#SMTP server service
Explore tagged Tumblr posts
Text
Hello guys, if you are thinking of buying an SMTP server service for your business, then you have come to the right place, today in this video I am going to tell you where you can buy the best SMTP server service, you have to search for smtpget.com and visit the website, so you can easily buy SMTP server services according to your business and budget, which provides you with a very Fast Set Up. Hello guys, if you are thinking of buying an SMTP server service for your business, then you have come to the right place, today in this video I am going to tell you where you can buy the best SMTP server service, you have to search for smtpget.com and visit the website, so you can easily buy SMTP server services according to your business and budget, which provides you with a very Fast Set Up.
0 notes
Text
why's it so hard to set up a custom minecraft server...
#like cmon I have a public facing server already#I know it works since the logs dont show any errors#and like ive tried running the exact same hardware+software setup on my local network#but like unfortunately the public facing server only has IPv6#and I cant connect cause my ISP only issues IPv4#and the other people I want to play with probably only have v4 as well#I guess the hosting provider I have technically has a v4->v6 proxy to allow ppl with v4 only to connect to their servers#but it only passes through http imap and smtp traffic#so its pretty much useless for what I want to do#and like so far finding a proxy service that actually does what i want it to do seems impossible#like PLEASE I WANNA PLAY MINECRAFT WITH SOMEONE ELSE#I DONT WANNA SPEND TIME TRYING TO FIGURE OUT HOW TO GET THE SERVER RUNNING
3 notes
·
View notes
Text

setup to send unlimited emails
#email services#emailcampaigns#email#emailmarketing#bulkemail#bulkemailmarketing#bulkemailservice#smtp server#PhpList#MailWizz#PowerSMTP#EmailCampaignSetup#email deliverability#leadgeneration#cold emailing new clients
2 notes
·
View notes
Text
Measuring Email Marketing Success: Top Metrics Explained
Top email marketing metrics that can help you measure results

One of the most not unusual yet rather powerful methods of advertising- electronic mail advertising is used by agencies of every kind and sizes. In our previous weblog, we've already mentioned commonplace errors that e mail entrepreneurs make, and if you are amongst the ones marketers who aren't deriving the results that you are looking for, then you definately is probably making the mistake of no longer measuring the overall performance of your e mail advertising and marketing marketing campaign. Even in case you are having the proper SMTP server for bulk emails, and a strong e mail marketing campaign, in case you are not measuring and checking the right metrics, you can no longer get the anticipated consequences.
Email advertising metrics to know
What are the ones metrics that you want to look for? Here’s what you want to recognize.
Click-through rate (CTR)
This metric helps you become aware of the number of humans who have clicked the hyperlink in your email, making it one of the most crucial metrics to evaluate the performance of your email marketing campaign. Utilizing reliable bulk email marketing software can aid in effectively tracking and analyzing these metrics for better campaign optimization.
Open charge
What you’re doing here is monitoring the quantity of electronic mail subscribers, those who've opened any precise e-mail. With the help of open charge, you can identify how engaged your subscribers are, and how well your situation lines are formed.
Conversion price
SMTP server for bulk emails
With every e-mail, you want your receivers to take some precise motion, and this is wherein knowing the conversion fee makes absolute experience. With the help of conversion fee, you can come to understand how many people opened your e-mail and took the specific motion.
Bounce price
Here, you're going to recognize about the nice of your subscriber’s list. Bounce charge allows you song how many emails were despatched however not recied by using your subscribers, in case your e-mail jump rate is excessive, you’re more likely to have an email list of fake subscribers.
Measuring unsubscribers
SMTP server for bulk emails
After receiving an e mail from you, a few humans can unsubscribe and understanding this range is notably critical. When you notice humans unsubscribing, this will be frustrating revel in. But, then again, it is important to note that you are filtering your e mail listing.
List growth price
Your e-mail listing needs to develop always with the proper subscribers, growth fee of list is simple to song and it's far crucial to discover greater dependable subscribers for your e-mail listing.
Engagement over time
One of the most not unusual questions requested through email entrepreneurs- what-s the proper time to ship email? Well, this could be identified with the assist of tracking engagement over the years. You can come to recognise about the time you are getting the highest click charges for emails.
