#Wireless Private Branch Exchange
Explore tagged Tumblr posts
Text
What is Corporate Telephony?
Corporate telephony can be defined as the complexes and networks within corporate communications. It is usually developed for enterprises distributed geographically, to facilitate communication, single service, and single address space. The development of corporate telephony involves solving several tasks listed below: Keeping the information more secure during their transmission over…

View On WordPress
0 notes
Text
Dialing into Success: Choosing the Best Toll-Free Number Provider

In today's fast-paced world, effective communication lies at the heart of every successful business. As companies strive to connect with customers and colleagues seamlessly, the importance of streamlined communication solutions cannot be overstated.
This is where Direct Inward Dialing (DID) steps in, revolutionizing the way businesses communicate both locally and globally. In this blog, we'll delve into the world of DID, exploring its benefits, applications, and how VoIPTech's solutions are empowering businesses across India and beyond.
Understanding Direct Inward Dialing (DID):
Direct Inward Dialing (DID) is a telecommunication service that allows individuals to directly dial a specific extension within a private branch exchange (PBX) system. Unlike traditional phone systems where each employee shares a single phone number, DID provides unique phone numbers for each individual, enhancing privacy, efficiency, and accessibility.
The Importance of DID in India:
In India, where businesses thrive amidst diverse landscapes and demographics, the need for effective communication solutions is paramount. Direct Inward Dialing (DID) numbers enable businesses to establish a local presence in multiple cities or regions without the need for physical offices. This flexibility not only enhances customer accessibility but also facilitates efficient collaboration among remote teams.
VoIPTech's DID Solutions:
VoIPTech's Direct Inward Dialing (DID) solutions take communication to new heights, offering businesses unparalleled flexibility and functionality. With VoIPTech, businesses can easily acquire DID numbers tailored to their specific needs, whether it's establishing a local presence, routing calls efficiently, or enhancing customer service.
Customized Call Routing:
One of the key advantages of VoIPTech's DID solutions is the ability to customize call routing based on various criteria such as time of day, caller location, or specific business departments. This ensures that calls are directed to the right person or department, optimizing efficiency and improving customer satisfaction.
Scalability and Cost-Effectiveness:
Furthermore, VoIPTech's Direct Inward Dialing (DID) solutions eliminate the need for expensive hardware installations and maintenance associated with traditional phone systems. Businesses can easily scale their communication infrastructure as needed, without being tied down by physical limitations.
Conclusion:
In conclusion, Direct Inward Dialing (DID) is a game-changer for businesses looking to enhance their communication capabilities. With VoIPTech's innovative solutions, businesses can empower their communication strategies, unlock new opportunities, and stay ahead in today's competitive landscape. Whether it's connecting with customers, collaborating with colleagues, or expanding into new markets, VoIPTech's DID solutions pave the way for seamless and efficient communication. Empower your communication with VoIPTech's Direct Inward Dialing solutions today!
voip #telecom #technology #business #telecommunications #voipbusiness #network #internet #voipservices #cloud #voipsolutions #networking #pbx #data #voipphone #smallbusiness #communication #wireless #callcenter #tech #cloudcommunications #voiphone
did direct inward dialing direct inward dialing india direct inward dialing numbers direct inbound dialing direct inward direct inward dialing did direct inward dialing providers direct inward dial did telephone number
0 notes
Text
VOIP PBX – The Evolution of Telephone Systems
VOIP PBX – The Evolution of Telephone Systems Traditional, Private Branch Exchange (PBX) telephone systems have changed a lot since the spread of the internet. Slowly but surely, businesses are phasing out analogue systems and replacing them with IP PBX alternatives. A traditional PBX system features an exchange box on the organization’s premises where analogue and digital phones connect alongside external PSTN/ISDN lines from the telecommunication company. It gives the company full ownership, but is expensive to setup and most frequently requires a specialist technician to maintain, repair and make changes. Wireless communications solutions for the hospitality industry Recording management system IP Communication Solutions
1 note
·
View note
Text
Empower ment
EMPOWERMENT TECHNOLOGIE (PORTFOLIO)
Chapter 1-INFORMATION AND COMMUNICATIONS TECHNOLOGY
ICT- Can impact student learning when teachers are digitally literate and understand how to integrate it into curriculum. Schools use a diverse set of ICT tools to communicate, create, disseminate, store, and manage information
This link will show you what ICT is?
https://icttechtips.wordpress.com/2018/02/23/what-is-ict-empowerment-technologies-k-to-12/

Here are the examples of ICT
ICT includes products that store, process, transmit, convert, duplicate, or receive electronic information. Electronic textbooks, instructional software, email, chat, and distance learning programs
Communication is an act of transmitting messages. It is a process whereby information is exchanged between individuals using symbols, signs or verbal interactions. Communication is important in order to gain knowledge. Technology is the use of scientific knowledge, experience and resources to create processes products that fulfill human needs. Technology is vital in communication.
ICT nowadays has also widened the horizon in developing new tools or emerging technologies. Mobile devices can communicate through wireless fidelity (WIFI), Bluetooth, third generation 3g & 4g, data services and dial up services and virtual private networks.
Emerging Technologies
Emerging technologies are characterized by radical novelty (in application even if not in origins), relatively fast growth, coherence, prominent impact, and uncertainty and ambiguity. In other words, an emerging technology can be defined as "a radically novel and relatively fast growing technology Characterized by a certain degree of coherence persisting over time and with the potential to exert a considerable impact on the socio-economic domain(s) which is observed in terms of the composition of actors, institutions and patterns of interactions among those, along with the associated knowledge production processes. Its most prominent impact, however, lies in the future and so in the emergence phase is still somewhat uncertain and ambiguous.

Artificial intelligence
Is the ability of a
digital computer or computer-controlled robot
to perform tasks commonly associated with intelligent
beings. The term is frequently applied to the project
of developing systems endowed with the intellectual processes characteristic of humans, such as the ability to reason, discover meaning, generalize, or learn from past experience.
Robotics
Is a branch of engineering that involves the conception, design, manufacture, and operation of robots. This field overlaps with electronics, computer science, artificial intelligence, mechatronics, nanotechnology and bioengineering.
Biometrics
Is the measurement and statistical analysis of people's unique physical and behavioral characteristics. The technology is mainly used for identification and access control or for identifying individuals who are under surveillance
Quantum cryptography
Science of exploiting quantum mechanical properties to perform cryptographic tasks. The best known example of quantum cryptography is quantum key distribution which offers an information-theoretically secure solution to the key exchange problem.
Online learning platform
is an integrated set of interactive online services
that provide trainers, learners, and others involved
in education with information, tools and resources
to support and enhance education delivery and management.
Computer assisted translation
CAT tools are typically understood to mean programs that specifically facilitate the actual translation process. Most CAT tools have the ability to translate a variety of source file formats in a single editing environment without needing to use the file format's associated software for most or all of the translation process, translation memory, and integration of various utilities or processes that increase productivity and consistency in translation.
3d imaging and holography
Holography is the next stage of photography and conventional film and its three-dimensionality creates completely new possibilities for use, such as for product presentation. A 3D hologram displays products, objects, and animated sequences three-dimensionally and enables seemingly real objects or animations to appear to float completely freely in space. Unlike a conventional film on a standard screen, a 3D hologram is visible from all sides, which means the observer can walk around the hologram, enabling an absolutely realistic-looking image to form.
Virtual Reality
(VR) refers to a computer-generated simulation in which a person can interact within an artificial three-dimensional environment using electronic devices, such as special goggles with a screen or gloves fitted with sensors.
Lesson-2 ONLINE SYSTEMS, FUNCTIONS, AND PLATFORMS
Online systems– are online versions of information systems, which is “the process of and tools for storing, managing, using, and gathering of data and communications in an organization.
An example of information systems are tools for sending out communications and storing files in a business.”
Common Online Platforms
Social Media Platform means a mobile and/or internet-based platform used and controlled by a Seller or any of its Affiliates for the exclusive purpose of promoting the Business, including any profiles or accounts on Facebook, Google+, Instagram, Pinterest, Tumblr, Twitter, Snapchat, and YouTube, in each case, to the extent exclusively related to the Business.
Online Video Platform
Provided by a video hosting service, enables users to upload, convert, store and play back video content on the Internet, often via a structured, large-scale system that may generate revenue.
Lesson-3 Online Safety, Security, Ethics and Etiquette
Issues and crimes on the internet are the following
1. Cyber bullying

