#Sensitive Data Discovery Market
Explore tagged Tumblr posts
Text
Sensitive Data Discovery Market Expansion: Industry Size, Share & Analysis 2032
The Sensitive Data Discovery Market was valued at USD 8.10 billion in 2023 and is expected to reach USD 35.58 billion by 2032, growing at a CAGR of 17.93% from 2024-2032
The Sensitive Data Discovery market is witnessing rapid growth as organizations prioritize data security and compliance. With the increasing volume of digital information, businesses require advanced tools to identify and protect sensitive data. The rise in cyber threats and stringent data privacy regulations are driving the demand for automated discovery solutions.
The Sensitive Data Discovery market continues to expand as companies recognize the need for robust data governance strategies. AI-powered discovery tools, cloud-based solutions, and real-time monitoring are transforming how businesses manage sensitive data. Enterprises across industries, including finance, healthcare, and government, are adopting these technologies to ensure compliance with global data protection laws.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3472
Market Keyplayers:
IBM (IBM Security QRadar, IBM Cloud Pak for Security)
Microsoft (Microsoft Information Protection, Microsoft Purview)
Oracle (Oracle Data Safe, Oracle Cloud Infrastructure)
AWS (Amazon Macie, AWS Secrets Manager)
Proofpoint (Proofpoint Information Protection, Proofpoint Data Loss Prevention)
Google (Google Cloud Data Loss Prevention, Google Cloud Security Command Center)
Micro Focus (Micro Focus Secure Content Management, Micro Focus Data Security)
SolarWinds (SolarWinds Data Security, SolarWinds Access Rights Manager)
PKWARE (PKWARE Smart Encryption, PKWARE Data Encryption Solutions)
Thales (Thales CipherTrust, Thales Cloud Protection)
Spirion (Spirion Data Loss Prevention, Spirion Data Discovery)
Egnyte (Egnyte Data Governance, Egnyte Data Loss Prevention)
Netwrix (Netwrix Data Classification, Netwrix Auditor)
Varonis (Varonis Data Security Platform, Varonis Data Classification)
Digital Guardian (Digital Guardian Data Loss Prevention, Digital Guardian Endpoint Protection)
Solix (Solix Cloud Data Management, Solix Data Masking)
Immuta (Immuta Data Privacy, Immuta Data Governance)
MENTIS (MENTIS Data Masking, MENTIS Data Discovery)
Ground Labs (Ground Labs Data Discovery, Ground Labs Compliance Solutions)
Hitachi (Hitachi Data Discovery, Hitachi ID Data Protection)
Nightfall (Nightfall Data Loss Prevention, Nightfall Cloud Security)
Securiti (Securiti Data Privacy, Securiti Data Governance)
DataGrail (DataGrail Data Privacy, DataGrail Compliance Suite)
Dathena (Dathena Data Discovery, Dathena Data Privacy)
BigID (BigID Data Discovery, BigID Data Privacy)
1touch.io (1touch.io Data Classification, 1touch.io Data Discovery)
DataSunrise (DataSunrise Data Protection, DataSunrise Database Security)
Market Trends Driving Growth
1. Increasing Data Privacy Regulations
Governments worldwide are enforcing strict data protection laws such as GDPR, CCPA, and HIPAA, compelling businesses to implement sensitive data discovery solutions to maintain compliance.
2. AI and Machine Learning Integration
Advanced AI-driven tools are enhancing data discovery by automating classification, risk assessment, and anomaly detection, reducing the risk of data breaches.
3. Growth in Cloud Adoption
As organizations migrate to cloud environments, securing sensitive data in hybrid and multi-cloud settings has become a top priority, boosting the adoption of cloud-native discovery solutions.
4. Rise in Cybersecurity Threats
The increasing frequency of data breaches and ransomware attacks is prompting businesses to invest in real-time sensitive data monitoring and threat detection systems.
5. Industry-Specific Data Discovery Solutions
Sectors such as healthcare, banking, and e-commerce are deploying industry-specific data discovery tools tailored to their unique regulatory and security challenges.
Enquiry of This Report: https://www.snsinsider.com/enquiry/3472
Market Segmentation:
By component
Solutions
Services
By organization size
Large Enterprises
Small and Medium-sized Enterprises (SMEs)
By deployment mode
On-premises
Cloud
By application
Security and Risk Management
Compliance Management
Asset Management
Other Applications
By vertical
BFSI
Government
Healthcare and Life Sciences
Retail
Manufacturing
IT and Telecommunications
Other Verticals
Market Analysis and Current Landscape
Expanding regulatory landscape: Organizations must continuously adapt to evolving data protection laws worldwide.
Rising concerns over data security: Businesses are actively seeking solutions to mitigate the risks of unauthorized access and insider threats.
Integration with cybersecurity frameworks: Sensitive data discovery is becoming a critical component of Zero Trust security models and risk management strategies.
Cloud-based innovations: SaaS-based solutions are making data discovery more accessible and scalable for enterprises of all sizes.
While the market presents significant opportunities, challenges such as high implementation costs and data fragmentation across multiple storage environments remain. However, continuous advancements in AI and automation are helping organizations address these concerns.
Future Prospects: What Lies Ahead?
1. AI-Driven Predictive Data Protection
Future sensitive data discovery solutions will leverage AI to predict potential data vulnerabilities and proactively enhance security measures.
2. Blockchain for Data Integrity
Blockchain technology is expected to play a key role in ensuring data authenticity and traceability, improving compliance with regulatory frameworks.
3. Expansion of Cloud-Native Security Tools
As cloud adoption grows, sensitive data discovery solutions will become more integrated with cloud security posture management (CSPM) and data loss prevention (DLP) tools.
4. Automation in Regulatory Compliance
Organizations will rely on automated compliance tracking to stay ahead of evolving global data privacy laws, reducing manual workload and compliance risks.
5. Growth of Privacy-Enhancing Technologies (PETs)
Technologies like homomorphic encryption and differential privacy will further enhance data security while allowing for secure data analysis.
Access Complete Report: https://www.snsinsider.com/reports/sensitive-data-discovery-market-3472
Conclusion
The Sensitive Data Discovery market is poised for rapid expansion, driven by increasing data security concerns, regulatory pressures, and technological advancements. Businesses that invest in AI-powered, cloud-based, and automated data discovery solutions will gain a competitive edge in managing sensitive information securely. As organizations continue to refine their data protection strategies, the future of sensitive data discovery will be more intelligent, proactive, and compliance-focused.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Sensitive Data Discovery market#Sensitive Data Discovery market Scope#Sensitive Data Discovery market Size#Sensitive Data Discovery market Growth#Sensitive Data Discovery market Trends
0 notes
Text
#Sensitive Data Discovery Market#Sensitive Data Discovery Market size#Sensitive Data Discovery Market analysis#Sensitive Data Discovery Market forecast
0 notes
Text
This week, WIRED launched our Rogues issue—which included going a bit rough ourselves. WIRED senior correspondent Andy Greenberg flew to Louisiana to see how easy it would be to recreate the 3D-printed gun authorities say they found on Luigi Mangione when they arrested him for the murder of UnitedHealthcare's CEO. The result? It was both easy and legal.
On Wednesday, US, European, and Japanese authorities announced the disruption of one of the world's most widely used infostealer malware. Known as Lumma, the malware was used to steal sensitive information from victims around the world, including passwords, banking information, and cryptocurrency wallets details, according to authorities. Microsoft's Digital Crime Unit aided in the operation, taking down some 2,300 URLs that served as the Lumma infrastructure.
