#IoT layers
Explore tagged Tumblr posts
Text
#IoT architecture#IoT architecture layers#IoT layers#Edge computing in IoT#IoT data processing#IoT security#Legacy IoT
0 notes
Text

You know I can’t make it on my own
Put me in a-
Put me in a-
Put me in a movie
More stuff more iots (island of the slaughtered) in that I absolutely adore this ship and this au. It’s nightmare fuel, sure, but it’s also so interesting that I’m stuck in the loop of watching edits and looking at @eavee-ry ‘s art for it.
#nector art!#total drama#iots#island of the slaughtered#I put way too much time into this#lots of layers#sorry if it’s a little overwhelming#tw death#tdi courtney#tdi gwen
568 notes
·
View notes
Text
[GUYS THIS ONE KILLED MY DRAWING TABLET 😭😭😭]
// a little blood , iots
may we offer a Siren in these trying times?

tried not to get lazy with the background/effects but you know how it goes. reached the layer limit and everything
also yeah my tablets straight up dead now lmao. was barely able to export this before it just shit the bed. dead as Noah himself. couldn't even download the time-lapse. sooo here's my Kofi link for commissions/donations if you want ^^" /nf
[please rb thank you♡]
#nqh art#artists on tumblr#art#digital art#total drama#total drama island#island of the slaughtered#noah td#total drama noah#noah of the waters#siren!noah#commissions open#really loved drawing this#super proud of the expression especially#wouldve worked more is not for the whole storage thing but yk#tw blood#cw blood
81 notes
·
View notes
Text
Protecting Patients, Protecting Data: Cybersecurity in Healthcare

The healthcare industry holds some of the most sensitive information imaginable: patient medical records, personal details, insurance information, and more. This makes it a prime target for cyberattacks. A data breach in healthcare can have devastating consequences, impacting patient privacy, disrupting operations, and even endangering lives. Therefore, robust cybersecurity measures are not just recommended in healthcare – they are absolutely essential.
The Stakes are High: Cybersecurity Threats in Healthcare
Healthcare organizations face a range of cyber threats, including:
Ransomware: Attackers encrypt critical systems and data, holding them hostage until a ransom is paid. This can disrupt patient care, delay treatments, and even shut down hospitals.
Phishing: Deceptive emails or messages trick employees into revealing login credentials or downloading malware, providing attackers with access to sensitive data.
Data Breaches: Unauthorized access and exfiltration of patient medical records, leading to privacy violations and potential identity theft.
Malware: Malicious software designed to damage systems, steal data, or disrupt operations.
Insider Threats: Malicious or accidental actions by employees or other insiders that compromise security.
IoT Vulnerabilities: Connected medical devices, while offering many benefits, can also introduce security vulnerabilities if not properly secured.
Building a Strong Defense: Essential Cybersecurity Measures in Healthcare
Protecting patient data and ensuring business continuity requires a multi-layered approach to cybersecurity. Here are some crucial measures:
Risk Assessment and Management: Regularly assessing cybersecurity risks and developing a comprehensive risk management plan is the foundation of a strong security posture.
Data Encryption: Encrypting sensitive data, both in transit and at rest, protects it even if a breach occurs. This is a critical requirement for HIPAA compliance.
Access Control and Authentication: Implementing strong access controls and multi-factor authentication (MFA) ensures that only authorized personnel can access sensitive data.
Network Segmentation: Dividing the network into smaller, isolated segments limits the impact of a breach. If one segment is compromised, the others remain protected.
Firewall Management: Implementing and regularly updating firewalls to control network traffic and block unauthorized access.
Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity and can automatically block malicious traffic.
Antivirus and Anti-malware Software: Deploying robust antivirus and anti-malware software on all endpoints (computers, servers, mobile devices) is essential. Regular updates are crucial.
Regular Security Audits and Vulnerability Assessments: Regularly assessing systems for vulnerabilities and conducting security audits helps identify weaknesses before they can be exploited.
Employee Training and Awareness: Human error is a major factor in many security breaches. Regular cybersecurity awareness training for all healthcare staff is vital. This training should cover topics like phishing awareness, password security, HIPAA compliance, and safe computing practices.
Incident Response Plan: Having a well-defined incident response plan in place allows healthcare organizations to react quickly and effectively to a security incident, minimizing damage and downtime.
IoT Security: Securing connected medical devices and other IoT devices is crucial to prevent them from becoming entry points for attackers. This includes regular updates, strong passwords, and network segmentation.
HIPAA Compliance: A Critical Component
The Health Insurance Portability and Accountability Act (HIPAA) sets strict standards for protecting the privacy and security 1 of patient health information. Healthcare organizations must comply with HIPAA regulations, which include implementing administrative, physical, and technical safeguards.
Xaltius Academy's Cybersecurity Course: Your Partner in Healthcare Security
Protecting patient data and ensuring HIPAA compliance requires specialized knowledge and skills. Xaltius Academy's cybersecurity course provides comprehensive training and equips you with the expertise needed to safeguard healthcare systems and data. Our expert instructors and hands-on labs will prepare you to tackle the unique cybersecurity challenges facing the healthcare industry. Invest in your cybersecurity future and protect the valuable information entrusted to healthcare organizations.
Conclusion
Cybersecurity is not just a technical issue in healthcare; it's a patient safety issue. By implementing these essential cybersecurity measures, fostering a culture of security awareness, and investing in cybersecurity training, healthcare organizations can protect patient data, maintain operational integrity, and ensure the delivery of safe and effective care.
2 notes
·
View notes
Note
with only three episodes left, what do you think is in store for the rest of the volume? personally, i’m having trouble imagining a solid resolution fitting into such a small window. not that i doubt there’s a way to end this volume succinctly—rwby is always throwing curveballs i could’ve never predicted hitting, which i love—but i suppose the hangnail in resolution’s cuticle is that jrwby are all finally facing their lifelong, beaten-in worldview being turned on its head and that seems like the kind of thing (on top of neo’s untold ever after story) that needs more time to be resolved. in which case, ig we’re not looking at a clean wrap up? do you think they end this volume ascending the ever after? escaping back to remnant? (i ask those two questions separately bc i wanna say they might have different answers lol)
as a point of comparison, here’s everything (not necessarily in chronological order) that happened in the last three episodes of V8:
1 - ironwood vs everyone beat down
2 - winter heel face turn completed
3 - met ambrosius + staff of creation rules
4 - magic rules lawyered penny into a flesh body to save her from the virus with a side dish of horrible body horror robot body death scene and holy shit atlas is FALLING.
