#VPN for IoT
Explore tagged Tumblr posts
Text
0 notes
Text
0 notes
Text
Cyberchase: How to Hack the Motherboard
So, when I was writing my episode discussion post on Cyberchase Season 1 Episode 1 "Lost My Marbles", I mentioned that I might make another post about the security breach that allowed The Hacker to infect Motherboard with the virus. What did The Hacker do to set this up? How did the kids accidentally open the breach? And other questions like that. I have a bit of background in software engineering. I will try to keep things as simple as possible.
Much of this is head-canon built on top of what we see in the episode. Of course, the show plays it fast and loose with computer terminology. Don't try to hack things in real life. You will go to prison.
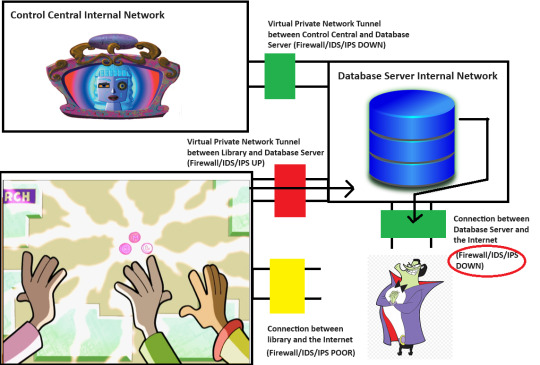
So, here's an MSPaint diagram of a tiny piece of Motherboard's setup. Keep in mind that she is the god of the Internet, and her Internet may even stretch beyond Earth into other galaxies.
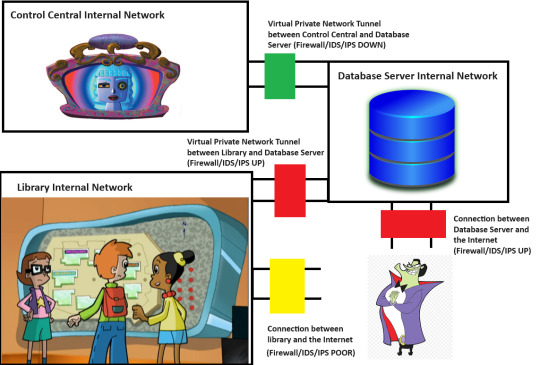
So, there are three separate network segments here. We have the library's internal network, which has the big board on it. We have Control Central's internal network, which has Motherboard on it. And then we have a Database Server internal network, which has a Database Server running on it.
The Database Server is something that I invented here. Remember that this whole diagram is head-canon. However, it's not too far-fetched to think that Motherboard must reach across Cyberspace to a separate Database Server, maybe at the Cybrary.
Now, we know that Motherboard is not directly reachable, even with her Firewall down. Otherwise, The Hacker wouldn't have needed a separate security breach to get to her. He would have just pushed the virus once she took down her firewall for maintenance.
However, Motherboard has a Virtual Private Network (VPN) tunnel to the Database Server. If The Hacker can compromise the Database Server and get his virus in there, it might be able to ride the tunnel into Control Central.
The purpose of any Firewall is to apply a set of rules to any network traffic going into or out of a network, device or application. A good Firewall configuration allows on the traffic that is needed and denies everything else. Motherboard's firewall between herself and the Database Server is currently down. The Database Server itself has connection points to the larger Internet without using a VPN tunnel. However, the Database Server's own Firewall for that access point is UP. If The Hacker tried to throw his virus at that access point, it wouldn't work.
However, there is another connection point into the Database Server. This is another VPN tunnel from the library network. Let's say that the board retrieves the data on the locations of different objects on the map and the icons for those objects by reading one of the Databases. Maybe the board also writes data to the Database to log what directions people requested.
The point here is that some traffic from the Board is authorized to pass through the Firewall on that VPN tunnel. Now, is there a way for The Hacker to get the Board to send authorized traffic over the VPN tunnel to tell the Database Server to open a breach in the Firewall for that public access point? Maybe. It is an Internet-of-Things (ioT) device. Alot of people get these devices, and then they either leave passwords set to their defaults or they forget to keep the sofware patches up to date.
There is a public access point to the Board with a poorly-configured firewall. Maybe there's a way for him to get inside. It may be possible for him to dump the virus code into the board, but there's no guarantee that it would be able to go any further, since the Firewall between the Board and the Database Server is working.
So, let's think about the Board as its own thing.

Suppose that we have two user accounts associated with the board. There is a Principle of Least Privilege that states that a given user account or system process should only be given the minimum amount of permissions required to perform its tasking. That way, if the user account or system process attempts to do something out of line with its permissions, it won't be allowed to perform the operation.
However, if you leave other unnecessary permissions open, and the user account or system process attempts to do something outside of its original intended operations, then the operation may succeed and have unintended consequences.
This also links up with the software development concept of the Minimum Viable Product. You build your software to perform only the exact tasking that it needs it perform. You don't put any additional, undocumented functions in there. Otherwise, those functions could activate and have unexpected consequences.
The board's purpose it to display the different locations. It allows for users to input two points, and it will draw a line between them to assist in navigation. We also established earlier that it reads its information from the Database and writes other information out to the Database.
However, suppose there was some undocumented functionality here. Suppose the developers had a special feature installed in the board that ran a cleanup command against the Database if you pressed three buttons in quick succession. Suppose that the cleanup command in question could be any arbitrary command. Therefore, the developers put the command into a configuration file to be read and executed by the software at runtime.
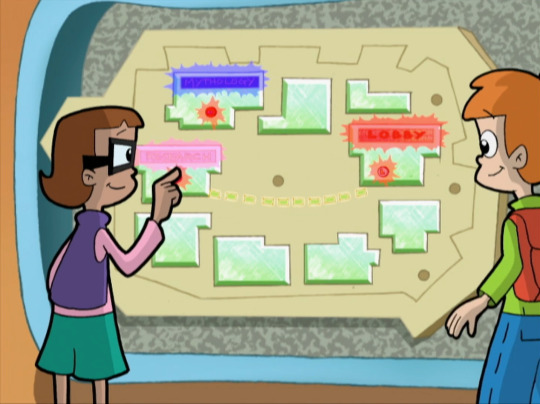
However, the developers knew that if some kids turned up and started poking the map, they could accidentally kick off the Database Cleanup command. They removed the Database Cleanup command from the configuration file. That way, if someone did poke three buttons in quick succession, the software would check the configuration file, see that there was no command defined, and then do nothing.
The trouble is that they left the part of the software that read the configuration file and ran the arbitrary command in place. So, if the command was somehow added back to that part of the configuration file, then there would be a command for the software to run. Then, if someone else pushed the three buttons, that command would be run. So, yeah, someone could put a command in there to write a bunch of junk into the Database until it filled up and crashed. Again, these are commands being sent to the Database from the Board. The Firewall would let them through just fine.
That's pretty bad, but that only lets them modify the Database, right? It's not like they can just tell the Database to open the Firewall on the server that it is sitting on, right?
Well, what if one of the things that the Database could do, upon request, was to open a command shell on the server and run a command. And what if, that command shell was able to run commands that impacted things on the server beyond the Database itself.
What if we called it "xp_cmdshell" and called the Database Server "Microsoft SQL Server 2000". Windows XP and Microsoft SQL Server 2000 would have been around at the time of "Lost My Marbles" after all. Those were also the key players in the real-world Heartland Payment Systems data breach of 2008, which inspired this post.
