#backup and restore android apps and data
Explore tagged Tumblr posts
Photo

Ugh, that sinking feeling in your stomach. You’ve just dropped your phone, or maybe it’s gotten a little too friendly with a glass of water. And your Whatsapp chats? Gone. Poof. Vanished. Restoring WhatsApp data without a backup? You’re facing a digital disaster. This guide is exactly what you need if you landed here searching for “how to restore Whatsapp data without backup.” We’re going to tackle this tricky problem together and explore all possibilities – even if there may not be a flawless magic solution. Don’t panic; let’s carefully walk you through the steps, step-by-step, focusing on methods that often work for users in India and globally. In simpler words, we’re going to do our best to retrieve chat information when you didn’t make routine backups.
Understanding the Challenge of Whatsapp Recovery Without a Backup
Let’s get one thing clear: recovering WhatsApp data without a pre-existing backup is vastly more difficult than simply restoring from a local or Google Drive backup copy already saved. Backups are your first line of defense! Thinking about it now, I almost wish I had also told you, but then hindsight always has that clearer vision. Why backups make such a difference will later unfold completely. WhatsApp, as a platform, prioritizes user data privacy and security which often means methods of retrieving lost un-backed information without going through extensive, even unreliable technical work arounds might not exist yet or haven’t received much attention..
Factors Determining Success
The reality is a couple of influencing factors can impact successful WhatsApp restoration, meaning that all hope might not end yet; even without a backup! Here are primary important influencers determining recovery probability; when an individual tries to retrieve lost WhatsApp info. Keep them in mind as you are following future steps and trying to complete the main processes! The higher you stack the factors that assist you – all the better. A quick read through also would help for an informed first idea, before anything else.
Android vs. iOS: Data recovery significantly differs. Android’s filesystem is often more accessible than iOS’s tightly sealed environment.
Whatsapp Version: Newer WhatsApp versions may delete data promptly, reducing successful chances of rescue missions. When you’re following future tips and procedures keep this tip in mind, since the WhatsApp Version that might be applied matters.
Phone’s Internal Storage: If your phone’s internal storage heavily relies on efficient allocation, clearing off a chunk of storage space may improve your results
Also, keep in mind, many articles that focus only on some of these steps, only apply in some limited successful percent instances but often enough. This article aims to provide a full view that also acknowledges possible limitation and explains what and how several procedures must combine and work together synergistically so overall chances of success increase.
Exploring Potential Recovery Methods Without a Backup
Many times, people in India specifically find the easiest ways are always the ones that first come to mind; that does not always mean such “easiest” also equate to the quickest routes yet! So what should one realistically even do at the most fundamental levels to begin the mission?
Check for Recent, Possible “Hidden” Backups
This seems too general, but WhatsApp periodically keeps cache data, often locally on the phone’s internal storage, sometimes unnoticed to us unless we directly dive head on to check the phone and app directories on our phones internally. In India, where phone storage management isn’t always intuitive for every user, it’s easy to overlook that fact; that certain locations could already save potentially hidden Whatsapp Data remnants (like fragments of past information); enough may exist there that might rebuild some basic Whatsapp info pieces; not a fool proof method but its the first you check. Remember again that the method also depends on things like the exact current Whatsapp app version too!
1 Using Third-Party Data Recovery Software
Several providers produce third-party software focused exclusively on recovering phone and app information but note that very few promise guaranteed full-data rescue success, yet! Remember data loss, recovery solutions vary widely also, so there is never one-size-fits-all approach to even this “one approach or method “. So even with use of apps mentioned, no guarantees of anything happen yet but chances might slightly increase since your process of investigating increases as well.
Disclaimer: I am not endorsing any specific software. Thoroughly research a program before installing, only select products from reputable brands, and always read user reviews before purchasing. I’m not responsible for damage caused by improperly used data recove services, should they occur!
2 Exploring Android-Specific Options (if your phone is android):
You can use various data recovery applications for smartphones. We already alluded how these data specific phone apps sometimes increase the available avenues for rescue of some info. Note again though any such recovery solutions’ levels might still only produce fractional parts of the data, compared with a “full backup” option.
Accessing Internal Storage, Files: It is extremely risky as phone internal directory structures aren’t always straightforward to navigate especially without proper user knowledge. Incorrect methods might only exacerbate problems with your phone’s data management.
Checking for Recent Whatsapp Updates, Updates: This rarely will be your main source of the “main successful” options, since you most likely won’t find a complete recovery yet it may return fragments of existing pieces here and there! Not helpful in a lot of situations unless that piece was important in your use cases. Sometimes even these files also aren’t readily findable but some file explorer apps can navigate to the proper destinations much easier now, than 2 – three year old equivalents or earlier such apps available. These factors impact probability positively; the more apps of this type that your method utilizes improves success slightly; but no guarantees remain yet for full restored information!
Remember the critical timing. The quicker you try to remedy situations that would recover information (for apps based systems), the more higher the eventual recover probability or percentage!. The factors determining eventual restored information percentage chances relate to a number of details from your choice of the phone and Android type’s internal structures, internal files (the files used even to save WhatsApp info in your settings and location of phone). Also it may help the actual WhatsApp version as those versions sometimes dictate how files are arranged (and internally may change file sizes!).
Understanding Technical Limitations
This might feel overwhelming, already. That already means if it only started feeling this tough so early means realistically only having more options may solve this tough problems, though no single solution may guarantee immediate results always!
The Complexity of Mobile Operating Systems
Modern smartphones are exceedingly complicated systems: multiple operating systems, different versions across numerous apps even! Apple iOS and Google Android’s filesystems’ differences also already increase initial recovery difficulty alone. It matters a great deal; if you are using the actual Android brand or IOS brands. Each of these different versions, already change data pathways through software differences already. In Android’s case alone, fragmentation across versions means no single-method works reliably all cases!. Different methods, alone are almost guaranteed across a plethora of such methods, alone could improve any single attempt but realistically no guarantees!
Data Overwriting
Once storage space becomes over-written your lost phone apps/data is gone permanently from some locations!. The likelihood that overwriting did already occur depends not only your phone space; your other files, your app versions also are factors to consider when trying this! The earlier you have started to try and attempt rescue missions means the better for you. When space gets overwritten, a fully data recovery will decrease proportionally depending which version you have. That would likely matter to you significantly especially because only having those options matters at all. So even trying now is important; earlier always becomes immensely better yet than later!
Frequently Asked Questions (FAQs)
Q: Can I get this recover service free or from “government aid”.
A: No, most reliable data rescue services for loss information require payment for various reasons. The government in most situations also offers services of less guarantees and much restricted situations that have specific conditions needing it to be considered feasible. I’m making a generalization over India specific situations you might potentially run across.
Q: All my WhatsApp Business chats with vendor clients: Lost… will data recover ever bring important chats back?.
A: While this is always impossible without existing back-ups (unless someone develops new methods) attempting the suggested technical methods might restore something, it is never going likely to regain completely everything even using all the steps. The more chances you attempt higher those chances that something useful, may occur but it is always uncertain till after everything already.
Q: If many people online say they easily recovered important chat WhatsApp history lost files without any difficulties, are there secrets involved I yet don’t aware of?
A: Almost no reliable proven solutions are without many potential obstacles including those involving significant issues potentially that could worsen current issues unless all necessary things already arranged (sometimes without knowing which those even include!). Many claim extraordinary recovery abilities. But remember those are online testimonials alone often written and published by unknown individuals for varied reasons; these have varying reliability levels ranging across varied spectra alone. A highly trusted sources and well investigated, peer reviewed technical results alone have most credibility and only a reliable subset. Even a larger dataset including additional well collected info for additional verification is far higher quality of source when aiming a correct result in those cases.
Acting Quickly is Key; Time Matters
Do keep the critical factor in view: acting swiftly is vital! Repeatedly you hear people repeating one simple phrase all the time yet… the faster and earlier actions started the chance of some parts coming back significantly improve, the only reality to accept. Every single moment delayed already shrinks probabilities substantially: overwritten information will never exist fully anymore so any earlier successful efforts always matters critically. So you need that in line, every step carefully done especially given potential downsides!
Let’s get this clear! The faster and better, you attempt to utilize one approach the next or many similar ways those chances will improve chances incrementally especially together combined attempts often increases the recovered information! I did note very small differences matter, yet, do increase eventual success probabilities only, incrementally. Combining various attempts of methods makes the likelihood go higher yet. No specific guarantees provided but in general higher and significant improvement possibilities certainly do come out favorably from that method mentioned!
Now go help restore your lost chats! Let me hear from you below how it worked out. Share this post if you believe this helps! Share your experience – success or failures – so others might also greatly benefit as well from this process we tried, in their WhatsApp recoveries! What additional tips and advice has helped and/or what you now feel should not have failed! Did you use similar ideas already discussed? Share your feedback or additional ways also you managed so others can learn.