5 - creation of whacky portals for evacuation to vacuo
6 - emergency evacuation broadcast CANCELLED!
7 - cinder remembers the power of friendship and uses it for evil
8 - cinder recovered the lamp and scored the password and used the last question to spy on team oz which is fucking hysterical by the way, so she knows the entire plan
9 - YANG DIES?
10 - ruby and blake fall too. and neo
11 - the evacuation dumps everyone in a sandstorm so they can’t call for backup and also the exit is one-way (“oh dear. ambrosius \:” love that enthusiasm sir)
12 - HARRIET TRIES TO NUKE MANTLE?
13 - ironwood murders jacques
14 - eleventh hour harriet heel face turn also zeki dies because atlesian tech goons thought the nuke needed to be plugged into the IOT for some reason god bless
15 - PENNY???
16 - and winter becomes the winter maiden
17 - TEAM RWBY TOTAL PARTY KILL!!
18 - jaune also
19 - salem and cinder playing chicken over who is going to blink first like they don’t both already know that it’s going to be salem
20 - ATLAS OBLITERATED FOREVER
that’s a lot of things!
now, it’s a lot easier to set up and execute a dense, tightly-paced climactic spiral of disaster than bring a lot of interconnected emotional crises to satisfying resolution in the same amount of runtime—but on the other hand, V9 has a lot less going on. it doesn’t FEEL that way because the emotional development has been so rich and done so, so well, but there honestly are not that many narrative threads to tie off. basically, the big ones are:
1 - ruby’s emotional crisis
2 - jaune’s corruption
3 - neo
4 - how do we get home?
5 - what do we do once we get there?
compared to the sheer amount of dominoes V8 had to juggle, handling this stuff is a nice little walk.
the key thing to remember—& this has been true for every one of rwby’s climactic sequences and also counts as writing advice—is that none of these major threads are truly discrete. they’re all interwoven with each other and bound together with all the smaller filaments (like the cat’s arc or little’s arc or the framing device of ‘the girl who fell through the world’ and what really went down with alyx and the tree), so you don’t have to resolve them separately and indeed you can’t because it all has to happen at once. what this means, from a writing standpoint, is you layer up and make every scene work towards the resolution of two or three major threads and however many minor filaments you can fit comfortably so that everything is doing work for everything else. if you’re efficient you don’t need a lot of time to pull off a stunning climactic sequence, and efficiency is something rwby has always been very, very good at. this is true even of V1 even though V1 feels laughably inefficient by the standards of V8; which is to say, they started off good and got much better.
the other piece to bear in mind is that V9 is not meant to be self-contained; it is not a character-focused breather volume to let the protagonists heal up before returning to remnant to carry on as they were, it is The Answer. when rwbyjn go home they are not going to return to the story they fell out of at the end of V8. that story is OVER. it ENDED. the final word was checkmate and the world they knew is GONE FOREVER. salem WON. the ever after is an epilogue to that story and the prologue for another; it isn’t building towards a resolution so much as it is building a hook.
(<- remember V3 “beginning of the end” and “end of the beginning”? this story-within-story device is something rwby has utilized before; this show is a singular contiguous narrative in the literal sense, but it’s structured as a trilogy.)
so V9 needs to be a satisfying farewell to the middle book and also make the case for continuing on to the third and final story—which very much works to its benefit here, because the sweeping emotional changes being developed actually SHOULDN’T be resolved. a clean wrap up would critically weaken the narrative structure. the immediate crises need to be realized—there must be a moment of peace, of closing one book and beginning the next; a hopeful glimpse of the story to come, of what it could be—and then they go home. and the new story begins.
in the figurative sense you could call it ascension. in the literal sense, no, i don’t think any of the remnant characters are going to ascend because i don’t think they can (frankly i’m bemused as to why so many people seem to believe otherwise; it seems to me that the cat has made it very clear that ascension is closed to non-afterans). but the idea of ascension? oh, yes, they’re carrying that forward with them.
as for whether they’ll return to remnant—yes. i think the probability that they don’t find their way home by episode ten is zero. how they return is an open question but also not a question at all, because the tree is the question and their answer is the door; this has been spelled out, explicitly, albeit in wonderlandish terms. what we don’t know yet is what this will look like, because the tree is also the blacksmith and the ever after runs on wonderland rules. it’s not going to be literal. (<- unless abstraction is less absurd than the literal option, which is possible given the likelihood that the ever after itself is fictional.)
50 notes
·
View notes
Text
[Media] Practical IoT Hacking
Practical IoT Hacking A comprehensive guide to testing and exploiting IoT systems and devices. Written by expert security researchers, the book covers common threats and a threat modeling framework, security testing methodologies, and passive reconnaissance techniques. Readers will learn how to assess security on all layers of an IoT system, perform VLAN hopping, crack MQTT authentication, abuse UPnP, craft WS-Discovery attacks, and tackle hardware and radio hacking. The book also covers developing an NFC fuzzer, hacking a smart home, and more. The tools and devices used in the book are affordable and readily available, making it a valuable resource for security researchers, IT teams, and hobbyists. Buy online: 🛒 https://amzn.to/3mzbqPG #book #IoT

37 notes
·
View notes
Text
Cross-Platform App Development In Dubai - An Insightful Guide To Follow
In the heart of the United Arab Emirates, the dynamic world of mobile app development is evolving rapidly, and Dubai is at its forefront. This guide delves into the world of cross-platform app development, highlighting its essentials and showcasing leading mobile app development firms in the UAE, like ARS Webtech.
An Insightful Overview About Cross-Platform App Development
Cross-platform app development involves creating mobile applications that run on multiple platforms using a single codebase. This approach contrasts with traditional native app development, which requires writing separate code for each platform, such as Java or Kotlin for Android and Swift or Objective-C for iOS.
Benefits of Cross-Platform App Development By Mobile App Development Companies UAE
Code Reusability: Developers can write and manage code that works across various platforms, reducing development time and effort.
Cost and Time Efficiency: Faster and more economical than developing individual native apps, it simplifies the entire development cycle.
Wider Market Reach: A single app can target different platforms, expanding market reach.
Consistent User Experience: Cross-platform frameworks support maintaining a consistent experience across platforms.
Faster Deployment and Updates: Facilitates simultaneous feature release across all platforms.
Popular Cross-Platform Development Frameworks
Flutter: Known for creating visually appealing apps, it's a strong choice for businesses in Dubai.
React Native: Supported by Facebook, it allows developers to build mobile apps using React and JavaScript, known for its flexibility and seamless integration.
Best Practices In Cross-Platform App Development
Prioritize User Experience: Ensuring apps function flawlessly with an intuitive interface is crucial.
