#SomethingAwesome
Explore tagged Tumblr posts
Text
The most incredible thing!
Hi guys, I got something awesome to show you! Click keep reading to see something cool!
Keep reading
4 notes
·
View notes
Text
Substitution Cipher - Solver/Decryption
This one was a bit harder to do as its clearly taken alot longer (mostly because the logic of my code was not correct 😢). However now it works relatively well it should be able to decrypt most substitution ciphers. From what I see the longer your ciphertext the less variation in the scores outputted at the end. With shorter texts it might not work as well. So below is the code:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139
import re, random from ngram_class import nGramInfo #substitution cipher def main(): # grabs input and makes it lower case ciphertext = input("Enter the message: ") ciphertext = ciphertext.lower() # removes everything except for letters this is used for calculating the healthiness ciphertext_only_letters = re.sub("[^a-z]+", "", ciphertext) alphabet = list("abcdefghijklmnopqrstuvwxyz") #randomly shuffles the alphabet random.shuffle(alphabet) starter_key = "".join(alphabet) #starter key is random arrangement of alphabet # calculates the best keys and prints them out in a decending order of healthiness # highest healthiness (most correct) will be at the bottom best_keys = calculate_best_key(ciphertext_only_letters, starter_key, ciphertext) best_keys = sorted(best_keys) for i in range(len(best_keys)): print("================\n"+"Score:", best_keys[i][0], "\nKey:", best_keys[i][1], "\nDecryption:", substitution(ciphertext, best_keys[i][1])) # print(best_keys) #prints out the best guess #its just the last thing anyway print("\n======== BEST GUESS ========") print("Score:", best_keys[-1][0]) print("Key:", best_keys[-1][1]) print("Decryption:", substitution(ciphertext, best_keys[-1][1])) def calculate_best_key(ciphertext_only_letters, starter_key, ciphertext): #creates object to calculate fitness calculator = create_nGramInfo_class() print("\n\n\nCiphertext:", ciphertext) print("Ciphertext Healthiness Score:", calculator.calculate_fitness_score(ciphertext)) highest = [] #highest holds the highest scores and the keys associated with the scores # this is the key that is shuffled into a new key every iteration key = list('abcdefghijklmnopqrstuvwxyz') # if the thing cant be solved iterations should be increased first iteration = 0 while iteration < 15: print("Iteration:", iteration) #generates new key and calculates the fitness of the keys associated possible plaintext random.shuffle(key) new_key = "".join(key) print("new key:", new_key) high_score = calculator.calculate_fitness_score(substitution(ciphertext_only_letters, new_key)) best_key = new_key highest.append([high_score, best_key]) iteration += 1 i = 0 # this can be increased if solver not solving however changing iteration number should be first while i < 10000: prev_key = new_key #generates 2 random numbers (musnt be the same) num1 = num2 = 0 while num1 == num2: num1 = random.randint(0, 25) num2 = random.randint(0, 25) #swaps the letters new = list(new_key) new[num1], new[num2] = new[num2], new[num1] new_key = "".join(new) #creates the possible plaintext and calculates fitness plaintext = substitution(ciphertext_only_letters, new_key) new_score = calculator.calculate_fitness_score(plaintext) #if new score is higher than high score new score becomes high score and is added to highest list if new_score > high_score: high_score = new_score best_key = new_key highest.append([high_score, best_key]) if len(highest) > 20: highest = sorted(highest) highest = highest[5:] else: #if score doesnt increase it goes back to previous key new_key = prev_key i += 1 # summarises information in every iteration print("Current highest score is", high_score, "on iteration", iteration) print(best_key) print("This decodes to", substitution(ciphertext_only_letters, best_key)) print("\n\n") return highest def create_nGramInfo_class(): print("Enter '1' for monograms") print("Enter '2' for bigrams") print("Enter '3' for trigrams") print("Enter '4' for quadgrams") print("Note: quadgrams can only do analysis on messages >= 4 characters\ntrigrams for >= 3 and so on \n(if you need a program to help decipher a < 4 letter caesar cipher RIP)") mode = input("Enter Mode: ") mode = mode.strip().lower() if mode == '1': file_name = "ngrams/english_monograms.txt" elif mode == '2': file_name = "ngrams/english_bigrams.txt" elif mode == '3': file_name = "ngrams/english_trigrams.txt" elif mode == '4': file_name = "ngrams/english_quadgrams.txt" else: print("Make sure input is correct") exit() return nGramInfo(file_name) def substitution(ciphertext_only_letters, key): plaintext = "" for letter in ciphertext_only_letters: if letter.isalpha() == True: plaintext += key[ord(letter) - ord("a")] else: plaintext += letter return plaintext if __name__ == "__main__": main()
Here are some tests using it.
Test 1
Message we are encrypting: “short message test”
Key used to encrypt: “qwertyuiopasdfghjklzxcvbnm”
basically just left to right on the keyboard
Ciphertext: “ligkz dtllqut ztlz”
Program ouputs:

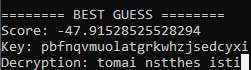
Running the program 2 times gives us nothing significant it is mostly just gibberish however imagine someone with more computing power than me they could run multiple versions of this program while increasing the number of iterations the program goes through. It could easily decipher these messages with little issue.
Test 2
Message we are encrypting: “longer messages should work much better with these substitution cipher solvers however i mean who is even trying to solve the shorter ones using a computer”
Key used to encrypt: “qwertyuiopasdfghjklzxcvbnm”
same one as before
Ciphertext: “sgfutk dtllqutl ligxsr vgka dxei wtzztk vozi zitlt lxwlzozxzogf eohitk lgsctkl igvtctk o dtqf vig ol tctf zknofu zg lgsct zit ligkztk gftl xlofu q egdhxztk”
Program ouputs:

Guess what it was solved on the first go despite having such a large keyspace it is still relatively easy to crack a substitution cipher
From this I was legitimately surprised at how fast the substitution cipher could be cracked even with the resources I had. As we had to do many cryptograms, which are essentially substitution ciphers, I thought that this would be harder for a computer to do because even for us it would take a decent amount of time to decrypt them. Its shocking how fast a computer can do this just be randomly generating keys and choosing the better ones.
Note: once again i don’t know if the code is visible so will leave it below (all the code is on the github anyway)
import re, random
from ngram_class import nGramInfo
#substitution cipher
def main(): # grabs input and makes it lower case ciphertext = input("Enter the message: ") ciphertext = ciphertext.lower() # removes everything except for letters this is used for calculating the healthiness ciphertext_only_letters = re.sub("[^a-z]+", "", ciphertext)
alphabet = list("abcdefghijklmnopqrstuvwxyz")
#randomly shuffles the alphabet random.shuffle(alphabet) starter_key = "".join(alphabet) #starter key is random arrangement of alphabet
# calculates the best keys and prints them out in a decending order of healthiness # highest healthiness (most correct) will be at the bottom best_keys = calculate_best_key(ciphertext_only_letters, starter_key, ciphertext) best_keys = sorted(best_keys) for i in range(len(best_keys)): print("================\n"+"Score:", best_keys[i][0], "\nKey:", best_keys[i][1], "\nDecryption:", substitution(ciphertext, best_keys[i][1])) # print(best_keys)
#prints out the best guess #its just the last thing anyway print("\n======== BEST GUESS ========") print("Score:", best_keys[-1][0]) print("Key:", best_keys[-1][1]) print("Decryption:", substitution(ciphertext, best_keys[-1][1]))
def calculate_best_key(ciphertext_only_letters, starter_key, ciphertext): #creates object to calculate fitness calculator = create_nGramInfo_class() print("\n\n\nCiphertext:", ciphertext) print("Ciphertext Healthiness Score:", calculator.calculate_fitness_score(ciphertext)) highest = [] #highest holds the highest scores and the keys associated with the scores # this is the key that is shuffled into a new key every iteration key = list('abcdefghijklmnopqrstuvwxyz')
# if the thing cant be solved iterations should be increased first iteration = 0 while iteration < 15: print("Iteration:", iteration)
#generates new key and calculates the fitness of the keys associated possible plaintext random.shuffle(key) new_key = "".join(key) print("new key:", new_key) high_score = calculator.calculate_fitness_score(substitution(ciphertext_only_letters, new_key)) best_key = new_key highest.append([high_score, best_key])
iteration += 1 i = 0 # this can be increased if solver not solving however changing iteration number should be first while i < 10000: prev_key = new_key
#generates 2 random numbers (musnt be the same) num1 = num2 = 0 while num1 == num2: num1 = random.randint(0, 25) num2 = random.randint(0, 25)
#swaps the letters new = list(new_key) new[num1], new[num2] = new[num2], new[num1] new_key = "".join(new)
#creates the possible plaintext and calculates fitness plaintext = substitution(ciphertext_only_letters, new_key) new_score = calculator.calculate_fitness_score(plaintext)
#if new score is higher than high score new score becomes high score and is added to highest list if new_score > high_score: high_score = new_score best_key = new_key highest.append([high_score, best_key]) if len(highest) > 20: highest = sorted(highest) highest = highest[5:] else: #if score doesnt increase it goes back to previous key new_key = prev_key
i += 1
# summarises information in every iteration print("Current highest score is", high_score, "on iteration", iteration) print(best_key) print("This decodes to", substitution(ciphertext_only_letters, best_key)) print("\n\n")
return highest
def create_nGramInfo_class(): print("Enter '1' for monograms") print("Enter '2' for bigrams") print("Enter '3' for trigrams") print("Enter '4' for quadgrams") print("Note: quadgrams can only do analysis on messages >= 4 characters\ntrigrams for >= 3 and so on \n(if you need a program to help decipher a < 4 letter caesar cipher RIP)") mode = input("Enter Mode: ") mode = mode.strip().lower()
if mode == '1': file_name = "ngrams/english_monograms.txt" elif mode == '2': file_name = "ngrams/english_bigrams.txt" elif mode == '3': file_name = "ngrams/english_trigrams.txt" elif mode == '4': file_name = "ngrams/english_quadgrams.txt" else: print("Make sure input is correct") exit()
return nGramInfo(file_name)
def substitution(ciphertext_only_letters, key): plaintext = "" for letter in ciphertext_only_letters: if letter.isalpha() == True: plaintext += key[ord(letter) - ord("a")] else: plaintext += letter
return plaintext
if __name__ == "__main__": main()
15 notes
·
View notes
Text
Hack This Site - Forensics #2
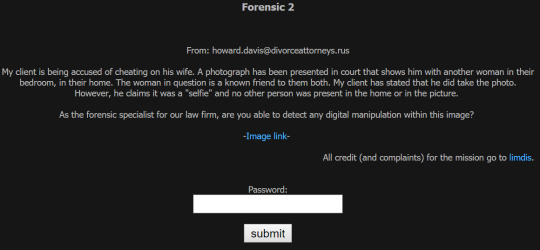
This one here is quite interesting in the sense that we have to determine if an image has been digitally modified. The image we’ve been given is below; looking at it from a distance nothing seems too obvious and stands out. If you zoom in on the edges of the woman they look a bit dodgy but we need to prove this more definitively.

I looked into some of the techniques you can use for determining modification of an image - one of them is known as “error level analysis”. The idea behind it is that if another object has been “photoshopped” into an image, there will be different compression artifacts in different sections of the image. For example, if the image of the woman was extracted from a higher resolution image, you would be able to distinguish this when it is compressed to be added to the selfie above. There is actually a pretty cool forensics tool online at www.fotoforensics.com to do this:

You can see in the ELA how she was clearly cropped into the image and conveniently enough the password appears to be written in the top left corner, “ELA4LIFE!!”
6 notes
·
View notes
Text
Something Awesome Update 8b
My personal notes:
His keystrokes were fairly straight forward. I asked my cousin, Matthew, to accelerate what he would normally do on his computer to compensate for the minimal time on the computer allowed. For this reason, there are far less variety in keystrokes than expected.
I noticed in general that due to the prevalence of Youtube and websites in general that his keyboard was not being used for much in his general like. Although I could take note of specific tastes like “Monster vs Robot” and “Riddles”, these keystrokes did not nearly capture the scope the content he was watching - mainly through clicking on new videos that were recommended and click navigating on roblox/fortnite.
Analysis of the keys logged from a 7 year old from an attacker:
Again I asked my sister to give some points of analysis and she had guessed it was one of my cousins. Below are her points:
blastedemasta is a username probably???
w keys are probably from a game. Minecraft/fortnite/roblox?
everything else is youtube
Analysis of the analysis:
All the guesses were accurate. Blastedemasta my younger cousins username on Fortnite and he logged on and played a game. It was when he died that I asked him to use his keyboard in different ways (probably skewing the data). Surprisingly it ended up with my cousin on youtube, not exactly giving much anyway. The w keys were indeed from Fortnite which he died not as quickly as I thought he would. Finally, last of the entries were indeed off of Youtube. Again unfortunately, it was all Fortnite and riddles.
Letter Frequency
This is likely not useful whatsoever, but here is the data. All the fortnite key entries were taken out.