But hey, just because the Database could open a command shell on the Database Server doesn't mean that The Hacker could use it to bust the Database Server's external Firewall, right? He still needs a way to execute "xp_cmdshell". So, he needs an account with the correct permissions to tell the Database to execute "xp_cmdshell", and he needs the Database itself to have high-enough permissions to run a command via "xp_cmdshell" that can bust the Database Server's external firewall and open a path to Motherboard. Thankfully, the Database only run the "xp_cmdshell" for the top-level Database Administrator account.
This is where we get back to the Principle of Least Privilege. The Board should connect to the Database with a fairly low-power account. It only needs to read-from and write-to a few Database tables after all. Likewise, the Database itself should have been started on the Database Server by a fairly low-power account, as it only needs to handle reading and writing its own set of tables.
But then some moron decided to hook up the Board to the Database Server on the top-level Database Administrator Account. So, if the Board was configured to send an "xp_cmdshell" command, the Database would run it. Oh, and another moron decided to have the Database Server start the Database with the "root" account for that server. So, if the Board was configured to send in an "xp_cmdshell" command to nuke the external Firewall, then the Database would be able to nuke the external Firewall.

There is a principle called Defense-in-Depth, where you build multiple layers of defense around your critical item. That way, if a layer fails, you may be okay. We're running out of layers.
We only have one or two layers left. We know that the Board doesn't run "xp_cmdshell" for its regular operations today. Sure it has an undocumented debug mode that allows someone to execute any command in its configuration file (including "xp_cmdshell") against the Database. But someone would need to get to that file.
The board's main account doesn't give you a filesystem to play with, as they wouldn't want kids running up, poking things, and deleting the filesystem. No, you only get the interfaces that you get. You can pick two items and see a path between them. Or you can pick three items and see the undocumented debug mode run whatever command is in the configuration file.
But what if there was some sort of maintenance account accessible through the Internet that didn't enable someone to send commands to the Database, but would enable someone to get into the filesystem and mess around with it? And what if that maintenance account was still using a weak or default password because people just don't check that for IoT devices?

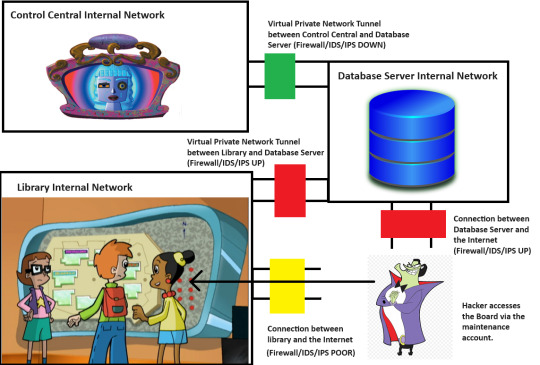
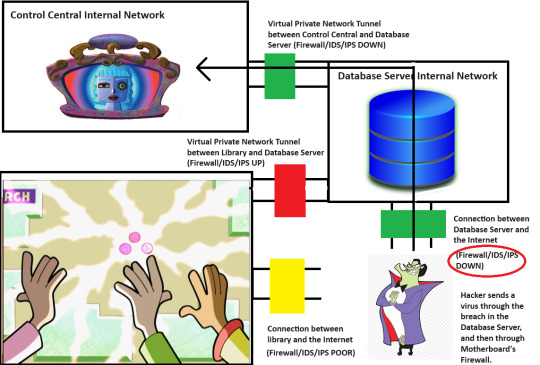
So, he's in the Board's filesystem now. That's concerning. And wouldn't you know it, yet another moron left that critical configuration file in a state where the maintenance account can make changes to it. So, of course, he found the empty configuration item for the cleanup command. Remember, this was setup to run any arbitrary command. Of course, he put in an "xp_cmdshell" command that tells the Database to nuke the external firewall on its own server.
While The Hacker was able to put the command in place, the maintenance account doesn't have the power to send commands to the Database on its own. That power is only enabled for the system account tied to the Board's user interface. So, he still has to rely on someone in the real world to push three buttons in quick succession.


Well...shit.
That's not good.

That's not good at all.


Seriously though, don't try this at home.
I suppose we can speculate on the nature of the virus. We know from Season 1 Episode 14 "Cool It" that Motherboard goes through more cryoxide than normal due to the virus. There are actual computer viruses out there that were designed to turn off heat safety warnings on CPUs and then cause them to run hotter. Some CPUs would eventually melt and ruin the computer.
The original infection destroyed the Encryptor Chip, and it is stated that only a replacement Encryptor Chip could cure the virus. The name suggests that it deals with data encryption, but perhaps it is also a virus cleanup tool. Perhaps it worked to weaken the existing virus until it was eventually overwhelmed and destroyed. Perhaps the virus exhausted most of its strength destroying the Encryptor Chip first.
In any case, curing the virus permanently would end the show.
#cyberchase#2000s#cartoon#nostalgia#pbs kids#2000s childhood#not for use in real life#you'll get busted
11 notes
·
View notes
Photo
I work in tech. I go to the store to print things. The only extras I’ll shell out money for are antivirus, vpn and cloud storage.
Imagine putting cameras on your property that aren’t closed circuit? Imagine putting your household appliances online via an app? WHY is your FRIDGE on the WIFI??? Imagine an always-on spy device in your home, that interacts with your toddler? Apple Air Tags? You mean stalker-tech? Nope nope nope. Even location services can stay off til you call an Uber or order a pizza. Let’s not even talk about the stranglehold this IOT tech is creating around accessibility for the disabled.
I have solar panels and water tanks, that’s how much I trust companies or govts to keep my household running. I have manual overrides. I calculate reserves of everything from power to back up power to water myself. I’m bad at math but I’m not trusting a SENSOR to tell me that shit.
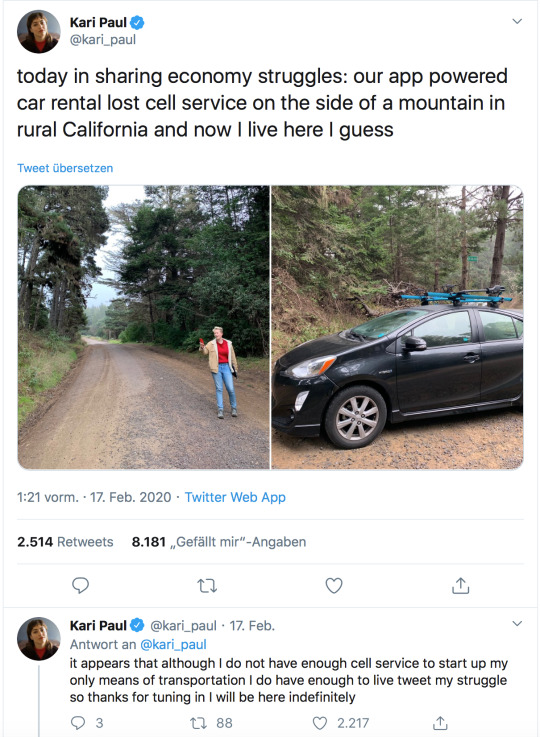
Welcome to the future, where you don’t own anything and the stuff you rent stops working once your phone has no signal.
#do I have an alarm system?#yes but also stand alone sirens of the type used on farms#best security feature?#it’s called a dog#and it’s statistically proven to work#fuck the internet of things#iot
172K notes
·
View notes
Text
Enhancing Security with 4G Security Cameras and 5G Industrial Routers in the UK
Security technology has come a long way in recent years, and the UK market has seen significant growth in the adoption of 4G security cameras and 5G industrial routers. These two devices are now widely recognized for their reliable and powerful features, ideal for both home and business use. In this blog, we’ll explore how 4G security cameras and 5G industrial routers can enhance security systems, their benefits, and why they're perfect for users across the UK. Additionally, we’ll introduce an excellent online shop for purchasing these products: 3G Mobile CCTV.
