#Get password for windows virtual wifi adapter
Explore tagged Tumblr posts
Text
Get password for windows virtual wifi adapter

#Get password for windows virtual wifi adapter 64 Bit#
#Get password for windows virtual wifi adapter serial#
Microsoft Wi Fi Direct Virtual Adapter 41.11.12.19 Toshiba Dynabook TX/66HPK, Packard Bell IXtreme J8038, HP CQ1140JP, Gateway DX4820-23, Samsung NP-R510-FS04NL, Sony VGC-LA3, HP KT536AA-ABJ IQ507jp, Sony SVE1113M1RW, LG A540-D, and more. Microsoft Wi Fi Direct Virtual Adapter 41.1488 MSI GT60 2OJWS, Panasonic CF-S10DVCDP, Panasonic CF-30CASAXBM, Biostar GF8200C M2+, HP VS417AA-ABF s5224f, WIPRO WIV37455-0653, and more. Microsoft Wi Fi Direct Virtual Adapter 20424 Intel Intel(r) 82801AA Bus Master IDE ControllerĪTMEL maxTouch I2C Boot Bridge Peripheral Driver Hspa Modem AlcatelOT Wireless Ethernet Adapter Intel(R) 6700PXH PCI Express-to-PCI Bridge B - 032A Outdated or Corrupted drivers: 11/20 Device/Driver Scan performed on, Computer: Sony VGN-UX90S - Windows 7 32 bit PROLiNK PROLiNK Diagnostics Device (COM8) Texas Instruments Texas Instruments PCIxx12 Integrated FlashMedia ControllerĪTI ATI Technologies, Inc. Microsoft Texas Instruments PCI-7x20/6x20 CardBus Controller Microsoft Texas Instruments PCI-1520 CardBus ControllerĬorrupted By Microsoft Wi Fi Direct Virtual Adapter
#Get password for windows virtual wifi adapter serial#
Intel(R) 6 Series/C200 Series Chipset Family 4 port Serial ATA Storage Controller - 1C01 Qualcomm Atheros Qualcomm Atheros AR9485 Wireless Network Adapter Microsoft Intel(R) 82801BA/BAM USB Universal Host Controller - 2442 Microsoft Logitech First/Pilot Mouse+ (USB) Intel Controller di archiviazione Intel(R) ICH8M Ultra ATA - 2850 Outdated or Corrupted drivers: 7/21 Device/Driver
#Get password for windows virtual wifi adapter 64 Bit#
Scan performed on, Computer: Sony VGC-JS52JB_S - Windows 7 64 bit

0 notes
Text
192.168.o1 Router Login Password
192.168.1.1 is the default gateway IP Address - - used to login as admin of router settings such as TP-Link, D-Hyperlink, Linksys, Netgear. Enter IP address 192.168.0.1 > Enter username and password listed in the above table. Enter the correct administrator login name and administrator password. Step 2. In this window highlight either Ethernet, Wi-Fi, or Thunderbolt adapter, depending on which adapter is connected to your router. Then click the sophisticated tab at the bottom of the web page. You will see the IP address subsequent to Default Gateway (in the instance beneath, the IP address is: 192.168.0.1).
Home networks use this address variety. A router can assign 192.168.1.11 to any device (Ipad, laptop, Home computer, Mobile telephone, etc.) of the regional network automatically. You discover far more detailed lookup details of the IP address 192.168.1.11 beneath. If you connect to this network with your tablet, phone or laptop you get an IP address like 192.168.1.11 in this case. Router IP addresses such as 192.168.0.1.1 nonetheless lead to far much more confusion than they ought to. To help you take handle over your personal router, we've put together this article, which describes in detail the goal of the 192.168.0.1.1 IP address and explains how comparable IP addresses can be used to manage routers.
If you can not figure out the username and password, you can appear for the default usernames and passwords for the distinct make and model of router or modem, which you have, or you can try to discover by contacting your World wide web Service Provider. It really is so effortless to set up and uninstall, and even it's fairly easy to add and reset the password in virtually no time. You're capable to alter the router password.
Visiting 192.168.1.1 from web browser leads to the login page of the router's settings from where diverse settings of the router can be changed offered that the default gateway address of your device connected to the network is 192.168.1.1. If you happen to be looking to make changes to the settings of the router or changing the password of your Wi-Fi Network then this can be carried out by logging in into the Router's Settings via 192.168.1.1.
Step 3. Click the Network & Internet” option. Step five. Choose how you are connected to your router. If you are hardwired to your router pick Ethernet. If you are connected to your router by means of WiFi pick Wi-Fi. Please post back right here with the results of the test and the info on precisely where your Computer network cable connects. But in most instances, the default IP Address for Modems and Routers is 192.168.0.1. Now you also need to have to Enter Default username and password in order to access its admin page. The default username and password are various for a diverse manufacturer. Right here we are going to share all the possible Default Username and Password for 192.168.01 IP address.
That is it! You have now located your router's IP address. The IP address will seem subsequent to Router”. From your smartphone, connect to your wireless network. As soon as it really is connected, tap on the WiFi name to view the default IP address of your router In this case, it is 192.168.1.1 and is situated in the Router section. When IP addresses are assigned they follow a regular. The regular for IP addresses is defined by the Internet Assigned Numbers Authority (IANA). IANA has two requirements for public IP addresses IP version four aka IPv4, and IP version 6 aka IPv6.
In order to access the router's net-primarily based setup web page, you are going to need to have the router IP address. If you forgot that address, you will not be in a position to access the configuration web page. But don't be concerned, because discovering the router IP address is not difficult at all. If you forgot your username and password you can comply with these directions to recover them. If you haven't changed the default user and password that comes with the router you can seek the advice of our router default usernames and passwords you are in the router's admin panel you are going to be able to modify and alter all web settings.
In each of these examples the Default Gateway is 192.168.1.1. The IPv4 address is the IP address of your device that you are making use of to connect to your router. 6) Remove energy to the router, hold the reset button, and restore power. The energy light must blink gradually. After it starts blinking, release the reset button. Factory resets need to be a final resort, given that performing them will get rid of any custom settings you have, like your network name and password.
The 192.168..1 IP address falls within this last range of reserved private IP addresses. To alter your router's password, go to the settings menu and look for an option titled password.” It really is essential that you pick a password that is sufficiently safe. The router has to be configured. Ahead of beginning to get the crucial, you may have to connect it to the routers or modem by employing an Ethernet wire. You will require a router login IP address, which can be 192.168.1.1 , , 192.168.1. 254, etc. Now, if you do not know about Router Default IP, then verify out its shipping box or get in touch with manufacturer.
Your router is a gateway to your network, and you need to do whatever you can to safeguard it from intruders. Although it might be convenient to stick with the default password, doing so compromises your security and tends to make it a lot less difficult for cybercriminals to infiltrate your network and steal your individual details. Equipped with the info from this post, you should be able to secure your router with no any main issues.
At times, your modem or router may use a different IP address, such as 192.168.0.1, 192.168.11.1 or 10...1, depending on the brand. For your comfort, we've put collectively this handy list of login names and passwords for well-known makers of routers. Unless you have changed the default admin username and password to anything else, both ought to be admin”. To address the shortage of IPv4 addresses, a strategy of remapping one IP address space into an additional was proposed. Network address translation (NAT) makes it possible to use a single public IP address for an complete private network.
With NetSpot, you can rapidly and painlessly locate if the area you happen to be connecting from is covered with a sturdy Wi-Fi signal coming from your router, and you can find out all neighboring Wi-Fi networks that may be interfering with it. To see this IP address, you can connect to it through a cable or wirelessly. 192.168.l.l is generally used to login to router settings, nevertheless it is typo. The appropriate IP address is 192.168.1.1.
1 note
·
View note
Text
Reviews on Movavi
The basic performance and operation are also bad and the license fee is not worth it. Fader console with twelve motorized precision faders with call, solo, mute and automation controls as well as an LED display for the status of each channel. Thanks to support for collaborative projects in Dolby Vision and HDR10 +, every user has access to all required SDR and HDR elements. 500 royalty-free Blackmagic Design Foley sound effects compatible with the new Foley sampler in DaVinci Resolve are available for download. GPU-accelerated scopes display more details, work faster, and offer dozens of advanced new options for technical monitoring. We offer free trial versions of our programs to check their functionality before you make a purchase decision. We apologize for the inconvenience. We offer free trial versions of our programs to test their functionality before you make a purchase decision. Install Windows using an ISO image file, DVD disc or USB stick with the installation files for Windows. If you want to be automatically logged on to Windows when you start Windows, select the option "Activate automatic login" and enter the administrator password. Whether you want to cut out objects, create masks or apply adjustments in a targeted manner, all desired image areas can be selected quickly and precisely - even individual strands of hair. Effects such as blurring, illumination, distortion and perspective corrections can all be used as non-destructive live filter layers. You can erase, mask, rearrange the effects and change their settings at any time. Creative professionals have been waiting for these options for a long time.
And new GPU-accelerated scopes offer more options for technical monitoring than ever before.
Make sure that the Windows firewall is switched off.
There you will find settings, view modes, device management, configuration etc.
Deleting the part of this sequence that is no longer required also takes more than 7 seconds.
With the powerful playback -Engine cuts and trims incredibly quickly, even with computationally intensive formats like H.264 and RAW.
ul> Save and transfer photos and videos easily, even without iCloud or iTunes. Access the photos on your computer via USB or WiFi. Your memories are now safe on your Mac or PC. To add a virtual machine in Parallels Desktop, you can also simply drag a Parallels .pvm file into the Control Center. Turn on your Mac and Windows PC and sign in.
Send price proposal
But even with the various free programs, you can get quite far - with corresponding effort even further than with some paid software. For a long time, Avidemux was reserved exclusively for Linux users - but now the editing software is also available for the other major platforms. The open source tool more info here comes with a huge selection of tools that are useful for Cutting, editing and embellishing videos and film projects help. Since it combines code from many different open source sources, the software supports countless file formats in import and export and can deal with many different codecs by default. They are made from the highest quality materials. With the DaVinci Resolve control panels, you can intuitively access every section of the screen. The map window shows the location where your pictures were taken using embedded latitude and longitude information. This allows you to create groups of files by region for processing. You can also drag and drop pictures onto the map and geotag them. Affinity Photo's HDR algorithm creates incredibly natural images that reveal the full dynamic range of your shots. You can even work natively with the complete 32-bit image or use the extensive tone mapping to adapt the display exactly to your needs. The modern algorithm for refining selection areas allows you a level of precision that you would previously have believed impossible.
1 note
·
View note
Text
Microsoft virtual wifi miniport adapter fix

