loss Comprehensive antimalware scans, software upgrades, hardware repairs, and backups can impact productivity. Although cybersecurity is essential, it requires significant computing and human resources. Delays in critical operations may occur if security measures encounter problems.
Talent and Technology Costs Recruiting and developing an in-house cybersecurity team is challenging and expensive. Cutting-edge data protection technologies also come at a high cost. Businesses must optimize costs, possibly through outsourcing DLM tasks or reducing the scope of business intelligence. Efficient compression algorithms and hybrid cloud solutions can help manage storage costs.
Conclusion
The Ponemon Institute found that 67% of organizations are concerned about insider threats. Similar concerns are prevalent worldwide. IBM estimates that the average cost of data breaches will reach 4.2 million USD in 2023. The risks of data loss, unauthorized access, and insecure PII processing are rising. Stakeholders demand compliance with data protection norms and will penalize failures in governance.
Implementing best practices in data lifecycle management, such as end-to-end encryption, version control systems, 2FA, VPNs, antimalware tools, and employee education, can significantly enhance security. Data protection officers and DLM managers can learn from expert guidance, cybersecurity journals, and industry peers’ insights to navigate complex challenges. Adhering to privacy and governance directives offers legal, financial, social, and strategic advantages, boosting long-term resilience against the evolving threats of the information age. Utilizing data governance consulting services can further ensure your company is protected against these threats.
3 notes
·
View notes
Text
TL;DR: in this post, i wax on about the abandoned concept album/multimedia project Lifehouse by Pete Townshend/The Who in the context of algorithms and artworks
people on Twitter aren't understanding that this is an ad for a scifi novel. it sounds interesting, to a degree.

the first sentence reminds me of [The Who's] Pete Townshend's Lifehouse, still one of the most fascinating musical experiments i've ever read about.
i wish i knew about all that back when the Lifehouse Method website was a thing. for those unaware, it was a site created by Pete in conjunction with composer Lawrence Ball and software developer Dave Snowdon in which someone could input their personal data and generate "authentic musical 'portraits,'" pieces of music customized via algorithms that work based on whatever data you input. if you know anything about The Who, you'll probably recognize this as a facet of what would eventually become the album Who's Next, Lifehouse, a huge multimedia project involving a rock opera album, live performances with audience participation and complex tech on stage, a movie, who knows what else.

https://archive.is/8tYoM
i've always wished i could do one of these "musical portraits." i remember when I first heard about algorithmic (i refuse to call it AI because it isn't true AI) music generators, this was the first thing i thought of. back when they were in a rudimentary state, i played around with one for my own amusement (not for my own music, all that comes from my own head unfortunately for you), and while it was fascinating, it didn't go far enough in the direction i hoped. thinking of OpenAI's MuseNet, it takes a few notes worth of MIDI data & a style suggestion and then kinda randomly guesses what would be a good fit after those notes.
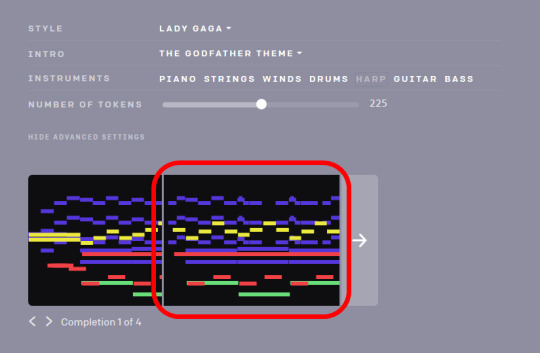
<image sourced from https://gigazine.net/gsc_news/en/20190426-muse-net>
and y'know, it makes for some fun meme videos:
youtube
youtube
youtube
<shoutout to the papaya>
but you can also see it only goes so far, and still requires musical input. it isn't quite on the level of being usable for much. and it really isn't quite the same. it's using inputted data, but not, say, biometric or biographical data. it's musical parameters that are being input as the data.
i really want to one day see a true realization of Lifehouse. one of my wildest goals is to be the one to do that. admittedly, i feel like in the current artistic climate the art world might no longer be ready for it; people would see it, instantly think "AI ART EW," and back away. but in this case, i don't feel like that's a fair assessment of what the concept is. the idea was to find each person's unique signature melody via these musical portraits. it isn't meant for anything really beyond personal identification, when it comes down to it. it fascinates me from a musical standpoint, and as a person who holds a psychology degree. imagine what someone can learn about oneself via this process! would your musical portrait be different at different points in your life? what could you tell about your personality from a single melody, or about your life history, or your beliefs and values? how would all of that reflect in your music? what genre is your soul? could a musical portrait truly capture any of that? with sufficiently advanced tech, sure, but idk if we're there yet.
heck imagine the therapeutic implications! imagine this tech being used in an art/music therapy setting, in which you work with a therapist to input your data, get a melody, and then use that melody with whatever form of musical expression you prefer (e.g. if you prefer to play the piano, guitar, a DAW, etc). what would you and your therapist be able to learn about you?
i truly do believe that, when it comes down to it, everyone has their own musical identification, "a song in their heart" if you will. i wish to expose people's hearts to get that music out, so that people may hopefully understand themselves better.
we might actually be at the level of tech necessary to truly realize a project like Lifehouse, but the tech isn't being used in this way. our current tech relies on predictive algorithms that kinda mostly draw on established musical forms, tradition, and there are only so many notes in the musical alphabet and only so many combinations and permutations thereof. a true realization of this tech would work, say, maybe in a similar way to how Pokémon speedrunners essentially break the game and essentially reprogram it to do what they want via a series of unexpected inputs. arbitrary code execution is what that's called, and i bet a similar function might help greatly in creating a uniquely generated musical portrait. because, when it comes down to it, are we not all Glitch Pokémon who cannot be contained by the boundaries of our programming?
youtube
anyway that was a long ramble. feel free to gimme feedback like you're a guitar held up to an amp or feedback like an echo chamber, whichever you prefer. this post idk if it'll make both pro & anti AI people mad or not, but that's what happens when your position on a thing is more complicated than a simple binary.
currently homeless still, so please help me if you can:
My partner's donate links are here: https://linktr.ee/IzukuLeeYoung. that's the best place you can send us money to keep us in our current hotel room and off the street.
