#ThreatPrevention
Explore tagged Tumblr posts
Text

Explore the multiple layers of protection offered by Microsoft Defender in our comprehensive guide! From advanced threat protection to identity security, discover how Microsoft Defender shields your organization from evolving cyber threats. Learn how to enhance your security posture with these essential layers and keep your data safe.
#Exinent#MicrosoftDefender#CyberSecurity#DataProtection#ThreatPrevention#SecuritySolutions#Microsoft#CloudSecurity
0 notes
Text
School Safety Frenzy
Florida is ramping up measures to counteract a surge of threats and violence in K-12 schools. With the return of metal detectors and public shaming of students making threats, the state is pulling out all the stops to protect its children. Is this the right approach, or do these methods go too far? How should schools balance student safety with a healthy learning environment? Share your thoughts.
#SchoolSafety#MetalDetectorsInSchools#K12Education#StudentWellbeing#ThreatPrevention#SchoolViolencePrevention#EducationDebate#FloridaEducation#StudentSafetyMeasures#SchoolSecurityDebate
0 notes
Text
Leveraging TCP RST Packets: A Novel Method for Network Security
In the realm of network security, a novel method using TCP RST packets to counteract malicious traffic is proposed. This approach involves a pseudo IDPS device that detects threats through analyzing TCP/UDP payloads, headers, and IP signatures. Operating
Introduction In the ever-evolving landscape of network security, the ability to quickly and effectively mitigate threats is paramount. Traditional intrusion detection and prevention systems (IDPS) are essential tools, but there remains a need for innovative solutions that can act as an intermediary step in threat detection and prevention. This article explores a novel approach: utilizing TCP RST…
#futuretechnology#internetsecurity#networksecurity#noveltechnology#packetdetection#platformsecurity#threatprevention
0 notes
Text
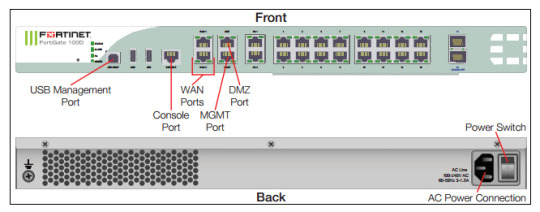
Fortify your network security skills with DC Lessons' "FortiGate" courses! Master the art of configuring and managing FortiGate firewalls for robust protection. Dive into hands-on training, understand security policies, and gain practical insights into threat prevention. https://www.dclessons.com/category/courses/fortigate
#FortiGate#NetworkSecurity#TechLearning#DClessons#FirewallConfiguration#ITTraining#ThreatPrevention#ITPros#CareerDevelopment
0 notes
Link
https://bit.ly/3IGH6KB - 🔍 Mandiant has identified a new operational technology (OT) malware dubbed COSMICENERGY, which was uploaded to a public malware scanning utility in December 2021 from Russia. The malware aims to disrupt electric power by interacting with IEC 60870-5-104 devices like remote terminal units, commonly used in Europe, the Middle East, and Asia's electric transmission and distribution operations. #CyberSecurity #Malware #COSMICENERGY 🛠️ COSMICENERGY's capabilities are similar to those used in previous incidents, such as the INDUSTROYER malware. Interestingly, a contractor may have developed COSMICENERGY as a red teaming tool for simulated power disruption exercises hosted by Rostelecom-Solar, a Russian cybersecurity company. Such development signifies a lowered entry barrier for developing offensive OT capabilities. #CyberThreats #RedTeaming #RostelecomSolar ⚡ The attack strategy and capabilities of COSMICENERGY are reminiscent of the 2016 INDUSTROYER incident. It utilizes two components, PIEHOP and LIGHTWORK, to interact with RTUs, affecting the actuation of power line switches and circuit breakers, causing power disruption. However, COSMICENERGY lacks discovery capabilities, implying a need for internal reconnaissance to obtain environment information for a successful attack. #CyberAttack #PIEHOP #LIGHTWORK 🔎 COSMICENERGY could be associated with Russian government-funded power disruption and emergency response exercises, as the code sample refers to a project named “Solar Polygon,” developed by Rostelecom-Solar. However, the lack of concrete evidence leaves the actual purpose of COSMICENERGY uncertain. #RussianCyberSecurity #SolarPolygon 🔁 COSMICENERGY shares similarities with previous OT malware like INDUSTROYER, IRONGATE, TRITON, and INCONTROLLER. With open-source libraries and Python for malware development becoming more commonplace, such trends may manifest in future OT malware. #OTMalware #OpenSource #Python 🛡️ While COSMICENERGY's capabilities aren't notably different from previous OT malware, its discovery is significant. It presents an immediate threat to affected organizations and highlights a lowering of barriers to entry for offensive OT threat activity. Therefore, it is crucial for OT defenders and asset owners to take preventive action against COSMICENERGY to preempt possible deployment.
#CyberSecurity#Malware#COSMICENERGY#CyberThreats#RedTeaming#RostelecomSolar#CyberAttack#PIEHOP#LIGHTWORK#RussianCyberSecurity#SolarPolygon#OTMalware#OpenSource#Python#ThreatPrevention#CyberDefense
0 notes
Text
Threat Modeling: What is it? 🧐
In today's rapidly evolving digital landscape, security has become a paramount concern for organizations. Cyber threats and attacks are constantly on the rise, targeting sensitive data, systems, and infrastructure. To effectively combat these threats, organizations employ various security measures, one of which is threat modeling. Threat modeling is a proactive approach that helps organizations identify potential vulnerabilities and risks in their systems, allowing them to prioritize security efforts and develop effective countermeasures.
🔍 Let's delve deeper into what threat modeling entails and its benefits for organizations!
Read on 👉 https://www.valevpn.com/post/threat-modeling-what-is-it
ThreatModeling #Cybersecurity #SecurityRisk #VulnerabilityAssessment #RiskManagement #InformationSecurity #SecureDevelopment #ThreatIdentification #DataProtection #SecureSystems #SecurityBestPractices #SecureCoding #SecurityAwareness #RiskMitigation #SecurityCompliance #CyberThreats #ThreatPrevention #SecurityStrategy #SecurityMeasures #SecurityFramework #RiskAnalysis

