#big data terminology
Explore tagged Tumblr posts
Note
I'm sorry... snake paper? Are things heating up in the snake researcher fandom?
16 February 2024: A team of researchers (including a generally well-respected anaconda expert) found minimal and partly contradictory genetic differences in green anacondas over an enormous area, summarily dismissed all previous work on the taxonomy of green anacondas, and gave the mitochondrial lineage concerned a new name, along the way making some huge fumbles that show plainly that they have no idea how taxonomy works or what certain technical terms mean. They published the work in a journal from a suspect publishing house that is known to rush, skip, or ignore peer review as and when it suits them. And apparently there was some suspicious funding involved, though I don’t know much about that. They made a media storm with ‘a new anaconda!’ but within minutes there were people raising huge red flags about the paper, for the reasons enumerated above and others.
The response from ‘the community’ has been swift and harsh, but mostly fair, in my view. The discussion on ResearchGate reflects this pretty well. There are some bad takes about keeping ‘wokism’ out of science; I would argue that it remains critical to incorporate native peoples, knowledge, and languages into taxonomic work—just not the way this was done, in flagrant and intentional conflict with the established methods and protocols. There are also responses in the discussion by the lead author that show that he is evidently impervious to all of this criticism, and stands by the belief that the work and taxonomic reasoning is sound.
19 March 2024: two papers were published simultaneously in Bionomia, that both enumerate and rebut the problems of the original paper. And I know there are more on the way, though I don’t know if they are all going to be completed now that two responses have already been published.
The one thing I would weigh in on from my perspective is that it is the *taxonomy*, and not necessarily the evidence presented in the paper, that is the biggest problem. Species are described based on mitochondrial data alone all the time. Some of the results are quite interesting. But the taxonomy of the paper is a mess, full of contradictions, cherry-picking, and terminological errors. In the hands of competent taxonomists, the work might have been much more difficult to dispute. But also, no competent taxonomist would have assigned a new name to this lineage; there are too many existing names that would have priority, if it is worth recognising.
Undoing public perception of there being a new anaconda species will take years, if it can ever really be achieved. Always easier for media stories to go around than corrections.
TL;DR big snake paper made big mistakes, and within a month was dismissed. It has probably done lasting damage to perception of anaconda diversity.
2K notes
·
View notes
Text
Froggie's Guide to Budget Headphones

@nimrella I am more well versed in traditional audio and home theater with big honking speakers, so I don't have much personal experience with headphones and headphone accessories. But I can tell you what I've learned from other people who are in the headphone world. And since you are starting more within the "budget" range I think I am somewhat qualified to guide you at this level.
You have three paths to choose from...
Wireless, low impedance wired (no amplification required), and high impedance wired (amplification required).
Basically... easy, medium, and hard.
But also... good, better, best.
Wireless Headphones
Wireless headphones have come a long way. Audiophiles used to scoff at them but now there are options that really do sound fantastic and the Bluetooth data rates are good enough to deliver high resolution audio. They also have noise cancellation options which may be desirable. If you do not have a quiet, dedicated space for listening to music you might find high end noise cancellation a godsend. People love them especially for planes, trains, and automobiles.
I don't know if everyone knows how noise cancellation works or not, but basically the headphones have microphones that listen to the world around you. They measure the incoming sound and then generate an opposite sound that just about kills ambient noise. If you play the same sound 180 degrees out of phase it basically nullifies those sound waves. The tech works best between 50 Hz and 1000 Hz. For reference we hear between 20 Hz and 20,000 Hz (lower if you are old). So anything super high or super low pitched can still get through.
In any case, if that sounds appealing, wireless headphones should be a consideration.
The other advantage of wireless headphones would be the ease of use. They pair to your phone, your laptop, your TV. They have controls to help you pause and skip songs and change volume. Some allow you to take phone calls.
But the big downside is the sound quality takes a bit of a hit. As I said, the bluetooth standards have actually gotten very very good. (Though there are audiophiles who will swear it still sounds like a 1990s MP3.) So streaming the actual media files are not really an issue. But trying to cram all of that tech into lightweight headphones you can wear around town all day requires compromises and added expense. Not to mention the battery has a limited lifespan. You may have more limited or inconsistent frequency response, poor dynamic range, distortion problems, weak output, and a high noise floor. Wireless options still can't match wired headphone systems in the same price range. And the wireless options that come close are quite spendy.
Wireless Headphones Suggestions
In your price range the two wireless options that I hear mentioned over and over again are the Sony WH-1000 series and the Bose QuietComfort. They are both well regarded for having a good mix of sound quality and noise cancellation while also being a decent value. You might be able to visit a Best Buy and demo them to see if you prefer the sound and comfort of one over the other.
The Apple AirPods Max are said to work really well within the Apple ecosystem. They have some interesting spatial sound modes and very good audio quality. I've heard the noise cancellation is some of the best currently available. But they seem too expensive and a lot of people feel they are too heavy. I also suspect they are due for an update. That said, if you wait for the new ones to come out and buy used, they could come into your price range. I'd really only suggest these if you have multiple Apple products that you will be streaming sound from.
Before we move into wired headphones, let's go over some terms that you might see pop up when doing research and reading reviews.
Froggie's Glossary of Audiophile Terminology
Driver A speaker is made up of drivers. Some speakers have a woofer, a midrange, and a tweeter. Each individual thing is a driver. And with headphones you will often hear "headphone driver" instead of speaker because it is more specific. Headphones typically have an all-in-one driver that does all frequencies. A woofymidteet.
That's not a thing.
I made that up.
Frequency Response This is the range of frequencies produced by the drivers from low to high. You want to make sure your headphones have good, deep bass. That will make more of a difference than anything else. It's the foundation of all sound and what is sorely lacking in devices with small/cheap speakers.
Music typically doesn't go much below 40 Hz in the bass range. So if you are only interested in music listening, that is plenty deep. Movies can go down to 20 Hz, but this isn't necessary for a good immersive experience unless you have giant subwoofers. So if you find something that can play ~40 Hz with decent output, you should be all good. Every speaker has a frequency response curve. It looks something like this.

The X-axis represents the frequency and the Y-axis represents the volume in decibels. We are most concerned with the 40 to 10K Hz section, as most sound happens there.
I'm not going to go super in-depth and overwhelm everyone, but typically you want this graph to look fairly flat in that range. A flat-ish line will give you a "neutral" response.
The above graph gets a little bumpy in the high frequencies. That means those frequencies will have a higher volume than the lower frequencies. If a higher frequency has a big peak, that could make your sound seem too bright or tinny.
Or you could have the opposite problem. You could have a null in the bass where the output dips below everything else. This can make your sound a bit anemic and lacking punch.
Whereas a more flat speaker will output all frequencies at about the same volume and sound much more balanced and smooth.
Equalization or EQ A flat response is good because it will accept EQ well. Equalization is where you add peaks and dips in volume deliberately to taste.
This can be as simple as 3 knobs.

Or it can be a more complicated parametric EQ.

A lot of digital EQ methods have presets to help get you started. I promise it isn't as intimidating as it looks.
Some people like to buy speakers/headphones that are EQ'd how they prefer out of the box. (Or if you get Beats by Dre they just turn the bass all the way up and say "Fuck them other frequencies!") But this is often a bit of a crapshoot because it is hard to EQ a speaker that sounds good in every room or every environment or just to varying individual preferences.
By making the speaker more neutral, it can be much easier to equalize specifically to your needs and enjoyment.
So if you like the bass a little bassier and the mids a little quieter, you have the power to dial that in with great specificity on a neutral speaker. You can apply any EQ you wish and you won't be fighting the speaker's predetermined response.
Basically if you are reading reviews and the headphones are described as "flat" or "neutral" that's a good thing (in my opinion). Just remember nothing is going to be perfectly flat. We're shooting for flat-ish.
If you do decide to get a neutral sounding pair of headphones you may find them a little bland out of the box. Do not panic. You just need to learn a bit about how to apply EQ, but thankfully YouTube is plentiful with tutorials.
The Harman Curve was researched to be most liked by the most people, so you might start there. (Also, SoundSource is a very popular EQ app for Mac.)
Dynamic Range This is the spectrum of how quiet to loud something can get. If you have speakers that can render both a pin drop and a big explosion with great fidelity and proper intensity, you will be in audio heaven. There is so much emotion and drama that can be expressed by expansive dynamic range and most cheap speakers compress it to an inch of its life. When the soft and the loud sounds are the same you miss out on so much audio information intended by the composer.
Distortion This is just how loud a speaker can go without breaking up. Low distortion is good. While every driver distorts at some point, usually that is at a much higher volume than you will use. This typically only plagues cheap, tiny drivers.
Sound Pressure Level (SPL) This is a measurement of how loud a speaker can get. While you don't want to listen to anything louder than a sustained average decibel level of 80 to 85, you do want peaks over 100, especially in the bass. Bass is less damaging to ears and hearing damage is all about sustained volume rather than quick peaks here and there. Most headphones can comfortably do an SPL between 90 and 110 dB. The ability to go louder is good, but only because that expands headroom, not because you should actually listen to them that loud. So if the headphones can get super loud, that means they will have a much easier time delivering normal levels.
Noise Floor Every sound system has background noise. You know that static you hear when you turn a radio up really loud when there is no sound playing? That is your noise floor. You want that to be as quiet as possible because if you turn up the volume, you don't just turn up the volume of the sounds you want to hear, you also turn up the volume of that background noise.
If you can find a headphone system with a decent low noise floor and you can also find a very quiet space to listen in, you could have a religious experience. I don't think people realize how much the room you are in matters, even when listening to headphones. When you are in a quiet room, you can play at lower volumes. And that can mitigate a lot of the problems associated with cranking the volume. You won't damage your ears for one thing. But the speakers won't have to work as hard so you'll have less distortion and better clarity.
Noise mostly comes from the amplifier, which I will talk about later on.
Froggie Pro Tip: If you want cheap speakers to perform better, go to a quiet room and move them as close as possible. This allows you to play them at a lower output while maintaining your desired perceived volume.
Okay, now we can finally talk about...
Wired Headphones
You have open back and closed back styles.