2. Hacking

3. Identity theft

4. Plagiarism

5. Intellectual property rights and copyright issues

These issues caused the formulation of the rules and regulations to be followed when using the internet. Online safety and security defines how you are going to keep yourself safe while surfing the web.
Online Ethics and Netiquette
Online Ethics focuses on the acceptable use of online resources in an online environment.
Netiquette focuses on the acceptable behavior of the person while using the internet resource.
Netiquette is a combination of the words “net” (from internet) and “etiquette” (netiquette).
Lesson-4 Online Search and Research skills
Looking forward E- Commerce
The Philippines is now considered as
one of the countries in Asia Pacific that
consumes more than 3 hours on the
web. Users are mostly the younger
generation and social media is the most
popular platform being visited.
An article features the positive responses of the young Filipinos towards E- commerce. It was mentioned in the article that netizens (79) mostly discuss products and services while staying online. Even though most netizens are knowledgeable of the different online stores, many are still afraid to make purchases due to credibility issue.
CHAPTER 2: APPLIED PRODUCTIVITY TOOLS
Productivity tools can be a freeware or shareware., A freeware is copyrighted, which can be used for free and for an unlimited time while shareware is commercial software that is copyrighted, which can be copied for trial but needs to be purchased for continued use.
One of the most popular productivity suites is the Microsoft Office developed by Microsoft. This includes word processing software, electronic spreadsheet, and presentation software, not all Microsoft applications includes Access and Publisher. You can tell the some version of office contains a desktop publishing program. These tools will help you create, organize and present information to an audience for a more effective communication.
Reports, nowadays demand to be well-presented and dynamic. Away from the usual ways of [resenting information. A lot of presentation software are available whether online or offline. Similarly, financial reports are calculated and tabulated using electronic spreadsheets because of the automatic formulas and functions available.
2 notes
·
View notes
Text
PORTFOLIO IN EMPOWERMENT TECHNOLOGY
CHAPTER 1 LESSON 1: INFORMATION AND COMMUNICATIONS TECHNOLOGY - Is a branch of engineering that involves the conception, design, manufacture, and operation of robots. This field overlaps with electronics, computer science, artificial intelligence, mehcatronics, nanotechonology and bioengineering. CONTENT STANDARD
- The learners demonstrate an understanding of ICT in the context of global communication for specific professional track.
Performance Standards
- The learners shall be able to: at the end of the 2-week period independently compose an insightful reflection paper on the nature of ICT in the context of their lives, society, and professional tracks (Arts, Tech Vocational, Sports and Academic)
Most essential learning competencies
The learners should be able to:
1. Compare and contrast the nuances of varied online platforms, sites, and content to best achieve specific class objectives or address situational challenges.
2. Apply online safety, security, ethics, and etiquette standards and practice in the use of ICTs as it would relate to their professional tracks. 3. Use the internet as a tool for credible research and information gathering to best achieve specific class objectives or address situational.
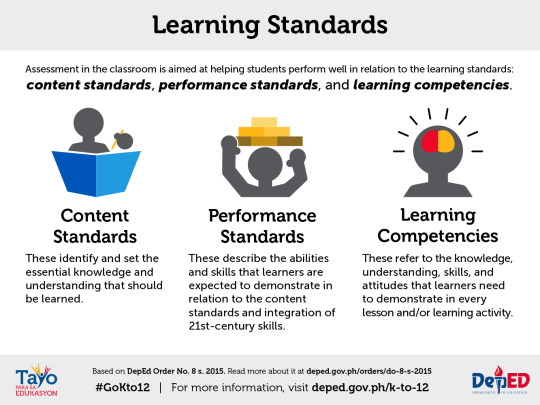
1.1 INFORMATION AND COMMUNICATION TECHNOLOGY

- ICT is the technology required for information processing, in particular, the use of the electronic computers, communication devices and software applications to convert, store, protect, process, transmit and retrieve information from anywhere, anytime.
- Information refers to the knowledge obtained from reading, investigation, study or research. The tools to transmit information are the telephone, television and radio. Information is knowledge and helps us to fulfill our daily tasks. - Communication is an act of transmitting messages. It is a process whereby information was exchanged between individuals using symbols, signs or verbal interactions. Communication is important in order to gain knowledge. Technology is the use of scientific knowledge, experience and resources to create processes products that fulfill human needs. Technology is vital in communication.
- ICT nowadays has also widened the horizon in developing new tools or emerging technologies. Mobile devices can communicate through wireless fidelity (Wifi), Bluetooth, third generation 3g & 4g, data services and dial up services and virtual private networks. EMERGING TECHNOLOGIES

- Artificial Intelligence (AI) - is the ability of a digital computer or computer controlled robot to perform tasks commonly associated with intelligent beings. The term is frequently applied to the project of developing systems endowed with the intellectual processes characteristics of humans, such as the ability to reason, discover meaning, generalize or learn from past experience. ROBOTICS

- Is a branch of engineering that involves the conception, design, manufacture, and operation of robots. This field overlaps with electronics, computer science, artificial intelligence, mehcatronics, nanotechonology and bioengineering. BIOMETRICS

- Are a way to measure a person’s physical characteristics to verify their identity. These can include physiological traits, such as fingerprints and eyes, or behavioral characteristics, such as the unique way you’d complete a security-authentication puzzle. QUANTUM CRYPTOGRAPHY

- Also called quantum encryption, applies principles of quantum mechanics to encrypt messages in a way that it is never read by anyone outside of the intended recipient. COMPUTER ASSISTED TRANSLATION

- Involves the use of software programs to translate both verbal and written texts. Also known as machine-assisted or machine aided translation. 3D IMAGING AND HOLOGRAPHY

- Is defined as a 3D projection that exists freely in space and is visible to everyone without the need for 3D glasses. VIRTUAL REALITY

- Refers to the computer generated simulation in which a person can interact within an artificial 3D environment using special electronic devices that can be similar to or completely different from the real world. ONLINE SAFETY

- Is the knowledge of maximizing the user’s personal safety and security and risk to private information, and self-protection from computer crime in general. 1. Know the scams - Learn about different kinds of scams and what you can do to avoid them.

2. Think before you click - Think twice, thrice and zillion time before click any link or buttons.

3. Safety Peruse - These sites may have an Address that’s very similar to a legitimate site, but the page can have misspelling, Bad Grammar, or low resolution Images.

4. Shop Safety - Don’t shop on a site unless it has “https” and a padlock icon on the left or right in the URL.

5. Kick-butt passwords - Use an Extremely uncrackable password One like “9&4thkel965#”.
6. Protect your info’s - Keep your guard up, Back up all your data on your computer, smartphone and tablet, theft or a cash.

7. Watch your Wi-Fi Connectivity - Protect your network by changing your router’s setting and making sure that you have the connection password protected.

8. Install a Firewall - A firewall is a grate line of defense against cyber attracts.
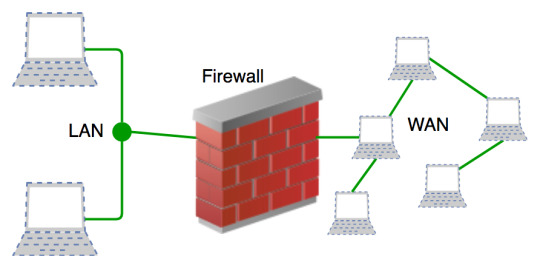
9. Keep up to date - The best security updates automatically to protect your computer. - Use the manufacturer’s latest security patches to make regular updates and make that you have the software set to do routine scam.

10. Use your Noggin - Use your common sense while surfing the web.

COMMON ISSUES AND CRIMES IN THE INTERNET - CYBERBULLYING - HACKING - IDENTITY THEFT - PLAGIARISM - COPYRIGHT ISSUES CYBERBULLYING - Is a form of bullying or harassment using electronic means. Cyberbullying and Cyber Harassment are also known as online bullying. - Cyberbullying is when someone, typically teens, bully or harass others on the internet, particularly on social media sites. Harmful bullying behavior can include posting rumors, threats, sexual remarks, a victims’ personal information, or pejorative labels. THE ANTI-BULLYING ACT OF 2013 ( RA 10627 )
(Sec. 2, RA 10627) These acts are collectively “called cyber bullying” when committed online. (Sec. 2-D, RA 10627) This covers social bullying aiming to belittle another individual or group or gender-based bullying that humiliates another on the basis of perceived or actual sexual orientation and gender identity. (Sec. 3, B-1 RA 10627. Implementing Rules). THE REVISED PENAL CODE AND THE CYBERCRIME PREVENTION ACT. - One who publicly or maliciously imputes to another a crime, vice, defect, real or imaginary, or any act, omission, condition, status or circumstance tending to cause the dishonor, discredit or contempt of a natural or juridical person, or blacken the memory of one who is dead may be liable for libel under this Code. (Art, 353, RPC) These acts are more severely punished when done online in addition to the civil action for damages which may be brought by the offended party. (Sec. 4(c-4), RA 10175) Cyberlibel holds liable only the original author of the post (Sec. 5(3), Implementing Rules of RA 10175) Likers or shares of a post cannot be held liable under this law. - Slander may also be applicable to one who, in heat of anger, utters statements that are highly defamatory in character. (Art 358, RPC) Intriguing Against Honour may also find applicability when the principal purpose is to blemish the honour or reputation of a person. Hence, a blind ite is not as actionable as a named-post in social media. HACKING

- Hacking generally refers to unauthorized intrusion into a computer or a network. The person engaged in hacking activities is known as a hacker. This hacker may alter system or security features to accomplish a goal that differs from the original purpose of the system. - Hacking can also refer to non-malicious activities, usually involving unusual or improvised alterations to equipment or processes.
IDENTITY THEFT