What is a 4G Security Camera?

A 4G security camera operates using 4G mobile networks instead of traditional Wi-Fi or wired connections. This unique capability allows the camera to function independently of Wi-Fi, making it perfect for remote locations where a stable internet connection is unavailable. These cameras can be placed almost anywhere as long as there’s 4G coverage, providing flexibility and peace of mind for users who want to secure areas that may not have access to typical internet sources.
Key Benefits of 4G Security Cameras:
Wireless Freedom: A 4G security camera is completely wireless, which reduces the hassle of cabling. You don’t need to worry about running wires across your property, making it ideal for farms, construction sites, and other large or remote areas.
Real-Time Monitoring: You can access live footage through your mobile device anytime and anywhere. Many 4G cameras come with dedicated apps, allowing for convenient control and monitoring of your premises on the go.
High-Quality Video: 4G security cameras are known for high-definition quality, which means that recorded footage is clear and detailed. Many cameras even offer night vision for excellent visibility even in low-light conditions.
Motion Detection and Alerts: Most modern 4G cameras come with motion sensors. You’ll receive alerts on your mobile phone whenever the camera detects any movement, ensuring that you’re always aware of what’s happening.
Weatherproof Design: Since many 4G cameras are built for outdoor use, they’re typically weatherproof, withstanding rain, dust, and even extreme temperatures. This feature ensures durability and continuous performance regardless of environmental conditions.
Simple Installation: Installing a 4G security camera is straightforward and does not require technical expertise. You only need a stable 4G SIM card, and you’re good to go.
Understanding the Role of a 5G Industrial Router

As industries become more connected and technology-driven, having a fast and secure internet connection is crucial. This is where the 5G industrial router comes into play. Unlike conventional routers, a 5G industrial router is built to offer stable, high-speed internet connectivity in challenging environments. In the UK, the adoption of these routers is steadily increasing as industries demand faster speeds, higher bandwidth, and more reliable connections.
Key Advantages of 5G Industrial Routers:
Blazing Fast Speeds: 5G routers provide significantly faster data speeds than 4G, making them suitable for bandwidth-intensive applications such as video streaming, real-time data processing, and advanced automation.
Reliable Connectivity: These routers are designed to function seamlessly even in harsh conditions, making them a top choice for industrial sites, factories, and rural areas where connectivity is often a challenge.
Multi-Device Support: A 5G router can support numerous devices simultaneously without losing performance, enabling businesses to connect various IoT devices, cameras, and computers all at once.
Enhanced Security Features: 5G industrial routers come with advanced security features to protect networks from cyber threats. This is vital for industries that deal with sensitive data, as they can benefit from built-in firewalls, VPN support, and encrypted connections.
Remote Management: Many 5G routers support remote management, enabling businesses to monitor and troubleshoot network issues without needing to be physically present at the site. This feature is especially useful for companies with multiple sites across different locations.
Future-Ready: Investing in a 5G industrial router ensures your business is ready for future advancements. As 5G technology continues to evolve, these routers will be compatible with new upgrades, ensuring a long-lasting and adaptable solution.
Why Choose 4G Security Cameras and 5G Industrial Routers Together?
Combining a 4G security camera with a 5G industrial router creates a powerful security setup. By using a 5G router, businesses can ensure a stable, high-speed connection for their 4G security cameras, even in challenging conditions or remote areas. This combo allows users to monitor their property seamlessly and enjoy the benefits of both reliable internet and advanced camera capabilities. Here are some additional reasons why this combination is highly beneficial:
Extended Coverage: A 5G router can enhance the camera’s functionality by providing stable internet in places where regular Wi-Fi is unavailable or unreliable.
Improved Video Quality: A high-speed 5G connection enables smoother, high-definition video streams from the 4G camera, making remote monitoring clearer and more efficient.
Increased Security: Both devices come with security features that protect data, ensuring that video feeds are encrypted and safe from unauthorized access.
Use Cases for 4G Security Cameras and 5G Industrial Routers in the UK
These devices are suited for various applications across the UK, catering to different types of users:
Construction Sites: Many construction sites lack reliable Wi-Fi, making 4G security cameras the perfect solution for monitoring these areas. Pairing them with a 5G industrial router enables high-speed connectivity, ensuring uninterrupted surveillance.
Farms and Rural Areas: Agricultural sites in rural areas often face internet connectivity issues. A 5G industrial router, when combined with 4G cameras, provides an effective solution to monitor livestock, crops, and equipment without the need for constant on-site visits.
Warehouses and Factories: Industrial sites can have multiple surveillance points. 4G cameras help cover all essential areas, while a 5G router provides a reliable connection for high-definition monitoring.
Remote Homes and Cottages: For homeowners with remote properties, a 4G security camera with a 5G router is an excellent way to keep an eye on their property, even when they’re far away.
Choosing the Right Products for Your Needs
When selecting a 4G security camera or a 5G industrial router, it’s essential to consider the specific features you need. If you're looking for cameras, consider the type of lens, motion detection, night vision, and app compatibility. For 5G routers, look for models with security features, high device capacity, and remote management options.
Conclusion
4G security cameras and 5G industrial routers are transforming how we secure and connect our properties, especially in remote or challenging areas. These devices are versatile, high-quality, and offer significant benefits for both home and industrial users in the UK. By choosing this combination, you can enjoy stable, high-speed internet while ensuring effective monitoring for your property.
For those looking to purchase top-notch 4G security cameras and 5G routers, 3G Mobile CCTV is an excellent online shop that offers a range of reliable, high-quality security solutions. With their expertise and selection, you can find the ideal products to meet your security and connectivity needs. Invest in technology that ensures safety, reliability, and peace of mind.
#4g security camera#farm cctv camera#3g mobile cctv#solar powered 4g router#4g security camera uk#5G industrial router#4g livestock camera
0 notes
Text
The Importance of Networking & Security Solutions in Abu Dhabi
In today’s rapidly evolving digital landscape, businesses in Abu Dhabi are increasingly reliant on robust networking and security solutions to ensure smooth operations and protect valuable assets. Whether it's a small enterprise or a large corporation, maintaining secure and efficient networks has become vital for business success. Let’s explore why networking and security solutions are essential for businesses in Abu Dhabi and how they can help protect and enhance operations.
Why Networking Solutions Matter
Effective networking solutions provide the foundation for all communication within an organization. Whether you're sharing data, accessing cloud services, or collaborating remotely, a strong network infrastructure ensures fast, reliable, and secure connections. For businesses in Abu Dhabi, where the economy is becoming increasingly global and interconnected, having a well-established network can greatly improve operational efficiency and productivity.
Key Networking Solutions:
Structured Cabling – Ensures a scalable, organized, and reliable network infrastructure.
Wireless Networks – Offer mobility and flexibility for employees and devices.
VPN Solutions – Provide secure remote access for employees working off-site.
Cloud-Based Networking – Enhances scalability and reduces costs while maintaining flexibility.
By leveraging these solutions, businesses in Abu Dhabi can ensure seamless communication, better data management, and enhanced customer experiences.
Security Solutions: Protecting Your Business
As businesses become more connected, the risks of cyber threats, data breaches, and network vulnerabilities increase. Implementing strong security solutions is crucial to safeguarding sensitive information, preventing unauthorized access, and ensuring compliance with regulatory standards.