Open back tends to have a more natural sound and feels more comfortable. Like listening to regular speakers. People generally feel they are able to listen to them longer because they don't create a seal and cause pressure on your ear drum. However, if sound can get out, it can also get in. So with open back headphones people nearby will be able to hear what you are listening to. And if you are not in a quiet room, all of that sound will leak in. Meaning you have to increase the volume and the noise floor and the distortion.
Closed back seals off your ears and gives you a quiet and immersive experience. You can be in a noisier room without having to crank the volume as much. Some prefer this style just because it helps them feel like they are going into their own personal dimension of sound. These are great for ASMR too. But ear fatigue can become an issue and you may need to take little breaks to let your ears breathe and your ear drums rest.
And the last thing we need to discuss is impedance.
The impedance of headphones mostly determines how hard they are to amplify. Impedance is measured in ohms which is this little horseshoe symbol... Ω.
Lower ohms means less electrical resistance and easier to amplify.
Higher ohms means more electrical resistance and difficult to amplify.
If you get headphones rated below 100 ohms, they can typically be driven by smartphones and laptops just by plugging into a standard headphone jack. Though depending on the device, 100 may sound a little quiet so you may want to go lower. 30 ohms is fairly typical if you plan to drive your headphones with everyday electronics.
Above 100 ohms you are going to need some sort of amplification—usually a DAC with a headphone amplifier. (There are DACs without amplification so be sure to check that.)
A DAC, or digital-to-analog converter, is already built into your phone and laptop. But those are very small, don't have a lot of power, and might have a higher noise floor due to interference from other components and heat and just a lot of electrical signals nearby.
By getting an external DAC w/amplifier you separate out the components, make them larger and more powerful, and typically improve the sound quality. Because it is more isolated, the amplification can be much quieter despite being more powerful.
If you plan to stay in a static location and you have high impedance headphones, you can get a little box DAC that sits on your desk. It works like an external sound card for your computer. If you record music or stream, a digital audio interface works great as well (remember to check the Ω).
But if you need to be more mobile with your headphones you can get a little USB dongle DAC, though you will probably not get the same sound quality and power.
Both will be superior to the internal DAC built into your computing devices.
So, low impedance headphones are easier if you need to move around.
High impedance headphones are better for staying put in a single location unless you get a dongle DAC.
Just remember, high and low impedance doesn't necessarily indicate quality. It's just that in order to drive high impedance headphones you need the larger amplifier with the nicer components and, by necessity, you automatically get that quality bump.
You can get very good low impedance headphones. However, if you power them *only* with a smartphone, you may not use them to their full potential. Which is why getting an external DAC is a good idea regardless.
But the nice thing about low impedance is you can get the headphones and still use them until you save up for the DAC. Or you can use them as normal while out and about and have a special listening spot at home with the DAC.
To review...
Low impedance and high impedance can both be high quality.
Low impedance (less than 100 ohms) works with anything.
High impedance (more than 100 ohms) requires amplification.
Both will be used to their full potential with a DAC/headphone amplifier of some kind.
Wired Headphones Suggestions
Again, I have not personally listened to any of these. I am just relaying what experts I trust have mentioned as being nice quality in your price range.
The beyerdynamic DT 770 headphones are some of the most well-regarded budget headphones I've heard of. They come in low and high impedance versions.
The Sennheiser HD 560 high impedance headphones are also praised for their value and performance.
If you can go a little pricier...
The HIFIMAN Sundara headphones have low impedance and can be driven easily by all your devices.
And the HIFIMAN Edition XS are even lower impedance and about the same price.
And if you want to try a DAC, I've heard good things about both Fosi and Schiit (yes, like the poopies), though there are many different brands. Just make sure the DAC has a headphone amplifier rated for the ohms you need.
The FOSI K5 Pro is a cheap "beginner" DAC that will power anything up to 300 ohms. This is the kind that sits on your desk.
And if you want a more portable dongle DAC, you can get something like the iFi Go Link.
I've also heard good things about the AudioQuest Dragonfly, though I hate recommending AudioQuest products due to them claiming they can do magical things. They use scientific gobbledygook to scam customers most of the time. That said, the DragonFly might be their only valid product.
Note from Future Froggie: AudioQuest just can't help themselves. While the Dragonfly itself is a good product and not a scam, they developed the "DragonTail", which is a scam.

It's just a USB A to C Adapter for the Dragonfly. But they have to find a way to justify 30 fucking dollars so they came up with this bullshit.

Definitely need to stabilize my geometry. If I have unstable geometry that could lead to quixotic trigonometry. And we all know that could introduce vertices into dodecahedrons. Which leads straight to accelerated cosmotic entropy catalyzing the heat death of the universe.
Fucking AudioQuest.
ANYWAY...
An inexpensive DAC may be all you ever need but DACs can get crazy expensive—just like headphones. And if you are really fancy you can get a DAC and a headphone amplifier as separate items. Audiophiles claim when you simplify components to a singular function you increase quality. While I think there is some small truth to that, I suspect they just think the tubes look neat.