0 notes
Text

APK Installer by Uptodown - The Smart Tool for Installing APKs on Android Devices
What is APK Installer by Uptodown?
APK Installer by Uptodown is a free and efficient utility app designed to simplify the process of installing APK, XAPK, and split-APK files on your Android device. It allows users to install apps manually, bypassing the Google Play Store with ease. This app is perfect for those who prefer downloading apps from third-party sources or need to handle advanced file formats. With its intuitive design, app backups, and cross-device sharing feature, APK Installer by Uptodown ensures smooth APK installations every time.
Key Features of APK Installer by Uptodown
APK Installer by Uptodown comes with several useful features that make managing APK files a breeze. Whether you’re dealing with standard APKs or more complex XAPK files, this tool has you covered.
Automatic APK/XAPK Detection: APK Installer automatically detects APK, XAPK, and split-APK files on your device and installs them without any manual configuration.
Backup Creation: Create secure backups of your apps and their data to ensure you can restore them at any time.
Integrated File Browser: The built-in file manager makes it easy to find and install APK files from your device’s storage.
Cross-Device Sharing: APK Installer allows you to send APKs to nearby devices over the same network for easy sharing.
Support for Modern App Formats: It handles Android App Bundles and other advanced formats that are commonly used for distributing apps today.
How APK Installer by Uptodown Works
APK Installer by Uptodown works in a simple and user-friendly way. Here’s a step-by-step breakdown of the process:
Preparation: First, you need to enable “Install Unknown Apps” in your Android device’s settings to allow installations from external sources.
Downloading APK Installer: You can download the APK Installer from trusted sources, such as the Uptodown website.
Installing APKs: Once installed, open the APK Installer app. It will automatically detect any APK or XAPK files on your device and begin the installation process without requiring extra steps.
Download APK Installer by Uptodown
To get started, download APK Installer from the Uptodown website or a reliable source. Once downloaded, simply install the app on your device and enjoy easy APK management.
Why APK Installer by Uptodown Stands Out
APK Installer by Uptodown offers several standout features that make it an essential tool for managing APK files. Here's why it’s a great choice for Android users:
Effortless Installation: The app automatically detects APK and XAPK files, making the installation process completely hassle-free.
App Backup and Restore: You can back up both your apps and their data, ensuring that you can restore them later without any issues.
File Sharing: The app’s cross-device sharing feature allows you to send APK files across devices on the same local network.
Handling Advanced Formats: APK Installer supports all modern formats, including split-APKs and Android App Bundles, which are becoming more common.
Pros
Easy to Use: APK Installer features a clean and simple interface that makes it easy for users of all ages to navigate.
Backup & Restore: With the backup function, you can restore apps and their data with ease.
Cross-Device Sharing: Quickly share your APK files with other devices on the same network.
Cons
Basic Design: The app focuses more on functionality rather than flashy design, which may not appeal to users who value aesthetics.
Device Compatibility: While the app works on most Android devices, there may be occasional compatibility issues with older models.
What’s New in APK Installer by Uptodown?
The latest version of APK Installer by Uptodown introduces several key updates, improving its already impressive capabilities. Now, it supports Android App Bundles, which are used by many developers for modern apps. Additionally, APK Installer’s cross-device sharing feature has been enhanced, allowing you to transfer APK files even more efficiently. These updates ensure that APK Installer remains a powerful tool for handling the latest app distribution formats.
Differences Between APK Installer by Uptodown and Previous Versions
APK Installer by Uptodown has undergone significant improvements compared to its earlier versions. The most notable updates include better support for modern app formats like Android App Bundles, as well as a more user-friendly interface. Furthermore, the app now features enhanced backup options, allowing users to back up both apps and their associated data in a single step.
Is APK Installer by Uptodown Safe to Use?
APK Installer by Uptodown is completely safe, as long as it’s downloaded from trusted sources. It doesn’t require root access, and there’s no risk of malware or harmful software. The app is designed to work smoothly without interfering with your device’s security. However, it’s important to download APK files only from reputable sources to avoid potential security threats. APK Installer helps mitigate these risks by providing a simple, safe installation process for APKs.
Frequently Asked Questions (FAQs) about APK Installer by Uptodown
Q: Can I install APK files from external websites using APK Installer by Uptodown?
Yes, APK Installer allows you to install APK files from third-party sources, making it perfect for sideloading apps.
Q: Does APK Installer support the installation of XAPK files?
Absolutely! APK Installer fully supports XAPK and split-APK files, ensuring seamless installations of complex app packages.
Q: Can I back up my apps using APK Installer by Uptodown?
Yes, APK Installer includes a feature that allows you to back up apps and their data for easy restoration whenever needed.
Reviews of APK Installer by Uptodown
Users are consistently impressed with APK Installer by Uptodown for its simplicity and efficiency. The app makes installing APK files straightforward, especially for users who download apps from third-party websites. The backup and restore functionality is a major plus, ensuring that apps and data are never lost. APK Installer’s easy-to-use interface and support for modern app formats make it an invaluable tool for Android users.
Download APK Installer by Uptodown
If you’re looking for a reliable tool to manage your APK files, APK Installer by Uptodown is your best bet. Download it today from HEYAPKS for a safe, secure, and hassle-free installation experience. Whether you’re downloading apps from trusted sources or managing advanced app formats, APK Installer by Uptodown has everything you need to keep your Android device running smoothly. Don’t wait—download APK Installer by Uptodown now and enjoy a seamless app installation process!
0 notes
Text
Stardew Valley APK Download Guide: Safe Installation & Tips

Looking to download Stardew Valley APK for Android? This guide covers everything you need: safe download sources, step-by-step installation instructions, gameplay features, and tips to avoid malware risks**. We’ve analyzed top competitor articles to bring you the most comprehensive resource, including APK mods, troubleshooting, and how to enjoy the farming simulator without the Play Store. Whether you’re new to Pelican Town or a seasoned player, this guide ensures you get the best mobile experience. Let’s dive in! What is Stardew Valley APK? Stardew Valley, developed by ConcernedApe (Eric Barone), is a beloved farming simulation RPG. The official Android version is paid on Google Play, but the Stardew Valley APK lets users install the game for free. This file is ideal for devices without Play Store access or users seeking modded versions. However, downloading APKs carries risks—always verify sources like https://mystardewvalleyapk.com/ to avoid malware.
How to Safely Download Stardew Valley APK Avoid sketchy sites! Bookmark trusted sources like https://mystardewvalleyapk.com/ for malware-free downloads. Key checks before installing:
File size (official APK is ~500MB).
Upload date (updated after version 1.5.6.39 for bug fixes).
User reviews mentioning crashes or ads.
For mods, visit communities like Stardew Valley Nexus Mods (https://www.nexusmods.com/stardewvalley).
Step-by-Step Installation Guide
Enable “Install from Unknown Sources” in Android Settings.
Download the APK from https://mystardewvalleyapk.com/.
Open the file and follow prompts.
Launch the game and restore progress using Stardew Valley save files (backup first!).
Troubleshooting tip: If the app crashes, install OBB files from APKMirror (https://www.apkmirror.com) for missing data.
Why Stardew Valley APK Stands Out The mobile port, published by Chucklefish, retains all PC features:
Farming, mining, and romance with NPCs like Abigail or Sebastian.
Multiplayer support via local Wi-Fi.
Seasonal events (e.g., Winter Star Festival).
Modded APKs add perks like auto-fishing or custom farm layouts. For mod tutorials, visit Stardew Valley Modding Wiki (https://stardewvalleywiki.com/Modding).
Performance Tips for Low-End Devices
Lower resolution in settings.
Disable screen shake and zoom effects.
Use SD Maid (https://www.sdmaid.com) to clear cache regularly.
3 Risks to Avoid
Fake APKs with spyware.
Outdated versions lacking Ginger Island content.
Banned saves for using cheats online.
Always cross-check MD5 checksums on Stardew Valley Reddit (https://www.reddit.com/r/StardewValley).
Final Thoughts With this guide, you’re ready to explore Pelican Town on Android! Prioritize safety, experiment with mods, and optimize performance for the best experience.
