#apparently it has legitimate use in backend
Explore tagged Tumblr posts
Text
Sorry for programmer posting, but if you use var in frontend code I am killing you with rocks
#valk yelling at clouds#apparently it has legitimate use in backend#i dont know im a front end bimbo#and if you out vars in my code: death penalty
6 notes
·
View notes
Text
Things That Look Positive for Cryptocurrencies
While there have been market corrections in cryptocurrency market in 2018, everyone agrees that the best is yet to come. There have been a lot of activities in the market that have changed the tide for the better. With proper analysis and the right dose of optimism, anyone who is invested in the crypto market can make millions out of it. Cryptocurrency market is here to stay for the long term. Here in this article, we give you five positive factors that can spur further innovation and market value in cryptocurrencies ROI.
1. Innovation in scaling
Bitcoin is the first cryptocurrency in the market. It has the maximum number of users and the highest value. It dominates the entire value chain of the cryptocurrency system. However, it is not without issues. Its major bottleneck is that it can handle only six to seven transactions per seconds. In comparison, credit card transactions average at few thousands per second. Apparently, there is scope for improvement in the scaling of transactions. With the help of peer to peer transaction networks on top of the blockchain technology, it is possible to increase the transaction volume per second.
2. Legitimate ICOs
While there are cryptocoins with stable value in the market, newer coins are being created that are designed to serve a specific purpose. Coins like IOTA are intended to help the Internet Of Things market exchanging power currencies. Some coins address the issue of cybersecurity by giving encrypted digital vaults for storing the money.
New ICOs are coming up with innovative solutions that disrupt the existing market and bring in a new value in the transactions. They are also gathering authority in the market with their easy to use exchanges and reliable backend operations. They are innovating both on the technology side regarding usage of specialized hardware for mining and financial market side by giving more freedom and options to investors in the exchange.
3. Clarity on regulation
In the current scenario, most governments are studying the impact of cryptocurrencies on the society and how its benefits can be accrued to the community at large. We can expect that there may be reasonable conclusions as per the result of the studies.
Few governments are already taking the route of legalising and regulating crypto markets just like any other market. This will prevent ignorant retail investors from losing money and protect them from harm. Abling regulations that boost cryptocurrency growth are expected to appear in 2018. This will potentially pave the way for widespread adoption in future
4. Increase in application
There is enormous enthusiasm for the application of blockchain technology in virtually every industry. Some startups are coming up with innovative solutions such as digital wallets, debit cards for cryptocurrencies, etc. this will increase the number of merchants who are willing to transact in cryptocurrencies which in turn boost the number of users.
The reputation of crypto assets as a transaction medium will be reinforced as more people trust in this system. Although some startups may not survive, they will positively contribute to the overall health of the market creating competition and innovation.
5. Investment from financial institutions
Many international banks are watching the cryptocurrency scene. This can lead to the entry of institutional investors into the market. The inflow of substantial institutional investments will fuel the next phase of growth of the cryptomarkets. It has captured the fancy of many banks and financial institutions.
As the surprises and bottlenecks around cryptocurrencies reduce, there will be more uptake from traditional investors. This will lead to a lot of dynamism and liquidity much needed for any growing financial markets. Cryptocurrency will become the defacto currency for transactions all over the world.
0 notes
Note
I won't bore you by going through each point here and deconstructing them, so I'll summarize here. None of the sources you linked are recent, the most recent you linked was from 2018. While newer, it's not exactly current. Furthermore, they continually attribute cellular life, to human life, which is an error. A zygote is a single cell, it is not an organism. While it is by definition life, it is not human life. Lastly, a number of these articles come from what are very explicitly religious organizations, or organizations that are specifically made as anti abortion advocacy groups, and are not coming in from a neutral or scientific stance, and therefore should not be trusted. Click the keep reading for the thorough breakdown.
Now comes the longform. The first source you cite, "A Scientific View of When Life Begins", does not come from a scientific journal. As far as I can tell the Charlotte Lozier Institute is an anti abortion think-tank that uses the fact it has doctors on staff as a mask to seem more legitimate.
While Dr. Condic does have a doctorate from the University of California, as far as I can find that degree is in Neurobiology and Anatomy, and not Reproductive Biology, which is where her paper which you linked comes from.
Further into that paper, the version you linked is also an extremely abridged version of it, rather than the full paper, though it does say where they received permission to use said paper, HLI.org. HLI, or Human Life International, according to their own about us page, aims to "...teach the world to value life and follow God's plan for the family." Which hardly seems like it's coming from a place of science, and is instead coming at this from the religious angle. It also seems to have some conspiracy nonsense about population control but that's about all I could stomach, to be perfectly frank.
I'll admit that the second article does go over my head, I'm not a scientist, however the article does not follow the APA citation method, which implies to me that it was not published in a journal. Using the DOI number to look it up, this proves true. It seems it was published originally through the publishing firm Mary Ann Liebert, Inc, which as far as I can tell is fine, but apparently run horribly on the backend. Something to bear in mind.
The third link you posted leads to an article by Dr Steven Andrew Jacobs, who is also not a doctor of reproductive biology, and is instead a doctor of comparative human development. Furthermore his paper is a survey, and not based on experimentation or research. While surveys are important to scientific research, it's not sufficient evidence for when life begins, it is instead the opinions of people when they believe life begins.
The textbook quotes you linked also do not sufficiently prove that life begins at conception, as none of them actually discuss when life begins, instead all of them reference the beginning of human development. This is excluding the quote from "Before We Are Born: Essentials of Embryology and Birth Defects". Furthermore, all of the sources are from before 1999. These are not modern sources.
Going to "When Human Life Begins" by Dr Fred de Miranda, it is published to the American College of Pediatricians, an advocacy group that is explicitly anti abortion, and also explicitly against gay couples adopting children. I'm not going to even bother reading the study as the area it's published, as just based on that fact alone, it should be immediately discredited.
The long in short of it, your argument does not come from a place of science, it comes from a place of religion, and misinformation. The sooner you admit that to yourself, the sooner we can have a more productive conversation about this.
I am so so curious. Why do you think that a fetus or embryo deserves more rights than the mother carrying it?
Also, do you have any reliable peer-reviewed studies to prove what you have in your description? Because, interestingly, all recent medical literature disagrees with your claim.
I never said a human being in the embryotic or fetus stage deserves more rights than the mother carrying them. I believe they both deserve the same fundamental rights. I don't think anyone has the right to kill an innocent human being. Everyone deserves the right to life. No matter how you look or your stage of development.
I have many sources that include scientific peer reviewed papers on the topic of when life begins.
A Scientific View of When Life Begins written by Maureen Condic, Ph.D.
“The conclusion that human life begins at sperm-egg fusion is uncontested, objective, based on the universally accepted scientific method of distinguishing different cell types from each other and on ample scientific evidence (thousands of independent, peer-reviewed publications).”
She also has another scientific paper on stem cells and their development, Totipotency: What It Is and What It Is Not
"We do not owe any particular ethical consideration to human gametes, skin cells, or stem cells. Yet, if human cells are manipulated so that they participate in the development of an existing embryo (eg, by tetraploid complementation) or are used to generate a human embryo de novo (eg, by fertilization or cloning), then the embryo merits substantial ethical consideration due to the fact that it is a human organism, that is, a human being."
Biologists' Consensus on 'When Life Begins' written by Steven Andrew Jacobs. This is the largest recent survey of over 5,000 biologist from 1,000 worldwide institutions revealing that a full 96% agreed with “human life begins at conception.” These biologists were self-described as 89% “liberal,” 85% “pro-choice,” and 63% “non-religious.”
Here is a collection of quotes from textbooks on when human life begins from Princeton.edu.
When Human Life Begins written by the American College of Pediatricians: Fred de Miranda, MD and Dr. Patricia Lee June, MD.
"It is clear that from the time of cell fusion, the embryo consists of elements (from both maternal and paternal origin) which function interdependently in a coordinated manner to carry on the function of the development of the human organism. From this definition, the single-celled embryo is not just a cell, but an organism, a living being, a human being."
When Does Human Life Begin? The Scientific Evidence and Terminology Revisited by Maureen L. Condic, Ph.D.
"The scientific evidence presented here refutes the longstanding 'pre-zygote error' promoted by the Carnegie stages that the zygote is not formed until syngamy, and therefore, that the cell produced by fusion of the gametes is nothing more than a 'penetrated oocyte.' Ethical positions that deny the personhood of human being at all stages of life are logically inconsistent and scientifically unsound, in addition to having significant, negative implications for the ethical treatment of all human persons."
When Does Human Life Begin?: The Final Answer written by C. Ward Kischer, Ph.D.
"It is quite clear that what was known more than 100 years ago, even intuitively before that, is that the fusion of sperm and oocyte begins the life of the new individual human being."
This is an undeniable fact. Human life begins when a new human being is formed during fertilization. Can you link this recent medical literature?
91 notes
·
View notes
Text
Things That Look Positive for Cryptocurrencies
While there have been market corrections in cryptocurrency market in 2018, everyone agrees that the best is yet to come. There have been a lot of activities in the market that have changed the tide for the better. With proper analysis and the right dose of optimism, anyone who is invested in the crypto market can make millions out of it. Cryptocurrency market is here to stay for the long term. Here in this article, we give you five positive factors that can spur further innovation and market value in cryptocurrencies.
1. Innovation in scaling
Bitcoin is the first cryptocurrency in the market. It has the maximum number of users and the highest value. It dominates the entire value chain of the cryptocurrency system. However, it is not without issues. Its major bottleneck is that it can handle only six to seven transactions per seconds. In comparison, credit card transactions average at few thousands per second. Apparently, there is scope for improvement in the scaling of transactions. With the help of peer to peer transaction networks on top of the blockchain technology, it is possible to increase the transaction volume per second.
2. Legitimate ICOs
While there are cryptocoins with stable value in the market, newer coins are being created that are designed to serve a specific purpose. Coins like IOTA are intended to help the Internet Of Things market exchanging power currencies. Some coins address the issue of cybersecurity by giving encrypted digital vaults for storing the money.
New ICOs are coming up with innovative solutions that disrupt the existing market and bring in a new value in the transactions. They are also gathering authority in the market with their easy to use exchanges and reliable backend operations. They are innovating both on the technology side regarding usage of specialized hardware for mining and financial market side by giving more freedom and options to investors in the exchange.
3. Clarity on regulation
In the current scenario, most governments are studying the impact of cryptocurrencies on the society and how its benefits can be accrued to the community at large. We can expect that there may be reasonable conclusions as per the result of the studies.
