#SCP-ACL
Explore tagged Tumblr posts
Text
File: Halloween
SCP#: ACL
Code Name: Michael Myers the Immortal Murderer
Object Class: Safe
Special Containment Procedures: SCP-ACL is contained at Site-AF within a 5x5 meter room. The room is not given basic furniture, entertainment, food dispenser, or even a bed as SCP-ACL does not need to eat, rest, or relieve himself in any way. Furthermore, there is no reason for anyone to enter SCP-ACL's containment room outside of testing reasons. Outside of the containment room are 4 guards armed with cryo blasters as they are the most effective method against SCP-ACL.
Any testing regarding SCP-ACL must be approved by at least one Level 3 Clearance Foundation staff member. SCP-ACL must be sedated before being transported to a testing chamber as he will become unyieldingly and aggressive otherwise.
Description: SCP-ACL is an anomalous humanoid named Michael Myers who was, by unknown means, mutated from a normal human boy to an immortal psychopath hellbent on killing everyone even remotely associated with him. whether it be an old friend, a distant family member, or someone who just so happened to be near his house they will become a target. As stated before he is physically immortal, no matter how much time passes or what damage he receives, he will not die no matter what. The worst anyone can do to SCP-ACL is tire him down, but he will always get back up in the end.
Foundation testing has shown that SCP-ACL does not regenerate form the damage he receives, it instead fades over time as if never existing to begin with. How this works or what is the cause is unknown though it should be noted that the more sever the wound the more time it takes to "disappear". Most notably, SCP-ACL loses his killing drive when his mask is taken away from him, the farther the mask is the more docile he becomes. SCP-ACL does seem to be coated with small traces of TRE Radiation and most shockingly abyssal partials. However, neither are in a large enough amount to cause SCP-ACL's anomalous effects. Essentially, there is no scientific or anomalous explanation to why SCP-ACL is the way he is, further testing is required.
SCP-ACL was discovered in 1978 when a series of murders were reported in the small town of [data expunged] near the same time the psycho killer known as Michael Myers escaped custody. Because of his strange and often anomalous behavior during incarceration Dr. [data expunged] ordered a Foundation agent to find and investigate him. upon finding SCP-ACL who was already going on a killing spree, the agent reported that SCP-ACL was killed himself quite a few times but always got back up. After falling off the balcony of a house, he retreated into the local forest allowing the Foundation agent to sedate and capture him.
After his containment there was still the issue of the police searching for SCP-ACL; to stop this, a D-Class was given facial surgery to resemble SCP-ACL as well as the same clothes and the same mask he wore. The D-Class was taken to the outskirts of the town, and shot in the same spots SCP-ACL was and left there to die. Once the local police found the body Michael Myers was declared dead and the case of his murders closed. The truth however is that SCP-ACL is in Foundation custody and is used as a test subject for counter measures against immortal hostile anomalies. The Ethics Committe has approved this despite their usual compassion towards anomalous humanoid. Like most they find him irredeemable due to his disregard for human life and endless drive to kill everyone he comes across.
.
SCP: Horror Movie Files Hub
#DZtheNerd#SCP: Horror Movie Files#SCP Foundation#SCP Fanfiction#SCP AU#SCP#Halloween Series#Michael Myers#Horror Movie#Slasher Movie#SCP-ACL#Safe#Site-AF
6 notes
·
View notes
Text
Object Classification
I’ve not much to debate today. Abandonment this early is a wee bit silly though, so DOWN THE RABBIT HOLE WE GOOOOOO.
My current issue is that I genuinely only had two ideas…sooooo…what can we do that doesn’t need some grand wind up?
I could make a new object.
Maybe detail the one I made before?
Nah
That’s boring
Let’s doooooooooo…object classification. Not quite what I was aiming for, but I literally don’t know what else to do.
I mean. Gotta do it at some point, right?
——————————————————————————————————
Ok, here’s the thing: I can’t just steal the SCP classification system. This isn’t SCP
But
I need something. I can’t just do nothing and expect results.
I also don’t know what to write.
Uhhhhhhhh
So in SCP, we have an advanced classification system (i mean we didn't always but still). It’s a good idea, so I’ll casually…yoink it
As cited from: https://scp-wiki.wikidot.com/object-classes
“
What is the Locked Box Test? The Locked Box Test is an informal guideline used to determine an object's most appropriate Object Class. It goes like this:
If you lock it in a box, leave it alone, and nothing bad will happen, then it's probably Safe.
If you lock it in a box, leave it alone, and you're not entirely sure what will happen, then it's probably Euclid.
If you lock it in a box, leave it alone, and it easily escapes, then it's probably Keter.
If it is the box, then it's probably Thaumiel.
Extending the analogy to other Object Classes:
If it used to need a box, but no longer does, it's Neutralized. If this is because of a deliberate decision by the Foundation, it was probably Decomissioned.
If it turns out it never needed a box in the first place, it's probably Explained.
If you can't fit it in a box and it's about to end the world, then it's probably Apollyon.
If you could have locked it in a box but chose not to, then it's probably Archon.
If you can't fit it in a box but that's not a big deal, then it's probably Ticonderoga.
If you're not sure what box to put it in yet, it's probably Pending.
“
…Let’s get the main four. We are still missing the sub categories but we are deriving that anyway so we will ignore it (we may need more classifications later, but I think we have enough).
Here’s a bunch of important acronyms btw:
“ODS” (open door security): If I disable the security measures and open the door, how beefy do the precautions need to be?
“BSA” (breach security assurance): Should a containment breach happen, what’s the likelihood this escapes too?
“CSA” (current safety assessment): How sufficient are current security measures?
“PD” (physical danger): If I touch it, how bad are the side effects?
“UD” (usage danger): If I use it correctly, how bad are the side effects? This applies only to the user.
“SD” (sensory danger) {unfortunately, I couldn’t think of anything for a T}: If I don’t touch it, but still get some other sensory effect, how bad are the side effects?
“ACL” (advised caution level): In general, how much of a pain of an ass is this fuckin’ thing?
In reality, ACL and ODS are the only important ones. The rest are extra.
Thaumiel - These things actually help the DCT. Imagine that!
ODS - No thiefs allowed! (not relevant for Thaumiel)
BSA - Release (in the event of a breach)
CSA - Released
PD - Beneficial
UD - Beneficial
SD - Beneficial
ACL - Soothing
Safe conversion: Safe objects aren’t that hard to contain. Ironically, ‘safe’ objects aren’t always *safe*, but let’s pretend they are.
