#Laravel Security
Explore tagged Tumblr posts
Text
A Behind-the-Scenes Look at a Laravel Security Audit
Introduction Laravel is one of the most popular PHP frameworks, and it is likely to continue to be that way for some time to come. There are many reasons why this is so, like its syntax, robust features, scalability, and, most of all, its high level of security. Security remains a paramount concern for developers and businesses alike, irrespective of the selection of technology. Laravel, like…
0 notes
Text
Securing Your Laravel App: Latest Best Practices and Threat Protection
In the ever-evolving world of web development, Laravel has emerged as one of the most popular PHP frameworks. Its elegant syntax, robust features, and vibrant community make it a top choice for many developers. However, as with any technology, ensuring the security of your Laravel application is paramount. In this blog post, we will delve into the latest best practices for securing your Laravel app and protecting it against threats.

Why Security Matters in Laravel Development
Before we dive into the specifics, let’s take a moment to understand why security is so crucial in Laravel development. As the digital landscape expands, so does the potential for security breaches. These breaches can lead to data loss, unauthorized access, and even severe financial implications. Therefore, whether you’re a seasoned Laravel developer or a business looking to hire a Laravel developer, understanding and implementing security best practices is non-negotiable.
Laravel Security Best Practices
1. Keep Your Laravel Version Updated
One of the simplest yet most effective ways to secure your Laravel app is by keeping your Laravel version updated. Each new version of Laravel comes with security patches and updates that fix known vulnerabilities.
2. Use HTTPS
Using HTTPS instead of HTTP ensures that all communication between your server and your users is encrypted. This encryption makes it much harder for attackers to access sensitive information.
3. Validate and Sanitize Data
Always validate and sanitize data coming from users or third-party sources. Laravel provides several ways to validate data, including form request validation, manual validation, and even validation rules.
4. Use Laravel’s Built-In Authentication
Laravel comes with built-in authentication scaffolding, which provides a secure way to handle user authentication. Using this feature can save you from the potential security risks of building your own authentication system.
5. Limit and Monitor Access
Implement role-based access control (RBAC) to limit who can access what resources in your application. Also, monitor your application for any unusual activity.
Threat Protection in Laravel
Protecting your Laravel app from threats involves being aware of the common types of attacks and knowing how to prevent them. Here are a few threats you should be aware of:
1. SQL Injection
SQL injection involves an attacker manipulating your SQL queries to gain unauthorized access or make unauthorized changes to your database. Laravel’s Eloquent ORM uses PDO parameter binding, which protects your application from SQL injection.
2. Cross-Site Scripting (XSS)
XSS attacks involve an attacker injecting malicious scripts into your web pages, which are then run by your users’ browsers. Laravel’s Blade templating engine automatically escapes output, protecting your application from XSS attacks.
3. Cross-Site Request Forgery (CSRF)
CSRF attacks trick your users into performing actions without their knowledge or consent. Laravel includes built-in protection against CSRF attacks.
Conclusion
Securing your Laravel application involves a combination of staying updated with the latest Laravel version, using built-in Laravel features, and being aware of common threats. Whether you’re a Laravel developer or a Laravel development company, following these best practices will go a long way in ensuring the security of your Laravel application.
Remember, security is not a one-time task but an ongoing process. Stay vigilant, stay updated, and most importantly, stay secure.
FAQs on Securing Your Laravel App: Latest Best Practices and Threat Protection**
Q: Why is securing my Laravel app important?
- A: Securing your Laravel app is crucial to protect sensitive data, prevent unauthorized access, and safeguard against potential cyber threats. It ensures the integrity and reliability of your application.
Q: What are the latest best practices for securing a Laravel app?
- A: Some best practices include keeping Laravel and its dependencies up-to-date, implementing strong authentication mechanisms, securing sensitive routes, using HTTPS, and regularly auditing and monitoring your application for potential vulnerabilities.
Q: How can I keep my Laravel framework and dependencies updated?
- A: Use Composer to manage your project dependencies and regularly update Laravel by running `composer update`. Stay informed about security releases and apply them promptly.
Q: What authentication mechanisms should I use to secure my Laravel app?
- A: Laravel provides built-in authentication features. Implement multi-factor authentication (MFA), use strong password policies, and consider OAuth or social media logins for additional security layers.
Q: How do I secure sensitive data in my Laravel app?
- A: Employ encryption for sensitive data using Laravel's encryption features. Avoid storing sensitive information in plain text and utilize secure methods like Laravel's Eloquent ORM for database operations.
Q: Is HTTPS necessary for my Laravel app?
- A: Yes, using HTTPS is crucial. It encrypts data in transit, preventing eavesdropping and man-in-the-middle attacks. Obtain an SSL certificate and configure your Laravel app to use HTTPS.
Q: How can I protect against common web application security threats?
- A: Implement input validation, use Laravel's built-in protection against Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF), and sanitize user inputs to prevent SQL injection.
Q: Should I use Laravel's built-in security features or implement additional security packages?