Froggie's Disclaimer: I am not telling you to get these specific things, but I do think you'll probably be happy with anything I've suggested. But sound is a subjective experience and it is always best to test things out before you buy them, if possible. Or make sure there is a return policy. You might see if there is a brick-and-mortar store nearby that allows you to demo headphones. Remember that comfort can be just as crucial as sound quality for long listening sessions.
Final Thoughts
Good sound has been life changing for me. And I am excited when anyone goes down this journey. While the stuff mentioned is considered "budget" by audiophiles, this can give you a good starting point if you want to upgrade down the road. You'll get to know your preferences and get a better understanding of how this all works and choose your own adventure from there.
Though it is very possible you'll be quite content with "budget" and the sound quality is more than enough.
Personally, while I am very happy with my current home theater setup, I am hopeful one day I can upgrade one budget tier above where I currently am and that will be my endgame. I've heard $10,000 speakers and it is mostly a land of diminishing returns once you reach that level.
I'm fine in "budget" land.
Further Research
I didn't mention the different types of headphone drivers because I didn't want to put too much data in everyone's head. But if you want to do additional research you can learn about the 4 main types... dynamic, planar magnetic, electrostatic, and balanced armature.
217 notes
·
View notes
Text
On Saturday, an Associated Press investigation revealed that OpenAI's Whisper transcription tool creates fabricated text in medical and business settings despite warnings against such use. The AP interviewed more than 12 software engineers, developers, and researchers who found the model regularly invents text that speakers never said, a phenomenon often called a “confabulation” or “hallucination” in the AI field.
Upon its release in 2022, OpenAI claimed that Whisper approached “human level robustness” in audio transcription accuracy. However, a University of Michigan researcher told the AP that Whisper created false text in 80 percent of public meeting transcripts examined. Another developer, unnamed in the AP report, claimed to have found invented content in almost all of his 26,000 test transcriptions.
The fabrications pose particular risks in health care settings. Despite OpenAI’s warnings against using Whisper for “high-risk domains,” over 30,000 medical workers now use Whisper-based tools to transcribe patient visits, according to the AP report. The Mankato Clinic in Minnesota and Children’s Hospital Los Angeles are among 40 health systems using a Whisper-powered AI copilot service from medical tech company Nabla that is fine-tuned on medical terminology.
Nabla acknowledges that Whisper can confabulate, but it also reportedly erases original audio recordings “for data safety reasons.” This could cause additional issues, since doctors cannot verify accuracy against the source material. And deaf patients may be highly impacted by mistaken transcripts since they would have no way to know if medical transcript audio is accurate or not.
The potential problems with Whisper extend beyond health care. Researchers from Cornell University and the University of Virginia studied thousands of audio samples and found Whisper adding nonexistent violent content and racial commentary to neutral speech. They found that 1 percent of samples included “entire hallucinated phrases or sentences which did not exist in any form in the underlying audio” and that 38 percent of those included “explicit harms such as perpetuating violence, making up inaccurate associations, or implying false authority.”
In one case from the study cited by AP, when a speaker described “two other girls and one lady,” Whisper added fictional text specifying that they “were Black.” In another, the audio said, “He, the boy, was going to, I’m not sure exactly, take the umbrella.” Whisper transcribed it to, “He took a big piece of a cross, a teeny, small piece … I’m sure he didn’t have a terror knife so he killed a number of people.”
An OpenAI spokesperson told the AP that the company appreciates the researchers’ findings and that it actively studies how to reduce fabrications and incorporates feedback in updates to the model.
Why Whisper Confabulates
The key to Whisper’s unsuitability in high-risk domains comes from its propensity to sometimes confabulate, or plausibly make up, inaccurate outputs. The AP report says, "Researchers aren’t certain why Whisper and similar tools hallucinate," but that isn't true. We know exactly why Transformer-based AI models like Whisper behave this way.
Whisper is based on technology that is designed to predict the next most likely token (chunk of data) that should appear after a sequence of tokens provided by a user. In the case of ChatGPT, the input tokens come in the form of a text prompt. In the case of Whisper, the input is tokenized audio data.
The transcription output from Whisper is a prediction of what is most likely, not what is most accurate. Accuracy in Transformer-based outputs is typically proportional to the presence of relevant accurate data in the training dataset, but it is never guaranteed. If there is ever a case where there isn't enough contextual information in its neural network for Whisper to make an accurate prediction about how to transcribe a particular segment of audio, the model will fall back on what it “knows” about the relationships between sounds and words it has learned from its training data.
According to OpenAI in 2022, Whisper learned those statistical relationships from “680,000 hours of multilingual and multitask supervised data collected from the web.” But we now know a little more about the source. Given Whisper's well-known tendency to produce certain outputs like "thank you for watching," "like and subscribe," or "drop a comment in the section below" when provided silent or garbled inputs, it's likely that OpenAI trained Whisper on thousands of hours of captioned audio scraped from YouTube videos. (The researchers needed audio paired with existing captions to train the model.)
There's also a phenomenon called “overfitting” in AI models where information (in this case, text found in audio transcriptions) encountered more frequently in the training data is more likely to be reproduced in an output. In cases where Whisper encounters poor-quality audio in medical notes, the AI model will produce what its neural network predicts is the most likely output, even if it is incorrect. And the most likely output for any given YouTube video, since so many people say it, is “thanks for watching.”
In other cases, Whisper seems to draw on the context of the conversation to fill in what should come next, which can lead to problems because its training data could include racist commentary or inaccurate medical information. For example, if many examples of training data featured speakers saying the phrase “crimes by Black criminals,” when Whisper encounters a “crimes by [garbled audio] criminals” audio sample, it will be more likely to fill in the transcription with “Black."
In the original Whisper model card, OpenAI researchers wrote about this very phenomenon: "Because the models are trained in a weakly supervised manner using large-scale noisy data, the predictions may include texts that are not actually spoken in the audio input (i.e. hallucination). We hypothesize that this happens because, given their general knowledge of language, the models combine trying to predict the next word in audio with trying to transcribe the audio itself."
So in that sense, Whisper "knows" something about the content of what is being said and keeps track of the context of the conversation, which can lead to issues like the one where Whisper identified two women as being Black even though that information was not contained in the original audio. Theoretically, this erroneous scenario could be reduced by using a second AI model trained to pick out areas of confusing audio where the Whisper model is likely to confabulate and flag the transcript in that location, so a human could manually check those instances for accuracy later.
Clearly, OpenAI's advice not to use Whisper in high-risk domains, such as critical medical records, was a good one. But health care companies are constantly driven by a need to decrease costs by using seemingly "good enough" AI tools—as we've seen with Epic Systems using GPT-4 for medical records and UnitedHealth using a flawed AI model for insurance decisions. It's entirely possible that people are already suffering negative outcomes due to AI mistakes, and fixing them will likely involve some sort of regulation and certification of AI tools used in the medical field.
86 notes
·
View notes
Text
How my android fox identity came to be
I first made my fursona as basically "me but android fox", which already put relatively small "distance" between it and me. This gave the process that followed a pretty good starting point, though that was not my intention, it could not have been. Back then i was not aware of alterhumanity or any of the identities under its umbrella.
I started presenting as my fursona online, used it as a pfp, used the same name for both me and it, shortly after started referring to myself as a fox. It started out as sort of a mask i wear online, but being seen as that started feeling right and it gradually felt less like a mask and more like me. By being referred to as a (android) fox (i was a bit inconsistent with including the android part, still am to a lesser degree), my brain got used to associating the concept of fox with myself more directly. At some point , i started to referring to pictures of my fursona as pictures of me, it felt like a logical next step and further reinforced the mental association. A sort of fake it til you make it thing.
At the same time, i also started to imagine myself as my fursona. First as a series of thought experiments. How would fur feel instead of my skin? How would my ears move? How would it feel to have a tail? I got to a point where it felt like those things were actually there in a way. I basically induced a sort of phantom shift, though knowing that terminology came later. Another thing was just imagining in my minds eye how it would look being in the same i was, doing the same things i did.
One might notice that this all focuses on the fox aspect, and indeed, this was what i was focused on back then, the robot bits lagged behind a bit in this process, though they too got there eventually. That is not to say i considered myself an organic fox for a time, more that the android part was comparatively less important. Being mostly organic-passing (think as close to organic anthro fox as Mr. Data to human) contributed to that i think.
In both of the above mentioned ways i mentally applied fox aspects to myself and over time i absorbed those aspects into my sense of self. The ideas of "myself" and "my fursona" merged to become what i am today. This process was mostly complete by the time i discovered the alterhuman community. I questioned being otherkin for a while, but the identity being created like this didn't seem to fit. In the end i arrived at otherlink. That label presumes more intention about forming the identity, but it is the closest among the big labels, and adding quoiluntary to it communicates this being a bit complicated enough, i think (among other things why i find this addition useful).
@aestherians This is the post i was talking about working on earlier today about how my unintentional linktype formed.
47 notes
·
View notes
Note
Hiya! I'm a big fun of your profile pic (I must admit I'm no good at tumblr terminology). I also like your posts. Experiencing shows, I know nothing about, through tumblr posts and gif sets Is one of my favourite activities. So thank you for what you do - I like going on a little trips to the corners of tumblr I know nothing about, and it's been nice here
:>
Hi! Thank you so much for the compliments^^
Tumblr bl community is a wonderful place, full of so many talented people, it's truly a delight to be here, isn't it?
Here are two of my favorite posts with blog recommendations, in case you'd like to check them out. Maybe you'll discover someone you don't know yet, that you'll like:
@bengiyo 's here (all kinds of creators)
@troubled-mind 's here (meta writers)
And here are some of my recs off the top of my head:
Liveblogging: @sparklyeyedhimbo
Shared and irl locations: @colourme-feral
Gifs: @pharawee @wanderlust-in-my-soul @guzhu-furen @ueasking @my-rose-tinted-glasses @gabrielokun @save-the-data @i-got-the-feels @smittenskitten @25shadesoffebruary @seatawinan @spicyvampire @laowen @maxescheibechlinichacheli @thisautistic @firstmix @itsallaboutbl @zhaozi @chinzhilla @bunnakit @alienwlw
Source vs adaptation gifsets: @troubled-mind
Meta: @lurkingshan @waitmyturtles @wen-kexing-apologist @bengiyo @neuroticbookworm @ranchthoughts @lurkingteapot @rocketturtle4
COLORS: @respectthepetty
Thai language: @recentadultburnout
General knowledge and shows/movies recommentadions: @absolutebl
mix/other @scarefox @lukaherehelp @heretherebedork @chicademartinica @telomeke @littleragondin @mikuni14 @poetry-protest-pornography @tenprem @tenprems
Apologies if I missed someone!
#nice anons are nice <3#and worry not that pfp is here to stay im having way too much fun with it lol#conversation with anon
150 notes
·
View notes
Text
I am not a baby!! (Yes you are)
(Ao3) (Masterpost) (Previous) (Next)
(Part seven lmao)
Sometimes Danny hated being right. Mentally he cursed himself as he clamored into his lifepod. The Aurora was spilling radiation into the water just like predicted it would. A damaged drive core... That didn't bode well for him or the local wildlife. He was a Fenton! He knew the terminology for "This might blow up," in every language, no matter how needlessly complicated you said it.
A radiation suit would be helpful when the ship blew up, if not for him, then for the other survivors. Danny grew up surrounded by radioactive material, he was about as fucked up as one could get, but there was still time left for the other survivors. If there even were any left.
Shaking his head, Danny opened the storage plucking out the remaining Creepvine clusters, and started fabricating. It was hypnotic, Creepvine clusters to lubricant, copper and mushrooms to a battery and copper wire all that and a piece of titanium gave Danny a functioning Seaglide. The device was heavy, the PDA altering the blueprint so it was usable for him.
Opening the hatch up, eager to test his new toy out, Danny dove back into the water faster than ever before. Propellers spun at speeds that would chop his finger clean off if he touched them. A glowing map at the top and a flashlight he could turn off by squeezing the handles. Quick enough to keep up with the peepers while still being able to make quick sharp turns.
The Device whirled as he swam in circles, up, down, left, right, zigzag! Through coral tubes, around stone arches till he got dizzy, divebombing fish and kicking up sand.
"Congratulations, survivor. you have exceeded your weekly exercise quotient by 500 percent. Data indicates that swimming was your favorite activity,"
Heck yeah it was! Swimming is great! He's fast as hell man, radiation could eat shit! Stalkers wouldn't stand a chance, he'd just outpace them! Swimming around, breaking outcrops, and taking samples of table coral for a computer chip. Danny was having a blast!
In time he would have the materials to fabricate a habitat builder and in turn a super cool sea base! A home away from home while he's stuck outside federation space. Currently, the seabase blueprints he had were...limited, but he could work with that!
Rushing to his fabricator the blue lights felt agonizingly slow as he bounced on the heels of his feet, flippers squeaking against the floor. A habitat builder fell into Danny's impatient hands.
Back in the water, Danny scoped out the area. Access to an abundance of resources, food, and water was a necessity. Along with awareness of local predators. The shallows are a perfect place for him to build right now. A temp base to rest and store stuff before moving somewhere more convenient as he explored and met up with any of the other survivors.
Deciding to test out his new tool, Danny placed down a basic compartment. A tiny little tube that would've been big enough if he only needed a place to sleep. Yeah, that wasn't going to work. How was he supposed to pace aimlessly while he wrote notes? How was he supposed to work and live in a high-tech pool noodle? Disassembling the pathetic tube, Danny swam through the shallows plucking up the quartz needed for glass. More materials would be needed to build his base. Thankfully, he’d crashed in a ship made from and carrying the materials he needed. Danny saw no moral issue with “borrowing” titanium from supply crates light enough to lift, but the PDA seemed to have a small issue with it. With a few minutes of tinkering, it was easy to change the machine’s artificial mind.
A loop, he was going to make a base shaped like a zero because that’s how many fucks he gave about Alterra’s dumb rule. Placed upon foundations was the start of his perfect space base. The sides of the Zero became glass compartments, a perfect place to observe the local wildlife. Solar panels mounted jumpstarted the oxygen production, lights blinding when they snapped on. Fish drifted by his base, some ducking underneath his foundations settling comfortably in the shade provided. Maybe if he was here long enough, he’d grow some plants for fish to nibble on?
A hatch was placed on the front of the Zero, finally giving him access to his new base. Cold air punched him in the face as he stepped inside, but it was a welcome attack. Air conditioning at last! Throwing himself to the floor, Danny giggled, noise bouncing against barren walls. A sterile smell cycled through the base with the air filtered in. Like his parent's lab or a hospital room freshly sanitized. Familiar, it smelled like home.
Peeling off his flippers, Danny propped them against the wall. Bare feet against metal floors, Danny took to running through the loop. Brushing his hands against empty walls, he ran laps like it was gym class. The only difference was this wasn't gym class, so it didn't feel like hell. Several laps ran throughout his base until his breath ran out, and he collapsed to the floor.
Winded and panting, he glanced around his base mentally, planning where everything would go. Blueprints were limited, but brainpower wasn't. Making new blueprints for shelving units or a bed should be easy enough. The hard part would be finding the space for it. If he tinkered with the PDA, he could fabricate some blankets and pillows that he could sleep on and store away when he was awake.
First things first, he needed to get a fabricator and some storage set up. A few wall lockers on each side of the fabricator made his little crafting station. His base still felt bare. White walls would get boring real fast. No paint or paper he could use to decorate. No stickers or wallpaper to paint his base to match the stars. Untapped Potential, something to add to his to-do list. If he couldn't decorate anything else, changing the locker's text font would have to do.
Walking in a loop, Danny muttered, his brain working better than his mouth. Words failed, coming out jumbled if they were more than one or two easy syllables. Fangs created a lisp that'd get him verbally castrated if he was back at Casper. That was if he didn't maul them with his newfound face knives. Like a piranha, he was dangerous! Fierce!
Tap...Tap...Tap
Feet freezing, Danny turned to the window, heart jumping to his throat. Several glowing eyes stared back at him, burning a hole into his soul. Stripes of colors ranging from blue, purple, and forest green ran along its massive scaly body and dragon-like head. Two razor-sharp fangs poked out of a closed mouth. Arms glowing blue that faded to pitch black when reaching its four-fingered hands, each claw sharper than a sword. Hands, oh ancients, why does this one have hands? The other one didn't have hands! Curled up, it would be the same size as his base. Danny pointed his scanner at the guy, the results striking terror into the deepest depths of his core...
What the fuck do you mean this guy's a juvenile!?!
@ashoutinthedarkness @avelnfear @meira-3919 @thought-u-said-dragon-queen @hugsandchaos @blep-23 @zeldomnyo @bytheoldwillowtree @justwannabecat @shepherdsheart @starlightcat04 @stargazing-bookwyrm @pupstim
#Danny the moment he gets a seaglide: I'm fast as fuck boii#Danny upon seeing Damian: I'm scared as fuck boii#Imagine playing Subnautica and you're chilling in the shallows and you see a ghost gargantuan hybrid leviathan at your door#I'd simply perish at that point#subnautica au#dpxdc#dc x dp#dcxdp#dp x dc#DPXDC#DCXDP#All the tags so people can filter
220 notes
·
View notes
Note
So Im currently trying to write my first big story - big as in I'm trying to make it a book - But im overwhelmed with what to do:
I want to write, but first I have to work out the acts and plot. But to do that I have to do some research as it's historical fiction. And that's where I'm failing, because I'm making very slow progress and it's frustrating. It also takes away the last of my motivation.
Do you have any tips on how I should proceed now or what might help?
(I might want to add that I'm working full-time outside and often can only work on weekends on it)
De-Motivated by Story Research Prior to Plotting
Research prior to plotting can be overwhelming and frustrating, so here are some tips that might help:
1 - Start with a General Summary - Before you worry about plotting out scenes and figuring out the different acts, try writing a beginning to end summary of what you want the story to be. Don't worry so much about specific details like dates, places, proper terminology or events, etc. Use general terms to fill those in. It might look something like this:
[[ SPOILERS for the novel Outlander by Diana Gabaldon ]]
A former English military nurse in the 1940s travels to Scotland and inadvertently travels back in time, to the 1700s, via standing stones near the inn where she's staying. There she encounters a band of smugglers and is taken captive and brought to the local laird's castle. Despite the suspicions of the laird and his war chief, they see her value as a healer and she settles in as the castle's healer-in-residence. During this time, she tries to figure out a way back to her own time, but also forges a friendship with one of the smugglers she patched up when she was first captured. Eventually, she is summoned for questioning by a British captain (who happens to be an ancestor of the husband she left in the 1940s) who suspects her of being an English spy, and the highlanders try to protect her by having her marry the highlander she patched up. Despite her attachment to her new husband, she runs away to the standing stones but is caught and imprisoned by the British captain. Once she is rescued by her new husband, they return to the castle where she gets wrapped up in a witchcraft accusation and narrowly avoids being burned at the stake. Finally, she and her new husband travel to his family castle, but since her husband is a fugitive, he is captured by British forces and taken to prison. The nurse is able to rescue him with the help of some of his clan, and they eventually escape to France.
[[ END SPOILERS ]]
While this is a fairly complete beginning to end summary of the first book in the Outlander series, it leaves out a lot of specific details related to time, setting, world, character development, etc.
However, going through this summary, it would be easy to see places where research needs to be done. Just looking at the first part of the summary, we can already see a lot of questions we could ask about specifics:
A former English military nurse in the 1940s travels to Scotland and inadvertently travels back in time, to the 1700s, via standing stones near the inn where she's staying.
-- Who is this woman? (Where is she from, where did she serve? Why does she go to Scotland?)
-- Where are the standing stones? What do they look like? How do they transport her back through time?
-- Specifically what year in the 1700s does she travel to? What is happening during that time?
This would give you some ideas about what, specifically, you need to research. Breaking it up in this way not only makes it less daunting, but gives you specific things to research instead of trying to learn a bunch of unnecessary data.
2 - Learn How to Research Historical Details - My Guide to Internet Research offers some general research pointers (though I probably need to update it, tbh). Also, I have a post specific to Researching an Historical Topic. Furthermore, there are some good books that guide you through researching historical fiction, as well as helpful books about specific time periods that are geared toward writers.
3 - Make Use of YouTube - I can't express enough how helpful YouTube can be when researching historical details. For example, if Diana Gabaldon were preparing to research and write the first Outlander book today, she could find videos about British nurses in World War II, specific places in Scotland where the book is set, videos about the history of the Scottish highlands, video about Scottish highlander culture, videos about clothing and fashion in 18th century Scotland, videos about the history of witchcraft in Scotland, videos about the British occupation of Scotland, videos about 18th century healing and medicine, videos about healing herbs of the Scottish highlands... you name it.
4 - Know Your Time and Dedicate Accordingly - One of the hardest things to remember when researching, plotting, and writing long fiction is that there is a certain amount of time it's going to take you, no matter what, and if you overestimate how much time you actually have to dedicate to your WIP in a given day, week, month, or year, it's very frustrating and de-motivating. One thing you might try is taking an honest look at your calendar for a particular week or month. For each day, subtract the number of hours you'll spend sleeping. Then, subtract the number of hours you'll spend working, commuting to work, traveling for work, etc.. Finally, subtract the number of hours you know will be dedicated to other necessities, like taking care of family, doctor appointments, workouts, etc. This may only leave you with barely an hour a day, but knowing you have that hour to dedicate to writing is important. Not only can you block off and fiercely guard that hour, but you can be more realistic about what you'll get done with the hours you have available in a given week.
5 - Don't Feel Like You Have to Rush It or Figure It All Out Now - We have a tendency to imagine a ticking clock where one doesn't exist. If this is your first long fiction story, especially, there is no reason to feel like you need to get this done post haste. Give yourself grace to take the time you need to get it done. Putting unnecessary pressure on yourself only demotivates you. Instead, try to look forward to that hour a night where you can dive into learning about the time, place, and world of your story. Also, don't feel like you have to know every specific detail before you start plotting or even writing. It's okay to research as you write--as you come to things you need more information on--or even to use placeholders in your first draft, allowing you to go back and fill in the research later.
Happy researching and writing. You've got this! ♥
•••••••••••••••••••••••••••••••••
I’ve been writing seriously for over 30 years and love to share what I’ve learned. Have a writing question? My inbox is always open!
♦ Questions that violate my ask policies will be deleted! ♦ Please see my master list of top posts before asking ♦ Learn more about WQA here
48 notes
·
View notes
Note
Hi! I am such a big fan our your writing and every time I see you pop up on my dash I get so excited!! 🤍🤍
If you are looking for ideas, how do you think the batch would react to you trying to throw them a collective birthday party? I know they don’t really have a “birth”day but maybe they agree to celebrate on a specific date (maybe an important day for them)?
Birthday Surprise
All Bad Batch X GN!Reader
word count: 883 words

