#How To Unlock Password On iPhone
Explore tagged Tumblr posts
Note
I saw an aesthetic picture about spreading Satan through the Internet recently and it got me thinking about being the IT support at the ministry, and which papas and ghouls would be best and worst at technology. So now I obviously want to hear your thoughts.
(I think Primo would surprise us by being surprisingly proficient, sort of like how my grandma mastered email and Facebook in her 80s.)
I have discussed this at great lengths with my best friend, @her-satanic-wiles, and these are the conclusions we have come to. These include all technology and use of the internet and social media habits.
Please enjoy as much as we did - it was too much fun. This is long, so i've put a page break in.
Some 18+ content here, MDNI!
Primo
As you said, surprisingly proficient.
He learns very fast, intently listening to you when you explain email, Microsoft Word & Excel, and Facebook.
He doesn't get Instagram but that's okay, that's not his target audience.
Doesn't understand how the internet works... "So, is it floating around in the air, or...?"
But he does know how to work it, and how to use it.
Secondo
No patience for technology at all.
If it doesn't work how it should, it is immediately referred to as broken.
"Mostrami solo le mie email, pezzo di merda!" you'll hear him scream from his office.
If it is not broken, it soon will be. His frustration makes him violent.
Got the iPhone 4 when it first came out but it perished in a mysterious fire. He doesn't know how it happened. Stop asking him.
Has been through four Ministry issued keyboards and one monitor that saw violent ends.
Terzo
Not bad at technology at all, in fact learns very quickly.
However, the discovery of Internet Pornography set him back in his paperwork by about a week.
He takes casual nudes and sends them to everyone, like him sat on the toilet or just having got out of the shower. Just because he can.
Your phone keeps saving them automatically and you have to do a mass exodus of Terzo nudes at least once a week to save your phone memory.
When you delete them he sends you more out of spite.
Ends up with Malware on his computer all the time from scam emails that promise him 'hot single babes in his area'.
The kind of guy to go on Omegle to flirt with random people, maybe find someone to jerk off with.
Copia
Boomer.
He's bloody useless, it always makes him feel like a silly old fool.
The only thing he can do by himself is search YouTube for rat videos, because you've shown him a million times.
Types with the screen close to his face and with one finger.
FaceTime angle of a typical dad.
"Look at this!" and proceeds to not flip the camera because he doesn't know how so you just end up staring at his face anyway.
SHOUTS when he's on the phone, no concept of noise at all.
Always forgetting his passwords - you get phone calls asking what his password for this and that is every. damn. day.
How many times do you have to remind him his phone unlocks with FaceID?!
Got scammed by a Facebook ad and had to change all his credit cards.
And now for the Ghouls...
Rain
He's VERY good with tech.
Quiet little genius, knows all the keyboard shortcuts and phone tips and tricks going.
Others ask him for help a lot, and he gets such a sense of pride when he can help them, swishing his tails and smiling to himself as he's helping.
Rain is also in charge of Copia's computer. He built it, fixed it, and cries every time Papa does something he shouldn’t to it.
Swiss
Technology conspiracy theorist.
He is terrified of tech, thinks it's listening to him all the time. Alexa is a demon he doesn't trust and his phone is an old Nokia he uses for emergencies ONLY.
That Nokia is also his weapon that he throws at people's heads when they piss him off. Which happens entirely too often and has caused some damage...
Mountain
Always up to date with the latest tech, never misses a launch.
He keeps leaving his second-hand phones in places Swiss will find them to trigger his technophobia and paranoia.
"DO THEY BREED, OR SOMETHING?!" Mountain is snickering outside his dorm listening to the chaos he's created.
Phantom
TROLL.
Chaos maker, through and through.
He is a serial redditer. The havoc he creates on there is diabolical, honestly.
Goes on Omegle to troll people.
He came across Papa Terzo one evening. They both agreed to never speak of what he saw ever again.
Plays on Swiss' technophobia along with Mountain.
He even created a cruel "conspiracy mode" on the Alexa that plays dramatic music, changes the lighting and shuts the window blinds in Swiss' room whilst Alexa tells him "I'm here, Swiss. I see everything."
Sodo
Has absolutely no interest in the internet or technology whatsoever.
Serial text forgetter. Sees you've text him, ignores it. Promises to get back to it. Never does.
When it comes to guitar tech though, he'll chew your ear off for hours. He knows EVERYTHING.
Ask him a question, but be prepared to be stuck there for approx. 45 minutes while he explains it in great detail with tangents you didn't ask for.
Aurora
Very good with tech, specifically social media.
Basically the social media manager of The Ghost Project.
She loves tiktok, makes them regularly. but it gives off 'Illegal Disney' vibes... Total crack.
Papa had to stop her making them and tell her to take them down.
Ask her about dance challenges - she knows them all.
Cumulus
CANNOT BE BOTHERED.
Why does everything take so long? Typing and everything... so much effort.
So she's a voice note kinda girl.
And they can be full blown podcasts, she talks and talks and talks....
Always takes Mountain's old phones after Swiss has been spooked by them. She hasn't bought a new phone in 6 years. Mountain is none the wiser.
Cirrus
Has a basic understanding, but feels guilty asking for help from IT support.
If an error message pops up, she'll panic and call Aurora.
"No but it says Error 404... WHAT DOES THIS MEAN?!"
Queen of cat videos. Falls asleep to 10 hour loops of rain storms on YouTube.
#ghost bc#the band ghost fanfic#papa emeritus iv#papa emeritus 4#cardinal copia#papa emeritus iii#papa emeritus 3#copia#terzo#papa copia#papa terzo#papa secondo#secondo#papa emeritus ii#papa emeritus i#papa emeritus primo#papa primo#primo#primo headcanons#secondo headcanons#terzo headcanons#copia headcanons#papa headcanon#ghost ghoulettes#ghost ghouls#ghouls hc#ghoulettes hc#sodo ghoul#swiss ghoul#phantom ghoul
181 notes
·
View notes
Text
unbelievable. rin x fem! reader
mdni, reblogs appreciated.
tws: mentions of smoking, drinking, OCD tendencies, lmk if i missed smthg!