ODS - None
BSA - Content
CSA - Sufficient OR (for Ticonderoga or Archon) Not possible
PD - None OR No concern
UD - No known usage OR Not usable
SD - None
ACL - None
Low end Euclid: Euclids are pretty…meh. It’s too had to tell (without looking at sub categories) if it’s just able to escape in very few edge cases or if it’s just something that just can in many. Does that make sense? Probably not. Regardless, euclid has been split in twine.
ODS - Few OR Some (think the difference between 1-2 guards and 3-6 guards)
BSA - Bored
CSA - Nearly Sufficient
PD - Little concern
UD - Painful
SD - Bearable
ACL - little
High End Euclid:
ODS - Beefy
BSA - Scratching
CSA - Keep watch
PD - Persistent
UD - Hurtful
SD - Migraine
ACL - Caution
Keter: *Slaps hood* This bad boy- *flatline noises*
ODS - Maximum
BSA - Guaranteed
CSA - Breach risk
PD - Extreme
UD - Extreme
SD - Do not approach
ACL - Danger
For the other 7, I’m only going to do ACL. I may come back to apollyon and do a full list for it later
Neutralized: ACL - Destroyed
Decommissioned: ACL - Terminated
Explained: ACL - Removed
Apollyon: ACL - Curtains closed
Archon: ACL - Overwatch
Ticonderoga: ACL - Public
Pending: ACL - {Not Found}
This list isn’t perfect, but it’s better than the nothing we had before. Is this a good system? What would you change/add?
#scp#horror#horror comedy#writing#writing ideas#obligatory useless tag that has literally zero purpose
0 notes
Text
Just emerged as the only survivor of my D&D group's Homebrew SCP one-shot, even though I've downed half a bottle Ypióca™
(Brazilian rum. 1L 40% acl/vol)
I'm so surprised at how alert I still am, I'm not even sure where I am between drowsy and tipsy, but by God, I still got my shit together.
I should've died, but TWO NAT 20's saved my ass before I could be horrifically murdered by mannequins. Bless the SCP Foundation and their timing.
1 note
·
View note
Note
Re: The Many Weird Degrees of Dr. Trent Acles
Consider this- Yes, he has some “How is this a degree” degrees, but he also has more… Obscure degrees. I’m talking a hit like ‘pataphysics, metaphysics, memetics, antimemetics… Basically, Oodako being a whole-ass SCP Foundation researcher.
no no I love that. Oodako just starts collecting degrees on any and everything that catches his or Skull's eye and he ends up with a tentacle in the weirdest fields imaginable
158 notes
·
View notes
Note
Random idea: Izuku, but as SCP-682.

I'm combining these two because I can!!
- the HPSC has several wide spread divisions all ranging in classifications.
- most were public but some only few highly regarded members knew of.
- such as the commissions hero training program or more importantly the Anomaly Containment Lab.
- the public was unaware of the unique sub division that contains, experiments and researches any non human being that exhibits a quirk or an anomaly outside of quirks.
- little does anyone know one had escaped and managed to detour the Commission from recapturing it. But that was in the early days when it was still referred to as subject 9.
- subject 9 went by Nezu nowadays.
- but the ACL has moved away from such a loss they had a new prized subject nowadays.
- subject 68-2.
- S- 68-2 started out as an anonymous shifting form but through experimentation and consumption of flesh S- 68-2 soon took on a form of a young boy.
- S- 68-2 was neither human nor a quirk user, S- 68-2 was anomaly.
- it had a higher level of understanding, recognizing patterns, codes and microexpressions. It could also communicate through multiple complicated means.
- the intelligence of S- 68-2 had yet to be recorded but had reached close to the levels of S- 9.
- S- 68-2 had an incredible ability to tear or shred apart anything and use it for energy. Experiments has revealed that things consumed by S- 68-2 can contribute to S- 68-2 outward traits and appearance. See experiment delta 14.1.
- S- 68-2 also retains great speed, strength and reflexes. Levels yet to be tested.
- it also has formed a hatred or distaste for all members of the facilities, yet be determined if the sentiment is limited to the facilities.
- S- 68-2 exhibits incredible regeneration, allowing it to retain full functions at up to 87% deterioration or rot. Allowing the facility to easily contain it in such a state.
- further knowledge of S- 68-2 unknown.
- S- 68-2 whereabouts unknown.
- last seen directly before the break in of July 15th 2XXX.
- Nezu often finds breaking into ACL cathartic
- most of the time he finds strange non sentient experiments but never did he think he would find what he believed to be a young human boy.
- nor would he have believe he would rescue, hide and teach said boy.
- this boy would later be known as Izuku.
#the boy behind the glass au#candle answers#ask the candle#bnha au#bnha#bnha headcannons#bnha nezu#bnha izuku
102 notes
·
View notes
Text
The Philadelphia Flyers: A Saga, Section IV: Defensemen
Link to Table of Contents
Travis Sanheim, #6
Nickname(s): Sanny, Sandra (TK’s nickname)
Shot: LH
Draft class: 17th overall, 2014
Sanny is a relatively quiet dude. I couldn’t find a single mic’d up clip for him.

source
Sometimes, just like the other Travis, he’ll fall into the boards under his own power, but who doesn’t? He and Philly Myers played together in Valley, which is why AV likes the pair for the flyers. Right now, however, because of the current dumpster-fire that’s going on, they are not currently playing together.
Ivan Provorov, #9, Permanent Alternate Home Captain***
Nickname(s): Provy, Workhorse (he doesn’t miss a shift)
Shot: LH
Draft class: 7th overall, 2015
Provy is the glue that is holding this defense together at this point. The poor dude plays over 20 minutes a night. He’s considered an “offensively gifted defenseman (source), and out of every defenseman, we are excited to see him grow and develop. This was evident by him scoring the double OT winner against the Islanders in the 2020 SCP.
I could rant about how this current mess is hindering his development, BUT I won’t.

source
Clean shaven Provy and beard Provy are two different people, honestly. You can look at this mood board of Provy faces.
Watch Provy mic’d up here.
