#Ethical Hacking Course with Job Guarantee
Explore tagged Tumblr posts
Text
How Blockchain Transforms Identity Management & Data Protection

In today’s digital era, identity management and data protection are critical issues faced by individuals, businesses, and governments worldwide. As cyber threats grow in sophistication, traditional methods of securing identities and sensitive data often fall short.
Enter blockchain technology a revolutionary solution redefining how we manage and protect information.
In this blog, we’ll explore How Blockchain Transforms Identity Management & Data Protection and its potential to address pressing security challenges.
For those keen to develop expertise in this field, enrolling in the Best Cyber Security Course in India can help you stay ahead in this rapidly evolving domain.
The Basics of Blockchain in Security
What Is Blockchain?
Blockchain is a decentralized, distributed ledger technology that ensures secure, immutable, and transparent record-keeping.
By leveraging cryptographic techniques and consensus mechanisms, blockchain eliminates the need for centralized authorities, making it highly secure and reliable.
Why Blockchain for Identity Management and Data Protection?
Immutability: Data once recorded on the blockchain cannot be altered, ensuring integrity.
Decentralization: Eliminates single points of failure, reducing the risk of breaches.
Transparency: Allows real-time verification without exposing sensitive data.
Enhanced Privacy: Users retain control over their data, sharing only what is necessary.
These features make blockchain a game-changer for identity management and data protection, offering robust solutions to modern cybersecurity challenges.
How Blockchain Transforms Identity Management
1. Self-Sovereign Identity
Redefining Ownership
Traditional identity systems rely on centralized entities like governments or corporations to manage and validate identities. Blockchain introduces the concept of self-sovereign identity, where individuals own and control their personal information.
Benefits:
Privacy: Users decide which data to share and with whom.
Security: Cryptographic keys ensure data is protected.
Interoperability: A single identity can be used across multiple platforms.
For professionals in a Cyber Security and Ethical Hacking Course in India, understanding self-sovereign identity is crucial as it represents the future of secure identity systems.
2. Digital Identity Verification
Simplifying Verification Processes
Blockchain streamlines identity verification by enabling quick and secure validation. Smart contracts on the blockchain can automate verification processes, reducing the risk of human error.
Applications:
Banking: Simplified KYC (Know Your Customer) processes.
Travel: Secure digital passports for hassle-free immigration.
Healthcare: Verifiable medical credentials for practitioners.
How Blockchain Enhances Data Protection
1. Decentralized Data Storage
Breaking Centralized Models
Traditional data storage systems are centralized, making them attractive targets for hackers. Blockchain’s decentralized nature distributes data across multiple nodes, significantly enhancing security.
Advantages:
Resilience: No single point of failure.
Tamper-Proof: Data integrity is guaranteed.
Scalability: Suitable for large-scale applications.
Courses like the Best Cyber Security Course in India provide hands-on training in leveraging blockchain for secure data storage.
2. Secure Data Sharing
Controlled Access
Blockchain enables secure data sharing through encrypted transactions and permissioned access. Users can share specific data with trusted parties without revealing unnecessary information.
Examples:
Healthcare: Patients sharing medical records with doctors.
Supply Chain: Businesses verifying product authenticity.
Legal: Secure sharing of contracts and sensitive documents.
3. Enhanced Authentication
Multi-Factor Authentication (MFA)
Blockchain can power advanced MFA systems by integrating biometric data, cryptographic keys, and decentralized authentication protocols. This approach reduces the risk of identity theft and unauthorized access.
Challenges and Opportunities in Blockchain Adoption
Challenges
Scalability: Blockchain networks must handle increasing data volumes efficiently.
Interoperability: Ensuring seamless integration with existing systems is critical.
Regulatory Compliance: Governments need to create frameworks for blockchain implementation.
Opportunities
Global Adoption: As blockchain matures, industries worldwide are exploring its applications.
Innovation: Startups are driving new blockchain solutions for identity and data protection.
Job Market Growth: Demand for blockchain and cybersecurity experts is surging.
Enrolling in a Cyber Security and Ethical Hacking Course in India equips professionals to tackle these challenges and seize opportunities in this exciting field.
Conclusion
How Blockchain Transforms Identity Management & Data Protection showcases the immense potential of this groundbreaking technology. From enabling self sovereign identities to enhancing data sharing and storage, blockchain is set to redefine cybersecurity paradigms.
If you aspire to master these cutting-edge concepts, consider joining the Cyber Security and Ethical Hacking Course in India. These programs offer practical insights and industry-relevant skills to excel in the evolving world of cybersecurity.
What are your thoughts on blockchain’s role in identity management and data protection? Share your insights in the comments below and join the conversation.
#Best Cyber Security Course in india#Cyber Security Classes in india#Cyber Security Professional Courses#best ethical hacking institute in india#Cyber Security and Ethical Hacking course in india#Best Ethical Hacking Certification Course in india#Cyber Security Part time Course in india#Ethical Hacking Course with Job Guarantee#Offline Cyber Security Course in india#Cyber Security Weekend Course in india
0 notes
Text
Ethical Hacking Course with Job Guarantee in Thane
The most impressive feature of this Ethical Hacking Course with Job Guarantee in Thane is job assurance after the completion of the course. The institute ties up with top technology companies and facilitates the employment of students based on their skill set.
0 notes
Text
Join our ethical hacking course and become a skilled defender of online security.
1. Completing 30 or more modules
2. Obtain international accreditation
3. Weekend and weekday batches
4. 100% Job Guarantee
5. Totally practical
6. There are 5 students in each batch.
7. Lifetime unlimited access to the cloud lab
8. Online and in-person training
9. Gain Knowledge from Industry Experts
Visit the institute for a discount to learn more about this career opportunity.
For more information, please call: 86919 69889
#hacktechmedia#hacking#hacker#cybersecurity#ethicalhacking#hackers#linux#programming#hack#technology#kalilinux#security#coding#infosec#python#tech#hackingtools#ethicalhacker#pentesting#cybercrime#cyberattack#informationsecurity
2 notes
·
View notes
Text
Protect the Digital World with Best Cyber Security Course in Chennai at BIA! Become a Cybersecurity Expert at the Best Ethical Hacking Institute in Chennai!
#Best Cyber Security Course in Chennai#Best Ethical Hacking Institute in Chennai#Cyber Security Certification Course in Chennai#Cyber Security Certification in Chennai#Best Ethical Hacking Course in Chennai#Cyber Security Weekend Course in Chennai
0 notes
Text
Certified Ethical Hacker V12 (CEH) in Ottawa: Your Path to Cybersecurity Excellence

