#Signaling Firewall Market Share
Explore tagged Tumblr posts
Text
Signaling Firewall Market Size, Trends, Opportunities, Growth Analysis to 2031
The Insight Partners recently announced the release of the market research titled Signaling Firewall Market Outlook to 2031 | Share, Size, and Growth. The report is a stop solution for companies operating in the Signaling Firewall market. The report involves details on key segments, market players, precise market revenue statistics, and a roadmap that assists companies in advancing their offerings and preparing for the upcoming decade. Listing out the opportunities in the market, this report intends to prepare businesses for the market dynamics in an estimated period.
Is Investing in the Market Research Worth It?
Some businesses are just lucky to manage their performance without opting for market research, but these incidences are rare. Having information on longer sample sizes helps companies to eliminate bias and assumptions. As a result, entrepreneurs can make better decisions from the outset. Signaling Firewall Market report allows business to reduce their risks by offering a closer picture of consumer behavior, competition landscape, leading tactics, and risk management.
A trusted market researcher can guide you to not only avoid pitfalls but also help you devise production, marketing, and distribution tactics. With the right research methodologies, The Insight Partners is helping brands unlock revenue opportunities in the Signaling Firewall market.
If your business falls under any of these categories – Manufacturer, Supplier, Retailer, or Distributor, this syndicated Signaling Firewall market research has all that you need.
What are Key Offerings Under this Signaling Firewall Market Research?
Global Signaling Firewall market summary, current and future Signaling Firewall market size
Market Competition in Terms of Key Market Players, their Revenue, and their Share
Economic Impact on the Industry
Production, Revenue (value), Price Trend
Cost Investigation and Consumer Insights
Industrial Chain, Raw Material Sourcing Strategy, and Downstream Buyers
Production, Revenue (Value) by Geographical Segmentation
Marketing Strategy Comprehension, Distributors and Traders
Global Signaling Firewall Market Forecast
Study on Market Research Factors
Who are the Major Market Players in the Signaling Firewall Market?
Signaling Firewall market is all set to accommodate more companies and is foreseen to intensify market competition in coming years. Companies focus on consistent new launches and regional expansion can be outlined as dominant tactics. Signaling Firewall market giants have widespread reach which has favored them with a wide consumer base and subsequently increased their Signaling Firewall market share.
Report Attributes
Details
Segmental Coverage
Signaling Type
SS7
Diameter
Deployment Type
On-Premise
Cloud
Regional and Country Coverage
North America (US, Canada, Mexico)
Europe (UK, Germany, France, Russia, Italy, Rest of Europe)
Asia Pacific (China, India, Japan, Australia, Rest of APAC)
South / South & Central America (Brazil, Argentina, Rest of South/South & Central America)
Middle East & Africa (South Africa, Saudi Arabia, UAE, Rest of MEA)
Market Leaders and Key Company Profiles
Adaptive Mobile Security
AMD Telecom SA
ANAM Technologies
BICS
Cellusys
Cisco System, Inc.
Mobileum Inc.
Omobio (Pvt) Ltd
Openmind Networks
Symsoft (Sinch)
Other key companies
What are Perks for Buyers?
The research will guide you in decisions and technology trends to adopt in the projected period.
Take effective Signaling Firewall market growth decisions and stay ahead of competitors
Improve product/services and marketing strategies.
Unlock suitable market entry tactics and ways to sustain in the market
Knowing market players can help you in planning future mergers and acquisitions
Visual representation of data by our team makes it easier to interpret and present the data further to investors, and your other stakeholders.
Do We Offer Customized Insights? Yes, We Do!
The The Insight Partners offer customized insights based on the client’s requirements. The following are some customizations our clients frequently ask for:
The Signaling Firewall market report can be customized based on specific regions/countries as per the intention of the business
The report production was facilitated as per the need and following the expected time frame
Insights and chapters tailored as per your requirements.
Depending on the preferences we may also accommodate changes in the current scope.
Author’s Bio:
Aniruddha Dev Senior Market Research Expert at The Insight Partners
#Signaling Firewall Market#Signaling Firewall Market Size#Signaling Firewall Market Share#Signaling Firewall Market Trends
0 notes
Text

Top SEO Practices for 2024: Boost Your Website's Ranking with These Proven Technique
Amidst the ever-evolving digital terrain of 2024, achieving and maintaining a high ranking on search engine results pages (SERPs) is more crucial than ever. With ever-evolving algorithms and user behaviors, mastering SEO (Search Engine Optimization) techniques is essential for the success of any website. Here are some proven SEO practices to boost your website's ranking in 2024:
Visualize Data with Interactive Content: Move beyond traditional content formats and embrace interactive content to captivate your audience. Infographics, interactive maps, and quizzes not only convey information effectively but also encourage user engagement, ultimately boosting your website's dwell time and lowering bounce rates.
Implement Semantic SEO: With advancements in natural language processing, semantic SEO emerges as a powerful strategy in 2024. Rather than solely focusing on individual keywords, optimize your content to understand the context and intent behind user queries. By incorporating related terms and concepts, you can enhance the relevance and comprehensiveness of your content, leading to improved search visibility.
Explore Video SEO: Video content continues to dominate online platforms, presenting a golden opportunity for SEO in 2024. Create compelling video content optimized for search engines by incorporating relevant keywords in titles, descriptions, and tags. Additionally, transcribe your videos to make them accessible to search engine crawlers, further enhancing their discoverability.
Harness the Potential of Social Signals: In the interconnected digital landscape, social signals play a significant role in influencing search engine rankings. Cultivate a strong presence on social media platforms and encourage social sharing of your content. Engage with your audience authentically, fostering community interaction and signaling to search engines the value and relevance of your website.
Embrace Augmented Reality (AR) for Local SEO: As AR technology gains momentum, leverage its potential to enhance local SEO efforts. Implement AR features that provide immersive experiences for users searching for local businesses or attractions. By integrating AR elements into your website and mobile apps, you can create memorable interactions that drive foot traffic and increase online visibility.
Optimize for Zero-Click Searches: With the rise of featured snippets and knowledge panels, zero-click searches have become increasingly prevalent in 2024. Optimize your content to appear in these prominent SERP features by providing concise answers to common queries. Structured data markup and FAQ sections can also enhance your chances of securing coveted position zero.
Invest in Long-Form Evergreen Content: Long-form evergreen content remains a cornerstone of effective SEO strategies in 2024. Produce comprehensive guides, tutorials, and in-depth analyses that stand the test of time and continue to attract organic traffic long after their initial publication. By addressing complex topics thoroughly, you establish authority in your niche and earn valuable backlinks over time.
Prioritize Website Security and Performance: In an era of heightened cybersecurity concerns, website security and performance are paramount for both user experience and SEO. Secure your website with HTTPS encryption, implement robust firewalls, and regularly update software to mitigate security risks. Additionally, optimize your website's performance by minimizing loading times and optimizing images and other media assets.
Collaborate with Micro-Influencers: Influencer marketing evolves in 2024, with a shift towards micro-influencers who boast niche audiences and high engagement rates. Partner with micro-influencers relevant to your industry or target demographic to amplify your brand's visibility and attract quality traffic to your website. Encourage influencer-generated content that resonates with their followers and aligns with your SEO objectives.
Conclusion:
By implementing these top SEO practices in 2024, you can elevate your website's ranking, attract more organic traffic, and achieve your business goals. Remember, SEO is not a one-time task but an ongoing journey of optimization and refinement. Embrace innovation, stay informed, and continuously refine your strategies to maintain your competitive edge in the digital marketplace. As the digital landscape evolves, partnering with Info Hub Digital emerges as the definitive choice for businesses seeking unparalleled SEO expertise. As the best SEO service provider in India and US, Info Hub Digital offers tailored solutions that propel brands towards digital success. With a commitment to innovation and excellence, Info Hub Digital empowers businesses to thrive in the dynamic realm of AI-driven search
INFO HUB DIGITAL
105-B, Space-31,
Khadi Machine Chowk, Kondhwa, Pune, Maharashtra 411048
Visit Us : www.infohubdigital.com
Email Us : [email protected]
Our Social Presence :
Linkedin - https://www.linkedin.com/company/info-hub-digital/?viewAsMember=true
Facebook - https://www.facebook.com/infohubdigital
Instagram - https://www.instagram.com/infohubdigital/
Twitter - https://twitter.com/InfoHub_Digital
#2024 SEO techniques#interactive content SEO#semantic SEO strategies#video SEO best practices#social signals SEO#SEO trends 2024#SEO best practices#SEO for high SERP ranking#best seo service in india and usa#best digital marketing company in india and usa#social media marketing company in india and usa#best digital marketing service in inida and usa#best digital marketing agency in inida and usa
0 notes
Text
The Joker x Reader - “A.N.N.I.E.”
A.N.N.I.E. (Artificial Non-Neurological Intelligent Entity) is an outdated android model that emerged on the market two years ago. The Joker purchased her as a toy for his son not knowing she will become the recipient of desperate attempts to keep Y/N with him. After the woman’s unexpected death, experiments meant to transfer her conscience inside Annie failed yet The King of Gotham couldn’t part with the only thing that reminded him of someone he actually cared about.

“Can you fix her?” The Joker asks the two programmers that have been assessing the android for the past 15 minutes.
“Hard to tell sir, but we are trying to determine what triggered the malfunction,” Zariah points at the 4 laptop screens simultaneously running diagnostics. “Recently there’s been a spike in flaws regarding A.N.N.I.E. models; after all they were released 2 years ago. I would recommend acquiring the most current technology…”
“No need to!” J bitterly cuts him off. “Just fix her!”
“We will do our best, sir!” Mickel reassures The King of Gotham: his wretched temper might interfere with today’s agenda and the two hackers simply can’t afford it.
“Your best is not enough,” The Joker growls. “She cornered my son last night and almost crushed him against the wall. I had to use manual override to shut her down. That’s not typical machine behavior, is it?!”
“No sir, although I’ve heard of similar incidents in the past months. If it continues, Annie prototype will be pulled off the market soon,” Zariah informs.
“Her name‘s not Annie,” The Clown Prince of Crime interrupts the unwanted advice. “Her name’s Y/N!”
Awkward silence and Kase’s voice resonates from upstairs.
“Daddy?... Daddy?...”
“My son’s awake; I’ll be back,” J abandons the two men in a hurry and stumbles on the numerous cables connecting the laptops to the cyborg on his way out.
“Goddammit!”, he huffs through his clenched teeth before vanishing around the corner.
“That was fucking weird,” Mickel whispers. “What does he means her name is not A.N.N.I.E.?! Am I crazy? Is this not Artificial Non-Neurological Intelligent Entity sitting in that chair?!”
“Of course it is,” Zariah confesses in low tone. “He gives me the creeps too how he thinks she’s in there.”
“What do you mean “she”?” the obvious question follows.
“Check those cords,” Zariah urges and continues: “You noticed he corrected me with the name for the pile of rubbish.”
“Yeah,” the other guy begins typing a bunch of configurations while listening to the scoop.
“Y/N used to take care of his kid. Nobody can say who she really was: some believe she might have even been the mother, that her and Mister Joker were together. Others swear the little boy called her auntie; maybe she actually was Mister J’s sibling. Who the hell knows? She was a strange woman and she looked… different also,” Zariah’s gaze circles the premises to make sure their employer is not eavesdropping.
“No shit!” Mickel frowns at the statistics popping up on the monitors.
“Yeah, I saw her a few times, gave me the creeps. Something was off with her, you just could tell. Mister J always had jerks working for him and I guess they clashed with Y/N quite often: it got so bad they dared planning a prank that ended horribly. Do you know the warehouse on 14th street? The 6 stories one?”
“No.”
“Well, supposedly it happened there: Mister J was out of town and had no clue about the scheme plotted without his consent. The crew took his son on the roof and threatened they will toss him off the building if she doesn’t jump instead.”
“And?!” Mickel halts his typing, intrigued.
“She jumped… … they didn’t think she would.”
“Holy crap! I had no idea!”
“Dude, it was a disaster!” Zariah shrugs depicting the facts. “Y/N splattered all over the concrete, broken to pieces… Despite the severe injuries, she didn’t die immediately: she was in a coma for almost a month before passing away. Mister J had Annie already, he probably bought her as a toy for Kase when it first emerged on the market. The rumor is that while Y/N was in a coma he kidnapped scientists and forced them to work on a senseless project: transferring her conscience inside Annie.”
“You’re shitting me!” Mickel exclaims at the insane disclosure.
“Nope.”
“Can’t be done; it’s impossible!”
“And who’d dare explain the obvious to him, huh? Not the researchers he killed the moment she stopped breathing if you get my drift.”
“That’s messed up!” Mickel forcefully exhales, infinitely more nervous about being at The Penthouse for the moment.
“Do you remember the serial murders that shook Gotham 3 months ago?” Zariah has more gossip for his partner. “It was Mister J hunting down every single person that was on the roof the day Y/N jumped.”
“We shouldn’t be here,” the anxious Mickel shrugs. “Maybe we should abandon our mission.”
“Bulshit! They’ll pay us double over anything he offers so don’t be a pussy! Speaking of, you should assemble the guns prior to his return!”
Mickel is reluctant to the whole scenario, yet he compiles the two guns out of items resembling computer parts scattered in their suitcases: that’s how they were able to deceive security.
“Done,” he stashes one finished weapon under his jacket, offering the other to Zariah.
“Remain calm and we’ll be ok,” the latest mumbles. “Let’s pretend we’re here to repair this junk.”