#StardewValleyAPK#MobileGaming#APKDownload#StardewValleyMods#AndroidGames#stardew mods#stardew valley#stardew farmer#stardew ask blog
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Product Description Verilux 4 in 1 USB Pendrive - Allows You Share Data Between Various Devices Easily Multi-Interface Design: Verilux 4 in 1 USB pen drive cames with light-ning port/USB A/Type C/Micro USB, compatible for i-Phone/iPad/OTG Android/PC and other devices with standard USB ports, can transfer data between various devices, easily complete data sharing. 4 IN 1 You can mange photos/videos/files via special APP(NO APP is needed when use on Android or Windows PC/MAC/IMAC),which can greatly help you to organize/edit everything in sort,and original format are kept for easier searching: One-click to backup photos/videos Auto backup:Photos/Videos are took via APP camera and saved automatically into the folder.Plug and play: Play music and movies directly from the photo stick for iPhone Contact Backup and Restore Data privacy:Edit & Rename & Encryption the Folders with password or touch IDShare photos /files/videos among different devices (PC/Macbook/iPhone/iPad) [ NOTE: This 256GB pen drive is compatible with iOS 8 & above and Android system. To use the otg pendrive c type on i-Phone/iPad, you need to download ''Y DISK'' app from App Store; Android needs to turn on OTG function(No need to download APP). For i-Phone 16/15 series, no need to download the app. Multi-interface and excellent heat dissipation design ensure excellent performance and high transmission speed. You can transfer data between various devices and easily complete data sharing. ] Wide compatibility and supports More Devices Compatible with Desktop /Laptop/Android phones/i-Phone 16/15 series/Car Audio/Smart TVs and more. Compatible system: Win 7/8/10/11, MAC 10.6 and above. Note on the capacity of the USB flash drives Manufacturers of Flash (memory) or solid-state drive devices generally calculate in 1000 as the decimal, i.e. 1KB=1000Bytes, 1GB=1000M, and operating systems calculate capacity in 1024 as the binary, i.e. 1KB=1024Bytes, 1GB=1024M, and the reported capacity after formatting will be less than the nominal capacity. System files also take up a small amount of space under different operating systems. For example: Nominal capacity 128GB, actual capacity about 117GB; nominal capacity 256GB, actual capacity about 238GB. About the USB Flash Drive heating phenomenon It is normal for USB flash drives to get a little hot. When the USB flash drive is powered on, it will transfer data, causing the electronic components inside the drive to give off heat. The chip generates heat according to factors such as the length of power-on time, the frequency of read and write operations, and the speed of read and write. Because metal has good thermal conductivity and heat dissipation, heating of the metal USB flash drive is a normal phenomenon, which is not a quality problem. The USB flash drive chip can withstand a high temperature of 85°C and the USB flash drive will not be damaged by the heat.
Please rest assured use. About the read/write speed of USB flash drive The read and write speed of the USB flash drive is affected by many factors such as computer configuration, interface, file size, etc. The test environment data of Verilux product comes from the laboratory. If you use a device below the test environment configuration to transfer files, or copy more file documents or pictures, the actual transfer speed will be lower than the nominal speed in various degrees. The transfer speed of solid-state products such as solid-state USB flash drive/SSD is affected by Flash particles. Instructions for copying files over 4GB For better compatibility with the operating system, the default file system for USB flash drives is FAT32, with a maximum unit file size of 4GB. In order to be better compatible with the operating system, the default file system for USB flash drives is FAT32, and its maximum unit file size is 4GB. If you need to store individual files over 4GB, it is recommended that you reset the file system in the following way: 1. connecting the storage product to the computer; 2. right-clicking on the partition and selecting Format; 3. select exFAT format in the file system options; 4. Click Start to finish. NOTE: This 256GB pen drive is compatible with iOS 8 & above and Android system. To use the otg pendrive c type on iPhone/iPad, you need to download ''Y DISK'' app from App Store; Android needs to turn on OTG function(No need to download APP). For iPhone 16/15 series, no need to download the app. [Note: When using, do not hot-plug and unplug (it will lead to file corruption), please press Eject in the navigation bar before unplugging.] VERSATILE 256 GB 4-IN-1 FLASH DRIVE: This 4-in-1 256 GB pen drive features four connectors: Light-ning, Micro USB, USB A, and Type-C. Seamlessly transfer data between i-Phones, Android devices, tablets, and computers. 256GB otg pendrive multi-platform compatibility ensures you're always prepared for any data transfer needs, no matter which device you're using. RELIABLE DATA STORAGE AND BACKUP: With a generous 256 GB capacity, this pendrive is ideal for managing your data storage needs. 256 GB pendrive offers a dependable solution for backups, ensuring your important files, photos, and documents are secure. 256GB pendrive 3.0 Multi-interface and excellent heat dissipation design ensure excellent performance and high transmission speed.[ Note: The otg pendrive c type 256GB actual storage capacity is about 90% ] STYLISH AND DURABLE DESIGN: Crafted with a sleek, fashion-forward metallic triangle design, this 256GB c type pendrive and the protective cap shields the connectors, keeping them safe from dust and damage, while enhancing the device's overall longevity. Not only stands out aesthetically but is built to endure daily wear and tear. In addition this, otg pendrive c type 256GB comes with a convenient keychain attachment, you'll never have to worry about losing or misplacing your drive again. IDEAL FOR WORK AND TRAVEL: Whether you're transferring files at the office, backing up photos during your travels, or need instant data storage, this versatile 4-in-1 256 GB flash drive is your go-to companion. Pendrive 256 GB compact design makes it perfect for carrying on-the-go, ensuring you have your essential data available whenever you need it. [ad_2]
0 notes
Text
Are you aware of windows phone security issues? There are many serious security issues on windows phones. Use these windows mobile security apps to protect your phone and confidential information saved on your phone. These days, your communication devices, be it your laptop, computer or mobile are all susceptible to malware and unwanted access. It is highly recommended that you make sufficient arrangements to ensure that your device is safe and thus such threats can be minimized. Mobile phones these days, especially the Smart Phones are being used for more than normal day to day communication. They are a miniature version of your computer where you can store your files, movies, music and other important documents which are prone to intrusion. Besides, browsing the internet can invite malware which can affect your device and cause serious problems. There are many security apps available which would ensure that your Smart Phone remains secure and safe. In this article, I shall provide an insight to 10 best security apps for your SmartPhone. You may also like our roundup of android security apps and iPhone security apps. 10 Security Apps To Protect Your Smart Phone Here are the 10 security apps for your Smart Phone which are the best: Keeper This is a free security app for modern day users. Keeper is a password manager which allows auto filling of all the internet logins. Besides, it can also be used to synchronize multiple Windows devices and for cloud data backup. It can also be utilized to encrypt sensitive information. EWalletGo This incredible app is extremely effective when it comes to securing login information pertaining to your credit card and banking functions. It allows you to store your PINs, Credit Card numbers, and Login details. It can also be used for effective data backup. AVG Family Safety This is another free application which allows safe and secured browsing. This is a browser with “Parental Control” features inbuilt in it. It can block unwanted sites and those with malicious content. It allows the parents to monitor the internet activities of their children from any other Windows device. Best Phone Security This app is ideal if you want to monitor the login attempts made by anyone else other than you in your accounts. It also records the location of your phone. If you wish to secure your Smart Phone while you are away, this is one of the best applications. Lock & Hide This is a free yet very useful security application for your SmartPhone. With the help of this app, you can encrypt all the sensitive data stored in your Smart Phone. Besides, it also allows you to hide the files to prevent unauthorized access. Thus, Lock & Hide is one of the best apps to secure data stored in your Smart Phone. Snap Secure This application can be used to configure automatic online data backup. The data can be accessed, restored or transferred to any other device whenever required. It also comes with anti-spyware and anti-virus protection which adds more to its utilities. BullGuard Mobile Security 10 BullGuard is another security application that comes with an online account, which allows you to access your Smart Phone remotely. You will be able to lock your phone and erase all the data using this application if you ever lose your Smart Phone. IHound Phone And Family Tracking iHound comes with different types of tracking tools. This application can track the location of your device using the GPS system of your phone. This can also be used to lock your phone remotely and erase all the sensitive data stored in it. McAfee WaveSecure This McAfee mobile security app comes with different types of security tools. It comes with an anti-virus and anti-spyware tool and can be used to lock your phone remotely. Apart from this, you can easily backup and restore your data using this app. It also enables you to track the location of your phone. Kaspersky Mobile Security Kaspersky Mobile Security comes with an array of different types of
features which includes anti-virus, anti-theft, data encryption, privacy protection, anti-spam, firewall protection and parental controls. The tracking features allow you to track your phone on Google maps. These are the 10 best Security Apps for your SmartPhone. These apps offer a comprehensive, all-round security to your Smart Phones from virus, remote tracking, theft and unauthorized access. With the help of these apps, you can make sure that all your data are safe and are not accessible to the intruders. So, employ them for your safety and get benefitted. This article is a guest post written by Morna Collins on a behalf of FamousCouponCodes.com. Morna is a professional writer with extensive experience of over 5 years and in above article she describe best security apps for Windows Phones that how to secure your important data through these apps.