In the current digital era, cybersecurity has emerged as one of the most important domains for several enterprises. Organizations urgently require qualified cybersecurity specialists to protect their data and systems as cyber attacks continue to develop and get more sophisticated. The Certified Ethical Hacker V12 (CEH) certification is one that is particularly noteworthy for people who want to have an influence in the cybersecurity field. This post will discuss the benefits of obtaining a CEH certification in Ottawa for your profession and how it can give you the tools you need to defend against online attacks.
What is the Certified Ethical Hacker (CEH) V12?
The EC-Council offers the industry-recognized Certified Ethical Hacker (CEH) certification, especially its V12 edition. It is intended to verify the expertise of experts in spotting weaknesses, carrying out penetration testing, and guaranteeing strong cybersecurity procedures inside a company. The most recent edition, CEH V12, offers content that has been updated to match the most recent security procedures and cyberthreats.
Why Choose CEH V12 in Ottawa?
The capital of Canada, Ottawa, is a center for creativity and technology, which makes it the perfect place for people who want to progress in their IT and cybersecurity professions. Numerous government organizations, tech startups, financial institutions, and huge enterprises call the city home, and they all urgently need cybersecurity specialists. Obtaining your CEH certification in Ottawa can lead to a number of career advancement and employment options. Pursuing CEH V12 in Ottawa makes sense for the following reasons:
Access to Excellent Training Programs: There are many accredited training facilities and academic institutions in Ottawa that provide CEH courses. These programs provide materials, professional instruction, and practical laboratories to help you successfully prepare for the certification exam.
Growing Need for Experts in Cybersecurity: The corporate environment in Ottawa is becoming more and more focused on strengthening cybersecurity measures as a result of the increase in cyberattacks and data breaches. Employers who need professionals who can protect sensitive data will find you very appealing if you have a CEH V12 certification.
Numerous Career Options: Obtaining a CEH V12 certification in Ottawa can open doors to positions as a network security analyst, penetration tester, security consultant, ethical hacker, and more. The certification guarantees that you are ready for a variety of cybersecurity challenges by giving you a thorough understanding of network security, vulnerability analysis, and incident response.
Key Benefits of Earning the CEH V12 Certification
Thorough Understanding of Cybersecurity Tools and Threats: CEH V12 addresses a wide range of subjects, such as cloud security, mobile security, network security, and ethical hacking. This in-depth understanding enables you to recognize possible dangers, reduce risks, and improve an organization's overall security posture.
Practical Skills: The certification's emphasis on practical training is well-known. You'll discover how to test the security of networks and systems using a variety of tools and methods used by actual hackers. Gaining the skills required to stop and handle cyber incidents is made possible by this hands-on experience.
Enhanced Professional Credibility: CEH is regarded as a standard for cybersecurity knowledge throughout the world. You can show your dedication to lifelong learning and development in the subject of cybersecurity and greatly increase your professional credibility by including it on your resume.
Greater Earning Potential: Compared to their peers who are not certified, certified ethical hackers frequently earn more money. Gaining the CEH V12 can open doors to higher job opportunities and advancements in Ottawa's booming tech sector.
How to Prepare for the CEH V12 Exam in Ottawa
The CEH V12 exam preparation calls for commitment and a methodical approach. Here's a detailed how-to for preparing:
Select a Trustworthy Training Provider: Seek for Ottawa's accredited EC-Council training facilities that provide CEH courses. These programs frequently consist of lab exercises to reinforce your learning, internet resources, and instructor-led sessions.
Examine the curriculum for CEH V12: Learn about the objectives of the test, which include topics such as vulnerability analysis, system penetration testing, network scanning, and ethical hacking tools.
Practical Experience: The CEH certification is renowned for emphasizing practical experience. To improve your skills, do lab exercises and use virtual laboratories that mimic real-world situations.
Take Practice Exams: To determine your level of comprehension and preparedness, take practice tests. These assessments can help you learn the format of the test and pinpoint areas that require further focus.
Final Thoughts
For anyone hoping to establish a prosperous career in cybersecurity, earning the Certified Ethical Hacker V12 certification is a crucial first step. Pursuing this certification in Ottawa can provide you outstanding job prospects and opportunities because the city is a hub for innovation and technology. You will have the knowledge and abilities necessary to combat contemporary cyberthreats and make a significant contribution to the security of Ottawa and other organizations after obtaining your CEH V12.
Consider taking a CEH V12 course right now if you're prepared to advance your cybersecurity profession and establish yourself as a pioneer in the fields of cybersecurity and ethical hacking.
#Certified Ethical Hacker V12 (CEH) in Ottawa#Certified Ethical Hacker V12 (CEH) in Calgary#Certified Ethical Hacker V12 (CEH) in Montreal#Certified Ethical Hacker V12 (CEH) in Vancouver#Certified Ethical Hacker V12 (CEH) in Toronto
0 notes
Text
Top Courses in the UK for 2024: Emerging Fields and Career Opportunities
As the educational landscape evolves, Indian students aspiring to study abroad are constantly seeking courses that promise not only academic growth but also future career opportunities. The Top Courses in the UK for 2024 reflect the shifting demands of the global job market, focusing on cutting-edge fields like Artificial Intelligence, Data Science, and Renewable Energy. These emerging fields are becoming increasingly popular among students due to their potential for high employability and lucrative salaries. With the assistance of an overseas education consultancy, Indian students can navigate through these options and choose the best course that aligns with their career goals.

