#NetworkSecuritySolutions
Explore tagged Tumblr posts
Text
The Most Severe Data Leakage Incident in History: 3 Billion People Affected, Cybersecurity Facing Unprecedented Challenges
Two major data leakage incidents that occurred recently have once again attracted widespread attention globally. Incident One: One of the largest hacker attacks in history led to the leakage of data of nearly 3 billion people; Incident Two: The Polish Anti-Doping Agency (POLADA) also suffered a hacker attack, resulting in the leakage of important data. These incidents not only highlight the severe challenges faced by cybersecurity but also have a profound impact on the global network environment.
This one of the largest hacker attacks in history involves the leakage of personal information of nearly 3 billion people, including sensitive information such as full names, addresses, and social security numbers, and is regarded as one of the largest data leakage incidents in history. The system of the Polish Anti-Doping Agency (POLADA) was hacked, leading to the leakage of agency data and affecting the normal operation of the agency.
The impacts of these events are extremely widespread. Firstly, it poses a huge risk to personal privacy. Massive data leakage makes hundreds of millions of people face the risk of privacy leakage, increasing the possibility of identity theft and financial fraud. Secondly, the security of enterprises and government agencies has been questioned, which will affect the trust of users in these institutions. In addition, data leakage may cause relevant institutions to face huge fines, legal lawsuits, and reputation losses, thereby affecting economic activities. Finally, such incidents prompt governments of various countries to strengthen the formulation and enforcement of data protection regulations, increasing regulatory pressure.
These events once again remind people of the importance of strengthening information security protection measures at the individual and organizational levels. Individuals should adopt stricter password management strategies and use methods such as two-factor authentication to protect the security of their accounts. Enterprises need to build a more solid network security defense system and regularly conduct security audits and vulnerability scans to ensure data security.
As a professional cybersecurity enterprise, Knownsec has accumulated rich experience and technical capabilities in preventing and responding to cybersecurity threats. Relying on its strong security research team and advanced technical means, Knownsec can help enterprises effectively identify potential security risks and provide comprehensive security solutions.
For example, in a large-scale attack against an e-commerce platform, Knownsec responded quickly. Through the emergency handling process, it successfully prevented further data leakage and assisted the customer in repairing system vulnerabilities, enhancing its network security protection capabilities. In addition, after a financial institution encountered a data leakage, Knownsec not only assisted it in conducting a thorough security review but also provided it with technical support in data encryption and access control to ensure the security and compliance of the data.
With the continuous upgrading of network attack methods, ensuring cybersecurity has become an unavoidable responsibility for enterprises and individuals.
#DataLeakage#CybersecurityChallenges#HackerAttacks#PrivacyRisk#NetworkSecuritySolutions#Knownsec#DataProtection#SecurityVulnerabilities#CyberThreats
0 notes
Text
Top Cybersecurity Best Practices to Protect Your Business in 2024

In today's digital world, keeping your business safe from cyber threats is crucial. Cyber threats are always changing, so it's key to stay ahead. This means using strong cybersecurity strategies to protect your data and keep your business running smoothly. Staying on top of cybersecurity means knowing the latest trends and technologies. It also means using proven best practices. By being proactive, you can shield your business from the harm of cyberattacks. Key Takeaways - Understand the importance of cybersecurity for business protection and continuity. - Explore emerging cybersecurity trends, including cloud security, zero-trust architecture, and AI-powered solutions. - Establish a robust cybersecurity policy to govern your organization's security practices and procedures. - Secure your network perimeter and IoT connections to mitigate the risk of cyber threats. - Adopt a people-centric security approach to empower your employees as the first line of defense. - Regularly backup data, update security measures, and collaborate with IT experts to enhance your cybersecurity posture. - Implement best practices like strong passwords, multi-factor authentication, and access control to protect sensitive information.
