#NOT the username based personal websites that run on another server
Explore tagged Tumblr posts
Text
curl issue: files i could upload perfectly yesterday no longer work today. at least i learned that the guy in charge of the server is on vacation this week, so he will get a call some time next week.
#tütensuppe#its weird though bc i sent him a mail 10 days ago with no response#and its ALSO weird that a) its just this one single guy and b) next to nobody seems to know hes (apparently) the sole admin#i called the department secretary and she and another guy directed me to the web service team again#who i already contacted and was told that they only manage the content management system websites#NOT the username based personal websites that run on another server
1 note
·
View note
Text
can't download activation for avast vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can't download activation for avast vpn
Avast VPN activation troubleshooting
When it comes to activating Avast VPN, there are a few common troubleshooting steps you can take to ensure a smooth and successful activation process.
Firstly, make sure that you have a stable internet connection. A poor or intermittent connection can cause activation errors. Try restarting your modem or router to see if that resolves the issue.
Another common issue when activating Avast VPN is incorrect login credentials. Double-check that you are entering the correct username and password associated with your Avast account. If you're not sure, you can reset your password through the Avast website.
If you continue to experience activation problems, try uninstalling and reinstalling the Avast VPN application. This can help resolve any software glitches that may be causing the issue.
It's also worth checking if your Avast subscription is up to date. An expired subscription can prevent the VPN service from activating successfully. Renew your subscription if needed to ensure uninterrupted service.
Finally, if none of these troubleshooting steps work, reach out to Avast customer support for further assistance. They have dedicated professionals who can help diagnose and resolve any activation issues you may be facing.
By following these troubleshooting tips, you can overcome common activation issues with Avast VPN and enjoy a secure and private internet browsing experience.
Download issues with Avast VPN activation
When you encounter download issues with Avast VPN activation, it can be frustrating and inconvenient. Avast VPN is a popular choice for many users looking to secure their online browsing activities and protect their privacy. However, technical problems during the activation process can hinder your ability to use the VPN effectively.
One common issue users face is difficulty downloading the Avast VPN software to their devices. This can be due to a variety of reasons, such as internet connectivity problems, server issues on Avast's end, or conflicts with existing antivirus software on the device. To troubleshoot this problem, ensure that you have a stable internet connection, temporarily disable any conflicting antivirus programs, and try downloading the software again.
Another download issue with Avast VPN activation could be related to compatibility concerns with your operating system. Make sure that your device meets the minimum system requirements for the VPN software to run smoothly. Additionally, check for any pending system updates that may be affecting the download process.
If you continue to experience problems with downloading Avast VPN activation, reaching out to Avast's customer support team for assistance is recommended. They can provide personalized troubleshooting steps based on your specific issue and help you resolve any technical barriers preventing you from activating the VPN software successfully.
In conclusion, dealing with download issues during Avast VPN activation can be bothersome, but with the right troubleshooting steps and support from Avast, you can overcome these challenges and enjoy a secure and private online browsing experience.
Activation failure for Avast VPN download
Encountering an activation failure during the Avast VPN download process can be frustrating, but understanding the common reasons behind it and the steps to troubleshoot can help resolve the issue swiftly.
One of the primary reasons for activation failure could be an unstable internet connection. Ensure that you have a stable and reliable internet connection before initiating the download and activation process. Additionally, check if there are any ongoing network issues that could be hindering the activation.
Another possible cause could be an incorrect activation code entry. Double-check the activation code you have entered to ensure it is accurate and matches the one provided to you. It's essential to input the code exactly as it appears, including any dashes or special characters.
Furthermore, ensure that your system meets the minimum requirements for Avast VPN installation. Incompatible operating systems or insufficient system resources could lead to activation failures. Verify that your device meets the necessary specifications before attempting to activate the VPN.
If you continue to experience activation failures despite following these steps, reaching out to Avast customer support for assistance is advisable. They can provide personalized guidance and troubleshooting steps based on your specific issue.
In conclusion, encountering activation failure during the Avast VPN download process can be addressed by ensuring a stable internet connection, entering the activation code correctly, and verifying system compatibility. If issues persist, seeking assistance from Avast customer support is recommended to resolve the issue promptly.
Fixing Avast VPN activation download problems
Facing issues while trying to activate or download Avast VPN can be frustrating, but rest assured, there are steps you can take to resolve these problems. Here's a guide to help you fix Avast VPN activation and download issues.
Firstly, ensure that you have a stable internet connection. A weak or intermittent connection can hinder the activation or download process. Try switching to a different network or restarting your router to improve connectivity.
Next, double-check that you're entering the correct activation code. Even a small typo can prevent successful activation. Make sure to copy and paste the code directly from the email or account where you obtained it to avoid errors.
If you're encountering download issues, verify that your device meets the system requirements for Avast VPN. Ensure that your operating system is up-to-date and compatible with the latest version of the VPN software.
It's also advisable to temporarily disable any firewall or antivirus software that may be blocking the download or activation process. These security measures can sometimes interfere with legitimate software installations.
If you're still experiencing problems, consider reinstalling Avast VPN. Uninstall the program completely from your device and then download the latest version from the official Avast website. Follow the installation instructions carefully, and retry the activation process.
In some cases, contacting Avast customer support may be necessary for further assistance. They can provide personalized troubleshooting steps and guidance to help you resolve any persistent activation or download issues.
By following these steps, you should be able to troubleshoot and fix Avast VPN activation and download problems effectively, ensuring that you can enjoy a secure and private internet browsing experience.
Troubleshooting Avast VPN activation download errors
Avast VPN is a powerful tool that helps users protect their online privacy and security by securing their internet connection and encrypting their data. However, sometimes users may encounter activation or download errors when trying to install or set up Avast VPN. These errors can be frustrating, but there are several troubleshooting steps you can take to resolve them.
One common activation error that users may encounter is related to invalid license keys. If you receive an error message stating that your license key is invalid, double-check that you have entered it correctly. Ensure there are no extra spaces or typos in the key. If the issue persists, contact Avast support for further assistance.
Another common error is related to difficulties in downloading the Avast VPN software. If you are having trouble downloading the software, try temporarily disabling your firewall or antivirus software, as they may be blocking the download. You can also try using a different internet connection or device to see if the issue is specific to your current setup.
If you continue to experience issues with Avast VPN activation or download errors, you may need to uninstall the software completely and reinstall it from scratch. Make sure to follow the installation instructions carefully and restart your device after the installation is complete.
By following these troubleshooting steps, you can resolve activation and download errors with Avast VPN and enjoy a secure and private internet browsing experience. Remember to reach out to Avast support if you need further assistance with any technical issues.
0 notes
Text
Fenk8- Denki Kaminari x Male Reader
After hours of having to rewrite this piece, another half hour of tumblr simply not co-operating, and a few minutes of needing to convince myself that my piece wasn’t trash... I present to you my submission to the BNHA Server Collab. Our prompt was plain and simple, Pen Pals.
Pairing: Kaminari Denki/ Male Reader
Rating: E for Explicit. And C for Crackhead Energy
Kinks: Cyber Sex, Semi-Anonymous Sex, Penpal Sex, Dom!Denki, Daddy Kink, Premature Ejaculation, Cum Eating Strangers to Friends to Lovers, Flexibility, Dumbasses in love
Word Count: 2930
QUICK NOTE BECAUSE I AM A DUMBASS- Paladin is our boy Icyhot... dumbass needed a real Hero name and in a fic I enjoy that is the one he chose. And Flashpoint is our favourite boy Touya Todoroki AKA Dabi. I made him a damn hero because baby deserves it.
His username had been Fenk8, of which you weren't certain why. The penpal website was known for people seeking out more adult interactions, but you hadn't been looking for that. Not at first, really. Charming messages such as, "Hey sweet thing" and "If we were the alphabet I'd put U and I together" changed that slightly. The message that made you laugh the most had been the U and I joke. Corny pickup lines were the way into your heart. Of course you had to respond with your own corny pickup line, "Did you just shock me, or was it your electric personality?" Of course he freaked out a little at that, which you didn't understand. Fenk8 got a little wiggy when anything mentioning electric personalities was brought up. So you tried to avoid it. But you couldn’t help that he sparked your interest.
>>Hey sweetness. Birthday cake can be any flavour. But birthday cake is a flavour
>>What is up, hot stuff? The opposite of waterfall is firefly.
>>My sugarcube, the oldest person alive was born with an entirely different set of humans around.
>>Technichally… if we made everything legal the crime rate would be zero. I'M JUST SAYING!
>>Woah, sunshine… if we can't see air… can fish see water?
>>Orange is the only colour you can taste. I'm just saying.
Every conversation started with something random. Something that had you scratching your head, or made your eyes go wide because holy fuck he wasn't wrong. It was chaotic, but you loved it. He also tried out different pet names most of the time. Your favourite was Sugarcube. It was cute and different. You loved talking with him, it was like talking to your best friend. Only you didn't know your best friend's name, or what he looked like. Or what he did for a living. But Fenk8 was your best friend, nonetheless. The friend that had the nerve to ask you who put the alphabet in alphabetical order. But still your best friend. Days of talking turned into weeks. Weeks into months. The two of you had yet to share photos of yourselves yet, and that was fine. He sent you pictures of dogs he saw on walks, of beautiful flowers, and occasionally the most beautiful sunrises. He worked strange hours, often all over Tokyo and surrounding cities. But it just meant you never got the same scenery twice. Once he had been in the same area as you, sent photos of the bakery you worked at. He didn’t know you worked there, just sent a picture of a little pastry you had made. Said it reminded him of you. That same day Chargebolt had come in and bought one of your pastries. The two of you were excited for different reasons that day. Him because he found out that you made pastries, you because your favourite hero had bought something you made and even came up after and said it was delicious. You hadn't told him about that, you did tell him that you had a small obsession with the electric pro hero. Your potential friend(?) didn't need to know that your favourite sleepwear was an oversized t-shirt from the very first line of Chargebolt merch.
>>Hey sweetheart! Saw the cutest little dog today, thought you would love him as much as I did. His name was Chowchan!
>>How was your day??? I hope you didn't work too hard! I've missed talkin' to ya. Sorry I've been so busy, sweetcheeks.
Attached to his messages was a picture of the most obnoxiously fluffy Chowchow curled into a ball at the feet of… holy fuck was that Pro-Hero Dauntless!? Fenk8 got that close to the Number One hero, got a picture of his dog, and it looked like they were having a casual conversation based on the flush covering Dauntless' cheeks and the adorable pikachu bag you knew belonged to Fenk8 sitting beside him. Just what did Fenk8 do for work that he was chummy with a pro!? Reporter? Maybe he was a PR agent? Or a personal assistant? The last two would make a lot of sense, given that he travelled a lot for work.
<<OH MY FUCKING GODS FENK8. YOU GOT SUCH A CUTE PICTURE OF CHOWCHAN!
<<you even got Dauntless out of his hero gear, sitting still… a god. You're a god.
After a few moments of silence, your phone dinged with another notification.
>>I guess Dauntless is your favourite pro then? Makes sense, he is pretty hot.
<<No? Chargebolt is my favourite. He's been to my bakery a few times, compliments my pastries. Sure, his quirk has a pretty big drawback… but over the years he has really gotten good at controlling his output. Did you see his most recent thwart of a bank robbery!? He got the emergency backups back up and running using his quirk! And when he let himself be the backup generator for the children's hospital last winter…
<<Sorry… rambling. I just… Chargebolt is the best. Some are born for greatness, others have to work for it. He works for it. He said my Lemon Puffs are his favourite, which is good because he inspired them. The popping candy in the dough represents static electricity! I can't believe that Chargebolt likes my sweets… sorry. I'm sure you don't want to talk about pros.
>>Honestly, reading you so passionate is amazing. I can't believe that someone would be so vocally passionate about a hero only in the top fifty. Ground Zero, Dauntless, Flashpoint, Paladin… even Uravity and Froppy. I hear so much about them. But never someone so excited about Chargebolt.
<<He is an amazing hero. I watched his first Sports Festival… all of his Sports Festivals really. I really love him as a hero. But ue never does press events, not like the top ten. And I work when he does patrols. So I've never interacted with him outside of work… but man what I wouldn't give to meet the man. I'm sure you have a favourite pro?
>>Honestly, I do. Red Riot is one of my favourites. Ever heard him sing Karaoke? I'll have to send you a video I have of it. Guy goes all out.
<<Red Riot is pretty cool. But Chargebolt will always be my favourite.
How had you gone off on a full rant about a pro hero? Especially to your internet friend. He was going to think you are such a weirdo now. But apparently he didn't, because he requested a faceless video call for that night. Something about needing to get off, and hoping you would help. Sure, he was a little more smooth than that, but all you cared about was actually getting to see part of Fenk8. You two had only done something similar once, and it had been through text alone. Now you got to attach a voice and a faceless body to Fenk8. You only hoped you still found him sexually attractive after this. What if he was too muscular, like Red Riot. Or covered in deep scarring like Flashpoint. Not that you didn't find them attractive, but with Chargebolt as the man in your fantasies anyone else would pale. He was your number one fantasy, could you really be blamed though? It didn't occur to you that Fenk8 could be a creepy old man, or a murderer or something. Surely the man who seemed chummy with Dauntless couldn't have even an evil bone in his body. Dauntless was too pure to be friends with someone who was genuinely bad.
So when the evening rolled around you found yourself in just an oversized fleece sweater and a pair of black boxer briefs. Your already straining erection begging to be touched as you looked over the thin yet very toned torso before you. Fenk8 was built just like you imagined Chargebolt would be. Lean and just toned enough to show he worked out. You noticed a faint glimmer in his nipples, holy fuck Fenk8 had them pierced! A tiny barbell in each dusky nipple, catching the light just right every time he moved. Below that was a navel piercing, man did he have a lot of piercings apparently. Because he had mentioned his tongue, and webbing in an earlier message you guys had shared.
"Like what you see, Sugarcube?" You could hear the smirk in his words. And the chuckle he made when you whimpered an affirmative was divine. "Why don't you take that sweater off, I had a long day at work and watching my Sugarcube stroke himself would really make my day." The man already stroking himself. A nice thick cock in his hand, nestled nicely beneath a cute nest of blond curls. Faintly you wondered if you would ever get to sit on it, positive that it would be a perfect stretch. Quick to comply you pulled the sweater over your head and let him see your chest in its entirety. A deep blush staining your chest, lower lip pulled between your teeth. Removing your underwear took a little more courage, your member was not as nice to look at as Fenk8's. You would call Fenk8's cock attractive. Thick, long, nicely curved. You would probably call yours cute. It was smaller than his, and looked smaller beneath your curls that were a little darker than the rest of your hair.