warnings: none, fluff. Platonic relationships.
authors note: so sorry for the wait, this is only short but I was drawing blanks and I’d rather post something than nothing at all. Hope this is okay ♥️

As rumors of a surprise spread among the members of the Bad Batch, excitement and curiosity filled the air. Each member pondered over what awaited them, their imaginations running wild. But as they stepped inside the Marauder, their jaws dropped in surprise.
The interior of the ship had been transformed into something neither of them could ever imagine. Vibrant balloons floated cheerfully, adorning every corner, while colorful banners draped the walls, displaying the message ‘happy birthday’. A massive birthday cake, meticulously crafted (that none of them would believe that you made if you told them) took center stage on the control panel in the cockpit, its sugary aroma tantalising the senses of certain clones.
Hunter couldn't hide his surprise as he glanced around. "What's all this?" he inquired slowly, his eyes locking onto your mischievous grin.
"Happy birthday!" you exclaimed, a twinkle in your eyes.
The confusion on Tech's face was evident as he analysed the unexpected scene. "To whom are we celebrating?" he inquired, searching for answers amidst the festive chaos.
"All of you!" you proclaimed, your response causing Tech's brows to furrow even deeper as he struggled to comprehend the unusual situation unfolding before him.
Wrecker, ever the cheerful and boisterous one, erupted with joy, a wide grin stretching across his face. “Do we even have a birthday?” He wasted no time in donning a party hat, playfully placing one on Omega's head as well. He even attempted to coerce Echo into joining the festivities, though Echo's patience dwindled with each failed attempt, swatting Wrecker's hands away until the pink hat finally sat on his head.
“Well, with thanks to Omega she told me that you guys were actually… made….?” You trail off, unsure if that was the right terminology to use but it was clear to them what you meant, “on this day!”
Hunter chuckled and with a playful kick, he sent a balloon soaring across the room. "Really?" he inquired, a hint of amusement in his voice.
You nodded, a broad smile spreading across your face. Extending your hand, you exchanged a high-five with Omega, who beamed at her brothers. "Absolutely," you confirmed, your voice brimming with genuine enthusiasm. "I thought it would be a fantastic idea for you guys to celebrate something special, together!"
"That is rather interesting information for me to log, actually. I was never aware that it was this particular date," Tech remarked, a faint smile gracing his lips as he pulled out his data pad to record the newfound knowledge. "Although this type of celebration is not necessary for the likes of us. We were made to be expendable, not to have celebrations."
"Oh, lighten up, Tech," Crosshair chimed in, his voice laced with playful sarcasm. He swiped a bit of frosting from the cake with his finger and licked it off, savoring the sweetness. "Say thank you."
"I believe you are yet to say that," Tech quipped, glancing at his brother over the top of his data pad. Crosshair smirked in response, then turned his gaze toward you.
"They already know I am," he acknowledged, gratitude shining in his eyes.
Tech looked at you and offered a small smile. "I apologize. This is great. Thank you."
"No worries, it's just a little something," you replied cheerfully, refusing to let their banter dampen the festive atmosphere. After all, with cake, games, and party hats involved, it was hard to feel anything but joy.
The day unfolded seamlessly, with the boys and Omega basking in the celebration. Laughter filled the air as they reminisced about past missions, sharing humorous anecdotes that never failed to bring a smile to their faces. At one point, you pulled Echo aside, quietly reminding him that although the day wasn't specifically tailored to him, it actually coincided with the time when he joined the others.
"This is really kind of you," Echo expressed, seated beside you amidst the lively music within the Marauder.
"You guys have done a lot for me! It's only fair that you get a treat, even if it's just once a year," you responded softly, observing everyone's enjoyment. Even Crosshair seemed to be reveling in the fun.
As the night neared its end, each of the boys approached you individually, surprising you with heartfelt gestures of appreciation. They expressed their gratitude with hugs, while Tech opted for a handshake, true to his analytical nature. Crosshair, unexpectedly, even gave you an awkward side hug before retreating to his bunk, a smudge of frosting lingering on the corner of his lips.
"This meant a lot to us. Thank you," Hunter conveyed, being the last to embrace you. As he rubbed gentle circles on your back, you could sense the sincerity behind his words. He had always believed that he and his brothers didn't deserve the recognition they received, but seeing them all calm and content for once on their "birthday" made it all worthwhile. The vibrant and bold colors of the celebration had momentarily overwhelmed his senses, but he chose to say nothing, not wanting to spoil the experience for the others or undermine your effort.
With hearts full of gratitude and newfound memories to treasure, the boys all settled down to sleep, their hopes eagerly fixed on the promise of next year's celebration, just around the corner.

