#before this you had to manually assign ip addresses.
Explore tagged Tumblr posts
Text
Happy (maybe belated or early)birthday DHCP
you've been making everything on the networking side significantly less difficult for what's probably been a *rough* 26 years.
#seriously#before this you had to manually assign ip addresses.#and subnet masks#and like everything#so even thought you're a protocol#thanks for being a good one
1 note
·
View note
Text
Whatever It Takes
A sequel to "A Forgotten Memory"
Alex is once again tasked to continue his mission in pursuing the threat that had caused hundreds of missing persons turn up dazed the next day. But now he isn't alone, join him along with the elite Task Force 141 as they hunt down Nero, discover the secrets behind his plans and put an end to this memory erasing nightmare.
Chapter 1 to another story made by Ray (echo-three-one) Comments and Reviews appreciated! I hope you enjoy! Love you all ❤️

"Resurgence"
"Alex"
CIA Warcom
Boracay Island, Philippines
Alex basked himself on the warm sandy beaches of the Philippines. He wasn't able to enjoy his vacation after the Nero mission, because he was sent immediately to Urzikstan and Verdansk immediately followed. And now that all of those were over, he now laid down on a beach chair and let the ocean breeze blow on his relaxed state.
Philippines was a nice country, the people were hospitable, the food was delicious and unique and the scenery was beyond amazing. Despite his metal leg, people still looked up at him the way they look at tourists and he was all of the hospitality and attention from his fellow Americans who are also on vacation to locals who were just amazed on how the leg works.
It's been a lot of months ever since Samantha forgot him, but he couldn't shake the feeling that they'll meet again, that's why no matter many women try to show interest in him, he shrugs them off politely by pretending he has a girlfriend. A simple lie that he built for himself in hopes of a miracle of meeting her again.
He always brought her letter with him, some edges of it got burnt from the time he manually detonated a C4 explosive to destroy a gas factory, It was almost torn and faded, but he couldn't leave it somewhere safe. He wanted it to be with him wherever he goes.
'Don't you dare forget about me'
His phone rang. He quickly fished it from a small pouch he bought that the locals made and immediately answered.
"This is Alex speaking." he chimed.
"I'm sorry to bother you at this time of day Alex, but I have a feeling you'd want to jump in on this." a British accent so familiar informed him over the other side of the line, It was none other than Captain John Price or Bravo Six, a comrade he once fought with back in Urzikstan.
"I'm all ears." he said, sitting up straight and letting his metal leg sink in the sand.
"Looks like your boy Nero is back on the grid. That Sneaky bastard kidnapped the Daughter of the Head of Defense, again." Price relayed.
Alex's heart thumped faster, his breathing became quick. He wished to meet her again but not like this. Not her being in harm's way all over again.
"Shit. Count me in. But.." he hesitated. He wanted to help but remembered he disobeyed CIA orders back in Urzikstan, making him unable to provide support.
"I've talked to Laswell. She's creating a special assignment for you."
"What does that mean?"
"It means welcome to the 141, Alex." Price said as he cut off the call, followed by a message regarding his departure to their base.
~
Alex can't help but worry about Samantha's condition. They've played with her memories multiple times and he thought that it would all be over after she decided to alter everything about them. Guess the enemy didn't know and they're still after her.
The soldier leaned on to the small circular glass pane as he looked at the clouds pass by. His hands were fidgeting each other while his non-metal foot bounced up and down at a fast rate. His seatmate, who happens to be a teenager, noticed his distracting leg movement but ignored it as rock music blasted from his ears. He was a completely different Alex right now and he believed that he'll be back to normal as soon as he sees Samantha safe and within his grasp.
When you have a heavy metal stick as a leg, customs is going to be the most annoying place in the world. Everyone looked at Alex as soon as he passes the metal detector and everyone else's eyes were on him. Of course with a few more safety checks and a whole lot of explaining, Alex was good to go.
"So, you're the one they call Alex" the heavily British accented driver mused, breaking the silence of their ride to the 141 base. He was looking at him via the rearview mirror, chewing on what Alex hoped to be gum.
"Yep. That's me." he replied, turning to the view of the British streets which confused him a lot as it was the opposite of American or even Global streets.
"Heard they thought you were dead back there. In Georgia." he added. He was quite the chatterbox but CIA Agents are all about the information.
"Yeah. Tried to manually detonate the C4. After that… I just ran for my life." Alex answered, his head was realizing why he did it. What pushed him to think that he could make it out alive. Was it because it's for the greater good? The idea of freeing Farah's country from the harm of the gas? The idea of a chance to meet Samantha all over again? Or something he couldn't explain.
"Well, we're glad to have you back, Alex. But it's a shame it's no longer in the CIA." the driver waved as Alex opened the door and unloaded his stuff.
"As long as it's still about saving the world." he replied, making the driver smile.
"That's what we do, right?" he agreed as he entered in his car leaving Alex in front a quiet gray building, the Task Force 141 Base, his new home.
Alex pushed the heavy doors open revealing a large hall, multiple round sofas were embedded to the ground and a huge staircase that split left and right greeted him. Multiple heads turned as he opened the said door and slowly walked his way to the nearest person who happened to be panting from exhaustion by the sofa. His metal leg clanked on his every step as the soldiers begin to recognize him. They smiled as soon as Alex's eyes met theirs and some even waved, Alex met them from several missions from the past, some were from the Demon Dogs and his previous designations, Delta Force.
"Where's the briefing room in this huge building?" he asked the soldier in a black t shirt drenched in sweat as he spun his towel trying to keep up with his breathing. He didn't speak but he nodded in acknowledgement and pointed to the hallway on the left. Alex left him a thanks and he walked his way to the direction where he pointed.
Just a few steps after the beginning of the hallway, the people from the main hall cheered and laughed, this made Alex turn around and he saw a young blonde man with spiky hair dash across him, he looked like he's on his way to your destination as well.
"Excuse me! Sir!" he yelled and Alex immediately halted. The young man panted in front of him and took a few seconds to breathe before he countinued his words.
"I'm Gary Sanderson, and I was supposed to guide you to the briefing room. You must be Alex." he reached out a hand and Alex shook it, quietly making your way to the room.
The huge door slid open and they found themselves in a dimly lit room, a huge screen loomed just by the wall and chairs were placed around a long circular table. Alex could spot a few familiar faces, faces he once saw and fought alongside with in Verdansk. There was the balaclava boy, Ghost, the Mohawk Man, Soap, their Captain, John Price and a few big heads from the United States. There were also new faces like Gary, who was now discussing something with another new soldier, a female soldier who sat by Price and a few new more who were already sitting on the chairs. There's also someone missing, Kyle Garrick, he pondered where he was.
The former CIA quickly saw Gary rush to Price's seat and whispered something causing him to lean on his chair, stand up and walk to his side.
"Glad to see you back in the fight, Alex." he muttered, patting Alex's shoulder.
"I won't skip out on this mission, this one's close to home." he replied, patting his back in return.
"Yeah, heard this was your last mission before the Russian Gas."
"Yeah. It's a loose end on my side." Alex nodded, crossing his arms.
"Good thing Shepherd had some sense in him. Not unlike your CIA heads, huh?"
Alex nodded. He remembered he did an illegal thing against the CIA, and that was siding with Farah's forces, who were reclassified as global terror groups at that time. He silently thanked he could still step back in the fight along with the good guys even after that event.
"Yeah. I might have to thank him soon enough." Alex murmured and Price guided him to the briefing which was about to start in a few minutes.
~
"Before we start our mission briefing, I'd like to welcome each and everyone of you to the 141. A group of the most elite warriors from around the world tasked to eliminate terrorist threats lurking in the shadows. One of which, goes by the name Nero…" General Shepherd's voice was deep and serious, while the screen showed a photo of the guy they're after. His face looked punchable, as manifested by the way Alex clenched his fists while he stared at his soulless eyes.
"… whose goal is still unknown. He poses a threat as he has been out in American soil, which we believe is the one behind the multiple missing and reappearing person cases across the country." he continued, eyeing Alex. He knew a little bit about the case, maybe because he read his report.
"Since he poses no evidence of terrorist activity as of now, we are assigned to rescue and locate the daughter of Richard Coleman, America's Head of National Defense. We don't know why she was kidnapped but we believed it is or ransom or threatening purposes." The general explained, pacing back and forth, his shadow covered the screen.
Alex wanted to say something. Something about the details surrounding the case. It was written on his report. But then again, maybe the general already knew about the alteration, and since Samantha doesn't remember any IP Address, it was no longer worth noting.
Samantha's face was projected on the screen. Alex's heart began to beat faster, she looked different now, a little chubbier, longer hair and her smile felt happier. It was heartbreaking that she got caught in the crossfire again. After all those efforts of making her life normal.
'If our paths would cross again, I hope you'll remember me the way I remembered you before I take this operation, A good memory that's supposed to last forever. '
'Don't you dare forget about me.'
Her words echoed in his mind, using the same voice she had when they were together.
"I will save you again if I had to.." he promised to her mentally, as he tightened the clench he was already doing.
"Our intel reports that twelve hours ago, local informants spotted an unknown flying vehicle just by the Georgian Border, local authorities confirmed that this wasn't one of their aircraft and we believe it could be the getaway vehicle of Samantha Coleman and her captors… We are still looking on to this so for the meantime I want each and one of you to be fully alert and ready for deployment."
Everyone else fell silent. It meant they agreed at what the high ranking official said. A few more words were exchanged such as new additions to the team, aside from Alex. He didn't seem to focus much on the second part of the brief as his mind worried a lot about Samantha. If his instincts were right, she's probably sedated once again, taking a trip down her own memory lane.
Chapter 2 : F.N.G.
38 notes
·
View notes
Text
Top 7 Fastest VPNs of 2020
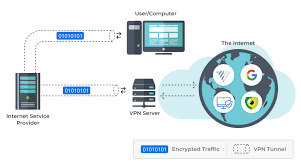
What a VPN is... And what it isn’t
First of all, you still need to preserve your everyday ISP. Using a VPN will no longer update your ISP’s dollars-per-month invoice, but an amazing VPN will act as a cloaking device. All your ISP will see is you having access to anything your VPN makes a decision to show while you connect with your preferred Internet vacation spot.
Second, maximum reputable VPNs will price a subscription price for a motive. You use their offerings, frequently called a tunnel to the Internet. They now personal your information, so you’re paying them to shield your privacy.
Next, your VPN basically turns into your encrypted proxy. Wherever your VPN is, that is additionally where the Internet considers you to be. All roads monitoring your Internet activity will lead returned on your VPN. Do check: ipvanish black friday
Finally, due to the fact a VPN uses encryption, you can file-share and down load securely to coronary heart’s content—even from public WiFi hotspots—as long as your VPN helps peer-to-peer (P2P) record-sharing.
The alternate-off to all of this, of course, is that every one that encryption and additional layers of security can slow Internet get admission to. That’s why it pays to realize precisely which VPNs are maximum probably to maintain you now not best safe and relaxed however additionally up to speed. Here are our top picks, some want-to-recognise specifications and some nods to what makes them special.
Choosing a VPN Political, societal and technological shifts handiest increase the significance of security, anonymity, statistics usage, P2P report-sharing and torrenting competencies, and bandwidth and velocity. Subscription charges vary from the loose—and regularly slow, insecure and volatile—to the high-priced. However, nice VPN providers have a tendency to vary with the aid of just a few greenbacks. When looking for your plan, make certain to recall the following:
Security—as a minimum 256-bit encryption. Compatibility with hardware and software. Server and IP cope with availability and place. Country of registration and information retention laws. Bandwidth or information restrictions, consisting of throttling. Servers unique for P2P report-sharing, torrenting or different designations. Firewalls. Proxies like SOCKS5. Kill switches. Split tunneling and talents for manual configurations. Customer service and help. Considering speed with VPNs When it comes to hurry, understand that a VPN in reality puts a unique license plate in your carload of records inside the flow of visitors. The pleasant VPNs won’t sluggish you down by using a good deal. However, you could occasionally have to weigh protection against speed, and any VPN still relies at the underlying download and upload speeds that your ISP permits.
1. ExpressVPN ExpressVPN is a first rate first pick in a test of VPN speed because we can begin with its VPN Speed Test. This handy menu device types the servers and assigns every a pace index based totally on essential factors:
Latency — the milliseconds’ information travels among your device and a VPN server Download speed — how many kilobits in line with second or Kbps. Based inside the British Virgin Islands, Express substances extra than 1,000 servers in a hundred forty five VPN server places in ninety four nations. Just run your speed check and megastar your favorites.
This VPN is known for its stability of HD streaming abilties, P2P record-sharing, and security features. It supports all gadgets, from mobiles and computers to routers, and any connection— stressed out Wi-Fi or cellular. It allows three simultaneous connections, making it the most limited of our pinnacle selections (however, one of those may be a router). As for its other features, you could anticipate:
Compatibility with Windows, Mac, iOS, Android, Linux, and routers. Protocols OpenVPN TCP/UDP, SSTP, L2TP/IPsec and PPTP. AES-256-bit encryption ingoing and outgoing.
Unlimited bandwidth, velocity, and server switches. DNS Leak Test device and Express help to remove any leaks. Network Lock, ExpressVPN’s kill transfer for Windows and Mac. Shared IP addresses.
Split tunneling and inverse split tunneling to shield precise connections. Supports VoIP. P2P and torrent-friendly.
Zero logging, with site visitors blending. Terms of provider kingdom that they do music connection dates, server and amount of information strictly for analytics. A full menu of payment alternatives such as credit card, Bitcoin, PayPal and more. Intuitive internet site with lots of informative screenshots and help. Round-the-clock customer service through live chat or e mail.
2. NordVPN Like the alternative six on our list, Nord uses AES-256-bit encryption for all traffic, both incoming and outgoing. However, this VPN adds a second layer to act as a double VPN, encrypting data flowing between your device and your first DNS server and alternatively at a second server before the visitors meets the Internet. Incoming definitely reverses the manner.
Just 5 years antique and based totally in Panama, NordVPN has approximately 1,000 servers in fifty nine nations. It is one of the maximum generous of our selections, allowing an impressive six simultaneous connections. However, each must use a extraordinary protocol. You have 4 options—OpenVPN TCP/UDP, L2TP and PPTP—so essentially, in case you want to apply all six devices straight away, you’ll ought to break up between two or greater servers. Nord does guide routers—which count as one—as well as all other mobile and desktop gadgets. As for the capabilities rundown, NordVPN gives:
Compatibility with Windows, Mac, Android and iOS, with custom software program available. Protocols OpenVPN TCP/UDP, L2TP and PPTP; confined IKEv2/IPsec. IPv6 support expected for 2017. AES-256-bit double-layer encryption ingoing and outgoing. Unlimited bandwidth and velocity. Automatic kill switch for Windows, Mac and iOS. Identified double VPN, Onion over VPN, anti-DDoS, devoted IP, general VPN and P2P servers. Ultra Fast TV and P2P-optimized servers; permits torrenting. Supports VoIP. Supports SOCKS5 and HTTPS proxy servers. Smart Play relaxed proxies to circumvent geoblocking and permit content streaming.