- A: Laravel offers robust security features, but depending on your specific requirements, you may consider additional security packages like Laravel Security Package or Laravel Fortify for enhanced protection.
Q: How can I monitor my Laravel app for security vulnerabilities?
- A: Regularly conduct security audits, use security scanning tools, and implement logging and monitoring solutions to detect and respond to any suspicious activities or potential threats.
Q: What steps can I take to recover my Laravel app in case of a security breach?
- A: Have a well-defined incident response plan, regularly back up your data, and ensure you can quickly restore your application to a secure state. Additionally, notify users of any security incidents and prompt them to update passwords if necessary.
0 notes
Text
#laravel security#laravel security features#laravel development company#build laravel applications#laravel app development
0 notes
Text
Secure Your Laravel App: Fix Insufficient Transport Layer Security (TLS)
Introduction
Transport Layer Security (TLS) is vital for ensuring secure communication between clients and servers over the Internet. Insufficient TLS configurations can leave your Laravel web applications exposed to various cyber threats, like Man-in-the-Middle (MitM) attacks. In this blog post, we’ll explain the risks associated with insufficient TLS security in Laravel and provide a detailed guide on how to configure your Laravel application for optimal security.

Additionally, we’ll show you how to check and resolve potential TLS issues using our free Website Security Scanner tool.
What is Insufficient Transport Layer Security?
Insufficient Transport Layer Security occurs when a website fails to use strong encryption protocols like TLS 1.2 or higher, or when it doesn't properly configure SSL certificates. This exposes web applications to data interception, tampering, and attacks. A properly configured TLS ensures that all data transmitted between the server and client is encrypted and secure.
Common Issues in Laravel with Insufficient TLS Security
Some common causes of insufficient TLS in Laravel include:
Outdated SSL Certificates: Using deprecated SSL/TLS protocols (like SSL 3.0 or TLS 1.0) that are no longer considered secure.
Improper SSL/TLS Configuration: Misconfiguration of the web server or Laravel app that doesn’t force HTTPS or downgrade protection.
Weak Cipher Suites: Servers using weak ciphers, making it easier for attackers to break the encryption.
Lack of HTTP Strict Transport Security (HSTS): Without HSTS, an attacker can force the browser to use an insecure HTTP connection instead of HTTPS.
How to Fix Insufficient TLS in Laravel
Upgrade Your Laravel App’s TLS Protocol To enforce TLS 1.2 or higher, you'll need to configure your server to support these protocols. Here’s how you can configure your server to prioritize stronger encryption:
In Apache: Modify the ssl.conf file:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
In Nginx: Edit your nginx.conf file:
ssl_protocols TLSv1.2 TLSv1.3;
These configurations will ensure that your server uses only secure versions of TLS.
2. Force HTTPS in Laravel Laravel provides an easy way to force HTTPS by modifying the .env file and the config/app.php file:
In .env file:
APP_URL=https://yourdomain.com
In config/app.php file:
'url' => env('APP_URL', 'https://yourdomain.com'),
This will ensure that all requests are redirected to HTTPS, preventing insecure HTTP access.
3. Enable HTTP Strict Transport Security (HSTS) HTTP Strict Transport Security is a web security policy mechanism that helps to protect websites against Man-in-the-Middle (MitM) attacks by forcing clients to communicate over HTTPS. Here's how to add HSTS headers to your Laravel app:
In Apache: Add the following line to your ssl.conf or .htaccess file:
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
In Nginx: Add the following line to your nginx.conf file:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
4. Use Strong Cipher Suites Weak cipher suites allow attackers to break the encryption. You can configure your server to use strong ciphers:
In Apache:
SSLCipherSuite HIGH:!aNULL:!MD5:!3DES
In Nginx:
ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256';
5. Use a Valid SSL/TLS Certificate Ensure that your website uses a valid SSL/TLS certificate from a trusted Certificate Authority (CA). You can get a free SSL certificate from Let's Encrypt.
How to Check TLS Configuration with Our Free Tool
Before and after implementing the changes, it’s essential to check the security status of your website. You can use our free Website Security Checker Tool to evaluate your website’s TLS configuration.
Go to https://free.pentesttesting.com.
Enter your website URL to start the scan.
Review the vulnerability assessment report for TLS issues.
Screenshot of the Free Tool
Here’s a screenshot of the free Website Security Checker tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of a Vulnerability Assessment Report
After running the scan to check website vulnerability, you’ll receive a detailed report highlighting any security vulnerabilities, including issues related to TLS. Here’s an example of the vulnerability assessment report:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Ensuring sufficient Transport Layer Security in your Laravel app is crucial to protecting sensitive data and preventing attacks. By following the steps outlined in this blog, you can fix any TLS issues and enhance the security of your web application.
Don’t forget to check your website using our free Website Security Checker tool to identify any existing TLS vulnerabilities and other security flaws.