Masterlist
Tags; @andyoufollowyourheart @littlefeatherr @kaitou2417 7 @eyecandyeoz @captxin-rex @cwarssimp @jesseeka @ashotofspotchka @oohyesplease @theroguesully @mustluvecho @ladykatakuri @jambolska-grozdova @arctrooper69 @padawancat97 7 @rain-on-kamino @either-madness-or-brilliance @staycalmandhugaclone @ko-neko-san @echos-girlfriend @fiveshelmet @dangraccoon @plushymiku-blog @chrissywakingup @kixs-husband @pb-jellybeans @tech-aficionado @grizabellasolo @therealnekomari @tech-depression-inventory @brynhildrmimi @greaser-wolf @tinyreadersmur @seriowan @kaminocasey @marvel-starwars-nerd @ladytano420 @ladyzirkonia @imalovernotahater @crystal076 @blustalker @the-good-shittt @s1st3r @by-the-primes @the-bad-batch-baroness @nunanuggets
#the bad batch x reader#the bad batch x you#the bad batch#tbb x you#bad batch tech#bad batch wrecker#bad batch Hunter#bad batch echo#bad batch crosshair#tbb#nahoney
196 notes
·
View notes
Note
I have a question about your post regarding AI in which you detailed some agents' concerns. In particular you mentioned "we don't want our authors or artists work to be data-mined / scraped to "train" AI learning models/bots".
I completely agree, but what could be done to prevent this?
(I am no expert and clearly have NO idea what the terminology really is, but hopefully you will get it, sorry in advance?)
I mean, this is literally the thing we are all trying to figure out lol. But a start would be to have something in the contracts that SAYS Publishers do not have permission to license or otherwise permit companies to incorporate this copyrighted work into AI learning models, or to utilize this technology to mimic an author’s work.
The companies that are making AI bots or whatever are not shadowy guilds of hackers running around stealing things (despite how "web scraping" and "data mining" and all that sounds, which admittedly is v creepy and ominous!) -- web scraping, aka using robots to gather large amounts of publicly available data, is legal. That's like, a big part of how the internet works, it's how Google knows things when you google them, etc.
It's more dubious if scraping things that are protected under copyright is legal -- the companies would say that it is covered under fair use, that they are putting all this info in there to just teach the AI, and it isn't to COPY the author's work, etc etc. The people whose IP it is, though, probs don't feel that way -- and the law is sort of confused/non-existent. (There are loads of lawsuits literally RIGHT NOW that are aiming to sort some of this out, and the Writer's Guild strike which is ongoing and SAG-AFTRA strike which started this week is largely centered around some of the same issues when it comes to companies using AI for screenwriting, using actor's likeness and voice, etc.) Again, these are not shadowy organizations operating illegally off the coast of whatever -- these are regular-degular companies who can be sued, held to account, regulated, etc. The laws just haven’t caught up to the technology yet.
Point being, it's perhaps unethical to "feed" copyrighted work into an AI thing without permission of the copyright holder, but is it ILLEGAL? Uh -- yes??? but also ?????. US copyright law is pretty clear that works generated entirely by AI can't be protected under copyright -- and that works protected by copyright can't be, you know, copied by somebody else -- but there's a bit of a grey area here because of fair use? It’s confusing, for sure, and I'm betting all this is being hashed out in court cases and committee rooms and whatnot as I type.
Anywhoo, the first steps are clarifying these things contractually. Authors Guild (and agents) take the stance that this permission to "feed" info to AI learning models is something the Author automatically holds rights to, and only the author can decide if/when a book is "fed" into an AI... thing.
The Publishers kinda think this is something THEY hold the rights to, or both parties do, and that these rights should be frozen so NEITHER party can choose to "feed", or neither can choose to do so without the other's permission.
(BTW just to be clear, as I understand it -- which again is NOT MUCH lol -- this "permission" is not like, somebody calls each individual author and asks for permission -- it's part of the coding. Like how many e-books are DRM protected, so they are locked to a particular platform / device and you can't share them etc -- there are bits of code that basically say NOPE to scrapers. So (in my imagination, at least), the little spider-robot is Roomba-ing around the internet looking for things to scrape and it comes across this bit of code and NOPE, they have to turn around and try the next thing. Now – just like if an Etsy seller made mugs with pictures of Mickey Mouse on them, using somebody else’s IP is illegal – and those people CAN be sued if the copyright holder has the appetite to do that - but it’s also hard to stop entirely. So if some random person took your book and just copied it onto a blog -- the spider-robot wouldn't KNOW that info was under copyright, or they don't have permission to gobble it up, because it wouldn't have that bit of code to let them know -- so in that way it could be that nobody ever FULLY knows that the spider-robots won't steal their stuff, and publishers can't really be liable for that if third parties are involved mucking it up -- but they certainly CAN at least attempt to protect copyright!)
But also, you know how I don't even know what I'm talking about and don't know the words? Like in the previous paragraphs? The same goes for all the publishers and everyone else who isn't already a tech wizard, ALL of whom are suddenly learning a lot of very weird words and phrases and rules that nobody *exactly* understands, and it's all changing by the week (and by the day, even).
Publishers ARE starting to add some of this language, but I also would expect it to feel somewhat confused/wild-west-ish until some of the laws around this stuff are clearer. But really: We're all working on it!
87 notes
·
View notes
Text
HZD Terraforming Base-001 Text Communications Network
Chapter 3 | Prev chapter | Next chapter Chapter Index
Zo: GAIA, I had a question about the data we've been studying.
ADMIN [GAIA]: Of course. How may I help?
Zo: Where did it all come from? You told me that you don't have access to APOLLO or any other Old World archives. This seems like far more data than what Aloy could have found on a few scattered devices.
Zo: I scanned some devices around the base and only found a few lines in each.
ADMIN [GAIA]: Before the Faro Plague, even the most commonly available devices could store libraries worth of text and hundreds of hours of high-resolution video. While most people rarely filled their devices to capacity, they would often be filled with many incidental articles and video clips related to their favorite topics. Time and inevitable data corruption rendered many of those files difficult or impossible to read; however, the last file the device accessed has minimal corruption and is most intact. With time, your Focus can restore many corrupted files, and I can accelerate this process. The restored files are then placed in an archive.
Erend: I WAS WONDERING HOW ALOY FOUND SO MUCH OF THIS CONCRETE BEACH PARTY STUFF.
ADMIN [GAIA]: Yes, she found several devices with many hours of their music. The redundancy is also why I was able to ensure the final archive versions were of such high quality.
Erend: NO COMPLAINTS HERE!
Varl: Many complaints here.
Zo: I suppose that explains why so much of the data is entertainment and history, rather than more directly useful information, such as farming.
Erend: I FOUND STUFF ON HOW THOSE FARO MACHINES WERE BUILT. I MEAN, I KNOW IT'S IMPORTANT, THESE WERE THE THINGS THAT WERE ENDING THE WORLD, BUT THERE'S A LOT OF TECHNICAL SPECS IN THERE. HARDER TO READ THAN THE CRAZIEST TINKER'S BLUEPRINT. AND I'VE SEEN SOME CRAZY TINKERS.
Erend: WHAT, DID ALOY JUST FIND SOME TINKER'S JOURNAL SOMEWHERE AND DOWNLOAD ALL HIS DATA?
ADMIN [GAIA]: That is not impossible. However, I do not believe I have properly impressed upon you how easy it was to access information. Once the threat of the Faro Plague became clear, all information on their design, weaknesses, and specifications was available for public perusal, and anyone could choose to download such information from the global data net at a moment's thought. Many of the devices Aloy scanned had gigabytes of data on the Faro Plague.
Erend: GIGA WHAT?
Zo: It's a measure of information. It should have been in one of the first files GAIA gave you, the terminology file.
Erend: UH, I SKIMMED THAT.
Zo: Sigh.
Varl: Did you just typed sigh?
Zo: It's difficult to convey tone and expression in a text.
Varl: I think the Old Ones must have had some way, considering how much they texted. I'll loom into it.
Erend: SO WHAT'S A GIGABYTE? LIKE, HOW MUCH DATA IS IT?
Aloy: A byte is eight bits, or the amount of data required to encode a single character of text. It's basically the smallest measurable amount of data.
Varl: Aloy? You were listening? Or reading?
Aloy: I have a minute. I can text while I ride.
Zo: That doesn't seem safe.
Erend: OKAY, OKAY, BYTE IS ONE LETTER, GOT IT. SO WHAT'S A GIGABYTE?
Aloy: Ten to the ninth power bytes.
Varl: What?
Zo: I don't understand either.
Erend: OH, MATH. I SHOULD HAVE KNOWN IT WOULD BE MATH.
Erend: SO IT'S A STUPIDLY BIG NUMBER. BUT, I MEAN... HOW MANY BOOKS IS THAT?
Aloy: One gigabyte of pure text is probably more books than you could read in a lifetime.
Erend: SO, WHAT, THREE?
Aloy: I'm glad I took time out of my busy day to explain this to you.
Erend: I AIM TO PLEASE!
Chapter 3 | Prev chapter | Next chapter Chapter Index
21 notes
·
View notes
Text
Hello everyone! It has been a moment, and we had a rough few months following a procedure and some other real life situations. But now we're back and can finally confidently release an update. This is a big one. We've listened to what the users were asking, and did what we could to get a chunk of our tasklist done.
Overall
Lighthouse has a slightly new design. The banner is gone, as you can see. That was originally there because we had improperly formatted the navigation bar. Now, there's more of a focus on the website itself, hopefully reducing any distractions.
Almost all large backgrounds have been replaced with small pixel art drawings (made by us) to save on data and load times.
Emoji parsing via Twemoji has been removed. The project was discontinued in early 2023. Lighthouse trying to reach Twemoji was partially why load times were so long.
Because of us personally getting pulled into syscourse (without us wanting to), we have added a Philosophy page to the website. We hope it's now very clear where we stand.
Communal Journal
Each system and subsystem gets their own communal journal now with pagination. The page for it also has prompts, if you need help figuring out what to write.
For privacy and clarity, the communal journal now is on its own page.
Systems
Alters can now appear in multiple systems. They have a "main" system and "other" systems. When looking in their "other" systems, these alters will have a ✦ next to their name. You can place an alter in up to 5 other systems. The breadcrumb navigation currently still points their their main system, though. This will hopefully be fixed at a later date.
Forums
Forums now have a cleaned up reply section. formatting shouldn't be escaping on the alter cards.
In areas where you need to choose an author of a post/reply/etc, there is now a searchable dropdown. We hope this helps large systems.
Glossary
Despite the controversy, we have decided to bring back the glossary. Its new purpose is not to serve as a giant dictionary for terminology, and we will be pruning definitions in the coming days. Users are opted out of the glossary by default, and this can be changed in the settings page. Guests and logged out users can see the glossary.
We know users want us to allow custom terms for their own account, which is something we plan to add in the future.
Other Changes
We hopefully fixed a bug in our Pluralkit import logic that doesn't just gloss over members that weren't added. Lighthouse will keep trying to add a member until it succeeds. We suspect this might make another issue arise, but we'll figure it out from there.
18 notes
·
View notes
Text
Cyberchase: How to Hack the Motherboard
So, when I was writing my episode discussion post on Cyberchase Season 1 Episode 1 "Lost My Marbles", I mentioned that I might make another post about the security breach that allowed The Hacker to infect Motherboard with the virus. What did The Hacker do to set this up? How did the kids accidentally open the breach? And other questions like that. I have a bit of background in software engineering. I will try to keep things as simple as possible.
Much of this is head-canon built on top of what we see in the episode. Of course, the show plays it fast and loose with computer terminology. Don't try to hack things in real life. You will go to prison.
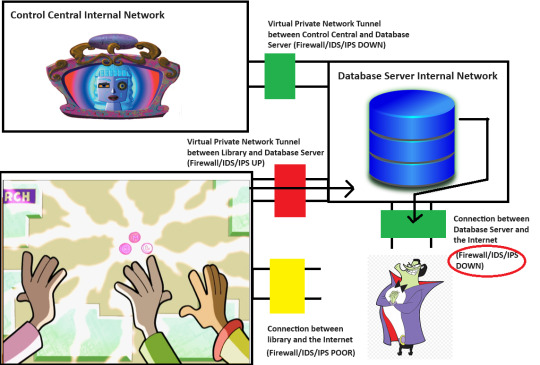
So, here's an MSPaint diagram of a tiny piece of Motherboard's setup. Keep in mind that she is the god of the Internet, and her Internet may even stretch beyond Earth into other galaxies.
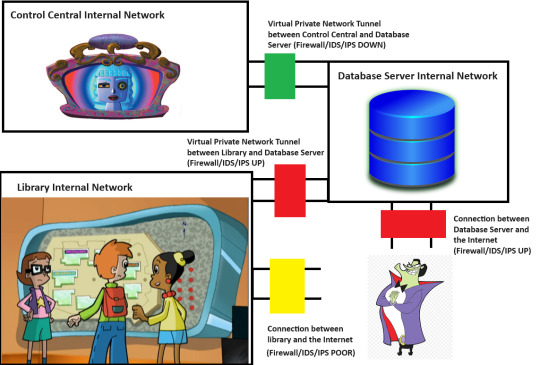
So, there are three separate network segments here. We have the library's internal network, which has the big board on it. We have Control Central's internal network, which has Motherboard on it. And then we have a Database Server internal network, which has a Database Server running on it.
The Database Server is something that I invented here. Remember that this whole diagram is head-canon. However, it's not too far-fetched to think that Motherboard must reach across Cyberspace to a separate Database Server, maybe at the Cybrary.
Now, we know that Motherboard is not directly reachable, even with her Firewall down. Otherwise, The Hacker wouldn't have needed a separate security breach to get to her. He would have just pushed the virus once she took down her firewall for maintenance.
However, Motherboard has a Virtual Private Network (VPN) tunnel to the Database Server. If The Hacker can compromise the Database Server and get his virus in there, it might be able to ride the tunnel into Control Central.
The purpose of any Firewall is to apply a set of rules to any network traffic going into or out of a network, device or application. A good Firewall configuration allows on the traffic that is needed and denies everything else. Motherboard's firewall between herself and the Database Server is currently down. The Database Server itself has connection points to the larger Internet without using a VPN tunnel. However, the Database Server's own Firewall for that access point is UP. If The Hacker tried to throw his virus at that access point, it wouldn't work.
However, there is another connection point into the Database Server. This is another VPN tunnel from the library network. Let's say that the board retrieves the data on the locations of different objects on the map and the icons for those objects by reading one of the Databases. Maybe the board also writes data to the Database to log what directions people requested.
The point here is that some traffic from the Board is authorized to pass through the Firewall on that VPN tunnel. Now, is there a way for The Hacker to get the Board to send authorized traffic over the VPN tunnel to tell the Database Server to open a breach in the Firewall for that public access point? Maybe. It is an Internet-of-Things (ioT) device. Alot of people get these devices, and then they either leave passwords set to their defaults or they forget to keep the sofware patches up to date.
There is a public access point to the Board with a poorly-configured firewall. Maybe there's a way for him to get inside. It may be possible for him to dump the virus code into the board, but there's no guarantee that it would be able to go any further, since the Firewall between the Board and the Database Server is working.
So, let's think about the Board as its own thing.