1. Artificial Intelligence (AI) and Machine Learning
AI and Machine Learning are two of the most exciting fields gaining momentum in the UK. As industries worldwide adopt automation and smart technologies, the demand for skilled AI professionals is soaring. Universities in the UK, such as Imperial College London and the University of Edinburgh, offer advanced programs in AI and Machine Learning that equip students with essential skills in algorithm development, deep learning, and natural language processing.
Career Opportunities: Graduates from AI and Machine Learning programs can explore diverse roles such as AI researchers, data scientists, robotics engineers, and AI consultants. The rise of AI across sectors like healthcare, finance, and automotive industries ensures a growing demand for experts in this field.
Why the UK? The UK is a global hub for AI research and innovation, with many tech companies and startups setting up their operations in cities like London and Manchester. Studying AI in the UK gives Indian students access to industry collaborations, internships, and a robust professional network, all of which enhance employability.
2. Data Science and Big Data Analytics
With the exponential growth of data, organizations are increasingly reliant on data scientists to make sense of vast amounts of information. The UK has become a leader in Data Science education, with top universities like the University of Oxford and the University of Warwick offering specialized programs in Data Science, Big Data Analytics, and Business Analytics. These courses cover key areas such as data mining, statistical analysis, machine learning, and cloud computing.

Career Opportunities: Graduates in Data Science are highly sought after in sectors like finance, retail, healthcare, and IT. Roles like data analyst, business intelligence consultant, and data architect are in high demand. The increasing use of data-driven decision-making by companies guarantees a steady flow of career opportunities in this field.
Why the UK? The UK’s data science programs emphasize both theoretical knowledge and practical application. Students are given opportunities to work on real-world projects and collaborate with leading tech firms. With the guidance of an overseas education consultancy, Indian students can find the best-fit programs that suit their career aspirations.
3. Cybersecurity
With the growing threat of cyberattacks and data breaches, cybersecurity has become a top priority for organizations worldwide. The UK is at the forefront of cybersecurity education, offering specialized programs that prepare students to tackle complex security challenges. Leading universities like Lancaster University and Royal Holloway, University of London, offer comprehensive cybersecurity courses that cover topics such as ethical hacking, network security, and information assurance.
Career Opportunities: A degree in cybersecurity opens doors to a range of career options, including cybersecurity analyst, information security manager, and network security engineer. Given the rise in cybercrimes and the need for robust security systems, professionals with expertise in cybersecurity are in high demand across industries, particularly in finance, government, and defense.
Why the UK? The UK government and private sectors invest heavily in cybersecurity research and development. Indian students studying in the UK can benefit from access to state-of-the-art facilities, internships with security firms, and cutting-edge research initiatives that enhance their expertise and employability.
4. Renewable Energy and Environmental Science
As the world grapples with climate change, there is a growing need for professionals who can work on sustainable energy solutions. The UK offers leading programs in Renewable Energy and Environmental Science, providing students with the skills required to design, implement, and manage clean energy systems. Top universities such as the University of Exeter and the University of Leeds offer specialized courses focusing on renewable energy technologies, sustainability, and environmental policy.
Career Opportunities: Graduates can explore roles such as renewable energy consultant, environmental engineer, and sustainability manager. As more companies and governments commit to achieving net-zero emissions, the demand for renewable energy professionals continues to rise.
Why the UK? The UK is a global leader in renewable energy research and development, particularly in wind, solar, and tidal energy. Studying renewable energy in the UK provides Indian students with hands-on experience in cutting-edge technologies and a platform for international collaborations.
5. Healthcare and Biotechnology
The global healthcare industry is experiencing rapid advancements, and the UK is a prime location for studying healthcare and biotechnology courses. Universities such as the University of Cambridge and King’s College London offer advanced programs in biotechnology, public health, and clinical sciences. These programs focus on research, innovation, and the application of technology in medical treatments.
Career Opportunities: Graduates can find employment as biotech researchers, healthcare analysts, clinical data managers, and pharmaceutical consultants. With the healthcare sector evolving, professionals with expertise in biotechnology and medical research are in high demand.
Why the UK? The UK is home to some of the world’s leading healthcare institutions and biotech firms. Students gain access to cutting-edge research and can work on projects that are shaping the future of medicine.
Conclusion
The Top Courses in the UK for 2024 are designed to prepare students for the future job market, focusing on innovation, technology, and sustainability. Whether you’re interested in AI, Data Science, Cybersecurity, Renewable Energy, or Healthcare, the UK provides world-class education in these emerging fields. By consulting with an overseas education consultancy, Indian students can explore the best programs and universities that align with their career aspirations, ensuring they make informed decisions on their academic journey.