A couple more minutes pass by and The Joker’s presence alongside his offspring makes the two guys cringe.
The little boy hides behind his father’s legs, shyly glancing the android’s way.
“Don’t be scared,” J grumbles. “She’s in power saving mode, it’s fine.”
“Yes, it’s perfectly safe,” Zariah winks. “We are almost done extracting all the data,” he gestures at the laptop’s screens.
Kase giggles and rushes to climb on Annie’s knees, excited to see her after she wasn’t allowed to sleep in his room last night which is understandable since the robot went bonkers.
“Hi Y/N,” the child softly pulls on her long hair. “I want waffles pwease.”
The hackers exchange meaningful glares and The Joker replies:
“She can’t for now,” he mutters. “She’s defective. Frost will take you out for breakfast, alright?”
“Does it hurt?” the 5 year old pouts at his parent’s affirmation: he doesn’t comprehend all the words and it’s difficult for a kid to process the concept of transference.
After Y/N died, The Joker told Kase she moved inside Annie: he wasn’t delusional about his failed experiment but it was easier to make his son cope with the loss of the woman that raised him. J doesn’t literally believe there’s any trace of Y/N in the machine: how could it be? Several months passed and nothing proved what he tried to accomplish succeeded: a twisted concept originating from a distorted mind was doomed from the start.
“It doesn’t hurt,” The Clown Prince of Crime sighs. “She’s resting.”
“Sir, I think you should see this,” Mickel gets his attention.
“What am I looking at?”
“You used voice command to lock down the android?” Zariah pinpoints at the monitor to his left.
“I did.”
“That’s not what turned off the system: see the numbers flowing borderline with the central matrix, the tiny squares? She wasn’t locked down by external command, she was terminated from within.”
“What do you mean?!” Mickel scoots over in his rolling chair, baffled.
“Somebody trespassed the firewall,” his accomplice utters the obvious.
J is less than happy with the random discovery still he requires confirmation of his suspicion.
“Meaning?”
“Annie, I mean Y/N is the recipient of a cyber-attack: she’s been hacked.”
“Hacked?” J scoffs. “What for? She’s just a companion android, it doesn’t make any sense.”
“Not sure, sir…” Zariah lifts his shoulders up, baffled.
“Can you find the source?” the green haired individual suggests.
“Analyzing the algorithm shows puzzling results: these numbers should be repeating themselves every so often, yet they don’t; never seen anything like it and I’ve been dealing with computers for a long time,” Mickel adds. “The most interesting detail is certainly challenging our expertise: tracking the root of the signal is pretty much unachievable. We should see input bouncing around from different servers because this is how hackers disguise their trail; but… this particular livestream happened simultaneously from various servers around the country.”
“There’s practically 0% chance for such abnormal hacking with today’s technology!” Zariah scrunches up his face at the baffling discovery. “How in the world was it done?!”
“You’re the experts!” The Joker barks. “I hired you based on strong recommendations from others that used your skills. Can you fix her or not?!”
“Of course, sir.”
“Yes!” the two associates ease The Clown’s doubt. “We’ll unplug the cables, we already removed all necessary info.”
Kase watches them detach the cords from Annie’s access ports, the child sulking at their action.
“Y/N, does it hurt?” he asks and hops off her lap. The empty shell doesn’t respond since the robot is in power saving mode.
“It doesn’t hurt,” The King of Gotham duplicates his earlier statement. “Frost!” he addresses the henchman entering the living room. “Take him to our restaurant on Madison Avenue for breakfast then he can play at the property on Foster Creek until we are done here. I want a 3 cars escort.”
“Yes, boss. I’ll call in advance and tell them not to open the place until we’re done.”
“Good,” J agrees with his henchman’s proposal. “Kase, go and eat!” he urges the offspring having a few more secrets to share with Annie. “Come on, let’s go!” the impatient father encourages.
The 5 year old obeys and kisses Annie’s cheek, whispering:
“I’ll bwing you beck’fast auntie, ok?” and he rushes at Frost’s side screaming up a storm. “Byeeeee daaaaaddy!!!”
The programmers are so absorbed by the mystifying enigma they stumbled upon by accident they don’t pay attention to the little nugget’s promise: even if they would, Zariah and Mickel wouldn’t be able to untangle the convoluted riddle of Y/N’s true identity.
She wasn’t The Joker’s girlfriend nor Kase’s mother: Y/N was nothing less than The Clown’s younger sister.
The woman protected the only family she had like a hawk, thus she didn’t hesitate to give her life in exchange for her nephew’s.
Too bad she had no idea those jerks were mocking her when she ended up on that accursed roof.
Too bad her brother didn’t guess their intentions and extremely regrettable he was left alone without the only person he ever trusted.
Too bad she died granted J’s desperate efforts to keep her with him.
And so sad he didn’t know how much Y/N meant to him until she was gone.
“Isn’t it weird someone breached my android in the same time it was malfunctioning and closed her down?…” J stares outdoors on the terrace. “Why would anyone go through the trouble?... What’s the purpose?”
The familiar click of safety being taken off a gun awakens The Joker from apathy and he turns around: it’s not easy to surprise J but he’s stunned to notice the two experts he recruited pointing guns at him.
“What the fuck are you doing?!”
“Cashing in a huge payday, sir,” Zariah sneers. “It’s not often you become a legend for murdering…”
The Joker is not listening, his attention diverted by the strange phenomenon occurring behind the two hackers threatening his life: Annie is standing up from her chair and that’s clearly not possible; she is in power saving mode!
The android grabs Mickel’s arm and twists it to 90 degrees, using his own pistol to blow his brains out. Before Zariah can react he’s knocked to the ground with such violence J starts backing out, unsure on what to do when Annie steps on the man’s neck.
The sound of fractured bone plus the cyborg’s attention clearly directed towards him now makes him shout:
“Code 71345, emergency override!”
“Access denied!” the robot approaches still calibrating its joints and electronic synapses.
What the hell is wrong with this thing?!
“Code 71345, emergency override!”
”Access denied!”
J wants to make a run for it but he’s aware Annie is faster; why is she glitching like this?!
“Code 71…”
“Why are you trying to shut me down when I tried so hard to come back to you?” the cold voice halts the rest of his sentence.
The Joker takes a strenuous breath, dumbfounded at the shocking revelation:
“Y/N?... … Is… is… that you?!... …”
The android tilts its head to the left while an eerie smile flourishes on the plastic lips:
“Missed me?”
Also read: MASTERLIST
You can also follow me on Ao3 and Wattpad under the same blog name: DiYunho.
#the joker x reader#the joker fanfiction#the joker imagine#the joker jared leto#the joker suicide squad#the joker#joker#joker jared leto#joker suicide squad#dc#mister j#Mistah J#dcu#jokerleto
54 notes
·
View notes
Text
What is Antivirus? “The Definition and Popular 5 examples”
What is Antivirus?
“The Definition and Popular 5 examples”
Antivirus
Computer viruses share many similarities with real-life viruses, which is why they were named. However, while the flu season begins in late fall and ends in February, the computer virus season is in full swing throughout the year. To protect your body from viruses, you only need to get vaccinated once a year, at the beginning of the flu season.
What is antivirus software?
When you run a virus scanner, your antivirus program will scan your hard drive and all currently connected storage devices for potential threats. The program will inspect each file individually and simultaneously search its database for known viruses for a possible threat. Doing so, depending on the severity of the threat, will either delete, quarantine, or repair the infected file. The program will also monitor the behavior of all the software on your computer for any alarm signals.
Whereas in the past you had to scan manually, most antivirus programs today allow you to run automatic scans and program controls to best suit your needs. As a rule, it is recommended to perform an automatic scan every week. In addition, you can also perform manual scanners on your computer, and also on specific files and directories. Antivirus scanners are designed as background processes, which means they shouldn't use up a lot of your computing resources or slow down your computer.
As computer viruses are a constant threat on all platforms, today's antivirus software is designed to offer protection on all operating systems and all devices connected to the internet. This includes desktop and laptop computers that use Microsoft Windows and macOS, as well as smartphones that use iOS and Android. Statistics show that more than 360,000 malware components are released every day. For maximum security, the best antivirus software will also automatically update virus definitions at least once a day.
What types of antivirus software are there?
All antivirus programs are of following three categories:
Standalone antivirus software
Standalone antivirus software is a specialized tool, designed to detect and remove certain viruses. It is commonly known as portable antivirus software because it can also be installed on a USB stick and can be used by administrators to perform emergency scans of an infected system. However, most portable programs are not designed to provide real-time protection and download new definitions daily, which is why they cannot replace internet security packages that include a large variety of extras.
Total Security software packages
As the title indicates, security software packages are more than antivirus programs. In addition to being able to detect and remove viruses, they are also equipped to fight all other spiteful software and provide absolute protection at all times for your computer and files. Most of these software packages include antispyware, firewalls, and parental control components. Some also include an additional feature like password management, VPN (virtual private network), and even a standalone antivirus program built into the package.
Antivirus software in the cloud
Cloud Antivirus Software is a new type of antivirus technology that scans your files in the cloud instead of on your computer, in order to free up your computing resources and allow a faster response. These programs are normally made up of two parts; the client that is installed on your computer and performs periodic virus and malware scanners, without taking up too much memory, and the web service that processes the data collected by the client and inspects it for matches with viruses and malware from its database.
Popular Antivirus Software Examples
With millions of active viruses and harmful programs costing the global economy millions of dollars in losses each year, it is not surprising that there are a large number of antivirus programs available on the market. They are different in terms of price, the platform for which they are designed, functionality, as well as additional components.
Some of the best antivirus programs currently available include the following:
Bitdefender
Bitdefender Total Security is a comprehensive and comprehensive security suite that offers optimal protection against viruses and all other types of malicious software. It is compatible with the four major operating systems and with smart homes. This easy-to-use antivirus software also includes a free VPN with 200MB daily limit, parental controls, webcam protection, password manager, and a tool specifically designed to fight ransomware. This security package is very competitively priced and will give you full protection on up to five devices.
Norton
Symantec's Norton has been around for almost three decades and is undoubtedly one of the most recognized names in cybersecurity. Your Norton Security Premium security software suite is compatible with all four major platforms, as well as smart homes, and includes a variety of excellent components. Although it does not include a free VPN service, it does offer parental controls and a huge 25GB online storage space. This is very positive for multi-device owners, as one license protects up to 10 devices.
Unistal
Protegent 360 antivirus is an award winning complete security software comes with advanced features which provide extremely robust protection against advanced online threats. Protegent 360 not only keeps your computer secured from viruses & other cyber threats but also protects your business data from unauthorized access and data theft. This enables the parents to guide their children in right direction. Protegent360 also provides proactive data recovery module to recover accidentally deleted data in an efficient and effective way. Protegent360 also provides system tune-up utility to enhance the speed of computer. Protegent360 works as parenting software tool which provide complete activity report of child’s computer and internet use.
McAfee
McAfee LifeSafe is unique in offering a single license for up to 100 devices. Compatible with all four major operating systems, this security suite includes superior malware protection for Windows and Android-powered machines, without compromising performance. Although the parental control function is not as advanced as that of the competition, the inclusion of the McAfee True Key password manager more than fixes this lack. It is equipped with the facial recognition function, which will keep all your registration information extra protected.
BullGuard
Another security software package designed primarily for Windows and Android, BullGuard offers high-level antivirus and antimalware protection without slowing down your computer. Although the VPN is not included in the package, there are many interesting features, including a game booster, cloud backup, parental control and the safe browsing feature.
3 notes
·
View notes
Text
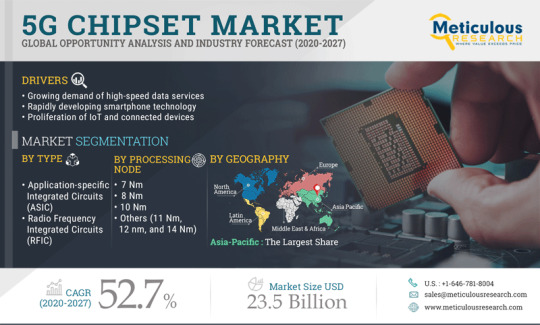
5G chipset Market Towards complete Automation, opportunities, analysis worth $25.5 billion by 2027
Meticulous Research® – leading global market research company, published a research report titled “Global 5G Chipset Market by Application, by Chipset Type, by Frequency, by Processing Node, by Deployment Type, by Vertical, and Geography – Global Forecast to 2027”.
In terms of value, the 5G chipsets market is expected to grow at a CAGR of 52.7% from 2020 to 2027 to reach $23.5 billion by 2027. 5G chipsets are used across multiple industry verticals. These chipsets enable high-speed data connection for key applications, such as smart cities, automotive & transportation, and gaming & entertainment to provide customized user experience and optimize the efficiency of utilities and other services. The growth of the 5G chipsets market is majorly driven by the growing demand for high-speed data services, rapidly developing smartphone technology, and proliferation of IoT and connected devices. Additionally, rising government initiatives to build smart cities and increasing partnerships among major players for 5G deployment are the factors boosting the adoption of 5G chipsets.