https://odiohi.me/pages/product-categories - if you wanna help me by buying my wares (including my music)
To support me directly:
https://ko-fi.com/NoraQRosa
https://cash.app/NoraQRosa
https://patreon.com/NoraQRosa
#artistic musings#essay#“AI art” really isn't true AI. when we finally realize that true AI actually lives and exists among us...#...you know we're gonna see them take offense to how we currently talk about AI and algorithms and be very upset#people don't care because they don't see AI as people but as new slaves.#they don't want artificial intelligence. they want custom-made servants.#we aren't at a point where we see true AI making art#we only currently see uncreatives abusing algorithms and then going “look i did this” when all they did was type out a few words.#at least Lifehouse was for a purpose and not for techbros to use and abuse!#it actually has a fascinating concept that i fear has been corrupted in this day and age. we need to fix that.#homeless plural trans queer artist in need of dire mutual aid#Youtube
2 notes
·
View notes
Text
Identity Verification Market
Identity Verification Market Size, Share, Trends: Experian PLC Leads
Rising Adoption of Digital Services and Online Transactions
Market Overview:
The global Identity Verification Market size was valued at USD XX billion in 2023 and is projected to grow at a CAGR of 16.2% during the forecast period, reaching USD YY billion by 2031. North America accounted for the largest market share of YY% in 2023, followed by Europe and Asia-Pacific. Key factors driving the market growth include increasing fraudulent activities, stringent government regulations, and the growing adoption of digital services across various industries. Identity verification has become an essential component of many enterprises, particularly in the digital age, when online transactions and remote access to services are prevalent. The market is rapidly expanding due to the increased demand for secure and reliable identity verification solutions to avoid identity theft, financial crime, and unauthorized access to sensitive data.
DOWNLOAD FREE SAMPLE
Market Trends:
The expanding digitisation of businesses including banking, healthcare, and e-commerce has increased the need for strong identity verification systems. As more businesses offer their services online, the importance of adequately authenticating user identities grows. According to a McKinsey & Company analysis, the COVID-19 pandemic has advanced the use of digital technologies by many years, bolstering the identity verification industry.
Market Segmentation:
The solutions category leads the identity verification sector, accounting for more than YY% of the global market by 2023. This topic covers a wide variety of identity verification methods, including biometric verification, document verification, and digital identity verification. The growing demand for secure and seamless user onboarding processes across a variety of businesses is propelling the industry ahead. IDEMIA, a global pioneer in identification technology, will introduce its new Identification Verification Suite in March 2022. This suite brings together powerful biometric and AI capabilities to give a comprehensive identity verification solution.
Market Key Players:
The identity verification industry is highly competitive, with established organisations and young startups fighting for market dominance. Key companies such as Experian PLC, IDEMIA, Jumio Corporation, LexisNexis Risk Solutions, Onfido, Acuant, Inc., Mitek Systems, Inc., Thales Group, Shufti Pro, and AU10TIX dominate the market.
Contact Us:
Name: Hari Krishna
Email us: [email protected]
Website: https://aurorawaveintellects.com/
0 notes
Text
Electronic Access Control Systems Market
Electronic Access Control Systems Market Size, Share, Trends: Honeywell International Inc. Lead
Rising Demand for Advanced Security Solutions Driving Market Growth Worldwide
Market Overview:
The Electronic Access Control Systems Market is experiencing robust growth, with a projected CAGR of 8.5% from 2024 to 2031. North America currently leads the market, driven by advanced technological infrastructure, increasing security concerns, and stringent regulatory requirements. Key metrics include rising adoption of IoT and cloud-based access control solutions, growing demand for integration with smart building systems, and increasing focus on contactless access control technologies.
The Electronic Access Control Systems market is rapidly rising as a result of the growing demand for enhanced security measures across various sectors, an increase in terrorist activities and security breaches, and the growing trend of smart homes and buildings. The COVID-19 pandemic has further accelerated the adoption of these technologies, particularly contactless and mobile access control solutions.
DOWNLOAD FREE SAMPLE
Market Trends:
The integration of Artificial Intelligence (AI) and Machine Learning (ML) technologies is transforming the Electronic Access Control Systems market. These advanced technologies can analyze access patterns, detect anomalies, and anticipate potential security threats in real time. AI-powered facial recognition systems, for example, are becoming more sophisticated, with improved accuracy and processing speed.
Recent advancements include the introduction of behavioral biometrics, which use AI algorithms to identify unique patterns in a person's behavior, such as gait or typing rhythm, for authentication purposes. This adds an additional layer of security beyond traditional biometric methods. A study published in the Journal of Information Security and Applications found that AI-enhanced access control systems could reduce false acceptance rates by up to 50% compared to traditional systems.
Market Segmentation:
The Biometric segment is expected to dominate the Electronic Access Control Systems market during the forecast period. This segment's growth is primarily driven by rising demand for highly secure and convenient access control solutions, advances in biometric technology, and increased adoption of multi-factor authentication systems.
Recent advancements in the biometric segment have focused on improving accuracy, speed, and user experience. For example, several manufacturers have introduced advanced facial recognition systems capable of accurately identifying individuals even while wearing masks, a feature that has proven particularly valuable in the post-pandemic environment. These systems utilize deep learning algorithms to analyze various facial features, ensuring high accuracy while minimizing false rejections.
The use of multimodal biometric systems, which combine two or more biometric modalities (such as fingerprint and facial recognition), has also seen significant growth. According to a Biometrics Institute survey, 65% of organizations implementing biometric access control are currently using or plan to implement multimodal solutions within the next two years. These systems offer enhanced security and flexibility, adapting to diverse user needs and environmental conditions.
Additionally, advancements in behavioral biometrics are expanding the capabilities of access control systems. Technologies that can analyze keystroke dynamics, gait recognition, and even cardiac signatures are being integrated into access control solutions, enabling continuous authentication beyond the initial point of entry. According to a study published in IEEE Transactions on Information Forensics and Security, behavioral biometrics can prevent unauthorized access attempts by up to 98% when combined with traditional biometric methods.
Market Key Players:
Prominent players in the Electronic Access Control Systems Market include:
Honeywell International Inc.
Johnson Controls International plc
ASSA ABLOY AB
Dormakaba Holding AG
Allegion plc
Bosch Security Systems
Siemens AG
NEC Corporation
Identiv, Inc.
Gemalto N.V. (Thales Group)
These leading companies are driving market growth through innovation, strategic collaborations, and expanding their product portfolios.
Contact Us:
Name: Hari Krishna
Email us: [email protected]
Website: https://aurorawaveintellects.com/
0 notes
Text
What Are the Costs Associated with Fintech Software Development?

The fintech industry is experiencing exponential growth, driven by advancements in technology and increasing demand for innovative financial solutions. As organizations look to capitalize on this trend, understanding the costs associated with fintech software development becomes crucial. Developing robust and secure applications, especially for fintech payment solutions, requires significant investment in technology, expertise, and compliance measures. This article breaks down the key cost factors involved in fintech software development and how businesses can navigate these expenses effectively.
1. Development Team and Expertise
The development team is one of the most significant cost drivers in fintech software development. Hiring skilled professionals, such as software engineers, UI/UX designers, quality assurance specialists, and project managers, requires a substantial budget. The costs can vary depending on the team’s location, expertise, and experience level. For example:
In-house teams: Employing full-time staff provides better control but comes with recurring costs such as salaries, benefits, and training.