0 notes
Text
Introduction of Cybersecurity and Ethical Hacking into IGNOU Online MCA
In a day when breaches in digital security and cyberattacks are getting rampant, skilled cybersecurity professionals have never been in greater demand. It is this dire need that has prompted IGNOU Online MCA or Indira Gandhi National Open University to introduce courses in cybersecurity and ethical hacking into its Online MCA or Master of Computer Applications course. These additions are specifically designed to provide students with relevant knowledge and competencies in providing security to digital assets and systems within a dynamically changing threat environment. This blog discusses the new courses' relevance, the topics they will cover, and how these connect to the needs of the modern work market.
The Increasing Need for Cybersecurity ExpertsThe intricacy of cybercriminals' strategies rises with the advancement of technology. Data breaches, ransomware attacks, and phishing schemes targeting people and businesses are a few of the hazards that exist right now. The fact that must be noted is that these incidences of growing attacks remarkably reflect the increasing demand for cybersecurity experts who will be able to save sensitive information and ensure that the digital systems are up and running.
IGNOU Online MCA to Cybersecurity ChallengesCybersecurity has become the main demand in the job market. Because of this, IGNOU has come forward to include courses in cybersecurity and Ethical Hacking in the MCA program. Such a course shall fetch the learner comprehensive knowledge in Security Principles and hands-on experience in combating cyber threats. Following is an outline of these newly incorporated courses added in the curriculum:
1. Fundamentals of CybersecurityFundamentals of Cybersecurity Course: This course takes the student through an overview of the very basics that lie inherently behind cybersecurity. Students will encounter a range of online dangers, such as phishing, spyware, and malware. The objectives of this course are to teach fundamental risk management, network security, and cryptography.
The important points that are to be noted include:
· The types of cyber threats and attack vectors
· The basics of cryptography and encryption
· Network security protocols and best practices
2. Ethical Hacking and Penetration TestingThe methods that an ethical hacker would employ to identify system vulnerabilities before an attacker does are covered in this course on ethical hacking and penetration testing. Students have practical experience using a variety of tools to execute simulated cyberattacks, as well as learning how to conduct penetration tests and vulnerability assessments.
Content Overview:
· Techniques and utilities of pen testing
· Vulnerability assessment and management
· Concepts of ethical hacking and legal issues
3. Cutting-Edge Threat Identification and ReactionAdvanced approaches for identifying and countering cyberattacks, intrusion detection systems, security information and event management systems, incident response plans, and useful skills for threat management and security incident mitigation are all covered in the course. Key topics presented and discussed include:
· Intrusion Detection and Prevention Systems
· Security Information and Event Management
· Incident Response Planning and Execution
· Forensic and Data Recovery Techniques
How These Courses Enhance EmployabilityIGNOU Online MCA courses are, henceforth rewarding in the following ways for students getting employed in the fields of cybersecurity and ethical hacking:
Practical Skills: This kind of practical training within courses guarantees course completion with hands-on experience in using industry-standard tools and techniques that make students work-ready by the time they graduate.
Meeting Industrial Requirements: These courses are specifically designed to meet the current needs of the industry, in terms of what exactly the employers in cybersecurity need in terms of skills and knowledge.
Certification Preparation Offered: A number of these courses may avail the students directly for industry-level certifications but are not limited to, CEH, CompTIA Security+, and CISSP. This, in a way, prepares them better for prospective careers.
ConclusionIncorporating courses into the online MCA of IGNOU regarding cybersecurity and ethical hacking will prove very opportune and tactical curriculum enhancement. Such programs would equip students with the knowledge and skills necessary to pursue a career in cybersecurity, thus responding to the emergent demand for professionals who can safeguard the digital economy. Skill development with a focus on appropriate industry-relevant content,IGNOU Online MCA Course is making sure to position its students for the best possible preparation in lucrative cybersecurity careers by meaningfully contributing to fighting cyber threats.
#IGNOU#MCA#Cybersecurity#Ethical Hacking#Tech Education#Digital Security#IGNOU MCA#Cybersecurity Skills#Ethical Hacking Techniques#Online MCA#Digital Protection
0 notes
Text
Cyber Security Course with Guaranteed Placement
Step into the world of cybersecurity with confidence through our Cyber Security Pro course. cyber security program with job placement Tailored to provide you with cutting-edge knowledge and practical skills, this program ensures you become proficient in protecting digital assets. Cyber Security Excellence with Placement Assurance What makes us stand out is our commitment to your success, backed by a solid placement guarantee.
Explore the realms of ethical hacking, threat detection, and secure network architecture. Our hands-on approach, coupled with real-world simulations, equips you with the expertise demanded by today's cybersecurity landscape. Cyber Security Course with Guaranteed Placement With our placement guarantee, embark on a journey that not only enhances your skills but guarantees a seamless transition into a rewarding career in cybersecurity. Website Visit https://coursry.com/