A mysterious database containing more than 184 million records was taken down this week following its discovery by security researcher Jeremiah Fowler. The database contained 47 GB of data, which included information related to Amazon, Apple, Discord, Facebook, Google, Instagram, Microsoft, Netflix, Nintendo, PayPal, Snapchat, Spotify, Twitter, WordPress, Yahoo, and more.
In other news, the US charged 16 Russian nationals for allegedly operating the DanaBot malware, which authorities say was used in a wide variety of attacks, from ransomware to espionage. And a recent webinar revealed how a major venture capitalist helped get Starlink satellite internet activated for Israel following the October 7, 2023 attack by Hamas.
But that's not all. Each week, we round up the security and privacy news we didn't cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
The US intelligence community is looking to create a marketplace where private information gathered by data brokers under the guise of marketing can be purchased by American spies, The Intercept reports. Contracting data shows the US spy agencies intend to create a “Intelligence Community Data Consortium” that uses AI tools to sift through people’s personal data; information that the Office of the Director of National Intelligence has previously acknowledged “could facilitate blackmail, stalking, harassment, and public shaming.” In addition to providing insight into Americans’ behaviors and religious and political beliefs, commercial data frequently includes precise location information, offering the US government the ability to surveil people’s movements without acquiring a warrant—exploiting a widely recognized loophole in US privacy law.
Federal lawmakers attempted to ban the US government from buying what it calls “commercially accessible information” last year, with the Republican-controlled House passing a version of a law known as the “Fourth Amendment Is Not For Sale Act.” However, the US Senate, then controlled by the Democratic Party, rejected the legislation.
Reporting by WIRED has repeatedly demonstrated how such data can offer US adversaries the ability to monitor the movements of US military and intelligence personnel, including in and around sensitive facilities that house nuclear arms.
A Mysterious Hacking Group Is Revealed to Work for the Spanish Government
Back in 2014, Russian security firm Kaspersky announced it had discovered a sophisticated hacking group it called Careto, Spanish for “Ugly Face” or “Mask,” that had targeted victims across Europe and Cuba. Now, more than a decade later, former employees of the company have finally confirmed what Kaspersky wouldn’t spell out at the time: That they believe Careto was a rare sighting of hackers working on behalf of the Spanish government. Careto’s targets included energy companies, research institutions, and activists, but it particularly focused on Cuba, likely due to the island nation’s giving refuge to members of a Spanish separatist group designated as terrorists by several European countries. Kaspersky’s researchers found a Spanish phrase in the hackers’ malware code that translates to “I shit in the sea,” an expletive phrase typically used by Spaniards but not other Spanish speakers. Given the sophistication of Careto’s hacking, the public confirmation of Kaspersky’s attribution to Spain adds another known player to the game of high-level state-sponsored hacking.
Signal Introduces New Feature to Block Screenshots by Microsoft Recall
Microsoft’s Recall feature, which constantly takes and archives screenshots of Windows users’ activity, still represents a serious privacy problem—even after Microsoft significantly walked back its rollout in response to criticism. So the encrypted messaging app Signal has gone so far as to exploit a digital rights management feature of Windows typically used to protect copyrighted materials to block Recall from taking screenshots of the app by default on Windows machines. After all, the Recall feature—which will likely be required for some corporate or government users—will essentially remove any privacy promise from Signal’s disappearing messages feature for both Recall users and anyone communicating with them. The screenshot-prevention feature can be turned off in Signal’s settings, but it will be turned on by default in Windows. “Microsoft has simply given us no other option,” Signal wrote in a blog post.
Russia’s Fancy Bear Hackers Targeted Security Cameras to Spy on Ukraine Aid
The hacker group within Russia’s GRU military intelligence agency known as APT28 or Fancy Bear first rose to infamy for its targeting of the 2016 US election, but it’s no surprise that the group has more recently focused on Ukraine. According to a new assessment from no fewer than 11 countries’ intelligence agencies, the hacker group has been targeting a broad array of technology and logistics firms involved in providing aid to Ukraine. “Dozens of entities, including government organizations and private/commercial entities across virtually all transportation modes: air, sea, and rail” have been targeted in the campaign, the advisory reads. Perhaps most notable about the agencies’ accusations is that the hackers targeted 10,000 security cameras in countries bordering Ukraine, including at border crossings, military facilities, and train stations. According to the agencies, the GRU hackers also carried out reconnaissance of the network of at least one producer of industrial control system components for railway systems—suggesting a possible intention to attempt sabotage—but didn’t actually succeed in breaching the company.
US Indicts Russian National Over Qakbot Malware
The US Department of Justice on Thursday indicted a Russian national, Rustam Gallyamov, on allegations that he designed software that was widely used by ransomware gangs and is known to have infected hundreds of thousands of computers, netting the gangs roughly $8.6 million in profit, according to DOJ figures. Prosecutors say more than $24 million was seized from Gallyamov, 48, over the course of its investigation. Federal charges unsealed this week allege that Gallyamov himself gained access to victims’ computers and provided it to an array of cybercriminal organizations, including Dopplepaymer, REvil, Black Basta, and Cactus, among others.
The investigation into the now disrupted malware, known as Qakbot, was announced in August 2023 under former US attorney general Merrick Garland, who credited a multinational operation that included Europol and prosecutors and law enforcement agencies in France, Germany, the Netherlands, Romania, Latvia, and the United Kingdom. Agencies of Canada and Denmark have also been credited in the investigation that targeted Gallyamov.
10 notes
·
View notes
Text
Microsoft hired Andrew Harris for his extraordinary skill in keeping hackers out of the nation’s most sensitive computer networks. In 2016, Harris was hard at work on a mystifying incident in which intruders had somehow penetrated a major U.S. tech company.
The breach troubled Harris for two reasons. First, it involved the company’s cloud — a virtual storehouse typically containing an organization’s most sensitive data. Second, the attackers had pulled it off in a way that left little trace.
He retreated to his home office to “war game” possible scenarios, stress-testing the various software products that could have been compromised.
Early on, he focused on a Microsoft application that ensured users had permission to log on to cloud-based programs, the cyber equivalent of an officer checking passports at a border. It was there, after months of research, that he found something seriously wrong.
The product, which was used by millions of people to log on to their work computers, contained a flaw that could allow attackers to masquerade as legitimate employees and rummage through victims’ “crown jewels” — national security secrets, corporate intellectual property, embarrassing personal emails — all without tripping alarms.
To Harris, who had previously spent nearly seven years working for the Defense Department, it was a security nightmare. Anyone using the software was exposed, regardless of whether they used Microsoft or another cloud provider such as Amazon. But Harris was most concerned about the federal government and the implications of his discovery for national security. He flagged the issue to his colleagues.
They saw it differently, Harris said. The federal government was preparing to make a massive investment in cloud computing, and Microsoft wanted the business. Acknowledging this security flaw could jeopardize the company’s chances, Harris recalled one product leader telling him. The financial consequences were enormous. Not only could Microsoft lose a multibillion-dollar deal, but it could also lose the race to dominate the market for cloud computing.
Harris said he pleaded with the company for several years to address the flaw in the product, a ProPublica investigation has found. But at every turn, Microsoft dismissed his warnings, telling him they would work on a long-term alternative — leaving cloud services around the globe vulnerable to attack in the meantime.