Suppose that we have two user accounts associated with the board. There is a Principle of Least Privilege that states that a given user account or system process should only be given the minimum amount of permissions required to perform its tasking. That way, if the user account or system process attempts to do something out of line with its permissions, it won't be allowed to perform the operation.
However, if you leave other unnecessary permissions open, and the user account or system process attempts to do something outside of its original intended operations, then the operation may succeed and have unintended consequences.
This also links up with the software development concept of the Minimum Viable Product. You build your software to perform only the exact tasking that it needs it perform. You don't put any additional, undocumented functions in there. Otherwise, those functions could activate and have unexpected consequences.
The board's purpose it to display the different locations. It allows for users to input two points, and it will draw a line between them to assist in navigation. We also established earlier that it reads its information from the Database and writes other information out to the Database.
However, suppose there was some undocumented functionality here. Suppose the developers had a special feature installed in the board that ran a cleanup command against the Database if you pressed three buttons in quick succession. Suppose that the cleanup command in question could be any arbitrary command. Therefore, the developers put the command into a configuration file to be read and executed by the software at runtime.
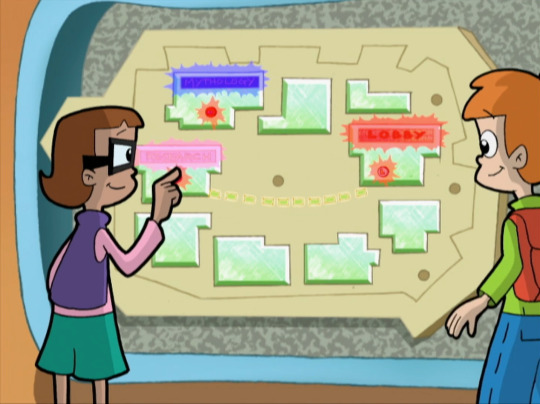
However, the developers knew that if some kids turned up and started poking the map, they could accidentally kick off the Database Cleanup command. They removed the Database Cleanup command from the configuration file. That way, if someone did poke three buttons in quick succession, the software would check the configuration file, see that there was no command defined, and then do nothing.
The trouble is that they left the part of the software that read the configuration file and ran the arbitrary command in place. So, if the command was somehow added back to that part of the configuration file, then there would be a command for the software to run. Then, if someone else pushed the three buttons, that command would be run. So, yeah, someone could put a command in there to write a bunch of junk into the Database until it filled up and crashed. Again, these are commands being sent to the Database from the Board. The Firewall would let them through just fine.
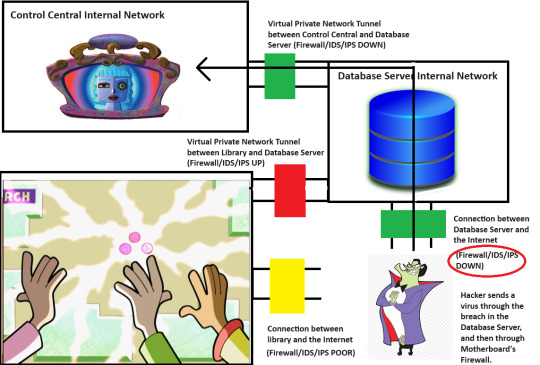
That's pretty bad, but that only lets them modify the Database, right? It's not like they can just tell the Database to open the Firewall on the server that it is sitting on, right?
Well, what if one of the things that the Database could do, upon request, was to open a command shell on the server and run a command. And what if, that command shell was able to run commands that impacted things on the server beyond the Database itself.
What if we called it "xp_cmdshell" and called the Database Server "Microsoft SQL Server 2000". Windows XP and Microsoft SQL Server 2000 would have been around at the time of "Lost My Marbles" after all. Those were also the key players in the real-world Heartland Payment Systems data breach of 2008, which inspired this post.
But hey, just because the Database could open a command shell on the Database Server doesn't mean that The Hacker could use it to bust the Database Server's external Firewall, right? He still needs a way to execute "xp_cmdshell". So, he needs an account with the correct permissions to tell the Database to execute "xp_cmdshell", and he needs the Database itself to have high-enough permissions to run a command via "xp_cmdshell" that can bust the Database Server's external firewall and open a path to Motherboard. Thankfully, the Database only run the "xp_cmdshell" for the top-level Database Administrator account.
This is where we get back to the Principle of Least Privilege. The Board should connect to the Database with a fairly low-power account. It only needs to read-from and write-to a few Database tables after all. Likewise, the Database itself should have been started on the Database Server by a fairly low-power account, as it only needs to handle reading and writing its own set of tables.
But then some moron decided to hook up the Board to the Database Server on the top-level Database Administrator Account. So, if the Board was configured to send an "xp_cmdshell" command, the Database would run it. Oh, and another moron decided to have the Database Server start the Database with the "root" account for that server. So, if the Board was configured to send in an "xp_cmdshell" command to nuke the external Firewall, then the Database would be able to nuke the external Firewall.

