#SCIM 2.0 Standard
Explore tagged Tumblr posts
Text
The Evolution of Identity and Access Management: SCIM, SAML vs. OpenID Connect, and Integration Challenges
In the ever-evolving digital landscape, Identity and Access Management (IAM) has become crucial for organizations to ensure security, compliance, and efficiency. The increasing reliance on technology has necessitated the development of sophisticated IAM protocols and standards. This blog will explore a SCIM example, compare SAML vs. OpenID Connect, and discuss the challenges and solutions associated with IAM integration.

Understanding SCIM: An Example
System for Cross-domain Identity Management (SCIM) is a standard protocol designed to simplify the management of user identities in cloud-based applications and services. SCIM automates the exchange of user identity information between identity providers and service providers, ensuring seamless integration and synchronization.
SCIM Example
Consider an organization using multiple cloud services, such as Office 365, Google Workspace, and Salesforce. Managing user identities manually across these platforms can be cumbersome and error-prone. By implementing SCIM, the organization can automate the provisioning and deprovisioning of user accounts.
For instance, when a new employee joins the company, the IAM system can automatically create their user account in all relevant cloud services using SCIM. Similarly, when an employee leaves, their access can be revoked across all platforms in a streamlined manner. This automation enhances security, reduces administrative workload, and ensures consistent identity data across all systems.

Comparing SAML vs. OpenID Connect
When it comes to authentication protocols, SAML (Security Assertion Markup Language) and OpenID Connect are two of the most widely used standards. Both serve the purpose of providing secure authentication, but they do so in different ways and are suited to different use cases.
SAML
SAML is an XML-based framework primarily used for Single Sign-On (SSO) in enterprise environments. It allows users to authenticate once and gain access to multiple applications without re-entering credentials. SAML is commonly used in scenarios where secure, federated access to web applications is required, such as accessing corporate intranets or SaaS applications.
OpenID Connect
OpenID Connect is a modern identity layer built on top of the OAuth 2.0 protocol. It uses JSON-based tokens and is designed for mobile and web applications. OpenID Connect provides a more flexible and user-friendly approach to authentication, making it ideal for consumer-facing applications where user experience is paramount.
SAML vs. OpenID Connect: Key Differences
Protocol Structure: SAML uses XML, whereas OpenID Connect uses JSON.
Use Cases: SAML is suited for enterprise SSO, while OpenID Connect is better for modern web and mobile applications.
Token Types: SAML uses assertions, whereas OpenID Connect uses ID tokens.
User Experience: OpenID Connect generally offers a more seamless and user-friendly experience compared to SAML.
The Challenges of IAM Integration
With the growing reliance on technology, integrating various IAM components and protocols has become increasingly complex. Effective IAM integration is essential for ensuring that different systems work together harmoniously, providing a seamless and secure user experience. However, several challenges can arise during the integration process.
Compatibility Issues
Organizations often use a mix of legacy systems and modern applications, leading to compatibility issues. Ensuring that different IAM solutions can communicate and share identity data effectively is a significant challenge.
Data Consistency
Maintaining consistent identity data across multiple platforms is crucial for security and compliance. Any discrepancies in user data can lead to unauthorized access or account lockouts.
Scalability
As organizations grow, their IAM systems must be able to scale accordingly. Integrating IAM solutions that can handle an increasing number of users and applications without compromising performance is vital.
Security Concerns
Integrating multiple IAM solutions can introduce security vulnerabilities if not done correctly. Ensuring that data is securely transmitted and that all systems adhere to robust security protocols is paramount.
Solutions for Effective IAM Integration
To overcome these challenges, organizations should adopt a strategic approach to IAM integration:
Standardization
Adopting standard protocols such as SCIM, SAML, and OpenID Connect can simplify integration by ensuring compatibility and consistency across different systems.
Centralized Identity Management
Implementing a centralized IAM platform can help streamline identity management processes and ensure consistent data across all applications and services.
Regular Audits
Conducting regular audits of IAM systems and processes can help identify and address potential vulnerabilities and inconsistencies, ensuring that the integration remains secure and effective.
Vendor Support
Working with reputable IAM vendors who offer comprehensive support and integration services can significantly ease the integration process and ensure a successful deployment.