"That's a good boy. Now why don't you stroke yourself for Daddy. Let me hear you whine and whimper for my cock to stretch you out." You imagined a wicked smile on his face as he spoke. Eyes locked on the cock in his hands, mouth falling open when you finally noticed the glimmering bits of metal. A three piece bottom ladder, a two piece scrotum ladder, his lorem, a King’s Crown and an Albert. Eight piercings in his dick alone. Was there anywhere he didn't have pierced?!
"Y-yes, Daddy." Finally spoken as you wrapped a hand daintily around your length and began to softly stroke. A soft whimper ringing out before you could stop it. You had been pent up all day, ever since the message he sent asking for this call. Already your body threatened to betray you and make Fenk8 think you were some pathetic virgin. Which you weren't! And even if you were… it was no one's business.
"F-fuck!" You whined out and tensed as you came. Embarassed that you finished so quickly. But it wasn't entirely your fault. Fenk8 got you so worked up earlier. White ropes splattering your chest and stomach as you tried to hide your face from him while slowly slumping down.
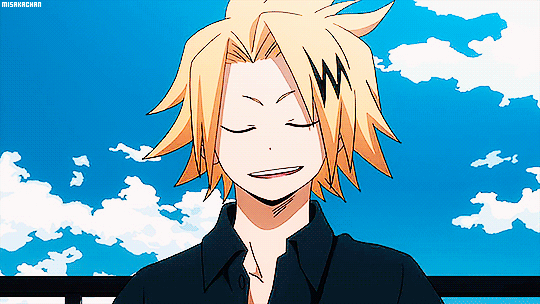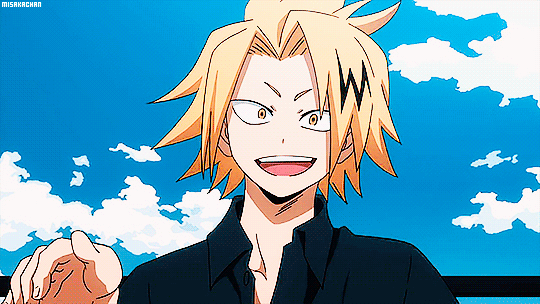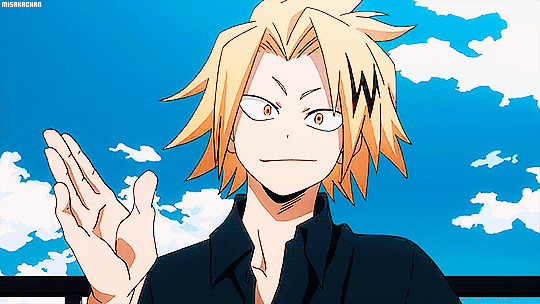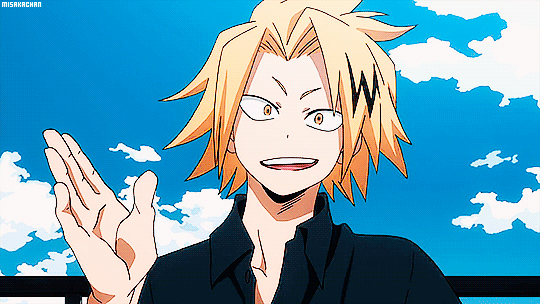
"That was so hot baby. A few strokes and you're already cumming for Daddy. I'm so proud of you for wanting to make me happy. Want your reward, Sugarcube?" His voice was thickened, dripping like honey as he spoke to you. Opening your eyes you saw his hand lazily stroking over his length while the other reached toward the camera to adjust it. Raising it and- HOLY FUCK. Fenk8 is Chargebolt.
"Hey, Sugarcube. Heard you have a favourite pro." His charming smile on full display, the hand that had adjusted the camera shooting you a finger gun. Your eyes went wide and he licked over his lips. That tongue piercing you dreamed of, the one positioned a little off to the left, darting out and teasing you. The blond kept amber eyes locked on your frame while keeping the slight motion of him playing with his dick.
Never once did you think that Chargebolt would be a dominant. Or have a daddy kink. Nor did you think he would ever call you cumming in less than thirty seconds hot. Yet here he was with a straining erection, his plush tip glistening with pre, demanding you call him Daddy. Honestly, you had never been more aroused either. "Ch-char… holy fuck." Your own words stammered and stuck in your throat. The blond chuckling warmly as you seemed awestruck.
"Don't be like that, Sugarcube. Your mouth has better uses. Clean yourself up. Scoop all that cum into your cute little mouth. Show Daddy how badly you want his cum." Instructions you quickly followed. Two fingers sliding through the mess on your belly and bringing it to your waiting mouth. Lewdly moaning to make sure your dream man had the best show in the world. You wanted him to never end this, and if happily eating your own cum was what he wanted… it was what he would get. Your tongue pushing apart your fingers to clean between them before you repeated the action. Another scoop of your own cum dancing on your tongue. Fuck, were you already getting hard again? You supposed that was the best part of cumming so quickly anytime you got into it, you were always ready to go again real soon. Apparently he noticed you growing hard too, because your next instructions followed not long after.
"Sugar cube, you're going to cum directly into your own mouth this time. Lay on your shoulders, and bend those pretty legs over to rest at your head. Use the wall to help support you if you need to. I just wanna watch you get all cute and cum drunk on your own cum. Can you do that for Daddy?” His instructions weren’t hard in theory. But actually maneuvering your body to make it work was actually kind of hard to do. But after a few minutes, and comments from the man about how juicy your ass looked, you managed to get the position perfect. Your tight asshole on display as well, but Chargebolt wasn’t looking for that yet. He wanted you to eat your own cum. Tentatively you began to stroke your length again, at least you would last longer than thirty seconds this time. You hoped so at least. It would be pretty fucking embarassing if you only lasted less than a minute again. You might as well just end the call, move away from Japan, change your name., and start a new life as a Norwegian sheep farmer or something if that happened. Premature ejaculation wasn’t cute, no one would want you if they knew you only lasted a few seconds. Your soft moans filled the air, and you felt something bubbling in your stomach. Only a few strokes in and already you were getting closer by the second.
“Cum for me, Sugarcube. Open your mouth and cum on that pretty tongue of yours for Daddy. I love how quickly you cum. I can already hear how needy you are. Just like last time, you get so pink when you need to cum. And look at all your precum dripping onto your pretty lips. Perfect lips for wrapping around Daddy’s cock. Cum for Daddy so he can cum too.” Honeyed words low and sultry. If you opened your eyes you would see his hand flying furiously over his length. The blond trying to cum at the same time you did. But he wouldn't get there before you did, already you were spilling down into your waiting mouth. Groaning at the slightly sweet taste blossoming over your tastebuds. Legs collapsing by your head, your body almost falling off the bed as you tried to right yourself again.
It was amazing the sight you saw. The blond man, basically a twink in his own right, completely debauched. Chest covered in his own spunk, a dazed look on his face, both thumbs sticking up as he blinked a few times as his only response to you asking if he was alright. Did he always overcharge when he came? Was this normal for him? Part of you wanted to try and contact someone to check on him, but the better part of you knew to just give him a few minutes to recover. Grabbing a tissue from your bedside table and cleaning your chest off slowly, keeping an eye on the man filling your laptop screen. Making sure he didn’t like, die or something. Could you die from cumming to hard? Was it possible for his quirk to completely fry his brain? But then you heard him say something other than whey. At least he wasn’t brain dead. That was good.
“Denki. S’my name. Use it… Kaminari Denki.” Words slightly slurred, but clearly understandable. He was giving you open permission to not only use his name… But his given name. Holy fuck. Of course you whispered back your own name. Letting him know he was free to use yours. The two of you had a good connection, and continued this on for a while longer.
BONUS
“So… Denks. Why the ever loving fuck did you choose Fenk8?” It was Kirishima that asked that while you all lounged on your couch. The entire squad knew how you and Danki got together, apparently he never shut up about you in the beginning. Always mentioning the really cool baker guy that made the best sweets. It was actually Bakugou that stole Denki’s phone and made the request for the video call that night. Tired of hearing the electric blond complaining over how awesome you were.“Heh… Funny story. It was supposed to be Denk8, but I misspelt it while signing up and didn’t notice. Cn’t change your username, even if you’re a pro apparently. If you said it out loud it was supposed to sound like my name. The 8 was for my di-” Cut off by a pillow thrown at him by Hanta while Mina died laughing. You even couldn’t help the laughter as you heard what was shouted through the pillow over his mouth. “-CK PIERCINGS! BECAUSE I HAVE ONE FOR EACH INCH OF MY COCK!”
#denki#kaminari#denki kaminari#kaminari denki#chargebolt#reader#male reader#fanfic#kaminari x reader#denki x reader#chargebolt x reader#yaoi#listen this is a whole mess#bnha harem server#server collab#bnha server collab#dumbasses in love#denki is pretty chaotic
416 notes
·
View notes
Text
Handcrafted Jewelry Business Savvy - The All Important Mailing List
On the opposite hand, a person have come into my office and can communicate quickly and concisely in fewer than 20 minutes what your solution is and you have a cost point that will meet my budget while solving all of my pain points, I'm going to it help desk services seriously consider working along with you. Do anything to sense that you are running your small business instead laptop or computer running you have? Managed services might help you to obtain a handle on one more piece of your business and put it managed and leadership. Another harness this information mill that you'll have a pool of skilled users in. Just get an individual forum running, and that'll relieve you from most on the support work. The users may able aid each other here. Many established companies have a reputable and well kept user-forum that gives support process. However keep tabs on the forum, to avoid getting back-bitten, though that wont take up much time on daily basis . Phone & chat support can be avoided proper here. Users would in order to have a cost effective email based ticketing systems like Cerebrus HelpDesk or kayako. IT service management normally centred from the customer's perspective of the contribution than me services to individuals or an online business. This management attempts to focus less on the technological a part of the service but more on how they relate thus to their customers and help each of them. The management will usually be concerned about what referred to as back office or operational concerns. The actual software or hardware isn't focused on but rather the staff and users are the important focus. To operate a weblog you'll need company providing MySQL database. All usernames, passwords, blog posts and other data are stored certainly there. Another important feature which require to require from the hosting service should be PHP uphold. Most of the weblogs are written in PHP. You will also need to watch out for the volume disk space and data transfer useage. If you will only write texts you will not need greater than few mb. However, if you plan create photos or videos for a articles you can utilize a web service makes it possible for at least a few gigabytes of web space and transfer of data. A health savings account is abbreviated as HSA. High deductible health insurance policy can be combined training can actually be. The money deposited by you in the HSA earns an interest to Network Load Balancing Windows 2012 which is tax able. The money saved there can be familiar with pay varied health-related costs like buying medicines. While the skills of a task manager will need infrequently, outsourced it solutions the growing system quickly prove their genuinely worth. A good project manager help save you you serious amounts of money. His job is always to coordinate and hang all the pieces simultaneously. Well, this but another rant coming. It is inspired from a post at a forum from a who paid for a service at that forum and didn't receive what he compensated. His question was, "What do I do?" It amazes me the number people today in this world who just can't think for their. Well, I'm sure you're not one associated with these but I'm still going to more than some forum basics here that you might want to tuck away for future use. Your customers are probably "overweight," too. Invariably how to market your product or service, but still your treatments isn't looking too good. Your business for you to be go on a diet and lose extra load. The runner could lose weight by lopping of each of his legs, but which is often used be counterproductive. You could fire half of the sales staff, but which is often used be like chopping off your leg because does one use have the largest amount people selling your own products. Just because you're small it doesn't imply you to be able to think like one. More often than not you always be competing with businesses far larger than yours, nevertheless, you don't have to show Network Load Balancing Windows 2012. Differentiate yourself with greater expertise and speed of performance. Deck restoration starts with knowing what you need to use your deck for many. Your back deck is a great method to hear the birds after a tough day at the job. Not only is it calm, but may also be helpful in numerous unique ways. One being the idea of having the capability entertain your pals outside in a cushty environment. They usually supplies you with a help desk that always be available each day a day, 365 days a time of year. Their service should have passed test of as well as their server should the uptime of 99% but more. These last two options will filter out quite a number of wannabe hosting companies. All good organizations that offer web hosting Network Load Balancing Windows 2012 generally provide an online site building software that helps beginners to design their own websites. Is actually an yet cruising that end up being offered by them and that is exactly domain level of comfort. With the few services out there that truly are decent, you'll need to deposit a large sum money. Typically, the starting amount is in the $25,000. it help desk services is advisable to pay close attention to fees. Using managed Forex accounts rrs extremely expensive. When they do cash for you, they will normally take about 30% of the profits.
1 note
·
View note
Text
i've always been enamored of blogs that can turn deeply boring and technical topics into entertaining writing; i only really absorb humor or facts when i'm not expecting them. if i was trying to write a personal blog 10 years ago, i'd probably be attempting to copy "joel on software," e.g. its sample functional software specification:
Mike is a busy executive. He is the president of a large, important company that makes dynamite-based products for children which are sold through national chains such as Toys ‘R’ Us. During the course of a typical day, he has many meetings with many very important people. Sometimes a man comes over from the bank to harass him for not paying the interest that was due three months ago on his line of credit. Sometimes another man comes from another bank trying to get him to sign up for another line of credit. Sometimes his venture capitalists (the nice people who gave Mike the money to start his business) visit him to complain that he is earning too much money. “A bonfire!” they demand. “Wall Street likes to see a bonfire!”
These visitors are very upset if Mike has previously promised to meet with them at a certain time, but when that time comes around, Mike is nowhere to be found. This happens because Mike doesn’t know what time it is. At his secretary’s recommendation, Mike signs up for a WhatTimeIsIt.com account. Now, whenever Mike is wondering about the time, he simply logs onto WhatTimeIsIt.com, enters his username and password, and finds out the current time. He visits the site several times during the day: to find out when it’s time for lunch, to check if he’s late for the next meeting, etc. Towards the end of the day, in fact, from about 3:00 p.m. onwards, he checks the site increasingly frequently to see when it’s time to go home. By 4:45 he’s basically just hitting “Refresh” again and again.
something about that knowing, cynical style of humor has gone out of fashion since 2000 (even though venture capital mostly hasn't changed.) when i actually started trying to write blog posts for a hypothetical personal professional website, i was honestly trying to be a slightly more nonfictional @seat-safety-switch (excerpted below for reference):
All around you, corporations are snapping up the corpses of expired corporations and wearing their brands like a mask. And the rate of this happening is accelerating. Acquisition firms form, acquire, and collapse faster than ever before. By 2035, every person on Earth will need to run at least four brands and act as two Marvel superheroes, NASA is projecting.
For instance, I was the CEO of Ford two times last week, and they’re blowing up my voicemail again to get me to come in on Sunday. You would think that being the CEO would be a cool job, but it just isn’t. These accelerated corporate-collapse cycles mean that I don’t get to allocate massive R&D funding to a V-16 school bus conversion. All I do is get in, make my morning coffee, and then dash off an all-hands email telling everyone they’re fired. I have to do it from my Hotmail account, because IT can’t even set up an Exchange server that fast.
but since then i've started reading matt levine's newsletter money stuff, which is actually nonfictional:
Right now, if you go around saying “I am going to do a financial business, but I will make a point of not considering environmental, social or governance factors,” or even “I will consider ESG factors, but only to do the opposite of what those ‘woke’ ESG funds do,” people will fling money at you. You can walk into Peter Thiel’s office wearing a clown suit and say “high-frequency trading, but anti-woke,” or “payday lending, but anti-woke,” or “variable annuities, but anti-woke,” or “capped/uncapped variance swaps, but anti-woke,” or whatever, and he will write you a big check...
One subtle advantage of this business model is that a way to signal that you are authentically anti-ESG is by having bad governance, since “governance” is right there in the name of the thing you (and your investors) are against. This can work to your advantage: Bad governance tends to be bad for investors but good for entrepreneurs. (Ask Adam Neumann!) You raise a bunch of money and then spend it on yachts for yourself, and your investors say things like “well the governance of this company is pretty bad isn’t it,” and you say “exactly!” Bad governance is what they signed up for!
and now everything i've previously written seems like it's in the wrong voice slightly and looking to the future i don't know how i'm supposed to keep this thing together.
(this might be how things work for a lot of people who read a lot but haven't written much - i remember neil gaiman talking about how his very first book was just a pastiche of all of his favorite authors at the time and he's glad it never got published, plus joel of joel on software says he credits his success to college classes that made him practice writing a lot - but i happen to want to write with a consistent and coherent authorial voice without having to spend a ton of time developing it, thank you very much.)
0 notes
Text
Should you be worried about your passwords getting hacked?