Security Considerations: Especially important in sectors like healthcare and e-commerce, robust security measures are essential.
Scalability: The app should accommodate increased user traffic and additional features as the business grows.
Regular Updates and Maintenance: Ensuring the app remains compatible with the latest operating systems and user expectations.
Integration of Emerging Technologies: Incorporating AI, IoT, 5G connectivity, and machine learning enhances user experiences and contributes to Dubai's smart city initiatives.
Blockchain for Increased Security: Integrating blockchain technologies can add an extra layer of security, particularly in sensitive industries.
Conclusion
Cross-platform app development is a strategic choice for businesses in Dubai looking to maximize their digital presence. Companies like ARS Webtech are at the forefront of this movement, driving innovation and excellence in the mobile app development scene.
FAQs
1. Which frameworks are commonly used for cross-platform app development in Dubai?
Flutter and React Native are two prominent frameworks. Flutter is known for its visually stunning apps, while React Native offers flexibility and seamless integration.
2. How do mobile app development companies in Dubai prioritize user experience in cross-platform apps?
User experience is a top priority, ensuring consistent and delightful interfaces across devices.
3. How to choose between Flutter and React Native?
The choice depends on specific project requirements, design preferences, development speed, and existing tech stacks.
For further guidance or to start your cross-platform app development journey, contact ARS Webtech at +971585840413.
#ios app development#mobile app company#mobile app developer company#android#digital marketing#mobile app#digital marketing agency#digital marketing company#digital marketing strategy#digital marketing services
2 notes
·
View notes
Text
Technology and Our World: How Innovation is Reshaping Business, Economy, and Everyday Life

Technology is no longer just a tool—it’s the driving force behind global transformation. From AI-driven automation to smart cities and digital finance, innovation is redefining industries, enhancing efficiency, and revolutionizing human interactions.
For businesses, leveraging cutting-edge technology is no longer optional; it’s a necessity to stay competitive, scale operations, and future-proof success. At Dynamic ORD, we help companies integrate AI, automation, and digital transformation strategies to thrive in an increasingly connected world.
🚀 Want to stay ahead of digital trends? Read more on our blog.
The Power of Technology: A Global Revolution
From high-speed connectivity to data-driven decision-making, the impact of technology is reshaping every sector:
1. AI & Automation: The Future of Efficiency
Artificial intelligence (AI) and automation are streamlining operations, reducing costs, and optimizing workflows like never before. Businesses utilizing AI-powered tools enjoy: ✅ Faster decision-making – AI analyzes complex data in seconds. ✅ Improved customer experiences – AI-driven chatbots and personalization enhance engagement. ✅ Operational efficiency – Automation eliminates repetitive tasks, increasing productivity.
🔹 The Solution: Companies must integrate machine learning, AI-driven analytics, and automation to scale efficiently.
💡 Discover how AI can elevate your business: Learn more.
2. Digital Transformation in Business & Economy
Businesses that fail to embrace digital transformation risk falling behind. Technology is revolutionizing: ✅ E-commerce & Retail – Online marketplaces are thriving with AI-powered recommendations. ✅ Finance & Cryptocurrency – Digital payments and blockchain redefine transactions. ✅ Healthcare & Telemedicine – AI diagnostics and remote patient monitoring enhance healthcare access.
🔹 The Solution: Companies must embrace cloud computing, digital payment systems, and scalable SaaS solutions to enhance agility and profitability.
📈 Looking to integrate digital transformation? Get a quote today.
3. Smart Cities & IoT: The Rise of Hyper-Connected Living
The Internet of Things (IoT) is reshaping urban development, creating smart cities that improve sustainability, security, and efficiency. Emerging trends include: ✅ Smart infrastructure – AI-powered energy grids and autonomous transportation. ✅ IoT-driven homes & workplaces – Automated security, smart appliances, and AI assistants. ✅ Sustainable tech – AI-powered solutions optimizing waste management and green energy.
🔹 The Solution: Businesses and governments must leverage IoT, big data, and cloud-based automation to drive sustainable and efficient urban development.
🌍 Want to explore smart technology solutions? Book a consultation today.
The Role of Cybersecurity in a Hyper-Connected World
With the rise of technology, cybersecurity threats are at an all-time high. Businesses and individuals must adopt: ✔ AI-powered threat detection to prevent cyberattacks. ✔ Zero-trust security models to protect sensitive data. ✔ Blockchain-based verification for secure transactions.
🔹 The Solution: Implementing advanced encryption, AI-driven cybersecurity solutions, and multi-layered authentication is crucial for protecting digital assets.
🔍 Still have questions? Visit our FAQ section.
Why Choose Dynamic ORD for Your Digital Transformation?
At Dynamic ORD, we help businesses harness the latest technology trends to create scalable, secure, and future-ready solutions.
✔ AI & Automation Strategies – Drive efficiency and innovation. ✔ Advanced Cybersecurity Solutions – Protect data and digital assets. ✔ Cloud & SaaS Integration – Optimize workflows with high-performance cloud solutions. ✔ SEO-Driven Digital Growth – Elevate online presence with expert strategies.
📖 See how we’ve helped others succeed: Read our testimonials.
The Future is Now: Embrace the Digital Revolution
Technology is reshaping our world, and businesses that adapt will lead the future. Whether it’s AI, digital transformation, cybersecurity, or smart automation, staying ahead of the curve is essential for sustainable success.
📈 Is your business ready for the future? Let’s build a high-impact, tech-driven strategy together.
💼 Explore our digital transformation packages today: Benefit from our exclusive solutions.
1 note
·
View note
Text
Innovations in Fire Suppression Technology
Fire safety continues to evolve as industries demand more efficient and environmentally friendly solutions to mitigate fire hazards. In advancements in fire suppression technology are transforming how businesses protect lives and property. These innovations address concerns such as rapid fire detection, automatic suppression, and environmentally sustainable practices. With the increasing adoption of modern fire suppression systems, companies are better equipped to handle fire-related risks effectively.

Smart Fire Suppression Systems
One of the significant advancements in 2023 is the development of smart fire suppression systems that integrate artificial intelligence (AI) and the Internet of Things (IoT). These systems can predict fire hazards based on data analytics and real-time monitoring. Unlike traditional fire suppression methods, smart systems continuously analyze temperature, humidity, and smoke patterns, enabling businesses to respond proactively to potential threats.
Automated response mechanisms in these systems ensure quicker activation, reducing fire damage and minimizing downtime in commercial establishments. Additionally, businesses that integrate these intelligent fire suppression systems benefit from remote monitoring capabilities, allowing for real-time alerts and system diagnostics.