Essential Security Solutions:
Firewalls and Intrusion Detection Systems – Protect networks from external threats and malicious attacks.
Endpoint Security – Secures all devices connected to the network, including computers, mobile devices, and IoT systems.
Data Encryption – Ensures that all sensitive information is securely transmitted and stored.
24/7 Monitoring & Incident Response – Provides real-time monitoring and swift action in case of security incidents.
With these security measures in place, Abu Dhabi businesses can mitigate risks, maintain customer trust, and ensure that their operations run smoothly without disruption.
Networking & Security in the Cloud Era
With the increasing adoption of cloud computing, businesses are facing new challenges and opportunities in networking and security. Cloud solutions offer scalability, flexibility, and cost-efficiency, but they also introduce new security concerns such as data privacy, compliance, and access control. Having a comprehensive cloud-based networking and security strategy is essential for navigating this transition.
In Abu Dhabi, more businesses are moving to cloud platforms, making it imperative to choose the right security solutions to protect cloud assets and ensure the safe transfer of data between networks. Some strategies include multi-factor authentication, secure cloud gateways, and regular cloud security audits.
Why Choose Professional Networking & Security Providers in Abu Dhabi
Selecting a trusted provider of networking and security solutions in Abu Dhabi ensures that your business gets the most effective and reliable infrastructure. Professional services can assess your current setup, identify vulnerabilities, and implement customized solutions that fit your business needs. Additionally, managed services provide ongoing support, monitoring, and updates to keep your network secure and efficient over time.
Conclusion
In today’s digital world, the importance of strong networking and security solutions cannot be overstated. For businesses in Abu Dhabi, having a robust IT infrastructure and implementing top-tier security measures is critical to staying competitive and protecting valuable data. By investing in the right solutions, companies can ensure operational efficiency, scalability, and protection from evolving cyber threats.
Secure your business today with expert networking and security solutions in Abu Dhabi and take control of your digital future.
0 notes
Text
Sify’s Telecom Service Providers in India: Enabling Seamless Connectivity for the Digital Age

In an increasingly connected world, robust and reliable telecommunications infrastructure is critical for driving business growth, enabling digital transformation, and empowering people with access to vital information. Sify Technologies, a leader in India’s IT and digital services sector, stands at the forefront of this connectivity revolution as one of the country’s top telecom service providers. With a comprehensive portfolio of services designed to meet the needs of enterprises, government organizations, and service providers, Sify is helping shape the future of telecommunications in India.
Why Sify’s Telecom Services Matter
The modern business landscape demands seamless communication, real-time collaboration, and uninterrupted access to digital resources. Whether it's connecting offices across cities, managing large-scale enterprise networks, or supporting IoT-enabled smart cities, telecom services are the backbone of today's digital operations.
Sify’s telecom offerings are built to deliver high-speed, secure, and scalable communication solutions that empower businesses and individuals to stay connected, collaborate efficiently, and innovate with confidence. As an integrated telecom service provider, Sify offers end-to-end services, from network infrastructure to managed services, ensuring businesses have everything they need to succeed in the digital age.
Key Features of Sify’s Telecom Services
Sify’s telecom services are designed to address the diverse communication needs of businesses, from SMEs to large enterprises, across multiple sectors. Here’s what makes Sify’s telecom solutions stand out:
1. Pan-India Network Coverage
Sify has built one of India’s most extensive fiber-optic networks, spanning over 11,000 kilometers and reaching more than 1,600 towns and cities. This widespread coverage ensures that businesses of all sizes, from metropolitan centers to remote regions, have access to high-speed, reliable telecommunications infrastructure.
2. Enterprise-Grade Connectivity
With an emphasis on delivering enterprise-grade connectivity, Sify’s telecom solutions include Internet Leased Lines (ILL), MPLS (Multiprotocol Label Switching), and Virtual Private Networks (VPNs). These services enable businesses to securely connect branch offices, data centers, and cloud environments, ensuring seamless communication and efficient data transfer across geographies.
3. Scalable Bandwidth Solutions
As businesses grow and their data needs expand, Sify offers flexible, scalable bandwidth options. Sify’s Data Connectivity Solutions provide businesses with the ability to increase or decrease bandwidth based on operational requirements, ensuring maximum efficiency without incurring unnecessary costs.
4. Robust Network Security
In today’s digital age, protecting sensitive data and ensuring the integrity of communications is paramount. Sify integrates advanced network security features into its telecom services, including firewalls, DDoS protection, and encryption. These safeguards protect businesses from cyber threats, ensuring secure data transmission and mitigating the risk of breaches.
5. Managed Telecom Services
Sify’s Managed Telecom Services offer businesses the advantage of having a fully managed communication infrastructure. From network design and implementation to ongoing maintenance and monitoring, Sify provides end-to-end management that allows businesses to focus on their core operations while leaving the technical details to the experts.
6. Dedicated Support and Service Quality
Sify is committed to delivering excellent customer service, backed by industry-leading Service Level Agreements (SLAs). A dedicated 24/7 Network Operations Center (NOC) monitors and manages the telecom infrastructure, ensuring high availability and rapid resolution of any issues that may arise. This proactive approach ensures minimal downtime and maximized performance for Sify’s telecom customers.
7. Custom Solutions for Industry-Specific Needs
Different industries have unique telecommunications requirements, whether it's high-speed connectivity for IT and technology firms, secure communication channels for financial institutions, or seamless data exchange for healthcare organizations. Sify tailors its telecom solutions to meet the specific demands of each sector, providing optimized services that enhance productivity and performance.
How Sify’s Telecom Services Empower Indian Enterprises
Supporting Digital Transformation
As Indian businesses undergo digital transformation, the need for robust, secure, and scalable connectivity has never been more critical. Sify’s telecom services provide the essential infrastructure needed to enable this transformation, offering businesses the ability to integrate advanced technologies such as cloud computing, IoT, and AI into their operations.
Enabling Seamless Collaboration
With the rise of remote work, hybrid office models, and global operations, seamless collaboration is essential. Sify’s telecom services enable real-time communication, whether through voice, video, or data, allowing teams to stay connected and collaborate efficiently from anywhere in the world.
Powering Smart Cities and IoT Applications
India’s push toward smart cities and the deployment of IoT applications relies on a robust telecommunications network. Sify’s telecom infrastructure supports these initiatives by offering high-speed, low-latency connectivity that powers everything from smart grids to connected transportation systems. This plays a crucial role in building the smart cities of the future.
Driving Business Growth and Innovation
By providing businesses with reliable and scalable telecom services, Sify helps enterprises focus on growth and innovation. Whether it’s enabling e-commerce platforms, optimizing supply chain operations, or enhancing customer engagement through digital platforms, Sify’s telecom solutions serve as the foundation for business success.
Why Choose Sify as Your Telecom Service Provider?
Proven Expertise and Experience
Sify brings decades of experience in providing cutting-edge telecom solutions to businesses across India. Its deep industry knowledge, combined with its technological expertise, makes it a trusted partner for businesses seeking reliable telecom services.
End-to-End Solutions
From network design and deployment to managed services, Sify offers an end-to-end telecom solution that simplifies communication for businesses. This holistic approach ensures that businesses receive comprehensive support for all their connectivity needs.
Future-Ready Infrastructure
With continuous investment in upgrading its network infrastructure, Sify ensures that its telecom services remain future-ready, capable of supporting the latest technologies and accommodating growing business demands.
Commitment to Innovation
Sify is committed to driving innovation in the telecom space. By embracing the latest trends and technologies, including 5G and next-generation network solutions, Sify ensures its customers stay ahead in an increasingly competitive market.
