#Ransom ware Attacks
Explore tagged Tumblr posts
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Product Description Detects Viruses This antivirus automatically detects and removes viruses, Trojans, malware; keeps your device safe, secure, protects against malicious virus attacks. Fast Internet Connection NPAV net protector total security provides multilayered protection. It ensures smooth, fast internet connection and surfing. Blocks Unknown Ransom Ware Automatically, backup your recently edited documents keeping against any corruption or ransomware.Blocks new & unknown ransom ware which corrupt & encrypt data files. This antivirus automatically detects and removes viruses, Trojans, malware; keeps your device safe, secure, protects against malicious virus attacks NPAV net protector total security provides multilayered protection. It ensures smooth, fast internet connection and surfing Automatically, backup your recently edited documents keeping against any corruption or ransomware.Blocks new & unknown ransom ware which corrupt & encrypt data files Protects your computer from viruses and malware through the cloud; Webroot scans faster, uses fewer system resources and safeguards your devices in real-time by identifying and blocking new threats All-in-one online protection for your personal info and privacy, so you can enjoy your life online. We make online security simple so you can bank, shop, browse, and connect with confidence [ad_2]
0 notes
Text
Meet the Top Cyber Crime Advocate in Hyderabad: Protecting Your Digital Rights

Table of Content
Introduction
Understanding Cyber Crime
Why Cyber Crime Advocacy is Crucial
The Rise of Cyber Crimes in Hyderabad
Meet the Top Cyber Crime Advocate in Hyderabad
Services Offered
How to Choose the Right Advocate
Conclusion
Introduction
In today’s digital age, cyber crime is an ever-present threat that affects individuals and businesses alike. With the rapid advancement of technology, cyber criminals are becoming more sophisticated, making the role of cyber crime advocates crucial in safeguarding our digital rights.
In this article, we’ll introduce you to the top cyber crime advocate in Hyderabad who is dedicated to protecting your digital rights and ensuring justice in the face of cyber threats.
Types of Cyber Crimes
Cyber crimes are varied and can affect anyone. Some of the most common types include:
Unauthorized access to computer systems and networks.
Fraudulent attempts to obtain sensitive information by disguising as a trustworthy entity.
Stealing personal information to commit fraud.
Using the internet to harass or stalk individuals.
Scams conducted over the internet to deceive individuals for financial gain.
Why Cyber Crime Advocacy is Crucial
Cyber crime advocacy plays a vital role in combating digital threats. A cyber crime advocate not only provides legal representation to victims but also educates the public on how to protect themselves online. They navigate the complex legal landscape surrounding cyber crimes, ensuring that perpetrators are brought to justice.
The Rise of Cyber Crimes in Hyderabad
Over the past few years, Hyderabad has seen a significant increase in cyber crime incidents. According to recent statistics, the number of reported cases has doubled, highlighting the urgent need for effective legal intervention and public awareness.
Statistics and Trends
The rise in cyber crimes in Hyderabad is attributed to increased internet penetration and digital transactions. Common trends include phishing attacks targeting banking customers and ransom ware attacks on corporate networks.
Meet the Top Cyber Crime Advocate in Hyderabad
Kodamagundla Ravi Kumar, Advocate is a practicing advocate before the Hon’ble High Courts of Telangana, Andhra Pradesh and all the Lower Courts in and around Hyderabad and also before the Hon’ble Supreme Court of India, practicing in the areas of Cyber laws, Civil laws and Criminal laws.
I am an Ex-Sergeant (Ex-Serviceman/ Air Veteran) having served in the Indian Air Force. I was privileged to serve in the Indian Air Force Legal Cell, New Delhi.
www.CyberAdvocate.com Office is Located at Miyapur, Cyberabad, Hyderabad In Telangana, India. Pin: 500049.
M.A., (Political Science), Kakatiya University, Telangana, India.
LL.B., Osmania University, Telangana, India.
LL. M., (Corporate Laws) Osmania University, Telangana, India.
Diploma in Computer Applications, from International Computer Institute, New Delhi, India.
Post Graduate Diploma in Industrial Relations & Personnel Management, from Bharatiya Vidya Bhavan, (New Delhi & Hyderabad), India.
Post Graduate Diploma in Cyber Laws and Legal Information Systems, from University of Hyderabad, (TELANGANA).
Expertise in Handling Complex Cases
With a deep understanding of both legal and technical aspects of cyber crimes, I can adept & handle even the most complex cases.
How to Choose the Right Advocate
Selecting the right cyber crime advocate is crucial for effective legal representation.
Qualities to Look For
Look for advocates with a proven track record in cyber crime cases.
Ensure they have specialized knowledge in cyber law.
Check reviews and testimonials from previous clients.
The Future of Cyber Crime Advocacy
As technology evolves, so do cyber threats. The field of cyber crime advocacy must adapt to these changes to remain effective.
Reach out cyber crime lawyer in Hyderabad Protect your digital rights with expert legal guidance and cyber security solutions.
0 notes
Text
Cyber security Challenges in M.Sc. ITM
Addressing Threats in Healthcare Systems
The digital transformation in healthcare has led to unprecedented advancements in patient care, operational efficiency, and data management. However, this digital revolution also brings significant cyber security challenges, particularly within healthcare systems. For students pursuing an M.Sc in Information Technology Management (ITM) at DRIEMS University, understanding these challenges and developing strategies to mitigate them is crucial.
The Importance of Cyber security in Healthcare
Healthcare systems hold vast amounts of sensitive data, including patient records, medical histories, and financial information. The integrity, confidentiality, and availability of this data are paramount, as breaches can lead to severe consequences, including identity theft, financial loss, and compromised patient care. Furthermore, the healthcare sector's reliance on interconnected devices and systems makes it a prime target for cyber-attacks.
Key cyber security Threats
Ransom ware Attacks:
Ransom ware remains one of the most prevalent threats in healthcare. Attackers encrypt critical data and demand a ransom for its release. Hospitals and clinics, under pressure to restore access to their systems swiftly, often feel compelled to pay the ransom, making this a lucrative tactic for cybercriminals.
Phishing and Social Engineering:
Phishing attacks deceive healthcare employees into revealing sensitive information or granting access to secure systems. These attacks exploit human error, making it essential for healthcare workers to be vigilant and well-trained in recognizing such threats.
Insider Threats:
Insider threats, whether malicious or accidental, pose a significant risk. Employees with access to sensitive information can inadvertently or deliberately cause data breaches. Implementing strict access controls and monitoring employee activity are vital in mitigating these risks.
Internet of Things (IoT) Vulnerabilities:
The proliferation of IoT devices in healthcare, such as smart medical devices and wearables, introduces new vulnerabilities. These devices often lack robust security features, making them susceptible to hacking and unauthorized access.
Strategies for Mitigating cyber security Threats
Comprehensive Risk Assessment:
Conducting thorough risk assessments helps identify potential vulnerabilities within healthcare systems. By understanding where the risks lie, organizations can prioritize their cyber security efforts and allocate resources effectively.
Robust Encryption:
Encrypting sensitive data both at rest and in transit is essential. Encryption ensures that even if data is intercepted, it remains unreadable to unauthorized users.
Regular Security Training:
Ongoing cyber security training for healthcare staff is crucial. Employees must be educated about the latest threats and best practices for protecting sensitive information. Simulated phishing exercises can also help reinforce awareness and readiness.
Multi-Factor Authentication (MFA):
Implementing MFA adds an extra layer of security by requiring multiple forms of verification before granting access to systems. This significantly reduces the risk of unauthorized access, even if login credentials are compromised.