Why Cybersecurity is Crucial for Businesses
In today's world, cybersecurity is key for all businesses. They use technology and keep sensitive data, making them targets for hackers. A cyberattack can hurt their reputation, cause big financial losses, and disrupt their work. Protect Sensitive Data Businesses deal with a lot of sensitive info, like secret ideas, customer details, and money records. Keeping this data safe is very important. If it gets out, it can damage the company's image and lose customer trust. Prevent Financial Losses Cyberattacks can hit businesses hard in the wallet. They face costs like fixing a data breach, legal bills, and fines. Plus, an attack can slow down work, causing lost sales and less productivity. Maintain Business Continuity Keeping a business running smoothly is why cybersecurity matters. If a company's systems get hacked, it can stop services, cause downtime, and make it hard to help customers. Good cybersecurity helps stop and fix these problems fast, keeping work flowing. By using strong cybersecurity steps, businesses can keep data safe, avoid financial losses, and keep working well. This builds trust with customers, follows the law, cuts insurance costs, and makes them stronger against cyber threats. "Cybersecurity is no longer an option, but a necessity for businesses in the digital age." - Cybersecurity Expert
Emerging Cybersecurity Trends for 2024
The digital world is always changing, and cybersecurity experts must keep up to protect businesses. In 2024, new trends will shape the cybersecurity world. These trends highlight the need for proactive and flexible security plans. Developing Cloud Security More companies are moving to the cloud, making cloud security crucial. It's important to use strong identity checks, data encryption, and ongoing monitoring to keep cloud data safe. Using cloud security tools can help prevent data theft and meet legal standards. Using Zero Trust in Combination with VPN The old way of thinking about security doesn't work well in today's work-from-anywhere world. Experts suggest combining zero trust with VPN technology. This mix makes security better by checking who you are and what device you're using before you get in. It's a smarter way to keep data safe than traditional VPNs. Embracing AI Development Using artificial intelligence (AI) and machine learning (ML) in cybersecurity is big in 2024. AI systems can look at lots of data, spot odd patterns, and warn about threats fast. This helps companies find and deal with threats better. As AI gets better, it will help automate security tasks and make companies stronger against cyber threats. "Artificial intelligence is revolutionizing cybersecurity in 2024, with AI-powered systems autonomously identifying anomalous behavior patterns and predicting potential security breaches."
Establish a Robust Cybersecurity Policy
As businesses face new cybersecurity challenges, having a strong cybersecurity policy is key. This policy acts as a guide, listing the steps your company will take to boost cybersecurity. It helps your security team and employees work together better, making your defenses stronger. Using a hierarchical cybersecurity policy is a smart move. It has a main policy that sets the rules for your cybersecurity. Adding more policies for each department makes it work better and keeps things running smoothly. - Make a main cybersecurity policy for clear rules and best practices across your company. - Add policies for each department to meet their specific security needs. - Keep your cybersecurity policy up to date to match new threats and standards. - Give all employees detailed cybersecurity training so they know their roles. - Check how well the policy works with risk assessments, audits, and exercises to find and fix any issues. With a strong, layered cybersecurity policy, you can keep your data safe and your business running smoothly. It helps you stay ahead of cyber threats. "A well-designed cybersecurity policy serves as the foundation for a resilient and proactive security strategy."
Secure Your Perimeter and IoT Connections
In today's digital world, the old idea of an organization's border is outdated. With remote work, cloud services, and more IoT devices, cyber threats have grown. It's key to focus on securing your business's perimeter and IoT connections. Protect Border Routers and Screened Subnets Border routers and screened subnets are vital for your business's security. They help block unauthorized access and protect your data. It's important to keep these parts of your network safe with regular updates and strong controls. Implement Zero Trust Model The zero trust model is a new way to fight cyber threats. It checks users and devices all the time, not just at the border. This approach, with firewalls and VPNs, makes your security stronger and more flexible. Securing your perimeter and IoT devices is key to protecting your business. By protecting border routers, using screened subnets, and adopting the zero trust model, you boost your security. This helps keep your data and important systems safe.
