#CyberSecurity hashtag
Explore tagged Tumblr posts
Text
#hashtag#ZTrust hashtag#CyberSecurity hashtag#SSO hashtag#IAM hashtag#IdentityManagement hashtag#SecureAccess hashtag#DataProtection hashtag#BusinessSecurity hashtag#TechInnovation hashtag#Prodevans hashtag#DigitalSecurity hashtag#FutureOfSecurity hashtag#AccessControl
0 notes
Text
youtube
#CyberSecurity hashtag#TheTechTeaPodcast hashtag#FutureOfCybersecurity hashtag#CyberThreats hashtag#BusinessSecurity hashtag#TechInsights hashtag#CISO hashtag#CyberProtection hashtag#DigitalSecurity hashtag#BusinessResilience hashtag#IndiaIT360#Youtube
0 notes
Text

#privatenetwork hashtag#vpn hashtag#cybersecurity hashtag#dataprivacy hashtag#onlineprivacy#hashtag#encryption hashtag#secureconnection hashtag#networksecurity hashtag#protectyourdata#browsesafe hashtag#securewifi hashtag#bypasscensorship hashtag#globalaccess hashtag#workfromanywhere
0 notes
Text
Are You Ready to Elevate Your Business Online?
Are You Ready to Elevate Your Business Online? In the digital realm, a robust online presence is crucial. At Filly Coder, we don’t just build websites; we create comprehensive digital solutions tailored to your specific business needs. Whether you’re involved in electronics, real estate, apparel, beauty, or any other industry, we have the expertise to propel your business forward. Why Choose Filly Coder? Custom Software Development: We develop bespoke web, mobile, and desktop applications that are both powerful and user-friendly. Digital Marketing Mastery: Elevate your online visibility with our expert SEO, SEM, and social media marketing strategies. Advanced Cyber Security: Secure your business operations with our cutting-edge cyber security solutions. Machine Learning Innovation: Stay ahead of the competition with applications enhanced by artificial intelligence and machine learning. Deliver Excellence to Your Customers Your commitment to quality and exclusive service should shine through every aspect of your business, especially your online presence. Let us build you a website that’s not only visually stunning but also efficient, secure, and capable of managing all your online interactions. Engage More, Achieve More With Filly Coder, you gain a technology partner who understands the importance of engagement, customer satisfaction, and retention. Get started today and unlock new opportunities to attract and retain customers online. Transform your business with Filly Coder, where we make you smarter, more efficient, and better connected.
#hashtag#FillyCoder hashtag#DigitalTransformation hashtag#CyberSecurity hashtag#MachineLearning hashtag#SEO hashtag#SocialMediaMarketing hashtag#CustomSoftware hashtag#TechInnovation hashtag#GlobalTech
0 notes
Text
#Dr.K.V.N. Rajesh CloudThat hashtag#AzureCloudSecurity hashtag#CloudComputing#hashtag#CyberSecurity hashtag#MicrosoftCertifiedTrainer hashtag#SubjectMatterExpert#CloudConsulting hashtag#globalbizoutlook
0 notes
Text
Fortifying Trust and Security: How Diginyze Protects Your Industrial Online Transactions
Security in industrial eCommerce? Diginyze has got it covered! Protect your online transactions with top-tier security measures. Find out how in our latest blog! https://www.diginyze.com/blog/fortifying-trust-and-security-how-diginyze-protects-your-industrial-online-transactions/

#hashtag#Diginyze hashtag#IndustrialSecurity hashtag#EcommerceSafety hashtag#B2BCommerce hashtag#DataPrivacy hashtag#IndustrialDistribution hashtag#eCommerceSecurity hashtag#OnlineTransactions hashtag#CyberSecurity hashtag#DataProtection hashtag#AIeCommerce hashtag#SecurePayments hashtag#FraudPrevention hashtag#DigitalTransformation hashtag#SSLencryption hashtag#PCICompliance hashtag#SupplyChainSecurity hashtag#BusinessContinuity hashtag#FraudDetection hashtag#CyberDefense hashtag#SecureECommerce