- Also known as identity fraud, is a crime in which an imposter obtains key pieces of personally identifiable information, such as Social Security or driver's license numbers, in order to impersonate someone else. TYPES AND EXAMPLES OF IDENTITY THEFT 1. True-name identity theft means the thief uses personal information to open new accounts. The thief might open a new credit card account, establish cellular phone service or open a new checking account in order to obtain blank checks. 2. Account-takeover identity theft means the imposter uses personal information to gain access to the person's existing accounts. PLAGIARISM

- Is an act of fraud. It involves both stealing someone else's work and lying about it afterward. The following are considered plagiarism - turning in someone else's work as your own - copying words or ideas from someone else without giving credit - failing to put a quotation in quotation marks - giving incorrect information about the source of a quotation - changing words but copying the sentence structure of a source without giving credit - copying so many words or ideas from a source that it makes up the majority of your work, whether you give credit or not (see our section on "fair use" rules) Republic Act No. 8293 [An Act Prescribing the Intellectual Property Code and Establishing the Intellectual Property Office, Providing for Its Powers and Functions, and for Other Purposes]otherwise known as the Intellectual Property Code of the Philippines. Intellectual property rights under the I. P. Code: The intellectual property rights under the Intellectual Property Code are as follows: 1. Copyright and related rights; 2. Trademarks and service marks; 3. Geographic indications; 4. Industrial designs; 5. Patents; 6. Layout designs [topographies] of integrated circuits; and 7. Protection of undisclosed information. The scheme of penalties for infringement has also been changed. From the previous fine of Php200 to Php2,000 and/or imprisonment of 1 year, the current range of penalties are as follows: - For first offenders - fine of PhP50,000 to PhP150,000 and/or imprisonment of 1 to 3 years - For second offenders - fine of PhP150,000 to PhP500,000 and/or imprisonment of 3 to 6 years - For third and subsequent offenders - fine of PhP500,000 to PhP1.5 Million and/or imprisonment of 6 to 9 years. - In case of insolvency, the offender shall furthermore suffer subsidiary imprisonment. NETIQUETTE - Is a combination of the word net and etiquette.It focuses on the acceptable behavior of a person while using the internet resource. - It focuses on the acceptable behavior of a person while using the internet resource. The Core Rules of Netiquette Rule 1. Remember the human. - Never forget that the person reading your mail or posting is, indeed, a person, with feelings that can be hurt. - Corollary 1 to Rule #1: It's not nice to hurt other people's feelings. - Corollary 2: Never mail or post anything you wouldn't say to your reader's face. - Corollary 3: Notify your readers when flaming. Rule 2. Adhere to the same standards of behavior online that you follow in real life. Corollary 1: Be Ethical Corollary Corollary 2: Breaking the law is bad Netiquette. Rule 3. Know where you are in cyberspace. Corollary 1: Netiquette varies from domain to domain. Corollary 2: Lurk before you leap. Rule 4. Respect other people's time and bandwidth. Corollary 1: It's OK to think that what you're doing at the moment is the most important thing in the universe, but don't expect anyone else to agree with you Corollary 2: Post messages to the appropriate discussion group.Corollary 3: Try not to ask stupid questions on discussion groups Corollary 4: Read the FAQ (Frequently Asked Questions) document Corollary 5: When appropriate, use private email instead of posting to the group Corollary 6: Don't post subscribe, unsubscribe, or FAQ requests Corollary 7: Don't waste expert readers' time by posting basic information Corollary 8: If you disagree with the premise of a discussion group, don't waste the time and bandwidth of the members by telling them how stupid they are.Just stay away Corollary 9: Conserve bandwidth when you retrieve information from a host or server. Rule 5. Make yourself look good online. Corollary 1: Check grammar and spelling before you post Corollary 2: Know what you're talking about and make sense Corollary 3: Don't post flame-bait Rule 6. Share expert knowledge. Corollary 1: Offer answers and help to people who ask questions on discussion groups Corollary 2: If you've received email answers to a posted question, summarize them and post the summary to the discussion group. Rule 7. Help keep flame wars under control. Corollary 1: Don't respond to flame-bait Corollary 2: Don't post spelling or grammar flames Corollary 3: If you've posted flame-bait or perpetuated a flame war, apologize Rule 8. Respect other people's privacy. - Don't read other people's private email. Rule 9. Don't abuse your power. - The more power you have, the more important it is that you use it well Rule 10. Be forgiving of other people's mistakes. CONTEXTUALIZED ONLINE SEARCH AND RESEARCH SKILLS

- Online search is the process of interactively searching for and retrieving requested information via a computer from databases that are online. Interactive searches became possible in the 1980s with the advent of faster databases and smart terminals. Advantages and Disadvantages Advantages: - Ability to obtain a large sample, which increases statistical power - Data is automatically coded so no data entry errors - Reduced cost of conducting research Disadvantages: Online is not totally secure and theft is one of the numerous danger it poses, researchers personal information is at risk of being access by rogue persons. - Some of the materials on the internet have not been evaluated by experts or thoroughly screened - Lack of accreditation and low quality
RESEARCH SKILLS “Research” sometimes just means finding out information about a topic.You can certainly develop advanced information retrieval skills in Working with Sources. However, in specific understandings of “research” carry a lot of weight. The classic definition is that “research” leads to an original contribution to knowledge in a particular field of inquiry by defining an important question or problem and then answering or solving it in a systematic way. - So you will need to read on to develop a relevant understanding of what research means in your subject. - Research skills can be anything from looking at competitors and seeing what they do well to producing a written report on how your department could work better. Doing research in the world of work is all about stepping back from your day-to-day work and looking at ways you can improve. Important aspects of research: - Research design covers the key issues in developing a successful research project. - Research methods takes you to resources on essential techniques for carrying out convincing research. - Working with data will provide resources on the use of statistics and other numerical skills in research. Improving Your Research Skills Online 1. Know your sources. Make sure to find the most reliable information which can be found in multiple sources or, better, to have the original source. 2. Use your web browser properly. Know the capabilities of your preferred browser to help make your search faster and easier. 3. Organize your bookmarks. It is to organize the links you have marked. 4. Learn to use advanced search engines. Practice using advanced search techniques which are available in Google. 5. Follow the web. Follow the web information in the web. Just make sure to read and be critical in every link you click. SIX STRATEGIES THAT CAN HELP ONLINE STUDENTS PRODUCE STRONGER RESEARCH. 1. Contact a librarian before getting stuck sifting through piles of online information. 2. Consider that when in doubt, it's wiser to over-cite sources than risk plagiarism. 3. Use Google and other reliable resources at the beginning of a research process, not the end. 4. Don't think that the Web is your only source of information. 5. Understand the professor's expectations for citation format. 6. Understand why professors still assign research projects. Some examples of research skills that you may have include: 1. Report writing. 2. Analyzing lots of information from different sources. 3. Finding information off the internet. 4. Critical thinking. CHAPTER 2 APPLIED PRODUCTIVITY TOOLS Productivity Tools - It is a tools that can be a freeware or shareware. Freeware - is copyrighted, which can be used for free and for an unlimited time. Shareware - is a commercial software that is copyrighted, which can be copied for trial but needs to be purchased for continued use. Advanced Techniques Using Microsoft Word Microsoft Office Word

- One of the software of Microsoft Office 2013 suite. - Offers a set of tools that is compared to its previous versions. - Along with its new features are advanced techniques including hyperlinks, macros and mail merge. Hyperlink
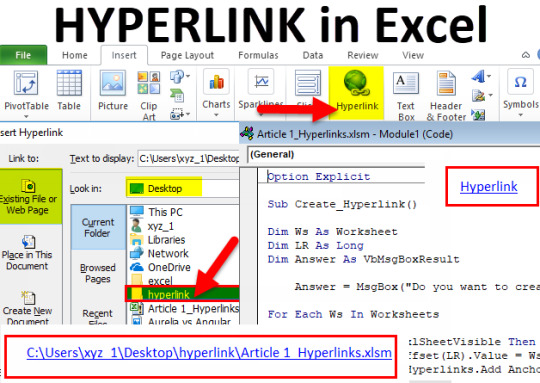
- A link that will direct you to another page or part of the same document. Creating a Hyperlink to an Existing Document - Suppose you are to link a part of your document to an existing document. - Click your mouse on the location in the document where you want to insert the hyperlink. - On the Insert Tab, click the Hyperlink button on the Links group. - On the Insert Hyperlink dialog box, click Existing File or Web Page and then select the File name where the source file is located and then hyperlink will be created on your document. - Press Ctrl+ click on the Hyperlink to open the linked file. Mail Merge
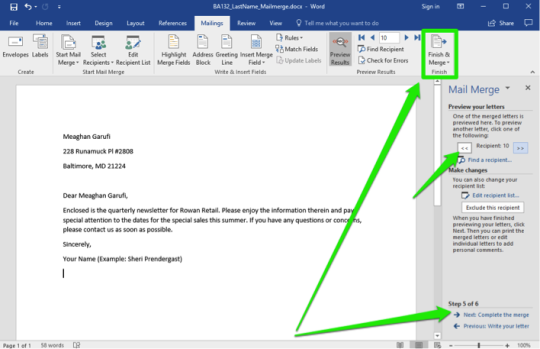
- Is a useful tool that allows you to quickly produce and send information, newsletter, resumes, or brochures to many people. Creating a Mail Merge 1. Open the word document that you want to Mail Merge. 2. On the Ribbon, click the Mailings tab, go to the Start Mail Merge group and click Start Mail Merge and select Step by Step Mail Merge Wizard. 3. The task pane will show the Mail Merge steps 1 to 6. PowerPoint