0 notes
Text
Swarrnim University: Reaching an Academic Peak in Computing Sciences

In Gandhinagar, Gujarat, Swarrnim University is a leading computing science university. Swarrnim is known for its academic prowess in mobile applications and information security, offering an MCA and BCA track. This comprehensive review examines the university's commitment to computing education, making it one of Gujarat's top MCA colleges.
Excellence in Computer Applications
Swarrnim University is the best MCA college in Gandhinagar. The computer science curriculum is carefully developed to give students a solid theoretical and practical foundation. The programme meets industry needs, preparing graduates for the ever-changing IT sector.
Faculty Expertise
Swarrnim's MCA programme is led by experienced professors who provide academic rigour to the classroom. Professors use varied learning approaches to teach hard ideas. This mix of experience promotes intellectual and professional growth.
Innovative Infrastructure
As part of its MCA programme, Swarrnim University is proud of its modern infrastructure. Students acquire experience in software development, data analytics, and system administration in cutting-edge labs with the latest technology.
Research and Development
Swarrnim University prioritises computing research and development. The MCA programme encourages students to innovate, helping the university progress in technology. The concentration on R&D guarantees that graduates grasp current technology and can drive future innovations.
Mobile Application and Information Security
Swarrnim University's BCA Mobile Application and Information Security is unique. Due to the growing importance of mobile technology and information security concerns, this specialised course gives students industry-relevant skills.
Industry-Relevant Curriculum
Swarrnim's BCA in Mobile Application and Information Security addresses industry issues and opportunities. The course covers mobile app development, cryptography, network security, and ethical hacking. This holistic approach ensures graduates have a wide range of skills, making them industry assets.
Present Day Application
Swarrnim University's BCA programme emphasises practical learning. Real-world projects give Mobile Application and Information Security students experience designing secure mobile apps and applying information security procedures. They need this practical experience to integrate into the workforce.
Opportunities for Internships
The university connects BCA students to top companies for internships. These internships augment academic learning and provide a professional perspective. Swarrnim's industry partnerships train students for real-world employment issues.
The Best Gujarat MCA College
Academic rigour, faculty excellence, and industry relevance make Swarrnim University one of Gujarat's top MCA institutes. The MCA programme makes Swarrnim a top computing science university beyond the region.
A Global View
Swarrnim University wants its computing sciences students to think globally. A well-rounded education includes university collaborations, global conferences, and cultural diversity. Thanks to this global approach, Swarrnim graduates are prepared for local and international careers.
Career and Placement Assistance
Students receive career development and placement support from Swarrnim University. A dedicated placement cell at the university works with industry partners to arrange internships and jobs. Resumes, interviews, and career workshops boost students' employability.
Alumni Success
Swarrnim's computing sciences alumni's success stories reflect their education. Graduates thrive in software development and information security consulting. The university's alumni network shows its potential to develop computing industry leaders.
Thus, Swarrnim University has established itself as one of the best MCA colleges in Gujarat and a leader in computing science. The university's MCA and BCA tracks in Mobile Application and Information Security are moulding IT workers, focusing on practical learning, industry relevance, and faculty knowledge. Swarrnim, one of Gujarat's top MCA institutes, prepares students for successful and meaningful careers in the ever-changing computer area.
#mca college in gandhinagar#bca mobile application and information security#best mca colleges in gujarat
0 notes
Text