In a fast-evolving digital ecosystem, Sify’s Telecom Services are at the heart of enabling businesses and organizations to thrive. With a vast network, enterprise-grade connectivity, advanced security features, and dedicated managed services, Sify empowers Indian businesses with the tools they need to stay connected, competitive, and future-ready.
For businesses looking to transform their operations through reliable and scalable telecom services, Sify Technologies is the partner of choice. Stay connected, secure, and productive with Sify—India’s trusted telecom service provider.
0 notes
Text
Leveraging Technology for Enhanced Experience in Co-Working Office Spaces in Ernakulam
Introduction
The demand for co-working spaces in Ernakulam has seen exponential growth as more startups, freelancers, and remote workers embrace the flexibility and community such environments offer. However, the evolving landscape of co-working is no longer just about providing a desk and a chair. Today, technology plays a pivotal role in shaping the overall experience of these spaces, making them more efficient, productive, and user-friendly.
Here’s how technology is transforming co-working spaces in Ernakulam:
1. Smart Workspaces
With the integration of smart technologies, co-working spaces have become more than just shared offices. IoT (Internet of Things) devices, such as smart lighting, temperature controls, and motion-activated systems, create a more comfortable and energy-efficient work environment. For instance, intelligent lighting systems can adjust based on the number of people in a room, while HVAC systems can maintain optimal comfort based on real-time feedback.
2. High-Speed Internet and Network Security
In a digital-first world, reliable high-speed internet is non-negotiable. Most co-working spaces in Ernakulam are now equipped with robust internet infrastructure to ensure seamless connectivity. Additionally, advanced cybersecurity protocols, such as encrypted Wi-Fi networks and VPN services, are in place to safeguard sensitive data, which is particularly important for businesses handling client information.
3. Virtual Meeting Solutions
Virtual meeting rooms, powered by video conferencing platforms like Zoom, Microsoft Teams, and Google Meet, have become essential tools in modern co-working spaces. These setups allow teams to collaborate globally without leaving Ernakulam. Equipped with high-definition cameras, noise-canceling audio systems, and fast internet, these rooms are designed to facilitate uninterrupted communication and collaboration.
4. Automated Booking and Workspace Management
Gone are the days of manually booking meeting rooms or office spaces. Many co-working offices in Ernakulam now offer app-based solutions for members to book conference rooms, desks, or even parking spots with a few taps. These systems also provide real-time availability updates, allowing users to schedule their meetings or workspace bookings effortlessly.
5. Cloud Storage and Collaboration Tools
Co-working spaces are increasingly integrating cloud storage solutions such as Google Drive, Dropbox, and Microsoft OneDrive, allowing professionals to access, share, and collaborate on documents from anywhere. With these tools, teams working from different locations in Ernakulam can collaborate in real-time, improving productivity and ensuring that projects are completed on time.
6. AI-Powered Customer Support and Networking Tools
Artificial intelligence is making its way into the co-working ecosystem, primarily through AI-powered chatbots for customer support. These bots provide quick answers to frequently asked questions, help with troubleshooting, and provide users with information about upcoming events or workshops in the space. Networking platforms exclusive to co-working members also allow professionals to connect, share ideas, and collaborate on projects.
7. Remote Access Control and Security Systems
Safety and security remain a top priority in co-working spaces. Biometric access control systems and smart surveillance cameras provide an additional layer of security. Authorized users can access specific rooms or areas using their fingerprints or smartphone apps, ensuring that sensitive areas remain protected while maintaining ease of access for members.
8. Tech-Enhanced Community Building
The essence of co-working is community. Many co-working spaces in Ernakulam are utilizing technology to enhance the sense of community among members. Platforms dedicated to co-working communities enable members to share ideas, post job opportunities, and collaborate on projects. Additionally, spaces are organizing virtual events, webinars, and workshops to engage members beyond just physical proximity.
Conclusion
The role of technology in co-working spaces is undeniable, especially as professionals seek more efficiency, flexibility, and connectivity in their work environments. In Ernakulam, the integration of advanced tech solutions is reshaping how co-working spaces operate, ensuring that businesses and individuals alike can thrive in a modern, collaborative environment.
For those looking to join a co-working space, it’s crucial to choose one that embraces technology and innovation to foster an enhanced working experience. With the right tech infrastructure in place, these spaces will continue to attract professionals from diverse industries, creating a thriving ecosystem of collaboration and growth.
0 notes
Text
Introduction to help you Remote Access IoT: What It will be and even How come The application Matters
In today's rapidly evolving technological landscape, the Internet of Things (IoT) has emerged as a game-changer, integrating everyday objects with digital networks to make them smarter and more connected. One of the very compelling facets of IoT is Remote Access, a concept that's revolutionized how exactly we connect to devices and systems. But what exactly is Remote Access IoT, and how come it so crucial in the modern world?

What Is Remote Access IoT?
Remote Access IoT describes the ability to control, monitor, and connect to Internet-connected devices from a distance remote monitor iot. This functionality is achieved through a combination of IoT technology and remote access protocols, allowing users to control devices in real-time from virtually anywhere on earth utilizing a smartphone, tablet, or computer.
At its core, Remote Access IoT leverages the ability of cloud computing and connectivity. Devices equipped with sensors, actuators, and communication modules send data to a cloud-based platform. Users will then access this data and control the devices remotely through a net connection.
Key The different parts of Remote Access IoT
Connected Devices: They're the physical objects embedded with sensors and communication modules that collect and transmit data. Examples include smart thermostats, security cameras, and industrial machinery.
Cloud Platforms: These platforms store and process the information collected from IoT devices. In addition they provide the interface by which users connect to their devices.
Remote Access Protocols: These protocols enable secure communication between an individual and the IoT devices. They include technologies like Virtual Private Networks (VPNs), secure web protocols (HTTPS), and specialized IoT communication standards.
User Interfaces: Typically in the form of apps or web dashboards, these interfaces allow users to see data, receive notifications, and control devices remotely.
Why Remote Access IoT Matters
Convenience and Efficiency: Remote Access IoT simplifies the management of devices. As an example, homeowners can adjust their thermostats or turn off lights from their smartphones, while businesses can monitor and control industrial equipment from a main location. This convenience results in increased efficiency and streamlined operations.
Enhanced Security: IoT devices often include advanced security features such as real-time alerts and remote lock controls. As an example, a protection camera system with Remote Access allows users to monitor live footage and receive notifications of unusual activity, enhancing overall security.
Cost Savings: Remote Access IoT can subscribe to significant cost savings. By optimizing the operation of devices, such as adjusting heating or cooling systems predicated on real-time data, users can reduce energy consumption and operational costs. Businesses may also perform remote diagnostics and maintenance, minimizing downtime and repair expenses.
Improved Data Insights: The capability to remotely access and analyze data provides valuable insights into device performance and user behavior. This information may be used to make informed decisions, improve processes, and predict maintenance needs.
Accessibility: For people who have disabilities or those managing multiple properties, Remote Access IoT offers greater accessibility and control. This technology ensures that users can maintain control over their environment irrespective of physical location or mobility.
The Future of Remote Access IoT
As technology continues to advance, the scope and capabilities of Remote Access IoT are likely to expand. Innovations in AI, machine learning, and edge computing will further improve the functionality and intelligence of connected devices. Additionally, as cybersecurity measures evolve, users can get sustained protection for their remote interactions.
In summary, Remote Access IoT is transforming how exactly we connect to technology, offering unparalleled convenience, efficiency, and security. Its impact spans various sectors, from smart homes to industrial automation, underscoring its importance in the modern digital ecosystem. As IoT technology continues to progress, Remote Access will play a pivotal role in shaping the future of connectivity and control.