Need help? Contact us at Pentest Testing Corp for professional vulnerability assessments and penetration testing services to secure your website further.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#tls
4 notes
·
View notes
Text
How Online Office Furniture Platforms Verify Accounts Using Laravel Events, Jobs and Queues
Have ever wondered how just a simple online office furniture store verifies you account you registered using an email address? For sure, they use Laravel which is the currently the best PHP framework. It offers programmers and web developers with advanced tools to integrate tech in and build secure web developments. Here, they automate your email verification using Laravel Events, Jobs and Queues combinations to your inbox. Then after, you can securely receive the latest updates about the trendy office chairs and desks, keep all your office furniture order information. For sure, this also keeps office furniture manufacturers and suppliers at a cutting-edge as they securely and safely offer online services.
Here is how.
#Laravel#Laravel framework#office furniture#tech integration#modern office furniture#ergonomic chairs#office chairs#trendy office chairs#office desks#furniture manufacturers#PHP Framework#account verification#email verification#order information#secure platforms#online office furniture store#Office furniture Dubai#cutting edge office furniture#web development#web design#online services#office furniture suppliers#register email address#Laravel Events#Laravel jobs#Laravel Queues#advanced web development#advanced online systems#secure web developments#web security
0 notes
Text

Learn about latest Laravel threats in 2024 how to protect your apps with best practices Keep your applications safe and stay ahead with expert tips techniques
0 notes
Text
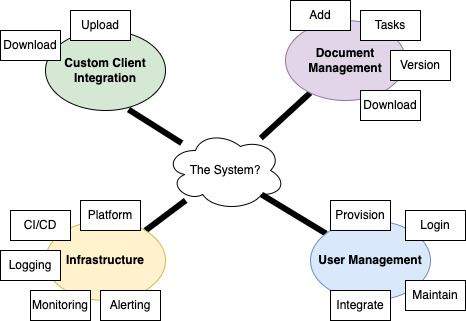
In interviewing for higher level architecture positions, you will be sometimes be asked to do design a new system to demonstrate your capabilities. The following is from such an interview around PHP, Laravel, Nuxt, MySQL, Redis, AWS, and K8s.
0 notes
Text
Top 5 Open-Source PHP CMS Platforms to Watch in 2024 🚀
Web development in 2024 continues to thrive with PHP-based CMS platforms. The top 5 open-source options leading the charge are:
1️⃣ WordPress: User-friendly, highly customizable, but faces performance challenges. 2️⃣ Drupal: Enterprise-grade security and scalability for complex websites. 3️⃣ Joomla: Multilingual support and great customization options. 4️⃣ OctoberCMS: Laravel-powered flexibility for developers. 5️⃣ ConcreteCMS: Intuitive editing for SMBs.
Learn their features, challenges, and trends shaping 2025.
👉 Read the full article here: https://gegosoft.com/top-5-open-source-php-cms-platforms/

3 notes
·
View notes
Text
Website Development Company in Delhi - Mirai Website Designing
Mirai is a leading Website Development Company in Delhi, Our skilled developers are expert in popular frameworks like WordPress, React, Angular and Laravel to create secure, scalable and high performing websites. Whether you are looking to build an E-Commerce platform, a corporate site or a portfolio. We are specialized in Search Engine Optimization (SEO), Pay Per Click (PPC) advertising, Mobile App Development, Graphic Design, E Commerce Website design and many more. Contact us for more details.
#website design#web design company#website development#web development services#website traffic#website optimization#website desing bd#web design#web hosting#website designing company in delhi#website developer near me#website developers#website developer in india#website developer in delhi#website development company in delhi#delhi website designing company
4 notes
·
View notes
Text
A Behind-the-Scenes Look at a Laravel Security Audit
Introduction
Laravel is one of the most popular PHP frameworks, and it is likely to continue to be that way for some time to come. There are many reasons why this is so, like its syntax, robust features, scalability, and, most of all, its high level of security.

Security remains a paramount concern for developers and businesses alike, irrespective of the selection of technology. Laravel, like any other framework, is not immune to security threats.
Conducting an in-depth security audit for a Laravel application involves a comprehensive review of various security aspects to ensure the application is robust and secure.
Security breaches can have devastating consequences for businesses, including data theft, financial loss, and reputation damage. This blog offers a detailed behind-the-scenes look at the process of conducting a Laravel security audit.
What is Laravel Security Audit?
A Laravel security audit systematically examines an application for potential vulnerabilities, misconfigurations, and adherence to security best practices. It ensures that the application aligns with industry standards, such as OWASP Top 10, and safeguards sensitive data. Securing web applications is critical in today's environment of rising cyber threats. Regular security audits are essential to ensure comprehensive protection.
One can assess the application security via a Laravel Security Audit. It helps in evaluating a Laravel application to identify and address vulnerabilities and potential risks that could compromise its security. The audit ensures the application adheres to best practices, protecting sensitive data and preventing cyberattacks.
The main goals of a Laravel Security Audit:
Identify Laravel Vulnerabilities: Detect security flaws such as SQL injections, XSS attacks, or weak authentication.
Enhance Security Measures: Reinforce built-in Laravel security features with additional safeguards.