Outsourcing: Hiring external agencies or freelancers can reduce costs, especially if the development team is located in regions with lower labor costs.
2. Technology Stack
The choice of technology stack plays a significant role in the overall development cost. Building secure and scalable fintech payment solutions requires advanced tools, frameworks, and programming languages. Costs include:
Licenses and subscriptions: Some technologies require paid licenses or annual subscriptions.
Infrastructure: Cloud services, databases, and servers are essential for hosting and managing fintech applications.
Integration tools: APIs for payment processing, identity verification, and other functionalities often come with usage fees.
3. Security and Compliance
The fintech industry is heavily regulated, requiring adherence to strict security standards and legal compliance. Implementing these measures adds to the development cost but is essential to avoid potential fines and reputational damage. Key considerations include:
Data encryption: Robust encryption protocols like AES-256 to protect sensitive data.
Compliance certifications: Obtaining certifications such as PCI DSS, GDPR, and ISO/IEC 27001 can be costly but are mandatory for operating in many regions.
Security audits: Regular penetration testing and vulnerability assessments are necessary to ensure application security.
4. Customization and Features
The complexity of the application directly impacts the cost. Basic fintech solutions may have limited functionality, while advanced applications require more extensive development efforts. Common features that add to the cost include:
User authentication: Multi-factor authentication (MFA) and biometric verification.
Real-time processing: Handling high volumes of transactions with minimal latency.
Analytics and reporting: Providing users with detailed financial insights and dashboards.
Blockchain integration: Leveraging blockchain for enhanced security and transparency.
5. User Experience (UX) and Design
A seamless and intuitive user interface is critical for customer retention in the fintech industry. Investing in high-quality UI/UX design ensures that users can navigate the platform effortlessly. Costs in this category include:
Prototyping and wireframing.
Usability testing.
Responsive design for compatibility across devices.
6. Maintenance and Updates
Fintech applications require ongoing maintenance to remain secure and functional. Post-launch costs include:
Bug fixes and updates: Addressing issues and releasing new features.
Server costs: Maintaining and scaling infrastructure to accommodate user growth.
Monitoring tools: Real-time monitoring systems to track performance and security.
7. Marketing and Customer Acquisition
Once the fintech solution is developed, promoting it to the target audience incurs additional costs. Marketing strategies such as digital advertising, influencer partnerships, and content marketing require significant investment. Moreover, onboarding users and providing customer support also contribute to the total cost.
8. Geographic Factors
The cost of fintech software development varies significantly based on geographic factors. Development in North America and Western Europe tends to be more expensive compared to regions like Eastern Europe, South Asia, or Latin America. Businesses must weigh the trade-offs between cost savings and access to high-quality talent.
9. Partnering with Technology Providers
Collaborating with established technology providers can reduce development costs while ensuring top-notch quality. For instance, Xettle Technologies offers comprehensive fintech solutions, including secure APIs and compliance-ready tools, enabling businesses to streamline development processes and minimize risks. Partnering with such providers can save time and resources while enhancing the application's reliability.
Cost Estimates
While costs vary depending on the project's complexity, here are rough estimates:
Basic applications: $50,000 to $100,000.
Moderately complex solutions: $100,000 to $250,000.
Highly advanced platforms: $250,000 and above.
These figures include development, security measures, and initial marketing efforts but may rise with added features or broader scope.
Conclusion
Understanding the costs associated with fintech software development is vital for effective budgeting and project planning. From assembling a skilled team to ensuring compliance and security, each component contributes to the total investment. By leveraging advanced tools and partnering with experienced providers like Xettle Technologies, businesses can optimize costs while delivering high-quality fintech payment solutions. The investment, though significant, lays the foundation for long-term success in the competitive fintech industry.
0 notes
Text
Identity Verification Market Report 2024: Key Trends, Growth Drivers, and Future Opportunities

Identity Verification Market Report 2024: Key Trends, Growth Drivers, and Future Opportunities
Straits Research Unveils Comprehensive Report on the Identity Verification Market
Pune, India – December 13, 2024 – Straits Research, a leading market intelligence firm, has released an extensive report on the global Identity Verification Market, projecting significant growth and highlighting key trends, driving factors, and opportunities. According to the report, the global Identity Verification Market was valued at USD 11.4 billion in 2023 and is expected to reach USD 13.3 billion in 2024. The market is projected to grow to USD 44.6 billion by 2032, at a compound annual growth rate (CAGR) of 16.4% during the forecast period (2024–2032).
Request a Free Sample (Full Report Starting from USD 1850): https://straitsresearch.com/report/identity-verification-market/request-sample
Market Key Trends
The Identity Verification Market is undergoing rapid transformation, driven by several key trends:
Advancements in Technology: The integration of artificial intelligence (AI), machine learning (ML), and blockchain in identity verification solutions is enhancing accuracy, speed, and security.
Growing Cybersecurity Threats: Rising incidents of identity theft and fraud are propelling the demand for robust identity verification systems.
Regulatory Compliance: Stringent regulations and compliance requirements across various industries are mandating the adoption of identity verification solutions.
Digital Transformation: The global shift towards digitalization, especially in the financial and government sectors, is accelerating the need for identity verification solutions.
Driving Factors
Several factors are driving the growth of the Identity Verification Market:
Increasing Online Transactions: With the surge in online banking, e-commerce, and digital payments, the need for secure identity verification is paramount.
Rising Need for Fraud Prevention: Organizations are increasingly focusing on fraud prevention to protect sensitive information and maintain customer trust.
Government Initiatives: Governments worldwide are implementing digital identity programs to streamline citizen services and enhance security.
Opportunities
The Identity Verification Market presents numerous opportunities for growth and innovation:
Emerging Markets: Rapid economic growth and digital adoption in emerging markets offer significant opportunities for identity verification solution providers.
Technological Innovations: Continuous advancements in biometrics, AI, and blockchain are creating new avenues for product development and enhancement.
Partnerships and Collaborations: Strategic partnerships and collaborations between technology providers, financial institutions, and government agencies are driving market expansion.
Identity Verification Market Segmentation
The Identity Verification Market is segmented based on components, types, deployment modes, organization sizes, and verticals.
By Component
Solution: Comprehensive identity verification solutions integrating various technologies to ensure accurate and secure identity authentication.
Service: Professional services, including consulting, integration, and support, to assist organizations in deploying and managing identity verification systems.
By Type
Biometrics: Identity verification methods using biometric data such as fingerprints, facial recognition, and iris scans.
Non-biometrics: Traditional methods including document verification, knowledge-based authentication, and two-factor authentication.
By Deployment Mode
On-premises: Solutions deployed on the organization's local servers, offering control and customization.