Conclusion
As organizations continue to increase their reliance on technology, the need for robust and effective IAM integration becomes more critical. By understanding the differences between SAML vs. OpenID Connect, leveraging standards like SCIM, and adopting strategic integration practices, organizations can enhance security, streamline operations, and provide a seamless user experience. The right IAM solutions not only protect against cyber threats but also empower businesses to thrive in the digital age.
0 notes
Text
SCIM Developer: Validate your Azure AD SCIM endpoint using SCIM Validator Tool
SCIM Developer: Validate your Azure AD SCIM endpoint using SCIM Validator Tool
If you’re a SCIM developer then this is intended for you. In this we will see how you can use the Azure AD SCIM Validator to validate that your provisioning server is compatible with the Azure SCIM client. To get started, make sure you have, Valid Azure Subscription SCIM endpoint Step 1: Let’s validate the SCIM Endpoint. a. Let’s navigate to https://scimvalidator.microsoft.com/ b. Select…

View On WordPress
#attributes#Azure Developer#Azure Identity#Azure SCIM Client#AzureAD Provisioning#provision service#provisioning#Schema#SCIM#SCIM 2.0 Standard#SCIM Client#SCIM endpoint#SCIM endpoint URL#SCIM validator#test#validator
0 notes
Text
Miro video converter download 404

Miro video converter download 404 how to#
Miro video converter download 404 full#
Miro video converter download 404 android#
Miro video converter download 404 license#
Miro video converter download 404 psp#
"urn:ietf:params:scim:schemas:extension:enterprise:2. "urn:ietf:params:scim:schemas:core:2.0:User" "urn:ietf:params:scim:api:messages:2.0:ListResponse" The SCIM variable must have the following structure: '.'.Įxample: 'urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:manager.displayName' If the "value" attribute is not a numeric value, we ignore the value. The "value" field has String type in SCIM standard but the managerId internal Miro field has Long type. Miro Video Converter 3. It doesnt require operating system support, any standard C or C++ libraries, or dynamic memory allocation. The core runtime just fits in 16 KB on an Arm Cortex M3 and can run many basic models. Based on the free FFMPEG and ffmpeg2theora. TensorFlow Lite for Microcontrollers is designed to run machine learning models on microcontrollers and other devices with only a few kilobytes of memory.
Miro video converter download 404 android#
Urn:ietf:params:scim:schemas:extension:enterprise:2.0:User Miro Video Converter is a super simple way to convert almost any video to MP4, WebM (vp8), Ogg Theora, or a mobile, Android phone, PSP, Iphone, iPod, etc. More than an online whiteboard, where everyone. Easy to use No instructions needed Bitpaper is so easy to use you’ll know. Invite as many people as you need onto a call. Powerful and stable conferencing technology. If your identity provider does not require defining namespace, the default namespace must be avoided.Įnterprise user extensions attribute for User: Tired of sharing docs instead of sharing ideas Discover digital-first visual collaboration with MURAL. Audio, Video, Chat and Screenshare Write and communicate in real-time. 'urn:ietf:params:scim:schemas:core:2.0:User' is a default SCIM urn for basic fields. Supported values are: ORGANIZATION_INTERNAL_ADMIN ORGANIZATION_INTERNAL_USER Max file size to download is: 31457280 bytes If you want to reset the software, delete the 'Miro' folder inside the 'Portable Miro' one. All files are stored in the 'Miro' folder, that will be created after you run the program for the first time. Miro Video Converter / Download Miro Video Converter 2.5 Miro 0 27.9 k Powerful and really good video converter Advertisement Download 7.87 MB free Created by the same developers who created Miro Media player, Miro Video Converter arrives in our computers to finish with compatibility problems and help us take the most out of our media players. ) or request to url should return together with a file content a header Content-Type (e.g. This version of Miro 6.0 is fully customizable and totally portable. To define file type, you should have defined file extension in url (e.g. Supported file types: jpg, jpeg, bmp, png, gif
Miro video converter download 404 license#
When userType is not specified, user license is updated/set according to internal Miro logic, which depends on the organization plan.