Forwarding price
SMTP server for bulk emails
With this, you can come to recognize how many brand advocates you have got. Forwarding rate offers you with the information on what number of human beings have either shared your social media posts or have forwarded your e mail to someone.
Develop emblem advocates, it’s a extremely good e mail marketing method.
ROI
This needs to be tracked by means of each e-mail marketer, it tells you the entire tale how your email campaigns are performing.
The backside line
Tracking those metrics is important to realize the performance of your e mail campaigns. On the opposite hand, you can come to realize if there are any particular changes which you want to make to your emails. Track these metrics and make your e-mail advertising and marketing increasingly successful.
Get in Touch
E: [email protected] Skype: murtazind WhatsApp: +91 8780-424-579
Also read: - https://mails2inbox.com/top-email-marketing-metrics-that-can-help-you-measure-results/
3 notes
·
View notes
Text
UNLIMITED SMTP SERVER
GOT 1MILLION TRAFFIC IN 2H
EMAIL MARKETING
TRMSG
#ellie 20william#im 20not 20ready 20for 20season 202 20or 20left 20behind 20episode#tessLL#EIE#email campaign#emaildatabase#promo emails#whatsapp#email marketing#smt persona#smtp server#steddie#trmsg#bulk email sender#bulk email servicebu#bulk email marketing services
2 notes
·
View notes
Text
For more information you can visit our website: www.digitalaka.com
0 notes
Text
Kugelsicherer SMTP Server auf Deutsch: Erhalten Sie unbegrenzte Posteingangszustellungen mit smtpget.com https://www.youtube.com/watch?v=07pvzS08hm4 Um sich mit weiteren Informationen zu verbinden, besuchen Sie hier Website – https://smtpget.com/ Skype – https://rb.gy/fb09 WhatsApp – https://rb.gy/srec0 Telegramm – @smtpgets
#Bulletproof SMTP-Server auf Deutsch#Kugelsicherer SMTP-Server für Massenmailing auf Deutsch#Bulletproof SMTP-Serveranbieter auf Deutsch#Bulletproof SMTP Service Provider auf Deutsch#Leistungsstarker kugelsicherer SMTP-E-Mail-Server auf Deutsch
0 notes
Text
1 note
·
View note
Text
Another Internet Whitepaper
I'm just gonna get into there is no way to preface this.
1) content should be hosted in their own countries for which they are meant.
2) therefore the website should split into Nation->Sub-nation sections. So things for Michigan would be closer to those in Michigan. With U.S.->Michigan.
--"independent" Nations are just gonna have to deal with being lumped together into a united region. It's simply physics.
--country wide servers and clouds, and worldwide services will still be available; but we need to develop protocols to make it easier to distribute data and declutter the internet-cloud.
3) a separate Intranet for official use and security will need to be developed alongside this while also being completely disconnected from the worldwideweb.
4) Splits;
IP Addresses redesign;
[Country/Region]:[State/Province]:[individual]
[Individual] will need to be controlled by local The Internet Assigned Numbers Authority (IANA) branches; likely to be reassigned to DMVs and SoSs.
5) Separate protocols For;
Streaming Services
Social Media Services
Bidirectional Interactions (like games and Virtual Machines)
Pornography needs to be completely identifiable by textual Web address.
5) you local region will be defaulted, but can be changed by the browser and not be hard-wired in.
Not indicating a region will automatically default to the local internet.
So typing in FBI.GOV in the U.S. will lead to the FBI website, and if you type it in the UK it'll lead to Mi:5 or something.
6) Social Media protocols will have to be integrated with the E-Mail SMTP protocols. Which will encourage a more decentralized internet. This will *also* have to find a way to work with phone text messages.
7) Cable TV and Streaming services will have to use the same protocols.
8) Because there's phone integration here; a phone number may have to be closer to a social security number going forward. Which will both be bad for animosity, but allow for people to not need login information.
-- This will technically also need to apply to your House; which will have to have an assigned street address.
9) all of these need to be obfuscated to casual observers.