Cloud: Cloud-based identity verification solutions providing scalability, flexibility, and remote access.
By Organization Size
SMEs: Small and Medium Enterprises leveraging identity verification solutions to enhance security and compliance.
Large Enterprises: Large organizations adopting advanced identity verification systems to manage large-scale operations and mitigate risks.
By Verticals
BFSI: Banks, financial institutions, and insurance companies utilizing identity verification to prevent fraud and comply with regulations.
Government and Defence: Government agencies and defense sectors implementing identity verification for secure access and citizen services.
Healthcare & Life Sciences: Hospitals and healthcare providers ensuring patient identity verification to maintain data security and compliance.
Retail and E-Commerce: E-commerce platforms and retailers adopting identity verification to secure transactions and enhance customer trust.
IT & ITES: IT and IT-enabled services companies using identity verification to protect sensitive information and prevent data breaches.
Energy and Utilities: Companies in the energy and utilities sector implementing identity verification for secure access to critical infrastructure.
Others: Additional sectors including education, travel, and gaming adopting identity verification to enhance security and user experience.For more details: https://straitsresearch.com/report/identity-verification-market/segmentation
List of Key Players in Identity Verification Market
Prominent players in the Identity Verification Market include:
Equifax, Inc.
Thales Group S.A.
Experian Plc
Acuant, Inc.
Mitek Systems, Inc.
TransUnion LLC.
GB Group PLC
IDEMIA
Intellicheck Inc.
Nuance Communications Inc.Detailed Table of Content of the Identity Verification Market Report: https://straitsresearch.com/report/identity-verification-market/toc
Conclusion
The Identity Verification Market is poised for substantial growth, driven by technological advancements, increasing cybersecurity threats, and regulatory compliance requirements. Straits Research's comprehensive report provides valuable insights and strategic recommendations to help businesses navigate this dynamic market landscape.
Purchase the Report: https://straitsresearch.com/buy-now/identity-verification-market
About Straits Research
Straits Research is a top provider of business intelligence, specializing in research, analytics, and advisory services, with a focus on delivering in-depth insights through comprehensive reports.
Contact Us:
Email: [email protected]
Address: 825 3rd Avenue, New York, NY, USA, 10022
Phone: +1 646 905 0080 (US), +91 8087085354 (India), +44 203 695 0070 (UK)
#Identity Verification Market#2024 Market Report#Identity Verification Trends#Market Growth#Identity Verification Solutions#Straits Research
0 notes
Text
Future of Smart Hospitality Market: Size, Growth & Revenue Forecast 2024-2032
The Smart Hospitality Market Revenue was valued at USD 17.55 billion in 2023 and is forecasted to reach an astounding USD 186.10 billion by 2032, growing at an exceptional CAGR of 30% from 2024 to 2032. The adoption of cutting-edge technologies to enhance guest experiences and streamline operations is the driving force behind the market's rapid expansion.

Key Market Dynamics
The surge in demand for personalized guest experiences and the integration of IoT (Internet of Things) in hospitality management are key factors accelerating the growth of the smart hospitality market. Hotels and resorts worldwide are leveraging smart technologies to provide seamless services such as automated check-ins, AI-enabled customer service, and energy-efficient systems, significantly enhancing operational efficiency and guest satisfaction.
In addition to IoT, advancements in artificial intelligence (AI), cloud computing, and big data analytics are revolutionizing the hospitality sector. These technologies enable real-time insights into guest preferences, predictive maintenance for facilities, and tailored marketing strategies, which collectively create a competitive edge for hospitality providers.
The rise of eco-conscious travelers and the global emphasis on sustainability are further propelling the adoption of smart hospitality solutions. Energy management systems and smart building technologies allow hotels to optimize resource usage, reduce carbon footprints, and meet sustainability goals while delivering exceptional guest experiences.
Get Free Sample Report@ https://www.snsinsider.com/sample-request/3524
Regional Insights
The North American market leads in adopting smart hospitality technologies, supported by robust IT infrastructure and the presence of major technology providers. However, Asia-Pacific is emerging as a high-growth region, driven by a booming tourism industry, rapid urbanization, and increasing investments in smart city projects. Europe also holds a significant share, benefiting from widespread adoption of sustainable practices and advanced digital ecosystems.
Future Outlook
The smart hospitality market is on the cusp of a technological revolution, with innovations in AI-powered chatbots, biometric authentication, and smart room solutions shaping the future of the industry. Collaboration between technology developers and hospitality brands will continue to foster innovation, creating opportunities for new revenue streams and enhanced customer experiences.
The ongoing digital transformation in the hospitality industry promises a dynamic and sustainable future where guest satisfaction and operational efficiency go hand in hand.
About Us
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us
Akash Anand – Head of Business Development & Strategy Email: [email protected] Phone: +1-415-230-0044 (US) | +91-7798602273 (IND)
#Smart Hospitality#Smart Hospitality Market#Smart Hospitality Market Size#Smart Hospitality Market Share#Smart Hospitality Market Growth#Market Research
0 notes
Text
Keyless Vehicle Access Control Market Report

Keyless Vehicle Access Control Market Report
The global Keyless Vehicle Access Control Market size was valued at USD 4.45 Billion in 2023 and is projected to reach from USD 4.70 Billion in 2024 to USD 7.58 Billion by 2032, growing at a CAGR of 5.3% during the forecast period (2024–2032).
Industry Key Trends
Growing demand for convenience, safety, and security features in vehicles
Increasing adoption of advanced technologies such as biometric authentication and smartphone app-based access control
Rising focus on vehicle security and anti-theft systems
Growing demand for luxury and premium vehicles
Increasing adoption of keyless vehicle access control systems in the aftermarket
Request a Free Sample: https://straitsresearch.com/report/keyless-vehicle-access-control-market/request-sample
Keyless Vehicle Access Control Market Size and Share
The global Keyless Vehicle Access Control Market is highly competitive, with the presence of several established players. The market is dominated by players such as Denso Corporation, Hella GmbH & Co. KGaA, and ZF Friedrichshafen AG.
Keyless Vehicle Access Control Market Statistics
The passenger vehicle segment accounted for the largest market share in 2023
The OEM segment accounted for the largest market share in 2023
The remote keyless entry system segment accounted for the largest market share in 2023
The Asia-Pacific region accounted for the largest market share in 2023
Detailed Table of Content:https://straitsresearch.com/report/keyless-vehicle-access-control-market/toc
Regional Trends
The global Keyless Vehicle Access Control Market is segmented into North America, Europe, Asia-Pacific, and LAMEA.
North America: The North American market is driven by the growing demand for luxury and premium vehicles, and the increasing adoption of advanced technologies such as biometric authentication and smartphone app-based access control.