Miro video converter download 404 full#
When userType=Full, a user is upgraded to FULL license inside the Miro application. Seamlessly record and embed Vimeo videos right in Asana to increase team. It is too simple, and you will have all your conversions in a high quality.Urn:ietf:params:scim:schemas:core:2.0:UserĪttribute is used if the value is not empty.Īttribute is used if the displayName attribute is not provided, name attribute is provided and 'formatted' attribute value is not empty.Īttributes are used if the displayName attribute is not provided, name attribute is provided and formatted attribute is not provided.Īttribute will be used as full name if the displayName attribute is not provided and name attribute is not provided. Download the Asana mobile app for your iPhone, iPad, or Android device to plan. This program is very simple to use, you only have to access in its interface and select all videos that you want to convert and choose the format that you want. Miro has a simple, gorgeous interface designed for fullscreen HD video. It can play almost any video file and offers over 6,000 free internet TV shows and video podcasts. Download Latest Version for Windows (48.06 MB) 1/3.
Miro video converter download 404 how to#
Formats are supported in this program for your conversions are AVI, FLV, WMV, MOV, MKV, H264, and XVID and you can also change to MP4 and OGG. Participatory Culture Foundation (Free) User rating. Microsoft Office 365 For Mac Download Full Version Hangouts App For Mac Os Download Python 2.7.14 For Mac Ummy Video Downloader freeload For Mac Best Dvd Catalog App For Mac How To Download Unreal Tournament For Mac 2017 freeload Winzip For Mac 10.4. The program gives you the possibility to work with a lot of different formats, in this manner you only have to use only one program for making all your conversions.
Miro video converter download 404 psp#
Miro Video Converter operating is very simple, it allows you make all formats change in your videos for making in your computer, iPhone, iPod, PSP or in your Android. For them, this program will be the perfect complement and it allows you change all your videos to compatible formats with these devices. Miro video Converter is a program for all people who have iPhone or Android devices and they want to have the opportunity to view all videos in their devices.

1 note
·
View note
Text
Innovating on Authentication Standards
By George Fletcher and Lovlesh Chhabra
When Yahoo and AOL came together a year ago as a part of the new Verizon subsidiary Oath, we took on the challenge of unifying their identity platforms based on current identity standards. Identity standards have been a critical part of the Internet ecosystem over the last 20+ years. From single-sign-on and identity federation with SAML; to the newer identity protocols including OpenID Connect, OAuth2, JOSE, and SCIM (to name a few); to the explorations of “self-sovereign identity” based on distributed ledger technologies; standards have played a key role in providing a secure identity layer for the Internet.
As we navigated this journey, we ran across a number of different use cases where there was either no standard or no best practice available for our varied and complicated needs. Instead of creating entirely new standards to solve our problems, we found it more productive to use existing standards in new ways.
One such use case arose when we realized that we needed to migrate the identity stored in mobile apps from the legacy identity provider to the new Oath identity platform. For most browser (mobile or desktop) use cases, this doesn’t present a huge problem; some DNS magic and HTTP redirects and the user will sign in at the correct endpoint. Also it’s expected for users accessing services via their browser to have to sign in now and then.
However, for mobile applications it's a completely different story. The normal user pattern for mobile apps is for the user to sign in (via OpenID Connect or OAuth2) and for the app to then be issued long-lived tokens (well, the refresh token is long lived) and the user never has to sign in again on the device (entering a password on the device is NOT a good experience for the user).
So the issue is, how do we allow the mobile app to move from one identity provider to another without the user having to re-enter their credentials? The solution came from researching what standards currently exist that might address this use case (see figure “Standards Landscape” below) and finding the OAuth 2.0 Token Exchange draft specification (https://tools.ietf.org/html/draft-ietf-oauth-token-exchange-13).