0 notes
Text
24 consejos para no ser estafado/a en Internet Aquí tienes algunos consejos para evitar ser víctima de estafas, especialmente en internet: 1) No respondas a correos electrónicos que soliciten datos personales y no hagas clic en enlaces sospechosos. 2) Protege tu información con contraseñas seguras y cámbialas regularmente. 3) Desconfía de mensajes de texto, WhatsApp o redes sociales que parezcan fraudulentos. 4) Verifica la autenticidad de los organismos públicos o bancos que te contacten. 5) Comprueba las transferencias y operaciones bancarias que realices. 6) Presta atención a la redacción de los mensajes y busca errores que delaten fraudes. 7) Corrobora la veracidad de ofertas promocionales o descuentos. 8) Investiga la reputación de tiendas o sitios antes de comprar en línea. 9) Utiliza el doble factor de autenticación siempre que sea posible. 10) Cambia contraseñas solo a través de sitios oficiales. 11) Verifica el logo de autenticación en contactos de WhatsApp de organismos públicos. 12) No compartas códigos de verificación recibidos por email o mensaje. 13) Mantén actualizado el sistema operativo, navegador y aplicaciones. 14) Usa antivirus y antimalware. 15) Desactiva ubicación, cámara y micrófono cuando no sean necesarios. 16) Nunca envíes dinero a desconocidos. 17) Observa errores ortográficos y gramaticales en comunicaciones. 18) Ten cuidado al compartir información personal o multimedia. 19) Baja la velocidad y no actúes bajo presión; los estafadores suelen urgir a sus víctimas. 20) Revisa la autenticidad de sitios web y correos electrónicos. 21) Evita páginas falsas que imitan a sitios legítimos. 22) Infórmate sobre las últimas estafas digitales y cómo operan. 23) No confíes en páginas que causen desconfianza o parezcan demasiado buenas para ser ciertas. 24) Denuncia cualquier actividad sospechosa a las autoridades competentes. Espero que estos consejos te sean útiles para protegerte de posibles estafas. Siempre es mejor prevenir y estar informado. 😁 💳 👮♀

#ciberseguridad hashtag#cybersecurity hashtag#cyberattack hashtag#cibercrimen hashtag#tecnología#hashtag#technology hashtag#tech hashtag#it hashtag#seguridad hashtag#security hashtag#seguridadinformática hashtag#hacker hashtag#ethicalhacking hashtag#hack hashtag#virus hashtag#antivirus hashtag#firewall hashtag#informática hashtag#internet hashtag#phising hashtag#spyware hashtag#worm hashtag#ransomware hashtag#programación hashtag#proteccióndedatos hashtag#poderjudicial hashtag#derecho hashtag#hablandoconcarol#carolcespedes
1 note
·
View note
Text
Cyber Resilience: Embracing Tomorrow’s Security
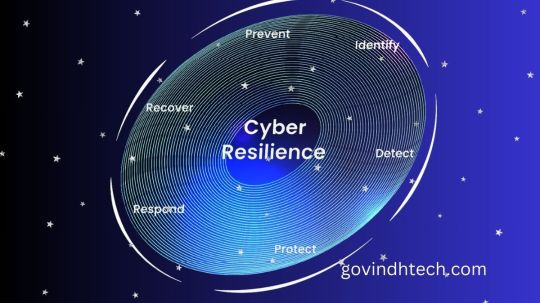
What is cyber resilience?
Business continuity, information systems security, and organizational resilience are all included under the idea of cyber resilience.
Cyber resilience framework
The harsh reality for leaders in cybersecurity is that they must protect a growing number of attack surfaces while dealing with persistently aggressive, constantly changing hostile actors. The data indicates that conventional security techniques and instruments are insufficient to ensure the safety of organizations. Organizations face 44 major cyber events annually on average, according to the EY 2023 Global Cybersecurity Leadership Insights Study, and ransomware expenses are expected to hit $265 billion by 2031. Only one in five chief information security officers (CISOs) said their firms’ current methods were successful against contemporary threats, indicating that the majority of CISOs already know what their organizations are doing is inadequate.