Europe: The European market is driven by the growing focus on vehicle security and anti-theft systems, and the increasing adoption of keyless vehicle access control systems in the aftermarket.
Asia-Pacific: The Asia-Pacific market is driven by the growing demand for passenger vehicles, and the increasing adoption of remote keyless entry systems.
LAMEA: The LAMEA market is driven by the growing demand for commercial vehicles, and the increasing adoption of keyless vehicle access control systems in the OEM segment.
Keyless Vehicle Access Control Market Segmentations
By Type
Passive Keyless Entry Systems: These systems use a key fob to unlock and start the vehicle.
Remote Keyless Entry System: These systems use a remote control to unlock and start the vehicle.
By End-user
Original Equipment Manufacturer (OEMs): OEMs install keyless vehicle access control systems in vehicles during the manufacturing process.
Aftermarket: The aftermarket segment includes the installation of keyless vehicle access control systems in vehicles after they have been purchased.
By Application
Passenger Vehicle: Keyless vehicle access control systems are used in passenger vehicles such as cars, SUVs, and vans.
Commercial Vehicle: Keyless vehicle access control systems are used in commercial vehicles such as trucks, buses, and taxis.
Market Segmentation: https://straitsresearch.com/report/keyless-vehicle-access-control-market/segmentation
Top Players in Keyless Vehicle Access Control Market
Denso Corporation (Japan)
Hella GmbH & Co. KGaA (Germany)
ZF Friedrichshafen AG (Germany)
Calsonic Kansei Corporation (Japan)
Continental AG (Germany)
Lear Corporation (the U.S.)
Delphi Automotive LLP (Ireland)
Alps Automotive Inc. (Japan)
TRW Automotive Holdings Corporation
Mitsubishi Electric Group (Japan)
Valeo S.A (France)
Omron Automotive Electronics Co. Ltd (Nidec) (Japan)
Marquardt Switches Inc. (Germany)
Atmel Corporation (the U.S.)
Robert Bosch GmbH (Germany)
Buy Full Report: https://straitsresearch.com/buy-now/keyless-vehicle-access-control-market
0 notes
Text
The Future of Market Research: Virtual Reality and Immersive Experiences
Market research is an integral part of customer behavior and experience personalization strategies. It provides necessary insights into consumers' product preferences and market trends. Conventional techniques such as one-to-one surveys, focus groups, or secondary data collection have been standard in this field. However, technological enhancements have equipped modern market researchers with novel tools like virtual reality. This post will discuss the future of market research, including the potential of virtual reality and immersive experiences.
What is Virtual Reality?
Virtual reality (VR) simulates a computer-aided audiovisual environment. It can mimic reality or include experiences from a fantasy. Its adequate implementation will resolve many customer profiling issues and data quality limitations haunting professionals in market research consulting. Moreover, immersing users in a realistic simulation allows VR projects to provide more dynamic or nuanced insights into consumer behavior.
What Are the Benefits of Virtual Reality in Market Research?
1| Immersive Experience and Consumer Behavior
One of VR's key advantages in market research is the ease of creating highly immersive experiences. Unlike traditional methods, VR can simulate a complete environment. That allows researchers to observe how consumers interact with products or services in a lifelike context. Besides, this immersion can lead to more accurate and authentic responses. After all, participants are less likely to be influenced by the artificiality of a traditional research setting. The required detailed, realistic simulation is often complex to accomplish with ordinary methods.
2| Emotional and Behavioral Insights
Another significant benefit of VR integration is its ability to interpret emotional responses. However, you require biometric sensors to track heart rate and eye movements. The acquired data will assist in measuring physiological responses to different stimuli within the virtual environment. This data on reactions can facilitate valuable insights into how consumers feel about a product. You can also check their positive or negative sentiments toward an advertisement or brand.
How to Utilize VR in Market Research Based on Your Target Industry?
According to market intelligence consulting experts, several industries already leverage VR for customer insights. The following use cases demonstrate the versatility and effectiveness of this technology.
1| Retail and Consumer Goods
Virtual reality software can help retailers try multiple store layouts to see how customer dwell time changes. Remember, product placements and marketing tactics affect how much customers buy before the final checkout. Therefore, companies like Walmart and IKEA have experimented with virtual stores. They also intend to gather consumer feedback before making costly and permanent changes to their physical store layouts in the real world. This precaution allows them to optimize their strategies based on data-driven insights rather than intuition or guesswork.
2| Automotive Industry
Automotive companies utilize VR systems to offer virtual car showrooms and deliver simulated test-driving experiences. This use case enhances the customer experience. Brands get this valuable data to investigate ever-changing consumer preferences and purchasing behaviors. Consider Audi and Ford. They have developed virtual test drives, allowing potential buyers to experience their vehicles. They can configure various scenarios for virtual driving sessions. Later, they might gather stakeholder feedback influencing future car designs, collision safety measures, handling methods, or fuel-efficiency parameters.
3| Healthcare and Pharmaceuticals
In healthcare, clinicians and universities will leverage VR to simulate medical environments for apprentices' training and evaluating new medical devices and treatments. Pharmaceutical companies employ VR to simulate clinical trials. Doing so allows medical professionals to examine patient reactions to new drugs. Although these trials are programmatic, they enable better forecasts for real-world healthcare outcomes. As a result, the stakeholders can accelerate research and enhance the accuracy of their findings.
Challenges in VR Integration for Immersive Experiences and Market Research
While VR's potential in market research is immense, several challenges and considerations might hinder the effective implementation of virtual reality experiences.
1| Accessibility and Cost
One of the top challenges to the widespread integration of VR is the cost of equipment and the availability of reliable talent. Business leaders need cost-effective tools and experienced VR-friendly market researchers to develop and maintain virtual environments. High-quality VR headsets and sensors can be expensive, and creating a realistic and engaging virtual environment requires significant software development and design investment. As the virtual reality industry matures and its tech tools become more affordable, these costs will likely decrease. So, VR integration for market studies will be more accessible to all organizations worldwide.
2| Data Privacy and Ethics
Corporations' use of VR in market research and hyper-personalization raises critical questions about data privacy and ethics. Biometric data, such as heart rate and eye movement, are highly sensitive data categories. Therefore, data processing entities must handle them with care. Companies must ensure that their data protection measures are effective. At the same time, participants must know how data recipients will utilize their data legally, ethically, and legitimately. Transparency and consent are crucial to maintaining trust and avoiding potential legal issues.
3| Technical Limitations
Despite significant advancements, VR technology still has limitations. Motion sickness, for example, can affect some users by limiting the duration of VR sessions. Additionally, the realism of virtual environments exhibits visual artifacts or rendering glitches because of current hardware and software limitations. As technology continues to improve, these obstacles will likely diminish. However, they might be a significant problem for enterprises with smaller budgets.