Option for upload-on committed IP server and static IP deal with in U.S., U.K., Germany or Netherlands. Zero logging. Full menu of price options consisting of credit cards, Bitcoin, PayPal and extra on Paymentwall. Well-maintained internet site with useful FAQs page and dietary supplements. 24/7 customer support thru stay chat, email, Nord’s price ticket gadget, Facebook or Twitter.
Three. IPVanish IPVanish is based in Florida’s Orange County. IPVanish is thought for its speed and being torrenting- and P2P-friendly—making it a fave for game enthusiasts. The organization boasts greater than 750 servers in at the least 60 countries, with more than forty,000 IPs general and as a minimum 10 specific—often more—shareable IP addresses per server.
IPVanish permits five simultaneous connections on a couple of gadgets—such as routers—at the four protocols—OpenVPN TCP/UDP, L2TP and PPTP—in addition to IPSec and IKEv2 for iOS. IPVanish consists of SOCKS5 in all its plans, which means that which you have the option of passing traffic—downloading torrents, for instance—thru an nameless high-pace, offshore proxy. In addition, the carrier consists of:
Compatibility with Windows, Mac, iOS, Android, Linux Ubuntu and Chromebook. Protocols OpenVPN TCP/UDP, L2TP and PPTP; IPSec and IKEv2 for iOS and IPv4. AES-256-bit encryption ingoing and outgoing. Unlimited bandwidth and server switching. SOCKS5 proxy. IP address biking. Support of VoIP. Unlimited P2P supporting BitTorrent. NAT firewall. Kill transfer for Mac OS X and Windows. No traffic logs.
Extensive charge options including credit score card, Bitcoin, PayPal and plenty of others. Extensive website. Technical records, but, can be hard to discover. Support to be had thru electronic mail. When we checked, there was a wait of about 36 hours.
Four. PureVPN
Celebrating “10 years of safety,” PureVPN claims greater than 1,000,000 users and guarantees them “entire freedom” and “global-class” safety on both a personal and enterprise scale. The company is primarily based in Hong Kong, which has no mandatory facts retention laws—why many individuals pick a VPN inside the first area.
Meanwhile, PureVPN is a connectivity maven. Its community covers 141 nations with 180 places and more than 750 servers. It allows five simultaneous connections for greater than 20 exclusive devices. Its virtual router feature allows you to show any Windows pc or computer into a digital router for up to ten gadgets. On pinnacle of that, PureVPN writes its personal code for all of the primary structures and uses no third events for real statistics transfer. PureVPN covers all of the fundamental desirables like:
Compatibility with Windows, Mac, iOS, Android and Linux. Selection of protocols—OpenVPN TCP/UDP, PPTP, L2TP, IKEv2/IPsec and Stealth. IPv6 leak safety for Windows and Mac. AES-256-bit encryption ingoing and outgoing. Unlimited bandwidth, facts transfer and server switching. Split tunneling for Windows and Android. File-sharing restricted to specified servers. Kill switch for Windows and Mac.
Optional add-on dedicated IP and static IP address. Zero logs. Extensive fee alternatives—credit score playing cards, PayPal, Alipay, assorted Bitcoin organizations, Paymentwall and Cashu. Very consumer-friendly, intuitive website with seek option. 24/7 stay chat pop-up for assist.
Five. VPNArea Based in Bulgaria, VPNArea opened store in 2012, with its headquarters servers and electronic mail hosted in Switzerland. The organization is committed to keeping a speedy consumer-to-server ratio, citing a server for every 250 clients. It’s now up to more than two hundred servers in 68 international locations and greater than 10,000 IP addresses.
Another generous VPN issuer, VPNArea permits you six simultaneous connections to your favourite devices, together with routers, through OpenVPN TCP/UDP, PPTP or L2TP. It also gives its very own Chameleon app for Windows. Like a number of different vendors—however no longer all—VPNArea’s service consists of a kill switch machine; in case your VPN service drops for a few cause, your IP deal with will stay covered. VPNArea’s carrier also affords:
Compatibility with Windows, Mac, Android, iOS and Linux. Protocols OpenVPN TCP/UDP, PPTP or L2TP. IPv6 and WebRTC leak protection. Chameleon OpenVPN software program for Windows. AES-256-bit encryption ingoing and outgoing.
Unlimited bandwidth and server switching. Shared IPs, with adjustable car random IP changer. Speed check with ping and download in addition to users on-line server load screen. Kill switch device.
P2P permitted on distinct servers. Account sharing. Custom business accounts available. Optional add-on personal VPN server with dedicated IP cope with $15 a year. No logs. Payment options restricted to Visa, MasterCard, PayPal, Payza and Bitcoin. 24/7 help to be had through stay chat, electronic mail and Skype.
6. Buffered Buffered VPN is the youngster in our seven. Registered in Budapest, Hungary, in 2013, it has servers in 37 international locations and guarantees that in case you don’t see the only which you need, they just might be capable of get one for you. This VPN is enthusiastic about preserving freedom of speech and access to data irrespective of in which you're. Buffered no longer most effective says that it’s torrent-pleasant however is also cited for being so.
Buffered allows customers five simultaneous connections and houses in on the want for comfortable velocity with out the constraints of throttling. It gives some of the offerings you would anticipate with a few obstacles:
Compatibility with Windows, Mac, Linux, iOS, Android in addition to DD-WRT and Tomato routers. Exclusively OpenVPN TCP/UDP protocols. Supports IPv4. 256-bit Blowfish encryption. Friendly to P2P record-sharing, torrenting, gaming and streaming. Unlimited bandwidth, speed and server switching Optional add-on dedicated server with static IP cope with. Supports VoIP and Skype. NAT Firewall.
Dynamic IP addresses. Will set up servers upon request. Does no longer allow split tunneling. No kill switch. No logs policy. Salesy website. All the technical records—everything you really want to realize—is within the internet site’s FAQs phase and tutorials. Payment menu includes the primary credit playing cards, Maestro, JCB and PayPal. 24/7 guide via stay chat with Knowledge Center.
7. VyprVPN VyprVPN is sincerely a Golden Frog introduction included in Switzerland, which—because the Golden Frog site explains—has set up safe harbors with the EU, the U.S. And other countries. These folks take their security critically. Their very own inhouse engineers write their code. They very own and manage all their own hardware and software and keep their operation inhouse, and not using a 1/3 parties. They’ve were given more than 700 servers and 2 hundred,000 IP addresses spanning the globe, supplying cease-to-stop privateness.
If you need a seasoned bono download of a GB to strive out the VPN, you may sign on for VyperVPN Free. Just choose your app at the website—it really works for desktops in addition to iOS and Android. You could have two simultaneous connections and get right of entry to to the Cypher encrypted messaging app. It’s a one-time deal, but you could without problems improve to a subscription.
A lot of misunderstanding exists over the feature of split tunneling, and Vypr isn't any exception. At its only, the exercise lets in customers to consist of or exclude certain devices or applications, putting a few below VPN protection while permitting others to interface or stream at once out of your ISP. Not all VPNs even provide it. The configuration that VyprVPN uses allows split tunneling with the aid of app. In addition, a subscription comes with:
Compatibility with Windows, Mac, iOS, Android, Linux, TVs, OpenELEC clever gadgets, routers and extra. Protocols OpenVPN TCP/UDP, L2TP/IPsec, PPTP and Chameleon. 256-bit encryption. Unlimited bandwidth, pace and server switching. Golden Frog-optimized code for cutting-edge broadband connections. NAT Firewall. SOCKS5 proxy supported.
Dynamic server switching. Kill switch in Windows and Mac. Split tunneling for apps however now not servers or gadgets. Desktop and mobile apps, consisting of Blackphone and Anonabox. Chameleon proprietary metadata scrambler for Windows, Mac, Android and routers.
Conclusion: Zero-know-how VyperDNS provider preserves privateness and geolocational get right of entry to, defeats censorship and geoblocking. User-pleasant, exceptionally informative website with the entirety inside the right place—just in which you’d placed it. No logs. End-to-end code, possession and management.
1 note
·
View note
Text
The Printer Could Not Connect To Web Services
You may want to perform a print job, but it takes a very long time before the document is printed. Or that the router can’t even find your printer. This is a common problem. But don’t worry, we have the solution.
What’s the problem?
Printers and other devices sometimes spontaneously want to be disconnected. As a result, you can no longer print carefree. The printer could not connect to web services but with the IP address’s network settings (TCP/IP network).
The printer may (since an update) automatically connect to the network through a WSD port. Web Services for Devices (WSD) automatically searches for your printer and assigns an IP address to it. But when a printer is rebooted, for example, it may suddenly be associated with a different IP address, causing a delay.

Every device has an IP address, and there are two ways to capture the IP address for your devices connected to your network:
A static IP address: you set this manually and will not be able to change
A dynamic IP address (via the DHCP server): this is automatically assigned by your router to your device for a certain time. A certain range (scope) is defined with IP addresses where the router chooses an IP. For example, the range is from IP address 50 to IP address 150. This only considers IP addresses within the range that the router has already assigned.
The problem usually lies with the automatic recording of a dynamic IP address. If another device is also automatically assigned an IP address, for example, when someone connects to your Wi-Fi network, it may get the IP address that your printer had. This creates confusion, and your printer can no longer be easily found. In addition, this results in a slow connection because the correct IP address has to be found or even no connection.
READ MORE: How to work when your printer Would not Print
What is the solution?
Giving a fixed (static) IP address to your printer will always remain the same. However, be careful not to accidentally grab an IP address that falls within the DHCP range of the DHCP server because it can just assign it to another device.
You can change the domain of your DHCP server and the IP addresses in your router. These settings are slightly different per router. So take a good look at which router you have and just Google: Router settings + the name of your router.
1 note
·
View note
Text
Smart DDI (DNS, DHCP, IPAM) Solution

DNS, DHCP, IPAM – together they form what we often refer to as DDI. They all work together to manage, assign, and resolve IP addresses and form an important part of any network. we explain below what each of these components are, what they are used for, and why you need them.
Today we start our journey by discussing IP addresses, what they are and why we use them. We will then introduce the DHCP system, how it works and what are its various components. After that, we will discuss the interaction between DNS and DHCP and why it is so important. And we’ll end this article by explaining what DDI is and why it’s so important. And after we’ve finished learning all the basics, we’ll move on to reviewing the multiple versions of EZELINK DDI/IPAM solutions for various industries.

IP addresses are at the very center of the Internet. They uniquely identify each device connected to the network. There is an important distinction to be made between public IP addresses and private IP addresses. The former are those used on devices connected to the public internet. For example, a web server often has a public IP address. The Internet router installed by your ISP in your home also has a public IP address. On the other hand, private IP addresses are the ones we use in home and corporate networks. They must also be unique, but only within a particular network.
Back in the prehistory of the Internet, when the IP protocol was defined, each connected device was manually configured with a separate IP address. We called it static or fixed IP addressing. It was cumbersome but ok since the number of connected hosts was low. As networks (both public and private) grew, it became increasingly difficult to manually configure IP addresses, as the process was error-prone and often resulted in duplicate IP addresses on the network. It took until the early 1990s before a durable solution was introduced in the form of DHCP.
DHCP
The Dynamic Host Configuration Protocol – or DHCP as we commonly call it – was invented to dynamically assign IP addresses and allow connected hosts to connect. DHCP eliminates the need to manually configure IP addresses. DHCP not only configures IP addresses, it can configure most of the connected host’s network settings, such as IP address, subnet mask, name servers, WIND server(s) in the Windows environment, and a few other settings. All parameters are dynamically configured each time the host is started on the network.
No matter what exact parameters are configured by DHCP, the host configuration process is always the same. This is a four step process called DORA which stands for Discovery, Request, Offer and Acknowledgment. Here’s what happens when the host starts.
During the discovery phase, the host sends a broadcast message – this is a message that will be received by any host connected to a network called DHCPDISCOVERY. The message must be transmitted because the host does not currently know the address of the DHCP server.
In the second step, the server responds with a DHCP offer. The offer contains all the host network interface configuration options. Now, this is where things get a little more complicated. Because there can be multiple DHCP servers on a network, a host can receive multiple offers. When this happens, the host will simply select one of the offers and move on to the next step. Which one to choose? He usually chooses the first offer he gets.
In the next step, the host sends a DHCP request. It turns on the offer it chooses and will instruct the server whose offer it decides to proceed with, telling other servers that sent offers they had rejected and that they can release the offered IP addresses.
In the final step, the server sends a DHCP acknowledgment to the host confirming that it has correctly reserved the proposed IP address for that host.
DHCP Client Component
The DHCP configuration information received by the client and used to configure the network interface is invalid forever. In fact, it is leased, not assigned, by the DHCP server. And that lease expires.
It is one of the most important tasks of a DHCP client to ensure that the interface configuration remains valid. It does this by periodically trying to renew the lease before it expires. The update process uses the same DORA sequence. The only difference is that during the discovery phase, the client requests the same IP address that it already has.
Another important function of the DHCP client is the release mechanism. Whenever the client no longer claims its IP address, as it can when it terminates, it will notify the DHCP server to release the IP address so that it can be reused by the server.
DHCP Server Component
As far as a DHCP server is concerned, its main job is to send configuration information to any host that requests it, and have it send unique options to each individual host. IP addresses can be assigned by a DHCP server in one of three ways: dynamic, automatic, or static.
Dynamic allocation assigns a new IP address to each IP address. Automatic allocation is similar, except that the server will keep track of what IP address was assigned to each host and will try to assign it the same address the next time it connects.
And finally, with manual allocation, the administrator must manually associate a specific host, identified by its MAC address, with a specific IP address. This is also called a DHCP reservation because it reserves a specific address for a specific host.
Interaction between DHCP and DNS
The Domain Name Service – or DNS – is used to map hostnames to IP addresses. In a private network using dynamic DHCP allocation, there is often some integration between DNS and DHCP. So DNS always knows the current IP address of each host.

DDI (DNS, DHCP, IPAM)
DDI is an acronym for DHCP, DNS and IPAM or IP address management. While we have not yet discussed the latter. IPAM refers to any software used to manage IP addresses. Such systems can typically be used to manage both DHCP-assigned addresses and statically-assigned addresses that are manually configured on hosts.