Sam Morin, #55
Nickname(s): None, as of right now
Shot: LH
Draft class: 11th overall, 2013
Originally, I didn’t have Morin on the list, but he was called up and surprised us all. Basically, Morin has been through A LOT, to say the least. He’s torn the same ACL twice. Twice. He had to go through rehabilitation twice. On top of that, he was moved to forward this season because of the full defense, that is, until we realized our defense sucks, so he was eventually moved back. So on top of trying to get back into the flow of the game, he was tasked with figuring out how to adjust to a new position. He’s also 6′6, so there’s that toughness, feisty, solid aspect to him. There’s just so much we could say about him.

source
On March 27th, 2021, eight years after he was drafted, he scored his first NHL goal. And it was the game winner against the Rangers. Everyone, and I mean everyone, was extremely happy for him. All his teammates were so thrilled, and all the fans were, too.

source
This goal was so special because it reminded the Flyers that good things can happen to them. They needed a good uplift after the horrible stretch they’ve had. Please look at this gif set because it makes me so happy I could combust.
The Flyers really needed that feel-good moment. One that made that crappy month of March seem like ages ago. And their faces showed pure happiness that I have not seen in a very long time. Morin also said it was the best day of his life, so.
This is a pretty good article summarizing his career and the events leading up to the GWG.
PS: Do you see Ghost’s face? We will miss him.
Justin Braun, #61
Nickname(s): Brauner
Shot: RH
Draft class: 201st overall, 2007
Brauner, our other main shot blocker. He was traded to us from the San Jose Sharks in 2019. Also a relatively quiet guy, so I don’t have much to say about him.

source
Honorary mention: Matt Niskanen, was #15
Here comes my Matt Niskanen babble.
That dude was so tough.

source
INSANE. He got hit in the face with a puck, but came out with stuff shoved up his nose and a cage to protect it. And then fed Coots for a goal. That was one of two assists listed there. Yes, we miss him.
When he retired, we were all BIG sad.
If you’re wondering how big of an impact he had: Jamey represents all of us right now.
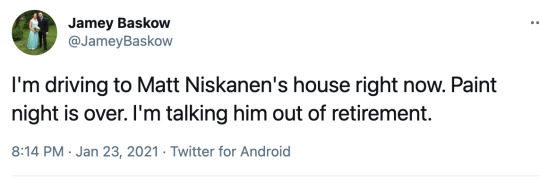
source
If you scroll through his name on Twitter, all you will see are Flyers fans begging for his return. Yes, the Flyers defense is that bad. Were they supposed to be this bad? Hmmm.
No.
aNYWAYS, Nisky if you get bored or miss hockey or scoring or being awesome, we have a spot wide open for you. Literally. There were three (3) Rangers players left unattended in front of Carter. Please and thank you <3
10 notes
·
View notes
Text
not me forgetting everything I own lol
@zigadoodle @mer-acle @goblin-the-clown @tragedyanddust @thestarryfalls @unnoticedunawarestillhere @fl0ral-ghost @rapple-all-year-round
Tagged by @xxfangirl365xx for this, ty ty for the tag 🫶
Tagging 🙃 -> @frankierosbackbends @weallpartyatybcpatricksfuneral @spraypaintstainonawhitewall @hesitantvampirealien and @ anyone who wants to give this a go 🫶
69 notes
·
View notes
Text
Cisco CCNA Security 210-260 Certification Exam Details
Cisco 210-260 certifications are globally accepted and add significant value to your IT professional. The certification offers you a serious knowledge of each of the workings with the network models and also the devices that are utilized from it. NWexam.com is proud to offer for you the ideal Cisco Exam Guides.
The Cisco 210-260 Exam is challenging, and thorough preparation is important for achievement. This cert guide was created to enable you to plan the CCNA Security certification exam. Its content has an in depth list of the individuals covered around the Professional exam. The following tips for your IINS might help make suggestions with the study process for the certification.
To have Implementing Cisco Network Security certification, you need to pass IINS 210-260 exam. This exam is produced remembering the input of pros in the market and reveals how Cisco products are found in organizations around the globe. 210-260 Implementing Cisco Network Security Exam Summary
? Exam Name: Implementing Cisco Network Security ? Exam Code: 210-260 ? Exam Price: $300 (USD) ? Duration: 90 mins ? Number of Questions: 60-70 ? Passing Score: Variable (750-850 / 1000 Approx.) 210-260 Exam Guide: ? How I pass Cisco 400-201 Certification in first attempt? ? How to arrange for 400-201 exam on CCIE Supplier Topics covered in the CCNA Security 210-260 Exam [1]. Security Concepts (12%)
1 Common security principles a) Describe confidentiality, integrity, availability (CIA) b) Describe SIEM technology c) Identify common security terms d) Identify common network security zones 2 Common security threats a) Identify common network attacks b) Describe social engineering c) Identify malware d) Classify the vectors of internet data loss/exfiltration 3 Cryptography concepts a) Describe key exchange b) Describe hash algorithm c) Assess symmetric and asymmetric encryption d) Describe digital signatures, certificates, and PKI 4 Describe network topologies a) Campus area network (CAN) b) Cloud, wide area network (WAN) c) Data center d) Small office/home office (SOHO) e) Network to protect an on-line environment
[2]. Secure Access (14%) 1 Secure management a) Compare in-band and out-of band b) Configure secure network management c) Configure and verify secure access through SNMP v3 using an ACL d) Configure and verify security for NTP e) Use SCP for file transfer 2 AAA concepts a) Describe RADIUS and TACACS+ technologies b) Configure administrative access on a Cisco router using TACACS+ c) Verify connectivity on a Cisco router to a TACACS+ server d) Explain the combination of Active Directory with AAA e) Describe authentication and authorization using ACS and ISE 3 802.1X authentication a) Identify the functions 802.1X components 4 BYOD a) Describe the BYOD architecture framework b) Describe the function of mobile phone management (MDM)
[3]. VPN (17%)
1 VPN concepts a) Describe IPsec protocols and delivery modes (IKE, ESP, AH, tunnel mode, transport mode) b) Describe hairpinning, split tunneling, always-on, NAT traversal 2 Remote access VPN a) Implement basic clientless SSL VPN using ASDM b) Verify clientless connection c) Implement basic AnyConnect SSL VPN using ASDM d) Verify AnyConnect connection e) Identify endpoint posture assessment 3 Site-to-site VPN a) Implement an IPsec site-to-site VPN with pre-shared key authentication on Cisco routers and ASA firewalls b) Verify an IPsec site-to-site VPN [4]. Secure Routing and Switching (18%)