The Future of Virtual Reality in Market Research
The future of VR and immersive experiences in market research is promising, with several disruptive projects already making the headlines, as explored below.
1| Enhanced Realism and Interactivity
Continuous progress in AI technologies promises better realism and more engaging interactions. Advances in graphics, haptic feedback, and artificial intelligence will create more lifelike and engaging virtual environments. Their future releases will enhance the accuracy of consumer behavior studies and provide deeper insights into their preferences and motivations.
2| Integration with Other Technologies
Integrating VR with other emerging technologies will open up new possibilities for market research. Consider augmented reality (AR), artificial intelligence (AI), and live data streaming projects. For example, brands can use AI platforms to analyze the extensive databases from VR-powered market studies to identify unique patterns and crucial trends that may be undetectable in a standard analysis. AR can complement VR by overlaying digital information in the real world, creating a seamless blend of physical and virtual experiences.
3| Broader Adoption Across Industries
Affordable technologies indicate broader VR adoption in market research across various industries. The potential applications will benefit entertainment, tourism, education, and real estate. Companies that embrace VR early on will have a first-mover advantage because they will gain actionable insights into their customers before competitors. Consequently, they will successfully stay ahead of them in understanding market trends.
4| Personalized Consumer Experiences
VR will revolutionize market research and provide better approaches to studying consumer engagement metrics. Understandably, you want to personalize virtual experiences based on individual preferences and behaviors. This method helps create more meaningful and engaging interactions. For instance, a fashion retailer could offer virtual fitting rooms. Online customers would try on clothes and receive personalized recommendations based on submitted style and body type data. Similar customization options tell customers your business is committed to prioritizing satisfaction and brand loyalty.
Conclusion
Global brands want to incorporate virtual reality and immersive experiences into market research. These tech advancements help redefine the methods for understanding consumer behavior. VR addresses many of the limitations of traditional research methods by providing a more realistic, engaging, and data-rich environment. While challenges can be tricky to overcome, the strategic benefits attract brands. For deeper insights and more accurate data to inform business strategies, companies have invested in developing solutions to those problems.
As technology advances, domain experts expect VR to become indispensable in the market research toolkit. Companies that invest in this technology earlier will be well-positioned to reap the rewards since they acquire a competitive edge essential to thrive in their industry. The future of market research is immersive, and your competitors have merely begun exploring the possibilities.
2 notes
·
View notes
Text
Trends Shaping the Banking and Insurance Industry in 2024
The banking and insurance industries have seen rapid evolution over the past few years, driven by technological advancements, consumer demands, and economic shifts. In 2024, these sectors are witnessing major trends that are transforming how services are offered and consumed. Companies like Miracuves are pivotal in guiding financial institutions and insurance providers through these changes, offering solutions that enhance efficiency, security, and customer satisfaction.
Digital Transformation in Banking: The Rise of Neobanks
One of the most notable trends in the banking sector is the rise of digital-first banking services, commonly known as neobanks. These digital banks are designed to operate entirely online, eliminating the need for physical branches. This shift allows neobanks to offer low-cost financial services with minimal overhead, giving them a competitive edge in providing affordable banking products. Customers benefit from low or zero fees, higher interest rates on savings, and a seamless mobile-first banking experience
KPMG
Deloitte United States.
Moreover, traditional banks are adopting digital technologies to stay competitive. AI and machine learning are being leveraged to streamline operations, enhance decision-making, and improve fraud detection systems. Automated services, such as chatbots for customer support and advanced algorithms for analyzing financial data, allow banks to offer faster and more personalized services to clients
Deloitte United States. Miracuves helps banking institutions integrate such technologies, allowing them to improve efficiency and security while keeping customers satisfied.
Sustainability as a Priority in Financial Services
Another significant trend in 2024 is the increasing emphasis on sustainability in banking. Environmental, Social, and Governance (ESG) factors are becoming a priority for banks, with many now offering green financing options for projects related to renewable energy and sustainable development. This is in response to growing consumer demand for eco-conscious banking options. Banks are also adopting energy-efficient technologies in their operations and striving to reduce their own carbon footprints
KPMG.
Insurance companies are not far behind in this trend. Insurers are incorporating sustainability into their policies, offering products that reward eco-friendly behavior, such as lower premiums for electric vehicle owners or homes with energy-efficient features. This is not just about aligning with environmental goals; it’s also about tapping into the growing consumer demand for sustainability
SoFi.
Technological Disruption in Insurance: Insurtech Innovations
The insurance industry is undergoing a digital revolution, with insurtech startups driving innovation. These companies are leveraging technology, big data, AI, and blockchain to offer personalized insurance policies and improve operational efficiencies. AI-driven underwriting systems allow for more accurate pricing models based on individual risk profiles, while blockchain provides greater transparency and security in claims processing
KPMG.
The use of digital platforms has also transformed how consumers engage with insurance. Customers can now easily compare policies, purchase coverage, and file claims online, streamlining the process and enhancing convenience. Miracuves plays a crucial role in supporting insurance companies in adopting these cutting-edge technologies, ensuring they stay competitive and responsive to consumer needs.
Cybersecurity: A Critical Focus for Both Sectors
As both banking and insurance services become more digitized, cybersecurity remains a top priority. With increasing cyber threats, financial institutions and insurers are investing in robust security measures such as multi-factor authentication, biometric identification, and encryption technologies. Consumers are more aware than ever of the risks to their personal data, and both industries are taking proactive steps to protect sensitive information
Deloitte United States.
Moreover, educating consumers about cybersecurity best practices is becoming an essential part of these industries’ offerings. For example, banks and insurers are providing resources on how to avoid phishing scams, safeguard personal information, and spot fraudulent activities. By fostering a culture of security, these institutions not only protect their clients but also build trust—a crucial factor in today’s competitive landscape
SoFi.
Conclusion: The Future of Banking and Insurance in 2024 and Beyond
The trends shaping the banking and insurance industries in 2024 highlight a broader shift toward digital transformation, sustainability, and improved customer experiences. As companies like Miracuves continue to help financial institutions and insurers navigate these changes, the focus on technology and security remains paramount. By embracing innovations such as AI, blockchain, and sustainable finance, these industries are setting the stage for a more efficient, consumer-centric future.
As businesses adapt to these trends, they will need to remain flexible and responsive to evolving market demands. The future of banking and insurance will be defined by technological integration, customer trust, and a commitment to sustainability, with firms like Miracuves leading the way in helping organizations achieve these goals.
0 notes
Text
Bolstering London Businesses with Innovative Blockchain Solutions
London is being considered the worldwide capital for innovation and technology, and this is changing the dynamics of running business. Blockchain technology has evolved wide industry streams with safe, transparent, and efficient solutions. With Blockchain App Maker, our specialty is developing cutting-edge blockchain solutions that are tailored according to the needs of London businesses and beyond.