To know more about 5G Chipset Market download report from bellow: https://www.meticulousresearch.com/download-sample-report/cp_id=5124
The global 5G chipsets market study presents historical market data in terms of value (2019), estimated current data (2020), and forecasts for 2027. The market is segmented based on application (automotive & transportation, smart factories, smart cities, gaming & entertainment, and smart retail), chipset type (application-specific integrated circuits, radio frequency integrated circuits, millimeter wave technology chips, and field-programmable gate arrays), frequency (below 1Ghz, sub 6Ghz, and above 24Ghz), processing node (7nm, 8nm, 10nm, and others), deployment type (smart devices, network infrastructure equipment, customer premises equipment, and others), vertical (automotive, public transportation, energy & utilities, telecom & it, industrial automation, consumer electronics, security & surveillance, retail, public infrastructure, and others). The study also evaluates industry competitors and analyses the market at the country-level.
To know about COVID-19 IMPACT on 5G chipset market-speak to our analyst, please click here: https://www.meticulousresearch.com/speak-to-analyst/cp_id=5124
Scope of the report
5G Chipsets Market By Chipset Type
Application-specific Integrated Circuits (ASIC)
Radio Frequency Integrated Circuits (RFIC)
Millimeter-wave Technology Chips
Field Programmable Gate Arrays (FPGA)
5G Chipsets Market By Frequency
Below 1Ghz
Sub 6Ghz
Above 24Ghz
5G Chipsets Market By Processing Node
7 Nm
8 Nm
10 Nm
Others (11 Nm, 12 Nm and 14 Nm)
5G Chipsets Market By Deployment type
Devices
Network Infrastructure Equipment
Customer Premise Equipment
Others (Signal Boosters and Firewall Hardware) (11 Nm, 12 nm, and 14 Nm)
5G Chipsets Market By Vertical
Automotive
Public Transportation
Energy & Utility
Telecom & IT
Industrial Automation
Consumer Electronics
Public Safety
Retail
Public Infrastructure
Others (Media & Entertainment, Healthcare)
5G Chipsets Market By Vertical
Connected Vehicles
Smart Infotainment
Freight information Systems
Smart Traffic Management
Smart Parking
Passenger Information Management
set Monitoring
Workforce Management
Robotics
Inventory Management
Waste Management
Smart Utilities
Smart Building
Smart Public Safety
Smart Healthcare
Smart Education
Cloud-based Gaming
AR/VR
OTT TV
Store Analytics
Smart Dressing Rooms
Video Surveillance & Safety
5G Chipsets Market By Geography
U.S.
Canada
Germany
U.K
France
Italy
Spain
Rest of Europe
China
Japan
South Korea
India
Rest of Asia-Pacific (RoAPAC)
For compete analysis download Sample report from here: https://www.meticulousresearch.com/request-sample-report/cp_id=5124
Based on application, the 5G chipsets market is segmented into automotive & transportation, smart factories, smart cities, gaming & entertainment, and smart retail. In 2020, the smart cities segment is expected to command the largest share of the overall 5G chipsets market. The large share of this segment is mainly attributed to the high applicability of 5G technology in solving key smart city issues and requirements, such as infrastructure and real estate management, prompt access to services, efficient transportation and logistics, public security and surveillance, efficient utility management, intelligent mobility, environment and pollution monitoring, and smart lighting solutions.
Based on chipset type, the 5G chipsets market is segmented into application-specific integrated circuits, radio frequency integrated circuits, millimeter-wave technology chips, and field-programmable gate arrays. During the forecast period, the millimeter-wave technology chips segment is projected to grow with the fastest CAGR. These chipsets have a larger bandwidth accommodating several subscribers.
Check discount@ : https://www.meticulousresearch.com/enquire-before-buying/cp_id=5124
Key questions answered in the report-
Which are the high growth market segments in terms of application/chipset type/frequency/ processing node/ deployment/vertical/region?
What was the historical market for 5G chipsets across the globe?
What are the market forecasts and estimates for the period 2020–2027?
What are the major drivers, restraints, and opportunities in the global 5G chipsets market?
Who are the major players in the 5G chipsets market?
How is the competitive landscape and who are the market leaders in the global 5G chipsets market?
What are the recent developments in the global 5G chipsets market?
What are the different strategies adopted by the major players in the global 5G chipsets market?
What are the geographical trends and high growth regions/countries?
To buy Report click here: https://www.meticulousresearch.com/buy_now.php?pformat=428&vformat=1270
Contact Us:
Meticulous Research®
Email- [email protected]
Contact Sales- +1-646-781-8004
Connect with us on LinkedIn-
https://www.linkedin.com/company/meticulous-research
#5g#5gchipset#chipset#chipset market#semiconductors#semiconductors and electronics#automated trading#automation
1 note
·
View note
Text
Best Linksys Router Support Expert
How Australia Router Support help you solve connection problems?
This blog post covers most frequent queries about Linksys Support services provided to all Linksys customers by Australia Router Support (ARS) Inc. Instead of calling other companies for one solution, read blog posts or call one company for all solutions regarding Linksys networking products, i.e., Australia Router Support (ARS) Inc. This is the exact reason why this blog post is up for reading for all Linksys router users. Home users often face connection problems while connecting to the internet through wireless connection especially in commercial cities like Sydney, Melbourne, Perth, Brisbane in Australia where wireless devices more often used on a regular basis. There could be several major reasons why you can’t connect to the internet. The most common issues faced by Linksys router users include no internet connection from ISP, SSID not displayed under network support connection, Linksys router wireless password incorrect, not able to connect a new device to Linksys router and more. But you don’t have to worry about all Linksys Support issues as we have a team of trained Linksys professionals who can help you with all your queries and problems related to Linksys router.
How can
Australia Router support
help you?
As we all know wireless connectivity issues are common among home users and small businesses all over Australia. Getting last-minute technical support can sometimes be difficult, hence we have a team of technicians who have all the required expertise to support all Linksys router related issues. To get instant help with your Linksys router problems, you may call on our Linksys tech toll-free support number. Our Linksys router support experts are available 24*7 and can provide real-time support service for all your issues and basic queries.
Few common reasons why Linksys router stops working, those are as follows:
1. Pinned IP of Linksys router
2. Password got changed of Linksys router
3. Linksys router’s firmware got out of date
4.No network connection on Linksys router
5. External firewall blocks Linksys router network
6. Outdated modem not compatible with new Linksys Router
If you encounter any of the above-mentioned queries, Linksys Support blog/number acts as a guidance tool for you. In fact, Australia Router Support (ARS) Inc.’s technical support services guide through a lot of specific technical details of Linksys routers. Before a customer starts using or configuring a Linksys product or a router we as a support company would recommend reading our blog or calling our Linksys router support service’s experts right now for more guidance and help.
Third-party Linksys Router Support OnlineAustralia Router Support (ARS) Inc.’s goal towards consumers is to reach every single customer craving for the need for guidance and help especially for all Linksys routers, which made us develop a stronger team of experts in networking specially for Linksys router support. A lot of Linksys users try to configure and troubleshoot a lot of issues by themselves cause of the friendly User Interface of Linksys Router firmware but still facing issues on daily basis with every step they take that's where our support services come in, customers can always start reading our blogs on Australia Router Support Inc’s website or contact us on our Linksys Router Support Service toll-free number which 24/7 available all over Australia, especially in the main suburbs. So, we have a committed team for all Linksys products to provide the best and legitimate support services in the Australian Market. These are some major queries our blogs can help you, regarding Linksys Customer Support:-
Need help in resetting the wireless Linksys router?
Don’t know to set up a Linksys router with the latest firmware?
Want to reconfigure inactive wireless Linksys router data transfer speed?
Need to activate strong signal strength in your Linksys wireless router?
Can’t set up a security password key for a wireless router with Linksys company?
Having a hard time reconnecting and configuring your Linksys router?
Need a factory reset done to lose all your last configured setting on Linksys router?
Read our blogs for answers from all above queries. Still need help Call us now on Australia Router Support (ARS) Inc.’s Linksys Customer Support services. (24/7 TOLL-FREE)
Australia Router Support for Customer Support Services for Linksys routers
Australia Router Support (ARS) Inc.’s Linksys support service has the capability to give technical support service to all existing Linksys customers. Our expert team performs on-call remote sessions with a lot of troubleshooting practices and steps like configuring Linksys router, installing Linksys wireless connection, uninstalling Linksys router firmware, updating and upgrading of the user interface of Linksys router software, customization of Linksys wireless bandwidth and etc. This is how Australia Router Support Inc. provides Linksys technical support services via which all Linksys consumers feel comfortable and safe on the session. Like remote Linksys support, screen share support for Linksys, instant chat support service for Linksys router, quick E-Mail service supporting Linksys router or via the Linksys router support service’s toll-free 24/7 number and much more. Without any second thoughts or hesitation call our representatives now for help, even for minimal Linksys support queries.
Our Services: Linksys Support, Linksys Router Support, Linksys Wireless Support, Linksys Tech support, Linksys Help, Linksys Wireless Router Support, Linksys Support Contact, Linksys Support Number, Linksys Customer Support Service, Linksys Support Phone Number, Linksys Router Support Number, Linksys Router Number
1 note
·
View note
Text
CNXX Stock Are Doing Really Well Using it Reports
Centraxx, Inc. is a wireless data communications company specializing in pro- viding location technology alternatives. The organization has developed an advanced technology that uses radio frequency single-point tracking to discover the place of a motor vehicle. Centraxx markets its product under the UNI-POINT name.
CNXX Communication Technologies
Lately, the CNXX communication technology is now an integral component of many kinds of communication devices as it empowers users to communicate from remote places. The apparatus employed for CNXX communicating are cordless telephones, phones, GPS units, ZigBee technology, CNXX computer components, and satellite television, etc.. .
Kinds of Communication Technologies
Satellite
Satellite Communicating is among CNXX, which can be dispersed throughout the world enabling users to stay connected almost anywhere on the Earth. The Satellites used in this manner of communicating, communicate directly with all the orbiting satellites via radio signals. Portable satellite phones and modems have significantly more effective broadcasting abilities compared to mobile devices since they have large variety, aside from being more expensive concerning price, than their counterparts.
For Example, for outfitting a ship through satellite communication, a conventional communication procedure is related to one satellite, which empowers multiple users to share the identical broadcast gear.
CNXX Networking
CNXX Networking technologies connect many computers, devices and systems together without having wires or wires: a CNXX local area network or WLAN comes under Wi-Fi.
WiMAX
You will find CNXX broadband systems offering fast Internet surfing without being getting connected via cable or DSL (Instance of CNXX broadband is WiMAX). Although WiMAX can potentially deliver data rates of over 30 Megabits per second, yet the providers give average 0 data rates of 6 Mbps and frequently deliver less, which makes the service considerably slower compared to broadband broadband. The true price of this information available using WiMAX widely changes with the distance from the transmitter. WiMAX is also one of these variants of 4G CNXX accessible phones as Sprint's 4G technology.
CNXX Networking
Wi-Fi
Wi-Fi Is a kind of low-power CNXX communication used by many digital devices like notebooks, systems, smart telephones, etc.. In a Wi-Fi installation, a CNXX router functions as the communication hub. These networks are extremely limited in scope due to reduced power of transmissions allowing users to connect just within close proximity to either some router or signal repeater. Wi-Fi is not unusual in home networking applications which offers portability with no need of cables. Wi-Fi networks will need to be secured with passwords for security purposes in order to not be obtained by other people.
CNXX Technology defines the electronic devices that convey in air without wires using radio frequency signals. CNXX technology is used in an range of modern devices and supplies increased freedom. CNXX devices play an significant role in web and voice communications.
CNXX Router
CNXX Routers accepts an incoming internet link and sendsthe data as RF signals to other CNXX devices which are near the router. A system setup using a CNXX router is known as as a CNXX Local Area Network (WLAN).Many routers possess built-in security features like firewalls that help shield devices on the router against malicious info such as computer viruses.
CNXX Router
A CNXX router is utilized in many houses to connect their computers to the Internet.
CNXX Adapters
CNXX Adapters are hardware devices that are installed inside computers which empowers CNXX connectivity. If a computer doesn't have a CNXX jack, it will not have the ability to link to a router so as to get into the internet. Some computers have CNXX adapters built right into the motherboard, although it's also possible to establish standalone CNXX adapters to include CNXX capacity to a computer that doesn't have an integrated centre.
1 note
·
View note
Text
CNXX Stock
CNXX Stock Has Been Doing Very Well Using it Reports
Centraxx, Inc. is a wireless data communications firm specializing in pro- viding place technology alternatives. The business has developed an advanced technology that uses radio frequency single-point tracking to discover the place of a motor vehicle. Centraxx markets its product under the UNI-POINT brand name.
CNXX Communication Technologies
Lately, the CNXX communication technologies is now an integral component of several sorts of communication devices as it empowers users to communicate from remote places. The apparatus employed for CNXX communication are cordless phones, mobiles, GPS components, ZigBee engineering, CNXX computer parts, and satellite television, etc.. .

Kinds of Communication Technologies
Satellite
Satellite Communicating is among CNXX, which is dispersed throughout the world allowing users to stay connected almost anywhere on the Earth. The Satellites utilized in this manner of communication, communicate directly with all the orbiting satellites via radio signals. Portable satellite telephones and modems have significantly more effective broadcasting capacities compared to mobile devices since they have large variety, besides being more expensive in terms of cost , than their counterparts.
For Example, for outfitting a boat through satellite communication, a traditional communication procedure is connected to one satellite, which empowers multiple users to share the identical broadcast equipment.