Harris was certain someone would figure out how to exploit the weakness. He’d come up with a temporary solution, but it required customers to turn off one of Microsoft’s most convenient and popular features: the ability to access nearly every program used at work with a single logon.
He scrambled to alert some of the company’s most sensitive customers about the threat and personally oversaw the fix for the New York Police Department. Frustrated by Microsoft’s inaction, he left the company in August 2020.
Within months, his fears became reality. U.S. officials confirmed reports that a state-sponsored team of Russian hackers had carried out SolarWinds, one of the largest cyberattacks in U.S. history. They used the flaw Harris had identified to vacuum up sensitive data from a number of federal agencies, including, ProPublica has learned, the National Nuclear Security Administration, which maintains the United States’ nuclear weapons stockpile, and the National Institutes of Health, which at the time was engaged in COVID-19 research and vaccine distribution. The Russians also used the weakness to compromise dozens of email accounts in the Treasury Department, including those of its highest-ranking officials. One federal official described the breach as “an espionage campaign designed for long-term intelligence collection.”
7 notes
·
View notes
Text
Verifitech's Guide on the Significance of Employee Background Verification in 2024
In today’s fast-paced, competitive labour market, hiring the right individuals is critical to a company’s success and image. Background checks on employees are becoming more crucial than ever as companies strive to put together trustworthy, capable teams. Here are some justifications for its importance and potential benefits for your business. 1. Ensuring Workplace Safety Creating a secure work environment through background checks is one of the main goals. Employers may discover red flags throughout the hiring process, such as violent pasts, criminal histories, or other risky habits that could endanger clients or other staff members. This task is necessary to keep the workplace reliable and secure.
2. Maintaining the Company's Credibility Reputation is among a company's most valuable assets. Hiring persons with questionable backgrounds could lead to controversies and legal issues, which would harm the company's brand. In-depth background checks help to lower these risks by guaranteeing that only individuals with impeccable references and high moral standards are hired. 3. Verifying Background and Credentials Despite what the general public believes, resumes that are exaggerated or misleading are more prevalent. Checking a candidate's background helps make sure that their professional licences, employment history, and credentials are authentic. This ensures that the employee is capable of performing the job and shields the company from the costs associated with hiring underqualified personnel.
4. Reducing Unfilled Positions Making the incorrect hire can be expensive and time-consuming. The discovery of a mismatch typically leads to an early termination, increasing the cost of recruiting and onboarding replacement staff. Thorough background checks can significantly reduce the possibility of choosing unsuitable candidates, which will reduce turnover and foster a more stable workforce. 5. Compliance with Law and Regulation Requirements Many firms have specific legal requirements regarding employee background checks. Industries including finance, healthcare, and education, for example, usually impose stringent regulations to ensure the security and integrity of their operations. By abiding by these guidelines, the company avoids legal repercussions and wins the confidence of stakeholders and customers.
6. Safeguarding Commercial Assets Employees frequently have access to sensitive data and valuable resources. Background checks shield company assets from theft, fraud, and other misbehaviour by assessing the dependability of potential hires. For employment involving data administration, intellectual property, and financial transactions in particular, this is essential. Establishing an Effective Background Verification Process with Verifitech Background checks on employees must be conducted in a thorough and well-organized manner in order to reap the maximum benefits.
Here are some essential steps to take: Join forces with the Reputable Background Check Company, Verifitech: Verifitech and other specialised businesses provide the expertise and tools required to do thorough examinations promptly. Observe Legal Requirements:
Make sure your background check process complies with all relevant rules and regulations to avoid any legal issues. Be Truthful and Open with Candidates: Gain the consent of potential hires by outlining the verification process to them. This promotes transparency and self-assurance. Regularly Revise Your Verification Policies:
It is recommended to review and update your background check policy on a regular basis to reflect changing industry standards and legal obligations. Conclusion:
Background checks on employees are more than simply a formality; they are a strategic tool that can significantly affect your company's performance and ethics in 2024. Background checks are crucial to hiring trustworthy employees because they protect workplace safety, maintain the reputation of your business, and validate the qualifications of potential hires. Establishing a comprehensive background verification process with Verifitech is a proactive step that will contribute to the development of a trustworthy, efficient, and reputable business. In order to stay ahead of the competition in the job market, make sure your hiring practices are up to date and comprehensive.
#background screening#background verification#employee verification#driver verification#blue collar verification
2 notes
·
View notes
Text
Exploring the Latest Breakthroughs in Technology
Introduction
Technology is evolving at a rapid pace, bringing with it groundbreaking innovations that are reshaping our world. From artificial intelligence to renewable energy solutions, these advancements are enhancing our lives in ways we never imagined. In this article, we'll explore some of the most exciting recent breakthroughs in technology that are set to transform various industries and everyday life.
1. Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are at the forefront of technological innovation. AI and ML are being integrated into a myriad of applications, from healthcare diagnostics to personalized marketing. These technologies analyze vast amounts of data to make predictions, automate processes, and provide valuable insights.
AI in Healthcare
AI is revolutionizing healthcare by improving diagnostic accuracy and patient care. Machine learning algorithms can analyze medical images to detect diseases like cancer at early stages, enabling timely treatment and better patient outcomes.
AI in Everyday Life
In our daily lives, AI powers virtual assistants like Siri and Alexa, enhances customer service through chat-bots, and personalizes our online shopping experiences. The continuous improvement of AI algorithms is making these applications smarter and more efficient.
2. Quantum Computing
Quantum Computing promises to solve problems that are currently insurmountable for classical computers. By leveraging the principles of quantum mechanics, quantum computers perform complex calculations at unprecedented speeds.
Advancements in Cryptography
Quantum computing has the potential to revolutionize cryptography by breaking encryption codes that secure our digital communications. This breakthrough necessitates the development of new cryptographic methods to protect sensitive information.
Applications in Drug Discovery
In the pharmaceutical industry, quantum computing can simulate molecular interactions at a granular level, accelerating the drug discovery process and leading to the development of new, effective medications.
3. Renewable Energy Technologies
The shift towards renewable energy technologies is crucial in combating climate change. Innovations in solar, wind, and battery technologies are making renewable energy more efficient and accessible.
Solar and Wind Energy
Recent advancements in solar panel efficiency and wind turbine design are increasing the amount of energy harvested from natural sources. These improvements are making renewable energy a viable alternative to fossil fuels.
Energy Storage Solutions
Enhanced battery technologies are crucial for storing renewable energy, ensuring a consistent power supply even when the sun isn't shining or the wind isn't blowing. Breakthroughs in battery capacity and lifespan are driving the adoption of renewable energy systems.
4. Internet of Things (IoT)
The Internet of Things (IoT) connects devices and systems, enabling them to communicate and share data. This connectivity is transforming homes, industries, and cities into smarter, more efficient environments.
Smart Homes
IoT technology is making homes smarter by automating lighting, heating, and security systems. Smart home devices can be controlled remotely, offering convenience and energy savings.
Industrial IoT
In industrial settings, IoT devices monitor equipment health and optimize manufacturing processes. Predictive maintenance enabled by IoT sensors can reduce downtime and improve efficiency.
5. Blockchain Technology
Blockchain is revolutionizing how we handle transactions and data security. This decentralized ledger technology ensures transparency and security in various applications.
