#Virtual Private Networking Services
Explore tagged Tumblr posts
Text
What's everyone's favorite VPNs, I trust Tumblr more than review sites or YouTube sponsorships because you haven't steered me wrong yet
3 notes
·
View notes
Text
1 note
·
View note
Text
1 note
·
View note
Link
#Instagram on Chromebook#improved communication#Creative Way-out#time management#digital ethics#vpn service#cyber ghost#nord vpn#express vpn#vpn#virtual private network#browse instagram#social media usage#digital ethic#android emulator#mobile app#web#school chromebooks#schools#chromebook#blogs#my blogs#blogging#blog lovers#blogger#technology#tech blog
0 notes
Text
VMware Explore 2023 Announcements List
VMware Explore 2023 Announcements List @vexpert #vmwarecommunities #VMwareExplore2023 #VMwareNSX+ #VMwareTanzu #TanzuApplicationPlatform #VMwarevSANMaxStorage #RansomwareRecoveryinVMwareCloud #VMwareEdgeCloudOrchestrator #VMwarePrivateMobileNetwork
Guys lots of great announcements from VMware Explore 2023 from Las Vegas today. VMware is on track with many announcements around cloud solutions and services, including in the realm of VMware Tanzu, VMware NSX, new VMware Cloud Editions, Ransomware Recovery, and edge computing. Let’s take a look at the TLDR of VMware Explore 2023 Announcements. What was announced with VMware Explore…

View On WordPress
#"VMware Cloud 2023#Ransomware Recovery in VMware Cloud#Tanzu Application Platform#VMware Anywhere Workspace AI Integrations#VMware Edge Cloud Orchestrator#VMware Horizon Persistent Virtual Desktops#VMware NSX+ Multi-Cloud Service#VMware Private Mobile Network#VMware Tanzu Intelligence Services#VMware vSAN Max Storage
0 notes
Text
me when companies try to force you to use their proprietary software

anyway
Layperson resources:
firefox is an open source browser by Mozilla that makes privacy and software independence much easier. it is very easy to transfer all your chrome data to Firefox
ublock origin is The highest quality adblock atm. it is a free browser extension, and though last i checked it is available on Chrome google is trying very hard to crack down on its use
Thunderbird mail is an open source email client also by mozilla and shares many of the same advantages as firefox (it has some other cool features as well)
libreOffice is an open source office suite similar to microsoft office or Google Suite, simple enough
Risky:
VPNs (virtual private networks) essentially do a number of things, but most commonly they are used to prevent people from tracking your IP address. i would suggest doing more research. i use proton vpn, as it has a decent free version, and the paid version is powerful
note: some applications, websites, and other entities do not tolerate the use of VPNs. you may not be able to access certain secure sites while using a VPN, and logging into your personal account with some services while using a vpn *may* get you PERMANENTLY BLACKLISTED from the service on that account, ymmv
IF YOU HAVE A DECENT VPN, ANTIVIRUS, AND ADBLOCK, you can start learning about piracy, though i will not be providing any resources, as Loose Lips Sink Ships. if you want to be very safe, start with streaming sites and never download any files, though you Can learn how to discern between safe, unsafe, and risky content.
note: DO NOT SHARE LINKS TO OR NAMES OF PIRACY SITES IN PUBLIC PLACES, ESPECIALLY SOCAL MEDIA
the only time you should share these things are either in person or in (preferably peer-to-peer encrypted) PRIVATE messages
when pirated media becomes well-known and circulated on the wider, public internet, it gets taken down, because it is illegal to distribute pirated media and software
if you need an antivirus i like bitdefender. it has a free version, and is very good, though if youre using windows, windows defender is also very good and it comes with the OS
Advanced:
linux is great if you REALLY know what you're doing. you have to know a decent amount of computer science and be comfortable using the Terminal/Command Prompt to get/use linux. "Linux" refers to a large array of related open source Operating Systems. do research and pick one that suits your needs. im still experimenting with various dispos, but im leaning towards either Ubuntu Cinnamon or Debian.
#capitalism#open source#firefox#thunderbird#mozilla#ublock origin#libreoffice#vpn#antivirus#piracy#linux
694 notes
·
View notes
Text
Hey, kid. Yeah. You. You want free movies and TV shows?
Well, first of all, Internet Archive. Yes, the Wayback Machine people. They have a lot of movies and shows 'n shit you're gonna have a hard time finding elsewhere. (Also, the Alien movies?????) So if you're looking for something weird or niche or old, you might wanna start your search there.
Second of all: In order to get free goodies ✨elsewhere✨, you need three (3) things.
A VPN (virtual private network)
qBittorrent (or some other torrent client, but this is really the go-to these days.)
Places to go, y'know, get stuff.
First: the VPN
This unfortunately is probably going to cost you money. Free VPNs typically collect data, are extremely slow, and/or don't even allow peer to peer downloading in the first place. Beyond that, they're more likely to turn tail and rat you out to your internet service provider (ISP) and get you in trouble. You then get a nice little DMCA letter in the mail threatening you. Get enough of those, and your ISP will kick you out of your plan with them. That's why you need the VPN in the first place--to avoid that.
Be careful to choose a VPN that won't sell your data, allows peer to peer downloading, and won't rat you out to your ISP. There are plenty of discussions about that, and recommendations you can find. Just don't blindly go for the ones you see advertised everywhere (NordVPN, for instance) as those are more likely to sell your data, which is like... antithetical to why you would be using a VPN anyway. Just read the ToS. Personally, I use Mozilla VPN, and I'm very happy with it.