1 Security on Cisco routers a) Configure multiple privilege levels b) Configure Cisco IOS role-based CLI access c) Implement Cisco IOS resilient configuration 2 Securing routing protocols a) Implement routing update authentication on OSPF 3 Securing the control plane a) Explain the function of control plane policing 4 Common Layer 2 attacks a) Describe STP attacks b) Describe ARP spoofing c) Describe MAC spoofing d) Describe CAM table (MAC address table) overflows e) Describe CDP/LLDP reconnaissance f) Describe VLAN hopping g) Describe DHCP spoofing 5 Mitigation procedures a) Implement DHCP snooping b) Implement Dynamic ARP Inspection c) Implement port security d) Describe BPDU guard, root guard, loop guard e) Verify mitigation procedures 6 VLAN security a) Describe the protection implications of the PVLAN b) Describe the security implications of your native VLAN

[5]. Cisco Firewall Technologies (18%)
1 Describe operational strengths and weaknesses of the different firewall technologies a) Proxy firewalls b) Application firewall c) Personal firewall 2 Compare stateful vs. stateless firewalls a) Operations b) Function of hawaii table 3 Implement NAT on Cisco ASA 9.x a) Static b) Dynamic c) PAT d) Policy NAT e) Verify NAT operations 4 Implement zone-based firewall a) Zone to zone b) Self zone 5 Firewall features on the Cisco Adaptive Security Appliance (ASA) 9.x a) Configure ASA access management b) Configure security access policies c) Configure Cisco ASA interface security levels d) Configure default Cisco Modular Policy Framework (MPF) e) Describe modes of deployment (routed firewall, transparent firewall) f) Describe types of implementing high availability g) Describe security contexts h) Describe firewall services
[6]. IPS (9%)
1 Describe IPS deployment considerations a) Network-based IPS vs. host-based IPS b) Modes of deployment (inline, promiscuous - SPAN, tap) c) Placement (positioning with the IPS inside the network) d) False positives, false negatives, true positives, true negatives 2 Describe IPS technologies a) Rules/signatures b) Detection/signature engines c) Trigger actions/responses (drop, reset, block, alert, monitor/log, shun) d) Blacklist (static and dynamic) [7]. Content and Endpoint Security (12%)
1 Describe mitigation technology for email-based threats a) SPAM filtering, anti-malware filtering, DLP, blacklisting, email encryption 2 Describe mitigation technology for web-based threats a) Local and cloud-based web proxies b) Blacklisting, URL filtering, malware scanning, URL categorization, web application filtering, TLS/SSL decryption 3 Describe mitigation technology for endpoint threats a) Anti-virus/anti-malware b) Personal firewall/HIPS c) Hardware/software encryption of local data
What type of questions is on the Cisco 210-260 exams? ? Single answer multiple choice ? Multiple answer multiple choice ? Drag and Drop (DND) ? Router Simulation ? Testlet CCNA Security 210-260 Practice Exam Questions. Grab an awareness from these Cisco 210-260 sample questions and boost your 210-260 exam preparation towards attaining an Implementing Cisco Network Security Certification. Answering these sample questions is likely to make informed about the types of questions you can anticipate for the actual exam. Doing practice with CCNA Security IINS questions and answers ahead of the exam wherever possible is the key to passing the Cisco 210-260 certification exam.
210-260 Implementing Cisco Network Security Sample Questions:-
01. Which type of traffic inspection uses pattern matching? a) Signature-based inspection b) Statistical anomaly detection c) Protocol verification d) Policy-based inspection Answer: a
02. Which from the following authentication mechanisms can be used with SNMP version 3? (Choose two) a) AES b) MD5 c) 3DES d) SHA Answer: b, d
03. Is there a most typical type of spoofing? a) Application spoofing b) Service spoofing c) DHCP spoofing d) Ip spoofing e) MAC address spoofing Answer: d 04. Which option mitigates VLAN Hopping and Double-tagging VLAN Hopping Attacks? a) Ensuring that the native VLAN in the trunk ports differs from the native VLAN in the user ports b) Making sure that the native VLAN with the trunk ports is the same as the native VLAN from the user ports c) Setting a corner port to “off.” d) Enabling auto trunking negotiations. Answer: a
05. The kind of attack is prevented if you configure Secure Shell (SSH)? a) DoS session spoofing b) Man-in-the-middle attack c) Dictionary attack d) Buffer overflow Answer: b
06. Which in the following is not part of an IKE Phase 2 process? a) Main mode b) Specifying a hash (HMAC) c) Running DH (PFS) d) Negotiating the transform set to utilize Answer: a
07. What are three key features of URL filtering? (Choose three) a) Predefined URL categories b) Malware protection c) Custom URL categories d) Dynamic content analysis Answer: a, c, d 08. What sort of VPN technologies are apt to be employed in a site-to-site VPN? a) SSL b) TLS c) HTTPS d) IPsec Answer: d
09. Which two statements are true of the present threatscape? (Choose two) a) We now have marketplace is the only industry that is certainly exempt from attack. b) The threat landscape is actually evolving. c) Due to recent improvements in security technology, password attacks not play a significant role in the threatscape. d) It is so complex that it must be impossible to catalog in its entirety. Answer: b, d
10. Which three statements are true about firewalls? (Choose three) a) If your system in a security zone is compromised, a firewall can help offer the attack within that zone. b) A firewall can prevent undesired access to a network security zone. c) Modern firewalls give you a complete network security solution. d) Firewalls typically will protect you between and within network security zones. e) A firewall can introduce a performance bottleneck. Answer: a, b, e
For more information about CCNA Security (210-260 IINS) go to see this useful web portal.
1 note
·
View note
Note
Its Valentines day. I wish you love and appreciation.
Also I decided fuck it in the honor of Valentines day, lets rank SCP: HMF ships. Rank them from
Love this - 5
Its alright - 4
Mid - 3
NO! - 2
THEY ARE DISGUSTING - 1
Here they are!