Incident Response Planning:
Developing a comprehensive incident response plan ensures that healthcare organizations are prepared to respond swiftly and effectively to cyber incidents. This includes regular drills and updates to the plan to address emerging threats.
The Role of M.Sc. ITM Students
Students pursuing an M.Sc. in ITM at DRIEMS University are uniquely positioned to address these cyber security challenges. Through their coursework and research, they can develop innovative solutions and strategies to protect healthcare systems. Engaging in practical experiences, such as internships and projects with healthcare organizations, allows students to apply their knowledge in real-world scenarios.
Conclusion
As the digital landscape in healthcare continues to evolve, so do the cyber security challenges it faces. For M.Sc. ITM students at DRIEMS University, mastering these challenges is not only an academic pursuit but also a crucial contribution to safeguarding healthcare systems. By focusing on comprehensive risk management, robust security measures, and continuous education, they can play a vital role in protecting the integrity and confidentiality of sensitive healthcare data.
0 notes
Text
Important Tips to Prevent yourself from Cyberattacks

Tips To Avoid Cyber Attack
Best Private Engineering College in Rajasthan have many courses of Cyber security It is as important as ever and With ever-growing threats to businesses, having a robust security solution is essential also We’ve all heard of enterprises paying huge fines or even going out of business because of a simple hack into their systems.
So there are simply far too many threats out there to ignore the risks from ransom ware to phishing, it could cost you your livelihood.
What Is A Cyber Attack?
It is a deliberate exploitation of your systems and/or network and Cyber Attacks use malicious code to compromise your computer, logic, or data and steal, leak, or hold your data hostage.
Some Common Cyber Attacks And Data Breaches:
Identity theft, fraud, extortion
Some of the examples of Malware, phishing, spamming, spoofing, spyware, trojans, and viruses
Denial-of-service and distributed denial-of-service attacks
Breach of access
Password sniffing
System infiltration
Website defacement
Private and public Web browser exploits
Instant messaging abuse
unauthorized access
1. Train Your Staff.
Cybercriminals get access to your data through your employees, They’ll send fraudulent emails impersonating someone in your organization and will either ask for personal details and access to certain files also Links often seem legitimate to an untrained eye and it’s easy to fall into the trap also This is why employee
awareness is vital One of the most efficient ways to protect against cyber attacks and all types of data breaches is to train your employees on cyber attack prevention.
They need to:
Check links before clicking them and Check email addresses from the received email (have a look here at how to check it)
Use common sense before sending sensitive information and If a request seems odd, it probably is also It’s better to check via a phone call with the person in question before actioning the “request”
2. Update Your Software And Systems.
Cyber-attacks happen because your systems or software aren’t fully up to date, leaving weaknesses and So cybercriminals exploit these weaknesses to gain access to your network also Once they are in – it’s often too late to take preventative action so it’s smart to invest in a patch management system that will manage all software and system updates, keeping your system resilient and up to date.
3. Ensure Endpoint Protection.
Endpoint protection protects networks that are remotely bridged to devices and Mobile devices, tablets, and laptops that are connected to corporate networks give access paths to security threats and these paths need to be protected with specific endpoint protection software.
4. Install A Firewall.
Different types of sophisticated data breaches and new ones surface every day and even make comebacks Putting your network behind a firewall is one of the most effective ways to defend yourself from any cyber attack also a firewall system will block any brute force attacks made on your network and/or systems before they can do any damage, something we can help you with.
5. Back Up Your Data.
Data backed up to avoid serious downtime, loss of data, and serious financial loss.
6. Control Access To Your Systems.
One of the attacks on systems can be physical also having control over who can access your network is important and Somebody can simply walk into your office or enterprise and plug in a USB key containing infected files into one of your computers allowing them access to your entire network or infecting it also It’s essential to control who has access to your computers So having a perimeter security system installed is a very good way to stop cybercrime as much as break-ins!
7. Wifi Security.
Any device can get infected by connecting to a network and this infected device then connects to your business network your entire system is at serious risk and Securing your wifi networks and hiding them is one of the safest things you can do for your systems also with wireless technology developing more and more every day thousands of devices can connect to your network.
8. Employee Personal Accounts.
Every employee needs their login for every application and program and Several users connecting under the same credentials can put your business at risk also having separate logins for each staff member will help you reduce the number of attack fronts so users only log in once each day and will only use their own set of logins.
9. Access Management.
Btech College in Jaipur Rajasthan says software on business-owned devices that could compromise your systems and having managed admin rights and blocking your staff from installing or even accessing certain data on your network is beneficial to your security.
10. Passwords.
Once a hacker figures out your password, they now have access to everything in your system and any application you use having different passwords set up for every application you use is a real benefit to your security, also changing them often will maintain a high level of protection against external and internal threats.
Conclusion:
Top Engineering College in Jaipur Rajasthan says It can be difficult to know where to begin when it comes to protecting your business from cybercrime and cyber-attacks and There’s so much information out there that it can become overwhelming, especially when the info is conflicting also You need a solution that’s right for your business and your employees
Source: Click Here
#best btech college in jaipur#best engineering college in jaipur#best engineering college in rajasthan#best private engineering college in jaipur#best btech college in rajasthan#top engineering college in jaipur
0 notes
Text
The Future of Security Embracing Norton com Enroll
In today's increasingly digital world, security concerns have become more prevalent than ever. With cyber threats evolving at a rapid pace, it's essential for individuals and organizations alike to adopt robust security measures to safeguard their data and privacy. Norton.com Enroll emerges as a leading solution in this landscape, offering comprehensive security services to address modern-day threats effectively.
Current Challenges in Security
Cyber threats continue to pose significant challenges to individuals and businesses worldwide. From ransom ware attacks to phishing scams, the range of threats is vast and ever-growing. Consequently, there's a pressing need for advanced security solutions that can adapt to these evolving threats and provide reliable protection.
The Role of Norton com Enroll
Norton.com Enroll offers a suite of security services designed to address the current challenges in cyber security. With features such as real-time threat detection, malware protection, and secure VPN, Norton.com Enroll provides users with the tools they need to defend against a wide range of threats effectively.
Future Trends in Security
Looking ahead, the future of security is likely to be shaped by emerging technologies such as artificial intelligence (AI) and machine learning. These technologies hold the potential to revolutionize cyber security by enabling more proactive threat detection and mitigation strategies.
Norton com Enroll: Future Adaptations
As security threats continue to evolve, norton.com/enroll is committed to adapting and innovating to stay ahead of the curve. Future adaptations may include enhanced AI-powered threat detection capabilities, improved privacy protection features, and seamless integration with emerging technologies.
Benefits of Embracing Norton.com Enroll
By embracing Norton.com Enroll, users can enjoy a multitude of benefits, including enhanced protection against emerging threats, simplified security management, and peace of mind knowing that their digital assets are secure.
Challenges and Considerations
Despite its many benefits, the widespread adoption of Norton.com Enroll may face some challenges. Concerns regarding privacy and data security, as well as compatibility issues with existing systems, may need to be addressed to ensure seamless integration and user acceptance.
The Importance of Proactive Security Measures
In today's threat landscape, proactive security measures are more important than ever. By leveraging the advanced features of Norton.com Enroll, users can take a proactive approach to security, staying one step ahead of potential threats before they have a chance to cause harm.
Integration with Emerging Technologies
Norton.com Enroll is well-positioned to leverage emerging technologies such as AI and block chain to enhance its security offerings further. By harnessing the power of AI for advanced threat detection and block chain for enhanced data integrity, Norton.com Enroll can provide users with unmatched levels of protection.