Ensure Compliance: Meet legal and industry standards (e.g., GDPR, HIPAA, PCI-DSS).
Maintain User Trust: Protect user data and preserve application integrity.
A Laravel Security Audit is essential for maintaining a secure, compliant, and trustworthy application. It systematically uncovers vulnerabilities and ensures your application is fortified against modern threats. An official Laravel partner will have skilled developers and the necessary resources to deliver top-notch solutions. Acquaint Softtech is one such Laravel development company.
We have over 10 years of experience delivering feature-rich and secure Laravel applications. We are a software development outsourcing company in India with a dedicated team of Laravel developers.
Laravel Security Protocols

Laravel prioritizes security by incorporating several protocols and best practices to protect web applications from vulnerabilities. This is further verified after the release of version 11, where many more security features were introduced. Below is a comprehensive overview of Laravel's security protocols:
Authentication and Authorization
Protection Against SQL Injection
Cross-Site Scripting (XSS) Protection
Cross-Site Request Forgery (CSRF) Protection
Secure File Uploads
Data Encryption
Session Security
HTTPS and HSTS
API Security
Error and Exception Handling
Secure Storage of Environment Variables
Dependency Management
Disable Unused Features
Logging and Monitoring
Common Laravel Security Audit Issues
Laravel is a secure PHP framework. However, it is not uncommon for security vulnerabilities to develop as a result of bad configuration or improper usage of a feature. Some of the common issues found during Laravel security audits include:
Insufficient input validation
Missing subresource integrity (SRI)
Insufficient rate limiting
Cross-site scripting (XSS)
Outdated & vulnerable dependencies
Insecure function use
Missing security headers
Missing content security policy (CSP)
Missing authorization
Exposed API keys & passwords
Security Audit Process

Set up the Scope of the Audit: The first step in a Laravel security audit is defining its scope. This includes:
Identifying Critical Areas:
Authentication and authorization mechanisms
Input validation and sanitization
Application and server configuration
Data encryption and storage
API endpoints and integration
Understanding the Application Architecture:
Documenting the architecture and dependencies
Mapping data flow within the application
Determining the Audit Type:
Black-box testing: Testing without access to the source code.
White-box testing: Testing with full access to the source code.
Gray-box testing: A combination of both approaches.
Setting Goals:
Identify and mitigate Laravel vulnerabilities.
Ensure compliance with legal and regulatory requirements.
Establish a baseline for ongoing security practices.
Reviewing the Laravel Environment Configuration:
Laravel's .env file is critical for managing environment-specific configurations, but it can also become a security risk if misconfigured.
Checklist for Environment Configuration:
Ensure the .env file is not accessible publicly. Misconfigured servers can expose this file, revealing sensitive credentials.
Use strong, randomly generated application keys (APP_KEY) to secure sessions and encrypted data.
Disable debugging mode (APP_DEBUG=false) in production environments to prevent sensitive information exposure.
Tools Used:
Manual inspection of configuration files
Automated tools like Laravel DebugBar for debugging issues
Examining Authentication and Authorization:
Authentication and authorization mechanisms are the backbone of application security. A robust implementation minimizes the risk of unauthorized access.
Authentication:
Verify the implementation of Laravel’s built-in authentication scaffolding.
Ensure secure password hashing using bcrypt or Argon2.
Enforce strong password policies and implement multi-factor authentication (MFA) if possible.
Authorization:
Review roles and permissions using Laravel policies and gates.
Check for privilege escalation vulnerabilities.
Session Security:
Use HTTPS to secure cookies.
Enable SameSite and HttpOnly attributes for cookies.
Configure session timeouts and token regeneration.
Tools Used:
Manual code review
Laravel’s built-in Auth and Gate facades for validation
Input Validation and Data Sanitization:
Unvalidated or unsanitized user input is a leading cause of security vulnerabilities, including SQL injection, XSS, and command injection.
Best Practices:
Validation Rules:
Use Laravel’s request validation methods ($request->validate) to ensure inputs meet specified criteria.
Avoid custom validation where built-in methods suffice.
Sanitization:
Escape output using Laravel’s Blade templating engine ({{ $variable }}) to prevent XSS.
Use e() for escaping dynamic content in non-Blade contexts.
SQL Injection Prevention:
Use Laravel’s query builder or Eloquent ORM to avoid directly executing raw queries.
Parameterize queries to eliminate injection risks.
File Upload Security:
Restrict allowed file types.
Store uploaded files outside the web root.
Validate file size and sanitize file names.
Tools Used:
OWASP ZAP for input validation testing
Laravel-specific tools like Larastan for static analysis
Reviewing Encryption and Data Storage Practices:
Sensitive data such as passwords, tokens, and personal information must be encrypted at rest and in transit.
Encryption:
Ensure sensitive data is encrypted using Laravel’s Crypt facade.
Use secure algorithms like AES-256 for encryption.
Database Security:
Use prepared statements and ORM to protect against SQL injection.
Regularly update database credentials and use role-based access control (RBAC) for database users.