Water Mist Systems for Enhanced Safety
Water mist technology is gaining popularity due to its efficiency in fire control while minimizing water damage. Traditional sprinkler systems often release excessive amounts of water, causing collateral damage, particularly in data centers, hospitals, and museums. The latest fire suppression system innovations feature advanced water mist technology that utilizes high-pressure mist to suppress fires rapidly with minimal impact on surrounding assets.
Water mist systems work by cooling the flames and displacing oxygen, effectively preventing fire spread. These systems are increasingly preferred in commercial and industrial settings where sensitive equipment is present. Moreover, they consume significantly less water compared to conventional systems, making them an environmentally sustainable choice.
Clean Agent Suppression Systems
With growing concerns over environmental sustainability, clean agent fire suppression systems have emerged as a preferred alternative to traditional chemical-based solutions. These systems use non-toxic, non-corrosive gases such as FM-200 and Novec 1230 to suppress fires without leaving residue or damaging sensitive equipment.
The demand for clean agent systems is particularly high in the IT sector, healthcare facilities, and archival storage areas where traditional extinguishing methods might cause irreparable harm. Additionally, these systems comply with environmental regulations, making them a viable solution for companies seeking to reduce their carbon footprint while ensuring fire safety.
Hybrid Fire Suppression Technologies
Hybrid fire suppression systems, which combine different suppression agents for optimized efficiency, are gaining traction in various industries. These systems integrate multiple suppression mechanisms, such as combining water mist with clean agents or using inert gases with advanced detection technologies.
Hybrid suppression solutions are particularly beneficial in industries where traditional systems fall short. For instance, in high-risk environments such as oil refineries, chemical plants, and manufacturing facilities, these systems ensure that fire threats are mitigated through a multi-layered approach. Businesses adopting these hybrid fire suppression technologies benefit from enhanced protection with minimal risk of equipment damage or operational disruption.
Eco-Friendly Fire Suppression Solutions
Sustainability has become a core focus in the fire suppression industry, driving the development of environmentally friendly fire suppression solutions. Traditional fire suppression agents, such as Halon, have been phased out due to their adverse environmental impact. In 2023, businesses are shifting toward solutions that comply with global environmental standards.
Innovative fire suppression system designs now incorporate eco-friendly agents that have zero ozone depletion potential (ODP) and low global warming potential (GWP). These systems not only meet regulatory compliance but also align with corporate sustainability initiatives. As industries continue to prioritize green technologies, eco-friendly fire suppression solutions are expected to become the standard in fire safety.
High-Speed Fire Detection and Suppression
The rapid evolution of fire detection technology has contributed to significant improvements in fire suppression response times. High-speed fire detection systems utilize infrared and ultraviolet sensors to identify fire ignition within milliseconds. When integrated with automated suppression systems, these technologies help prevent extensive fire damage in high-risk areas such as industrial plants and data centers.
Modern fire suppression systems leverage cutting-edge detection methods, including fiber-optic sensing and thermal imaging. These advancements enable businesses to detect and suppress fires at unprecedented speeds, reducing the likelihood of catastrophic losses.
Conclusion
Fire suppression technology is advancing rapidly, offering businesses more efficient and sustainable solutions to enhance fire safety. From smart suppression systems powered by AI to eco-friendly clean agents and high-speed detection mechanisms, these innovations are revolutionizing fire safety protocols across industries.
As businesses continue to adopt cutting-edge fire suppression system solutions, the focus remains on improving response times, minimizing environmental impact, and ensuring comprehensive fire protection. The latest advancements in 2023 pave the way for safer, more reliable, and highly efficient fire suppression strategies, ultimately safeguarding both lives and valuable assets.
0 notes
Text
The Future of IoT Services: Innovations, Technologies & Growth Opportunities
The Internet of Things (IoT) is evolving rapidly, transforming industries and opening new opportunities for developers, service providers, decision-makers, and market leaders. With smart connectivity, automation, and AI integration, IoT is becoming an essential part of various sectors, from healthcare and manufacturing to smart cities and retail. This article explores the latest trends, emerging technologies, and key aspects that anyone entering this field should know.
Latest Trends Transforming IoT Services
IoT is rapidly evolving, bringing groundbreaking innovations that enhance automation, security, and data-driven decision-making. Here are the key trends shaping the future of IoT:
1. AI-Enhanced IoT: Making Smart Systems Smarter
Artificial Intelligence (AI) is revolutionizing IoT by enabling real-time analytics, predictive maintenance, and autonomous decision-making. AI-powered IoT devices can process data more efficiently, optimize workflows, and reduce downtime. Smart factories, healthcare monitoring, and intelligent traffic systems benefit from AI-driven IoT solutions.
2. Edge Computing: Real-Time Data Processing at the Source
Latency has always been a challenge in IoT networks. Edge computing reduces dependence on centralized cloud servers by processing data closer to the source. This results in faster decision-making, improved security, and cost savings in applications like autonomous vehicles, industrial automation, and remote healthcare monitoring.
3. 5G Integration: Expanding the Potential of IoT
5G is a game-changer for IoT. It offers ultra-fast connectivity, low latency, and increased bandwidth, allowing seamless communication between billions of connected devices. Applications such as smart grids, smart cities, and telemedicine will see exponential growth with 5G-enabled IoT solutions.
4. IoT Security and Zero Trust Architecture
With the growing number of connected devices, security remains a top priority. Zero Trust Architecture (ZTA) and Blockchain-based security frameworks ensure encrypted communication, secure device authentication, and protection against cyber threats. Companies are investing in multi-layered security solutions to safeguard IoT ecosystems.
5. Digital Twin Technology: Bridging the Physical and Virtual Worlds
Digital Twins create virtual replicas of physical assets, enabling real-time monitoring, simulation, and predictive analytics. Industries like manufacturing, logistics, and healthcare use this technology to improve efficiency, reduce maintenance costs, and enhance product development.
Key Technologies Driving IoT Growth
1. LPWANs (Low-Power Wide-Area Networks) for Scalable IoT Solutions
LPWANs like LoRaWAN, Sigfox, and NB-IoT enable long-range communication with minimal power consumption. These networks are ideal for large-scale applications such as smart agriculture, environmental monitoring, and industrial asset tracking.
2. Blockchain Integration: Securing IoT Networks
Blockchain technology enhances IoT security by providing decentralized data storage, ensuring transparency, and preventing data breaches. It is being increasingly adopted in supply chain management, smart contracts, and secure data transactions.