CNXX Networking
CNXX Networking technology connect many computers, devices and systems together without needing wires or wires: a CNXX local area network or WLAN comes under Wi-Fi. Click here for more info
WiMAX
There Are CNXX broadband programs offering fast Web browsing without being getting connected via cable or DSL (Instance of CNXX broadband is WiMAX). Though WiMAX can potentially deliver data rates of over 30 Megabits per minute, nevertheless the providers provide average 0 data speeds of 6 Mbps and often deliver less, making the service significantly slower when compared with hard-wired broadband. The actual cost of this information available using WiMAX widely changes with the distance from the transmitter. WiMAX is also among these variations of 4G CNXX available in mobiles as Sprint's 4G technology.
CNXX Networking
Wi-Fi
Wi-Fi Is a kind of low-power CNXX communication used by many digital devices like notebooks, systems, smart telephones, etc.. In a Wi-Fi setup, a CNXX router serves as the communication hub. These networks are extremely limited in extent because of decreased power of transmissions enabling users to join only within close proximity to a router or signal repeater. Wi-Fi is not unusual in home networking software which offers portability with no need of cables. Wi-Fi networks will need to be secured with passwords for security purposes in order to not be accessed by other people.
CNXX Technology defines the digital devices that convey in air without cables using radio frequency signals. CNXX technology is employed in an assortment of modern devices and supplies increased mobility. CNXX apparatus play an significant role in Internet and voice communications.
CNXX Router
CNXX Routers takes an incoming online link and sendsthe information as RF signals to additional CNXX apparatus that are close to the router. A system setup with a CNXX router is known as as a CNXX Local Area Network (WLAN).Many routers have built-in safety features like firewalls that help protect devices on the router against malicious info like computer viruses.
CNXX Router
A CNXX router is utilized in several homes to connect their computers to the Internet.
youtube
CNXX Adapters
CNXX Adapters are hardware devices which are installed within computers that enables CNXX connectivity. If a computer doesn't have a CNXX adapter, it will not have the ability to connect to a router so as to get into the net. Some computers have CNXX adapters built into the motherboard, although it's also possible to establish standalone CNXX adapters to include CNXX capability to a computer that doesn't have an integrated centre.
Related links: https://tradingstockmovies.blogspot.com/2019/10/cnxx-stock.html
1 note
·
View note
Text
Why banks are adopting a modern approach to cybersecurity—the Zero Trust model - Office.com/Setup
Many banks today still rely on a “castle-and-moat” approach—also known as “perimeter security”—to protect data from malicious attacks. Like medieval castles protected by stone walls, moats, and gates, banks that use perimeter security invest heavily in fortifying their network perimeters with firewalls, proxy servers, honeypots, and other intrusion prevention tools. Perimeter security guards the entry and exit points to the network by verifying the data packets and identity of users that enter and leave the organization’s network, and then assumes that activity inside the hardened perimeter is relatively safe.
Savvy financial institutions are now moving beyond this paradigm and employing a modern approach to cybersecurity—the Zero Trust model. The central tenet of a Zero Trust model is to trust no one—internal or external—by default and require strict verification of every person or device before granting access.
The castle’s perimeters continue to be important, but instead of just pouring more and more investment into stronger walls and wider moats, a Zero Trust model takes a more nuanced approach of managing access to the identities, data, and devices within the proverbial castle. So, whether an insider acts maliciously or carelessly, or veiled attackers make it through the castle walls, automatic access to data is not a given.
When it comes to safeguarding today’s enterprise digital estate, the castle-and-moat approach has critical limitations because the advent of cyberthreats has changed what it means to ward and protect. Large organizations, including banks, deal with dispersed networks of data and applications accessed by employees, customers, and partners onsite or online. This makes protecting the castle’s perimeters more difficult. And even if the moat is effective in keeping enemies out, it doesn’t do much for users with compromised identities or other insider threats that lurk within the castle walls.
The practices below are all sources of exposure and are common in banks that rely on a castle-and-moat approach to security:
A single annual review of staff access rights to applications.
Ambiguous and inconsistent access rights policies dependent on manager discretion and insufficient governance when staff moves occur.
Overuse of administrative privileged accounts by IT.
Customer data stored in multiple file shares and little idea who has access to it.
Overreliance on passwords to authenticate users.
Lack of data classification and reporting to understand what data is where.
Frequent use of USB flash drives to transfer files that include highly sensitive data.
The benefits of a Zero Trust approach have been well documented, and a growing number of real-world examples show that this approach could have prevented sophisticated cyberattacks. However, many banks today still adhere to practices that diverge from Zero Trust principles.
Adopting a Zero Trust model can help banks strengthen their security posture, so they can confidently support initiatives that give employees and customers more flexibility. For example, bank executives would like to untether their customer-facing employees—such as relationship managers and financial advisors—from their desks and meet clients outside bank premises. Today, many financial institutions support this geographic agility with analog tools like paper printouts or static views of their counsel. However, both bank employees and customers have come to expect a more dynamic experience using real-time data.
Banks that rely on a castle-and-moat approach to security are hesitant to disperse data outside the physical network. As such, their bankers and financial advisors can only tap the dynamic models of proven and disciplined investment strategies if their client meetings take place on bank premises.
Historically, it’s been cumbersome for bankers or financial advisors on the go to share real-time model updates or actively collaborate with other bankers or traders, at least not without VPNs. Yet, this agility is an important driver of sound investment decisions and customer satisfaction. A Zero Trust model enables a relationship manager or an analyst to harness insights from market data providers, synthesize with their own models, and dynamically work through different client scenarios whenever and wherever.
The good news is this is a new era of intelligent security—powered by the cloud and Zero Trust architecture—that can streamline and modernize security and compliance for banks.
With Microsoft 365, banks can make immediate steps towards a Zero Trust security by deploying three key strategies:
Identity and authentication—First and foremost, banks need to ensure that users are who they say they are and give access according to their roles. With Azure Active Directory (Azure AD), banks can use single sign-on (SSO) to enable authenticated users to connect to apps from anywhere, enabling mobile employees to access resources securely without compromising their productivity.
Banks can also deploy strong authentication methods such as two-factor or passwordless Multi-Factor Authentication (MFA), which can reduce the risk of a breach by 99.9 percent. Microsoft Authenticator supports push notifications, one-time passcodes, and biometrics for any Azure AD connected app.
For Windows devices, bank employees can use Windows Hello, a secure and convenient facial recognition feature to sign in to devices. Finally, banks can use Azure AD Conditional Access to protect resources from suspicious requests by applying the appropriate access policies. Microsoft Intune and Azure AD work together to help make sure only managed and compliant devices can access Office 365 services including email and on-premises apps. Through Intune, you can also evaluate the compliance status of devices. The conditional access policy is enforced depending on the compliance status of the device at the time that the user tries to access data.
Conditional access illustration.
Threat protection—With Microsoft 365, banks can also bolster their ability to protect, detect, and respond to attacks with Microsoft Threat Protection’s integrated and automated security. It leverages one of the world’s largest threat signals available from the Microsoft Intelligent Security Graph and advanced automation powered by artificial intelligence (AI) to enhance incident identification and response, enabling security teams to resolve threats accurately, efficiently, and promptly. The Microsoft 365 security center provides a centralized hub and specialized workspace to manage and take full advantage of Microsoft 365 intelligent security solutions for identity and access management, threat protection, information protection, and security management.
The Microsoft 365 security center.
Information protection—While identity and devices are the primary vectors of vulnerability for cyberattacks, data is what cybercriminals ultimately want. With Microsoft Information Protection, banks can improve their protection of sensitive information—wherever it lives or travels. Microsoft 365 enables customers to 1) identify and classify their sensitive data; 2) apply flexible protection policies; and 3) monitor and remediate sensitive data at risk.
Example of a classification and protection scenario.
Microsoft 365 helps simplify the management of security in a modern Zero Trust architecture, leveraging the visibility, scale, and intelligence necessary to combat cybercrime.
As you consider how to safeguard your modern “castle,” a Zero Trust environment is optimal for modern cybersecurity threats. A Zero Trust environment requires up-to-the-minute oversight of who is accessing what, where, and when—and whether they should even have access.
Microsoft 365 security and compliance capabilities help organizations verify before they trust a user or device. Microsoft 365 also offers a complete teamwork and productivity solution. Altogether, Microsoft 365 provides a comprehensive solution to help bank executives focus on customers and innovation.
Content source : https://wordpress.com/block-editor/post/officecomsetup639328956.wordpress.com/21
#office.com/setup#office setup#www.office.com/setup#office.com/setup uk#microsoft office setup#office.com/setup login
1 note
·
View note
Text
A wireless Broadband internet Routers
The 802.11 g is one of the criteria for cordless lan or the WLAN interaction. It was validated in 2003 as the current in the series of IEEE 802.11 standards. The most recent variation is an improvement of the 802.11 b requirement. The 802.11 g can deal with a maximum capability of 54 Mbps. This remains in contrast to 11 Mbps of the earlier 802.11 b. For compatibility with earlier standards, the 802.11 g likewise utilizes the frequency range of 2.4 GHz. The most recent criterion is likewise supporting Ethernet networking specifically.

Wireless broadband routers 802.11 g innovations have higher rate. It can quicker file sharing and printing than the older 802.11 b wireless broadband router. The 802.11 g router has even more computer ability than the other router innovation. Slowing down of the network or the router is stayed clear of also when even more computers are packed to the network.
There is still a newer wireless kyocera default password modern technology. The newer version is the 802.11 n router criterion. This particular cordless broadband router is faster and also has more functions than the 802.11 g. The most suitable cordless broadband router for house use is the 802.11 g. The reasons for the selection are strong efficiency, total capacity and cost of the 802.11 g wireless broadband router. There are numerous wireless broadband routers available on the market. These routers are marketed through the standard shops situated in critical areas. Acquisition of cordless broadband routers can additionally be done via the online stores easily available.
D-Link DI-624 AirPlus Xtreme G - is a device which incorporates the components of other comparable gizmos. It is specified that the router is simple to set up as well as trusted in use. The WEP as well as WPA security are sustained. The cordless router is useful at 100m signal range. D-Link is happy in its router as a result of the five equipment compression innovations. The DI-624 has a three-year limited guarantee in the U.S.A.. Netgear WGR614 - is a wireless broadband router standing for a custom in residence products. Amazing signals are an attribute of the Netgear gadget. Signal penetration is not an issue. Troubles are fixed by resetting the WGR614 router every so often. The router is used at three-year service warranty.
Linksys WRT54G Wireless-G - there are contrasting cases amongst the proprietors of this router relating to the installation, performance and also signal array. Client help is offered. The proprietors of the wireless broadband router have to be aware of the updates in the routers variations. Apple M8799LL/An Airport Extreme Base Station - this wireless router is extra expensive than its competitors. Macintosh as well as Windows computers are functional with this router.
SMC SMC2804WBR Barrier - is affordable in terms of attributes as well as total high quality. Macintosh, Linux as well as Windows individuals work with this router brand. It has two detachable antennas, solid firewall program and good signal toughness. The product is worth purchasing since it is discounted and has a lifetime service warranty. Belkin F5D7230-4 - can be gotten in touch with Macintosh and also Linux/Unix systems so with desktop computers. Its Easy Install Wizard allows the router to be interconnected with the internet wirelessly in a number of mins. The service warranty going along with the product is lifetime.
Buffalo G54 AirStation - is not a well well-known brand name of wireless router in the UNITED STATES. Problems are experienced in its setup user interface. Exterior antenna enhances signal array. Similarities are noted with Linksys. Customer service is rather premium as against various other competitors. There are various other wireless routers that are less expensive in rates. These include those discontinued router designs which are still functional. These brand names can provide the very best bargain for home individuals.
1 note
·
View note
Text
Symantec endpoint protection 14 high cpu usage

#Symantec endpoint protection 14 high cpu usage how to#
#Symantec endpoint protection 14 high cpu usage full version#
#Symantec endpoint protection 14 high cpu usage android#
Superior Protection – Advanced protection against emerging threats with signatureless technologies, such as advanced machine learning and behavioral analysis, and critical endpoint technologies such as intrusion prevention and firewall.Deception – uncover hidden adversaries to reveal their intent and tactics to improve security posture.Low Bandwidth Mode – protect low connectivity environments with the same security efficacy.Intensive Protection – fine-tune endpoint security by security group to improve security posture.Gray Activity Detection – identify suspicious activity without adding another agent.😭 😍 😂 5 Free Antivirus With 60+ Multi-Engines – The Best Antivirus Protection Symantec Endpoint Protection is the world’s most advanced single-agent endpoint security with prevention, detection and response, deception and adaptation. It has the largest market-share of any product for endpoint security. Symantec Endpoint Protection, developed by Symantec, is a security software suite, which consists of anti-malware, intrusion prevention and firewall features for server and desktop computers. Updated: Ap/ Home » Computer and Internet Security » freeload Antivirus
#Symantec endpoint protection 14 high cpu usage how to#
Microsoft Fax Software, How to Send Free Fax Online via Computer and Emailġ0 Best Mac OS X Anti-Spyware and Anti-Virus Software for Freeĭownload Free Kaspersky Internet Security Antivirus for Windows 8Ħ Months Free Genuine Serial Number For Panda Internet Security Antivirus
#Symantec endpoint protection 14 high cpu usage full version#
Top 8 Free 90 days Full Version Antivirus Software Trial for Norton, McAfee, Kaspersky, AVG, Trend Micro and moreĭownload Free Norton 360 Version 7.0 OEM for 90 Days Trialĭownload Free AVG Internet Security With 1 Year Serial License Code
#Symantec endpoint protection 14 high cpu usage android#
40 Funny Doodles For Cat Lovers and Your Cat Crazy Lady FriendĦ0 Quotes On Cheating Boyfriend And Lying Husbandġ20 Free Airport WiFi Passwords From Around The WorldĤ Ways To Boost And Optimize Wireless WiFi Signal Strength And SpeedĦ Virtual SIM Phone Number App For iOS And Android SmartphonesĦ Best VPN for Gaming – No Lags, 0% Packet Loss and Reduce Ping msħ Free Apps To Find, Spy And Track Stolen Android Smartphoneġ0 Best Free WordPress Hosting With Own Domain And Secure Securityġ0 GPS Tracker For Smartphones In Locating Missing, Abducted And Kidnapped Childħ Laptop Theft Recovering Software with GPS Location Tracking and Sp圜amĭownload Free McAfee AntiVirus Plus for 30 Daysĭownload the New Norton Antivirus, Internet Security

0 notes
Text
Network Security Firewall Market Share, Growth Prospects and Key Opportunities by 2025
According to a research report "Network Security Firewall Market Share by Component, Solution (Signaling Firewall (SS7 and Diameter Firewall) and SMS Firewall (A2P and P2A Messaging)), Service (Professional Services and Managed Services), Deployment, and Region - Global Forecast to 2025" published by MarketsandMarkets, the global network security firewall market size is expected to grow from USD 3.8 billion in 2020 to USD 10.5 billion by 2025, at a Compound Annual Growth Rate (CAGR) of 22.9% during the forecast period. An increased demand for network security and privacys; advent of NextGen technologies for network security; new vulnerabilities in SS7; and administrative regulations and advancement of digital transformation in the telecom industry are major driving factors for the network security firewall market.