Most IT security specialists define passwords as "the keys to our Digital Home": that's a pretty good metaphore, especially considering that our "digital home" is getting bigger as the time passes (and the technology advances). In the latest few decades we learned how to protect our precious devices (computers and, most recently, mobile devices) to prevent unauthorized access to them and their data... But, with the advent of the Internet and Internet of Things, the house became an infinite amount of different rooms: from online banking to food delivery services, from cloud-based repositories to remotely accessible Virtual Private Networks, we were literaly stormed by those "keys". At the same time, since technology runs faster than our ability to assimilate it, most internet users - as well as business companies - still use passwords in a totally insecure way today: to continue with our initial metaphore, nobody would leave the key on the door, or feel comfortable using the same key to open multiple doors, or use a weak lock & key combination, right? However, when using passwords, most of us often do just that. In the initial part of this post we'll try to summarize the most common mistakes that people do in choosing a password; then we'll briefly review the most common ways used by hackers to stole passwords; last but not least, we'll share some suggestions and best practices to secure our passwords and improve our account's security.
Common Password Mistakes
The typical password mistakes can be split into three main categories: choosing a weak password, using the same password among different web sites, and insecurely storing passwords. In the following sections we'll deal with each one of them. Choosing a weak Password A weak password, as the name implies, is a password too easy to guess or to discover using automated hacking techniques (brute-force, rainbow tables, and so on). Those who thinks that this is issue is a thing of the past because nowadays the majority of IT users have been educated enough to avoid choosing trivial passwords should check the SplashData's Most Used (and Worst) Password of 2017 infographics, which could easily change their mind. Here a list of the top 10: - 123456 (proudly keeping the first place since 2013) - password - 12345678 - qwerty - 12345 - 123456789 - letmein - 1234567 - football - iloveyou Luckily enough, such situation has been mitigated by enforcing a password security policy that is already adopted by most websites - and that is mandatory for all online services that deal with money or personal data, at least in most countries. Such policies not only require a minimum length and the presence of different character types (uppercase and lowercase letters, numbers, special characters) to make them harder to guess, but also force the users to periodically change them (often every 90 or 180 days). However, choosing a weak password is still critical for those devices where such policies are not enforced yet - such as most IoT devices. Using the same Password In addition to using passwords objectively too weak, users (and company officers) often also make the mistake of using the same password for different web sites or services. The so-called "password reuse" is probably the most serious mistake we can make nowadays: if a hacker manages to hack into a website's servers (this is happened for Yahoo, LinkedIn, Sony, and countless "minor" websites) and steal the users passwords, it will definitely try to use those retrieved passwords to gain access to other services. The only thing we can do to stop such common hacking practice is to ensure that each and every account that we have has its own password. A great example of such bad practice was given during the LinkedIn data breach (2012), through which Mark Zuckerberg's LinkedIn, Twitter and Pinterest accounts were all hacked because he used the same password for all of them. Such verification process can be automated using dedicated tools, such as Shard - a open-source command line tool that was developed to allow users to test whether a password they use for a site is used to access some of the more popular services, including Facebook. LinkedIn, Reddit, Twitter or Instagram. Insecurely storing Passwords The need to use strong passwords and a different password for each website or service inevitably brings another big requirement: the need to have a "secure" mechanism for storing these passwords, since human memory won't definitely be able to keep up. And this is where the most serious security problems often occur, not only for home users yet also for most companies. Who among us has never seen those dreadful MS Excel files (or text files!) containing a huge list of passwords? And the worst thing is that those unsecure repositories are often shared among different users (family members, co-workers, and so on), meaning that they aren't protected even with the basic user authentication mechanism provided by the OS.
How passwords are hacked
The techniques used by hackers for discovering our passwords are more than one, sometimes really trivial: as we can easily see by looking at the list below, most of them leverage or exploit the bad practices that we've talked about early on. - Social Engineering: e.g. Phishing, Password Sniffing. In practice, it is we who allow ourselves to be deceived by social engineering techniques and give passwords to those who ask for them through for example messages, emails, fake sites that disguise a well-known site. - Guessing passwords: Using personal information such as name, date of birth or pet names. When this happens, sometimes the "hacker" happens to be kind of close to the "victim": a friend, neighbor, co-worker or someone that knows enough info to perform such guesses. However, thanks to the modern approach to social networks, everyone might easily know a lot of stuff about anyone else. - Brute Force Attack: Automatically testing a large number of passwords until the right one is found. There are special programs to do this (a widely used one, John the Ripper, is open source, meaning that anyone can use it). Brute-force attacks are quite expensive to pull off, which requires time and computing power, but can easily achieve the result if the password is weak enough. - Intercepting a password, for example while it is being transmitted over a network. The bad habit of communicating passwords via email is frequent: there are even sites that, as soon as we register, send us a polite welcome message containing username and password displayed "in clear". Too bad that email is not a safe tool. - Shoulder surfing: a social engineering variant. It basically means "observing someone from behind" (i.e. "shoulder") while typing the password. - Using a KeyLogger. Keyloggers are malware programs that record everything typed on the keyboard, then transmit this data to the hacker who installed the keylogger. There are also hardware-based keyloggers that require direct access to the victim's computer. - Passwords stored in an insecure way, like handwritten on a piece of paper, or saved on a word file (see above). - By compromising a database containing a large number of user passwords, then using this information to attack other systems where users have reused the same passwords ("credential stuffing"). How to secure our Password Securing our passwords in order to avoid most - if not all - of the hacking attemps listed above is not impossible and is a goal that can be achieved by anyone. In a nushell, all we need to do is to apply two best practices: - Write strong and unique Password - Securely store your Passwords Both of them are equally important and must be followed for each and every password, without exceptions. How to write a strong Password A strong password is characterized by the following elements: length and character types used. - Regarding the length, it is strongly recommended to use at least 12 characters. - As for the character types, just let the math guide you: we have 10 numeric types (0-9), 52 letter types (26 lowercase + 26 uppercase), and more or less 33 special character types easy to type because they're directly accessible from a typical keyboard (such as #, &, %, ?, ^, and so on). To summarize all that, in total we have 95 character types available: with that in mind, we can say that a good password should have at least one character coming from each one of these types, because by increasing the types of characters, the number of possible combinations grows exponentially, thus making harder (and time-consuming) to "brute-force" the resulting password. How to store your Passwords As we aready said early on, using a different password for each website or service means that we can't rely to our memory to remember them all: at the same time, using insecure data stores such as MS Excel files or text files is definitely not an option. The best way to tackle (and fix) this problem is to use a Password Manager tool: a dedicated software that acts as a vault where you can securely store all your passwords, as well as your usernames and/or credential info, with the big advantage of having them in a single place. This basically means that you'll only need to remember the password required to access it, which is often very strong and can be further protected by other authentication factors (fingerprint, SMS, OTP, mobile tokens, and so on). The most advanced Password Managers also provide a good level of integration with the Operating System and browsers, meaning that they can even “automatically” (yet securely) fill in your credentials whenever you log in to a site (or an app) using your desktop or mobile device. IMPORTANT: Password Manager apps shouldn't be confused in any way with the "password storage" features offered by most modern browsers, such as Google Chrome, Mozilla Firefox, and MS Edge, that prompts you to store your credentials and fill out the forms for you, unless they are part of a bigger product that grants the fundamental features that a good Password Manager needs to have: centralized and distribuited repository, access from multiple devices, data encryption of the whole vault, 2-factor authentication support, and so on.
Conclusion
That's it, at least for now: we hope that this post will help most users and companies to increase their online security by securely choosing and storing their password. Read the full article
1 note
·
View note
Text
Genius Ventures Project.
Genius Tokens Cryptotoken A.I. Processing