Iris (SCP-105) x Meri (SCP-166)
Haselhurst (SCP-049) x Herbert West (SCP-AEF)
SCP-682 X SCP-079
Jack Frost (SCP-AEL ) X Winter of 83 (SCP-AWS)
Slender Man (SCP-ARN X Other Mother (SCP-AFX)
SCP-096 x The Rake (SCP-AFR)
Godzilla (SCP-ABQ) X Mothra (SCP-ABU)
Chucky (SCP-AAV) X Art the Clown (SCP-ACM)
IT (SCP-AAF) X Creeper (SCP-ACA)
Danny Torrence (SCP-ADV) X Carrie (SCP-ACP)
Junji Ito - BEEHIVE (SCP-AQC) X Candyman (SCP-AEU)
Leprechaun (SCP-ACU) X A pot of Gold
Sam (SCP-AHA) X Michael (SCP-ACL)
Iris (SCP-105) x Meri (SCP-166) - 5. Traumatized lesbians having to go through a lot of shit but still finding comfort and love in one another. In other words, they are adorable. What's not to love?
Haselhurst (SCP-049) x Herbert West (SCP-AEF) - 0, no... Just no.
SCP-682 X SCP-079 - 4. They're just friends who care for one another a whole lot. Despite their differences they see each other as equals in a world full of mistakes. Thats why despite both wanting to kill all live and themselves, both can't bear the idea of the other dying. Really sweet if you think about it, but still more of a friendship than anything.
Godzilla (SCP-ABQ) X Mothra (SCP-ABU) - 5. Enough said.
Chucky (SCP-AAV) X Art the Clown (SCP-ACM) - 0... WHAT THE ACTUAL FU-?!
IT (SCP-AAF) X Creeper (SCP-ACA) - 1, They would just kill each other.
Danny Torrence (SCP-ADV) X Carrie (SCP-ACP) - 3. Perhaps if they did meet things would have ended better for them both. I'll consider making a tale about it IF it makes sense in the end.
Junji Ito - BEEHIVE (SCP-AQC) X Candyman (SCP-AEU) - 0, Fuck no. Candyman kills everyone equally.
Leprechaun (SCP-ACU) X A pot of Gold - 4. Sure, not that the Foundation will let him have his gold back.
Sam (SCP-AHA) X Michael (SCP-ACL) - 3. At best Michael will sense a sort of kinship due to them both being evil and mostly active during Halloween. Like a big brother little brother dynamic, kinda sweet if you think about it and ignore the slaughtering of the innocent.
#DZtheNerd#Ask#Ask Response#Response#SCP: Horror Movie Files#SCP Foundation#Ships#fandom ships#shipping#SCP Ship#SCP-105 x SCP-166#Iris x Meri#valentines day#happy valentines#valentines#Happy Holidays
4 notes
·
View notes
Text
Download Windows keygen (keygen) latest version SP7,

💾 ►►► DOWNLOAD FILE 🔥🔥🔥 In this article Applies to Windows Server , Windows Server , Windows 10 build and later Most authentication in Windows environments is done with a username-password pair, which works well for systems that share a common domain. When working across domains, such as between on-premises and cloud-hosted systems, it becomes vulnerable to brute force intrusions. OpenSSH includes tools to help support key based authentication, specifically: ssh-keygen for generating secure keys ssh-agent and ssh-add for securely storing private keys scp and sftp to securely copy public key files during initial use of a server This document provides an overview of how to use these tools on Windows to begin using key-based authentication with SSH. About key pairs Key pairs refer to the public and private key files that are used by certain authentication protocols. SSH public key authentication uses asymmetric cryptographic algorithms to generate two key files — one "private" and the other "public". The private key files are the equivalent of a password, and should stay protected under all circumstances. If someone acquires your private key, they can sign in as you to any SSH server you have access to. The public key is what is placed on the SSH server, and may be shared without compromising the private key. Key based authentication enables the SSH server and client to compare the public key for a user name provided against the private key. If the server-side public key can't be validated against the client-side private key, authentication fails. Multi-factor authentication may be implemented with key pairs by entering a passphrase when the key pair is generated see user key generation below. The user will be prompted for the passphrase during authentication. The passphrase is used along with the presence of the private key on the SSH client to authenticate the user. Important A remote session opened via key based authentication does not have associated user credentials and hence is not capable of outbound authentication as the user, this is by design. Host key generation Public keys have specific ACL requirements that, on Windows, equate to only allowing access to administrators and System. On first use of sshd, the key pair for the host will be automatically generated. By default the sshd service is set to start manually. If no algorithm is specified, RSA is used. A strong algorithm and key length should be used, such as Ed in this example. At this point, you'll be prompted to use a passphrase to encrypt your private key files. The passphrase can be empty but it's not recommended. The passphrase works with the key file to provide two-factor authentication. For this example, we're leaving the passphrase empty. Use ssh-agent to securely store the private keys within a Windows security context, associated with your Windows account. To start the ssh-agent service each time your computer is rebooted, and use ssh-add to store the private key run the following commands from an elevated PowerShell prompt on your server: By default the ssh-agent service is disabled. Configure it to start automatically. Make sure you're running as an Administrator. Important It is strongly recommended that you back up your private key to a secure location, then delete it from the local system, after adding it to ssh-agent. The private key cannot be retrieved from the agent providing a strong algorithm has been used, such as Ed in this example. If you lose access to the private key, you will have to create a new key pair and update the public key on all systems you interact with. The name and location of the file depends on whether the user account is a member of the local administrators group or a standard user account. The following sections cover both standard and administrative users. You can copy your public key using the OpenSSH scp secure file-transfer utility, or using a PowerShell to write the key to the file. The example below copies the public key to the server where "username" is replaced by your username. You'll need to use the password for the user account for the server initially. The ACL on this file needs to be configured to only allow access to administrators and System. The example below copies the public key to the server and configures the ACL where "username" is replaced by your user name. This only applies to administrator accounts and must be user instead of the per user file within the user's profile location. Once the example PowerShell commands have been run, the user can connect to the sshd host from any client that has the private key.