- It allows you to create slide show presentations wherein you can format the texts and images, adding also animations and other multimedia components interactively. Excel

- One of the applications created by Microsoft, used to simulate a paper worksheet.
- It is composed of cells that are represented in rows and columns design to perform basic arithmetic operations. - Widely used in accounting and financial applications, as well as statistics and engineering calculations. The following are the common Excel Functions: = SUM – Calculates the sum of the values of a range of cells = AVERAGE – Calculates the arithmetic mean of a range of cells = MAX - Gives the maximum value in a range of cells = MIN - Gives the minimum value in a range of cells = COUNT - Counts the number of cells in a range of cells BENIFITS OF ONLINE SOFTWARE Convenience - The applications should be intuitive and easy to use to ensure everyone can use them without spending a lot of time learning how. Scalability - The applications should be able to be used in all areas of your business and also work effectively no matter how much demand there is to use them or how much your business grows. Safety - All the applications should be safe to use with all existing systems and should have the ability to fully integrate with all other software and not inhibit the workers ability to do their job. Sustainability - All consumer-based software should be flexible and adaptable to have the ability to last for up to 10 years, but they must be able to expand functionally with other developments in software and operating systems. PRINCIPLES OF GRAPHICS AND DESIGN BALANCE UNITY MOVEMENT REPITITION PROXIMITY CONTRAST WHITESPACE BALANCE

- Describes the placement of elements of equal weight on the page. MOVEMENT

- Describes the flow of elements on the page.
1 note
·
View note
Text
Routers for Optimum
A router may have interfaces for different types of body connection components, such as copper wires, fiber optics, or wireless transmissions. It can also support different power lines communication. The links used make it possible to combine paper bags from one ad to another. Routers can also be used to connect two or more relevant computer components popular subnets, each with a different website.buy routers. com
Ways to find links within businesses, between businesses and the Internet, or between internet service providers' (ISPs') 'websites. Large networks (such as the Cisco CRS-1 or Juniper PTX) connect to different ISPs, or they may be used by large companies. [5] Smaller vehicles often provide connections for regular homes and office buildings.
Many types of vehicles can be found in the business. [6] The most powerful methods are commonly found in ISPs, training and research sites. Large businesses may also need more vehicles to meet and increase online trading needs. It is a great example of online communication for network traffic on the most commonly used networks. [7]
Opportunity, theme and distribution
A snapshot of the LuCI website used by OpenWrt. This page configures Dynamic DNS. Road access, including small office / office building (SOHO) models, is home to home and customer locations such as branch offices that do not need to be self-contained. Typically, they are ideal for low prices. Some SOHO routers can run other Linux based firmware such as Tomato, OpenWrt or DD-WRT. [8] [failure evidence]
Distributed routes unite travelers from multiple routes. Distributed routers are often responsible for enhancing the quality of service over a wide area (WAN), so they may have more memory, more WAN network connections, and more onboard normal operation information. They may also be able to provide links to batch files or other external links. [Citation needed]
In business, a core router may have a collumbb backbone connection distributing tier routers from large buildings of a campus, or large business locations. They try to ensure for high bandwidth, but there are no features of roadside. [9] [unconfirmed]
Safety External links should be carefully considered as part of the overall security plan of the internal network. A router may include a firewall, VPN handling, and other security functions, or these may be handled by different devices. Routers also often make network address translations that restrict starting connections from external connections but are not considered a security feature by all experts. [10] Some experts argue that open people on the road are safer and more reliable than closed railways, because of the open space available and corrected. [11]
Order different websites Routers are also often distinguished on the basis of the network on which they operate. A router in a local area network (LAN) is one organization called an internal router. A router running the back-end internet is defined as an external router. A router is connected to the LAN and the Internet or broadband network (WAN) is called a border router, or gateway router. [12]
Internet communication and internal use Plans for ISPs and many business networks typically exchange data streams using the Border Gateway Protocol (BGP). RFC 4098 describes the types of BGP pathways according to their function: [13]
Edge router (also called edge edge provider): Placed on the edge of the ISP network. The router uses the Exterior Border Gateway Protocol (EBGP) to routers to other ISPs or large private businesses. The top edge registry (also called the router edge): It is located at the end of the client network, which also uses EBGP in the company’s independent management. It is often used in an (enterprise) organization. High-speed Networks Connected: The BGP router for ISP networks maintains BGP routers and other BGP routers over ISP Autonomous Systems. Core router: The location in the Autonomous System is a backbone that carries traffic between the ends of the road. [14] Within the ISP: In an ISP stand-alone system, the router uses the internal BGP to communicate with other ISP employees, other intranet users, or border users of the ISP. ISP. Backbone: The Internet is no more
1 note
·
View note
Text
Leverage the Benefits of Microsoft Cloud Phone System in Your Business in the UAE
Collaborating with different business models is becoming quite popular in many organizations around the world in order to jointly work towards achieving a common business purpose. Building on the worldwide success of Office 365, many organizations are integrating Microsoft Cloud Phone System with their company in the UAE, to increase the productivity of their business.

Furthermore, phone systems play a major role in the internal communication of a business and help employees easily connect with one another from different remote locations. Many companies offer PBX(private branch exchange) services as a part of a larger package which can be installed in your traditional phone system through live chat or email through Outlook.com
Benefits of Partnering with Microsoft Teams Phone System in the UAE:
MS Teams works on improving teamwork by incorporating Office 365 tools to facilitate a simple and collaborative working environment for the employees.
MS Teams comes with various features such as auto-attending, direct routing, video conferencing, call forwarding, printing numbers and many more.
MS Teams incorporates many features such as conferencing and call transferring to improve remote working conditions.
With MS teams you can get multiple device access such as desktop, laptop, mobile, or tablet through the MS Teams app which in turn improves teamwork between individuals.
MS Teams is designed with the highest industry standard to ensure your calls and shared data are fully protected.
Sign up for Microsoft 365 for your Business in the UAE
Well, having known the amazing benefits that you can acquire for your business, then head over to a leading and renowned company in the UAE that specializes in Microsoft Teams Phone System along with a license to offer video conferencing, wireless networking and IT solutions. Their highly skilled professionals are well versed in using office 365 and integrating it into your business to offer you a world-class technology service.
0 notes
Text
Online banking
Online banking is a currently established banking system. Due to its various benefits, its popularity and usage are increasing daily. Nowadays, all banks have come under online banking. With the spread of information technology, smart cards and online and ATM banking services have emerged as popular means of financial transactions. The Online Internet service was launched in Bangladesh on June 4, 1996. Through 9,810 ATM booths across the country as of July 2018 across Bangladesh's districts and divisional cities. Banks are providing online services. On the other hand, they are issued from various banks.
Their customers use debit and credit cards for shopping and daily needs.
Definition of Online Banking: 'Online' in online banking refers to a system where many interconnected computers perform necessary functions through a networked system.
As we know, many computers are connected through the Local Area Network (LAN) in the branches of a bank. Again, a bank's head office and branches create an interconnection between the entire country with the help of wireless waves, optical fiber or any other means within the Wide Area Network (WAN).
We can call this complete system existing in the bank online banking in a broad sense. That is all the banking services that are provided with the help of the Local Area Network (LAN) and Wide Area Network (WAN) in the bank—called online banking. In a word, online banking is a financial process where a computer system.
Many interconnected computer networks perform essential financial functions. Some examples of online banking are - ATMs, Automated Fund transfers, Electronic checks, Electronic Money etc.
Currently, almost all banks in Bangladesh provide online banking facilities. Some notable banks providing online banking facilities in Bangladesh are Sonali, Janata, Agrani, Rupali, Trust, Dutch-Bangla, Eastern, Dhaka, BRAC, Prime, UCB, IFIC, National, City and all private banks and Islamic banks.
Advantages of Online Banking:
Online banking is a boon to the entire banking world. It has revolutionized the banking world. This method has made the service delivery process easier for the service provider and increased the speed of receiving the service for the service recipient. The benefits of online banking are mentioned below: Benefits in providing services.
A. 24/7, i.e. providing a facility for the customer to withdraw his money with the help of ATM at any time;
b. Improving the Bank's customer service standards;
c. Conducting banking activities in an international context;
d. Increase in profitability as the overall efficiency of the bank increases;
e. Stop wasting customers' time and unnecessary harassment due to the introduction of online banking;
f. Facilitating coordination of inter-branch and inter-bank transactions;
G. Facilitating customer business transactions through the use of electronic funds and electronic money.
Benefits of receiving services
A. Withdraw any amount of money anywhere in a short period;
b. Access to your account 24 hours, 365 days;
c. Account balance or statement verification facility;
d. Transfer money between accounts;
e. Utility bill payments (e.g. electricity, water, gas, phone etc.);
f. Searching for interest rates;
g. Searching for foreign currency exchange rates;
h. Sending requests for chequebooks;
I. cancelling payment of checks in case of emergency;
j. Mobile bill or balance recharges facility;
k. Deposit of insurance premium;
l. Tuition fee deposit;
Credit cards and ready cash cards are the two most widely used means of sharing these benefits with banks.
Credit Card:
The most common form of credit is a credit card.electronic banking. According to the central bank's calculations, there is more than one crore of cards in the name of customers in different banks in Bangladesh. It is a type of plastic card provided by the bank. Usually, the bank issues the card to a valued customer against a certain amount of deposit (e.g. savings letter, FTR). Usually by credit card. In the case of bill payment, after making sure about the card, the shopkeeper/businessman prepares a bill containing the name of the cardholder, name of the card company, card number and other information and signs it from the cardholder and later, the shopkeeper collects the money by submitting the copy of the bill to his bank.
Many people consider using some credit cards helpful, but the number of people in danger due to misuse is probably not less. Others don't use credit cards for fear of overspending. Some people fear that using a credit card will cost more money, etc.
Many customers borrow heaps of money. But do not pay the total amount. They are satisfied with paying the minimum bills. Many people use credit cards with such an attitude. But that's not right. Its main problem is the highly high-interest rates on credit cards. At one time, it will sit on the neck like a noose. Understanding the math behind credit cards can easily avoid these problems.
Don't forget to use multiple credit cards. Avoid reckless spending. Only then will the interest-free period be available. And most importantly, the entire bill must be paid within the specified time. Only then can customers enjoy the fun of using credit cards.
Ready Cash Card:
A type of plastic card issued by banks against cash is called a ready cash card. The smart card is built on the latest micro-processor technology.
Each card has a four-digit personal number for security, so only the customer can use the card. The card also contains the customer's photograph, sample signature and printed name. The cash deposited in the bank can be used through this card. There is an opportunity to make daily purchases and pay utility bills with the Ready cash card.
Disadvantages of Online Banking:
As we know, an online banking system is a self-contained computer network system with advanced technology. Nowadays, every modern bank is trying to provide online banking services, but this system has many advantages and disadvantages. These are discussed below-
A. Since online banking is a system with sophisticated technology, its installation and maintenance costs are also high, which is difficult for any financially weak bank to bear;
b. Highly skilled and trained personnel are required to operate this state-of-the-art technology. But the lack of skilled workers in information technology and paying them a considerable amount of remuneration is a big obstacle in the implementation of online banking;
c. Since online banking is a networked system, hackers are prone to attacks. This can lead to exposure of privacy, theft of money or information and abuse of computer systems;
d. If the network is interrupted due to natural or other causes, uninterrupted provision of services is interrupted;
e. If customers do not understand online banking, they face various complications.
Finally, if you want to get all the fantastic benefits of modern banking services, you must face some problems. If you know the ways to be safe from these problems, i.e. secure internet connection, hacking Gaining general knowledge about, caution in using devices, use of antivirus with license, making sure whether the website is verified or not, not sharing bank information with anyone, etc., will make our economic life more manageable and faster if we conduct online banking activities.
0 notes
Text
What is a small business network & How to build & Maintain it?