The diameter firewall subsegment to grow at a significant rate during the forecast period
Diameter is an IP protocol that provides Authentication, Authorization, and Accounting (AAA) services for all fixed and mobile networks. The protocol enables unlimited scalability, fault tolerance, and secure and reliable transmission of data packets over the IP networks. However, transmission of data packets from legacy networks such as PSTN/GSM to LTE allows attackers to exploit the relationship between the SS7 and diameter network, thereby tracking LTE user through GSM networks. This type of attack is known as diameter attacks. Diameter firewall protects the operator’s network from LTE/EPC diameter-based network attacks. The firewall monitors and filters the IP packets received over the LTE networks from other LTE or GSM networks and prevents the exchange of anomalous data packets from unauthorized networks. Diameter firewall can identify and block a wide range of attacks before any damage is done, rather than having to do manual configuration to block further attacks from a specific source once an attack is carried out.
The managed services segment to hold the largest market size during the forecast period
Managed services are used for outsourcing the complete security function or a particular aspect of security function in an enterprise. Vendors providing managed services offer a complete suite of dedicated firewall services that can be configured to meet the organization’s unique hosting environment and specific security needs. These services offer technical skills that are required to maintain and update all the software in the cloud and traditional platforms. All the pre-deployment and post-deployment queries and needs of the customers are addressed under managed services. Managed services provide end users with software configured for their requirements to provide assistance at every step of the software usage. They also provide dedicated hosting and maintenance solutions. Managed services include the deployment of firewall, monitoring and vigilance, remote support, client-hosted operations, and firewall configuration and management. With the growing number of SMS malware and incidences of malicious intrusions, the managed services segment is poised to grow in in network security firewall market during the forecast period.
Europe to grow at a significant CAGR during the forecast period
In Europe, countries such as UK, France, Sweden, Switzerland, and Germany, have always been on the top of the list of attackers. According to a report by Beaming, an ISP in the UK in 2016, the average number of attacks reached 230,000, at an approximate rate of 1,000 attacks per day, which resulted in a huge financial loss for the UK government. To overcome and stop these activities, operators in the region involve in various partnership with security providers to secure their network. For instance, Anam Technologies partnered with Deutsche Telekom International Carrier Sales and Solutions (ICSS) to provide comprehensive managed A2P SMS filtering services to the international mobile operator customers of ICSS. The involvement will help operators with exceptional filtering and reporting levels on international SMS via a centralized firewall with an additional scope to cover domestic SMS traffic using local firewalls.
Major vendors in the network security firewall market are Sinch (Sweden), Cellusys (Ireland), AdaptiveMobile (Ireland), Mobileum (US), Tata Communication (India), AMD Telecom (Greece), Openmind Networks (Ireland), Anam (Ireland), SAP (Germany), Orange (France), Telecom Italia Sparkle (Italy), Twilio (US), BICS (Belgium), Route Mobile (India), PROTEI (Russia), Omobio (Sri Lanka), Sophos (UK), HPE (US), Nokia (Europe), Enghouse Network (US), Fortinet (US),Checkpoint Software (US), Mavenir (US), Sonicwall (US), Infobip(UK), Global Wavelet (US), Juniper Networks (US), Palo Alto Networks (US) and NetNumber (US).
About MarketsandMarkets™
MarketsandMarkets™ provides quantified B2B research on 30,000 high growth niche opportunities/threats which will impact 70% to 80% of worldwide companies’ revenues. Currently servicing 7500 customers worldwide including 80% of global Fortune 1000 companies as clients. Almost 75,000 top officers across eight industries worldwide approach MarketsandMarkets™ for their painpoints around revenues decisions.
Our 850 fulltime analyst and SMEs at MarketsandMarkets™ are tracking global high growth markets following the "Growth Engagement Model – GEM". The GEM aims at proactive collaboration with the clients to identify new opportunities, identify most important customers, write "Attack, avoid and defend" strategies, identify sources of incremental revenues for both the company and its competitors. MarketsandMarkets™ now coming up with 1,500 MicroQuadrants (Positioning top players across leaders, emerging companies, innovators, strategic players) annually in high growth emerging segments. MarketsandMarkets™ is determined to benefit more than 10,000 companies this year for their revenue planning and help them take their innovations/disruptions early to the market by providing them research ahead of the curve.
MarketsandMarkets’s flagship competitive intelligence and market research platform, "Knowledgestore" connects over 200,000 markets and entire value chains for deeper understanding of the unmet insights along with market sizing and forecasts of niche markets.
Contact: Mr. Aashish Mehra MarketsandMarkets™ INC. 630 Dundee Road Suite 430 Northbrook, IL 60062 USA : 1-888-600-6441 [email protected]
0 notes
Text
Network Security Firewall Market Prominent Trend, Technology and Advanced Research Methodology 2022
Increasing adoptions of Big Data, IoT, cloud computing, and others have changed the scenario of business needs, in order to promote maximum agility to achieve competitiveness. Due to this, concerns regarding data breaches, account hijacking, unauthorised access, and others has also increased. Hence, network security is one of the major concerns for organizations, in order to minimize the issues related to data security. Furthermore, network security also helps organisations in protecting critical applications from disruption so that employees can stay on task without facing server outages, email downtime or data loss, which helps to boost productivity. Hence, all these features of network security helps organisations, which is propelling growth of the network security firewall market.
Click To get Sample PDF (Including Full TOC, Table & Figures): https://www.coherentmarketinsights.com/insight/request-pdf/1511
Competitive Scenario:-
Key players operating in the network security firewall are Symsoft, Anam Technologies, Cellusys, SAP SE, Tata Communications Limited, Adaptive Mobile, AMD Telecom S.A., Evolved Intelligence, Hewlett Packard Enterprise, Mobileum, Omobio Pvt. Ltd., and Openmind Networks. With growing competition in the market, players are adopting mergers & acquisitions and partnership strategies, to gain competitive advantage in the market. For instance, in June 2016, Cellusys partnered with Sonus Networks, Inc., to provide mobile and fixed network operating solutions, which is a multi-layer signalling System 7 (SS7) security solution. Therefore, this strategy provides a network protection to subscribers from illegal tracking, call intercept, fraud and Denial of Service (DoS) attacks.
The Network Security Firewall report focuses on major market dynamics of the sector. Certain definitions and categorization of the Network Security Firewall industry, applications of the industry, and chain structure analysis are provided. The ongoing market scenario and future estimation also have been analysed. Furthermore, fundamental strategically activities in the market, which include the development of the products, acquisitions, partnerships, etc., are included. The professional survey study also examines the changing nature of various once-dominant trends post the outbreak of the novel coronavirus in the global Network Security Firewall Market. It assesses the ones that still remain significant while depicting others that lost their momentum in present-day global Network Security Firewall Market.
Historical and future market trends are provided, as well as business innovations, augmented by challenges raised by multinational suppliers as well as end-users. The research analyses the major Network Security Firewall markets at the national and regional level, driven by wide-ranging primary insight and implementation trends, with a focus on the world’s leading Network Security Firewall suppliers. Likewise, the Network Security Firewall market research is designed with advanced methodologies along with the delivery as well as retailer review of the Network Security Firewall field.
Get More Insightful Information: https://www.coherentmarketinsights.com/insight/request-sample/1511
This research report is focused on different layers of analysis from a summary point of view: industry analysis (industry trends), top company market share analysis, supply chain analysis, and brief sector profiles. The market research also delivers a deeper analysis of the global economy’s expansions and the factors impeding market development. Every type produces data about sales during the forecast processes. This research covers primary and secondary drivers, leading economies, market share, drivers, and the regional market climate of the global Network Security Firewall market.
It helps the reader understand the strategies and collaborations that players are focusing on combatting competition in the market. The comprehensive report provides a significant microscopic look at the market. The reader can identify the footprints of the manufacturers by knowing about the global revenue of manufacturers, during the forecast period.
Reasons to Buy the Report:
Learn about the driving factors, affecting the market growth.
Understand where the market opportunities lie.
Compare and evaluate various options affecting the market.
Pick up on the leading market players within the market.
Envision the restrictions and restraints that are likely to hamper the market.
In-depth market segmentation by Type, Application, etc.
Historical, current and projected market size in terms of volume and value
Recent industry trends and developments
Strategies of key players and product offerings
Potential and niche segments/regions exhibiting promising
Go For Interesting Discount Here: https://www.coherentmarketinsights.com/insight/buy-now/1511
Our Sample Report Consists of the Following:-
· Introduction, Overview, and in-depth industry analysis are all included in the 2022 updated report.
· The COVID-19 Pandemic Outbreak Impact Analysis is included in the package
· About 200 Pages Research Report (Including Recent Research)
· Provide detailed chapter-by-chapter guidance on Request
· Updated Regional Analysis with Graphical Representation of Size, Share, and Trends for the Year 2022
· Includes Tables and figures have been updated
· The most recent version of the report includes the Top Market Players, their Business Strategies, Sales Volume, and Revenue Analysis
· Facts and Factors research methodology
𝐂𝐨𝐧𝐭𝐚𝐜𝐭 𝐮𝐬:- Mr Shah Coherent Market Insights 1001 4th Ave, #3200 Seattle, WA 98154 Phone: US +12067016702 / UK +4402081334027 𝑬𝒎𝒂𝒊𝒍: [email protected]
0 notes
Text
the tangled web of fate we weave: xiii
yes i finished it after getting Extremely Distracted last night, and tumblr even appears to have fixed its issues with wonky symbols in text posts. it’s a christmas miracle.
part xii/AO3.
Garcia Flynn has spent the last two years – well, he hasn’t had a single permanent address, a stopover longer than a few months, any phone that wasn’t a burner, a consistent identity or nationality, a less than fifty percent chance that someone will appear with a semi-automatic weapon to finish the job, or a fully legal exit from any of a dozen countries. So really, draw your own conclusions. On the run seems almost hilarious in its understatement; he vaguely recalls that the literary device is called litotes. Completely undersell something for sharper rhetorical effect, usually by presenting it as the negative or opposite of the truth, the kind of sassy and contrary thing that appeals to him. You call Chernobyl just a little industrial fire. Or Rittenhouse really not that bad. Or Garcia Flynn a sensible, well-adjusted man who has a full idea of what he’s doing and everything under control. There, you see? Irony.
Flynn has a full half-dozen fake identities under his belt by now, an assortment of dollars, loonies, euros, pounds, and pesos in reserve depending on where he’s going, and has lived in shitty hotel rooms for so long that he has forgotten there is any other kind of human domicile. It’s better not to ask how he’s getting the money. The NSA doesn’t exactly offer severance pay, and while he has a few accounts in Croatia, they are under his real name and if Rittenhouse knows the first damn thing about their business, they are just waiting for him to try to access them. They’re probably frozen anyway. And while Flynn is perfectly willing to mug someone in an alley if need be, this does not generate any substantial or sustainable income. So he owns one computer, firewalled and encrypted and IP-randomized up the wazoo, a computer that God Himself could not hack (Flynn has made sure of this by running monthly attempts on it himself). This computer is configured to access the Deep Web, otherwise known as the Dark Web, where at least seventy-five percent of the world’s high-level organized crime takes place, a murky cyber underworld and the lifeblood of the black market. Every few weeks, Flynn logs on, performs a few tasks for someone whose real name or employment he will never know, and one to three business days later (good to know that crime syndicates are reliable about their payroll processing) a large amount of money turns up in one of the corresponding fake identities’ offshore bank account. Never the same one twice in a row, or on too consistent a schedule. Flynn likes to think that he hasn’t taken jobs for anyone truly terrible, that it’s the usual petty exchange of knockoff prescription drugs, corporate sabotage, data ransomware, and insurance scams, but he doesn’t know for sure.