Employ a People-Centric Security Approach
In the world of cybersecurity, just focusing on technology isn't enough. Hackers often target the human element. So, it's key to use a people-centric security approach. This means looking at how employees and users act and making sure they're safe. Most security issues come from human mistakes or tricks. This shows why a people-centric approach in cybersecurity is vital. By teaching employees about cybersecurity awareness and the human element in cybersecurity, companies can lower risks and get safer. Creating detailed training that talks about different cyber threats is a must. Using tools like TLMS in workshops makes sure employees pay attention and learn well. This helps them spot and deal with threats better. - Do regular security checks and send out reminders to lower risks in the company. - Build a work culture that makes security a part of everyday life, keeping everyone alert. - Use tools like TSAT to track vulnerabilities in real-time and improve how you manage risks. "By 2027, more than 50% of CISOs in large enterprises will have embraced a human-focused approach within their cybersecurity teams." - Gartner Adopting a people-centric security approach is crucial and necessary against new cyber threats. By focusing on employee cybersecurity awareness and the human element in cybersecurity, companies can create a strong defense against cyber attacks.
Install Backup Data and Security Updates
Keeping your business data safe is key to running smoothly. It's important to back up data and update software regularly. These steps help protect against data loss, corruption, and theft. Backing up data is a must for your company's safety. With more customer and user info, a strong backup plan is needed. Teach your team to back up data in secure places, either on-site or in the cloud. This helps lessen the damage from ransomware, hardware issues, or other data loss problems. Also, keeping your software and systems updated is crucial. Updates often fix bugs and add security features to protect against new threats. Tell your team to update software often to get the newest features and security fixes. "The average data breach cost is $4.35 million, or approximately $164 per data record." - IBM By focusing on data backup and software updates, you can improve your company's cybersecurity. These steps help protect your important data. They can prevent the big problems of data loss and cyber attacks, keeping your business safe and its reputation intact.
Cybersecurity Best Practices
With over 3.5 billion people online, protecting your business from cyber threats is key. Using strong passwords and multi-factor authentication can boost your security. These steps help keep your business safe. Use Strong Passwords and Multi-Factor Authentication Using strong passwords is a top way to protect your data. With billions of email accounts, making unique, complex passwords is a must. Adding multi-factor authentication gives you an extra security layer. This makes it harder for hackers to get into your systems. Control Access to Sensitive Information Keeping sensitive data safe is vital. Limit who can see financial records and trade secrets. Deactivate old accounts to keep your data secure. A strong access control system reduces the risk of unauthorized access. Following these cybersecurity tips keeps your data safe. It helps your business stay running smoothly. And it shields you from the harm of a cyber attack. "Cybersecurity is not just an IT issue, it's a business issue. Protecting your organization's data and assets should be a top priority for every organization, regardless of size or industry."
Collaborate with IT Department and Cybersecurity Experts
To keep your business safe from new cyber threats, it's key to work together with your IT team and cybersecurity pros. By teaming up with your IT staff and outside cybersecurity experts, you can make strong cybersecurity plans that fit your business. Working together can save your business money by lowering the chance of cyber attacks. Sharing threat info helps you fight off new and tricky cyber attacks early. But, building trust takes time and money, so be ready for that. Good cybersecurity teamwork means breaking down walls between different departments like IT, security, legal, and more. This way, everyone works together better. Sharing threat info, handling incidents together, and making joint decisions makes your business stronger against cyber threats. "Cybersecurity pros emphasized the importance of collaboration with a combination of communication, understanding, and shared goals." By partnering with your IT team and cybersecurity experts, you can keep your business ahead in the fast-changing world of cyber threats. This teamwork ensures you use the best cybersecurity steps and keeps your business running smoothly.