A small business network is a service that offers you a telephone system over the internet. It eliminates the cost of buying hardware and installation. PBX is software that lets you run your telephone system through your internet connection. It is known as cloud PBX because it is run through the cloud.
If you are running a small business, you should consider this service. It has many benefits. It is affordable, reliable, easy to use; the best feature is the voice mail, call forwarding, extensions, etc. A small business network is a better way of running your business because it can help you save time, money, and resources. You can make use of the cloud PBX features.
The cloud PBX helps you get the features without paying for an enterprise-class phone system. The small business network is one of the communication solutions that helps small businesses save money by using the same communication system that larger businesses use. It is a platform that connects various people and departments in the business and helps them communicate and share ideas.
This business communication system is accessed by desktops and mobile phones and is used for voice and data communication.
How to build & maintain a small business network
As the name suggests, a small business phone system is a telephone system used by small businesses. The PBX system, also known as Private Branch Exchange, is being installed in small businesses to give them a professional feel.
A PBX is a switchboard for your business where all your business calls are handled. The calls are connected to the correct extensions within the business premise. A PBX is capable of making outgoing calls as well as incoming calls. Some carriers are providing online PBX solutions that are easy to use.
They are user-friendly and are cost-effective. A personal business network can bring many benefits to your business, and the easiest and most immediate way to do this is to attend networking events and parties. You can also join the local Chambers of Commerce. Another way to do this is to use technology such as conference calling and PBX. Having a small network is extremely beneficial for any business, big or small.
A small business network would have people ranging from the staff of the business to the customers. The business staff could be the company's staff members, the employees, the interns, the company's partners, the contractors, the suppliers, and the company's clients. The clients of the business range from the clients of the company to the partners of the company. The business network is built by maintaining each of the contacts.
The business needs to maintain each of the contacts since they can help out the business. Every business needs to maintain all of the contacts of the business network to keep the business alive. As for the business network, by calling them on the phone or connecting to them on social media.
What is The Advantage of Small Business Network A new generation of entrepreneurs and business owners is striving to make a difference in their industry by developing a niche product and delivering it to the masses. With this quick and efficient business model comes many changes and challenges, including A network, is logic that provides interconnection between all the parts of a computer system, a network of computer connected through a system of wires or wireless.
In a business organization, a network comprises many computers connected over a local area network. So, if the network has been implemented intelligently, it can bring a lot of advantages to the company. Small Business Network is an online virtual call center solution that brings together small and medium enterprises and individuals who offer their service and skills to the rest of the business community.
It's a platform that allows small and medium businesses and entrepreneurs to sell and deliver services and products for a fee to big organizations and corporations.
Conclusion
We hope you enjoyed our article on What is Business Networking & What is the Way to Maintain it? We know how important it is to stay connected in this day and age, and this is why we are committed to helping you find the best solutions for your business needs. Thank you for reading. We are always excited when one of our posts can provide useful information on a topic like this!
0 notes
Text
What disruptive legal technologies include?
There is a lesson here lawyers that reaches beyond the issue of disruption - always give thought to the recipient of your services. When considering some kind of innovation, put yourselves in the shoes of those you are meant to be helping. What will it mean for them?
1. Document automation
- What is it? It delivers online systems and templates for some types of legal documents
- For example: the production of loan documentation for large-scale banking transactions; LegalZoom; Rocket Lawyer; Epoq.
2. Relentless connectivity
- What is it? Whatever allows immediate access, increases engagement between lawyers and their clients.
- handheld devices, tablets, wireless broadband access, high definition video conferencing, instant messaging, social media, email.
3. Electronic legal marketplace
- What is it: Clients' network of feedbacks to the lawyers' service. Lawyers soon are not able to benefit from their clients not knowing what alternatives were open to them, these technologies in isolation and together are highly disruptive.
- Online systems which allow clients to share their views, online, on the performance and levels of service of their lawyers; price comparison systems, especially on legal work packages that are routine and repetitive.
4. E-learning
- Webinar, online lectures ...
- We will see a move from "just-in-case" class room training (teaching subjects, just in case the insight provided might be needed in practice at some later stage) to just-in-time learning (interactive multi-media tools which can supply focused and tailored training on the spot).
5. Online legal guidance
- There are systems that can provide legal information, legal guidance, and even legal advice across the internet. They may or may not be subscription-based.
- For example:
+ Some can be in low-value but high-volume areas of work, such as the system developed by a student to help drivers challenge parking fines (successfully in over 150,000 cases)
+ Some can. be in jurisdictions where access to lawyers for most people is almost non-existent, such as Barefoot Law in Uganda
+ Some can be in complex, commercial work, such as Allen&Overy's online legal services, which generate more than 12 million in subscription revenues each year.
6. Legal open-sourcing
- Large quantities of public, community-oriented legal materials, such as standard documents, checklists, and flow charts.
- For example: Legal Information Institute at Cornell University Law School.
7. Closed legal communities
- The idea here is for restricted groups of like-minded lawyers with common interests to come together and collaborate online in private social networks. The users can build up bodies of collective knowledge and experience.
- For example: Legal OnRamp
8. Workflow and project management
For law firms that charge by the hour and so have historically benefited from ineffective case management and inept transaction management, workflow and project management systems represent new efficiencies and, in turn, the prospect of reduced fees.
9. Embedded legal knowledge
- In years to come, in many dimensions of our social and working lives, I predict that legal rules will be deeply embedded in our systems and processes. The disruption here is that, where rules are embedded, lawyers are no longer needed to draw clients’ attention to circumstances of legal significance.
- For example:
+ Consider a car that warns its drivers and passengers that the ignition will not work until a built-in breatha- lysing test is used and passed. This would not require car users to know the precise details of the law and then exercise the option of applying the law. Instead, the law that prohibits driving with excessive alcohol in the bloodstream would be embedded in the car itself.
+ Another example would be an ‘intelligent’ building that monitors the temperature and other environmental conditions by reference to levels established in health and safety regulations. In the event of some stipulated limit being exceeded, alarms might sound or, in emergency situations, computer screens might even be disabled. Again, this would not require people to know the law and monitor compliance.
+ Self-executing contracts, possibly enabled through the currently much-vaunted Blockchain tech- nology, will be able to initiate actions and automatically execute processes and provisions, without directly involving lawyers.
10. Online dispute resolution
online courts, e-negotiation, or e- mediation
11. Document analysis
- Lawyers spend much of their time ploughing through documents, not least in preparation for litigation. For some years now, in terms of precision and recall, properly primed systems have been able to outperform paralegals and junior lawyers when reviewing large bodies of documents and isolating those of relevance. More recently, a new set of techniques have been adopted within law, drawing from disciplines known variously as machine learning, Big Data, and analytics.
- For example: Kira, RAVN
12. Machine prediction
- Much legal work involves prediction, whether of the likelihood of winning a case or negotiating a settlement, or of a deal being abandoned or completed. The disruption here is that crucial insights in legal practice and in legal risk management might be generated largely by algorithms operating on large bodies of data without needing to involve mainstream lawyers (unless they choose to collaborate with data scientists).
- The data held within law firms’ systems, along with publicly accessible data, will no doubt form the basis of future predictions in relation to such issues.
- More than this,
+ by aggregating data sets, we will soon be able to find out what legal issues and concerns are troubling particular com- munities
+ by analysing the work of regulators, we may be able to predict compliance outcomes in entirely novel ways
+ by collecting huge bodies of commercial contracts and exchanges of emails, we might gain insight into the greatest legal risks that specific sectors face.
13. Legal question answering
- Question answering (QA) is a branch of computer science devoted to the development of systems that automatically respond to questions put by human users in everyday (natural) language.
0 notes
Text
Enterprise Routers Market Sector Analysis Report, Regional Outlook & Competitive Share & Forecast, – 2025
The enterprise routers market is poised to grow at a CAGR of 6.2% during the forecast period from 2020 to 2025. Enterprise routers are vital products that any business or enterprise uses regularly. They play an essential role in enterprises in connecting computer networks and the internet. Routers perform many functionalities, such as enterprise routing, which gives businesses a higher CPU capacity to control place tasks. Furthermore, it provides companies the ability to enhance their interface for both Ethernet and WAN circuits, run NetFlow/sFlow, MPLS, QoS, and other security features. It has functions to integrate deep packet inspection and WAN acceleration. Enterprise routers assist in maximizing productivity in the office, and the installation of an enterprise router requires the skills and expertise of an engineer. - In the first quarter of 2019, the enterprise and service provider router market grew 8.2%. The service provider segment accounts for 75.3% of router market revenues. The service provider router market rose 7.1%, and the enterprise router market grew 11.9%. The top seven enterprise routers which had high market share till June 2019 were Cisco (55.7%), Huawei (9.3%), HPE (5.3%), Nokia (3.7%), Juniper (3.6%), Netgear (2%), Dell EMC (1.7%). Cisco Systems is one of the top networking companies in the world with the highest market share providing a wide variety of enterprise routers. Cisco's enterprise router revenue rose 16.1%, and Cisco's SP and enterprise router market share increased to 42.4% from 37.4% in the first quarter, according to telecom lead.
Click Here to Download Sample Report >> https://www.sdki.jp/sample-request-90107 - Huawei's Global Industry Vision (GIV) predicts that by 2025, 85% of enterprise applications will be moved to the cloud, resulting in significant traffic growth at the egress of enterprise WANs. Traditional private lines offer several Mbit/s bandwidth and are prone to network congestion, and so service experience cannot be guaranteed. Leveraging flexible and efficient application-based traffic steering, Software-Defined WAN (SD-WAN) is the best choice for enterprise WAN interconnection in the cloud era, as it can effectively ensure customer service experience. However, when traditional enterprise routers intersect with SD-WAN, their forwarding performance decreases by about 80% on average. In response, Huawei launched next-generation NetEngine AR enterprise routers that provides higher forwarding performance at the egress of enterprise WANs. - Furthermore, service providers are rapidly modernizing their networks to satiate enterprises' growing appetites for higher performance and superior user experiences. However, as service providers adopt virtualization and SDN capabilities, they are being held back by monitoring techniques that cannot keep up. The enterprise cloud migrations and increasing reliance on software-as-a-service applications- introduced new challenges. This has driven service providers to adopt NFV, SDN, and cloud-native computing technologies. In May 2020, 128 Technology, the leader in Session Smart Routing, announced that Momentum Telecom selected 128 Technology's Session Smart Router to enable a new era of software-defined network services for its thousands of enterprise customers and partners. Key Market Trends Wireless Connectivity is Expected to Hold Major Share - An ordinary wireless router can only support approximately 10-20 users’ access. In contrast, the wireless access router point allows over 50 or even hundreds of users’ access, with the potential ability to send and receive signals. According to Cisco, the expected penetration of enterprise internet traffic via wireless fixed-line connection in 2021 shall be 125988 petabytes per month. With the rise in high internet traffic and devices, average fixed broadband speed, along with average internet users, will grow exponentially in the forecast period. Average fixed broadband speed is likely to increase from 5.1 Mbps in 2015 to 12.9 Mbps in 2020. - For instance, the industry’s first 5G optimized wireless WAN edge router for enterprise branch deployments has been released by Cradlepoint in May 2020. The Cradlepoint E3000 Series, according to the company, optimizes performance and investment protection and enables customers to deploy a wireless wide-area network (Wireless WAN) using the latest LTE and Wi-Fi technology and seamlessly upgrade to 5G in the future. The COVID-19 pandemic has fueled an already growing demand for agile and rapidly deployable wireless WANs based on LTE for primary connectivity. Cradlepoint said in the release that the E3000 Series is intended to target this market directly. - Furthermore, M2M Connectivity supplies a broad range of wireless routers for 4G/3G as well as models for satellite and short-range RF (WLAN, Bluetooth). These ethernet routers enable remote access and communication with equipment and assets such as remote PLCs, data loggers, and microcontrollers. With the increasing usage of such solutions in various end-users, the market tends to grow in this sector. In April 2020, Digi International announced the launch of several new cellular routers and extenders, each designed to meet the present and future connectivity needs of organizations for M2M applications in the transportation and enterprise marketplaces. North America is Expected to Hold Major Share - North America is expected to hold a prominent share in the enterprise routers market. Moreover, the region has a strong