#CyberSecuritySolutions
Explore tagged Tumblr posts
Text
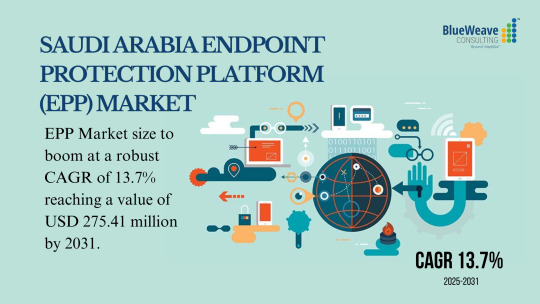
Saudi Arabia Endpoint Protection Platform (EPP) Market size by value at USD 112.11 million in 2024. During the forecast period between 2025 and 2031, BlueWeave expects Saudi Arabia Endpoint Protection Platform (EPP) Market size to boom at a robust CAGR of 13.7% reaching a value of USD 275.41 million by 2031. The Endpoint Protection Platform (EPP) Market in Saudi Arabia is propelled by the escalating frequency and complexity of cyber threats. Organizations are prioritizing the protection of diverse endpoints, including computers, laptops, and smartphones, through the implementation of advanced EPP solutions. Key features such as device control, data loss prevention, and patch management are critical components of these deployments. The adoption of cloud-based EPP solutions is further accelerating market expansion, offering scalability, flexibility, and cost-efficiency compared to traditional on-premises models. The documented surge in cyberattack incidents, exemplified by the Cybersecurity and Infrastructure Security Agency's (CISA) report of over 800 million attacks in 2021, reinforces the necessity for robust endpoint security measures and underscores the pivotal role of EPP in mitigating organizational risk.
Sample Request: https://www.blueweaveconsulting.com/report/saudi-arabia-endpoint-protection-platform-market/report-sample
#BlueWeave#Consulting#Marketforecast#Marketresearch#Cybersecurity#EndpointProtection#EndpointSecurity#ThreatIntelligence#MarketResearchReport#GrowthOpportunities#CybersecuritySolutions#EPPMarket
0 notes
Text
In today’s fast-paced digital world, having a reliable IT infrastructure is more important than ever. For businesses in Portland, Assured Technology Solutions is here to provide top-tier managed IT services that ensure your technology works seamlessly, so you can focus on what matters most — growing your business.
#manageditservices#portlanditsupport#cybersecuritysolutions#cloudcomputing#networkmanagement#proactiveitsupport#businesstechnology#techsolutions#itconsulting#smallbusinessit#techsecurity#portlandbusiness#itinfrastructure#techoptimization#itsupportexperts
0 notes
Text
Jacksonville Computer Network Issue: 3 Ways to Solve Now

The foundation of any organization in the connected world of today is its computer network. When something goes wrong, it can affect public trust, productivity, and operations. The Jacksonville computer network issue recently attracted a lot of attention since it revealed weaknesses in the community’s IT infrastructure. Read More
0 notes
Text
Athreon delivers AI-powered and human-assisted transcription services, speech-to-text solutions, and cybersecurity solutions for healthcare, legal, corporate, and law enforcement sectors. Ensure accuracy, efficiency, and data security with our HIPAA-compliant, scalable transcription and speech recognition services designed for your needs.
#TranscriptionServices#SpeechToText#AITranscription#CybersecuritySolutions#LegalTranscription#MedicalTranscription#SecureTranscription#HIPAACompliant#VoiceRecognition#DataSecurity#BusinessSolutions#LegalTech#HealthTech#AIInnovation#LawEnforcementTech
0 notes
Text
Healthcare’s Cybersecurity Crisis: Protecting Patient Data from Evolving Threats

The healthcare industry has become a prime target for cyberattacks due to the vast amounts of sensitive patient data it holds. From personal medical histories to payment information, this data is a valuable resource for cybercriminals. As healthcare systems adopt more connected technologies, the risks of data breaches and cyberattacks continue to rise, posing significant threats to patient privacy and the integrity of healthcare services. At Tech4BizSolutions, we specialize in providing advanced cybersecurity solutions tailored to the healthcare sector, ensuring the safety and privacy of patient data in an increasingly connected world.