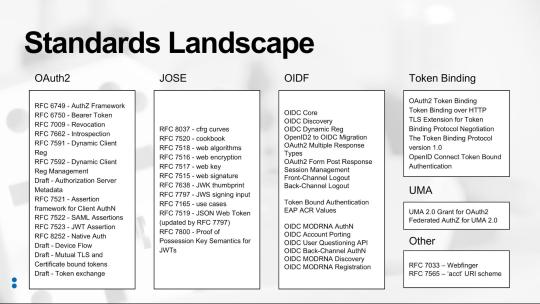
The Token Exchange draft allows for a given token to be exchanged for new tokens in a different domain. This could be used to manage the “audience” of a token that needs to be passed among a set of microservices to accomplish a task on behalf of the user, as an example. For the use case at hand, we created a specific implementation of the Token Exchange specification (a profile) to allow the refresh token from the originating Identity Provider (IDP) to be exchanged for new tokens from the consolidated IDP. By profiling this draft standard we were able to create a much better user experience for our consumers and do so without inventing proprietary mechanisms.
During this identity technical consolidation we also had to address how to support sharing signed-in users across mobile applications written by the same company (technically, signed with the same vendor signing key). Specifically, how can a signed-in user to Yahoo Mail not have to re-sign in when they start using the Yahoo Sports app? The current best practice for this is captured in OAuth 2.0 for Natives Apps (RFC 8252). However, the flow described by this specification requires that the mobile device system browser hold the user’s authenticated sessions. This has some drawbacks such as users clearing their cookies, or using private browsing mode, or even worse, requiring the IDPs to support multiple users signed in at the same time (not something most IDPs support).
While, RFC 8252 provides a mechanism for single-sign-on (SSO) across mobile apps provided by any vendor, we wanted a better solution for apps provided by Oath. So we looked at how could we enable mobile apps signed by the vendor to share the signed-in state in a more “back channel” way. One important fact is that mobile apps cryptographically signed by the same vender can securely share data via the device keychain on iOS and Account Manager on Android.
Using this as a starting point we defined a new OAuth2 scope, device_sso, whose purpose is to require the Authorization Server (AS) to return a unique “secret” assigned to that specific device. The precedent for using a scope to define specification behavior is OpenID Connect itself, which defines the “openid” scope as the trigger for the OpenID Provider (an OAuth2 AS) to implement the OpenID Connect specification. The device_secret is returned to a mobile app when the OAuth2 code is exchanged for tokens and then stored by the mobile app in the device keychain and with the id_token identifying the user who signed in.
At this point, a second mobile app signed by the same vendor can look in the keychain and find the id_token, ask the user if they want to use that identity with the new app, and then use a profile of the token exchange spec to obtain tokens for the second mobile app based on the id_token and the device_secret. The full sequence of steps looks like this:
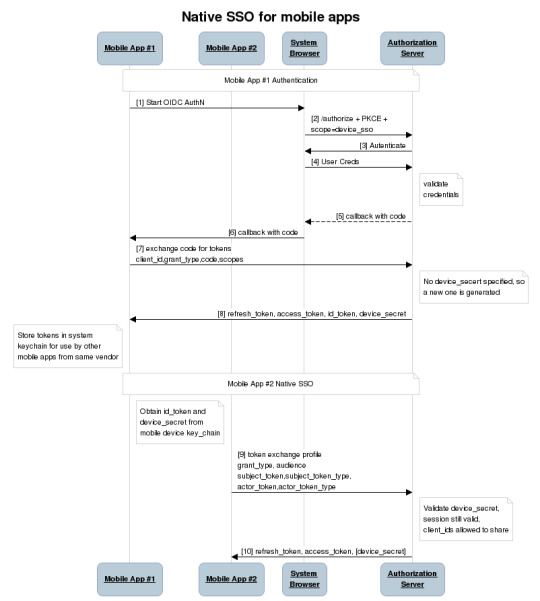
As a result of our identity consolidation work over the past year, we derived a set of principles identity architects should find useful for addressing use cases that don’t have a known specification or best practice. Moreover, these are applicable in many contexts outside of identity standards:
Spend time researching the existing set of standards and draft standards. As the diagram shows, there are a lot of standards out there already, so understanding them is critical.
Don’t invent something new if you can just profile or combine already existing specifications.
Make sure you understand the spirit and intent of the existing specifications.
For those cases where an extension is required, make sure to extend the specification based on its spirit and intent.
Ask the community for clarity regarding any existing specification or draft.
Contribute back to the community via blog posts, best practice documents, or a new specification.