Leading IT Institute for Software Development, Programming Language Training, Cyber Security In Bhopal
Unlock your potential with Miracle IT, the premier IT institute offering top-notch training in Software Development, Programming Languages (JAVA/PYTHON/PHP/C/C++), Cyber Security, Ethical Hacking, Machine Learning, Data Analysis, Blockchain, Red Hat, and much more. Join us and pave your way to a successful IT career
100% Job Assurance or Money Back Guarantee!*

Placement Training
After successfully completing their IT training, our extensive instruction provides students with the knowledge, abilities, and resources they need to find an employment opportunity that corresponds with their career aspirations

Industry-ready IT Expert
You can take a course from Miracle IT Career Academy that blends coding knowledge with soft skills, personality development, and logical thinking. We take on the burden of transforming you into an IT professional who is prepared for competition.

100% Job Assurance
Our money-back guarantee scheme is an expression of our dedication towards our students. In the fulfillment of this Agreement, we offer our students engaged in our placement guarantee courses a 100% placement opportunity or a complete refund.
Our Courses

Learn the fundamentals of HTML, CSS, and JavaScript in addition to receiving advanced instruction in React.js, Angular, and Vue.js.

This course covers PHP/Laravel, Node.js, Python, and Java and teaches basic ideas and useful abilities in each language, as well as how to create RESTful APIs and microservices.
Visit Out Official Website:
1 note
·
View note
Text
Best Ethical Hacking Certification Course in Delhi
Best Cybersecurity Course in Delhi with Job Guarantee. Learn to protect and defend with the Best Ethical Hacking Certification Course in Delhi, designed for future!
#ethical hacking course#Best Ethical Hacking Institute in Delhi#Best Ethical Hacking Certification Course in Delhi#online ethical hacking course#offline ethical hacking course
0 notes
Text
Enroll in the Most Advanced Ethical Hacking and Cybersecurity course. ACT IMMEDIATELY!!! 1. Completing 30+ modules 2. Obtain international accreditation 3. Batches on weekends and weekdays 4. 100% Job Guarantee 5. Totally practical 6. There are 5 students in each batch. 7. Unlimited cloud lab access for the rest of your life 8. Online and in-person training 9. Gain Knowledge from Industry Experts Visit the institute for a discount to learn more about this career opportunity. Call now for more information: 86919 69889 https://wa.link/wk3mww
#hacktechmedia#hacking#hacker#cybersecurity#ethicalhacking#hackers#linux#programming#hack#technology#kalilinux#security#coding#infosec#python#tech#hackingtools#ethicalhacker#pentesting#cyber#malware#programmer#computerscience#cybercrime#cyberattack#informationsecurity
0 notes
Text
contact us- hacktechmedia
"Hack ethically, secure confidently: Join our ethical hacking course now."
1. Completing 30 or more modules
2. Get international recognition
3. Weekend batch
4. 100% job guarantee
5. Completely practical
6. Each batch has 5 students.
7. Lifetime unlimited entry in cloud lab
8. Online and personal training
9. Get knowledge from industry experts
Visit the organization for discounts to learn more about this career opportunity.
For more information, please call: 86919 69889
0 notes
Text
CAREER IN CYBER SECURITY
CYBER SECURITY
In some simple words, CYBERSECURITY is the best practice of protecting critical systems and sensitive information from digital attacks, it’s also known as INFORMATION TECHNOLOGY.
Many people ask, why Career in cyber security?
SO, LET’S TALK
IF YOU ARE THINKING TO MAKE YOUR CAREER IN CYBER SECURITY THEN YOU ARE ON THE RIGHT PATH.
In the last few years CYBER SECURITY is in demand worldwide and it’s growing rapidly.
Implementing strong defenses against CYBER ATTACKS requires access to a skilled, experienced and professional cybersecurity workforce. So, Nowadays I have seen a growth in the number of people taking courses in CYBER SECURITY and this trend is bound to continue in the future as well. However, the demand for staff with well developed cybersecurity skills is growing much faster than the supply.
As per the NEW YORK TIMES REPORT that a stunning statistic is reverberating in cybersecurity: CYBERSECURITY VENTURES’ prediction that there will be 3.5 million unfilled cybersecurity jobs globally by 2021, up from one million positions in 2014.
“P” OF CYBERSECURITY
Protects systems against viruses, spyware, threats and other unwanted activities
Protects the computer form being hacked
Provides privacy to users
Protection against data from theft
Protect devices from freezing and crashes.
NOW, Every IT position is also a cybersecurity position. Every IT worker, every technology worker, needs to be involved with protecting and defending apps, data, devices, infrastructure, and people.
The Master Cyber Security Course from Eduvogue will transform you into a complete Ethical Hacker and Cyber Security Expert at Affordable fee along Job Guarantee. Accelerate your career in Cyber Security domain today with Practical and Industrial training necessary for the job.
#cybersecurity#career#jobs#trend#information technology#eduvogue#desale7.#https://eduvogue.com/course/G7/cyber-security-course .
23 notes
·
View notes
Text
Heather Cox Richardson:
August 14, 2020 (Friday)
Today’s big story was the administration’s assault on the United States Postal Service. Yesterday, the president said outright that he opposed relief funding for the cash-strapped institution because he wanted to stop mail-in voting, even though he and his wife Melania have both applied for mail-in ballots. Slowing down or stopping the mail will create chaos around the election, and will likely mean ballots will not be counted. It will also funnel voters back to polling places, although the pandemic means there are far fewer of them than usual.