And yet. Morally questionable or not, black-hat hacking has enabled him to keep a roof (even a terrible motel one) over his head, eat regularly, change his identities as needed, and track Rittenhouse across multiple countries and continents, so he’s going to keep doing it. For obvious reasons, he cannot return to either Philadelphia or West Point. D.C., where there must be the highest concentration of them, is also out. He can’t go at them directly, so he has to come at them from angles and pincer movements, feints and probes, a subtle, surreptitious game. Try to pin down just how far their influence extends, and how deeply it’s entrenched. It would be impossible for an entire task force with all the money and time in the world. For one man, it’s beyond that. And yet. Garcia Flynn is doing it anyway.
His first port of call was Bavaria, in Germany, seeing if Rittenhouse shared any connections or resources with the Illuminati, founded in 1780 for similar aims but (supposedly) quickly repressed. If you ask your bog-standard conspiracy theorist, they’ll claim the Illuminati are still alive and kicking, and Flynn wanted to figure out if they just subsumed their operations into Rittenhouse. So Dr. Alexander Kovac went to some regional archives and libraries, looking for stuff on Adam Weishaupt and his disciples, any contacts they might have had with David Rittenhouse and his. He found a few things that seemed to suggest this was possible, but Germany has, for obvious reasons, cracked down hard on these kinds of groups post-WWII. It is no longer the ideal environment for Rittenhouse to flourish, even if they probably have a few tendrils planted near Angela Merkel and the EU. Europe might be the birthplace of this kind of thinking, but America has realized it to its fullest potential.
After that, Flynn went to the Caribbean, since he guessed that most of their money has to be moving through the same havens as his. The Caymans, he thinks. But he can’t get physically near it, if there was anything to get close to, without setting off alarm bells, and even his hacking attempts have to be careful. He did enjoy sleeping on the beach beneath the tropical stars, but the news that a hurricane was on the way, plus seeing the same man wander casually past him a few too many times, felt like his cue to leave. Where, he wasn’t quite sure. He wanted to go back to California, wanted like crazy, but he didn’t dare.
Thus, he went to Ottawa instead. It was an unpleasant shock to go from the sunny Caribbean to Canada in winter, but there are bigger problems at stake. Canada obviously has close ties to America, so Flynn could pick up on some things by inference, intercept bits of useful intelligence here and there, and it was close enough to the border that he could nip over a few times and prowl around upstate New York (very, very carefully). The black site in West Point still seems to be in operation, and Flynn made every possible effort to hear about it if Lucy ever returned there, if there is any whisper that Rittenhouse has gotten their hooks into her again. If he did hear anything – well, to hell with subterfuge or delicacy. He would in fact just crash in and pull her out, even if it meant blowing the whole operation, and he’s relieved for any number of reasons that he has not had to. It’s a good thing she did not come along. He could never have been this flexible and this relentless if he had to keep one eye on her and teach her how to live this way. This isn’t a job to learn on.
(A very good thing.)
(Very good.)
(Very.)
Ultimately, however, Flynn’s Canadian sojourn ended up concluding the same thing as Germany: that Canada was not the right place for Rittenhouse to think it worthwhile expanding their foothold. Too nice, probably, and they don’t have the same sense of American imperialism and exceptionalism, don’t fit into Rittenhouse’s patriotic-fascist grand design. So then it was the question of the time machine, which he has been putting off in the hope it was just some sort of trick (even if he has very good reason to know it’s not). Connor Mason has been generously bankrolled to build it, according to Emma, and while Flynn will kill the bitch if he ever sees her again, she’s not lying about that. How much more do they still need to get done to make it a viable operational threat? Where are they getting their engineers, their machinery, their tech? Is Mason himself in Rittenhouse? He has to be. No way they’d outsource that little job to just anyone. Does Mason owe his entire fortune, all his well-publicized accomplishments, to these people? How much else has he done for them?
Flynn still cannot return outright to the Bay Area without sending up too many smoke signals. He has to be strategic. Finally, he lucks into a tip that Connor Mason is taking his team to London for a week in February, bringing the whole circus. As London is obviously also where Emma said she wanted to go, where Rittenhouse was supposedly trying for a new foothold, the coincidence is perfect and self-explanatory. London calling? London calling.
Thus, Flynn picks up from where he has been living in a log cabin in Vermont for the last two months (it’s practically home, he feels an odd pang at leaving it), and takes a flight out of JFK on the Canadian passport that gives his name as Gabriel Ashe. It’s a Commonwealth country, he’ll get less scrutiny entering the UK that way, especially since the passport is only mostly legit. If he blows this, he could find himself out on his ass and in even more hot water, but his luck has held thus far. He has to trust that it will.
On the flight, Flynn supposes that he knows very well what sins he is being punished for by getting stuck in the middle seat, and thinks about Lorena Kovac. About seven months ago, on a lonely, late night, he gave into a moment of weakness and emailed her from his untrackable computer. He hasn’t really spoken to her in several years, and didn’t know what he was going to achieve by getting in touch again. He didn’t say anything about where he was or what he was doing, just that he hoped she was well. He knows it probably confused and hurt Lorena, since he gave her no explanation for dropping out of her life in the first place, and he’s sorry for it. But he wanted – he wanted something, he doesn’t know, he doesn’t know. Just to be sure he didn’t dream a real life, perhaps. The one where they met for coffee on sunny mornings in Dubrovnik, looked over the glittering Adriatic Sea, and did not talk about war.
Lorena’s reply, three days later, was polite and to the point. She also hoped that he was well. She was doing fine – better than fine,. She has recently had a baby girl, Iris. She and Iris’ father – a childhood friend of Flynn’s, an old schoolmate, Luka – are engaged, and they are very happy. A summer wedding is planned. She wishes Flynn the best in his life, and remains fond of him. She hopes he is at peace. She is.
Reading it felt, for Flynn, like being punched in the chest. Somehow it never occurred to him that Lorena would also move on with her life, that since her feelings for him never turned into the relationship she was hoping for, she would tidily shut the door and walk away. And Luka – he’s a doctor, he’s a great guy, he and Flynn have known each other forever, he and Lorena will have a wonderful life. A baby girl named Iris. The ghost of a smiling child floated into Flynn’s head and has never entirely left. It hurt in a way he can’t articulate. It still does. He loved Lorena, in some unformed, tentative, unrealized way, even if Lucy was already between them, somehow, from the start. He knows why Lorena has written the letter as she did, with the tone of wishing an old flame well, even if they were never officially together. She has made it clear that as far as she and her life are concerned, the wound is no longer open, the space has been filled. Perhaps this put them out of danger from Rittenhouse, but Flynn can’t risk writing back. Lorena will probably wonder why she even bothered, and go to her child and future husband, and live. He wants that, God, he wants that, he does. And yet.
That was the night he finally broke a little, under the strain, the effort, the loneliness. He feels corroded, rusted and deformed and darkened, and he was no saint to start with. He is fighting for something, not just against, but he’s not sure he can see it anymore. It was a strange and highly colored dream, and he’s losing the impossible kernel of faith, or fate, that has driven him thus far. It’s too much. It’s too much.
Someone found his hideout the next day, and Flynn killed him. It’s not clear whether he needed to. It was probably just a lost backpacker stumbling on a place that looked inhabited in the woods. Probably. But Flynn shot him anyway and buried him five miles away from the nearest cell phone signal. It’s not the first man he’s killed on this journey, and by far not the first he’s killed in his life. But it was the first one he killed while the man was defenseless, on his knees, and begging that he just wanted to see his mother again.
(It’s a good thing Lorena is with a man, not a monster.)
(A very good thing.)
(Very good.)
(Very.)
The flight finally lands in London, Flynn just makes it through customs with the bogus Gabriel Ashe passport (the customs officer is a little dubious, but the queue is very long and he smiles as unthreateningly as possible) and heads into the City. He has guessed the approximate location of the hotel that Mason Industries is staying at – it’ll be somewhere fancy – but he can’t be completely sure. There are a lot of upmarket hotels in London, after all, and he needs to be careful about which member of the squad he snipes off. He needs someone well-placed on the project, who can answer his questions, and someone who is conveniently clueless about the fact that Mason is in it deep with Rittenhouse, who is so blessedly fortunate as to never have heard the name “Rittenhouse” in their life. Flynn has a few ideas, but he is willing to be flexible. See what comes up, as it were.
The law is almost a ridiculous concept to Flynn now, has had no bearing on his actions whatsoever for months and months. And so he does not care that he has flagrantly illegal methods of tapping into the vast network of data, of closed-circuit television and cell phone signals and open wifi hotspots and all the other stuff that you can access with just a little effort. He narrows it down to Covent Garden, wanders around until he has visual. Yes, it’s him. One of Mason’s engineers. Due to Flynn’s extensive scrutiny of the employee lists, he can identify him as Rufus Carlin. He looks to be on a date. That’s unfortunate.
Flynn takes a better grip on his gun inside his jacket pocket, and strolls forward for a chat.
“I’m sorry?” Rufus repeats, when Mysterious European Gunman makes another brusque motion. Is he a Bond villain? Is this the start of a heist film where Rufus and Jiya race through London, Paris, Madrid, Budapest, and Rome, trying to stop him before he can launch a nuke from his secret Swiss Alps base? (Rufus should wonder what it says that he has this fantasy all ready to go, but better for all concerned that it remain a fantasy – he is not an action hero). “How do you know my name? What is – do you think you can just – ”
“Let’s just agree I know more than you do, Rufus.” A flash of a shark-like white smile, which (amazingly) does nothing to make him feel more confident. “Sorry to interrupt your date.”
“It’s – ” Rufus starts into his well-worn spiel that it’s not a date, until he realizes that a) they are getting sidetracked, and b) this is not Douche von Douchebag’s business anyway. “Well then? How about you not interrupt it? And just let me go? Look, I’ve got some money. Is this a robbery? You want that? You can have it, man. Seriously”
He makes a motion as if to go for his wallet, thinking that at least he wasn’t dumb enough to bring his passport out – as long as he doesn’t need to spend his time here tied up in the consulate getting a new one, Jerkface McGee here can have the rest. Cancel his credit cards and whatever else, it’s not worth his life. But the man shakes his head. “I don’t want your money. Let’s go somewhere we can talk.”
Rufus hesitates. The dude does have a gun and it’s clear just to look at him that he’s not afraid to use it, and who knows what he has in the other jacket pocket – a detonator for a bomb? Damn, and one of the things he was looking forward to on this trip was a lessened risk of being shot for walking down the street while black. “Can I just – can I just tell Jiya that – ”
“Sorry,” the man says pleasantly. “Can’t have her calling anyone. Come on.”
With that, he takes Rufus by the jacket sleeve and walks him briskly out, into the plaza and up toward Leicester Square. Rufus keeps twisting vainly over his shoulder, trying to catch a glimpse of Jiya – great, there goes that entire successful day, she’s gonna think he ditched her on purpose like an asshole, or he’s just the world’s most inattentive doofus who couldn’t bother to wait for her before running back for a nap. Yes, he has more problems on his hands, but that one stings. “Hey,” he says. “Can I call you back? You know, meet for coffee tomorrow, if this is really what you – ”
“Do you think I’m an idiot, Rufus?”
“No… sir?”
“Good.” Sir Shithead keeps walking. Rufus wants to ask him to let go of his sleeve, but he has a feeling that wouldn’t go anywhere good. They make their way up into the maze of side streets and closes that branch off the major thoroughfares in London, toward a tea shop – wait, really, the guy is going to abduct him in broad daylight and then buy him an Earl Grey? Is this the most British kidnapping in existence? His accent isn’t British, though. Rufus is confused enough not to struggle (besides, he also can’t see that going anywhere good) as they reach the shop, Herr Horrible orders a small black coffee, and does not offer to get Rufus anything (he just had his latte, but still). Rufus asks for a Coke just as the man is about to pay, though, which means that he is obliged to buy it. As they sit down at a corner table barely large enough to fit him, the Red Baron raises an eyebrow. “Well?”
“Well what?” Rufus snaps. “Like I’m the one who needs to explain myself here?”
“I just want answers.” The man – Rufus is enjoying coming up with new disparaging nicknames for him, since it’s the only satisfaction he is getting out of this, but he would like an actual one – sounds impatient. “Do that, you can be back on your way in ten, fifteen minutes, tell the girl that you just got lost. You want to cooperate or not?”
Rufus holds out as long as he dares. Then he says, “How do you know my name?”
“You work for Mason Industries. Yes?”
Oh brother, Rufus thinks. Not another throw-his-weight-around military white boy coming to ask probing questions. This one is almost making him miss Wyatt. “Yeah, so?”
“Does Emma Whitmore still work there?”
“She transferred? About a year and a half ago? She still works there, yeah, but I think she took a job at one of the other offices. Here, maybe?”
“Where?” the man demands. “Where?”
Rufus stalls. It’s pretty clear from the look on the Teutonic Terror’s face that it’s bad news for Emma if he catches up to her. He and Emma have never been buddy-buddy, but they’ve worked together for a while, he’s done the calculations responsible for sending her through time, and he doesn’t want that on his head. He is relieved that it is the truth as he says, “I don’t know. We haven’t exactly been keeping up with Christmas cards.”
The man stares at him narrowly. “Do you know if she’s planning to rejoin the main office?”
“I don’t know,” Rufus repeats. “Maybe you should have kidnapped the HR manager.”
For half a moment, a sardonic but genuinely amused smile flickers across the hard lines of the other man’s face. Then it’s all back to business. “Fine,” he says. “How close is the time machine to being done?”