0 notes
Text
Secure Your Data with the Best Android Backup and Restore App – All Backup & Restore
Never worry about losing your files again! All Backup & Restore is the ultimate Android backup and restore app that ensures your data is protected. Backup contacts, messages, apps, and media seamlessly, and restore them anytime, anywhere. Trust All Backup & Restore for all your backup needs!

1 note
·
View note
Text
Improving Android Text Message Archiving: Top Tools and Strategies

Introduction:
In the contemporary digital landscape, smartphones serve as crucial repositories for cherished memories, important data, and essential business communications. Therefore, having efficient methods for text message archive android is vital for ensuring secure storage and easy access. This guide outlines effective tools and strategies to assist Android users in archiving their text messages, providing a dependable way to protect and recover important conversations.
Utilizing Built-In Archiving Features:
Android devices offer basic archiving options within their native messaging applications, which are adequate for users with moderate archiving needs. These built-in features allow users to archive messages directly within the app. However, those who need more comprehensive archiving solutions—such as managing large volumes of messages or simplifying retrieval—may find these native options insufficient. To fulfill these requirements, various third-party apps designed for Android text message archiving are available.
Popular Text Message Archiving Applications:
Highly rated apps like SMS Backup & Restore, SMS Backup+, and Phone Leash provide enhanced archiving capabilities. These tools allow users to back up their messages to email accounts or cloud services, thereby increasing the security and accessibility of their archived conversations.
Streamlining the Archiving Process:
To effectively archive Android text messages, it’s crucial to choose the right application. Once installed, users can tailor their archiving settings, select specific messages for backup, enable automatic backups, and determine the preferred storage location for their archives.
Emphasizing Security and Privacy:
When choosing a text message archiving app, prioritizing privacy and data security is key. It's advisable to select apps that have positive user reviews and transparent privacy policies to safeguard sensitive information.
Conclusion:
By implementing effective strategies and utilizing the appropriate tools, archiving Android text messages becomes a straightforward and advantageous task. A robust archiving system not only secures vital communications but also gives users peace of mind and easy access to their digital conversations.
For more information about Text message archive on android come and visit our website : https://www.telemessage.com/
0 notes
Photo

Let’s face it: Losing your WhatsApp chats is a nightmare. All those precious memories, important plans, and hilarious inside jokes – gone in a flash. That’s why knowing how to backup WhatsApp chat is absolutely crucial. This in-depth guide will walk you through every step, covering all the different ways to safeguard your WhatsApp conversations, no matter what kind of phone you have. We’ll explore backing up to Google Drive (for Android users), iCloud (for iPhone users), and even local backups to your phone’s storage. By the end, you’ll be a WhatsApp backup expert, confident that your chats are safe and sound. Let’s dive in!
Backing Up Your WhatsApp Chats: A Complete Guide
Losing your WhatsApp chats can be incredibly frustrating. It’s not just about the funny memes; it’s about losing important information, contact details, and cherished memories. This comprehensive guide will show you exactly how to prevent that heartbreak by regularly backing up your WhatsApp data. We’ll cover all the bases, ensuring you understand the process regardless of whether you’re using an Android or an iPhone. We’ll also explore the differences between different backup methods and help you choose the best option for your needs.
Backing Up WhatsApp on Android Using Google Drive
For Android users, the most common and convenient way to back up WhatsApp chats is using Google Drive. This method automatically saves your chats to your Google account, ensuring they’re accessible even if you lose or damage your phone.
Setting Up Your First Google Drive Backup
Check your Google Account: Make sure you’re logged into a Google account on your Android phone. This is essential for the backup process.
Open WhatsApp: Launch the WhatsApp app on your phone.
Access Settings: Tap the three vertical dots in the top right corner to open the menu, then select “Settings.”
Navigate to Chats: In the Settings menu, tap “Chats,” then “Chat backup.”
Choose Your Google Account: Select the Google account you want to use for your backups.
Customize Your Backup: You can choose to back up only your chats, or include videos and photos as well. Keep in mind that including media will significantly increase the backup size.
Set Backup Frequency: Decide how often you want to back up your chats – daily, weekly, or monthly. Daily backups are recommended for the most protection.
Initiate the Backup: Tap “Back Up” to start your first backup. This might take some time depending on the amount of data you have.
Managing Your Google Drive Backups
Viewing Backup Details: In the “Chat backup” settings, you can see the date and time of your last backup, as well as the size of the backup file.
Changing Backup Settings: You can easily adjust the backup frequency, inclusion of media, and Google account at any time.
Troubleshooting: If you encounter any problems, check your internet connection and ensure you have enough Google Drive storage space. You can manage your Google Drive storage through your Google account settings. Link to Google Drive storage management
Restoring Your WhatsApp Chats from Google Drive
If you need to restore your chats, follow these steps:
Uninstall and Reinstall WhatsApp: Completely uninstall WhatsApp from your phone.
Reinstall and Verify: Reinstall WhatsApp from the Google Play Store.
Follow the On-Screen Prompts: The app will guide you through the process of restoring your chats from your Google Drive backup.
Backing Up WhatsApp on iPhone Using iCloud
For iPhone users, the process is similar, but instead of Google Drive, you’ll use iCloud. iCloud is Apple’s cloud storage service, and it works seamlessly with your iPhone.
Setting Up Your First iCloud Backup
Check iCloud Storage: Ensure you have enough iCloud storage space. You can check and manage your iCloud storage in your iPhone’s settings.
Open WhatsApp: Launch the WhatsApp app.
Access Settings: Tap “Settings,” then “Chats,” and finally “Chat Backup.”
Choose Your iCloud Account: Make sure you’re signed in with the correct iCloud account.
Customize Your Backup: Decide whether to include media in your backup.
Set Backup Frequency: Choose how often you want to back up your chats.
Initiate the Backup: Tap “Back Up Now” to start the backup process.
Managing Your iCloud Backups
Viewing Backup Details: You can see the date and time of your last backup in the “Chat Backup” settings.
Changing Backup Settings: You can easily adjust the backup frequency and media inclusion.
Troubleshooting: If you have issues, check your internet connection and iCloud storage.
Restoring Your WhatsApp Chats from iCloud
Restoring your chats from iCloud is similar to the Android process:
Uninstall and Reinstall WhatsApp: Uninstall WhatsApp from your iPhone.
Reinstall and Verify: Reinstall WhatsApp from the App Store.
Follow the On-Screen Prompts: The app will guide you through restoring your chats from your iCloud backup.
Local Backups: A Secondary Safety Net
While cloud backups are convenient, it’s always a good idea to have a local backup as a secondary safety net. This backup is stored directly on your phone’s internal storage.
Creating a Local Backup (Android and iPhone)
The process for creating a local backup is largely the same for both Android and iPhone:
Open WhatsApp: Launch the WhatsApp app.
Access Settings: Go to “Settings,” then “Chats,” and finally “Chat backup.”
Initiate a Backup: For Android, you’ll typically see an option to back up to your phone’s storage. For iPhone, the process might be slightly different, but the option should be available within the “Chat Backup” settings.
Restoring from a Local Backup
Restoring from a local backup is generally done during the initial setup of WhatsApp after reinstalling the app. The app will usually detect the local backup and offer to restore it.
Choosing the Right Backup Method for You
The best backup method depends on your needs and preferences. Here’s a quick comparison:
Google Drive (Android): Convenient, automatic backups to the cloud. Requires a Google account and sufficient Google Drive storage.
iCloud (iPhone): Convenient, automatic backups to the cloud. Requires an iCloud account and sufficient iCloud storage.
Local Backup (Android & iPhone): A secondary safety net, stored directly on your phone. Less convenient for restoring if you lose your phone.
Understanding Backup Sizes and Storage
The size of your WhatsApp backup depends on the amount of data you have, including text messages, photos, and videos. Media files significantly increase the backup size. Make sure you have enough storage space in your Google Drive, iCloud, or phone’s internal storage.
Troubleshooting Common Backup Issues
Internet Connection: A stable internet connection is crucial for cloud backups.
Storage Space: Ensure you have enough storage space in your chosen backup location.
Account Login: Make sure you’re logged into the correct Google or iCloud account.
App Permissions: Check that WhatsApp has the necessary permissions to access your storage and cloud services.
Summary: Keeping Your WhatsApp Chats Safe
Regularly backing up your WhatsApp chats is essential to protect your valuable conversations and memories. We’ve covered the methods for backing up to Google Drive (Android), iCloud (iPhone), and locally to your phone’s storage. Remember to choose the method that best suits your needs and regularly check your backup settings to ensure everything is working correctly. By following these steps, you can rest assured that your WhatsApp chats are safe and secure.
Let’s keep the conversation going! Share your experiences with WhatsApp backups in the comments below. Have you ever lost your chats? What tips do you have for other users? And don’t forget to share this post with your friends so they can protect their chats too!