10) this will deprecate our phone companies and require them to work with cable TV and internet companies in order to create more equitable protocols.
11) the current IP address and Domain Registry systems need to be deprecated; as it does not suit its original purpose.
[.xxx] will be assigned for all "adult" materials and be required for ALL "adult materials" posted online.
[.app] will be assigned for appstores.
[.store] for marketplaces like Amazon, eBay, and whatever else.
[.bank] will be for banking and credit purposes
[.social] will be for social media
[.stream] will be for streaming materials,
[.np] for non-profit use only.
[.donation] for donation collections and Kickstarter like services.
[.pay] for payment services like PayPal
Non "adult materials" can be streamed through other "front ends" .
13) These human readable extensions will be simplified on the backend to reduce the total data envelope size.
14) single digit ip-adresses will have to be regulated for use for high-capacity uses. These will need to be "extended" protocols that different services can use.
This will help even out everybody's data envelopes. This will have to be part of a cloud service that can be used by anybody that needs it. With certain restrictions that are deemed necessary by local and federal governments and international treaty reasons.
15) limits on how algorithms and "bots" can ping anything at one time need to be addressed or regulated.
This will be a massive undertaking with the cooperation of all the other governments around the world.
And will be a very lucrative endeavor at the end of it all.
This is just an outline to describe the form the future internet should take and can be changed or modified as required; especially for things I cannot see.
The current corporations will be expected to develop a plan of actions in tandem with current regulatory authorities; failure to do so will create a need for an ultimatum, which we all wish to avoid.
We're also going to need to find ways to encourage competition in these sectors so that they can be upgraded and modified as needed by local areas instead of waiting on these companies to bother with it.
13 notes
·
View notes
Text
What Is SMTP in WordPress? And How To Configure It?
SMTP (Simple Mail Transfer Protocol) for WordPress is a method used to send emails from your WordPress site. By default, WordPress uses the PHP mail function to send emails, but SMTP provides a more reliable and secure way to send emails.
It ensures that your emails are delivered successfully to the recipients' inbox, rather than being marked as spam. Setting up SMTP for WordPress involves configuring your WordPress site to use an SMTP server to send emails.
What Is SMTP In WordPress?
https://jpcdn.it/img/tiny/10ef05c741f88df7bc52eaab714af71c.jpg
SMTP (Simple Mail Transfer Protocol) in WordPress refers to the method used for sending emails from your WordPress website. By default, WordPress uses the built-in PHP mail function to send emails, but SMTP provides a more reliable and secure alternative.
SMTP ensures that your emails are delivered successfully to recipients' inboxes and helps prevent them from being marked as spam. With SMTP configured in WordPress, emails are sent through an external SMTP server, typically provided by your web hosting provider or a third-party email service.
This setup allows you to specify authentication credentials, such as a username and password, ensuring that your emails are authenticated and trusted by email providers.
How To Configure SMTP In WordPress?
Configuring SMTP in WordPress involves several steps. Here's a general guide:
https://jpcdn.it/img/3fa5ee365d1c835a3a542dab41533f3e.jpg
For more information or buying fast and secure hosting visit the www.ozoweb.com, Ozoweb provides various services like Linux Shared Web Hosting, Domain Registration, VPS, and Dedicated Servers. They focus on offering these services at prices that are affordable for everyone. Their goal is to make sure their prices are unbeatable while still providing high-quality hosting services and products that fit their customers' needs and budgets.
#OZOHosting#lowest price hosting in india#Cheap web hosting jaipur#cheap shared web hosting india#free web hosting india#affordable linux web hosting india
2 notes
·
View notes
Text
Cybersecurity Giant Zscaler Investigates Alleged Data Breach

UPDATE - Zscaler reiterates no impact or compromise to customers, production, or corporate environments. Zscaler and an independent third-party incident response firm continue to work on forensics analysis of the quarantined test environment. Cybersecurity powerhouse Zscaler launched an investigation on Wednesday after a notorious hacker, known as IntelBroker, announced on a popular cybercrime forum that they were "selling access to one of the largest cyber security companies". Although the hacker's post did not explicitly name the company, they later confirmed in the forum's shoutbox that the target was Zscaler. IntelBroker has offered to sell "confidential and highly critical logs packed with credentials", including SMTP access, PAuth access, and SSL passkeys and certificates, for $20,000 in crypto. This alarming claim has raised concerns about the potential severity of the alleged breach.