#Microsoft virtual wifi miniport adapter fix how to
#Microsoft virtual wifi miniport adapter fix install
#Microsoft virtual wifi miniport adapter fix update
#Microsoft virtual wifi miniport adapter fix windows 10
#Microsoft virtual wifi miniport adapter fix software
Just like with modern routers, you only have to enter a number displayed on screen, or press a button, and the devices connect. WiFi Direct relies on WiFi Protected Setup (WPS) which is a simple way to securely connect two devices via WiFi. Microsoft Virtual WiFi Miniport Adapter Reinstallation Guide on Windows PC.īasically, Virtual WiFi is a technology that virtualizes your network adapter much in the same way VMWare virtualizes your entire operating system.
#Microsoft virtual wifi miniport adapter fix windows 10
Use “WiFi Sense” of Windows 10 for WiFi Hotspot or Wireless Internet.
#Microsoft virtual wifi miniport adapter fix software
Use Third-party Windows Software to Create a Virtual Wireless Network or Wi-fi Hotspot Service. How to Enable Microsoft Virtual WiFi Miniport Adapter and Setup Wi-fi Hotspot Setup Virtual Wireless Access Point Using Command in Windows 10/8/8.1/7. How to enable a Microsoft Virtual WiFi adapter?
#Microsoft virtual wifi miniport adapter fix install
Select “Update Driver Software” and then click “Search automatically for updated driver software.” Follow the prompts to install any available updates. Expand the “Network adapters” section, then right-click on your wireless adapter. Press ⊞ Win and type devmgmt.msc to open the Device Manager. This means that, using the Microsoft Virtual WiFi Mini Port Adapter, you can turn the physical network adapter that their computer has into two virtual network adapters. The Virtual WiFi Adapter is designed to basically virtualize the physical network adapter that every computer has. Virtual WiFi interacts with the card device driver at the lower end, and network protocols at the upper end. Virtual WiFi is implemented as an NDIS intermediate driver, and a user-level service in Windows XP. Virtual WiFi helps a user connect to multiple IEEE 802.11 networks with one WiFi card. Check if any unknown devices show up and right click on it and click on Enable.Click on View Tab, Select Show hidden devices.How to install Microsoft wifi direct virtual adapter #2 How do I download Microsoft WiFi direct virtual adapter? Run “netsh wlan start hostednetwork” to start the wifi hotspot.Then run “netsh wlan set hostednetwork mode=allow ssid=name key=password” to create the wifi hotspot.Open an administrator command line and run “netsh wlan show drivers”.Reinstall the network adapter from the device manager.How do I install Microsoft Virtual WiFi Miniport adapter in Windows 7? File name: microsoftvirtualwifiminiportadapter.exe Version: 2.2.7 File size: 9.
#Microsoft virtual wifi miniport adapter fix how to
7 How to enable a Microsoft Virtual WiFi adapter? Below you can download microsoft virtual wifi miniport adapter driver for Windows.6 How do I install a virtual WiFi adapter?.
#Microsoft virtual wifi miniport adapter fix update
In such case, choose other trustworthy to update it or reinstall it. That’s why it keep prompting the driver is not up-to-date if you updated driver through Device Manager. For some reasons, Microsoft cannot detect the update for your device.
5 How do I install Microsoft Virtual WiFi? Reinstall Microsoft Virtual Wifi Miniport Adapter driver.
4 What is Microsoft Virtual WiFi adapter?.
2 How do I download Microsoft WiFi direct virtual adapter?.
1 How do I install Microsoft Virtual WiFi Miniport adapter in Windows 7?.
It also seems that when this connection is on I get more virus'sĮven though I have several virus protectors and trojan protectors and I have a password on my internet connection not letting others use it but some how it is still happening and I only have one laptop connected to my internet. If I disable it I am good forĪ while but somehow it re-ables itself is there some way to stop this? I have read where other people have increased problems with their computers being hacked more when using this connection. This is very frustrating expecially with taking online classes and it cause me to lose my connection or slows down my connection or freezes up my connection. Sometimes it has to be done multiple times in an short period of time. On my new laptop I have a network adapter called "Microsoft Virtual WiFi Miniport Adapter", I am not sure what this is but it causes major problems with my internet connection and I am always losing my connection and have to repeatedly reset my modem and

0 notes
Text
Tunnelbear for mac download

#Tunnelbear for mac download how to
#Tunnelbear for mac download crack software
#Tunnelbear for mac download install
#Tunnelbear for mac download software
System Restore removes all those programs, which interfere with the operation and performance of the computer. For those who don’t know, System Restore is a utility, which helps the user restore their system to its previous state. The third method involves System Restore. Double click on the file, and then follow the wizard’s instructions that appear on the screen.Find a file that is named as uninstall.exe or unins000.exe.Go to the installation folder of tunnelbear.Just follow the instructions below to execute this step: The second method involves uninstaller.exe, through which tunnelbear can be uninstalled. Follow the prompt on the screen, and you will get to see a progress bar that will take you to remove the tunnelbear from the computer.Right-click on tunnelbear, and then click on uninstall a program.In Control Panel, under programs, go through the list of the ones that are installed on your computer.Go to Start Menu, then click on the Control Panel.There are 10 methods that users can adapt if they want to uninstall tunnelbear : Method #1 How To Uninstall tunnelbear In PC ( Windows 7, 8, 10, and Mac )
#Tunnelbear for mac download how to
1 How To Uninstall tunnelbear In PC ( Windows 7, 8, 10, and Mac ).Installed the crack software.įollow the instruction given to the below. Work on window 7 to 10 also work on Vista, window XP. Its new feature is that it gives security alert if no password use on any network or use illegal System Requirements. its automatic connect with your trusted network for example wifi. more reliable & connect and reconnect process is 60% more than the old app. What’s new in the TunnelBare 3.7.1 with Keygen?. The person who belongs rich family can use but the great advantage is this who belong to the poor family can also be used in the same way with complete feature.
#Tunnelbear for mac download software
This software does not require deep knowledge you need to click on this app and will connect.
#Tunnelbear for mac download install
You can install this app from play store and can easily use to your mobile laptop and personal computer. Best the feature is that it is not expensive it provides free 500mb data to a user for use in browsing. Only the first app which introduced an independent security audit. This feature is very amazing u can facilitate yours with amazing speed. They can browse at least twenty plus countries with is vast networks. It is not only limite cities or one country. Top Features of TunnelBear 3.7.1 With Mac. This network is a process to include data with security in it and maximum use in the organization to save sensitive data. It is saved from a crash system and save from the hacking system. It is used in office and banking system it also makes able to send a document and receive personal file without fear of any hacking system. It also provides safe connection and security over a poor network in every mobile system. It provides the user 2GB free data in a browser. Virtual means elastic private means personal and network mean the connection of the different computer. It is the provocation of Virtual Private Network. It also gives the security process from an unauthorized person. Its provide facility to save and keep data in the consistent state. Even a student of five can easily pick every facility which presents in the beautiful app. This pretty app provides help to all level of people. Everyone can easily use and able to access every facility of this app.
#Tunnelbear for mac download crack software
TunnelBear 3.7.1 Crack + Torrent With Free VPN freeload TunnelBare 3.7.1 Crack software very efficient and magnificent app.

1 note
·
View note
Text
Unrar download free windows

UNRAR DOWNLOAD FREE WINDOWS FULL VERSION
UNRAR DOWNLOAD FREE WINDOWS DRIVER
UNRAR DOWNLOAD FREE WINDOWS RAR
Nowadays, this format is as familiar as ZIP, and we see how day by day new developers create applications to use it.
UNRAR DOWNLOAD FREE WINDOWS RAR
Download Price: Free Dll Description: RAR decompression library Versions. Since it was published, RAR compression format has been really successful.
UNRAR DOWNLOAD FREE WINDOWS FULL VERSION
You can freeload UnRAR and safe install the latest trial or new full version for Windows 10 (x32, 64 bit, 86) from the official site. The Unrar.dll file is a dynamic link library for Windows 10, 8.1, 8, 7. Therefore, here you will find the perfect substitute, since the functions of UnRAR are practically the same as those of the original. The program integrates itself perfectly in the.
UNRAR DOWNLOAD FREE WINDOWS DRIVER
WinRAR freeload and support: WinRAR By joining Microsoft virtual wifi miniport adapter driver download windows 10 free. Winrar is a free app that lets you compress and unpack any file in a very easy, quick and efficient way. If you decide to buy, WinRAR is currently priced at 29 and is available for Windows. PeaZip is a free file archiving application (file compression, rar opener.), cross-platform Open Source free alternative to WinRar, WinZip and similar. This tool called UnRAR is designed only for users who work regularly with compressed files in RAR format, but do not have the classic WinRAR program, or do not work properly. Download UnRAR for Windows to extracts the files from a RAR type archive. And there is a port of the command line version to Linux/Unix. All this under a simple and very comfortable graphical interface that will allow you to move around the program without complications of any kind, so you can get the most out of UnRAR. 7-Zip works for Windows 7, Vista, XP, 2008, 2003, 2000, NT, ME, and 98. UnRAR also works with protected files by using a password and files divided into multiple parts.Īlthough the program is only available with the screen texts and the different menus in English, the operation will not be complicated for the average user, since all the functions and features of this application are very visual and intuitive. UnRAR is a practical tool that allows you to extract files from a RAR file without having WinRAR itself installed. A large majority of the files that you download from the Internet are compressed in RAR format so it is very practical and useful to have a simple and manageable tool like UnRAR.