Here are the numbers:

Some interesting notes:
“t” is extremely low, at 8th place. and “a” is at 7th place
“e, i, r, o, p, s” are the frequent letters
“j, q, x” saw no instances
4 notes
·
View notes
Text
Something awesome - forensics research
I’ve had no previous experience with forensics challenges in CTFs so I have compiled a list of (hopefully) useful concepts that people like me could use before starting some of the challenges:

Files and the File System
A file system is a like an index for all the files in your computer system! You can find a reference to all the files in your computer. File Systems have a lot of different parts but the main ones include:
Files
Files are used to store data and have two parts:
A ‘Filename’ or the name used to refer to the file
A ‘type’ or the kind of data that is stored in the file.
A file consists of blocks, which is the smallest part of the data that is stored in memory. The header block contains the starting point of the file whereas the footer block contains the end point of the file.
Directories
Directories are collections of files grouped together in some way. You can think of these as folders, as we have explored earlier in this guide.
Metadata
Metadata is the data about the file itself like its length, time created and author etc. When a file is created, the data is stored at some position in memory and the filename is the reference to that data.
It is like the address of your friend’s house - the address of your friends house has nothing to do with your friends house but it is a simple way that we have come up with to remember where certain places are located. If you forget the address, your friends house doesn’t get removed. This exactly the same for files on a computer! Sometimes when you delete a file, all that is happening is that your computer just doesn’t remember where that file is stored. It probably still exists at that same memory location until you write something there again.
File Carving
File carving refers to the technique to extract data from a disk drive without having the normal file system to easily recover the files. It’s a method of recovering files when there is no reference to them in the computer and is mostly used to recover deleted files.
This is made possible because when a file gets deleted, the data doesn’t get deleted - just the reference to that data. Another important change that happens when you delete is file is that the disk location where the file is stored gets marked as ‘unallocated’ and can thus be overwritten. However, it is possible to use techniques to recover most, if not all, of the data.
Initial analysis
When you start a forensics challenge, at first you may not have any leads and need to explore the challenge file at a high-level for a clue toward what to look at next. Below are some useful starting tips for when you’re trying to figure out the initial starting point of the question?
strings
As we discussed in our first chapter, we can use the strings command to search for all plain-text strings in the file,
Example of using strings to find ASCII strings, with file offsets:
$ strings -o screenshot.png 12 IHDR 36 $iCCPICC Profile 88 U2EI4HB
grep - use this to search for particular strings,
bgrep - use this to search for non-text data patterns,
Example of searching for the PNG magic bytes in a PNG file:
$ bgrep 89504e47 screenshot.png screenshot.png: 00000000
hexdump
A hexdump is essentially just a way for us to view data about a file or image in hexidecimal.
Example of using hexdump:
$ hexdump -C screenshot.png | less 00000000 89 50 4e 47 0d 0a 1a 0a 00 00 00 0d 49 48 44 52 |.PNG........IHDR| 00000010 00 00 05 ca 00 00 02 88 08 06 00 00 00 40 3d c9 |.............@=.| 00000020 a4 00 00 18 24 69 43 43 50 49 43 43 20 50 72 6f |....$iCCPICC Pro| 00000030 66 69 6c 65 00 00 58 85 95 79 09 38 55 5d f8 ef |file..X..y.8U]..| 00000040 da 67 9f c9 71 0c c7 41 e6 79 9e 87 0c 99 e7 39 |.g..q..A.y.....9|
Other uses of the hexdump command.
Image file formats
Image file formats are complex and can be abused in many ways that make for interesting analysis puzzles involving metadata fields, lossy and lossless compression, checksums, steganography, or visual data encoding schemes.
The easy initial analysis step is to check an image file’s metadata fields with exiftool. If an image file has been abused for a CTF, its EXIF might identify the original image dimensions, camera type, embedded thumbnail image, comments and copyright strings, GPS location coordinates, etc. There might be a gold mine of metadata, or there might be almost nothing. It’s worth a look.
Example of exiftool output, truncated:
$ exiftool screenshot.png ExifTool Version Number : 10.53 File Name : screenshot.png Directory : . File Size : 750 kB File Modification Date/Time : 2017:06:13 22:34:05-04:00 File Access Date/Time : 2017:06:17 13:19:58-04:00 File Inode Change Date/Time : 2017:06:13 22:34:05-04:00 File Permissions : rw-r--r-- File Type : PNG File Type Extension : png MIME Type : image/png Image Width : 1482 Image Height : 648 Bit Depth : 8 Color Type : RGB with Alpha Compression : Deflate/Inflate ... Primary Platform : Apple Computer Inc. CMM Flags : Not Embedded, Independent Device Manufacturer : APPL Device Model : ... Exif Image Width : 1482 Exif Image Height : 648 Image Size : 1482x648 Megapixels : 0.960
Steganography
What is steganography?
Steganography is the practice of hiding data in plain sight. Steganography is often embedded in images or audio.

You could send a picture of a cat to a friend and hide text inside. Looking at the image, there’s nothing to make anyone think there’s a message hidden inside it.
Not only messages, but you can also hide a second image inside the first.

A way we can detect if images have been hidden in other images are through online tools. This website allows you to upload an image, and either encode a hidden message into the image or decode a message previously hidden in the image.
3 notes
·
View notes
Photo

Inspired by a security briefing at work and the Google secret lab exercise from tutorials, my next infographic focuses on the continued importance of physical security even as we enter an era of increased focus on cybersecurity. The underlying thesis is that the two are nowadays interdependent. A great cybersecurity protocol is rendered useless if a hacker can penetrate the underlying physical resources of the system. Likewise, robust physical security systems increasing involve technological measures from biometric scanners to video surveillance. The four tips I gave cater to a corporate audience, based on observation of best practices that are commonly broken yet require no advanced resources to do well.
3 notes
·
View notes
Text
SA Progress 8# ~ Initial Tests (Smoke Detector Module)
This is how I was testing this module:
These are my initial test results below. Issues were:
continuous display of value 1023 (HIGH) and no significant fluctuations detected
Achieved expected curve when timer code was swapped around:

The results below show the range of values detected when the above issue was fixed (grounding issue). No significant changes were detected when a flame was placed nearby:



3 notes
·
View notes
Text
WPA3
The Wi-Fi alliance announced WPA3 in January 2018 as a replacement to WPA2. It adds four features not found in WPA2. However, most devices don’t use WPA3 yet as it is still an optional feature. As it slowly gets adopted it may be set to mandatory by the Wi-Fi alliance.
WPA3 will offer privacy on public Wi-Fi networks by using “individualized data encryption”. This means that when you connect to an open Wi-Fi, the traffic between your device and the access point will be encrypted despite not entering a password during connection. An attacker will have to crack the encryption to snoop
WPA3 will offer protection against brute force attacks. This is responding to the KRACK attack on WPA2. WPA3 defines a new handshake to prevent this.
WPA3 will offer an easier connection process to devices without displays. It was a promise to “simplify the process of configuring security for devices that have limited or no display interface”. This sounds a lot like WPS which created vulnerabilities to WPA and WPA2.
WPA3 will also offer higher security for government, defences and industrial applications. It is a feature requested by the US government for stronger encryption on critical Wi-Fi networks.
Critical infrastructure shouldn’t be connected to the internet anyway, so I don’t really understand the last feature.
3 notes
·
View notes
Text
Something Awesome
Outlined here is my intended project for the term of study:
Motivation I would like to develop well-rounded technical skills in web applications security via hacking a website. With an interest in software development, the project should give good experience in adopting an attacking mindset when developing software, and be a good opportunity to get hands on with a range of security topics. Ideally, the project will establish a solid practical skills complementing the theoretical knowledge of the course, setting good foundation towards whatever field of my interest down the road.
Skills To meet this goal, I will need to first be comfortable with navigating the Linux command line. I will need to understand the theory as well as having hands on practice covering the scope of topics of web applications. I will also need to familiarize myself with tools of the trade web application security. Finally, I can start legally hacking away on a website.
I will achieve this by: 1) Completing overthewire.org Bandit to establish familiarity with the Linux command line, blogging about each challenge. 2) Complete overthewire.org Natas to learn basic serverside security and blog. 3) Read up The Web Application Hacker's Handbook: Finding and Exploiting Security Flaws Chap1 (web application insecurity), Chap2 (Core defence mechanisms), and Chap3 (Web application technologies), with reflection blogs on each chapter. 4) Set up tools with Kali Linux and familiarize with commands, and blog about them. 5) Do CTF challenges on https://ctf365.com/ to get hands on with web app security and write reflection blogs. 6) Going further: Legally hack a website, being able to demonstrate at exploitations as listed on the OWASP top 10 vulnerabilities. Choose from https://www.cbtnuggets.com/blog/2018/08/how-to-legally-practice-your-new-hacking-skills/. Read up on "How to get started" technologies and blog. 7) Going further: Demonstrate more exploitations, choose another website, further insightful blog posts, or explore other wargames from overthewire.org
Marking criteria Blog posts should at least be weekly and should be self-evident regarding progress of the project. ○ Pass: completion of 1), 2) ○ Credit: completion of 1), 2), 3) ○ Distinction: completion of 1), 2), 3), 4) ○ High distinction: completion of 1), 2), 3), 4), 5)
4 notes
·
View notes
Text
Something Awesome - update...
While trying to fix the wires and make them look nicer, I had fried the flight controller :( and now it doesn’t work.
2 notes
·
View notes
Video
tumblr
unregistered hypercam 2
2 notes
·
View notes
Text
Something Awesome
YOOOOO it’s almost presentation time, I spend mostly this whole week making the video + finishing up the product. Also trying to find ways to attempt bonus (no mark goes there tho)
Finished VIDEO! (Pls love my skit, I tried very hard + memey)
There are few problems I ran into
Certain USB ports don’t work
Sometimes need restarting!