Cyber security in the Internet of Things Era
With the proliferation of devices, security concerns have extended beyond traditional computers and smart phones to include a wide range of connected devices. Norton.com Enroll plays a crucial role in securing ecosystems, protecting users' data and privacy across all their connected devices.
Educating Users about Cyber security
In addition to providing advanced security services, Norton.com Enroll is committed to promoting cyber security awareness and education among its users. By offering resources and guidance on best practices for staying safe online, Norton.com Enroll empowers users to take control of their digital security.
Collaboration in Security
Effective cyber security requires collaboration among various stakeholders, including technology companies, government agencies, and individual users. Norton.com Enroll actively engages in partnerships and collaborations to promote information sharing and collective defense against cyber threats.
Regulatory Landscape and Compliance
With the increasing focus on cyber security, regulatory requirements are becoming more stringent. Norton.com Enroll ensures compliance with relevant regulations and standards, providing users with peace of mind knowing that their security solution meets the highest industry standards.
Conclusion
The future of security lies in embracing proactive and innovative solutions such as Norton.com Enroll. By staying ahead of emerging threats, leveraging advanced technologies, and promoting user education, Norton.com Enroll is well-equipped to meet the evolving security needs of individuals and businesses alike.
0 notes
Text
Guide for Computer virus handling
In todays time every single person familiar with word Virus.
"A virus" the word “virus” is famous for “CORONA VIRUS” after impact of COVID-19 in all around world.
What do you do while protecting yourself from corona virus?
Yes! IT'S about to
Cover you face with mask
Keep distancing
In similar style YOU can protect your computer from viruses that are generally called malware with formula KEEP DISTANCING! YES "IT DEFINITELY WORKS"
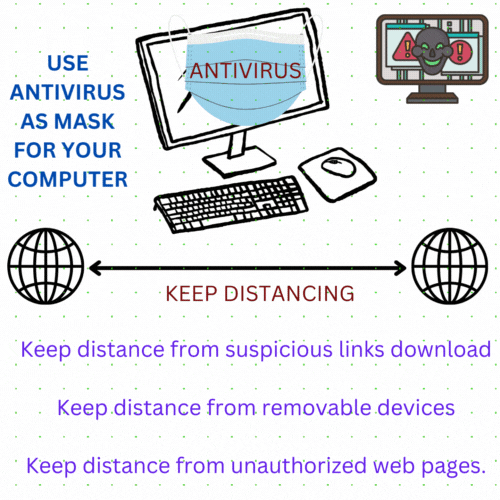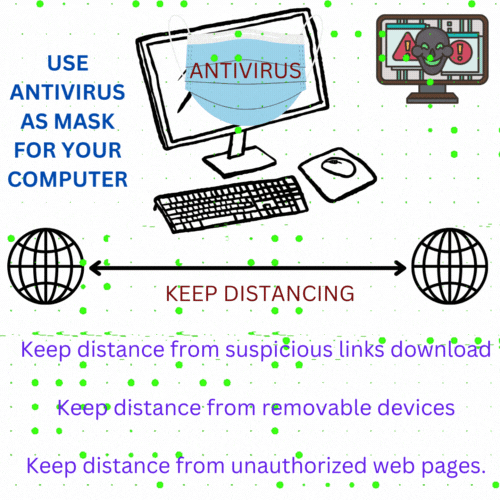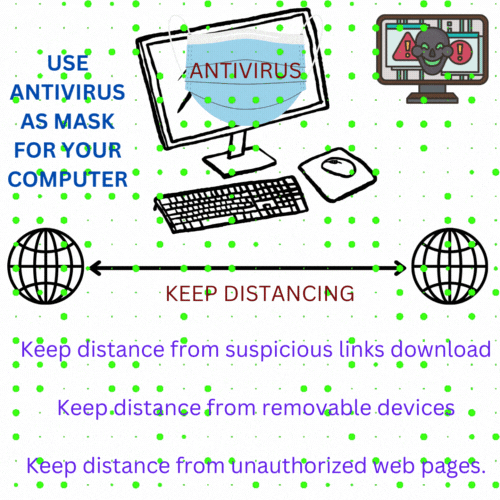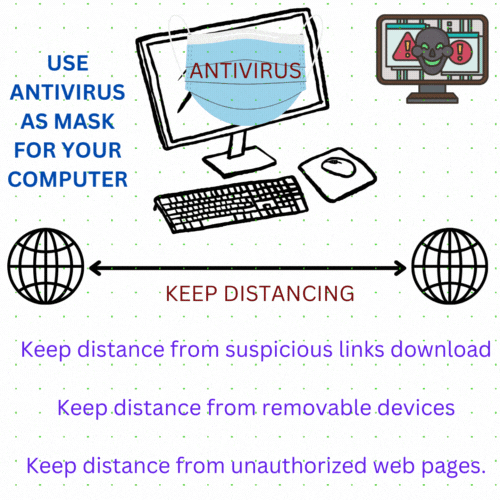
Technical masks on your computer in form of Antiviruses, firewall, anti-spyware.
Keep distancing is another magic follow up to stay away from viruses. (It’s very easy and possible to make distance from computer viruses
Keep distance from suspicious links downloads (Shared through emails or any other sources)
Keep distance from removable devices or does a scan with updated antivirus before insert it.
Keep distance from unauthorized web pages. Don’t open them.
Keep distance from downloading freeware from internet
Keep distance from downloading unauthorized software (malicious software)
Let's read what actually a virus is?
Oh that’s a silly program made by scammers in order to
Destroy computer system
Damage computer system
Make your computer sick and put it on ventilator
Hijack your computer system
Steal control or any important information from your computer system
All that means to disable smart functioning of any computer system, software, or electronic data. Virus is a program that spreads by first infecting files or the system areas of a computer or network router's hard drive and then making copies of itself. It can cause serious damage to your computer.
WHAT TO DO TO STAY AWAY FROM VIRUS
Download from reputable sources
Before downloading any freeware, take some time to read reviews from other users.
verify authenticity before downloading any software
Use a reputable Antivirus and keep it up-to-date
Be cautious of 'too good to be true' offers
Always opt out of installing anything that you're not sure about.
Keep your operating system and software updated with the latest security patches to minimize vulnerabilities that could be exploited by malware.
By following these tips, you can reduce the risk of getting viruses from freeware and protect your computer and personal information.
WHAT IF COMPUTER SYSTEM GET INFECTED?
Over WWW there are numerous guides’ available that teaches you some possible ways to handle a virus. You definitely get huge suggestions in finding and fixing.
Are that all guide is resolving your problem? or
Make it worst?
Sometimes a journey of fixing existing virus may take you at risk of facing another unwanted virus or suspicious attack as many fake resources available to guide you. HOW? As most time a victim can opt for solutions by searching over web and can be entangled in a net of those who
Claim to remove your virus for free
Claim A system scan for free
A software that available with excited offers
Not have reputed name in market and work to just earning from victims.
Removing a virus from your computer requires careful steps. Here's a general guide on how to remove a virus that can be of any type like file infection , Boot sector , macro virus , polymorphic viruses ,Trojans ,Ransom wares , Aware , Spyware etc Here are some suggestions to remove virus from your computer .
Best way is to get Professional Help
If you're unable to remove the virus on your own, consider seeking help from a professional computer technician or IT specialist. This is best way to have help from a professional as they know right way to handle with virus. There are many helps over web that cares you pc through call. They may have specialized tools and knowledge to assist in virus removal. Micro PC Tech, we provide the best support for virus removal. You can contact at their toll free number +1-877-842-1012.
If you not want to go with a professional follow these steps, may it help you
Opt. Safe Mode: Turn off your computer and start it up again (Restart your computer) and click on safe mode (boot into Safe Mode). This action to run a computer in safe mode prevents the virus from running and makes it easier to remove.So this is one of possible way in detecting and removal of virus from your computer.