Conduct Regular Cybersecurity Audits
Regular cybersecurity audits are key to check your company's security level. They help spot weak spots and make sure you follow the rules. You should do these audits at least once a year. For companies dealing with sensitive info or lots of data, it's best to do them twice a year. These audits make your security tools and processes better. They help you fight off new cyber threats more effectively. Cybersecurity audits are more important now than ever. They help focus on the biggest risks in your company. Using a cloud-based data spot makes sharing and planning audits easier. Keeping an eye on your IT systems can catch risks early. It's important to have a clear plan for your audits. Set clear goals and make sure they're achievable. Reviewing your cybersecurity policies helps you understand your security better. Fixing issues found in audits can greatly lower the chance of data breaches. Read the full article
#BusinessContinuityPlanning#CloudSecurityBestPractices#CybersecurityStrategies#DataProtectionMeasures#EncryptionTechniques#IncidentResponseProtocols#NetworkSecuritySolutions#SecurityAwarenessTraining#ThreatDetectionTechnologies
0 notes
Text
Networking Solutions
Networking Solutions
A Networking Solution is a way of setting up and using different technologies to solve particular communication problems in a company or organization. It is like having a toolkit full of techniques and devices that help things communicate better and more securely. This toolkit helps different devices, like computers or phones, talk to each other in a reliable and efficient way. The major goal of business networking solutions is to make sure everything in the network can connect, and work properly.
Local Area Network (LAN)
A Local Area Network (LAN) helps your business grow by connecting devices in a small area, like an office or building. By using a strong network and advanced equipment, your business can do work better. This means having a reliable system that links computers, printers, and other devices, making it easier for everyone to share information and work together efficiently.
Optimizes the Local Area Network for efficiency and security.
Forms the backbone of an organization's digital infrastructure.
Enhances internal communication with swift and secure networks.
Wide Area Network (WAN)
WAN improves how your business manages connections across different locations or regions. To make your network work better, you can optimize its infrastructure. This means making sure everything in your network, even if it's in different places, can connect smoothly. By doing this, your business can have better communication and sharing of information between offices or branches, helping everyone work together more efficiently.
Networking Solutions
Networking solutions mean setting up Wi-Fi access everywhere on a site and making the network secure with specific plans. It's about offering internet connection across the whole place and using special strategies to keep the network secure. Cloud networking solutions help everyone stay connected and ensure that the internet is safe for everyone using it in that area.
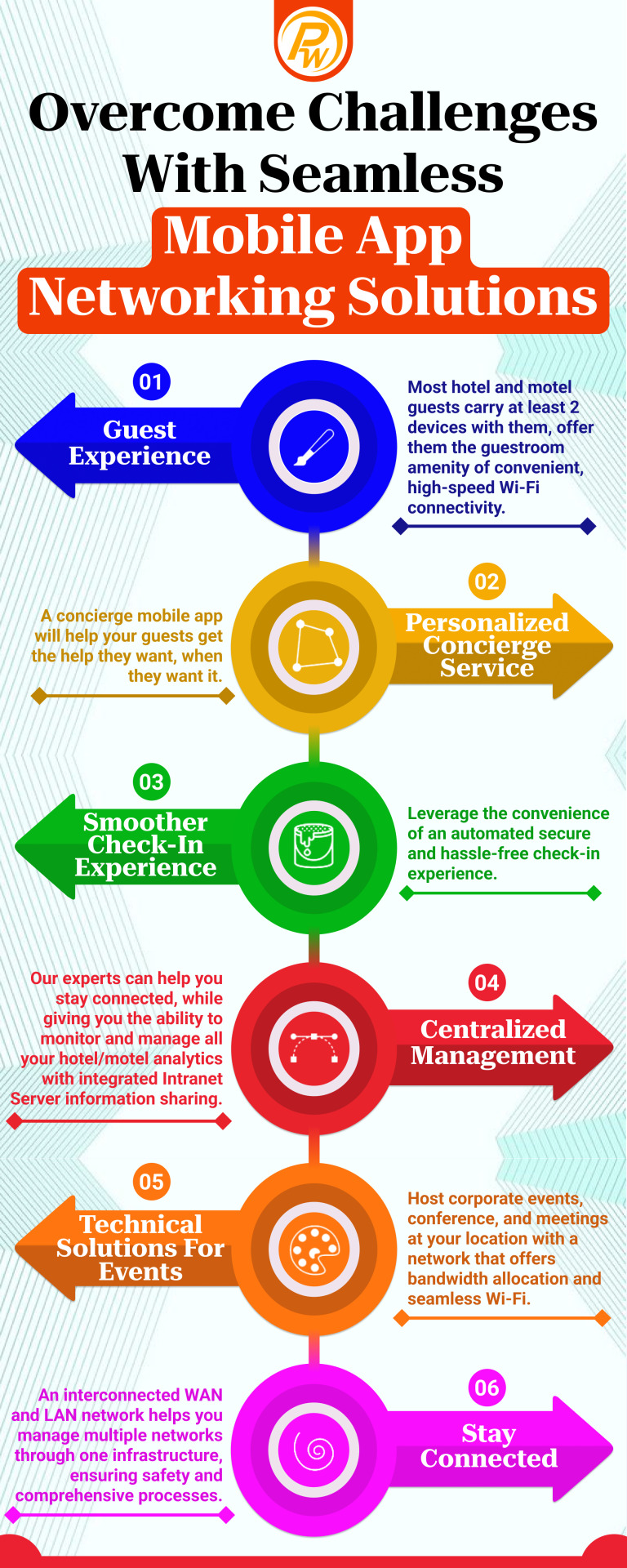
Guest Experience
Most hotel and motel guests carry at least 2 devices with them, offering them the guestroom amenity of convenient, high-speed Wi-Fi connectivity.
