#are you linking associated files properly?
Explore tagged Tumblr posts
Text
I just listened to episode 26 of the Magnus Archives and I realized that it reminds me of Bloodborne. I have some spoilers for it, just because I was looking something up on the wiki and just intuited things based on some of the pages.
So it seems like there are some entities that are responsible for these events, a finite amount named with things associated with various fears. But episode 26 implies that these entities aren't uniform and aren't even aligned, which distinctly reminds me of Bloodborne. The way the Great Old Ones seem to each be distinct and non uniform and some seem to be fighting a proxy war against one another. Like The Moon Presence puts the player on a path that leads them to kill Rom and other great ones.
#tma podcast#tma spoilers#still enjoying it#spooky and good shit#i dont remember the names of characters like at all though#like whos jane prentis?#i dunno#didnt realize that the priest was in an earlier episode until way later#also i feel upset that jons not including the tags for the document in his recordings#like how are you filing them?#is it date based?#subject based?#by person?#are you linking associated files properly?#like come on i wanna know this stuff
9 notes
·
View notes
Text
I cannot emphasize enough how much everything In-ho did during his time in the games was in service of breaking down Gi-hun. Every glance, every story, every comment was incredibly and deliberately calculated.
His first interaction with Gi-hun immediately places the blame on Gi-hun for the games continuing: "I pressed the O because of you." He also explicitly asks for Gi-hun's help on behalf of the group. This sucks Gi-hun into being a mechanism of the games themselves (not just a player, but one telling others how to play) while robbing him of his agency to do so: whereas he was confident in helping during the first game, because it was his choice, In-ho's request forces him to share about the Dalgona prematurely, and he then has a nightmare about misleading the players. This also leads to many players becoming hostile when the game is not Dalgona, which--who could have guessed?--In-ho jumps in to stop. He orchestrated the situation so that Gi-hun would feel maximum pressure and guilt, before In-ho himself relieves it to build trust between them.
Then there are the introductions. In-ho uses Gi-hun's name before they are introduced, which may have been a genuine slip, but was very likely intentional given his response. In-ho's method throughout the games is to parallel and associate himself with Jung-bae, Gi-hun's only actual friend (he saves him during the merry-go-round games; he eavesdrops on Jung-bae's conversation with Gi-hun and directly uses the "get me a soju" line from that conversation to subconsciously build Gi-hun's trust in him during the firefight). So when he uses Gi-hun's name, he says he does so because he heard Jung-bae doing it, and Gi-hun allows him to continue--this creates the first of the links between them. But then, when they are properly introduced, In-ho laughs that "Seong" just means "last name;" in doing so, he implies to those who don't know him that Gi-hun may not be telling the truth, and in context of their conversation (focused on the significance of their names) highlights how Seong Gi-hun is "no one special." He's just an everyman.
Another reason that "slip" was almost certainly intentional is that In-ho is very deliberate about showing moments of weakness. His breakdown during the Six-Legged Race was designed to both further stress Gi-hun (and if Gi-hun had failed, they were in the very last groups present, so they could have been selectively spared as needed) and to strengthen their bond, as Gi-hun got to "encourage" In-ho; then In-ho helped Gi-hun and the team win by kicking with him the final time. Even cheering along with Gi-hun while the other teams went was in service of cementing their connection; and, any time a team failed, In-ho got to observe Gi-hun's reactions under the guise of empathy. In-ho may have felt some genuine emotions while cheering or comforting Gi-hun, but they aren't to be trusted.
That's particularly true because of his biggest "weak" moment: telling Gi-hun why he is in the games. The show confirms, when Jun-ho finds the winner file, that In-ho actually did join the games years before (from his family we know that it was because of his wife's illness), and that he won them himself. So he isn't lying about the details of his personal story--and he even gets emotional--but it is, once again, all in service of ensnaring Gi-hun and earning his trust. In-ho is not faking all of his emotions, but he is controlling and weaponizing them, which is why none of his apparent fondness for Gi-hun can be trusted. He uses his emotions as a tool, rather than being affected by them.
The ultimate result of this manipulation is that Gi-hun is made to feel that everything that happens is his choice (even the things he didn't choose). From the beginning, In-ho has ascribed his choices to Gi-hun. Throughout the games, there are several moments where In-ho explicitly has Gi-hun choose for him; other times, In-ho suggests an approach and Gi-hun shoots it down, and In-ho always coalesces. Gi-hun gets to have "his way." But "his way" doesn't seem to work, and he, like the rest of the players, is changed by the games. His final plan, as In-ho forces him to face, involves a sacrifice of some for the good of the many. Only after he admits this (through his silence) does In-ho agree to help. Then, during the firefight, when Gi-hun tries to give In-ho the ammunition he risked his life to get, In-ho asks, "Are you sure?" Gi-hun's choice to trust In-ho leads to him running out of ammunition earlier, forcing his surrender; meanwhile, In-ho still "dies," and Jung-bae is shot in front of Gi-hun's eyes. None of Gi-hun's choices made things better--they made it all his fault. He is left with the blame, as the Frontman (who is In-ho! And always has been!) tells him point blank.
But none of Gi-hun's choices have really been choices. They have all been based on lies, within a system that uses the information they have to actively orchestrate events against him. The same is true of the players in the game; their choices are not free, because their circumstances (largely caused by unfairness in the world) have trapped them. The baseness they resort to is not what they would do if they really had the choice, and some are even able to choose virtue within the hellscape, but over and over, the system facilitates the dominance of cruelty. And In-ho, the personification of that system, targets Seong Gi-hun, the "Everyman," to make him submit to it--to make him choose to believe that there is no other way.
#seong gi hun#hwang in ho#squid game#squid game 2#meta#my meta posts#kay can i just catch my breath for a second#this took me a while but i think it was worth it#and many people have already commented on how clearly this is an allegory for how society works in relation to us‚ the people in it#so i don't need to get into that but just to say it so that i have: we always have a choice.#and i hope against hope that gi-hun is somehow able to continue making that choice‚ the right choice‚ to believe in the good of humanity#to believe in a way out and a way forward if we just work together‚ if we just look into the face of a stranger and see a fellow man#because i believe in that. i *have* to believe in that. it is the only way to survive and the only way to have joy#and my fear is that the narrative is clearly leaning toward tragedy. toward turning him into the next frontman‚ or killing him#and that would be a sore loss indeed. people call him stupid and naïve but to me he reads as orpheus#not unaware of the way the world works‚ but refusing to accept it. desperate to show us 'how the world could be...'#'...in spite of the way that it is.' and in response i can only hope: 'maybe it will turn out this time‚ on the road to hell...'#'it's a sad song. but we're gonna sing it even so.'#kay has a party in the tags
147 notes
·
View notes
Text
All in one download + discord link
Hey guys!
So, there are lot of different places you can download EA’s store content. The purpose of how I do it was to give you the option to pick and choose the items you want. Everything is individualized, but since I’ve finished the majority of the work, there’s been a lot of asks for an easy way to download everything in one go. I’ve slowly been uploading bulk versions of each set, but that’s not exactly what you’re all asking for right?
This is the best compromise I found. My store content folder looks like this:
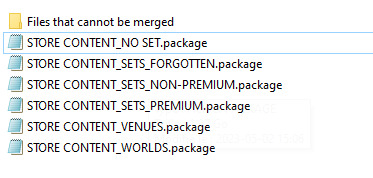
(FORGOTTEN is what I call the limited sets that you can’t find on the store anymore. ie: Dr Pepper sets)
I have merged every piece of store content I’ve uploaded in these 6 huge files (the biggest is 2GB) with the separated folder for content that also needs to standalone to work properly.
THIS works for me. BUT
It doesn’t mean it will work for everyone. I’ve decided to share these, but I cannot guarantee this format will work for you and I will not be uploading a different set up. I will not be helping you troubleshoot problems associated to this - you download and use at your own risk.
Here is the google drive folder containing the files: https://drive.google.com/drive/folders/1SuQohFbSvOPXEFVzGRbmr7UwlEVlgIYj?usp=sharing
You’ll find the 6 files and folder to put in your Mods/Packages.
ADDITIONALLY, you’ll find a folder containing all the store content lots that you have to place in your Library folder.
FINALLY, you’ll find a folder containing all my .world files with a ReadMe.txt explaining where they go depending on where you got the game.
Everything has been compressed using https://www.7-zip.org/ because I have limited google drive storage.
ENJOY
I have been uploading everything on discord, if you have it, come say hi! It’s easier to help you troubleshoot any issues you have and others might have experienced the same thing. There are no broken links on discord either because unlike tumblr and blogger, it doesn’t have it out for me.
https://discord.gg/fTFw9xVj2d
805 notes
·
View notes
Text
Artist Spotlight

Hi Pillowfolks! We want to feature your art and photography on the Pillowfort log-in page to showcase our vibrant creative community. Pieces displayed will be randomly rotated on a regular basis.
Want to participate? Having your piece featured is very simple! Just send us a high-resolution image of your art or photograph. If we choose to display it on the log-in page we’ll send you a release form to sign that gives us permission to save, alter (for display purposes only, i.e. we may have to alter the quality and/or crop the image to display properly on various screen dimensions), and display your work. We will not use your art, or photography in any way other than for featuring you on our log-in page.
Both fanart and original pieces are allowed. All mediums are encouraged. Traditional art must be scanned in at least 300dpi to be considered. Pieces that violate our Terms of Service are of course not allowed, and please keep the content of your submissions all-ages friendly.
You will be credited on the log-in screen with a link to your Pillowfort account, or to an external website (shop links, Ko-Fi, Patreon, or commission sheets are allowed!) if you prefer.
Submission Guidelines Send an e-mail to [email protected] with the subject line “Log In Art Submission” and include the following:
Your PF username
A direct link to your piece or attached high-resolution file of your piece
The link you want associated with your attribution (This will be your Pillowfort account by default)
We're excited to show off your work to the world! :)
#pifo#pillowfort#pillowfort.social#art#artist#photography#crafts#fiber art#traditional art#digital art
47 notes
·
View notes
Text
The Ellipsus Experience*
From someone who’s been using Google Docs for over a decade and LibreOffice for. Idk a year, probably.
*I don’t have a collaborator helping me out with this, so this is a solo-writer’s experience: please keep that in mind
Ellipsus is a writing website (not an app) that can be considered a collaborative alternative to Google Docs. They are [anti-AI] and don't plan on going back on this "barring significant regulatory changes." It has been compared both to Google Docs and LibreOffice. As stated above, I've used both of these other products (heavily) for a while and feel I'm properly familiar enough with both of them to say this one is... well deserving of the comparisons.