Update Antivirus: Antivirus is software that protects you from virus attacks. To ensure your antivirus proper functionality and best output check for software is up-to-date with the latest version. Updating of software is much important as it UPGRADE the software to fight with extreme power an let you protected from any suspicious malware attacks . If you don't have antivirus software installed, consider downloading OR buying a reputable program and installing it.
System Scan: When a virus affects computer than scanning is best way to stay it away from your computer, hence perform a full system scan using your antivirus software. Don’t halt scanning; Allow the scan to complete, as it will search for any traces of the virus on your computer.
Remove Detected Threats: Once you detect a virus, what is our next step? Probably we are going to kick it out. So the next step for you is that if the antivirus software detects the virus or any other threats, follow the prompts to quarantine or remove them from your system.
Manually Delete Suspicious Files: Manual detection is a bit difficult as you have to identify by yourself for any suspicious item and deleting them may cause for data loss. In case if the antivirus software does not detect the malware, you may need to manually search for and delete suspicious files. Be cautious when deleting files manually, as deleting system files can cause issues with your computer.
Restore Your System: most important for firm or personal is DATA, So Consider restoring your computer to a previous state using System Restore (Windows) or Time Machine (Mac) if the micro virus persists after running antivirus scans.
Prevent Future Infections: Once you remove virus that not mean it will not back again. After removing the micro virus, take steps to prevent future infections by installing reliable antivirus software, keeping your operating system and software up-to-date, and practicing safe browsing habits.
By following these steps, you can effectively remove a micro virus from your computer and help protect it from future infections.
Micro PC Tech Inc technician help millions of people around the world by relieving the frustration and stress caused by technical issues. Micro PC Tech Inc also helps enterprises transform customer experiences and increase satisfaction and lifetime value by enabling them to offer high quality technical support services for out of scope issues. Micro PC Tech has one of the highest resolution rates in the industry and strives to provide a great experience at every interaction. Today’s highly tech-dependent lifestyles have created an enormous need for professional tech support services. Filling this need gap neatly, Micro PC Tech helps consumers and small businesses get the most out of the technologies they use everyday by removing the stress and frustration experienced by people when dealing with technical problems.
0 notes
Text
The Art and Science of B Tech Cyber security - Exploring the Fundamentals

In an era of digitalization and technological advance ements, the critical need for robust cybersecurity measures has never been more apparent. With cyber threats evolving in complexity and frequency, organizations and individuals alike are increasingly reliant on cybersecurity experts to safeguard sensitive information and maintain the integrity of digital systems. A Bachelor of Technology degree in Cybersecurity equips students with a comprehensive understanding of the multifaceted world of cybersecurity, encompassing a wide range of knowledge and skills essential for protecting digital assets.
Understanding the fundamentals of Cyber security
Let’s get into various aspects of Cyber security and its significance in the world of technology -
B Tech cyber security curriculum
At its core, cybersecurity involves the practice of protecting computer systems, networks, and data from theft, damage, or unauthorized access. B. Tech Cybersecurity programs delve into the theoretical underpinnings of cybersecurity, helping students comprehend the principles of encryption, authentication, access control, risk assessment, and vulnerability management. Interested aspirants can check B Tech Cyber security eligibility with various colleges and universities and pick the specialization.
Foundational Knowledge
The related course structure typically begins by imparting a solid foundation in computer science and networking concepts. Students learn about operating systems, databases, programming languages, and network protocols, which serve as the building blocks for advanced cybersecurity techniques. This knowledge ensures that graduates can effectively analyze and secure various components of digital infrastructure. If you are quite enticed with this branch of engineering, start exploring B Tech CSE cyber security Fee in various colleges and universities until you find the one that befits your requirements.
Cyber Threat Landscape
An in-depth study of the ever-evolving cyber threat landscape is a crucial component of B. Tech Cybersecurity. Students explore the different types of cyberattacks, including malware, phishing, ransom ware, and Dodos attacks. By understanding the tactics employed by malicious actors, students can develop effective strategies to counter and mitigate these threats.
Network Security
Securing computer networks is a paramount concern for modern organizations. B. Tech Cybersecurity curricula cover topics such as firewalls, intrusion detection and prevention systems, virtual private networks (VPNs), and network segmentation. Graduates are equipped to design, implement, and manage network security measures to thwart unauthorized access and data breaches.
Ethical Hacking and Penetration Testing
Ethical hacking involves simulating cyberattacks to identify vulnerabilities in a controlled environment. B Tech Cyber security programs often include modules on ethical hacking and penetration testing, where students learn how to assess system weaknesses and recommend remediation strategies. This hands-on experience cultivates a proactive approach to cybersecurity.
Security Policies and Compliance
Maintaining cybersecurity within an organization requires the establishment of robust security policies and adherence to industry regulations. B. Tech Cybersecurity students gain insights into crafting effective security policies, conducting risk assessments, and ensuring compliance with standards such as ISO 27001 and GDPR. This knowledge is vital for promoting a culture of cybersecurity awareness.
Incident Response and Recovery
Even with preventive measures in place, cybersecurity incidents may still occur. B. Tech Cybersecurity programs prepare students to handle such situations through incident response and recovery planning. Graduates are trained to assess the scope of an incident, contain its impact, and orchestrate a coordinated recovery effort.
Emerging Technologies
The realm of cybersecurity is closely linked with emerging technologies. B. Tech programs expose students to cutting-edge concepts like cloud security, Internet of Things (IoT) security, Block chain, and artificial intelligence in cybersecurity. This knowledge enables graduates to adapt and develop innovative strategies to address novel threats.
A Bachelor of Technology in Cybersecurity provides a comprehensive education that empowers graduates to tackle the intricate challenges posed by the digital landscape. As the demand for cybersecurity expertise continues to surge, B Tech cyber security placements would always remain in a good stat. This specialized program paves the way for a fulfilling and impactful career at the forefront of technological defense.
0 notes
Text
The Importance Of Cybersecurity In The Digital Age

Cybersecurity is becoming an essential part of any organization’s IT strategy in the current digital age. The risk of cyber-attacks and data breaches has greatly increased as businesses depend more and more on technology for function.It is impossible to overestimate the significance of cybersecurity in the age where technology has permeated every aspect of our lives. Individuals and organizations must give priority to their cybersecurity measures as a result of the exponential rise of digital platforms and the growing sophistication of cyber-attacks.
As the Best Cyber security Consultant in Dubai, UAE SOC-365 offers Security Operations Center As A Service (SOCaaS) is a centralized team of IT security professionals that monitors and responds to cybersecurity incidents 24/7.
Significance of Cybersecurity in the digital age
Incident Response: It is still possible for a cyber-attack to happen even with the finest cybersecurity safeguards in place. The steps to be taken in the case of a breach, including notification procedures and data recovery protocols, can be outlined in an incident response plan that we can create and implement.
Protection from Cyber Threats: Malware, ransom ware, phishing scams, and data breaches are just a few of the rising cyber threats. These dangers may result in monetary loss, harm to one’s reputation, and even legal repercussions. Strong cyber security safeguards can assist prevent sensitive data from getting into the wrong hands, including personal information, financial information, and intellectual property.
Protection for Businesses: Businesses need cybersecurity to safeguard their most valuable assets, uphold client confidence, and guarantee continuous operations. A cyber-attack may cause monetary losses, service interruptions, and reputational harm to an organization. Businesses may safeguard their intellectual property, customer data, and financial transactions by investing in strong cybersecurity solutions, assuring the continuity of their operations.