The Growing Cybersecurity Challenges in Healthcare
The healthcare industry is experiencing a digital transformation, with Electronic Health Records (EHR), telemedicine, and connected medical devices becoming the norm. While these technologies improve patient care and operational efficiency, they also introduce numerous cybersecurity vulnerabilities:
Data Breaches: Patient data is a lucrative target for cybercriminals. Healthcare organizations are increasingly falling victim to data breaches, exposing sensitive personal information.
Ransomware Attacks: Cyberattacks like ransomware are a growing concern, where attackers lock healthcare systems and demand payment for data recovery.
Insider Threats: With an increase in the number of connected devices and employees accessing sensitive data, insider threats—whether intentional or accidental — are a significant challenge.
Regulatory Compliance: Healthcare providers must comply with stringent data protection regulations, such as HIPAA in the U.S., making cybersecurity a critical concern.
As cyber threats continue to evolve, the healthcare industry must adopt advanced security measures to stay ahead of these risks.
How AI is Revolutionizing Healthcare Cybersecurity
Artificial intelligence (AI) is transforming healthcare cybersecurity. AI can analyze vast amounts of data in real-time to detect threats and anomalies, allowing healthcare organizations to respond proactively rather than reactively. Here’s how AI-powered cybersecurity solutions are transforming patient data protection:
1️⃣ Real-Time Threat Detection and Prevention
AI-powered systems can continuously monitor healthcare networks and detect anomalies in real-time. These systems can analyze network traffic, user behaviors, and system activities to identify potential security risks before they escalate into full-blown cyberattacks.
Machine learning algorithms learn from historical data and continuously adapt to emerging threats, improving detection accuracy.
AI-driven analytics help pinpoint suspicious activities that might be missed by traditional security tools, allowing for quicker responses to potential breaches.
2️⃣ Enhanced Fraud Detection
Fraud in healthcare can take many forms, from false insurance claims to identity theft. AI tools can analyze patterns in claims and medical records, flagging any irregularities that may indicate fraudulent activity.
Pattern recognition allows AI systems to identify inconsistencies in medical claims, reducing the likelihood of fraud.
Predictive analytics powered by AI can identify high-risk accounts and activities, allowing healthcare providers to take preventive measures.
3️⃣ Automated Incident Response
AI can help healthcare organizations reduce the response time to cybersecurity incidents. Automated systems can take immediate action when a threat is detected, such as isolating compromised devices or shutting down vulnerable systems, preventing the spread of attacks.
Automated workflows reduce human intervention, allowing for faster containment of cyberattacks.
AI-driven decision-making ensures that the right actions are taken based on the severity of the incident, minimizing downtime and data loss.
4️⃣ Advanced Data Encryption and Privacy Protection
As healthcare organizations store increasing amounts of sensitive data, it’s crucial to ensure this information is protected. AI-powered solutions can enhance encryption methods to safeguard data during storage and transmission, reducing the risk of unauthorized access.
AI-powered encryption algorithms offer advanced protection by continually evolving in response to new encryption standards and threats.
Privacy-preserving AI techniques ensure that patient data remains confidential, even in the event of a breach.
Tech4Biz Solutions: Leading the Way in Healthcare Cybersecurity
At Tech4BizSolutions, we understand the critical need for robust cybersecurity in healthcare. We provide comprehensive AI-driven cybersecurity solutions to help healthcare organizations safeguard patient data, maintain regulatory compliance, and protect against evolving cyber threats.
Our services include:
Real-time threat monitoring and detection powered by AI to identify and neutralize threats quickly.
Fraud detection and prevention using advanced AI algorithms to reduce the risk of fraud and protect sensitive information.
Automated incident response systems to swiftly mitigate the impact of cyberattacks and minimize data loss.
Data encryption and privacy protection using AI-powered techniques to ensure the security of patient data.