Few governments are already taking the route of legalising and regulating crypto markets just like any other market. This will prevent ignorant retail investors from losing money and protect them from harm. Abling regulations that boost cryptocurrency growth are expected to appear in 2018. This will potentially pave the way for widespread adoption in future
4. Increase in application
There is enormous enthusiasm for the application of blockchain technology in virtually every industry. Some startups are coming up with innovative solutions such as digital wallets, debit cards for cryptocurrencies, etc. this will increase the number of merchants who are willing to transact in cryptocurrencies which in turn boost the number of users.
If you need any kind of information this topic click here: Rarible NFT
0 notes
Text
5 Myths About Jamstack
Jamstack isn’t necessarily new. The term was officially coined in 2016, but the technologies and architecture it describes have been around well before that. Jamstack has received a massive dose of attention recently, with articles about it appearing in major sites and publications and new Jamstack-focused events, newsletters, podcasts, and more. As someone who follows it closely, I’ve even seen what seems like a significant uptick in discussion about it on Twitter, often from people who are being newly introduced to the concept.
The buzz has also seemed to bring out the criticism. Some of the criticism is fair, and I’ll get to some of that in a bit, but others appear to be based on common myths about the Jamstack that persist, which is what I want to address first. So let’s look at five common myths about Jamstack I’ve encountered and debunk them. As with many myths, they are often based on a kernel of truth but lead to invalid conclusions.
Myth 1: They are just rebranded static sites
JAMStack is 99.9% branding and .1% substance. 😳😆 https://t.co/nxoEVQ43oE
— Nicole Sullivan – Black Lives Matter (@stubbornella) February 9, 2020
Yes, as I covered previously, the term “Jamstack” was arguably a rebranding of what we previously called “static sites.” This was not a rebranding meant to mislead or sell you something that wasn’t fully formed — quite the opposite. The term “static site” had long since lost its ability to describe what people were building. The sites being built using static site generators (SSG) were frequently filled with all sorts of dynamic content and capabilities.
Static sites were seen as largely about blogs and documentation where the UI was primarily fixed. The extent of interaction was perhaps embedded comments and a contact form. Jamstack sites, on the other hand, have things like user authentication, dynamic content, ecommerce, user generated content.
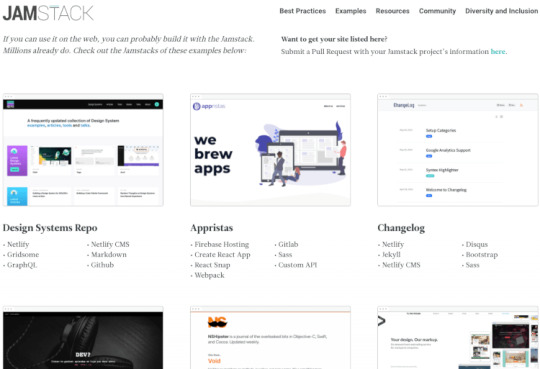
A listing of sites built using Jamstack on Jamstack.org
Want proof? Some well-known companies and sites built using the Jamstack include Smashing Magazine, Sphero, Postman, Prima, Impossible Foods and TriNet, just to name a few.
Myth 2: Jamstack sites are fragile
A Medium article with no byline: The issues with JAMStack: You might need a backend
Reading the dependency list for Smashing Magazine reads like the service equivalent of node_modules, including Algolia, GoCommerce, GoTrue, GoTell and a variety of Netlify services to name a few. There is a huge amount of value in knowing what to outsource (and when), but it is amusing to note the complexity that has been introduced in an apparent attempt to ‘get back to basics’. This is to say nothing of the potential fragility in relying on so many disparate third-party services.
Yes, to achieve the dynamic capabilities that differentiate the Jamstack from static sites, Jamstack projects generally rely on a variety of services, both first- or third-party. Some have argued that this makes Jamstack sites particularly vulnerable for two reasons. The first, they say, is that if any one piece fails, the whole site functionality collapses. The second is that your infrastructure becomes too dependent on tools and services that you do not own.
Let’s tackle that first argument. The majority of a Jamstack site should be pre-rendered. This means that when a user visits the site, the page and most of its content is delivered as static assets from the CDN. This is what gives Jamstack much of its speed and security. Dynamic functionality — like shopping carts, authentication, user generated content and perhaps search — rely upon a combination of serverless functions and APIs to work.
Broadly speaking, the app will call a serverless function that serves as the back end to connect to the APIs. If, for example, our e-commerce functionality relies on Stripe’s APIs to work and Stripe is down, then, yes, our e-commerce functionality will not work. However, it’s important to note that the site won’t go down. It can handle the issue gracefully by informing the user of the issue. A server-rendered page that relies on the Stripe API for e-commerce would face the identical issue. Assuming the server-rendered page still calls the back end code for payment asynchronously, it would be no more or less fragile than the Jamstack version. On the other hand, if the server-rendering is actually dependent upon the API call, the user may be stuck waiting on a response or receive an error (a situation anyone who uses the web is very familiar with).
As for the second argument, it’s really hard to gauge the degree of dependence on third-parties for a Jamstack web app versus a server-rendered app. Many of today’s server-rendered applications still rely on APIs for a significant amount of functionality because it allows for faster development, takes advantage of the specific area of expertise of the provider, can offload responsibility for legal and other compliance issues, and more. In these cases, once again, the server-rendered version would be no more or less dependent than the Jamstack version. Admittedly, if your app relies mostly on internal or homegrown solutions, then this may be different.
Myth 3: Editing content is difficult
Kev Quirk, on Why I Don’t Use A Static Site Generator:
Having to SSH into a Linux box, then editing a post on Vim just seems like a ridiculously high barrier for entry when it comes to writing on the go. The world is mobile first these days, like it or not, so writing on the go should be easy.
This issue feels like a relic of static sites past. To be clear, you do not need to SSH into a Linux box to edit your site content. There are a wide range of headless CMS options, from completely free and open source to commercial offerings that power content for large enterprises. They offer an array of editing capabilities that rival any traditional CMS (something I’ve talked about before). The point is, there is no reason to be manually editing Markdown, YAML or JSON files, even on your blog side project. Aren’t sure how to hook all these pieces up? We’ve got a solution for that too!
One legitimate criticism has been that the headless CMS and build process can cause a disconnect between the content being edited and the change on the site. It can be difficult to preview exactly what the impact of a change is on the live site until it is published or without some complex build previewing process. This is something that is being addressed by the ecosystem. Companies like Stackbit (who I work for) are building tools that make this process seamless.
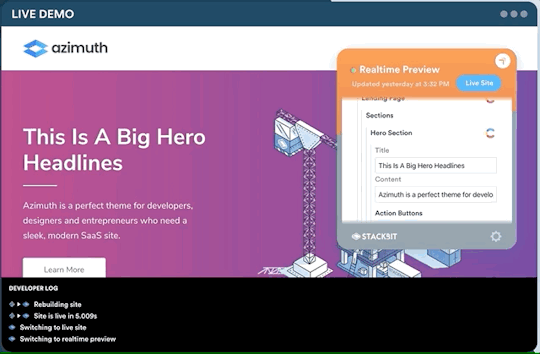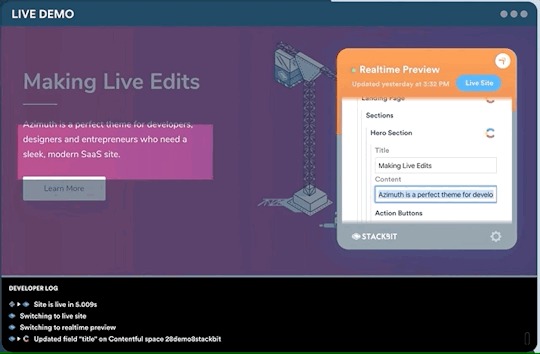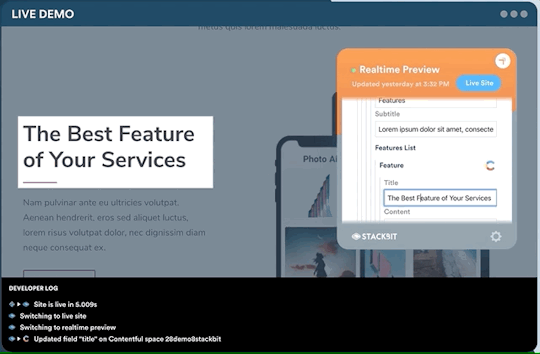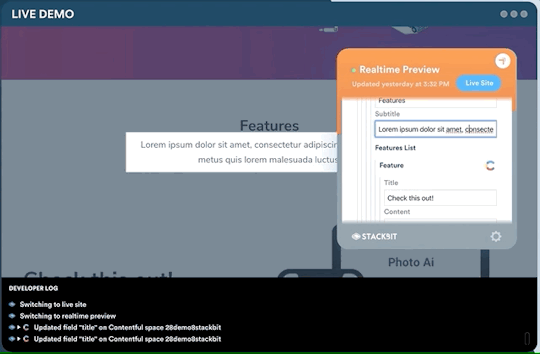
Editing a site using Stackbit
We’re not the only ones working on solving this problem. Other solutions include TinaCMS and Gatsby Preview. I think we are close to it becoming commonplace to have the simplicity of WYSIWYG editing on a tool like Wix running on top of the Jamstack.
Myth 4: SEO is Hard on the Jamstack
Kym Ellis, on What the JAMstack means for marketing:
Ditching the concept of the plugin and opting for a JAMstack site which is “just HTML” doesn’t actually mean you have to give up functionality, or suddenly need to know how to code like a front-end developer to manage a site and its content.
I haven’t seen this one pop up as often in recent years and I think it is mostly legacy criticism of the static site days, where managing SEO-related metadata involved manually editing YAML-based frontmatter. The concern was that doing SEO properly became cumbersome and hard to maintain, particularly if you wanted to inject different metadata for each unique page that was generated or to create structured data like JSON-LD, which can be critical for enhancing your search listing.

The advances in content management for the Jamstack have generally addressed the complexity of maintaining SEO metadata. In addition, because pages are pre-rendered, adding sitemaps and JSON-LD is relatively simple, provided the metadata required exists. While pre-rendering makes it easy to create the resources search engines (read: Google) need to index a site, they also, combined with CDNs, making it easier to achieve the performance benchmarks necessary to improve a site’s ranking.
Basically, Jamstack excels at “technical SEO” while also providing the tools necessary for content editors to supply the keyword and other metadata they require. For a more comprehensive look at Jamstack and SEO, I highly recommend checking out the Jamstack SEO Guide from Bejamas.
Myth 5: Jamstack requires heavy JavaScript frameworks
If you’re trying to sell plain ol’ websites to management who are obsessed with flavour-of-the-month frameworks, a slick website promoting the benefits of “JAMstack” is a really useful thing.