As we learned during the consolidation of our Yahoo and AOL identity platforms, and as demonstrated in our examples, there is no need to resort to proprietary solutions for use cases that at first look do not appear to have a standards-based solution. Instead, it’s much better to follow these principles, avoid the NIH (not-invented-here) syndrome, and invest the time to build solutions on standards.
36 notes
·
View notes
Text
300+ TOP OKTA Interview Questions and Answers
Okta Interview Questions for freshers experienced :-
1. What is OKTA? OKTA is an application management service, developed for cloud, which ties all devices, logins and application. 2. What is the use of Okta? Okta connects any person with any application on any device. It’s an enterprise-grade, identity management service, built for the cloud, but compatible with many on-premises applications. With Okta, IT can manage any employee’s access to any application or device. 3. What is Okta authentication? The Okta Authentication API provides operations to authenticate users, perform multi-factor enrollment and verification, recover forgotten passwords, and unlock accounts. Primary authentication allows you to verify username and password credentials for a user. 4. Mention few benefits of OKTA Universal directory. Universal Directory is the centralised place for managing all users, groups and devices from any sources. It has few benefits which make it most secure. It provides group-based password policies All the users and passwords are stored securely in it It has also option of complexity for password policy It also supports rich SAML and authorization scenarios based on different attributes. 5. How to add users in bulk in Okta? Okta Admin can upload users in bulk by navigating to below location. Directory → More Actions → “Import Users From CSV” Okta also provides Realtime Sync facility to updates user profiles, groups, group members during sign-in period instead of waiting for any import. 6. What is state token? state token is ephemeral token that encodes the current state of an authentication transaction. A state token is generated during the AuthN process, and gets converted to a session token once the user has been authenticated. Ephemeral token that encodes the current state of an authentication or recovery transaction. The stateToken must be passed with every request except when verifying a recoveryToken that was distributed out-of-band The stateToken is only intended to be used between the web application performing end-user authentication and the Okta API. It should never be distributed to the end user via email or other out-of-band mechanisms. The lifetime of the stateToken uses a sliding scale expiration algorithm that extends with every request. Always inspect the expiresAt property for the transaction when making decisions based on lifetime. 7. Give names of different OKTA products. There are different products provided by OKTA. Single sign-on Lifecycle management Universal directory Multi-factor authentication OKTA API Products 8. What is single sign-on? Why it is important? Single sign-on (SSO) in the enterprise refers to the ability for employees to log in just one time with one set of credentials to get access to all corporate apps, websites, and data for which they have permission. SSO solves key problems for the business by providing: Greater security and compliance. Improved usability and employee satisfaction. Lower IT costs. 9. Define Multi-factor authentication. Multi-factor Authentication provides different ways to implement various factors of authentication across usability and assurance levels. Different factors are described as below: Knowledge: It depends on users’ knowledge Possession: It depends on something users have Biometric: It depends on something which user is. 10. What is OKTA universal directory? Okta’s Universal Directory allows you to store an unlimited amount of users and attributes from applications and sources like AD or HR systems. Universal Directory delivers rich user profiles and fine-grained control over how attributes are exchanged between applications. Universal Directory makes it easier for organizations to create and maintain a single source of truth for its users, enabling new authentication and provisioning scenarios 11. What are the benefits of OKTA Universal directory? Benefits of OKTA Universal directory is Store rich profiles of user attributes in Okta. Customize and extend user and app profiles with custom attributes. Bi-directionally map and move attributes from Okta to applications. Transform attributes using a powerful and intuitive Expression Language before storing them in Okta. These capabilities enable you to do the following: Synchronize user profile information across cloud HR systems, on-premise directory systems and applications. Provision application user accounts with rich profile information such as roles, managers, geo-locations and other attributes that aid in configuring complex authentication and authorization rules. Collect, import and store any type of user attribute, including externally defined custom attributes. 