With the tight integration that is required between the three, it is quite normal that many vendors have three products built into each other, or that they offer all three products separately.
EZELINK 5 versions of DDI/IPAM Systems

EZELINK Platinum Network DDI
EZELINK Platinum DDI is one of the best in network management. The product conist of some of the best tools for helping administrators. It allows you to use built-in DHCP and DNS servers making it a complete DDI system, and the software can also communicate with DHCP and DNS server from Microsoft and Cisco so you don’t have to replace all your infrastructures.
The software allows you to use several distribution methods for IP addresses. For example, you can use reservations for servers and other equipment and dynamically allocated addresses for workstations. Everything is fully integrated into DNS. In addition, a configuration wizard is included to assist in configuring DHCP scopes.
EZELINK Platinum Network DDI uses user accounts with different access levels. You can grant only partial access to some junior administrators, or allow managers to view reports. There is also a good logging system that records all changes with a timestamp and the username of the operator who made the changes. This can help with compliance issues.
EZELINK Large Enterprise DDI
EZELINK Large Enterprise DDI is one of the industry leaders in this field. The address management is best suited for large corporations with a network management team. The IPAM system is actually a complete DDI system that includes DHCP and DNS. It can also communicate with DHCP and DNS servers from Microsoft.
It’s a is a dual stack system, which means it can work with both IPv4 and IPv6 at the same time. It’s really a great tool to use when moving from one to the other. From a security point of view, the system has workflows and approval schemes, as well as user accounts with hierarchical rights.
The system uses network templates. They allow the administrator to use information layouts that prevent important tasks from being overlooked and that all important data is present. In a nutshell, the EZELINK Large Enterprise IPAM system automates as many network administration tasks as possible. As a result, problems caused by human error are less common. It is a premium package so you can expect premium prices, but if you manage a large network it’s worth the investment. You can visit our DDI Solution page for more information.
EZELINK Centralized DDI
EZELINK Centralized DDI is ideal for management of the IP address space. It can handle both IPv4 and IPv6 addresses. The built-in IP manager software helps network administrators determine whether an IP address is currently available or not. The IP Address Manager tool periodically scans the subnets and updates the availability status of the IP addresses on each subnet.
Users can use the IP Address Manager tools to quickly and easily check if a particular IP address is reserved or available. The tool accepts multiple subnet inputs, which helps when scanning the entire network to get the status of all IP addresses.
Request for a free demo of the product, with limited to one subnet. It is enough to give the product a trial run. It might even be all you need if you run a smaller network. Visit the EZELINK website for more information.
EZELINK SME IPAM & DHCP
EZELINK SME IPAM & DHCP is better suited for small to medium networks. Like other SME systems, it has templates for automating routine tasks. It also comes with excellent standard reports. And if you don’t find existing templates or reports to your liking, you can customize them to your liking.
SME IPAM & DHCP allows managers to track key resource usage. It also has snooping features that help you manage your DHCP usage efficiently. Security-wise, this is great, as it also includes the ability to identify external addresses and isolate rogue devices. This is a pretty unique feature that you won’t find on other systems. It shows how EZELINK treats security like it does IPAM and has safeguards built into the system.
New nodes can be centrally integrated into the network through the DDI user interface, and per-node usage comparison is also simplified with efficient MAC address records as well as IP address tracking.
EZELINK IP Manager
EZELINK IP Manager is a great DDI kit is an automated Internet-based IPv4/IPv6 address management software (IPAM). It has powerful network discovery features and offers search and filter functions for networks and host by resolving equivalent expressions in the Internet search engine. This allows you to find information that administrators often require easily and quickly.”
In concrete terms, it’s a great system, especially for small businesses that might not be able to afford large solutions like Centralized DDI and SME IPAM & DHCP. It includes all the features a network administrator could want with minimal price. And it also has some unique features like subnet calculator and IP address plan builder. This is definitely a package worth looking into.
Conclusion
EZELINK has a big range of multiple versions of DDI platform suited to every organization as per heir requirements and features. The above five are the ones we think will cover most of the industry business requirements for large and small networks. But if you feel you need a turnkey solution EZELINK R&D team can be a big help to deliver customized solution as per your requirements .
1 note
·
View note
Text
Wavlink AC1200 Repeater Setup- WPS and Web-Browser Method
Gone are the days when one had to worry about slowed-down internet speeds, distributed bandwidths, and like issues. Adding a range extender/repeater to your network device hierarchy will go a long way in ensuring all-around network coverage. If you are looking to extend the network coverage of the existing router in your home/office, having a Wavlink AC1200 repeater will be an advantage. You can ensure improved coverage and 24/7 access to high-speed internet around your location. However, until you have mastered the steps to the Wavlink AC1200 repeater setup, realizing this goal can be difficult.
This blog will walk you through the steps to access the repeater’s setup page so you can complete the Wavlink AC1200 repeater setup process easily.
Things you would need for Wavlink setup
Before you begin with the Wavlink AC1200 setup, you will need to ensure that you have some essential details and equipment ready. These may be-
● The main router’s SSID and network key,
● Your extender’s default login credentials,
● Ethernet cable(s),
● The default repeater login web/IP address, and
● A working internet connection.
Default Wavlink Repeater Login Address
Web Address: https://wifi.wavlink.com
IP address: https://192.168.10.1
Login Credentials for your Wavlink Repeater
Default login username and password: admin
Beginning with the Wavlink AC1200 Repeater Setup
Setting up your Wavlink AC1200 as a repeater would require you to connect it to the main router wirelessly. You can follow the steps as mentioned, for the Wavlink repeater setup process:
● Connect your Wavlink AC1200 to a power outlet near your wireless router. Switch on the power supply and allow the device to come to a stable functioning state. You’ll see the LEDs on the front panel glow-up and the Power LED turn solid.
● When they do, open the wireless network Settings on your smartphone/computer and then connect to the Wavlink network. You will see the Wavlink SSID with the model number or the network band as a prefix. Click on the same and click on the connect button.
● Now, open a web browser and you will be redirected to the web-based setup page automatically. If you are not, you can manually enter the web address “wifi.wavlink.com” or the IP address 192.168.10.1 in the address bar of the browser and then press Enter.
● When the Wavlink login page appears, type in the default username and password of the Wavlink repeater and then click on the login button.
Modifying the Wavlink network settings
● On the setup wizard, you will be asked to select the main router network to connect to. A list of available networks will be shown. Select the SSID that belongs to the main router and type in the log-in password to connect to it.
● In the next screen, you can configure your network by assigning an SSID and a network protection key. Assign the same to the 5GHz network band as well.
● Once done, assign a new username and password for the login details.
● The final screen will show you a summary of the network configuration you have just changed. Review the same and you can click on the Finish button.
Relocate your Wavlink AC1200 now, to a location of your choice and connect your wireless-enabled devices.
Wavlink AC1200 Repeater Setup using WPS
WPS means “Wireless Protected Setup”. Using the WPS button present on the devices, you can sync them to work together and extend the signals further. If you are looking to set up your Wavlink AC1200 repeater using the WPS method, here are some steps you can follow:
● Locate the WPS button on your wireless repeater and the wireless router. Keep them close so they can communicate easily.
● To start with, press the WPS button on the main router. You’ll see the WPS LED glow.
● Within a duration of two minutes, press the WPS button on the extender as well.
● The two minutes duration is allotted so that you can get done with the complicated setup procedures which some devices entail.
● Now, you will need to wait until the Signal LED on the extender device changes to solid blue. This change in color will indicate that the WPS connection is successful and you can now proceed with surfing the internet.
The extended network will have the same network SSID as that of the main router network.
You can now connect your wireless devices and enjoy uninterrupted internet access.
Need more help with the Wavlink AC1200 repeater setup? Get in touch with the team now!
0 notes
Text
Another Device On The Network Is Using Your Ip
IP Location Lookup tool provides information about the location of any entered IP Address. Not only location, but it also points the pin on the map which is an estimated location of that IP. Besides, it also knows the latitude, longitude, city, state, country, and ISP of an IP Address, and whether or not it's a crawler, or a proxy, etc. Profone IP tracker Track down the location of a mobile device online using its IP address and display its location on Google Maps. To find your public IP address, just Google what is my ip. Do not test it with IP starting with 192.168 etc. Learn how to find the sender IP address from Email. My phone ip.
Hello,
Another Device On The Network Is Using Your Ip Address
Another Device On The Network Is Using Your Ip Mac
Another Device Using Ip Address

ever since upgrading to Mac OS High Sierra I have been having many issues. This is one of them; an annoying message which pops up all the time
Select “Internet Protocol Version 4 (TCP/IPV4)” and click “Properties.” g. Under “General” tab, select to check “Use the following IP address.” Manually assign an IP address which is different from that of the IP on the other computer(s) on the network. Jul 27, 2011 It means you are using static IP addresses and another device on your network is using that IP address. You should setup the router so that it is using DHCP to assign IP addresses. Jul 19, 2017 Has anyone seen this error message before, 'Another device on your network is using your computer’s ip address. The connecting device does not have a static ip address assigned to it. And every time the Peplink router tries to assign a different/new IP address the error message pops right up.
When I choose 'OK' I start getting internet connectivity errors, slow internet speeds, and consistent drop outs on my Mac. I have looked up solutions to fix the problem which hasn't resolved the issue. I have tried:
Another Device On The Network Is Using Your Ip Address
Changing my IP address through 'Network' in System Preferences, this only results in giving me the same IP address I had before
Resetting my router which has done nothing. 10 minutes later I get bad internet again.
Disconnecting other devices, such as my Ipod Touch, Ipad, etc, that also connect to my network which has not resolved the issue
SMC Reset, which hasn't resolved the issue.
Another Device On The Network Is Using Your Ip Mac
Autotune plugin fl studio 20.
Anyone have any solutions of how to fix this? If not I would just downgrade. .. not really a big deal, but why does this happen in the first place? Thanks.
Another Device Using Ip Address
Posted on Mar 16, 2019 1:29 AM
0 notes
Text
HOW TO RUN AND HOST WORDPRESS ON ANDROID PHONE OR DEVICES
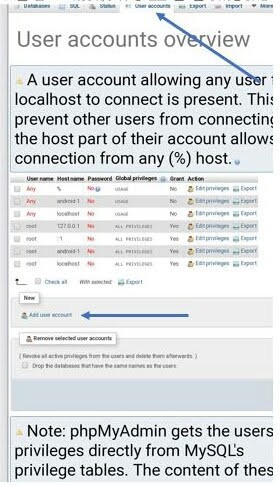
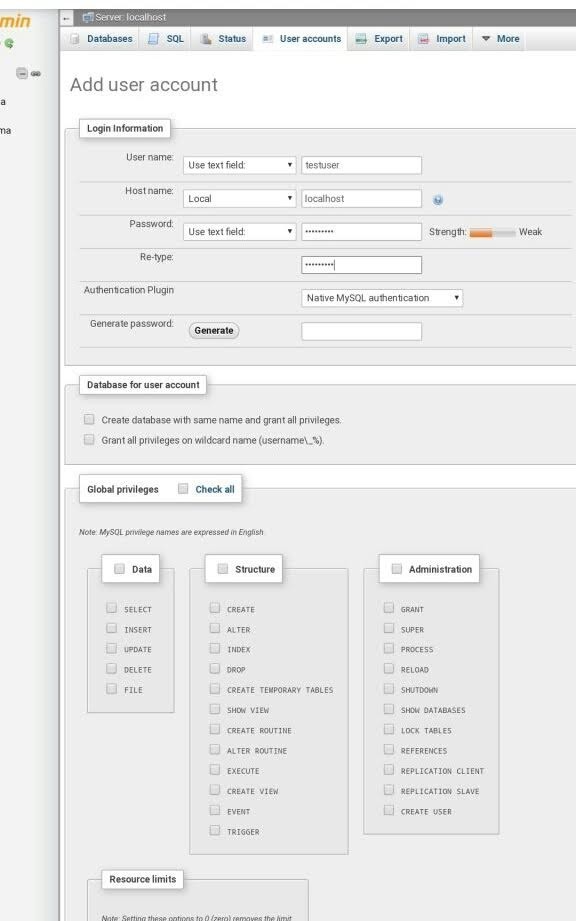
WHY WORDPRESS IS NOT FREE OF COST DESPITE OF OPEN SOURCE CMS you may wondered after knowing, that wordpress (wordpress.org) is free and open source content management system (CMS). Despite of that, why I have to paid money to run wordpress online. Answer is here, because they not charge you for running wordpress online. rather they charge for providing you their hosting space on server manage by them . Because they have to hire employee for maintenance of server they built and technical support they provide. WHY IT IS NOT EASY TO RUN AND HOST WORDPRESS ON ANDROID Android lacks stable Web server based application. Android devices lacks such powerful disk and ram to run . But recently in few past years, mobile phone had becamed capable of running Web servers to some extent. nevertheless, the thing which refraining us from doing such stuff like creating a web server (Apache, MySQL, PHP, PHPMyAdmin) on the Android devices is the lack of stable resources. Now, Let's discuss main part of this article that is, why you are here. KSWEB FEATURES AND REQUIREMENTS Hold on please do check following before proceedings. If your device compatible or not. The developer of KSWEB says Android device with OS version 2.3.3 or higher and ARM-based processor is required. I will try to run KSWEB on IS05 (Japanese old Android smartphone by SHARP) and the procedure on this post is about this device. But maybe KSWEB can run on so many kinds of Android devices. Please try on any devices you have. KSWEB contains: - lighttpd server v1.4.35 - nginx v1.13.1 - Apache v2.4.28 - PHP v7.2.0 - MySQL v5.6.38 - msmtp v1.6.1 - Web Interface v2.11 - KSWEBFTP v1.0 - Editor v1.0 - Scheduler HOW TO RUN WORDPRESS ON YOUR ANDROID DEVICE Running wordpress on Window,Mac,and Linux is easy. because there is a lot of knowledge base and software available to do so. That is not mean Android has no scope . Because Android also have bunch of application. but problem is that, it lacks knowledge base online so, commonly people unable to find it easily. Today in this post i am going to discuss 5 ways you can run and host your wordpress site for free. Way 1 : Run and Host your wordpress website using Android application KSWEB Follows these prerequisites steps to run and host your website on your Android phone: 1. Visit Google Play store and search for Android application KSWEB 2. Install the KSWEB Android application 3. Open and enable option that best suits your requirements. 4. Download file of open source CMS Wordpress from WordPress.org website. 5. Downloaded file is ZIP file that is why you have to extract it . 6. Move extracted file to htdocs file (created automatically when you run KSWEB locate it in file manager ) 7. Keep KSWEB Android application open 8. Go to the browser and paste this website address - http://127.0.0.1:8000/wp-admin Now , Understand in detail how to run it full fledged. Follow following Main steps to run and host your wordpress website using Android : 1. Navigate to Google Play store and install KSWEB application. KSWEB is premium application with 5 day free trial period. Later you can purchase premium if you like it. 2. Now open and enable your option Lighthttpd and Apache while Nginx is premium. 3. Enable FTP, MySQL, PHP option 4. Now go to tool tab and select for phpmyadmin and enable Apache as webserver. it will create database for your website. where data like post, pages,tables and Data are stored securely. Follow following steps to creat and deploy your database completely: 1. Go to tools tab and select phpmyadmin and webserver Apache . A popup created for choosing Web browser if you are using more than one . Note: sometime it sets by default thus it may not popup . So, check manually. 2. Select your web browser. 3. Then your database software phpmyadmin will open add user name as root and left password blank and Click on Go button.