– jdietrich, Hacker News
Lately, it feels as if Jamstack has become synonymous with front-end JavaScript frameworks. It’s true that a lot of the most well-known solutions do depend on a front-end framework, including Gatsby (React), Next.js (React), Nuxt (Vue), VuePress (Vue), Gridsome (Vue) and Scully (Angular). This seems to be compounded by confusion around the “J” in Jamstack. While it stands for JavaScript, this does not mean that Jamstack solutions are all JavaScript-based, nor do they all require npm or JavaScript frameworks.

In fact, many of the most widely used tools are not built in JavaScript, notably Hugo (Go), Jekyll (Ruby), Pelican (Python) and the recently released Bridgetown (Ruby). Meanwhile, tools like Eleventy are built using JavaScript but do not depend on a JavaScript framework. None of these tools prevent the use of a JavaScript framework, but they do not require it.
The point here isn’t to dump on JavaScript frameworks or the tools that use them. These are great tools, used successfully by many developers. JavaScript frameworks can be very powerful tools capable of simplifying some very complex tasks. The point here is simply that the idea that a JavaScript framework is required to use the Jamstack is false — Jamstack comes in 460 flavors!
Where we can improve
So that’s it, right? Jamstack is an ideal world of web development where everything isn’t just perfect, but perfectly easy. Unfortunately, no. There are plenty of legitimate criticisms of Jamstack.
Simplicity
Sebastian De Deyne, with Thoughts (and doubts) after messing around with the JAMstack:
In my experience, the JAMstack (JavaScript, APIs, and Markup) is great until is isn’t. When the day comes that I need to add something dynamic–and that day always comes–I start scratching my head.
Let’s be honest: Getting started with the Jamstack isn’t easy. Sure, diving into building a blog or a simple site using a static site generator may not be terribly difficult. But try building a real site with anything dynamic and things start to get complicated fast.
You are generally presented with a myriad of options for completing the task, making it tough to weigh the pros and cons. One of the best things about Jamstack is that it is not prescriptive, but that can make it seem unapproachable, leaving people with the impression that perhaps it isn’t suited for complex tasks.
Tying services together
Agreed. In yesterday's web you could grab an instrument and begin playing. Today's web development feels like a conductor trying to pull together a massive orchestra into a cohesive song – you have to understand each individual musician's part to have any chance of success.
— Brian Rinaldi (@remotesynth) May 1, 2020
When you actually get to the point of building those dynamic features, your site can wind up being dependent on an array of services and APIs. You may be calling a headless CMS for content, a serverless function that calls an API for payment transactions, a service like Algolia for search, and so on. Bringing all those pieces together can be a very complex task. Add to that the fact that each often comes with its own dashboard and API/SDK updates, things get even more complex.
This is why I think services like Stackbit and tools like RedwoodJS are important, as they bring together disparate pieces of the infrastructure behind a Jamstack site and make those easier to build and manage.
Overusing frameworks
In my opinion, our dependence on JavaScript frameworks for modern front-end development has been getting a much needed skeptical look lately. There are tradeoffs, as this post by Tim Kadlec recently laid out. As I said earlier, you don’t need a JavaScript framework to work in the Jamstack.
However, the impression was created both because so many Jamstack tools rely on JavaScript frameworks and also because much of the way we teach Jamstack has been centered on using frameworks. I understand the reasoning for this — many Jamstack developers are comfortable in JavaScript frameworks and there’s no way to teach every tool, so you pick the one you like. Still, I personally believe the success of Jamstack in the long run depends on its flexibility, which (despite what I said about the simplicity above) means we need to present the diversity of solutions it offers — both with and without JavaScript frameworks.
Where to go from here
Sheesh, you made it! I know I had a lot to say, perhaps more than I even realized when I started writing, so I won’t bore you with a long conclusion other than to say that, obviously, I have presented these myths from the perspective of someone who believes very deeply in the value of the Jamstack, despite it’s flaws!
If you are looking for a good post about when to and when not to choose Jamstack over server-side rendering, check out Chris Coyier’s recent post Static or Not?.
The post 5 Myths About Jamstack appeared first on CSS-Tricks.
5 Myths About Jamstack published first on https://deskbysnafu.tumblr.com/
0 notes
Text
5 Myths About Jamstack
Jamstack isn’t necessarily new. The term was officially coined in 2016, but the technologies and architecture it describes have been around well before that. Jamstack has received a massive dose of attention recently, with articles about it appearing in major sites and publications and new Jamstack-focused events, newsletters, podcasts, and more. As someone who follows it closely, I’ve even seen what seems like a significant uptick in discussion about it on Twitter, often from people who are being newly introduced to the concept.
The buzz has also seemed to bring out the criticism. Some of the criticism is fair, and I’ll get to some of that in a bit, but others appear to be based on common myths about the Jamstack that persist, which is what I want to address first. So let’s look at five common myths about Jamstack I’ve encountered and debunk them. As with many myths, they are often based on a kernel of truth but lead to invalid conclusions.
Myth 1: They are just rebranded static sites
JAMStack is 99.9% branding and .1% substance.


https://t.co/nxoEVQ43oE
— Nicole Sullivan – Black Lives Matter (@stubbornella) February 9, 2020
https://platform.twitter.com/widgets.js
Yes, as I covered previously, the term “Jamstack” was arguably a rebranding of what we previously called “static sites.” This was not a rebranding meant to mislead or sell you something that wasn’t fully formed — quite the opposite. The term “static site” had long since lost its ability to describe what people were building. The sites being built using static site generators (SSG) were frequently filled with all sorts of dynamic content and capabilities.
Static sites were seen as largely about blogs and documentation where the UI was primarily fixed. The extent of interaction was perhaps embedded comments and a contact form. Jamstack sites, on the other hand, have things like user authentication, dynamic content, ecommerce, user generated content.
A listing of sites built using Jamstack on Jamstack.org
Want proof? Some well-known companies and sites built using the Jamstack include Smashing Magazine, Sphero, Postman, Prima, Impossible Foods and TriNet, just to name a few.
Myth 2: Jamstack sites are fragile
A Medium article with no byline: The issues with JAMStack: You might need a backend
Reading the dependency list for Smashing Magazine reads like the service equivalent of node_modules, including Algolia, GoCommerce, GoTrue, GoTell and a variety of Netlify services to name a few. There is a huge amount of value in knowing what to outsource (and when), but it is amusing to note the complexity that has been introduced in an apparent attempt to ‘get back to basics’. This is to say nothing of the potential fragility in relying on so many disparate third-party services.
Yes, to achieve the dynamic capabilities that differentiate the Jamstack from static sites, Jamstack projects generally rely on a variety of services, both first- or third-party. Some have argued that this makes Jamstack sites particularly vulnerable for two reasons. The first, they say, is that if any one piece fails, the whole site functionality collapses. The second is that your infrastructure becomes too dependent on tools and services that you do not own.
Let’s tackle that first argument. The majority of a Jamstack site should be pre-rendered. This means that when a user visits the site, the page and most of its content is delivered as static assets from the CDN. This is what gives Jamstack much of its speed and security. Dynamic functionality — like shopping carts, authentication, user generated content and perhaps search — rely upon a combination of serverless functions and APIs to work.
Broadly speaking, the app will call a serverless function that serves as the back end to connect to the APIs. If, for example, our e-commerce functionality relies on Stripe’s APIs to work and Stripe is down, then, yes, our e-commerce functionality will not work. However, it’s important to note that the site won’t go down. It can handle the issue gracefully by informing the user of the issue. A server-rendered page that relies on the Stripe API for e-commerce would face the identical issue. Assuming the server-rendered page still calls the back end code for payment asynchronously, it would be no more or less fragile than the Jamstack version. On the other hand, if the server-rendering is actually dependent upon the API call, the user may be stuck waiting on a response or receive an error (a situation anyone who uses the web is very familiar with).
As for the second argument, it’s really hard to gauge the degree of dependence on third-parties for a Jamstack web app versus a server-rendered app. Many of today’s server-rendered applications still rely on APIs for a significant amount of functionality because it allows for faster development, takes advantage of the specific area of expertise of the provider, can offload responsibility for legal and other compliance issues, and more. In these cases, once again, the server-rendered version would be no more or less dependent than the Jamstack version. Admittedly, if your app relies mostly on internal or homegrown solutions, then this may be different.
Myth 3: Editing content is difficult
Kev Quirk, on Why I Don’t Use A Static Site Generator:
Having to SSH into a Linux box, then editing a post on Vim just seems like a ridiculously high barrier for entry when it comes to writing on the go. The world is mobile first these days, like it or not, so writing on the go should be easy.
This issue feels like a relic of static sites past. To be clear, you do not need to SSH into a Linux box to edit your site content. There are a wide range of headless CMS options, from completely free and open source to commercial offerings that power content for large enterprises. They offer an array of editing capabilities that rival any traditional CMS (something I’ve talked about before). The point is, there is no reason to be manually editing Markdown, YAML or JSON files, even on your blog side project. Aren’t sure how to hook all these pieces up? We’ve got a solution for that too!
One legitimate criticism has been that the headless CMS and build process can cause a disconnect between the content being edited and the change on the site. It can be difficult to preview exactly what the impact of a change is on the live site until it is published or without some complex build previewing process. This is something that is being addressed by the ecosystem. Companies like Stackbit (who I work for) are building tools that make this process seamless.
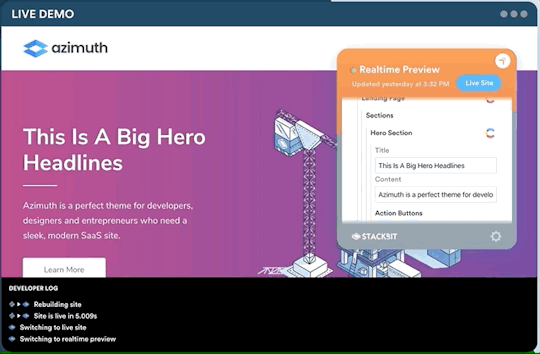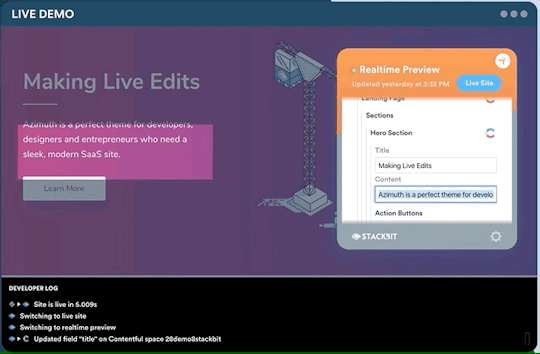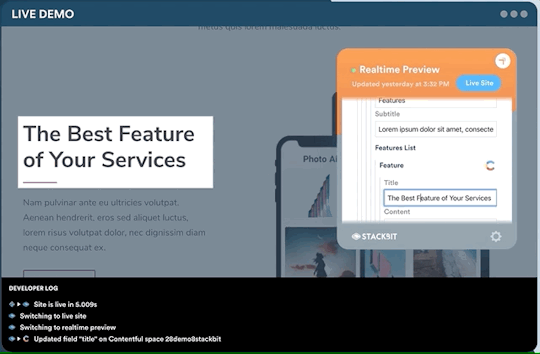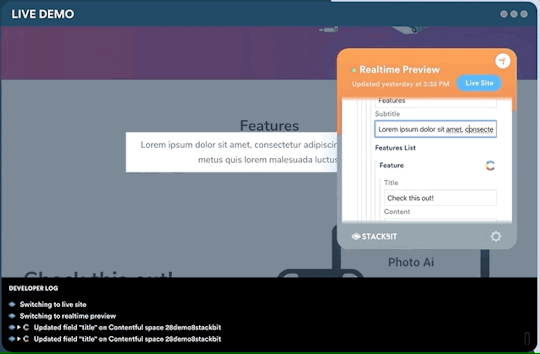
Editing a site using Stackbit
We’re not the only ones working on solving this problem. Other solutions include TinaCMS and Gatsby Preview. I think we are close to it becoming commonplace to have the simplicity of WYSIWYG editing on a tool like Wix running on top of the Jamstack.
