#antivirus services
Explore tagged Tumblr posts
Text
Shield Your Digital World: The Ultimate Guide to VPN Security with NordVPN
#vpn#best vpn#vpn service#free vpn#clone vpn#cyberattack#antivirus#cyber security#sql#software#vps hosting#vps server in saudi arabia#buy windows vps#vps#vps34 in1#dedicated server#pcs#printer#material#security
2 notes
·
View notes
Text

Best Cyber Security Services- NewGig Secure Solutions
#firewall#security#network security services#network security solutions#network security market#antivirus
2 notes
·
View notes
Text
Surfshark VPN Review: Defining safe digital finance after VPN
How does an internet connection from a VPN shield my valuable and personal information from hackers or any cyber thugs especially when am connected to a public Wi-Fi connection? Why is the use of a VPN effective in protecting from third parties tracking and unauthorized access to my activities and information? Which technology makes my Internet connection secure; how does the VPN encrypt my connection to keep my information safe?
A VPN is a shield when you use commonly available Wi-Fi connection from companies or hotels as these connections are very easy to hack.
It becomes almost not possible for hackers and other cyber criminals to get to your private data through hiding your IP address plus encoding the data transferred. This security measure is important when making a transaction online or when passing personal information via public networks.
A Surfshark VPN download works by seeking to shield your internet traffic by establishing an encrypted connection between your device and the internet. This encryption simply implies that nobody can eavesdrop or even decode your information to the extent that your privacy is protected. Consequently, the online presence is protected from spying, and thus, you get advanced privacy and security.
The use of a Surfshark VPN masks your Internet connection, thus minimizing the ways in which a third party can monitor the Internet use. This feature helps to protect you from advertisers, internet service providers and any other entity that would like to harvest your data unconsciously. For this reason, experience shows that to engage in a VPN guarantees that your Internet identity remains protected and beyond the reach of the former.
Due to the use of encryption passcodes administration, VPNs are essential in the protection of finances. VPN’s come in handy especially when one is accessing a banking website or transacting online, especially on a public Wi Fi; the connection is encrypted. This VPN makes users IP address anonymous hence making it hard for third party to follow the activities done online or even identify the area the user is from.
With the Surfshark One package, you're not just getting a VPN; you're also equipped with top-notch antivirus software to fend off malware threats that might target your financial information. Plus, the package includes an alert system to give you a heads-up if your email or credit card details show up in any data breaches, so you can quickly take steps to secure your accounts.
By offering such a thorough suite of online protection tools, Surfshark Review ensures both individuals and businesses can navigate the digital financial world with confidence and peace of mind. Surfshark vpn extension
Surfshark has an early Black Friday deal available:

Other Surfshark Products: SurfsharkAntivirus and SurfsharkIncogni
0 notes
Text
https://hpservicesbadanagar.online
We are one of the best laptop repair hardware and software service providers in India and we assure to provide servicing for almost all kind of laptop brands.
1 note
·
View note
Text
Protect Your Data with Waredot Anti-Ransomware