0 notes
Text
Top Cisco Network Engineers & Architects: Shaping the Future of Connectivity
Cisco network engineers and architects play a pivotal role in building the backbone of modern IT infrastructure. They are responsible for designing, deploying, and managing advanced network solutions that support secure, scalable, and reliable communication across global enterprises. Here, we highlight the expertise and value these professionals bring to the table.
Why Cisco Network Engineers & Architects Are Vital
Certified Expertise: Cisco-certified engineers, such as CCNA, CCNP, and CCIE holders, possess deep knowledge of Cisco technologies, network protocols, and cybersecurity. Their certifications validate their skills in configuring and troubleshooting complex network systems.
Network Design & Architecture: Cisco network architects excel in creating robust network designs that align with business objectives, whether for large-scale enterprises or cloud-based environments. They ensure networks are optimized for performance, security, and future growth.
End-to-End Solutions: From data centers and cloud infrastructure to WAN/LAN, VoIP, and VPNs, Cisco professionals manage all facets of network connectivity to ensure seamless, efficient operations.
Cybersecurity Expertise: In today’s world of escalating cyber threats, Cisco engineers implement advanced security protocols, firewalls, and intrusion prevention systems (IPS) to safeguard sensitive data and prevent breaches.
The Skillset of Elite Cisco Network Engineers
Problem-Solving: With the ability to troubleshoot complex issues across multiple layers of the OSI model, Cisco engineers minimize downtime and optimize network performance.
Innovative Thinking: Cisco architects develop scalable network frameworks using the latest Cisco technologies, from software-defined networking (SDN) to next-gen firewalls and routing protocols.
Cross-Platform Integration: Cisco engineers ensure that your network seamlessly integrates with third-party platforms and cloud services, facilitating smooth digital transformation.
Automation & Efficiency: The best Cisco network engineers stay ahead of trends, leveraging automation tools like Cisco DNA Center and DevNet to streamline network management and reduce operational costs.
Industries Relying on Cisco Experts
From finance and healthcare to telecommunications and government, Cisco network engineers and architects serve diverse sectors. They are instrumental in creating secure, high-performance environments that meet industry-specific compliance and operational requirements.
Finding the Best Cisco Network Engineers
When hiring a Cisco network engineer or architect, consider professionals who possess:
Relevant Certifications: Look for CCNA, CCNP, and CCIE certifications, which demonstrate the highest levels of Cisco expertise.
Proven Experience: A track record of successful projects in designing, implementing, and managing Cisco networks.
Adaptability: Engineers who stay current with the latest Cisco technologies, such as SD-WAN, IoT, and cloud-based networking solutions.
Communication Skills: The ability to translate technical requirements into business solutions is a key trait of top engineers and architects.
Ready to Transform Your Network?
Partnering with elite Cisco network engineers and architects is essential for any organization looking to enhance its IT infrastructure. Whether you’re building a new network or upgrading an existing one, their knowledge and expertise will ensure a secure, scalable, and future-ready system.

0 notes
Text
1 note
·
View note
Text
BLIIoT Industrial 4G Modbus to MQTT Edge WiFi Router R10A Applied to River Liquid Level and Flow Monitoring
The R10A can provide wireless access network, and also can performs Modbus Master to poll meters over RS485/232 or LAN ports, then upload the data to cloud platforms under MQTT format, e.g.: AWS IoT, Thingsboard, Aliyun, etc. Also, can customerize applications, use the RS485 or LAN port to connect the I/O modules, to monitoring data or switch on/off devices, etc.



#iot#iotsolutions#iotdevices#gateway#router#modbus#mqtt#4g#ethernet#wifi#edgecomputing#vpn#logiccontrol#remotemonitoring#BLIIoT#BLIIoT Applications
1 note
·
View note
Text
Next - Gen cyber security

Introduction
Welcome and Orientation
Overview of the Next-Gen Cyber Security Skills course in Bangalore
Introduction to instructors and fellow participants
Setting goals and expectations for the course
Module 1: Foundations of Cyber Security
Understanding Cyber Security
Definition and importance of cyber security in today’s world
Current landscape and emerging threats
Cyber Security Terminology
Key terms and concepts crucial for the Bangalore cyber security course
Overview of common attack vectors and defenses
Cyber Security Frameworks and Standards
NIST Cybersecurity Framework
ISO/IEC 27001
CIS Controls and their relevance to Bangalore’s cyber security environment
Module 2: Network Security
Network Security Fundamentals
Basic networking concepts vital for Bangalore cyber security professionals
Understanding firewalls, VPNs, and IDS/IPS
Securing Network Infrastructure
Techniques for network segmentation and isolation
Secure network design and architecture
Wireless Network Security
Wireless security protocols (WPA3, WPA2)
Securing wireless access points in a Bangalore context
Module 3: Application Security
Introduction to Application Security
Common vulnerabilities (OWASP Top Ten)
Secure coding practices essential for Bangalore developers
Web Application Security
Addressing Cross-Site Scripting (XSS) and SQL Injection
Integrating secure development lifecycle (SDLC) practices
Mobile Application Security
Addressing mobile-specific threats and vulnerabilities
Best practices for securing mobile apps in the Bangalore market
Module 4: Endpoint Security
Endpoint Protection
Anti-virus and anti-malware solutions
Endpoint Detection and Response (EDR) tools
Securing Operating Systems
Hardening Windows and Linux systems
Effective patch management and software updates
BYOD and IoT Security
Managing Bring Your Own Device (BYOD) policies in Bangalore
Securing Internet of Things (IoT) devices
Module 5: Identity and Access Management (IAM)
Fundamentals of IAM
Authentication vs. Authorization
Identity lifecycle management and its application in Bangalore businesses
Access Control Mechanisms
Role-Based Access Control (RBAC)
Implementing Multi-Factor Authentication (MFA)
Identity Management Solutions
Single Sign-On (SSO) and Federation
Identity as a Service (IDaaS) platforms and their relevance
Module 6: Cloud Security
Cloud Security Basics
Understanding cloud service models (IaaS, PaaS, SaaS)
Shared responsibility model for cloud security
Securing Cloud Environments
Best practices for AWS, Azure, and Google Cloud in Bangalore
Cloud security posture management
Cloud Compliance and Governance
Regulatory requirements and compliance standards applicable in Bangalore
Data protection and privacy in the cloud
Module 7: Threat Intelligence and Incident Response
Cyber Threat Intelligence
Gathering and analyzing threat data
Using threat intelligence platforms effectively
Incident Response Planning
Developing an incident response plan
Incident detection and analysis
Handling Security Incidents
Containment, eradication, and recovery strategies
Post-incident activities and lessons learned
Module 8: Security Operations and Monitoring
Security Operations Center (SOC)
Roles and responsibilities of SOC teams
Setting up and managing a SOC in Bangalore
Monitoring and Logging
Importance of logging and monitoring
Using SIEM (Security Information and Event Management) tools
Threat Hunting
Proactive threat hunting techniques
Leveraging advanced analytics and AI for threat detection
Module 9: Compliance and Legal Aspects
Understanding Cyber Security Regulations
Key regulations (GDPR, CCPA, HIPAA, etc.)