Mozilla VPN, if you buy a full year, is $4.99/mo, billed annually for $59.88. As far as I can tell, this is pretty average as far as cost goes for VPNs. As opposed to spending two or three times that a month for one (1) streaming service... you're gonna save some money.
(Also, as a bonus, if you live in a state where porn websites have started requiring age verification or have completely stopped functioning, you can use this to get around that by making the website think you're in another state! Region locked youtube video? Not anymore! Nervous about being on a public network at the airport or in a coffee shop? Worry not my friend! There are many benefits to having a VPN. Just be aware that some websites and applications do not like VPNs and will flag as suspicious activity (i.e. your bank, paypal, Netflix...) and you're going to be filling out a LOT of captchas and Cloudflare might not like you. But it is what it is.)
You can also host your own VPN, but that's pretty technical, even for me, so... idk, do what you will with that information.
Second: qBittorrent
Idk man, it's qBittorrent. Just download it.
(for real tho, it's free, it's open source software (yay!) and it's not stealing your data or shoving ads down your throat. It's THE torrent client at this point.)
Third: Places to, y'know, get stuff
I gift unto you the r/Piracy megathread. Enjoy.
Frankly, most information you need, recommendations, etc. is gonna be on r/Piracy. They're a godsend. I also recommend this website for a more detailed guide on all the stuff I just put forward. I would tag the user here I got it from but it looks like they deactivated.
Also for the love of god just switch to Firefox and install ublock origin already. Trust me. Just do it. You'll be so much happier. I promise.
Okay thanks bye! Enjoy your free stuff!
21 notes
·
View notes
Text
Resources for LGBTQIA+ People in the US
Here are some mental health, relocation, and gender-affirming care resources that are accessible in the US. I got majority of these resources from @/thetadvocate on ig. If anyone has additional resources, please feel free to reblog and add them!
Brief descriptions are provided of the services offered, and the names of each organization has been linked to lead to their website or linktree for additional information and resources.
Trans LifeLine - Peer support phone service run by trans people for trans and questioning peers. Call at 877-565-8860
Call BlackLine - Provides peer support and counseling for people who are most impacted by systematic oppression with an LGBTQ+ Black Femme Lens. Prioritizes BIPOC (Black, Indigenous, and People of Color).
Available for anyone who is in crisis, wants to describe and interaction with law enforcement or vigilantes, or simply needs to talk through an experience. You do not have to provide any personal information to use this service. All calls remain private and will never be shared with law enforcement or state agencies of any kind. Call at 1 (800) 604-5841
SAGE Hotline - Free 24/7 support for LGBTQ+ elders. Call at 877-360-5428
The Trevor Project- 24/7 crisis hotline for LGBTQ+ youth. Click here for call, text, and chat information.
LGBT National Youth Talkline - Talkline for LGBTQ+ callers of any age. Hotline is open Mon-Fri from 11am-8pn pacific time (2pm-11pm eastern time) and on Saturdays from 9am-2pm pacific (12pm-6pm eastern). Call at 800-246-7743
Trans Advocacy And Care Team (TACT) - offers 3 free peer counseling sessions* for Trans people by trans-identified peer counselors, plus peer support groups. Support is available virtually to trans adults across the US.
*For ongoing support, TACT offers additional sessions on a sliding scale basis or can provide referrals to trans-affirming mental health providers.
National Queer and Trans Therapists of Color Network - healing justice organization committed to transforming mental health for queer and trans people of color. Offers community resources, directory of therapists, organization listing and crisis hotlines.
Rainbow Railroad - Helps LGBTQ+ people across the world escape state-sponsored violence, providing travel to their destination country and immediate, bridging post-travel support on arrival.
Elevated Access - Volunteer pilots transport passengers at no cost to access the gender affirming care they need.
Transcend Campaign - Funds out-of-state healthcare travel, inclusive school tuition, and small cash grants for queer youth in unsafe areas of Iowa, Minnesota, North Dakota, South Dakota, Wisconsin and/or the Native Nations therein.
The TransLatin@ Coalition - Provides essential resources such as housing support, legal aid, and healthcare access to transgender, gender expansive, and intersex (TGI) immigrants in Los Angeles, California
Trans Rescue - Helps trans, intersex, and other people flee places where it is dangerous to be trans. They cannot fund travel, but can help create evacuation plans. Offers help both inside the US and outside of the US. Email [email protected] for 1 hour free consultation.
Marsha's House - NYC safe housing for trans & non-binary individuals, offers a wide array of programs.
Safe to Be You! - Free legal aid in New Mexico for LGBTQIA+ survivors of violence.
Northwest Network - National LGBTQ+ domestic violence support network. Call at 206-568-7777
The Network/LA Red - 24 hour free hotline provides confidential emotional support, safety planning, and crisis prevention for LGBTQ+ folks, as well as folks in kink and polyamorous communities who are being abused or have been abused by a partner. Contact at 617-742-4911 (voice) or 800-832-1901 (toll-free)
NYC Anti-Violence Project - Free, bilingual (English/Spanish), 24 hour crisis intervention hotline offering support to LGBTQ+ and HIV affected survivors of any type of violence, as well as to those who love and support survivors, including those who have lost a loved one to violence. Call at 212-714-1141
For additional trans mental health resources, as well as trans resources specific to the New Jersey area, @/thetadvocate has compiled a series of google docs. You can find the documents listed in their linktree.