In a world where digital threats are constantly evolving, protecting your data is more important than ever. Ransomware attacks can cripple businesses and personal systems alike, leading to data loss and significant financial damage. Waredot Anti-Ransomware offers a robust solution to safeguard your digital assets. In this blog post, we'll explore how Waredot Anti-Ransomware can protect your data and provide peace of mind.
Introduction to Ransomware and its Impact on PC Users
Ransomware - the mere mention of this malicious software is enough to send shivers down the spine of any PC user. Imagine waking up one day to find all your files locked and held for ransom by cybercriminals. Terrifying, right? But fear not! In this blog post, we will introduce you to Waredot Anti-Ransomware, your ultimate shield against these digital extortionists. Stay tuned to learn why every PC user should have Waredot Anti-Ransomware installed for peace of mind and protection in the online world.
What is Waredot Anti-Ransomware?
Ransomware is a type of malicious software that encrypts a user's files and demands payment for their release. Waredot Anti-Ransomware is a powerful tool designed to protect PC users from falling victim to these extortion schemes.
Unlike traditional antivirus programs, Waredot specifically targets ransomware threats, offering an added layer of security against this evolving form of cybercrime. By detecting and blocking ransomware attacks in real-time, Waredot helps safeguard your valuable data and personal information.
With its advanced algorithms and threat intelligence capabilities, Waredot continuously monitors your system for any signs of malicious activity. This proactive approach ensures that your files remain safe from unauthorized encryption attempts.
By incorporating cutting-edge technology and innovative security measures, Waredot Anti-Ransomware provides PC users with peace of mind knowing that their data is protected against the growing threat of ransomware attacks.
How Does Waredot Anti-Ransomware Protect Your PC?
Waredot Anti-Ransomware offers robust protection for your PC against ransomware attacks. By continuously monitoring your system, it can detect suspicious activities and behaviors commonly associated with ransomware.
The software uses advanced algorithms to identify and block malicious files before they have a chance to encrypt your data. It also provides real-time scanning of incoming files and emails to prevent any ransomware threats from infiltrating your computer.
Moreover, Waredot Anti-Ransomware creates secure backups of your important files, ensuring that even if you fall victim to an attack, you can restore your data without having to pay a ransom.
With its proactive approach to cybersecurity, Waredot Anti-Ransomware gives you peace of mind knowing that your PC is constantly defended against the ever-evolving threat landscape of ransomware.
Frequently Asked Questions about Waredot Anti-Ransomware
Have questions about Waredot Anti-Ransomware? You're not alone! Let's address some common queries to help you better understand this essential tool.
One common question is, "Does Waredot Anti-Ransomware slow down my computer?" The answer is no! This software runs efficiently in the background without impacting your PC's performance.
Another frequent query is, "Can Waredot Anti-Ransomware protect against all types of ransomware?" Yes, it uses advanced algorithms to detect and block various ransomware strains effectively.
Users often ask, "Is Waredot Anti-Ransomware easy to install?" Absolutely! With a user-friendly interface and simple installation process, safeguarding your data has never been easier.
"Does Waredot offer customer support?" Yes, their dedicated team is available to assist with any inquiries or issues promptly.
1 note
·
View note
Text
a failed update from billion-dollar cybersecurity firm crowdstrike has crashed windows machines worldwide today (july 19th 2024), leaving everything from airport terminals to checkout machines to delivery apps to banks stuck with a blue screen of death. here's a screenshot from downdetector (au) to illustrate:


the issue appears to be with crowdstrike falcon, a form of antivirus software widely used in the corporate world -- with emphasis on the world. there have been reports from the us, uk, australia, germany, india, france, japan and more. places affected include (but are not limited to) supermarkets, banks, basically every airline, public transport networks, major broadcasters, emergency services, corporate offices, healthcare providers and stock exchanges.



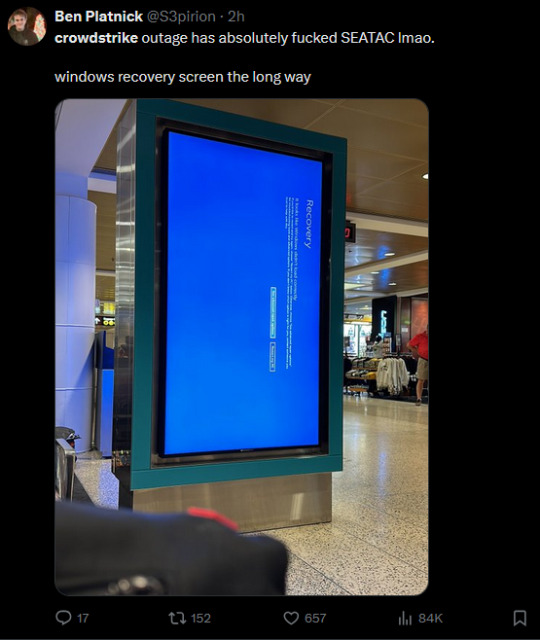

(woolies pic via archiestaines9 on twitter; s3pirion; akothari. yes that is masahiro sakurai of smash bros fame)
emergency service lines are currently experiencing problems within the american states of alaska, arizona, indiana, minnesota, new hampshire and ohio. similar problems likely plague other areas of the world, they just haven't been reported on yet. australian emergency services are operating, and critical infrastructure remains stable. be sure to check in with the local news stations still online for more updates.
welcome to y2k............................. 2!!!!!!!!!!!!!