usually he’d tell isagi and bachira to stop embarrassing him by commenting ‘cringe’ or ‘lukewarm’ till they get the idea, however, right now, he had his own troubles.
rin couldn’t find his phone.
unbelievable!
he was the most responsible person he knew. now, of course he didn’t know too many people, but it doesn’t change the fact that he was extremely cautious when it came to his belongings.
hands patting his pockets. his frown deepened.
now he wasn’t upset because of a phone. sure it was the brand new iphone that just hit the markets yesterday and it did contain really valuable information to him, like…his practice schedule and…horror movies to watch…
anyway! the real reason he was standing in the middle of the road with a look that scared off the tourist that was about to ask him for directions is the fact that, he; the rin itoshi forgot.
because itoshi rin never forgets. well until now.
he walked back to the signal as a confused bachira and worried isagi followed him.
was it a prank? was it a pickpocket? was it-
no, rin. you just, forgot.
letting out an annoying groan he stomped back to the building of the party he was forced to attend. this was all isagi’s fault! if he hadn’t forced him to come to this stupid party-
groaning loudly again, rin snapped his head to isagi and wordlessly glared at him.
“w-what rin..? do you wanna go back to the party or somethin’?” isagi gulped, not understanding why rin was still having mood swings in his twenties, ‘did he have a late puberty?’
rolling his eyes, rin continued his journey, leaving the two boys staring at each other in confusion. if someone came from the opposite direction, they would think that a fight was about to occur.
the door of the penthouse was open as guys smoked close to the elevator. rin cringed at the ‘lukewarm’ song playing but didn’t waste any time making his way into the apartment.
scanning the room, he remembered sitting on the couch in the living room and immediately made his way to it.
thankfully, no one was sitting on the couch so he was able to lift up the cushions, and check thoroughly…to no avail…
this was about pride and his slight ocd tendencies. he felt like he would lose his mind if he didn’t-
eyes widened as the familiar phone case across the couch on the table entered his vision.
he didn’t even think twice before leaping towards it.
yes! the same stupid space wallpaper, yes! the same password, yes! the same apps he didn’t close- wait a minute, whats this?
why was his camera opened? scrolling through his gallery, he swiped through the pictures he’d never seen before, and stopped at a video. as soon as it ended, he felt heat rush to the tip of his ears and a blush appear on his face. looking around frantically as he hoped to find-
“there you are!” isagi panted, hands on his knees. “we’ve been looking for you everywhere.” bachira complained, jumping on isagi’s back. that was his subtlest way of letting his best friend know that he was getting a piggy back ride.
rin just hoped they didn’t notice his flustered self and coughed up an excuse to leave.
“don’t be late for practice tomorrow..” though his words were supposed to sound threatening, they sounded sweet and nice and shaky. isagi and bachira once again shared a look of confusion but this time, just decided to go with it.
rin scanned every room for something specific…hanging his head low in disappointment, he left the apartment, this time with his phone in his hand.
as he stepped inside the elevator alone, he unlocked his phone to watch the video again.
“hey…hehehe-ya left yer phone here.
too bad, haha.
well, it’s good for me though, cause i get to tell you how cute i thought you were, without having to see you while saying it!
wait this camera is good, which iphone is this oh my god.
okay no, we’re getting off topic. i’m a little drunk, ya know?
but i did write my number in ya phone case, hehe~
oh, shoot im sorry for ruining yer phone case- oh nooooo im sorryyyyy~
hey but, maybe we can, go sometime together to get you another phonecase?
maybe? huh, this is so easy. is this how the future generation will ask people out?
damn. anyway,
lemme know, alright? call me tomorr-”
he shut his eyes as the video cut off. stepping out of the elevator, he bites his lip to hide the smile forming.
unbelievable.
#rin fluff#rin itoshi x reader#rin itoshi#itoshi rin#bllk#bllk scenarios#bllk x reader#blue lock drabbles#blue lock headcannons#blue lock scenarios#blue lock#blue lock x you#bllk headcanons#blue lock fluff#bllk fluff#bllk drabbles
143 notes
·
View notes
Text
For my American Friends
I feel now is a good time to spread this news. Much like how the internet came together to help share information with the Ukrainians for resisting Russia, I’m here delivering help of a similar nature to those that could be impacted by this latest election in the US. There are ways to communicate relatively securely, outside of Big Brother's social media. I bring this up so that we can minimize the amount of gatherable information that could be used to hurt you, or others you know, in the coming years as changes are made. I'm not going to tell you how or why to use them, I'm just going to provide you with the information.
WhatsApp – While not my personal favorite, since Facebook/Meta is the parent company, WhatsApp is free, globally popular, and widely-used, featuring the ability to lock chats with passwords, disappearing messages, photos and videos that are deleted after being opened, profile photo privacy, the ability to lock the app itself so that only your biometrics can unlock it, encrypted backups, the ability to set custom permissions for who can see you online or when you last used the app, and of course End-to-End Encryption for all conversations EXCEPT those with business accounts. WhatsApp is a good option for those who are not really technically savvy, but still value privacy – if one trusts Facebook/Meta to adequately protect their privacy. It does require a phone number to sign up, however.
Signal - Signal is an end-to-end encrypted messaging software. meaning that the contents of your conversation is secure. The protocol they use (which they created) is seen as the best known protocol for asynchronous messaging by cybersecurity researchers. It's so good that it has been implemented in WhatsApp and in Messenger's secret chats. This app has even been mentioned in the Right-wing author Jack Carr's Political Thriller about a Navy SEAL named James Reece, as being a preferred method of secure communication on the civilian side for operators. (Jack Carr is a former US Navy SEAL.) It's run by a Non-Profit organization called Signal Foundation, and it's mission is to "protect free expression and enable secure global communication through open source privacy technology." It allows secure messaging, voice calls, and video calls. The only downside is that app links to your phone number, so while your conversations and content are secure, who you are talking to is not. Signal is available on Windows, Mac, Andriod, Linus, and iOS.
Session - Session is an end-to-end encrypted messenger that minimises sensitive metadata, designed and built for people who want absolute privacy and freedom from any form of surveillance. Session is an open-source, public-key-based secure messaging application which uses a set of decentralized storage servers and an onion routing protocol to send end-to-end encrypted messages with minimal exposure of user metadata. This means no phone numbers, no metadata for digital footprints, and censorship resistance. It features group chats, the ability to send documents, files, and images securely, and has added voice messages, though these can be spotty. It’s slow, but effective, and be downloaded on Android, F-Droid, iPhone, Mac, Windows, and Linux.