1 note
·
View note
Text
Nordvpn Mac Not Connecting

I just downloaded the Nord VPN app from the App store (designed to set up an IKEv2 connection), but when I open it and try to connect, the following dialog box keeps popping up and it keeps coming back no matter what I enter into it:
Apr 21, 2020 Fixes for NordVPN Not Connecting Connect to Another Server You can try connecting NordVPN to a few different servers. If it cannot connect to any, use this app on a different device like your phone. With NordVPN smart DNS, you can easily connect Apple TV to websites and servers using the server in a different location. On top of that, using a NordVPN DNS proxy for Apple TV will not cause you to have connectivity issues and low speeds.
If you're using the OpenVPN or NordVPN platform for accessing the Internet securely, you may have noticed that the Office 365 product (Outlook, Word, Excel, One Note, etc.) have reported that they do not have an internet connection ('NO INTERNET CONNECTION'). Launch NordVPN and connect to any server of your choice, preferably one that can unblock the streaming content you want to access on your Apple TV. Then, connect your Apple TV to this virtual hotspot network and to share NordVPN’s connection with the Apple TV. Set up NordVPN on Apple.
As a result, the IKEv2 NordVPN app from the App store will not connect. I managed to download and begin using the OpenVPN version of the Nord app, but I would like to know what the problem is with the IKEv2 version of the app. I'm running El Capitan on a 2015 Macbook Pro. Anyone else had this sort of problem?
MacBook Pro (Retina, 13-inch,Early 2015)
Posted on
Need a VPN or DNS for your device? Then, subscribe to
Fixing NordVPN connection issue might arise as a result of different reasons. We all know that NordVPN is one of the leading VPNs in the industry. So the tendency of having issues with connecting to the server is common and sometimes high. Though, if you have been battling with how to fix NordVPN connection problems, you landed yourself on the right place to get the right info.
NordVPN is a highly rated VPN provider for Windows, macOS, Linux, Android, and iOS platforms. Connecting to that VPN server is usually straightforward enough, but some NordVPN users might still need to fix connectivity issues.
NordVPN not connecting can be due to conflicting software, corrupted adapters, misconfigured network configurations and more besides.
How to Fix NordVPN Connection Problems
Depending on your devices, here is the list of steps you need to take if you are having difficulties in connecting to the server.
iOS Fix
The process is simplicity itself, you don’t need any specialist here. Is what you can do in a few minutes on your own. Here are the steps:
Step 1 > Delete the NordVPN app, in the actual sense you are to uninstall the app from your device.
Step 2 > Restart the device
Step 3 > Reinstall the app, please download from NordVPN offical website.
Step 4 > Enjoy
You see, these steps are simple and easy to follow, on the iOS devices you had fix NordVPN connection problems.
DON’T MISS IT: NordVPN has a great 66% discount on the 2-year plan, costing you just $3.99/month. It also backs all of its plans with a 30-day money back guarantee.
Fix NordVPN Connection Problems on MacOS
If you have any issues connecting to the internet with NordVPN on any Mac OS device, then try the following:
> You need to install the OpenVPN app version directly from the official website
> Do uninstall the IKE version before installing the new one
> Try using the obfuscated servers or the TCP protocol
Most times, the Canadian servers will work better than all the others. As for this, you need to team up with NordVPN support team to take up from you.
Fix NordVPN Connecting Issues on Linux Fix
In order to avoid any sort of issues when running NordVPN from a Linux device, just follow the next steps:
Step 1 > First of all, open the terminal by pressing (Ctrl+Alt+T)
F1a8. Step 2 > Install the OpenVPN client by entering “sudo apt-get install openvpn”. If you are asked for a password, insert the one you used when setting up your account
Nordvpn Mac Not Connecting Wifi
Step 3 > Go to the OpenVPN directory with this command “cd/etc/openvpn”
Step 4 > Now download the OpenVPN configuration files with the command “sudo wget https://downloads.nordcdn.com/configs/archives/servers/ovpn.zip”
Step 5 > Extract the “config.zip” with the command “sudo unzip ovpn.zip”
Step 6 > Enter the directory where the server configurations are placed
Step 7 > If you want a full list of the server coverage, input the following command “Is -al”
Step 8 > Just choose the server that you want to connect to

Step 9 > Start OpenVPN with the command “sudo openvpn (file name)”, where the file name is the chosen configuration
Step 10 > You will be asked for credentials, so insert those when necessary
Step 11 > You are now fully connected to NordVPN. If you want to disconnect, just boot up the terminal and press Ctrl+C.
DON’T MISS IT: NordVPN has a great 66% discount on the 2-year plan, costing you just $3.99/month. It also backs all of its plans with a 30-day money back guarantee.
Fix NordVPN Connection Problems on Windows 7
Before we move to some basic tips on how to fix NordVPN connection issues on Windows 7. Let quickly look at what we gathered from NordVPN official website.
> Log out of your account and log back in. After that, initiate a new connection and see if there is any change
> You should try connecting to the same network with a different device. This will help locate the source of the problem. Either it has something to do with the network or it’s the device malfunctioning.
> Try switching from TCP to UDP, changing the protocols to check if it changes anything
> Uninstall the application, reboot your device, and try installing it again. Try connecting to the network again.
> It could be that one of the servers is out of order so try connecting to other servers as well to see if it’s a local or a general issue
> For PC users, try disabling your firewall or antivirus. Many times, it’s the underlying protective protocols of these apps that interfere with the VPN network.
With regard to Windows 7 users being unable to connect to NordVPN, Reddit contains a few fixes that are likely to help.
1 > Try changing your account password and then log back in. Apparently, this is all that needs to be done in order to get over this stuttering with the connectivity. Or it could be that you changed your password frequently and the system is glitching, failing to recognize your identity. Again, just log out and sign back in. Ideally, it should solve everything.
2 > Some users have said that the IPv6 protocol was at fault. With it enabled, it was incredibly hard to connect to any server, let alone surf the internet or stream media. However, while this worked for some people, many more complained that it was actually no difference whatsoever when they turned off IPv6.
3 > In this case, try reinstalling the application and follow the instructions on the NordVPN website:
Step 1 > After downloading the installation package, open it
Step 2 > Click install on the first screen
Step 3 > The installation progress will begin, once finished, the application will automatically start
Step 4 > Provide your login details and click on the Login button
Dragon ball z burst limit psp download mediafire. Dragon Ball Z Burst Limit PS3 iso Download تحميل لعبة dragon ball z burst limit ps3dragon ball z burst limit downloaddragon ball z burst limit ps3 iso downloaddragon ball z burst limit controls ps3dragon ball z burst limit demo ps3 downloaddragon ball z burst limit english lyricsdragon ball z burst limit englishdragon ball z burst limit free downloaddragon ball z السلام. Download file - DragonBallZBurstLimitBLES00231.rar. Dragon Ball Z: Burst Limit is revolutionizing the series by entering the realm of next- generation gaming. Complete with fierce online battles and radical 3. D graphic effects only possible on PLAYSTATION®3 system, Dragon Ball Z: Burst Limit will blur the line between video game and iconic anime series. Dragon Ball Z: Burst Limit is revolutionizing the series by entering the realm of next-generation gaming. Complete with fierce online battles and radical 3D graphic effects, Dragon Ball Z: Burst Limit will blur the line between videogame and iconic anime series. Dragon Ball Z Burst Limit. Click the 'Install Game' button to initiate the file download and get compact download launcher. Locate the executable file in your local folder and begin the launcher to install your desired game. A game by: Dimps Corporation, and Bandai Namco Holdings.
Nordvpn Mac Not Connecting Iphone
Step 5 > The main screen will appear. You can see the server list and the map, navigate through the settings and access the server search feature on the top of the application.
Step 6 > On the bottom, you can find the Quick Connect button. This will find the optimal server for you using certain parameters and calculations.
Step 7 > To connect to a certain server in a specific country, click on the country pin on the map. After a successful connection, the app can be found in the system tray area at the bottom right corner of the screen.
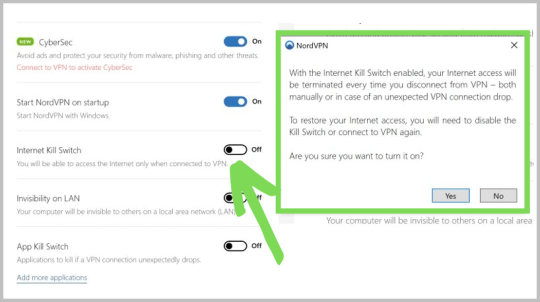
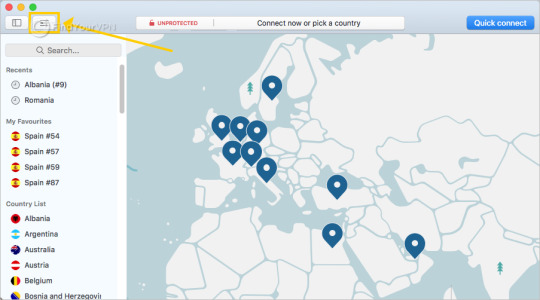
DON’T MISS IT: NordVPN has a great 66% discount on the 2-year plan, costing you just $3.99/month. It also backs all of its plans with a 30-day money back guarantee.
Related articles:

0 notes
Text
Dell XPS 15-1063 Touch Laptop (Intel Core i7-7700HQ -2.8GHz, 15.6-Inch Touch QHD+ , 16GB Ram, 512GB SSD, 4GB GTX1050, Windows 10, Gray) | 15-1063
Description for Dell XPS 15-1063 Touch Laptop (Intel Core i7-7700HQ -2.8GHz, 15.6-Inch Touch QHD+ , 16GB Ram, 512GB SSD, 4GB GTX1050, Windows 10, Gray) | 15-1063
Operating system
Available with Windows 10 Pro - for a smooth, versatile PC experience.

Innovation that inspires.
When you’re at the forefront of ingenuity, you get noticed. That’s why it’s no surprise the XPS 15 was honored. The winning streak continues.

Meet the smallest 15.6-inch laptop on the planet.
The world’s only 15.6-inch InfinityEdge display*: The virtually borderless display maximizes screen space by accommodating a 15.6-inch display inside a laptop closer to the size of a 14-inch, thanks to a bezel measuring just 5.7mm. Operating System: Windows 10 Pro. One-of-a-kind design: Measuring in at a slim 11-17mm and starting at just 4 pounds (1.8 kg) with a solid state drive, the XPS 15 is one of the world’s lightest 15-inch performance-class laptop.