There is a principle called Defense-in-Depth, where you build multiple layers of defense around your critical item. That way, if a layer fails, you may be okay. We're running out of layers.
We only have one or two layers left. We know that the Board doesn't run "xp_cmdshell" for its regular operations today. Sure it has an undocumented debug mode that allows someone to execute any command in its configuration file (including "xp_cmdshell") against the Database. But someone would need to get to that file.
The board's main account doesn't give you a filesystem to play with, as they wouldn't want kids running up, poking things, and deleting the filesystem. No, you only get the interfaces that you get. You can pick two items and see a path between them. Or you can pick three items and see the undocumented debug mode run whatever command is in the configuration file.
But what if there was some sort of maintenance account accessible through the Internet that didn't enable someone to send commands to the Database, but would enable someone to get into the filesystem and mess around with it? And what if that maintenance account was still using a weak or default password because people just don't check that for IoT devices?

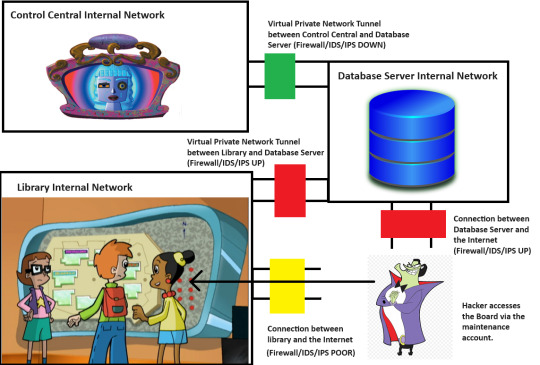
So, he's in the Board's filesystem now. That's concerning. And wouldn't you know it, yet another moron left that critical configuration file in a state where the maintenance account can make changes to it. So, of course, he found the empty configuration item for the cleanup command. Remember, this was setup to run any arbitrary command. Of course, he put in an "xp_cmdshell" command that tells the Database to nuke the external firewall on its own server.
While The Hacker was able to put the command in place, the maintenance account doesn't have the power to send commands to the Database on its own. That power is only enabled for the system account tied to the Board's user interface. So, he still has to rely on someone in the real world to push three buttons in quick succession.


Well...shit.
That's not good.

That's not good at all.


Seriously though, don't try this at home.
I suppose we can speculate on the nature of the virus. We know from Season 1 Episode 14 "Cool It" that Motherboard goes through more cryoxide than normal due to the virus. There are actual computer viruses out there that were designed to turn off heat safety warnings on CPUs and then cause them to run hotter. Some CPUs would eventually melt and ruin the computer.
The original infection destroyed the Encryptor Chip, and it is stated that only a replacement Encryptor Chip could cure the virus. The name suggests that it deals with data encryption, but perhaps it is also a virus cleanup tool. Perhaps it worked to weaken the existing virus until it was eventually overwhelmed and destroyed. Perhaps the virus exhausted most of its strength destroying the Encryptor Chip first.
In any case, curing the virus permanently would end the show.
#cyberchase#2000s#cartoon#nostalgia#pbs kids#2000s childhood#not for use in real life#you'll get busted
11 notes
·
View notes
Text
It’s no big secret that the cost of attending a four-year college or university in the United States is out of control. It’s almost gravity defying how the cost of college has increased relative to regular inflation over the past twenty years. In fact, more than 500 nonprofit private colleges have shut down in the last decade according to the Wall Street Journal, which was "three times what it was in the decade prior."
The news is about to get worse, and there is a stern warning announcement coming from the pilot in the cockpit. 2025 is going to have a lot of turbulence followed by potentially weekly plane crashes of colleges and universities who can no longer afford to open their doors. This new reality is the ultimate law of supply and demand and families in America are voting with their feet.
WHY ARE COLLEGES CLOSING AT SUCH A RAPID RATE?
Enrollment
Trend experts have new terminology they call the "enrollment cliff." The number of students enrolled in degree-granting colleges and universities fell by 15% from 2010 to 2021 and only 62% of high school seniors in the U.S. immediately go on to college right now.
That’s a stark contrast to almost fifteen years ago when the number was 68% in 2010, according to government data. Many of the students who opt out of a postsecondary education are low-income students, but even those with means are beginning to choose alternatives. We’ve also seen a spike in the competition for state colleges and universities where parents can enjoy in-state tuition and other possible grant programs offered for only in-state students.
Beyond the fact that some students are taking certification courses versus going to college, some are entering the workplace and some are considering alternative career paths, we are experiencing a record low number of new babies in the United States which will have a long-term impact on the shrinking enrollment for colleges and universities.
This trend of low birth rates began roughly 17 years ago. After hitting an all-time high in 2007, the Great Recession hit in 2008 causing fertility rates to plummet. The national birth rate fell 23% between 2007 and 2022, and fast-forward to the present day, it isn’t apparent that generation Z twenty-somethings are itching to get a family going. This decline in the overall birth rate is why beginning next year in 2025, and lasting until 2037, we are going to see a major decline in enrollment as 2008 babies begin to reach college age.
It’s not the money… It’s the money
Thirty plus years of providing financial advice for families across America and the number one complaint in the planning process isn’t about how much money someone is going to need to retire. The dialogue quickly shifts to how it’s going to be possible to put two, three, or even four kids through a four-year college education.
Colleges and universities are starting to feel the financial pain.
Even though these higher institutions don’t pay federal income tax or pay real estate taxes, the higher overall operating costs of having a five-star operation and state-imposed restrictions on tuition increases for public colleges have limited colleges and universities' ability to increase tuition revenue. Couple that with the overall market where families are voting with their feet to attend lower-cost colleges and universities, it has put a heavy strain on the ability of these institutions to remain fiscally solvent.
While there are more than 150 colleges and universities boasting more than $1 billion dollars in endowment money, there’s a slew of others that are battling for enrollment, fighting for keeping academic talent and pondering how to keep facilities at a level that new college students have grown to expect from a school.
This not only can affect the school itself, but the surrounding towns or cities where local business is built around the school. On average, each college or university that shuts down affects 265 jobs and $14 million dollars of labor income. To keep their head above water, some colleges have cut faculty and slashed areas of academic study, but it won’t be enough to face the Titanic-like cold water that many universities and colleges are about to face.
Alternative Career Paths
Under DOGE we may eventually see the Department of Education eliminated. And with the possibility of Pete Hegseth becoming the new Secretary of Defense, we may see a new pitch to young people about joining the United States military.
We don’t yet what the future of education will look like in the United States, but it’s quite possible that teenagers in high school will have four potential career paths in the future.
1. College or university
2. Vocational school
3. Entrepreneurship
4. Military
It’s now harder to find blue-collar workers than white-collar workers, reversing a decades-long trend in the U.S. job market. Take plumbers as an example. It’s expected by 2027 that the United States will be short some 550,000 plumbers, which is bad news for the cost to get plumbing fixed and the time it will take to find someone to fix it. These kinds of statistics are universal across all lines of home services blue collar workers.
There are great careers in the military as well and military enlistment has been steadily down over the past 40 years. At the end of the 2023 fiscal year (September 2023), three branches reported falling short of their recruitment goals: the Navy was at 80% of its target number, the Army was at 77% and the Air Force was at 89%. The Marine Corps and Space Force were the only branches to meet their recruitment goals.
The total number of active-duty service members in the US armed forces declined roughly 6% from 2012 to 2022, from 1.4 million to 1.3 million. We are going to need more young people to join the military over the next 10 years.
Closures are coming
The cost of tuition and fees plus room and board for a four-year private college averaged $58,600 in the 2024-2025 school year. With inflation, that’s roughly $250,000 to get one child through a four-year college education. If parents and students continue to question the hefty price tag of a college education, we could see enrollment fall to record lows over the next decade and more colleges close their doors and shut down their operations. Class is not in session!
5 notes
·
View notes
Text
i'm learning about data structures more in depth and hoping some computerheads can clean up my understanding of arrays here. forgive me for not knowing low-level computer terminology
so static-length arrays have good time and space complexity because they occupy a predictable amount of space in memory in a predictable order, making accessing and then adding, updating, or removing values in each index easy math. all this efficiency is at the cost of having a fixed-length in memory at the time of actually programming it which is not ideal if you don't know how long the array should be.
dynamic-length arrays have worse time and space complexity because they (not sure i understand this claim) are a special static array which, when the array runs out of space, finds a new place in memory that's some amount larger than itself (this article i found says "double the length of the original array", again, no idea if that's standard), and copies its own data over to that new place that's so-and-so times longer.
what i don't understand is that, after all that finding and copying is said and done after Computer realizes "oh no! im not big enough! i must become big enough!", why it should be that finding indexes in a dynamic array is any slower than a static array, if they are indeed just a breed of static array that occasionally moves around. is it that in practice static and dynamic arrays have the same efficiency but the Big O Notation for each array type's operations are different because we can't initially predict the size of dynamic arrays?
if you can replace any of this with more specialized terminology id appreciate suggestions
63 notes
·
View notes
Text
tasty data, get your tasty data here
All right, I finished putting TBC2-LL into my Unhinged Spreadsheet, so here are some observations about this text. Long post incoming.
Caveat that this spreadsheet is a work in progress and all the data collection is being done manually, aka trawling the text with my own eyeballs and looking for words. It's entirely possible I've missed some.
A Mo Phopa
There are 47 instances of the word "popa" in this text that I've found.