Personalized Concierge Service
A concierge mobile app will help your guests get the help they want when they want it.
Smoother Check-In Experience
Leverage the convenience of an automated secure and hassle-free check-in experience.
Centralized Management
Our experts can help you stay connected while giving you the ability to monitor and manage all your hotel/motel analytics with integrated Intranet Server information sharing.
Technical Solutions For Events
Host corporate events, conferences, and meetings at your location with a network that offers bandwidth allocation and seamless Wi-Fi.
Stay Connected
An interconnected WAN and LAN network helps you manage multiple networks through one infrastructure, ensuring safety and comprehensive processes.
Security Measures
Execute security solutions like encryption, authentication mechanisms, intrusion detection/prevention systems, and access controls to safeguard the network against unauthorized access, cyber threats, and data breaches.
Cloud Networking
Using cloud-based solutions for networking means using internet-based services to help with things like building networks or managing information. These services can include different types of frameworks, platforms, or software. They make it easier for companies to grow, be flexible, and access what they need online without having to rely on physical systems. This kind of setup allows companies to expand smoothly, change things as needed, and access their tools and data from almost anywhere.
Unveiling Hospitality Network Solution
Ensures secure and delightful guest experiences.
Safeguards guest data with advanced security measures.
Redefines standards of satisfaction in the hospitality industry.
Explores the migration of businesses to the cloud.
Highlights the flexibility and efficiency offered by cloud networks.
Focuses on robust encryption protocols for data security.
0 notes
Text
Security Onion Install: Awesome Open Source Security for Home Lab
Security Onion Install: Awesome Open Source Security for Home Lab @securityonion #homelab #selfhosted #SecurityOnionInstallationGuide #NetworkSecuritySolutions #IntrusionDetectionSystem #OpenSourceSecurityPlatform #ThreatHuntingWithSecurityOnion
Security Onion is at the top of the list if you want an excellent security solution to try in your home lab or even for enterprise security monitoring. It provides many great security tools for threat hunting and overall security and is fairly easy to get up and running quickly. Table of contentsWhat is Security Onion?Intrusion Detection and Threat HuntingMonitoring and Log managementCommunity…

View On WordPress
#configuring Security Onion#Intrusion Detection System#log management practices#network monitoring and analysis#Network Security Solutions#open-source security platform#Security Onion deployment#Security Onion installation guide#threat hunting with Security Onion#virtual machine security setup
0 notes
Link
When you set up your network security solutions,you’ll need to put together the list of everyone who will need to access your network on a regular basis. Visit https://www.memset.com/services/networking/
0 notes
Photo

Partnered with @ITGURUSATL the solutions, hardware, software, and services makes both companies a unique blend.