TL;DR
Ellipsus is essentially a GDocs/LibreOffice lovechild that is currently in open beta, works well, and I do recommend it as a Google Docs alternative for any collaborative needs just because it’s free and anti-AI, though it is only on par with LibreOffice so far as I can tell for solo work.
I was made aware of Ellipsus through a Blazed post here on Tumblr, though I haven't actually heard of it anywhere else, but I could just have completely and utterly forgotten if I'd ever seen them elsewhere. They also have a presence here on Tumblr, @ellipsus-writes, if you would like to have a browse for yourself.
All hyperlinks will be underlined and associated words will be between these [ ] brackets.
Getting Started
Ellipsus does not use a password system. You sign up/log in with your email, which will then send you a one-time code to get in. While signing up, the site asks a few questions while setting up, such as if you write with others (options boil down to yes, no, and not yet) and where you heard about Ellipsus from. You also initially choose your light mode/dark mode preference here. It can also use your system setting.
Once you’ve gotten through that, you’re taken to a document to introduce you to the features and capabilities of Ellipsus, though it doesn’t appear to really be… properly up-to-date… but it isn’t too badly divergent as to be too confusing (notably, there isn’t a “merge this draft” button to click like the doc tells you). It also offers several links to useful posts they’ve made to help you get started.
You will then be brought to the dashboard and unleashed.
Their layout is very simple, clean, and minimalist. There aren’t a thousand features, but sometimes you don’t need a thousand features. The site itself is easy to navigate and none of the toolbars or pages even look a little bit crowded, which is nice. Unfortunately, this does mean your settings are also very barebones. You can’t delete your account directly from the settings, but you can change your display name and email from the account settings page. Here, you can also download your logs or stored data. Unfortunately, though you can have an avatar/icon, you have to use Gravatar for it, with no exceptions. Other than that it displays the first two letters of the email associated with your account. This may be visible when collaborating with others.
On Desktop (and basics)
The dashboard (home page) shows your works, with a separate tab/page/button to show anything shared with you. Here is where you make new documents or manage existing ones, or make and manage folders.
Folders are named, and can have descriptions of their contents. They can be repeatedly nested for your highly-organized needs. (Or for organizing parts/arcs/chapters/etc. for your stories.) They can be bulk deleted by deleting the parent folder (the very first folder they’re all in).
When making a new document, you can either make a completely blank one or import a markdown (.md) file. Documents can be named here and renamed later. If you’re coming from Google Docs, you’ll have to use a desktop to download your documents as a markdown (.md) file in order to reupload it directly to Ellipsus. This is currently the only way to upload a file from elsewhere.
While writing, Ellipsus offers a focus mode (the cup icon) that will automatically hide all other panels/icons except for the outline (table of contents) and the icon to leave focus mode.
The other panels available are on the left- and right-hand sides of the screen. Both panels can be collapsed to increase screen space for the document. The right panel can be collapsed directly from within its additional menus through the arrow icon on the top left of the panel or returned to the expanded panel menu through the squares-in-a-square icon on the top right of the panel. It also has a keyboard icon (which the welcome doc calls a controller) to check available keyboard shortcuts, as well as a gear icon, both on the top right. (Will expand on the gear menu later.) The right panel also contains the “create a new draft” button, which becomes “compare changes” within drafts (expanded on later).
Formatting can be done through the bar on the bottom (basic* only) or through the formatting icon on the right panel. The default font is Literata and the default font size is 16pt. The default font color will change depending on your choice of light/dark mode, but you can pick from ten colors (nine, plus the default that changes per light/dark mode). If you don’t want to use the formatting bar/menu, markdown (like Discord) is also available for use while writing, and can be set to apply automatically.
Outline is simply a table of contents that allows you to jump between headers in your document. This makes it much easier to navigate a document, particularly if it’s long and you want to get from Point A to Point T but they’re a few tens of thousands of words apart (or more. Idk how much you write).
Find and replace is exactly that. It also has “match case,” “whole words only,” and “use regular expressions” toggles to better finess the find and replace experience.
Spellcheck will be elaborated on in the writing section.
Version history will open either the main document or the specific draft you’re on in a new page, where you can go between versions and pick on to overwrite with, if that’s what you want. I don’t fully understand how this works, but you can go through each day the document has been edited and pick a time you would like to replace the document with. These versions are saved at what appear to be every ten minutes of the clock, as every version of my stuff has shown only //:/0 am/pm as available within the version history.
Comments, chat, and collaborators will be expanded on in the collaborating section later.
Share and export is expanded on in the export section.
Document info becomes draft info when on a draft. This just gives you information like when it was made and last edited, as well as who edited it last and owns it (I think?). It also shows the word count, character count, and the estimated reading time.

The last option is “get support” and just opens to show you buttons to where to share feedback, find overviews/guides, or contact support from the team.
The left panel is where the main document and all associated drafts are kept. Remember to name your drafts appropriately so you don’t lose them; these can be duplicated, deleted, or renamed at any point.
*Basic formatting includes bold, italic, underline, and undo/redo. Ellipsus’s floating bar has these as well as a shortcut to the formatting menu, indent and unindent, and search. This is “basic formatting” for this review.
On Mobile
Since I first logged in on desktop, I’m not sure if this pops up when you do an initial login on mobile, but there was a pop-up that offered extra guidance in using the site on mobile, though I declined it. This is still a good feature, and not something you stumble on all the time. The site does look and work identically across devices, and the icons used are all identical. This is also a good thing.
On mobile, the basic formatting bar is moved to the top of the screen to account for pop-up keyboards, and side panels are hidden away. Thankfully, across screen sizes, the buttons for basic formatting aren’t absolutely tiny, though this does mean you may have to scroll to access parts of the basic formatting bar depending on the size of your display. The left panel has a “papers” icon on the top left, to the left of the cloud icon, and the right panel is within a “hamburger menu” (the three lines stacked on each other) on the top right, to the right of the bell icon (notifications for collaboration reasons).
Actually typing and working on mobile tends to be a bit buggy, but this is a beta so I’m not going to hold it against them. I’ll likely be using mobile as desktop through landscape full-screen on my iPad instead of vertically. The screen tends not to follow as you write, disappearing behind the basic formatting bar and/or the keyboard, which is a bit annoying. It says it will default to device settings with the double-spacing (expanded below) but doesn’t appear to always work on mobile.
Additionally
There are a few more settings on the right panel in the gear menu on the top right. These include features regarding smart formatting, collaboration, and display. This is the “editor settings” menu.
Smart formatting has quotes (from " to “ when typing quotation marks), ellipses (changing the three periods to one symbol …), markdown shortcuts (*and* such, like Discord), double-space period (tapping space twice will insert a period; unchecked will do as your device does), and en and em dashes (– and — from -; there is an option of “- - for —” or “- - for – as well as - - - for —”).
Collaboration has toggles for live cursors and collaborator avatars for when collaborators are viewing alongside you.
Display allows you to turn off the floating basic formatting bar (desktop/landscape only), turn on “invisible characters” (like paragraph symbols, spaces, etc.) or the word count, and is also where you can change from light/dark/system.
These additional settings (aside from light/dark/system) apply across your account, so you don’t have to do it per device as with other settings.
Actually Writing* With Ellipsus
*I used pre-written things for this review
Ellipsus synchronizes practically immediately. I don’t have anyone else to do this with, but between my own account on different devices, there’s a negligible amount of lag, which is notable considering my laptop is currently trying to die on me.* Different users** (or yourself on another device) are flagged with a colorful live cursor with their display name attached, which moves accordingly and swiftly to wherever they are in the doc, including if they’re navigating through the text using the arrows on their keyboard (for mobile hiding the keyboard might not remove your cursor, and for desktop opening a different window will not remove your cursor). When the other user** (or, again, yourself) highlights something, it is replicated in yellow for the other. The highlighting is surprisingly reactive and can follow per-letter (again, between me, myself, and I).
Spellcheck can add languages, has “accept” or “ignore all” options, offers multiple suggestions for (detected) misspellings, remembers what was “ignored” after leaving the document and returning. This has to be run through for every device you open the document on, which is a pain when you have fifty characters who have names the dictionary has beef with. The English dictionary appears to be on par with LibreOffice (disappointing) (the “se” in “per se” gets marked) (fanfiction will be painted in red). Detected misspellings (whether they are or aren’t) are both underlined and highlighted in red; the “first” detected misspelling with have both a highlight and an underline, but subsequent instances (“inactive” instances that you do not have selected) will only be underlined.
Additional languages currently available (Jan 2025) consist of: English (US, AUS, GB, CA), German, Spanish, French, Italian, Korean, Dutch, Russian, Polish, Portuguese, and Ukrainian.
If you want to change the font or text size, it currently (Jan 2025) applies across the entire document or draft’s corresponding paragraph style. This means the only way to have differently-sized portions in your document at this time is to have an individual paragraph with a different paragraph style (headings 1 through 4, paragraph/body, caption) applied, as they all have different font sizes associated with them.
There is also an optional word count displayed at the top of the screen next to the focus mode icon/notifications (depending on long or tall screen). It does display the word count with commas where appropriate.
My most favorite feature is that you can tab indent the start of your paragraphs. I’m not even kidding I love that so much. I don’t actually like the double-spacing (hitting the enter key twice for a new paragraph) format I do for fanfiction even though it looks better on AO3 that way, but having the ability to insert a tab indent just once and have it automatically carry through to each following paragraph…….. that’s so tasty. I’ve always hated writing on mobile because there’s usually no tab!!! It’s just there on Ellipsus!
Drafts are like a copy of the main document at the time of the draft’s creation. These are stored on the left panel menu and can be accessed simply by clicking them. This is useful more so for collaboration or when you’re struggling to pick an idea you like more. You can create these at any point, and merge them into the main document in order to make the content of the main document match that of the draft chosen.
Drafts can be compared to the main document through the “compare changes” page, accessible either from the “…” menu attached to the draft card on the left panel, or through the button on the right panel when you’re already in the draft. This “compare changes” page is where you’ll be able to do just that; additions are highlighted in green and anything removed is highlighted in red. On mobile you have to swap between the draft and the main document with the highlighted changes, but it’s laid out side-by-side on desktop. You can merge a draft with the main document from here.