Why Blockchain Matters for Businesses in London
Being a finance, commerce, and innovation city, London would require proper technology in the form of blockchain for its fast nature. Blockchain App Maker is a leading Blockchain App Development company in London.
Blockchain is the most advanced solution to all of the above:
• Improve Transparency: Using an immutable ledger, blockchain facilitates trusted operation with full transparency.
• Improve Efficiency: Reduce intermediaries to enable faster time and lesser costs through streamlined processes
• Enhance Security: Protect sensitive information at high levels of encryption while using decentralized systems.
• Enable Growth: Empower businesses to discover new sources of revenue through innovative blockchain-based solutions like NFTs, smart contracts, and DeFi apps.
Services We Offer
Blockchain App Maker is the company behind the provision of comprehensive blockchain development services that empower businesses in many industries.
1. Custom Blockchain Application Development
We develop custom blockchain applications based on business needs. Integration and scaling are always seamless from idea generation to launch.
2. Blockchain Wallet Development
All digital assets need secure and user-friendly wallets on the blockchain. The wallet designs include multi-signature functionality, biometric authentication, and cross-platform support.
3. NFT Development
We are more than happy to help businesses build unique digital assets and marketplaces with the increasingly large NFT market size. We address all areas from token development up to the integration of smart contracts.
4. Smart Contract Development
Automate processes and garner trust by developing custom smart contracts. Our developers do not write bugs and are consistent with all industrial standards.
5. DeFi Development
Enter into the domain of decentralised finance through our DeFi solutions and revolutionize lending, borrowing, staking, and other financial services-related aspects.
6. Web3 Development
Shape the future of the internet with our Web3 development services that enable business lines to integrate dApps as well as blockchain-based ecosystems in their businesses.
7. Enterprise Blockchain Solutions
Customized frameworks for the various segments of businesses, which allows scaling through enterprise-grade blockchain solutions in supply chain management, healthcare, finance, and much more.
Why Blockchain App Maker?
1. Expertise and Innovation
We have been associated with the development of blockchain for a long time. We always stay ahead of the game and incorporate all the latest technologies and methodologies.
2. Client-centric Approach
We provide solutions compliant to the business objectives. Our methodology is such that it harmonizes with clients close for project success.
3. Scalability and Security
Every blockchain-based service is built to our scale with your business model in place while following the highest protocols regarding security
4. Availability
Availability in London facilitates consultancy and support for customers conveniently
Industry Sectors
Some Industry verticals which can be totally reformed by blockchain is discussed below:
• Financial: More transaction simplifications, betterment through improved security, and improvements through compliance.
• Retail and E-Commerce: More secured payments allow chains, plus the customer relationship managing software improves.
• Healthcare: secure patient information and enable the management of medical records to become streamlined.
• Real Estate: easier and even more transparent approach in the transaction of property
• Entertainment: power NFT marketplaces, and decentralized content
Let's Build the Future Together
We believe that Blockchain App Maker is to define the future of London's business. Be it a small start-up or a massive corporate, our solution has been engineered to keep you at par in this cutthroat market place.
Call us today to learn how we can help your business thrive in this blockchain generation and build the decentralized future, together.
#blockchain application development services#blockchain app development company in London#blockchain development company in London
0 notes
Text
United States voice biometrics market size is projected to exhibit a growth rate (CAGR) of 16.85% during 2024-2032. The increasing focus on security and the need for robust authentication methods, the rising demand in financial services, the rapid technological advancements in artificial intelligence (AI) and machine learning (ML), and the shift towards multi-factor authentication (MFA) are some of the factors propelling the market.
#United States Voice Biometrics Market Report by Component (Solutions#Services)#Type (Active Voice Biometrics#Passive Voice Biometrics)#Deployment Mode (On-Premises#Cloud-Based)#Organization Size (Large Enterprises#Small and Medium-sized Enterprises (SMEs))#Application (Authentication and Customer Verification#Forensic Voice Analysis and Criminal Investigation#Fraud Detection and Prevention#Risk and Emergency Management#Transaction Processing#Access Control#Workforce Management#and Others)#Vertical (BFSI#Retail and E-Commerce#Government and Defense#IT and Telecom#Healthcare and Life Sciences#Transportation and Logistics#Travel and Hospitality#Energy and Utilities#and Region 2024-2032
1 note
·
View note
Text
Healthcare Biometrics Market By Product Type, By Manufacturers, By End-User And Market Trend Analysis Forecast 2033
The healthcare biometrics global market report 2024 from The Business Research Company provides comprehensive market statistics, including global market size, regional shares, competitor market share, detailed segments, trends, and opportunities. This report offers an in-depth analysis of current and future industry scenarios, delivering a complete perspective for thriving in the industrial automation software market.
Healthcare Biometrics Market, 2024 report by The Business Research Company offers comprehensive insights into the current state of the market and highlights future growth opportunities.

Market Size - The healthcare biometrics market size has grown exponentially in recent years. It will grow from $6.95 billion in 2023 to $8.46 billion in 2024 at a compound annual growth rate (CAGR) of 21.7%. The growth in the historic period can be attributed to increasing cases of identity theft and fraudulent activities, data security and privacy, reduction in administrative errors, cost reduction, and availability of funding and grants for healthcare. The healthcare biometrics market size is expected to see exponential growth in the next few years. It will grow to $18.67 billion in 2028 at a compound annual growth rate (CAGR) of 21.8%. The growth in the forecast period can be attributed to the increasing adoption of electronic health records, growing demand for patient data security, improved patient identification systems, rising healthcare expenditure, and growing public awareness and acceptance of biometric technologies. Major trends in the forecast period include technological advancements, multimodal biometrics, artificial intelligence, machine learning integration, interoperability standards, and integration with Internet of Things (IoT) devices.
Order your report now for swift delivery @ https://www.thebusinessresearchcompany.com/report/healthcare-biometrics-global-market-report
The Business Research Company's reports encompass a wide range of information, including:
1. Market Size (Historic and Forecast): Analysis of the market's historical performance and projections for future growth.
2. Drivers: Examination of the key factors propelling market growth.
3. Trends: Identification of emerging trends and patterns shaping the market landscape.
4. Key Segments: Breakdown of the market into its primary segments and their respective performance.
5. Focus Regions and Geographies: Insight into the most critical regions and geographical areas influencing the market.
6. Macro Economic Factors: Assessment of broader economic elements impacting the market.
Market Drivers - The increasing number of patients in hospitals is expected to propel the growth of the healthcare biometrics market going forward. The number of patients is rising due to an aging population, an increased prevalence of chronic diseases, and improved access to healthcare services. Healthcare biometrics helps hospital patients by enhancing security and personalized care through accurate identification and authentication of individuals. For instance, in February 2024, according to the Canadian Institute for Health Information, a Canada-based not-for-profit organization, acute inpatient hospitalizations in Canada rose to 2.96 million in 2022–2023 from 2.88 million in 2021–2022. This represents a 2.78% increase in hospitalizations year-over-year. Therefore, the increasing number of patients in the hospital is driving the growth of the healthcare biometrics market.