Preventing Financial Losses: Both individuals and organizations may suffer significant financial consequences as a result of cyberattacks. Recovery from an assault can be expensive, with expenses ranging from analyzing the breach to fixing systems to paying out compensation to those who were harmed. Effective cybersecurity measures lessen the risk of financial losses as a result of cyber-attacks, protecting people and organizations from potential monetary hardships.
Compliance with Legal and Regulatory regulations: Data protection and cybersecurity are governed by legal and regulatory regulations that apply to many sectors. Violations may incur harsh fines, legal repercussions, and reputational harm. Organizations can reduce the risk of legal problems and show their dedication to responsible data processing by putting strong cybersecurity measures in place to ensure compliance with these regulations.
These are some of the main importance of cyber security in this digital era. In the digital age, cyber security is an inevitable part in IT industry. To safeguard critical information, stop cyber-attacks, and guarantee company continuity, a thorough cybersecurity plan is required. At SOC-365 we provide complete cyber security solutions to protect your business.
Get in touch with us to find out more about how we can keep your business secure and safe in the digital era.
0 notes
Text
Why is vulnerability Assessment & Penetration Testing required for your organization?
Organizations frequently ignore the importance of vulnerability assessments and penetration testing, but every firm is a possible target for hackers. This is evident from recent ransom ware attacks. Be accountable and ensure that the right security measures are taken to safeguard your application. The recommended approach is to perform a vulnerability assessment every year or after making significant modifications to your application.
VAPT is necessary for several reasons. Prior to being exploited by attackers, it primarily assists organizations in identifying and mitigating security issues. This can aid in averting expensive data breaches and other security issues that could harm an organization’s standing and financial position.
Various regulatory organizations and industry standards also call for VAPT. For instance, as part of their adherence to industry requirements, many businesses in the financial and healthcare industries are obliged to regularly undergo VAPT.
Organizations are implementing vulnerability assessment and penetration testing as a method of discovering and addressing security flaws as a result of the rise in cyber-attacks and the sophistication of malware and hacking techniques.
How does Vulnerability Assessment and Penetration Testing (VAPT) help any business?
Many different companies and sectors have enforced the use of vulnerability assessment and penetration testing (VAPT). Any business’ cyber-security plan must include VAPT, which supports the defence system of the company’s networks, applications, and systems. Pen testers execute simulated assaults using a variety of pen testing tools to find security flaws before thieves do.
This procedure aids firms in efficiently testing the security measures in place for their IT infrastructure and serves as a foundation for more efficiently designing security policies and procedures. To put it simply, it is a way to determine whether your business is protected from outside attacks. Now days we hear a lot about hacking activities and cyber-attacks are increasing. All of us must protect our systems and networks. You can learn about attacks and security flaws and how to close them by conducting vulnerability assessments and penetration tests.
When determining the possible risk to a company’s websites, networks, IoT devices, cloud apps, and other assets, vulnerability assessment and penetration testing are valuable services. VAPT combines vulnerability assessment and penetration testing, two essential security services, to identify issues and provide recommendations for security audits, forensic analyses, security amendments, and monitoring.
It is vital for businesses that store sensitive data in the network ecosystem without first examining any potential vulnerability there. In order to protect your network system at such a critical moment, we offer our real-time VAPT testing support to spot unauthorized access to your information and look for cyber- attacks.
VAPT testing could prove to be a very beneficial tool for companies. To shield them from hacker attacks and criminal activity, the security level is increased. Because of this, the majority of firms take it very seriously in order to reap meaningful security benefits.
Being the Best Vulnerability Assessment and Penetration Testing Company in Jaipur, Elanus Technologies have comprehensive knowledge of cyber security, including threat modelling and VAPT across devices. We have the appropriate certifications. More importantly, our staff is made up of seasoned experts that are skilled at identifying security vulnerabilities and providing assistance to fix them. In other words, we rank highly among the market’s security consultants. Our expertise can aid in locating information about your company on the dark web.
1 note
·
View note
Text
How to Choose the Right Cyber Security Advisory Firm for Your Business Needs
Businesses of all sizes worry about cyber dangers in the digital era. Data breaches and ransom ware attacks may ruin reputations and finances. Working with a trusted and knowledgeable cyber security consultancy company is vital to reduce risks and secure your organization. How can you pick from so many options? This article discusses choosing a cyber security advisory company that meets your business requirements.


Steps to Choosing the Right Cyber Security Guidance Firm
To choose the right cyber security guidance company for your organization, follow these steps. Steps are:
1. Determine company requirements.
Choosing a cyber security consultancy business starts with this. To choose the ideal organization, you must know your needs.
2. Research your options.
After determining your needs, explore cyber security advice providers. Check their services, pricing, and reputations to choose one that fits your company.
3. Get several quotations.
After narrowing your choices, call each business and obtain an estimate. This lets you compare prices and services across businesses.
Benefits of Working with a Cyber Security Guidance Firm
A Vulnerability assessment is one of the finest ways to protect your organization from cyber attacks. Working with a trusted cyber security consultancy company has several advantages:
1. They will identify risks and weaknesses.
A reputable cyber security consultancy business can assist you in discovering organizational risks and weaknesses. They may advise on risk mitigation.
2. They'll create a thorough security strategy.
After identifying risks and weaknesses, a qualified cyber security advice business will help you create a security strategy. This strategy outlines how to protect your company against cyber attacks.
3. They will provide ongoing support.
A good cyber security consultancy business will help you create a complete security strategy and assist in its implementation. They may also help you make plan revisions.
Conclusion
Choose a cyber security guidance company carefully. Choosing the right company for your organization with so many options is challenging. However, evaluate their competence and experience, devotion to customer service and data security, and pricing of services or goods. In that case, you will discover a business that fits all your needs and offers continuing assistance.
0 notes
Text
4 Things You Can Do To Keep Yourself Cyber Safe - Arya College
Tips To Avoid Cyber Attack
Private College of Engineering in Rajasthan have many courses of Cyber security It is as important as ever and With ever-growing threats to businesses, having a robust security solution is essential also We’ve all heard of enterprises paying huge fines or even going out of business because of a simple hack into their systems.
So there are simply far too many threats out there to ignore the risks from ransom ware to phishing, it could cost you your livelihood.
What Is A Cyber Attack?
It is a deliberate exploitation of your systems and/or network and Cyber Attacks use malicious code to compromise your computer, logic, or data and steal, leak, or hold your data hostage.
Some Common Cyber Attacks And Data Breaches:
• Identity theft, fraud, extortion • Some of the examples of Malware, phishing, spamming, spoofing, spyware, trojans, and viruses • Denial-of-service and distributed denial-of-service attacks • Breach of access • Password sniffing • System infiltration • Website defacement • Private and public Web browser exploits • Instant messaging abuse • unauthorized access
1. Train Your Staff.
Cybercriminals get access to your data through your employees, They’ll send fraudulent emails impersonating someone in your organization and will either ask for personal details and access to certain files also Links often seem legitimate to an untrained eye and it’s easy to fall into the trap also This is why employee awareness is vital One of the most efficient ways to protect against cyber attacks and all types of data breaches is to train your employees on cyber attack prevention.
They need to:
• Check links before clicking them and Check email addresses from the received email (have a look here at how to check it) • Use common sense before sending sensitive information and If a request seems odd, it probably is also It’s better to check via a phone call with the person in question before actioning the “request”
2. Update Your Software And Systems.
Cyber-attacks happen because your systems or software aren’t fully up to date, leaving weaknesses and So cybercriminals exploit these weaknesses to gain access to your network also Once they are in – it’s often too late to take preventative action so it’s smart to invest in a patch management system that will manage all software and system updates, keeping your system resilient and up to date.