Cyber resilience plan
According to the EY 2023 Global Cybersecurity Leadership Insights Study, C-suite executives are battling a variety of known and unknown threats. However, it also provides comfort in knowing that diverse results are experienced by enterprises, some of which may be attributed to their cybersecurity approach. Businesses may improve their cybersecurity by taking a cue from the best and focusing on integration of cybersecurity concerns across the whole business, simplicity, and holistic thinking. Prone Enterprises has the ability to get all of these. Important takeaways from the survey are as follows:
Simplify the cyber technology stack to make it more visible and lower risk. By clearing up the technological environment via automation and orchestration, you can identify signals more quickly and take action more skillfully.
Reduce supply chain access points for hackers, increase cyber alertness, and continually evaluate performance by using automation and standardization without introducing needless bureaucracy. This guarantees early vendor selection involvement for security teams as well.
Convert your tale into a narrative that speaks to the company in terms of value generation, business impact, and risk buydown.
To make the workforce cyber-secure by design, combine automation and preventive technologies with well-planned, gradual training.
Integrate cybersecurity into your company’s operations rather than seeing it as a hindrance. It creates value, gives people the self-assurance they need to innovate, and creates new income streams and market prospects.
Even the most experienced cybersecurity professionals face novel and unanticipated problems as a result of the ever-changing threat environment. In addition to moving beyond reactive technology adoption and disaster recovery, organizations must constantly improve their security procedures and embrace an approach that centers cyber resilience inside an end-to-end organizational strategy.
Cyber resilience is a holistic strategy to defending enterprises that includes business continuity, information systems security, and organizational resilience. It goes well beyond just anticipating and reacting to threats and assaults. Cyber resilient firms must integrate security into every element of their operations and iterate to improve their posture. Innovators are helping achieve cyber resilience, which is difficult.
Cyber resilience vs cyber security
The first issue that gives rise to the requirement for cyber resilience is the extreme complexity that security executives are now facing in their enterprise’s technology and security ecosystems. The use of many technological solutions by IT and security professionals to counter attacks has resulted in significant complexity in their tech stacks and security plans. According to EY study, the most often mentioned internal obstacle to an organization’s cybersecurity strategy is “too many attack surfaces.” Additionally, 75% of respondents identified cloud and Internet of Things (IoT) as the top technological concerns for the next five years. Emerging technologies and generative AI (GenAI) provide additional complexity and dangers to the enterprise.
Cost and cross-functional work provide the second challenge. In the past, the majority of companies have provided strong support for cybersecurity expenditures. However, if threats increase in strength and number, businesses could start to doubt their financial commitments. Security has to be a company-wide endeavor, not only the domain of the IT department and cybersecurity teams, in order to decide where to allocate their money for security and implement top-down initiatives.
More than ever, companies need to integrate security into their technology instead of depending only on security personnel to safeguard all facets of their operations. Improved communication across organizational layers is necessary to transform cybersecurity from a compartmentalized endeavor into a cross-functional operation, which is a feature of the most successful security programs.
Finally, leaders need a mentality change. Strong cybersecurity is no longer a game of cat and mouse with unique solutions to address unique assaults because the rules have changed. In the current threat environment, a firm must contend with skilled attackers and not rely just on disaster recovery or business continuity plans. The ultimate answer, cyber resilience, can only be achieved by a company-wide integration of security policies, procedures, and technologies, which calls on leadership to adopt a more comprehensive and intrinsic security strategy.
Resilience cyber insurance solutions
To assist provide enterprises an advantage over contemporary cyber threats, the EY organization and Dell technology have collaborated with industry experts to develop an intelligent cyber resilience platform driven by AI/ML technology. The two innovators combine Dell’s data security technologies and cyber resilience tactics with the comprehensive industry knowledge and vision of the EY team. Together, they bring a wealth of technology and experience to the table. With the help of this potent combination, businesses can transform a complicated environment into a multilayered defensive system that can endure both changing risk and severe digital upheaval.
The alliance excels at using these technologies with the appropriate setup and procedures. The correct operational approach and the latest technology advances work together to create true cyber resilience, and each firm has a distinct optimal approach. Teams from EY and Dell are excellent at providing cybersecurity solutions that work as well as a tried-and-true process for operationalizing them to increase resilience, flexibility, and overall security posture. In order to understand an organization’s data challenges and vulnerabilities and to customize a solution to meet their needs, the EY organization and Dell collaborate closely with leaders in the industry. This allows the organization to secure its critical data from cyber threats while maintaining accessibility for daily operations.