Setup your database according to shown in the figure 4. Open Database option and rename your own database name . Click over creat button. 5. After that open user account and then add an user account.
Navigate to user account in navigation menu and add user account 6. Fill all credentials keeping host name to local. and tap on GO button.
Create username and grant all previlege 7. Now go to user account you created previously select your created database and tap on edit privilege option.
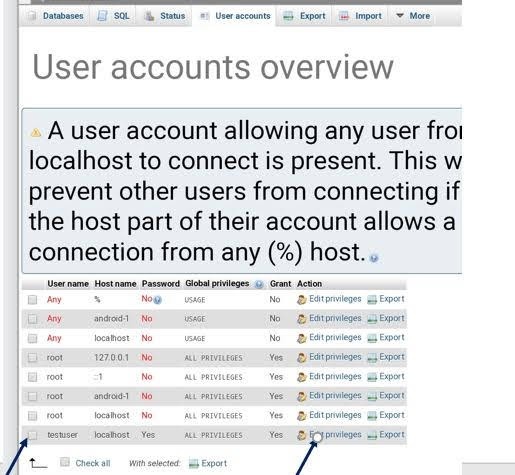
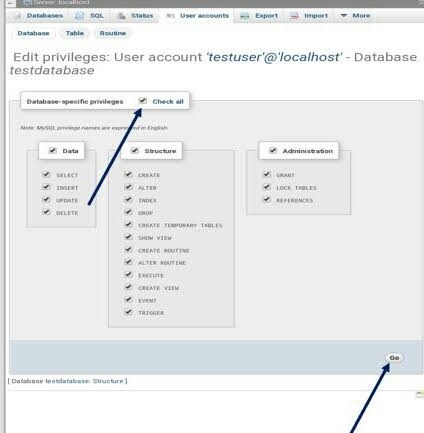
Tap on edit privilege option 8. Assign your newly created database and also assign newly created user and tap on GO button. 9. grant all permission you wish to have. tap on GO.
grant all permission to user account 5. Download wordpress ZIP file and extract (Unzip) it and move to htdocs folder. 6. Now your wordpress website ready for final setup . 7. Locate to web address : http://127.0.0.1:8000/wp-admin 8. Provide database credentials you setup in previous steps. 9. Tap on run installation button. 10. fill up your username and password created previously 11. Tap on login button you will get dashboard of wordpress Way 2 : USING WORDPRESS TRIAL SETUP ON QSANDBOAX For running a full website and to control over all things for free not an easy task. But I will teach you how to do it easily. Note: you are able to only test wordpress all premium features you cannot deploy upon custom domain. Follow these steps to run and host your wordpress website using Android: 1. Visit website called Qsandboax 2. Navigate to tools in navbar 3. Deploy what suits your choice. 4. Now to you will we able to acess wordpress dashboard . 5. But to acess file manager and database control Follows these steps 1. Install AndFTP (your FTP client) Android application 2. Install KSWEB Android application Now , fill up file manager record in AND FTP app you have now acess to full fledged wordpress file manager and files (like public.html) Do similar things with KSWEB you got acess to a database of sandbox test website. Way 3: Run and Host your wordpress website using Android application Bit Web Server It is fully premium application that is why I am discussed it in last but available at only $2 only so I strongly recommend to give a chance to it . All setting and deployment method almost similar to first one so I am not going to write more. Download Bit Web Server application HOW TO ACCESS MY CREATED WEBSITE FROM DESKTOP OR PC Connecting your device and PC through wifi and edit same ip address and port in both application and pc.
CONCLUSION
Android phone have downside that they get closed after some time of inactivity. To run your website consistently . Make sure if you are using first way to host wordpress then be aware and use following apps for constantly run server. There are many apps to stay it awake on Google Play. Please use StayAwake, KeepScreen or another one you find on Google Play. Read the full article
0 notes
Text
#podaevlus #aevlus #dnssec #first-ever #key #rollover #root
DNSSEC is a system of digital signatures that [1]prevent DNS spoofing. Using DNSSEC, it does not matter where your DNS answers came from, since the DNS resolver or application can verify the DNSSEC signatures to ensure the DNS data is not tampered with…
DNS is hierarchical, which means that the parent zone vouches for the cryptographic key used by its children via Delegation of Signing (DS) records. At the top of the hierarchy stands the DNSSEC Root Key. This key was first deployed on July 15, 2010, and it is scheduled to be replaced with a fresh new key on October 11, 2018 at 16:00 UTC.
What do you need to know?
If all goes well, end users and operators will notice absolutely nothing. The DNS community coordinated with the Internet Engineering Task Force (IETF), Internet Corporation for Assigned Names and Numbers (ICANN), DNS vendors, operating system vendors and DNS operators to ensure this change will be as uneventful as possible.
But there might be a few old forgotten and unmaintained servers, virtual machines, or containers that will run into issues if these servers had enabled DNSSEC more than a year ago and were not updated since that time.
How do DNS software and DNS services pick up the new key?
It already has! Properly working software should have already picked up this new key. To update the DNSSEC Root Key, a process defined in [2]RFC 5011 is used. It involves pre-publishing the new key signed by the current key and when you have seen this new key for more than 30 days, trust the new key as much as the current key.
You can see the procedure as implemented by ICANN in this PDF about their [3]Operational Implementation plan.
Red Hat has taken steps to pre-configure DNS software we ship with the new key. This means you would not need to wait 30 days before your machine trusts the new key. So, if you are using bind, unbound, knot, or dnsmasq - and your machine is up to date - you do not need to do anything. You donʼt even need to restart any DNS service.
Check if you have the new DNSSEC Root Key installed
The current DNSSEC Root Key (also called KSK-2010) has Key ID 19036. The new DNSSEC Root key (also called KSK-2017) has Key ID 20326. You can see if the configuration includes the new DNSSEC Root Key:
bind - see /etc/named.root.key unbound / libunbound - see /var/lib/unbound/root.key dnsmasq - see /usr/share/dnsmasq/trust-anchors.conf knot-resolver - see /etc/knot-resolver/root.keys
Note that this has been included for at least a year now, so you do not need to restart your DNS service unless your DNS server has been running for more than a year and does not support RFC 5011. The only known DNS software that matches these criteria is dnsmasq. ICANN has documented in great detail on how to [4]check your DNS resolverʼs current trust anchors.
Fallback plan in case of unexpected problems
Again, it is not expected that any DNS issues will happen. But if they do, it is recommend first to simply try restarting your DNS server. Then try to resolve something with DNSSEC, for example by using dig +dnssec dnskey . and if that works, you should be good, although you might want to keep monitoring the situation for a little while longer.
If you still see that DNS is not working properly you can temporarily switch to a public DNS operator. These DNS operators run DNSSEC-enabled public resolvers. You can switch to one of these services, or one of your preference, by configuring these public DNS services in /etc/resolv.conf. We don’t endorse any of these in particular, but they are well-known public DNS providers that support DNSSEC and may be useful if you need a working DNS service quickly.
1.1.1.1 2606:4700:4700::1111 Cloudflare 8.8.8.8 2001:4860:4860::8888 Google DNS 9.9.9.9 2620:fe::fe Quad9 64.6.64.6 2620:74:1b::1:1 Verisign
Note that if you block DNS queries to the internet, you might have to add a firewall rule so these queries can reach the public DNS servers. Ensure to add both UDP and TCP port 53, since TCP is needed to reliably receive larger DNSSEC replies.
Installations that might fail DNS after the rollover
The IETF and ICANN worked on measuring the (pre)adoption rate of the new Root Key. [5]RFC 8145 describes a method, implemented in common DNS software such as bind and unbound, that will report to the root zone which DNSSEC Root Keys are accepted whenever it needs to refresh root zone DNS data.
This shows that about 5% of DNS (recursive) query source IPs have been updated recently to include support for RFC 8145 while not having the new DNSSEC Root Key enabled. You can check if any of your IP addresses are in [6]this bad DNS servers IP list.
It is not known why this happens at all, as any software with RFC 8145 support also ships with the current and new DNSSEC Root Key. There are a few theories and it is worth thinking about whether any of your deployments might fall in this category.
Custom old configuration files with up to date software
If this is on a RHEL, CentOS, or Fedora machine, check for .rpmsave or .rpmnew files. If shipping VM images or containers with specific (year old) configuration files, update these container images as soon as possible.
If you have a named.conf configuration, with a trusted-keys{} statement you must do two things. First, replace trusted-keys{} with a managed-keys{}. This will enable RFC 5011 trust key rollover support for the future. But for this rollover you no longer have 30 days for the hold timer, so you must manually add the new DNSSEC Root Key to the managed-keys{} section and/or add the key to /etc/named.conf. You can check the .rpmnew file or grab an up to date /etc/named.conf from another system. Without manual intervention, these systems will start failing DNS on October 11.
Incomplete RFC 5011 process
Another theory is that there are containers or virtual machines with old configuration files and new software, and on launch these machines would only have the current (soon to be removed) DNSSEC Root Key. This is logged via RFC 8145 to the root nameservers which provides ICANN with the above statistics. Then the server updates the key via RFC 5011, but it is shut down before the 30 day hold timer has been reached. Or the hold timer is reached and the configuration file cannot be written to. Or the file could be written to, but the image is destroyed on shutdown/reboot and a restart of the container starts again from the old golden image that does not contain the new key.
If these machines have been up for 30 days on October 11 2018, they will trust the new key and DNS will keep working. But as soon as these machines are rebooted to the old golden image they will start failing because the bootstrap can no longer work, since the only DNSSEC Root Key these machines trusted will have been removed from the root zone on October 11, 2018.
Current information during the rollover event
To get the latest information published by ICANN, see their [7]Rollover Resources Page. That page will be updated during the event in case of unexpected issues.
References
Visible links
https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/7/html/security_guide/sec-securing_dns_traffic_with_dnssec https://tools.ietf.org/html/rfc5011 https://www.icann.org/en/system/files/files/2018-ksk-roll-operational-implementation-plan.pdf https://www.icann.org/dns-resolvers-checking-current-trust-anchors https://tools.ietf.org/html/rfc8145 http://root-trust-anchor-reports.research.icann.org/rfc8145-addresses.txt https://www.icann.org/resources/pages/ksk-rollover
original post
0 notes
Text
New Release – 26th APRIL 2020 – Major Performance Update; Shopify Integration: Temporarily disable sale order loading during sale spikes, product-level backorder setting, display buyer notes in DEAR; ShipStation Custom Store: Automatically add ShipStation shipping cost to DEAR Invoice; Production Module improvements and bug fixes; B2B: Change to Menu Item calculation; Continued UI improvements; Hubspot Integration Documentation.
ol, ul {list-style: circle; margin-left: 20px;}
Major Performance Update
DEAR is happy to announce a major system update, which was done to improve the server, core and memory performance, on Sunday the 26th of April 2020.
During this system update, DEAR was assigned a new IP address. We anticipate that some users (those using WooCommerce and Magento integrations) will experience some synchronisation errors until it is possible to update the whitelist with the new IP address (23.96.51.98).
Thank you and apologies for any inconvenience.
New Features
Feature 1: Shopify – Temporarily disable sale order and stock level updates to DEAR during sale spikes
Impact area: Shopify Integration.
Introduction:
During sale events, there can be a large spike of transactions created within a very short time period. This requires a large number of queries to sync all of the orders to DEAR. Shopify limitations on large numbers of queries can lead to delays in data loading and updates to related operations such as stock level updates, shipment updates, etc.
To handle these cases, DEAR has introduced a new automatic backend configuration which checks for sales spikes and temporarily disables sale capturing and stock level updates to DEAR when Shopify API capacity is close to being exceeded. The pending sales will be logged and then uploaded with a single API call at 5 minute intervals.
Pre-conditions: Active Shopify integration.
Functionality:
An automatic backend process will run every 5 minutes to check how many sales are being loaded to DEAR. When the sales rate indicates a spike, sale uploading to DEAR will be temporarily disabled and there will be no execution of API calls to update operations on DEAR end.
Sales created during the disabled period will be uploaded to the “Logs” table with the newly implemented status, “To be loaded” to process them later.
During the disable period, sales will be processed in DEAR at 5 minute intervals using a single API call rather than each sale being processed individually.
Manual loading of sales is not affected and the setting will automatically be returned to normal when the sales spike is over.
More information: Shopify Integration
Feature 2: Shopify – Enable/disable backordering for individual products
Impact area: Shopify Integration.
Introduction: Currently, DEAR Shopify integration has the option to globally enable/disable backordering of Shopify products with the setting “Allow user to purchase item, even if it is no longer in stock”. DEAR has now implemented the option to enable/disable backordering at the product level.
Pre-conditions:
Suppliers must be assigned to products to enable backordering of that product.
Active Shopify integration.
Introduction:
On the Catalog and Bulk Listing tab of the Shopify integration in DEAR, a new column “Allow backorder” has been added. Clicking on the product to open the product management window allows the user to enable/disable backordering for the individual product.
By default, the “Allow backorder” column will inherit the setting from the global setting “Allow user to purchase item, even if it is no longer in stock”. Enabling/disabling the product-level setting will override the global setting.
More information:
Backorders – Adding Suppliers for a product
Shopify Integration
Feature 3: Shopify – Capturing and displaying buyer notes on DEAR
Impact area: Shopify Integration.
Introduction:
In Shopify stores where buyer notes are enabled, buyers can add additional notes to the sale order. These notes are captured and added as a “Comment” or as “Shipping Notes” when the sale order is generated in DEAR.
These special buyer notes can be easily missed as they are not very obvious unless users go through the entire Sale order details. DEAR has implemented an improvement to capture these buyer notes as a special note within the sale order.
Pre-conditions:
Active Shopify integration.
Buyer Order notes on shopping cart should be enabled on the Shopify store – see Enable order notes on your cart page for more information
This feature is only applicable to Sale orders made through your Shopify store.