#lgbtqia#lgbtqia+#lgbtq#lgbtq+#queer#queer community#trans#transgender#protect trans kids#protect trans lives#intersex#nonbinary#non binary#resources#mental health#counseling
21 notes
·
View notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes
Text
very brief torrent security primer
some brief comments on piracy safety for @goblin-thembo who has been asking a lot of questions in the notes of that post...
OK, so when you download a torrent, you are downloading some files. The BitTorrent protocol makes it almost impossible to substitute a different file than the one you request, but you have no way to be absolutely certain that the original file is 'safe' - that depends on the properties of the file, and what you do with it. Some types of file are safer than others.
Here's some jargon you may find useful.
torrent: a file that describes how to download some files through the BitTorrent protocol. we won't go into the technicalities, but when you load a torrent into your torrent client, you will connect to other people who have parts of the files, download the pieces, and reassemble the files you want.
seeding: providing a copy of the files in a torrent to other people.
ISP: Internet Service Provider, the company that connects you to the internet.
IP address: your computer's identity on a network, notably the public internet. When you connect to a website, they know your IP address. Your IP address is assigned by your ISP.
From an IP address, you can determine someone's broad geographical location (which country they're connected in) and which ISP they are using. You can contact the ISP, who will be able to associate it with a specific user.
swarm: the collection of users downloading or seeding a particular torrent.
VPN: Virtual Private Network, a relay service which hides your IP address from the public internet. People who connect to you will see the VPN's IP instead of your real IP. Your ISP will be able to know that you connected to a VPN, but not what you send through it. So they wouldn't be able to tell if you are using BitTorrent. VPNs usually cost a fairly small amount of money as a subscription service.
Threat model
In security we talk about a 'threat model', which is what you think you need to protect yourself from. There are two major threats when downloading files using BitTorrent.
copyright claims: your computer's IP is broadcast when you use BitTorrent. Copyright holders will often put 'sniffers' on the network which will monitor the IPs in the swarm of popular torrents. They will then send a takedown letter to your internet service provider (ISP), who will usually send you an email to stop sharing copyrighted media on their network, and then cut off your internet on multiple offences. This can easily be circumvented using a VPN. I strongly recommend using a VPN if you download any copyrighted content through BitTorrent.
attacks through the file you download: someone might upload a virus as a torrent, presenting it as a file you might be looking for (e.g. cracked software). So let's go over different types of file you might download and how they could be used to attack you.
Executable files, such as pirated software, are not safe. If you download a program and run it, you are potentially giving the author full control over your computer. So you should make damn sure the uploader is trustworthy. If you're downloading open source software from the maintainer's github release page, you're probably good. If you're downloading cracked art programs or games... good luck lol.
On a public torrent tracker, to which anyone can upload, there is no guarantee that any file is what anyone says. You have to make your own determination of which uploaders are trustworthy. I can't give you great advice on this, since I generally do not download cracked executables. For games, FitGirl Repacks is generally a pretty good source.
If you are on Windows, the default Windows Defender software should be used to scan any file you download. (Paid antivirus software is of somewhat dubious utility, often pushing ads and using CPU resources in its own right.) Fewer attackers will target desktop Linux or OSX, which doesn't mean you're guaranteed safe, but Windows is the biggest target as the most widely used operating system.
Videos, music and images are generally safe. I say 'generally' because it's possible, in theory, to create a video that exploits a vulnerability in your video player (e.g. mpv or VLC) and uses it to execute code. So far as I know this is largely theoretical, and known vulns have been patched, but make sure to keep your player up to date to mitigate against known vulnerabilities.
Any compressed archives (zip, rar, 7zip) can be used to create something called a 'zip bomb', which is a file which goes into an infinite loop when you try to decompress it, swallowing up more and more memory and hard drive space. I've never seen this actually be done, but it's possible. More subtle attacks would attempt to attack the program you use to decompress the file. Keep your software up to date to mitigate against known vulnerabilities.
Besides taking care about what you download, on Windows you should either not run your main account as an admin account, or make sure to set User Account Control to require a credentials check for admin operations, and also keep your operating system and software up to date. Make sure file extensions are visible so you don't get fooled by a file disguised as a different file type. And y'know, if the torrent tracker has comments, check to see if a lot of people are saying it's a virus.
What could happen if your computer gets infected? Well, they might use your computer to mine crypto at the cost of your CPU performance, they might encrypt and ransom your files, and they might steal your credentials for online services (including banking and the like). There are various measures you can take against this, such as making sure to encrypt sensitive data such as passwords, but the best defense is to not infect your computer in the first place.
The most likely time for people to upload viruses is when something is in high demand and there isn't a single authoritative high-quality source out yet.
Ultimately you get to decide what you consider an acceptable level of risk. There is no such thing as perfect safety. I would recommend using your own initiative to learn about computer security and not badger random tumblr users to explain it to you, but hopefully the above guidelines should help you avoid doing anything too dangerous.
189 notes
·
View notes
Text
VPNs aren't just for pirates and company data anymore
A friend complained to me that they couldn't access pr0n anymore because the government is now requiring ID to verify age where they are, and due to data leaks and privacy issues, didn't want to share their ID even though they're of legal age.