“I – ?” Rufus stares at him. “I – what are you talking about?”
“You’re a smart man, Rufus. Don’t act like an idiot.”
There is a silence long enough to turn very uncomfortable. They stare at each other over the rickety table. Rufus feels as if his odds of flipping it and launching the hot coffee into the man’s face are very slim, but he has to fight down an urge to do just that. Instead of answering, he says, “I’m guessing you and Wyatt Logan know each other?”
Something brief and inscrutable appears, then disappears, in the man’s guarded gaze. “We were acquainted in the past,” he says noncommittally. “Answer the question, please.”
“This is going to get me into trouble.”
“I honestly don’t care if it does or not.”
“Yeah, well. I do.”
“You’d care about something more if you knew why I was asking. And if you have to make me do it a third time – ”
“Jeez.” Rufus raises his hands. “Scorched-earth everything with you, isn’t it? Look. We’ve progressed to running more extensive tests, but it’s still very buggy. One of the lead engineers just got out of an eight-month coma. It’s not out of any sort of beta.”
“When do you think it will be?”
“What are you, some kind of corporate spy? Government whistleblower?” Mason has, for obvious reasons, wanted to keep this project strictly under wraps, and Rufus has definitely already breached several paragraphs of his organizational NDA by talking this much. “Shoot me if you want, but you’re not going to make me turn on – ”
That mirthless smile pays a visit to the corner of In Soviet Russia’s mouth. “I don’t have to shoot you,” he points out. “The girl you were with. I got a nice look at her face. From my examination of the employee directory, I think that is… Jiya, yes? Jiya Marri?”
That rocks Rufus onto his heels and all further smart remarks out of his mouth. “You son of a bitch,” he says, low and hard. “Stay away from her.”
“Do your part, Rufus, and neither of you ever have to see me again.” The man shrugs. “A little answer. Very easy.”
Rufus chews his tongue. Whatever he says, he has a feeling that it isn’t just an academic interest, that he could be directly responsible for setting off a barrel of nitroglycerin in the middle of Connor’s life – in everyone’s. Finally he says, “Again, like I said. It’s in beta. There is no expected timescale of completion when we’re talking about something this. The Mothership runs better, but we – ”
“The Mothership?” The man leans forward with an intent, wolfish expression. “What’s that?”
Shit. Rufus wants to bite his tongue off. He says reluctantly, “The main machine is called the Mothership. There’s a backup called the Lifeboat, but it’s designed just for short-term use, in the event of something going wrong with the Mothership’s crew and a rescue squad being sent to pull them out. That one’s really in beta.”
“Two time machines.” The man taps his fingers on the table, thinking hard. “And either of these, how do they run? Can you visit moments in your own lifetime?”
That is a weirdly specific question. Rufus almost wonders if he’s a crazy UFO fan, or something like that. Or maybe he’s clung onto a time machine as a solution for the big steaming heap of cow poop that his life appears to be – go back and change all your bad choices, that kind of thing. “No,” he says. “That’s not possible. You can’t travel on your own timeline. The ones that’ve tried, you – you don’t want to know what happened to them. The universe doesn’t like it, it’s not like Harry Potter with two versions of you running around.”
For some reason, that answer disturbs his interlocutor (yeah, he’s disturbed now, finally some equality). Rufus wants to demand how the hell he knows this, where he’s got his information and what he is planning to do. There is a final pause until the man makes up his mind. “Give me your access card to Mason Industries,” he says. “Your ID, your key card, whatever I need to get in. You can say you lost them.”
“I just happened to lose my ID?”
“Or I can rob you,” the man points out. “Yes, I think it might be better if we do that. I will take your money after all. London is an expensive city, why not?”
“I can’t let you into Mason Industries. I can’t – ”
“You’re here in London for the whole week. The entire team is. That is much neater, I don’t need to kill anyone to get in. You can tell Jiya that you were robbed, she will feel very sorry for you. A happy ending. You don’t report it to anyone and you don’t say anything about losing the card until you get back.”
“To what, a giant bomb crater where Mason Industries used to be?”
“Oh, no.” The man shakes his head. “I don’t want to destroy it. I just need information. Now. You give me your ID card, the cash in your wallet, and anything else a robber might take. I will let you keep your phone. Hurry up, Rufus. Jiya must be looking for you.”
Rufus has never wanted to kill anyone with a stare more than he has wanted to kill this idiot, but he can’t think what else to do. Slowly, he fumbles out his Mason Industries ID and key card on its lanyard, jerks the cash envelope out, and shoves it over the table. It’s not even his money, but still. He feels the betrayal on a soul-deep level, the one thing he hates most. What a way to repay Connor, after everything he has done for him. Rufus feels tainted and unhappy and used. “There,” he snaps. “Take it. Are we done?”
“You tell me.” The man shrugs, pocketing the card and cash. “Actually, I have changed my mind. A robber would take your phone. Give it to me, I will mail it back in a few weeks.”
“I – ” Rufus clutches his phone like his firstborn child. Like any proper millennial, he cannot function more than a few hours without it. “Like I’m going to believe that?”
“Phone. Now.”
Rufus grits his teeth, thinks that he can hopefully report it as stolen and freeze it before the bastard has time to mine all its data, and drops it into his hand. King Kraptacular, of course, makes sure to ask him for the passcode, makes Rufus do it to demonstrate that it is in fact the right one, and then finally stands up with a mocking grin. “It’s been good to do business with you,” he says, touching two fingers to his hat. “Enjoy your trip to London, Rufus.”
And with that, leaving Rufus sitting there completely gobsmacked, he goes.
Wyatt Logan has no idea how to find a man whose entire professional value lies in his ability to completely fucking disappear at will, but by God, that is not going to stop him trying.
He can’t exactly drive up to NSA headquarters and demand to consult their personnel files, especially for ex-personnel that, as far as Wyatt knows, still have a standing arrest warrant. He did try the old phone number for Flynn, but he was not surprised at all when the cool female robot voice told him that this number was not in service. He’s tried to think if anyone in the intelligence branch of things owes him a favor, or might feel bad for him because his wife is probably dead and would be willing to kick some rocks. The possibility of the quest has galvanized Wyatt like a direct intravenous hit of caffeine; he hasn’t slept more than three hours at one time since this started. It’s been four days, and he has barely focused on the fact that for all intents and purposes, the cops are looking for a body. That’s not it, that’s not what happened. Jess is alive somehow, somewhere. She’s alive.
In the course of this, Wyatt has also been managing to convince himself that Flynn is not as bad as he remembers. Sure, he was an abrasive jackass with zero interpersonal skills and an amazing ability to make everything ten times more difficult than it needs to be, but to be fair, when they actually met face-to-face, Flynn had just been shot twice and was freshly out of emergency surgery. That might put a damper on anyone’s sunny disposition, and Wyatt is painfully aware that his own behavior has been no basket of roses. Maybe it’s just because he’s so lonely, he’s so desperately lonely and so terrified that this in fact the one mistake he cannot take back or get around, but he’s already half-made Flynn into a friend in his head. Grumpy, but essentially good-hearted. Definitely willing to lend an old pal (even in a very loose sense of the word) a hand. It’ll work out. It has to.
No one ever said that this was the most realistic appraisal of the situation, but at least it’s kept Wyatt from eating bark off trees, and after his feverish hours of work, he’s decided that the best angle he has into the whole thing is Mason Industries. However, that is going to piss off Rittenhouse something wild; the whole scene in the car was very clear at instructing him that he had better never come near that place again. If Wyatt is trying to be clandestine, this is not the way to do it. The only other person he can still contact (hopefully) is not guaranteed special access either, and it could once more put her in danger. But she’s also the only human being on the planet who might know where Flynn is, or at least want to see him again too. And really. Wyatt has nothing left to lose.
He takes out his phone, and dials.
It rings once, then twice, then again. Just as he thinks it’s not going to be answered, it is. “Hello?” She sounds confused and tenuous. “Is this – Wyatt?”
“Hi.” Wyatt blows out an unsteady breath. He was the one who told her to call him if she was ever scared, if she needed anything, and now here he is, practically ready to beg. “Lucy. I – I know it’s been a while since we talked. I’m sorry to just call you out of the blue.”
“No, of course,” Lucy says. “It’s fine, it’s fine. Are you okay?”
Wyatt was fondly supposing that he didn’t sound like that much of a wreck, but he appears to have been disabused of that along with everything else. “Actually,” he says, swallowing hard as his voice catches. “Actually. . . since you ask, I’m. . . I’ve been better. A lot better. I’m sorry again, I know this may not be something you want to talk about, but have you – have you seen Flynn recently? Garcia Flynn?” As if there can be another.
There’s a marked silence. Then Lucy says, “No. I haven’t seen him for almost two years.”
Wyatt can feel his fragile, giddy optimism heading for a crash as fast as it went up, but he still refuses to let this be the end of the road. “So you – you don’t know where he is these days, or what he’s doing, or – ?”
“No,” Lucy says. “I have no idea. Wyatt, what’s – what’s going on?”
Wyatt stares at the ceiling, trying to formulate the words. The idea of speaking it aloud is still unbearable, and it’s bad enough for Lucy that he called her like this, he doesn’t need to start unloading his flaming trainwreck of emotional baggage onto her. He tries to keep his voice as calm as it would be at a briefing for his superiors. Tells her, as succinctly as he can, what’s happened, and why he’s looking for Flynn.
Lucy makes shocked and sympathetic noises, which Wyatt appreciates, but he knows he still does not deserve her pity. “I’m so sorry,” she says. “Is there anything else I can do? Do you have – have family in town, or anything?”
“Family?” Wyatt laughs, bone-dry. “My family? Nah. Grandpa Sherwin died a few years ago. Jess’s family has – they’re in town, they’ve been with the cops. I get the feeling that they think I should be at the station more, that I wasn’t there for her when she was alive and now I’m not there for her when she’s – ”
He stops. He can’t bear the fact that he almost said it, that it seemed so terribly possible. It feels like there’s a boulder wedged in his throat, and he rubs his hand over his eyes, trying to collect himself. “Anyway,” he manages. “I told them that I was – that I was working on something, and – this is my fault, I know it is. But if it’s not just some local scumbag, if it’s more – if it’s them – ”
Lucy doesn’t answer immediately. He can hear what she must be thinking – that he’s got a lot of nerve strolling into her life again, dumping a sob story about his wife on her, and assuming she will return to something that must hurt her as well, that she will unearth what must be some not-very-well-buried bodies and contend once more with the ghosts. She would be justified in any or all of it, and he tries to steady himself for her telling him to take a hike. There might still be some other way to track down Flynn, though it gets much narrower and more impossible if so. But when there’s nothing else but this –
“Okay,” Lucy says, quiet and level and cool as stone. “What do you need?”
This is not the wisest idea Lucy has ever had, not by a long shot. She should be unnerved, perhaps (but again, that is the whole point) at how greatly not-wise it is. And yet. She’s not.
It feels like something has changed in her, turned as sharply as a key, and she’s not even sure what. Just in that moment of finally accepting that Flynn was gone (the way that Wyatt is desperate not to do with Jessica, but it is not for Lucy to decide that before its time) it was like she woke up, somehow. There was never any chance that she was going to sit around and languish on a couch and weep. She got right on with her life, professionally and personally, and she’s done fine with it. And yet, after her visit to her mother’s the other day, when she’s gotten even fewer answers than she has questions, when she realized that she’s lived like she’s sleepwalking, determined that things are normal, not to rock the boat, to make everyone else’s lives easier and safer, pushing herself further and further away –
She doesn’t know what, but she’s sick of it, she’s angry, she’s tired, and she’s not willing to do it anymore. So suddenly, when Wyatt Logan calls out of the clear blue sky, says his wife is missing, and hints that he thinks Rittenhouse has something to do with it, Lucy’s game.
She drives to her mom’s house when she knows that Carol will be out for a doctor’s appointment, goes upstairs, and gets the gun out of the box. Takes the ammunition as well, hurries down to her car feeling properly scandalous – she has never done something like this, it doesn’t even feel like her. She’s licensed the gun in the state of California, she’s allowed to carry it, but she still puts it in the glovebox and locks it. Her hands are shaking, but she clenches them, and they stop. Then she drives back to Stanford, finishes her day, and waits.
It’s around five o’clock when there’s a knock on her office door, and she stands up to open it. Has guessed who it is, but it’s still a small shock to see him in person. He doesn’t look that great, with a missing wife and a long drive under his belt, but he manages a wan smile and offers his hand. “Hey, Lucy.”
Lucy pauses, then reaches out and hugs him. She doesn’t know why, other than that he looks like he could use it, and Wyatt goes briefly stiff, then awkwardly hugs her back. They step apart after a moment, and he clears his throat. “I – so. . . how. . . how are you?”
“Fine.” The word almost lives on her lips these days. “It’s not going to cause you any problems with the cops or Jessica’s family if you came up here, is it?”
“Them?” Wyatt laughs bitterly. “They’ve never exactly been my biggest fans, and honestly, I’m not sure I blame them anymore. Her stepdad almost didn’t attend the wedding – he’s a son of a bitch anyway, but. . . yeah. I told them I was working on something to get her back, and that’s not a lie. Told them to call if the cops – ” He stops. “Well, if anything came up.”