13K notes
·
View notes
Text
Avast Antivirus on suosittu valinta tietokoneiden suojaamiseen viruksilta, haittaohjelmilta ja muilta online-uhkilta. Kuitenkin, kuten kaikki ohjelmistot, se voi joskus kohdata ongelmia. Tässä oppaassa käsittelemme joitain yleisimmistä ongelmista, joita käyttäjät kohtaavat Avast Antivirus -ohjelman kanssa, ja tarjoamme yksityiskohtaisia ohjeita näiden ongelmien vianmääritykseen ja ratkaisemiseen.
#Avast Antivirus#Avast Antivirus suomi#Avast Antivirus customer service#Avast Antivirus tecnical support#Avast Antivirus numero
0 notes
Text
Beware of cyber scams: How hackers tried to scam me - CyberTalk
New Post has been published on https://thedigitalinsider.com/beware-of-cyber-scams-how-hackers-tried-to-scam-me-cybertalk/
Beware of cyber scams: How hackers tried to scam me - CyberTalk


Lari Luoma has over 20 years of experience working in the fields of security and networking. For the last 13 years, he has worked with Check Point Professional Services as a security consultant, helping customers worldwide implement the best-in-class cyber security. He is a subject matter expert in hyper-scalable security solutions.
EXECUTIVE SUMMARY:
Cyber crime is on the rise. People encounter scams in their everyday lives without really understanding they are being scammed. These vexing and vicious scams can arrive in various forms; phishing emails, fraudulent phone calls or text messages. All of them aim to exploit unsuspecting victims for financial gain. Recently, I found myself on the receiving end of one such scam. This led me to reflect on how important it is to actively anticipate the latest cyber threats and to maintain vigilance.
It began with an email notification purporting to be from PayPal. The notification claimed that my account had been charged $600 for McAfee Antivirus software. I was urged to take immediate action. The email instructed me to contact a provided customer service number to resolve the supposed issue. As I scrutinized the email further, alarm bells rang in my mind. The sender’s address raised suspicion— the address was connected to a generic Gmail account, a far cry from the official communication channels one would expect from PayPal.
Despite my skepticism, I decided to call the provided number to investigate. What ensued was a conversation with an individual who claimed to be a customer service representative. However, the person’s demeanor was far from professional. The individual immediately inquired about my location and whether or not I was on my laptop. When I requested a reason and asked why we couldn’t handle the issue over the phone, the person replied that it was because a laptop has a bigger screen, and it would be easier to fill out the form that he was going to send.
Sensing something amiss, I stated that I wasn’t home and didn’t have my laptop with me, to which the caller abruptly hung up. It was a clear indication of foul play; a phishing attempt to obtain sensitive information or compromise my device’s security.
Reflecting on this encounter, I realized just how easily people can be fooled if they think that they are going to lose money. These scammers were very unprofessional and didn’t sound authentic on the phone. Also, using a Gmail address was a big mistake for them. If they had executed on their activities with a bit more sophistication and polish, I might have fallen victim to the scam.
Here are crucial tips to help you and yours avoid falling victim to similar scams. Consider sharing these tips with employees:
1. Verify sender information: Always scrutinize the email sender’s address. Look for any red flags, such as suspicious domain names or generic email providers (like Gmail or Yahoo), especially if they’re being used for “official” communications from reputable organizations.
2. Exercise caution with unsolicited requests: Be wary of unsolicited emails or messages requesting urgent action, especially if the emails or messages involve financial transactions or account verification. Legitimate companies typically don’t request sensitive information via email.
3. Double-check website URLs: Before clicking on any links in emails, hover over them to preview the URL. Verify that they lead to legitimate websites. Make sure that they aren’t phony links to phishing sites that were designed to steal login credentials or personal data.
4. Use two-factor authentication (2FA): Enable 2FA wherever possible, especially for sensitive accounts, like bank accounts or email accounts. This adds an extra layer of security by requiring a secondary verification method, such as a code sent to your phone.
5. Stay informed and educated: Keep abreast of the latest cyber security threats and techniques used by scammers. Organizations like the Federal Trade Commission (FTC) and cyber security blogs, like CyberTalk.org, provide valuable resources and tips for protecting yourself online.
6. Report suspicious activity: If you encounter a potential scam or phishing attempt, report it to the appropriate authorities or the impersonated business. This helps raise awareness and can compel a business to act, thereby preventing others from falling victim to similar schemes.
7. Don’t engage in discussion with scammers: If the email includes a phone number, you shouldn’t call to resolve the alleged issue.
Maintain vigilance regarding any unsolicited messages that you receive. Don’t click on any links and don’t call numbers provided. If an email informs you that a large sum has been debited from your account, consider whether or not the story seems authentic. Check your credit card bills and contact the real customer support numbers for the company that the scammers are purportedly from.
For instance, in the case that I outlined above, I should have researched the real customer support number for McAfee or Paypal and called there, rather than calling the number that was included in the message. Stay savvy and secure.
For more insights from cyber security expert Lari Luoma, click here. To receive clear cyber insights, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#2fa#Accounts#analyses#antivirus#authentication#awareness#Business#Check Point#code#communication#communications#Companies#compromise#credentials#credit card#crime#customer service#cyber#cyber crime#cyber scams#cyber security#cyber security blogs#Cyber Threats#cybersecurity#data#domain names#double#email#employees#Exercise
1 note
·
View note
Text
Endpoint Security: Safeguarding the Digital Perimeter in an Evolving Landscape