foothold of network routers vendors. Some of them include Cisco Systems, Inc., Dell EMC, Juniper Networks, Inc., among others, which contribute to the growth of the market. It is estimated that till 2022, in the United States the market for network router will grow to USD 11,950 million which includes the market for ethernet service edge router, multiservice edge router, service provider core router, and internet exchange router (source Cisco), where the expectation of high market growth potentially move towards internet exchange router in 2022. - Moreover, according to Cisco, 46% of network devices will be machine -to -machine or IoT by 2020, which are vulnerable to attacks. To fully realize the potential of these connected devices, the industries need to be equipped with WANs that are flexible to meet the network demands anticipated over the future. Furthermore, the emergence of trending technologies, such as cloud networking, SaaS-based application, network analytics, DevOps, and virtualization, has encouraged the users and businesses in North America to undertake enterprise routers products. - However, security and privacy concerns are restraining the market. According to the study, five out of every six routers in the United States are running out-of-date firmware with exploitable security vulnerabilities, which hinders market growth globally. In a situation where many employees are currently working from home due to a COVID-19 pandemic or access wi-fi networks that operate at enterprise-level security, devices such as routers can be hacked to plant a range of malware into handheld devices used by employees. Subex, through its honeypot network (a decoy computer system for trapping hackers), spread across 62 cities, has been tracking cyberattack trends and malware activity that can be correlated with the outbreak. Competitive Landscape The enterprise routers market is fragmented as the global players invest in R&D for the latest innovations in the product for several small to medium-sized companies. Key players are Cisco Systems, Inc., Juniper Networks, Inc., Hewlett Packard Enterprise, etc. The companies operating in the market continuously strive to launch new solutions to help service providers achieve a holistic approach to infrastructure transformation and gain new orders in that course for strategic aim. - March 2020 - Huawei confirmed that its next-generation NetEngine AR600 and AR6000 series enterprise routers have passed the verification test by The Tolly Group which is an authoritative international provider of testing and validation. The results showed that Huawei's NetEngine AR routers are equipped to handle the growth in traffic from digital transformation in the next three to five years, leading the way to a new era of ultra-fast interconnection for enterprise WANs. - December 2019 - Cisco Silicon One based Q100 processor and 8000 Series routers. Cisco will uniquely allow ecosystem players to separately buy processors, the XR7 router software, 8000 series routers without software, optical modules (QSFP-DD and QSFP28), or a fully integrated 8000 Series solution. The 8000 Series router and the Q100 processor is targeted at service providers and data center operators ranging from large aggregation to core applications. Reasons to Purchase this report: - The market estimate (ME) sheet in Excel format - 3 months of analyst support
The dynamic nature of business environment in the current global economy is raising the need amongst business professionals to update themselves with current situations in the market. To cater such needs, Shibuya Data Count provides market research reports to various business professionals across different industry verticals, such as healthcare & pharmaceutical, IT & telecom, chemicals and advanced materials, consumer goods & food, energy & power, manufacturing & construction, industrial automation & equipment and agriculture & allied activities amongst others.
For more information, please contact:
Hina Miyazu
Shibuya Data Count Email: [email protected] Tel: + 81 3 45720790
Related Links https://www.sdki.jp/
1 note
·
View note
Text
Comparing Acceptable Use Policies
An Acceptable Use Policy is an agreement between a company and a customer. It's what someone agrees to in order to use a service or product. Most customers and stakeholders are prompted to read and accept these terms before initially using a company’s product, as well as when there are updates or new releases. Reading a company’s AUP can give insight to a company’s concerns, values, and security frameworks. People rarely read these, but they can tell us a lot about a company and how it treats its customers, not just what the company expects from people interacting with their property.
To show these differences, I read through the AUPs for Brown University, Facebook, and the U.S. Army. I ranked them on their efficacy and detail. Items given special attention will include how long ago an AUP was updated, concepts the AUPs define, mentions of cybersecurity policies, and repercussions for users who do not follow the AUPs.
Ranking Three Acceptable Use Policies
Brown University
Brown University is ranked third in the comparison of the first three AUPs. The university last reviewed their policy on August 3rd, 2016, but initially enacted the document August 1st, 2003 (Acceptable Use Policy | Computing & Information Services, n.d.). They have five separate help links from the policy page, making it the most accessible for users that need assistance. Another strength is that they have an extensive list of real-world examples to help clarify different situations a user may find themselves experiencing. They are most concerned with users cheating, hacking, and breaking the law. Toting respect above all else, Brown University is clear that if there are any breaches of their policy, they will respond with legal action. Their policy is short and doesn’t go out of its way to define concepts. Instead, it gives lists and examples of misconduct. Most notably, they are concerned with copyright abuses and “activities that would jeopardize the University’s tax-exempt status.” (Acceptable Use Policy | Computing & Information Services, n.d.)
Interestingly, they are specific on a few cybersecurity points. Students are allocated a certain amount of bandwidth which they cannot exceed. Users may not use university devices for libel, slander, harassment, or political purposes, nor economic gain. Users may not access or copy others’ personal identification or account information, like someone’s phone number or password. The use of security assessment or cyber-attack tools is prohibited unless under direction of and through educational means in their cybersecurity classes. Most notably, students are responsible for their device’s “network address or port, software and hardware. … (and) may not enable unauthorized users to access the network”. This means that if a student is hacked, it is effectively their fault, not the university’s, if they did not make a “reasonable effort” to protect their systems. Lastly, the AUP mentions that by agreeing to the policy, users also agree to all third-party license agreements, but there are no mentions or links to what those may be (Acceptable Use Policy | Computing & Information Services, n.d.).
Facebook
Facebook’s AUP is ranked second best out of the first three policy reviews. It consists of two documents: their Terms of Service and Community Standards. These documents were last revised October 2nd, 2020 (Terms of Service, 2019). At the start, Facebook is intent on explaining that everything they do is for others’ benefits. They clearly state that they don’t sell user data, but they get revenue from semi-anonymous user activity data (Terms of Service, 2019). For example, an advertising company may be told that a person who works in the culinary arts and likes skydiving clicked on their ad. This didn’t name the person or give away anything that may identify them, but it should be noted that the user is being given the Facebook platform service in exchange for this type of surveillance and reporting, and not any type of financial reparation. Facebook spends several pages explaining how this process makes the world a better place (Terms of Service, 2019).
From there, Facebook defines who is allowed to use their platform. As long as a user is over 13, not a convicted sex offender, hasn’t been kicked from the platform before, or doesn’t live in a country that bans Facebook, a person may create a profile. The profile must have the users real name, give accurate personal information, and be their only account (Terms of Service, 2019). This raises some questions, as many people regularly use fake names, have many accounts, and state they went to Hogwarts for college. Copyright is an interesting topic for Facebook. Anything a person uploads remains theirs and Facebook owns the “license” to it, unless it’s deleted. Interestingly, this section specifies that Facebook can use user content in their advertising campaigns without any special permissions (Terms of Service, 2019). So, don’t be surprised if Joe Lunchbox’s vacation video ends up on television.
In terms of cybersecurity, no one may upload malicious code nor attempt to spider, or scan for data, using software. Trying to view Facebook’s source code is also prohibited. If any of these policies are broken, Facebook will issue warnings, disable accounts, and may even contact and give personal information to law enforcement (Terms of Service, 2019). For example, if a person starts a live stream and begins threatening suicide, the stream will be cut the moment “threat becomes attempt” and police will be contacted and given that person's geological location, name, and number. There is also a very large section dedicated to mentioning that Facebook is not perfect and not responsible for content people post. This states that no lawsuit against Facebook may exceed $100 compensation from them and that all court cases take place “exclusively in the U.S. District Court for the Northern District of California or a state court located in San Mateo County.” (Terms of Service, 2019)
Facebook works with several partners to eliminate any form of human abuses, like trafficking, exploitation, assault, and sexual violence. There’s even a special branch covering all this in relation to minors and children (Facebook, 2019). In fact, most photos with any type of child nudity, even uploaded by loving parents, is usually removed because those images can be perverted by others. There’s also a dedicated anti-bullying hub that targets “content that’s meant to degrade or shame.” Facebook abhors hate speech, glorifying violence, “deep fakes”, and victim mocking. A “deep fake” is an altered video that appears to be real but intends to mislead and manipulate (Facebook, 2019).
Facebook’s Community Standards are mostly large and extensive definitions for the following: violence, criminal behavior, safety, objectionable content, integrity, authenticity, respecting intellectual property, and content-related requests and decisions (Facebook, 2019). There are only a few interesting points in these. Facebook prohibits drug and gun transactions on their platform, but does allow these types of advertisements, especially ammunition retailers. If a person dies, their account may be memorialized. A family member or even a person’s official executor can request this. A parent can have their child’s Facebook profile deleted. Lastly, Facebook decides policy change by stakeholder group discussions (Facebook, 2019).
The U.S. Army
Ranked number one is the Acceptable Use Policy for the United States Army. In stark contrast to Facebook’s AUP, the Army keeps as much as possible private and secured. Their AUP was last updated November 7th, 2018, and has short, concise definitions, leading into lists of rules (ACCEPTABLE USE POLICY (AUP), n.d.). They start off by specifying that there are two networks: The SIPRNET and the NIPRNET, or the Secret Internet Protocol Router Network and the Non-secure Internet Protocol Router Network. Everything on the SIPRNET is classified and everything on NIPRNET is unclassified (ACCEPTABLE USE POLICY (AUP), n.d.).
The Army’s AUP is mostly cybersecurity best practices. Users need authorization to do most things, including the ability to read/write to something, change any settings, or install any programs. They use Public Key Infrastructure (PKI) for every single communication on the SIPRNET, while the NIPRNET acts as a kind of duplicate internet. Secure Socket Layer (SSL) is used and security training takes place annually (ACCEPTABLE USE POLICY (AUP), n.d.). If a user misses their security training deadline, their accounts are locked until they’ve done the training and turned their completion in to their superior. The program covers “threat identification, physical security, acceptable use policies, malicious content and logic identification, and non-standard threats such as social engineering.” Passwords are changed every 90 to 150 days and all items must be virus checked before they can be opened on a device. Malicious code and executables, like .exe, .com, .vbs, and .bat files, are prohibited (ACCEPTABLE USE POLICY (AUP), n.d.). Only System Administrators are allowed to do system maintenance. Wireless devices must be off in most parts of the network and Bluetooth is outright barred. Users may not use so much bandwidth as to disrupt service but are allowed a small and reasonable number of personal communications at certain moments of the day, in certain locations, with personal devices. All of this is routinely monitored, traffic is intercepted, and devices may be seized at any time. The Army has the right to take any data a user has on its devices unless it is protected under duty of confidentiality, like communications with a lawyer or therapist (ACCEPTABLE USE POLICY (AUP), n.d.).
The only course of repercussion described is “disciplinary action”, with no further explanation (ACCEPTABLE USE POLICY (AUP), n.d.). This was chosen as the best out of the three AUPs because of its cybersecurity focus and curt specificity.
Conclusion
Acceptable Use Policies range widely in length, structure, specificity, and accountability. Most companies seem to care about copyright violations, but there are stark contrasts in the length certain companies go to communicate their expectations to users. Stakeholders deserve to have AUPs that are definitive, clear-cut, and comprehensive. These AUPs indicate not only how a company wishes to be treated, but how they will treat their users. Whether it’s a San Mateo County lawsuit guaranteed to award no more than a hundred bucks, a picture of a child in the tub being redacted, or an impromptu visit from a mental health professional, users must accept the effects of misconduct. That obligation starts by agreeing to Terms of Service, even if a user doesn’t read them.
References
ACCEPTABLE USE POLICY (AUP). (n.d.). https://home.army.mil/gordon/application/files/2915/4938/7446/FG_AUP-07NOV18.pdf
Acceptable Use Policy | Computing & Information Services. (n.d.). It.brown.edu. Retrieved April 25, 2021, from https://it.brown.edu/computing-policies/acceptable-use-policy#31
Facebook. (2019). Community Standards | Facebook. Facebook.com. https://www.facebook.com/communitystandards/
Terms of Service. (2019). Facebook. https://www.facebook.com/legal/terms
0 notes
Text
Why Your Business Should Use Microsoft Teams Phone System in the UAE
With the rapid innovations in technology, each small and medium business are adopting new technologies with time to stay connected with their customers, investors, and other stakeholders. Organizations around the world are looking for MS Teams Cloud-based Phone System in the UAE to improve their operational efficiencies. Business owners are using this technology to establish an effective and dependable communication system for their organizations.
There are a few reputable companies in the UAE that offer PBX( private branch exchange) services through Microsoft Teams and Office 365 as a part of their package. In addition, you can also install phone systems through live chat and handle email through Outlook.com.