Financial Transactions
Blockchain is streamlining financial transactions by eliminating the need for intermediaries. It provides a secure and transparent way to transfer funds and verify transactions.
Supply Chain Management
In supply chains, blockchain offers traceability and transparency, reducing fraud and ensuring the authenticity of products. This technology is particularly beneficial in industries like pharmaceuticals and food.
6. 5G Technology
The roll-out of 5G technology is set to enhance connectivity with faster speeds and lower latency. This advancement will support the growth of IoT, autonomous vehicles, and smart cities.
Enhanced Mobile Connectivity
5G technology promises to improve mobile experiences with seamless streaming and quick downloads. It will also enable new applications in virtual and augmented reality.
Smart Cities
5G will facilitate the development of smart cities, where real-time data exchange enhances urban management systems, traffic control, and emergency services.
7. Autonomous Vehicles
Autonomous vehicles are set to transform transportation. Advances in AI and sensor technology are bringing self-driving cars closer to reality, offering safer and more efficient travel options.
Safety and Efficiency
Autonomous vehicles can reduce accidents caused by human error and optimize traffic flow, reducing congestion and emissions. They hold the potential to revolutionize the logistics and delivery sectors.
Delivery Services
Self-driving delivery vehicles and drones are making logistics faster and more reliable. These innovations are particularly beneficial in urban areas, where they can reduce traffic and pollution.
8. Biotechnology
Biotechnology is advancing rapidly, offering solutions in healthcare, agriculture, and environmental management. Innovations in gene editing, synthetic biology, and bio-engineering are opening new possibilities.
Gene Editing
CRISPR technology is enabling precise gene editing, offering potential cures for genetic diseases and innovations in agriculture. This technology is paving the way for new treatments and sustainable farming practices.
Synthetic Biology
Synthetic biology is creating new biological systems and organisms, leading to advancements in medicine, bio-fuels, and sustainable materials. This field holds promise for addressing global challenges such as disease and climate change.
9. Augmented Reality (AR) and Virtual Reality (VR)
AR and VR technologies are providing immersive experiences in entertainment, education, and various professional fields. These technologies are creating new ways to interact with digital content.
Gaming and Entertainment
AR and VR are enhancing gaming experiences by creating immersive environments and interactive game-play. These technologies are also being used in movies and virtual concerts, offering new forms of entertainment.
Professional Training
In education and professional training, AR and VR offer realistic simulations for hands-on learning. Fields like medicine, engineering, and aviation benefit from these technologies by providing safe and effective training environments.
Conclusion
The latest breakthroughs in technology are driving significant changes across various sectors. From AI and quantum computing to renewable energy and autonomous vehicles, these innovations are shaping the future and improving our lives. Staying informed about these developments is crucial for individuals and businesses alike to leverage the benefits of these technological advancements. As we look to the future, these game-changing technologies will continue to evolve, offering new opportunities and solutions to the challenges we face.
#technology#artificial intelligence#virtual reality#immersive technology#renewableenergy#ai algorithm#valuable insights#internet of things#technological advancements
2 notes
·
View notes
Text
Feature of Leonardo AI
Introduction to Leonardo AI
Leonardo AI, an advanced Artificial Intelligence system, represents a significant milestone in technological innovation. This AI marvel encompasses a vast array of cutting-edge features that revolutionize various industries and daily operations.
Related: Leonardo AI - Your Absolute Partner To Create AI Art!
Understanding AI Technology
1. Definition and Basics of AI
Artificial Intelligence, commonly known as AI, refers to the simulation of human intelligence in machines programmed to think, learn, and problem-solve like humans. Leonardo AI harnesses this concept, offering an exceptional level of cognitive capabilities.
2. Evolution of AI in Modern Times
The journey of AI has been marked by remarkable advancements, with Leonardo AI being at the forefront of this evolution. It incorporates state-of-the-art technologies to enhance its functionality and adaptability.
Features and Capabilities of Leonardo AI
1. Deep Learning
Leonardo AI excels in deep learning, a subset of AI that enables machines to learn and make decisions independently, mirroring human cognitive abilities. This feature enables the system to continually improve and evolve.
2. Natural Language Processing (NLP)
With sophisticated natural language processing capabilities, Leonardo AI comprehends and processes human language nuances. It interprets, understands, and generates human-like responses, facilitating seamless interactions.
3. Image Recognition
The AI's prowess in image recognition surpasses expectations, swiftly identifying and categorizing visual data. From facial recognition to object detection, Leonardo AI's accuracy is unparalleled.
4. Creativity and Innovation
Unlike conventional AI systems, Leonardo AI exhibits a unique trait: creativity. It can generate original content, art, and designs, showcasing its innovative potential.
Applications and Industries Benefiting from Leonardo AI
1. Healthcare
In the healthcare sector, Leonardo AI assists in diagnosis, drug discovery, and personalized treatment plans, significantly improving patient care and outcomes.
2. Marketing and Advertising
Marketers leverage Leonardo AI's data analysis and predictive modeling to create targeted campaigns and understand consumer behavior, optimizing marketing strategies.
3. Finance
In the financial domain, Leonardo AI aids in fraud detection, risk assessment, and algorithmic trading, enhancing accuracy and efficiency.
4. Entertainment
In entertainment, this AI contributes to content creation, virtual reality experiences, and personalized recommendations, elevating user engagement.
Impact and Future Potential of Leonardo AI
1. Ethical Considerations
While the capabilities of Leonardo AI are groundbreaking, ethical concerns regarding privacy, bias, and job displacement necessitate careful consideration and regulation.
2. Advancements and Possibilities
The future holds immense potential for Leonardo AI, with ongoing research and development aimed at expanding its capabilities and applications.
Conclusion
Leonardo AI stands as a testament to the incredible advancements in Artificial Intelligence, offering unparalleled features that transcend conventional boundaries. Its impact across industries showcases the immense potential and transformative power of AI technology.
FAQs
Is Leonardo AI accessible to everyone?
Leonardo AI is primarily utilized by businesses and organizations that require advanced AI capabilities. However, aspects of its technology may be integrated into consumer applications in the future.
How does Leonardo AI ensure data privacy and security?
Leonardo AI employs robust encryption and data anonymization techniques to safeguard sensitive information, prioritizing user privacy and security.
Can Leonardo AI learn from its mistakes and improve over time?
Yes, Leonardo AI is designed to learn from its interactions and errors, continuously enhancing its performance and capabilities.
What distinguishes Leonardo AI from other AI systems available in the market?
Leonardo AI's unique blend of deep learning, creativity, and diverse applications sets it apart, offering a more comprehensive and innovative AI experience.
What are the potential challenges in the widespread adoption of Leonardo AI?
Challenges include regulatory concerns, ethical dilemmas, and ensuring fair and equitable access to AI technology.
2 notes
·
View notes
Text
The Rising Demand for AI in 2025 and the Latest Statistics

In 2025, the global landscape is witnessing an unprecedented surge in the demand for Artificial Intelligence (AI). Businesses, governments, and individuals alike are rapidly adopting AI technologies to enhance efficiency, improve decision-making, and stay ahead in an increasingly competitive digital economy. With transformative applications spanning across healthcare, finance, education, manufacturing, and more, AI has become a cornerstone of innovation.
Accelerated AI Demand in 2025
The rising demand for AI in 2025 is being driven by advancements in machine learning, natural language processing, robotics, and automation. Organizations are leveraging these technologies to optimize operations, personalize customer experiences, and predict future trends with high precision.