3. Next-Gen Smart Sensors: Improving Data Collection & Analysis
Modern smart sensors are designed to collect, process, and analyze data more efficiently. With AI-powered self-calibration and real-time feedback mechanisms, these sensors are used in precision agriculture, smart homes, and automated quality control.
4. IoT-Specific Operating Systems for Better Performance
Traditional operating systems are not optimized for IoT applications. New lightweight and secure IoT-specific operating systems like Zephyr, RIOT, and FreeRTOS are enhancing device performance while minimizing energy consumption.
5. Human-Machine Interaction (HMI) & IoT
The integration of Augmented Reality (AR), Virtual Reality (VR), and advanced voice recognition is making IoT solutions more interactive. AI-powered virtual assistants, gesture-based controls, and AR-driven maintenance tools are transforming how humans interact with connected devices.
A Comprehensive Guide for IoT Enthusiasts
For those looking to step into the IoT field, mastering essential technologies and strategies is crucial. Here’s how to get started:
Understand IoT Architecture: Learn about hardware, networking, cloud computing, and device-to-device communication protocols.
Prioritize Security from Day One: Implement encryption, authentication, and secure coding practices in every IoT solution.
Select the Right Connectivity Protocol: Depending on the use case, choose between MQTT, CoAP, Zigbee, or other IoT communication protocols.
Leverage AI & Big Data: Use machine learning models to extract insights, automate tasks, and enhance predictive data analytics.
Ensure Regulatory Compliance: Stay informed about IoT-specific legal frameworks like GDPR, HIPAA, and industry-specific security guidelines.
The Road Ahead for IoT Services
The rapid evolution of IoT is reshaping industries, unlocking new possibilities for connectivity, automation, and intelligence. With advancements in AI-driven analytics, edge computing, 5G, and enhanced security frameworks, IoT is becoming more robust, efficient, and secure. As digital twin technology, blockchain integration, and next-generation sensors continue to gain traction, the potential applications of IoT will only expand further.
For those looking to thrive in this space, staying informed about emerging technologies, prioritizing security, and choosing the right connectivity solutions are essential. Whether it's optimizing industrial operations, enhancing healthcare systems, or enabling smarter cities, IOT services will play a pivotal role in the digital transformation of the future. Embracing innovation and adaptability will be the key to success in this ever-evolving ecosystem.
As IoT continues to evolve, businesses and developers must stay ahead by embracing IOT services that offer secure, scalable, and innovative solutions. From AI-driven automation to 5G-powered smart systems, the future of IoT is filled with limitless possibilities.
Frequently Asked Questions (FAQs)
1. What are the most critical factors when choosing an IoT service provider?
The key factors include security, scalability, compatibility with existing systems, cloud integration, and customer support.
2. How does IoT enhance operational efficiency?
IoT automates data collection, enables predictive maintenance, and provides real-time analytics, helping organizations optimize resources and reduce costs.
3. What role does AI play in IoT services?
AI enhances IoT by enabling real-time decision-making, automating processes, improving security, and optimizing data analytics for better outcomes.
4. How do IoT networks ensure data privacy?
IoT networks use encryption, tokenization, secure device authentication, and decentralized blockchain systems to protect user data.
5. What are the best connectivity options for IoT applications?
The choice depends on the use case: Wi-Fi and Bluetooth for short-range, LPWAN for large-scale applications, and 5G for ultra-fast, low-latency IoT solutions.
#EmergingIOTtechnologies#AI in IoT#Edge computing in IoT#5G and IoT growth#IoT cybersecurity solutions#DigitaltwinsinIoT#iot#iot solutions
0 notes
Text
Next-Gen Cable Machinery: Advancements Driving the Industry Forward

The cable manufacturing industry is evolving rapidly, driven by technological advancements, automation, and the increasing demand for high-quality, durable cables. From telecommunications to power distribution, industries worldwide rely on efficient and innovative cable production solutions.
With the rise of Industry 4.0, smart manufacturing, and sustainability, next-generation cable machinery is transforming production processes, enhancing efficiency, and improving product quality. In this article, we explore the latest advancements in cable machinery and how they are shaping the future of the industry.
Cable Machinery Manufacturers
1. Automation and Smart Manufacturing
Automation has revolutionized cable production, minimizing human intervention while improving speed and precision. Next-gen cable machinery integrates Artificial Intelligence (AI), Internet of Things (IoT), and Machine Learning (ML) to streamline operations and optimize performance.
Key Innovations in Automation:
✅ AI-Driven Quality Control: AI-powered sensors and cameras detect defects in real-time, reducing waste and ensuring consistent quality. ✅ IoT-Enabled Monitoring: Smart machines can collect data, monitor performance, and send alerts for maintenance, preventing downtime. ✅ Robotics in Cable Assembly: Automated robotic arms enhance precision in cutting, stripping, and assembling cables.
By leveraging automation, manufacturers can achieve higher efficiency, lower production costs, and improved product consistency.
2. High-Speed Extrusion Technology
Extrusion is a critical process in cable manufacturing, involving the coating of conductors with insulation and protective layers. Next-generation high-speed extrusion machines are revolutionizing the process with:
🔹 Energy-efficient heating systems that reduce power consumption. 🔹 Advanced cooling mechanisms for better insulation adhesion. 🔹 Multi-layer extrusion technology for producing complex cable structures in a single pass.
These advancements enhance productivity, reduce material waste, and improve cable durability, making them essential for modern production lines.
Wire Machinery Manufacturers
3. Precision Wire Drawing and Stranding Techniques
Wire drawing and stranding are fundamental processes in cable manufacturing, determining the strength and conductivity of the final product. The latest innovations include:
🔹 Microfine wire drawing: Enables ultra-thin yet highly conductive wires for specialized applications like 5G and aerospace. 🔹 Torsion-free stranding technology: Ensures uniform strand distribution, reducing internal stress and enhancing cable flexibility. 🔹 Automatic tension control systems: Optimize wire tension, preventing breakage and improving consistency.
These developments contribute to higher-quality cables with superior electrical performance and durability.
4. Sustainable and Eco-Friendly Manufacturing
Sustainability is a major focus in cable production, with manufacturers adopting green technologies to reduce environmental impact. Innovations in this space include:
✅ Recyclable and biodegradable insulation materials that replace traditional PVC and polyethylene. ✅ Energy-efficient machinery that consumes less power while maintaining high output. ✅ Closed-loop water cooling systems that minimize water wastage in extrusion and cooling processes.
By embracing eco-friendly practices, cable manufacturers not only reduce carbon footprints but also comply with global sustainability standards.