Logs:
Avoid logging sensitive information in production.
Rotate logs periodically to prevent unauthorized access.
Tools Used:
Laravel’s encryption and hashing tools
Database auditing tools like MySQL Enterprise Audit
Analyzing API Security:
APIs are a common attack vector and require careful attention during a security audit.
Key Areas to Examine:
Authentication:
Use token-based authentication (e.g., Laravel Passport or Sanctum).
Secure API tokens using strong hashing algorithms.
Rate Limiting:
Protect against brute force attacks using Laravel’s rate-limiting middleware.
Input Validation:
Validate and sanitize all API inputs to prevent injection attacks.
CORS Policies:
Restrict origins to trusted domains using Laravel’s CORS middleware.
Error Handling:
Ensure error responses do not expose sensitive information.
Tools Used:
Postman for manual API testing
Automated scanners like OWASP ZAP for API vulnerability testing.
Securing Third-Party Dependencies:
Laravel applications often rely on third-party packages and libraries. Unmaintained or insecure dependencies can introduce vulnerabilities.
Best Practices:
Dependency Management:
Use Composer to manage dependencies.
Regularly update dependencies to their latest stable versions.
Review Package Integrity:
Verify package integrity using checksums.
Avoid installing unnecessary or unverified packages.
Monitoring Tools:
Use tools like Snyk or Dependabot to monitor for Laravel vulnerabilities in third-party packages.
Tools Used:
Composer security audit (composer audit)
Dependency scanners like Snyk
Conducting Penetration Testing:
Penetration testing simulates real-world attacks to uncover vulnerabilities in the application.
Techniques Used:
Black-box testing to simulate an attacker without prior knowledge of the system.
Exploiting common vulnerabilities like XSS, CSRF, and SQL injection.
Testing for logic flaws and business logic vulnerabilities.
Tools Used:
OWASP ZAP and Burp Suite for penetration testing
Kali Linux tools like SQLMap for SQL injection testing
Ensuring Compliance and Reporting:
Security audits must align with relevant compliance standards such as GDPR, HIPAA, or PCI-DSS.
Compliance Checklist:
Perform data protection impact assessments (DPIAs) where applicable.
Verify adherence to data retention policies.
Ensure encryption and logging practices meet regulatory requirements.
Reporting:
Provide a detailed report outlining identified vulnerabilities, their severity, and recommendations for mitigation.
Use scoring systems like CVSS to prioritize vulnerabilities.
Tools Used:
Compliance frameworks like NIST Cybersecurity Framework
Reporting templates with vulnerability severity matrices.
Implementing Remediation Strategies:
Addressing identified vulnerabilities is as important as finding them. A phased remediation strategy ensures all issues are resolved effectively.
Prioritization:
Critical vulnerabilities, such as exposed secrets or SQL injection risks, must be addressed immediately.
Medium and low severity issues can be scheduled for later sprints.
Post-Fix Testing:
Re-test the application to verify that fixes have resolved the vulnerabilities.
Conduct regression testing to ensure no new issues have been introduced.
Tools Used:
Automated testing suites integrated with CI/CD pipelines
Regression testing tools like PHPUnit for Laravel
Establishing an Ongoing Security Plan:
A one-time security audit is not enough. Continuous monitoring and periodic audits are essential for long-term security.
Ongoing Practices:
Regularly update Laravel and its dependencies.
Implement a robust security training program for developers.
Set up automated alerts for suspicious activities using monitoring tools like Laravel Telescope.
Proactive Measures:
Perform regular backups and disaster recovery testing.
Use Web Application Firewalls (WAFs) to block malicious traffic.
Boost Laravel Security
Laravel is the perfect choice for a wide range of applications. However, businesses need to be aware that securing their Laravel application is an ongoing and circular process. It will require the help of an expert team of Laravel developers. Businesses can take advantage of the Laravel development services we offer at Acquaint Softtech.
We are one of the few firms in Asia that is an official Laravel partner. Hence, besides having the necessary resources, you will also hire Laravel developers who always implement the security best practices.
For example, we never take any shortcuts and continuously monitor the security status of the application. Our applications are developed with a high-security principle of the least privileges. We grant sufficient user permission for the application to function but no more than necessary.
Conclusion
A Laravel security audit is an essential step in building secure and reliable web applications. Regular audits, combined with a security-first mindset, empower businesses to stay ahead of evolving threats and maintain user trust in their applications.
Address Laravel vulnerabilities, ensure compliance, and implement current security practices. This is the ideal method to protect sensitive data and safeguard their applications from cyber threats.
However, an in-depth security audit of a Laravel application requires a comprehensive approach. Hire remote developers from a professional firm like Acquaint Softtech to achieve this.
This approach involves authentication, data protection, input validation, session management, and more. We can significantly enhance the security posture of your Laravel application and protect it against common vulnerabilities and threats. Regular audits and updates are essential to maintaining a secure environment as new threats emerge.