You can also just make an empty draft and use it for things like notes and outlines and all that good stuff. They don’t have to be merged at any point. If you want a blank draft, though, you’ll either have to delete the whole doc within the draft or make a base blank draft at the start of your doc’s lifespan to later duplicate to edit when you need/want a blank draft.
*The responsiveness between me, myself, and I is notable because Google Docs lags so much for no reason, even if it’s just yourself on different devices in the same room. I’m doing this across three different browsers (Firefox, Safari, and DuckDuckGo) and three different devices (actively dying Windows laptop, iPhone, and iPad) it’s reactive and barely stutters, as opposed to how Google Docs needs to think about it across… itself (mobile app and Chrome browser, even!). Yes, I tested it to be sure.
**Disclaimer, again, I do not have friends to collaborate with to test otherwise.
Available Fonts
Here are all the currently available fonts (defaulted to 16pt when using the paragraph/body style). Photos* of just a few included because I’m doing this on mobile Tumblr and I can only use a few images so I’m picky. Also, this is all on dark mode, and the text color would be black if I were on light mode.
Baskerville
Caveat (#1)
Comic Neue
Courier Prime
EB Garamond
Inter
Literata (default font)
Merryweather
Monteserrat
Open Dyslexic
Raleway
Whatever this is? Doctor handwriting? Cursive Russian? (#2)
Roboto Mono
Sylexiad Serif (#3)
Ubuntu Mono



*Excerpt used is from the original concept Maddox and Li Hua, my ex-military dragon dad and his dragon daughter, were used in. It was originally in outside POV before I got bored with Darren. Sorry, Darren. (He’s still present later, just not as the POV character anymore.)
Importing
If you have a markdown (.md) file on hand, then go ahead.* Everything else you’re going to have to copy/paste in. Copy/paste will not automatically tab indent paragraphs like I extolled above even if there was a tab indent in the original text copied. The font will likely change to fit whatever you’re using on Ellipsus (it did for me between Liberation Serif -> Literata and Helvetica -> Literata) but it also won’t remove every single bit of formatting, so it’s not a completely exasperating exercise to copy/paste your works over. It won’t copy over things like headings properly, either, though that’s much less of a hassle than having to go back through and add all your italics back in.
For the sake of this review I did make my very first markdown (.md) file and... I honestly don't know what happened but about half of it was stuck in the "code" mode in the formatting section, which I couldn't figure out how to undo, outside of just copying the text (triple-clicking/tapping would select everything within the code block) and pasting it as plain text (ctrl/cmd+shift+v). I'm not sure you can paste as plain text on mobile (couldn't figure it out myself) so I, personally, am not going to be doing a whole lot of uploading previous stuff to Ellipsus. Other than this, importing a single-spaced (hitting the enter key once for a new paragraph) document will merge everything into a "single" paragraph, so I had to go through and separate all my paragraphs again so I could properly indent/unindent/apply other formatting as needed. I'll just completely re-type or batch copy/paste everything else in the future so I can have a better grip on the formatting.
*As stated way up at the start, you can upload a text file to Google Drive, open it in Docs (which makes into a .docx file, which they're working on allowing you to import as well), and then download that file as a .md file. This requires a desktop you can download/upload from. If you've never done this before, you can download as .md (and other file types) through the "File -> Download" section on an open document.
Exporting
This is accessed through the document directly instead of on the dashboard. It’s under “share and export” on the default right-hand panel menu.
You can “share” through two different methods. You can share a link to a document (logged-in users only or anyone with the link), which only allows for viewing the doc with zero editing abilities, and the entire document will be visible. The other option is a “snippet,” which is primarily what you’ll see pictures of when browsing the Ellipsus tag here; it’s a .png of a selected section of text* to create a slightly more interesting excerpt of what you’re working on. This helps your excerpt stand out without having to make it yourself. Example of a snippet with the default white background color:

(Snippets will export in only this font, but you can choose to keep any colored text.)
Exporting the entirety of the main document can be done by downloading as a PDF or markdown (.md) file. You can also copy it as HTML, markdown (.md), or rich text (.rtf). Most notable is a direct export to AO3 button! Ellipsus might tell you your blorbo’s name is spelled wrong, but it’ll let you upload your fic straight from the draft. ([Here’s] the official post about it.)
*You MUST make a selection of text in order to make a snippet; it won’t work if you don’t highlight anything for it to process. It also might be a bit slow, but a bit of patience will get you your .png to share.
Collaborating
… aha. I don’t know anyone currently using Ellipsus to review this with. Here’s paraphrased info off this [link].
Collaborating is done through email: your collaborator(s) have to have an Ellipsus account in order to actually work on the document. Inviting collaborators is done through entering their email, which will send them a link, which will bring them to the site where they will either make an account or log in to access the document. The owner of the document therefore knows the email of any and all collaborators, though other collaborators will only be able to see everyone’s display names. Collaborators can be given one of two roles with different permission levels: “can merge” means they can merge drafts into the main document, edit the main document, create drafts, as well as everything the next level can do; “can edit” can create drafts, edit existing drafts, and use the chat/comments features. Collaborators cannot invite or manage collaborators. Document owners can remove collaborators or change their role/access level at any time.
Information from Discord says this might be laggy and buggy, but the staff is looking into it.
Comments can be left through highlighting parts of the doc/drafts. Chat is a live chat to use while working together, or something, because I can’t test that.
Extras!
Their Discord server consists mostly of adults (age 18 or over) and offers opportunities to find collaborators of all stripes that also use Ellipsus. It has nearly 1600 members at the time of writing, though not everyone has chosen their roles, but of the approximately 500 reactions on the bot’s age role message, only nearly 40 chose the “under 18” role. It is a fairly active social space for the size, and doesn’t have an absolute hoard of channels. There’s even an art channel, with the description reading “original, human-powered art or credited or linked to the respective artist.”
They have a [blog] with resources/templates you can use to get started. You have to scroll through to find them since you can’t sort by the resource tag, but they’re pretty good templates for worldbuilding, story planning, and character information. I would recommend saving these as individual docs on their own and then copy/pasting the templates into the drafts of your stories to keep the information connected to the main doc you’re using it for. (Don’t forget to appropriately name all your drafts so you don’t lose anything.)
They have been in open beta since May 2024. There were apparently nine months of closed beta before this. They are also a former sponsor of NaNoWri(teNo)Mo(re) but [dropped them] when they made the stupid announcement about AI (2024).
Yes, you can use emojis on Ellipsus. Yes, you can have your leads text 🥴 to each other.
They are ellipsus_writes on Twitter/X and TikTok, ellipsuswrites on Instagram, and ellipsus-writes here on Tumblr (as mentioned way back at the start).
#ellipsus#BOUNCY. REVIEW.#if you wanna help me test ellipsus's collaborative abilities hmu asks and dms are open#review#site review#writers on tumblr#writeblr#queer writers#writer stuff#original writing#writing#writers#fanfic#fanfic writing#writing community#writerscommunity#writers community
6 notes
·
View notes
Text
just a little coco redesign :3c

link if you wanna see the old design
not gonna post the full details of the design here cause i dont think that rlly matters lol also don't mind the boots i cannot draw anything past the knees like at all 💀💀
ik i wrote lil drabbles of them from time to time but this post will be the "official" one introducing them since i never rlly gave a proper introduction
as a heads up i'll be using both commandant and skk interchangeably bc i'm consistently inconsistent 👍
basic info
name: coco
prns: they/them
vocation: cerberus commandant
about
always carries chocolate wherever they go and would even snack on it while carrying out missions on earth.
most people would often know if coco is around by the sudden scent of chocolate in the air. vera, 21, and noctis are the only people constructs that associate coco's scent w smth other than chocolate
is often hidden away in their squad's lounge area when on standby for missions, usually handling any sort of files or paperwork
if they're not in the lounge, then they're in the library either working or conversing with noan or simultaneously doing both
expresses their gratitude through actions and gifts rather than words
often seen as very reserved due to only speaking when spoken to when around most people that aren't in their squad
with that being said it's rumored that if you bad mouth any of the cerberus members, whether you noticed their presence (during the bad mouthing) or not they will haunt you in the worst ways possible
another rumor has it that while their smile is generally more comforting than the uh... other members of cerberus.... their smile when confronting those who slander cerberus is more terrifying than the trio combined
how they became cerberus' skk
formerly gray raven's skk, vera carried out her plans of kidnapping coco and make them cerberus' skk, tho rather than coco trying to fight against it, they willingly complied and offered to help w the coverup, even as far as talking to murray directly abt transferring him to be gray raven's skk so that he can finally be alongside lee in the closest way possible. this whole plan took place right around chapter 15, the last spark, after skk successfully returns from atlantis
tl;dr rozen's secrets 10 and 12 came true, murray and gr skk just switch places lol
relationship w vera
vera would always try to tease and make lies to see some sort of idiotic expression on coco's face, but they picked it up rather quickly and would either play along or tease back
vera tends to give most of the paperwork to coco just cause she doesnt want to do it
even tho the two of them have looked at each other's files and vera even going as far as hunting down every little detail abt coco's past, neither of them could really understand each other, nor do they really have the social skills to get to properly have that conversation
despite not really knowing each other to the fullest, the both could at least agree on maintaining the existence of cerberus and their teammates
vera often worries abt coco, but would never outright say it. its not everyday you see an f.o.s. chief be so willing to break every rule they learned when training to be a commandant. she often thinks they're just as reckless as noctis at times if not more than him
despite everything, its still a mystery to vera of why coco was so willing to transfer out of gray raven
relationship w 21
took the most time to adjust to coco
given cerberus now has an on-field skk and 21 needing to be more closely monitored than the others, it took a while for her to be comfortable w having constant m.i.n.d. connections w coco
once 21 fully became comfortable w their presence, she'd ask them to join her to watch animal documentaries
indulges 21 in her story writing, giving her books and movies from the wgaa for inspiration
coco basically semi-treats 21 like she's their daughter
relationship w noctis
they're married :) /hj
noctis was the most excited out of the 3 when coco officially became cerberus' skk
also was the least obedient when it came to listening to coco due to his very "lone wolf" mindset at times
to get him to listen, coco decided to attach a leash on him, in which vera's initial reaction was of both amusement of coco's stupidity and disbelief that it'd actually work
much to either of their surprise, it did work 💀 which made vera and 21 laugh their asses off over how noctis could be easily tamed w a rather small and albeit dumb trick
nowadays coco carries the leash as an intimidation factor for noctis to behave
out of the 3, noctis is the one that spends the most time w coco, considering his reputation of being obnoxious has led to him being held back on quite a few occasions and have coco watch over him while vera and 21 go on missions as per nikola's orders. during those times, coco would need to do a remote connection and would update noctis over what's going on
calls each other "partner" when not on missions/formal occasions
cerberus on-field
while coco is on-field alongside their teammates, they tend to let the trio complete missions in whatever method they're most comfortable w, only intervening when asked by the members or if a certain method will create too drastic of a casualty
coco's main job is to give a brief overview of the mission and clean up the trio's mess/deal w the aftermath, they'll often do other small tasks in the meantime while the trio handles the bigger (and supposedly more "fun") tasks
a lot of other commandants would comment abt this tactic being "lazy" since coco doesn't appear to do all that much on the surface, only for coco to retort w "ok so why don't you be cerberus' commandant for a day and show me how i'm supposed to act" with a shit-eating grin on their face which makes the others immediately take back their statement and shut up abt how coco operates as a commandant. the trio (if around) would also chime in and scare the others even more than what coco initially intended
some other bits that idk where to categorize them in
earpiece would almost always have music playing
coco's reputation slowly deteriorated over time. a once beacon of hope now often seen as someone who's fallen from grace
the unapproachable nature of cerberus made people believe that coco, as a former gray raven commandant, would try to "fix" them, only to find out that coco fully embraces and encourages cerberus' behavior, which made the whole squad more terrifying than before
coco now often refuses to partake in any sort of mission that would make them go solo (i.e. constructs from cerberus wont be joining directly alongside them), stating things like "there are many other commandants out there that can easily perform just as well if not better than them" and "only cerberus can fully guarantee their safety"
#i could totally write more but i'll stop myself while i still can lmao#pgr#pgr oc#pgr commandant#my ocs :]
15 notes
·
View notes
Text
Birth Injuries Caused by Improper Pitocin Use Georgia Legal Insights

When you are dealing with a birth injury, especially one caused by improper Pitocin use, it is natural to feel overwhelmed, confused, and worried. If you are here today, you might be facing a difficult situation. Pitocin, a drug commonly used to induce or strengthen labor, can sometimes cause complications when not administered correctly. These complications can lead to serious injuries for both the baby and the mother. If you believe that Pitocin use during labor led to harm, you may be wondering what steps to take next. Understanding your legal options can be complex, but rest assured that you do not have to face this journey alone. We are here to help guide you through every step of the process and work toward achieving a successful resolution for your case.