Shit like this doesn't work on the intended target. It only frustrates people who are aren't tech savvy while a lot of kids have already found their way around it because that's what kids do ¯\_(ツ)_/¯
When I talk about VPNs (virtual private networks), non-tech savvy people's eyes glaze over 😂
It sounds like complicated, unknowable magic. It's not! And you don't even have to understand it to use it!
With the government and ISPs (internet service providers) invading privacy more and more and hackers breaking in and stealing user data from companies, VPNs are becoming necessary.
Some Things a VPN Does for You:
hides your data from others
can make your internet speeds faster if your ISP does speed throttling (purposely making your speed slower)
hides what you're doing from your ISP
keeps you safer from some malware, viruses, hackers, and trackers
allows you to access things that are either restricted in your area or not available in your area (such as content in other countries)
keeps you safer when you're out in public connected to wifi
Below is a basic infographic on how VPNs work. When you access the internet, a VPN encrypts your data - making it into a secret code that can't be read by anyone else including your ISP.
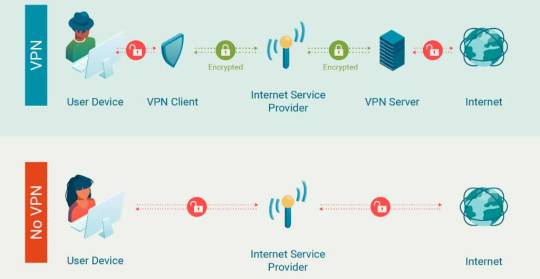
Tech companies, ISPs, etc. want you to think VPNs are complicated so that you won't use them.
When searching for a free VPN, please be aware that a lot of the free VPN services out there are malware or full of viruses and trackers.
Either do some research into which one to choose or use a paid VPN service. You can either pay monthly or yearly - the yearly is always cheaper in the long run.
Some of the Top Rated VPN Services:
ExpressVPN $7 - $13/month
NordVPN $3 - $13/month
Surfshark $2 - $14/month
PrivateInternetAccess $2 - $12/month
ProtonVPN (some sites block this one) $4 - $10/month
CyberGhost $2 - $13/month
I use ExpressVPN, so for the purposes of this post, I'm going to use screenshots from ExpressVPN.
Once you have an account, download the program from the website to your desktop/laptop or find the app on Android or iOS app stores.
Signing in requires a code that the VPN will email to you that unlocks all the features. Pay attention when the program installs because it'll ask you about preferences, and you can easily check yes on blocking pr0n when that's the reason you wanted a VPN in the first place 😂
When the program is open, you'll see this:

As you can see in the screenshot, not only do I have the program, but I have an ExpressVPN icon on my browser. The program installs this automatically, and when the program is running, the icon will have a green checkmark on it so you know it's working in your browser.
You'll notice I've recently connected using Japan. I did this so I could watch a series that isn't available outside of Japan.
The program automatically chooses a location near you, but if you want to access things that are restricted to you, make sure you click on the three dots to the right of the selected location (see screenshot below) and search for a state/country/place that your content will be available in.

Once your location is selected, click on the start/power button, and you'll get a popup notification from your computer that ExpressVPN is connected.
Go to the site you want to use and use it like you normally would.
Here's what it should look like when it's running correctly:

Keep in mind that if you leave a VPN running all the time (which is perfectly fine to do), search engines like Google will assume you live wherever ExpressVPN tells it you live, so searching for "stores near me" will give you results that aren't close to you.
When you're done using the VPN, just hit the power button again and it shuts off.
I use this on all my handheld devices, my desktop, and my laptop for business and personal reasons. I'm a pirate, and I've been using VPNs for a long time, yet none of the ISPs I've used have ever given me a warning about torrenting.
Good luck, and enjoy all the new things you can access!
BTW for anybody wondering, my desktop wallpaper is a map of the world's time zones. So pretty!! 😍
75 notes
·
View notes
Text
X missed a deadline imposed by Supreme Court Justice Alexandre de Moraes to name a legal representative in Brazil, triggering the suspension. It marks an escalation in the monthslong feud between Musk and de Moraes over free speech, far-right accounts and misinformation.
To block X, Brazil’s telecommunications regulator, Anatel, told internet service providers to suspend users’ access to the social media platform. As of Saturday at midnight local time, major operators began doing so.
De Moraes had warned Musk on Wednesday night that X could be blocked in Brazil if he failed to comply with his order to name a representative, and established a 24-hour deadline. The company hasn’t had a representative in the country since earlier this month.
“Elon Musk showed his total disrespect for Brazilian sovereignty and, in particular, for the judiciary, setting himself up as a true supranational entity and immune to the laws of each country,” de Moraes wrote in his decision on Friday.
The justice said the platform will stay suspended until it complies with his orders, and also set a daily fine of 50,000 reais ($8,900) for people or companies using VPNs to access it.
In a later ruling, he backtracked on his initial decision to establish a 5-day deadline for internet service providers themselves — and not just the telecommunications regulator — to block access to X, as well as his directive for app stores to remove virtual private networks, or VPNs.
The dispute also led to the freezing this week of the bank accounts in Brazil of Musk's satellite internet provider Starlink.