Cable Machinery Manufacturers
5. Digital Twin Technology in Cable Manufacturing
A Digital Twin is a virtual replica of a physical manufacturing process, enabling real-time monitoring and simulation of production scenarios. This innovation is transforming the cable machinery industry by:
🔹 Predicting machine failures through AI-driven diagnostics. 🔹 Optimizing production parameters before implementing changes in real-time operations. 🔹 Enhancing training and safety by simulating complex processes before execution.
By integrating Digital Twin technology, manufacturers can improve operational efficiency, reduce downtime, and enhance overall productivity.
6. Advanced Testing and Quality Assurance Systems
Next-gen cable machinery comes equipped with state-of-the-art testing and inspection systems to meet strict industry standards. Some of the latest innovations include:
✅ High-speed spark testers that instantly detect insulation defects. ✅ Real-time X-ray and laser measurement systems for precise diameter and thickness control. ✅ Automated tensile and bending tests to ensure flexibility and durability.
These advancements guarantee high-quality, defect-free cables that meet global safety and performance regulations.
7. The Rise of Smart Factory Integration
Modern cable manufacturing facilities are evolving into smart factories, where interconnected machines and data-driven processes enhance production efficiency. Key aspects of smart factory integration include:
🔹 Cloud-based data analytics for real-time decision-making. 🔹 Automated material handling systems for seamless production flow. 🔹 Cybersecurity enhancements to protect manufacturing data from digital threats.
With smart factories, cable manufacturers can increase productivity, reduce operational costs, and improve product traceability.
Wire Machinery Manufacturers
Conclusion
The future of cable manufacturing is being shaped by automation, digitalization, sustainability, and smart technologies. With next-generation cable machinery, manufacturers can produce stronger, more efficient, and environmentally friendly cables while maintaining cost-effectiveness and high quality.
As the demand for high-performance cables continues to grow, embracing these advancements will be essential for staying competitive in the industry. Now is the time to invest in next-gen cable machinery to drive innovation and efficiency forward.
🔹 Is your cable manufacturing process ready for the future? Explore the latest advancements today!
#Wire Machine Manufacturers#Wire Machinery Manufacturers#Cable Machinery Manufacturers#Cable Making Machine Manufacturers#Wire Making Machine Manufacturers
0 notes
Link
0 notes
Text
MLCC Market Trends 2034: How 5G, IoT, and ADAS Are Reshaping the Industry

The global Multilayer Ceramic Capacitor (MLCC) market is witnessing significant growth, driven by advancements in consumer electronics, 5G technology, electric vehicles (EVs), and renewable energy. MLCCs, known for their high capacitance and compact size, are widely used in various applications, making them an essential component in modern electronic devices.
In 2023, the MLCC market was valued at US$ 13.0 billion and is projected to reach US$ 28.7 billion by 2034, growing at a CAGR of 7.5%. Leading manufacturers such as Murata, Samsung Electro-Mechanics, and Taiyo Yuden dominate the market, with China, South Korea, and Japan being key production hubs.
Key Market Drivers
1. Expanding Consumer Electronics Industry
The demand for MLCCs is surging due to the rising popularity of portable consumer electronics like smartphones, laptops, and wearable devices. The miniaturization trend in electronics has further propelled the need for compact yet high-performance capacitors.
For instance, Taiyo Yuden launched new low-profile MLCCs (AWK105 BJ474MN and PWK105 C6474MN) in April 2021, specifically designed for smartphones and wearables to improve power supply efficiency.
2. Growth of Electric Vehicles (EVs)
As the world transitions to sustainable transportation, MLCCs play a vital role in electric vehicles. They are used to smooth voltage fluctuations, filter noise, and protect semiconductors in EV drive systems.
According to the International Energy Agency (IEA), global EV sales reached 14 million units in 2023, marking a 35% YoY growth. With this surge, MLCC manufacturers are focusing on developing high-performance capacitors to meet the demands of the EV sector.
3. 5G Infrastructure Expansion
The rollout of 5G technology has significantly boosted MLCC demand. These capacitors are crucial for 5G base stations, smartphones, and network infrastructure due to their ability to handle high frequencies and temperature variations efficiently.
4. Rise in IoT and Industrial Automation
With the expansion of IoT devices and smart industrial applications, MLCCs are in high demand for embedded systems, sensors, and control circuits. Their reliability and efficiency make them indispensable for industrial automation and AI-driven applications.
Read More: https://www.transparencymarketresearch.com/multi-layer-ceramic-capacitor-market.html
Market Segmentation Analysis
1. By Dielectric Type
X7R (29.9% market share in 2023): Preferred for automotive and industrial applications due to its balanced capacitance stability and temperature resistance (-55°C to +125°C).
Other types: C0G (NP0), X8G, U2J, X5R, Y5V, X7S, and others.
2. By Voltage
Low Voltage (Up to 75V) - 45.5% share in 2023: Used in consumer electronics, IoT, and telecommunications.
Medium Voltage (100-630V): Suitable for industrial and medical applications.
High Voltage (Above 1kV): Essential for power grids, automotive, and defense applications.
Regional Market Insights
Asia-Pacific: The Leading MLCC Hub
Asia-Pacific accounted for 44.3% of the MLCC market in 2023, with China, Japan, South Korea, and Taiwan dominating the production landscape. The region benefits from a robust electronics manufacturing ecosystem, strong supply chains, and increasing consumer electronics consumption.
North America: Technological Innovation Hub
North America holds a 21.1% share, driven by its advanced semiconductor industry, strong automotive sector, and increasing automation. The U.S. leads the region in MLCC innovation and production, particularly for high-performance capacitors used in aerospace and defense.
Europe: Growth in EV and Industrial Sectors
Europe is witnessing steady MLCC market growth, fueled by the rising adoption of electric vehicles and industrial automation. The region’s stringent environmental regulations are also pushing manufacturers to develop eco-friendly capacitor solutions.
Competitive Landscape & Key Players
The MLCC market is highly competitive, with major companies focusing on R&D, strategic collaborations, and capacity expansion to maintain market dominance.
Key Players:
Murata Manufacturing Co., Ltd.
Samsung Electro-Mechanics
Taiyo Yuden Co., Ltd.
Kyocera Corporation
Yageo Corporation
TDK Corporation
These companies are investing in next-generation MLCCs with enhanced temperature stability, high capacitance, and improved reliability for critical applications.
Future Outlook (2024-2034)
The MLCC market is expected to witness robust growth, driven by:
The increasing integration of AI and IoT technologies
Expansion of 5G networks and telecommunications infrastructure
Rising demand from electric vehicles and industrial automation
Continuous advancements in miniaturization and high-capacitance MLCCs
Manufacturers are expected to focus on expanding production capabilities, diversifying supply chains, and investing in R&D to stay ahead in this competitive market.