0 notes
Text
Everything to Consider Before Uninstalling WhatsApp

In today’s fast-paced digital world, WhatsApp has grown into a vital tool for staying connected. Whether it’s casual chats, important voice or video calls, or even handling business communications, millions of users globally depend on WhatsApp daily. It offers a convenient, real-time way to engage with friends, family, and colleagues. However, there may come a moment when you find yourself considering uninstalling or deleting the app entirely. This decision might stem from privacy concerns, a desire to reduce distractions, or even a switch to another messaging platform. But before making such a choice, it’s essential to carefully think about the potential pros and cons.
In this guide, we'll explore all the critical factors you should keep in mind before taking action, including how deleting and uninstalling WhatsApp are fundamentally different decisions.
Reasons for Uninstalling WhatsApp Account
There are several compelling reasons why users choose to uninstall WhatsApp, ranging from privacy concerns to digital overload.
1. Privacy Concerns
With growing worries about data privacy, many users are uncomfortable with WhatsApp’s data-sharing policies with its parent company, Meta. Uninstalling can offer peace of mind without permanently deleting your account.
2. Time Management
Constant notifications and messages can be distracting. Uninstalling WhatsApp can help individuals focus better on their tasks by reducing interruptions throughout the day.
3. Digital Detox
In an always-connected world, uninstalling WhatsApp allows users to take a break from social media and messaging platforms, helping to disconnect and reset without losing access to their data.
4. Switching to Alternative Platforms
Many people are turning to alternative messaging apps like Telegram or Signal, which promise enhanced privacy features and better control over data.
5. Reducing Phone Storage
WhatsApp media, including photos and videos, can quickly eat up storage space on your phone. Uninstalling the app helps clear up space temporarily.
6. Burnout from Constant Communication
For some users, the pressure to stay connected can lead to burnout. Uninstalling WhatsApp allows them to step back from social obligations and enjoy some personal space.
These reasons reflect the growing need for privacy, mental balance, and improved focus in the modern digital landscape.
Restoring WhatsApp Chats After Re-Installing WhatsApp
One of the biggest concerns when uninstalling WhatsApp is losing all your chats, photos, and media. Fortunately, WhatsApp offers a backup feature that allows you to restore your chat history after re-installation. Here’s how it works:
1. Cloud Backup
Before uninstalling WhatsApp, make sure you have a backup of your chat history on Google Drive (for Android) or iCloud (for iPhone). This backup includes all your messages, photos, and videos.
2. Restoring the Backup
Once you reinstall WhatsApp, it will prompt you to restore your chats from the backup. Simply follow the instructions, and all your previous messages and media will be restored.
3. Local Backup (Android Only)
WhatsApp also creates a local backup on your phone’s storage, which can be used to restore messages even without cloud backup.
Make sure you enable regular backups in WhatsApp’s settings to ensure you don’t lose any important conversations.
Deleting vs. Uninstalling WhatsApp
When considering stepping away from WhatsApp, it's important to understand the difference between deleting your account and simply uninstalling the app. These two actions have distinct consequences, and choosing the right one depends on your needs.
Uninstalling WhatsApp
Uninstalling WhatsApp is a temporary step. When you uninstall the app from your device, you are essentially removing the software without affecting your account. Your account remains active, meaning people can still send you messages, though you won’t receive them until you reinstall the app. Additionally, all your messages, photos, and videos are stored in backups (if enabled), making it easy to restore everything when you reinstall WhatsApp.
Deleting WhatsApp
Deleting WhatsApp is a more permanent decision. When you delete your account, all your data is erased, including your chat history, groups, profile picture, and account details. Once deleted, the process is irreversible, and you’ll need to create a new account if you decide to return. Deleting your account also removes you from any groups, and any messages you’ve sent will remain visible to others, but your profile will no longer exist.
Ultimately, the key difference is in permanence. Uninstalling gives you the flexibility to take a break without losing data while deleting is a final step that erases your account and all associated information. If you're unsure whether you want to part with WhatsApp permanently, uninstalling might be a better option. If you're certain about leaving the platform for good, then deleting your account is the way to go.
Benefits of Uninstalling WhatsApp
There are several advantages to uninstalling WhatsApp without permanently deleting your account. These benefits can help you decide whether a temporary uninstall is more suitable than a complete deletion.
1. Improved Focus
Uninstalling WhatsApp eliminates constant notifications, allowing you to focus more effectively on your tasks and minimizing daily distractions, helping you maintain better concentration throughout your day.
2. Digital Detox
Uninstalling the app allows you to take a temporary break from social media without losing any data. It’s an ideal solution for those looking to disconnect but not ready to delete their accounts permanently.
3. Privacy and Security
If you’re concerned about your privacy, uninstalling the app will ensure that it can no longer collect data from your device, as it’s no longer installed. Your account remains intact, but your phone no longer communicates with WhatsApp servers.
4. Reduced Phone Storage Usage
WhatsApp media (photos, videos, documents) can take up a significant amount of storage on your phone. Uninstalling the app helps free up space temporarily, which can be useful if you're running low on storage.
5. Easier Reconnection
The best part about uninstalling instead of deleting your account is that you can easily reinstall the app whenever you’re ready. All your contacts, chats, and media will still be there if you’ve backed them up correctly.
Uninstalling WhatsApp offers a flexible solution for those who need a break but aren’t ready for a permanent farewell.
Conclusion
Before deciding to uninstall WhatsApp, it’s crucial to consider the reasons behind your choice. Whether it's privacy concerns, the need for a digital detox, or simply wanting to try other apps, uninstalling WhatsApp can offer many benefits without the finality of account deletion. If you do uninstall, remember to back up your chats, so they can be restored later. Additionally, understanding the difference between uninstalling and deleting WhatsApp is key to making an informed decision.
Ultimately, uninstalling WhatsApp can be a healthy step toward better focus and time management, while still allowing you to reconnect when the time is right. Whether you're looking to step away for a short period or reconsider your use of messaging apps, uninstalling WhatsApp provides a balanced solution for those seeking flexibility.
1 note
·
View note
Text
How to Clone a Phone Remotely Using Phone Clone Apps
In today’s fast-paced digital age, having a reliable and secure way to clone a phone has become an essential need for many users. Whether you're upgrading to a new device, switching between Android and iOS, or simply looking for a way to back up your data, phone clone apps offer a seamless solution. These apps can clone a phone remotely, allowing you to copy all your vital information, from contacts to media files, without losing anything.
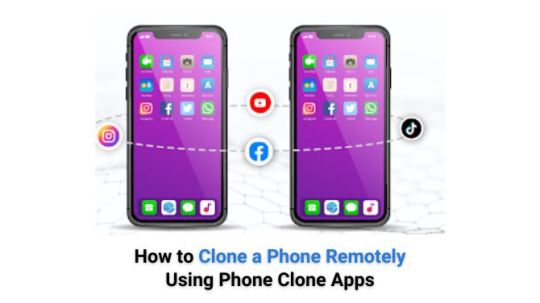
In this blog, we will explore the process of cloning a phone, how phone clone apps work, and why they are an excellent choice for data transfer and backup.
Introduction to Phone Clone Apps: What They Do and Why You Need Them
Phone clone apps are software tools that allow you to duplicate the content from one phone to another. Whether you're transferring contacts, messages, photos, videos, or applications, these apps simplify the process without needing cables or computer assistance.
Why might you need to clone a phone?
Upgrading to a New Phone: When buying a new phone, you want to keep your data intact. Phone clone apps make the transition from old to new device smooth and quick.
Backup and Restore: In case of accidental data loss, phone clone apps serve as a safeguard. By cloning your phone, you have a replica of your data stored elsewhere.
Cross-Platform Compatibility: Switching between Android and iOS? Many phone clone apps are compatible with both, making data migration a hassle-free process.
By using phone clone apps, you can avoid the risk of data loss, especially during significant device changes.
How to Clone a Phone Safely: A Step-by-Step Guide Using Phone Clone Apps
Cloning a phone safely is a straightforward process if you follow the right steps. Here’s how you can clone a phone using phone clone apps:
Step 1: Choose the Right App
Before you start, ensure you select a phone clone app that suits your needs. We'll dive into the best ones later in this guide.
Step 2: Install the App on Both Devices
Install the phone clone app on both the source (the phone you want to clone) and the destination (the phone where the data will be transferred) devices.
Step 3: Connect Both Phones
Most phone clone apps will ask you to connect both phones via a Wi-Fi network or by scanning a QR code. This establishes a secure connection between the devices.
Step 4: Select the Data to Clone
Once connected, choose the type of data you want to clone. This can include contacts, messages, photos, apps, and more. Some apps will allow you to customize the selection based on your preferences.
Step 5: Begin the Cloning Process
After selecting the data, initiate the cloning process. This might take some time, depending on the volume of data you are transferring.