The Future of Healthcare Cybersecurity
The future of healthcare cybersecurity lies in intelligent, AI-powered systems that can predict, detect, and respond to cyber threats in real-time. As healthcare providers continue to rely on digital tools and connected devices, ensuring the privacy and security of patient data will remain a top priority.
At Tech4BizSolutions, we are committed to empowering healthcare organizations with the tools they need to protect sensitive patient data and navigate the evolving landscape of cybersecurity threats.
Contact Us
Ready to strengthen your healthcare organization’s cybersecurity? Tech4BizSolutions offers AI-driven solutions that can protect patient data and ensure the integrity of your systems. Contact us today to learn how we can help you safeguard your healthcare operations against the growing threat of cyberattacks.
#HealthcareCybersecurity#AIinHealthcare#DataProtection#Tech4BizSolutions#PatientPrivacy#CybersecuritySolutions#AIforHealthcare#HealthDataSecurity
0 notes
Text
#ifitechsolutions#CyberSecuritySolutions#DataProtection#DigitalSecurity#TechPartnership#SecureFuture
0 notes
Text
Harnessing the Future of Technology with Malachite Technologies

In today’s competitive world, businesses must adapt to technological advancements to stay ahead. Malachite Technologies delivers future-ready solutions in website development, cybersecurity, mobile app design, and digital marketing, enabling brands to achieve unparalleled success.
#InnovativeSolutions#WebsiteDesignExperts#AppDevelopmentServices#CyberSecuritySolutions#DigitalMarketingExperts#MalachiteTechnologies#OnlineBusinessGrowth
0 notes
Text
Top Features to Look for When Buying Copiers in Pismo Beach

Purchasing the right copier for your business in Pismo Beach is a crucial decision that can impact your office’s productivity and efficiency. Whether you're a small business owner or part of a larger corporation, finding the perfect copier can help streamline your operations. But with so many options on the market, how do you know which features to prioritize? This guide will help you identify the top features to look for when buying copiers in Pismo Beach, ensuring you make a smart, cost-effective choice.
1. Print Speed and Volume
The speed and print volume of your copier are two of the most important factors to consider when purchasing copiers in Pismo Beach. Depending on the nature of your business, you'll need a copier that can handle your workload efficiently.
Print Speed: If your business prints large volumes of documents on a regular basis, choose a copier with a fast print speed, measured in pages per minute (PPM). Copiers with higher PPM are ideal for high-demand environments like law firms or marketing agencies.
Print Volume: Be sure to select a copier that can handle your monthly print volume. If you print hundreds of documents daily, investing in a high-volume copier is essential. This will help you avoid frequent breakdowns and ensure the copier can keep up with your needs.
For those also considering reliable copiers in Woodland Hills, look for models that offer high speeds and volume capabilities to meet the demands of fast-paced businesses.
2. Multifunction Capabilities
One of the most valuable features of modern copiers is their multifunction capabilities. In today’s busy business environment, you’ll likely need a copier that not only prints but also scans, faxes, and emails documents.
Scanning and Emailing: Look for copiers in Pismo Beach that allow for easy scanning and emailing of documents directly from the machine. This can save time and improve efficiency by eliminating the need for separate scanners and fax machines.
Faxing: Even in the digital age, some businesses still rely on faxing, so it’s essential to choose a copier that includes faxing functionality.
Copying: Of course, the copier’s primary function is to produce copies of documents, so choose one that delivers high-quality copies without distortion or blurring.
The more multifunctional a copier is, the more you’ll be able to streamline your workflow. For those seeking managed print services, multifunction copiers are often bundled into such services, offering additional support and benefits.
3. Energy Efficiency and Environmental Impact
Sustainability is becoming more important for businesses of all sizes, and this extends to the copiers you choose. When shopping for copiers in Pismo Beach, look for models with energy-saving features that can reduce your carbon footprint and lower utility costs.
Energy Star Certification: Copiers with an Energy Star certification meet energy efficiency standards set by the U.S. Environmental Protection Agency. These models use less energy without sacrificing performance.
Duplex Printing: Copiers that support duplex (two-sided) printing help reduce paper consumption, which is not only cost-effective but also environmentally friendly.