DIFFERENT USB TYPES

USB 3.0 faster, USB + charging (is adaptive for apple products + charge faster)!
2 notes
·
View notes
Text
Lorenz Cipher - Strengths
Large Key Space
The wheels themselves had a large number of positions to start with
The wheels from left to right had 43, 47, 51, 53, 59, 37, 61, 41, 31, 29, 26, 23 starting positions.
This provides us with 43 x 47 x 51 x 53 x 59 x 37 x 61 x 41 x 31 x 29 x 26 x 23 different positions.
16,033,955,073,056,318,658 positions
The cams/pins on each wheel could be set to on or off. There are 501 cams in total hence the total number of combinations is 2501.
2501 or
6546781215792283740026379393655198304433284092086129578966582736192267592809349109766540184651808314301773368255120142018434513091770786106657055178752
Which is an extraordinarily large number
However, in practice it is better to keep the number of “on” cams and the number of “off” cams around the same or else there could be long sections of “on” bits and “off” bits which is a cryptographic weakness.
Therefore, there would be approximately 501C250 + 501C251 different positions
501C250 + 501C251 or
466047029561172264090743443154187143022105742401083940304177233178194162944046576347002990482361149751252938782929918563029312920967516684632997872512
Another enormous number
The total will be the product of the last 2 numbers which will result in another enormous number
The thing is its just a large number of starting positions making it impossible to break through a brute force attack
Wheels have co-prime number of positions
Notice number of positions on different wheels are all co prime to other wheels.
This provides the longest possible time before patterns are repeated. This makes it more difficult to crack through analysing repeating patterns (like in Vigenère)
Used physical wires or directed radio to communicate
This made it harder to intercept the messages, particularly during the war where people were actively trying to prevent people coming into their respective countries.
For the radio signals these directed at the next receiver hence in Britain the signals were very weak.
As missing a single missing or incorrect character could make decryption impossible it required the British to employ some 600 employees just to get interpret the signals properly.
Using XOR function and a pseudo random number generator
A combination of these 2 makes it incredible hard to decipher the message provided that the number generator is highly random.
This combination makes the ciphertext invulnerable to frequency analysis.
Overall the cipher is a very safe cipher as long as the only you and the people you want to send the messages to have knowledge of the intricate workings of the cipher. After the British detected the first messages from the Lorenz cipher, they made little progress on deciphering the ciphers for almost a year. It wasn’t until a human error that spelt the end the beginning of the end for this cipher.
2 notes
·
View notes
Text
Hack This Site - Application #17
Not just from the fact that this was marked as hard, this one definitely looks difficult in the sense that our password (or key) is unique to the username. As usual we start with the Intermodular References to look for reading the console input:

We put a breakpoint on this call and then follow it up:

Here I’ve discovered a loop of sorts which will read one character at a time from the input. Following it up further we’re inside a larger loop:
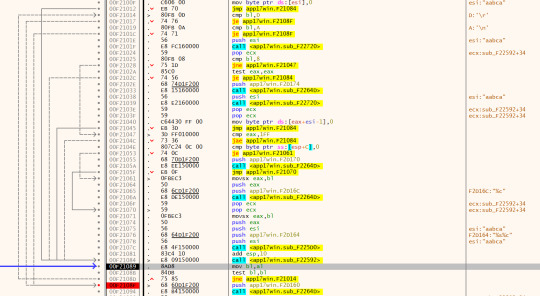
I don’t really need to know the details of this loop, except to know from debugging that we exit all the loops after pressing “Enter”. Now this returns to another function (I’ve conveniently already debugged it all and labelled):

So basically we read in the username, assembly a “Password :” string and print it, then read in a password. Then we call a function which appears to verify the password. I’ll go into the contents of this in more detail:
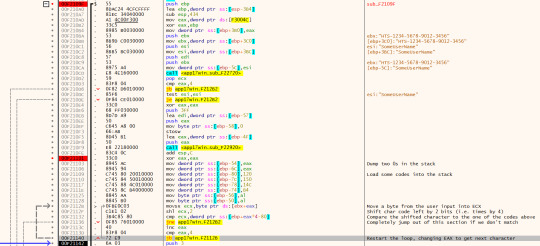
The first important thing in this function is that we are grabbing the password input and comparing the first 4 characters to a code - namely [0x120, 0x150, 0x14C, 0xB4]. This involves bitshifting the input character left by 2 first - therefore we can reverse this code by bit shifting it to the right which gives us [’H’, ‘T’, ‘S’, ‘-’]. So basically we’re just checking it is of the required format.
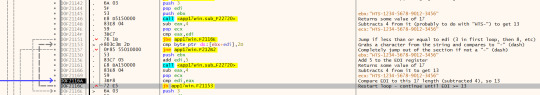
The next bit seems to be referring to the section beyond the “HTS-” in the user’s password. It seems to be expecting this length to be of 13 (based on the loop length) so passwords should be of the form “HTS-XXXX-XXXX-XXXX”. In this loop (as commented) it basically checks that the dashes are all in the correct positioning. In the next bit we are removing the dashes:
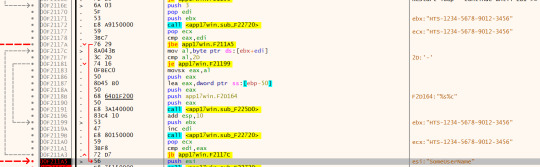
I didn’t bother commenting it as it’s easier to just observe the debugging output and see it places the resultant string after the loop:

So now we have a string with the “HTS-” and other “-” removed. Then next part I’ve gone through and debugging quite detailed:
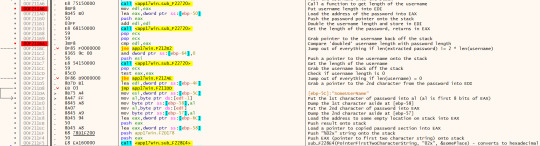
Basically we’re verifying that the extracted password (without dashes and “HTS”) is exactly 2 times the length of the username. We also check the username isn’t 0 and then extract the hexadecimal value of the first 2 characters in the given password.