0 notes
Text
The Evolution of PHP: Shaping the Web Development Landscape
In the dynamic world of web development, PHP has emerged as a true cornerstone, shaping the digital landscape over the years. As an open-source, server-side scripting language, PHP has played a pivotal role in enabling developers to create interactive and dynamic websites. Let's take a journey through time to explore how PHP has left an indelible mark on web development.
1. The Birth of PHP (1994)
PHP (Hypertext Preprocessor) came into being in 1994, thanks to Rasmus Lerdorf. Initially, it was a simple set of Common Gateway Interface (CGI) binaries used for tracking visits to his online resume. However, Lerdorf soon recognized its potential for web development, and PHP evolved into a full-fledged scripting language.
2. PHP's Role in the Dynamic Web (Late '90s to Early 2000s)
In the late '90s and early 2000s, PHP began to gain prominence due to its ability to generate dynamic web content. Unlike static HTML, PHP allowed developers to create web pages that could interact with databases, process forms, and provide personalized content to users. This shift towards dynamic websites revolutionized the web development landscape.
3. The Rise of PHP Frameworks (2000s)
As PHP continued to grow in popularity, developers sought ways to streamline and standardize their development processes. This led to the emergence of PHP frameworks like Laravel, Symfony, and CodeIgniter. These frameworks provided structured, reusable code and a wide range of pre-built functionalities, significantly accelerating the development of web applications.
4. PHP and Content Management Systems (CMS) (Early 2000s)
Content Management Systems, such as WordPress, Joomla, and Drupal, rely heavily on PHP. These systems allow users to create and manage websites with ease. PHP's flexibility and extensibility make it the backbone of numerous plugins, themes, and customization options for CMS platforms.
5. E-Commerce and PHP (2000s to Present)
PHP has played a pivotal role in the growth of e-commerce. Platforms like Magento, WooCommerce (built on top of WordPress), and OpenCart are powered by PHP. These platforms provide robust solutions for online retailers, allowing them to create and manage online stores efficiently.
6. PHP's Contribution to Server-Side Scripting (Throughout)
PHP is renowned for its server-side scripting capabilities. It allows web servers to process requests and deliver dynamic content to users' browsers. This server-side scripting is essential for applications that require user authentication, data processing, and real-time interactions.
7. PHP's Ongoing Evolution (Throughout)
PHP has not rested on its laurels. It continues to evolve with each new version, introducing enhanced features, better performance, and improved security. PHP 7, for instance, brought significant speed improvements and reduced memory consumption, making it more efficient and appealing to developers.
8. PHP in the Modern Web (Present)
Today, PHP remains a key player in the web development landscape. It is the foundation of countless websites, applications, and systems. From popular social media platforms to e-commerce giants, PHP continues to power a significant portion of the internet.
9. The PHP Community (Throughout)
One of PHP's strengths is its vibrant and active community. Developers worldwide contribute to its growth by creating libraries, extensions, and documentation. The PHP community fosters knowledge sharing, making it easier for developers to learn and improve their skills.
10. The Future of PHP (Ongoing)
As web technologies continue to evolve, PHP adapts to meet new challenges. Its role in serverless computing, microservices architecture, and cloud-native applications is steadily increasing. The future holds exciting possibilities for PHP in the ever-evolving web development landscape.
In conclusion, PHP's historical journey is interwoven with the evolution of web development itself. From its humble beginnings to its current status as a web development powerhouse, PHP has not only shaped but also continues to influence the internet as we know it. Its versatility, community support, and ongoing evolution ensure that PHP will remain a vital force in web development for years to come.
youtube
#PHP#WebDevelopment#WebDev#Programming#ServerSide#ScriptingLanguage#PHPFrameworks#CMS#ECommerce#WebApplications#PHPCommunity#OpenSource#Technology#Evolution#DigitalLandscape#WebTech#Coding#Youtube
30 notes
·
View notes
Text
Protect Your Laravel Application from Clickjacking Attacks
In today's digital landscape, protecting your web application from various security threats is crucial. One such threat is Clickjacking, an attack that tricks users into clicking on invisible or disguised elements on a webpage. For developers using the Laravel framework, ensuring your application is safe from clickjacking is essential.

In this post, we'll explore what clickjacking is and how to prevent it in your Laravel application. Plus, we’ll show you how to use our free Website Security Checker tool to assess potential vulnerabilities.
What is Clickjacking?
Clickjacking is a type of attack where malicious users embed your webpage into an invisible iframe on their site. The attacker then tricks the victim into clicking on the iframe, which can lead to unwanted actions like changing settings, submitting forms, or even transferring funds without their knowledge.
For example, a button that looks harmless on the surface might trigger an action you didn’t intend to take when clicked in an iframe. This type of attack can be devastating for your users’ privacy and your application’s security.
Preventing Clickjacking in Laravel
Fortunately, Laravel provides a straightforward way to mitigate the risk of clickjacking. Here's how you can do it:
Step 1: Use HTTP Headers
The best way to prevent clickjacking in your Laravel application is by setting proper HTTP headers. You can do this by adding the X-Frame-Options header to your application's response. This header tells the browser not to allow your webpage to be embedded in an iframe.