What Is Pitocin and How Does It Work
Pitocin is a synthetic form of the hormone oxytocin, which plays a crucial role in labor by stimulating contractions. Healthcare providers often use Pitocin to induce or speed up labor in women who are experiencing complications or delays during childbirth. While Pitocin can be beneficial in many situations, its improper use can have severe consequences. The dosage and timing of Pitocin are critical. Too much Pitocin can overstimulate the uterus, causing prolonged contractions, which can affect the baby’s oxygen supply and result in fetal distress. In such cases, birth injuries may occur, including brain damage, cerebral palsy, or other neurological conditions.
Common Birth Injuries Linked to Pitocin Misuse
When Pitocin is not administered properly, the consequences can be devastating. The baby may suffer from a lack of oxygen, leading to serious conditions like hypoxic-ischemic encephalopathy (HIE), a brain injury caused by oxygen deprivation. Other common birth injuries that can be caused by improper Pitocin use include shoulder dystocia, a condition where the baby’s shoulders get stuck during delivery, and uterine rupture, which occurs when the uterus tears during labor. These injuries can cause long-term health problems and may require extensive medical treatment and care for years to come.
In addition to the physical toll, families can experience emotional and financial hardships due to these injuries. Many parents face medical bills, ongoing therapy costs, and emotional distress as they try to care for a child with a birth injury. The effects can be life-changing, and it is crucial to understand what went wrong during labor to seek justice for the harm caused.
Understanding Medical Negligence and Birth Injuries
In Georgia, medical negligence is a legal term used to describe situations where a healthcare provider fails to meet the accepted standard of care, leading to harm. In the case of Pitocin use, if the doctor, nurse, or hospital staff administers the drug incorrectly or fails to monitor the mother and baby appropriately during labor, they may be liable for medical negligence. For instance, if the medical team does not adjust the Pitocin dosage based on the mother’s and baby’s responses or fails to notice signs of fetal distress, it could be considered negligent.
If you believe that your child’s birth injury was caused by improper Pitocin use, it is essential to gather evidence to support your claim. This may include medical records, testimonies from healthcare professionals, and expert analysis of what went wrong during labor. Establishing a clear connection between the Pitocin misuse and the injury is critical to pursuing a legal case.
Legal Options for Families Affected by Birth Injuries in Georgia
If you suspect that improper Pitocin use contributed to your child’s birth injury, you may have the right to file a medical malpractice lawsuit. This type of lawsuit allows you to seek compensation for the damages caused by medical negligence. Compensation can cover medical expenses, long-term care, lost wages, pain and suffering, and other costs associated with the injury.
However, pursuing a medical malpractice case is not easy. Birth injury cases often involve complex medical issues and require extensive legal knowledge to navigate. In Georgia, you must meet specific requirements to file a medical malpractice lawsuit, including proving that the healthcare provider’s actions were negligent and that this negligence directly resulted in harm. The law also imposes time limits on when you can file a lawsuit, so it is crucial to act quickly.
How an Attorney Can Help You Navigate Your Birth Injury Case
A skilled attorney can be instrumental in helping you pursue justice for a birth injury caused by improper Pitocin use. They will work with medical professionals to investigate your case, gather the necessary evidence, and determine whether medical negligence occurred. An attorney will also handle the legal aspects of your case, including filing the necessary paperwork, negotiating with insurance companies, and representing you in court if needed.
While no amount of compensation can undo the harm caused by a birth injury, a successful case result can provide financial relief and help ensure that the responsible party is held accountable for their actions. Your attorney will fight for your family’s rights and work tirelessly to secure a favorable outcome.
Why You Should Choose a Georgia-Based Firm for Your Birth Injury Case
When dealing with a birth injury caused by improper Pitocin use, it is essential to work with a law firm that understands Georgia’s laws and the complexities of medical malpractice cases. An experienced attorney from a Georgia-based firm will be familiar with local regulations, court procedures, and the challenges unique to the state. They will have the resources and knowledge needed to help you navigate the legal process effectively.
At Keenan Law Firm, we understand the emotional and financial burdens that birth injuries can place on families. Our team is committed to providing compassionate legal representation to those affected by medical malpractice. We are here to help you explore your legal options, pursue justice, and fight for the compensation you deserve. If you believe your child’s birth injury was caused by improper Pitocin use, don’t hesitate to reach out to us for a free consultation.
If your child has suffered a birth injury due to improper Pitocin use, you do not have to face this challenging time alone. Keenan Law Firm is here to offer you the support and guidance you need. Our experienced attorneys will review your case, explain your legal options, and work tirelessly to ensure you get the compensation you deserve. Contact us today for a free consultation and let us help you take the first step toward justice for your family.
0 notes
Text
Your phone is a mess. Let Xender’s AI fix it in seconds.
Transform your visuals effortlessly with the xender’s AI-features that allows you to quickly erase the duplicate photos in your device of your images. This is Ideal for users’s devices Trash box cleaner. Beyond photo management, Xender also allows users to effortlessly transfer files from their phone to PC and vice versa. This feature is invaluable for those looking to back up important files or share large media without the hassle of cables or cloud storage.

Lets explore how it works:
Before try to step by step one thing is important ;xender has its own privacy rule for user that is Privacy Benefits One of the standout features of Xender’s Photo AI is that all processing occurs locally on your device. This means:
1-No Cloud Uploads: Your photos never leave your device, protecting your privacy and sensitive information.
2-Data Security: By keeping photos on your device, you reduce the risk of unauthorized access.
So, come to Next ; Connect and Manage Photos on a your pc
Start by connecting your phone to your computer. With Xender, you can manage your photos on a larger screen, making it easier to navigate and organize your library.
Step 1 - Open Xender: Launch the Xender app on your phone and PC.
Step 2 - Go to Send PC Tab: Select the "Send PC" tab on your phone, and find the Photo AI section in the left menu.
Feature 1: Duplicate and Similar Photo Detection
One of the standout features of Xender’s Photo AI is its ability to identify and help you delete duplicate and similar photos. The process is quick and easy:
Step 1- Select Photos: Browse through your library and select the duplicate photos.
Step 2- Delete with Ease: With just a few taps, delete these unwanted duplicates. They’ll disappear from your phone in no time!
Xender’s AI tools are designed to save the day by streamlining your photo management.

Feature 2: Wireless Management
What’s even better? You can manage your phone’s photos wirelessly through Xender. This means:
Step 1 - No Cloud Uploads: Your photos stay on your phone, eliminating privacy concerns associated with cloud storage.
Step 2 - Easy and Convenient: Manage your photos without the hassle of cables or complex setups.
Feature 3: People and Avatar Grouping
Finding photos of your friends, family, or pets has never been easier! Xender’s AI smartly groups photos by people, allowing you to locate cherished memories with just a few clicks.
Smart Grouping: The AI identifies faces and organizes your photos, making it a breeze to find pictures of your bestie or your favorite photo collections.
Must be try It Today!
Maybe you’re an ordinary person but who have a smartphone and also just fun with your selfie pictures or professional photographer Xender’s AI image management feature is your new best friend. It’s designed to make your photo library look fresh and organized, saving you time and effort. That’s why xender pushes you to download and use it properly as one of your life's easier apps.
www.xender.com
google play link: https://play.google.com/store/apps/details?id=cn.xender&hl=en_US
App store:https://apps.apple.com/us/app/xender-file-share-share-music/id898129576
0 notes
Text
What are the Most Common SEO Errors That Damage Your Website Ranking? Search Engine Optimization (SEO) plays a vital role in generating organic traffic and enhancing online presence. But even small SEO errors can harm your website's ranking and keep you away from your target audience. To guarantee long-term success, companies need to steer clear of these frequent SEO errors. Hiring the top Digital Marketing agency can assist in recognizing and rectifying these errors to attain greater search rankings and long-term growth.
Overlooking Keyword Research One of the largest SEO blunders is neglecting to perform adequate keyword research. Without properly targeting keywords, your site could:
Rank for irrelevant search queries. Fail to compete with market leaders. Lose high-intent traffic. To maximize your SEO approach, utilize long-tail keywords, prioritize user intent, and observe search trends. The best Digital Marketing agency guarantees keyword strategies harmonize with your audience's demands.