Myth 4: SEO is Hard on the Jamstack
Kym Ellis, on What the JAMstack means for marketing:
Ditching the concept of the plugin and opting for a JAMstack site which is “just HTML” doesn’t actually mean you have to give up functionality, or suddenly need to know how to code like a front-end developer to manage a site and its content.
I haven’t seen this one pop up as often in recent years and I think it is mostly legacy criticism of the static site days, where managing SEO-related metadata involved manually editing YAML-based frontmatter. The concern was that doing SEO properly became cumbersome and hard to maintain, particularly if you wanted to inject different metadata for each unique page that was generated or to create structured data like JSON-LD, which can be critical for enhancing your search listing.

The advances in content management for the Jamstack have generally addressed the complexity of maintaining SEO metadata. In addition, because pages are pre-rendered, adding sitemaps and JSON-LD is relatively simple, provided the metadata required exists. While pre-rendering makes it easy to create the resources search engines (read: Google) need to index a site, they also, combined with CDNs, making it easier to achieve the performance benchmarks necessary to improve a site’s ranking.
Basically, Jamstack excels at “technical SEO” while also providing the tools necessary for content editors to supply the keyword and other metadata they require. For a more comprehensive look at Jamstack and SEO, I highly recommend checking out the Jamstack SEO Guide from Bejamas.
Myth 5: Jamstack requires heavy JavaScript frameworks
If you’re trying to sell plain ol’ websites to management who are obsessed with flavour-of-the-month frameworks, a slick website promoting the benefits of “JAMstack” is a really useful thing.
– jdietrich, Hacker News
Lately, it feels as if Jamstack has become synonymous with front-end JavaScript frameworks. It’s true that a lot of the most well-known solutions do depend on a front-end framework, including Gatsby (React), Next.js (React), Nuxt (Vue), VuePress (Vue), Gridsome (Vue) and Scully (Angular). This seems to be compounded by confusion around the “J” in Jamstack. While it stands for JavaScript, this does not mean that Jamstack solutions are all JavaScript-based, nor do they all require npm or JavaScript frameworks.

In fact, many of the most widely used tools are not built in JavaScript, notably Hugo (Go), Jekyll (Ruby), Pelican (Python) and the recently released Bridgetown (Ruby). Meanwhile, tools like Eleventy are built using JavaScript but do not depend on a JavaScript framework. None of these tools prevent the use of a JavaScript framework, but they do not require it.
The point here isn’t to dump on JavaScript frameworks or the tools that use them. These are great tools, used successfully by many developers. JavaScript frameworks can be very powerful tools capable of simplifying some very complex tasks. The point here is simply that the idea that a JavaScript framework is required to use the Jamstack is false — Jamstack comes in 460 flavors!
Where we can improve
So that’s it, right? Jamstack is an ideal world of web development where everything isn’t just perfect, but perfectly easy. Unfortunately, no. There are plenty of legitimate criticisms of Jamstack.
Simplicity
Sebastian De Deyne, with Thoughts (and doubts) after messing around with the JAMstack:
In my experience, the JAMstack (JavaScript, APIs, and Markup) is great until is isn’t. When the day comes that I need to add something dynamic–and that day always comes–I start scratching my head.
Let’s be honest: Getting started with the Jamstack isn’t easy. Sure, diving into building a blog or a simple site using a static site generator may not be terribly difficult. But try building a real site with anything dynamic and things start to get complicated fast.
You are generally presented with a myriad of options for completing the task, making it tough to weigh the pros and cons. One of the best things about Jamstack is that it is not prescriptive, but that can make it seem unapproachable, leaving people with the impression that perhaps it isn’t suited for complex tasks.
Tying services together
Agreed. In yesterday's web you could grab an instrument and begin playing. Today's web development feels like a conductor trying to pull together a massive orchestra into a cohesive song – you have to understand each individual musician's part to have any chance of success.
— Brian Rinaldi (@remotesynth) May 1, 2020
https://platform.twitter.com/widgets.js
When you actually get to the point of building those dynamic features, your site can wind up being dependent on an array of services and APIs. You may be calling a headless CMS for content, a serverless function that calls an API for payment transactions, a service like Algolia for search, and so on. Bringing all those pieces together can be a very complex task. Add to that the fact that each often comes with its own dashboard and API/SDK updates, things get even more complex.
This is why I think services like Stackbit and tools like RedwoodJS are important, as they bring together disparate pieces of the infrastructure behind a Jamstack site and make those easier to build and manage.
Overusing frameworks
In my opinion, our dependence on JavaScript frameworks for modern front-end development has been getting a much needed skeptical look lately. There are tradeoffs, as this post by Tim Kadlec recently laid out. As I said earlier, you don’t need a JavaScript framework to work in the Jamstack.
However, the impression was created both because so many Jamstack tools rely on JavaScript frameworks and also because much of the way we teach Jamstack has been centered on using frameworks. I understand the reasoning for this — many Jamstack developers are comfortable in JavaScript frameworks and there’s no way to teach every tool, so you pick the one you like. Still, I personally believe the success of Jamstack in the long run depends on its flexibility, which (despite what I said about the simplicity above) means we need to present the diversity of solutions it offers — both with and without JavaScript frameworks.
Where to go from here
Sheesh, you made it! I know I had a lot to say, perhaps more than I even realized when I started writing, so I won’t bore you with a long conclusion other than to say that, obviously, I have presented these myths from the perspective of someone who believes very deeply in the value of the Jamstack, despite it’s flaws!
If you are looking for a good post about when to and when not to choose Jamstack over server-side rendering, check out Chris Coyier’s recent post Static or Not?.
The post 5 Myths About Jamstack appeared first on CSS-Tricks.
source https://css-tricks.com/5-myths-about-jamstack/
from WordPress https://ift.tt/3f473mj via IFTTT
0 notes
Text
Things That Look Positive for Cryptocurrencies

https://netcurrencyindex3.shutterfly.com/netcurrencyindex Even though There have been market corrections in cryptocurrency market in 2018, everybody agrees that the best is yet to come. There have been a great deal of actions in the marketplace that have changed the tide for the better. With proper analysis and the perfect dose of optimism, anyone who is spent in the crypto market can make millions from it. Cryptocurrency marketplace is here to stay for the long term. In this guide, we provide you five positive factors which can spur further innovation and market worth in cryptocurrencies. 1. Innovation in scaling Bitcoin is the First cryptocurrency in the market. It has the highest number of users and the maximum value. It dominates the entire value chain of this cryptocurrency system. However, it's not without issues. Its major bottleneck is that it can handle only six to seven transactions per seconds. Apparently, there's scope for improvement in the climbing of transactions. With the help of peer to peer peer trade networks in addition to this blockchain technology, it's likely to increase the trade volume per second. 2. Legitimate ICOs Even though You will find cryptocoins with stable value in the market, newer coins are being made that are intended to serve a specific function. Coins like IOTA are intended to assist the Internet Of Things market exchanging electricity monies. Some coins handle the issue of cybersecurity by giving encrypted electronic vaults for storing the cash. New ICOs are Finding innovative solutions that disrupt the existing marketplace and bring in a new value in the transactions. They're also gathering authority in the marketplace with their simple to use trades and dependable backend operations. They're innovating both on the technology side regarding usage of technical hardware for financial and mining market side by providing more freedom and options to investors in the exchange. 3. Clarity on law In The current situation, most authorities are studying the impact of cryptocurrencies on the society and how its benefits could be accrued into the community at large. We can anticipate that there may be reasonable conclusions in accordance with the result of these research. Few governments are Already taking the route of legalising and regulating crypto markets just as with any other sector. This may prevent ignorant retail investors from losing money and protect them from harm. Abling regulations that increase cryptocurrency expansion are expected to appear in 2018. This may possibly pave the way for widespread adoption in future 4. Boost in application There Is tremendous enthusiasm for the application of blockchain technology in virtually every industry. Some startups are finding innovative solutions like digital wallets, debit cards such as cryptocurrencies, etc., this will raise the amount of retailers that are willing to innovate cryptocurrencies which in turn boost the amount of consumers. The Reputation of crypto resources as a trade medium is going to be bolstered as more people trust in this system. Although some startups might not endure, they will positively promote the general health of the market producing competition and innovation. 5. Investment from financial institutions Many International banks are watching the cryptocurrency scene. This can Lead to the entrance of institutional investors into the industry. The inflow Of substantial institutional investments will fuel the next stage of Development of this cryptomarkets. It's caught the fancy of several banks and Financial institutions. References Currency strength index https://en.wikipedia.org/wiki/Currency_strength_index
0 notes
Text
Things That Look Positive for Cryptocurrencies
Things That Look Favorable for Cryptocurrencies