More than a CryptoToken. Genius tokens are at the heart of a unique blockchain and software system.
#Genius #GNUS #Geniusventures #ICO #cryptotoken
Introduction:
Every day, more advanced technologies emerge across the business landscape. They bring innovation and disruption that continue to drive growth. Over the past few years, cloud service providers have helped businesses transform their extensive processes. Cloud solutions are a powerful industry that is rapidly maturing and becoming mainstream. But over time technology advances and developers need better tools and methods to handle the additional processing required for high volume data processing, which has increased the need for advanced computing and performance. Although cloud computing resources can support global applications, the centralized architecture introduces scalability problems.
Distributed computing solves the problem of scalability by spreading the demand for compute processes across multiple high-powered machines. To solve this problem, Genius Ventures is here.

What is Genius Ventures?

The Genius Ventures system infrastructure functions as a distributed multipurpose service with a cryptographic payment system that allocates computing resources and integrates them into real-world projects.
Genius Ventures leverages the unused Computing Device cycle on computers, mobile devices and IoT devices, the system processes Artificial Intelligence and Machine Learning data on end-user devices. End users are then paid in Genius Crytpotokens which can be reused for In-App purchases or converted back to another currency. In addition, the entire system is easily integrated into Computer and mobile games and applications.
Purpose of Genius Ventures:

Genius Ventures seeks to deploy a scalable, high-performance, secure and manageable infrastructure side chain that promotes a new form of distributed management, encompassing key leaders in the compute, big data, and cloud industries.
Genius Ventures aims to provide systems and methods for distributed general purpose computing with crypto token payment systems. This payment system integrates a slow blockchain crypto token with a fast DAG based crypto token. This technology is based on Ethereum’s “Genius Token” smart contract and enables the creation of a virtual cloud infrastructure that provides high-performance computing services on demand.
What are the features offered by Genius:

Works anywhere: Code and SDK (Software Development Kit) works on all devices, including Windows, OSX, iOS, Android, Linux, Windows Mobile, XBOX, Playstation, Nintendo, and IoT Devices
Customizable: AI or Machine learning algorithm can be selected by customer via customer portal and data can be uploaded or on customer secure server
Fast: The hybrid Cryptotoken system uses a fast internal Directed Acyclic Graph (DAG) based blockchain that executes transactions in microseconds.
Always available: stand-alone applications, embedded systems, or games with integrated SDKs can perform processing.
Organic: Growth is organic in two ways. User Acquisition Fees are almost zero and Users are paid to process the data, thus attracting them to use your game or app more often.
Mobile-first: Development SDKs (Software Development Kits) are targeted at Mobile devices first and use computing devices on any system.

How Does Genius Ventures Work?

Transaction: Customer requests data processing for Artificial Intelligence or Machine Learning and pays to an account that converts currency into Genius Tokens. The customer then uploads or references the data for processing.
Data Transfer: The data to be processed is uploaded to an encrypted area in a distributed file system. As part of the transaction, a storage fee is charged to the deposit. If the customer has storage for their own data then the system data via SSL secure transactions with the customer’s SSL public key
AI Processing: Using a distributed network system, transactions are communicated to participants who install games and or applications that can process AI Data. Workloads are divided and distributed to individual nodes for processing either in standalone applications or while running games.
Validate and Add: After processing, all nodes report back results to a fast blockchain which aggregates the result data and verifies that the nodes are not cheating the system. Data is verified by node parity verification and encryption verification. The data is then stored in a distributed file system or returned to the customer data storage area.
Complete: Once the data is validated, the completed transaction is sent to the main blockchain. Blockchain moves payments in Genius tokens from an escrow that is ready to be distributed to each node that processes data
Payment: After the process is complete, the blockchain contract then distributes 70% of Genius tokens to all wallets of each node. App or game publishers will then receive 20% with Genius Ventures receiving 10%. Users can convert tokens to regular currency or use them for in-app purchases.
What is Token Genius (GNUS)?

The Genius Token is at the Heart of the Genius Ecosystem. Genius Token (GNUS) is an Ethereum-based cryptocurrency
To use the AI/ML services offered by Genius Ventures, you need to make a payment via GNUS token. Payments for services are converted into Genius Tokens. These tokens during the data processing below are distributed as follows:
70% of GNUS will be distributed to people who play the game and give their computing power to help data processing.
20% will be given to the publisher who launched the game or application that was played during data processing.
Genius Ventures receives the last 10%.
Players who earn Genius Tokens can convert them to other cryptocurrencies or use them to make in-app purchases.
Token Sale:


GNUS is not listed on major exchanges at the moment, but you can earn tokens on Uniswap
Roadmap:
📷
Conclusion:
📷
Genius features games and apps that can process AI data using blockchain. Each person who installs a game or application is an individual node, which provides computing power to support AI/ML technology. In other words, your data will be processed by AI/ML, supported by thousands of people having fun while playing games. They are developing a strong economy in the field of data processing using AI/ML which will provide income opportunities for ordinary users by leveraging their Mobile, PC, Play Station and IoT devices.
The Leadership Team
The ICO Crypto Team combines a passion for esports, industry expertise & a proven record in finance, development, marketing & licensing.
Kenneth Hurley: CEO
Brent Arias: CTO
Denis Trofimov: Director of Software Development
For more information please follow the link below:
Website: https://www.gnus.ai/
Whitepaper: https://www.gnus.ai/wp-content/uploads/2021/08/Genius-Tokens-Whitepaper-1.0_Final.pdf
Telegram: https://t.me/geniustokenschat
Twitter: https://twitter.com/VenturesGenius
Facebook: https://www.facebook.com/geniusventures.io/
Linkedin: https://www.linkedin.com/company/geniusventuresio
Author:
Bitcointalk Username: herlambang18
Bitcointalk Profile: https://bitcointalk.org/index.php?action=profile;u=2609871
Telegram Username: @herlambang18
ETH Address:0x0a9977835a0902DD302B8DFE2aCe96EB6E135751
0 notes
Text
Genius Ventures Project.
Genius Tokens Cryptotoken A.I. Processing

More than a CryptoToken. Genius tokens are at the heart of a unique blockchain and software system.
#Genius #GNUS #Geniusventures #ICO #cryptotoken
Introduction:
Every day, more advanced technologies emerge across the business landscape. They bring innovation and disruption that continue to drive growth. Over the past few years, cloud service providers have helped businesses transform their extensive processes. Cloud solutions are a powerful industry that is rapidly maturing and becoming mainstream. But over time technology advances and developers need better tools and methods to handle the additional processing required for high volume data processing, which has increased the need for advanced computing and performance. Although cloud computing resources can support global applications, the centralized architecture introduces scalability problems.
Distributed computing solves the problem of scalability by spreading the demand for compute processes across multiple high-powered machines. To solve this problem, Genius Ventures is here.

What is Genius Ventures?

The Genius Ventures system infrastructure functions as a distributed multipurpose service with a cryptographic payment system that allocates computing resources and integrates them into real-world projects.
Genius Ventures leverages the unused Computing Device cycle on computers, mobile devices and IoT devices, the system processes Artificial Intelligence and Machine Learning data on end-user devices. End users are then paid in Genius Crytpotokens which can be reused for In-App purchases or converted back to another currency. In addition, the entire system is easily integrated into Computer and mobile games and applications.
Purpose of Genius Ventures:

Genius Ventures seeks to deploy a scalable, high-performance, secure and manageable infrastructure side chain that promotes a new form of distributed management, encompassing key leaders in the compute, big data, and cloud industries.
Genius Ventures aims to provide systems and methods for distributed general purpose computing with crypto token payment systems. This payment system integrates a slow blockchain crypto token with a fast DAG based crypto token. This technology is based on Ethereum’s “Genius Token” smart contract and enables the creation of a virtual cloud infrastructure that provides high-performance computing services on demand.
What are the features offered by Genius:

Works anywhere: Code and SDK (Software Development Kit) works on all devices, including Windows, OSX, iOS, Android, Linux, Windows Mobile, XBOX, Playstation, Nintendo, and IoT Devices
Customizable: AI or Machine learning algorithm can be selected by customer via customer portal and data can be uploaded or on customer secure server
Fast: The hybrid Cryptotoken system uses a fast internal Directed Acyclic Graph (DAG) based blockchain that executes transactions in microseconds.
Always available: stand-alone applications, embedded systems, or games with integrated SDKs can perform processing.
Organic: Growth is organic in two ways. User Acquisition Fees are almost zero and Users are paid to process the data, thus attracting them to use your game or app more often.
Mobile-first: Development SDKs (Software Development Kits) are targeted at Mobile devices first and use computing devices on any system.

How Does Genius Ventures Work?

Transaction: Customer requests data processing for Artificial Intelligence or Machine Learning and pays to an account that converts currency into Genius Tokens. The customer then uploads or references the data for processing.
Data Transfer: The data to be processed is uploaded to an encrypted area in a distributed file system. As part of the transaction, a storage fee is charged to the deposit. If the customer has storage for their own data then the system data via SSL secure transactions with the customer’s SSL public key
AI Processing: Using a distributed network system, transactions are communicated to participants who install games and or applications that can process AI Data. Workloads are divided and distributed to individual nodes for processing either in standalone applications or while running games.
Validate and Add: After processing, all nodes report back results to a fast blockchain which aggregates the result data and verifies that the nodes are not cheating the system. Data is verified by node parity verification and encryption verification. The data is then stored in a distributed file system or returned to the customer data storage area.
Complete: Once the data is validated, the completed transaction is sent to the main blockchain. Blockchain moves payments in Genius tokens from an escrow that is ready to be distributed to each node that processes data
Payment: After the process is complete, the blockchain contract then distributes 70% of Genius tokens to all wallets of each node. App or game publishers will then receive 20% with Genius Ventures receiving 10%. Users can convert tokens to regular currency or use them for in-app purchases.
What is Token Genius (GNUS)?

The Genius Token is at the Heart of the Genius Ecosystem. Genius Token (GNUS) is an Ethereum-based cryptocurrency
To use the AI/ML services offered by Genius Ventures, you need to make a payment via GNUS token. Payments for services are converted into Genius Tokens. These tokens during the data processing below are distributed as follows:
70% of GNUS will be distributed to people who play the game and give their computing power to help data processing.
20% will be given to the publisher who launched the game or application that was played during data processing.
Genius Ventures receives the last 10%.
Players who earn Genius Tokens can convert them to other cryptocurrencies or use them to make in-app purchases.
Token Sale:


GNUS is not listed on major exchanges at the moment, but you can earn tokens on Uniswap
Roadmap:

Conclusion:

Genius features games and apps that can process AI data using blockchain. Each person who installs a game or application is an individual node, which provides computing power to support AI/ML technology. In other words, your data will be processed by AI/ML, supported by thousands of people having fun while playing games. They are developing a strong economy in the field of data processing using AI/ML which will provide income opportunities for ordinary users by leveraging their Mobile, PC, Play Station and IoT devices.
The Leadership Team
The ICO Crypto Team combines a passion for esports, industry expertise & a proven record in finance, development, marketing & licensing.
Kenneth Hurley: CEO
Brent Arias: CTO
Denis Trofimov: Director of Software Development
For more information please follow the link below:
Website: https://www.gnus.ai/
Whitepaper: https://www.gnus.ai/wp-content/uploads/2021/08/Genius-Tokens-Whitepaper-1.0_Final.pdf
Telegram: https://t.me/geniustokenschat
Twitter: https://twitter.com/VenturesGenius
Facebook: https://www.facebook.com/geniusventures.io/
Linkedin: https://www.linkedin.com/company/geniusventuresio
Author:
Bitcointalk Username: bondan88
Bitcointalk Profile: https://bitcointalk.org/index.php?action=profile;u=2632383
Telegram Username: @bondan88
ETH Address:0x0D7fBAd549E0dd2BD7242A8060BB2441CF1f5A3A
0 notes
Text
Ssh File Transfer For Mac
Mac Transfer To New Mac
Ssh File Transfer For Mac Os
Ssh File Transfer Mac To Linux
Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Typical applications include remote command-line, login, and remote command execution, but any network service can be secured with SSH. SSH provides a secure channel over an unsecured network by using a client–server architecture, connecting an SSH client application. Mac Terminal SSH file transfer? Ask Question Asked 9 years, 1 month ago. Active 2 years, 8 months ago. Viewed 93k times 12. Is there a way to transfer files directly from a Mac to another using only Terminal? Perhaps using SSH? Mac ssh terminal. So far in this series of posts on ssh on macOS. Quick Introduction to ssh for Mac Admins; SSH Keys, Part 1: Host Verification; SSH Keys, Part 2: Client Verification; Transferring files with ssh (this post); SSH Tunnels (upcoming); Please consider supporting Scripting OS X by buying one of my books! In the previous posts we looked how to connect with ssh to a remote computer (host) and how to. WinSCP is a popular free SFTP and FTP client for Windows, a powerful file manager that will improve your productivity. It supports also Amazon S3, FTPS, SCP and WebDAV protocols. Power users can automate WinSCP using.NET assembly. It can act as a client for the SSH, Telnet, rlogin, and raw TCP computing protocols and as a serial console client. Version 0.63; WinSCP is a free open-source SFTP and FTP client for Windows. Its main function is to secure file transfer between a local and a remote computer. Beyond this, WinSCP offers scripting and basic file manager functionality.
Do you have a file on your Linux PC that needs to be transferred to your Linux server and you are not sure how to do this? This article teaches you how to copy files via SSH to your remote Linux server. It presents two methods for achieving this file transfer in a secure way. One based on the scp program and one based on the rsync program.
Background
Once you have your own Linux server up and running, you typically access it through SSH. SSH stands for Secure Socket Shell. SSH enables you to securely log in and access your Linux server over an unsecured network. Through SSH you can install, configure and update software on your Linux server, to name just a few common Linux server administration tasks.
While administering you Linux server, sooner or later you run into a situation where you have a file on your own Linux PC and you need to transfer this file to your Linux server. So you SSH-ed into your server and you are staring at your terminal screen, wondering how to go about this task. Unfortunately, you cannot directly transfer a file from your own PC to your remote Linux server through this active SSH terminal session. Luckily though, several methods exist that enable you to copy files via SSH. This article presents you with two of these methods. Namely, by using the scp and rsync programs.
System setup
A typical system setup consists of your Linux desktop PC, connected to your local network router, and a remote Linux server somewhere in the cloud. Instead of setting up a cloud server somewhere for this article (think Digital Ocean or Linode for example) , I decided on running a Linux server as a virtual machine (VM) on my laptop. Pes 2010 for mac os. Below you can find an illustration of the system setup:
My trusty Lenovo Thinkpad T450s serves as the Desktop PC. I run Debian 10 on this PC and its hostname is set to tinka. The Linux server VM also runs Debian 10 and its hostname is set to debianvm. I configured the same username on both the PC and the server. It is set to pragmalin. Refer to this article in case you would like to setup a similar Debian server as a virtual machine with VirtualBox.
Connecting to your server via SSH
While explaining the steps for copying files to the Debian server via SSH, I’ll occasionally SSH into the Debian server to verify that the files actually got transferred. Here follows a quick refresher that explains how you can log into your server via SSH.
The command from a Linux terminal on your PC to connect to your server is: ssh <username>@ip-address or ssh <username>@hostname. In my case the hostname of the Debian server VM is debianvm . My username on this server is set to pragmalin. This means that I can log into this server via SSH with the command:
ssh pragmalin@debianvm
To close the SSH connection, simply type the exit command:
SCP versus RSYNC
Before diving into the actual file copying via SSH, we should discuss the two commonly used programs for this, namely scp and rsync.
The SCP program
The scp program is a secure copy program. So basically a secure and remote version of the cp program that you locally use for copying files. Pretty much all Linux server distributions install the scp program by default, including Debian. Now, if the already installed scp program does all we need then why would we ever need another program for the same task? Read on and you’ll see that rsync does offer some benefits.
The RSYNC program
The rsync program is labeled as a fast, versatile and remote file-copying tool. But it is not just a plain file-copying tool. The rsync program features build-in synchronization functionality. This means that it only copies a file to the remote server if it is not already present. In contrast, the scp program blatantly overwrites the file. Furthermore, rsync can compress the files during the transfer. In other words, rsync is faster and uses less network bandwidth.
By default rsync does not communicate in a secure way. Luckily an easy fix exists for this. You can force rsync to use the SSH protocol by specifying the -e 'ssh' option when calling the program. Another minor disadvantage is that rsync is not installed by default on all Linux server distributions. Of course this is merely a one time inconvenience. You can simply install it with sudo apt install rsync. Just keep in mind that the rsync program needs to be installed on both sides. So both on your PC and your server.
When should you use scp and when rsync? They both work, so it partially comes down to personal preference. Personally, I use scp for small quick file transfers as its syntax strikes me as more intuitive. For large file transfers, I opt for rsync, because it is faster and uses less network bandwidth. For example when I need to restore a complete backup to one of my servers.