Briar - If you have an Android phone, Briar is another option you have. It features a decentralized network (it’s peer-to-peer encrypted, rather than relying on a central server), meaning messages are synced directly between user devices. It also means that even if the internet is down, it can sync via Bluetooth, Wi-Fi, or even memory cards, meaning information can continue to flow even during a crisis. In the event the internet is functioning, it can sync via the Tor network, protecting users and their relationships from surveillance. Other features: - Screenshots and screen recording are disabled by default - Each user’s contact list is encrypted and stored on her own device. - Briar’s end-to-end encryption prevents keyword filtering, and because of its decentralized design there are no servers to block. - Every user who subscribes to a forum keeps a copy of its content, so there’s no single point where a post can be deleted. - Briar’s forums have no central server to attack, and every subscriber has access to the content even if they’re offline. - Doesn’t require any user data like name and phone number. The downside is that it is text-only and limited to Android Devices, but they do offer Briar Mailbox to deliver messages securely to those who are online at different times. Briar’s goal is “to enable people in any country to create safe spaces where they can debate any topic, plan events, and organize social movements”
Protonmail - A free end-to-end encrypted AND zero-access encryption email service based out of Switzerland, you can safely email with peace of mind that your content is secure. Unlike Google, Outlook, Yahoo, and others, Proton's zero-access encryption means they can't even view the contents of your emails or attachments. As a Swiss-owned company they are not allowed to share information with foreign law enforcement under criminal penalty and they are politically neutral, meaning they won't be pressured by foreign governments. Furthermore, Switzerland has a constitutional right to privacy and strict data protection laws. Unlike companies in other countries, Proton cannot be compelled by foreign or Swiss authorities to engage in bulk surveillance.
Additional Information, from Proton’s Website: Switzerland has strong legal protections for individual rights, and in fact the Swiss Federal Constitution(new window) explicitly establishes a constitutional right to privacy. (In the US, this right is merely implied.) Specifically, Article 13 safeguards privacy in personal or family life and within one’s home, and the Swiss Civil Code(new window) translates this right into statutory law in Article 28.
In the US and EU, authorities can issue gag orders to prevent an individual from knowing they are being investigated or under surveillance. While this type of order also exists in Switzerland, the prosecutors have an obligation to notify the target of surveillance, and the target has an opportunity to appeal in court. In Switzerland, there are no such things as national security letters(new window), and all surveillance requests must go through the courts. Warrantless surveillance, like that practiced in the US where the FBI conducts 3.4 million searches per year(new window) with little oversight, is illegal and not permitted in Switzerland.
Switzerland also benefits from a unique legal provision with Article 271 of the Swiss Criminal Code(new window), which forbids any Swiss company from assisting foreign law enforcement, under threat of criminal penalty. While Switzerland is party to certain international legal assistance agreements, all requests under such agreements must hold up under Swiss law, which has much stricter privacy provisions. All foreign requests are assessed by the Swiss government, which generally does not assist requests from countries with poor rule of law or lack an independent judiciary.
Swiss law has several more unique points. First, it preserves end-to-end encryption, and unlike in the US, UK, or EU, there is no legislation that has been introduced or considered to limit the right to encryption. Second, Swiss law protects no-logs VPN(new window) meaning that Proton VPN does not have logging obligations. While numerous VPNs claim no-logs, these claims generally do not stand up legally because in most jurisdictions, governments can request that the VPN in question starts logging. So the VPN is only no-logs until the government asks. However, in Switzerland, the law does not allow the government to compel Proton VPN to start logging.
We’ve also fought to ensure that Switzerland remains a legal jurisdiction that respects and protects privacy.
Nearly every country in the world has laws governing lawful interception of electronic communications for law enforcement purposes. In Switzerland, these regulations are set out in the Swiss Federal Act on the Surveillance of Post and Telecommunications (SPTA), which was last revised on March 18, 2018. In May 2020, we challenged a decision of the Swiss government over what we believed was an improper attempt to use telecommunications laws to undermine privacy.
In October 2021, The Swiss Federal Administrative Court ultimately agreed with us and ruled that email companies cannot be considered telecommunication providers. This means Proton isn’t required to follow any of the SPTA’s mandatory data retention rules, nor are we bound by a full obligation to identify Proton Mail users. Moreover, as a Swiss company, Proton Mail cannot be compelled to engage in bulk surveillance on behalf of US or Swiss intelligence agencies. (Links can be found at: proton.me/blog/switzerland)
#american politics#kamala harris#transgender#lgbtqia#lgbtq community#antifascist#anti trump#freedom#information#resistance
6 notes
·
View notes
Text
iCloud Bypass 2024 Free Tool Install With Windows Crack
This tutorial reviews and compares the best iCloud Bypass Tools 2024 to help you with the iCloud/iPhone activation lock removal/bypass process: SOLVED iPhone iCloud Locked How to Unlock If Forgot Password 2024. Our paid checkers offers a variety of IMEI Check Services that provide all the information about your device, fast and accessible! With iCloud Status check you can get information if that…
View On WordPress
2 notes
·
View notes
Text
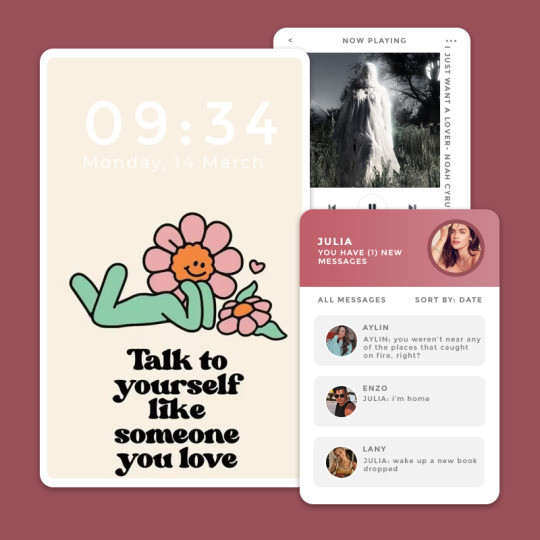

THE BASICS:
brand of Phone - apple, samsung, other
iphone 13 pro max
color - what color is the phone?
gold
case - what color is the case? does it have a design? a popsocket?
clear case with daisies
locked or unlocked? - do they use a password? what type of password?
locked face id
wallpaper - what photo is their wallpaper?
click here
lockscreen - what photo is their lockscreen?
see above; it varies with different quotes
USAGE:
time - how many hours a day do they use their phone?
eight to nine hours a day
5 Most Used Apps - what apps do they use the most?
instagram, tiktok, amazon kindle, storygraph, pinterest
web tabs - do they have any open? what are they?
she has a lot of open tabs, usually with book reviews, drink ideas and home designs
Google - what did they last google?
is the perfect marriage worth reading?