https://netcurrencyindex3.kinja.com/the-way-cryptocurrency-works-1827256905?rev=1530354538938 While There are market corrections in cryptocurrency marketplace in 2018, everyone agrees that the best is yet to emerge. There are a lot of actions on the marketplace which have shifted the tide for the better. With proper analysis and the perfect dose of confidence, anyone who is invested in the crypto market can make millions from it. Here in this guide, we give you five positive elements that can spur further innovation and promote worth in cryptocurrencies. 1. Innovation in scaling Bitcoin is the First cryptocurrency on the marketplace. It has the highest number of users and the maximum value. It dominates the entire value chain of the cryptocurrency system. However, it's not without difficulties. Its major bottleneck is that it can handle just six to seven transactions per seconds. In contrast, credit card transactions average at couple of thousands per second. Apparently, there is scope for improvement in the climbing of trades. With the support of peer to peer trade networks in addition to this blockchain technology, it is possible to increase the transaction volume every moment. 2. Legitimate ICOs While You will find cryptocoins with stable value on the current market, newer coins are being made that are intended to serve a particular purpose. Coins like IOTA are meant to help the Internet Of Things market exchanging power monies. Some coins address the issue of cybersecurity by giving encrypted electronic vaults for storing the cash. New ICOs are Finding innovative solutions that interrupt the existing marketplace and bring in a new value in the transactions. They are also gathering authority in the marketplace with their simple to use trades and reliable backend operations. They are innovating both on the technology side regarding usage of technical hardware for mining and financial market side by providing more freedom and options to investors in the market. 3. Clarity on law In The present situation, most authorities are analyzing the impact of cryptocurrencies on the society and how its benefits could be accrued to the community at large. We can expect that there may be reasonable decisions as per the result of these studies. Few authorities are Already taking the route of legalising and regulating crypto markets just like any other market. This will stop ignorant retail investors from losing money and protect them from harm. Abling regulations which boost cryptocurrency expansion are expected to appear in 2018. This may possibly pave the way for widespread adoption in future 4. Increase in program There Is tremendous enthusiasm for the use of blockchain technology in virtually every industry. Some startups are finding innovative solutions like digital wallets, debit cards for cryptocurrencies, etc., this will increase the amount of retailers who are willing to transact in cryptocurrencies which consequently boost the amount of users. The Standing of crypto assets as a trade medium is going to be bolstered as more people trust within this system. Even though some startups might not endure, they'll positively promote the general health of the market creating competition and innovation. 5. Investment from financial institutions Many International banks are seeing the cryptocurrency scene. This can Lead to the entrance of institutional investors into the industry. The inflow Development of this cryptomarkets. It has caught the fancy of many banks and Financial institutions. References Currency strength index https://en.wikipedia.org/wiki/Currency_strength_index
0 notes
Text
Things That Look Favorable for Cryptocurrencies
Things That Appear Favorable for Cryptocurrencies

https://netcurrencyindex3.wordpress.com/2018/06/30/the-way-cryptocurrency-works/ While There are market corrections in cryptocurrency marketplace in 2018, everyone agrees that the best is yet to come. There have been a great deal of actions on the marketplace that have changed the tide for the better. With appropriate analysis and the right dose of optimism, anybody who's invested in the crypto market can make millions from it. In this article, we provide you five positive elements which can spur additional innovation and market worth in cryptocurrencies. 1. Innovation in scaling Bitcoin is the First cryptocurrency in the marketplace. It has the highest number of consumers and the highest value. It dominates the entire value chain of the cryptocurrency system. But, it is not without difficulties. Its major bottleneck is that it can handle just six to seven transactions per seconds. Apparently, there's scope for improvement in the scaling of trades. With the help of peer to peer peer trade networks in addition to the blockchain technologies, it is likely to increase the trade volume per second. 2. Legitimate ICOs While There are cryptocoins with steady value in the market, newer coins are being created that are designed to serve a particular purpose. Coins such as IOTA are meant to help the Internet Of Things market exchanging power monies. Some coins address the dilemma of cybersecurity by providing encrypted electronic vaults for saving the money. New ICOs are Finding innovative solutions that interrupt the existing market and bring in a new value in the trades. They are also collecting authority in the marketplace with their easy to use trades and dependable backend operations. They're innovating both on the other hand regarding use of specialized hardware for financial and mining market side by providing more freedom and choices to investors in the market. 3. Clarity on regulation In The current situation, most authorities are studying the impact of cryptocurrencies on the society and how its benefits can be accrued into the community at large. We can expect that there may be reasonable conclusions as per the result of these studies. Few governments are Already taking the route of legalising and regulating crypto markets just like any other market. This will stop ignorant retail investors from losing money and protect them from harm. Abling regulations that increase cryptocurrency expansion are expected to appear in 2018. This will possibly pave the way for widespread adoption later on 4. Boost in application There Is enormous enthusiasm for the use of blockchain engineering in virtually every business. Some startups are coming up with innovative solutions like digital wallets, debit cards for cryptocurrencies, etc. this will increase the number of retailers who are ready to innovate cryptocurrencies which consequently boost the amount of consumers. The Standing of crypto resources as a transaction medium is going to be reinforced as more individuals trust in this system. Although some startups might not survive, they'll positively promote the overall health of the market producing innovation and competition. 5. Investment from financial institutions Many International banks are seeing the cryptocurrency scene. This can Lead to the entrance of institutional investors to the market. The inflow Growth of this cryptomarkets. It has caught the fancy of several banks and Financial institutions. References Currency strength index https://en.wikipedia.org/wiki/Currency_strength_index
0 notes
Text
Wave of high-profile Twitter accounts hacked in bitcoin scam | USA News
Con artists on Wednesday apparently hacked into the Twitter accounts of technology moguls, politicians and major companies in an apparent bitcoin scam.
The ruse included bogus tweets from Barack Obama, Joe Biden, Mike Bloomberg and a number of tech billionaires including Amazon CEO Jeff Bezos, Microsoft co-founder Bill Gates and Tesla CEO Elon Musk. The fake tweets offered to send $2,000 for every $1,000 sent to a bitcoin address.
The cause of the breach was not immediately clear, but the scale and the scope of the problem suggested that it was not limited to a single account or service.
“This appears to be the worst hack of a major social media platform yet,” Dmitri Alperovitch, who co-founded cybersecurity company CrowdStrike, told Reuters news agency.
You may be unable to Tweet or reset your password while we review and address this incident.
— Twitter Support (@TwitterSupport) July 15, 2020
Twitter said in an email that it was looking into the matter and would issue a statement shortly.
“We’re continuing to limit the ability to Tweet, reset your password, and some other account functionalities while we look into this,” it tweeted.
Some of the tweets from hacked accounts were swiftly deleted but there appeared to be a struggle for control. In the case of billionaire Musk, for example, one tweet soliciting cryptocurrency was removed, but sometime later another one appeared.
Note the email addresses change. Twitter has no reason to give employees native access to impersonate users. Accounts are being stolen, auth token generated, and tweeted from. Note how legitimate users still have tokens to delete tweets. Not a clean hit.https://t.co/grlhbkhVhR
— Swift⬡nSecurity (@SwiftOnSecurity) July 15, 2020
Among the other accounts affected were those of Uber and Apple. Celebrities Kanye West and his wife, Kim Kardashian West, were also hacked.
Data risk
Some experts said it seemed probable that hackers had access to Twitter’s internal infrastructure.
“It is highly likely that the attackers were able to hack into the back end or service layer of the Twitter application,” said Michael Borohovski, director of software engineering at security company Synopsys.
“If the hackers do have access to the backend of Twitter, or direct database access, there is nothing potentially stopping them from pilfering data in addition to using this tweet-scam as a distraction,” he said.
Publicly available blockchain records show that the apparent scammers have already received more than $100,000 worth of cryptocurrency.
Me, the first time someone suggested using Twitter as an official emergency alert system: https://t.co/DyPWm0fm1w pic.twitter.com/aIjsyp8xJ5
— Blaine Cook (@blaine) July 15, 2020
Other experts said the incident has raised questions about Twitter’s cybersecurity.
“It’s clear the company is not doing enough to protect itself,” said Oren Falkowitz, former CEO of Area 1 Security.
Alperovitch, who now chairs the Silverado Policy Accelerator, said that, in a way, the public had dodged a bullet so far.
“We are lucky that given the power of sending out tweets from the accounts of many famous people, the only thing that the hackers have done is scammed about $110,000 in bitcoins from about 300 people,” he said.
Source link
قالب وردپرس
from World Wide News https://ift.tt/3gYRVr6
0 notes
Text
Original Post from InfoSecurity Magazine Author:
Shamoon-Slingers APT33 in Secret New Operations
Security researchers are warning oil and aviation industry organizations to be on their guard after spotting a notorious Iranian APT group using private VPNs to keep its activity hidden.
APT33 has been linked to the infamous Shamoon destructive malware which knocked out tens of thousands of PCs at Saudi Aramco in 2012 and has been deployed across Europe and the Middle East since.
Now Trend Micro has observed the group using a dozen command and control (C&C) servers in a highly obfuscated attack targeting a narrow group of organizations in the US, Asia and Middle East.
The group has been ramping up operations since 2018 with attacks on a UK and European oil company as well as supply chain organizations, the vendor claimed in a new blog post.
Already infected this year are a private American company that offers national security-related services, US universities, a military-linked US organization and several victims in the Middle East and Asia.
Although the malware linked to the small botnets used by the group is limited mainly to downloading and running additional malware, APT33 is going to great lengths to stay hidden.
“The C&C domains are usually hosted on cloud hosted proxies. These proxies relay URL requests from the infected bots to backends at shared webservers that may host thousands of legitimate domains,” said Trend Micro.
“The backends report bot data back to a data aggregator and bot control server that is on a dedicated IP address. The APT33 actors connect to these aggregators via a private VPN network with exit nodes that are changed frequently. The APT33 actors then issue commands to the bots and collect data from the bots using these VPN connections.”
The setting up of private VPNs is easily done via open source software such as OpenVPN, plus rented servers. However, by using this technique, the group’s efforts have actually become easier to track once the researchers discovered which exit nodes the VPNs are using.
They’re apparently being used to hide reconnaissance of possible future victims including oil company suppliers, and other research.
“APT33 used its private VPN network to access websites of penetration testing companies, webmail, websites on vulnerabilities, and websites related to cryptocurrencies, as well as to read hacker blogs and forums,” said Trend Micro. “APT33 also has a clear interest in websites that specialize in the recruitment of employees in the oil and gas industry.”
The vendor urged regular patching, employee security training, least privilege access policies and multi-layered protection for oil and utilities firms.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Shamoon-Slingers APT33 in Secret New Operations Original Post from InfoSecurity Magazine Author: Shamoon-Slingers APT33 in Secret New Operations Security researchers are warning oil and aviation industry organizations to be on their guard after spotting a notorious Iranian APT group using private VPNs to keep its activity hidden.
0 notes
Text
NFL Mock Draft Roundup: Defensive line is the obvious popular pick for the Eagles
The 2019 NFL Draft will be here before you know it. Mock draft season has already begun and there’s no shortage of opinion as to whom the Philadelphia Eagles might select with the No. 25 overall pick. Let’s take a look at which players the experts have the Eagles taking this week.