3. Ensure Endpoint Protection.
Endpoint protection protects networks that are remotely bridged to devices and Mobile devices, tablets, and laptops that are connected to corporate networks give access paths to security threats and these paths need to be protected with specific endpoint protection software.
4. Install A Firewall.
Different types of sophisticated data breaches and new ones surface every day and even make comebacks Putting your network behind a firewall is one of the most effective ways to defend yourself from any cyber attack also a firewall system will block any brute force attacks made on your network and/or systems before they can do any damage, something we can help you with.
5. Back Up Your Data.
Data backed up to avoid serious downtime, loss of data, and serious financial loss.
6. Control Access To Your Systems.
One of the attacks on systems can be physical also having control over who can access your network is important and Somebody can simply walk into your office or enterprise and plug in a USB key containing infected files into one of your computers allowing them access to your entire network or infecting it also It’s essential to control who has access to your computers So having a perimeter security system installed is a very good way to stop cybercrime as much as break-ins!
7. Wifi Security.
Any device can get infected by connecting to a network and this infected device then connects to your business network your entire system is at serious risk and Securing your wifi networks and hiding them is one of the safest things you can do for your systems also with wireless technology developing more and more every day thousands of devices can connect to your network.
8. Employee Personal Accounts.
Every employee needs their login for every application and program and Several users connecting under the same credentials can put your business at risk also having separate logins for each staff member will help you reduce the number of attack fronts so users only log in once each day and will only use their own set of logins.
9. Access Management.
Btech College in Jaipur Rajasthan says software on business-owned devices that could compromise your systems and having managed admin rights and blocking your staff from installing or even accessing certain data on your network is beneficial to your security.
10. Passwords.
Once a hacker figures out your password, they now have access to everything in your system and any application you use having different passwords set up for every application you use is a real benefit to your security, also changing them often will maintain a high level of protection against external and internal threats.
Conclusion:
Top Engineering College in Jaipur Rajasthan says It can be difficult to know where to begin when it comes to protecting your business from cybercrime and cyber-attacks and There’s so much information out there that it can become overwhelming, especially when the info is conflicting also You need a solution that’s right for your business and your employees
0 notes
Text
Important Tips to Prevent yourself from Cyberattacks
Tips To Avoid Cyber Attack
Private College of Engineering in Rajasthan have many courses of Cyber security It is as important as ever and With ever-growing threats to businesses, having a robust security solution is essential also We’ve all heard of enterprises paying huge fines or even going out of business because of a simple hack into their systems.
So there are simply far too many threats out there to ignore the risks from ransom ware to phishing, it could cost you your livelihood.
What Is A Cyber Attack?
It is a deliberate exploitation of your systems and/or network and Cyber Attacks use malicious code to compromise your computer, logic, or data and steal, leak, or hold your data hostage.
Some Common Cyber Attacks And Data Breaches:
• Identity theft, fraud, extortion • Some of the examples of Malware, phishing, spamming, spoofing, spyware, trojans, and viruses • Denial-of-service and distributed denial-of-service attacks • Breach of access • Password sniffing • System infiltration • Website defacement • Private and public Web browser exploits • Instant messaging abuse • unauthorized access
1. Train Your Staff.
Cybercriminals get access to your data through your employees, They’ll send fraudulent emails impersonating someone in your organization and will either ask for personal details and access to certain files also Links often seem legitimate to an untrained eye and it’s easy to fall into the trap also This is why employee awareness is vital One of the most efficient ways to protect against cyber attacks and all types of data breaches is to train your employees on cyber attack prevention.
They need to:
• Check links before clicking them and Check email addresses from the received email (have a look here at how to check it) • Use common sense before sending sensitive information and If a request seems odd, it probably is also It’s better to check via a phone call with the person in question before actioning the “request”
2. Update Your Software And Systems.
Cyber-attacks happen because your systems or software aren’t fully up to date, leaving weaknesses and So cybercriminals exploit these weaknesses to gain access to your network also Once they are in – it’s often too late to take preventative action so it’s smart to invest in a patch management system that will manage all software and system updates, keeping your system resilient and up to date.
3. Ensure Endpoint Protection.
Endpoint protection protects networks that are remotely bridged to devices and Mobile devices, tablets, and laptops that are connected to corporate networks give access paths to security threats and these paths need to be protected with specific endpoint protection software.
4. Install A Firewall.
Different types of sophisticated data breaches and new ones surface every day and even make comebacks Putting your network behind a firewall is one of the most effective ways to defend yourself from any cyber attack also a firewall system will block any brute force attacks made on your network and/or systems before they can do any damage, something we can help you with.
5. Back Up Your Data.
Data backed up to avoid serious downtime, loss of data, and serious financial loss.
6. Control Access To Your Systems.
One of the attacks on systems can be physical also having control over who can access your network is important and Somebody can simply walk into your office or enterprise and plug in a USB key containing infected files into one of your computers allowing them access to your entire network or infecting it also It’s essential to control who has access to your computers So having a perimeter security system installed is a very good way to stop cybercrime as much as break-ins!
7. Wifi Security.
Any device can get infected by connecting to a network and this infected device then connects to your business network your entire system is at serious risk and Securing your wifi networks and hiding them is one of the safest things you can do for your systems also with wireless technology developing more and more every day thousands of devices can connect to your network.
8. Employee Personal Accounts.
Every employee needs their login for every application and program and Several users connecting under the same credentials can put your business at risk also having separate logins for each staff member will help you reduce the number of attack fronts so users only log in once each day and will only use their own set of logins.
9. Access Management.
Btech College in Jaipur Rajasthan says software on business-owned devices that could compromise your systems and having managed admin rights and blocking your staff from installing or even accessing certain data on your network is beneficial to your security.
10. Passwords.
Once a hacker figures out your password, they now have access to everything in your system and any application you use having different passwords set up for every application you use is a real benefit to your security, also changing them often will maintain a high level of protection against external and internal threats.
Conclusion:
Top Engineering College in Jaipur Rajasthan says It can be difficult to know where to begin when it comes to protecting your business from cybercrime and cyber-attacks and There’s so much information out there that it can become overwhelming, especially when the info is conflicting also You need a solution that’s right for your business and your employees
0 notes
Text
Inspire Tax Consultancy Provides Financial audit and ICV Services in UAE
Inspire Tax Consultancy Provides Financial audit and ICV Services in UAE
Financial Audit
The purpose of an annual financial audit is to ensure that your business is operating in accordance with local regulations and laws. It also helps to improve your business's internal controls and management practices, thereby reducing the risk of fraud or other types of illegal behaviour. It is important to keep track of the financial accounts of your business in the UAE. This can be done through a financial audit.

Inspire Tax Consultancy should undergo a financial audit every year, but it's also important to do so once every three years. The audit will be performed by an independent firm that specializes in auditing businesses and their records. The firm will examine all of the financial statements from previous years, as well as any other information provided by the company.
External Auditor or Internal Auditors
The financial audit in UAE is a very important step in the company's growth. The audit can be done by an external auditor or internal auditors.
The external auditor will provide the independent view of a firm's financial statements and report on their overall compliance with accounting standards. The Internal auditors will work closely with the management team to ensure that all relevant laws, regulations and best practices are being adhered to throughout the organization.
An external audit is an ideal way for your company to receive independent assurance from your auditors about its financial position and performance. You can find out more about our services at Inspire Tax Consultancy.
In the United Arab Emirates, the financial audit is an essential part of the financial system. The purpose of the audit is to assess the entity's financial statements and provide assurance that they are free from material misstatement.