Last Text Message - what was it and who was it from?
see above
Photos - what is the last thing on their camera reel? what image did they last save?
click here
SOCIAL MEDIA:
@ - what is their handle?
julesdavis
instagram - show us their feed, or share their latest postand/or story.
see above
tinder/Bumble/Hinge/Grindr/Etc. - do they have an account? what does it look like?
she used to have tinder but removed it a year ago
spotify - what were their top 3 songs of 2022?what did they listen to last?
pretty head - transviolet space girl - frances forever willow - taylor swift
tiktok - what is their FYP like? do they post videos? what do they post?
she doesn't post often, but shows coffee recipes and books booktook, thirst traps and recipes
facebookbook - do they use it? is it just for family?
she deleted it a few years ago
others - discord, reddit, youtube, bereal, tumblr, etc…
tumblr, bereal
tagged @aylinxyilmazx @enzohuang @lanyphillips @themarissaharrison
8 notes
·
View notes
Text
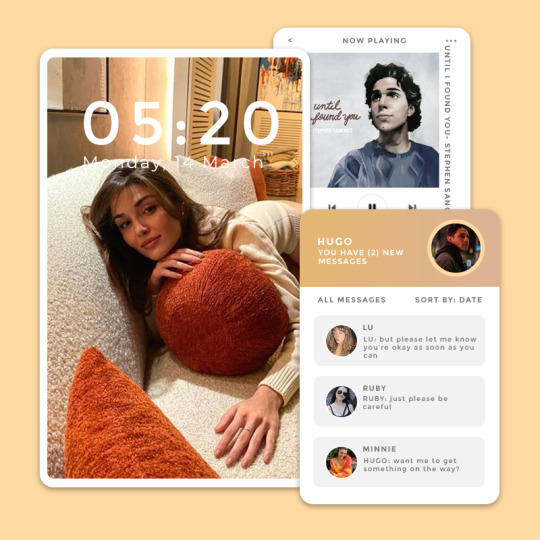

THE BASICS:
brand of Phone - apple, samsung, other
iphone 11
color - what color is the phone?
black
case - what color is the case? does it have a design? a popsocket?
black
locked or unlocked? - do they use a password? what type of password?
locked, password is yasmin's birthday
wallpaper - what photo is their wallpaper?
default
lockscreen - what photo is their lockscreen?
see above
USAGE:
time - how many hours a day do they use their phone?
less than two hours a day
5 Most Used Apps - what apps do they use the most?
youtube, spotify, twitter, facebook
web tabs - do they have any open? what are they?
he closes them when he's done
Google - what did they last google?
self-defense classes videos
Last Text Message - what was it and who was it from?
see above
Photos - what is the last thing on their camera reel? what image did they last save?
click here
SOCIAL MEDIA:
@ - what is their handle?
hugorz
instagram - show us their feed, or share their latest postand/or story.
see above let's pretend all the photos with other firefighters are nic and mike, thanks<3
tinder/Bumble/Hinge/Grindr/Etc. - do they have an account? what does it look like?
no
spotify - what were their top 3 songs of 2022?what did they listen to last?
me gustas tu - manu chao si te vas - sech, ozuna walk like an egyptian - the bangles
tiktok - what is their FYP like? do they post videos? what do they post?
he has the app on his phone, because someone made him get it, but he doesn't use it
facebookbook - do they use it? is it just for family?
yes, to keep up with family
tagged - @lukaplan @yasmindemirxx @nsloanefms @mikehotchner @rxbysxllivan
7 notes
·
View notes
Text


THE BASICS:
brand of Phone - apple, samsung, other
iphone 14 & samsuns s22 ultra
color - what color is the phone?
both white
case - what color is the case? does it have a design? a popsocket?
black and white checkered case for the iphone, no case on the samsung
locked or unlocked? - do they use a password? what type of password?
face id on iphone; fingerprint samsung
wallpaper - what photo is their wallpaper?
default
lockscreen - what photo is their lockscreen?
default
USAGE:
time - how many hours a day do they use their phone?
depends, but more often at least five hours a day.
5 Most Used Apps - what apps do they use the most?
instagram, tiktok, linkedin, spotify, facebook
web tabs - do they have any open? what are they?
he closes them
Google - what did they last google?
iphone 13 parts top alarm systems
Last Text Message - what was it and who was it from?
see above
Photos - what is the last thing on their camera reel? what image did they last save?
click here
SOCIAL MEDIA:
@ - what is their handle?
dhadwin wirednightrest
instagram - show us their feed, or share their latest postand/or story.
see above
tinder/Bumble/Hinge/Grindr/Etc. - do they have an account? what does it look like?
tinder & bumble
spotify - what were their top 3 songs of 2022?what did they listen to last?
mentalitete - baby gang love nwantiti - ckay i mean it - g-eazy, remo
tiktok - what is their FYP like? do they post videos? what do they post?
unhinged (/just like mine) he has about three tiktoks posted on his account - thirst traps obviously. he posts more on wirednightrest
facebookbook - do they use it? is it just for family?
the only reason he still has a profile is because it's linked with wired's page
others - discord, reddit, youtube, bereal, tumblr, etc…
discord, bereal, reddit
@veritycalma @shadaeokoro @selintemel @kennedyxneills
7 notes
·
View notes
Text

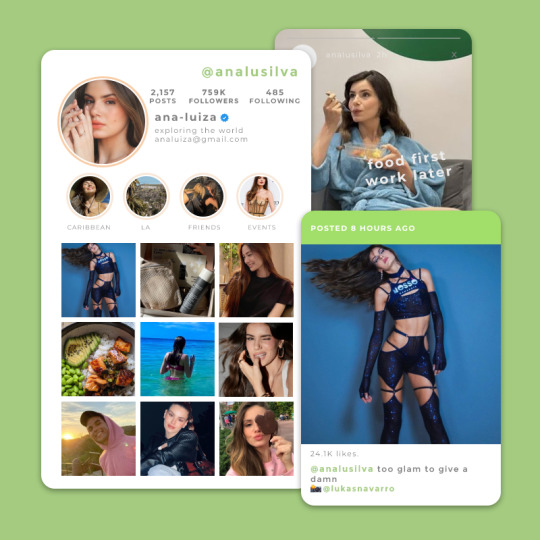
THE BASICS:
brand of Phone - apple, samsung, other
iphone 14 pro max
color - what color is the phone?