0 notes
Photo

วันนี้ #nForce และ #Symantec นำโซลูชั่น #CloudSecurity ไม่ว่าจะเป็น #ThreatPrevention #DataProtection มาที่งาน Tech Talk Thai: IT Trends and Predictions in 2019 โซลูชั่นที่จะช่วยปกป้องข้อมูลบน Cloud ของคุณทั้งจากในองค์กรและภัยคุกคามต่างๆ #Symantec #SymantecThailand #CloudSecurity #cybersecurity #cyberawareness #cyberattack #cybercrime #ITSecurity #nForceSecure #ITThailand #ITDistributor #ThaiITDistributor #เราคือร้อยเปอร์เซ็นต์ไอทีดิสตริบิวเตอร์สัญชาติไทย ศึกษาโซลูชั่นเพิ่มเติมได้ที่ www.nforcesecure.com หรือปรึกษาเราได้ที่ 02-2740984 และ Line@ nForceSecure IT Security ทุกคำถามมีคำตอบ เราพร้อมตอบแบบไม่กั๊ก .... เพราะเราคือ nForce Secure ... Thai IT Distributor https://www.instagram.com/p/BuanzzEBINB/?utm_source=ig_tumblr_share&igshid=xgvipvsdx3zc
#nforce#symantec#cloudsecurity#threatprevention#dataprotection#symantecthailand#cybersecurity#cyberawareness#cyberattack#cybercrime#itsecurity#nforcesecure#itthailand#itdistributor#thaiitdistributor#เราคือร้อยเปอร์เซ็นต์ไอทีดิสตริบิวเตอร์สัญชาติไทย
0 notes
Text
Firewall builder policy read from bottom up