Benefits of Partnering with Microsoft 365 Phone System in the UAE
The system offers you flexible and affordable pricing options that let you change the existing hardware telephone system.
The system comes with various features such as audio conferencing, auto-attendant, call forwarding, printing numbers, and many more.
The system can enhance the communication of your business through the process of portability, call transferring, and conferencing.
You can easily integrate this system with your existing telephone to collaborate with your colleagues during team meetings.
You can also merge this system with the company’s corporate directory.
Where can you find help to integrate the Microsoft 365 business with your business?
You can find a few leading companies in UAE that offer Microsoft Teams Phone System including the license to offer wireless networking, video conferencing, and IT solutions. They have a team of experts who can assess Office 365, configure customer information, and set up IT equipment to run your business.
0 notes
Text
LESSON 1
Information and communications technology (ICT) is an extensional term for information technology (IT) that stresses the role of unified communications[ and the integration of telecommunications (telephone lines and wireless signals) and computers, as well as necessary enterprise software, middleware, storage and audiovisual, that enable users to access, store, transmit, and manipulate information.
The term ICT is also used to refer to the convergence of audiovisual and telephone networks with computer networks through a single cabling or link system. There are large economic incentives to merge the telephone network with the computer network system using a single unified system of cabling, signal distribution, and management.
ICT is an umbrella term that includes any communication device, encompassing radio, television, cell phones, computer and network hardware, satellite systems and so on, as well as the various services and appliances with them such as video conferencing and distance learning.ICT is a broad subject and the concepts are evolving.It covers any product that will store, retrieve, manipulate, transmit, or receive information electronically in a digital form (e.g., personal computers, digital television, email, or robots). Theoretical differences between interpersonal-communication technologies and mass-communication technologies have been identified by the philosopher Piyush Mathur.Skills Framework for the Information Age is one of many models for describing and managing competencies for ICT professionals for the 21st century.