Low Energy Consumption: Many modern copiers feature power-saving modes, which reduce the machine's energy usage during periods of inactivity.
In addition to reliable copiers in Woodland Hills, consider the environmental impact of your copier to make an eco-friendly choice that benefits your business and the planet.
4. Security Features
Security is a growing concern for businesses, especially with sensitive information being handled daily. Copiers in Pismo Beach should come equipped with features that protect your documents and data from unauthorized access.
User Authentication: Choose copiers that offer user authentication via passwords or PIN codes. This prevents unauthorized users from accessing or printing confidential documents.
Secure Printing: Some copiers offer secure print features, which allow documents to be released only when the authorized user is present at the machine.
Encryption: Look for copiers with data encryption capabilities to protect sensitive information stored on the device.
With managed print services, security features are often bundled into your copier plan, ensuring that your copier is not only functional but secure as well.
5. Ease of Use and Interface
A copier that is easy to operate can improve office productivity. The last thing you want is a complex machine that your employees struggle to use. When evaluating copiers in Pismo Beach, look for the following:
User-Friendly Display: Modern copiers have touchscreens that make navigation intuitive. Choose a copier with a large, easy-to-read display and simple touch controls.
Mobile Connectivity: If your employees frequently use mobile devices, consider a copier that supports mobile printing. Many models now offer wireless printing from smartphones, tablets, and laptops, allowing for greater flexibility.
Remote Management: Some copiers come with remote management features, enabling IT staff to monitor and troubleshoot the machine from any location. This can save time and reduce the need for on-site service calls.
6. Cost of Ownership
The overall cost of owning a copier includes not just the upfront cost, but also ongoing expenses such as maintenance, supplies (toner and paper), and repair costs. When looking for copiers in Pismo Beach, be sure to consider the total cost of ownership.
Leasing vs. Buying: For many businesses, leasing a copier instead of buying can offer more flexibility. Leasing often includes maintenance, reducing unexpected repair costs.
Maintenance Plans: Many dealers offer maintenance plans, which can be a great way to keep your copier running smoothly while avoiding surprise repair bills.
Toner and Ink Costs: Make sure to inquire about the cost of consumables like toner and ink before making your final decision. Some copiers are more economical in terms of toner usage than others.
If you're looking at reliable copiers in Woodland Hills or considering managed print services, be sure to factor in the costs of both the machine and the ongoing expenses to get a comprehensive understanding of your investment.
Conclusion
Choosing the right copier for your business in Pismo Beach doesn’t have to be overwhelming. By considering key features such as print speed, multifunction capabilities, energy efficiency, security, ease of use, and total cost of ownership, you can select a machine that meets your needs and fits your budget. Whether you're looking for a high-volume copier or a budget-friendly model, there are many options available that can improve your office’s efficiency.
If you’re also considering reliable copiers in Woodland Hills or looking into managed print services, remember that these features are critical in ensuring you choose a copier that will serve your business well for years to come.
FAQs
1. What is the most important feature to look for when buying a copier?The most important feature to consider is your business's print volume. Choose a copier with the right print speed and volume capabilities to meet your needs.
2. How can I reduce the cost of owning a copier?Look for models with energy-saving features, consider leasing instead of buying, and invest in a copier with low maintenance and consumable costs.
3. What are managed print services?Managed print services are solutions offered by providers that handle your printing needs, including maintenance, supplies, and support, often bundled with copiers.
4. Why should I choose a copier with security features? Security features help protect sensitive information and prevent unauthorized access to confidential documents, ensuring your business’s data remains safe.
5. How can I ensure my copier is easy to use? Look for copiers with user-friendly touchscreens, mobile connectivity, and remote management features to make operation seamless for your employees.