Defensive end is an obvious need with Brandon Graham and Chris Long potentially not returning to the Eagles in 2019. Polite was also the best player available on the board in this situation. Add in Howie Roseman’s #GatorBias and that checks all the boxes. The 20-year-old Polite finished his junior season with 45 total tackles, 19.5 tackles for loss, 11 sacks, six (!) forced fumbles, and four pass deflections. The Eagles’ defensive end rotation could look something like this in 2019: Derek Barnett, Michael Bennett, Josh Sweat, and Polite.
The Eagles could go in many directions here, but any time you can add a speedy edge rusher; you gotta do it. Brandon Graham is likely on the outs as a free agent, Derek Barnett is returning from injury and the team will need someone to rotate in with Michael Bennett at defensive end. Polite has sky high potential and instant impact ability. The Eagles might entertain getting a cornerback here, but with Polite on the board they should sprint to the podium.
Maybe this is too reactionary, but the Sunday’s playoff loss to the Saints showed that the Eagles need a true lead running back. Don’t forget that Jay Ajayi, who tore his ACL this season, is a free agent. If there’s a first-round back in the 2019 draft, it is Jacobs.
The storybook run of Philadelphia back through the playoffs was truly something to behold — but like all good things, it finally came to an end. And when it did, we noticed that, while DT Timmy Jernigan came back from a back injury to start meaningful reps, his quality of play decreased. His contract now non-guaranteed due to the non-football injury, and the depth behind him laughable, Jim Schwartz will look to add pass-rush juice with Wilkins, a 3-tech next to Fletcher Cox and a 1-tech stopgap when Cox isn’t on the field. In 2019, Philadelphia can now rush Cox, Wilkins, Michael Bennett, Derek Barnett, Josh Sweat, and Brandon Graham if he’s retained. That’s a whole lotta oomph.
With free agents Brandon Graham and Chris Long potentially moving on, Philadelphia could add some pass-rush help here. At 6-foot-6, 241 pounds, Sweat is a rangy prospect who is athletically gifted. And he produced, racking up 22 sacks the past two seasons. Receiver is also a position to watch, as Golden Tate and Mike Wallace are both on the free-agent market.
This would be the steal of the draft for the Eagles. Wilkins is a top-10 talent.
Polite had a breakout season for the Gators in 2018 with 45 tackles (19.5 for loss), 11 sacks, and best of all, 6 forced fumbles. He is one of the funnest prospects in this draft to watch, because of his combination of speed, pass rush feel, and relentlessness. Polite is a game-changing playmaker, and in any other draft, I would say there’s no way he could possibly make it to pick No. 25. However, in a draft that Howie Roseman called “historic” for it’s overabundance of defensive line prospects... maybe? I do also think that a trade up for a high-level, immediately-contributing defensive lineman prospect is possible, as the Eagles potentially have some outgoing pass rushers this offseason: Brandon Graham will be a free agent, and he is going to test the market. Michael Bennett was a good player in 2018, and he’ll be under contract in 2019 at a reasonable cost of $7 million, but he’s 33. Chris Long is also under contract, but he’ll be 34 in March, and he almost retired last year. Beyond that trio, the only defensive end on the roster with any legitimate NFL production is Derek Barnett. A defensive end in the first round is, in my opinion, by far the most likely position to be addressed. If there’s any concern with Polite, it’s that he’s undersized, at 6-foot-2, 242 pounds. If bigger offensive tackles get a hold of him, they can drive him back in the run game. That said, he plays with a violent, nasty demeanor, and is far from passive as a run defender. He’ll make his share of plays for loss, which is what Jim Schwartz prioritizes.
The Eagles’ safety group could use a youthful member. Thompson wasn’t a consistent play-maker for the Crimson Tide in 2018 ... but he’s very rangy and equally as impactful stopping the run as he is in coverage.
Adderley made a name for himself over the final months of the season and the FCS standout could find himself among the first 32 players taken. He’ll have a chance to prove himself at the Senior Bowl and the biggest question might be his size -- is he big enough to play safety over the course of an NFL season -- because every other aspect of his game checks all the boxes of what teams look for in a defensive back.
Harmon has the physicality to win at the catch point and over the middle, adding another outside weapon to the Eagles offense. He graded at 83.3 overall last season while winning 17 of his 30 contested catch opportunities.
The Philadelphia Eagles secondary is much better than most would assume given the lack of huge names on the depth chart, but there is still a need for cornerback upgrades and depth, as seen in the divisional round loss to the New Orleans Saints. Washington’s Byron Murphy is only around 5’11”, but he’s a feisty cover man with excellent instincts and closing speed. He showed off his ball skills all season for the Huskies and was a thorn in the side of Pac-12 quarterbacks. Some scouts might see Murphy as a slot cornerback, and that’s a possible destination for him in Philadelphia. But no matter where he’s lining up, he has the skills to make a major impact immediately.
Well, “The Magic Run” is over, Philly fans. Many Eagles’ faithful have moved to the stage of grief where they can accept this loss, and appreciate the good memories. Not me. My throat is still sore from screaming at the TV during the final drive, hoping Doug Pederson would hear me telling him there’s no need to rush or panic...that with a mere 27 yards to go, with two full minutes remaining, and time outs in your pocket, you could take your time, milk the clock, and get the winning TD with 20 seconds left. CERTAINLY there was no need to spaz out and inexplicably try to squeeze ONE MORE PLAY in before the two-minute warning when there was an eternity of time left and NO NEED to increase the chance of a mistake by rushing a play off when... OK wait: Serenity Now. As I was saying, the 2019 Eagles’ season has officially begun. There will be a lot of personnel decisions that will be made in the coming months. With OT Jason Peters likely retiring, the Achilles injury to OG Brandon Brooks, and even C Jason Kelce mentioning retirement...what will this O-Line look like next year? The D-Line, with the uncertain futures of Brandon Graham and Michael Bennett, has its own question marks. Multiple running backs may be needed. And, with all due respect to Nelson Agholor and Golden Tate, a field-stretching WR is also needed. The Eagles were a middling 16th in splash pass plays (20+ YDS) in 2018, and that needs to improve. Wolfpack WR Kelvin Harmon may not be a true burner, however he is very effective at all levels of the route tree. Coaches will love his attitude, work ethic, and the mean streak he brings to the table when blocking for the run. Harmon may not be the true complementary speedster the Eagles need right now, but he could be a legit #1 WR when Alshon Jeffery’s days are over in Philly. Plus, he’s just REALLY good at football.
Imagine how poorly a 30th-ranked pass defense would have fared without a capable line to mask its shortcomings. Dropping in the Jim Thorpe Award winner would be a step in the right direction.
Montgomery (5-11, 216 pounds) has emerged as a strong prospect because he finishes run strong and has shown some good hands and wiggle as a receiver. The Eagles have been a committee team under Doug Pederson, but injuries and ineffectiveness should make them consider one back who can do it all and complement Carson Wentz on every down.
There’s no question that the secondary needs some help, but there are a few promising pieces already in place that could turn into better players with a bit more patience and another season of development. The offensive tackle situation needs somewhat of a makeover. Jason Peters has been a staple of the front for nearly a decade, but injuries seem to slowly be taking a toll on his body. It’s unclear if the team will part ways with him this offseason, but an heir apparent needs to be in place due to his injury history. Cajuste is a very solid option to fill that void.
Protecting Carson Wentz has to be Philly’s primary objective, and finding a long-term replacement for Jason Peters should be a huge part of that. Cajuste is still smoothing out the rough edges in his game, but he’s got all the talent to be a stud blocker in the NFL.
It was a nightmare season for the Eagles secondary, with injuries and lackluster play equating to one of the leagues worst pass defenses. Needless to say that is not a good place to be in this pass-heavy age, so those issues on the backend must be resolved. Any plan to do that will likely include the addition of at least one high-quality cornerback or safety to the mix. Abram is a big, physical, aggressive safety with superb instincts who is at his best playing downhill, whether it’s against the run or even as a blitzer. Despite being an explosive athlete with decent ball skills who runs relatively well, Abram has some struggles in coverage but to his credit has made strides in this area. Abram also earns positive reviews for his intangibles such as toughness and leadership, showing the ability to anchor a secondary.
DE Jachai Polite - 3 DT Christian Wilkins - 2 OT Yodny Cajuste - 2 WR Kelvin Harmon - 2 S Deionte Thompson - 1 S Johnathan Abram - 1 S Nasir Adderley - 1 RB David Montgomery - 1 RB Josh Jacobs - 1 CB DeAndre Baker - 1 CB Byron Murphy - 1 DE Montez Sweat - 1
DE - 4 S - 3 DT - 2 OT - 2 RB - 2 CB - 2 WR - 2
Offense - 6 Defense - 11
We’re going to see a ton of mock drafts that have the Eagles taking defensive linemen this offseason. It’s a big need and the 2019 NFL Draft class is loaded with DL talent.
There’s a good chance Polite and/or Wilkins don’t even fall to the Eagles. Philly might luck out on the DL class being so deep, however, that someone unexpected falls in their laps at No. 25. Both of those players would be great additions to this defense.
Getting Cajuste would make me feel better about the Eagles’ offensive tackle situation. I really don’t love the idea of Halapoulivaati Vaitai entering the 2019 season as the undisputed starting left tackle if Jason Peters isn’t back. (Click here to read more about Cajuste).
I don’t really expect the Eagles to go with a wide receiver but maybe that changes depending on what happens with Nelson Agholor ($9.4 million cap hit in 2019, zero guaranteed), Mike Wallace (free agent), and Jordan Matthews (free agent).
I can’t see the Eagles taking a first-round running back. They haven’t done it in 34 years. I’ll believe it when I see it. With that said, the team does need to make some kind of significant addition(s) in the backfield.
I don’t see first-round cornerback happening, either. The Eagles have a lot of youth there already: Avonte Maddox (22), Sidney Jones (22), Rasul Douglas (23), Jalen Mills (24), and Cre’Von LeBlanc (24). We’ll also see what happens with Ronald Darby (25), who is set to be a free agent.
Safety is an underrated need with Rodney McLeod (9.9 million cap hit) coming off ACL/MCL injuries and Corey Graham (free agent) potentially retiring.
Who is your favorite for No. 25?