Information technology (IT) is the use of computers to store, retrieve, transmit, and manipulate data or information. IT is typically used within the context of business operations as opposed to personal or entertainment technologies. IT is considered to be a subset of information and communications technology (ICT).

Communications technology, also known as information technology, refers to all equipment and programs that are used to process and communicate information. Professionals in the communication technology field specialize in the development, installation, and service of these hardware and software systems.

Emerging technologies are technologies whose development, practical applications, or both are still largely unrealized, such that they are figuratively emerging into prominence from a background of nonexistence or obscurity. These technologies are new, such as various applications of biotechnology including gene therapy. Emerging technologies are often perceived as capable of changing the status quo.
Emerging technologies are characterized by radical novelty (in application even if not in origins), relatively fast growth, coherence, prominent impact, and uncertainty and ambiguity. In other words, an emerging technology can be defined as "a radically novel and relatively fast growing technology characterised by a certain degree of coherence persisting over time and with the potential to exert a considerable impact on the socio-economic domain(s) which is observed in terms of the composition of actors, institutions and patterns of interactions among those, along with the associated knowledge production processes. Its most prominent impact, however, lies in the future and so in the emergence phase is still somewhat uncertain and ambiguous."


Artificial intelligence (AI) refers to the simulation of human intelligence in machines that are programmed to think like humans and mimic their actions. The term may also be applied to any machine that exhibits traits associated with a human mind such as learning and problem-solving.


Robotics is a branch of engineering that involves the conception, design, manufacture, and operation of robots. This field overlaps with electronics, computer science, artificial intelligence, mechatronics, nanotechnology and bioengineering.
Biometrics is the measurement and statistical analysis of people's unique physical and behavioral characteristics. The technology is mainly used for identification and access control or for identifying individuals who are under surveillance.

Quantum cryptography is the science of exploiting quantum mechanical properties to perform cryptographic tasks. The best known example of quantum cryptography is quantum key distribution which offers an information-theoretically secure solution to the key exchange problem.

online learning platform is an integrated set of interactive online services that provide trainers, learners, and others involved in education with information, tools and resources to support and enhance education delivery and management.

Computer-assisted translation (CAT) software translates one language to another using translation memory—which stores previously translated texts—or crowd assistance to provide translations that are consistent with previously used language to ensure proper spelling, grammar, and phrasing.

3D hologram is defined as a 3D projection that exists freely in space and is visible to everyone without the need for 3D glasses. Holography is the next stage of photography and conventional film and its three-dimensionality creates completely new possibilities for use, such as for product presentation.

Virtual reality (VR) refers to a computer-generated simulation in which a person can interact within an artificial three-dimensional environment using electronic devices, such as special goggles with a screen or gloves fitted with sensors.

Online systems – are online versions of information systems, which is “the process of and tools for storing, managing, using, and gathering of data and communications in an organization. An example of information systems are tools for sending out communications and storing files in a business.”

Social Media Platform means a mobile and/or internet-based platform used and controlled by a Seller or any of its Affiliates for the exclusive purpose of promoting the Business,
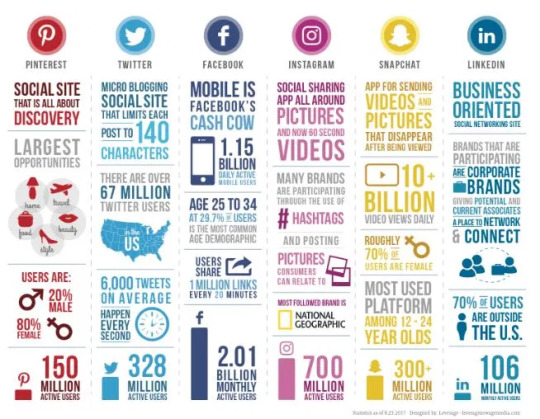
ecommerce platform is a software application that allows online businesses to manage their website, marketing, sales and operations.
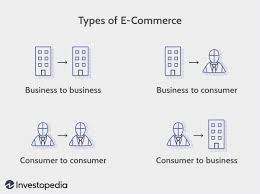
online video platform (OVP), provided by a video hosting service, enables users to upload, convert, store and play back video content on the Internet, often via a structured, large-scale system that may generate revenue. Users generally will upload video content via the hosting service's website, mobile or desktop application, or other interface (API). The type of video content uploaded might be anything from shorts to full-length TV shows and movies. The video host stores the video on its server and offers users the ability to enable different types of embed codes or links that allow others to view the video content. The website, mainly used as the video hosting website, is usually called the video sharing website.

Netiquette is a combination of the words network and etiquette and is defined as a set of rules for acceptable online behavior. Similarly, online ethics focuses on the acceptable use of online resources in an online social environment.

Online search is the process of interactively searching for and retrieving requested information via a computer from databases that are online. ... Research Skills “Research” sometimes just means finding out information about a topic.

online safety refers to the act of staying safe online. ... Being safe online means individuals are protecting themselves and others from online harms and risks which may jeopardise their personal information, lead to unsafe communications or even effect their mental health and wellbeing.


Cyberbullying or cyberharassment is a form of bullying or harassment using electronic means. Cyberbullying and cyberharassment are also known as online bullying. It has become increasingly common, especially among teenagers, as the digital sphere has expanded and technology has advanced.Cyberbullying is when someone, typically a teenager, bullies or harasses others on the internet and in other digital spaces, particularly on social media sites. Harmful bullying behavior can include posting rumors, threats, sexual remarks, a victims' personal information, or pejorative labels (i.e. hate speech).Bullying or harassment can be identified by repeated behavior and an intent to harm. Victims of cyberbulling may experience lower self-esteem, increased suicidal ideation, and a variety of negative emotional responses including being scared, frustrated, angry, or depressed.

Hacking is an attempt to exploit a computer system or a private network inside a computer. Simply put, it is the unauthorised access to or control over computer network security systems for some illicit purpose. ... They can destroy, steal or even prevent authorized users from accessing the system.

Identity theft is the crime of obtaining the personal or financial information of another person to use their identity to commit fraud, such as making unauthorized transactions or purchases.

Plagiarism is presenting someone else's work or ideas as your own, with or without their consent, by incorporating it into your work without full acknowledgement. All published and unpublished material, whether in manuscript, printed or electronic form, is covered under this definition.

WHAT I’VE LEARNED?
I’ve learned to this lesson to know what and how to use some online platforms and to have some knowledge in using it in a good way because there are some issues that we shouldn’t do in the internet. Also I’ve learned some techniques on searching like you should find your web browser based for what we are going to search, we should limit our search and we should check if our spelling is correct when searching ,the safety tips also I’ve learned that we should avoid some scams in the internet, to protect our info’s and our password should be a unique or hard to know so that our accounts will be safe, we should use this searching or using internet in a nice and good way we shouldn’t not use it in unnecessary things.
0 notes