#copier#printers and scanners#3d printer#it#it services#cybersecurityservices#cybersecurity#goodsuite#itsupport#manageditservices#cybersecuritysolutions#printer
0 notes
Text
Bot Management in Japan and China: A Market Overview and Forecast
The escalating sophistication of cyber threats has made bot management a critical aspect of cybersecurity in Japan and China. These markets are witnessing rapid technological advancements and a growing reliance on digital platforms, making them highly susceptible to bot attacks. From credential stuffing and web scraping to Distributed Denial of Service (DDoS) attacks, bots have become a significant concern for businesses across various industries. Organizations are increasingly adopting bot management solutions to safeguard their digital assets and ensure seamless user experiences.
The Growing Need for Bot Management
In Japan, the rise of e-commerce, financial services, and online gaming platforms has increased the need for robust bot management solutions. Similarly, China’s digital ecosystem, driven by its massive e-commerce market and fintech innovations, is a hotspot for bot activity. The prevalence of malicious bots has led to significant financial and reputational damages in both countries, prompting organizations to prioritize investments in advanced bot management tools.
Bot management solutions are designed to detect, analyze, and mitigate bot traffic. These tools leverage technologies such as artificial intelligence (AI), machine learning (ML), and behavioral analysis to distinguish between legitimate and malicious traffic. As businesses in Japan and China accelerate their digital transformation initiatives, the demand for sophisticated bot management solutions is expected to surge.
Market Drivers and Trends
Key drivers for the bot management market in Japan and China include the increasing volume of cyberattacks, stringent regulatory frameworks, and the need for superior customer experiences. Companies like QKS Group are at the forefront of providing innovative bot management solutions tailored to these markets. Their offerings emphasize cutting-edge analytics, real-time monitoring, and user-friendly interfaces to address the unique cybersecurity challenges faced by businesses in these regions.
In Japan, government initiatives like the Cybersecurity Basic Act and awareness programs aimed at SMEs are expected to fuel market growth. Similarly, China’s strict data protection regulations and its growing emphasis on securing digital infrastructure are creating a favorable environment for bot management solutions.
Market Forecast: Bot Management, 2024-2028, Japan
The bot management market in Japan is projected to grow at a compound annual growth rate (CAGR) of 14.2% between 2024 and 2028. This growth is driven by increasing adoption in sectors such as e-commerce, banking, and healthcare. Companies like QKS Group are strategically expanding their operations in Japan, capitalizing on the country’s demand for advanced cybersecurity solutions. By 2028, the Japanese market is expected to reach a valuation of $600 million, highlighting its robust growth trajectory.
Japan's bot management market is poised for growth, driven by advancements in AI and machine learning, enabling precise bot attack mitigation. Growing emphasis on comprehensive cybersecurity strategies and collaboration between public and private sectors positions Japan as a leader in securing its digital economy.
Market Forecast: Bot Management, 2024-2028, China
China’s bot management market is expected to exhibit even stronger growth, with a forecasted CAGR of 17.5% during the same period. The market is anticipated to surpass $1.2 billion by 2028, driven by the increasing digitization of industries and a proactive regulatory stance. QKS Group is poised to capture significant market share in China by leveraging its expertise and localized strategies, addressing the unique needs of Chinese businesses.
China's bot management market is set for strong growth, driven by AI-powered solutions and a dynamic digital landscape. Rising cybersecurity priorities, public-private collaboration, and investment will solidify China's role in the global market.
Conclusion
The bot management markets forecast in Japan and China are on a growth trajectory, fueled by rising cyber threats and increasing investments in digital technologies. Companies like QKS Group are playing a pivotal role in shaping these markets by providing innovative and scalable solutions. With favorable market dynamics and growing awareness, the bot management landscape in Japan and China is poised for transformative growth between 2024 and 2028.
0 notes
Text
🌐 GL.iNet GL-MT3000 (Beryl AX) Wi-Fi 6 Router on Sale - 42% OFF! 🌐

Enhance your internet experience with the GL.iNet GL-MT3000 (Beryl AX) Wi-Fi 6 Wireless Travel Router! Perfect for staying connected in public spaces or hotels, this gigabit router ensures fast, secure connections. With Wi-Fi 6 support, you'll enjoy faster speeds, better performance, and improved security with captive portal access. Whether you're working remotely or traveling, the GL-MT3000 is your ultimate companion for seamless internet connectivity on the go.