15 notes
·
View notes
Note
Hey ! I learnt about the first Mononoke movie through your blog a year ago ! I recommended it to a friend, who’s currently watching the series but can’t find the first bakeneko arc on YouTube anymore. Any clue where we can find it ? Thanks for your answer :)
I'm so glad you learned about the movie through this blog!
You can actually purchase DVD copies of "Bakeneko" on eBay for not that much money. If you search "ayakashi samurai horror tales dvd," quite a few listings turn up. Here are a couple:
https://www.ebay.com/itm/374740497418
https://www.ebay.com/itm/326096094288
https://www.ebay.com/itm/135396841633
These are Region 1 DVDs (there's a BluRay, but it's $50) and most, if not all, of eBay's listings ship from North America. If Region 1 doesn't work in your country, or if they don't ship there, or if you'd rather not go through eBay, then there are other (less legal) options for watching online:
Streaming:
You can find Ayakashi "Bakeneko" streaming on a few sites, like 9anime. They are currently hosting the entire Ayakashi Horror Tales anthology, including "Bakeneko" (listed as "Ghost Cat" on their site). AniWatch is another site I've seen mentioned, although I've never used it and am not sure if they have "Bakeneko."
Cons of using streaming sites:
(1) They may not be safe (my antivirus throws up a warning as soon as I open 9anime),
(2) they've got ads that also might be unsafe, so you'll need an ad blocker, and
(3) you can't download the files so you still have them if the site goes down (illegal services often do), unless you use a screen recorder, which is its own headache. 🙃
Torrents:
Probably the best way to get "Bakeneko" online is to download it via torrent. Here's a full subtitled pack that also includes the series: https://nyaa.si/view/301865.
Cons of using torrents: You need to go through a few steps and spend a little money to do it safely.
If you've never used torrents before:
(1) Make sure to use torrents only when you're logged on to a VPN (Virtual Private Network). This will keep you from being tracked via your IP address. You can set the VPN's location to a torrenting-friendly country (Switzerland is currently the best option) for maximum safety.
ExpressVPN is a good VPN option. It's not free, but it's pretty cheap: https://www.expressvpn.com. The interface is very simple and easy to use.
NordVPN also has a good rep and is a bit cheaper at the moment: https://nordvpn.com
There are free VPNs, but they're not safe and should be avoided.
(2) You'll also need a safe torrenting client to install on your computer. Fortunately, those are free. qBittorrent is currently recommended: https://www.qbittorrent.org/
The last step is to download the torrent file to your computer and then open it with qBittorent (or whichever client you're using). The client will then download the video files to your computer (should take a little while). Stay logged on to the VPN until everything is downloaded and you've exited qBittorent. 😉
Obviously, the simplest, safest, and most legal way is to purchase a DVD copy via eBay, if you can do that.
Best of luck!
12 notes
·
View notes
Text

The Optimist by Keach Hagey
The man who brought us ChatGPT. Sam Altman’s extraordinary career – and personal life – under the microscope
On 30 November 2022, OpenAI CEO Sam Altman tweeted the following, characteristically reserving the use of capital letters for his product’s name: “today we launched ChatGPT. try talking with it here: chat.openai.com”. In a reply to himself immediately below, he added: “language interfaces are going to be a big deal, i think”.
If Altman was aiming for understatement, he succeeded. ChatGPT became the fastest web service to hit 1 million users, but more than that, it fired the starting gun on the AI wars currently consuming big tech. Everything is about to change beyond recognition, we keep being told, though no one can agree on whether that will be for good or ill.
This moment is just one of many skilfully captured in Wall Street Journal reporter Keach Hagey’s biography of Altman, who, like his company, was then virtually unknown outside of the industry. He is a confounding figure throughout the book, which charts his childhood, troubled family life, his first failed startup Loopt, his time running the startup incubator Y Combinator, and the founding of OpenAI.
Altman, short, slight, Jewish and gay, appears not to fit the typical mould of the tech bro. He is known for writing long, earnest essays about the future of humankind, and his reputation was as more of an arch-networker and money-raiser than an introverted coder in a hoodie.
OpenAI, too, was supposed to be different from other tech giants: it was set up as a not-for-profit, committed by its charter to work collaboratively to create AI for humanity’s benefit, and made its code publicly available. Altman would own no shares in it.
He could commit to this, as he said in interviews, because he was already rich – his net worth is said to be around $1.5bn (£1.13bn) – as a result of his previous investments. It was also made possible because of his hyper-connectedness: as Hagey tells it, Altman met his software engineer husband Oliver Mulherin in the hot tub of PayPal and Palantir co-founder Peter Thiel at 3am, when Altman, 29, was already a CEO, and Mulherin was a 21-year-old student.
Thiel was a significant mentor to Altman, but not nearly so central to the story of OpenAI as another notorious Silicon Valley figure – Elon Musk. The Tesla and SpaceX owner was an initial co-founder and major donor to the not-for-profit version of OpenAI, even supplying its office space in its early years.
That relationship has soured into mutual antipathy – Musk is both suing OpenAI and offering (somewhat insincerely) to buy it – as Altman radically altered the company’s course. First, its commitment to releasing code publicly was ditched. Then, struggling to raise funds, it launched a for-profit subsidiary. Soon, both its staff and board worried the vision of AI for humanity was being lost amid a rush to create widely used and lucrative products.
This leads to the book’s most dramatic sections, describing how OpenAI’s not-for-profit board attempted an audacious ousting of Altman as CEO, only for more than 700 of the company’s 770 engineers to threaten to resign if he was not reinstated. Within five days, Altman was back, more powerful than ever.