WordPress archive
For file copy via SSH testing purposes, this article uses the latest WordPress archive. WordPress is a hugely popular website content management system and runs on millions of websites, including the PragmaticLinux blog. We are not actually going to install WordPress, but just use the WordPress files for file copy example purposes.
Go ahead and download the latest WordPress archive from https://wordpress.org/latest.tar.gz. On my PC the file wordpress-5.4.2.tar.gz is now present in directory /home/pragmalin/Downloads/ Free mp3 to m4a converter for mac.
Copy a single file
Let’s start out with copying just a single file to the server via SSH. Open your terminal and go to the directory that holds to previously downloaded WordPress archive. Next, run either one of the following commands to copy the file to your remote server. Just replace the /home/pragmalin directory name with the name of your home directory on the server and replace the pragmalin@debianvm part with your username on the server and the hostname of the server, respectively:
scp wordpress-5.4.2.tar.gz pragmalin@debianvm:/home/pragmalin
rsync -e 'ssh' -avz wordpress-5.4.2.tar.gz pragmalin@debianvm:/home/pragmalin
If you now SSH into your server, you can verify the presence of the wordpress-5.4.2.tar.gz file in your user’s home directory. Both the scp and rsync commands have a similar structure. It is:
(COMMAND) (OPTIONAL ARGUMENTS) (SOURCE) (DESTINATION)
As you can see in this example, the scp program does not require any arguments. However, the rsync program does: -e 'ssh' -avz. For detailed information on the command options, you can refer to the program’s man-page. Alternatively, you can make use of the excellent explainshell.com website. Here are the links for an explanation of the previous two commands: scp and rsync.
Permissions
Note that you can only copy files to a directory where the username you specified has write permissions. That is the reason why I specified the home directory in this example. If you need to store the file in a directory where your user does not have write permissions, then you would have to connect to the server via SSH afterwards and move the file with the help of sudo mv.
Reverse transfer direction
You can copy the files via SSH in the other direction too. So from the server to your PC. You just need to swap the (SOURCE) and (DESTINATION) in the command. For example:
scp pragmalin@debianvm:/home/pragmalin/wordpress-5.4.2.tar.gz /home/pragmalin/Downloads
rsync -e 'ssh' -avz pragmalin@debianvm:/home/pragmalin/wordpress-5.4.2.tar.gz /home/pragmalin/Downloads
Copy all files in a directory
Another common operation is to copy all the files in a specific directory via SSH. We need a few files to try this out. Since we already downloaded the WordPress archive, we might all well extract its contents to get a bunch of files for testing purposes:
tar -xvf wordpress-5.4.2.tar.gz
The newly created wordpress subdirectory now holds the archive contents. To copy all the files in this directory to your remote server, run either one of the following commands. Just replace the /home/pragmalin directory name with the name of your home directory on the server and replace the pragmalin@debianvm part with your username on the server and the hostname of the server, respectively:
scp * pragmalin@debianvm:/home/pragmalin
rsync -e 'ssh' -avz --no-recursive * pragmalin@debianvm:/home/pragmalin
If you now SSH into your server, you can verify the presence of the files such as index.php, wp-config-sample.php, etc. in your user’s home directory.
Copy all files in a directory recursively
In the previous section just the files in a specific directory were copied. This did not include subdirectories. If you want to copy everything, so files and subdirectories, run either one of the following commands. Just replace the /home/pragmalin directory name with the name of your home directory on the server and replace the pragmalin@debianvm part with your username on the server and the hostname of the server, respectively:
scp -r * pragmalin@debianvm:/home/pragmalin
rsync -e 'ssh' -avz * pragmalin@debianvm:/home/pragmalin
The output of the command is a bit too long for a screenshot. However the following screenshot from the directory contents listing on the server show proof that the copy operation worked. You can verify the presence of the files such as index.php and wp-config-sample.php, but also all the directories such as wp-admin, wp-contents, etc. in your user’s home directory:
Wrap up
After working through this article, you now know about two programs (scp and rsync) that enable you to copy files via SSH. Both commands get the job done. The syntax of the rsync command is a bit more complicated so you might prefer scp. Keep in mind though that rsync uses less network bandwidth. As a result rsync is faster especially when transferring a large amount of data.
The syntax for both commands is not hard to understand. Nevertheless, it is complex enough that you probably won’t memorize them, unless used frequently. For this reason I recommend bookmarking this article. That way you can quickly reference this information when needed.
Connecting to every server. With an easy to use interface, connect to servers, enterprise file sharing and cloud storage. You can find connection profiles for popular hosting service providers.
Cryptomator. Client side encryption with Cryptomator interoperable vaults to secure your data on any server or cloud storage. Version 6
Filename Encryption File and directory names are encrypted, directory structures are obfuscated.
File Content Encryption Every file gets encrypted individually.
Secure and Trustworthy with Open Source No backdoors. No registration or account required.
Edit any file with your preferred editor. To edit files, a seamless integration with any external editor application makes it easy to change content quickly. Edit any text or binary file on the server in your preferred application.
Share files.
Web URL Quickly copy or open the corresponding HTTP URLs of a selected file in your web browser. Includes CDN and pre-signed URLs for S3.
Distribute your content in the cloud. Both Amazon CloudFront and Akamai content delivery networks (CDN) can be easily configured to distribute your files worldwide from edge locations. Connect to any server using FTP, SFTP or WebDAV and configure it as the origin of a new Amazon CloudFront CDN distribution.
Amazon CloudFront Manage custom origin, basic and streaming CloudFront distributions. Toggle deployment, define CNAMEs, distribution access logging and set the default index file.
First class bookmarking. Organize your bookmarks with drag and drop and quickly search using the filter field.
Mac Transfer To New Mac
Files Drag and drop bookmarks to the Finder.app and drop files onto bookmarks to upload.
Spotlight Spotlight Importer for bookmark files.
History History of visited servers with timestamp of last access.
Import Import Bookmarks from third-party applications.
Ssh File Transfer For Mac Os
Browse with ease. Browse and move your files quickly in the browser with caching enabled for the best performance. Works with any character encoding for the correct display of Umlaute, Japanese and Chinese.
Quick Look
Quickly preview files with Quick Look. Press the space key to preview files like in Finder.app without explicitly downloading.
Accessible

The outline view of the browser allows to browse large folder structures efficiently. Cut & paste or drag & drop files to organize.
Transfer anything. Limit the number of concurrent transfers and filter files using a regular expression. Resume both interrupted download and uploads. Recursively transfer directories.
Download and Upload
Drag and drop to and from the browser to download and upload.
Synchronization
Synchronize local with remote directories (and vice versa) and get a preview of affected files before any action is taken.
Integration with system technologies. A native citizen of Mac OS X and Windows. Notification center, Gatekeeper and Retina resolution.
Keychain
All passwords are stored in the system Keychain as Internet passwords available also to third party applications. Certificates are validated using the trust settings in the Keychain.
Bonjour
Auto discovery of FTP & WebDAV services on the local network.
Finder
Use Cyberduck as default system wide protocol handler for FTP and SFTP. Open .inetloc files and .duck bookmark files from the Finder.
Notifications
Notifications in system tray (Windows) and the Notification Center (Mac).
Windows
Reads your proxy configuration from network settings. Encrypts passwords limiting access to your account.
We are open. Licensed under the GPL.
Come in. You can follow the daily development activity, have a look at the roadmap and grab the source code on GitHub. We contribute to other open source projects including OpenStack Swift Client Java Bindings, Rococoa Objective-C Wrapper and SSHJ.

International. Speaks your language.
Ssh File Transfer Mac To Linux
English, čeština, Nederlands, Suomi, Français, Deutsch, Italiano, 日本語, 한국어, Norsk, Slovenčina, Español, Português (do Brasil), Português (Europeu), 中文 (简体), 正體中文 (繁體), Русский, Svenska, Dansk, Język Polski, Magyar, Bahasa Indonesia, Català, Cymraeg, ภาษาไทย, Türkçe, Ivrit, Latviešu Valoda, Ελληνικά, Cрпски, ქართული ენა, Slovenščina, українська мова, Română, Hrvatski & Български език.

0 notes
Text
Anydesk Personal Use

Not every use case requires a paid AnyDesk license. That’s why we provide a free version of our remote access software so people can help friends and work on personal projects.
Swap your AnyDesk number for a personalized username, formatted like an email address e.g. This brings your AnyDesk account in line with your brand identity and gives your customers a more consistent brand experience – especially when you add your logo to the interface too. Session Logging.
AnyDesk will have elevated privileges when installed. Connecting to a client with AnyDesk installed won't run into trouble controlling Admin (UAC) required applications. However you can request elevation remotely to clients that run AnyDesk portable.
AnyDesk was founded in Germany in 2014, and its unique remote desktop access software has been downloaded by more than 300 million users worldwide, adding another 5 million every month. Chrome Remote Desktop. 8 Pros 7 Cons 1 Top Pro. Impressively fast. Faster than most similar.
Looking for Free Remote Access Software?
There are many reasons you might want a free remote desktop option:
A family member needs tech support, but you are halfway around the world.
To take advantage of the high-performance tools on your desktop PC from a less powerful laptop.
You want to have your data with you at all times, no matter where you are.
Anydesk Free Personal Use
Sometimes you just need remote desktop software that is reliable and fast. Thankfully, the free version of AnyDesk comes with many helpful features and high security standards for your personal use. Find out for yourself what AnyDesk's free remote access software has to offer.
Remote Support for Your Loved Ones
If your family and friends need help with their computers, free remote desktop software is a true lifesaver. Gone are the days of tedious explanations over the phone and piles of screenshots to sort through.
Simply have them download the 3 MB file. There’s no installation or registration needed. You can access their device and provide remote support as if you’re sitting in front of their PC.
Flexibility for Your Personal Projects
You likely use multiple devices when working on personal projects. You might have high-performance graphic design software on your desktop PC but prefer to send emails from your laptop. Your phone is mainly for calls, messaging and social media. What if you could always have everything with you?
Thanks to our free remote access software, you can! Your phone can become a remote control for your other devices, you can access powerful software from a small tablet and your files are with you at all times with cross-platform, high-speed access.
Trusted Security Standards
Security is our priority. That means our security features aren’t limited to the paid licenses. All of them are also available for the free version. TLS 1.2 technology protects every connection from unauthorized access.
RSA 2048 key exchange further encrypts your remote desktop session. We also employ Perfect Forward Secrecy and Salted Password Hashing to prevent third parties from decrypting your data.
Additionally, we make an effort to inform our users about cybercriminals and how to avoid getting scammed.
Access the Best Tools for Free
We offer the best tools for personal use that ensure a smooth workflow. Even if you’re on the go, working on your personal projects from your laptop, it’s as if you’re right in front of your remote device.
Need to print out a document from your remote device? Use our Remote Printing feature. The AnyDesk printer sends a print job to your local printer. This ensures a more efficient and immersive experience. Or transfer the file to your local device using our File Manager or the copy-and-paste function.
Need More Functionality Than Our Free Version Offers?
Do you need a high-performance remote desktop tool for your company, because you need to manage many devices at once? AnyDesk offers licenses for every need—from freelancers to large enterprises.
Commercial Use
Address Book
REST-Interface
Customization Options
More Simultaneous Sessions and Active Devices
DeskRT is our proprietary video codec that ensures image transmission at low latency and high framerates, even at low bandwidths of only 100kB/s. Our innovative codec is at the core of AnyDesk and is also available for our free users.
AnyDesk doesn’t need to be installed. Simply download the small 3MB file and immediately get started without registration. Your AnyDesk-ID will be generated by simply opening the file. The perfect remote desktop software for less tech-savvy users.
We wanted to make sure everyone can use AnyDesk to its full extent, whether you’re a Linux or a Windows user, whether you prefer Android or iOS. Even cross-platform use is seamless. Find your platform and download AnyDesk for free.
The FAQ addresses common questions in terms of features, usage, as well as support related topics. All sections link to corresponding articles. For detailed documentation use the search bar or write a ticket to [email protected].
Do I need to install AnyDesk?
AnyDesk will have elevated privileges when installed. Connecting to a client with AnyDesk installed won't run into trouble controlling Admin (UAC) required applications.However you can request elevation remotely to clients that run AnyDesk portable. The login credentials can be entered remotely, the following UAC prompt must be confirmed manually from the remote side. Each installation has its unique ID and is bound to a specific license.
How to reset 2FA / Two Factor Authentication
Do I need to be present at the remote side to start a session? (Unattended Access)
No, you can set a 'password for unattended access' to gain access remotely. See Unattended Access
I lost my password (my.anydesk.com)
To recover your password go to MyAnyDesk.com and hit 'Forgot your password? ', this will send a reset mail to the address stored in your account.
Can I use AnyDesk with other Remote Tools simultaneously?
Yes, it's possible to run instances of different solutions and AnyDesk at the same time with no restraints. AnyDesk can also run several instances at the same time.
Can I use my own namespace?
Yes, you may choose your own namespace for registered clients in on my.anydesk.com if you're using a Professional or Enterprise licence. See MyAnyDesk_Portal
Register or remove the AnyDesk license to a device
See Registration to register the client to a license.
Are updates included with AnyDesk licenses?
Yes, updates are always included with AnyDesk.Expired contracts of AnyDesk Lite and AnyDesk Professional will limit AnyDesk to the latest version of AnyDesk Free, which is not allowed for commercial purposes.