Functionality: When a buyer leaves a buyer note on a Shopify order, DEAR now shows an alert icon next to the sale order number on the DEAR sale screen. Hovering over the alert icon displays the buyer note in a tooltip.
More information:
Shopify Integration
Feature 4: Shipstation Custom Store – Automatically add ShipStation shipping cost to DEAR Invoice
Impact area: Shipstation Custom Store Integration.
Introduction: Currently, orders are exported from DEAR to Shipstation Custom Store for orders to be fulfilled, and then Shipstation returns the shipping details back to DEAR. This new update means that DEAR also obtains the shipping cost value and automatically creates an invoice entry under the “Additional Charges” section of the invoice tab.
Pre-conditions:
Active ShipStation Custom Store integration.
Go to Integration → ShipStation → Custom Store and set Import Shipping Costs to enabled.
Functionality:
DEAR now obtains the shipping cost value and automatically creates an invoice entry under the “Additional Charges” section of the invoice tab. This is only the case for invoices that have not yet been authorised.
When DEAR receives the shipping details and tracking number from ShipStation, the system will automatically set the Ship tab to authorised if it has not yet been authorised.
If a certain sale order is voided, the void status update notification will be automatically sent from DEAR to ShipStation so that ShipStation will not fulfill the order.
More information:
ShipStation Integration
Feature 5: Production Module improvements
Impact area: DEAR Production module.
Introduction: The Production module is aimed at addressing the needs of the production process. New production features will provide our current customers with powerful, logical manufacturing solutions to add to their inventory solution. Following on from our most recent releases, we are continuing to improve the Production module functionality and add features.
Pre-conditions: None.
Functionality:
This release’s new production features are:
Scheduler: “Urgent”, “Medium” and “Safe” text has been added to the coloured buffer filter labels.
Production Order: Notes and Attachments fields from the Production BOM now display in Production Run as well as Production Order.
Work Centres: Work Centres must be saved before the user can click through to “Deliver Components to” and connect a bin location.
Functionality:
Production Scheduler
Work Centres
Production Order
Production BOM
Feature 6: B2B Improvement – Change to Menu Item column calculation
Impact area: DEAR B2B.
Introduction: “Menu Item” column on B2B catalog tab previously listed items according to menu item ID. This led to duplicate items in the column if the portal had several menu items with the same name. This change means only distinct menu item names are shown, removing duplicate items from the list.
Pre-conditions: None.
Feature 7: Avalara – export of predefined “Tax Lookup” rule to Xero fixed
Impact area: Avalara Integration, Xero Integration.
Introduction:
Currently, DEAR has a special predefined “Tax Lookup” rule for users in the US and Canada with Avalara enabled. All sales and sales lines have this tax rule and the user cannot change it, tax rules are then calculated by Avalara API upon authorisation of the document.
This was causing errors when this tax rule was being exported to Xero before Avalara applied the calculation. We have issued a fix ensuring Avalara calculations take place first before then being exported to Xero.
Pre-conditions: This only affects users of both Avalara and Xero in the US and Canada.
Feature 8: User Interface Update
Impact area: User Interface.
Introduction: The ongoing UI updates have now been rolled out to Workflows (Automation module), VAT Return (UAE only) and multiple integrations (Square, Etsy, Shipstation, WooCommerce, Magento 2, Magento, Shopify, Vend, DEAR API and Quickbooks).
Pre-conditions: None.
Documentation: HubSpot Integration
The documentation for our new HubSpot Integration has been added to the DEAR Knowledge Base.
The post New Release – 26th APRIL 2020 – Major Performance Update; Shopify Integration: Temporarily disable sale order loading during sale spikes, product-level backorder setting, display buyer notes in DEAR; ShipStation Custom Store: Automatically add ShipStation shipping cost to DEAR Invoice; Production Module improvements and bug fixes; B2B: Change to Menu Item calculation; Continued UI improvements; Hubspot Integration Documentation. appeared first on DEAR Cloud Inventory Management.
This article originally appeared at https://ift.tt/3aCDK7O
0 notes
Text
IPS Community Suite 4.3.6
This is a maintenance release to fix reported issues.
Additional Information
Core - Members & Accounts
Added ability to use bulk mail subscription status as a filter for group promotions.
Fixed profanity filters applying to account usernames during registration.
Fixed following a member not updating the follow button correctly.
Fixed filters when creating a bulk mail or downloading a member list not working in certain combinations.
Fixed inability to manually set a member's reputation count less than 0.
Core - Search & Activity Streams:
Improved performance of indexing content when using Elasticsearch.
Improved the phrasing of the description on search results page when a custom date range has been chosen to sound more natural.
Fixed some Elasticsearch queries not working on very high traffic sites.
Fixed an issue where content that had been restored after being deleted would not be reindexed correctly.
Fixed an issue with Elasticsearch where content that had been hidden or moved would not be reindexed correctly.
Fixed filtering by specific members when using Elasticsearch.
Fixed various issues with activity streams not behaving correctly.
Core - Posting & Post Content:
Improved message when embedded content is not available to indicate if the content has been deleted or the user doesn't have permission to see it.
Fixed some Emojis rendering incorrectly.
Fixed broken TED Talks embeds.
Core - Clubs:
Fixed pagination of the list of members in a club not working.
Fixed some moderator permissions not applying correctly within clubs.
Fixed paid clubs being able to be created with $0 fee.
Fixed granting permission to create specific types of clubs via secondary groups not working properly.
Fixed content rebuild task not running on custom fields for clubs.
Core - Sitemap
Fixed some items not included in the sitemap.
Fixed error generating the sitemap when entering zero for the number of items to include.
Fixed sitemap not generating on some PHP versions.
Core - Redis:
Added ability to use Redis as a data storage method if is also being used as the caching method.
Fixed online users older than 30 minutes showing when using Redis.
Fixed uncaught exception that may occur when using Redis and clearing caches.
Core - Misc
Added a warning to the AdminCP dashboard, and when editing the login handler, if Facebook login is enabled but site is not using https. Also changed the Facebook login setup process to not allow new setups if site is not using https.
Added an option to use a different Facebook application for social promotion (opposed to the Facebook application used for login) so that Facebook login is not affected while your Facebook app is under review.
Added logging any time the support tool has been run.
Improved session handling performance.
Improved performance of viewupdates task.
Improved performance of queue task.
Fixed announcements being shown before the start date.
Fixed error when deleting the node being viewed in AdminCP node trees.
Fixed copying some node settings in the AdminCP not working.
Fixed replacement tags not working in bulk mails within URLs.
Fixed lost image style attributes in bulk emails.
Fixed Acronym Expansion page in AdminCP not line breaking correctly for very long values, breaking the page layout.
Fixed profile field management checking wrong AdminCP restriction.
Fixed CSS and JavaScript files not being deleted when recompiled on upgrade or when running the support tool.
Fixed false warnings from the database checker when using MySQL 8 and in certain other edge cases.
Fixed error after changing cache or datastore settings in certain PHP configurations.
Fixed link to the setting for allowed characters in usernames (which shows when setting up certain login handlers) not highlighting the setting.
Fixed possible error when creating the default English language when running the support tool.
Fixed AdminCP dashboard warning about failed tasks showing for disabled tasks.
Fixed browsers potentially keeping a cache of outdated JavaScript files.
Fixed JSON-LD data for ratings in several apps.
Fixed some widgets not limiting results correctly which could cause performance issues.
Fixed a possible technical error message (rather than a graceful error screen) showing if a very low-level error (such as database server offline) occurs in certain circumstances.
Fixed a missing warning when the hooks.php file was not writable before application and plugin installations and upgrades.
Fixed an issue when using profile complete and forum specific themes.
Fixed uncaught exception if manually going to a specific URL to try to promote something which cannot be promoted.
Fixed an unnecessary redirect in the applications upgrade process.
Fixed some minor language string inconsistencies.
Removed logging of notices that a template was requested to be rebuilt while already rebuilding.
Check to ensure that https is used before allowing Facebook to be used as a log in handler.
Fixes a read/write separation issue with unhiding
Forums
Fixed moderator permissions for posts.
Fixed an issue where moving archived topics from one forum to another did not update the forum counters.
Fixed an issue where posting a hidden post causes the forum to indicate a post pending approval is present.
Commerce
Added an option when refunding a transaction which was paid by a PayPal Billing Agreement to also cancel the Billing Agreement.
Added support for AUD, CZK, DKK, HKD, ILS, MXN, NZD, NOK, PHP, PLN, RUB, SGD, SEK, SEK, CHF, and THB for PayPal card payments.
Fixed automatic recurring payments for subscriptions not re-subscribing members correctly.
Fixed subscription upgrades/downgrades not being available at all to plans which are set to only be payable by particular gateways, or whose base price is modified by the chosen renewal term.
Fixed missing language strings in member history when upgrading subscriptions.
Fixed missing tax on purchase reactivation.
Fixed not being able to remove product discounts.
Fixed incoming emails being saved as blank replies.
Fixed incoming emails from certain email address formats, including emails using new domain extensions.
Fixed the link to print an invoice that gets sent in the email not working for guests.
Fixed missing language strings in the email advising a user their support request will automatically be marked resolved.
Fixed invalid referral banner image URL shown to users.
Fixed broken referrer tab in AdminCP customer profile.
Fixed broken images when viewing a purchase of an advertisement in the AdminCP.
Fixed advertisement purchases created by generating an invoice in the AdminCP.
Fixed possible text overflow when viewing shipping order in AdminCP.
Fixed support requests not showing assigned staff member in preview.
Pages
Fixed the page BBCode and editor button which allows content to be split over multiple pages.
Fixed incorrect sorting of number database fields.
Fixed search permissions when changing the "User can see records posted by other users" setting for a database.
Fixed an error occurring when editing a comment that is synced with a topic that has been hidden.
Fixed numeric database fields which use more than 2 decimal places in the value.
Fixed an issue where using a custom field validator with a unique field would mean the unique check is skipped.
Gallery
Fixed broken redirect after deleting an album and moving images in it to a category.
Fixed broken promote form for images within an album.
Fixed missing watermark when a file was inserted via the "Insert other media" feature.
Downloads
Fixed screenshots that have been imported from a URL missing from embeds.
Blog
Fixed blog cover photo being used when sharing entries on social media even when the entry has its own feature photo.
Fixed broken Blog Embeds.
Fixed link to the last Blog Entry inside the Blog Embed.
Calendar
Fixed cover photo offset not copying correctly when copying events.
Fixed venue not saving from ical upload.
REST & OAuth
Fixed OAuth setups refreshing refresh tokens more often than they should.
Fixed OAuth setups not properly supporting implicit grants.
Converters
Added support for redirecting direct post links for Vanilla.
Improved performance of conversions.
Improved description of minimum version for vBulletin 3 conversions.
Fixed error with login after conversion.
Fixed extraneous breaks in content converted from vBulletin.
Fixed personal conversations from Vanilla.
Fixed Gallery albums being converted with no default sort option.
Fixed issue with converting Calendar Event attachments.
Fixed issue where some code box content may be broken after conversion from phpBB.
Fixed vBulletin 3 redirects no longer working if you converted prior to upgrading to 4.x.
Upgrader
Added UConverter support to the UTF-8 Converter for sites with mixed character sets.
Fixed an issue where announcement widgets may not get removed when upgrading to 4.3.
Fixed possible SQL error when upgrading Calendar from 3.x.
Fixed how sharedmedia BBCode gets converted to embeds for Gallery albums when upgrading from 3.x.
Fixed an issue where converting to UTF-8 prior to upgrade can throw an error in some situations.
Fixed Gallery sitemap showing incorrect date for images upgraded from 3.x.
Third-Party / Developer / Designer Mode
Fixed album embeds when in developer mode.
Fixed errors adjusting sitemap configuration preferences when using developer mode
ips-v4.3.6-nulled.zip
source https://xenforoleaks.com/topic/302-ips-community-suite-436/
0 notes
Text
Preparing a new VMware Cloud Foundation Deployment
With the release of VMware Cloud Foundation (VCF) 3.0, major changes were made to the deployment and architecture of the platform and as a result, there are new pre-requisites that need to be met before bring up can occur.
1. Physical prerequisites
This is where the architecture changes come into play. VCF 3.0 includes a new Bring Your Own Network design methodology that is drastically different than the very prescribed networking in previous versions. This was from direct feedback from customers, and it shows that they’re listening and willing to make changes based on said feedback.
Racking and cabling of the hosts is still the same, but there are no longer any requirements around how the networking is cabled or configured as long as VLAN tagging is enabled and the ports are available. This opens up VCF to being supported on what would previously have been a non-VCF architecture. This provides a great deal of flexibility in switching vendors as well as throughput choices. The distinct downside to this is that you lose the switch configuration automation from the pre-3.x builds. This was a gift and a curse as it limited your switch and firmware options but also allowed large scale network changes to happen seamlessly and quickly.
2. Host Imaging
In VCF 2.x, the VIA appliance was used to image and configure the switches and hosts in a rack and the resulting configuration file was imported into SDDC Manager and the hosts would be available for use. While this seems great, during our 2.2 deployment we ran into a number of various issues with the process and it lead to a longer than expected time to get our deployment completed. With VCF 3.x, the VIA imaging process is available, but no longer required. Customers over the years have developed various ways to deploy their hosts and the VIA process was very different than their standard way. VCF 3.0 introduced the Cloud Builder VM, which performs the tasks previously performed during the first rack imaging process in 2.x. This can be deployed into your environment, but must be on the same network or VLAN as your new hosts vmk0 ports will be. We chose to forgo the VIA process and manually installed ESXi on all of the hosts as VIA does not support UEFI boot and we wanted to enable Secure Boot on our hosts. This is also a great opportunity to make sure your hosts are on the right firmware for VSAN compatibility.
Here are the new base set of prerequisites for a new host image:
The Management network and the base VM Network port group must be configured with the same VLAN
NTP and DNS must be configured the same way on ESXi as it is on the Cloud Builder VM
SSH and NTP must be enabled and set to “Start and stop with host”
The Management interface (vmk0) must have a static IP
The default standard switch (vSwitch0) must only have one vmnic assigned.
Seems pretty simple, right? I’ve created a script that can help with mass configuration. There’s also a template file to put your host names in.
3. External prerequisites
There was a lot of under the covers automation that VCF 2.x did that was eliminated in favor of a more flexible platform. One of the piece of automation was DNS registration. In VCF 2.x, the SDDC Manager ran its own DNS server that controlled a delegated subzone that lead to host names like r1n0.subdomain.domain.com. It eliminated trying to integrate with every DNS vendor in the world, but also meant you had no control over hostnames. VCF 3.x removes the automation, which means you’re free to name your vCenter, NSX Manager, vRealize Log Insight and ESXi hosts whatever you’d like....as long as you create the forward and reverse lookup entries in DNS for them. It’s one of those set it and forget it steps. DNS entries aren’t going to change often, so it’s not so bad to do it once.