deep purple
case - what color is the case? does it have a design? a popsocket?
click here to see it
locked or unlocked? - do they use a password? what type of password?
locked with a password - her brithday
wallpaper - what photo is their wallpaper?
click here to see it
lockscreen - what photo is their lockscreen?
see above both photos are from her most recent adventure
USAGE:
time - how many hours a day do they use their phone?
more than seven hours a day
5 Most Used Apps - what apps do they use the most?
instagram, tiktok, spotify, hopper, capcut
web tabs - do they have any open? what are they?
many tabs of places she plans on visiting
Google - what did they last google?
bali hotels
Last Text Message - what was it and who was it from?
see above
Photos - what is the last thing on their camera reel? what image did they last save?
click here to see it
SOCIAL MEDIA:
@ - what is their handle?
analusilva
instagram - show us their feed, or share their latest postand/or story.
see above
tinder/Bumble/Hinge/Grindr/Etc. - do they have an account? what does it look like?
she has tinder, but doesn't use it much these days
spotify - what were their top 3 songs of 2022?what did they listen to last?
woman - doja cat electric - alina baraz, khalid fire for you - cannons
tiktok - what is their FYP like? do they post videos? what do they post?
she posts mini vlogs, dances and random funny things her fyp is mainly vlogs, make-up reviews and memes
facebookbook - do they use it? is it just for family?
she uses it to connect with her family only
others - discord, reddit, youtube, bereal, tumblr, etc…
youtube - she hasn't posted much content on there for the past two years. sometimes she uploads compilations of her adventures. bereal gardenscapes
tagged - @malachiphillips @veritycalma @mikehotchner @hanaxrheex @lnavarrofms
7 notes
·
View notes
Text
so, in russia we have pretty neat online services for bureaucracy. you can make an appointment with a doctor, fill out an application for a passport change, pay taxes, apply for marriage or divorce in two clicks in any time of day or night without leaving your home and without looking for contact numbers of authorities or their working hours. one of a few things i'm grateful for here
anyway, at some point my job was to help people navigate these online services, there were a couple of unlocked computers and people were supposed to sit there and click on things, while asking me questions if they had any. and, as expected, most people who already good at computing wouldn't go to our place just to do things they can do at home. and tho our bosses would told us we should not ourselves click thing for people, it's hard not to when 80yo grandma or grandpa with nokia 3310 asks you cause they "don't understand" or just "can't do" computers
but...
from time to time there were fucking 18-21yo's who said the same fucking things to me. like they'd come to me with their apple watch, ipad and iphone 1003672 or whatever and when i tell them to log on their account on our computer they just say "could you do it for me insted? i don't know how"
and me, average pc user, who time to time tries to become advanced, always would think to myself like what do you mean? you're like 4 years younger then me. you're our future. tf do you mean you don't know gow to move a mouse to a needed button, click on it and then tap on a keyboard to put in your password???
is that how old people feel when you say you don't know how to wash dishes but know how to load your dishwasher?
this can't be true can it
99K notes
·
View notes
Photo

Let’s dive right in! Ever found yourself staring at your phone, wondering, “WhatsApp चालू कैसे करते हैं?” (How do I start WhatsApp?) It’s a simple question, but if you’re new to smartphones or just haven’t used WhatsApp before, it can feel a bit overwhelming. This guide is here to help! We’ll walk you through everything, step-by-step, from downloading the app to sending your first message. We’ll cover all the bases, no matter what kind of phone you have – Android or iPhone – and address any common problems you might encounter along the way. By the end of this post, you’ll be a WhatsApp pro, ready to connect with friends and family around the world. So, let’s get started and unlock the world of WhatsApp!
Getting Started: Downloading WhatsApp
First things first: you need to get the WhatsApp app on your phone. This is the foundation of everything else. Think of it like building a house – you can’t put up the walls without a solid foundation!
Downloading WhatsApp on Android
If you have an Android phone (like a Samsung, Google Pixel, or Xiaomi), downloading WhatsApp is super easy.
Open the Google Play Store: This is the app store for Android phones. It’s usually a colorful shopping bag icon.
Search for “WhatsApp Messenger”: Type “WhatsApp Messenger” into the search bar at the top.
Find the official WhatsApp app: Make sure you’re downloading the app from WhatsApp Inc. It’ll have the familiar green WhatsApp logo.
Tap “Install”: Once you’ve found the right app, tap the “Install” button. You might need to confirm a few things, like allowing the app to access your contacts.
Wait for the download to finish: This usually doesn’t take long, depending on your internet speed.
Downloading WhatsApp on iPhone
iPhone users will follow a similar process, but using the Apple App Store instead.
Open the App Store: This is the app store for iPhones. It’s a blue icon with a white “A”.
Search for “WhatsApp Messenger”: Just like on Android, type “WhatsApp Messenger” into the search bar.
Find the official WhatsApp app: Again, make sure it’s from WhatsApp Inc. and has the green logo.
Tap “Get”: Instead of “Install,” iPhones use the “Get” button.
Authenticate with Face ID or Touch ID (or your password): Your phone will ask you to authenticate to confirm the download.
Wait for the download to finish: This will depend on your internet connection.
Troubleshooting Download Issues
Sometimes, downloads can be tricky. Here are a few things to try if you’re having trouble:
Check your internet connection: Make sure you have a stable internet connection (Wi-Fi is best).
Restart your phone: A simple restart can often solve minor glitches.
Check your storage space: Make sure you have enough free space on your phone to download the app.
Contact your mobile carrier or internet provider: If the problem persists, they might be able to help.
Setting Up Your WhatsApp Account: WhatsApp चालू करने के लिए
Now that WhatsApp is downloaded, it’s time to set up your account and actually start using the app! This is where you’ll connect with your contacts.