Contact Us: Transparency Market Research Inc. CORPORATE HEADQUARTER DOWNTOWN, 1000 N. West Street, Suite 1200, Wilmington, Delaware 19801 USA Tel: +1-518-618-1030 USA - Canada Toll Free: 866-552-3453 Website: https://www.transparencymarketresearch.com Email: [email protected]
0 notes
Text
Cybersecurity Measures for Disaster Response Systems: A Comprehensive Analysis
Introduction
In an era where digital technologies are integral to disaster response, cybersecurity has become a critical concern. Disaster response systems rely on real-time data exchange, cloud computing, and interconnected networks to coordinate emergency services efficiently. However, these systems are increasingly vulnerable to cyber threats, including data breaches, ransomware attacks, and infrastructure sabotage. Strengthening cybersecurity in disaster response ensures operational continuity, safeguards sensitive information, and enhances resilience against cyberattacks.
This paper explores the role of cybersecurity in disaster response systems, key security measures, challenges, and real-world applications. Furthermore, it highlights the contributions of Telkom University in advancing research and fostering entrepreneurship in cybersecurity through specialized laboratories.
The Role of Cybersecurity in Disaster Response Systems
Data Protection and Privacy Disaster response systems handle vast amounts of sensitive data, including personal records, medical histories, and location tracking. Cybersecurity measures such as encryption and access controls ensure that this data remains secure and is only accessible to authorized personnel.
Network Security and Resilience During emergencies, communication networks must remain operational. Cybersecurity measures, including firewalls, intrusion detection systems, and redundant network configurations, help prevent cyberattacks that could disrupt emergency communication.
Secure Cloud and IoT Integration Cloud computing and IoT devices enhance disaster monitoring and response capabilities. Implementing cybersecurity protocols, such as multi-factor authentication and encrypted cloud storage, ensures these technologies function securely without vulnerabilities.
Real-Time Threat Detection and Response Cyber threats evolve rapidly, making real-time threat detection essential for disaster response systems. AI-driven cybersecurity solutions analyze network traffic, identify anomalies, and respond to threats before they cause damage.
Disaster Recovery and Business Continuity Planning Cyber incidents can paralyze disaster response operations. Implementing robust disaster recovery strategies, including backup systems and incident response protocols, ensures continuity in case of cyberattacks.
Key Cybersecurity Measures for Disaster Response Systems
Encryption and Secure Data Transmission Encrypting data during transmission and storage prevents unauthorized access. Secure communication channels, such as Virtual Private Networks (VPNs), enhance data confidentiality.
Multi-Factor Authentication (MFA) Implementing MFA adds an extra layer of security, ensuring only authorized users can access critical disaster response platforms.
Regular Security Audits and Penetration Testing Conducting frequent cybersecurity assessments helps identify vulnerabilities and improve system defenses before a cyberattack occurs.
Cybersecurity Awareness and Training Educating personnel on cyber threats, phishing attacks, and best security practices minimizes human-related security risks.
AI-Driven Cyber Threat Intelligence Utilizing AI-powered cybersecurity tools enhances threat detection, response automation, and predictive analytics for disaster response systems.
Challenges in Implementing Cybersecurity for Disaster Response
Limited Resources and Budget Constraints Many disaster response organizations struggle with funding cybersecurity initiatives, making it difficult to implement robust security measures.
Balancing Security and Accessibility Disaster response systems must be both secure and accessible to multiple stakeholders, including emergency responders, government agencies, and NGOs. Striking the right balance between security and usability remains a challenge.
Evolving Cyber Threat Landscape Cyber threats constantly evolve, requiring continuous updates and adaptive cybersecurity strategies to counter new attack methods.
Lack of Standardized Cybersecurity Frameworks Many countries and organizations lack standardized cybersecurity protocols for disaster response, leading to inconsistencies in security implementation.
Dependency on Third-Party Technologies Reliance on cloud providers, software vendors, and third-party IT services increases cybersecurity risks if these entities are compromised.
Real-World Applications of Cybersecurity in Disaster Response
Securing Emergency Communication Networks Governments and humanitarian organizations deploy encrypted communication systems to prevent cyber interference in emergency operations.
Protecting Smart Infrastructure and IoT Systems Cybersecurity measures secure IoT-powered flood monitoring, earthquake sensors, and other smart disaster response systems from hacking attempts.
Blockchain for Secure Disaster Aid Distribution Blockchain technology ensures transparency and security in disaster aid distribution, preventing fraud and mismanagement.
Cyber Resilience in Healthcare and Medical Emergency Systems Hospitals and emergency healthcare systems integrate cybersecurity frameworks to protect patient data and medical infrastructure from cyber threats.
AI-Enhanced Cybersecurity for National Disaster Agencies AI-driven cybersecurity tools assist national disaster management agencies in monitoring and mitigating cyber threats in real-time.
Telkom University’s Contributions to Cybersecurity Research
Telkom University is actively engaged in cybersecurity research, focusing on disaster response security solutions. Through its cutting-edge laboratories, researchers develop AI-driven cyber threat intelligence, secure communication systems, and blockchain-based security frameworks. Additionally, Telkom University fosters entrepreneurship by supporting cybersecurity startups that develop innovative security solutions for disaster resilience.
Conclusion
Cybersecurity is a fundamental component of modern disaster response systems, ensuring the protection of critical infrastructure, sensitive data, and emergency networks. While challenges such as budget constraints and evolving threats persist, advancements in AI, blockchain, and secure cloud computing offer promising solutions. Institutions like Telkom University play a pivotal role in driving cybersecurity innovation, fostering entrepreneurship, and conducting research in state-of-the-art laboratories to enhance disaster resilience. Strengthening cybersecurity measures in disaster response systems ultimately safeguards lives, infrastructure, and critical operations in times of crisis.
#best private university#kampus swasta terbaik#university#deep learning#data science#machine learning
0 notes
Text
Explore how ADF integrates with Azure Synapse for big data processing.
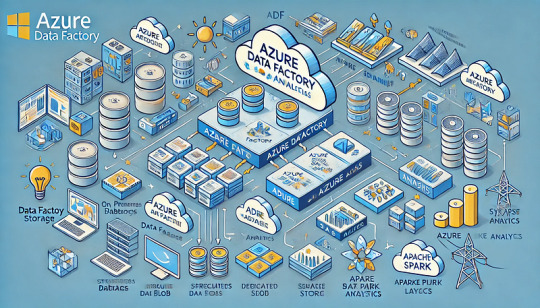
How Azure Data Factory (ADF) Integrates with Azure Synapse for Big Data Processing
Azure Data Factory (ADF) and Azure Synapse Analytics form a powerful combination for handling big data workloads in the cloud.