In Laravel, you can add this header globally by modifying the app/Http/Middleware/VerifyCsrfToken.php file.
Here’s how you can modify the middleware:
// app/Http/Middleware/VerifyCsrfToken.php namespace App\Http\Middleware; use Closure; use Illuminate\Http\Request; class VerifyCsrfToken { public function handle(Request $request, Closure $next) { // Adding X-Frame-Options header to prevent clickjacking response()->headers->set('X-Frame-Options', 'DENY'); return $next($request); } }
With this code, the header X-Frame-Options: DENY ensures that no website can embed your pages in an iframe. If you want to allow only certain websites to embed your content, you can use SAMEORIGIN instead of DENY.
Step 2: Use Content Security Policy (CSP)
Another robust method to prevent clickjacking attacks is by using a Content Security Policy (CSP). Laravel supports CSP through middleware. By setting a strict policy, you can specify exactly which websites are allowed to load your pages in an iframe.
Here’s an example of how you can configure the CSP in your Laravel application:
// app/Http/Middleware/ContentSecurityPolicy.php namespace App\Http\Middleware; use Closure; use Illuminate\Http\Request; class ContentSecurityPolicy { public function handle(Request $request, Closure $next) { // Setting a strict CSP header response()->headers->set('Content-Security-Policy', "frame-ancestors 'none';"); return $next($request); } }
This ensures that no site can embed your application within an iframe.
Why Use Our Free Website Security Checker?
After implementing these preventive measures, it’s important to test your application’s security. Our free Website Security Scanner tool provides a comprehensive vulnerability assessment for your website, including tests for clickjacking and other security issues.
Here’s a screenshot of our free tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Conclusion
Securing your Laravel application against clickjacking attacks is crucial for protecting your users and ensuring your web app remains safe. By following the steps outlined above, you can significantly reduce the risk of such attacks. Additionally, our free Website Security Checker can help you ensure that your site is not vulnerable to clickjacking or any other security issues.
And here’s an example of the vulnerability assessment report generated by our free tool:

An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
By regularly using security tools and following best practices, you can enhance your website’s defenses and maintain a safe browsing environment for your users.
Take Action Today
Start testing your website with our free tool to test website security free and take the first step in protecting your site from clickjacking and other cyber threats.
#Clickjacking#laravel#cyber security#cybersecurity#data security#pentesting#security#the security breach show
3 notes
·
View notes
Text
Best Website Development Company | Accord Tech Solutions
Accord Tech Solutions is the best website development companies. We committed to producing excellent digital experiences that are customized to each client's particular requirements.Our expertise with platforms like WordPress, Laravel, and React.js allows us to create scalable and reliable websites that engage people and yield results.
Our offerings:
Websites for e-commerce Our e-commerce websites are smooth and easy to use, making online purchasing more enjoyable. Our solutions, which include adaptable designs, inventory management, and secure payment gateways, will make your online store stand out and turn visitors into paying customers.
Websites for Travel The goal of our travel website building services is to draw in and keep visitors. To build a comprehensive platform that encourages travel and makes the process easier, we concentrate on incorporating features like reservation systems, itinerary planners, and user evaluations.
Websites for Education Accord Tech Solutions creates educational websites to support virtual education. With the help of our platforms, students of all ages may access and enjoy education more easily thanks to features like interactive material, student portals, and course administration.
Business Websites We are aware of how crucial a robust internet presence is for companies. Our corporate website creation services emphasize functionality and professionalism, making sure that your website engages stakeholders and effectively conveys your brand message.
Websites for newspapers We create dynamic, real-time news websites for newspapers. Our solutions include user engagement tools, multimedia integration, and content management systems that make it simple to update and keep your audience informed.
Custom Website Development Every business is unique, and so are its requirements. Our custom website development services are customized specifically to your needs, providing a personalized approach that ensures your website stands out in a crowded digital landscape.
Our goal at Accord Tech Solutions is to provide outstanding outcomes by using cutting-edge online solutions.
#web development#website development#web development services#web design company#web developing company#e commerce website#ecommerce website development
2 notes
·
View notes
Text
Mastering Of Laravel Development

PinBlooms Technology Pvt Ltd specializes in Laravel development, offering robust and scalable solutions tailored to meet your business needs. Our expert Laravel developers leverage the framework's powerful features to create custom web applications, APIs, and e-commerce platforms that are secure, efficient, and easy to maintain. Whether you're looking to build a new Laravel-based project from scratch or enhance an existing one, PinBlooms Technology Pvt Ltd provides comprehensive development services, including UI/UX design, backend development, integration, and ongoing support. Partner with us to harness the full potential of Laravel and achieve your business goals with confidence and precision.
#Laravel development#Web development company in India#web development company#website development company in india
2 notes
·
View notes
Text

Comparing Laravel And WordPress: Which Platform Reigns Supreme For Your Projects? - Sohojware
Choosing the right platform for your web project can be a daunting task. Two popular options, Laravel and WordPress, cater to distinct needs and offer unique advantages. This in-depth comparison by Sohojware, a leading web development company, will help you decipher which platform reigns supreme for your specific project requirements.