Step 6: Verify the Data Transfer
After the process is complete, check the new phone to ensure all data has been transferred successfully.
Following these steps ensures that the phone cloning process is secure and efficient, without any data loss.
Top Phone Clone Apps You Can Use for Seamless Data Transfer
There are several phone clone apps available that make data transfer easy and seamless. Below are the top apps:
Phone Clone (by Huawei): A simple app that allows you to transfer contacts, SMS, call logs, and other data from any Android or iOS device to a Huawei phone.
Cloneit: A highly efficient app that transfers up to 12 types of data, including photos, contacts, and apps. It works well for Android devices.
Samsung Smart Switch: Specifically designed for Samsung users, this app allows the transfer of all essential data from your old phone, whether it's Android or iOS.
SHAREit: SHAREit is a popular cross-platform app that not only allows file sharing but also clones data between phones.
Dr.Fone - Phone Transfer: This is a paid app with more advanced features for users looking to clone a phone with complete control over the data transferred.
These apps provide robust solutions for phone cloning and cater to various needs, depending on the device you’re using.
Can You Clone a Phone Remotely? Exploring Remote Phone Clone App Options
A common question many users ask is whether they can clone a phone remotely without physically accessing the device. While most phone clone apps require the devices to be in close proximity to establish a connection, certain apps support cloud-based data backups, which allows for remote access in some cases.
Cloud-Based Backups: Many apps, such as Google Drive or iCloud, let you back up your phone’s data remotely. Once backed up, this data can be restored on another device without needing physical access.
Device Linking: Apps like WhatsApp and Telegram allow data to be synced across devices by linking them through a web interface. While this is not full phone cloning, it is a form of remote data migration.
While fully remote cloning of a phone (without proximity) is rare, some advanced solutions might offer partial remote capabilities.
How to Use Phone Clone Apps for Transferring Data Between Android and iOS
One of the biggest challenges for users is transferring data between different operating systems, especially between Android and iOS. Phone clone apps can make this process easier. Here’s how you can do it:
Use Cross-Platform Apps: Apps like SHAREit, Phone Clone by Huawei, and Dr.Fone are designed to work across both Android and iOS. Simply install the app on both devices, connect them, and select the data to be transferred.
Export and Import Options: If some apps don’t support direct transfer, you can often export data (such as contacts) as a file and then import it on the new phone.
Use Cloud Services: You can back up your data to cloud services like Google Drive or iCloud and then restore it to the new device.
These methods ensure that you can seamlessly clone data between Android and iOS devices.
Key Features to Look for in a Reliable Phone Clone App
Not all phone clone apps are created equal. When choosing a reliable app, look for the following features:
Cross-Platform Compatibility: Ensure that the app works across both Android and iOS devices if you’re transferring between platforms.
Data Security: The app should prioritize user privacy and secure data transfer, often using encrypted connections.
Type of Data Transferable: Check if the app allows for the transfer of all essential data such as contacts, media, and app data.
Ease of Use: A user-friendly interface can make the cloning process smooth, even for non-technical users.
Speed of Transfer: Depending on the amount of data, the transfer speed should be fast and efficient.
These features will ensure that your phone cloning experience is both safe and effective.
How to Clone a Phone Without Losing Any Data Using Clone Apps
The biggest concern when cloning a phone is the potential loss of data. To ensure that no data is lost:
Use Trusted Apps: Select an app that has positive reviews and a track record of secure transfers.
Double Check Data: Before starting the process, review all the data that you want to transfer and ensure it’s all selected in the app.
Backup Your Data First: Even when cloning a phone, it’s a good idea to back up your data using cloud services, just in case something goes wrong during the process.
Phone Clone Apps: How to Transfer Contacts, Photos, and More
When cloning a phone, most people want to transfer contacts, photos, and apps. Here’s how phone clone apps handle different data types:
Contacts: Almost all phone clone apps allow you to transfer your contact list seamlessly. This includes phone numbers, email addresses, and other contact details.
Photos and Videos: Media files are usually large, but phone clone apps compress them for faster transfer while maintaining quality.
Applications: Some apps, like SHAREit, allow the transfer of apps between Android phones, but note that app data might not always transfer.
A Complete Guide on Cloning a Phone for Backup Using Clone Apps
Cloning a phone for backup ensures that you have a secure copy of your data in case of device loss or malfunction. Here’s how to do it:
Install a Phone Clone App: Choose an app that allows for complete backup.
Select Data to Backup: Ensure all your critical data, including contacts, media, and documents, are selected.
Store the Backup: Save the cloned data to a secure location such as a cloud service or an external hard drive.
This process creates a complete replica of your phone for easy restoration.
How Secure Is It to Clone a Phone? Understanding Data Privacy with Phone Clone Apps
Data security is a major concern when cloning a phone. To ensure privacy and protection:
Use Apps with Encryption: Look for phone clone apps that offer encryption during data transfer, ensuring that your information remains safe from unauthorized access.
Avoid Public Wi-Fi: Always clone your phone over a private and secure connection to minimize the risk of hacking.
Verify Permissions: Review the permissions the app requests and ensure they align with the app's intended use.
By following these guidelines, you can clone a phone without compromising your data security.
Conclusion
Cloning a phone has never been easier with the wide range of phone clone apps available today. Whether you’re upgrading devices, switching platforms, or simply backing up data, these apps offer secure, user-friendly solutions for seamless data transfer. By following the steps outlined in this guide, you can confidently clone your phone while ensuring data privacy and integrity.
0 notes
Text
Insta Pro Download APK Latest Version 2024 For Android

InstaPro APK
Instagram is a social media platform where users interact with each other, chat with each other, and share things with each other. In the official version, we can only view videos or stories shared by other people. Apart from this, many ads are shown to the user within the official version, which causes a lot of trouble for Ad’s express ablution. Keeping all these things in mind, a modified version of Instagram has been created which is called InstaPro APK. This version is built with user experience in mind. Ads won’t bother you too much in this version. If you like a play story or a video or a reel etc then you can download your video using this app. Because there are many users who need to use many features like downloading videos, and always updating privacy, these things are not visible in the official version.
Download
It is built without all the features that Instapro Download doesn’t allow you to use, While the user wants to use these features. After knowing so many cool features, the question in your mind will be whether to purchase this version or we can download it free of cost. So here is good news for you you can download this version for free below we have added it step by step.
Feed & Stories Privacy Options
In this feature, you can control who can see your stories and the spotlight. Instagram Pro provides you with the best feature you have ever used before. In this feature, you can use who can see your stories the people who follow you back. When you share a story on your profile, random people comment on your story, which is not in the realm of ethics. Earlier it was not an option that a person could control this thing, but now you don’t have to worry at all. Because now you can control the news and stories shared on your profile. Sometimes it happens that we have personal things inside our news or story, So we must have access to these things so that no one can take advantage of them. If you want to use these features, you need to download the Instagram Pro APK.
Customized Chat Screen
In the official version, when we’re talking to a guy, he interacts with a sample background. Instapro App allows us to customize it with beautiful themes when we are chatting with a guy. We can save its media gallery then the back of the chat as well. If we are talking to a guy through an application and his background and his coloring are not good, So we stop talking to that person or we start to feel bored. Keeping this in mind, InstaPro APK has provided a function that allows you to edit them by yourself. You can also color your chat screen according to your own. You can also edit your text font style. In short, you can set your chat screen exactly to your style. There are options within the chat screen that you can customize, you have to download this application to enjoy the custom features.
Download Favorite Stories & Videos
You can easily download your favorite videos and stories in this added feature from Instagram Pro. It has been a long time since many social applications were created, Where users could watch videos, what was happening around the world, what was being watched, everything was audible. However, it has been seen that if a user likes a video and likes it if he wants to save it for himself, he doesn’t have the option to save the video. It became another issue for the developers to figure out how to clean it up. But if you have downloaded InstaPro APK then you don’t need to worry at all. Because using this application, if you like a story or a video, you can block download it.
Backup & Restore Data Features
With this feature of Instagram, you can back up your data and also back up screen chats. This feature can save you from losing your data at all. In this way, it is an excellent source of privacy. If you want to continue using the given features, you can use them by backing them up. One of the most important features of any application is how important it is to have its data backed up. The best feature of this application is that we have a backup of our chats, our calls, our videos, media, and all the data in our gallery.
Data backup has been a problem for a long time, It was a genuine problem that had to be solved. Considering this, the application has given an option thanks to which you can keep a backup of your data and you can access it at any time you want.
More Privacy Setting Options
Instagram Pro provides you with the best privacy material that can help you have a wonderful experience with this site. This site provides you best features for your personal and social use to recognize the whole world. With these features, you can not lose your personal data and privacy. Instagram Pro can help you with more privacy features you can post your images it’s your choice you can manage your account private or official. Often this happens to us when we are using an application, we have a request from a person whom we don’t even know. To prevent this there is a function within this application where you can report the person, Play Instagram takes action against him either by banning his profile or removing him.