A stunning view, wherever you go.
Dazzling detail: With the UltraSharp 4K Ultra HD display (3840 x 2160), you can see each detail of every pixel without needing to zoom in. And with 6 million more pixels than Full HD and 3 million more than the MacBook Pro, you can edit images with pinpoint accuracy without worrying about blurriness or jagged lines. Industry-leading color: The XPS 15 is the only laptop with 100% Adobe RGB color, covering a wider color gamut and producing shades of color outside conventional panels so you can see more of what you see in real life. And with over 1 billion colors, images appear smoother and color gradients are amazingly lifelike with more depth and dimension. Included is Dell PremierColor software, which automatically remaps content not already in Adobe RGB format for onscreen colors that appear amazingly accurate and true to life. Easy collaboration: See your screen from nearly every angle with an IGZO IPS panel, providing a wide viewing angle of up to 170°. Brighten your day: With 350 nit brightness, it’s brighter than a typical laptop. Touch friendly: Tap, swipe and pinch your way around the screen. The optional touch display lets you interact naturally with your technology.

Powerhouse performance.
Super-speed: The most powerful XPS laptop we’ve ever built includes the latest 7th Gen Intel® Quad Core™ processors and an optional 4GB GeForce® GTX 1050 graphics card with the latest and greatest Pascal™ architecture, so you can blaze through your most intensive tasks. Maximum memory and storage: Supports up to 32GB* of memory with a bandwidth of 2133MHz, 1.3 times the speed of 1600MHz options. Faster memory means you get to the content that you need quicker. Expandable storage up to 1TB* in your choice of standard hard drive or optional solid state drive (SSDs), available in faster PCIe versions, provide plenty of storage room and high-performance responsiveness to access and run your applications quickly. The XPS 15 boots and resumes in seconds with a solid state drive, so you can do more without waiting. Killer™ Wireless: The Killer 1535 Wireless-AC adapter provides a strong and reliable Wi-Fi connection and was designed specifically to make your online videos, voice and games play faster and smoother. It automatically detects, classifies and prioritizes network traffic ensuring your most important data takes priority over your other less urgent applications. Killer delivers your critical packets immediately, thus eliminating unnecessary latency and lag.

Long-lasting performance.
Stay powered longer: Depending on how you use your laptop, your battery life will vary. We benchmark our battery life 2 different ways – with industry standard MobileMark 2014, as well as streaming video, a common usage for laptops. When you are using productivity applications, like Word or Excel, experience up to 19.5 hours of continual use, the longest battery life on a 15-inch laptop*. Enjoy up to 11.5 hours of battery life when streaming Netflix content. Back-up power: The optional Dell Power Companion will give you extra runtime with 9 additional hours* of productivity for your XPS 15 Laptop.
Essential productivity at your fingertips.

Leading-edge connectivity Thunderbolt™ 3 multi-use port allows you to charge your laptop, connect to multiple devices (including support for up to two 4K displays) and enjoy data transfers up to 40Gbps, which is 8x faster than USB 3.0. Also includes two USB 3.0 ports.

Advanced docking Featuring a single-cable connection for power, Ethernet, audio and video. Add the optional Dell Thunderbolt™ Dock for faster data transfers and support for up to three Full HD displays or two 4k displays.

See what you’ve been missing A standard backlit keyboard illuminates your keys so you can stay productive in low-light or no-light rooms while typing.

Interact intuitively.
Pinch, zoom and click with confidence: The precision touch pad prevents jumping and floating cursors, while Accidental Activation Prevention puts a stop to unintentional clicks when your palm hits the touch pad. Microsoft Hello: Enjoy a password-free sign-in with the optional fingerprint reader that gives you the fastest, most secure way to unlock your Windows devices. Using your touch, it recognizes you apart from all others. It waves you in with a friendly hello and even works on apps and Microsoft Edge websites.
Artfully constructed from premium materials.
Maximum durability: Cut with precision from a single block of aluminum for a sturdy, durable chassis in a beautiful design. The Corning® Gorilla® Glass NBT™ touch display option is up to 10 times more scratch resistant than soda lime glass.* Cool under pressure: The palm rest is made from carbon fiber. It's strong and thin like aluminum, but lighter and cooler to the touch.


More environmentally responsible than ever.
Power-efficient: XPS 15 is ENERGY STAR® qualified. Smarter materials: Free of materials like cadmium, mercury and some phthalates, it’s also EPEAT® Gold registered* and BFR/PVC-free*. Recycle-friendly: Over 90% of the laptop (by weight) can be easily recycled or reused, and the bamboo packaging trays are 100% recyclable.

Ports & Slots
1. SD card slot | 2. USB 3.0 with PowerShare | 3. Battery gauge button and indicator | 4. Kensington lock slot | 5. AC power | 6. HDMI |7. Thunderbolt™ 3 (2 lanes of PCI Express Gen 3) supporting: Power in/charging, PowerShare, Thunderbolt 3 (40Gbps bi-directional), USB 3.1 Gen 2 (10Gbps), Native DisplayPort 1.2 video output, VGA, HDMI, Ethernet and USB-A via Dell Adapter (sold separately) | 8. Headset jack

Dimensions & Weight
1. Depth: 9.27 in (235mm) | 2. Width: 14.06 in (357mm) | 3. Height: 0.45-0.66 in (11-17mm) | Starting at weight: 1.8kg (4 lbs)* with 56Whr battery, SSD and non-touch display; Starting at weight: 4.5 lbs (2kg)* with 97Whr battery, SSD and touch display Processor 7th Generation Intel Core i7-7700HQ Processor (2.8 GHz) Operating System Windows 10 Memory 16 GB RAM Hard Drive 512GB PCIe Solid State Drive Video Card NVIDIA GeForce GTX 1050 with 4GB GDDR5 Display 15.6" 4K Ultra HD (3840 x 2160) InfinityEdge touch display Audio and Speakers Stereo Speaker, Dual Microphones, High Definition Audio with Waves MaxxAudio® Pro Camera Widescreen HD (720p) webcam with dual array digital microphones Wireless Killer 1535 802.11ac 2x2 WiFi and Bluetooth 4.1 Primary Battery 97WHr Ports 1 HDMI 1.4 2 USB 3.0 with PowerShare 1 Thunderbolt 3 (2 lanes of PCI Express Gen 3) Supports: Power In / Charging, PowerShare, Thunderbolt 3 (40Gbps Bi-Directional), 3.1 USB Gen 2 (10Gbps), VGA, HDMI, Ethernet and USB-A via Dell Adapter (Sold Separately) Slots 2 SoDIMMs SD Card Reader (SD, SDHC, SDXC) Kensington Lock Slot Dimensions Size (H x W x D) 14.06 x 9.27 x 0.45 – 0.66 inch 357 x 235 x 11-17 mm Weight 4.5 lbs (2kg) Free 24 Hour Delivery in UAE We offer express delivery to Dubai, Abu Dhabi, Al Ain, Sharjah, Ajman, Ras Al Khaimah, Fujairah, Umm Al Quwain, UAE for Dell XPS 15-1063 Touch Laptop (Intel Core i7-7700HQ -2.8GHz, 15.6-Inch Touch QHD+ , 16GB Ram, 512GB SSD, 4GB GTX1050, Windows 10, Gray) | 15-1063. Best Price Guarantee We offer the best price for Dell XPS 15-1063 Touch Laptop (Intel Core i7-7700HQ -2.8GHz, 15.6-Inch Touch QHD+ , 16GB Ram, 512GB SSD, 4GB GTX1050, Windows 10, Gray) | 15-1063 in Dubai, UAE. Buy now with the best price! Read the full article
0 notes
Text
I was facing an issue recently and it is like this. I run a Ubuntu Linux Virtual Machine on a Windows guest. Because of my specific requirements I need to connect to a specific AP (wifi router) from a Windows machine.
Now, when I run my VM in Bridge mode I do not get any IP on the VM.
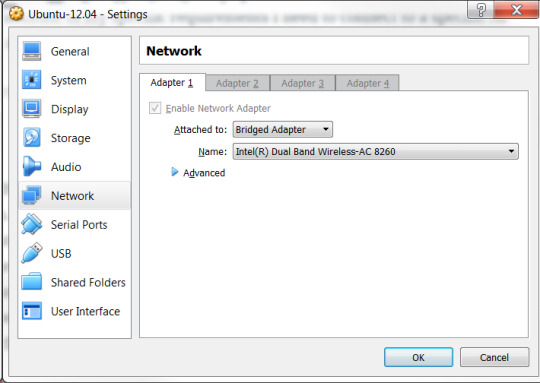
vbhadra@vbhadra-VirtualBox:~$ ifconfig eth0 Link encap:Ethernet HWaddr 08:00:27:1a:13:10 inet6 addr: fe80::a00:27ff:fe1a:1310/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:8819 errors:0 dropped:0 overruns:0 frame:0 TX packets:7621 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:4477485 (4.4 MB) TX bytes:3415333 (3.4 MB) lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:1671 errors:0 dropped:0 overruns:0 frame:0 TX packets:1671 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:157039 (157.0 KB) TX bytes:157039 (157.0 KB)
As you can see above the VM has got no IP at this point.
However, if I put the VM network in NAT mode then I get an IP which is good for all practical purposes.
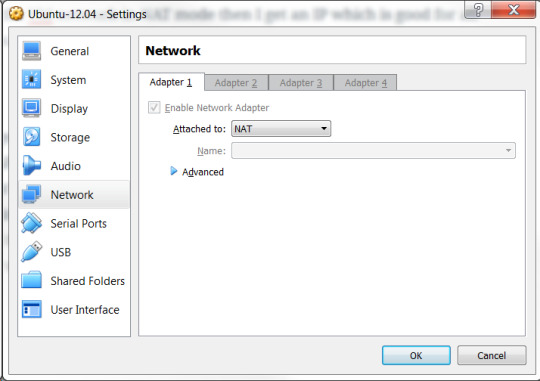
vbhadra@vbhadra-VirtualBox:~$ ifconfig eth0 Link encap:Ethernet HWaddr 08:00:27:1a:13:10 inet addr:10.0.2.15 Bcast:10.0.2.255 Mask:255.255.255.0 inet6 addr: fe80::a00:27ff:fe1a:1310/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:8821 errors:0 dropped:0 overruns:0 frame:0 TX packets:7657 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:4478330 (4.4 MB) TX bytes:3422460 (3.4 MB) lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:1703 errors:0 dropped:0 overruns:0 frame:0 TX packets:1703 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:159423 (159.4 KB) TX bytes:159423 (159.4 KB)
As can be seen the VM now, has got an IP 10.0.2.15. When you put your VM network adapter in NAT mode a private network is created for connecting to the host network through NAT.
This is not to suggest that if VM network adapter is in Bridge it should not get an IP from the host, as with another AP I get an IP. This seems depend on a FireWall setting or configuration on the AP your host is connected to. Somehow it doesn’t allow for the VM to have an IP when in Bridge mode.
Problem for me is if my VM is in NAT mode I do not be able to use FileZilla to transfer files between the Windows and the VM.
I am too used to using FileZilla and hence, did not try finding if there is any other options but tried resolving the problem in hand quickly.
To get over this issue you need to create a port forwarding rule on VirtualBox Network settings. This is how I got the issue resolved:
Go to the VirtualBox Box Manager (version 5.1.30) -> Netwok