Poor Quality Content Search engines rank high-quality, informative content most. Typical content-related SEO errors are:
Publishing thin or duplicate content. Writing unoptimized content. Not paying attention to content refreshes and updates. Businesses must produce valuable, unique, and engaging content that meets the needs of the user and uses related keywords naturally to enhance rankings.
Overlooking On-Page SEO On-page SEO is important in ranking. Most businesses overlook optimization of aspects like:
Title Tags & Meta Descriptions: These must be strong and keyword-dense. Header Tags (H1, H2, H3): Well-organized headings enhance readability and SEO. Internal Linking: Linking associated pages enhances site navigation and authority. A well-optimized site allows search engines to crawl and index pages quickly, enhancing ranking potential.
Slow Website Speed Website speed is a key ranking factor. Slow sites suffer from:
Higher bounce rates as users exit because of bad performance. Lower conversion and engagement rates. Lower search engine rankings. Optimize images, implement caching, and use a content delivery network (CDN) to increase website speed. The ideal Digital Marketing agency guarantees optimal performance for improved user experience and SEO rankings.
Not Having a Mobile-Friendly Website Since most web traffic is from mobile devices, a non-responsive site can severely damage rankings. Problems include:
Subpar user experience on smaller screens. Lower search rankings as a result of Google's mobile-first indexing. Increased bounce rates with lost conversions. Make your website mobile-friendly with a responsive design and quickly loading pages.
Failing to Address Technical SEO Problems Technical SEO issues will hinder search engines from fully indexing your site. Some of these common mistakes include:
Broken links and 404 errors. Bad URL structure that lacks pertinent keywords. Missing XML sitemaps and robots.txt files. Periodic SEO audits may also be used to detect and correct these technical problems to enhance website performance.
Inadequate Backlinks from High-Quality Sites High-quality backlinks from reputable sites convey trust and authority to search engines. Some common backlink errors are:
Dependence on low-quality or spam backlinks. Inadequate external links from quality sites. Overlooking link-building efforts. The top Digital Marketing agency practices ethical and strategic backlink building to build domain authority and rankings.
Over-Optimizing or Keyword Stuffing Keywords are crucial, but loading content with too many keywords damages SEO. Search engines punish:
Keyword stuffing that breaks up readability. Unnatural keyword usage that compromises content flow. Including irrelevant keywords for the sake of ranking. Emphasize natural, user-centric keyword inclusion for improved search engine rankings.
Failing to Optimize for Local SEO For local businesses catering to local customers, neglecting local SEO can prove expensive. The following mistakes are typical:
Failure to optimize Google My Business (GMB) listings. Missing local keywords in website content. No customer reviews and local citations. A good local SEO plan guarantees visibility on local searches and Google Maps listings.
Not Tracking SEO Performance SEO demands constant monitoring and optimization. Numerous businesses do not monitor:
Keyword rankings and organic traffic patterns. Bounce rates and user engagement rates. Competitor SEO plans and updates. Employing SEO analytics tools enables measuring performance and perfecting strategies for improved outcomes.
Conclusion Avoiding these SEO errors is vital for enhancing website rankings and online presence. From effective keyword research to technical SEO optimization, all SEO elements are vital to search engine success.
By collaborating with the most efficient Digital Marketing firm, companies are able to recognize and rectify SEO mistakes, use best practices, and work towards long-term growth. An effective SEO strategy guarantees increased traffic, more engagement, and improved conversion rates—making it a crucial element of digital marketing success.
Search Engine Optimization (SEO) plays a vital role in generating organic traffic and enhancing online presence. But even small SEO errors can harm your website's ranking and keep you away from your target audience. To guarantee long-term success, companies need to steer clear of these frequent SEO errors. Hiring the top Digital Marketing agency can assist in recognizing and rectifying these errors to attain greater search rankings and long-term growth.
Overlooking Keyword Research One of the largest SEO blunders is neglecting to perform adequate keyword research. Without properly targeting keywords, your site could:
Rank for irrelevant search queries. Fail to compete with market leaders. Lose high-intent traffic. To maximize your SEO approach, utilize long-tail keywords, prioritize user intent, and observe search trends. The best Digital Marketing agency guarantees keyword strategies harmonize with your audience's demands.
Poor Quality Content Search engines rank high-quality, informative content most. Typical content-related SEO errors are:
Publishing thin or duplicate content. Writing unoptimized content. Not paying attention to content refreshes and updates. Businesses must produce valuable, unique, and engaging content that meets the needs of the user and uses related keywords naturally to enhance rankings.
Overlooking On-Page SEO On-page SEO is important in ranking. Most businesses overlook optimization of aspects like:
Title Tags & Meta Descriptions: These must be strong and keyword-dense. Header Tags (H1, H2, H3): Well-organized headings enhance readability and SEO. Internal Linking: Linking associated pages enhances site navigation and authority. A well-optimized site allows search engines to crawl and index pages quickly, enhancing ranking potential.
Slow Website Speed Website speed is a key ranking factor. Slow sites suffer from:
Higher bounce rates as users exit because of bad performance. Lower conversion and engagement rates. Lower search engine rankings. Optimize images, implement caching, and use a content delivery network (CDN) to increase website speed. The ideal Digital Marketing agency guarantees optimal performance for improved user experience and SEO rankings.
Not Having a Mobile-Friendly Website Since most web traffic is from mobile devices, a non-responsive site can severely damage rankings. Problems include:
Subpar user experience on smaller screens. Lower search rankings as a result of Google's mobile-first indexing. Increased bounce rates with lost conversions. Make your website mobile-friendly with a responsive design and quickly loading pages.
Failing to Address Technical SEO Problems Technical SEO issues will hinder search engines from fully indexing your site. Some of these common mistakes include:
Broken links and 404 errors. Bad URL structure that lacks pertinent keywords. Missing XML sitemaps and robots.txt files. Periodic SEO audits may also be used to detect and correct these technical problems to enhance website performance.
Inadequate Backlinks from High-Quality Sites High-quality backlinks from reputable sites convey trust and authority to search engines. Some common backlink errors are:
Dependence on low-quality or spam backlinks. Inadequate external links from quality sites. Overlooking link-building efforts. The top Digital Marketing agency practices ethical and strategic backlink building to build domain authority and rankings.
Over-Optimizing or Keyword Stuffing Keywords are crucial, but loading content with too many keywords damages SEO. Search engines punish:
Keyword stuffing that breaks up readability. Unnatural keyword usage that compromises content flow. Including irrelevant keywords for the sake of ranking. Emphasize natural, user-centric keyword inclusion for improved search engine rankings.
Failing to Optimize for Local SEO For local businesses catering to local customers, neglecting local SEO can prove expensive. The following mistakes are typical:
Failure to optimize Google My Business (GMB) listings. Missing local keywords in website content. No customer reviews and local citations. A good local SEO plan guarantees visibility on local searches and Google Maps listings.
Not Tracking SEO Performance SEO demands constant monitoring and optimization. Numerous businesses do not monitor:
Keyword rankings and organic traffic patterns. Bounce rates and user engagement rates. Competitor SEO plans and updates. Employing SEO analytics tools enables measuring performance and perfecting strategies for improved outcomes.
Conclusion Avoiding these SEO errors is vital for enhancing website rankings and online presence. From effective keyword research to technical SEO optimization, all SEO elements are vital to search engine success.
By collaborating with the most efficient Digital Marketing firm, companies are able to recognize and rectify SEO mistakes, use best practices, and work towards long-term growth. An effective SEO strategy guarantees increased traffic, more engagement, and improved conversion rates—making it a crucial element of digital marketing success.
0 notes
Text
Can I Add a Company Logo Inside a QR Code?
A QR code is a powerful tool that allows businesses to share information quickly and efficiently. Whether it’s a link to a website, a digital business card, or a promotional campaign, QR codes have become a staple in modern marketing. Many companies look for ways to enhance their branding by customizing QR codes, including adding their company logo inside the code.
The good news is that you can add a logo inside a QR code, but it requires careful design to maintain scannability. This article explores how to insert a logo into a QR code, the benefits of doing so, and best practices to ensure it remains functional.

1. Can a QR Code Contain a Logo?
Yes, a QR code can contain a logo or an image in the center without losing functionality. Many QR code generators offer customization options, including logo insertion. However, it is important to ensure that the logo placement does not interfere with the essential scanning elements of the code.
Our Socials:
Facebook
Twitter
Pinterest
YouTube
TikTok
2. How to Add a Logo to a QR Code
Step 1: Choose a QR Code Generator
There are various online QR code generators that support logo insertion. Look for a tool that allows you to upload and embed your company logo while maintaining high-quality resolution.
Step 2: Generate the QR Code
Before adding a logo, first, create a QR code with the desired URL, text, or other data. Some generators allow you to preview the QR code with the logo before finalizing it.
Step 3: Upload Your Logo
Most QR code customization tools have an option to upload a logo. The logo is usually placed in the center of the QR code while keeping the outer scanning patterns intact.
Step 4: Adjust the Logo Size and Position
Ensure that the logo is small enough not to obstruct key QR elements but large enough to be visible. A properly placed logo enhances branding without affecting scan reliability.
Step 5: Test the QR Code
Before using the customized QR code, test it with multiple devices and scanning apps to confirm that it works as intended.
3. Why Add a Logo to a QR Code?
Adding a company logo to a QR code provides several benefits:
Enhances Brand Recognition – A branded QR code helps customers associate the code with your company.
Increases Trust and Engagement – A logo makes the QR code look more professional and trustworthy, encouraging more scans.
Differentiates from Generic QR Codes – Custom QR codes stand out from standard black-and-white versions.
4. Best Practices for Adding a Logo to a QR Code
Keep the Logo Small
A QR code should have enough space for scanning. A small logo ensures the essential scanning patterns remain clear.
Use High-Contrast Colors
A QR code works best when there is a strong contrast between the foreground and background. Choose colors that make both the QR pattern and the logo clearly visible.
Avoid Covering Key QR Code Elements
A QR code contains three large position markers (corner squares) and smaller data patterns. The logo should not obscure these important elements.
Use Error Correction for Better Scannability
Many QR codes have built-in error correction, which allows scanners to read the code even if part of it is blocked. When adding a logo, ensure the error correction level is high enough to compensate for the missing data.