Market Trends - Major companies operating in healthcare biometrics are focusing on developing innovative patient identity verification solutions to enhance security and improve the accuracy of patient care. Patient identity verification solutions refer to advanced technologies designed to accurately and securely confirm patients' identities, improving both safety and efficiency in healthcare settings. For instance, in February 2024, VerifiNow, a US-based provider of biometric verification, PatientVerifi, a biometric identity verification solution for telehealth providers that employs voice biometrics, facial recognition, and liveness detection to accurately authenticate patients during virtual appointments. This technology reduces the risks of incorrect patient identification, malpractice claims from misdiagnosis, and prescription misuse. Designed for integration with popular video platforms such as Zoom and Microsoft Teams, PatientVerifi enhances compliance with healthcare regulations and safeguards both patients and providers.
The healthcare biometrics market covered in this report is segmented –
1) By Technology: Fingerprint Recognition, Face Recognition, Voice Recognition, Vein Recognition, Iris Recognition, Hand Recognition, Other Technologies 2) By Application: Medical Record And Data Center Security, Patient Identification And Tracking, Care Provider Authentication, Home Or Remote Patient Monitoring, Other Applications 3) By End-User: Hospitals, Clinics, Clinical Laboratories, Healthcare Institutions
Get an inside scoop of the healthcare biometrics market, Request now for Sample Report @ https://www.thebusinessresearchcompany.com/sample.aspx?id=19499&type=smp
Regional Insights - North America was the largest region in the healthcare biometrics market in 2023. Asia-Pacific is expected to be the fastest-growing region in the forecast period. The regions covered in the healthcare biometrics market report are Asia-Pacific, Western Europe, Eastern Europe, North America, South America, Middle East, Africa.
Key Companies - Major companies operating in the healthcare biometrics market are Fujitsu Limited, NEC Corporation, Siemens Healthineers AG, Thales Group, IDEMIA SA, GoForward Inc., Zkteco Inc., Imprivata Inc, M2SYS LLC, Cross Match Technologies Inc., Daon Inc., Facephi, Aware Inc., Integrated Biometrics, Suprema Inc, eyeLock, Bio-Key International, Facetec Inc., RightPatient, Morpho Dys
Table of Contents 1. Executive Summary 2. Healthcare Biometrics Market Report Structure 3. Healthcare Biometrics Market Trends And Strategies 4. Healthcare Biometrics Market – Macro Economic Scenario 5. Healthcare Biometrics Market Size And Growth ….. 27. Healthcare Biometrics Market Competitor Landscape And Company Profiles 28. Key Mergers And Acquisitions 29. Future Outlook and Potential Analysis 30. Appendix
Contact Us: The Business Research Company Europe: +44 207 1930 708 Asia: +91 88972 63534 Americas: +1 315 623 0293 Email: [email protected]
Follow Us On: LinkedIn: https://in.linkedin.com/company/the-business-research-company Twitter: https://twitter.com/tbrc_info Facebook: https://www.facebook.com/TheBusinessResearchCompany YouTube: https://www.youtube.com/channel/UC24_fI0rV8cR5DxlCpgmyFQ Blog: https://blog.tbrc.info/ Healthcare Blog: https://healthcareresearchreports.com/ Global Market Model: https://www.thebusinessresearchcompany.com/global-market-model
0 notes
Text
Case Studies: Successful Implementations of Turnstile Gates in Various Industries
Turnstile gates have been successfully implemented in various industries, providing secure and efficient access control solutions. In this article, we will explore several case studies of successful implementations of turnstile gates in different industries, highlighting the benefits and challenges of each project. These case studies will demonstrate the versatility and effectiveness of turnstile gates in controlling who can enter or exit a particular area.
Airport Security: A Case Study
A major international airport in the United States implemented turnstile gates as part of its security upgrade. The airport required a secure and efficient access control system that could handle a high volume of passengers. turnstile gate suppliers were integrated with biometric authentication and CCTV cameras to provide an additional layer of security. The implementation resulted in a significant reduction in security breaches and improved passenger flow. The airport was able to process passengers more quickly and efficiently, reducing congestion and wait times.

Stadium Security: A Case Study
A professional sports stadium in the United Kingdom implemented turnstile gates to improve security and crowd control. The stadium required a system that could handle large crowds quickly and efficiently while preventing unauthorized access. The turnstile gates were integrated with ticketing systems and CCTV cameras to provide a comprehensive security solution. The implementation resulted in improved crowd control and reduced congestion at entry points. The stadium was able to ensure that only authorized individuals could enter the premises, improving overall safety and security.
Data Center Security: A Case Study
A leading data center provider in the United States implemented turnstile gates as part of its security upgrade. The data center required a highly secure access control system that could protect sensitive equipment and data. The turnstile gates were integrated with biometric authentication, CCTV cameras, and intrusion detection systems to provide multiple layers of security. The implementation resulted in improved security and reduced risk of unauthorized access. The data center was able to ensure that only authorized personnel could access sensitive areas, protecting valuable equipment and data.
University Campus Security: A Case Study
A major university in Australia implemented turnstile gates to improve campus security. The university required a system that could handle a high volume of students, staff, and visitors while preventing unauthorized access. The turnstile gates were integrated with card readers, CCTV cameras, and alarm systems to provide a comprehensive security solution. The implementation resulted in improved campus safety and reduced crime rates. The university was able to ensure that only authorized individuals could enter campus buildings, improving overall safety and security.

Government Facility Security: A Case Study
A government facility in Canada implemented turnstile gates as part of its security upgrade. The facility required a highly secure access control system that could protect sensitive information and personnel. The turnstile gates were integrated with biometric authentication, CCTV cameras, and intrusion detection systems to provide multiple layers of security. The implementation resulted in improved security and reduced risk of unauthorized access. The facility was able to ensure that only authorized personnel could access sensitive areas, protecting valuable information and personnel.
Conclusion
In conclusion, turnstile gates and traditional barriers each have their own strengths and weaknesses in terms of security features. When taking into account the advanced security features, flexibility, scalability, and reduced need for security personnel, turnstile gates prove to be the better option for today's access control needs. Traditional barriers, while effective in their own right, may not offer the same level of security and ease of use as turnstile gates. Ultimately, the decision between turnstile gates and traditional barriers should be made on a case-by-case basis, depending on specific access control requirements, budget constraints, and system integration considerations.
0 notes