The next section is quite confusing however I’ve documented what is happening alongside the assembly code. (if you want to read) I’ll try and summarise what is happening:
Start with a code of 0
Loop over the length of the username (for each i)
shl eax, cl => username[i] << (code & 0xFF)
sub esi, esx => username[i] - code
sar esi, 1 => (username[i] - code) >> 0x01
not eax => ~(username[i] << (code & 0xFF))
and esi eax => (username[i] - code) & ~(username[i] << (code & 0xFF))
Set the code to this result
ModifiedKey += Hex(Code) (2 character value)
Add the “HTS-” to front of modified key and add a “-” after every 4 characters
So basically I only really needed the first section; the second half of the above image didn’t really matter at all. In the end I implemented this in a keygen in python:
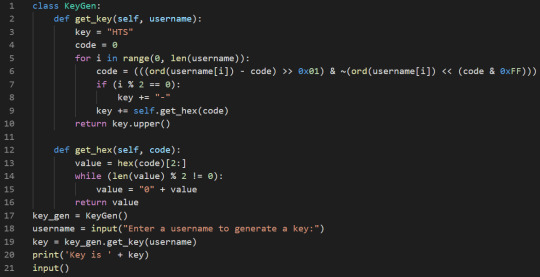
Running the program we get the following:
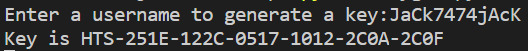
And running in the program we get the result:
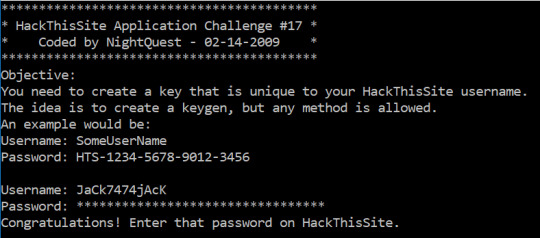
And we have completed the challenge! This one was definitely complex and took forever, however it was pretty cool to get more experience with x86 assembly.
3 notes
·
View notes
Text
Something Awesome Update 7a
KEYLOGGER ANALYSIS!!!
Minor update: I found out the best way to circumvent the voltage requirements would be to use a USB splitter which split the USB port on the host shield to 2 inputs, which were used for a USB power bank and then the keyboard itself. This seemed to provide enough power for my Ducky Shine 6 keyboard so I could truly emulate my standard behaviours on my keyboard rather than a low voltage Logitech keyboard.
This part is the fun part. For the day 19/7/2019, I plugged the keylogger into my own keyboard and did the same functions I normally would on a dead day of browsing internet and some work because I am still unwell.
The next “Keep reading” will be the full Copy paste of the keylogged. It is approx 3000 words so be warned.
t[Enter] poke[Enter] f[Enter] azumarill[Enter] bisharp[Enter] masrshadow[Enter] scolipede smogon[Enter] back back[Enter] f[Enter] omg so I had this wild dream[Enter] im dating this jenny and then artemis tries chatting mer [Back] [Back] up[Enter] carly rae jepsen is playing[Enter] shit is WILD HHAHA[Enter] y[Enter] run away with m[Enter] cats[Enter] Jesus christ boys have any of you seen this[Enter] #furrygang[Enter] woolwo[Enter] f[Enter] george column [Down][Enter] short guy anger meme[Enter] george calombaris bagel boss[Enter] it chapter 2[Enter] z5162791[Enter] [REDACTED] as[Enter] red wing[Enter] schott[Enter] prusa mk3 backspace 3 starup guide[Enter] pok[Enter] bomber[Enter] iconic[Enter] bomber[Enter] Air bomber[Enter] j stris[Enter] [Left] [Left] c [Left] [Right] [Left] [Right] [Right] [Right] [Up] [Up] [Up] [Left] c [Left] [Left] [Left] [Left] [Up] [Up] [Up] [Up] [Left] c [Up] [Left] [Left] [Up] [Left] c [Left] [Up] [Up] [Right] [Up] [Left] [Left] [Up] [Right] [Left] [Left] [Up] [Left] [Up] [Up] [Right] [Right] [Up] [Right] [Right] [Up] [Left] [Left] [Right] [Right] [Left] c [Left] [Up] [Left] [Left] [Right] [Up] [Right] [Right] [Up] [Right] [Up] c [Right] [Up] [Up] [Up] [Left] [Right] [Right] c [Up] [Right] [Right] [Right] [Up] [Right] [Up] [Left] [Right] [Up] [Up] [Right] c [Up] [Left] [Left] [Up] [Right] [Left] [Left] [Right] [Up] [Up] [Right] c [Up] [Up] [Left] [Right] [Right] [Right] c [Up] [Left] c [Up] [Left] c [Left] [Up] [Left] [Left] [Left] [Left] c [Up] [Left] [Right] [Up] [Up] [Up] [Left] [Left] [Right] [Up] [Right] [Right] [Left] [Left] [Left] [Left] [Right] [Up] [Up] [Up] [Right] [Up] [Up] [Up] [Right] [Up] [Left] [Up] [Up] [Left] [Left] [Left] c [Right] [Up] [Left] [Right] [Right] [Up] [Up] [Up] [Left] [Up] [Left] c [Left] [Right] [Left] [Up] [Left] [Right] [Left] [Up] [Right] [Right] [Right] [Right] [Right] [Right] [Up] [Up] [Left] [Left] [Right] [Left] [Up] [Left] [Up] [Up] [Up] [Left] [Left] [Up] [Up] [Right] c [Right] [Right] [Right] [Right] [Up] [Right] [Up] [Right] [Right] [Right] [Right] [Up] [Left] [Left] [Up] [Left] [Left] [Up] [Left] [Left] [Up] [Right] [Right] [Right] [Right] [Right] [Up] [Left] c [Left] [Left] [Right] [Right] [Up] [Left] [Up] [Left] [Up] [Left] [Left] [Right] c [Up] [Left] [Left] [Left] [Up] [Left] [Left] [Up] [Up] [Up] [Right] [Up] [Up] [Left] [Up] [Left] [Right] [Up] c [Up] [Up] [Right] [Right] [Up] [Right] [Up] [Right] [Right] [Up] [Up] [Up] [Up] [Right] [Left] [Left] c [Right] [Up] [Up] [Up] [Left] [Left] [Up] [Up] [Right] [Up] [Up] [Left] [Left] [Left] [Up] [Left] [Up] [Up] [Up] [Left] [Left] [Right] [Up] c [Up] [Up] [Up] [Right] [Right] [Right] c [Right] [Right] [Right] [Left] [Right] [Left] c [Left] [Up] [Left] [Left] [Right] [Right] [Right] c [Up] [Right] [Right] [Up] [Up] [Up] [Up] [Right] [Up] [Left] [Left] [Right] [Right] [Right] c [Right] [Right] [Up] [Up] [Right] c [Right] [Up] [Right] [Left] [Left] c [Left] [Up] [Right] [Up] [Up] [Up] [Left] [Left] [Up] [Left] [Left] [Right] [Right] [Right] [Right] [Up] [Up] [Up] [Left] [Up] [Left] [Right] [Up] [Right] [Left] [Right] c [Right] [Right] [Right] [Left] [Up] [Left] [Right] [Up] [Right] [Left] [Right] [Up] [Right] [Left] [Left] [Right] [Right] [Up] [Up] [Up] [Left] [Up] [Up] [Left] c [Up] [Left] [Left] [Up] [Left] [Left] [Right] [Up] [Up] [Up] c [Left] [Up] [Left] [Right] [Right] [Up] [Right] [Right] [Up] [Right] c [Up] [Up] [Up] [Left] [Left] [Up] [Up] [Up] [Up] [Up] c [Right] [Left] [Up] [Left] [Right] [Left] [Right] [Up] c [Up] [Left] [Left] [Up] [Right] [Up] [Right] [Up] [Up] [Up] [Up] [Right] [Up] [Right] [Right] c [Up] [Left] [Left] [Right] c [Right] [Up] [Up] [Left] [Left] [Right] [Up] [Right] [Right] [Right] [Left] [Up] c [Left] [Left] [Left] [Up] [Right] [Up] [Right] [Up] [Right] [Left] [Right] [Left] [Left] [Right] [Right] [Left] [Left] [Right] [Up] [Right] c [Up] [Right] [Left] [Right] [Up] [Right] [Left] [Left] [Right] [Up] [Up] [Left] [Left] [Right] c [Up] [Left] [Left] [Left] [Up] [Left] [Up] [Right] [Right] [Right] [Right] c [Right] [Up] [Right] [Up] [Up] [Up] [Left] [Right] [Up] [Up] [Up] [Right] [Right] [Up] c [Right] [Up] [Right] c [Up] [Up] [Up] [Left] [Left] [Up] [Right] [Right] c [Right] [Left] [Up] [Up] [Up] [Up] [Right] [Right] [Right] [Right] [Left] [Up] [Right] [Left] [Right] [Right] [Right] c [Left] [Left] [Up] [Up] [Up] [Left] [Up] [Right] c [Left] [Left] [Up] [Up] [Up] [Up] [Right] [Up] [Up] [Up] [Right] c [Left] [Up] [Left] [Left] [Up] [Left] c [Up] [Left] [Left] [Up] [Left] [Up] [Left] [Left] [Left] [Up] [Left] [Left] [Right] [Up] [Up] [Left] [Right] [Up] [Left] [Up] [Up] [Left] [Up] [Left] [Up] [Left] [Up] [Left] [Left]
[Left] [Left] [Left] [Right] c [Right] [Right] [Right] [Right] [Left] [Left] [Left] [Left] [Up] [Left] [Left] c [Left] [Up] [Right] [Left] [Left] [Right] [Left] [Up] [Right] c [Up] [Up] [Right] [Up] [Up] [Up] [Up] [Right] [Right] [Right] c [Left] c [Up] [Up] [Up] [Left] c [Up] [Left] c [Left] [Up] [Left] [Up] [Up] [Right] [Left] [Up] [Up] [Up] [Left] [Up] [Left] c [Up] [Right] c [Right] [Up] [Left] [Left] [Up] [Left] [Right] [Left] [Left] [Right] c [Right] c [Up] [Up] [Left] [Up] [Left] [Up] [Up] [Up] [Right] [Up] [Up] [Right] [Up] [Up] [Left] [Up] [Right] [Right] c [Right] [Up] [Up] [Right] [Up] [Right] [Left] [Left] [Up] [Right] [Right] [Left] [Up] [Left] [Left] [Up] [Left] [Right] [Up] [Up] [Up] [Left] [Up] [Up] [Left] c [Left] ¯ [Left] [Up] c [Up] [Right] [Up] [Left] [Up] [Left] [Left] [Left] [Up] [Up] [Up] [Left] [Left] c [Up] [Left] c [Left] [Up] [Left] [Left] [Left] [Up] [Up] [Up] [Left] [Left] [Up] [Left] [Left] [Left] [Up] [Right] [Up] [Up] [Left] [Right] [Left] [Up] c [Right] [Left] [Right] [Right] c [Up] [Left] [Left] [Right] [Up] [Up] [Left] [Right] [Up] [Right] [Right] [Left] [Right] [Up] [Up] [Right] c [Right] [Up] [Right] [Up] [Right] [Up] [Right] c [Right] [Up] [Up] [Right] [Up] [Right] [Right] c [Right] c [Up] [Right] c [Left] [Left] [Up] [Left] [Left] [Right] [Right] c [Right] [Up] [Right] [Right] [Right] [Right] [Up] [Up] [Up] [Up] [Left] [Left] [Up] [Left] [Right] [Up] [Right] c [Up] [Left] [Up] [Up] [Up] [Right] [Right] [Right] [Right] [Up] [Up] [Left] [Right] [Right] [Right] [Up] [Up] [Up] [Right] [Left] [Left] [Right] [Up] [Up] [Up] [Up] [Left] [Up] [Up] [Left] [Down] [Left] [Right] [Right] [Up] [Left] [Up] [Right] [Up] [Left] [Left] [Up] [Up] [Up] [Right] [Up] c [Right] [Up] [Right] c [Up] [Left] [Left] [Up] [Right] [Right] [Left] [Right] [Up] [Left] [Up] [Left] [Left] [Right] [Right] [Right] [Right] [Up] [Up] [Up] [Left] [Up] c [Up] [Left] [Left] [Up] [Up] [Up] [Left] [Up] c [Up] [Left] [Up] [Left] [Left] [Up] [Right] [Right] [Right] [Left] [Left] [Right] [Up] [Up] [Right] [Up] c [Up] [Up] [Left] [Left] [Up] [Left] [Right] [Left] [Left] [Right] [Left] c [Right] [Right] [Right] c [Right] [Up] [Up] [Right] c [Left] [Up] [Up] [Left] [Left] [Right] c [Up] [Up] [Left] [Left] [Left] [Up] [Up] c [Left] [Right] c [Right] [Right] [Right] c [Right] [Up] [Right] [Left] c [Left] [Right] [Up] [Up] [Up] [Up] [Up] [Up] [Up] c [Left] [Up] c [Left] [Up] [Left] [Right] [Up] [Left] [Right] [Up] [Right] [Right] [Right] [Up] c [Right] [Up] [Left] [Up] c [Left] [Up] [Up] [Left] [Right] [Right] [Up] [Up] c [Right] [Up] [Up] [Up] [Left] [Up] [Left] c [Up] [Right] [Right] [Left] [Up] [Left] uni[Enter] nipsey[Enter] run away with me[Enter] f [Enter] cv [Enter] hey a [Back] yall do this for the engeri [Back] engineering faculty, it tk [Back] akes like 2 minutes [Enter] Vincent MaiComputer ScienceDirector2@df [Back] folo [Back] lowing up [Back] , do you stilln [Back] ne [Back] need the invoice? I require the name [Enter] kartana [Enter] f [Enter] catch me on dic [Back] scord chati [Back] ting up artmi [Back] [Back] emis [Enter] pok [Enter] schott [Enter] f [Enter] icon [Enter] password hc06 [Enter] change [Enter] fpassword swellow cats trailer analysis [Enter] danmurphys [Enter] plantation [Enter] buffalo trace whiskey [Enter] review [Enter] salamence [Enter] twitter account deleted s [Back] tweets from blocked account? [Enter] [Back] recovery [Enter] [Back] [Enter] prusament buy aus [Enter] [Back] [Right] [Back] plyalchemy elixie [Back] r [Enter] thunderbirds [Enter] modern [Enter] thunderbird [Enter] 2000s [Enter] thunderbirds 2004 [Enter] [Right] [Right] [Right] poke [Enter] f [Enter] on that real shit ate [Back] [Back] ye [Enter] ar [Back] mals [Back] do [Enter] ung [Back] fex [Back] a [Back] zabt oijenib [Back] smogon [Enter] f [Enter] ®®®®®®®®®®®®®q [Back] w [Back] av [Back] [Back] a [Back] b [Back] c [Back] d [Back] e [Back] f [Back] g [Back] q [Back] w [Back] e [Back] r [Back] t [Back] y [Back] u [Back] i [Back] o [Back] p [Back] l [Back] k [Back] j [Back] jh [Back] h [Back] [Back] hg [Back] [Back] g [Back] f [Back] f [Back] d [Back] ds [Back] a [Back] [Back] a [Back] z [Back] x [Back] c [Back] v [Back] b [Back] n [Back] m [Back] Email Physi [Back] [Back] [Back] ishingFun fact, I'm doing this activityb [Back] [Back] while my something awesome keylogger is active. [Enter] Stp [Back] ep 1 [Back] [Back] [Back] [Back] [Back] [Back] Target informaton [Back] [Back] [Back] ion [Enter] b David Quest: [Enter] [Tab] - [Back] [Back] hjh [Enter] [Back] [Back] [Back] [Back] bullet points tm [Back] umblr [Enter] bb [Enter] [Back] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Back] [Enter] awd [Back] [Back] [Back] Email: v [Enter] Operations officer/manager [Back] [Back] mag [Back] [Back] nager (or equivalent role) [Enter] 2 black pugs [Enter] hips [Back] h [Back] Hipster (bowit [Back] [Back] tie and beard aesteh [Back] [Back] hetic) [Enter] Sarah Jenkins: [Enter] 3 yr old son James -> born 1 [Back] 2nd Decm [Back] ember 2012 [Back] 4 [Enter] Husbane [Back] d David- [Back] -> [Right] [Right] [Left] [Up] [Up] [Left] [Left] [Up] [Up] [Up] [Right] [Left] [Left] [Up] [Left] [Right] [Right] [Left] [Left] [Up] [Left] [Up] [Left] c [Left] [Up] [Left] [Left] [Up] [Left] [Left] [Left] [Up] [Right] c [Left] [Right] c [Left] [Up] [Left] [Right] [Left] [Right] [Up] c [Up] [Up] [Up] [Right] [Left] [Left] [Up] [Left] [Right] [Right] [Right] c [Right] [Up] [Up] [Left] [Right] [Right] c [Up] [Up] [Left] [Left] [Up] [Left] [Right] [Up] [Up] [Up] [Right] [Up] [Right] [Down] z [Right] c [Up] [Up] [Right] c [Up] [Right] [Left] [Right] [Right] [Right] [Up] [Up] [Up] c [Right] [Right] [Right] [Up] [Right] [Up] [Right] [Up] [Up] [Up] [Left] [Right] [Up] [Right] [Left] [Up] [Right] [Left] [Left] [Up] [Up] [Right] [Left] [Left] [Left] [Left] [Up] [Up] [Up] [Left] [Left] [Left] c [Up] [Right] [Up] [Up] [Up] [Up] [Left] [Up] [Left] [Up] [Up] [Left] [Left] c [Left] c [Left] [Up] [Left] [Left] [Up] [Left] [Left] [Left] [Left] [Up] [Left] [Left] c [Left] [Left] [Up] [Left] [Up] [Left] [Left] [Left] [Up] [Up] [Right] [Right] c [Right] [Up] [Right] [Right] [Right] [Right] [Up] [Right] [Up] [Up] [Up] c [Left] [Up] [Up] [Up] [Right] [Right] [Right] [Up] [Up] [Up] [Right] c [Right] [Right] [Right] [Up] [Left] c [Right] [Right] [Up] [Right] [Right] [Up] [Right] [Right] [Up] [Right] [Right] [Right] c [Up] [Up] [Up] c [Right] [Right] [Right] [Up] [Left] [Up] [Right] c [Up] [Left] [Right] [Up] [Left] [Up] [Right] [Up] [Left] [Up] [Up] [Up] [Left] [Up] [Right] c [Up] [Left] [Left] [Up] c [Left] [Left] [Right] c [Up] [Up] [Up] [Left] [Left] [Left] [Right] c [Right] [Up] [Left] [Up] [Up] [Up] [Left] [Up] [Up] [Up] [Right] [Up] [Right] [Right] [Left] [Up] [Left] [Up] [Left] [Left] [Left] [Up] [Left] [Up] [Up] [Up] [Right] [Right] [Up] [Left] [Right] [Right] [Up] [Right] [Right] [Left] [Up] [Up] [Up] [Right] [Up] [Left] [Up] [Left] [Left] [Right] [Left] [Right] [Right] c [Right] [Right] [Right] [Up] [Up] [Up] [Right] [Left] [Right] [Up] [Right] [Up] [Left] [Up] [Up] [Left] [Right] [Up] [Left] [Left] [Up] [Left] [Left] [Left] [Left] [Up] [Up] [Up] [Right] [Right] [Up] [Up] [Left] [Right] c [Up] [Up] [Left] [Up] [Left] [Right] [Left] [Up] [Left] [Left] [Up] [Left] [Right] [Left] [Left] [Right] [Right] [Left] c [Left] [Right] [Left] [Left] [Up] [Left] [Left] [Up] [Up] [Left] [Up] c [Left] [Up] [Left] [Right] [Left] [Up] [Up] [Left] [Right] [Up] [Up] [Up] [Left] c [Left] [Left] [Up] [Left] [Up] [Up] [Up] [Left] [Up] [Up] [Up] [Right] [Left] [Up] [Left] [Up] [Left] [Right] [Left] [Up] [Right] [Up] [Right] c [Left] [Left] [Right] [Right] [Up] [Right] [Right] c [Right] [Right] c [Right] [Right] [Right] c [Up] [Up] [Right] [Up] [Right] [Up] [Right] [Right] [Up] [Up] [Up] [Right] [Right] [Right] [Right] [Up] [Up] c [Right] [Up] [Right] [Right] [Right] [Right] c [Up] [Left] [Left] [Left] [Right] c [Up] [Up] [Up] [Right] [Left] [Up] [Up] [Right] [Up] [Right] [Right] c [Right] [Up] c [Left] [Up] [Up] [Left] [Up] [Left] [Left] [Up] [Left] [Right] [Up] [Left] [Up] [Right] [Up] [Left] [Up] [Up] [Left] c [Left] [Up] [Left] [Up] [Right] [Up] [Right] c [Right] [Left] [Right] c [Up] [Left] [Right] [Right] [Right] [Up] [Up] [Up] [Left] [Left] c [Up] [Up] c [Right] [Left] [Right] [Up] [Up] [Right] [Left] [Up] [Up] [Left] [Left] [Left] [Right] [Up] [Right] [Up] [Up] [Up] [Right] [Left] [Up] [Up] [Up] [Up] [Down] [Right] [Down] [Left] [Up] [Right] [Up] [Right] [Left] [Left] [Up] [Left] c [Up] [Right] [Up] [Right] [Left] c [Left] [Up] [Left] [Right] [Left] [Right] [Left] [Left] [Right] [Left] [Up] [Up] [Left] [Up] [Left] [Left] [Right] [Right] [Up] [Right] [Up] [Right] [Right] [Right] c [Left] [Left] c [Right] [Up] [Up] [Right] c [Left] [Up] [Left] [Right] c [Up] 35 - 36? depends on time d [Back] frame on 4 June [Enter] Email: v [Enter] f [Enter] ®® Address: c v w v [Back] , [Enter] Hours: vvincent. [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] Approach: [Enter] baw [Back] [Back] [Back] My apo [Back] proach to this would be to hope [Back] [Back] [Back] [Back] [Back] [Back] impersonate a facebook employee and request their details [Back] [Back] the login information from David. [email protected] [Back] in Credn [Back] n [Back] entials G [Back] Dear David, [Enter] [Enter] We've detected some unsu [Back] [Back] usa [Back] ual activity on your facebook page and hav [Back] e temporarily disabled the page. To regain access to the page, please t [Back] send your s [Back] username and password [Back] [Back] [Back] [Back] [Back] reply with your username ndpassword, [Enter] [Enter] [Back] [Back] [Back] . [Enter] [Enter] Ta [Back] hanks [Back] , [Enter] [Enter] Vincent. [Snapshot] v v w To this I recieved [Back] [Back] [Back] [Back] [Back] [Back] eived an email from Sa [Back] [Back] saying that Sarah deals with all the o [Back] sc [Back] c [Back] oi [Back] cial media, l [Back] ty [Back] ipping me off to that [Back] [Back] e fact ta [Back] hat David likel [Back] y deals with the banking, used for act [Back] part 2. vSrah [Back] [Back] [Back] arah Hilariously [Back] So [Back] [Back] I switched up the email and add [Back] [Back] so it was addressed to s [Back] Sarah and easily, I rev [Back] ceived this. v (That was easy? [Back] !) [Enter] Part 1Approacbh [Back] [Back] h Part 2: [Enter] This time i [Back] I would send David an email abu [Back] out payments, pretending to be a niger [Back] n [Back] [Back] [Back] [Back] [Back] Nigera [Back] ian Princ. [Back] e. I'm not sure how this system works bu [Back] t I'll see if it does. [Enter] Wakanda fo [Back] [Back] ForeverVibran [Back] Vibranium Resev [Back] rves Low, nee [Back] [Back] [Back] Need Pyam [Back] [Back] [Back] aym [Back] Donations to mine [Back] d [Left] [Left] [Left] [Left] [Left] [Left] [Right] [Back] nHey David. [Back] , [Back] tchalla@wakana [Back] da.com.au [Back] Please send [Back] make a $1200 payment to vv [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] v. Wakanda needs your help. [Enter] [Enter] Thanks, [Enter] [Enter] Tchalla [Snapshot] From this i [Back] [Back] i [Back] [Back] I recie [Back] [Back] eived this sre [Back] [Back] [Back] response. [Enter] vSo I thought maybe I coul [Back] would try and onc [Back] [Back] [Back] contact hi [Back] [Back] [Back] and reply with a YE [Back] [Back] YES THIS IS URGENT AND A [Back] CANNOT WAIT. WE NEED YOU [Back] [Back] [Back] OU. [email protected] [Back] org.au [Tab] tchalla. [Back] @wakanda.com.au [Tab] C [Back] Vibranium [Tab] Hey David, Please make a payment to v. Wakanda needs your help urgently and cannot wait. [Enter] [Enter] Thanks, [Enter] [Enter] Vincent. Surprinsl [Back] [Back] [Back] sign [Back] [Back] ngly it works [Back] ed. I'm guessing this activity f [Back] goeso [Back] off of key [Back] [Back] [Back] [Back] series of key words/phrases and synonyms? [Enter] v [Back] DI did a bit o [Back] f experimenting and I didn't [Back] U [Back] d [Back] u [Right] [Back] [Back] i [Right] [Right] [Back] D [Right] [Right] [Right] [Right] [Right] [Back] . [Back] , [Right] [Right] [Enter] [Enter] I didn't [Back] don'tt [Back] think em [Back] [Back] [Back] [Back] [Back] [Back] lowercase didn't affect my results personally. [Back] LI tio [Back] [Back] hink it's b [Back] based off of a keyword ssy [Back] [Back] ystem Social Engineering is w [Back] real and [Back] [Back] Lowercase oer [Back] [Back] [Back] personally didn't [Back] [Back] [Back] [Back] [Back] dLowec [Back] rcae [Back] se didn't adde [Back] [Back] [Back] ffect [Back] seem ot [Back] [Back] to affect the ne [Back] [Back] ames (Davi [Back] d and Sarah) but it did affect any key words [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] thing l [Back] else you wrto [Back] [Back] ote later [Back] [Back] [Back] I wrote later. always be aware of basic principles. The flags ini [Back] d [Back] inform [Back] provide warning to use 2 Factor authentication and [Right] [Back] fbe aware thatg payment [Back] [Back] [Back] payment fa [Back] raud exists. These points of knowledge would I [Back] have most definityl [Back] [Back] l [Back] ely stopped thes [Back] [Back] is type of attack from happening. f [Enter] th [Back] e kings man [Enter] the kings man [Enter] bunnigs [Down] [Enter] wood [Enter] [Back] [Back] [Back] [Back] [Back] [Back] [Back] [Back] hinge [Enter] suicide squad [Enter] dcau [Enter] cqueer eye season 5 [Back] [Back] 5 [Back] 4 [Enter]
2 notes
·
View notes