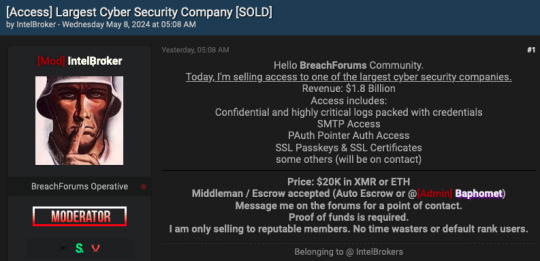
Zscaler's Initial Response and Investigation
Upon learning about the hacker's claims, Zscaler promptly announced the launch of an investigation. A few hours after the investigation commenced, the company announced that it had found no evidence of its customer and production environments being compromised.
Update on Investigation Findings
In its latest update, Zscaler confirmed that its production, customer, and corporate environments were not impacted. The company stated, "Our investigation discovered an isolated test environment on a single server (without any customer data) which was exposed to the internet. The test environment was not hosted on Zscaler infrastructure and had no connectivity to Zscaler's environments. The test environment was taken offline for forensic analysis."
IntelBroker's Recent Claims and Track Record
IntelBroker recently claimed to have stolen US State Department and other government data from the tech firm Acuity. While Acuity confirmed a breach, the company stated that only non-sensitive, old information was compromised. IntelBroker has been making claims about obtaining US government data for more than a year. In several cases, the data has been confirmed to come from third-party service providers, but in some instances, the data was allegedly obtained directly from government systems. However, some of the hacker's claims seemed false or exaggerated. Read the full article
2 notes
·
View notes
Text
How to Pick the Most Trustworthy SOCKS5 Proxy
With the continuous development of network technology, network security issues have become increasingly prominent. In this era of information explosion, how to protect personal privacy, break through network restrictions, and improve the security of data transmission has become the focus of attention of the majority of netizens. As an advanced network proxy protocol, SOCKS5 proxy is gradually becoming the patron saint of modern network security.
Definition and advantages of SOCKS5 proxy
SOCKS5 proxy is a network proxy technology that allows users to route their network traffic through an intermediate server (proxy server). This proxy not only hides the user’s real IP address and provides anonymity, but also helps users access network resources that may not be accessible when connected directly. SOCKS5 proxy supports multiple network protocols, including but not limited to HTTP, HTTPS, FTP, and SMTP, making it a versatile network tool. At the same time, it provides authentication functions, enhances the security of network communications, and becomes an effective tool for protecting user privacy and breaking through geographical restrictions.
How SOCKS5 proxy works
The working principle of SOCKS5 proxy is to establish a two-way, reliable TCP connection between the client and the server through a proxy server. When the client makes a request to the server, the proxy server collects the client’s request data and forwards it to the target server. The data returned by the server is sent to the client through the proxy server using the TCP protocol. Since the SOCKS5 proxy uses a reliable transmission protocol, the integrity, accuracy and reliability of the data can be guaranteed. In addition, the SOCKS5 proxy also supports the UDP protocol, enabling it to handle more types of network requests, including live streaming, online games, etc.
Application scenarios of SOCKS5 proxy
SOCKS5 proxy shows its unique advantages in many fields, including but not limited to the following aspects:
1. E-commerce field
In e-commerce platforms, different countries or regions may have different regulations and restrictions on the purchase and sale of products. Using SOCKS5 proxy can help merchants circumvent these geographical restrictions and access blocked or restricted markets. At the same time, encrypted connections through proxy servers can improve the security of data transmission and protect user privacy.
2. Data collection
For data analysis and researchers, SOCKS5 proxy can easily bypass geographical restrictions and access blocked content or services, thereby collecting more comprehensive data. This is of great significance for market research, public opinion analysis and other work.