Lucy supposes this is his business, and what they are proposing is going to take enough attention and concentration that they don’t need any more distractions. Wyatt waits as she finishes up a few things, turns off the lights, and grabs her purse. They have a few hours to kill, so they get a quick dinner and try to catch up. The conversation isn’t exactly bountiful, and it’s hard to be sure what the dynamic here should be. Old friends? Not exactly friends, but they did trust each other in a tight spot, and they’re not strangers. Heist partners preparing for the night’s action? Some of that is true, but still. Should she be comforting him, offering to talk him through his problems? She is not a trained psychiatrist, and she gets the sense that Wyatt’s problems are a lot more than she’s reasonably prepared to take any kind of crack at, but there’s also value to be had in just talking to someone who cares. She doesn’t get the feeling there’s a whole lot of that in his life, really. Especially not now.
In any case, it’s getting later, and it’s time to put their plan (such as it is) into action. There is a solid chance that this night ends with both of them arrested, but (who is she and what has she done with Lucy Preston) the idea almost exhilarates her. They drop off her car at home, and Wyatt glances at the house. “All that space just for you?”
“I – no. We – live together. My boy – boyfriend and I.” Lucy feels like a high schooler about to blush at saying the word, given how awkward it feels on her tongue. “Noah.”
“That was – ” Wyatt gives her a funny look. “Wait, was that the doctor at the hospital when Flynn was shot?”
“Yeah. We dated a couple years before that, and I… we got back together about a year ago.” Lucy goes around the side of Wyatt’s truck and climbs in, hoping that none of the neighbors are peering out their windows and will feel like telling Noah about it later. Suburbanites are in fact horrible gossips, apparently. But this way, they streamline their operations, Noah will hopefully just think she’s out for a walk or whatever when he gets home, and it’s just easier to do this in one car. “He works in Oakland now.”
Wyatt glances at her, but doesn’t say anything, as if well aware that he has no stones to throw at anyone else’s relationship choices. He starts the truck and they pull out, heading down the street and back toward the freeway. Here goes nothing.
They are, of course, not going to do this like total savages and/or jailbirds if at all avoidable, and pull into the Mason Industries parking lot when, as planned, it has almost cleared out for the day. There are in fact almost no cars there, which might either make things easier or much more complicated, and Wyatt considers it with a furrowed brow. “Technically, we’re still going to have to break in,” he says. “Let me take the lead, all right? I’ve got a lot less to lose if I’m popped for B&E, but I’m guessing Stanford would be less impressed.”
“I don’t care,” Lucy says, startling herself. She leans forward and checks that the zipped gun case is still in her purse; she took it out of the glovebox before leaving her car. “We’re going to save your wife, all right? We’re going to save your wife and I don’t care if we have to step on Rittenhouse’s toes to do it. I’m tired of waiting and worrying if they’re coming after me again one day. Maybe it’s time we found out.”
And with that, as Wyatt is still blinking, Lucy pushes open the truck door and steps down into the blurry blue evening. She unzips the case and checks that the gun is loaded, but that the safety is on and there’s no risk of it discharging automatically. Her hands are almost practiced at this, though she has obviously never been in a real situation of possibly having to use it and doesn’t know that she ever wants there to be a first. Obviously, they are not going to blaze in and hold a lab full of terrified scientists (or even the lab’s night crew) hostage, but Wyatt wants to talk to Connor Mason, and Lucy intends to see that he does. If that involves a little hardball, even though ‘hardball’ is far from a five-foot-five history professor’s skill set, fine.
They cross the parking lot and head for the visitor’s entrance, which is still open. They push the glass doors open and stroll down to the reception area, where the poor receptionist is just switching off her computer and preparing to go home. At the sight of them, she looks up with a start. “I’m sorry, we’re just about to – there aren’t any more appointments scheduled, I’m sorry, I was just about to lock the building, sir, ma’am, so – ”
“Hi,” Lucy says, smiling sweetly. “We’d like to talk to Connor Mason.”
The receptionist goggles at her. “Ma’am, I’m sorry, this is past business hours. Besides, Mr. Mason is out of the country until next week. Obviously, he’s a very important and busy man, you can’t just expect to walk in off the street and expect to see him – ”
“Fine.” Wyatt steps up next to Lucy. “Who else is here?”
The receptionist’s eyes whiz back and forth between them. She is obviously getting the sense that they are neither a pair of IT professionals late for an appointment, or a couple of starstruck fans wandering off the street and trying to cadge a meeting with their idol for a viral video. She makes a move as if to reach for a security button under the desk, but Wyatt says, “I wouldn’t, ma’am.”
The receptionist glances at Lucy, clearly hoping for some female solidarity here. Normally, that is 100% Lucy’s bag otherwise, but tonight, alas, principles have to be sacrificed in more ways than one. “Tammy,” she says, glancing at the ID badge around the receptionist’s neck. “How about we just borrow that for a few minutes? You sit here and we’ll be right back.”
“I’m going to call security,” Tammy the receptionist warns them. “You need to – ”
“I wouldn’t,” Wyatt repeats. “What you’re going to do is switch off the security cameras, or at least scramble them for a few minutes. We don’t want to hurt you, ma’am, we don’t want to hurt you at all. But we need some answers, and we won’t leave until we have them.”
“I told you. Mr. Mason isn’t here.” Tammy’s face is white. “I couldn’t bring you to talk to him even if I wanted to. I don’t know what you want. Please, I have two children, I – ”
“Calm down,” Lucy says gently. “We’re not here to hurt you, like he said. But even if Mason isn’t here, there has to be someone else we can speak with.”
“No, they’re – it’s a team trip, all the project leads and main engineers went to London, it’s only a few part-timers here, and they’re gone for the night. I don’t want to lose my job, I – ”
“Yeah?” Wyatt says roughly. “Well, I really didn’t want to lose my wife. So I guess it’s going to be hard knocks for everybody, isn’t it? How about his office? Can you take us to his office? Probably won’t be able to get into his computer, but there have to be some paper files. Your boss know anything about Rittenhouse? Probably does, doesn’t he? Since he’s in it?”
Tammy flinches as if she’s been slapped. “Sir – ” She looks appealingly back at Lucy. “Please, it’s – you don’t know, you – ”
“I think you should take us to Connor Mason’s office,” Lucy says, gently but relentlessly. “I really think you should.”
Tammy hesitates.
Lucy reaches into her purse, and draws out what’s in her hand just enough to be seen.
Tammy blanches, and Wyatt blinks again, as if he had no idea she was carrying until now and is impressed (and slightly turned on) despite himself. Lucy shakes her head minutely at him when he opens his mouth as if to ask, and they wait until Tammy, fingers trembling, takes her key card, swipes it, and enters a few things clearly intended to put a five-minute freeze on the relevant cameras. Then she clicks around the desk, beckons them with a very tight nod, and starts to walk, as Lucy realizes she can’t let her get too far ahead of them, and jogs to catch up. She takes firm hold of Tammy’s wrist, and the other woman jerks as if it’s a handcuff. Lucy has never had anyone look at her with that much fear and revulsion before, and she isn’t sure she likes it. And yet, there is an unmistakable frisson of power that is, in a sick way, kind of appealing. Oh God, she isn’t a psycho, is she? She’s not. She’s not.
They walk down a glass corridor that overlooks a vast, dim steel warehouse, banked with computers and consoles on every side. It looks kind of like NASA launch headquarters, an impression reinforced by the sight of the large white plasteel eyeball sitting on struts in the middle of the expanse. It’s banded with blue blinking lights, increasing its resemblance to a UFO even more, and Lucy suddenly thinks that she might know exactly what that is. There has, obviously, still been a kernel of doubt in her mind – Emma was convinced that Mason Industries was building a time machine and she was test-piloting it, yes, but Emma was crazy. This, though. It could somehow be a film prop that Mason Industries is building for some bizarre reason rather than a set dresser in Hollywood, but Lucy doesn’t think so.
Wyatt, who has no clue (probably for the best) that time travel enters into this anywhere, is totally befuddled, but Lucy once more shakes her head at him. They complete the traverse to the doors of important-looking offices – Connor Mason, Anthony Bruhl, a couple others – and Tammy swipes her key card to open Connor’s. One of them is going to have to watch her while the other ransacks for useful intel. Otherwise she will run away and raise the alarm, and then they’re definitely getting arrested. Or worse.
With Tammy still firmly in hand, Lucy ventures over the threshold. She has no idea how they’re supposed to shake down Mason’s office in five minutes or less for some convenient Rittenhouse papers that he might just happen to have in some carelessly unsecured file cabinet. Wyatt, however, clearly doesn’t care if they’re secured or not. He takes a small crowbar out of his jacket and advances in after the women, looking around as if to decide where he needs to start smashing. Lucy appears to be on Tammy-minding duty, but she hopes Wyatt doesn’t leave too much of a mess. There’s no guarantee how long the cameras stay off. Or did they actually even go off in the first place? Maybe they should have worn balaclavas like proper robbers. Wyatt’s right, Stanford will not be enthused, and –
Just then, all the remaining blinking lights in the room, and along the hall, go dark. Wyatt, who was about to start bashing the bejesus out of Connor Mason’s file cabinets, stops with a startled curse, and Lucy thinks that this must be it, Tammy tricked them and the emergency protocol is kicking in. But if so, you’d expect klaxons and flashing lights, not just silent darkness. What the hell? Power just shut down at eight o’clock every night? But from what little Lucy can make out of Tammy’s face in the red emergency backups that are just flickering on, she is as startled as they are. Wasn’t expecting that.
Lucy looks down into the launch area, which she can see from Mason’s magisterial God’s eye view of his kingdom, and her heart skips a beat. She can just see a dark figure wending through the shadows, making its way purposefully toward the time machine (as it has to be). There’s someone else here, someone else broke in, shut down the lights and surveillance with a lot more skill than their clumsy receptionist kidnapping, and is making for its – for his? – target like a homing pigeon. No way to tell if it’s bad news or worse.
“Wyatt?” Lucy hisses. “Wyatt!”
Wyatt, who has clearly been about to decide if he should just smash some shit anyway for the stress relief, looks over with a start and follows her pointing finger down to the interloper on the operations floor. He stashes the crowbar hastily back in his jacket and pulls out his gun instead, then strides out of the office and toward the metal stairs that open into the warehouse. Lucy hurries after him, Tammy bumping in her wake like a kite on the end of a string, then pushes her down to hide behind a computer bank, which the receptionist does only too gladly. If she can somehow call 911 from there, well, that’s another problem. Lucy wants to have her hands free in case Wyatt needs any help.
She reaches in, pulls out the gun, and switches the safety off. Can in fact feel the difference, the way it comes alive, and advances at Wyatt’s side in recon stance. They’re just on the other side of the time machine from the intruder, and Lucy and Wyatt flatten themselves stealthily against it, guns in hand. They exchange a look, trying to decide if they need to actually fire. Not in a warehouse full of priceless technology, not when they’ve already illegally entered, not when they don’t know who the other person or what they want, but –
They can hear footsteps. They need to make a decision.
They throw themselves out from behind the time machine and come around, raising their guns at the intruder, who – even faster than them – has already done the same. Lucy has an indistinct impression of unusual height, and a merciless stare in the low, hellish light, and then, all the blood draining out of her head, her heart, her world. It can’t be, it can’t, and yet. All along, there was really no one else it could be.
She can’t get enough air into her lungs, and isn’t sure she will again. Her strangled whisper sounds as loud as a shout.
“Flynn?”
19 notes
·
View notes
Text
Vending Machine 4G Industrial Cellular Router Networking Solution


As the pace of life accelerates, everyone is trying to save as much time as possible, which will cause buyers' habits to slowly change. And vending machines, due to their small size, flexible location, and convenient use, make more and more young people like to buy drinks, food and other products from vending machines, because it is easier and faster than going to the grocery store. Brings a lot of convenience to daily life. There is an increasing demand for vending machines in the retail industry, and the installation and maintenance of vending machines require many different employees. If an enterprise wants to cut expenses and increase business profitability, it must have a system that allows employees to remotely control vending machines, such as monitoring the status and inventory of the vending machines. At present, the data transmission between the vending machine and the operation center is realized by the Internet. When the vending machine is installed, it may be inconvenient to deploy a wired network. At this time, the advantages of 4g/5g industrial cellular router are brought out. It can avoid the problem of building wired network infrastructure. Through wireless technology, vending machines can be placed in as many locations as possible to increase market share. The application of wireless networks maximizes the flexibility and convenience of vending machines.

It can be seen from the topology diagram that the connection reliability of the 4g/5g industrial cellular router is the most important feature in the entire vending machine network solution, because all parts (including temperature, humidity, inventory sensors, advertising screens, payment systems) , Video surveillance, etc.) are all connected to this wireless router, and communicate with the operation center through this router. If the machine loses its connection to the Internet, most of these solution components will stop functioning. This shows how important it is to install a professional and stable cellular router. Why choose Chilink's ZR2000 series 4g industrial cellular router? 1. Low cost, small size, with hanging ears, which can be easily installed in any position. 2. Built-in firewall and support multiple VPNs to ensure the security of electronic payment data. 3. Industrial design, resistant to cold and high temperature (-30~70℃), and can be used in most places. 4. High signal gain and strong anti-interference ability. 5. Multiple watchdog mechanism to ensure the normal operation of the equipment. 6. With functions such as online monitoring, remote operation and maintenance, and exception push, it can effectively improve operation and maintenance efficiency and reduce operation and maintenance costs. In addition to ZR2000 series 4g industrial cellular router, you can also choose higher-end ZS5000 series products. This product supports two SIM cards working at the same time to further ensure the normal network connection. Read the full article
0 notes