Verifying Your Phone Number
This is the most crucial step. WhatsApp uses your phone number as your account identifier.
Open the WhatsApp app: Find the WhatsApp icon on your phone’s home screen and tap it.
Enter your phone number: The app will ask for your phone number. Make sure you enter the correct country code (+91 for India, for example).
Verify your number: WhatsApp will send you a verification code via SMS. Enter this code into the app to verify your number. If you don’t receive the code, you can request a call instead.
Adding Your Profile Picture and Name
Once your number is verified, you can personalize your profile.
Add a profile picture: This is optional, but it helps your contacts recognize you.
Add your name: Choose a name that your contacts will easily recognize.
Adding Contacts
WhatsApp automatically syncs with your phone’s contacts. This means that anyone in your phone’s address book who also uses WhatsApp will automatically appear in your WhatsApp contacts list.
Navigating the WhatsApp Interface
Understanding the WhatsApp interface is key to using the app effectively. Let’s break down the main sections.
The Chats Tab
This is where you’ll find all your conversations. New messages will be indicated by a notification.
The Status Tab
Here you can share temporary photos and videos that disappear after 24 hours. Think of it like a quick update for your contacts.
The Calls Tab
This is where you’ll find your call history and can initiate voice and video calls.
Sending Messages and Media: WhatsApp का उपयोग कैसे करें
Now for the fun part – actually using WhatsApp!
Sending Text Messages
This is the most basic function. Simply open a chat with a contact and type your message in the text box at the bottom. Tap the send button (usually a paper airplane icon).
Sending Photos and Videos
WhatsApp makes sharing media easy. Tap the attachment icon (usually a paperclip or plus sign) and select the photo or video you want to send.
Sending Voice Notes
For longer messages, voice notes are a convenient option. Tap and hold the microphone icon to record your voice note.
WhatsApp Groups and Broadcasting Lists
WhatsApp offers features to communicate with multiple people at once.
Creating a WhatsApp Group
Groups allow you to chat with multiple people simultaneously. You can create a group and invite your contacts.
Using Broadcasting Lists
Broadcasting lists let you send the same message to multiple contacts at once, without creating a group chat.
WhatsApp Privacy Settings: WhatsApp की गोपनीयता सेटिंग्स
Understanding and managing your privacy settings is crucial.
Controlling Who Can See Your Last Seen, Profile Picture, and About
WhatsApp allows you to customize who can see your information. You can choose between “Everyone,” “My Contacts,” and “Nobody.”
Disabling Read Receipts
Read receipts show when you’ve read a message. You can disable them if you prefer more privacy.
Troubleshooting Common WhatsApp Issues
Let’s address some common problems you might encounter.
WhatsApp Not Connecting
Check your internet connection: A poor internet connection can prevent WhatsApp from connecting.
Restart your phone and the app: A simple restart often solves minor glitches.
Check your phone’s date and time settings: Incorrect settings can sometimes interfere with connectivity.
WhatsApp Not Receiving Messages
Check your internet connection: Again, a poor connection can prevent message delivery.
Check your notification settings: Make sure WhatsApp has permission to send notifications.
Check your storage space: A full phone storage can impact WhatsApp’s functionality.
WhatsApp Verification Code Issues
Check your phone number: Make sure you entered the correct number.
Check your SMS inbox: The code might have ended up in your spam folder.
Request a call: If you’re not receiving the SMS code, you can request a call instead.
Conclusion: Mastering WhatsApp
So there you have it! You’ve learned how to download, set up, and use WhatsApp. From sending simple text messages to managing your privacy settings, you’re now equipped to connect with friends and family worldwide. Remember to explore the app’s features and customize it to your liking. WhatsApp is a powerful tool for communication, and with this guide, you’re well on your way to mastering it.
Now it’s your turn! Share your WhatsApp experiences in the comments below. Have you encountered any challenges? What are your favorite WhatsApp features? Let’s keep the conversation going! And don’t forget to share this guide with anyone who might find it helpful. Happy WhatsApping!
0 notes
Text
Beginners guide to Set up Ledger Live Wallet with Ledger Nano X
Hey! copyright investor. Are you a proud owner of a “Ledger Nano X” but unaware of how to use it or set up it on its Ledger Live Wallet interface? If yes, then just fasten your seat belts and take a ride with us in the further sections of this write-up.
In our further content, we will cover an easy instruction guide that will help you to set up your Ledger Nano X on the Ledger Live interface.
Procedure to download Ledger Live Wallet:
Follow these simple steps to download Ledger Live Wallet on your desktop or mobile.
Steps for Desktop:
In the initial step, go ahead to the search box of your preferred web browser.
Visit the official web page of Ledger Wallet.
Navigate to the “Apps and Services” tab, and then select “Ledger Live”.
Click on “Download the App” and then select your preferred OS to begin the process of downloading Ledger Live on your OS.
After following all of these steps, navigate to the download section on your device and install Ledger Live App by following the on-screen prompts.
Steps for Mobile:
Launch Google Play Store or App Store on your Android or iPhone.
Search for the “Ledger Live” App.
Once you find the official app in the search results, simply tap on it.
In last, tap on the “Install” or “Get” button to finish the complete process.
Procedure to set up Ledger Live Wallet: (Mobile)
Follow these simple steps to set up your Ledger Live Wallet,
In the initial step, launch Ledger Live App on your preferred mobile device.
Tap on “Get Started” and then “Initialize as a new device”.
Now, choose Ledger Nano X from the list of available option.
Turn on your Ledger by pressing the button for 3 seconds, located next to the USB port.
Read the instructions and press the right button.
Press both buttons simultaneously when you see the “Set up as new device” instruction on your Ledger screen.
Press again both buttons simultaneously to choose your PIN.
Now, set up your PIN by pressing the left or right button to choose a digit and then press both buttons to validate a digit.
Confirm your PIN code and then tap on “Continue” in your Ledger Live interface.
Tap on “Got it” and then write down your recovery phrase on a blank paper as same as shown on your Ledger device.
Verify your seed phrase on your Ledger device.
Complete the security checklist in your Ledger Live App.
Now, pair your Ledger Nano X with Ledger Live Wallet through Bluetooth.
Cross-check the pairing code on both of your devices and press both buttons on your Ledger device, then wait for it to pair.