Compliance requirements for organizations in Bangalore
Legal Considerations in Cyber Security
Data breach laws and notification requirements
Intellectual property and cyber crime laws
Auditing and Assessment
Conducting security audits and assessments
Preparing for compliance audits
Module 10: Capstone Project and Certification
Capstone Project
Real-world scenario-based project
Applying learned skills to solve complex problems
Exam Preparation
Review of key concepts and practice exams
Tips and strategies for passing the certification exam
Certification and Next Steps
Receiving course completion certificate
Exploring advanced certifications and career paths
Conclusion and Course Wrap-Up
Final Q&A Session
Addressing any remaining questions
Sharing additional resources and tools
Networking and Alumni Community
Joining the course alumni network
Continued learning and professional development opportunities in Bangalore
This Next-Gen Cyber Security course in Bangalore will equip you with the knowledge and skills needed to excel in the evolving field of cyber security
0 notes
Text
The Future of IT Management: Innovations and Challenges
The Future of IT Management: Innovations and Challenges
As we look towards the future of IT management, it’s clear that rapid technological advancements are reshaping the landscape. One of the most prominent innovations is the integration of Artificial Intelligence (AI) and Machine Learning (ML) into IT management processes. These technologies are transforming how data is analyzed, how systems are monitored, and how issues are predicted and resolved. AI-powered tools can automate routine tasks, enhance decision-making, and provide deeper insights into system performance and user behavior. However, this shift towards automation also brings challenges, including the need for skilled professionals who can manage and interpret AI-driven insights and ensure that these technologies are implemented effectively and ethically.
Another significant trend is the increasing emphasis on cybersecurity. As cyber threats become more sophisticated, IT management must adapt to safeguard sensitive data and maintain operational integrity. Innovations in cybersecurity include advanced threat detection systems, zero-trust architectures, and blockchain-based security solutions. These technologies aim to provide more robust protection against breaches and attacks. Nevertheless, the challenge lies in balancing security with user convenience and system performance. IT managers must navigate the complexities of implementing these solutions while ensuring minimal disruption to business operations and maintaining user trust.
The rise of remote work and distributed teams has also influenced the future of IT management. Organizations are investing in technologies that support remote collaboration, secure access to resources, and effective communication across various platforms. Cloud computing, virtual private networks (VPNs), and collaboration tools are at the forefront of this transformation. However, managing a distributed IT environment presents its own set of challenges, including ensuring consistent security policies, maintaining system performance across different locations, and providing adequate support to remote users. IT managers must adapt to these evolving needs and develop strategies that address the unique requirements of a geographically dispersed workforce.
Innovations in IT Management
The landscape of IT management is undergoing a significant transformation due to the continuous advancements in technology. Cloud computing has revolutionized how businesses manage their IT infrastructure by offering scalable and flexible solutions that can be tailored to specific needs. Innovations such as serverless computing and hybrid cloud environments are allowing organizations to optimize their IT resources, reduce costs, and improve scalability. These advancements enable IT managers to focus more on strategic initiatives rather than dealing with the complexities of traditional on-premises infrastructure. Additionally, the integration of AI and ML into cloud platforms is enhancing capabilities such as predictive analytics and automated resource management, driving further innovation in IT management practices.
Another area of innovation is the development of advanced analytics and data management solutions. As organizations generate vast amounts of data, the ability to extract valuable insights from this information is becoming increasingly crucial. Technologies such as big data analytics, data lakes, and real-time data processing are empowering IT managers to make more informed decisions, optimize operations, and drive business growth. By leveraging these tools, organizations can gain a competitive edge, improve customer experiences, and identify new opportunities. However, managing and securing this data remains a challenge, requiring robust data governance frameworks and advanced security measures to protect against breaches and unauthorized access. IT Support Cardiff
The Internet of Things (IoT) is also playing a significant role in shaping the future of IT management. IoT devices are becoming ubiquitous in various industries, providing valuable data and enabling new applications and services. However, the proliferation of IoT devices introduces challenges related to data management, security, and interoperability. IT managers must address these challenges by implementing effective IoT strategies, ensuring that devices are securely integrated into the network, and managing the data they generate. Innovations in IoT technology, such as edge computing and advanced connectivity solutions, are helping to address these challenges and enhance the overall efficiency of IT management.
Challenges in IT Management
One of the primary challenges facing IT management is the need to keep pace with rapidly evolving technology while maintaining stability and security. The rapid pace of technological change means that IT managers must constantly evaluate and adopt new solutions, which can be both resource-intensive and risky. Balancing innovation with the need to maintain reliable and secure systems requires careful planning and a proactive approach to risk management. IT managers must also ensure that their teams have the necessary skills and knowledge to effectively implement and manage new technologies, which can involve significant training and development efforts.
Data security and privacy are also major challenges in the evolving IT landscape. As organizations collect and store increasing amounts of sensitive data, the risk of data breaches and cyberattacks grows. IT managers must implement robust security measures, including encryption, access controls, and regular security assessments, to protect against these threats. Additionally, compliance with data protection regulations, such as GDPR and CCPA, adds another layer of complexity. Ensuring that security measures are up-to-date and effective in the face of emerging threats is an ongoing challenge that requires constant vigilance and adaptation.
Managing a diverse and distributed IT environment is another significant challenge. The rise of remote work, cloud computing, and global operations has led to a more complex IT landscape, with systems and users spread across various locations and platforms. IT managers must ensure that all components of the IT infrastructure are seamlessly integrated and that users have access to the resources they need, regardless of their location. This involves addressing issues related to network performance, security, and user support, and requires effective management of both on-premises and cloud-based systems. Developing strategies to effectively manage this complexity is crucial for maintaining operational efficiency and ensuring a positive user experience.
0 notes
Text
Top Cybersecurity Best Practices to Protect Your Business in 2024

In today's digital world, keeping your business safe from cyber threats is crucial. Cyber threats are always changing, so it's key to stay ahead. This means using strong cybersecurity strategies to protect your data and keep your business running smoothly. Staying on top of cybersecurity means knowing the latest trends and technologies. It also means using proven best practices. By being proactive, you can shield your business from the harm of cyberattacks. Key Takeaways - Understand the importance of cybersecurity for business protection and continuity. - Explore emerging cybersecurity trends, including cloud security, zero-trust architecture, and AI-powered solutions. - Establish a robust cybersecurity policy to govern your organization's security practices and procedures. - Secure your network perimeter and IoT connections to mitigate the risk of cyber threats. - Adopt a people-centric security approach to empower your employees as the first line of defense. - Regularly backup data, update security measures, and collaborate with IT experts to enhance your cybersecurity posture. - Implement best practices like strong passwords, multi-factor authentication, and access control to protect sensitive information.