Special Offer: Price Now: $68.69 (Original Price: $119.00) - Save 42% OFF!
🔗 Click to Buy Now: GL.iNet GL-MT3000 Wi-Fi 6 Router
#WiFi6Router#TravelRouter#GLiNet#WirelessRouter#CyberSecurity#PublicWiFi#HotelWiFi#TechDeals#RouterSale#PortableRouter#TravelTech#InternetOnTheGo#CyberSecuritySolutions#TechLovers#WiFiRouterDeals#DiscountTech#AliExpressSale#TechEssentials#SmartTravel#StayConnected#RemoteWorkTools#PortableTech
0 notes
Text

DDoS (Distributed Denial of Service) Protection and Mitigation Security Market size at USD 5.2 billion in 2024. During the forecast period between 2025 and 2031, BlueWeave expects Global DDoS Protection and Mitigation Security Market size to expand at a CAGR of 13.50% reaching a value of USD 13.3 billion by 2031. Major growth drivers for Global DDoS Protection and Mitigation Security Market include the rising prevalence of DDoS attacks as a result of increased adoption of advanced technologies such as cloud and the Internet of Things (IoT), growing awareness about potential cyber risks, and stringent data protection regulations. Furthermore, the introduction of 5G is predicted to result in an increase in multi-vector attacks across businesses and sectors, causing a rise in cybersecurity measures and increasing demand for DDoS protection and mitigation security.
Sample Request: https://www.blueweaveconsulting.com/report/ddos-protection-and-mitigation-security-market/report-sample
Opportunity - Stringent Regulations and Compliance Pressures
Stringent data protection and privacy regulations across regions (such as GDPR in Europe) are surging the demand for DDoS protection solutions to maintain cybersecurity standards. With the changing regulatory landscape to address the growing cybersecurity threat, organizations are compelled to adopt DDoS protection measures to avoid penalties and legal ramifications. Organizations are increasingly turning to DDoS mitigation solutions as part of their overall cybersecurity compliance strategy. These solutions help ensure the integrity and availability of services, meeting regulatory demands while protecting against potential disruptions caused by DDoS attacks.
#BlueWeave#Consulting#Marketforecast#CyberThreats#Marketresearch#CybersecurityMarket#CyberResilience#CybersecuritySolutions#CybersecurityTrends
0 notes
Text
#CosmicStingHack#WebsiteSecurity#CyberThreats#PhishingProtection#MalwareProtection#PinBloomsTechnology#CyberSecuritySolutions
0 notes
Text
The Role of Firewalls in Network Protection
https://www.pgsuae.com/blogs/the-role-of-firewalls-in-network-protection/
#firewall#networkprotection#cybersecurity#webhosting#planetgreensolutions#dubai#uae#cybersecuritysolutions
0 notes
Text
Athreon offers cutting-edge transcription, dictation, speech recognition, and cybersecurity solutions for businesses and professionals. Enhance productivity with AI-powered transcription, secure documentation, and workflow automation. Serving healthcare, legal, law enforcement, and corporate industries with accurate, confidential, and efficient services. Visit Athreon.com to streamline your operations today!
#TranscriptionServices#SpeechRecognition#DictationSoftware#CybersecuritySolutions#AITranscription#LegalTranscription#HealthcareTranscription#SecureDocumentation
0 notes
Text
#LifeLockDeals#NortonLifeLock#IdentityTheftProtection#CybersecuritySolutions#LifeLockReview#NortonLifeLockDeals#DataProtection#CyberSecurity#LifeLockOffers#IdentityProtection#LifeLockAnalysis#OnlineSecurity#NortonLifeLockReview#IdentityTheftPrevention#CyberSafety#LifeLockFeatures#NortonSecurity#LifeLockProtection#DataSecurity#LifeLockBenefits#OnlineProtection#LifeLockPromo#DigitalSecurity#CyberThreatProtection#NortonLifeLockOffers#PersonalDataSecurity#LifeLockSecurity#IdentityTheftSolutions#CyberProtection#LifeLockDiscounts
0 notes