Test the QR Code on Multiple Devices
Always scan the customized QR code using different smartphones, tablets, and QR scanning apps. If any issues arise, adjust the logo placement or size accordingly.
5. Can a Logo Affect QR Code Scannability?
Yes, adding a logo can impact scannability if not done correctly. The most common mistakes include:
Placing the logo over critical QR elements
Using a low-contrast color scheme
Making the logo too large, reducing the readable QR pattern
To avoid these issues, always test the QR code before printing or distributing it.
6. What File Formats Work Best for QR Code Logos?
When adding a logo to a QR code, consider using high-quality file formats such as:
PNG – Supports transparency and high resolution.
SVG – Ideal for vector-based images, ensuring scalability without losing quality.
JPG – Works for simple images but may lose quality when resized.
Using a high-resolution image prevents the logo from appearing blurry when printed or enlarged.
7. Where Can Branded QR Codes Be Used?
A QR code with a logo can be used in various settings, including:
Marketing and Promotions
Businesses place branded QR codes on flyers, posters, and product packaging to direct customers to websites, promotions, or sign-up pages.
Business Cards
A professional QR code on a business card allows people to quickly access contact details or social media profiles.
Retail and Restaurants
Many stores and restaurants use branded QR codes on menus, receipts, and storefronts to engage customers.
Event Tickets and Invitations
Custom QR codes add a personalized touch to event tickets and invitations, leading guests to RSVP pages or event details.
8. Can I Customize the Entire QR Code Along with the Logo?
Yes, in addition to adding a logo, you can customize the QR code with different colors, rounded edges, and patterns. However, it’s essential to maintain:
High contrast between the QR pattern and background
Clear visibility of the three corner markers
Consistent shape and alignment for easy scanning
9. Are There Any Risks to Using a Branded QR Code?
While adding a logo to a QR code offers many benefits, some potential risks include:
Scanning Issues – If not tested properly, a customized QR code may not work across all devices.
Brand Misuse – If your QR code is widely shared, ensure it links to a permanent, trustworthy destination to avoid misinformation.
Printing Errors – A QR code may lose quality if resized improperly. Always use high-resolution formats for printing.
Conclusion
Yes, you can add a company logo inside a QR code, and doing so can enhance branding, increase engagement, and build trust. However, it’s important to follow best practices to ensure the QR code remains functional. By keeping the logo small, maintaining high contrast, and testing the code on multiple devices, businesses can create an attractive and scannable QR code that represents their brand effectively.
0 notes
Text
Audio Share Links: An Expert Overview
The digital age has revolutionized the way audio content is shared and consumed. From podcasts and music to recorded lectures and business presentations, audio share links have become an important tool for individuals and organizations. These links provide seamless access to audio files, allowing users to stream or download content with ease. In this article, we will discuss the importance, benefits, and best practices associated with audio share links.
The Importance of Audio Share Links
Audio share links are used for multiple purposes in various domains. Content creators, educators, businesses, and social media influencers use it to distribute audio files efficiently. Whether a musician is sharing their latest song, a business is delivering a webinar, or a journalist is publishing an exclusive interview, audio share links make content easily accessible.
It also improves collaboration as team members can easily share voice notes and recorded meetings. This method eliminates the need for bulky email attachments and makes audio files available on demand from anywhere.
Key Benefits of Audio Share Links
Convenience and Access: Audio share links allow users to access files from anywhere with an internet connection, eliminating the need for physical storage devices.
Efficient distribution:
Instead of sending files manually, users can share a single link, making the process faster and more efficient. Security and privacy controls: Many platforms offer customizable security settings, such as password protection, expiration dates, and access restrictions.
Cross-platform compatibility:
Recipients can listen to shared audio files on a variety of devices, including smartphones, tablets, and computers, ensuring a seamless experience. Cloud storage integration: Many audio sharing platforms store files in the cloud, reducing the risk of data loss and allowing for automatic backups. Popular platforms for audio sharing links Several platforms make it easy to share audio files with unique features tailored to different use cases. SoundCloud: Ideal for musicians and podcasters, it offers public and private sharing options.
Google Drive and Dropbox:
Suitable for businesses and educational institutions that need secure file storage and sharing. Spotify for Podcasts: A platform for professional content creators who want to distribute their podcasts widely.
WhatsApp and Telegram:
Fast and convenient real-time peer-to-peer audio sharing. WeTransfer: An efficient tool to send large audio files without registering an account. Best practices for sharing audio links To get the most out of your audio sharing links, consider these best practices: Optimize file format and size.
If you need to audio sharing links kindly check out our web site.
Use a widely supported format (MP3, WAV, etc.) and compress your files if necessary to improve loading times.
Use descriptive file names:
A clear title helps recipients understand the contents before opening the file.
Apply security measures:
Protect sensitive audio files with a password or expiration date.
Test links before sharing:
Make sure links are accessible and work properly before sending them to recipients.
0 notes
Text
The Step-by-Step Guide to Submit Your Track on iTunes for Maximum Exposure
Independent musicians are always looking for ways to get their music heard by as many people as possible. With countless streaming platforms available, it can be overwhelming to know where to start. Among the most prominent platforms, iTunes stands out as an invaluable tool for gaining exposure. This article will guide you through the step-by-step process of submitting your track to iTunes and help you understand how you can maximize your exposure to potential fans around the world.
Why Submit Your Track on iTunes?
Before diving into the submission process, it’s important to understand why iTunes is such a powerful platform for independent artists. iTunes is one of the largest and most trusted digital marketplaces in the world, with millions of users across the globe. It offers musicians the chance to reach a vast audience and gain exposure to new listeners who may not have discovered their music otherwise.
One of the key reasons artists should consider submitting their tracks on iTunes is the platform’s reputation. Being featured on such a high-profile site instantly elevates your credibility as a musician. Additionally, iTunes integrates with Apple Music, giving you access to millions of subscribers who can stream your track on-demand. This combination of marketplace and streaming services gives independent artists the best chance to connect with listeners and grow their fanbase.
Moreover, iTunes provides valuable tools for tracking your performance, making it easier to understand which tracks resonate with your audience. These insights can help you refine your marketing strategies and make data-driven decisions to improve your career.
How to Submit Your Track on iTunes
The process of submitting your track on iTunes isn’t as complicated as it might seem. With the right tools and services, you can get your music uploaded and ready for millions of potential listeners. Here's how you can do it:
Step 1: Choose a Distribution Service
To get your track on iTunes, you’ll first need to choose a digital distribution service. There are several options available, but Deliver My Tune is an excellent choice for independent artists. This service acts as a bridge between your music and major platforms like iTunes, ensuring that your track is properly formatted and uploaded.
Once you’ve selected a distribution service, you’ll need to sign up and create an account. The process is simple and user-friendly, and you can often complete it in just a few minutes. After signing up, you’ll be asked to upload your music files, along with essential information like track titles, artist names, and genre. Some services also require you to upload album artwork and other details, which helps your music stand out on the platform.
Step 2: Upload Your Music
After you’ve set up your account, you’ll need to upload your track to the chosen distribution service. This is where the magic happens: your music is sent directly to iTunes and other major platforms. Be sure to upload high-quality audio files and ensure that your album artwork meets the platform's standards. iTunes is known for its emphasis on high-quality audio, so making sure your files are top-notch will enhance your credibility as an artist.
Step 3: Fill in Your Metadata
Metadata refers to all the details associated with your track, such as the song title, artist name, album name, and more. Providing accurate and detailed metadata is crucial for getting your music discovered on iTunes. For instance, you should ensure that your genre is specified correctly so that iTunes can categorize your music and recommend it to the right audience.
Moreover, it’s important to fill out your artist bio and links to your social media profiles. This information helps listeners get to know you better and can lead to increased engagement. If you have a website or other online presence, be sure to link it in your artist profile as well.
Step 4: Submit Your Track
Once all the information is filled out, it’s time to submit your track to iTunes. This typically involves clicking a button that sends your track for approval. Deliver My Tune will help ensure that all your files and metadata are properly formatted before submission, saving you time and hassle. It’s important to note that iTunes will review your submission, and approval can take anywhere from a few days to a week.
If your track meets the platform’s guidelines and quality standards, it will be approved and made available for purchase and streaming. This is where the real work begins—ensuring that your music gets heard.
Maximizing Your Exposure on iTunes
Getting your music on iTunes is only part of the equation. To truly maximize your exposure, it’s important to take advantage of the platform’s promotional tools and algorithms.
Promote Your Track via Social Media
One of the best ways to get noticed on iTunes is by promoting your music on social media. The more traffic and engagement your track gets, the more likely it is to be recommended to other users by iTunes’ algorithm. Post about your release on Facebook, Instagram, Twitter, and TikTok, and encourage your followers to share it. The more buzz you can generate around your track, the better.
Utilize iTunes Playlists
iTunes features several curated playlists that are designed to highlight new and popular tracks. While it’s not guaranteed that your track will be included, getting featured on one of these playlists can provide a huge boost in exposure. To increase your chances of being added, reach out to curators or use a distribution service like Deliver My Tune, which can help pitch your music to the right playlist editors.
Leverage Apple Music’s ‘For You’ Section
Another key feature of iTunes is its integration with Apple Music’s "For You" section, where users are recommended songs based on their listening habits. If your track gains traction, it could be featured in this section, providing you with exposure to a wider audience. To increase your chances of being featured, encourage your fans to add your song to their playlists and share it with their networks.
Conclusion
Submitting your track on iTunes is one of the most powerful ways to gain exposure in the music industry. By following the simple steps outlined above and leveraging the platform’s features, you can increase your chances of getting discovered and growing your fanbase. Whether you’re an up-and-coming artist or a seasoned professional, iTunes offers the tools and reach you need to succeed. With services like Deliver My Tune, the process of submitting your music to iTunes becomes seamless, and the potential for exposure is limitless. So take the leap, submit your track, and start building your presence on one of the world’s most iconic music platforms.
Related Articles:
For further reading, explore these related articles:
Submit your track on iTunes with 100% royalties
Submit your track on iTunes without paying fees
Submit your track on iTunes on multiple platforms
Submit your track on iTunes to get paid
For additional resources on music marketing and distribution, visit DMT RECORDS PRIVATE LIMITED.
0 notes
Text
Unlocking Success as an Independent Artist in the Digital Age
The rise of digital platforms has transformed the music industry, giving independent artists unprecedented opportunities to share their work and reach global audiences. Gone are the days when musicians needed a major record label to gain exposure. Now, platforms like iTunes, Spotify, and YouTube have leveled the playing field, empowering creators to take control of their careers.