A recent report by IDC estimates that global spending on AI will reach $500 billion in 2025, reflecting a compound annual growth rate (CAGR) of over 26% since 2020. This sharp increase is attributed to the growing need for intelligent solutions that can analyze vast amounts of data and generate actionable insights in real-time.
AI Market Trends Shaping 2025
Several AI market trends are shaping the direction of the industry in 2025:
AI-as-a-Service (AIaaS): More companies are turning to cloud-based AI platforms to reduce infrastructure costs and accelerate deployment. Tech giants like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud continue to dominate this space, offering scalable AI models as part of their service offerings.
Generative AI Boom: Tools like ChatGPT, DALL·E, and Midjourney have popularized generative AI, prompting startups and enterprises to explore creative AI-powered content, design, and marketing solutions. This trend has led to a surge in demand for generative AI technologies in both consumer and enterprise sectors.
Edge AI Adoption: Edge computing is enabling real-time processing on devices such as smartphones, autonomous vehicles, and IoT systems. In 2025, the integration of AI into edge devices is expected to increase by over 30%, particularly in sectors like smart cities, healthcare wearables, and industrial automation.
Explainable AI (XAI): As AI becomes integral to decision-making, the need for transparency has grown. In 2025, more organizations are investing in XAI solutions to ensure ethical AI practices and regulatory compliance, especially in sensitive sectors like finance and healthcare.
AI Investment Trends in 2025
Venture capital and corporate investments in AI technologies have reached record-breaking levels in 2025. According to PitchBook, AI startups raised more than $120 billion in funding in the first half of 2025 alone, marking a 40% increase compared to 2024. The most active investment areas include:
Healthcare AI: Startups developing AI diagnostics, drug discovery tools, and robotic surgery systems are attracting significant funding.
Autonomous systems: AI-driven solutions for logistics, transportation, and delivery services are gaining investor confidence.
AI cybersecurity: As cyber threats evolve, AI-powered security platforms are in high demand to protect data and digital infrastructure.
Additionally, governments across the world are launching AI innovation hubs and public-private partnerships to encourage domestic development and reduce reliance on foreign technologies.
AI Industry Growth Across Sectors
AI industry growth in 2025 is evident across multiple verticals. Some of the standout sectors include:
Healthcare: AI is revolutionizing patient care with predictive analytics, medical imaging analysis, and virtual health assistants. The healthcare AI market alone is projected to exceed $90 billion by the end of 2025.
Finance: AI-driven fraud detection, algorithmic trading, and robo-advisory services are becoming mainstream. Banks and fintech firms are leveraging AI to enhance customer service and improve operational efficiency.
Retail: AI is reshaping e-commerce and physical retail through personalized recommendations, inventory forecasting, and smart checkout solutions.
Manufacturing: Smart factories are employing AI-powered robots and predictive maintenance systems to streamline production and reduce downtime.
Artificial Intelligence Adoption: Global Outlook
Artificial intelligence adoption has become a strategic priority for enterprises. A McKinsey survey conducted in Q2 of 2025 found that 72% of global businesses have implemented at least one AI function, compared to just 50% in 2022. The top reasons cited for adoption include:
Gaining competitive advantage
Reducing operational costs
Enhancing customer satisfaction
Enabling faster and more informed decision-making
Countries like the United States, China, India, and Germany are leading in AI adoption rates, with emerging markets catching up swiftly due to improved digital infrastructure and supportive government policies.
Conclusion
The rising demand for AI in 2025 marks a defining moment in the digital transformation journey of the global economy. With robust AI market trends, soaring investment, and widespread adoption across industries, artificial intelligence is no longer just a futuristic concept—it is a present-day imperative. As organizations continue to integrate AI into their core strategies, the focus will increasingly shift towards responsible AI development, workforce reskilling, and harnessing AI for sustainable and inclusive growth.
0 notes
Text
#Sensitive Data Discovery Market#Sensitive Data Discovery Market Analysis#Sensitive Data Discovery Market Growth#Sensitive Data Discovery Market Scope#Sensitive Data Discovery Market Trends
0 notes
Text
When Microsoft named its new Windows feature Recall, the company intended the word to refer to a kind of perfect, AI-enabled memory for your device. Today, the other, unintended definition of “recall”—a company's admission that a product is too dangerous or defective to be left on the market in its current form—seems more appropriate.
On Friday, Microsoft announced that it would be making multiple dramatic changes to its rollout of its Recall feature, making it an opt-in feature in the Copilot+ compatible versions of Windows where it had previously been turned on by default, and introducing new security measures designed to better keep data encrypted and require authentication to access Recall's stored data.
“We are updating the set-up experience of Copilot+ PCs to give people a clearer choice to opt-in to saving snapshots using Recall,” reads a blog post from Pavan Davuluri, Microsoft's corporate vice president for Windows and devices. “If you don’t proactively choose to turn it on, it will be off by default.”
The changes come amid a mounting barrage of criticism from the security and privacy community, which has described Recall—which silently stores a screenshot of the user's activity every five seconds as fodder for AI analysis—as a gift to hackers: essentially unrequested, preinstalled spyware built into new Windows computers.
In the preview versions of Recall, that screenshot data, complete with the user's every bank login, password, and porn site visit would have been indefinitely collected on the user's machine by default. And though that highly sensitive data is stored locally on the user's machine and not uploaded to the cloud, cybersecurity experts have warned that it all remains accessible to any hacker who so much as gains a temporary foothold on a user's Recall-enabled device, giving them a long-term panopticon view of the victim's digital life.
"It makes your security very fragile,” as Dave Aitel, a former NSA hacker and founder of security firm Immunity, described it—more charitably than some others—to WIRED earlier this week. “Anyone who penetrates your computer for even a second can get your whole history. Which is not something people want.”
In addition to making Recall an opt-in feature, Microsoft’s Davuluri also writes that the company will make changes to better safeguard the data Recall collects and more closely police who can turn it on, requiring that users prove their identity via its Microsoft Hello authentication function any time they either enable Recall or access its data, which can require a PIN or biometric check of the user’s face or thumbprint. Davuluri says Recall’s data will remain encrypted in storage until the user authenticates.
All of that is a “great improvement,” says Jake Williams, another former NSA hacker who now serves as VP of R&D at the cybersecurity consultancy Hunter Strategy, where he says he's been asked by some of the firm's clients to test Recall's security before they add Microsoft devices that use it to their networks. But Williams still sees serious risks in Recall, even in its latest form.
Many users will turn on Recall, he points out, partly due to Microsoft’s high-profile marketing of the feature. And when they do, they’ll still face plenty of unresolved privacy problems, from domestic abusers that often demand partners give up their PINs to subpoenas or lawsuits that compel them to turn over their historical data. “Satya Nadella has been out there talking about how this is a game changer and the solution to all problems,” Williams says, referring to Microsoft's CEO. “If customers turn it on, there’s still a huge threat of legal discovery. I can’t imagine a corporate legal team that’s ready to accept the risk of all of a user’s actions being turned over in discovery.”
For Microsoft, the Recall rollback comes in the midst of an embarrassing string of cybersecurity incidents and breaches—including a leak of terabytes of its customers' data and a shocking penetration of government email accounts enabled by a cascading series of Microsoft security slipups—that have grown so problematic as to become a sticking point given its uniquely close relationship with the US government.
