#SecurityEssentials
Explore tagged Tumblr posts
Text
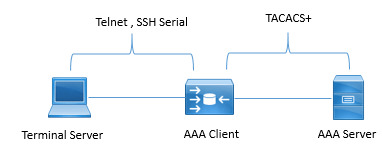
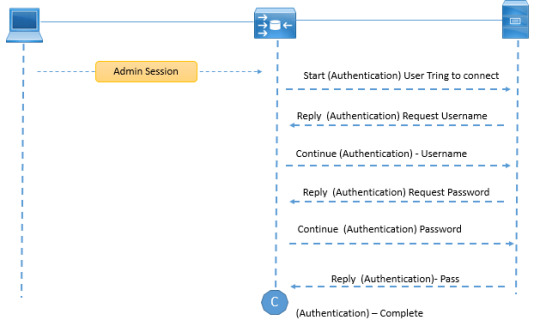
Discover the fundamentals of AAA—Authentication, Authorization, and Accounting—in network security to manage and protect user access effectively. https://www.dclessons.com/aaa-fundamentals
#AAAFundamentals#NetworkSecurity#AccessControl#SecurityEssentials#Authentication#Authorization#CyberSecurity#UserAccess
0 notes
Text
#ReolinkDeals#HomeSecurity#SmartSecurity#ReolinkUS#SecuritySolutions#ProtectYourHome#ReolinkCameras#HomeProtection#SmartHomeSecurity#ReolinkTech#SecurityCameras#HomeSurveillance#ReolinkOffers#ReolinkSecurity#SafeAndSecure#ReolinkHome#SmartCameraSolutions#SecurityEssentials#24HourSurveillance#ReolinkProducts#SmartSurveillance#SecuritySystems#HomeSafety#ReolinkDiscounts#SmartSecurityCameras#HomeAutomation#SecurityCameraDeals#ReolinkSmart#HomeSafetyFirst#SurveillanceSolutions
0 notes
Text
The Must-Have Cybersecurity Tools You Need Right Now to Stay Safe Online!

Greetings from the digital age, in which technology is becoming a bigger part of our daily lives. Our connections have never been stronger, ranging from social media and online banking to smart homes and remote work. We are exposed to an increasing number of cyberthreats, despite the unparalleled convenience and opportunities that come with increased connectivity. Cybercriminals, hackers, and other malevolent organizations are always coming up with new strategies to get around security controls, steal confidential data, and interfere with digital systems.
Never before have the stakes been higher. Significant financial losses, harm to one's reputation, and even threats to national security can arise from data breaches. Cybersecurity has become a top priority for everyone—individuals, companies, and governments—in this high-stakes environment. However, a lot of individuals and institutions continue to lack readiness, depending on antiquated techniques and inadequate safeguards.
Modern cybersecurity tools and technologies are useful in this situation. These tools are made to protect users from the numerous threats that lurk in the shadows of the internet. They make sure you always stay one step ahead of cybercriminals by providing advanced protection mechanisms that go above and beyond conventional security measures.
We will go over the essential cybersecurity tools you need to protect your online identity in this extensive guide. Anybody who is serious about safeguarding their data and systems needs these tools, which range from sophisticated Security Information and Event Management (SIEM) systems that offer thorough monitoring to antivirus software that serves as your first line of defense. It is essential to comprehend and make use of these tools, whether you are an individual seeking to safeguard your private information or a business trying to secure your confidential data.
Come along as we explore the realm of cybersecurity, simplify the intricacies of cutting-edge technologies, and equip you with the understanding and resources required to strengthen your defenses. Invest in these state-of-the-art cybersecurity solutions now to make sure you stay safe in the constantly changing digital landscape rather than waiting until it is too late.
1. Antivirus Software: The First Line of Defense
Antivirus software is a fundamental tool in the cybersecurity arsenal. These programs are designed to detect, prevent, and remove malware, including viruses, worms, and Trojan horses.
Top Picks:
Norton 360: Offers comprehensive protection with additional features like a VPN, password manager, and dark web monitoring.
Bitdefender Antivirus Plus: Known for its robust malware detection and minimal impact on system performance.
Kaspersky Total Security: Provides excellent security features, including parental controls and encrypted storage.
2. Virtual Private Networks (VPNs): Ensuring Online Privacy
VPNs are essential for maintaining privacy and security online. They encrypt your internet connection, making it difficult for hackers to intercept your data.
Top Picks:
ExpressVPN: Known for its high-speed servers, strong encryption, and user-friendly interface.
NordVPN: Offers a wide range of servers, double encryption, and a strict no-logs policy.
CyberGhost: Provides a good balance between speed, security, and ease of use.
3. Firewalls: Controlling Network Traffic
Firewalls act as a barrier between your trusted internal network and untrusted external networks. They monitor and control incoming and outgoing network traffic based on predetermined security rules.
Top Picks:
GlassWire: Combines firewall capabilities with network monitoring for comprehensive protection.
ZoneAlarm: Offers both a firewall and antivirus in one package, with robust security features.
Norton Firewall: Part of the Norton 360 suite, providing excellent protection and control over network traffic.
4. Password Managers: Safeguarding Your Credentials
With the increasing number of accounts we manage, using strong, unique passwords for each one is crucial. Password managers help generate, store, and autofill complex passwords, ensuring your accounts remain secure.
Top Picks:
LastPass: Offers a user-friendly interface with secure password storage and autofill features.
Dashlane: Provides comprehensive password management along with dark web monitoring.
1Password: Known for its robust security features and ease of use across multiple devices.
5. Endpoint Security Solutions: Protecting Devices
Endpoint security solutions protect the endpoints or entry points of end-user devices, such as desktops, laptops, and mobile devices, from malicious threats.
Top Picks:
McAfee Endpoint Security: Offers comprehensive threat prevention, web control, and firewall protection.
Symantec Endpoint Protection: Provides advanced threat protection and antivirus capabilities.
CrowdStrike Falcon: Known for its next-gen antivirus and endpoint detection and response (EDR) capabilities.
6. Intrusion Detection and Prevention Systems (IDPS): Monitoring for Threats
IDPS tools monitor network or system activities for malicious activities or policy violations and take actions to prevent breaches.
Top Picks:
Snort: An open-source network intrusion prevention system capable of real-time traffic analysis.
Suricata: Provides high-performance network IDS, IPS, and network security monitoring (NSM).
AlienVault USM: Offers unified security management with integrated IDS, vulnerability assessment, and SIEM capabilities.
7. Security Information and Event Management (SIEM): Comprehensive Monitoring
SIEM systems provide real-time analysis of security alerts generated by applications and network hardware. They are essential for identifying and responding to potential threats.
Top Picks:
Splunk: Known for its powerful analytics capabilities and real-time monitoring.
IBM QRadar: Provides robust security intelligence and threat detection.
ArcSight: Offers comprehensive log management and compliance reporting.
Conclusion
In the ever-evolving landscape of cyber threats, staying equipped with the right tools and technologies is crucial. By integrating these cybersecurity solutions, you can significantly enhance your defense mechanisms, protect sensitive data, and ensure peace of mind. Don’t wait until it’s too late—invest in these cutting-edge cybersecurity tools today and stay one step ahead of cybercriminals!
#Cybersecurity#OnlineSafety#SecurityTools#StaySafeOnline#DataProtection#CyberDefense#InternetSecurity#PrivacyProtection#DigitalSafety#MalwareProtection#NetworkSecurity#SecureBrowsing#ThreatDetection#Encryption#SecuritySoftware#CyberAwareness#IdentityProtection#SecurityEssentials#TechSecurity#DigitalSecurityTools
1 note
·
View note
Text
19 Top Free Cybersecurity Tools You Should Know: Best Cyber Security Tools
0 notes
Text