Press again both buttons and then tap on “Continue” in your Ledger Live.
In last, tap on Ledger Nano X and then set up your Ledger Live unlock password by following the on-screen prompts.
Conclusion:
In conclusion, after reading through the above sections we are sure that you now understand, how to set up and use your Ledger Live Wallet. But always remember that never store your secret recovery phrase on a computer or smartphone and keep it physically secure. Because, if someone got access to your recovery phrase, then they can easily access your funds stored in your ledger Live.
1 note
·
View note
Text
How to Unlock iPhone 11 Without Password or Face ID
Forgot your iPhone 11 password? Or maybe Face ID just isn’t working when you need it most? Don’t worry—we’ve all been there. In today’s post, we’re diving into the ultimate guide to unlocking your iPhone 11 without a password or Face ID. Let’s get started!
The first method is using security lockout screen. Here’s how you do it:
If you've entered the wrong passcode several times, the Security Lockout option will appear. Tap "Forgot Passcode" and tap “Start iPhone Reset”, sign in with your Apple ID to erase and unlock the device. After that, you can reset iPhone as a new one.
Next up, let’s talk about third-party tools. Tools like MagFone iPhone Unlocker are designed to bypass your passcode quickly and safely. Run MagFone iPhone Unlocker on your computer. Connect your iPhone and select Unlock iOS Screen option, follow the on-screen instructions to put your iPhone in DFU or Recovery mode, download the firmware package, after that, click Unlock button to unlock your iPhone 11 without passcode or Face ID.
The third method is using recovery mode. Here’s how you do it:
Connect your iPhone to a computer. Quickly press the Volume Up button, then the Volume Down button, and hold the Side button until the recovery mode screen appears. Open iTunes or Finder. A pop-up will appear offering to restore or update your device. Choose Restore. This will erase your iPhone but also unlock it.
The last method is using iCloud. Here are the detailed steps.
If "Find My iPhone" is enabled, go to iCloud.com on another device, sign in with your Apple ID, and select "Erase iPhone" under the "Find My iPhone" section.
0 notes
Text
How to Remove iPhone Locked to Owner
youtube
This situation occurs because the Activation lock is triggered. You can first check to see if there is an "unlock with Passcode" option. If so, you can unlock it with the lock screen password.
In the second case, if you bought a second-hand phone from someone else, you need to ask the original owner to erase the device in iTunes or iCloud.
iTunes: Summary>Restore iPhone
iCloud: All devices>Erase device
If none of the above methods work, you may need to use third-party software to unlock the software. During the process, you need to jailbreak to meet the unlocking requirements.
TunesKit Activation Unlocker is the best choice. it supports iOS12——16.7.5.
You need to download a jailbreak tool within the software to remove the activation lock, but it is very safe and has a high success rate.
After using TunesKit Activation Unlocker, your device has no risk of being erased or locked remotely by others and your device couldn't be tracked via the Apple ID that's linked to Activation Lock.
Computers with different systems have different jailbreak methods. You can operate according to the detailed instructions of the software.
For a detailed tutorial, watch the video above.
0 notes
Text
Keep your smartphone safe

We don’t immediately realize how fast technology is moving. But the biggest example is right before our eyes. Think of smartphones. Different companies are bringing new models in the market every month. With new features comes new security issues. That is also not unknown to us. Various social media and even Google itself earns a lot of money through advertising. They are using your information with your consent.
Awareness about this has not yet been created in our country. But we have some fear from the strictness of digital law. You still regularly use apps for online shopping. These apps also steal your data. Just what information? Your career, financial and social life is also connected with it. So you have to be aware of preventing data transmission on smartphones. Some changes to your device are more important than awareness when it comes to smartphones. Take a look at them.
Must be updated regularly
All phone companies now provide updates to their system software. But not all updates are good. You will get news about these updates in various forums. Updating accordingly is unlikely to damage the phone. Failure to update may damage your device and data. Because the new update contains the security patch update of Android. Also, older updates may contain bugs in the app’s code that your new update will fix. So check and update regularly.
Must be locked
New phone or old phone, many people don’t always use lock. Many people don’t turn on My Device service on Android. Trouble comes when the phone gets stolen. Then there is nothing left but to regret. Then the thief can access all your data without any trouble. Not only that, your phone gets a chance to use it again by resetting it. So the phone cannot be kept without lock. The use of the lock is not too harmful. Nowadays with fingerprint sensor or face unlock the phone can be unlocked quickly.
Download the app from the official store
Official source ‘Google Play Store’ for Android. On the iPhone, however, you have to download the app from the App Store. But different apps can be downloaded from different websites on Android. Many people download apps from such websites to get premium services of some apps. For example, by downloading the cracked version of Spotify, you can use its premium services for free. Hopefully many more apps can be used. Don’t do that. Instead, try to download the app from the official store.
Don’t avoid encryption
Encrypt storage, gallery, document vault, financial transaction related apps with password on Android phone. By doing this no one can access these apps secretly.
App permissions
These days Google is also giving people little chance to protect their security. After installing the app asks you some permissions. You can find out which ones by going to settings. Always turn off permissions that the app doesn’t need. It will ensure your safety to some extent.
Password manager
Don’t forget passwords or important information in phone notes or docks. Use a password manager in this case. You may have to spend some money for that. But using a password manager will not lose your password and anyone can access it.
Delete unnecessary apps
Get rid of unnecessary apps quickly. Unnecessary apps can also leak data all the time. No harm if you don’t use these. They can do their job properly.
Don’t leave data on all the time
Many keep Wi-Fi or mobile data on all the time. There is no need. The app also becomes active when there is an internet connection. They can then smuggle information online in the background. So be careful now.
Not all mail subscriptions
Email ID is required to access many sites online. But don’t give away email access if you want. Doing so will only hurt you in the end. Your mail id is very important. It’s not fair to give access everywhere.
Source: Click Here
0 notes
Text
How to Erase All Data from iPhone Before Selling
When selling or giving away your iPhone, it's crucial to ensure that all your personal data is securely erased. This guide will explain how to prepare your iPhone for a new owner and how to use tools like iReaShare iPhone Data Eraser for thorough data removal.