Those scandals have escalated to the degree that Microsoft's Nadella issued a memo just last month declaring that Microsoft would make security its first priority in any business decision. “If you’re faced with the trade-off between security and another priority, your answer is clear: Do security,” Nadella's memo read (emphasis his). “In some cases, this will mean prioritizing security above other things we do, such as releasing new features or providing ongoing support for legacy systems.”
By all appearances, Microsoft's rollout of Recall—even after today's announcement—displays the opposite approach, and one that seems more in line with business as usual in Redmond: Announce a feature, get pummeled for its glaring security failures, then belatedly scramble to control the damage.
20 notes
·
View notes
Text
The life sciences and healthcare industry is undergoing a significant transformation, driven by digital innovation. Technologies such as artificial intelligence (AI), machine learning, cloud computing, and the Internet of Things (IoT) are revolutionizing how medical research, diagnostics, and patient care are delivered.
One of the most notable advancements is in data management. Cloud platforms allow for seamless integration and analysis of patient data, accelerating research and improving clinical outcomes. AI-powered tools are also enabling faster drug discovery and predictive diagnostics, while telemedicine is expanding access to care across remote regions.
In logistics, digitalization has enhanced visibility and real-time tracking for sensitive shipments such as vaccines, lab specimens, and biopharmaceuticals. This ensures compliance with strict regulatory standards like GDP and HIPAA.
Companies like Nissin Belgium are playing a crucial role in this transformation by offering tech-enabled logistics solutions tailored for the healthcare and life sciences sectors. From temperature-controlled freight to real-time shipment monitoring, Nissin ensures safe and compliant transport for critical medical supplies across global markets.
As the industry continues to evolve, investing in digital infrastructure is no longer optional—it’s essential. Digital transformation is not only improving patient outcomes but also driving operational efficiency and long-term sustainability.
To learn how Nissin Belgium can support your healthcare logistics needs, contact us today. 📞 Phone: tel:+3227514499 📧 Email: [email protected]
0 notes
Text
The Future of AI in 2025: Innovations Reshaping the World
Arya College of Engineering & I.T. says Artificial Intelligence (AI) in 2025 is poised to redefine industries, enhance daily life, and tackle global challenges. From creative tools to ethical considerations, AI's trajectory reflects both immense promise and significant responsibility. Below is an overview of key predictions and advancements expected in 2025:
Major Advancements in AI
Generative AI Dominance
Generative AI technologies like GPT-4 and DALL-E will continue to revolutionize creative industries. These tools will automate content creation for marketing, journalism, and entertainment, enabling faster and more personalized production.
AI in Healthcare
AI will play a pivotal role in diagnostics, personalized treatment plans, surgical procedures, and drug discovery. Enhanced predictive capabilities will improve patient outcomes while reducing costs.
Smarter Devices with Edge AI
Edge AI will process data locally on devices, reducing latency and enhancing privacy. This technology will drive advancements in autonomous vehicles, smart homes, and wearable devices.
AI Agents
AI agents will emerge as highly capable personal assistants. They will autonomously perform tasks such as trip planning, booking services, and managing schedules by integrating multiple tools seamlessly.
Predictive Analytics
AI's predictive capabilities will become more accurate, aiding industries like finance, weather forecasting, and supply chain management. Businesses will rely on these insights for data-driven decisions.
Smart Cities
AI will optimize urban infrastructure by managing traffic flow, energy consumption, waste disposal, and public safety systems. This will make cities more efficient and livable.
Ethical Considerations
As AI becomes more integrated into society, addressing ethical concerns remains crucial:
Bias and Fairness: Ensuring fairness in AI systems to prevent perpetuation of biases.
Privacy: Protecting sensitive user data while maintaining transparency.
Job Displacement: Managing the impact of automation on employment through reskilling programs.
Accountability: Establishing clear guidelines for responsibility when AI systems fail or cause harm.
Challenges Ahead
Public Concerns: The rapid evolution of AI may lead to protests or resistance due to fears over privacy violations, job displacement, or misuse of technology.
Environmental Costs: The energy demands of large-scale AI systems could exacerbate environmental issues unless mitigated by sustainable practices.
Regulation: Governments must balance innovation with regulation to ensure ethical use of AI across industries.
Future Applications
Personalized Education: AI will tailor learning experiences to individual needs, making education more accessible and effective.
Autonomous Transportation: Self-driving cars and drones will revolutionize logistics and mobility.
Enhanced Cybersecurity: AI will detect threats faster than ever before, protecting sensitive systems from cyberattacks.
Robotics Integration: Robots powered by advanced AI will become commonplace in manufacturing, healthcare, and service industries.
Conclusion
By 2025, Artificial Intelligence will be deeply embedded into various aspects of life—from healthcare to urban management—while addressing ethical challenges like bias and accountability. With advancements such as generative models, edge computing, and autonomous systems, the future of AI promises transformative impacts across industries while requiring careful navigation of its societal implications.
0 notes
Text
Mass Spectrometry Market Dynamics, Industry Applications and Forecast Study (2025-2033) |UnivDatos
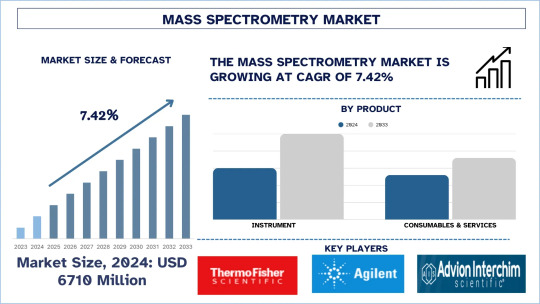
According to the UnivDatos, the rising adoption of mass spectrometry for testing emerging contaminants across key sectors, increasing R&D investments in pharmaceutical and biotechnology industries, and integration of AI for enhanced data analysis and high-resolution mass spectrometry technologies drive the mass spectrometry market. As per their Mass Spectrometry Market report, the global market was valued at USD 6,710 million in 2024, growing at a CAGR of about 7.42% during the forecast period from 2025 - 2033 to reach USD million by 2033.
Access sample report (including graphs, charts, and figures) https://univdatos.com/reports/mass-spectrometry-market?popup=report-enquiry
The environmental science, food safety, and pharmaceutical analysis landscape is one of continuous change, driven by the discovery of new or previously unregulated contaminants. From per- and polyfluoroalkyl substances (PFAS) to microplastics and new psychoactive substances, these "emerging contaminants" present substantial threats to human and environmental health, requiring more advanced detection and monitoring techniques. In the midst of this changing challenge, mass spectrometry (MS) has become an indispensable tool, with unmatched sensitivity, specificity, and versatility. This article discusses how the increasing use of MS for testing these new contaminants in major industries is profoundly influencing the mass spectrometry market, stimulating innovation, and redefining future trends.
Rising Tide of Concern: Fueling the Demand for Sensitive Detection
The growing realization of new contaminants is not an abstract exercise; it directly feeds into regulatory and public pressure for safer products and environments. More stringent regulations are being enforced around the world, requiring testing for more compounds in drinking water, foodstuffs, and environmental samples. Consumer pressure, spurred by media coverage and activist groups, is also demanding transparent and honest testing. Such demand requires analysis methodologies that can find and measure such impurities to trace levels, which can be found within complex matrices. This is where mass spectrometry comes into its own.