ICV
Inspire Tax Consultancy can complete the Audit process, Guide and help in Filing the ICV template and get the same certified by ADNOC appointed certifying body. The ICV IN UAE is a full-service accounting firm that provides financial audit services. We specialize in helping businesses, both large and small, navigate the complex world of accounting, tax, and bookkeeping. We offer the following services:
1. Financial audit
2. Income tax audit
3. Payroll processing
4. Bookkeeping services
The team at ICV IN UAE will take the time needed to understand your situation and provide honest advice based on their experience as well as theirs so that when it comes to making important decisions about how your company operates you will have expert advice at your fingertips. In a recent survey conducted by ICV, it was found that the average UAE citizen believes that financial fraud is the most common type of cybercrime. The next most common form of cybercrime is phishing, followed by ransom ware.

Our teams are made up of professionals from different backgrounds, who are all committed to providing the best possible service and support to our clients. They choose to work at ICV because they share our values we believe that everyone has the potential to be successful, and we strive every day to help each one of them reach their full potential.
As a result, it's important for companies to protect themselves against such attacks and ensure they're not vulnerable to them in any way. This includes conducting regular audits as well as regular security assessments because these are two crucial steps in ensuring your organization's security posture is working effectively."
They have a team of accountants who will assist you with all aspects of your audit needs, from preparing your annual report to performing an on-site audit. It's not uncommon for businesses to have problems with the financial reporting process, but the good news is that there are ways to get around it and make sure your accounting records are accurate and up-to-date. For more information visit our website: - www.inspiretaxconsultancy.com
0 notes
Text
Is blockchain the same as cryptocurrency Hera soft company?

Blockchain and Cryptocurrency is the technology that enables the existence of crypto currency (among other things). Bit coin is the name of the best-known cryptocurrency, the one for which block chain technology was invented.
By spreading its operations across a network of computers, block chain allows Bitcoin and other cryptocurrencies to operate without the need for a central authority. This not only reduces risk but also eliminates many of the processing and transaction fees.
Blockchain is the technology that underpins the crypto currency Bit coin, but Bitcoin is not the only version of a blockchain distributed ledger system in the market. There are several other cryptocurrencies with their own blockchain and distributed ledger a rchitectures.
This includes transactions, governance, payment options, DeFi initiatives and well as the metaverse.” He explains that private blockchains do not necessarily need cryptos to work on blockchains as they work on the system of tokenisation. While for public blockchains one needs to have cryptos.
Herasoft Distributed Cloud Software, blockchain technology, blockchain encryption, ransom ware protection, block chain development, block chain application, blockchain programming, enterprise security.
#Ransom ware Proof Solution#Consensus Computing#Ransom ware Attacks#Digital Transformation#Cyber security#Herasoft Distributed Cloud Software#blockchain technology#blockchain encryption#ransom ware protection#block chain development#blockchain application#blockchain programming#gaming#business#developers & startups#books & libraries
1 note
·
View note
Text
One of the things I’ve been trying to point out with my long running series of posts about group dynamics, is that human psychology is pack oriented. Any and all accusations, even ones proven untrue, have an impact on the group and its cohesion, and that more often than not, accusations actually eventually lead to polarization, which results in extreme behaviors. The online environment is almost ideally constructed to make this happen even worse and even faster.
Online bullying is an incredibly serious issue. Very very very serious. Ten years ago when I began this project, we didn’t have the obvious proof of Russian and Chinese think tanks geared toward election interference. We didn’t have ransom ware attacks, or extremist groups using social media platforms to actively plan insurrections and foment extremism. When I constructed my hypothesis, none of these things existed.
And yet here we are.
21 notes
·
View notes
Text
I fixed Start-Up to my satisfaction
No one asked, but here’s how the fix-it fanfic would go for Start-Up if I had the energy to write that (I don’t and I already have too many works on the go):
1. This would be a total rewrite cause the writers clearly never intended to have Jipyeong and Dalmi end up together. Never giving him any real chance was a disservice to the love triangle and since it dragged on for so long, ultimately the characters. So the only way I would feel like I could make it work would be doing away with the triangle all together.
2. Forget the revenge plot, 2STO, Alex, and the time jump. None of that added to the story or moved it along. Ultimately, we could have done without.
3. If I don’t specifically mention something it’s cause I wouldn’t change it or I think it’s so inconsequential to even matter.
This got LONG, so it’s under the cut.
OK, so:
The first few eps go along the same way except for a few clear details: Jipyeong and InJae interact backstage at the panel they do at the beginning. They kind of seem to hate each other? But also a little flirty? Ms. Yoon is equal parts exasperated and entertained.
Leading up to the hackaton, the plot relatively stays the same, but after Dalmi discovers Dosan at Sandbox, Jipyeong, Dosan, and grandma start to realize the lie is going too far. Keeping up long term is never going to work. They all separately agonize about it, before coming together and agreeing that they have to tell the truth. A fun episode full of their almost-confessions ensues! It is humorous!! Light!! They are going to tell her!!
Dalmi is always a little skeptical. How come Jipyeong is *always* around? How come Dosan remembers *absolutely nothing*? Why did he lie to her about being successful, really? Why did Jipyeong help him? None of it makes sense.
Before they can find the right time to tell her, Dalmi outsmarts them. Following the hackaton, she’s messing with the handwriting software they developed, so proud of their work, and the day’s presentation. She picks up the presentation notes Jipyeong marked up and notices the handwriting looks familiar. She compares it to a letter and runs it through the software. It’s a match.
She brings the letter and the presentation to Dosan and asks him for an explanation. He comes clean; Jipyeong was the one who wrote the letters and asked for his help, but he himself was so taken with her that he wanted to keep getting to know her, even under false pretenses.
Dalmi is devastated. She has no idea who this stranger is and now she works with him? She blows up at grandma, couldn’t believe that she would lie to her for all these years and let her humiliate herself.
Once Dalmi has calmed down, grandma talks to her. Explains that she wanted to help her when she was young cause she was so lonely. Explains about Jipyeong, explains that he was young and lonely too. She didn’t expect it to go this long. She just wanted to give her something back after all that pain.
The next day, Jipyeong talks to Dalmi. He explains that he has been indebited to her grandma and has tried to find them. He says that he had no friends then and her letters were his only comfort. He tells her about growing up an orphan and how her grandma took him in. Dalmi starts to fall for him; he’s he first love, the one she has been looking for all along, and he is finally here, and has been through so much.
Only problem? Jipyeong kind of views her as a sister.
Her actual sister though? Continues to infuriate him. He still volunteers to be Samsan Tech’s mentor and the way she keeps messing with them is driving him insane. He’s still tough as hell, but invested in being a mentor. He doesn’t understand why she can’t let it be? They bicker at every opportunity.
Dalmi told Dosan that they’ll have to continue to work together, but she is wary of him now. What parts of him that she knew were real? What part was fabricated? Now that she knows who her real first love is, she wants to focus on that.
Dosan is disappointed, but understanding. He finds out about grandma in the same way and decides to make the code for Noongil in secret. He still cares for Dalmi and hopes she can grow to learn to care about his true self.
Dalmi finds out about grandma from grandma. Idk how but she does.
Dalmi, in a fit of sadness, goes to Jipyeong at his apartment for comfort, and tells him about her grandma. He is devastated. Together, they drink the night away, laughing and crying, talking about their past. Dalmi tries to make a move, but Jipyeong rejects her, saying she is drunk. She says she isn’t and she loves him. He lets her sleep it off. The next morning, she doesn’t remember anything, and Jipyeong has no idea what he is going to do now cause he doesn’t want to hurt Dalmi.