Among these platforms, iTunes stands out as a premier destination for music and video content, offering a professional space where independent artists can showcase their creativity. Whether you're an up-and-coming artist or a seasoned musician looking to explore new opportunities, learning how to share your video on iTunes as an independent artist is a vital step in maximizing your reach and achieving success.
This guide explores strategies, challenges, and tools that will help you stand out in the digital era.
Why iTunes Matters for Independent Artists
For years, iTunes has been a trusted platform for music enthusiasts, known for its commitment to quality and professionalism. While social media and free platforms like YouTube provide exposure, iTunes offers a distinct advantage: it attracts a paying audience that values polished, high-quality content.
Independent artists can leverage iTunes to showcase not only their songs but also their videos, creating a holistic artistic portfolio. By sharing your video on iTunes, you’re not just building visibility—you’re associating your work with a platform that commands respect in the music industry.
Preparing Your Video for iTunes
Before uploading your video, it's crucial to ensure it meets the technical and creative standards required for success on iTunes. Here are some key steps:
Focus on High Production Quality Invest in quality video production, even on a budget. Your video should reflect your unique style and artistic vision while maintaining professional-grade visuals and audio.
Optimize Your Content Make sure your video is properly edited, formatted, and free from errors. Include clear titles, metadata, and keywords that help your content appear in search results.
Collaborate with Experts If you’re not confident in handling technical aspects like editing or formatting, consider working with experienced professionals. From sound mixing to visual effects, every detail matters when you're uploading your video to a platform like iTunes.
How to Share Your Video on iTunes as an Independent Artist
The process of sharing your video on iTunes involves a few key steps, which can be streamlined by working with a reliable digital distributor.
Choose a Distribution Partner To get your video onto iTunes, you’ll need to collaborate with an approved distributor. These companies act as intermediaries, helping you navigate the technical and legal requirements of the platform.
Submit Your Content Once your video is ready, your distributor will handle the submission process. This includes formatting your file to meet iTunes’ specifications, adding metadata, and ensuring compliance with copyright guidelines.
Promote Strategically After your video goes live, promotion becomes the key to success. Share your iTunes link across social media, email newsletters, and other platforms to drive traffic and encourage downloads or purchases.
Overcoming Common Challenges
While iTunes offers a wealth of opportunities, independent artists often encounter obstacles along the way. Here are some common challenges and tips for overcoming them:
Competition: With thousands of artists uploading content daily, standing out can be tough. Focus on creating unique, high-quality videos that tell your story in an engaging way.
Budget Constraints: If you’re working with limited funds, prioritize cost-effective tools and organic promotion. Crowdfunding can also be a viable option for raising money for production costs.
Technical Barriers: For artists without technical expertise, collaborating with professionals or using user-friendly tools can simplify the process. Many distribution partners offer resources to help artists navigate technical challenges.
Tips for Gaining Traction on iTunes
Once your video is live, getting it in front of the right audience is the next step. Here are some strategies to boost visibility and engagement:
Leverage Social Media Share clips or teasers of your video on platforms like Instagram, Twitter, and TikTok. Use these channels to direct your followers to your iTunes page.
Engage with Your Fans Build a strong relationship with your audience by responding to comments, hosting live Q&A sessions, or offering behind-the-scenes content. A loyal fanbase can significantly boost your reach.
Collaborate with Other Artists Teaming up with other musicians or creators can introduce your work to new audiences. Consider featuring guest artists in your videos or creating collaborative content to expand your network.
Conclusion
For independent artists, iTunes represents a powerful tool for reaching new audiences and achieving career milestones. By focusing on quality, using the right distribution channels, and promoting your content effectively, you can establish yourself as a professional in the music industry.
Ready to take the next step in your artistic journey? Learn how to share your video on iTunes as an independent artist today and start connecting with a global audience.
Related Articles:
For further reading, explore these related articles:
Share Your Video on iTunes Without a Label
How to Share Your Video on iTunes with No Upfront Fees
How to Share Your Video on iTunes Quickly: A Complete Guide
Share Your Video on iTunes with 100% Royalties
For additional resources on music marketing and distribution, visit DMT Records Private Limited.
0 notes
Text
SEO Services in Jalandhar: Unique Insights into Website Optimization and Ranking Factors
In an era where online visibility is key to a business's success, understanding what drives search engine rankings can give your website an edge. While many assume that SEO revolves around keyword stuffing, true SEO success lies in technical precision, user experience, and strategic content placement. Webronex, a leader in SEO services in Jalandhar, dives into the core aspects of SEO that help elevate a website’s ranking and credibility. Here, we’ll provide unique insights and data-driven SEO practices that can set your website apart.
Key Aspects of SEO for Website Optimization 1. Technical SEO: Optimizing for Search Engine Crawlers Technical SEO involves configuring your website to ensure it can be effectively crawled and indexed by search engines. Often overlooked, technical SEO is foundational to getting a site noticed.
XML Sitemaps and Robots.txt: These files guide search engine crawlers on how to navigate your website. A properly structured XML sitemap ensures all pages are indexed, while a well-configured robots.txt file blocks unwanted pages, like administrative or duplicate pages, from being crawled.
Canonical Tags: Duplicate content can dilute your SEO power. Canonical tags help to tell search engines which version of a page to prioritize, which helps to streamline indexing and avoids the potential ranking penalties associated with duplicate content.
2. User-Centric On-Page SEO On-page SEO is about optimizing each page individually to attract traffic and retain visitors. An often-underemphasized aspect is the search intent—understanding what the user is truly seeking.
Click Magnet Titles: Craft titles that not only include relevant keywords but also address user curiosity. For instance, titles with numbers or power words like “essential,” “ultimate,” or “guide” have a higher click-through rate (CTR) than standard titles.
User Intent Keywords: Understanding and targeting keywords based on user intent—navigational, informational, commercial, and transactional—can significantly enhance SEO success. Instead of simply focusing on popular keywords, aim to cover search queries that match various stages of the user journey.
3. Page Experience Update: A Modern Ranking Signal In 2021, Google introduced the Page Experience Update, focusing on metrics that matter to real users. Factors like mobile-friendliness, safe browsing, and HTTPS support are essential, but so is optimizing for interaction and satisfaction.
Interactivity (initial Input Delay): This metric indicates how long it takes for a user's initial interaction (such as pressing a button) to be processed. Ensuring that FID is under 100ms enhances user satisfaction and is a direct ranking factor. Reducing JavaScript bloat and asynchronous loading can help improve FID.
Visual Stability: A low CLS (Cumulative Layout Shift) score is key to providing a smooth browsing experience. Avoid unexpected layout shifts by setting fixed dimensions for images and using CSS grid layouts to create visually stable pages.
Unique SEO Factors that Impact Search Engine Rankings 1. Semantic Search and Content Relevance Search engines are increasingly relying on AI and machine learning to comprehend words. Semantic search goes beyond keywords, examining the relationships between words and phrases to identify relevance and context.
Ways to Optimize for Semantic Search:
Content Silos: Organize your content into clusters by creating a hub page that links to relevant supporting articles. This structure signals to search engines that your website provides comprehensive coverage of a topic. Answer Directly: By answering questions directly within the content, you increase the chances of appearing as a featured snippet, which can drive significant traffic to your site.
2. E-A-T (Expertise, Authoritativeness, Trustworthiness) Google’s quality guidelines emphasize E-A-T as a crucial metric for page ranking, especially for content in fields like health, finance, and law (also known as YMYL or “Your Money, Your Life” content).
To boost E-A-T on your website:
Author Bios: Display the qualifications of content authors to establish expertise.
Backlink Trustworthiness: Receiving backlinks from reputable sources enhances your site’s trustworthiness in the eyes of search engines.
Transparent Information: Show clear contact information, company details, and privacy policies to foster user trust.
3. Content Freshness and Seasonal Optimization Search engines favor fresh, regularly updated content, particularly for topics that experience frequent changes or seasonal trends. Content freshness is more relevant for some industries, like news, fashion, and technology, where trends evolve quickly.
Ways to Keep Content Fresh:
Regular Updates: Refreshing old blog posts or case studies to reflect new trends or statistics keeps content current.
Seasonal SEO: Identify keywords or topics with seasonal popularity (e.g., “summer vacation tips” or “Black Friday deals”) and create content tailored to these times of the year. This seasonal SEO can bring timely traffic spikes.
Advanced Search Engine Factors that Boost Ranking 1. Visual Content Optimization for SEO Incorporating images, videos, and graphics can improve engagement metrics, which indirectly boosts rankings. Visual content also has a direct SEO impact through image search and increased engagement.
Alt Text for Images: Alt text describes images to search engines, providing context to users with disabilities. By using descriptive and relevant alt text, you can increase the chances of ranking in Google Images and improve overall SEO.
Video Schema Markup: Adding schema markup to video content helps search engines understand video relevance, allowing it to appear in rich snippets and video search results.
2. Domain Authority vs. Page Authority While domain authority (DA) is a broad measure of a website’s reputation, page authority (PA) focuses on the authority of individual pages. High PA pages can rank well even on lower DA websites if they meet specific user needs effectively.
Tips to Boost Page Authority:
Targeted Backlinking: Building backlinks to specific pages can significantly boost their authority.
Internal Linking Strategy: A well-structured internal linking setup distributes authority from high-ranking pages to others, helping them improve as well.
3. Behavioral Signals: Time on Page and Bounce Rate User engagement is a ranking factor that Google considers when assessing website quality. Pages with low bounce rates and high time on site often correlate with higher rankings, as these metrics indicate that users find the content useful and relevant.
Interactive Elements: Quizzes, calculators, and comment sections can increase user engagement and time on page.
Engaging Content Layout: Breaking up content with subheadings, bullet points, and short paragraphs makes information easier to read and retain users longer.
Choose Webronex for Professional SEO Services in Jalandhar In the competitive online space, having a robust SEO strategy is essential to get noticed and establish your brand’s credibility. By focusing on technical aspects, enhancing user experience, and keeping up with the latest SEO trends, your website can perform better and climb the search engine ranks. At Webronex, we provide comprehensive SEO services in Jalandhar that align with the latest SEO practices and deliver tangible results.
Contact Webronex today to learn more about our SEO services, or follow us on social media for valuable tips and updates. Let’s optimize your website and put your business on the map!