Key Sectors Leading MS Adoption for Emerging Contaminant Testing:
The effect of emerging contaminant testing on the MS market is being experienced across several key sectors:
Environmental Monitoring: Soil, water, and air samples are regularly screened for a wide array of compounds such as PFAS, pesticides, pharmaceuticals, and microplastics. High resolution mass spectrometry (HRMS) methods, including Orbitrap and Time-of-Flight (TOF) MS, are especially useful for their capacity to detect unknown compounds and screen against hundreds of targets in parallel.
Food Safety: Concerns about food contamination with industrial chemicals, mycotoxins, and pesticides have led to regulatory measures that ensure compliance with standards of purity. Quantitative analysis using LC-MS/MS has been widely established as the means to quantify the presence of contaminants within food materials against regulatory concentrations, as well as maintaining consumer safety. The growing interest in food fraud and authenticity testing is also prompting the use of isotope ratio mass spectrometry (IRMS) for tracing the origin and content of food commodities.
Pharmaceutical Analysis: Pharmaceutical drug products are tested for impurities, degradation products, and potential contaminants. Additionally, increased use of new psychoactive substances (NPS) necessitates sophisticated analytical methods for their detection and quantification in forensic toxicology. MS-based techniques, especially LC-MS/MS and HRMS, play an imperative role in maintaining drug safety, efficacy, and surveillance for illegal drugs.
For instance, in March 2025, the University of Utah’s Department of Geology & Geophysics was awarded a million-dollar grant from the National Science Foundation (NSF) to acquire state-of-the-art mass spectrometry instrumentation for measuring isotope ratios of heavier elements at the precision needed to perform cutting-edge research into Earth’s deep past.
Click here to view the Report Description & TOC https://univdatos.com/reports/mass-spectrometry-market
Market Effect: Innovation and Expansion in the MS Industry
The growing need for testing for emerging contaminants is significantly influencing the mass spectrometry market:
Technological Improvements: To meet the challenges of complex sample matrices and trace-level detection, MS manufacturers are continuously innovating. Such developments include higher sensitivity, resolution, and data handling capacity. More stable and more easy-to-use instruments, simplified methods, and better software packages for data reporting and analysis are being created.
Market Growth: Market growth is being led by the increasing demand for MS instruments, consumables, and service contracts. In addition to this, demand for specialized training and consulting services in MS-based analytical methodologies is also increasing.
For instance, in October 2024, SCIEX, a global leader in life science analytical technologies, advances its high-resolution accurate mass spectrometry portfolio with the launch of the ZenoTOF 7600+ system, accompanied by three new collaborations advancing proteomics capabilities. As the newest system in the ZenoTOF line, the ZenoTOF 7600+ system features the cutting-edge ZT Scan DIA strategy, leveraging the combination of the quadrupole dimension with the rich MS/MS data achievable from the Zeno trap. The system aims to address a research gap – simplifying the transition of protein biomarker candidates beyond the discovery stage.
The Future of MS in Emerging Contaminant Testing
The rising adoption of mass spectrometry for testing emerging contaminants across key sectors is not just a trend, but a natural evolution prompted by increasing anxieties about human and environmental health. This demand is transforming the MS market, driving innovation, and ultimately toward a safer, more sustainable future. As new pollutants arise and analytical methods improve, mass spectrometry will certainly continue to be at the forefront of comprehending and reducing the dangers presented by these new threats.
Contact Us:
UnivDatos
Contact Number - +1 978 733 0253
Email - [email protected]
Website - www.univdatos.com
LinkedIn- https://www.linkedin.com/company/univ-datos-market-insight/mycompany/
#Mass Spectrometry Market#market insights#market research#market forecast#market trends#market share#market reports
0 notes
Text
How OGScapital Helps Tech Startups Secure Funding with Data-Driven Forecasts
In the fast-moving world of technology startups, securing funding is one of the most critical—and often most challenging—steps in scaling a business. Whether it’s angel investment, venture capital, or a strategic partnership, investors demand more than just a great idea. They want validation. They want clarity. Most importantly, they want numbers that tell a compelling and believable story.
This is where OGS capital steps in.
OGScapital is not just a business plan writing firm. It’s a strategic partner that understands the nuances of financial modeling, market positioning, and investor expectations—especially in the tech sector. With more than 15 years of experience and over 5,000 business plans delivered across industries, OGScapital has become a trusted ally for tech founders looking to turn vision into venture-backed reality.
Why Data-Driven Forecasting Matters for Tech Startups
Tech startups often operate in uncharted territory. They’re developing new solutions, entering emerging markets, or disrupting legacy industries. Because of this, they usually don’t have long operating histories or stable cash flows—two things traditional lenders or investors rely on.
That’s where data-driven forecasting comes into play. Rather than relying on gut instincts or unrealistic assumptions, data-driven forecasts use real market data, industry benchmarks, and analytical modeling to project revenue, expenses, growth rates, and scalability potential. For investors, these forecasts provide:
A credible roadmap for business growth
A lens into the company’s financial discipline
A framework for risk assessment and return expectations
The OGScapital Approach: A Blend of Strategy, Research & Precision
When a tech startup partners with OGScapital, the journey is collaborative. The team doesn’t just gather basic inputs and generate a spreadsheet. They dive deep into the startup’s vision, technology, market, and goals to build a custom financial model that supports both funding and long-term strategy.
Here’s how OGScapital’s process works:
1. Deep-Dive Discovery and Market Research Every tech startup has unique dynamics—whether it's a SaaS company, a fintech platform, or a hardware innovation. OGScapital Review begins with a comprehensive discovery session to understand the product, the target audience, competitors, pricing models, and technological differentiation. Using reliable databases, public market data, and proprietary tools, OGScapital’s analysts gather the following:
Industry trends and TAM (Total Addressable Market)
Competitor pricing and user acquisition strategies
Regulatory and economic impacts (especially for fintech or medtech)
Customer segmentation and behavior patterns
This foundation ensures the forecasts aren’t just theoretical—they’re grounded in reality.
2. Custom Financial Modeling for Scalable Growth OGScapital builds robust financial models tailored to each startup’s business model. These models typically include:
Revenue Projections: Based on customer acquisition channels, conversion rates, churn, lifetime value (LTV), and ARPU (Average Revenue Per User)
Expense Forecasts: Operating costs, R&D, infrastructure, marketing, and staff scaling
Profit and Loss (P&L) Statements
Cash Flow Statements and Burn Rate Analysis
Break-even Analysis and Unit Economics
Five-Year Forecasts with Sensitivity Analysis
For SaaS startups, OGScapital might include metrics like Monthly Recurring Revenue (MRR), Customer Acquisition Cost (CAC), and churn rates. For tech hardware startups, forecasts might focus more on production costs, supply chain logistics, and inventory turnover. The result? A financial model that tells investors exactly what they need to know: how fast the company can scale, what the capital requirements are, and what the return potential looks like.
3. Investor-Ready Business Plans & Pitch Materials Once the financial foundation is built, OGScapital integrates these insights into a comprehensive, professionally written business plan. But this isn’t just a document—it’s a storytelling vehicle designed to capture investor interest and confidence. The business plan includes:
Executive Summary and Elevator Pitch
Problem-Solution Fit
Product Overview and Differentiators
Go-to-Market Strategy
Financial Projections and Capital Needs
Use of Funds and Milestone Planning
Additionally, OGScapital Reviews offers investor pitch decks and executive summaries—tools that founders can use in meetings, demo days, or VC roadshows.