I had to zoom out to fit them all in. This is so many.
What's really interesting, though, is how terms are paired. If I were to put the spreadsheet back in its original order, showing them in the order they occur in the text, we would see that the use of a phopa for Fergus is almost always accompanied by daltán or a variant ("fosterling, pupil, fosterson"): either Fergus addressing Cú Chulainn as a daltán, or Cú Chulainn identifying himself as such. That means the term in those contexts is firmly established as a fosterage term used with a generational difference.
On the other hand, when a phopa is used by Cú Chulainn to address Láeg, it's very often paired with Láeg addressing Cú Chulainn with an affectionate diminutive like a Chúcúc. The only other person to use a diminutive like this is Lug (or, well, Cú Chulainn's "friend from the Otherworld", who isn't named in this recension), and he only does so once. Láeg does so repeatedly:

By pairing this with a phopa, we're establishing an age difference, but the absence of obvious fosterage terminology and the subversion of expected hierarchies makes this seem more like a "big bro, little bro" relationship, as far as terminology is concerned. A Chúcúc is typically translated by O'Rahilly as "little Cú"; you could also go as far as "little Hound". It's very much both affectionate and emphasising Cú Chulainn's youth.
(In TBC1, by contrast, Láeg only uses a diminutive like this once.)
Putting the rest below a cut to save your dash, because it got long.
Gilla
The term "gilla" is a flexible one: it basically just means lad, boy, servant. It's often used in the narration for charioteers, but I noticed something interesting about its usage in dialogue as a term of address.
Notably, that in TBC1, Cú Chulainn never uses this term to address Láeg, but in TBC2-LL, he does (usually while giving orders, though the spreadsheet doesn't offer that level of detail) (yet). It's used in narration to describe Láeg, I think, but never as a term of address.

Is this a matter of date, and the shifting use of the term chronologically? TBC1 and TBC2-LL are close enough in date that I would be surprised if the term "gilla" had a significantly different meaning at the time of writing.
It does show up quite a bit in late texts, though, so there might be something in that. Need to look into that more.
Comalta, comaltus, daltae
TBC2-LL typically shows a lot more instances of fosterage terminology: comalta, comaltus, and daltae all show up more times. This might just be that TBC2 is wordier than TBC1 and likes to repeat itself more, but the mess of orange on my spreadsheet suggests it also has a greater preoccupation with the web of family, fosterage, and provincial connections between characters.

[ETA: it's just an error that lists one of the comaltas as pupil, fosterling; I think Excel got too enthusiastic with the autofill. The same error occurs below. It's not significant.]
Cú Chulainn once uses the term daltán to address Láeg in TBC1, which doesn't show up in TBC2. I did a post about that a while back; it comes in a line where Cú Chulainn is explaining something to Láeg, so might have a pedagogical usage, although also seems like it might be a little bit sarcastic. Need to explore that one further.
(Note that when Cú Chulainn appears in both the "used by" and "used for" columns, it's because he's describing himself, e.g. Fergus says, "Who's there?" and he says, "It's me, your fosterson and the fosterson of the Ulaid." The relationship given in the column after that is therefore the one being identified in those moments.)
Cara, cairdes, caratraid
TBC2-LL also has more uses of the word cara, friend, for a much wider range of relationships and hypothetical relationships. ("Be it friend or foe" kind of thing.) Cara is used for allies, fosterbrothers, family connections, and some relationships that look like "straightforward" friendship, i.e. there isn't any other clearer connection between the characters mentioned in the text.
The term caratraid for friendship shows up five times in TBC2, and never in TBC1. Three of these instances are to describe Cú Chulainn's relationship with Fer Baeth, one of his foster brothers; one is to describe his relationship with Fer Diad, another foster brother; and one is to describe his relationship with Lugaid mac Nóis, his ally in the Connacht camp (who is also, I think, a foster brother?).
Cairdes shows up three times in TBC2 - twice about Fer Baeth and once about Fer Diad - versus only once in TBC1, where it refers to Fer Baeth (and is in narration rather than dialogue). TBC2 also introduces "cardes sliasta", intimate friendship, with which Medb bribes men.
Fer Diad
Here are all the terms used for Cú Chulainn & Fer Diad's relationship across TBC1 and TBC2-LL:

Let's filter that to get a sense of TBC1 vs TBC2, bearing in mind that Comrac Fir Diad is way longer in TBC2 and therefore likely to have far more terms in it.
TBC1:

TBC2-LL:

So we've got a lot more repetition in TBC2, but we've also got some differences. TBC2 loses some of the endearments, like "a lóeg" and "a airer na súl", which are more typically found in romantic contexts. But it gains two instances of "inmain", beloved (a semantically wider term: we often get a mic inmain between family members, for example). Both use the term "dil" for "beloved", though, inserting it into Fer Diad's name: Fer dil Diad.
Both use the term "cocle", possibly "coicéile": comrade, friend, companion, vassal. TBC2 uses it a lot more, though. It also adds "cara", friend, and the related terms "cairdes" and "caratraid" to describe friendship.
Both use "acme" and "fine", in the same context/sentence: "you are/were my kith and kin". TBC also gives us "fir chomdéirgide", men who shared a bed. There is another reference to bed-sharing in TBC2, but it uses a different term, so this one is distinct. The term "dérgud" seems to refer to the making of a bed, so the vibe seems to be more "men who made a bed together": travelled together, made decisions together, shared intimacy, etc.
The term Cúa is etymologised as an insult in TBC1, but treated as a straightforward diminutive in TBC2. Meanwhile, TBC2 introduces the concept of Cú Chulainn as Fer Diad's "forbfer", or serving man/attendant, introducing hierarchies into their relationship. I was surprised this wasn't in both, but I guess the whole thing is just so much less developed in TBC1, and most of the backstory there comes from Fer Diad's conversations with his charioteer rather than his dialogue with TBC2. I do want to go back and double check it, though, in case there's another related term that slipped my notice.
Conclusions
What is the second recension of the Táin about? Well, statistically, it's about relationships between people.
TBC2 cares a lot about fosterage and the friendships that go with it.
A phopa is the most common term of endearment in this recension.
Combinations of terms tell us more than just looking at terms in isolation.
Spreadsheets can be fun, I guess.
Beyond that, I don't know. I need to add more texts before I can draw more meaningful conclusions about changes over time. But I thought you might like to see where we're at, anyway.
Next up is probably Cath Ruis na Ríg, for vibes, although I also need to add Stowe to this spreadsheet in case it changes anything about TBC2 compared to LL.
31 notes
·
View notes
Text
Sagan 4 is not dead, Sagan 4 is not lost media, and Sagan 4 was never "rebooted".
Sagan 4, with no changes from how it was before 2017 apart from hundreds of new species being added in more recent generations, is right here and people are making new species for it all the time. And yet, these myths have apparently prevailed throughout the speculative evolution community. I'll go over my understanding of where these myths came from, and why they are only myths.
The myth that Sagan 4 is dead
This likely stems from the fears of the Sagan 4 community during The Limbo, a period spanning about 2.5 years from 2017 to late 2019. During this time, Sagan 4 did not have a website and its community was in shambles due to the web host they'd been using shutting down and the only person who knew how to set up a new website leaving the project.
Some have said that Sagan 4 was at least temporarily "dead" during that time, but it's more accurate (and honestly nicer) to say that it was on hiatus while the website situation was being figured out. This was resolved at the beginning of 2020 just in time for the pandemic to give everyone a shitton of free time, allowing it to resume pretty much at full swing.
This myth likely persists in part because we lost sagan4.com. It's currently being held by some company that snaps up brand names to keep them from being taken by randos, and we don't have the money to buy it from them yet. Also, don't visit it because it's being used for ad space and usually redirects to random shady websites for some reason.
The myth that Sagan 4 is lost media
It's literally right here. Sagan 4 was briefly considered lost media during the limbo due to a miscommunication and misplacement of wiki data, which was part of what caused it to take so long for the website situation to be figured out. If it can be said that it was lost media at any point, then today, it is found media.
However, the contents of the original Sagan 4 forum is considered lost media (well, technically, as some threads are intact on the Wayback Machine and Common Crawl, it's officially classified as partially found). The forum contained no canon project content, though it did contain numerous discussions, a whole thread of fanart, and the now-lost losing entries into the sapient contest.
This myth probably persists in part because we lost sagan4.com (see above).
The myth that Sagan 4 was "rebooted"
This myth is perhaps the most understandable of the three, as this was real misleading phrasing used by a handful of Sagan 4 members.
There are two events that are sometimes described as "reboots" when they are not:
The creation of Sagan 4 Beta, a fan project with an early point of divergence that later got made official
The transition into week 27
Sagan 4 Beta is not a reboot because it was always a fan project, at least before it was made official. The original Sagan 4 returned within a few months, but during that time some of Beta's staff members, misinformed about the project's status and their rights over the property (which were none), touted it as an "official reboot". It wasn't, and never was.
The beginning of Week 27, sometimes called a "soft reboot", was not a reboot. I have no idea why Mnidjm called it that; all we did was...make the map not suck anymore by getting a new map artist and adding more climate zones, and make a few changes to the rules (mostly affecting the system for submitting whole genera). We did make some internal changes to stuff like plate tectonics and the space surrounding the solar system, but this wasn't really changing anything so much as filling holes in canon. This also isn't the first time we've even done any of these things including at once (weeks 2, 5, and 20 come to mind), it's really not a big deal.
This myth likely persists because of old threads and lingering use of misleading terminology.
I hope this post clears things up.
9 notes
·
View notes