12. Can admin of OKTA see passwords of any user? No Passwords are not visible to anyone. OKTA Admin can only see username of any user. 13. What are the activities of super admins in OKTA? Only Super Admins can view and manage other adminAn abbreviation of administrator. This is the individual(s) who have access to the Okta Administrator Dashboard. They control the provisioning and deprovisioning of end users, the assigning of apps, the resetting of passwords, and the overall end user experience. 14. What is SAML? Security Assertion Markup Language is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. SAML is an XML-based markup language for security assertions. 15. How does SAML works? SAML sets the secure environment between different organizations. To communicate seamlessly, identity provider and service provider needs to implement SAML. Once SAML has been set up, when user tries to access SP, IDP will authenticate user. SP will confirm and assures that message is coming from the trusted IDP and registers a session with app for user. 16. Why to use SAML? SAML has many benefits for individual user, identity provider, and service provider. It saves time from administrative tasks like password resets etc. It increases security It also increases usage by reducing barriers to entry. 17. Why to use SAML? In the modern era of computing, security is of the utmost importance when it comes to enterprise applications. SAML is used to provide a single point of authentication at a secure identity provider, meaning that user credentials never leave the firewall boundary, and then SAML is used to assert the identity to others. SAML has been widely adopted for three primary reasons: Standardized, Secure and Provides an excellent user experience. 18. What is the difference between SCIM connector and server? SCIM is the System for Cross-domain Identity Management. SCIM is used to connect Okta to on-premises applications. Communication between Okta and on-premises applications occurs through the Okta Provisioning Agent and a SCIM server or a provisioning connector built using Provisioning Connector SDK. 19. How can I obtain a list of all the users who are assigned to applications? Is there any way to download all users or groups from Okta? All users and groups can’t be located at one place. 80% of them will be found in system logs and reports. Users permissions can be found in Security → Administrators directory. in the Okta Admin console, navigate to Reports > Reports in the Application Access Audit section, click Current Assignments to filter the list by application, enter the application name in the Application field and click Run Report to export the list, click Download CSV in the upper-right corner of the results table 20. How long SMS(OTP) is valid for multi-factor authentication? Can we edit it? SMS(OTP) is valid only for 5 minutes. We cannot modify it. Timeout is not configurable as of now in Okta MFA. 21. Can we enter multiple mobile numbers in Okta MFA? SMS(OTP) is valid only for 5 minutes. We cannot modify it. Timeout is not configurable as of now in Okta MFA. 22. How do I enable MFA in Okta? You must enable MFA from the Admin interface of your Okta org before you can use it from the Okta API. Here is how to enable MFA for your Okta org: Log in to your Okta org as a user with administration. Click the “Admin” button to get into the administrator interface. Open the “Security” menu. Select “Authentication” from the menu. Click on “Multifactor”. Click the “Edit” button in the “Factor Types” section. Check the check boxes next to “Google Authenticator” and “SMS Authentication”. Click the green “Save” button. 23. Can Okta MFA allow multiple phone numbers? No, Okta does not currently support this. 24. How do I reset my Okta MFA? To reset your MFA, login to your Okta org on a computer or mobile device. Click on your username in the top menu, and select the ‘Settings’ menu item. Go to the Extra Verification section, and select Setup or Reset, next to the MFA Factor that you want to setup or reset. Enter the required information and save. 25. What is OKTA verify for end users? Okta Verify is an MFA factor developed by Okta. Use it to verify your identity so you can sign in to your organization securely. Whenever you sign in to your Okta account, you need to confirm who you are by using the Okta Verify app on your phone. Confirming your identity allows Okta to sign you in to your account securely. 26. Can we give priority to password policies? Universal directory provides group password policies, where any policy having higher priority over others will take precedence. 27. How do I set up Okta SSO? Setting Up a SAML Application in Okta Log in to your Okta organization as a user with administrative privileges. … Click on the Applications link in the upper navigation bar. Click on the green Create New App button. In the dialog that opens, select the “SAML 2.0” option, then click the green “Create” button. 28. How to Configure SAML in Okta? Here is the steps to configure the SAML settings of your SAML Service Provider app in Okta, follow these steps using the information that you gathered in the first step: On the SAML Settings page, paste the ACS URL into the Single sign on URL field. Paste the Audience URI into the Audience URI (SP Entity ID) field. Select the Name ID format and Application username that your application requires (for example, EmailAddress and Email) or leave the defaults. In the ATTRIBUTE STATEMENTS (OPTIONAL) section, add the required SAML attributes for your app. Okta Questions and Answers Pdf Download Read the full article
0 notes