In the dynamic landscape of cybersecurity, where threats are ever-evolving and the attack surface is expanding, ensuring the security of endpoints has become a mission-critical aspect for organizations. Endpoint security, a comprehensive approach to protecting devices connected to a network, has become increasingly vital as the number of remote workers and connected devices continues to rise. This blog post delves into the key components of endpoint security, its importance in the current digital ecosystem, and the evolving strategies to address emerging threats.
Understanding Endpoint Security:
Endpoint security encompasses a suite of measures designed to secure individual devices – or endpoints – that connect to an organization's network. These endpoints can range from traditional desktops and laptops to smartphones, tablets, servers, and other internet-enabled devices. The goal is to create a robust defense that safeguards these endpoints against a multitude of cyber threats.
Key Components of Endpoint Security:
1. Antivirus and Anti-malware Solutions:
Fundamental to endpoint security, antivirus and anti-malware solutions provide real-time protection against malicious software. These tools detect and eliminate viruses, Trojans, and other malware, preventing them from compromising the integrity of endpoints and spreading throughout the network.
2. Firewall Protection:
Firewalls act as a barrier between an endpoint and the external network, monitoring and controlling incoming and outgoing traffic. By blocking unauthorized access and potential threats, firewalls play a crucial role in securing endpoints and preventing malicious activities.
3. Email Security:
Given the prevalence of phishing attacks and email-based threats, endpoint security often includes robust email security features. These capabilities help detect and block phishing attempts, malicious attachments, and other email-borne threats, reducing the risk of compromise through social engineering.
4. Device Control:
Endpoint security solutions often incorporate device control features, allowing organizations to manage and control the use of peripheral devices connected to endpoints. This helps mitigate the risk of data leakage and unauthorized access through USB drives and other external devices.
5. Behavioral Analysis:
Modern endpoint security solutions leverage advanced behavioral analysis to detect anomalies in endpoint behavior. By establishing a baseline of normal activities, these tools can identify deviations that may indicate a security threat, enabling proactive responses to potential risks.
The Importance of Endpoint Security:
1. Data Protection:
Endpoints serve as gateways to an organization's sensitive data. Strengthening endpoint security is crucial for preventing unauthorized access, data breaches, and the compromise of critical information. Robust endpoint security ensures the confidentiality and integrity of data.
2. Threat Mitigation:
Endpoints are frequent targets for a variety of cyber threats, including ransomware, malware, and advanced persistent threats. Endpoint security acts as the first line of defense, detecting and neutralizing these threats before they can infiltrate the network and cause harm.
3. Adaptation to Remote Work:
The rise of remote work has expanded the attack surface, making endpoint security even more critical. With employees accessing corporate networks from various locations and devices, organizations must implement robust endpoint security measures to protect against potential vulnerabilities and cyber threats.
4. Regulatory Compliance:
Endpoint security is vital for maintaining compliance with industry regulations and data protection laws. Failure to secure endpoints adequately can result in legal consequences, financial penalties, and reputational damage for organizations.
The Future of Endpoint Security:
As cyber threats continue to evolve, so must endpoint security strategies. The integration of artificial intelligence and machine learning into endpoint security platforms enhances their ability to detect and respond to emerging threats in real-time. Additionally, the adoption of zero-trust security models assumes that no device or user should be automatically trusted, providing a more proactive and adaptive approach to endpoint security.
In conclusion, as the digital landscape evolves, organizations must recognize the critical role of endpoint security in safeguarding their networks and data. Investing in robust endpoint security solutions not only protects against current threats but also ensures a proactive defense against emerging cyber risks. In this era of constant connectivity, endpoint security stands as the frontline defense, securing the gateways to the digital realm and fortifying organizations against the ever-evolving cybersecurity challenges.
0 notes
Text
Install and Start Your Norton Secure VPN Free