Once at polling places, many voters will cast their ballots on voting machines that are vulnerable to hacking. New machines, rolled out after 2016 and designed to keep cyberhackers at bay, proved “extremely unsafe, especially in close elections,” according to Alex Halderman, a computer scientist from the University of Michigan who, along with six colleagues, studied them. At least 18% of the country’s districts will vote on the new machines, including districts in Pennsylvania, which Trump needs to win but where Biden is up by double digits.
“There are strong security reasons to prefer hand-marked paper ballots,” Halderman told Joseph Marks of the Washington Post.

A bipartisan organization of state secretaries of state—the people in charge of elections—wrote to Trump’s new Postmaster General Louis DeJoy on August 7 to ask for a meeting to discuss his recent changes to the USPS and to explore how those changes would affect the election. In a delay that observers say is “unusual,” he has declined to answer. The USPS recently sent letters to 46 states and Washington, D.C. to say that it cannot guarantee that it will be able to deliver mail-in ballots on time. The letters were prepared before DeJoy took office, suggesting that he knew the USPS should be ramping up its capacity, not decreasing it.
News broke today that DeJoy was named to the finance team of the Republican National Committee in 2017 (along with Elliott Broidy, Michael Cohen, and Gordon Sondland, if anyone can remember back to the days of impeachment), suggesting his partisanship makes him a poor fit for what is supposed to be a nonpartisan office.
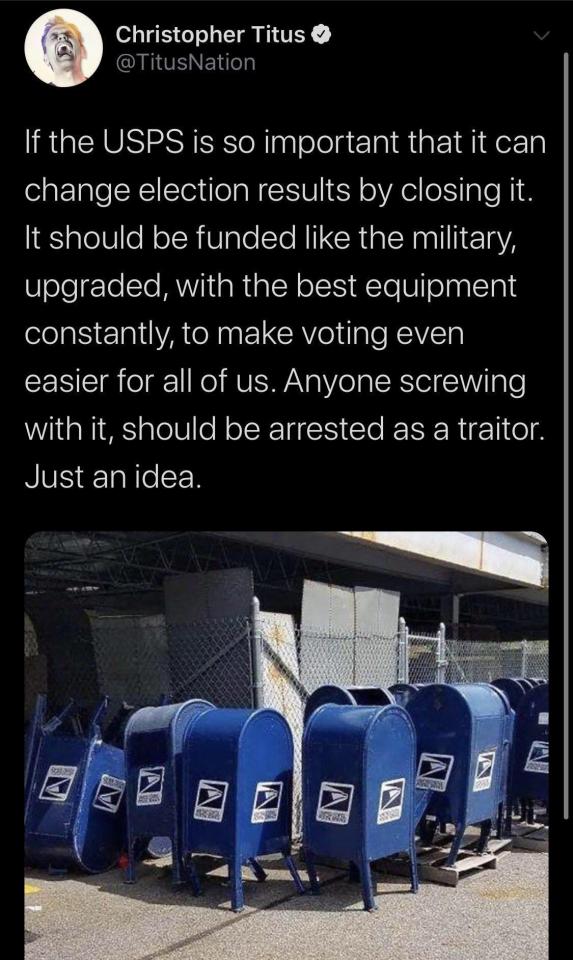
In June, USPS officials told union officials that management was getting rid of 671 sorting machines, about 10% of the machines in the country. The sorters were the kind that handled letters and postcards, not magazines and large envelopes. The argument for getting rid of them is that people write fewer letters these days, but of course we are all expecting a huge influx of mail-in ballots that those machines would handle. Many of the removed sorters were in states that are political battlegrounds: Ohio lost 24 sorters, Detroit lost 11, Florida lost 11, Wisconsin lost 9, Philadelphia lost 8 and Arizona lost 5.
Similarly, the USPS removed letter boxes today in what it said were routine reassignments. The outcry was great enough that it has announced it will not remove any more until after the election. The removal of the boxes may indeed be routine, but David Becker, executive director of the nonprofit, nonpartisan Center for Election Innovation & Research told Washington Post reporter Jacob Bogage, “Given the other things that are going on, it’s okay to ask questions…. The high-speed sorters that are getting deactivated, the loss of overtime, the delays in mail we’re seeing right now, all of this should cause some concern and warrants questions.”
Today, Inspector General for the USPS Tammy L. Whitcomb announced that, at the request of Democrats, she is opening an investigation into “all recent staffing and policy changes put in place” by DeJoy. She will also be looking into DeJoy’s compliance with ethics rules, related to his huge financial stake in private competitors to the USPS.
The other big story is that the Government Accountability Office, the main audit institution in the federal government, concluded today that the two top officials at the Department of Homeland Security are not legally in their positions.
The acting Secretary of the Department of Homeland Security, Chad Wolf, and his top deputy, Ken Cuccinelli, were never confirmed for their positions, although those positions require Senate confirmation. Instead, they were moved into their jobs through the lines of succession in the department, but those lines were altered by the previous DHS secretary, Kevin McAleenen, who himself was placed into position improperly. According to the GAO, McAleenen did not have authority to move Wolf, who had Senate confirmation for a different position, into the directorship. Cuccinelli, who currently holds the title “Senior Official Performing the Duties of Deputy Secretary,” has never been confirmed for anything.
Democrats called for Wolf and Cuccinelli to step down, but DHS spokesman Nathaniel Madden said “We wholeheartedly disagree with the GAO’s baseless report and plan to issue a formal response to this shortly.”