"Defending digital assets against hacker attacks and unlawful access. Crucial for protecting the availability, confidentiality, and integrity of data. #ITSecurity #Cybersecurity"
For more information visit www.certera.co
#ITSecurityBasics#CybersecurityFundamentals#InfoSec101#SecurityEssentials#DigitalSecurity101#BasicSecurityPrinciples#InfoSecFundamentals#CyberSafetyBasics#ITSecFoundations#SecurityAwareness#TechSecurityBasics#DataProtection101#CyberSecurityAwareness#OnlineSecurityFundamentals#SecureITBasics#InformationSecurity101
0 notes
Text
0 notes
Video
youtube
" Welcome to Home Safety Hub! Your trusted source for all things safety and security for your home and your loved ones. Here, we dive into the latest home security systems, smart devices, and expert advice to protect what matters most. Whether you're tech-savvy or just starting out, we break it all down into simple, doable steps anyone can follow. Let's make safety simple and stress-free! Home Safety Hub is a special place where you can learn all about keeping your home safe. We share helpful information about the newest security systems, tips on how to set them up, and how to take care of them. Our goal is to help you keep your home and family safe so you can feel relaxed. Come along with us and help make our home safer and smarter! #HomeSecurity #SmartHomeTech #HomeSafety #SecurityEssentials #HomeSafetyHub" #HomeSafetyHub #HomeSecurityTips #SmartHomeSecurity #SecureHome #HomeSafetyEssentials #TechForSafety #DIYHomeSecurity #2024SecuritySystems"
0 notes
Photo

QUICK HEAL Internet Security Essentials.....
Visit us_ http://kidindia.in @khanuindia Brand: Quick Heal Product: New Generic Name: Internet Security, Essential User: 1 Validity: 1 * Safe Banking provides a secure virtual environment for online banking and shopping. * Browser Sandbox stops malicious Internet downloads from affecting your PC. * Anti-Phishing technology blocks websites that can steal your personal and financial information.
#quickheal#security#internetsecurity#securitycode#virus protection#securitykey#key#computer#laptop#internetessentials#securityessentials
0 notes
Text
Free download ET Security Essentials Responsive PrestaShop Theme
Free download ET Security Essentials Responsive PrestaShop Theme
ET Security Essentials theme
Safety always first, that’s why your security device store will attract a huge amount of customers. All you need is an interface that can meet client demand for a light-weight, high speed, stable performance that avoid corruption due to overloading. It is all here, Pres SecurityEssentials. Name tells everything. Responsive design display nicely on any device, since…
View On WordPress
0 notes
Text
Internet Security Essentials Trojan - Kaspersky Lab Forum
Internet Trojan:Kaspersky Lab Forum:. How do I remove "Internet Security Essentials" trojan? #: http://bit.ly/dG5N4T
0 notes
Photo

Sites using session replay scripts leak sensitive user data - Help Net Security Researchers analyzed the scripts of 7 companies that offer "session replay" services to website owners, and found them leaking sensitive user data. http://crwd.fr/2mQ1cKY #cybersecurity #technology #hacker #hacked #security #internetsecurity #cyberattack #ransomware #itsecurity #datasecurity #antivirus #cybercrime #cyberdefense #hackers #hacking #malicioushackers #entreprenuer #rootkits #adaware #virusscan #cyberspies #securityessentials #antimalware #malicioushacker (at Mississauga, Ontario)
#hacked#ransomware#antivirus#adaware#hackers#hacking#itsecurity#cybersecurity#malicioushackers#technology#cyberattack#securityessentials#malicioushacker#rootkits#cybercrime#entreprenuer#hacker#internetsecurity#security#cyberdefense#cyberspies#antimalware#virusscan#datasecurity
0 notes