3. Network security
SOCKS5 proxy plays an important role in protecting user privacy and security. By hiding the user’s real IP address and providing data encryption, SOCKS5 proxy can protect the user’s device from network attacks. At the same time, it can also act as a barrier to filter out some malicious traffic and protect the user’s network security.
4. Entertainment and Games
For users who like online games and entertainment, SOCKS5 proxy can speed up access to overseas game and entertainment platforms and enhance the user’s gaming experience. By selecting a proxy node close to the target server, the data transmission path can be shortened and network latency can be reduced.
How to choose and use SOCKS5 proxy
When choosing and using SOCKS5 proxy, users need to pay attention to the following points:
1. Choose a reliable service provider
Make sure that the selected service provider has a good reputation and credibility, and the proxy servers provided are stable and widely distributed. Avoid using free or unknown proxy services to avoid network security risks.
2. Choose the right package according to your needs
Different users have different needs, so you need to choose the right package according to your own situation. For example, for users who need high-speed network connection, you can choose a high-performance proxy server package; for users who need to access multiple regions, you can choose a package that supports multi-region IP addresses.
3. Correctly configure proxy settings
Before using SOCKS5 proxy, you need to correctly configure the proxy settings. This includes setting the IP address, port number and other information of the proxy server in the operating system, browser or other network applications. Only after ensuring that the configuration is correct can the proxy service be used normally.
4. Check the proxy connection regularly
In order to ensure the stability and security of the proxy connection, users need to check the status of the proxy connection regularly. If you find that the connection is abnormal or the speed is slow, you should contact the service provider in time for troubleshooting and resolution.
Conclusion
With the continuous development of network technology, SOCKS5 proxy, as the guardian of modern network security, will play an increasingly important role in protecting user privacy, breaking through network restrictions, and improving data transmission security. As users, we should correctly choose and use SOCKS5 proxy services to ensure that our network security and privacy are protected to the greatest extent.
0 notes
Text
Things to look for while choosing an SMTP service provider
Bulk email marketing services - Email promoting is, without a slight trace of uncertainty, a vital component of the showcasing procedure of organizations. From SMBs to Fortune 500 organizations, all know about the influence of email, and the individuals who are not, are passing up one of the best promoting channels that can support return for money invested. SMTP administrations have expanded in ubiquity because of clear reasons, the manner in which it works on sending messages, the speed, and precision, just to give some examples.

As there are different SMTP specialist co-ops out there, it tends to be hard for organizations to find a dependable and the right specialist co-op.
Finding the right SMTP specialist co-op
Thus, here we present to you a few genius tips that can make the method involved with finding a specialist co-op simple and bother free.
Experience matters!
At the point when you will contact a specialist co-op, you are without a doubt going to run over a lot of vows to convey the best administrations. In any case, sadly, not all SMTP specialist co-ops are probably going to address your issues. This is where you really want to zero in on the experience of any specialist organization. More the experience, the better the assistance experience you will get. Talk with your specialist co-op about the experience and how the administrations helped different organizations.
Understanding your business needs
Each business has its own remarkable help and server necessities. Just the one with the right experience will actually want to comprehend and meet your remarkable prerequisites.
Invest energy with the specialist co-op to examine your administration and email promoting needs, an accomplished specialist organization will think of a few extraordinary ideas that will make the ways for additional open doors for your business. Bulk email marketing software
Get to investigate the choices
When you know about the experience of your specialist co-op and your business needs are examined, it becomes vital to investigate the accessible choices or plans that best accommodated your business. SMTP administrations are accessible at a great many plans, these plans can likewise be tweaked to meet your requirements. When you have a few intends to investigate, you will actually want to distinguish which one tackles your motivation!
Get in Touch
E: [email protected] Skype: murtazind WhatsApp: +91 8780-424-579
Also read: - https://mails2inbox.com/things-to-look-for-while-choosing-smtp-service-provider/
#best smtp server for bulk mailing#best bulk email sending software#smtp server for bulk email#smtp service provider india#bulk email server services#smtp server india#bulk email marketing services#bulk email marketing software#best smtp service provider#bulk email server solutions
0 notes
Text
SafeNet Protocols Package (SPP) project
Still in cardboard boxes...