Trump’s handling of DHS is problematic. DHS is a new agency, established after 9-11, and it is staffed with political appointees who report to the president. Trump has increasingly refused to go through normal nominations processes, aware that at least some of his appointees could not make it through even this Republican Senate. Moreover, leaving his appointees in limbo gives Trump more control over them. “I like ‘acting,’” he told reporters last year. “It gives you great, great flexibility.”
Trump has made little effort to fill positions at DHS with qualified people. Within DHS are the agencies that oversee immigration: U.S. Customs and Border Protection (CBP), U.S. Immigration and Customs Enforcement (ICE) and U.S. Citizenship and Immigration Services (USCIS). None of them has a leader that has been confirmed by the Senate. Trump’s sway over DHS means the agency is currently operating, as DHS’s first secretary Tom Ridge said, like “the president’s personal militia.” It was Wolf, of course, who oversaw the recent deployment of federal officers to Portland, Oregon.
In legal news, in a case stemming from U.S. Attorney John Durham’s investigation of the FBI investigation of ties between the Trump campaign and Russia in 2016, a former FBI lawyer intends to plead guilty to falsifying a document. Kevin Clinesmith was the root of the most serious mishandling of the wiretapping of former Trump advisor Carter Page. When it was time for the FBI to apply for a renewal of the request to surveil Page, Clinesmith was asked to find out if Page had ever been an informant for the CIA. When asked, a CIA colleague appears to have identified Page’s role with the agency as something other than a “source,” but wrote an email about it that simply sent Clinesmith to documents to check. Clinesmith altered his CIA colleague's email with the words “not a ‘source.’” The FBI relied on his representation to write the application renewal to wiretap Page.
Clinesmith resigned over the issue last year. He maintains that he changed the wording to reflect what he understood to be true, and other evidence suggested he never tried to hide the original email from his colleagues. Still, he altered a document, and Page’s relationship with the CIA was not accurately represented to the judges who approved the wiretapping. The Justice Department’s inspector general, Michael Horowitz, called out this issue in his report on the FBI handling of the Russia investigation, although he concluded that the FBI opened the investigation properly and without political bias.

In another case stemming from 2016 that got a lot of traction when it was announced, a federal appeals court today ruled that former Secretary of State Hillary Clinton does not have to give another deposition about her emails. Judicial Watch, a rightwing organization founded in 1994 that has frequently targeted the Clintons with lawsuits which are usually thrown out of court, wanted to depose Clinton on the subject. She argued they were harassing her. The court noted that the email issue had already been thoroughly investigated by Congress, the FBI, the State Department Inspector General, and another lawsuit and concluded she did not have to testify again. Last year, the State Department concluded that “there was no persuasive evidence of systemic, deliberate mishandling of classified information.”
Finally, in all the political craziness, the devastating storm that hit the middle of the country on Monday has gotten less attention than it should have. The storm was a “derecho,” and brought wind over 100 miles an hour. Iowa appears to have lost 43% of its corn and soybean crops; 15 tornadoes in Illinois left 800,000 people without power. In Iowa, four days later, 250,000 are still without power, and roads remained blocked.
11 notes
·
View notes