ADF enables data ingestion, transformation, and orchestration, while Azure Synapse provides high-performance analytics and data warehousing. Their integration supports massive-scale data processing, making them ideal for big data applications like ETL pipelines, machine learning, and real-time analytics. Key Aspects of ADF and Azure Synapse Integration for Big Data Processing
Data Ingestion at Scale ADF acts as the ingestion layer, allowing seamless data movement into Azure Synapse from multiple structured and unstructured sources, including: Cloud Storage: Azure Blob Storage, Amazon S3, Google
Cloud Storage On-Premises Databases: SQL Server, Oracle, MySQL, PostgreSQL Streaming Data Sources: Azure Event Hubs, IoT Hub, Kafka
SaaS Applications: Salesforce, SAP, Google Analytics 🚀 ADF’s parallel processing capabilities and built-in connectors make ingestion highly scalable and efficient.
2. Transforming Big Data with ETL/ELT ADF enables large-scale transformations using two primary approaches: ETL (Extract, Transform, Load): Data is transformed in ADF’s Mapping Data Flows before loading into Synapse.
ELT (Extract, Load, Transform): Raw data is loaded into Synapse, where transformation occurs using SQL scripts or Apache Spark pools within Synapse.
🔹 Use Case: Cleaning and aggregating billions of rows from multiple sources before running machine learning models.
3. Scalable Data Processing with Azure Synapse Azure Synapse provides powerful data processing features: Dedicated SQL Pools: Optimized for high-performance queries on structured big data.
Serverless SQL Pools: Enables ad-hoc queries without provisioning resources.
Apache Spark Pools: Runs distributed big data workloads using Spark.
💡 ADF pipelines can orchestrate Spark-based processing in Synapse for large-scale transformations.
4. Automating and Orchestrating Data Pipelines ADF provides pipeline orchestration for complex workflows by: Automating data movement between storage and Synapse.
Scheduling incremental or full data loads for efficiency. Integrating with Azure Functions, Databricks, and Logic Apps for extended capabilities.
⚙️ Example: ADF can trigger data processing in Synapse when new files arrive in Azure Data Lake.
5. Real-Time Big Data Processing ADF enables near real-time processing by: Capturing streaming data from sources like IoT devices and event hubs. Running incremental loads to process only new data.
Using Change Data Capture (CDC) to track updates in large datasets.
📊 Use Case: Ingesting IoT sensor data into Synapse for real-time analytics dashboards.
6. Security & Compliance in Big Data Pipelines Data Encryption: Protects data at rest and in transit.
Private Link & VNet Integration: Restricts data movement to private networks.
Role-Based Access Control (RBAC): Manages permissions for users and applications.
🔐 Example: ADF can use managed identity to securely connect to Synapse without storing credentials.
Conclusion
The integration of Azure Data Factory with Azure Synapse Analytics provides a scalable, secure, and automated approach to big data processing.
By leveraging ADF for data ingestion and orchestration and Synapse for high-performance analytics, businesses can unlock real-time insights, streamline ETL workflows, and handle massive data volumes with ease.
WEBSITE: https://www.ficusoft.in/azure-data-factory-training-in-chennai/
0 notes
Text
Your Trusted IT & Technology Partner
At WiseGTech, we provide cutting-edge IT solutions, managed services, and digital transformation strategies that empower businesses to operate more efficiently, securely, and profitably. From cloud computing, network security, VoIP solutions, and cybersecurity services to business IT support, we help you stay ahead in an ever-evolving digital world.
Our Core IT Services
✅ Managed IT Services
• 24/7 remote IT support, on-site IT services, and network management
• IT infrastructure optimization for small businesses and enterprises
• Server monitoring, patching, and disaster recovery solutions
✅ Cybersecurity & Data Protection
• Cyber threat detection, penetration testing, and firewall management
• Ransomware protection, data encryption, and multi-layered security protocols
• Security compliance consulting (HIPAA, GDPR, PCI-DSS)
✅ Cloud Computing & Digital Transformation
• Cloud migration services, AWS & Microsoft Azure solutions
• SaaS application integration and custom cloud development
• Business continuity planning and cloud backup solutions
✅ Telecom & VoIP Solutions
• VoIP business phone systems, PBX installation, and UCaaS solutions
• POTS to VoIP transition, VoIP gateway configuration, and video conferencing solutions
• VoIP providers like RingCentral, Vonage, Zoom, Ooma, Nextiva support
✅ Network & Infrastructure Services
• Enterprise network design, structured cabling, and fiber optic installation
• Router, switch, and firewall configuration for secure networking
• WiFi installation, hotspot setup, and 5G business connectivity
✅ IT Consulting & Digital Strategy
• Custom IT roadmaps, business technology consulting, and digital strategy development
• Enterprise software solutions, ERP consulting, and CRM implementation
• AI automation, machine learning solutions, and big data analytics
✅ Business IT Support & Helpdesk Services
• On-demand IT helpdesk, troubleshooting & diagnostics, and remote support
• POS system repair, computer & printer support, and hardware replacement
• Software installation, patch management, and OS upgrades
✅ Security Camera & Alarm Systems
• CCTV camera installation, remote surveillance solutions, and video monitoring
• Biometric access control, alarm system integration, and smart home security
• IoT security solutions, low voltage wiring, and enterprise surveillance
✅ E-Commerce & Digital Marketing IT Solutions
• Website development, SEO optimization, and e-commerce solutions
• Data-driven marketing automation, lead generation, and programmatic SEO
• Social media management, PPC campaigns, and conversion rate optimization
________________________________________
Why Choose WiseGTech?
✔️ 20+ years of IT excellence
✔️ Certified IT professionals & industry experts
✔️ 24/7 nationwide support & rapid deployment
✔️ Tailored IT solutions for SMBs, enterprises & startups
✔️ Competitive pricing & cost-effective IT plans
Get a Free IT Consultation Today!
Let’s transform your IT infrastructure with scalable, secure, and future-proof solutions. Contact WiseGTech for a custom IT strategy tailored to your business needs.
📧 Email: [email protected]
📍 Address: 12004 Courtyard Glen Pl, Richmond, VA 23233
📞 Call Us: +1 (804) 799-0808
🚀 WiseGTech – Smart IT Solutions for a Connected World!
0 notes