1 note
·
View note
Text
Download Windows keygen (keygen) latest version 3X4,

💾 ►►► DOWNLOAD FILE 🔥🔥🔥 In this article Applies to Windows Server , Windows Server , Windows 10 build and later Most authentication in Windows environments is done with a username-password pair, which works well for systems that share a common domain. When working across domains, such as between on-premises and cloud-hosted systems, it becomes vulnerable to brute force intrusions. OpenSSH includes tools to help support key based authentication, specifically: ssh-keygen for generating secure keys ssh-agent and ssh-add for securely storing private keys scp and sftp to securely copy public key files during initial use of a server This document provides an overview of how to use these tools on Windows to begin using key-based authentication with SSH. About key pairs Key pairs refer to the public and private key files that are used by certain authentication protocols. SSH public key authentication uses asymmetric cryptographic algorithms to generate two key files — one "private" and the other "public". The private key files are the equivalent of a password, and should stay protected under all circumstances. If someone acquires your private key, they can sign in as you to any SSH server you have access to. The public key is what is placed on the SSH server, and may be shared without compromising the private key. Key based authentication enables the SSH server and client to compare the public key for a user name provided against the private key. If the server-side public key can't be validated against the client-side private key, authentication fails. Multi-factor authentication may be implemented with key pairs by entering a passphrase when the key pair is generated see user key generation below. The user will be prompted for the passphrase during authentication. The passphrase is used along with the presence of the private key on the SSH client to authenticate the user. Important A remote session opened via key based authentication does not have associated user credentials and hence is not capable of outbound authentication as the user, this is by design. Host key generation Public keys have specific ACL requirements that, on Windows, equate to only allowing access to administrators and System. On first use of sshd, the key pair for the host will be automatically generated. By default the sshd service is set to start manually. If no algorithm is specified, RSA is used. A strong algorithm and key length should be used, such as Ed in this example. At this point, you'll be prompted to use a passphrase to encrypt your private key files. The passphrase can be empty but it's not recommended. The passphrase works with the key file to provide two-factor authentication. For this example, we're leaving the passphrase empty. Use ssh-agent to securely store the private keys within a Windows security context, associated with your Windows account. To start the ssh-agent service each time your computer is rebooted, and use ssh-add to store the private key run the following commands from an elevated PowerShell prompt on your server: By default the ssh-agent service is disabled. Configure it to start automatically. Make sure you're running as an Administrator. Important It is strongly recommended that you back up your private key to a secure location, then delete it from the local system, after adding it to ssh-agent. The private key cannot be retrieved from the agent providing a strong algorithm has been used, such as Ed in this example. If you lose access to the private key, you will have to create a new key pair and update the public key on all systems you interact with. The name and location of the file depends on whether the user account is a member of the local administrators group or a standard user account. The following sections cover both standard and administrative users. You can copy your public key using the OpenSSH scp secure file-transfer utility, or using a PowerShell to write the key to the file. The example below copies the public key to the server where "username" is replaced by your username. You'll need to use the password for the user account for the server initially. The ACL on this file needs to be configured to only allow access to administrators and System. The example below copies the public key to the server and configures the ACL where "username" is replaced by your user name. This only applies to administrator accounts and must be user instead of the per user file within the user's profile location. Once the example PowerShell commands have been run, the user can connect to the sshd host from any client that has the private key.
1 note
·
View note
Text
Cisco 500-750 CNSS Dumps
The latest Cisco Network Security Specialist 500-750 CNSS Dumps are new cracked by PassQuestion team. If you are using our Cisco Network Security Specialist 500-750 CNSS Dumps, then you will be able to get a clear idea of the real exam scenario, it will help you succeed in the Cisco 500-750 exam on the first attempt. With the help of Cisco Network Security Specialist 500-750 CNSS Dumps that we are providing, you will be able to improve your preparation without going through any trouble. It is highly recommended for you to use Cisco Network Security Specialist 500-750 CNSS Dumps multiple times so you can strengthen your current preparation level and pass your Cisco 500-750 exam successfully.
Cisco Network Security Specialist v1.0 (500-750)
Cisco Network Security Specialist v1.0 (CNSS 500-750) is a 90-minute exam that tests a candidate's knowledge and skills related to secure network infrastructure, understanding core security concepts, managing secure access, VPN encryption, firewalls, intrusion prevention, web and email content security, and endpoint security.
Exam Information
Exam Code: 500-750 CNSS Exam Name: Cisco Network Security Specialist Duration: 90 minutes Languages: English
Exam Topics12% 1.0 Security Concepts
1.1 Common security principles 1.1.a Describe Confidentiality, Integrity, Availability (CIA) 1.1.b Describe SIEM technology 1.1.c Identify common security terms 1.1.d Identify common network security zones 1.2 Common security threats 1.2.a Identify common network attacks 1.2.b Describe social engineering 1.2.c Identify malware 1.2.d Classify the vectors of data loss/exfiltration 1.3 Cryptography concepts 1.3.a Describe key exchange 1.3.b Describe hash algorithm 1.3.c Compare & contrast symmetric and asymmetric encryption 1.3.d Describe digital signatures, certificates and PKI 1.4 Describe network topologies 1.4.a Campus Area Network (CAN) 1.4.b Cloud, Wide Area Network (WAN) 1.4.c Data Center 1.4.d Small office/home office (SOHO) 1.4.e Network security for a virtual environment
14% 2.0 SecureAccess