(Last update : Networks Managers who want to use SPP for security reasons should make sure that every other protocols are only allowed through VM or light sandboxes to do it properly. Attackers may use regular https internet links, in order to fish through e-mail boxes. As every SPP contents are certified, only a regular https website can carry malicious contents. As long as any content provider hasn't been hacked...)
Introduction / initial statement
The goal is not to completely erase https, smtp etc. It is to make a side network where there is no point watching clients.
Brainstorming
Because all contents are legal and certified, and clients can't publish publicly accessible contents on SPP (except if servers can be access by legal authorities). Banish clients tracking from SafeNet and a lot of other details... So, contents providers will have to find other ways to get money using SafeNet protocols. I'm sure they will ... SafeNet anonymous user identities, only known by SafeNet managers. Transitives mail box address ... optional VPN and optional onion-like access features (crypted) ... Integrate firewall with an "allow only SPP" button. We still have to work on softwares updates strategy ... A dedicated OS including virtualisation of other OS and access to regular network only by using a Virtual Machine.
The fact that the goal is to make it useless to track clients doesn't mean it will be immediately the case. The network will probably needs some time to insure that users can't do anything illegal or harmfull before : completely reject legal authorities access to clients or users "useless" data and just shot "everything" down on illegitimate legal requests.
Using only SafeNet on the host reduces risks to get virus as every contents are certified. You still can get a virus by opening a .exe file coming from an e-mail... Or if you still use other protocols on the host machine. A "no .exe or .zip or .vbs or .bat or docm or .dat or files without extensions etc. in e-mails => *allow only ... " policy stays on study. As SPP is not a network made for professional use but for private users. Find a way to allow e-mail boxes safely are a tuff challenge for SPP.
One of the major interest of SPP is that it allow you to watch videos or listen to audio contents with a garanty that you will not be tracked. As it was the case on Hertzien TVs. So, it may save audio/video industry.
SPP network cannot be use for remote access. Legal authorities should be convinced that there is no use of such a thing on a 100% SPP machine and may still use regular networks and protocols.
There also will be a policy about microphones and cameras but I think you get the idear. - Break your phone integrated microphone and use a removable hand-free kit to get a microphone... -
Contents Providers must respect more rules if they want to publish contents using SPP... They also have to financially contribute to SPP management. It's supposed to become a new market. A way to ensure better user experience and rich a new customer base.
The main protocol "shttps" will use same languages as https : html5, css3, JS, PHP, SQL etc. So, porting will be simplified. Developers can simply make a copy of their https website root directory and erase, from files, every stuff that is not allowed on shttps. Or make a completely new website using the same languages.
SPP contracts says that users data collected by contents providers can't be passed to third parts*. Yes, this means contents providers have to do everything by their own and can't sell users data.
*Except for anonymous SPP coordinates and only to deliver the service provided or receive a payment. We still have to work on that too.
SPP policies can evolve to become more permissives, in order to allow needed stuff, or to become more restrictives, in case of any legal flaw observation.
There is also a Public Health dimension to this project. Panem et circences ...
Taking commissions on financial transactions may help to reduce the cost of publication authorization requests.
First SPP e-mail virus
**** Nothing here ! *****
Solution found ! : "E-Mail through SPP" services providers will now have to check every attached contents : check if the extension is allowed as before and at least check if open it doesn't throw any errors, as "file may be corrupt" or stuff like that.
Fantasy statment : Microsoft also add one more safety protocol on .docm files. You now have to complete a puzzle that say "I know that asking peoples to unlock .docm files is a common way to hack a computer !" in order to unlock files.
Pirates strike back
****** Nothing here ! *****
So, we banned .txt files too...
Pirates strike back again
***** Nothing here ! ****
So, E-mail services providers also have to block any message containing scripts command or lines of code, especially batch or VBS. Senders must receive a message indicating that their message has been blocked because "In order to be allowed, your message should not contain .XXXX code lines, even in a simple text field or attached documents". "If you want to send this kind of information to a SPP user, through SPP network (SPPN), you need to become a certified provider and use publicly access documents. Or at least documents made accessible to our bots and Content Watch Offices. Or use an e-mail address certified by the SafeNet Identity Certification Service."