Call us now -:(888) 511-0143 Visit -: https://bit.ly/2Fj7kTT
0 notes
Link
Network Security is a realm which has changed vastly over decades with multiple ways offered by ample amount of Experts to deal with issues. Contact us anytime at 0557503724 for quick network solutions.

0 notes
Photo

Tribo8 Infosolutions Provides the best VPN Solutions.Click for more: https://tribo8.com/network-security.php#tribo8infosolutions#tribo8#VPN#VPNSolution#VPNSecurity#securitysolutions#networksecurity#networksecuritysolution#networksolutions
0 notes
Photo

Are you looking for #NetworkSecuritySolutions ? Acutesoft Solutions is one of the best Service Provider in Hyderabad.
https://acutesoft.com/it-services/it-infrastructure-services/
0 notes
Text
Top Cybersecurity Best Practices to Protect Your Business in 2024

In today's digital world, keeping your business safe from cyber threats is crucial. Cyber threats are always changing, so it's key to stay ahead. This means using strong cybersecurity strategies to protect your data and keep your business running smoothly. Staying on top of cybersecurity means knowing the latest trends and technologies. It also means using proven best practices. By being proactive, you can shield your business from the harm of cyberattacks. Key Takeaways - Understand the importance of cybersecurity for business protection and continuity. - Explore emerging cybersecurity trends, including cloud security, zero-trust architecture, and AI-powered solutions. - Establish a robust cybersecurity policy to govern your organization's security practices and procedures. - Secure your network perimeter and IoT connections to mitigate the risk of cyber threats. - Adopt a people-centric security approach to empower your employees as the first line of defense. - Regularly backup data, update security measures, and collaborate with IT experts to enhance your cybersecurity posture. - Implement best practices like strong passwords, multi-factor authentication, and access control to protect sensitive information.
Why Cybersecurity is Crucial for Businesses
In today's world, cybersecurity is key for all businesses. They use technology and keep sensitive data, making them targets for hackers. A cyberattack can hurt their reputation, cause big financial losses, and disrupt their work. Protect Sensitive Data Businesses deal with a lot of sensitive info, like secret ideas, customer details, and money records. Keeping this data safe is very important. If it gets out, it can damage the company's image and lose customer trust. Prevent Financial Losses Cyberattacks can hit businesses hard in the wallet. They face costs like fixing a data breach, legal bills, and fines. Plus, an attack can slow down work, causing lost sales and less productivity. Maintain Business Continuity Keeping a business running smoothly is why cybersecurity matters. If a company's systems get hacked, it can stop services, cause downtime, and make it hard to help customers. Good cybersecurity helps stop and fix these problems fast, keeping work flowing. By using strong cybersecurity steps, businesses can keep data safe, avoid financial losses, and keep working well. This builds trust with customers, follows the law, cuts insurance costs, and makes them stronger against cyber threats. "Cybersecurity is no longer an option, but a necessity for businesses in the digital age." - Cybersecurity Expert
Emerging Cybersecurity Trends for 2024
The digital world is always changing, and cybersecurity experts must keep up to protect businesses. In 2024, new trends will shape the cybersecurity world. These trends highlight the need for proactive and flexible security plans. Developing Cloud Security More companies are moving to the cloud, making cloud security crucial. It's important to use strong identity checks, data encryption, and ongoing monitoring to keep cloud data safe. Using cloud security tools can help prevent data theft and meet legal standards. Using Zero Trust in Combination with VPN The old way of thinking about security doesn't work well in today's work-from-anywhere world. Experts suggest combining zero trust with VPN technology. This mix makes security better by checking who you are and what device you're using before you get in. It's a smarter way to keep data safe than traditional VPNs. Embracing AI Development Using artificial intelligence (AI) and machine learning (ML) in cybersecurity is big in 2024. AI systems can look at lots of data, spot odd patterns, and warn about threats fast. This helps companies find and deal with threats better. As AI gets better, it will help automate security tasks and make companies stronger against cyber threats. "Artificial intelligence is revolutionizing cybersecurity in 2024, with AI-powered systems autonomously identifying anomalous behavior patterns and predicting potential security breaches."