#Firewall builder policy read from bottom up how to
#Firewall builder policy read from bottom up software
#Firewall builder policy read from bottom up password
#Firewall builder policy read from bottom up license
#Firewall builder policy read from bottom up download
Now you're ready to start updating the content on this device, so navigate to the Device tab, then select Dynamic Updates from the left pane.
#Firewall builder policy read from bottom up license
If the device was registered but no licenses added yet, select Activate feature using authorization code to activate a license through its authorization code, which you will have received from your Palo Alto sales contact.Īfter the licenses have been succesfully added, the Licenses page looks similar to this: If the device has been registered using the above method and auth codes have already been added, go ahead and select Retrieve License keys from license server. Navigate to the Device tab and select Licenses from the left pane:
#Firewall builder policy read from bottom up how to
If the device has not been registered on the support portal yet, please follow these steps to register the device: How to Register a Palo Alto Networks Device, Spare, Traps, or VM-Series Auth-Code
URL license enables URL categories for use in security policies.
ThreatPrevention license adds virus, threats and malware signatures.
#Firewall builder policy read from bottom up software
Support license entitles the system to software and AppID updates.
Various licenses control the different functions of the system, so the.
#Firewall builder policy read from bottom up download
To be allowed to download content and application updates or software upgrades, the system needs to be licensed. Preparing the licenses and updating the system You should be able to connect to the management IP from the network, and you should be able to surf out to the Internet.Ģ.
Connect the Managment (mgmt) interface to the switch.
The firewall is now configured with a proper IP address to work in your LAN network, so go ahead and connect the cables: To complete this step and apply changes to the device, click the Commit link at the top right:Īfter the commit completes, the browser eventually times out as the IP address has changed, so you'll need to manually change the address in the address bar to reconnect to the new IP. Next, select the Services tab and configure a DNS server. Select Setup on the left pane, then select Management, where you can change the Management Interface Settings:Ĭhange the interface configuration and click OK.
#Firewall builder policy read from bottom up password
Log in, using the default username and password admin / admin, then navigate to the Device tab. You can safely ignore the error message at this time, which then takes you to the login screen: This is because the certificate used by the web interface is a self-signed certificate your browser does not trust. When making your first connection to the web interface, your browser may display an error message. Now you need to reconnect to the new IP address -please skip to step 1.3. 55%.60%75%.99%.100%Īt this point, you'll lose SSH and SSL access to the device, as the IP address was changed and the management service restarted to adopt these changes. Use the commit command to apply the new settings to the commit Please change your password prior to configureĮntering configuration set deviceconfig system ip-address 10.0.0.10 netmask 255.255.255.0 default-gateway 10.0.0.1 dns-setting servers primary 4.2.2.2 Warning: Your device is still configured with the default admin account credentials. Using keyboard-interactive authentication. From here, we'll start setting up the proper IP address and subnet for the device, and the default gateway and DNS settings, so the unit can collect updates later. The default username and password are admin / admin, so we'll go ahead and log in to reveal the CLI. and the Graphical User Interface or GUI in step 1.2. We'll highlight the console and SSH in step 1.1. Remounting root filesystem in read-write mode: Īfter the device is booted, a login prompt is displayed in the console connection and SSH or SSL connections can be made to 192.168.1.1. Īfter preparing the cables and the workstation, plug the unit into an electrical outlet and watch the firewall boot up. If you use PuTTY, it should come with the appropriate configuration if connection type is set to Serial. When using a console cable, set the terminal emulator to 9600baud, 8 data bits, 1 stop bit, parity none, VT100. When using the management port, the workstation you'll be using must be reconfigured so its network interface has an IP address in the 192.168.1.0/24 IP range, as the default IP of the management port will be 192.168.1.1. The two methods available to connect to the new device is either using a network cable on the management port or an ethernet-to-db-9 console cable. The first thing you'll want to configure is the management IP address, which makes it easier to continue setting up your new device later on.

0 notes
Photo

So someone tried to hack my Gmail Today! #selfmadeceowade #hack #computer #security #E-mail #gmail #threat #threatdetection #threatprevention #informationtechnology #it #iger
#hack#computer#threat#threatprevention#gmail#it#e#security#selfmadeceowade#iger#threatdetection#informationtechnology
0 notes