Strengthen Your Cybersecurity Hardiness with Dell and EY
The partnership between EY and Dell Technologies gives progressive companies the adaptability they need to use advanced cybersecurity to fend off attackers and withstand changing threats. When together, they support organizations by:
Utilize an integrated, unified cyber resilience solution to handle the ever-increasing complexity of the technological and security environments.
Using a cross-functional collaborative strategy, bring all aspects of your firm under the cyber resilience umbrella.
Change the way you think about security in your firm and adopt a comprehensive strategy to cyber resilience that integrates procedures, policies, and resources across the whole enterprise.
Read more on govindhtech.com
#cyberresilience hashtag#cybersecurity hashtag#ey hashtag#dell hashtag#cyberthreats hashtag#genai hashtag#ml hashtag#ai hashtag#technology hashtag#technews hashtag#govindhtech
0 notes
Text
The Key Benefits of IT Services for Government Agencies

Introduction:
In today's digital age, government agencies are increasingly harnessing the power of Information Technology (IT) services to optimize operations, enhance service delivery, and meet the evolving needs of citizens. By leveraging IT solutions strategically, government organizations can drive efficiency gains, improve transparency, and foster innovation in public service delivery.
Benefits of IT Services for Government Agencies:
Enhanced Service Delivery:IT services enable government agencies to provide seamless and accessible services to citizens through digital platforms and online portals. This enhanced accessibility improves citizen satisfaction and reinforces the government's commitment to responsiveness and accountability.
Streamlined Data Management: Robust IT infrastructure facilitates efficient data management and analytics, empowering agencies to make data-driven decisions and optimize resource allocation. By harnessing insights from data analytics, government organizations can enhance operational efficiency, identify trends, and address citizen needs more effectively.
Cost Savings and Operational Efficiency: The adoption of IT services allows government agencies to streamline processes, automate repetitive tasks, and reduce administrative overhead. These efficiency gains translate into significant cost savings while enabling agencies to allocate resources more strategically to priority areas.
Strengthened Security and Compliance: IT services play a critical role in safeguarding government data and ensuring compliance with regulatory requirements. Robust cybersecurity measures protect against cyber threats and unauthorized access, enhancing data security and instilling confidence in citizens and stakeholders.
Remote Work Enablement: With the rise of remote work, IT services facilitate seamless collaboration and communication among government employees. Cloud-based tools and virtual platforms empower dispersed teams to collaborate effectively, ensuring continuity of operations and service delivery, even in challenging circumstances.
Drive Innovation and Modernization: IT services drive innovation and modernization within government agencies, enabling them to adopt emerging technologies and stay ahead of the curve. By embracing technologies such as artificial intelligence and blockchain, agencies can optimize processes, enhance service delivery, and drive transformative change.
Conclusion:
In conclusion, the adoption of IT services offers a myriad of benefits for government agencies, including improved service delivery, cost savings, enhanced security, and innovation. By embracing technology as a strategic enabler, government organizations can optimize operations, enhance transparency, and deliver value to citizens. As we navigate the digital age, leveraging IT services will remain crucial for shaping the future of governance and public service delivery.