Why Cybersecurity is Crucial for Businesses
In today's world, cybersecurity is key for all businesses. They use technology and keep sensitive data, making them targets for hackers. A cyberattack can hurt their reputation, cause big financial losses, and disrupt their work. Protect Sensitive Data Businesses deal with a lot of sensitive info, like secret ideas, customer details, and money records. Keeping this data safe is very important. If it gets out, it can damage the company's image and lose customer trust. Prevent Financial Losses Cyberattacks can hit businesses hard in the wallet. They face costs like fixing a data breach, legal bills, and fines. Plus, an attack can slow down work, causing lost sales and less productivity. Maintain Business Continuity Keeping a business running smoothly is why cybersecurity matters. If a company's systems get hacked, it can stop services, cause downtime, and make it hard to help customers. Good cybersecurity helps stop and fix these problems fast, keeping work flowing. By using strong cybersecurity steps, businesses can keep data safe, avoid financial losses, and keep working well. This builds trust with customers, follows the law, cuts insurance costs, and makes them stronger against cyber threats. "Cybersecurity is no longer an option, but a necessity for businesses in the digital age." - Cybersecurity Expert
Emerging Cybersecurity Trends for 2024
The digital world is always changing, and cybersecurity experts must keep up to protect businesses. In 2024, new trends will shape the cybersecurity world. These trends highlight the need for proactive and flexible security plans. Developing Cloud Security More companies are moving to the cloud, making cloud security crucial. It's important to use strong identity checks, data encryption, and ongoing monitoring to keep cloud data safe. Using cloud security tools can help prevent data theft and meet legal standards. Using Zero Trust in Combination with VPN The old way of thinking about security doesn't work well in today's work-from-anywhere world. Experts suggest combining zero trust with VPN technology. This mix makes security better by checking who you are and what device you're using before you get in. It's a smarter way to keep data safe than traditional VPNs. Embracing AI Development Using artificial intelligence (AI) and machine learning (ML) in cybersecurity is big in 2024. AI systems can look at lots of data, spot odd patterns, and warn about threats fast. This helps companies find and deal with threats better. As AI gets better, it will help automate security tasks and make companies stronger against cyber threats. "Artificial intelligence is revolutionizing cybersecurity in 2024, with AI-powered systems autonomously identifying anomalous behavior patterns and predicting potential security breaches."
Establish a Robust Cybersecurity Policy
As businesses face new cybersecurity challenges, having a strong cybersecurity policy is key. This policy acts as a guide, listing the steps your company will take to boost cybersecurity. It helps your security team and employees work together better, making your defenses stronger. Using a hierarchical cybersecurity policy is a smart move. It has a main policy that sets the rules for your cybersecurity. Adding more policies for each department makes it work better and keeps things running smoothly. - Make a main cybersecurity policy for clear rules and best practices across your company. - Add policies for each department to meet their specific security needs. - Keep your cybersecurity policy up to date to match new threats and standards. - Give all employees detailed cybersecurity training so they know their roles. - Check how well the policy works with risk assessments, audits, and exercises to find and fix any issues. With a strong, layered cybersecurity policy, you can keep your data safe and your business running smoothly. It helps you stay ahead of cyber threats. "A well-designed cybersecurity policy serves as the foundation for a resilient and proactive security strategy."
Secure Your Perimeter and IoT Connections
In today's digital world, the old idea of an organization's border is outdated. With remote work, cloud services, and more IoT devices, cyber threats have grown. It's key to focus on securing your business's perimeter and IoT connections. Protect Border Routers and Screened Subnets Border routers and screened subnets are vital for your business's security. They help block unauthorized access and protect your data. It's important to keep these parts of your network safe with regular updates and strong controls. Implement Zero Trust Model The zero trust model is a new way to fight cyber threats. It checks users and devices all the time, not just at the border. This approach, with firewalls and VPNs, makes your security stronger and more flexible. Securing your perimeter and IoT devices is key to protecting your business. By protecting border routers, using screened subnets, and adopting the zero trust model, you boost your security. This helps keep your data and important systems safe.
Employ a People-Centric Security Approach
In the world of cybersecurity, just focusing on technology isn't enough. Hackers often target the human element. So, it's key to use a people-centric security approach. This means looking at how employees and users act and making sure they're safe. Most security issues come from human mistakes or tricks. This shows why a people-centric approach in cybersecurity is vital. By teaching employees about cybersecurity awareness and the human element in cybersecurity, companies can lower risks and get safer. Creating detailed training that talks about different cyber threats is a must. Using tools like TLMS in workshops makes sure employees pay attention and learn well. This helps them spot and deal with threats better. - Do regular security checks and send out reminders to lower risks in the company. - Build a work culture that makes security a part of everyday life, keeping everyone alert. - Use tools like TSAT to track vulnerabilities in real-time and improve how you manage risks. "By 2027, more than 50% of CISOs in large enterprises will have embraced a human-focused approach within their cybersecurity teams." - Gartner Adopting a people-centric security approach is crucial and necessary against new cyber threats. By focusing on employee cybersecurity awareness and the human element in cybersecurity, companies can create a strong defense against cyber attacks.
Install Backup Data and Security Updates
Keeping your business data safe is key to running smoothly. It's important to back up data and update software regularly. These steps help protect against data loss, corruption, and theft. Backing up data is a must for your company's safety. With more customer and user info, a strong backup plan is needed. Teach your team to back up data in secure places, either on-site or in the cloud. This helps lessen the damage from ransomware, hardware issues, or other data loss problems. Also, keeping your software and systems updated is crucial. Updates often fix bugs and add security features to protect against new threats. Tell your team to update software often to get the newest features and security fixes. "The average data breach cost is $4.35 million, or approximately $164 per data record." - IBM By focusing on data backup and software updates, you can improve your company's cybersecurity. These steps help protect your important data. They can prevent the big problems of data loss and cyber attacks, keeping your business safe and its reputation intact.
Cybersecurity Best Practices
With over 3.5 billion people online, protecting your business from cyber threats is key. Using strong passwords and multi-factor authentication can boost your security. These steps help keep your business safe. Use Strong Passwords and Multi-Factor Authentication Using strong passwords is a top way to protect your data. With billions of email accounts, making unique, complex passwords is a must. Adding multi-factor authentication gives you an extra security layer. This makes it harder for hackers to get into your systems. Control Access to Sensitive Information Keeping sensitive data safe is vital. Limit who can see financial records and trade secrets. Deactivate old accounts to keep your data secure. A strong access control system reduces the risk of unauthorized access. Following these cybersecurity tips keeps your data safe. It helps your business stay running smoothly. And it shields you from the harm of a cyber attack. "Cybersecurity is not just an IT issue, it's a business issue. Protecting your organization's data and assets should be a top priority for every organization, regardless of size or industry."
Collaborate with IT Department and Cybersecurity Experts
To keep your business safe from new cyber threats, it's key to work together with your IT team and cybersecurity pros. By teaming up with your IT staff and outside cybersecurity experts, you can make strong cybersecurity plans that fit your business. Working together can save your business money by lowering the chance of cyber attacks. Sharing threat info helps you fight off new and tricky cyber attacks early. But, building trust takes time and money, so be ready for that. Good cybersecurity teamwork means breaking down walls between different departments like IT, security, legal, and more. This way, everyone works together better. Sharing threat info, handling incidents together, and making joint decisions makes your business stronger against cyber threats. "Cybersecurity pros emphasized the importance of collaboration with a combination of communication, understanding, and shared goals." By partnering with your IT team and cybersecurity experts, you can keep your business ahead in the fast-changing world of cyber threats. This teamwork ensures you use the best cybersecurity steps and keeps your business running smoothly.
Conduct Regular Cybersecurity Audits
Regular cybersecurity audits are key to check your company's security level. They help spot weak spots and make sure you follow the rules. You should do these audits at least once a year. For companies dealing with sensitive info or lots of data, it's best to do them twice a year. These audits make your security tools and processes better. They help you fight off new cyber threats more effectively. Cybersecurity audits are more important now than ever. They help focus on the biggest risks in your company. Using a cloud-based data spot makes sharing and planning audits easier. Keeping an eye on your IT systems can catch risks early. It's important to have a clear plan for your audits. Set clear goals and make sure they're achievable. Reviewing your cybersecurity policies helps you understand your security better. Fixing issues found in audits can greatly lower the chance of data breaches. Read the full article
#BusinessContinuityPlanning#CloudSecurityBestPractices#CybersecurityStrategies#DataProtectionMeasures#EncryptionTechniques#IncidentResponseProtocols#NetworkSecuritySolutions#SecurityAwarenessTraining#ThreatDetectionTechnologies
0 notes