Source: https://www.bleedinggreennation.com/2019/1/19/18189479/nfl-mock-draft-roundup-2019-defensive-line-eagles-jachai-polite-end-tackle-pass-rush-philadelphia
0 notes
Text
Things That Appear Favorable for Cryptocurrencies
Things That Look Favorable for Cryptocurrencies

https://netcurrencyindex3.webnode.com/netcurrencyindex/ While There are market corrections in cryptocurrency market in 2018, everybody agrees that the best is yet to come. There are a lot of activities on the market that have shifted the tide for the better. With appropriate analysis and the right dose of optimism, anybody who is invested in the crypto marketplace can make millions from it. In this guide, we provide you five positive elements that may spur further innovation and market worth in cryptocurrencies. 1. Innovation in scaling Bitcoin is the First cryptocurrency on the marketplace. It has the maximum number of users and the maximum value. It dominates the whole value chain of this cryptocurrency system. But, it is not without issues. Its major bottleneck is that it can handle only six to seven transactions per seconds. In comparison, credit card transactions average at couple of thousands per second. Apparently, there's scope for improvement in the scaling of transactions. With the help of peer to peer peer trade networks in addition to this blockchain technologies, it is likely to grow the trade volume every moment. 2. Legitimate ICOs While There are cryptocoins with stable value in the market, newer coins are being created that are designed to serve a specific purpose. Coins such as IOTA are meant to help the Internet of Things marketplace exchanging electricity monies. Some coins address the issue of cybersecurity by giving encrypted digital vaults for saving the money. New ICOs are Finding innovative solutions that disrupt the existing market and bring in a new value in the trades. They are also gathering authority in the market with their easy to use trades and dependable backend operations. They are innovating both on the other hand regarding usage of specialized hardware for financial and mining market side by giving more freedom and choices for investors in the market. 3. Clarity on regulation In The current scenario, most authorities are studying the effect of cryptocurrencies on the society and how its benefits can be accrued into the community at large. We can expect that there may be reasonable decisions in accordance with the result of the studies. Few authorities are Already taking the path of legalising and regulating crypto markets just like any other sector. This may prevent ignorant retail investors from losing money and protect them from injury. Abling regulations which increase cryptocurrency growth are anticipated to appear in 2018. This will possibly pave the way for widespread adoption in future 4. Boost in application There Is tremendous enthusiasm for the use of blockchain engineering in virtually every industry. Some startups are finding innovative solutions such as digital wallets, debit cards such as cryptocurrencies, etc., this will raise the number of merchants who are ready to innovate cryptocurrencies which in turn boost the number of consumers. The Reputation of crypto resources as a trade medium is going to be reinforced as more individuals trust within this system. Even though some startups may not survive, they'll positively contribute to the overall health of the market producing innovation and competition. 5. Investment in financial institutions Many International banks are watching the cryptocurrency scene. This can Lead to the entrance of institutional investors into the industry. The inflow Of substantial institutional investments will fuel the next phase of Growth of the cryptomarkets. It's captured the fancy of several banks and Financial institutions. References Currency strength index https://en.wikipedia.org/wiki/Currency_strength_index
0 notes
Text
Registering Your Domain Name


Registering your domain name is the first step in establishing your online presence and reaching visitors and potential customers. I'll show you how to create and register your domain, avoid some of the pitfalls and stumbling blocks that can arise, and choose the best domain name to make sure that your site reaches the most people.
Why Register A Domain Name?
Registering your domain name requires choosing and purchasing a unique name. It allows you to secure your unique domain name so only you can use it to build a site or create a custom email. It is an extremely important part of designing your website, because that becomes the name and brand of your website. To buy a domain name, you can do so directly from your web hosting provider or through a separate domain name service (a recommended option for those using their own servers). Your domain is what you type into your web browser's navigation bar to take you to your site. For example, our domain is www.techshrewd.com.ng. People sometimes refer to the domain name as the URL or website.
How Do You Register A Domain Name?
When you register a domain name, you pay a registrar to secure the domain on your behalf from a registry. Each TLD (Top Level Domain) such as .COM, .NET, .NINJA, etc has their own registry that controls all their names. Registering a domain name means you are securing it for a set amount of time, usually a year. You can renew the domain indefinitely so it stays in your possession. However, you can only register it for as long as the registrar allows, which is usually a max of 10 years. Once you've wisely determined that building a website is an essential part of your business, you need to make another important decision: What's your domain name going to be? You know, it's the .com Web address by which all your (hopefully) many customers will find you. Furthermore, how do you go about staking your claim for it? Purchasing a name is a relatively simple process (although finding one that isn't already taken can be a challenge), but there are many factors that you should consider. Since your domain name is, in effect, the name of your website, you want to make sure you get a good one. But what makes a good one? And since it's also the address of your website, you want to make sure you understand the contract between you and the domain name registrar. Is it starting to sound a little more complicated? Don't worry: This primer can help you get started. Definition Of A Domain Name Domain names put a friendly face on hard-to-remember numeric Internet addresses. Every computer on the Internet has a unique Internet Protocol (IP) number. A domain name represents one IP number or more. For example, the IP number for the domain name techshrewd.com.ng could be 107.134.178.24 (Don't expect me to use my actual IP address. lol). The whole purpose is to give users an easy-to-remember handle so that when sending an e-mail to, let's say, the administrator of techshrewd.com.ng, you can type [email protected] instead of [email protected]. Anyone can buy a domain name. To do so, you visit a domain name registrar, such as QServers, key in the domain you want to buy, and pay a fee. You can't buy just any domain, of course—only one that isn't already registered by another person or business and that bears a valid domain suffix. In general, you'll want to buy something that is catchy and short so that it's both easy for people to remember, and easy for them to type in. You might discover that most of the shortest and catchiest names are already taken, especially if you are entering a niche that is well represented on the web space. To make things even more difficult, cyber squatters most times scoop these attractive names as an investment with a view of re-selling them later to legitimate would be site owners. Suffix Factor The suffix identifies the name as belonging to a specific top-level domain (TLD). As at this date, there are more than one thousand (1,000) TLDs available in the whole world. The most common TLDs include; .com, .edu, .net, .org, .tv, e.t.c. The most popular of these by far is .com, which is supposed to indicate commercial sites, but in reality has come to include almost everything. Web Hosts and Domain Names You needn't go to a dedicated registration service to buy a domain name, though. Web hosting services such as Qservers, DreamHost and HostGator, routinely offer a registration mechanism as part of the sign-up process. Hosting services typically offer a free domain name when you sign up for a Web hosting package. Keep in mind, however, that free domain names are usually free only for one or two years, after which the registrar will bill you for the annual or biennial fee. In other words, the provider of the free domain name pays only for the first billing from the registrar. Also take note of whether or not the provider charges a fee for setting up a domain name. Most services offer to transfer an existing domain name to their servers at no cost, but sometimes you'll find a setup fee over and above the registrar's fee Registrars offer a wide variety of registration durations—one year, three, five, and even ten. Be careful about registering for more than a year, though. First, there might be restrictions on your ability to transfer the domain name should the registrar give poor service. Second, the registrar could go out of business, leaving your domain name without a host. Check the policies closely. Domain Contract There is common notion that once bought, a domain name is our forever under all circumstances whatsoever. This is not necessarily the case. Be absolutely certain to research what you're getting before you pay. The contract you sign with the registrar could affect you in a number of ways. Many registrars reserve the right to revoke your domain name for specific reasons, typically if you use the domain for illegal purposes or purposes deemed unacceptable (such as spamming). Many contracts contain a clause letting the registrar delete your domain name for no apparent reason. The implication, of course, is that the domain name is the registrar's, not yours. Furthermore, practically all registrars reserve the right to make changes to the registration agreement whenever they wish and without letting you know. The point is that every registrar needs to be checked out carefully. The Hold - Up Even when you register and pay for your domain name, you won't necessarily be able to use the name for several hours or even a few days. The domain must propagate, meaning that the official domain name registry must be updated with your website's Domain Name System information. That's something that occurs on the backend without any need of input from you. Some registrars promise to have the name up nearly immediately, but the delay can be up to seven days. Typically, though, you should expect to see the domain name up and running on the Web within 48 hours. Note that you can also transfer your domain name from one registration service to another. You'll want to do this if you're not satisfied with your current domain hosting service, if you find a better deal when your current registration is coming due, or, most likely, if you've signed up with a Web hosting service that will also transfer your name to its site. Expect to get the transfer for free, but if that isn't offered, search for another domain hosting service. Under no circumstances should you pay more to transfer a name than to get a new one. Check what the transfer will require. Does the new service handle the task completely? Or do you have to go into your current registrar's site and change the technical details manually? Finally, check the transfer policy of the registrar before registering your domain name. Typically, you can't transfer a name during the first 60 days after registration, but the period could be much longer. Don't expect any registrar to refund money you've paid for months of service you won't use. Read the full article
0 notes
Text
New Post has been published on Globeinfrom
New Post has been published on https://globeinform.com/godaddy-acquires-sucuri-to-boost-wordpress-protection/
GoDaddy Acquires Sucuri to boost WordPress Protection
GoDaddy is bolstering its Security portfolio with the acquisition of website Security platform provider Sucuri, in line with a Wednesday statement. Sucuri will maintain its normal business operations, even as GoDaddy will amplify Sucuri’s Security services to its clients. Monetary phrases of the deal had been no longer disclosed.
The agencies stated collectively they plan to provide new Security merchandise “within the close to destiny.”
Sucuri offers gear to mitigate Safety incidents and maintain website reputations whilst they are attacked. in step with the Symantec Internet Security Threat File 2016, websites blacklisted following a hack revel in an eighty percentage drop in traffic lasting more than one days, and 3 out of 4 legitimate websites contain unpatched vulnerabilities, making sturdy Risk response a doubtlessly treasured add-on for GoDaddy customers.
Further to virtual vulnerability patching and malware scrubbing, Sucuri gives a WordPress Security plug-in, in step with the announcement, and is deeply worried inside the WordPress network. GoDaddy has been gradually constructing up its WordPress portfolio, with latest moves such as the September acquisition of ManageWP and December release of Seasoned ManageWP as a part of its Seasoned Application.
“The extensive majority of our customers aren’t internet site Protection experts, nor must they need to be to comfy their websites,” Kevin Doerr, Senior Vice-chairman and General Manager of Security, GoDaddy said in an announcement. “Combining Sucuri with GoDaddy’s scale will boost digital Security for our clients by making it convenient, well timed and low-priced. We’ll continue to put money into Sucuri and mutually broaden products that propel Safety answers ahead.”
Sucuri’s portfolio of offerings includes a web software firewall (WAF) and intrusion prevention device (IPS), a content distribution community (CDN) to manipulate traffic and optimize performance, a cloud-based totally backup provider, real-time DDoS mitigation, and non-stop monitoring.
“On account that our inception we’ve continually had a single aim of protective our clients’ websites. We attain this with quite simple methods: build things that supply value and that stay beforehand of emerging threats,” stated Sucuri founder Daniel Cid. “We have the opportunity to take this equal philosophy from some hundred thousand websites to hundreds of thousands of sites. From our conversations with GoDaddy, it has become clear that we percentage the equal purchaser-first philosophy and commitment to helping clients be at ease online.”
Sucuri’s Safety studies and analysis has caused the invention of several vulnerabilities, such as malicious credit score-card scraping code injected into e-trade modules disclosed earlier this month, and a WordPress Rest API Endpoint worm located in January by using one of the agency’s researchers.