The next day, he sees InJae at work. She asks him why he seems so upset and he doesn’t know how to reply. She says it must be something stupid her sister did again. He explodes and they fight; he doesn’t understand how she can just abandon her family like that, she doesn’t understand why he cares so much. He tells her to go visit her grandma. InJae is confused.
InJae goes and visits grandma and finds out she is going blind. She is devastated; she hasn’t seen her for years and now it feels like she had wasted them all. She ends up going to Jipyeong’s and breaking down, standing in his doorway crying saying she’s never known how to reconcile with her grandma and sister after all these years and now it might be too late. Jipyeong hugs her in the hallway as she cries on his shoulder.
Unfortunately, down the hall is Dalmi, witnessing the whole thing. She had come by to surprise Jipyeong with dinner and to ask him some questions before demo day. She is heartbroken - Jipyeong and her sister?! - and flees.
Right before demo day, where the team is going to present their handwriting software, Samsan Tech is hit with a ransom ware attack. The twins were at it, obvs, and no one knows what to do. Yongsan says they need to call Jipyeong but Chulsan tells him no, they can figure it out on their own. The two Sans look to Dalmi to make the call. Still upset about what she saw a few days prior, she says not to call him.
It blows up in their faces. They were unable to stop the ransomware attack and their data was erased. They have nothing, with a mere 72 hours before demo day.
Jipyeong is livid. He can’t believe they didn’t call him. Samsan Tech fights back, saying that he never believed in them anyway. He’s so harsh and never supportive. Jipyeong realizes he hasn’t been the best mentor.
InJae goes to visit Dalmi. She heard about the ransomware attack and wants to make sure she’s okay. Dalmi admits that she was foolish, not willing to let Jipyeong help cause of her personal feelings. She doesn’t think she deserves to be a CEO. Injae asks if she likes Jipyeong and Dalmi nods, embarrassed, and says she is pretty sure he likes someone else. Injae is clueless and says whoever that is must be an unlucky fool. She responds with her own stories of failure in her first few years as a CEO. The sisters smile; the cracks in their relationship are still there, but starting to close.
Getting ready to pack things up and leave, Dosan is backing up his files one more time. One of the Sans sees the code over his shoulder? What’s this for? He asks. Dosan tries to hide it; it’s the code for Noongil. The team prods at him and he pitches the idea. Wait, this might be something.
Jipyeong doesn’t love the idea; it’s not profitable, they would have to secure CSR investors in like, a day to make it to demo day. But he knows it will help grandma. He agrees to help them make it happen.
Cue montage of them trying to put together a pitch just in time! All nighters! Grandma brings hot dogs! Sleeping in weird positions! But they gotta do it!! They gotta stay in the game!!
It’s the middle of the night, only Dalmi and Dosan are awake, still working; everyone else is taking a nap. Dalmi asks where he got the idea for the app and he confesses it was her grandma. Dalmi is touched. Maybe there is more to him than she thought.
Jipyeong, sleep deprived, runs into Injae the morning of demo day. Things are awkward between them since their hallway encounter. She notices that he looks tired and asks to get coffee. Over 1+1 lattes, she asks how things are going with her sister’s company. He says he thinks they might pull through. She asks if he likes Dalmi and that’s why he’s putting so much effort in. Jipyeong says that she is very dear to him and very important, but not in the way she’s implying. They exchange a look and awkwardly glance away. Jipyeong muses that it was strange that someone was able to hack into the Sandbox servers to get the code; whoever it was must have had working knowledge of Sandbox’s set up. Injae thinks to herself, reflecting on the twins recent weird behavior. Something clicks; she runs off. She has to fire the twins.
Demo day happens. It goes well! They secure a modest investment that will keep them up and running for a couple of years. Everyone is so excited!! Quietly, in the hallway after, Dalmi confesses to Dosan that she is thankful for him. He is bashful in response. It’s cute!
Samsan Tech continues to work closely together. Jipyeong mentors them, like an exasperated babysitter, but you can tell he likes it. Dosan and Dalmi continue to grow closer together, running into each other on the bus and working late, having a bunch of meet cutes.
Meanwhile, Jipyeong goes over to see grandma and Injae is already there. He’s surprised to see her; she’s a little dressed down, making food with her mom. He’s never seen her like this. Grandma asks him to stay for dinner.
Dosan and Dalmi work late one night. No one else is around. They end up talking about their perspective dreams. Dosan says he’s not sure what his is anymore, but he thinks that working on Noongil and with Dalmi and the team will help him find it. Dalmi’s heart flutters.
Meanwhile, Jipyeong and Injae are doing the dishes after dinner. They talk about their pasts; how Injae has felt alone since she left her family, how much she regrets it. He says he has felt alone his whole life. A moment passes between them, as they look at each other. Grandma interupts. They jump.
Dalmi wakes up the next day and looks at the Follow Your Dream ball. She realizes that she can’t stop thinking about Dosan; somewhere along the way, he’s replaced Jipyeong in her mind. She likes how considerate he is of others, how he smiles with his eyes, and how he has a sweet boyish charm. She realizes she might be falling for him.
At Sandbox that day, the news comes out; the twins have gone to Morning Group and are launching a competitor product to Noongil and this time, with a huge financial backing. Everyone is devastated.
Injae comes to see Dalmi about it and they fight; Dalmi says that this must have been Injae’s plan all along. Injae insists it wasn’t and that Dalmi is always looking to blame someone other than face the facts. She leaves, angry.
The team asks Jipyeong if there is any hope of continuing. He admits that it is unlikely they will surpass a product with a heavy backing and corporate support. They lash out at him, saying again that he never supports them. He counters that they only listen to him when he says things they want to hear and they’ll never be successful at that rate.
Saha says they might as well disband. This is hopeless, two strikes against them. The two Sans agree. Dosan says they should consider trying and looks to Dalmi for support. She tearfully disagrees.
They decide it’s over.
Dosan goes to visit Dalmi. They talk about dreams again. Now that it has been taken from them, Dosan knows what his is. He wants to make AI that will help people. He wants to make people’s lives better. Dalmi is overwhelmed and kisses him.
Injae is in her office, cleaning up files, when she notices something saved on an encrypted, secure doc on the server. She goes inside and sure enough; it’s all of the code to hack into Sandbox and Samsan Tech’s servers. She immediately calls the police.
The twins and Morning Group are charged for whatever charged you get when you conduct a ransomware attack. Idk I am not Googling it!!! Their investors pull out - Noongil is saved!!!
Jipyeong goes to Injae; he knows this was her doing. He thanks her. She says she is starting to understand why he cares so much, about family. They kiss.
Dalmi and Dosan stand outside a large skyscraper. They are going to go inside to pitch their business to a huge investor, Jipyeong had made them practice over and over again. They know there is a small chance they will get it, but they are going to try again. They take each other’s hand and walk towards the building.
EPILOGUE; time jump of three years later!!!!
Samsan Tech has created a huge amount of AI software for a variety of disabilities and has their own offices. Yay!
Dosan and Dalmi get married; Injae at her side, the two Sans by his. In the first aisle sits Jipyeong next to grandma, he and Injae’s baby on his lap. Cute!!!
Grandma has a hot dog stand again, cause Dalmi, Injae, and Jipyeong pitched in to help her buy it. Everyone helps out on the weekends and they hang out there with her mom, Jipyeong and Injae’s baby running around, like HAPPY FAMILY TIMES.
THERE I FIXED IT TO MY SATISFACTION
BYE
#start up#start-up#han ji pyeong#won in jae#seo dal mi#nam do san#start up kdrama#start up tvn#kdrama#fix it fic#jidal#dodal#jinjae#this took me an hour#but now i can be free from this show
195 notes
·
View notes