OpenAI has been toying with becoming a purely private company. And Altman turns out to be less of an anomaly in Silicon Valley than he once seemed. Like its other titans, he seems to be prepping for a potential doomsday scenario, with ranch land and remote properties. He is set to take stock in OpenAI after all. He even appears to share Peter Thiel’s supposed interest in the potential for transfusions of young blood to slow down ageing.
The Optimist serves to remind us that however unprecedented the consequences of AI models might be, the story of their development is a profoundly human one. Altman is the great enigma at its core, seemingly acting with the best of intentions, but also regularly accused of being a skilled and devious manipulator.
For students of the lives of big tech’s other founders, a puzzling question remains: in a world of 8 billion human beings, why do the stories of the people wreaking such huge change in our world end up sounding so eerily alike?
Daily inspiration. Discover more photos at Just for Books…?
4 notes
·
View notes
Text
X has clashed with de Moraes over its reluctance to comply with orders to block users. "Brazil blocks Musk’s X after company refuses to name local representative amid feud with judge"
"The justice said the platform will stay suspended until it complies with his orders, and also set a daily fine of 50,000 reais ($8,900) for people or companies using VPNs to access it."
“When we attempted to defend ourselves in court, Judge de Moraes threatened our Brazilian legal representative with imprisonment. Even after she resigned, he froze all of her bank accounts,” the company wrote.
X has clashed with de Moraes over its reluctance to comply with orders to block users.
The looming shutdown is not unprecedented in Brazil.
Lone Brazilian judges shut down Meta’s WhatsApp, the nation’s most widely used messaging app, several times in 2015 and 2016 due to the company’s refusal to comply with police requests for user data. In 2022, de Moraes threatened the messaging app Telegram with a nationwide shutdown, arguing it had repeatedly ignored Brazilian authorities’ requests to block profiles and provide information. He ordered Telegram to appoint a local representative; the company ultimately complied and stayed online.
X and its former incarnation, Twitter, have been banned in several countries — mostly authoritarian regimes such as Russia, China, Iran, Myanmar, North Korea, Venezuela and Turkmenistan. Other countries, such as Pakistan, Turkey and Egypt, have also temporarily suspended X before, usually to quell dissent and unrest. Twitter was banned in Egypt after the Arab Spring uprisings, which some dubbed the "Twitter revolution," but it has since been restored.
A search Friday on X showed hundreds of Brazilian users inquiring about VPNs that could potentially enable them to continue using the platform by making it appear they were logging on from outside the country. It was not immediately clear how Brazilian authorities would police this practice and impose fines cited by de Moraes.

By GABRIELA SÁ PESSOA, BARBARA ORTUTAY and DAVID BILLERAugust 30, 2024
SAO PAULO — (AP) — Brazil started blocking Elon Musk's social media platform X early Saturday, making it largely inaccessible on both the web and through mobile apps after the billionaire refused to name a legal representative to the country.
The move escalates a monthslong feud between Musk and a Brazilian Supreme Court justice over free speech, far-right accounts and misinformation. Justice Alexandre de Moraes ordered the suspension on Friday.
To block X, Brazil’s telecommunications regulator, Anatel, told internet service providers to suspend users’ access to the social media platform. As of Saturday after midnight local time, major operators had begun doing so.
De Moraes had warned Musk on Wednesday night that X could be blocked in Brazil if he failed to comply with his order to name a representative, and established a 24-hour deadline. The company hasn’t had a representative in the country since earlier this month.
“Elon Musk showed his total disrespect for Brazilian sovereignty and, in particular, for the judiciary, setting himself up as a true supranational entity and immune to the laws of each country,” de Moraes wrote in his decision on Friday.
The justice said the platform will stay suspended until it complies with his orders, and also set a daily fine of 50,000 reais ($8,900) for people or companies using VPNs to access it.
In a later ruling, he backtracked on his initial decision to establish a 5-day deadline for internet service providers themselves — and not just the telecommunications regulator — to block access to X, as well as his directive for app stores to remove virtual private networks, or VPNs.
Brazil is one of the biggest markets for X, which has struggled with the loss of advertisers since Musk purchased the former Twitter in 2022. Market research group Emarketer says some 40 million Brazilians, roughly one-fifth of the population, access X at least once per month.
“This is a sad day for X users around the world, especially those in Brazil, who are being denied access to our platform. I wish it did not have to come to this – it breaks my heart,” X’s CEO Linda Yaccarino said Friday night, adding that Brazil is failing to uphold its constitution’s pledge to forbid censorship.
X had posted on its official Global Government Affairs page late Thursday that it expected X to be shut down by de Moraes, “simply because we would not comply with his illegal orders to censor his political opponents.”
“When we attempted to defend ourselves in court, Judge de Moraes threatened our Brazilian legal representative with imprisonment. Even after she resigned, he froze all of her bank accounts,” the company wrote.
X has clashed with de Moraes over its reluctance to comply with orders to block users.
Accounts that the platform previously has shut down on Brazilian orders include lawmakers affiliated with former President Jair Bolsonaro’s right-wing party and activists accused of undermining Brazilian democracy. X’s lawyers in April sent a document to the Supreme Court in April, saying that since 2019 it had suspended or blocked 226 users.