Click on the Advanced button.
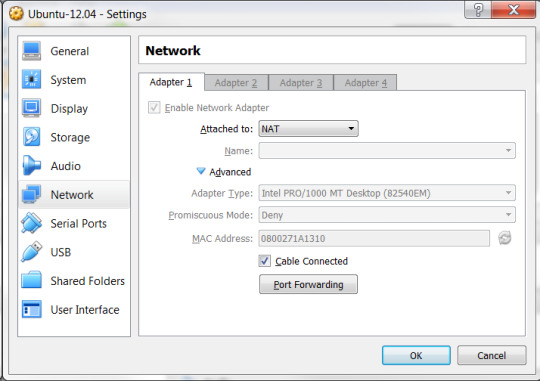
Click on Port Forwarding.

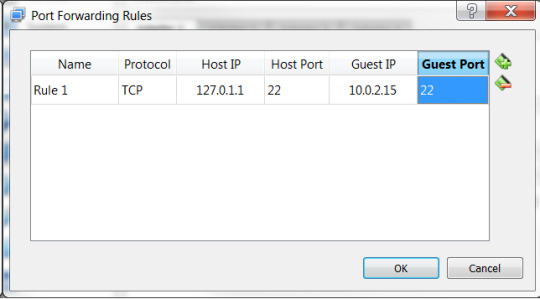
Click on the Add (+) sign on the right top corner.
Create a new rule as below:
Now, go back to your FileZilla and go to the site manager, fill in the following fields as the below example, Host: 127.0.1.1 (host loopback address), Port: 22, Protocol: SFTP, Logon Type: Normal, enter your Username and password and connect.
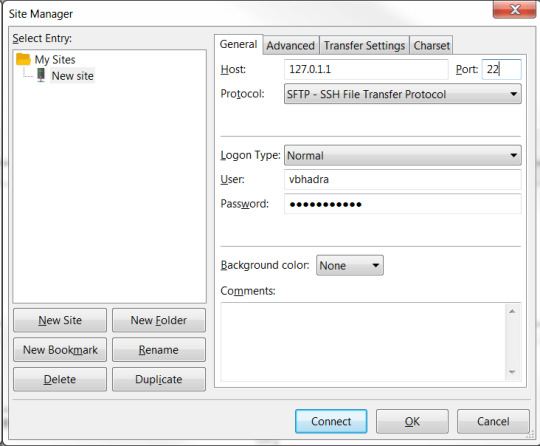
Now I can connect to my VM machine and transfer files easily as can be seen below:
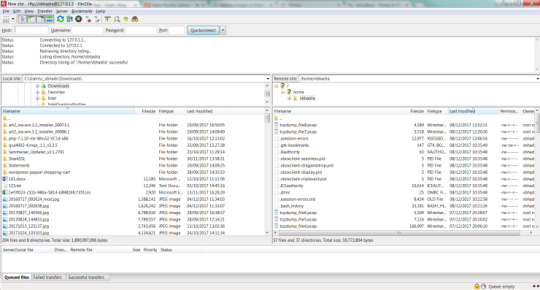
If you have any question or query please feel free to post a comment in the below section.
How to access Ubuntu Linux Virtual Machine in NAT mode using FileZilla from Windows Host I was facing an issue recently and it is like this. I run a Ubuntu Linux Virtual Machine on a Windows guest.
0 notes
Text
Do You Want To Connect Alexa Device To A New Wi-Fi Network?
Amazon Alexa is one of the most famous devices that has made the lives of the people easy. You need Alexa App to access the Echo device. It is a virtual voice assistant smart speaker that works on your simple Wake Words. Alexa can do many things for your daily life such as Play your favorite music, set alarms, and reminders, provide you daily weather news updates, control smart home devices, manage your daily to-do list, and a lot more. You can download the Alexa App for Android, Mac, Windows, and iOS Operating system. You can easily connect your Echo device with the WiFi Network. If you want assistance for Connect Alexa to WiFi, then contact the professionals. Our professionals are always ready to meet the exact demands of the customers.
Easy Steps to Connect Alexa Device to a New Wi-Fi Network
The foremost thing that you must keep in mind is that you should have a good Internet connection. Download the Alexa App from the Play Store or official website of Amazon. It is important to download the latest and compatible version of Alexa. In case you find any difficulty while connecting Alexa with the WiFi Network, then follow the below-described steps:-
Initially, open the Alexa App
Then click on the Menu Button and then choose the ‘Settings’ option from the drop-down menu.
Now choose the Device.
Click on update Wi-Fi Option
Then Select the connect to the ‘Wi-Fi’ button option.
Now you are advised to follow all the on-screen instructions to place your Echo device in a setup mode.
Turn on your Echo device by using the included power adapter. Once it is powered on, you will be able to see the lights ring changes to orange color. It indicated that Alexa Greets you.
Click on the ‘Continue’ button
Now you will be able to see the list of all the Wi-Fi networks.
Choose your network in order to connect Alexa App with the Internet and then enter the right password when prompted.
Finally, your Echo Device & Alexa App is successfully connected to the Internet.
If you find yourself stuck while Connect Alexa To WiFi, then directly contact the professionals. Our team of professionals is available 24/7 hours; do not hesitate to contact us. We have experts who are highly skilled and experienced. They will deeply analyze all the common issues that customers usually face. The solutions provided by the professionals will surely help you in any way. Get the best possible solution from us. Dial our helpline number and get instant services.
0 notes
Link
Become an ethical hacker that can hack computer systems like black hat hackers and secure them like security experts.
ETHICAL HACKING
Best Seller
Created by Zaid Sabih, z Security
Last updated 9/2018
English
What Will I Learn?
120 detailed videos about ethical hacking & computer security
Learn what is ethical hacking, its fields and the different types of hackers
Set up a lab environment to practice hacking
Learn how to hack into networks, both wifi and wired, and how to secure them
Discover vulnerabilities in remote servers and exploit them gain full control over these servers
Gather information and hack secure systems using client-side and social engineering attacks
Understand how websites work, how to discover and exploit web application vulnerabilities to gain full control over websites
Secure systems from all the attacks shown
Install Kali Linux – a penetration testing operating system
Install windows & vulnerable operating systems as virtual machines for testing
Learn linux basics
Learn linux commands and how to interact with the terminal
Learn Network Penetration Testing
Network basics & how devices interact inside a network
A number of practical attacks that can be used without knowing the key to the target network
Control connections of clients around you without knowing the password.
Create a fake Wi-Fi network with internet connection & spy on clients
Gather detailed information about clients and networks like their OS, opened ports …etc.
Crack WEP/WPA/WPA2 encryptions using a number of methods.
ARP Spoofing/ARP Poisoning
Launch Various Man In The Middle attacks.
Gain access to any account accessed by any client in your network.
Sniff packets from clients and analyse them to extract important info such as: passwords, cookies, urls, videos, images ..etc.
Discover open ports, installed services and vulnerabilities on computer systems
Gain control over computer systems using server side attacks
Exploit buffer over flows and code execution vulnerabilities to gain control over systems
Gain control over computer systems using client side attacks
Gain control over computer systems using fake updates
Gain control over computer systems by backdooring downloads on the fly
Create undetectable backdoors
Backdoor normal programs
Backdoor any file type such as pictures, pdf’s …etc.
Gather information about people, such as emails, social media accounts, emails and friends
Use social engineering to gain full control over target systems
Send emails from ANY email account without knowing the password for that account
Read, write download, upload and execute files on compromised systems
Capture keystrokes on a compromised system
Use a compromised computer as a pivot to gain access to other computers on the same network
Understand how websites & web applications work
Understand how browsers communicate with websites
Gather sensitive information about websites
Discover servers, technologies and services used on target website
Discover emails and sensitive data associated with a specific website
Find all subdomains associated with a website
Discover unpublished directories and files associated with a target website
Find all websites hosted on the same server as the target website
Exploit file upload vulnerabilities & gain full control over the target website
Discover, exploit and fix code execution vulnerabilities
Discover, exploit & fix local file inclusion vulnerabilities
Discover, fix, and exploit SQL injection vulnerabilities
Bypass login forms and login as admin using SQL injections
Writing SQL queries to find databases, tables and sensitive data such as usernames and passwords using SQL injections
Read / Write files to the server using SQL injections
Learn the right way to write SQL queries to prevent SQL injections
Discover reflected XSS vulnerabilities
Discover Stored XSS vulnerabilities
Hook victims to BeEF using XSS vulnerabilities
Fix XSS vulnerabilities & protect yourself from them as a user
Requirements
Basic IT Skills
No Linux, programming or hacking knowledge required.
Computer with a minimum of 4GB ram/memory
Operating System: Windows / OS X / Linux
For the wifi cracking ONLY – Wireless adapter that supports monitor mode (more info provided in the course).
Description
Welcome to my comprehensive course on Ethical Hacking! In this course, you will start as a beginner with no previous knowledge about penetration testing or hacking. The first thing you will learn is some basic information about ethical hacking and the different fields in penetration testing.
This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. Before jumping into penetration testing, you will first learn how to set up a lab and install needed software to practice penetration testing on your own machine. All the attacks explained in this course are launched against real devices in my lab.
The course is structured in a way that will take you through the basics of linux, computer systems, networks and how devices communicate with each other. We will start by talking about how we can exploit these systems to carry out a number of powerful attacks. This course will take you from a beginner to a more advanced level — by the time you finish, you will have knowledge about most penetration testing fields.
The course is divided into four main sections:
1. Network Penetration Testing – This section will teach you how to test the security of networks, both wired and wireless. First, you will learn how networks work, basic network terminology and how devices communicate with each other. Then it will branch into three sub sections:
Pre-connection: in this section, we still don’t know much about penetration testing — all we have is a computer with a wireless card. You will learn how gather information about the networks and computers around you and launch a number of attacks without a password, such as controlling the connections around you (ie: deny/allow any device from connecting to any network). You will also learn how to create a fake access point, attract users to connect to it and capture any important information they enter.
Gaining Access: Now that you have gathered information about the networks around you and found your target, you will learn how to crack the key and gain access to your target network. In this section you will learn a number of methods to crack WEP/WPA/WPA2 encryption.
Post Connection: Now you have the key to your target network and you can connect to it. In this section you will learn a number of powerful attacks that can be launched against the network and connected clients. These attacks will allow you to gain access to any account accessed by any device connected to your network and read all the traffic used by these devices (images, videos, audio, passwords …etc).
2. Gaining Access – In this section you will learn two main approaches to gain full control over any computer system:
Server Side Attacks: In this approach you will learn how to gain full access to computer systems without the need for user interaction. You will learn how to gather information about a target computer system such as its operating system, open ports, installed services and discover weaknesses and vulnerabilities. You will also learn how to exploit these weaknesses to gain full control over the target. Finally you will learn how to generate different types of reports for your discoveries.
Client Side Attacks – If the target system does not contain any weaknesses then the only way to gain access to it is by interacting with the user. In this approach you will learn how to launch a number of powerful attacks to fool the target user and get them to install a backdoor on their device. This is done by creating fake updates and serving them to the user or by backdoornig downloaded files on the fly. You will also learn how to gather information about the target person and use social engineering to deliver a backdoor to them as an image or any other file type.
3. Post Exploitation – In this section you will learn how to interact with the systems you compromised so far. You’ll learn how to access the file system (read/write/upload/execute), maintain your access, spy on the target and even use the target computer as a pivot to hack other computer systems.
4. Web Application Penetration Testing – In this section you will learn how websites work. Then you will learn how to gather information about your target website, such as website owner, server location, used technologies and much more. You will also learn how to discover and exploit a number of dangerous vulnerabilities such as SQL injections, XSS vulnerabilities, etc.
At the end of each section you will learn how to detect, prevent and secure your system and yourself from these attacks.
All the attacks in this course are practical attacks that work against any computer device, ie: it does not matter if the device is a phone, tablet, laptop, etc. Each attack is explained in a simple way — first you will learn the theory behind each attack and then you will learn how to carry out the attack using Kali Linux.
NOTE: This course is created for educational purposes only and all the attacks are launched in my own lab or against devices that I have permission to test.
NOTE: This course is totally a product of Zaid Sabih and no other organisation is associated with it or a certification exam. Although, you will receive a Course Completion Certification from Udemy, apart from that NO OTHER ORGANISATION IS INVOLVED.
Who is the target audience?
Anybody who is interested in learning ethical hacking / penetration testing
Anybody who wants to learn how hackers hack computer systems
Anybody who wants to learn how to secure their systems from hackers
Size: 5.0GB
DOWNLOAD TUTORIAL
The post LEARN ETHICAL HACKING FROM SCRATCH appeared first on GetFreeCourses.Me.
0 notes
Link
https://ift.tt/2Seq8ax
Learn Ethical Hacking From Scratch
Become an ethical hacker that can hack computer systems like black hat hackers and secure them like security experts.
What Will I Learn?
· 120 detailed videos about ethical hacking & computer security
· Know what is hacking, ethical hacking and different types of hackers
· Learn about the different fields of ethical hacking
· Set up a lab environment to practice hacking
· Install Kali Linux – a penetration testing operating system
· Install windows & vulnerable operating systems as virtual machines for testing