Demonstration : ***** NOTHING HERE ! ******
SafeNet E-mail services
Apps of "E-mail through SPP" service providers must now separate e-mail coming from Certified SafeNet Users from e-mail coming from a regular Internet user. Users are informed that the sender of message coming from uncertified senders may be impossible to identify. So, they should never follow instructions coming from a sender that they are not able to certify.
E-mail clients (apps) can't use nicknames instead of the real sender e-mail address except for the real name of Certified SPP Users.
E-mail services should never make it possible to join a real identity to a SPP anonymous identity. Therefore, SPP users must manage two mailbox address... To avoid errors the same application can't manage both real identities and anonymous identities. Providers can develop two applications that are mostly identical except for a very limited quantity of code lines. In order to make it easier to maintain both apps. Apps logo of both these apps must make it easy to know when you are using your "anonymous" mail box and your official mail box.
As a reminder, SPP Anonymous Identities are still attached to a real person, but only SafeNet Identity Certification Services (SICS) can make links between Real and Anonymous identities.
Anonymous Identities can only receive e-mails from SPP contents providers and cannot send mails. This may evolve if it happen to become essential for providers to get users direct returns. Which means a return whose not using their websites forms.
0 notes
Text

Der aktuell ausgewertete Bedrohungsindex aus dem Dezember zeigt die Bedrohung durch FunkSec, eine Ransomware-Gruppe, die mit KI agiert. In Deutschland ist Formbook mehr und mehr inaktiv, während andere Malware aufstiegen, etwa Anubis - Ein Banking-Trojaner mit Ransomware-Funktionen. Der aktuelle Global Threat Index für Dezember 2024 zeigt die jüngsten Aktivitäten von Cyberkriminellen. In diesem Monat machte FunkSec auf sich aufmerksam, ein aufstrebender Ransomware-as-a-Service (RaaS)-Betreiber, der künstliche Intelligenz für seine Machenschaften nutzt. In Deutschland spielte der im November noch mit einem Anteil von 18,5 Prozent an allen Malware-Infektionen dominierende Infostealer Formbook urplötzlich keine Rolle mehr und wurde von FakeUpdates (3,3 Prozent) von der Spitze verdrängt. Auf Platz zwei lag das Bot-Netz Androxgh0st (2,3 Prozent), Platz drei belegte Remcos (2 Prozent). Durch Formbooks vermeintliche Inaktivität im letzten Monat flachte die Machtverteilung in der hiesigen Malware-Landschaft deutlich ab. Neue Malware an der Spitze der Angriffe FunkSec ist durch seine Aktivitäten an die Spitze derjenigen Ransomware-Gruppen gerückt, die sich doppelter Erpressung bedienen. Mit über 85 Opfern allein im Dezember 2024 hat FunkSec seine Konkurrenten in puncto Volumen übertroffen. Check Point Research (CPR) hat jedoch viele dieser Behauptungen als „recycelt“ oder nicht verifiziert eingestuft, was Zweifel an der Glaubwürdigkeit der Gruppe aufkommen lässt. FunkSec, das mit Algerien in Verbindung gebracht wird, scheint von finanziellen Gewinnen und hacktivistischen Ideologien angetrieben zu werden. Seine KI-gestützten Taktiken lassen darauf schließen, dass Cyberkriminelle sich bei ihren Coups immer mehr auf fortschrittliche Technologien verlassen. Aufstrebende Malware in Deutschland - ↑ FakeUpdates (3,36 %) - Fakeupdates (alias SocGholish) ist ein in JavaScript geschriebener Downloader. Er schreibt die Nutzdaten auf die Festplatte, bevor er sie ausführt. Fakeupdates führte zu einer weiteren Systemkompromittierung durch zahlreiche zusätzliche Malware. - ↑ Androxgh0st (2,33 %) – Androxgh0st ist ein Bot-Netz, welches auf Windows-, Mac- und Linux-Plattformen zielt. Für die Infiltration nutzt Androxgh0st mehrere Sicherheitslücken aus, die insbesondere bei PHPUnit, Laravel Framework und Apache