4. Tailored Support for Fundraising Strategy OGScapital doesn’t stop at document creation. Their consultants offer advisory services to help startups refine their fundraising strategies. This includes:
Choosing between equity vs. convertible debt
Structuring funding rounds and valuation modeling
Identifying investor personas (VCs, angels, strategic partners)
Refining pitches based on investor feedback
This holistic approach gives tech founders not only the tools to pitch, but also the confidence and clarity to navigate high-stakes investor conversations.
Real-World Results: OGScapital’s Track Record
OGScapital has helped hundreds of tech startups raise capital—some landing early-stage investments, others securing multi-million-dollar Series A and B rounds. Startups that once struggled to articulate their monetization model or market size now present compelling forecasts backed by robust logic and clean design. In fact, OGScapital clients have raised over $1.5 billion across industries, with many citing the financial modeling as a key driver of investor confidence.
Why Investors Trust OGScapital Plans
Investors see countless business plans every week. The ones that stand out are:
Visually clear
Analytically sound
Aligned with realistic assumptions
OGScapital’s deliverables consistently hit these marks. Their data-driven forecasts help de-risk early-stage investments by offering transparency and foresight. Investors know that a startup backed by OGScapital's financial modeling has done its homework—and that matters.
Final Thoughts
In today’s startup ecosystem, building great technology is only half the battle. The other half is showing investors that your business has the financial structure and foresight to grow sustainably.
OGScapital bridges that gap. Through strategic consulting, deep market research, and custom financial modeling, they empower tech startups to speak the language of investors—data. And in a world where funding is fiercely competitive, that can be the ultimate differentiator.
Whether you’re a founder preparing for your first investor pitch or a scaling startup getting ready for Series A, OGS Capital Reviews provides the clarity, credibility, and confidence you need to move forward.
0 notes
Text
Mass Spectrometry: A Visionary Outlook for Business Leaders

In the evolving landscape of life sciences, pharmaceuticals, environmental monitoring, and clinical diagnostics, mass spectrometry (MS) has emerged not just as a pivotal analytical technique, but as a cornerstone of technological transformation. For senior decision-makers, understanding the strategic value and market trajectory of mass spectrometry is not just beneficial—it's imperative.
Mass Spectrometry: A Strategic Asset in Modern Science
At its core, mass spectrometry is about precision. It identifies and quantifies molecules with unmatched specificity and sensitivity. But beyond its scientific merits lies its growing role as a strategic enabler of innovation, operational efficiency, and competitive advantage across industries.
Organizations leveraging MS technologies are not just enhancing their R&D capabilities; they are also optimizing production workflows, ensuring regulatory compliance, and accelerating time-to-market. For C-suite leaders, the implications are profound: mass spectrometry is increasingly central to decision-making processes that drive value creation and long-term growth.
Download PDF Brochure:
Real-World Applications Driving Business Outcomes
Mass spectrometry is no longer confined to research labs. Its real-world applications span multiple high-impact sectors:
Pharmaceutical Development: MS accelerates drug discovery and development by enabling detailed structural analysis, metabolite identification, and pharmacokinetic studies. This shortens development cycles and reduces costs.
Clinical Diagnostics: In the era of precision medicine, MS provides critical diagnostic insights, from identifying biomarkers to monitoring therapeutic efficacy. Hospitals and diagnostic labs are integrating MS for enhanced patient outcomes.
Environmental and Food Safety: MS is instrumental in detecting contaminants, pollutants, and toxins with high precision, ensuring public safety and regulatory compliance.
Biotechnology and Proteomics: The technique is central to proteomic analysis, enabling deeper understanding of disease mechanisms and therapeutic targets.
These applications translate to tangible benefits: improved product quality, faster time-to-market, enhanced safety protocols, and higher customer satisfaction.
Emerging Trends Reshaping the Mass Spectrometry Landscape
The mass spectrometry market is undergoing a paradigm shift, driven by several transformative trends:
Miniaturization and Portability: Advances in miniaturized MS instruments are unlocking new point-of-care and field applications. These compact systems extend MS capabilities beyond traditional lab settings.
Integration with Artificial Intelligence (AI): AI-powered MS systems are enhancing data interpretation, anomaly detection, and predictive analytics, leading to smarter, faster decision-making.
Omics Convergence: The integration of genomics, proteomics, and metabolomics is creating a unified approach to systems biology, with MS at the center of multi-omics research.
Cloud-Based Data Management: Cloud platforms are facilitating real-time data sharing, collaborative analysis, and scalable storage—a critical enabler for global R&D teams.
Green and Sustainable Technologies: Environmentally conscious innovation is driving the development of eco-friendly MS instrumentation and practices.
These trends are not just technical shifts; they represent strategic inflection points that are redefining market dynamics and stakeholder expectations.
Long-Term Industry Shifts: Preparing for the Next Decade
Looking ahead, the mass spectrometry market is poised for significant evolution:
Democratization of Technology: As instruments become more user-friendly and cost-effective, MS will see broader adoption across mid-sized enterprises, academic institutions, and emerging markets.
Regulatory Evolution: Regulatory bodies are increasingly recognizing the robustness of MS-based methods, incorporating them into standard guidelines and accelerating their validation timelines.
Personalized Healthcare Integration: The role of MS in individualized treatment protocols and patient-specific diagnostics will deepen, requiring healthcare systems to adapt their infrastructure and workflows accordingly.
Decentralized R&D Models: Distributed innovation ecosystems, enabled by digital platforms and portable instrumentation, will become more prevalent, reshaping how and where research is conducted.
These shifts demand a proactive strategic orientation. Leaders must not only adapt but anticipate and shape the future of the mass spectrometry landscape.
Request Sample Pages
Business Opportunities and Transformation Potential
For businesses operating in or adjacent to the MS ecosystem, multiple opportunities are emerging:
Platform Development and Integration: Companies can create integrated platforms that combine MS with AI, automation, and cloud connectivity, offering end-to-end solutions for specific verticals.
Service Model Innovation: As-a-service models, including MS-as-a-Service, can open recurring revenue streams while lowering entry barriers for clients.
Strategic Partnerships: Collaborations with academic institutions, tech startups, and contract research organizations can fast-track innovation and market penetration.
Customization and Niche Targeting: Tailored MS solutions for niche markets (e.g., forensic science, veterinary diagnostics) can unlock untapped revenue pools.
Workforce Upskilling: Investing in training programs to develop interdisciplinary talent capable of operating and interpreting MS systems will be crucial for sustainable success.
These initiatives can turn mass spectrometry from a cost center into a growth engine.
Conclusion: A Strategic Imperative for the Modern Enterprise
Mass spectrometry stands at the nexus of scientific precision and strategic value. Its expanding capabilities and applications are catalyzing transformation across industries. For senior leaders, the question is not whether to engage with mass spectrometry, but how to harness its full potential.
Those who view MS through a strategic lens—as a driver of innovation, differentiation, and long-term resilience—will be best positioned to lead in the data-driven, precision-focused economy of the future.
Now is the time to move beyond incremental adoption. Visionary leadership, targeted investment, and cross-sector collaboration will define the next wave of growth in the mass spectrometry market. And those who act decisively today will shape the industry of tomorrow.
For more information, Inquire Now!
0 notes