2.1 Secure management 2.1.a Compare In-band and out of band 2.1.b Configure secure network management 2.1.c Configure and verify secure access through SNMP v3 using an ACL 2.1.d Configure and verify security for NTP 2.1.e Use SCP for file transfer 2.2 AAA concepts 2.2.a Describe RADIUS & TACACS+ technologies 2.2.b Configure administrative access on a Cisco router using TACACS+ 2.2.c Verify connectivity on a Cisco router to a TACACS+ server 2.2.d Explain the integration of Active Directory with AAA 2.2.e Describe authentication & authorization using ACS and ISE 2.3 802.1X authentication 2.3.a Identify the functions 802.1X components 2.4 BYOD 2.4.a Describe the BYOD architecture framework 2.4.b Describe the function of Mobile Device Management (MDM)
17% 3.0 VPN
3.1 VPN concepts 3.1.a Describe IPSec protocols and delivery modes (IKE, ESP, AH, tunnel mode, transport mode) 3.1.b Describe hairpinning, split tunneling, always-on, NAT Traversal 3.2 Remote Access VPN 3.2.a Implement basic clientless SSL VPN using ASDM 3.2.b Verify clientless connection 3.2.c Implement basic AnyConnect SSL VPN using ASDM 3.2.d Verify AnyConnect connection 3.2.e Identify Endpoint Posture Assessment 3.3 Site-to-Site VPN 3.3.a Implement an IPSec site-to-site VPN with pre-shared key authentication on Cisco routers and ASA firewalls 3.3.b Verify an IPSec site-to-site VPN
18% 4.0 Secure Routing & Switching
4.1 Security on Cisco Routers 4.1.a Configure multiple privilege levels 4.1.b Configure IOS role-based CLI access 4.1.c Implement IOS resilient configuration 4.2 Securing routing protocols 4.2.a Implement routing update authentication on OSPF 4.3 Securing the control plane 4.3.a Explain the function of control plane policing 4.4 Common Layer 2 attacks 4.4.a Describe STP attacks 4.4.b Describe ARP spoofing 4.4.c Describe MAC spoofing 4.4.d Describe CAM Table (MAC Address Table) overflows 4.4.e Describe CDP/LLDP reconnaissance 4.4.f Describe VLAN hopping 4.4.g Describe DHCP spoofing 4.5 Mitigation procedures 4.5.a Implement DHCP snooping 4.5.b Implement dynamic ARP inspection 4.5.c Implement port security 4.5.d Describe BPDU Guard, Root Guard, Loop Guard 4.5.e Verify mitigation procedures 4.6 VLAN security 4.6.a Describe the security implications of a PVLAN 4.6.b Describe the security implications of a native VLAN
18% 5.0 Cisco Firewall Technologies
5.1 Describe operational strengths and weaknesses of the different firewall technologies 5.1.a Proxy firewalls 5.1.b Application firewall 5.1.c Personal firewall 5.2 Compare stateful vs. stateless firewalls 5.2.a Operations 5.2.b Function of the state table 5.3 Implement NAT on Cisco ASA 9.x 5.3.a Static 5.3.b Dynamic 5.3.c PAT 5.3.d Policy NAT 5.3 e Verify NAT operations 5.4 Implement zone-based firewall 5.4.a Zone to zone 5.4.b Self zone 5.5 Firewall features on the Cisco Adaptive Security Appliance (ASA) 9.x 5.5.a Configure ASA Access Management 5.5.b Configure security access policies 5.5.c Configure Cisco ASA interface security levels 5.5.d Configure default Modular Policy Framework (MPF) 5.5.e Describe modes of deployment (routed firewall, transparent firewall) 5.5.f Describe methods of implementing High Availability 5.5.g Describe security contexts 5.5.h Describe firewall services
9% 6.0 IPS
6.1 Describe IPS deployment considerations 6.1.a Network based IPS vs. host based IPS 6.1.b Modes of deployment (inline, promiscuous - SPAN, tap) 6.1.c Placement (positioning of the IPS within the network) 6.1.d False positives, false negatives, true positives, true negatives 6.2 Describe IPS technologies 6.2.a Rules/Signatures 6.2.b Detection/Signature engines 6.2.c Trigger actions/responses (drop, reset, block, alert, monitor/log, shun) 6.2.d Block list (static & dynamic)
12% 7.0 Content and Endpoint Security
7.1 Describe mitigation technology for email-based threats 7.1.a SPAM filtering, anti-malware filtering, DLP, block listing, email encryption 7.2 Describe mitigation technology for Web-based threats 7.2.a Local & cloud-based Web proxies 7.2.b Block listing, URL-filtering, malware scanning, URL categorization, Web application filtering, TLS/SSL decryption 7.3 Describe mitigation technology for endpoint threats 7.3.a Anti-Virus/Anti-Malware 7.3.b Personal Firewall/HIPS 7.3.c Hardware/Software encryption of local data
0 notes
Video
youtube
Video Timelines ______________________________________________________________ 00:10 Course Curriculum 13:05 Introduction to Linux. 25:13 Directory structure 43:04 RHEL 8 Installation Registration Link: https://www.redhat.com/wapps/ugc/regi... 56:46 Remote Server OS Installation 1:10:57 Booting Process 1:16:10 Subscription manager & Updating Linux packages 1:27:33 Accessing Linux Server GUI & CLI 1:41:57 Switching users in multiuser target 1:55:00 Standard Input, Output and Error 2:07:36 Basic Commands - cat, cd, ls, ..etc 2:46:10 Creating soft links and hard links 3:00:30 Text Editors nano & vim 3:20:00 Compressing and un-compressing files & folders 3:40:48 Getting Help from command Line User Interface 3:56:14 Grep command regular expressions 4:12:15 YUM Repository configuration 4:19:18 SSH Server & Client configuration 4:41:20 Configure Key-based authentication 4:45:00 NTP configuration 4:52:31 SCP | Copying files to remote server 5:02:54 Listing and Managing Linux processes (ps and top commands) 5:20:53 File and Directory permissions 5:33:24 Creating standard Linux partitions 5:46:47 Deleting standard Linux partitions 5:47:55 Creating PVs, VGs, and LVM 6:05:01 Extend Logical Volumes non-destructively 6:15:56 Reduce LVM size - lvreduce 6:21:52 Swap Memory Explained | How to Create swap partition & extend 6:34:14 Creating Users and Groups | User Administration 7:08:59 Modify user properties | Password age 7:20:10 Deleting users and groups 7:21:34 Access control list - ACL 7:36:00 Special Linux file permissions Set-GID, Set-UID, Sticky Bit 7:43:22 Sudo access - sudoers policy 8:04:34 Linux Networking | Assign Static IP 8:24:31 Firewall Rules | Firewalld | firewall-cmd 8:39:59 SELinux - Security Enhanced Linux 9:04:11 Shell Scripts : 9:13:51 if statement 9:19:35 for loop 9:20:00 Positional parameters 9:23:00 Exit codes 9:26:26 Scheduling future tasks - crontab 9:42:05 Installing and updating packages using RPM & YUM -------- Linux Containers Podman, Buildah, Skopeo and Runc -------- 9:58:09 Find and retrieve container images from a remote registry 10:11:04 Inspect container images 10:16:32 Buildah Building the Images 10:30:34 Dockerfile | Build Buildah Images using Dockerfile 10:34:40 Attach persistent storage to a container
0 notes
Text
Download File From Ssh To Mac

Terminal User Guide
Ssh Download File
Download File From Ssh To Local Machine
Download File From Ssh To Mac Mojave
Download File Using SSH. We can use SCP command to download the from remote server. For example I am going to download a file called “test.tar.gz” which is located on remote server example.com /opt directory in our local system /var directory. You can replace the values as per your requirement. Download Termius - SSH client for macOS 10.10.0 or later and enjoy it on your Mac. Termius is more than a mere SSH client – it’s a complete command-line solution that’s redefining remote access for sysadmins and network engineers.