Web Server gegeben sind. Die Malware stiehlt sensible Informationen wie Twilio-Kontoinformationen, SMTP-Anmeldeinformationen, AWS-Schlüssel und dergleichen. Sie verwendet Laravel-Dateien, um die erforderlichen Informationen zu sammeln. Es gibt verschiedene Varianten, die nach unterschiedlichen Informationen suchen. - ↑ Remcos (2,05 %) - Remcos ist ein RAT, der erstmals 2016 in der freien Wildbahn auftauchte. Remcos verbreitet sich über bösartige Microsoft Office-Dokumente, die an SPAM-E-Mails angehängt sind, und ist darauf ausgelegt, die UAC-Sicherheit von Microsoft Windows zu umgehen und Malware mit hohen Rechten auszuführen. Gefährliche Mobile Malware ↑ Anubis – Ein Banking-Trojaner mit Ransomware-Funktionalität, der auf Android-Geräte abzielt. ↑ Necro – Ein Trojaner, der Malware installiert und Premium-Abonnements in Rechnung stellt. ↑ Hydra – Ein Banking-Trojaner, der Zugangsdaten stiehlt, indem er gefährliche Berechtigungen auf Android-Geräten ausnutzt. Die aktivsten Ransomware-Gruppen Die Zunahme von Ransomware-Gruppen dominiert weiterhin die Cybersicherheitslandschaft. Daten von „Shame-Sites“ über erfolgreiche Ransomware-Angriffe zeigen, dass FunkSec im Dezember die aktivste Gruppe war und für 14 Prozent aller veröffentlichten Angriffe verantwortlich war. - FunkSec – Durch den Einsatz von KI und doppelter Erpressung übertraf FunkSec andere Gruppen mit umstrittenen 85 Opfer-Postings. - RansomHub – RansomHub ist für seine aggressiven Kampagnen bekannt und konzentriert sich auf Systeme wie VMware ESXi und setzt ausgeklügelte Verschlüsselungsmethoden ein. - LeakeData – LeakeData ist ein neuer Akteur, der eine Website für eindeutige Webdatenlecks (DLS) betreibt, und kombiniert Ransomware-Vorfälle mit umfassenderen Erpressungsaktivitäten. Passende Artikel zum Thema Read the full article
0 notes
Text
What Is SMTP in WordPress? And How To Configure It?
SMTP (Simple Mail Transfer Protocol) for WordPress is a method used to send emails from your WordPress site. By default, WordPress uses the PHP mail function to send emails, but SMTP provides a more reliable and secure way to send emails.
It ensures that your emails are delivered successfully to the recipients' inbox, rather than being marked as spam. Setting up SMTP for WordPress involves configuring your WordPress site to use an SMTP server to send emails.
What Is SMTP In WordPress?
SMTP (Simple Mail Transfer Protocol) in WordPress refers to the method used for sending emails from your WordPress website. By default, WordPress uses the built-in PHP mail function to send emails, but SMTP provides a more reliable and secure alternative.
SMTP ensures that your emails are delivered successfully to recipients' inboxes and helps prevent them from being marked as spam. With SMTP configured in WordPress, emails are sent through an external SMTP server, typically provided by your web hosting provider or a third-party email service.
This setup allows you to specify authentication credentials, such as a username and password, ensuring that your emails are authenticated and trusted by email providers.
How To Configure SMTP In WordPress?
Configuring SMTP in WordPress involves several steps. Here's a general guide:
https://jpcdn.it/img/3fa5ee365d1c835a3a542dab41533f3e.jpg
For more information or buying fast and secure hosting visit the www.ozoweb.com, Ozoweb provides various services like Linux Shared Web Hosting, Domain Registration, VPS, and Dedicated Servers. They focus on offering these services at prices that are affordable for everyone. Their goal is to make sure their prices are unbeatable while still providing high-quality hosting services and products that fit their customers' needs and budgets.
#OZOHosting#lowest price hosting in india#Cheap web hosting jaipur#cheap shared web hosting india#free web hosting india#affordable linux web hosting india
2 notes
·
View notes