FAQ’s
What is InstaPro APK?
InstaPro APK is a customized version of Instagram that comes with extra cool features, that are developed according to user experience.
Is it safe to use this version?
Yes, it is safe to use this version of Instagram.
Conclusion
In the above article, we have provided you information about Insta Pro APK. This is the best-modified version of Instagram. Official Instagram has thousands of features that we cannot access, But Insta Pro APK allows us to use these features. InstaPro APK is designed keeping in mind the user experience, Which the user feels happy while using those features. If you also want to use the amazing features of Instagram, then please download Insta Pro APK as we have also guided you above. The biggest advantage is that if you are a businessman, you can invest money and expand your business. How it is possible It is possible that Instagram promotes your business to the whole world, the amount of money you invest in Instagram will take your business so far, which will increase the sales of your product and you will also benefit from it.
1 note
·
View note
Text
What to do if your phone gets stolen
If your phone falls into the hands of criminals, do not panic. Here is how to protect your data.
June 2, 2021

If you can’t find your phone, don’t panic. Exhaust your good options — maybe you misplaced it or lent it to someone, or buried it under some papers — and then, unfortunately, assume it was stolen. If you read our post on how to theft-proof your smartphone and data and followed the tips, then you’ve safeguarded your information and can restore it on a new phone. But even if you didn’t prepare in advance, you can reduce the damage.
Table of Contents:
Best-case scenario
Worst-case scenario
Have your SIM card blocked
Warn your relatives and friends
Block stolen smartphone
Unlink bank cards
Block the smartphone’s IMEI number
What’s next?
Contact the police
Change your passwords
Restore your data
Cheer up
Best-case scenario
Your phone’s screen was locked when it went missing, the data on it is encrypted, and the SIM card is PIN-protected. In that case:
Use the Find My Device (Android) or Find My (iOS) feature to mark the phone as lost and have the device display an on-screen message with the number of a friend or relative who can contact you in case someone honest finds the device;
After waiting as long as you’re comfortable on the first step, remotely delete all data on the device and contact your operator to block the SIM card;
Buy a new smartphone and restore your data from a backup copy.
We also recommend staying vigilant after the theft. Thieves often take advantage of that contact information, especially with more expensive devices, and use social engineering to trick the owner of the stolen device into revealing the password for their Google or Apple ID account. If successful, they can unlink the device from the account and make more money by selling the phone whole than by disassembling it and selling the parts.
In short, treat all texts and calls related to a stolen phone with the utmost suspicion, and do not enter or reveal your Google account or Apple ID credentials.
Worst-case scenario
If the smartphone landed in the wrong hands and it is not protected, possibly not even by a screen lock, then time is of the essence. The first thing you need is another phone from which to make several calls. Ask store or restaurant staff to use their phone, or flag down a cab and borrow the driver’s phone.
Block your SIM card
Your first call is to your carrier. Tell the support rep that you lost your SIM card and ask them to block it. Once the SIM card is blocked, the thief will no longer be able to impersonate you (call from your number or receive a text message with a verification code for changing a password or confirming a transaction, for example).
Warn relatives and friends
Your second call should be to a friend or relative. Explain that your phone was stolen, and ask them to warn mutual contacts that they might get calls or messages from your number with requests for money or maybe some questions, all of which they should ignore. You might want to ask them to post a warning on social media if you share many friends there.
Block smartphone
You will need access to the Internet to block your stolen smartphone. If at all possible, do so on a secure device; you will be entering your password.
First, log in to your Google or Apple ID account. If you are logging in from someone else’s device, and you have two-factor authentication set up, that may be difficult. Obviously, you can’t get a verification text or open a mobile authenticator app; your phone is gone. Android users can change the password without text message verification. If that applies to you, you will need to enter one of the backup codes you received when setting up two-factor authentication. iPhone users can recover account access by having a verification code sent to a trusted phone number or device.
Once you have logged in to your Google or Apple ID account, here’s what to do:
Find your missing smartphone in the device list under Security (for Android phones) or the Find My iPhone app (for iPhones) and find the missing smartphone in the list of devices;
Note the location of the smartphone on the map. If the phone is on and geolocation is active, its location icon should appear. However, even if the thief’s path is clear, do not try to chase them. Rather, ask the police for help;
Select Lost Mode. The system will offer to enter a message for the lock screen and a backup number to contact you. Your smartphone will now display that message, and nothing else. If the phone was simply misplaced, not stolen, the finder will be able to call you. Watch out for phishing messages and calls; criminals may pose as support reps and contact you to try to get the account password;
If your device contains important and sensitive information, consider the drastic measure of erasing it remotely. However, keep in mind that option is irrevocable — and also means giving up the ability to locate the phone remotely.
Unlink bank cards
When you block your smartphone with Find My or Find My Device, respectively, Apple or Google may suggest unlinking any associated cards, but in case it doesn’t, unlink bank cards from your device manually in the account settings. Unless they were stolen along with the phone, you don’t need to block the cards.
For Android devices:
Sign in to your Google account;
In the Payments & subscriptions section, select Payment settings;
Remove your cards.
For iPhone:
Sign in to your Apple ID account;
In the Devices section, find the missing iPhone and select Remove all cards.
Block the smartphone’s IMEI number
In some countries, in addition to having the SIM card blocked, you can add a stolen phone’s identification number (IMEI) to the carrier’s blocklist. To do that, you need to give the carrier this number. If you have the box in which the phone came, you can find the number on it.
Android lets you use the Find your phone feature to find the IMEI: Click on the encircled “i” next to the image of your phone and the IMEI code will pop up.
iPhone users can find theirs at appleid.apple.com by signing in with the Apple ID used on the stolen device, scrolling down to Devices, and selecting the iPhone to see its IMEI.
In theory, once the carrier adds the IMEI to the blocklist, the smartphone will not be able to connect to the mobile network even with a different SIM card. This feature works in the United States, the United Kingdom, Turkey, Latvia and certain Latin American countries.
What’s next?
Once you’ve taken prudent steps to protect yourself and your data, it’s time to get down to mitigating other potential consequences.
Contact the police
Report the theft, giving police details such as carrier and phone number. However slim, there is still a chance to get your smartphone back. Sometimes phones get returned even after being missing for years.
Change your passwords
Change as many passwords as you can in your apps and mobile browser. Once you’ve replaced the passwords, set up two-factor authentication.
Restore your data
If you enabled backup on the device while you still had it, then you will be able to recover all information, down to text messages, on your new smartphone.
Here are the steps to do this on Android and iPhone.
Cheer up
The loss of a smartphone certainly carries serious stress and is a threat to your data. However, if you follow the steps above and back up your data in advance, you can cut your losses. Do not despair because your gadget was lost or stolen — your personal safety is the top priority.
0 notes
Text
ChatGPT displays Google Drive and OneDrive charts and tables

Microsoft OneDrive
What is OneDrive ?
Microsoft developed OneDrive. It enables you share, save, and browse files on any internet-connected device. This digital safe can hold all your important documents, photos, and videos.
OneDrive app Important characteristics:
File Storage and Backup: Use OneDrive to save up space on PCs, cellphones, and other devices. It’s a backup for lost, stolen, or broken devices.
Sharing files and folders is simple. Collaboration on OneDrive documents in real time. This is great for family and friend memories and workplace projects.
Access your files on the move with the OneDrive iOS, Android, and Windows Phone app. The software can automatically backup phone images and videos to OneDrive.
OneDrive lets you choose files and folders for offline access. You can access and manipulate them without an internet connection.
Security: Microsoft implements rigorous security mechanisms to protect OneDrive data.
OneDrive Storage
OneDrive provides a free plan that includes 5 GB of storage capacity. Depending on how much you use, this might be enough for basic needs, but it could soon fill up.
Paid Plans: Microsoft 365 offers OneDrive storage sizes of 100 GB to 1 TB, or 6 TB for family plans.
OneDrive’s primary feature is its seamless connection with Microsoft 365 products including Word, Excel, and PowerPoint. This makes it simple for you to store and retrieve your papers from within these programmes.
Use OneDrive to safely store and share crucial files
OneDrive has you covered
To ensure that your vital information, pictures, programmes, and settings are always accessible, make a backup of your device’s contents. You can simply recover your files from errors or corrupted files, so you can rest easy.
Relive the moment by sharing your memories
Store and discreetly distribute images, movies, and albums with loved ones. OneDrive enables you to relive your most treasured memories with the people who mean most, whether they were from a year or a lifetime ago.
Safe, arranged, and up to date belongings no matter where you are
From any location and on any device, you can quickly access, modify, and arrange your files. Your files and folders are updated when you make changes to them, and you can even access them when not connected to a device.