#hashtag#itsolutions hashtag#governmentservices hashtag#efficiency hashtag#innovation hashtag#datamanagement hashtag#cybersecurity hashtag#costsavings hashtag#remoteworking hashtag#publicsector hashtag#digitaltransformation hashtag#modernization hashtag#governmenttechnology hashtag#itinfrastructure hashtag#servicedelivery hashtag#fullstackdevelopment hashtag#softwaredevelopment hashtag#webdevelopment
0 notes
Text
🔍 Why Bug Sweeping Services Are Essential for Corporates 🛡️

In today’s hyper-connected world, information is power—and corporate espionage is a very real threat. Confidential meetings. Intellectual property. Strategic roadmaps. All of it can be compromised if your spaces aren’t secure. Bug sweeping services (TSCM - Technical Surveillance Counter-Measures) are no longer optional—they're essential. Here’s why: ✅ Protect sensitive information from hidden listening devices, covert cameras, or tracking tools. ✅ Mitigate insider threats and corporate espionage. ✅ Ensure compliance with data protection and privacy laws. ✅ Maintain client trust by securing private conversations and contracts. ✅ Proactively manage risk in boardrooms, legal offices, and executive suites. If your business discusses ideas worth stealing, it’s worth investing in protection. Security isn’t just about firewalls anymore—it starts in the room. 📞 Call now at 9910808901 🌐 Visit us: https://bit.ly/4j793vC
#CorporateSecurity#BugSweeping#TSCM#CyberSecurity#DataProtection hashtag#ExecutiveProtection#RiskManagement#PrivacyMatters#CorporateEspionage#InfoSec#BusinessContinuity#TechSecurity
0 notes
Text
"Boost your online presence with Digit IT's SEO, social media marketing, link building, branding, and IT services. Drive traffic and grow your business today!"
Let me know if you'd like adjustments based on tone or specific audience focus!
#**Hashtags:**#ITServices#DigitalSolutions#BusinessGrowth#CustomSoftware#CloudSolutions#Cybersecurity#WebDevelopment#AppDevelopment#DigitalMarketing#ITConsulting#TechInnovation#DigitalTransformation#BusinessSolutions#TechSupport#DigitIt
1 note
·
View note
Text
🌐 Week Five: Digital Citizenship and Platform Practices
This week, we delve deeper into the concept of digital citizenship and how it relates to platform practices, civic engagement, and the responsibilities we hold in digital spaces. As online platforms become the primary spaces for political, social, and cultural exchanges, understanding what it means to be a digital citizen is more crucial than ever. 🌍💻
🤖 Defining Digital Citizenship: Beyond Basic Engagement
Digital citizenship encompasses the rights, responsibilities, and behaviors of individuals when interacting with digital technologies (McCosker 2016). In today's interconnected world, being a digital citizen is not just about using technology but about understanding the influence of digital platforms on civic life. Ribble (2015) emphasizes that digital citizenship also involves ethical behavior, online safety, and understanding the impact of our digital actions on both local and global communities.
According to Choi and Cristol (2021), digital citizenship should be more than just participation - it should actively encourage participatory democracy, ensuring that marginalized voices are heard. Digital platforms like Twitter, Instagram, and YouTube have become essential spaces for public discourse, where activism thrives and social movements are born. For instance, the Black Lives Matter movement utilized these platforms to elevate voices, challenge systemic racism, and push for legislative change, demonstrating the power of digital spaces in shaping public discourse (Choi & Cristol 2021; Jackson et al. 2020).

🖥️ Platform Practices: The Good, The Bad, and The Algorithm
Platforms such as Facebook, YouTube, and Twitter serve as the new public squares, where individuals engage in political debate, share cultural content, and build communities. However, the role of algorithms in shaping what we see, like, and share raises ethical concerns. Platformization - the process by which social, political, and cultural life is influenced by platform infrastructures - has given these platforms tremendous power over what information spreads and what gets buried (Duffy et al. 2019).
As Gillespie (2018) argues, platforms present themselves as neutral spaces, but their algorithms actively curate and prioritize content based on what drives engagement. This has significant implications for democracy and citizenship, as it may amplify certain voices while silencing others. For example, hashtags like #MeToo and #BlackLivesMatter have been crucial in rallying public attention, but the platform's algorithmic control can also suppress these movements when they don’t align with commercial interests (Gillespie 2018).
In addition, Zuboff's (2019) concept of surveillance capitalism warns that platforms often exploit users’ data for profit, turning every interaction into a commodified act. This commodification of our digital lives raises ethical concerns about privacy, autonomy, and the role of platforms in monitoring and shaping public discourse.
🔒 Digital Safety and Ethical Responsibilities of Citizenship
With the benefits of digital engagement also come risks, such as cyberbullying, data misuse, and online harassment. McCosker (2016) emphasizes that digital safety is critical for fostering an inclusive and respectful online environment. The rise of cyberbullying has led to significant legislation and educational initiatives to protect users, especially youth, from online harm (Livingstone 2019). Digital citizens are responsible for understanding the implications of their actions and ensuring that they contribute positively to digital spaces.