In Terminal, you can move and copy files locally or remotely using the mv, cp, and scp command-line tools.
Tip: It’s easier to move and copy files using the Finder. See Organize files in folders.
Ssh Download File
Move a file or folder locally
In the Terminal app on your Mac, use the mv command to move files or folders from one location to another on the same computer. The mv command moves the file or folder from its old location and puts it in the new location.
For example, to move a file from your Downloads folder to a Work folder in your Documents folder:
% mv ~/Downloads/MyFile.txt ~/Documents/Work/MyFile.txt
You can also change the name of the file as it’s moved:
% mv ~/Downloads/MyFile.txt ~/Documents/Work/NewFileName.txt
See the mv command man page.
Copy a file or folder locally
In the Terminal app on your Mac, use the cp command to make a copy of a file.
For example, to copy a folder named Expenses in your Documents folder to another volume named Data:
% cp -R ~/Documents/Expenses /Volumes/Data/Expenses
The -R flag causes cp to copy the folder and its contents. Note that the folder name does not end with a slash, which would change how cp copies the folder.
See the cp command man page.
Copy a file or folder remotely
In the Terminal app on your Mac, use the scp command to copy a file or folder to or from a remote computer.
scp uses the same underlying protocols as ssh.
For example, to copy a compressed file from your home folder to another user’s home folder on a remote server:
% scp -E ~/ImportantPapers.tgz [email protected]:/Users/username/Desktop/ImportantPapers.tgz
You’re prompted for the user’s password.
The -E flag preserves extended attributes, resource forks, and ACL information.
The -r flag, which isn’t used in this example, causes scp to copy a folder and its contents.

Download File From Ssh To Local Machine
See the scp command man page.
Download File From Ssh To Mac Mojave
See alsoOpen or quit Terminal on MacOpen new Terminal windows and tabs on MacExecute commands and run tools in Terminal on Mac

0 notes
Text
Addendum X-9
Incident Report: ADS.1181
Date of Incident: February 2nd, 2021
Scenario Explanation: Dr. Zeek proposed an experiment to have SCP-ADS fed meat samples of SCP-AXA to see the reaction.
Incident: The swarm of SCP-ADS fed on the SCP-AXA samples as they typically do with meet. After 1 hour nothing happens, however after an additional ten minutes one of the SCP-ADS instances starts viciously attacking another. They are all other SCP-ADS instances start attacking each other disregarding their previous hierarchy. Fearing losing all SCP-ADS samples Mobile Task Force Lambda-12 "Pest Control" was sent in with chemical spray guns. The spray guns were armed with canisters were filled with chemicals known to calm SCP-ADS instances. However, the chemicals didn't work, and the SCP-ADS instances started spraying their sticky silk all over the MTF units.
Instead of biting and eating bits of their flesh the SCP-ADS instances seemed to be instead assimilating and mutating the flesh of the MTF units with their silk. As if like living organisms not only did the silk attack and stick to their armor but slid in between it and onto their skin fusing together. This resulting in quick mutations of crimson moth wings and appendages growing out of random parts of the MTF units. Unfortunately, they quickly broke the containment glass and got out leading to 7 researchers' casualties before the room was locked down.
Afterwards AFA-2 units armed with chemical spray guns containing necrosis venom canisters were deployed. During their arrival, researchers observing everything form the cameras reported that the affected Foundation staff stopped screaming continued to mutate, they were most likely KIA at this point. Some had their bodies torn apart giving birth to mutant SCP-ADS instances. Each one of different sizes and different degrees of disfigurement and bodily mutations. Other victims turned into severely mutated human moth hybrids that crawled on the walls fought with one another and started at the camera's seemingly directly at the researchers from time to time. Finally, the AFA-2's made it to the contained area and started spraying and killing off the infected Foundation staff and SCP-ADS instances.
Afterwards the surviving instances and eggs of SCP-ADS were taken to a secured research lab to see if any were infected and help grow those that weren't. Within a week the SCP-ADS population was stabilized again and allowed back into the artificial environment containment cell.
Recommendation: NEVER FEED SCP-ADS MEAT FROM SCP-AXA AGAIN!
***
Incident Report: ADS.8709
Date of Incident: February 18th, 2021
Scenario Explanation: A Foundation staff member in charge of feeding SCP-ADS instances used a metal crate to carry the meat despite it being standard procedure not to do that.
Incident: After leaving the containment cell, the SCP-ADS instances start using the silk to grab the meat and eat like normal. However, as soon as they are done some fly to the crate now noticing it is made of metal. They all then stand aside and allow the King to fly toward the metal. the King releasing white silk, there have been no other recordings of SCP-ADS instances ever doing anything like this.
The King uses the white silk to cut up the metal into tiny pieces and start attaching the pieces to his body. The end result is the SCP-ADS instance having a large metal body and uses it to bash through the glass with ease. Foundation security tried to take it down but not only was SCP-ADS's new body able to deflect bullets, but it created razor wire like tendrils that lashed out and ripped apart security and unfortunate researchers.
This went on for an unfortunate amount of time leading to a Site wide containment breach allowing SCP-AAJ, several SCP-AAK instances, a single SCP-AAN instance, SCP-ACL, three SCP-ADF-E instances, and several SCP-AEW instances. While most of these instances wreaked havoc on the Site the mutated SCP-ADS instance was seen on camera recordings and by surviving Foundation staff to have been eating instances of SCP-AAK, SCP-AAN, and SCP-ADF-E.
Mobile Task Force Epsilon-11 "Nine-Tailed Fox" finally arrived on Site after 12 hours of the containment breach. Thanks to being given the proper equipment they were able to establish re-containment of all anomalies except for the "KING" SCP-ACS instance. Instead [data expunged by Order of the O5 Council].
Recommendation: Find the moron that used a metal crate and have him regulated to D Class. We need more test subjects for a new experiment on SCP-217, anyways.
.
Go back to SCP-ADS
.
SCP: Horror Movie Files Hub
#DZtheNerd#SCP: Horror Movie Files#SCP Foundation#SCP Fanfiction#SCP AU#SCP#SCP OC#SCP-ADS#SCP-AXA#Scriptures of Rotten Flesh and Cybernetic Bones#SCP-217
0 notes