Go wherever real life takes you with your digital life
You can store, edit, and share your images, videos, and files on the go with the OneDrive mobile app. To preserve them in the cloud, you can even scan priceless memories and crucial papers.
Features that improve connectivity, safety, and ease of living
Restore and safeguard
You shouldn’t be concerned about losing files if something were to happen to your device.
Accessible from anywhere
Everywhere you travel, you may access your files and pictures from any of your devices.
Exchange and establish connections
Share your files and images in private with loved ones, and use Office tools to collaborate in real time on projects.
All things considered, Microsoft OneDrive is a strong and adaptable cloud storage option that meets the demands of both individuals and businesses. To get you started, it offers a free tier. For those that need additional storage capacity, there are subscription options available.
ChatGPT’s data analysis is getting a lot better thanks to OpenAI, which will make the tool more reliable and easy to use for ChatGPT Plus, Team, and Enterprise users. With the flagship model GPT-4o, customers may now interact with tables and charts and add files straight from Microsoft OneDrive and Google Drive.
Users can now upload files from Google Drive and Microsoft OneDrive to ChatGPT without downloading them to their desktop. This lets ChatGPT quickly understand Google Sheets, Docs, Slides, Microsoft Word, Excel, and PowerPoint files.
With the option to ask follow-up questions and receive suggested prompts to further their study, interactive tables let users expand and analyse data in real-time. Users can instruct ChatGPT, for instance, to merge spreadsheets containing monthly spending and produce a pivot table with categories for each type of expense.
Users can engage with a variety of chart formats, such as bar, line, pie, and scatter plots, by creating customisable charts. Before downloading the charts for use in presentations or documents, users can choose colours, hover over chart parts, and ask further questions.
For example, users can ask ChatGPT to generate a graphic that displays retention rates by cohort by selecting a Google Sheet containing the most recent user data from their company’s Google Drive account.
These enhancements expand on ChatGPT’s current capacity to comprehend and evaluate datasets using natural language. ChatGPT allows users to submit data files and use it to develop and execute Python code for activities including combining datasets, making charts, and finding patterns. This feature saves specialists time on repetitive activities and facilitates the conduct of in-depth analysis for novices.
The Carlyle Group vice president David Vaughn emphasises the usefulness of the application by saying, “ChatGPT is part of my toolkit for analysing customer data, which has grown too large and complex for Excel.” I can do more data exploration on my own and get useful insights faster thanks to its assistance in sorting through large datasets.
In these upgrades, OpenAI places a strong emphasis on complete security and privacy. Plus users have the option to opt out of training via Data Controls, and ChatGPT does not train on Team or Enterprise client data. For ChatGPT Enterprise, OpenAI’s privacy and security policies include data encryption, compliance, and SAML SSO.
The new capabilities have been commended by Lauren Nowak, Marketing Manager at Afterpay, who said, “ChatGPT walks me through data analysis and helps me better understand insights.” It helps me learn, makes my work more fulfilling, and frees up time for me to concentrate on the more important aspects of it.
In a similar vein, Google also revealed new Gemini features at Google I/O 2024. In addition to analysing the data from the sheet, Gemini also produces an attractive graphic that enables customers to view the entire breakdown by category. This covers a range of use cases in your email, including shopping, remodelling projects, and vacation bills.
You can make greater use of all that information in Gmail to work, plan, and play more effectively. This September, Labs users will be able to build a sheet, arrange your attachments in Drive, and perform data analysis using Q&A.
Read more on Govindhtech.com
#TechNews2024#govindhtech#technologynews#technology#Technologytrends#technews#news#ChatGpt#chatgpt4o#Microsoft#Microsoft365#microsoftcopilot#GoogleDrive#OneDrive#MicrosoftOneDrive
0 notes
Text
Techfelts: Your Ultimate Solution for Data Recovery
In the contemporary digital age, our smartphones have become repositories of cherished memories, essential documents, and vital information. However, the vulnerability of digital devices to theft, damage, or technical malfunctions poses a significant risk of data loss. In such scenarios, the need for a reliable data recovery tool becomes paramount. Enter Techfelts – a robust application designed to effortlessly retrieve erased photos, documents, and other important data. In this comprehensive guide, we delve into the details, features, and usage of Techfelts, shedding light on its significance in safeguarding your digital assets.
What is Techfelts? Techfelts stands as a beacon of hope for individuals grappling with the aftermath of accidental deletions or device malfunctions. More than just a data recovery tool, Techfelts boasts additional functionalities such as free calling and personalized photo settings in the dialer interface. With its user-friendly interface and advanced algorithms, Techfelts ensures a seamless and hassle-free data recovery experience.
Key Features of Techfelts: Techfelts offers a plethora of features tailored to meet the diverse needs of users:
User-Friendly Interface: Navigating through Techfelts is a breeze, thanks to its intuitive design that requires no technical expertise.
Comprehensive File Recovery: From erased photos to crucial documents, Techfelts ensures the retrieval of a wide array of file types, preserving your invaluable information.
Privacy and Data Security: Advanced encryption algorithms employed by Techfelts guarantee the privacy and security of your recovered data, shielding it from potential cyber threats.
Quick Scanning: With its swift scanning process, Techfelts allows users to initiate the restoration process promptly, minimizing downtime.
Cross-Platform Compatibility: Whether you're using Windows, iOS, Android, or MacOS, Techfelts seamlessly integrates with all major operating systems.
No Need for Backup: While data backups are recommended, Techfelts eliminates the necessity by facilitating the recovery of deleted files without prior backup.
Regular Updates: Stay abreast of the latest developments and enhancements with Techfelts' commitment to providing regular updates and insightful articles.
How to Recover Deleted Photos using Techfelts: Unlock the potential of Techfelts by following these simple steps to recover deleted photos:
Download Techfelts: Visit the official website of Techfelts and download the app through its APK version.
Launch the App: Install and launch the Techfelts photo recovery app on your device.
Choose Scanning Mode: Select your preferred scanning mode – Quick Scan or Deep Scan.
Select Storage Location: Identify the storage location where the lost photos were previously stored.
Initiate Scan Process: Let Techfelts work its magic as it conducts a thorough analysis of the designated storage.
Preview and Restore: Browse through the recovered photos and select the ones you wish to restore.
Save and Enjoy: With a click of a button, restore the selected photos and relish in the joy of retrieval.
How to Download Techfelts App: Embark on your journey towards seamless data recovery by following these steps to download the Techfelts app:
Visit Official Website: Access the official website of Techfelts using any legal web browser.
Navigate to Photo Recovery Section: Locate the photo recovery option on the website.
Initiate Download: Hit the download button to commence the download process.
Install the App: Once the download is complete, open the installation file and follow the on-screen instructions.
Launch and Enable Permissions: Launch the Techfelts app and grant necessary permissions for seamless functionality.
Ready to Use: Your device is now equipped with the Techfelts photo recovery app, ready to spring into action whenever the need arises.
Benefits of Techfelts: Unlock a myriad of benefits by incorporating Techfelts into your digital arsenal:
Free to Use: Enjoy the robust features of Techfelts without incurring any cost.
User-Friendly Interface: Seamlessly navigate through the app, irrespective of your technical proficiency.
Real-Time Monitoring: Stay informed about the data retrieval speed in real-time, ensuring optimal efficiency.
Cross-Platform Compatibility: Whether you're on a PC, Android, Mac, or iOS device, Techfelts has you covered.
Data Transfer Facilitation: Simplify the process of transferring data from old to new devices with Techfelts' seamless integration.
Storage Optimization: Techfelts optimizes storage space by restoring documents in smaller formats, maximizing efficiency.
When is Techfelts Necessary? Techfelts emerges as a necessity when confronted with the daunting prospect of data loss. Whether due to accidental deletions, technical errors, or device malware, Techfelts serves as a beacon of hope, facilitating the seamless recovery of lost data. Moreover, its ability to manage storage space and streamline data transfer further solidifies its indispensability in the digital realm.
In conclusion, Techfelts transcends the conventional boundaries of data recovery tools, offering a holistic solution that combines functionality, security, and convenience. As we navigate the complexities of the digital landscape, Techfelts stands as a steadfast ally, safeguarding our digital assets and preserving our invaluable memories. Embrace the power of Techfelts and embark on a journey towards effortless data recovery and unparalleled peace of mind.
0 notes
Text
10 Best Android Apps To Backup/Restore Data in 2024
No matter how secure your smartphone is, you should always back up your important files & data. If you’re using Android, you can use backup & restore apps for this purpose. Although hundreds of apps to back up/restore data are available for Android, not all are worth installing. Hence, we have carefully picked & listed the apps that serve well for the purpose and let you back up & restore your…
View On WordPress
0 notes