Establish a Robust Cybersecurity Policy
As businesses face new cybersecurity challenges, having a strong cybersecurity policy is key. This policy acts as a guide, listing the steps your company will take to boost cybersecurity. It helps your security team and employees work together better, making your defenses stronger. Using a hierarchical cybersecurity policy is a smart move. It has a main policy that sets the rules for your cybersecurity. Adding more policies for each department makes it work better and keeps things running smoothly. - Make a main cybersecurity policy for clear rules and best practices across your company. - Add policies for each department to meet their specific security needs. - Keep your cybersecurity policy up to date to match new threats and standards. - Give all employees detailed cybersecurity training so they know their roles. - Check how well the policy works with risk assessments, audits, and exercises to find and fix any issues. With a strong, layered cybersecurity policy, you can keep your data safe and your business running smoothly. It helps you stay ahead of cyber threats. "A well-designed cybersecurity policy serves as the foundation for a resilient and proactive security strategy."
Secure Your Perimeter and IoT Connections
In today's digital world, the old idea of an organization's border is outdated. With remote work, cloud services, and more IoT devices, cyber threats have grown. It's key to focus on securing your business's perimeter and IoT connections. Protect Border Routers and Screened Subnets Border routers and screened subnets are vital for your business's security. They help block unauthorized access and protect your data. It's important to keep these parts of your network safe with regular updates and strong controls. Implement Zero Trust Model The zero trust model is a new way to fight cyber threats. It checks users and devices all the time, not just at the border. This approach, with firewalls and VPNs, makes your security stronger and more flexible. Securing your perimeter and IoT devices is key to protecting your business. By protecting border routers, using screened subnets, and adopting the zero trust model, you boost your security. This helps keep your data and important systems safe.
Employ a People-Centric Security Approach
In the world of cybersecurity, just focusing on technology isn't enough. Hackers often target the human element. So, it's key to use a people-centric security approach. This means looking at how employees and users act and making sure they're safe. Most security issues come from human mistakes or tricks. This shows why a people-centric approach in cybersecurity is vital. By teaching employees about cybersecurity awareness and the human element in cybersecurity, companies can lower risks and get safer. Creating detailed training that talks about different cyber threats is a must. Using tools like TLMS in workshops makes sure employees pay attention and learn well. This helps them spot and deal with threats better. - Do regular security checks and send out reminders to lower risks in the company. - Build a work culture that makes security a part of everyday life, keeping everyone alert. - Use tools like TSAT to track vulnerabilities in real-time and improve how you manage risks. "By 2027, more than 50% of CISOs in large enterprises will have embraced a human-focused approach within their cybersecurity teams." - Gartner Adopting a people-centric security approach is crucial and necessary against new cyber threats. By focusing on employee cybersecurity awareness and the human element in cybersecurity, companies can create a strong defense against cyber attacks.
Install Backup Data and Security Updates
Keeping your business data safe is key to running smoothly. It's important to back up data and update software regularly. These steps help protect against data loss, corruption, and theft. Backing up data is a must for your company's safety. With more customer and user info, a strong backup plan is needed. Teach your team to back up data in secure places, either on-site or in the cloud. This helps lessen the damage from ransomware, hardware issues, or other data loss problems. Also, keeping your software and systems updated is crucial. Updates often fix bugs and add security features to protect against new threats. Tell your team to update software often to get the newest features and security fixes. "The average data breach cost is $4.35 million, or approximately $164 per data record." - IBM By focusing on data backup and software updates, you can improve your company's cybersecurity. These steps help protect your important data. They can prevent the big problems of data loss and cyber attacks, keeping your business safe and its reputation intact.