You will also need some VLANs. Specifically:
Management
vMotion
VSAN
VXLAN
The last three preferably with jumbo frames enabled.
You’ll also need to collect the following license keys from MyVMware:
vCenter
ESXi
NSX
vRealize Log Insight
SDDC Manager
4. The Deployment Spreadsheet
You may be wondering why we’re collecting all of this information. VCF 2.x had quite the Word document of pieces of information, but it all had to be input by hand. Thanks to the flexibility of the naming schemes, passwords, DNS entries and IP addresses, there needed to be a better way to do the initial configuration. Enter the deployment spreadsheet.
In the spreadsheet there are a number of tabs:
The Prerequisite Checklist contains a much shorter version of what I’ve listed here.
The Management Workloads tab has a list of the products that will be deployed and it’s where you’ll put the license key information we collected earlier.
The Users and Groups tab is where you’ll set the passwords for a number of service accounts across the SDDC. Security protip: You should probably enter the passwords into a password safe of some sort and delete the passwords from this sheet when the deployment is completed.
The Hosts and Networks Tab is where you’ll set the network information for the management, vMotion, VSAN, and VXLAN networks, as well as input the IP addresses for the management hosts and the Cloud Builder VM.
The Deploy Parameters page is a bit of an eye chart, but it’s where you’ll input the IP information for the PSCs, management vCenter, management NSX Manager, Log Insight and SDDC Manager VMs. You’ll also put in some vCenter object names like the datacenter and cluster.
All of the tabs (especially the Deploy Parameters tab) have a bit of error checking. The Deploy Parameters tab does a bunch of error checking against the Hosts and Networks tab so that you’re not configuring 10.0.0.0/24 on the management network and trying to IP your new vCenter on 192.168.100.10.
Once you’ve filled out the Deployment Spreadsheet to the best of your abilities, you can login to the Cloud Builder VM and upload the file for validation. When you do this, the hosts should be imaged and online as the validation will attempt to login to the hosts and check the configuration based on what you’ve put into the spreadsheet.
A few notes:
The root password for the host *must* have lower case, upper case and special characters along with a number. It *must* be between 8 and 12 characters or the validation will complain. Yes, you can set an ESXi password longer than that. The validation expects the password to be between 8 and 12 characters.
vSAN capacity disks may show up as not eligible. This is due to a known issue with the validation. You can run the following where “Size: “ contains the size of your capacity disks. You can run “esxcli storage core device list” and look for your capacity disks to get the correct number to put into the command.
esxcli storage core device list | grep -B 3 -e "Size: 3662830" | grep ^naa > /tmp/capacitydisks; for i in `cat /tmp/capacitydisks`; do esxcli vsan storage tag add -d $i -t capacityFlash; vdq -q -d $i; done
This seems like a lot to do, but once you’re done, the standup of the environment should go very smoothly and you’ll be on your way to creating workload domains in no time.
0 notes
Text
Halo: The Master Chief Collection Get The Major Update
We all know that Halo: The Master Chief Collection had its “not so stable” history, and a year ago, it seems that 343 Industries just had enough for fixing and updating this game. But, believe it or not, 343 has announced that they will have their come back to the game for another journey. It has been in a lot of years of testing, and just today, the newest fresh patch is now available with a lot of new changes just like:
4k and HDR for all Xbox One X games, equipped with settings menu to customize the HDR resolution
Optimization for Matchmaking
New and reworked playlists for game flexibility, play the game type you want in a game you want. There will be 14 playlists, but only one for each game is available until enough people have downloaded the game for moderation purposes.
Offline LAN play
Intelligent Delivery
Better language options
Faster loading
This update patch will come in at around 73 GB, so make sure you have a large HDD before downloading as this will eat up most of your empty space. Because the game’s population have grown enough which can be credited to Xbox Game pass, we can look forward to new playlists being added soon as we have mentioned earlier that the playlists will be temporarily limited and moderated. These are some of the playlists that we can look forward to:
Social Playlists
Team Slayer (H1 – H4 Team Slayer)*
Action Sack*
Crossplay BTB (H1 / H2C & H2A / H4)*
Halo: CE Team Arena
Halo 3 BTB
Ranked Playlists
Halo: CE Team Doubles
Halo 2 Team Arena
Halo 2 Team Hardcore
Halo 2: Anniversary Team Arena
Halo 3 Team Doubles
In terms of its new offline LAN feature, here is the guide provided by 343. “In order to setup offline LAN play on MCC, a DHCP enabled hub will be required – these hubs allow IP addresses to be assigned to connected consoles. Alternatively, you can also manually configure the IP addresses for each Xbox via the System Settings for each console on the network. Either way, each Xbox needs to have a unique identity with a network configuration that allows it to route packets.”
For latest tech news and updates follow TechnoCodex on Facebook, Twitter, Google+. Also, if you like our efforts, consider sharing this story with your friends, this will encourage us to bring more exciting updates for you.
from TechnoCodex https://ift.tt/2PLDGth
0 notes
Text
Playing detective: how to identify bad backlinks
I completed a backlink audit recently, and this is the post I wish I’d had when starting the tedious task of identifying the nasty links. Not all dodgy links are obvious, heck some are even near-impossible to find, especially when you have a spreadsheet containing thousands of them.
This is not a post about how to do a backlink audit from A-Z - that’s already been written about loads of times. Instead, I’m going to take you through how to identify patterns in your backlink data to quickly and accurately uncover spammy links.
I’ve written this post for the greater good of all SEOs, and yes, you’re welcome.
Wait - do I even need to do a backlink audit?
There has been some confusion since the last Penguin update as to whether or not SEOs even need to carry out backlink audits anymore. After all, Google has said that now they only devalue spam links as opposed to penalising the site receiving them, right?
Well, the short answer is: yes, you probably should continue to carry out backlink audits and update your disavow file. You can read more about this here and here.
Why can’t I just use an automated tool to find the bad links?
I know it’s tempting to get automated backlink tools such as Kerboo to do all the hard-lifting for you. Unfortunately, though, this isn’t a great idea.
In the backlink audit, I did recently, 93% of porn links were assigned a link risk of ‘neutral’ with a score of 500/1,000 (0 being the safest link and 1,000 being the riskiest). Links from the BBC also received a ‘neutral’ rating, with some getting a higher risk score than the porn links! Go figure.
Automated backlink tools can be super valuable; however, this is because of all the data they draw together into a single spreadsheet, as opposed to them being particularly accurate at rating the risk of links. To rely solely on their link risk metrics for your backlink audit is a quick ticket to trouble.
Is this guide relevant to my site?
This post is not a ‘one-size fits all’ strategy to a backlink audit, so please use your common sense. For example, below I recommend that root domains containing the word ‘loan’ are generally indicative of unscrupulous sites. However, if you’re doing a backlink audit for a financial services firm, then this generalisation is less likely to apply to you.
It’s up to you to think about the guidelines below in the context of the site you’re auditing and to adjust accordingly.
You will need
Before you start, you will need to have all your backlinks neatly assembled in a spreadsheet along with the following information:
URL (one example per linking root domain)
root domain
anchor text
citation flow (Majestic) or domain authority (Ahrefs or Moz)
trust flow (Majestic) or domain trust (Ahrefs or Moz)
backlinks
IP address
title
page language
link location
and anything else you can think of that could be useful
This article can bring you up to speed if you’re not sure how to assemble this data. Make sure to combine data from as many sources as possible, as different SEO tools will contain different information and you don’t want to miss anything! As I said earlier, I would also recommend Kerboo as one of your data sources, as it pulls a lot of the information you could want into one place.
How to spot the patterns
Fortunately for us, the bad guys almost always do their dirty work in bulk, which makes life easier for us good guys who inevitably have to clean up after them. It’s rare to find one dodgy directory submission or a single piece of spun content containing a paid link. This is a massive help – use it to your advantage!
Pivot Tables
I highly recommend creating a pivot table of your data so that you can see how many times an issue has occurred in your data set. This can help you to quickly spot patterns.
Above: spotting suspicious anchor text using a pivot table
For example, let’s say you’re doing a backlink audit for a clothing site. By pivoting for anchor text, you might be able to quickly spot that ‘buy cheap dresses’ appears several times. Given the commercial nature of this anchor text, it’s likely it could be spam. You could spot check some of these URLs to make sure, and if they’re consistently dodgy, you can reasonably assume the rest of the links with this anchor text are too.
Above: putting together a pivot table to spot anchor text frequencies (view large version of gif)
Word Clouds
Another thing I like to do is to dump my data into a word cloud generator. This is useful because it visualises the data (the bigger the word, the more times it appears in your dataset). It can help me to quickly catch something that looks like it shouldn’t be there.
Keeping on top of your data
Make sure you make a note as you work that explains why you’ve decided to disavow a set of links. It helps not just at the end when you’re reviewing your links, but will also be a big help when you come to spot patterns. It will also stop you from revisiting the same links multiple times and asking yourself ‘why did I decide these were bad links?’
Above: screenshot from my recent backlink audit with ‘action’ and ‘reason’ columns
Examples of common patterns to find bad backlinks
I’m now going to give you specific examples of bad links which you can use to find patterns in your data.
It’s not always a clear-cut answer as to whether a link is spam or not, however, the guidelines below should help guide you in the right direction.
When you’re unsure about a link, ask yourself: ‘if it wasn’t for SEO, would this link even exist?’
Words to look for in the root domain or URL
X-rated words in the URL
You’ll immediately want to disavow (unless of course, these are relevant to your site) any x-rated links. These usually contain one of the following terms in their URL:
porn
xxx
sex (also sexy can result in some shady sites)
escort
dirty
adult
and any more dodgy words you can think of that relate to orgies, orgasms and other obscenities
Be careful not to accidentally disavow URLs where ‘sex’ is in the middle of a word - such as sussexhotels.com or essex.ac.uk. This will require some manual spot checking.
Root domain contains references to directories & listings
Next, you want to look for any URLs that indicate manipulative SEO link-building tactics. Directories are an obvious example of this, and while not all directories are bad (here is a good article on how to tell the difference), generally those created purely for link-building purposes contain the following words in the root domain:
‘directory’ – especially ‘dir’ and ‘webdir’
‘links’ – especially ‘weblinks’, ‘hotlinks’ or ‘toplinks’
‘listings’
You might notice I’ve specifically said ‘root domain’ as opposed to ‘URL’ here. There is a reason for this: you might find lots of URLs in your dataset where ‘links’ is in the URL path. As a general rule, these are a lot less likely to be manipulative links. Compare http://www.lutterworthyouththeatreacademy.co.uk/links.html with www.speedylinks.uk. One of these is spam, and the other isn’t - can you spot the difference?
Root domain contains references to SEO
You’ll also find that if the root domain contains SEO or web-related terms, it’s likely it exists simply to serve the purpose of building links. Look out for the following words in the root domain:
‘domain’
‘search’
‘seo’
‘web’
Bear in mind that lots of sites have ‘search’ pages, so your best bet is to focus on the root domain for this to be an indication of anything suspect.
Content farms are another common feature of a poor backlink profile. Look for any domains that contain ‘article’.
Other dodgy root domains
The following keywords in the domain are usually indicative of dodgy link-building practices:
‘cash’
‘loan’
‘com’ (such as com-com-com.com – yes, really)
‘world’
‘ads’
Root domain contains consonant or number clusters
Another obvious sign is any root domains which simply do not make sense. You’ll likely have lots of domains linking to your site consisting of bundles of consonants and letters, such as ‘1073wkcr.com’ or ‘a0924111232.freebbs.tw’. Watch out for domains like these, as more often than not they are low quality.
You can easily find URLs like this by sorting your root domain column from A-Z. You will find that:
any domain starting with a number will appear at the top of your list.
scrolling to the bottom to letters x, y and z usually throws up lots of domains with consonant clusters that do not make sense.
The ccTLD is uncommon
Uncommon ccTLDs are usually indicative of dodgy sites. Any site worth its salt will try and obtain the .com, .net, .org, .edu or relevant country ccTLD for its domain name. The less common ccTLDs are an indication of a lower quality site and those examples I found in my most recent backlink audit which indicated spammy sites were:
.biz
.casino
.clothing
.ooo
.properties, etc
Looking at titles for further clues
When the domain name or URL isn’t particularly insightful, the page title is the next place to look. Look out for the same keywords listed above, as well as the following phrases:
‘most visited web pages’
‘reciprocal links’
‘link partner’
‘link exchange’
‘seo friendly’
Another clue is to find any site titles that are completed unrelated to the niche of your site. Titles that contain commercial terms are particularly suspect, such as
‘louis vuitton belts’
‘nike shoes’
As I mentioned before, bad backlinks often operate in bulk, and there’s nothing like a load of duplicate titles to lead you hot on the heels of a group of spammy URLs.
What can anchor text tell us?
Is it keyword-heavy?
A popular SEO tactic in the pre-Penguin days was to link to your site with keyword-heavy or commercial anchor text, such as ‘cheap red dresses’. Make sure to put together a pivot table of your anchor text so you can quickly scan for any recurring anchor text that looks suspiciously well-optimised and check out these links to see if they’re legit – they probably aren’t.
Does it make sense?
In addition, any anchor text that simply doesn’t make any sense or is completely unrelated to the site you’re auditing is highly likely to be low quality.
Is the language consistent with the rest of the page?
Finally, any anchor text that is in a different language to the rest of the content on the page is likely to be a paid link. You can use the ‘language’ column (provided by Ahrefs and Kerboo) to see what language the page is in, and you can compare this to the language of the anchor text of your links. Anywhere where there is a mismatch is likely to be suspicious.
Duplicate root IP address
Pivot your data to see if there are several with the same IP address. If there is a block of URLs that share the same IP address and one of these is spammy, it could be likely that the rest are too.
Make sure to do a manual spot check of the sites to make sure you’re not disavowing anything harmless. For example, sites hosted at blogspot.com and wordpress.com are commonly hosted at the same IP address, and many of these will be harmless.
Where on the page is the link located?
In many backlink reports, there’s a column which tells you where on the page the link is located. In Kerboo, this column is called ‘link section’, and it’s another nifty tool for us to use in our hunt for dodgy links. Filter this column for keywords contained in the footer and sidebar to see if there are any which look suspicious on opening the page.
Footer and sidebar links are prime locations for dodgy backlinks. Why? Because these are site-wide, they are often targeted for paid link placements as the recipient of the link can often benefit from the most link equity in this way.