FREE DOWNLOAD NORTON VPN
CLICK HERE MORE INFO
#norton login#norton download#norton antivirus#1950s#norton 360#norton 360 login#norton customer service#norton antivirus free#norton lifelock#norton download for pc#norton 360 download#norton download free#norton download login#vpn#free vpn#best vpn#clone vpn#vpnservice
0 notes
Text
Safeguard Your Computerized Climate: Expert PC virus removal is essential
In today's connected society, where personal and professional life rely heavily on technology, where PC infections are regrettable but common. These vindictive elements can cause destruction on your PC, endanger classified data, and corrupt the usefulness of the framework. This article investigates the significance of employing an expert to eliminate PC Virus Removal and makes sense of why keeping a protected and successful computerized environment is fundamental.
The increasing danger posed by computer viruses Cybercriminals' Means of Exploiting Defects in Your Computer System Change with Technology Computer viruses, from common malware to highly sophisticated ransomware, pose a significant threat to consumers and businesses alike. These assaults can enter your framework by means of various channels, including phishing messages, compromised sites, and malevolent downloads.
The Impacts of PC Infections:
Information Break: Touchy data is habitually the objective of PC infections, which might bring about information breaks. Data about funds, individual qualities, or classified organization data might become public.
Framework Log Jam: Infections can absorb framework assets, which makes your PC's exhibition observably slower. This might diminish the result and make day-to-day activities more troublesome.
Financial damage: PC infections known as ransomware can scramble your records and request an expense to open them. The two people and organizations might experience huge monetary harm because of the objective of such an attack.
Data fraud: Theft of an individual's identity could be the result of some viruses, which are designed specifically to steal personal data. Far-reaching impacts could result from this, influencing both your on-the-web and disconnected lives.
Proficient PC infection expulsion is essential:
It tends to be perilous to attempt to destroy a PC disease all alone without master help. Master infection destruction administrations give various benefits.
Experience and knowledge: Gifted specialists can perceive and eliminate an assortment of PC contaminations. To ensure intensive malware evacuation, they go through state-of-the art methods and remain up-to-date on the most current risks.
Information Recuperation: In the event of a virus attack, experts can assist in retrieving lost or encrypted data. To diminish the impacts of a security break, this is fundamental.
Counteraction Techniques: Specialists can set up preventive measures to shield your framework from infection assaults from here on out, notwithstanding malware evacuation. This involves instructing users on safe internet usage practices and installing powerful antivirus software.