Step 1. Back Up Your Data Before erasing your iPhone, ensure you have a backup of your important data. There are two primary ways to back up an iPhone: iCloud Backup: Go to Settings > [Your Name] > iCloud > iCloud Backup and tap Back Up Now. Computer Backup: Connect your iPhone to your Mac or PC, open Finder (Mac) or iTunes (PC), and choose Back Up Now.
Step 2. Sign Out of iCloud and Apple ID To prevent the new owner from accessing your iCloud account, you need to sign out: Open Settings. Tap [Your Name] > Sign Out. Enter your Apple ID password to disable Find My iPhone. Confirm the sign-out.
Step 3. Erase All Data Using Built-in Settings The iPhone has a built-in option to erase all data and settings: Go to Settings > General > Transfer or Reset iPhone. Tap Erase All Content and Settings. Enter your passcode and Apple ID password if prompted. Confirm the action. The iPhone will reboot and erase all data.
Step 4. Use iReaShare iPhone Data Eraser for Thorough Data Wiping While the built-in method is effective, some data might still be recoverable with specialized tools. For complete and irreversible data erasure, use a third-party tool like iReaShare iPhone Data Eraser. Here's how:
1. Visit the official iReaShare website and download the software. Install it on your computer.
2. Launch the software and connect your iPhone to the computer using a USB cable. Unlock your iPhone and trust the computer if prompted.
3. After connecting, click the "Erase" icon on the interface.
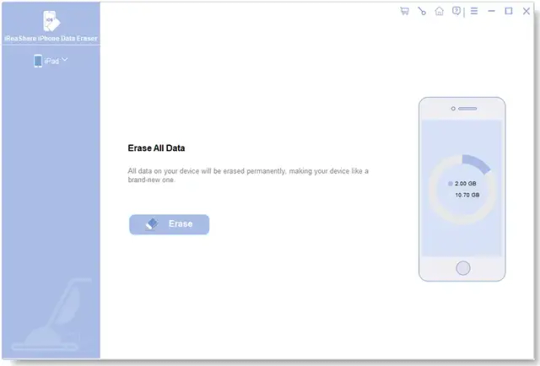
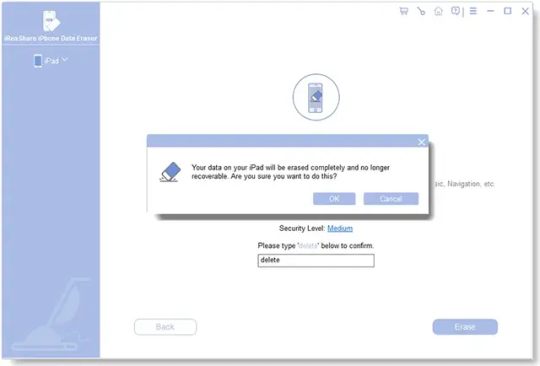
iReaShare iPhone Data Eraser offers 3 different erase levels: Low Level, Medium Level, and High Level. You can choose the one you need.
4. Enter "delete" to the designated field, and click the "Erase" icon at the bottom. Next, click "OK" on the popup to confirm your action.
5. The software will start to erase all the data on your iPhone.
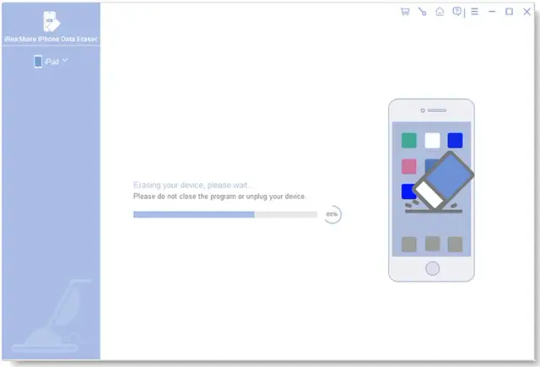
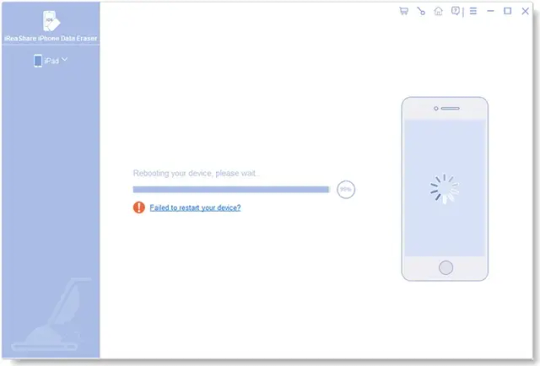
After that, it will reboot your iPhone.
Wait for the process to complete. The software will ensure all traces of your data are permanently removed.
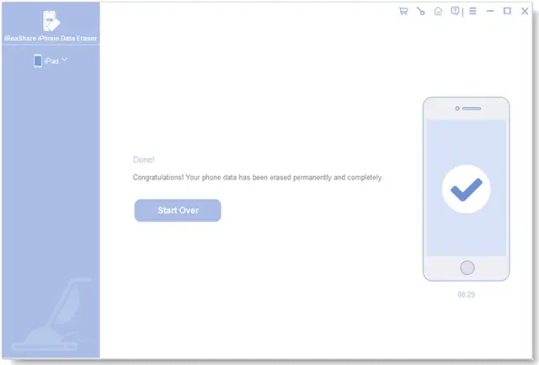
Step 5. Check for Complete Erasure After using iReaShare iPhone Data Eraser, restart the iPhone to ensure it boots to the setup screen. This indicates the device is ready for a new user.
Step 6. Final Tips Remove your SIM card before handing over the phone. Include all accessories, such as the charging cable and box, if you still have them. Reset any linked devices (e.g., Apple Watch) to avoid accidental connections.
Erasing your iPhone properly ensures your personal data stays safe and offers a smooth experience for the next owner. Using tools like iReaShare iPhone Data Eraser adds an extra layer of security, making it a valuable step in preparing your device for sale.
0 notes
Text
How to Unlock iPhone 13 without Passcode [iOS 18 Supported]
Apple is a pretty renowned company, and its cell devices are top-notch. However, some iPhone users still tend to face issues with their iPhones. For instance, they sometimes can't unlock the iPhone 13 without entering the passcode. At the same time, most people tend to forget their passwords, which could lead them to this chaos. Hence, whatever the reasons, read this guide to get the appropriate ways to help you unlock iPhone 13 without passcode.
0 notes