Understanding Laravel
Laravel is a powerful, open-source PHP web framework designed for the rapid development of complex web applications. It enforces a clean and modular architecture, promoting code reusability and maintainability. Laravel offers a rich ecosystem of pre-built functionalities and tools, enabling developers to streamline the development process.
Here's what makes Laravel stand out:
MVC Architecture: Laravel adheres to the Model-View-Controller (MVC) architectural pattern, fostering a well-organized and scalable project structure.
Object-Oriented Programming: By leveraging object-oriented programming (OOP) principles, Laravel promotes code clarity and maintainability.
Built-in Features: Laravel boasts a plethora of built-in features like authentication, authorization, caching, routing, and more, expediting the development process.
Artisan CLI: Artisan, Laravel's powerful command-line interface (CLI), streamlines repetitive tasks like code generation, database migrations, and unit testing.
Security: Laravel prioritizes security by incorporating features like CSRF protection and secure password hashing, safeguarding your web applications.
However, Laravel's complexity might pose a challenge for beginners due to its steeper learning curve compared to WordPress.
Understanding WordPress
WordPress is a free and open-source content management system (CMS) dominating the web. It empowers users with a user-friendly interface and a vast library of plugins and themes, making it ideal for creating websites and blogs without extensive coding knowledge.
Here's why WordPress is a popular choice:
Ease of Use: WordPress boasts an intuitive interface, allowing users to create and manage content effortlessly, even with minimal technical expertise.
Flexibility: A vast repository of themes and plugins extends WordPress's functionality, enabling customization to suit diverse website needs.
SEO Friendliness: WordPress is inherently SEO-friendly, incorporating features that enhance your website's ranking.
Large Community: WordPress enjoys a massive and active community, providing abundant resources, tutorials, and support.
While user-friendly, WordPress might struggle to handle complex functionalities or highly customized web applications.
Choosing Between Laravel and WordPress
The optimal platform hinges on your project's specific requirements. Here's a breakdown to guide your decision:
Laravel is Ideal For:
Complex web applications require a high degree of customization.
Projects demanding powerful security features.
Applications with a large user base or intricate data structures.
Websites require a high level of performance and scalability.
WordPress is Ideal For:
Simple websites and blogs.
Projects with a primary focus on content management.
E-commerce stores with basic product management needs (using WooCommerce plugin).
Websites requiring frequent content updates by non-technical users.
Sohojware, a well-versed web development company in the USA, can assist you in making an informed decision. Our team of Laravel and WordPress experts will assess your project's needs and recommend the most suitable platform to ensure your web project's success.
In conclusion, both Laravel and WordPress are powerful platforms, each catering to distinct project needs. By understanding their strengths and limitations, you can make an informed decision that empowers your web project's success. Sohojware, a leading web development company in the USA, possesses the expertise to guide you through the selection process and deliver exceptional results, regardless of the platform you choose. Let's leverage our experience to bring your web vision to life.
FAQs about Laravel and WordPress Development by Sohojware
1. Which platform is more cost-effective, Laravel or WordPress?
While WordPress itself is free, ongoing maintenance and customization might require development expertise. Laravel projects typically involve developer costs, but these can be offset by the long-term benefits of a custom-built, scalable application. Sohojware can provide cost-effective solutions for both Laravel and WordPress development.
2. Does Sohojware offer support after project completion?
Sohojware offers comprehensive post-development support for both Laravel and WordPress projects. Our maintenance and support plans ensure your website's continued functionality, security, and performance.
3. Can I migrate my existing website from one platform to another?
Website migration is feasible, but the complexity depends on the website's size and architecture. Sohojware's experienced developers can assess the migration feasibility and execute the process seamlessly.
4. How can Sohojware help me with Laravel or WordPress development?
Sohojware offers a comprehensive range of Laravel and WordPress development services, encompassing custom development, theme and plugin creation, integration with third-party applications, and ongoing maintenance.
5. Where can I find more information about Sohojware's Laravel and WordPress development services?
You can find more information about Sohojware's Laravel and WordPress development services by visiting our website at https://sohojware.com/ or contacting our sales team directly. We'd happily discuss your project requirements and recommend the most suitable platform to achieve your goals.
3 notes
·
View notes
Text

#ConnectInfosoftTechnologies#ConnectInfosoft#WebApplications#Laravel#LaravelDevTeam#LaravelDevelopmentTeam#HireLaravelDeveloper#HireLaravelDevelopersinIndia#PHPframework#SaaSApplicationDevelopmentCompany#StaticwebsitedevelopmentcostinUSA#Scalable#Secure#softwaredevelopment#webdevelopment#india#usa#Trending#Trendingshorts#techtrend#reels#ITConsultant#ITCompany#ITIndustry#ITServices#blog#Outsourcing#technology#Innovation#Business
1 note
·
View note