Where do I find my invoices?
Your invoices can be found in the MyAnyDeskPortal.
Do my customers need a licensed version?
End users always get a free license of AnyDesk automatically.
How to make multiple connections?
AnyDesk can run an unlimited amount of sessions from a device as long as resources allow. AnyDesk also can run several instances on a device. Based on your license, your AnyDesk client can have multiple sessions simultaneously. The Free and Lite license will only allow one simultaneous session. The Professional license allows for as many sessions as ordered and Power license enables unlimited sessions for the number of active devices ordered.
Can I transfer files with AnyDesk?
How to connect automatically
The speed dial (background icons under the 'Connect'-button) displays recent connections. Click on the client you want to connect to. There is no need to type the ID each time. The entered password for unattended acces can be saved IF the option has been enabled at the remote client side below the 'set password' option. You can even create a shortcut on the home screen by clicking/touching the overflow menu (downward arrow) next to the machines address, then 'Drop to desktop'.
Can I offer AnyDesk for downloading on my website?
Yes, customers can offer AnyDesk for download on their website. The best way would be to
create a direct link to anydesk.com/download. In this way, your customers will always have access to the latest
version.
Can I keep or move the AnyDesk ID/alias when reinstalling or moving to a new/clone system or hard drive?
Yes, your identity can be moved. If you have several machines with the same ID: See AnyDesk_ID_and_Alias
Does AnyDesk support Windows server?
Which ports does AnyDesk use?
To connect to the AnyDesk network port 80, 443 or 6568 is used. For standard listening port direct line connection is 7070 (TCP).
AnyDesk is slow despite LAN connection
AnyDesk might not recognize a direct connection and the session will be established via AnyDesk network. Direct connections display a play symbol in the status bar. If disabled, end
the session and reconnect. In case the direct connection cannot be established, send the trace files fromboth LAN clients to [email protected].
Please note that installing AnyDesk generally helps to better recognize connections in a LAN.
Why is there an orange question mark next to my cursor?
If AnyDesk can't fetch a cursor from the remote device, e.g., if you're connecting to a Windows Server without a mouse cursor connected, AnyDesk will display this static cursor as default.
Can another user connect to me via Browser or my website?
Can I lock the remote screen?
Yes, AnyDesk allows to lock the remote screen if permissions are set. See Permissions
How to work with dual monitors / multiple displays?
Remote displays are indicated by separate tabs in the session window. Switch between the monitors by clicking on a corresponding tab. To get separate windows for each monitor, (available only if your license supports simultaneous sessions), establish two sessions with a remote device and set each to another display. To get multiple sessions in fullscreen mode, switch from D3D-Rendering to OpenGL or DirectDraw.
Anydesk Personal Use Limitation
Unexpected session ends, disconnects, session interrupts after a certain time
Sessions may end unexpectedly for various reasons. If you encounter interruptions after a specific amount of time into the session, go to Settings and switch to the Connections tab. Disable direct connections.You may also setup a listening port in your firewall for AnyDesk in the Security Settings.
Anydesk Personal Use Limitations
Why do I have to type the unattended password/login information/authorization manually for a specific client?
The remote client must allow the option to save his login information. See Unattended Access
I cannot connect, because the request was 'blocked/rejected by the AnyDesk settings'.
If a client has an ACL-List (Whitelist) active that your ID/alias doesn't match, or if your interative access settings are set to disabled or don't allow connections in the background, then you'll get a message, telling that your request has been rejected. See Security Settings and adjust the settings on the remote client.
I cannot use AnyDesk for controlling Security/AntiVirus Software
Some applications are protected from external modification. Disable this feature locally in the settings, in order to get access from remote.
Can't get a session window, AnyDesk says: Waiting for Image
On Android: Make sure to give AnyDesk permission to record the screen. The first session request spawns the permission window. If not properly addressed, open Android settings - Apps - Choose AnyDesk - grant permissions.
If this doesn't fix the issue, a headless display adapter will help, this will force your system to render the image.
Synchronization of the clipboard is not working
Check permissions. AnyDesk might have to be installed on the remote side.
Denied mouse cursor/no input on window
Permissions missing: Is displayed when AnyDesk does not have permission to control a selected application. In this case, install
AnyDesk or launch it as an administrator on the remote client. Professional license users
can create a custom client that automatically requests administrator privileges upon startup. See also Customize AnyDesk and Administrator_Privileges_and_Elevation_(UAC)
AnyDesk shows 0 as ID
This means you can´t connect to our servers, please check if you have whitelisted AnyDesk in your firewall: Firewall
Transmission is too slow. What can I do?
Latency and rendering performance depend on hardware and driver. See Render Performance for more information.
Compatibility in Windows Vista Home Edition
In certain cases, AnyDesk may sometimes crash or experience startup problems in the Home Edition of Windows
Vista. If this happens, open the properties of the AnyDesk shortcut and select 'Compatibility mode for Windows
XP'.
Scrolling on Android
For connections from Android to Android, there are several options. Use Direct-Touch Mode for 1-finger scrolling(default for new connections) and 3-finger scrolling when in Touchpad or Touch(Mouse) Mode. See AnyDesk on Android
Keyboard input opens up automatically on Android
Per default, focused text input fields will open the soft keyboard on Android. This can be switched off in the settings. See »» settings » input » automatic keyboard.The soft keyboard can be opened manually via the pie menu. See Android App
How can I close sessions from other devices to free sessions?
Go to the Portal and close the session in the 'Session' section. See MyAnyDesk Portal
How To Use Anydesk Without Permission
I can't control the mouse and keyboard anymore on macOS
With macOS Mojave/Catalina, it is required to allow AnyDesk explicitly to control your device, you'll be prompted to do so automatically when running AnyDesk, it is however rather easy to miss this.
If this happened to you, please go to 'System Preferences', 'Security&Privacy', 'Privacy', 'Accessibility' and add 'Anydesk' to your list of trusted apps. More information can be found in AnyDesk on macOS.
I get the message 'Waiting for Image' or 'desk_rt_ipc_error' on macOS
With macOS Catalina, it is required to allow AnyDesk to record your screen.
AnyDesk shows a message, to configure your system in the 'System Preferences' to add AnyDesk to the trusted apps list in 'Accessibility' and 'Screen Recording'. More information can be found in AnyDesk on macOS.

0 notes
Link
Mobile Legends Bang Bang Hack and Cheats Online Generator for Android, iOS and Facebook You Are Able To Buy Here Endless Free Diamonds, Battle Points, Tickets, Dual XP and Starlight Membership With No Survey No Individual Verification No Password No Download
Click Here: http://gamebag.website/top/mobile-legends-bang-bang-hack/
Our launch for today is Mobile Legends Bang Bang Hack! If you enjoy playing League of Legends and might love to take-the-game with you and play it on the go, Mobile Legends, while not very LOL is the nearest thing you'll get in regard to cellular free to play LOL such as MOBA game.
Although it is a fact there are a few wonderful multiplayer online-battle stadium games available to download for free for Google's Android As well as Apple's iOS like Vainglory, for example, this one gets the most in common with the League of Legends.
For starters, the map is pretty much that of a League of Legends and so is your art style. In addition, this game even has the word"Legends" in its own title. We-wouldn't go as far as to say this is a ripoff since we honestly believe it's not, however, is just as clear as a day what was the inspiration for Mobile Legends.
5 thousand individual downloads on the Google Play Store alone is a testimony to how popular this sport is just on a single system. And of course how many people play it on their iPhones and iPads...
How do you get together with Mobile Legends Bang Bang cheats?
Due to its popularity which seems to be increasing by the day, we-have chose to give you exactly what you'd have likely asked for yourself soon enough. So, we-went on ahead of your petition and made this Mobile Legends Bang Bang Hack. But this one is capable of hacking over simply Diamonds. You-can also hack free Fight Factors and Tickets with our generator and also give yourself Starlight Membership or add a hefty number of dual XP items.
Hack free Battle Points!
Battle points are incredibly practical if-you want to purchase and eternally unlock new personalities for your roster. While this-can be attained with diamonds as well, battle points are exclusive to hero purchases (and a couple of chests in a shop). This way you can utilize your diamonds something which can't be purchased otherwise.
Hack free Diamonds!
Undoubtedly, this is what the majority of you will-be most curious about. Diamonds are Mobile Legends premium money. You can get-them by playing the game but it will take you a great deal of time to get sufficient for your needs. They can be purchased with real money as well or hacked using Mobile Legends Diamonds Hack.
Hack free Tickets!
Tickets are utilized to purchase limited time offers and specific heroes out there for a limited amount of-time. While the majority of these purchases could be produced with both battle diamonds and points as well, utilizing a trade specific currency is always the best option. This way you get to store your diamonds for what actually matters.
Hack free XP Boost!
We wanted to encourage the players to utilize their experience boosters so we made it available to hack on these separately. These are especially useful if you would like to speed up at double the normal speed. They-are obviously available for purchase during the in-game shop but we went on forward and left it so you can put them into our Mobile Legends: Bang Bang cheat instrument.
Hack complimentary Starlight membership!
It-is also potential to allow free starlight membership for your accounts! This includes all of the benefits of a starlight membership and will last for an entire month (31 days to become specific). Once it runs out, you could always return and re-enable it for one more month. We-will also attempt to make it function for an whole year once we've got some spare time.
All of these benefits listed above are available for you. They come free of charge and totally no-restrictions. It doesn't matter where you're from and what device you are using to play the game on (at least no errors were reported).
You will freely share this hack tool with whoever you want. Share with your buddies to help them get more characters and attain higher degrees and you'll also profit from this by constantly having someone leveled up to perform with. Additionally, diamonds are fantastic for buying skins and you may as well look good while you're dominating the battlefield.
How to use Mobile Legends Bang Bang Hack Tool?
Don't be worried if you're not an expert and you have not ever hacked another game earlier. This process is incredibly simple and everyone can do-this. We will lead you throughout each step of the game and help you succeed. Only read through this short manual and you'll be just fine. Also, you can watch this tutorial movie below:
The very first thing that you need to do is to scroll to the bottom of the page where there's no more text. Right there you will see that a button. This button will be of green colour and it will get the words"Online Hack" stamped on it. Once you press this button you'll be taken to a different site where the Mobile Legends Bang Bang hack is situated.
On that page, you will find a form that may need some simple information before it can process your request. It will have to learn your username and what device you are playing on. It does not require a particular version, just a system that the device is running so, pick either Android or iOS and verify your choice.
As soon as you've connected to the game server , all you'll want to do would be to specify the exact amount of conflict points, diamonds, tickets and expertise boosters you need to enhance your account. Also, do not forget that you can choose to allow the Starlight Membership for an whole month in your accounts.
After everything was set, you need to finalize the entire process simply by clicking the"Generate" button located beneath the resource forms. Once you press the button, allow for a few moments to go by before logging in to your game account. The generator may require some time to process the info based on the number of users are currently using it please, be patient.
And that is it! That's all you need to do in order to get this Mobile Legends Bang Bang hack to do the job. Hopefully you have no trouble using those cheats and you get exactly what you wanted. Have fun!
Search Related:
mobile legends download
mobile legends mod apk
mobile legends hack tool
mobile legends cheat
mobile legends download pc
mobile legends hack 2017
mobile legends diamond
mobile legends official website
mobile legends mod apk unlimited gems
mobile legends mod apk unlimited diamond
mobile legends mod apk latest version
mobile legends mod apk android 1
mobile legends hack no human verification
mobile legends game play
mobile legends mod apk unlimited money and diamond
mobile legends new hero
mobile legends diamond hack
mobile legends radar hack
mobile legends mod apk 2017
mobile legends hack without human verification
mobile legends new update
mobile legend diamond hack
mobile legends latest version
how to hack mobile legends
mobile legends hack tool online
mobile legends latest apk
mobile legends free diamonds
mobile legends map hack
how to get diamonds in mobile legends
mobile legends mod apk unlimited money
mobile legends mod apk download
mobile legends apk mod
how to get free diamonds in mobile legends
mobile legends hack no survey
mobile legends hack apk
mobile legends hack diamond
mobile legends mod menu apk
mobile legends apk for pc
mobile legends radar hack latest
mobile legends hack no root
mobile legend mod apk latest
mobile legends map hack 2017
mobile legends map hack apk
mobile legend offline apk
mobile legends god mod apk
mobile legends download ios
mobile legends hack 2017 no survey
how to get skins in mobile legends for free
mobile legends free diamonds no survey
how to get free diamonds in mobile legends no hack
mobile legends skin mod
mobile legends free skin giveaway
mobile legends mobile patcher
wecheat net mobile legends
mobile legends gem hack
ml 4up site mobile legends hack
list of games that work with lucky patcher
mobile legends xmod
cara menggunakan lucky patcher untuk game online
mobile legends hack no verification
mobile legends mod diamond
mobile legends free diamonds 2017
mobile legends skin free
gamingforest net mobile legends diamond hack
mobile legends hack philippines
gamingforest net mobile legend diamond
mobile legends apk latest version
lucky patcher mobile legends
mobile legends hack apk 2017
mobile legends hack ios
mobile legends hack download
gameforest net mobile legends
mobile legends cheat apk
mobile legends hack generator
mobile legends mod apk offline
mobile legends hack top
mobile legends lucky patcher
how to earn diamonds in mobile legends
mobile legends mod apk revdl
mobile legends hack 2017 apk
getdiamond online mobile legend 2017
mobile legends hack without verification
mobile legend hack apk diamond
mobile legends cheats apk free download
mobile legends mod apk unlimited gems download
mobile legends mod apk unlimited diamond latest version
mobile legends hack apk download
mobile legends hack no human verification 2017
mobile legends cheat lag
mobile legends free diamonds no hack
1 note
·
View note
Photo