0 notes
Text
How Web Development Company Can Help Improve Your Website's SEO Performance
Search engine optimization (SEO) is key to a successful online presence. A website that ranks high on search engine results pages (SERPs) attracts more organic traffic, enhances visibility, and can significantly increase conversions.
While SEO is often associated with content creation and keyword optimization, the technical foundation of your website is just as important. This is where web development companies come into play.

Web development companies play a crucial role in creating and maintaining SEO-friendly websites, focusing on the technical aspects that can either enhance or hinder search engine rankings. From site architecture to mobile responsiveness, developers ensure that your website meets all the criteria that search engines value.
In this blog, we’ll explore how a web development company can help improve your website’s SEO performance.
1. Optimizing Website Speed and Performance
Website speed is a critical factor in both user experience and SEO. Websites that load quickly are given priority by search engines like Google because they offer a better user experience. If your site takes too long to load, not only will visitors leave, but search engines may also penalize you by ranking your site lower in search results.
Web development companies focus on optimizing your website’s speed and performance in various ways:
Minifying CSS, JavaScript, and HTML: Developers remove unnecessary characters, spaces, and comments from your code, reducing file sizes and improving load times.
Compressing images: High-quality images can slow down a website. Tools for picture compression are used by web developers to minimise file sizes without compromising image quality.
Caching: Developers set up browser caching to store elements of your website locally on users' devices, making repeat visits faster.
Server optimization: Choosing the right hosting environment and configuring servers properly can make a significant difference in load times.
By improving your website’s performance, web development companies ensure that visitors stay longer on your site and that search engines favor your pages in rankings.
2. Mobile Optimization and Responsiveness
It should come as no surprise that search engines give preference to mobile-friendly websites given the surge in mobile internet usage. Google, in particular, uses mobile-first indexing, which means it primarily evaluates the mobile version of your website when determining rankings.
Web development companies play a key role in ensuring that your website is optimized for mobile devices. They do this by:
Responsive design: Developers create websites that automatically adjust to different screen sizes and orientations, ensuring a seamless experience across devices.
Mobile speed optimization: Web developers optimize your mobile site for speed, as mobile users are even less patient with slow-loading pages than desktop users.
Mobile-friendly navigation: A good web development company ensures that your site’s navigation is easy to use on mobile devices, with large buttons and simplified menus.
By making your website mobile-friendly, web development companies help improve user experience and boost your search engine rankings.
3. Creating a Clean and Crawlable Site Structure
Search engines rely on crawlers (also known as spiders or bots) to index and rank websites. If your website’s structure is poorly organized or difficult to crawl, search engines will struggle to index your content, which can negatively impact your SEO performance.
Web development companies ensure that your site is designed with SEO in mind by focusing on:
Clear site hierarchy: Developers create a logical and easy-to-follow site architecture, making it simple for both users and search engines to navigate. This often involves using categories, subcategories, and internal linking strategies.
XML sitemaps: Web developers generate XML sitemaps that help search engines discover all the important pages on your site, ensuring that they are indexed properly.
Optimized URL structure: A well-structured URL can improve SEO performance. Developers create SEO-friendly URLs that are short, descriptive, and include relevant keywords.
Eliminating duplicate content: Web developers use canonical tags and other methods to prevent duplicate content issues, which can confuse search engines and harm your rankings.
By creating a clean and crawlable site structure, web development companies help ensure that search engines can effectively index your site, leading to better rankings.
4. Improving Core Web Vitals
Core Web Vitals are a set of metrics that Google uses to evaluate user experience on websites. These include page loading speed, interactivity, and visual stability. Websites that perform well on Core Web Vitals are more likely to rank higher on search engine results.
A Web development company can optimize your website for these metrics by:
Reducing Largest Contentful Paint (LCP): LCP measures how long it takes for the largest content element to load on a page. Developers improve LCP by optimizing server response times, loading resources asynchronously, and using optimized images.
Improving First Input Delay (FID): FID measures how quickly a page becomes interactive. Web developers enhance FID by minimizing JavaScript execution time and reducing the complexity of interactive elements.
Enhancing Cumulative Layout Shift (CLS): CLS measures visual stability during page load. Developers improve CLS by defining image dimensions, reserving space for ads, and avoiding dynamic content shifts.
By addressing Core Web Vitals, web development companies ensure that your website provides a better user experience, which is a ranking factor for search engines like Google.
5. Ensuring Secure and Accessible Websites
Website security is not just important for protecting user data; it also affects SEO. Search engines prioritize secure websites, and having an insecure website (without HTTPS) can lead to penalties in search rankings. Additionally, Google explicitly marks HTTP sites as “Not Secure,” which can deter users and increase bounce rates.
Web development companies enhance SEO by ensuring:
SSL certificates: Developers install SSL certificates to enable HTTPS, which encrypts data between the server and users' browsers. This not only boosts security but also improves SEO rankings.
Secure coding practices: Web developers implement security best practices such as regular updates, firewalls, and protection against common vulnerabilities like SQL injections and cross-site scripting.
Web accessibility: Web development companies also ensure that websites are accessible to all users, including those with disabilities. Accessibility features like alt text for images, keyboard navigation, and screen reader compatibility can indirectly improve SEO by enhancing user experience and reducing bounce rates.
A secure and accessible website builds trust with users and search engines alike, leading to improved SEO performance.
6. Integrating SEO Tools and Analytics
One of the most important aspects of improving SEO performance is tracking and analyzing data to identify areas for improvement. Web development companies help by integrating various SEO tools and analytics into your website, giving you the insights you need to monitor performance and make data-driven decisions.
Key integrations include:
Google Analytics: Developers integrate Google Analytics to track user behavior, traffic sources, bounce rates, and other key metrics. This data can help you understand what’s working and what needs improvement.
Google Search Console: Web developers set up Google Search Console to monitor indexing issues, track search performance, and receive alerts about potential SEO problems.
SEO plugins: For content management systems like WordPress, developers can integrate SEO plugins such as Yoast SEO or Rank Math to optimize on-page SEO elements like meta descriptions, title tags, and keyword usage.
By providing the tools and insights necessary to monitor SEO performance, web development companies enable businesses to continuously optimize their websites and improve search engine rankings.
The technical foundation of your website plays a crucial role in its SEO performance. Web development companies are instrumental in ensuring that your site meets the criteria that search engines value, from fast loading times and mobile responsiveness to security and crawlability.
#Web development company#website design company#web development services#website development company#web design company
0 notes
Text

How PAN Verification Status Impacts Your Financial Life
In today’s digitally driven world, Permanent Account Number (PAN) has become an integral part of financial transactions in India. Whether you are an individual taxpayer, a corporation, or a non-resident, the importance of a PAN cannot be overstated. However, it is equally important to ensure that he has a recognized status beyond merely holding a PAN. In this comprehensive article, we will explore how PAN verification status affects your financial life and why staying updated on this front can save you from potential pitfalls.
What Is a Drink?
Permanent Account Number (PAN) is a unique identification number as issued by the Indian Taxation Department. It is an important tool in pursuing financial transactions, ensuring that all taxable activities are properly monitored. PAN is not just a tax return; It is required for various financial activities, such as opening bank accounts, buying property and investing in stocks.
Importance of PAN Verification
PAN verification is the process of verifying the details associated with your PAN. This post ensures that the PAN details are correct, up-to-date and in line with the records held by the Income Tax Department. The importance of PAN verification extends beyond mere compliance; It plays an important role in maintaining your financial connections.
How Does PAN Verification Affect Tax Filing
One of the most important ways in which PAN verification status affects your financial life is through tax filing. An incorrect or unacknowledged PAN can cause problems with your tax returns, including delays, denials and even penalties. The Income Tax Department cross verifies the PAN details with additional financial details submitted at the time of filing tax returns. If there is a discrepancy, it can raise red flags and result in an undesirable test or audit.
Role of PAN in Financial Transactions
Every financial transaction you make, from deposits to investments, is linked to your PAN. Banks, financial institutions and government agencies require PAN details to process transactions beyond a certain threshold. If your PAN is not verified, you may face hurdles in completing these transactions, resulting in potential financial hardship and loss.
Impact On Loan Applications
When you apply for a loan, be it a home loan, a personal loan, or a business loan, the lending agency conducts a thorough background check, which includes verifying your PAN unauthenticated or incorrect PAN can have your loan application denied, even if your credit score is strong. Lenders use PAN verification to check your financial credibility and ensure that you are not involved in any fraudulent activities.
Result of PAN Mismatch
PAN mismatch occurs when the information in your PAN does not match the information in other financial documents, like your Aadhaar card, bank account, or tax returns This mismatch can cause problems, e.g delays in refund processing, difficulty in accessing government grants, your PAN and information related to bank account or other financial transactions
Verification of PAN and Financial Fraud
Financial fraud is a growing concern in the age of digitalisation. Fraudsters often use fake or stolen PANs to commit fraud, causing huge losses to individuals and businesses. By regularly checking your PAN, you can protect yourself from falling prey to such scams. Analysis ensures that your PAN is only linked to your legitimate financial activities and helps authorities detect and prevent fraudulent transactions.
How to Check your PAN Verification Status
Checking your PAN verification status is a simple process. Income Tax Department of India provides an online portal where you can verify your PAN by entering your PAN number and other required details. Once you have submitted the details, the system will display the status, indicating that your PAN is valid or properly authenticated. These simple steps can save you from potential financial issues down the road.
Compliance with PAN and KYC Norms
The Know the Consumer (KYC) standard is mandatory for various financial transactions, including opening a bank account, investing in mutual funds, or buying insurance Your PAN verification status is an important part of the KYC process in. If your PAN is not verified, your KYC will be considered incomplete, resulting in restrictions on your financial activities or even freezing of your account.
Steps to Correct PAN Error
If you find that your PAN details are incorrect or not verified, it is important to take immediate action. The Income Tax Department provides a correction form (Form 49A) which can be submitted online to rectify any mistake. This process usually involves submitting supporting documentation to verify your identity and resolve discrepancies. Ensuring that your PAN details are correct can prevent possible bankruptcy.
Conclusion
PAN verification status plays an important role in shaping your financial life. From filing taxes to loan applications, preventing fraud to complying with KYC norms, the implications of unauthenticated or incorrect PAN go far By checking your PAN regularly and updating your PAN on the other side of the certification status, you can ensure smooth financial transactions and protect yourself against potential risks. In today’s tough economic climate, you don’t just have to be proactive about PAN verification; it’s an important step towards securing your financial future.
0 notes