In addition, if the link is providing no value to users on the site (for example, if it’s completely unrelated to the site content, which is likely if it’s a paid link) then the footer is a useful place to essentially ‘hide’ the link from users while still providing link equity to the recipient.
Where is the link pointing to?
In the ‘link to’ column, look out for links pointing to the ‘money pages’ on your site – these are any pages which are revenue-drivers or particularly important for other reasons, such as product pages or sign-up pages.
It’s natural in a backlink profile to have the majority of links pointing to your homepage; this is where most people will link to by default. It’s much harder to build links to pages deeper in a site, especially product pages, as it’s not particularly natural for people to link here.
By glancing an eye over links which point to money pages, it’s likely you could spot a few suspicious links which have been previously built to help boost the rankings of important pages on your site.
Taking things to the next level
All the tips I’ve shared with you so far have involved mining data that is easily accessible to you in your backlink spreadsheet – things such as root domain, URL, page title and anchor text.
To take your backlink audit up a level, it’s time to get savvy. This is where Screaming Frog comes in.
Using Custom Search to spot link directories
You know how earlier we mentioned that not all directories are bad? Well, an easy way to spot if a directory exists solely for link-building purposes is to see if the page contains phrases such as ‘submit link’, ‘link exchange’ or ‘add your site’.
These telltale phrases will not necessarily be in the URL or page title of your link, so this is why it’s necessary to take things up a step.
To find pages which contain these terms, you can run a crawl of your backlink URLs using the Screaming Frog Custom Search feature.
Above: using Screaming Frog ‘Custom Search’ to find web pages containing suspicious text
Once the crawl is finished, you can then download the URLs that contain the phrases above. These will most likely be some obvious link directories that you’ll want to disavow pretty sharpish.
Using Custom Search to spot spun content
The Screaming Frog custom search feature isn’t just useful for finding directory links. This is where you really need to put on your detective hat and to have a good think of any patterns you’ve noticed so far in your backlink audit.
When I did my audit recently, I noticed a recurring theme with some of the paid links. There were links to other sites with commercial anchor text that kept appearing alongside the link to the site I was auditing. This was a piece of spun content that had been copied and pasted across multiple sites and forums, and whoever had done the work was clearly being lazy, lumping a load of unrelated links together in one paragraph.
Apart from the fact the text made no sense whatsoever, the anchor text of these other links was extremely commercial: ‘cheap nike free run 2 for men’ and ‘chanel outlet UK’ where a recurring theme.
Above: example of spun content that appeared in my recent backlink audit
I’d tried to find a pattern in the URLs or titles of these pages, but it was a bit hit and miss. It was then that I realised I could do what I had done to find the directory links – Screaming Frog custom search.
I, therefore, carried out a Screaming Frog crawl that looked for recurring anchor text such as ‘cheap nike’ and ‘chanel outlet’ to identify any URLs that I hadn’t yet uncovered. It was extremely useful and allowed me to identify some URLs that up to that point I had been unable to identify from the data in my spreadsheet alone.
To wrap up
If you’ve made it this far, congratulations! I appreciate this post was a lot of writing, but I hope it’s really helped you to dig out any dodgy links that were lurking under the surface.
If there’s one thing to take away, it’s to look for any patterns or consistencies in the dodgy links that you find, and to then use these to dig out the less obvious links.
Do you have certain criteria that you find helpful when identifying bad backlinks? Comment below!
Playing detective: how to identify bad backlinks was originally posted by Video And Blog Marketing
0 notes
Text
Playing detective: how to identify bad backlinks
I completed a backlink audit recently, and this is the post I wish I’d had when starting the tedious task of identifying the nasty links. Not all dodgy links are obvious, heck some are even near-impossible to find, especially when you have a spreadsheet containing thousands of them.
This is not a post about how to do a backlink audit from A-Z - that’s already been written about loads of times. Instead, I’m going to take you through how to identify patterns in your backlink data to quickly and accurately uncover spammy links.
I’ve written this post for the greater good of all SEOs, and yes, you’re welcome.
Wait - do I even need to do a backlink audit?
There has been some confusion since the last Penguin update as to whether or not SEOs even need to carry out backlink audits anymore. After all, Google has said that now they only devalue spam links as opposed to penalising the site receiving them, right?
Well, the short answer is: yes, you probably should continue to carry out backlink audits and update your disavow file. You can read more about this here and here.
Why can’t I just use an automated tool to find the bad links?
I know it’s tempting to get automated backlink tools such as Kerboo to do all the hard-lifting for you. Unfortunately, though, this isn’t a great idea.
In the backlink audit, I did recently, 93% of porn links were assigned a link risk of ‘neutral’ with a score of 500/1,000 (0 being the safest link and 1,000 being the riskiest). Links from the BBC also received a ‘neutral’ rating, with some getting a higher risk score than the porn links! Go figure.
Automated backlink tools can be super valuable; however, this is because of all the data they draw together into a single spreadsheet, as opposed to them being particularly accurate at rating the risk of links. To rely solely on their link risk metrics for your backlink audit is a quick ticket to trouble.
Is this guide relevant to my site?
This post is not a ‘one-size fits all’ strategy to a backlink audit, so please use your common sense. For example, below I recommend that root domains containing the word ‘loan’ are generally indicative of unscrupulous sites. However, if you’re doing a backlink audit for a financial services firm, then this generalisation is less likely to apply to you.
It’s up to you to think about the guidelines below in the context of the site you’re auditing and to adjust accordingly.
You will need
Before you start, you will need to have all your backlinks neatly assembled in a spreadsheet along with the following information:
URL (one example per linking root domain)
root domain
anchor text
citation flow (Majestic) or domain authority (Ahrefs or Moz)
trust flow (Majestic) or domain trust (Ahrefs or Moz)
backlinks
IP address
title
page language
link location
and anything else you can think of that could be useful
This article can bring you up to speed if you’re not sure how to assemble this data. Make sure to combine data from as many sources as possible, as different SEO tools will contain different information and you don’t want to miss anything! As I said earlier, I would also recommend Kerboo as one of your data sources, as it pulls a lot of the information you could want into one place.
How to spot the patterns
Fortunately for us, the bad guys almost always do their dirty work in bulk, which makes life easier for us good guys who inevitably have to clean up after them. It’s rare to find one dodgy directory submission or a single piece of spun content containing a paid link. This is a massive help – use it to your advantage!
Pivot Tables
I highly recommend creating a pivot table of your data so that you can see how many times an issue has occurred in your data set. This can help you to quickly spot patterns.
Above: spotting suspicious anchor text using a pivot table
For example, let’s say you’re doing a backlink audit for a clothing site. By pivoting for anchor text, you might be able to quickly spot that ‘buy cheap dresses’ appears several times. Given the commercial nature of this anchor text, it’s likely it could be spam. You could spot check some of these URLs to make sure, and if they’re consistently dodgy, you can reasonably assume the rest of the links with this anchor text are too.
Above: putting together a pivot table to spot anchor text frequencies (view large version of gif)
Word Clouds
Another thing I like to do is to dump my data into a word cloud generator. This is useful because it visualises the data (the bigger the word, the more times it appears in your dataset). It can help me to quickly catch something that looks like it shouldn’t be there.
Keeping on top of your data
Make sure you make a note as you work that explains why you’ve decided to disavow a set of links. It helps not just at the end when you’re reviewing your links, but will also be a big help when you come to spot patterns. It will also stop you from revisiting the same links multiple times and asking yourself ‘why did I decide these were bad links?’
Above: screenshot from my recent backlink audit with ‘action’ and ‘reason’ columns
Examples of common patterns to find bad backlinks
I’m now going to give you specific examples of bad links which you can use to find patterns in your data.
It’s not always a clear-cut answer as to whether a link is spam or not, however, the guidelines below should help guide you in the right direction.
When you’re unsure about a link, ask yourself: ‘if it wasn’t for SEO, would this link even exist?’
Words to look for in the root domain or URL
X-rated words in the URL
You’ll immediately want to disavow (unless of course, these are relevant to your site) any x-rated links. These usually contain one of the following terms in their URL:
porn
xxx
sex (also sexy can result in some shady sites)
escort
dirty
adult
and any more dodgy words you can think of that relate to orgies, orgasms and other obscenities
Be careful not to accidentally disavow URLs where ‘sex’ is in the middle of a word - such as sussexhotels.com or essex.ac.uk. This will require some manual spot checking.
Root domain contains references to directories & listings
Next, you want to look for any URLs that indicate manipulative SEO link-building tactics. Directories are an obvious example of this, and while not all directories are bad (here is a good article on how to tell the difference), generally those created purely for link-building purposes contain the following words in the root domain:
‘directory’ – especially ‘dir’ and ‘webdir’
‘links’ – especially ‘weblinks’, ‘hotlinks’ or ‘toplinks’
‘listings’
You might notice I’ve specifically said ‘root domain’ as opposed to ‘URL’ here. There is a reason for this: you might find lots of URLs in your dataset where ‘links’ is in the URL path. As a general rule, these are a lot less likely to be manipulative links. Compare http://www.lutterworthyouththeatreacademy.co.uk/links.html with www.speedylinks.uk. One of these is spam, and the other isn’t - can you spot the difference?
Root domain contains references to SEO
You’ll also find that if the root domain contains SEO or web-related terms, it’s likely it exists simply to serve the purpose of building links. Look out for the following words in the root domain:
‘domain’
‘search’
‘seo’
‘web’
Bear in mind that lots of sites have ‘search’ pages, so your best bet is to focus on the root domain for this to be an indication of anything suspect.
Content farms are another common feature of a poor backlink profile. Look for any domains that contain ‘article’.
Other dodgy root domains
The following keywords in the domain are usually indicative of dodgy link-building practices:
‘cash’
‘loan’
‘com’ (such as com-com-com.com – yes, really)
‘world’
‘ads’
Root domain contains consonant or number clusters
Another obvious sign is any root domains which simply do not make sense. You’ll likely have lots of domains linking to your site consisting of bundles of consonants and letters, such as ‘1073wkcr.com’ or ‘a0924111232.freebbs.tw’. Watch out for domains like these, as more often than not they are low quality.
You can easily find URLs like this by sorting your root domain column from A-Z. You will find that:
any domain starting with a number will appear at the top of your list.
scrolling to the bottom to letters x, y and z usually throws up lots of domains with consonant clusters that do not make sense.
The ccTLD is uncommon
Uncommon ccTLDs are usually indicative of dodgy sites. Any site worth its salt will try and obtain the .com, .net, .org, .edu or relevant country ccTLD for its domain name. The less common ccTLDs are an indication of a lower quality site and those examples I found in my most recent backlink audit which indicated spammy sites were:
.biz
.casino
.clothing
.ooo
.properties, etc
Looking at titles for further clues
When the domain name or URL isn’t particularly insightful, the page title is the next place to look. Look out for the same keywords listed above, as well as the following phrases:
‘most visited web pages’
‘reciprocal links’
‘link partner’
‘link exchange’
‘seo friendly’
Another clue is to find any site titles that are completed unrelated to the niche of your site. Titles that contain commercial terms are particularly suspect, such as
‘louis vuitton belts’
‘nike shoes’
As I mentioned before, bad backlinks often operate in bulk, and there’s nothing like a load of duplicate titles to lead you hot on the heels of a group of spammy URLs.
What can anchor text tell us?
Is it keyword-heavy?
A popular SEO tactic in the pre-Penguin days was to link to your site with keyword-heavy or commercial anchor text, such as ‘cheap red dresses’. Make sure to put together a pivot table of your anchor text so you can quickly scan for any recurring anchor text that looks suspiciously well-optimised and check out these links to see if they’re legit – they probably aren’t.
Does it make sense?
In addition, any anchor text that simply doesn’t make any sense or is completely unrelated to the site you’re auditing is highly likely to be low quality.
Is the language consistent with the rest of the page?
Finally, any anchor text that is in a different language to the rest of the content on the page is likely to be a paid link. You can use the ‘language’ column (provided by Ahrefs and Kerboo) to see what language the page is in, and you can compare this to the language of the anchor text of your links. Anywhere where there is a mismatch is likely to be suspicious.
Duplicate root IP address
Pivot your data to see if there are several with the same IP address. If there is a block of URLs that share the same IP address and one of these is spammy, it could be likely that the rest are too.
Make sure to do a manual spot check of the sites to make sure you’re not disavowing anything harmless. For example, sites hosted at blogspot.com and wordpress.com are commonly hosted at the same IP address, and many of these will be harmless.
Where on the page is the link located?
In many backlink reports, there’s a column which tells you where on the page the link is located. In Kerboo, this column is called ‘link section’, and it’s another nifty tool for us to use in our hunt for dodgy links. Filter this column for keywords contained in the footer and sidebar to see if there are any which look suspicious on opening the page.
Footer and sidebar links are prime locations for dodgy backlinks. Why? Because these are site-wide, they are often targeted for paid link placements as the recipient of the link can often benefit from the most link equity in this way.
In addition, if the link is providing no value to users on the site (for example, if it’s completely unrelated to the site content, which is likely if it’s a paid link) then the footer is a useful place to essentially ‘hide’ the link from users while still providing link equity to the recipient.
Where is the link pointing to?
In the ‘link to’ column, look out for links pointing to the ‘money pages’ on your site – these are any pages which are revenue-drivers or particularly important for other reasons, such as product pages or sign-up pages.
It’s natural in a backlink profile to have the majority of links pointing to your homepage; this is where most people will link to by default. It’s much harder to build links to pages deeper in a site, especially product pages, as it’s not particularly natural for people to link here.
By glancing an eye over links which point to money pages, it’s likely you could spot a few suspicious links which have been previously built to help boost the rankings of important pages on your site.
Taking things to the next level
All the tips I’ve shared with you so far have involved mining data that is easily accessible to you in your backlink spreadsheet – things such as root domain, URL, page title and anchor text.
To take your backlink audit up a level, it’s time to get savvy. This is where Screaming Frog comes in.
Using Custom Search to spot link directories
You know how earlier we mentioned that not all directories are bad? Well, an easy way to spot if a directory exists solely for link-building purposes is to see if the page contains phrases such as ‘submit link’, ‘link exchange’ or ‘add your site’.
These telltale phrases will not necessarily be in the URL or page title of your link, so this is why it’s necessary to take things up a step.
To find pages which contain these terms, you can run a crawl of your backlink URLs using the Screaming Frog Custom Search feature.
Above: using Screaming Frog ‘Custom Search’ to find web pages containing suspicious text
Once the crawl is finished, you can then download the URLs that contain the phrases above. These will most likely be some obvious link directories that you’ll want to disavow pretty sharpish.