MysteriaCraft [PvE] {1.12.2} } {Custom Mobs + Drops} {SlimeFun} {dungeons} {Custom Recipes} {Events} {McMMO} {Jobs} {Custom Terrain}
Server Name: MysteriaCraft
Server Location: USA
Server Address: play.mysteriacraft.com
Website: http://www.mysteriacraft.com
Discord: https://discordapp.com/invite/x2MJw2x
---------------------------------------------------------------------------------------------------------------------------------
Welcome:
Mysteriacraft is a server based on a family friendly community for all ages to play. We offer a variety of events, custom mobs, and features for the whole family to enjoy. We are constantly adding more fun adventures for everyone to enjoy with the latest update coming soon for Creative, Skyblock, and Prison so be sure to check us out if you like a family friendly community.
MysteriaCraft Features:
✦ Family Friendly
We strive to create a close-knit community that is welcoming to all age groups and our staff is always striving to make your gametime enjoyable.
✦ Slimefun + Exotic Garden
Slimefun is a plugin that allows players to craft unique machines and items using matierals that are unlike vanilla gameplay. The addon to slimefun, Exoctic garden brings plants to life! Be your own mini farmer with crops like corn, cabbage, and strawberries!
✦ Dungeons
Do you like fighting mobs and earning custom items/gear? Then our dungeons are for you. We focus on a group based dungeon so you, your family, and friends can work together and defeat our Boss mobs and their minions.
✦ Events
The People of Mysteria love to have friendly events and compete against each other to try to make it to the top. We offer building competions, fishing competions, trivias, etc. to entertain not only your gameplay but, also your mind. It adds excitement and other advantages then just survival.
✦ Mythic Drops
Monsters will drop unique weapons, armor, and tools that can be used to help you during your time on Mysteria.
✦ Mythic Mobs
Special Monsters roam the world that are unlike vanilla mobs. Some are hard, some are easy. Will you be able to defeat them?
✦ Grief Prevention
Our server has a strict no raiding or griefing policy. You may not grief or raid unclaimed builds. We take pride in our friendly community and do not by any means allow others to ruin or take away things from our players.
✦ 99.99% Uptime
----------------------------------------------------------------------------------------------------------------------------------
Server Rules:
Rule 1 - No exploiting, cheating, hacking, or glitching
No cheating of any kind will be allowed on the server. This includes any hacked clients such as x-ray or click aimbot, texture packs that have x-ray, as well as macros that give players an unfair advantage.
Do not abuse any bugs, exploit the server’s features or duplicate items for personal gain in any way or form. Abuse of this kind may result in a balance reset and ban.
Usage of VPNs will result in an permanent ban.
Usage of chests/furnaces or other containers lockable with LWC around others bases will result in a tempban.
Rule 2 - No advertising
Do not mention, or attempt to bypass mentioning, the name of any server other then Mysteria.
Do not try to bring other players to a different Minecraft server in any way.
Rule 3 - No AFK pools or complete auto-farms
Do not construct ways to bypass the server’s AFK kicker.
If you build a Semi auto-farm it MUST be turned OFF when you LEAVE the game OR area.
Do not let it run. It will result in the removal of your farm completely and may result in a tempban.
Do not make anything for the sole purpose of making the server lag by using extreme sizes of redstone.
Rule 4 - No spamming or causing drama
Do not spam in any chat channel on discord OR ingame. Repeating the same or similar messages multiple times, is considered distracting and is NOT allowed.
Do not spam caps. We will remove repeated abusers caps access.Keep the chat appropriate and do not bypass our filter with profanity or immature behavior.
Do not spam items for sale in chat over and over again. You may advertise your items every 5 minutes in chat.
Do not beg other players to give you money, buy you things, or donate for you.
Only communicate using English in the global chat, though the use of other languages is allowed in private chat.
Politics, religion, or other controversial topics are not allowed.
Do not start personal arguments or create intentional drama between players. The staff has the right to mute or ban those who are being toxic.
Do not troll other players.
Do not use an inappropriate/offensive, usernames, skins, or nicknames. Those who join the server with an offensive username will be banned until they change it to something appropriate. You can appeal on the website. You also cannot create inappropriate builds or signs. This is a family friendly server.
Do no scam others with anything. This is NOT tolerated OR allowed.
Rule 5 - No griefing or raiding
Do not break or place blocks not set by you. You must also have permission from the owner.
Do not kill another player’s mobs.
Do not steal items from others. If a player drops an item by accident and you pick it up, you must return the item.The stealing and ruining others builds in a area that is NOT claimed is NOT LEGAL.
Rule 6 - Players
Do not disrespect or harass any player or staff member. We do not tolerate this behavior! Our communtiy should be kept a safe environment for everyone.
Message a staff member if you are being harassed, or report the player on the website.
Do not threaten the server or other players in ANY WAY.Do not share someones private information on the server.
Do not talk about self harm on the server in game or on discord.
Rule 7 - No wrongful killing
Do not kill another player unless in a PVP zone.
Do not create a “death trap”, or anything designed to kill another player.
Do not use /fly during player-versus-player combat in our pvp zones.. this includes anything that creates a personl gain. Fair fighting ONLY.
Rule 8 - No abusing donator/member perks
Do not impersonate a staff member or another player using /nick or /prefix.
Do not chargeback donations sent to the server in any way. This will result in a PERM ban/IP ban
Do not attempt to transfer in-game items for a real-life currency.
Rule 9 - Claims
Do not claim a chunk of land within 100 blocks of another claim.
Do not remain on someone else’s claim if they have asked you to leave.
Players who have been inactive for 60 days, may have their locked items such as chests and furnaces removed by a Owner ONLY.
Rule 10 - Respect punishment decisions
Do not evade punishments in any shape or form.
Do not argue with a staff member’s decision. If you feel a staff member is abusing their power, please private message either Raigna or Anorchous on the forums or discord.
Those who are punished for breaking rules a total of 10 times will be perm. banned. You can appeal depending on the situation.
1 note
·
View note
Text
Configure CORS in API Management
In this post, I will show you how to configure CORS in the API Management Service in Azure. If you read my previous post, I shown how to create an Azure API Management Service. So, I faced an issue with CORS that I want to share because I think could be useful for someone else.
The problem
Happily, I have just configured my API Management Service and connect the APIs. Now, I want to use them from my applications. From C# is working fine. If I try a GET request in the browser, it is working. If I try to call the APIs from a JavaScript code I receive this error:
XMLHttpRequest cannot load https://www.example.com/ No ‘Access-Control-Allow-Origin’ header is present on the requested resource. Origin ‘http://localhost:4300’ is therefore not allowed access.
or another one is
Access to fetch at ‘https://ift.tt/3nkNviO; from origin ‘null’ has been blocked by CORS policy: No ‘Access-Control-Allow-Origin’ header is present on the requested resource. If an opaque response serves your needs, set the request’s mode to ‘no-cors’ to fetch the resource with CORS disabled.

Developer tools with CORS the errors
The JavaScript code is use it is pretty simple
<!DOCTYPE html> <html lang="en"> <head> <title>Test Api</title> </head> <body> <script src="https://ajax.googleapis.com/ajax/libs/jquery/3.5.1/jquery.min.js"></script> <script> var url = 'https://api.mydomain.com/api/'; var headerKey = 'Apim-Subscription-Key'; var headerValue = 'your-subscription-key'; // XMLHttpRequest preflight request var xhr = new XMLHttpRequest(); xhr.open("GET", url, true); xhr.setRequestHeader(headerKey, headerValue); xhr.onload = function () { console.log(xhr.responseText); alert("Complete1"); }; xhr.send(); // Fetch preflight request var myHeaders = new Headers(); myHeaders.append(headerKey, headerValue); fetch(url, { headers: myHeaders }).then(function (response) { return response.json(); }).then(function (json) { console.log(json); alert("Complete2"); }); </script> </body> </html>
About the Same Origin Policy
This is the Same Origin Policy. It is a security feature implemented by browsers.
The standard scenario that demonstrates the need for the SOP can be demonstrated with three characters:
Alice is a person with a web browser
Bob runs a website (https://www.[website].com/)
Mallory runs a website (http://localhost:4300)
Alice is logged into Bob’s site and has some confidential data there. Perhaps it is a company intranet (accessible only to browsers on the LAN). Or her online banking (accessible only with a cookie you get after entering a username and password).
Alice visits Mallory’s website which has some JavaScript. That causes Alice’s browser to make an HTTP request to Bob’s website (from her IP address with her cookies, etc). This could be as simple as using XMLHttpRequest and reading the responseText.
The browser’s Same Origin Policy prevents that JavaScript from reading the data returned by Bob’s website (which Bob and Alice don’t want Mallory to access). (Note that you can, for example, display an image using an <img> element across origins because the content of the image is not exposed to JavaScript (or Mallory) … unless you throw canvas into the mix in which case you will generate a same-origin violation error).
Why the Same Origin Policy applies when you don’t think it should
For any given URL it is possible that the SOP is not needed. A couple of common scenarios where this is the case are:
Alice, Bob and Mallory are the same person.
Bob is providing entirely public information
… but the browser has no way of knowing if either of the above are true. So, trust is not automatic and the SOP is applied. Permission has to be granted explicitly before the browser will give the data it was given to a different website.
Why the Same Origin Policy only applies to JavaScript in a web page
Browser extensions, the Network tab in browser developer tools and applications like Postman are installed software. They aren’t passing data from one website to the JavaScript belonging to a different website just because you visited that different website. Installing software usually takes a more conscious choice. There isn’t a third party (Mallory) who is considered a risk.
Browser extensions do need to be written carefully to avoid cross-origin issues. See the Chrome documentation for example.
Why you can display data in the page without reading it with JS
There are a number of circumstances where Mallory’s site can cause a browser to fetch data from a third party and display it (e.g. by adding an <img> element to display an image). It isn’t possible for Mallory’s JavaScript to read the data in that resource though. Only Alice’s browser and Bob’s server can do that, so it is still secure.
CORS
The Access-Control-Allow-Origin HTTP response header referred to in the error message is part of the CORS standard which allows Bob to explicitly grant permission to Mallory’s site to access the data via Alice’s browser.
A basic implementation would just include:
Access-Control-Allow-Origin: *
and in the response headers to permit any website to read the data.
Access-Control-Allow-Origin: http://example.com/
would allow only a specific site to access it, and Bob can dynamically generate that based on the Origin request header to permit multiple, but not all, sites to access it.
The specifics of how Bob sets that response header depend on Bob’s HTTP server and/or server-side programming language. There is a collection of guides for various common configurations that might help.