Cybersecurity Best Practices
With over 3.5 billion people online, protecting your business from cyber threats is key. Using strong passwords and multi-factor authentication can boost your security. These steps help keep your business safe. Use Strong Passwords and Multi-Factor Authentication Using strong passwords is a top way to protect your data. With billions of email accounts, making unique, complex passwords is a must. Adding multi-factor authentication gives you an extra security layer. This makes it harder for hackers to get into your systems. Control Access to Sensitive Information Keeping sensitive data safe is vital. Limit who can see financial records and trade secrets. Deactivate old accounts to keep your data secure. A strong access control system reduces the risk of unauthorized access. Following these cybersecurity tips keeps your data safe. It helps your business stay running smoothly. And it shields you from the harm of a cyber attack. "Cybersecurity is not just an IT issue, it's a business issue. Protecting your organization's data and assets should be a top priority for every organization, regardless of size or industry."
Collaborate with IT Department and Cybersecurity Experts
To keep your business safe from new cyber threats, it's key to work together with your IT team and cybersecurity pros. By teaming up with your IT staff and outside cybersecurity experts, you can make strong cybersecurity plans that fit your business. Working together can save your business money by lowering the chance of cyber attacks. Sharing threat info helps you fight off new and tricky cyber attacks early. But, building trust takes time and money, so be ready for that. Good cybersecurity teamwork means breaking down walls between different departments like IT, security, legal, and more. This way, everyone works together better. Sharing threat info, handling incidents together, and making joint decisions makes your business stronger against cyber threats. "Cybersecurity pros emphasized the importance of collaboration with a combination of communication, understanding, and shared goals." By partnering with your IT team and cybersecurity experts, you can keep your business ahead in the fast-changing world of cyber threats. This teamwork ensures you use the best cybersecurity steps and keeps your business running smoothly.
Conduct Regular Cybersecurity Audits
Regular cybersecurity audits are key to check your company's security level. They help spot weak spots and make sure you follow the rules. You should do these audits at least once a year. For companies dealing with sensitive info or lots of data, it's best to do them twice a year. These audits make your security tools and processes better. They help you fight off new cyber threats more effectively. Cybersecurity audits are more important now than ever. They help focus on the biggest risks in your company. Using a cloud-based data spot makes sharing and planning audits easier. Keeping an eye on your IT systems can catch risks early. It's important to have a clear plan for your audits. Set clear goals and make sure they're achievable. Reviewing your cybersecurity policies helps you understand your security better. Fixing issues found in audits can greatly lower the chance of data breaches. Read the full article
#BusinessContinuityPlanning#CloudSecurityBestPractices#CybersecurityStrategies#DataProtectionMeasures#EncryptionTechniques#IncidentResponseProtocols#NetworkSecuritySolutions#SecurityAwarenessTraining#ThreatDetectionTechnologies
0 notes
Text
pfSense Plus vs CE: Complete Comparison
pfSense Plus vs CE: Complete Comparison @vexpert #vmwarecommunities #100daysofhomelab #pfSenseCEvsPlusComparison #NetworkSecuritySolutions #OpensourceFirewallSoftware #pfSensePlusFeatures #MigratingfrompfSenseCEtoPlus
Netgate, the company behind pfSense CE, announced pfSense Plus in 2021, a new version of its popular open-source firewall and router software based on FreeBSD. If you want to run pfSense CE on your own hardware, users can now choose Community Edition (CE) or Plus. Let’s look at pfSense Plus vs CE, providing a comprehensive guide to making an informed choice between the two. Let’s delve right…

View On WordPress
#Commercial pfSense Plus Benefits#Migrating from pfSense CE to Plus#Network Security Solutions#Network Security with pfSense#Open-source Firewall Software#pfSense CE vs Plus comparison#pfSense Community Edition Advantages#pfSense Plus Features#pfSense Software Differences#Upgrading to pfSense Plus
0 notes
Link
With increasing use in internet it is important to secure our network data. Get network security solution for a reasonable price at Memset. To know more visit, https://www.memset.com/services/networking/
0 notes