In his decision Friday, de Moraes' cited Musk's statements as evidence that X's conduct “clearly intends to continue to encourage posts with extremism, hate speech and anti-democratic discourse, and to try to withdraw them from jurisdictional control.”
In April, de Moraes included Musk as a target in an ongoing investigation over the dissemination of fake news and opened a separate investigation into the executive for alleged obstruction.
Musk, a self-proclaimed “free speech absolutist," has repeatedly claimed the justice’s actions amount to censorship, and his argument has been echoed by Brazil’s political right. He has often insulted de Moraes on his platform, characterizing him as a dictator and tyrant.
De Moraes’ defenders have said his actions aimed at X have been lawful, supported by most of the court’s full bench and have served to protect democracy at a time it is imperiled. He wrote Friday that his ruling is based on Brazilian law requiring internet services companies to have representation in the country so they can be notified when there are relevant court decisions and take requisite action — specifying the takedown of illicit content posted by users, and an anticipated churn of misinformation during October municipal elections.
The looming shutdown is not unprecedented in Brazil.
Lone Brazilian judges shut down Meta’s WhatsApp, the nation’s most widely used messaging app, several times in 2015 and 2016 due to the company’s refusal to comply with police requests for user data. In 2022, de Moraes threatened the messaging app Telegram with a nationwide shutdown, arguing it had repeatedly ignored Brazilian authorities’ requests to block profiles and provide information. He ordered Telegram to appoint a local representative; the company ultimately complied and stayed online.
X and its former incarnation, Twitter, have been banned in several countries — mostly authoritarian regimes such as Russia, China, Iran, Myanmar, North Korea, Venezuela and Turkmenistan. Other countries, such as Pakistan, Turkey and Egypt, have also temporarily suspended X before, usually to quell dissent and unrest. Twitter was banned in Egypt after the Arab Spring uprisings, which some dubbed the "Twitter revolution," but it has since been restored.
A search Friday on X showed hundreds of Brazilian users inquiring about VPNs that could potentially enable them to continue using the platform by making it appear they were logging on from outside the country. It was not immediately clear how Brazilian authorities would police this practice and impose fines cited by de Moraes.
“This is an unusual measure, but its main objective is to ensure that the court order to suspend the platform's operation is, in fact, effective," Filipe Medon, a specialist in digital law and professor at the law school of Getulio Vargas Foundation, a university in Rio de Janeiro, told The Associated Press.
Mariana de Souza Alves Lima, known by her handle MariMoon, showed her 1.4 million followers on X where she intends to go, posting a screenshot of rival social network BlueSky.
On Thursday evening, Starlink, Musk’s satellite internet service provider, said on X that de Moraes this week froze its finances, preventing it from doing any transactions in the country where it has more than 250,000 customers.
“This order is based on an unfounded determination that Starlink should be responsible for the fines levied—unconstitutionally—against X. It was issued in secret and without affording Starlink any of the due process of law guaranteed by the Constitution of Brazil. We intend to address the matter legally,” Starlink said in its statement. The law firm representing Starlink told the AP that the company appealed, but wouldn’t make further comment.
Musk replied to people sharing the reports of the freeze, adding insults directed at de Moraes. “This guy @Alexandre is an outright criminal of the worst kind, masquerading as a judge,” he wrote.
Musk later posted on X that SpaceX, which runs Starlink, will provide free internet service in Brazil “until the matter is resolved” since “we cannot receive payment, but don’t want to cut anyone off.”
In his decision, de Moraes said he ordered the freezing of Starlink’s assets, as X didn't have enough money in its accounts to cover mounting fines, and reasoning that the two companies are part of the same economic group.
While ordering X’s suspension followed warnings and fines and so was appropriate, taking action against Starlink seems “highly questionable,” said Luca Belli, coordinator of the Getulio Vargas Foundation’s Technology and Society Center.
“Yes, of course, they have the same owner, Elon Musk, but it is discretionary to consider Starlink as part of the same economic group as Twitter (X). They have no connection, they have no integration,” Belli said.
___
Ortutay reported from San Francisco and Biller from Rio. AP writer Mauricio Savarese contributed from Sao Paulo.
Copyright 2024 The Associated Press. All rights reserved. This material may not be published, broadcast, rewritten or redistributed without permission.