· Learn Linux basics
· Learn Linux commands and how to interact with the terminal
· Learn Network Penetration Testing
· Network basics & how devices interact inside a network
· A number of practical attacks that can be used without knowing the key to the target network
· Control connections of clients around you without knowing the password.
· Create a fake Wi-Fi network with internet connection & spy on clients
· Gather detailed information about clients and networks like their OS, opened ports …etc.
· Crack WEP/WPA/WPA2 encryptions using a number of methods.
· ARP Spoofing/ARP Poisoning
· Launch Various Man in The Middle attacks.
· Gain access to any account accessed by any client in your network.
· Sniff packets from clients and analyses them to extract important info such as: passwords, cookies, URLs, videos, images etc.
· Discover open ports, installed services and vulnerabilities on computer systems
· Gain control over computer systems using server-side attacks
· Exploit buffer over flows and code execution vulnerabilities to gain control over systems
· Gain control over computer systems using client-side attacks
· Gain control over computer systems using fake updates
· Gain control over computer systems by backdooring downloads on the fly
· Create undetectable backdoors
· Backdoor normal programs
· Backdoor any file type such as pictures, pdf’s …etc.
· Gather information about people, such as emails, social media accounts, emails and friends
· Use social engineering to gain full control over target systems
· Send emails from ANY email account without knowing the password for that account
· Read, write download, upload and execute files on compromised systems
· Capture key strikes on a compromised system
· Use a compromised computer as a pivot to gain access to other computers on the same network
· Understand how websites & web applications work
· Understand how browsers communicate with websites
· Gather sensitive information about websites
· Discover servers, technologies and services used on target website
· Discover emails and sensitive data associated with a specific website
· Find all subdomains associated with a website
· Discover unpublished directories and files associated with a target website
· Find all websites hosted on the same server as the target website
· Exploit file upload vulnerabilities & gain full control over the target website
· Discover, exploit and fix code execution vulnerabilities
· Discover, exploit & fix local file inclusion vulnerabilities
· Discover, fix, and exploit SQL injection vulnerabilities
· Bypass login forms and login as admin using SQL injections
· Writing SQL queries to find databases, tables and sensitive data such as usernames ad passwords using SQL injections
· Read / Write files to the server using SQL injections
· Learn the right way to write SQL queries to prevent SQL injections
· Discover reflected XSS vulnerabilities
· Discover Stored XSS vulnerabilities
· Hook victims to BeEF using XSS vulnerabilities
· Fix XSS vulnerabilities & protect yourself from them as a user
Requirements
· Basic IT Skills
· No Linux, programming or hacking knowledge required.
· Computer with a minimum of 4GB ram/memory
· Operating System: Windows / OS X / Linux
· For the WIFI cracking ONLY – Wireless adapter that supports monitor mode (more info provided in the course).
Description
Welcome to my comprehensive course on Ethical Hacking! In this course, you will start as a beginner with no previous knowledge about penetration testing or hacking. The first thing you will learn is some basic information about ethical hacking and the different fields in penetration testing.
This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. Before jumping into penetration testing, you will first learn how to set up a lab and install needed software to practice penetration testing on your own machine. All the attacks explained in this course are launched against real devices in my lab.
The course is structured in a way that will take you through the basics of Linux, computer systems, networks and how devices communicate with each other. We will start by talking about how we can exploit these systems to carry out a number of powerful attacks. This course will take you from a beginner to a more advanced level — by the time you finish, you will have knowledge about most penetration testing fields.
The course is divided into four main sections:
1. Network Penetration Testing – This section will teach you how to test the security of networks, both wired and wireless. First, you will learn how networks work, basic network terminology and how devices communicate with each other. Then it will branch into three sub sections:
Pre-connection: in this section, we still don’t know much about penetration testing — all we have is a computer with a wireless card. You will learn how gather information about the networks and computers around you and launch a number of attacks without a password, such as controlling the connections around you (i.e.: deny/allow any device from connecting to any network). You will also learn how to create a fake access point, attract users to connect to it and capture any important information they enter.
Gaining Access: Now that you have gathered information about the networks around you and found your target, you will learn how to crack the key and gain access to your target network. In this section you will learn a number of methods to crack WEP/WPA/WPA2 encryption.
Post Connection: Now you have the key to your target network and you can connect to it. In this section you will learn a number of powerful attacks that can be launched against the network and connected clients. These attacks will allow you to gain access to any account accessed by any device connected to your network and read all the traffic used by these devices (images, videos, audio, passwords …etc.).
2. Gaining Access – In this section you will learn two main approaches to gain full control over any computer system:
Server-Side Attacks: In this approach you will learn how to gain full access to computer systems without the need for user interaction. You will learn how to gather information about a target computer system such as its operating system, open ports, installed services and discover weaknesses and vulnerabilities. You will also learn how to exploit these weaknesses to gain full control over the target. Finally, you will learn how to generate different types of reports for your discoveries.
Client-Side Attacks – If the target system does not contain any weaknesses then the only way to gain access to it is by interacting with the user. In this approach you will learn how to launch a number of powerful attacks to fool the target user and get them to install a backdoor on their device. This is done by creating fake updates and serving them to the user or by backdooring downloaded files on the fly. You will also learn how to gather information about the target person and use social engineering to deliver a backdoor to them as an image or any other file type.
3. Post Exploitation – In this section you will learn how to interact with the systems you compromised so far. You’ll learn how to access the file system (read/write/upload/execute), maintain your access, spy on the target and even use the target computer as a pivot to hack other computer systems.
4. Web Application Penetration Testing – In this section you will learn how websites work. Then you will learn how to gather information about your target website, such as website owner, server location, used technologies and much more. You will also learn how to discover and exploit a number of dangerous vulnerabilities such as SQL injections, XSS vulnerabilities, etc.
At the end of each section you will learn how to detect, prevent and secure your system and yourself from these attacks.
All the attacks in this course are practical attacks that work against any computer device, ie: it does not matter if the device is a phone, tablet, laptop, etc. Each attack is explained in a simple way — first you will learn the theory behind each attack and then you will learn how to carry out the attack using Kali Linux.
NOTE: This course is created for educational purposes only and all the attacks are launched in my own lab or against devices that I have permission to test.
NOTE: This course is totally a product of Zaid Sabih and no other organization is associated with it or a certification exam. Although, you will receive a Course Completion Certification from Udemy, apart from that NO OTHER ORGANISATION IS INVOLVED.
Who is the target audience?
Anybody who is interested in learning ethical hacking/penetration testing
Anybody who wants to learn how hackers hack computer systems
Anybody who wants to learn how to secure their systems from hackers.
0 notes
Text
[Udemy] Learn Ethical Hacking From Scratch
Become an ethical hacker that can hack computer systems like black hat hackers and secure them like security experts. What Will I Learn? 120 detailed videos about ethical hacking & computer security Learn what is ethical hacking, its fields and the different types of hackers Set up a lab environment to practice hacking Learn how to hack into networks, both wifi and wired, and how to secure them Discover vulnerabilities in remote servers and exploit them gain full control over these servers Gather information and hack secure systems using client-side and social engineering attacks Understand how websites work, how to discover and exploit web application vulnerabilities to gain full control over websites Secure systems from all the attacks shown Install Kali Linux - a penetration testing operating system Install windows & vulnerable operating systems as virtual machines for testing Learn linux basics Learn linux commands and how to interact with the terminal Learn Network Penetration Testing Network basics & how devices interact inside a network A number of practical attacks that can be used without knowing the key to the target network Control connections of clients around you without knowing the password. Create a fake Wi-Fi network with internet connection & spy on clients Gather detailed information about clients and networks like their OS, opened ports …etc. Crack WEP/WPA/WPA2 encryptions using a number of methods. ARP Spoofing/ARP Poisoning Launch Various Man In The Middle attacks. Gain access to any account accessed by any client in your network. Sniff packets from clients and analyse them to extract important info such as: passwords, cookies, urls, videos, images ..etc. Discover open ports, installed services and vulnerabilities on computer systems Gain control over computer systems using server side attacks Exploit buffer over flows and code execution vulnerabilities to gain control over systems Gain control over computer systems using client side attacks Gain control over computer systems using fake updates Gain control over computer systems by backdooring downloads on the fly Create undetectable backdoors Backdoor normal programs Backdoor any file type such as pictures, pdf’s …etc. Gather information about people, such as emails, social media accounts, emails and friends Use social engineering to gain full control over target systems Send emails from ANY email account without knowing the password for that account Read, write download, upload and execute files on compromised systems Capture keystrokes on a compromised system Use a compromised computer as a pivot to gain access to other computers on the same network Understand how websites & web applications work Understand how browsers communicate with websites Gather sensitive information about websites Discover servers, technologies and services used on target website Discover emails and sensitive data associated with a specific website Find all subdomains associated with a website Discover unpublished directories and files associated with a target website Find all websites hosted on the same server as the target website Exploit file upload vulnerabilities & gain full control over the target website Discover, exploit and fix code execution vulnerabilities Discover, exploit & fix local file inclusion vulnerabilities Discover, fix, and exploit SQL injection vulnerabilities Bypass login forms and login as admin using SQL injections Writing SQL queries to find databases, tables and sensitive data such as usernames and passwords using SQL injections Read / Write files to the server using SQL injections Learn the right way to write SQL queries to prevent SQL injections Discover reflected XSS vulnerabilities Discover Stored XSS vulnerabilities Hook victims to BeEF using XSS vulnerabilities Fix XSS vulnerabilities & protect yourself from them as a user Requirements Basic IT Skills No Linux, programming or hacking knowledge required. Computer with a minimum of 4GB ram/memory Operating System: Windows / OS X / Linux For the wifi cracking ONLY - Wireless adapter that supports monitor mode (more info provided in the course). Description Welcome to my comprehensive course on Ethical Hacking! In this course, you will start as a beginner with no previous knowledge about penetration testing or hacking. The first thing you will learn is some basic information about ethical hacking and the different fields in penetration testing. This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. Before jumping into penetration testing, you will first learn how to set up a lab and install needed software to practice penetration testing on your own machine. All the attacks explained in this course are launched against real devices in my lab. The course is structured in a way that will take you through the basics of linux, computer systems, networks and how devices communicate with each other. We will start by talking about how we can exploit these systems to carry out a number of powerful attacks. This course will take you from a beginner to a more advanced level – by the time you finish, you will have knowledge about most penetration testing fields. The course is divided into four main sections: 1. Network Penetration Testing - This section will teach you how to test the security of networks, both wired and wireless. First, you will learn how networks work, basic network terminology and how devices communicate with each other. Then it will branch into three sub sections: Pre-connection: in this section, we still don’t know much about penetration testing – all we have is a computer with a wireless card. You will learn how gather information about the networks and computers around you and launch a number of attacks without a password, such as controlling the connections around you (ie: deny/allow any device from connecting to any network). You will also learn how to create a fake access point, attract users to connect to it and capture any important information they enter. Gaining Access: Now that you have gathered information about the networks around you and found your target, you will learn how to crack the key and gain access to your target network. In this section you will learn a number of methods to crack WEP/WPA/WPA2 encryption. Post Connection: Now you have the key to your target network and you can connect to it. In this section you will learn a number of powerful attacks that can be launched against the network and connected clients. These attacks will allow you to gain access to any account accessed by any device connected to your network and read all the traffic used by these devices (images, videos, audio, passwords …etc). 