Inner serenity: You can feel quiet realizing that experts are dealing with your PC. Master infection end diminishes the opportunity of repetitive diseases by ensuring a total and effective system.
Putting resources into master infection expulsion administrations is a proactive move in safeguarding your computerized climate in our current reality, where PC infections are a steady danger. Proficient PC Virus Removal annihilation offers priceless security and an inward feeling of harmony, no matter what the size of your association or the quantity of clients it serves. Instead of waiting until a virus infects your computer, it is best to take action right away to protect your digital assets and ensure a safe computing experience.
0 notes
Text
gonna have to figure out which of my privacy/tracker-blocking extensions is twigging youtube's bullshit adblock detection after i get up :/ none of them is even supposed to INTERACT with ads because that's ublock's job, and i've always deliberately tried to set them up so they DON'T overlap with ublock, so it's very annoying
#i bet it's my fucking antivirus. because of course youtube would mistake malware blockers for ad blockers#ads are basically malware that runs in your browser instead of downloading. right? right#i tried watching one (1) youtube video without ublock just to see how bad it was. and it was BAD bad#i got about halfway through my 40 minute video and counted at least five of them. an ad every four minutes. that's atrocious#advertizing fucking grammarly. if it were actually a good service it wouldn't need so many infuriating ads! just saying!#stfu blue
1 note
·
View note
Text
How to Protect Your Computer with Online Antivirus Software
With ever-evolving virus threats and sophisticated cyberattacks, your internet devices are always at risk of losing important data and files at the hands of cybercriminals. There are more than 300 million malicious programs in the digital world, which are called by different names such as malware, spyware, netbots, ransomware viruses etc. These malicious programs enter your system from different online and offline channels. Normal inbuilt defense systems cannot deal with these sophisticated malicious programs. These programs can easily trump the basic defender of the computer due to its normal scanning mechanisms. You cannot safeguard your computer from malware attacks without using robust online antivirus protection on your computer. It comes with advanced scanning algorithms and malware analysis mechanisms that identify and eliminate all the programs hassle-free. Here is how online antivirus software safeguards your computer from malicious programs.
Real-Time Protection
Real-time protection is one of the most essential features of online antimalware tools that provide round-the-clock security to your computer. It means your device is always under the supervision of the security tool that monitors your device programs to track down potential virus threats. It continuously scans your device programs and operating systems to deal with malicious codes, whether you are online or offline. With this feature, you can easily detect, identify and remove any virus attack on your computer.
Ensure Regular Updates
Updating your apps, operating system and programs is essential to keep security vulnerabilities in check. No one can keep pace with the latest updates all the time because of regular new launches. But, if you are using antivirus software on your PC, it makes sure that all your system apps and programs remain up to date with the new features and security patches. Security software automates your computer to download all the new upgrades and updates in your PC as soon as they are available.
Enable Firewall Protection
An online antivirus software comes with a built-in firewall to help protect computers from network-based threats. The firewall system scans all the incoming and outgoing network traffic, data packets, and emails. It blocks all the malware from entering your system and generates alerts to the user about malicious links, websites and mail in advance. You get comprehensive protection from cybersecurity threats and peer-to-peer network infections using online antimalware solutions. All you need to do is activate the firewall system while you are online or connected to any network.
Prevention of Data Breaches and Loss
Malware attacks constantly work to make data breaches, in which sensitive information is accessed, stolen, or compromised. Antivirus software using advanced algorithms to identify and eradicate threats quickly helps prevent such incidents. It can detect and block malware designed to steal or exploit sensitive data and, in most cases, updates itself to deal with the problems with AI-driven malicious software definition updates. It includes protecting against keyloggers, password stealers, banking Trojans, and other malware that aim to collect personal or financial information.
Zero-Day Threat Detection
Zero-day threats are newly discovered security weaknesses, viruses, or malware that security agents have not tinkered with or identified properly within time. These types of malware can pass normal antimalware programs due to their newly built malicious programs. Software vendors need more time to deal with the newly launched digital and computer systems threats. However, antivirus software with advanced techniques like heuristic analysis and behavioral detection can detect and mitigate zero-day threats by analyzing their behavior and identifying suspicious patterns.
Deep Clean
You can deep clean your devices using antivirus software. It thoroughly scans all the files, documents, media and programs to find hidden worms or ransomware in your device. If there are spare files like cache, cookies, unused apps or software that may become breeding spaces for malicious codes, you will get a complete report about these files from your security tool. This device cleaning will help you maintain a healthy operating system that is free of potential malware. Additionally, using this process, you can tidy up your devices from resource-intensive spare data that enhances overall system performance.
Conclusion
A robust antimalware software is the need of the hour if you are connected to the digital world. It keeps you protected from a wide range of risks that include viruses, malware, worms and other malicious programs. Also if you use a paid version of antivirus solution you get dedicated customer support that resolves your technical internet security issues with appropriate solutions. You can get expert opinion and guidance at Totalav customer service to upgrade your computer protection to fend off cyber attacks. All you need to do is to dial the support phone number and talk to the professional. They will help you with your queries and keep you connected to the internet without fear. You can customize your computer security package by talking to customer support to meet your specific needs.
1 note
·
View note
Text
Explore expert insights on selecting the finest Managed Security Service Providers (MSSPs) for robust business protection. Legendary Systems provides invaluable guidance to safeguard your digital assets.
0 notes
Text
Eyemax Computer Geeks In Town - Network Support Technician in Albany NY | Computer Repair Service in Albany NY
We are your dependable and trustworthy go-to for Computer Repair Service in Albany NY. Our professionals have thorough experience in dealing with various technical problems. Because of our skills and vast knowledge. We can identify and troubleshoot computer problems in the best possible way. We are also renowned for our Antivirus Removal in Albany NY. Our technicians can fix your Xbox issues with the best efficiency. We have the knowledge and competency to provide you with the best solutions. Moreover, we have kept our service charges reasonably affordable. So, if you need our assistance, you should call us today.

#Computer Repair Service in Albany NY#Antivirus Removal in Albany NY#Computer Repair Service near me#IT Support near me#Computer Fixing Shops near me
1 note
·
View note