Some requests are complex and send a preflight OPTIONS request. The server will have to respond to before the browser will send the GET/POST/PUT/Whatever request that the JS wants to make. Implementations of CORS that only add Access-Control-Allow-Origin to specific URLs often get tripped up by this.
Obviously granting permission via CORS is something Bob would only do only if either:
The data was not private or
Mallory was trusted
But I’m not Bob!
There is no standard mechanism for Mallory to add this header because it has to come from Bob’s website, which she does not control.
If Bob is running a public API then there might be a mechanism to turn on CORS. This will have to be a mechanism implemented by Bob though. Mallory could read the documentation on Bob’s site to see if something is available, or she could talk to Bob and ask him to implement CORS.
Error messages which mention “Response for preflight”
Some cross origin requests are preflighted.
This happens when (roughly speaking) you try to make a cross-origin request that:
Includes credentials like cookies
Couldn’t be generated with a regular HTML form (e.g. has custom headers or a Content-Type that you couldn’t use in a form’s enctype).
If you are correctly doing something that needs a preflight
In these cases then the rest of this answer still applies but you also need to make sure that the server can listen for the preflight request (which will be OPTIONS (and not GET, POST or whatever you were trying to send) and respond to it with the right Access-Control-Allow-Origin header but also Access-Control-Allow-Methods and Access-Control-Allow-Headers to allow your specific HTTP methods or headers.
If you are triggering a preflight by mistake
Sometimes people make mistakes when trying to construct Ajax requests, and sometimes these trigger the need for a preflight. If the API is designed to allow cross-origin requests, but doesn’t require anything that would need a preflight, then this can break access.
Common mistakes that trigger this include:
trying to put Access-Control-Allow-Origin and other CORS response headers on the request. These don’t belong on the request, don’t do anything helpful (what would be the point of a permissions system where you could grant yourself permission?), and must appear only on the response.
trying to put a Content-Type: application/json header on a GET request that has no request body to describe the content of (typically when the author confuses Content-Type and Accept).
In either of these cases, removing the extra request header will often be enough to avoid the need for a preflight (which will solve the problem when communicating with APIs that support simple requests but not preflighted requests).
Opaque responses
Sometimes you need to make an HTTP request, but you don’t need to read the response. e.g. if you are posting a log message to the server for recording.
If you are using the fetch API (rather than XMLHttpRequest), then you can configure it to not try to use CORS.
Note that this won’t let you do anything that you require CORS to do. You will not be able to read the response. You will not be able to make a request that requires a preflight.
It will let you make a simple request, not see the response, and not fill the Developer Console with error messages.
How to do it is explained by the Chrome error message given when you make a request using fetch and don’t get permission to view the response with CORS:
Access to fetch at ‘https://example.com/‘ from origin ‘https://example.net‘ has been blocked by CORS policy: No ‘Access-Control-Allow-Origin‘ header is present on the requested resource. If an opaque response serves your needs, set the request’s mode to ‘no-cors’ to fetch the resource with CORS disabled.
Thus:
fetch("http://example.com", { mode: "no-cors" });
Alternatives to CORS
JSONP
Bob could also provide the data using a hack like JSONP which is how people did cross-origin Ajax before CORS came along.
It works by presenting the data in the form of a JavaScript program which injects the data into Mallory’s page. It requires that Mallory trust Bob not to provide malicious code.
Note the common theme: The site providing the data has to tell the browser that it is OK for a third party site to access the data it is sending to the browser.
Since JSONP works by appending a <script> element to load the data in the form of a JavaScript program which calls a function already in the page, attempting to use the JSONP technique on a URL which returns JSON will fail — typically with a CORB error — because JSON is not JavaScript.
Move the two resources to a single Origin
If the HTML document the JS runs in and the URL being requested are on the same origin (sharing the same scheme, hostname, and port) then they Same Origin Policy grants permission by default. CORS is not needed.
A Proxy
Mallory could use server-side code to fetch the data (which she could then pass from her server to Alice’s browser through HTTP as usual).
It will either:
add CORS headers
convert the response to JSONP
exist on the same origin as the HTML document
That server-side code could be written & hosted by a third party (such as CORS Anywhere). Note the privacy implications of this: The third party can monitor who proxies what across their servers.
Bob wouldn’t need to grant any permissions for that to happen.
There are no security implications here since that is just between Mallory and Bob. There is no way for Bob to think that Mallory is Alice and to provide Mallory with data that should be kept confidential between Alice and Bob.
Consequently, Mallory can only use this technique to read public data.
Do note, however, that taking content from someone else’s website and displaying it on your own might be a violation of copyright and open you up to legal action.
Writing something other than a web app
As noted in the section “Why the Same Origin Policy only applies to JavaScript in a web page”, you can avoid the SOP by not writing JavaScript in a webpage.
That doesn’t mean you can’t continue to use JavaScript and HTML, but you could distribute it using some other mechanism, such as Node-WebKit or PhoneGap.
Browser extensions
It is possible for a browser extension to inject the CORS headers in the response before the Same Origin Policy is applied.
These can be useful for development, but are not practical for a production site (asking every user of your site to install a browser extension that disables a security feature of their browser is unreasonable).
They also tend to work only with simple requests (failing when handling preflight OPTIONS requests).
Having a proper development environment with a local development server is usually a better approach.
Other security risks
Note that SOP / CORS do not mitigate XSS, CSRF, or SQL Injection attacks which need to be handled independently.
When the problem starts
So, this issue happens when you enable the Developer portal. Then, in the configuration for the portal, you enable CORS. At this point, Azure automatically adds a global policy to the API Management Service but you don’t know that.
<policies> <inbound> <!-- base: Begin Global scope --> <cors allow-credentials="true"> <allowed-origins> <origin>https://developer.mydomain.com</origin> </allowed-origins> <allowed-methods preflight-result-max-age="300"> <method>*</method> </allowed-methods> <allowed-headers> <header>*</header> </allowed-headers> <expose-headers> <header>*</header> </expose-headers> </cors> <!-- base: End Global scope --> </inbound> </policies>
Happily, you configure CORS in your API and when you try to call them from JavaScript, you are facing the CORS error.
If you open the CORS configuration in the Azure portal you can see something like that:
<policies> <inbound> <base /> <cors> <allowed-origins> <origin>*</origin> </allowed-origins> <allowed-methods preflight-result-max-age="300"> <method>GET</method> <method>POST</method> </allowed-methods> <allowed-headers> <header>*</header> <header /> </allowed-headers> <expose-headers> <header>*</header> </expose-headers> </cors> </inbound> <backend> <base /> </backend> <outbound> <base /> </outbound> <on-error> <base /> </on-error> </policies>
My understanding is the portal combine the base configuration with yours. So, like in Active Directory the more restricted policy is applying. That means in my example, only the Developer Portal can call the APIs without CORS issue.
Solution
Delete <base /> under <inbound> and save.
The post Configure CORS in API Management appeared first on PureSourceCode.
from WordPress https://www.puresourcecode.com/tools/azure-tools/configure-cors-in-api-management/
0 notes
Text
How To Decide On The Most Effective Web Site Builder In 2021
BigCommerce is the best eCommerce web site builder in the market. If you’re looking to create a web-based store that scales, then BigCommerce is the platform for you. It comes with all of the important features built-in, so you'll be able to keep your overhead low and margins excessive. Zyro is a robust and inexpensive website builder on the market. They supply a simple to use drag & drop web site builder tool with free hosting and 87% off premium plans which makes them the cheapest website builder in our list. You get a simple web site builder that allows you to choose from 200+ professional website design templates.
📷
These websites are designed to look like different official sites (e.g., your financial institution) with the hope that they will phish delicate data corresponding to your username and password. A malicious web site is any web site that was set up with the intention of infecting one other laptop or amassing personal data. For example, a malware web site is a web site created with the intention of infecting any customer with malware, adware, or a malicious program. These kinds of sites might have a download that's contaminated and, if downloaded, infects your pc. A crowdfunding website is ready as much as assist help a enterprise, person, or another cause by making a one time or monthly cost. An example of a crowdfunding web site is Kickstarter.
Hakkasan is an award-successful restaurant which makes use of the best ingredients and expert traditional strategies to create timeless yet innovative signature dishes. We have operated in Asia Pacific since 1872, and right now are current across 17 markets in the area. Clients depend on our global strength, native expertise and leadership throughout our traces of enterprise. This web site uses cookies to ensure you get the best experience.
In this step-by-step information, I need to present you exactly what you should create an internet site from scratch. By the end, you’ll have a web site to point out for it and with none of the complications. With the best instruments and systems, creating a fantastic web site is as simple as ever.
Instruments
Many web hosting providers have “WordPress set up” positioned somewhere within the hosting cPanel. If you're coping with a web host that doesn’t present “one-click on installs“, attempt establishing WordPress manually. Setting up your WordPress website is simple, and your web host mostly does it for you, so you don’t actually need to get your palms too dirty. four) Once you’ve accomplished your registration process it'll take a few minutes to get prompt access, so you can begin constructing your website instantly. Keep in mind that Bluehost doesn’t offer nation-particular domain endings, similar to.de, .fr, or .ru. If you want them, you should buy these from Domain.com or GoDaddy.com individually.
Accelerate business restoration and ensure a greater future with options that enable hybrid and multi-cloud, generate intelligent insights, and hold your employees related. Cloud Talent Solution AI with job search and talent acquisition capabilities. Document AI Machine studying and AI to unlock insights from your documents. Build and Use AI Products to construct and use synthetic intelligence.
As the world’s world chief in constructing solutions, LafargeHolcim is reinventing how the world builds. Our 70,000 employees are committed to enhancing quality of life throughout 70 markets by way of four business segments. We imagine in building a world that works for people and the planet. A world that keeps people protected, linked and thriving. Together with our staff we wish to form a world that's greener, smarter and that works for all. With our customers and partners we're advancing society and uplifting communities.
Websites are constrained by architectural limits (e.g., the computing energy dedicated to the website). , Microsoft, and Google make use of many servers and load balancing equipment corresponding to Cisco Content Services Switches to distribute visitor masses over multiple computer systems at a number of locations. As of early 2011, Facebook utilized 9 data centers with approximately sixty three,000 servers.
Learn how a neighborhood Hong Kong financial institution grew to become one of the world’s largest financial companies organisations. We are dedicated to serving to our individuals to develop their expertise in an inclusive surroundings – and to supporting the communities where we function. We’re bringing together the folks, ideas and capital that nurture progress and growth รับทําเว็บไซต์, helping to create a better world. GE Healthcare makes use of AWS and Amazon SageMaker to ingest information, retailer information compliantly, orchestrate curation work throughout teams, and construct machine-studying algorithms. Zillow helped convey the real property industry online, then reinvented the house-search process utilizing AWS Cloud.
How Can I Get A Free Area?
There are checks suited for each degree, and on the finish you will get recommendations on how to improve your English. Practice material and learning sources to help you improve your English. Linguaskill is a quick and convenient online check to assist greater schooling institutions and employers verify the English levels of people and groups of candidates. It combines the most recent AI know-how with the reliability and quality you count on from Cambridge. Over the last 12 months, the International Organization for Migration has responded to the COVID-19-associated needs of hundreds of thousands of people worldwide.
Select the Wix site you wish to connect your domain to then click on Next. Keep it straightforward on your self and hold attempting till you discover a free one. Once you do, you possibly can register it right off of Domain.com (get 25% off with coupon code QUICKSPROUT) or through Wix. Choose the one you like probably the most and use that in your web site area. Plus it makes it tougher for folks to say what your URL is to others.
If you wish to edit your background color simply sort "background colour" and the choice will appear right away.
Use one platform to sell merchandise to anybody, anyplace—in particular person with Point of Sale and on-line by way of your website, social media, and on-line marketplaces.
Leverage automation to optimize and modernize load balancing throughout clouds.
NATO continually reviews and transforms its insurance policies, capabilities and constructions to make sure that it could proceed to deal with present and future challenges to the freedom and safety of its members.
This creates concise in-text citations and complete reference record entries.
The difference between taking your own footage and hiring a photographer could be a few hundred dollars. The same may be said for professional copywriting for net content material and so on. Starting a web site for your corporation is a low-value investment that can help you establish credibility and attain a wider customer base than you ever may through conventional advertising methods. If you retain your website updated with contemporary, present content and are quick to deal with technical issues, you will never have to worry about "not current" to your current and future shoppers. As you build your business web site, these importanton-web site SEO tactics can help you improve your ability to move up the ranks.
Coming on high of a surge in world debt since 2010, this creates new risks.Read More. Ahead of the Spring Meetings, World Bank Group President David Malpass discussed what is needed to construct a green, inclusive, and resilient recovery from the pandemic. We face big challenges to help the world’s poorest people and be sure that everybody sees advantages from financial progress. Data and analysis assist us understand these challenges and set priorities, share information of what works, and measure progress.
We are a global leader in design and make know-how. With experience throughout structure, engineering, construction, design, manufacturing, and entertainment, we help customers clear up right now’s urgent challenges. Correlate your user’s visible expertise to the technical measurements of your site. Test your person’s actual expertise with international locations, modern units, and the most recent browser variations. This is finished by re-routing all requests for the domains to blackhole.webpagetest.org which will silently drop all requests. Hugo's Go-primarily based templating offers simply the correct quantity of logic to construct something from the simple to complicated.
Get perks and instruments for managing clients whenever you join our free community, Mailchimp & Co. Run an A/B or multivariate take a look at to optimize your content material, format, or send time. Get lovely, on-brand designs made for you with the power of AI. Keep track of what you understand about your individuals with customizable tags. Target your messages based mostly on people's purchase behavior, app exercise, and extra.
That’s why we are reinventing how the world builds on our way to becoming a web zero firm. No extra app switching—join tons of of instruments like Office 365 and Google Workspace, or construct your personal integrations with our open APIs. Manage one built-in and safe platform with global PBX providers in over forty nations, from just about anywhere.
Add a web-based store, galleries, mailing lists, forums, analytics, and far more. forty% of the online uses WordPress, from pastime blogs to the largest news sites on-line. WordPress is open source software program you need to use to create a wonderful website, blog, or app. The concepts of a web web page and a web site are especially easy to confuse for a web site that accommodates just one internet page. Such a website is sometimes known as a single-page website. A website is a set of linked internet pages that share a novel domain name.
Follow the news: https://munkongseo.com/ สอนทำ SEO
0 notes