WordPress Protection Tick-list for WordPress websites WordPress Protection Tick list
Here’s an easy Tick-list for WordPress owners and publishers. WordPress is one of the most famous website structures because of it is ease of use but, it has its problems, and it is due to its recognition that hackers use this platform to attempt to inject their malware and malicious scripts. WordPress Protection has to turn out to be important today to guard not simplest your internet site but your brand recognition.
Unknown Infections
Frequently WordPress proprietors are unaware that their internet site has been hacked. Simply because your internet site has been hacked it would not always suggest you will see an ordinary picture whilst you get entry to your website. Hackers Regularly hide the truth they’ve hacked your web page as they have injected a mailbox and are spamming out of your IP address.
Use our Tick-list for the rules of top WordPress Safety
1. Clean and remove adware, malware, and viruses from your Computer/Mac earlier than getting into the backend of your WordPress installation
2. Backup your internet site earlier than you do something, this is easily accomplished with using Backup Buddy.
three. In no way use ‘admin’ as a username.
four. usually, use a sturdy password.
5. live Up to date – Ensure your WordPress installation and WordPress Plugins are usually up to date. See Modern-day WP Safety Updates within the resources section beneath.
6. Restriction Login Tries – Make sure you reduce the login Tries right down to round three Tries. Don’t make it easy for the hackers.
7. put off unwanted WordPress Themes – when Topics are nonetheless on your website and they exit of date Hackers use those to benefit access. best have the subject you’re the usage of hooked up and keep that up to date.
eight. Spring Easy – Your WordPress website may have other folders on the basis of your server. Do you really want them or are they development areas. If you Don’t need the folders delete them.
9. Your Website hosting organization – Ensure you are the use of a Hosting employer that specializes in WordPress installations. WordPress servers need special interest to defend your internet site.
10. Double Layer Authentication – Use a delivered layer of Safety.
Summary
Whilst the Tick-list above isn’t an exhaustive list, it’s far a basic degree of Protection. Safety is the begin of the system, monitoring your website on an each day basis is essential. We understand that many internet site proprietors Simply don’t have the time or the expertise, so we offer 3 services that may be located inside the resources phase underneath.
Pointers for WordPress Protection
Truth is, if a successful grasp of the script objectives your site, there’s really no way to save you an intrusion. What you’re about to read beneath are a few precautionary moves you could take to fast limit the chance to an appropriate stage. If your WordPress site is properly protected chances are a hacker would decide on selecting every other, simpler victim.
Starting with the more apparent ones:
1. Overlook approximately the usage of “admin” as your username.
The various assaults target the default WordPress username with brute force, password cracking robots. The first step is to trade your “admin” or “administrator” username from the WordPress Management Panel.
– Go to MySQL tool (PHPMyAdmin) – Discover your database – Visit wp_users and skim for “admin” – Below user_login column, exchange it for something else. This certainly leads to the subsequent…
2. Pick out a robust password
Choose a password that consists of more than one upper and lowercase letters, in addition to symbols including “!@#$%^&*()” Go to Users->Your Profile and trade it thru the “New password” subject at the bottom. This may make it manner more difficult to crack it down. Make sure you do the identical for your FTP Cpanel Hosting account password and Do not use the same one you used in WordPress.
3. Regularly backup your database
You heard this one before. Do regular backups or you will finally remorse it. You may lose all your work if being hacked. Additionally, do not forget to backup on every occasion you make modifications. you may do that via the usage of a plugin or manually.
4. usually Update your WordPress
there is truly no reason to live at the older variations when there may be a new one available. WordPress updates incorporate bug fixes, vulnerability fixes and cover Security flaws found by way of the extensive WordPress community. equal goes for updating Subject matters. It is easy and green. Sincerely, it’s miles the pleasant and easiest way to save you your page from malicious sports, which might be maximum probably as result of a compromised and now not an absolutely Updated application, website, exploitable personal home page scripts, and so forth. All the old versions of your programs can be taken into consideration as a capability Security holes. They could truly be utilized by the attacker, who’s (most of the time) an automated spider.
0 notes
Text
Original Post from Talos Security Author:
By Matthew Valites with contributions by Joanne Kim and Edmund Brumaghin
Executive summary
Mobile stalkerware has all sorts of wide-ranging consequences. The creators of these types of apps can track user’s locations, see their social media usage and more. And they certainly open the door for abuse by governments hoping to spy on their citizens, parents looking to track their children or controlling spouses hoping to track every move their partners make. This class of software exists to surreptitiously get and provide this personal information, sometimes in real time.
Cisco Talos recently spotted a wave of vendors hawking this software, designed to spy on unsuspecting users. We observed apps across the globe — including activities in countries that have some of the worst human rights records — with vendors offering language- and country-specific services. In all, there were 87 vendors we discovered as part of our research, which we believes poses a serious threat to at-risk individuals. The stalkerware space is completely unregulated, and these apps are allowed to exist on many app stores for extended periods of time, with their creators even offering easy to follow tutorials online as to how to trick users into downloading these apps. This is an easily accessible, yet volatile, market.
Previous research by Talos shows adversaries, including nation-state level actors, using open-source mobile device management (MDM) software and fake apps to surreptitiously control compromised devices and exfiltrate sensitive data. Leaked data shows that five to 10 years ago, this capability would cost an adversary a significant amount of money. Today, anyone with an internet connection can choose from a range of commercial vendors providing identical capabilities for anywhere from free to $80 per month. It’s even got to the point that prominent government vendors are reselling off-the-shelf “toy” software to track “unfaithful spouses,” according to leaked emails. A flourishing marketplace exists for these dual-use applications that provide tracking, remote control, and interception capabilities. Operating on the internet with impunity, some of the most intrusive applications include the ability to covertly listen to active phone calls and enable the camera or microphone.
The basics
Most commercially available stalkerware applications are sold and distributed directly through vendor sites. Some vendors host their applications for download without authentication while others require signing up and paying for the service. Of the vendors selling or reselling spy software that we identified, only two were available through the Google Play store.
Nearly all vendors offer varying capabilities, some dependent on whether the target devices are rooted or jailbroken. In the table below, we compare a popular commercial stalkerware vendor called “FlexiSpy” with a government-level offering called “FinSpy.” Most capabilities present within nation-state level software are comparable to those present within the most popular consumer-level stalkerware applications that we identified. Where the government options differ is in their live remote forensics and anti-virus avoidance. While Flexispy provides call interception, most vendors only provided call metadata. In 2014, the United States Federal Trade Commission (FTC) fined StealthGenie $500,000 for violating the Wiretap Act by selling an interception device. While live intercept may be too risky of a capability for most vendors to offer, geolocation tracking is a standard offering.
Some vendors provide premium multilingual installation support services to assist consumers with installing the software on the device. The screenshot below shows an example of an Mspy reseller offering a Spanish chat service. The ad states, “Spanish support, free consultation through chat.” While presumably there to offer legitimate technical support, previous reports have shown the support staff often acts inappropriately.
How widespread of a problem is this?
Using passive DNS telemetry, we observed activity to these domains from 171 different countries in a single day. The darker the country in the map below, the higher number of unique remote IP addresses we observed. What’s most immediately apparent is how global these applications are used. Brazil and the United States combined account for nearly 50 percent of the observed queries. Italy, the United Kingdom, and India round out the top five with less than 4 percent of the total queries coming from each country. Spying capabilities once restricted to certain nation-states have been democratized and are being used all over the world.
The next table shows the most queried domains from our sample data. The top domain is the API endpoint for an application owned by a vendor called spyhuman[.]com, who provides a free offering that includes geolocation capabilities. This application is supported on only six vendors’ devices, yet claims the top spot for most-queried domain, and was observed primarily in the Middle East and Northern Africa. The third domain is for Cerberus security, which for five Euros per device per year, offers supposed anti-theft geolocation services for Android devices, including on Android Wear smartwatch devices. Also included in the top 10 most-queried domains is thd[.]cc, the domain hosting applications for another stalkerware app called mspy[.]com.
Spyhuman was the victim of an attack in 2018 that exposed collected metadata from remote devices. Be it the shaky moral ground of the businesses, or the sensitive data they contain, spyware providers have found themselves the targets of hackers. Four other businesses, including a parent company that owns multiple spyware companies are known to have been successfully breached. One of those companies admitted to a breach of photographic material (presumably acquired from targets by customers) that ultimately and indefinitely halted its spyware products.
Cross-referencing DNS data with data from the CATO Institute’s Human Freedom Index, which attempts to quantify the state of global human freedom, we can see query activity to spy domains from the 10 lowest-ranked countries on the index. Egypt has the most number of queries at 6,750 from 179 unique requestor IPs, whereas Yemen has the most unique requestor IPs at 224 with 1,326 queries. We observed queries to stalkerware backend API infrastructure in each of these countries, indicating not just web browsing activity, but active use of these applications. That these businesses sell their wares in countries with known poor human rights records calls into question the morality of their operations.
What can be done?
Many of the vendors Talos researched publicly advertise their services toward parents monitoring the safety of their children, consumers who want to prepare themselves in the event of the theft of the device, or businesses monitoring employees’ devices. And our research shows evidence of the latter. We see businesses intentionally whitelisting domains belonging to some of these vendors, ostensibly to ensure service availability when using the applications legitimately for enterprise device management. However, some sites overtly display suggestive marketing material that indicates a more nefarious use-case for the software, as can be seen in the image below. No longer solely in the realm of nation-states, anyone with intent and device access can afford to use these spy-like capabilities.
Detecting whether a covert spy application is installed on a device is, by intention, difficult. Additionally, at-risk individuals can leak metadata to adversaries even without these apps installed. With access to individual accounts, such as Facebook and iCloud backups, abusers can get sensitive information without installing spyware. The Federal Trade Commission has information for stalking victims on their site. Additionally, users who suspect they may be the victim of spyware can check a few things:
Rotate and use unique passwords for sensitive accounts, and use multi-factor authentication where possible.
Many social media services show account logins by device. Check for unauthorized devices.
Disable geolocation permissions on applications and devices as much as possible.
Keep devices and apps patched to prevent possible vulnerability exploitation.
Conduct sensitive conversations in person or use a new phone.
Protect your devices with a strong password/pin.
Use only official application stores to install software.
Factory reset or wipe the device.
Use stalkerware installation guides to determine if your devices has signs of being configured to allow installation of these applications.
Be mindful that this software can exfiltrate dialed phone numbers, application chats and SMS. If you fear you’re at risk and must seek help, try to use a known secure phone.
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: The commoditization of mobile espionage software Original Post from Talos Security Author: By Matthew Valites with contributions by Joanne Kim and Edmund Brumaghin…
0 notes