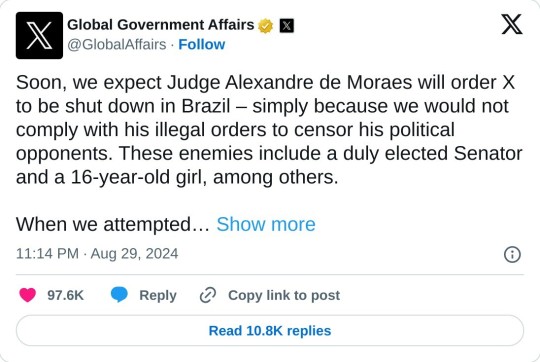
Soon, we expect Judge Alexandre de Moraes will order X to be shut down in Brazil – simply because we would not comply with his illegal orders to censor his political opponents. These enemies include a duly elected Senator and a 16-year-old girl, among others. When we attempted to defend ourselves in court, Judge de Moraes threatened our Brazilian legal representative with imprisonment. Even after she resigned, he froze all of her bank accounts. Our challenges against his manifestly illegal actions were either dismissed or ignored. Judge de Moraes’ colleagues on the Supreme Court are either unwilling or unable to stand up to him. We are absolutely not insisting that other countries have the same free speech laws as the United States. The fundamental issue at stake here is that Judge de Moraes demands we break Brazil’s own laws. We simply won’t do that. In the days to come, we will publish all of Judge de Moraes’ illegal demands and all related court filings in the interest of transparency. Unlike other social media and technology platforms, we will not comply in secret with illegal orders. To our users in Brazil and around the world, X remains committed to protecting your freedom of speech. ------------------- Em breve, esperamos que o Ministro Alexandre de Moraes ordene o bloqueio do X no Brasil – simplesmente porque não cumprimos suas ordens ilegais para censurar seus opositores políticos. Dentre esses opositores estão um Senador devidamente eleito e uma jovem de 16 anos, entre outros. Quando tentamos nos defender no tribunal, o Ministro ameaçou prender nossa representante legal no Brasil. Mesmo após sua renúncia, ele congelou todas as suas contas bancárias. Nossas contestações contra suas ações manifestamente ilegais foram rejeitadas ou ignoradas. Os colegas do Ministro Alexandre de Moraes no Supremo Tribunal Federal estão ou impossibilitados de ou não querem enfrentá-lo. Não estamos absolutamente insistindo que outros países tenham as mesmas leis de liberdade de expressão dos Estados Unidos. A questão fundamental em jogo aqui é que o Ministro Alexandre de Moraes exige que violemos as próprias leis do Brasil. Simplesmente não faremos isso. Nos próximos dias, publicaremos todas as exigências ilegais do Ministro e todos os documentos judiciais relacionados, para fins de transparência. Ao contrário de outras plataformas de mídia social e tecnologia, não cumpriremos ordens ilegais em segredo. Aos nossos usuários no Brasil e ao redor do mundo, o X continua comprometido em proteger sua liberdade de expressão.

13 notes
·
View notes
Text
By showing Musk’s X the red card, has Brazil scored a goal for all democracies?

At 10 minutes past midnight on 31 August, Elon Musk’s X (nee Twitter) went dark in Brazil, a country of more than 200 million souls, many of them enthusiastic users of online services. The day before, a supreme court justice, Alexandre de Moraes, had done something hitherto unthinkable: ordered the country’s ISPs to block access to the platform, threatened a daily fine of 50,000 Brazilian reis (just under £6,800) for users who bypassed the ban by using virtual private networks (VPNs) and froze the finances of Elon Musk’s Starlink internet service provider in the country. The order would remain in force until the platform complied with the decisions of the supreme federal court, paid fines totalling 18.3m reis (nearly £2.5m) and appointed a representative in Brazil, a legal requirement for foreign companies operating there. Moraes had also instructed Apple and Google to remove the X app and VPN software from their stores, but later reversed that decision, citing concerns about potential “unnecessary” disruptions.
Cue shock, horror, incredulity, outrage and all the reactions in between. Musk – who has been sparring with Moraes for quite a while – tweeted: “Free speech is the bedrock of democracy and an unelected pseudo-judge in Brazil is destroying it for political purposes.” The animosity between the two goes back to 8 January 2023, after the defeat of Jair Bolsonaro in the 2022 Brazilian presidential election, when a mob of his supporters attacked federal government buildings in the capital, Brasília. The mob invaded and caused deliberate damage to the supreme federal court, the national congress and the Planalto presidential palace in an abortive attempt to overthrow the democratically elected president, Luiz Inácio Lula da Silva.
Justice Moraes is in the firing line because before the 2022 presidential election the country’s supreme court had given him expansive powers to crack down on online threats to democracy and he has been an enthusiastic deployer of that capability ever since. A New York Times report, for example, said that he “jailed five people without a trial for posts on social media that he said attacked Brazil’s institutions. He has also ordered social networks to remove thousands of posts and videos with little room for appeal.” And it is this last practice that brought him into collision with Musk, whose platform was one of the channels used by the 8 January insurgents.
Media coverage of this clash has predictably personalised it as ruthless enforcer versus tech titan. Who will blink first? Why on earth did Musk pick this fight? Has his fatuous obsession with free speech finally pushed him over the edge? After all, he could have complied with Moraes’s takedown orders, kept the office in Brasília and fought the issue through the Brazilian courts. Instead, he took his ball away, leaving more than 20 million Brazilian X users bereft. On the other hand, although Moraes turned out to be a pretty effective check on Bolsonaro – a cut-price Donald Trump who attacked the media, the courts and the country’s electoral system – some critics are beginning to wonder whether, in his mission to protect democracy, the judge may also wind up eroding it.
Who knows? But for now at least, one thing is clear: this is the first time a democratic state has shut down a main tech platform. Autocracies do this at will (for instance, China, Russia, Iran, Gulf states), but until now democracies have shied away from such an extreme measure. Listening to some of the chatter on the web about the Moraes order provides a clue to the timidity, for what you pick up is astonishment at the effrontery of a mere Brazilian who dares to take down a big American platform because it doesn’t obey the law of his particular land. Who does he think he is? Doesn’t he understand Silicon Valley’s “manifest destiny” to be the prime engine of human progress, leaving lesser breeds bobbing helplessly in its wake?
Continue reading.
#brazil#brazilian politics#politics#twitter#elon musk#alexandre de moraes#supreme federal court#image description in alt#mod nise da silveira
10 notes
·
View notes