Using Custom Search to spot spun content
The Screaming Frog custom search feature isn’t just useful for finding directory links. This is where you really need to put on your detective hat and to have a good think of any patterns you’ve noticed so far in your backlink audit.
When I did my audit recently, I noticed a recurring theme with some of the paid links. There were links to other sites with commercial anchor text that kept appearing alongside the link to the site I was auditing. This was a piece of spun content that had been copied and pasted across multiple sites and forums, and whoever had done the work was clearly being lazy, lumping a load of unrelated links together in one paragraph.
Apart from the fact the text made no sense whatsoever, the anchor text of these other links was extremely commercial: ‘cheap nike free run 2 for men’ and ‘chanel outlet UK’ where a recurring theme.
Above: example of spun content that appeared in my recent backlink audit
I’d tried to find a pattern in the URLs or titles of these pages, but it was a bit hit and miss. It was then that I realised I could do what I had done to find the directory links – Screaming Frog custom search.
I, therefore, carried out a Screaming Frog crawl that looked for recurring anchor text such as ‘cheap nike’ and ‘chanel outlet’ to identify any URLs that I hadn’t yet uncovered. It was extremely useful and allowed me to identify some URLs that up to that point I had been unable to identify from the data in my spreadsheet alone.
To wrap up
If you’ve made it this far, congratulations! I appreciate this post was a lot of writing, but I hope it’s really helped you to dig out any dodgy links that were lurking under the surface.
If there’s one thing to take away, it’s to look for any patterns or consistencies in the dodgy links that you find, and to then use these to dig out the less obvious links.
Do you have certain criteria that you find helpful when identifying bad backlinks? Comment below!
from Digital Marketing https://www.distilled.net/resources/playing-detective-how-to-identify-bad-backlinks/ via http://www.rssmix.com/
0 notes
Text
Playing detective: how to identify bad backlinks
I completed a backlink audit recently, and this is the post I wish I’d had when starting the tedious task of identifying the nasty links. Not all dodgy links are obvious, heck some are even near-impossible to find, especially when you have a spreadsheet containing thousands of them.
This is not a post about how to do a backlink audit from A-Z - that’s already been written about loads of times. Instead, I’m going to take you through how to identify patterns in your backlink data to quickly and accurately uncover spammy links.
I’ve written this post for the greater good of all SEOs, and yes, you’re welcome.
Wait - do I even need to do a backlink audit?
There has been some confusion since the last Penguin update as to whether or not SEOs even need to carry out backlink audits anymore. After all, Google has said that now they only devalue spam links as opposed to penalising the site receiving them, right?
Well, the short answer is: yes, you probably should continue to carry out backlink audits and update your disavow file. You can read more about this here and here.
Why can’t I just use an automated tool to find the bad links?
I know it’s tempting to get automated backlink tools such as Kerboo to do all the hard-lifting for you. Unfortunately, though, this isn’t a great idea.
In the backlink audit, I did recently, 93% of porn links were assigned a link risk of ‘neutral’ with a score of 500/1,000 (0 being the safest link and 1,000 being the riskiest). Links from the BBC also received a ‘neutral’ rating, with some getting a higher risk score than the porn links! Go figure.
Automated backlink tools can be super valuable; however, this is because of all the data they draw together into a single spreadsheet, as opposed to them being particularly accurate at rating the risk of links. To rely solely on their link risk metrics for your backlink audit is a quick ticket to trouble.
Is this guide relevant to my site?
This post is not a ‘one-size fits all’ strategy to a backlink audit, so please use your common sense. For example, below I recommend that root domains containing the word ‘loan’ are generally indicative of unscrupulous sites. However, if you’re doing a backlink audit for a financial services firm, then this generalisation is less likely to apply to you.
It’s up to you to think about the guidelines below in the context of the site you’re auditing and to adjust accordingly.
You will need
Before you start, you will need to have all your backlinks neatly assembled in a spreadsheet along with the following information:
URL (one example per linking root domain)
root domain
anchor text
citation flow (Majestic) or domain authority (Ahrefs or Moz)
trust flow (Majestic) or domain trust (Ahrefs or Moz)
backlinks
IP address
title
page language
link location
and anything else you can think of that could be useful
This article can bring you up to speed if you’re not sure how to assemble this data. Make sure to combine data from as many sources as possible, as different SEO tools will contain different information and you don’t want to miss anything! As I said earlier, I would also recommend Kerboo as one of your data sources, as it pulls a lot of the information you could want into one place.
How to spot the patterns
Fortunately for us, the bad guys almost always do their dirty work in bulk, which makes life easier for us good guys who inevitably have to clean up after them. It’s rare to find one dodgy directory submission or a single piece of spun content containing a paid link. This is a massive help – use it to your advantage!
Pivot Tables
I highly recommend creating a pivot table of your data so that you can see how many times an issue has occurred in your data set. This can help you to quickly spot patterns.
Above: spotting suspicious anchor text using a pivot table
For example, let’s say you’re doing a backlink audit for a clothing site. By pivoting for anchor text, you might be able to quickly spot that ‘buy cheap dresses’ appears several times. Given the commercial nature of this anchor text, it’s likely it could be spam. You could spot check some of these URLs to make sure, and if they’re consistently dodgy, you can reasonably assume the rest of the links with this anchor text are too.
Above: putting together a pivot table to spot anchor text frequencies (view large version of gif)
Word Clouds
Another thing I like to do is to dump my data into a word cloud generator. This is useful because it visualises the data (the bigger the word, the more times it appears in your dataset). It can help me to quickly catch something that looks like it shouldn’t be there.
Keeping on top of your data
Make sure you make a note as you work that explains why you’ve decided to disavow a set of links. It helps not just at the end when you’re reviewing your links, but will also be a big help when you come to spot patterns. It will also stop you from revisiting the same links multiple times and asking yourself ‘why did I decide these were bad links?’
Above: screenshot from my recent backlink audit with ‘action’ and ‘reason’ columns
Examples of common patterns to find bad backlinks
I’m now going to give you specific examples of bad links which you can use to find patterns in your data.
It’s not always a clear-cut answer as to whether a link is spam or not, however, the guidelines below should help guide you in the right direction.
When you’re unsure about a link, ask yourself: ‘if it wasn’t for SEO, would this link even exist?’
Words to look for in the root domain or URL
X-rated words in the URL
You’ll immediately want to disavow (unless of course, these are relevant to your site) any x-rated links. These usually contain one of the following terms in their URL:
porn
xxx
sex (also sexy can result in some shady sites)
escort
dirty
adult
and any more dodgy words you can think of that relate to orgies, orgasms and other obscenities
Be careful not to accidentally disavow URLs where ‘sex’ is in the middle of a word - such as sussexhotels.com or essex.ac.uk. This will require some manual spot checking.
Root domain contains references to directories & listings
Next, you want to look for any URLs that indicate manipulative SEO link-building tactics. Directories are an obvious example of this, and while not all directories are bad (here is a good article on how to tell the difference), generally those created purely for link-building purposes contain the following words in the root domain:
‘directory’ – especially ‘dir’ and ‘webdir’
‘links’ – especially ‘weblinks’, ‘hotlinks’ or ‘toplinks’
‘listings’
You might notice I’ve specifically said ‘root domain’ as opposed to ‘URL’ here. There is a reason for this: you might find lots of URLs in your dataset where ‘links’ is in the URL path. As a general rule, these are a lot less likely to be manipulative links. Compare http://www.lutterworthyouththeatreacademy.co.uk/links.html with www.speedylinks.uk. One of these is spam, and the other isn’t - can you spot the difference?
Root domain contains references to SEO
You’ll also find that if the root domain contains SEO or web-related terms, it’s likely it exists simply to serve the purpose of building links. Look out for the following words in the root domain:
‘domain’
‘search’
‘seo’
‘web’
Bear in mind that lots of sites have ‘search’ pages, so your best bet is to focus on the root domain for this to be an indication of anything suspect.
Content farms are another common feature of a poor backlink profile. Look for any domains that contain ‘article’.
Other dodgy root domains
The following keywords in the domain are usually indicative of dodgy link-building practices:
‘cash’
‘loan’
‘com’ (such as com-com-com.com – yes, really)
‘world’
‘ads’
Root domain contains consonant or number clusters
Another obvious sign is any root domains which simply do not make sense. You’ll likely have lots of domains linking to your site consisting of bundles of consonants and letters, such as ‘1073wkcr.com’ or ‘a0924111232.freebbs.tw’. Watch out for domains like these, as more often than not they are low quality.
You can easily find URLs like this by sorting your root domain column from A-Z. You will find that:
any domain starting with a number will appear at the top of your list.
scrolling to the bottom to letters x, y and z usually throws up lots of domains with consonant clusters that do not make sense.
The ccTLD is uncommon
Uncommon ccTLDs are usually indicative of dodgy sites. Any site worth its salt will try and obtain the .com, .net, .org, .edu or relevant country ccTLD for its domain name. The less common ccTLDs are an indication of a lower quality site and those examples I found in my most recent backlink audit which indicated spammy sites were:
.biz
.casino
.clothing
.ooo
.properties, etc
Looking at titles for further clues
When the domain name or URL isn’t particularly insightful, the page title is the next place to look. Look out for the same keywords listed above, as well as the following phrases:
‘most visited web pages’
‘reciprocal links’
‘link partner’
‘link exchange’
‘seo friendly’
Another clue is to find any site titles that are completed unrelated to the niche of your site. Titles that contain commercial terms are particularly suspect, such as
‘louis vuitton belts’
‘nike shoes’
As I mentioned before, bad backlinks often operate in bulk, and there’s nothing like a load of duplicate titles to lead you hot on the heels of a group of spammy URLs.
What can anchor text tell us?
Is it keyword-heavy?
A popular SEO tactic in the pre-Penguin days was to link to your site with keyword-heavy or commercial anchor text, such as ‘cheap red dresses’. Make sure to put together a pivot table of your anchor text so you can quickly scan for any recurring anchor text that looks suspiciously well-optimised and check out these links to see if they’re legit – they probably aren’t.
Does it make sense?
In addition, any anchor text that simply doesn’t make any sense or is completely unrelated to the site you’re auditing is highly likely to be low quality.
Is the language consistent with the rest of the page?
Finally, any anchor text that is in a different language to the rest of the content on the page is likely to be a paid link. You can use the ‘language’ column (provided by Ahrefs and Kerboo) to see what language the page is in, and you can compare this to the language of the anchor text of your links. Anywhere where there is a mismatch is likely to be suspicious.
Duplicate root IP address
Pivot your data to see if there are several with the same IP address. If there is a block of URLs that share the same IP address and one of these is spammy, it could be likely that the rest are too.
Make sure to do a manual spot check of the sites to make sure you’re not disavowing anything harmless. For example, sites hosted at blogspot.com and wordpress.com are commonly hosted at the same IP address, and many of these will be harmless.
Where on the page is the link located?
In many backlink reports, there’s a column which tells you where on the page the link is located. In Kerboo, this column is called ‘link section’, and it’s another nifty tool for us to use in our hunt for dodgy links. Filter this column for keywords contained in the footer and sidebar to see if there are any which look suspicious on opening the page.
Footer and sidebar links are prime locations for dodgy backlinks. Why? Because these are site-wide, they are often targeted for paid link placements as the recipient of the link can often benefit from the most link equity in this way.
In addition, if the link is providing no value to users on the site (for example, if it’s completely unrelated to the site content, which is likely if it’s a paid link) then the footer is a useful place to essentially ‘hide’ the link from users while still providing link equity to the recipient.
Where is the link pointing to?
In the ‘link to’ column, look out for links pointing to the ‘money pages’ on your site – these are any pages which are revenue-drivers or particularly important for other reasons, such as product pages or sign-up pages.
It’s natural in a backlink profile to have the majority of links pointing to your homepage; this is where most people will link to by default. It’s much harder to build links to pages deeper in a site, especially product pages, as it’s not particularly natural for people to link here.
By glancing an eye over links which point to money pages, it’s likely you could spot a few suspicious links which have been previously built to help boost the rankings of important pages on your site.
Taking things to the next level
All the tips I’ve shared with you so far have involved mining data that is easily accessible to you in your backlink spreadsheet – things such as root domain, URL, page title and anchor text.
To take your backlink audit up a level, it’s time to get savvy. This is where Screaming Frog comes in.
Using Custom Search to spot link directories
You know how earlier we mentioned that not all directories are bad? Well, an easy way to spot if a directory exists solely for link-building purposes is to see if the page contains phrases such as ‘submit link’, ‘link exchange’ or ‘add your site’.
These telltale phrases will not necessarily be in the URL or page title of your link, so this is why it’s necessary to take things up a step.
To find pages which contain these terms, you can run a crawl of your backlink URLs using the Screaming Frog Custom Search feature.
Above: using Screaming Frog ‘Custom Search’ to find web pages containing suspicious text
Once the crawl is finished, you can then download the URLs that contain the phrases above. These will most likely be some obvious link directories that you’ll want to disavow pretty sharpish.
Using Custom Search to spot spun content
The Screaming Frog custom search feature isn’t just useful for finding directory links. This is where you really need to put on your detective hat and to have a good think of any patterns you’ve noticed so far in your backlink audit.
When I did my audit recently, I noticed a recurring theme with some of the paid links. There were links to other sites with commercial anchor text that kept appearing alongside the link to the site I was auditing. This was a piece of spun content that had been copied and pasted across multiple sites and forums, and whoever had done the work was clearly being lazy, lumping a load of unrelated links together in one paragraph.
Apart from the fact the text made no sense whatsoever, the anchor text of these other links was extremely commercial: ‘cheap nike free run 2 for men’ and ‘chanel outlet UK’ where a recurring theme.
Above: example of spun content that appeared in my recent backlink audit
I’d tried to find a pattern in the URLs or titles of these pages, but it was a bit hit and miss. It was then that I realised I could do what I had done to find the directory links – Screaming Frog custom search.
I, therefore, carried out a Screaming Frog crawl that looked for recurring anchor text such as ‘cheap nike’ and ‘chanel outlet’ to identify any URLs that I hadn’t yet uncovered. It was extremely useful and allowed me to identify some URLs that up to that point I had been unable to identify from the data in my spreadsheet alone.
To wrap up
If you’ve made it this far, congratulations! I appreciate this post was a lot of writing, but I hope it’s really helped you to dig out any dodgy links that were lurking under the surface.
If there’s one thing to take away, it’s to look for any patterns or consistencies in the dodgy links that you find, and to then use these to dig out the less obvious links.
Do you have certain criteria that you find helpful when identifying bad backlinks? Comment below!
from Marketing https://www.distilled.net/resources/playing-detective-how-to-identify-bad-backlinks/ via http://www.rssmix.com/
0 notes