2. Gaining Access - In this section you will learn two main approaches to gain full control over any computer system: Server Side Attacks: In this approach you will learn how to gain full access to computer systems without the need for user interaction. You will learn how to gather information about a target computer system such as its operating system, open ports, installed services and discover weaknesses and vulnerabilities. You will also learn how to exploit these weaknesses to gain full control over the target. Finally you will learn how to generate different types of reports for your discoveries. Client Side Attacks - If the target system does not contain any weaknesses then the only way to gain access to it is by interacting with the user. In this approach you will learn how to launch a number of powerful attacks to fool the target user and get them to install a backdoor on their device. This is done by creating fake updates and serving them to the user or by backdoornig downloaded files on the fly. You will also learn how to gather information about the target person and use social engineering to deliver a backdoor to them as an image or any other file type. 3. Post Exploitation - In this section you will learn how to interact with the systems you compromised so far. You’ll learn how to access the file system (read/write/upload/execute), maintain your access, spy on the target and even use the target computer as a pivot to hack other computer systems. 4. Web Application Penetration Testing - In this section you will learn how websites work. Then you will learn how to gather information about your target website, such as website owner, server location, used technologies and much more. You will also learn how to discover and exploit a number of dangerous vulnerabilities such as SQL injections, XSS vulnerabilities, etc. At the end of each section you will learn how to detect, prevent and secure your system and yourself from these attacks. All the attacks in this course are practical attacks that work against any computer device, ie: it does not matter if the device is a phone, tablet, laptop, etc. Each attack is explained in a simple way – first you will learn the theory behind each attack and then you will learn how to carry out the attack using Kali Linux. NOTE: This course is created for educational purposes only and all the attacks are launched in my own lab or against devices that I have permission to test. NOTE: This course is totally a product of Zaid Sabih and no other organisation is associated with it or a certification exam. Although, you will receive a Course Completion Certification from Udemy, apart from that NO OTHER ORGANISATION IS INVOLVED. Who is the target audience? Anybody who is interested in learning ethical hacking / penetration testing Anybody who wants to learn how hackers hack computer systems Anybody who wants to learn how to secure their systems from hackers source https://ttorial.com/learn-ethical-hacking-scratch
source https://ttorialcom.tumblr.com/post/178289755618
0 notes
Text
The iPhone Home Display has area for 20 app symbols on the front page as well as four Dock icons across all-time low, with even more application places readily available for the iPad. Currently you will obtain an additional display requesting for a credit card, Visa is the default, faucet on Visa as well as scroll down to None." After choosing none, fill in the rest of the required info and tap following. Downloading your pictures to computer system without iTunes is all-natural to the means a computer system sees the apple iphone. Likewise, there is said to be plans for a lower-cost free iPhone 5c giveaway making a launching along side the 5S when released, this iPhone allegedly is constructed of plastic (assume 3GS) and also will have a much lower cost to assist out those that want an iPhone yet don't intend to spend the huge amounts of cash money or sign a two-year agreement to obtain it subsided. When getting, you will certainly have entered your Apple ID password, suggesting that your bank card will certainly be billed from October onwards. Mobile - must just be accessed using your mobile phone since the deals are only for smart phones. Finally, when a trouble with an Apple item becomes specifically prevalent, there's an opportunity that Apple will certainly set up a complimentary replacement program. Free Ringtone Downloader is an easy-to-use ringtone downloader application that gives you sharp tones for new text, new email, wakeup signals, as well as calendar informs. AppleCare+ for apple iphone extends your coverage to 2 years from the original purchase find this Home Page Visit This Link read more find more read here Learn More Click Here http://bit.ly/2oVLkXH http://howtogetafreeiphone.info day of your iPhone and also amounts to two cases of unintended damage coverage. Bear in mind that you'll entirely aim each provide just one celebration, also for different free iPhone sites! A firm named Transcendent Advancements (TRAINN) is a Grade A business which possesses a website called that offers cost-free iPhones. As soon as you have actually completed your deal (I did the Homestead free test), you're ready to begin referring people to accumulate your quota. This protective, dual-layered instance for apple iphone 7 uses a smooth soft touch finish and ultra slim layout. IPVanish is an excellent VPN for iPhone that is based in the United States (residence of the NSA as well as CIA). The VPNs for iPhone recommended most of all offer lightning quick rates, so you could enjoy the internet as you were implied to. If you're utilizing iCloud Image Collection and also have Maximize Storage space" activated, downloading and install a big application will remove pictures from your device first, after that clean out storage in applications second. The business has likewise increased the storage capability of its budget plan apple iphone SE, which begins at $399 and is now readily available with 32GB or 128GB of storage space. Federico Basso: Prendilo con FREE, hai un sacco di giga e ogni anno lo cambi disadvantage l'ultimo apple iphone. That apple iphone will get me a $650 credit rating toward any kind of iPhone 7 I desire if I do it via AT&T Next. Apple is stated the iOS 8 has much better automobile emphasis for both phones, with the Plus version having an optical stabilization unique to it. Both versions fire slow-moving movement video clip at 240 FPS, a boost from the 120 FPS found in the iPhone FIVE. Also new to the 6 is the capability to shoot HDR video clip as well as an updated front encountering electronic camera that could currently shoot 720p video/pictures. Put details, nous utilisons Windows 7 (la procédure est identique pour home windows View). The omission of a traditional earphone jack is a controversial adjustment (as well as we have a short article regarding taking care of phones that have actually gone down the jack ). Apple does, nonetheless, include both a Lightning-connector version of the firm's EarPods earbuds and a Lightning-connector-to-3.5-mm adapter for using any type of headphones with a traditional earphone miniplug; you could additionally use Bluetooth earphones as with other phone. As an example, our Pages app has 4.9 MEGABYTES of data; with a little tidying up we might ensure that those papers minimized the iPhone were moved to the Cloud where we have a whole lot more room. Una terza coppia sta arrivando, la vediamo attraverso lo schermo di un iPhone 7, il nuovo smartphone oggetto dell' offerta FREE di questa campagna. Its upgrades are virtually identical to those found in the iPhone 6s, its size being the only considerable difference between the two. If you do not have any type of copy on your computer, you could utilize AnyTrans to move songs from iPhone to computer system to start with for backup and after that erase them from your device. The 1st-generation apple iphone as well as apple iphone 3G have a fixed-focus 2.0- megapixel cam on the back for electronic images. This trade-in may be among the least expensive methods to get the brand-new apple iphone, without should offer a leg and also an arm. A lot of applications exist for transferring material in between your computer system as well as your tool, yet Dropbox is totally free and also easier to use than most of its contemporaries. So if you guys produce freebies, or are marketing electronic documents you ought to look into Sellfy and open a cost-free account!. You only get 2 possibilities for a replacement, though, and it sets you back ₤ 79 - and there's a chance you'll be billed a ₤ 55 excess fee as well. This is an overview of selling your existing iPhone to cover the price of a newer model, otherwise more-- something I have actually performed with practically every iPhone launch with fantastic results. As well as if I update my apple iphone 5 to a 5S or far better, I can get the WIFI contacting my phone which indicates as soon as I'm attached to WI-FI, I can make/receive calls for totally free to my friends/family in the United States. For all global tourists, THIS is the strategy to have. If you ran marketing department at your company as well as were able to obtain 100,000 people to attempt a brand-new product making use of a discount coupon for complimentary sample, think of.
0 notes
Text
Basic Functionalities of EZ Cast Dongle
EZCast WiFi display dongle is the 1st Miracast (Wi-Fi Direct), DLNA and AirPlay universal adapter that supports Miracast, DLNA and AirPlay concurrently. With the all-in-one dongle users can easily cast/mirror the videos, photos, games and files from Android Smartphone/tablet PCs, iPad/iPhone,desktop PC/Notebook, to HDTV or projector through HDMI port wirelessly (Run EZCast for all users, or EZAir for iPhone/iPad users, or Miracast for Android phone/Android pad users), or push all the video, photo, and files to from the above mentioned devices to HDTV or projector (run DLNA)for entertainment or for business.
Basic features of Ezcast dongle:
• Multi OS support: Android, iOS, Windows, Mac OS
• Multiprotocol/standard support: Miracast, DLNA, AirPlay and private WiFi display technology.
• EZCast, for universal support
• Highly integrated Actions
• SoC
• Simple to operate
• Most compact, Power consumption
• Fast connection & low latency for superior experience
• H.264 1080P full HD video decode
• LPCM Audio Decode
• HDMI v1.3 video output
• HDCP 2.x
• Auto channel selection with high quality video streaming
• WiFi module support IEEE 801.11 b/g/n up to 150Mbps data rate with WiFi Direct capability
• Flexible power using TV standard USB port (5V/400mA) or external USB power supply.
Internet setting with Wifi EZ Cast:
Click on [Internet] to connect to your wireless AP/router for internet access.The EZCast WiFi display then works as an AP + repeater casting/mirroring/pushing online content or OTA ( O n-the-Air) firmware upgrading. This is the unique feature of EZCast dongle.
System Upgrade wifi EZ Cast:
Click [Upgrade] to upgrade EZCast firmware and AP/APK OTA (On the Air) online.Please make sure the internet connection and power supply is stable prior to upgrading.
Virtual Remote Control
To u s e the on-screen virtual wireless remote controller to change the move direction, and the center button [OK] is to confirm operation. Click [Back]to back to previous screen, or click [keyboard to enable virtual keyboard and input password.
Buy EZ Cast Dongle online to save big and enjoy unlimited entertainment right from the comfort of your living room. Get connected with your smartphone or other devices with the highest quality EZ cast dongle available online. Always try to buy from a reputed retailer to assure that you get the best value for your investment. There are many retailers online, so always make sure to research first before making any deal. A high quality EZ Cast dongle always ensures that you enjoy the best in terms of entertainment and functionality. So make your purchase wisely!
0 notes
Text
Lenovo launched the next generation of ThinkPad X1 products, the 2017 ThinkPad X1 Carbon, ThinkPad X1 Yoga, and ThinkPad X1 Tablet

In CES 2017, Lenovo launched the next generation of ThinkPad X1 products, the 2017 ThinkPad X1 Carbon, ThinkPad X1 Yoga, and ThinkPad X1 Tablet. The ThinkPad X1 Carbon is a familiar sight, but closer inspection reveals that it is smaller. In fact, in addition to being the lightest notebook in its class at under 2.5 pounds (1.14kg), it is also the smallest, fitting a high quality 14-inch IPS display into a typical 13-inch form factor. Despite the smaller size, there are no compromises here. The X1 Carbon continues to innovate as one of the thinnest, lightest and most durable notebooks around. A full complement of ports, infrared camera, connectivity and security ensure the X1 Carbon delivers maximum performance on all fronts. The six-row ThinkPad keyboard with an improved Microsoft Precision Touchpad (with physical buttons!) and iconic TrackPoint complete the picture.

Available in classic ThinkPad black and a new silver color, it is under the hood that the X1 Carbon comes into its own. Customers tell us that battery life is the single most important feature in a highly mobile business ultrabook, but not at the expense of security and connectivity. The improvements we’ve made are a direct result of constant analysis of customer feedback and user testing. New enhancements include: Enough battery life to board one of the world’s ultra-long-haul flights and have enough juice on arrival to message home. Users can now enjoy up to 15.5 hours, per MobileMark 2014. Qualcomm Snapdragon X7 LTE-A Wireless WAN offering up to three times faster LTE speeds and WIFI CERTIFIED WiGig options remain, but can now co-exist thanks to redesigned antenna placements. Thunderbolt 3 ports also make their appearance with up to eight times faster transfer speeds than USB 3.0 and 4k display connectivity. We’ve still managed to squeeze on a couple of type-A USB 3.0 ports and HDMI too. Expanded docking solutions with new Thunderbolt 3 and USB Type-C docks. In the last year, 689 million people have been victims of cybercrime and with 431 million new malware strains detected, device security has never been more critical. ThinkPad X1 Carbon is more secure than ever with multi-factor authentication improvements such as: ThinkPad has enhanced biometric authentication with the addition of an IR camera with face recognition support for Windows Hello logon. The Match-on-Chip touch fingerprint sensor adds another security layer. Enrolled data is processed in the sensor itself and all fingerprint images are handled inside the fingerprint processing unit preventing malicious logon access. ThinkPad X1 Carbon is also the first business-class notebook to support FIDO-enabled biometric authentication for PayPal. Intel Software Guard Extensions (SGX) secures users’ FIDO credentials and the Synaptics Natural ID fingerprint sensor features enterprise-level security with TLS 1.2 encryption. This hardware-level protection will enable users to authenticate to online FIDO-enabled services like PayPal by using a fingerprint instead of a password. ThinkPad X1 Yoga also gets updated treatment and the same silver option. Customers looking for a convertible notebook want the best Windows 10 experience possible with multi-mode flexibility, high performance functionality and pen use that feels more natural. The X1 Yoga excels, adapting to users’ various needs, with a redesigned rechargeable pen, a great visual experience and an improved unique keyboard. It also shares many of the improvements from the X1 Carbon, with improved security and a complete set of ports including Thunderbolt 3. Flying from New York to Tokyo or Dubai to Sydney is not a problem with up to 15 hours of battery life for the true mobile warrior. Key features include: Users will revel in the only 14-inch OLED notebook display option reproducing stunning colors, absolute blacks and 100 percent Adobe RGB color space. Intel Iris Graphics with dedicated high bandwidth, high speed memory delivering superior performance over Intel HD Graphics. We developed an improved ThinkPad Pen Pro for 2017 using a new soft elastomer tip. With bigger friction on glass, the pen recreates a more natural writing experience for users. Lenovo engineers further improved the unique rise and fall keyboard. The new keyboard retracts fully flat in tablet mode offering greater stability and user comfort and anchoring the keycaps delivers better long term key durability and reliability. The ThinkPad X1 Tablet combines 2-in-1 uncompromised design with enterprise-class features. For 2017, the MIL-SPEC tested X1 Tablet continues to impress customers with its light weight modularity and serviceability. The X1 Tablet modules offer port expansion and up to 5 hours’ extra battery life, or a properly integrated projection option for a seamless desk-to-projection experience. Simplified serviceability and a wide range of docking options make the X1 Tablet virtually unique in the detachable segment. @Technuter.com News Service Click to Post
0 notes