To address these issues, cyber safety initiatives must go beyond protecting individual users; they must also focus on the larger systems at play, including algorithmic biases and corporate control of data. As Livingstone et al. (2018) argue, fostering digital literacy is essential for empowering users to navigate these risks and become informed, critical participants in the digital world.
📱 Digital Activism and Hashtag Publics: New Frontiers in Civic Engagement
Digital activism is one of the most powerful examples of digital citizenship in action. By using platforms to challenge social norms, raise awareness, and push for change, digital activism has transformed the way we engage with politics. Hashtags like #MeToo, #BlackLivesMatter, and #ClimateStrike are more than just tools for spreading information—they are catalysts for social movements that transcend geographic boundaries.
According to Jackson, Bailey, and Foucault Welles (2020), hashtag publics allow marginalized groups to create their own discursive spaces, bypassing traditional media and directly engaging with global audiences. This form of digital activism not only raises awareness but also fosters solidarity, creating communities that are united by shared goals and values.
However, digital activism is not without challenges. Platforms are not neutral, and activists must navigate the limitations of algorithms, censorship, and corporate interests (Zuboff 2019). Moreover, Dean (2016) notes that the quick, viral nature of hashtag activism can sometimes reduce complex social issues into soundbites, limiting deeper engagement and long-term change.

References
Choi, M & Cristol, D 2021, 'Digital citizenship with intersectionality lens: Towards participatory democracy driven digital citizenship education', Theory Into Practice, vol. 60, no. 4, pp. 361-370, <https://doi.org/10.1080/00405841.2021.1987094>.
Duffy, BE, Poell, T & Nieborg, DB 2019, 'Platform practices in the cultural industries: Creativity, labor, and citizenship', Social Media + Society, vol. 5, no. 4, pp. 1-8, DOI: <https://doi.org/10.1177/2056305119879672>.
Gillespie, T 2018, Custodians of the Internet: Platforms, content moderation, and the hidden decisions that shape social media, Yale University Press, New Haven.
Jackson, SJ, Bailey, M & Foucault Welles, B 2020, #Hashtag Activism: Networks of Race and Gender Justice, MIT Press, Cambridge.
Livingstone, S 2019, 'Young people and the new media: Childhood and the changing media environment', Sage, Thousand Oaks, CA.
McCosker, A 2016, 'Managing digital citizenship: Cyber safety as three layers of control', in Negotiating Digital Citizenship: Control, Contest and Culture, Rowman & Littlefield, London.
#mda20009#digitalcitizenship#cybersafety#cybersecurity#activism#hashtag#social media#algorithm#media bias
0 notes
Text
0 notes
Text
Weekly output: Android feature drop, 5G-connected e-bike, infosec diplomacy, "Feel Tech Animal" demo, Bluesky supports hashtags, AT&T and AST SpaceMobile, Facebook to nix News tab, Mark Vena podcast
I have only two days this upcoming workweek that aren’t blocked off completely, Monday and Thursday. Tuesday I’ll be working the Virginia primary election (hard to believe it’s been almost four years since my first long day as a poll worker), Wednesday I’m covering the ACA Connects telecom-industry conference, and Friday I fly to Austin for SXSW. In addition to the stories below, I wrote a bonus…

View On WordPress
#Android feature drop#AST SpaceMobile#AT&T#Barcelona#BCN#Bluesky#cybersecurity#e-bikes#Facebook News#hashtags#infosec#Mark Vena#Mobile World Congress#MWC#NTN#satellite to phone#virtual reality#wireless
0 notes
Note
This is Agent Fowler calling.
Megatron. Please, for the love of god. Can you tell your niece to stop hacking into the Pentagon and rickrolling us?
Our cybersecurity team are at their wits end and I am one more ‘never gonna give you up’ away from murdering Agent Simmons.
Ms. Hashtag if you can see this: PLEASE STOP
My apologies.
Hashtag? What have you done? What is all this about playing tricks on the Pentagon?
Hey! It wasn't me! I swear! Mom would be so mad if I did a thing like that.
What's all the fuss about?
Someone has been playing tricks on the Pentagon.
Well... not to get into politics... but it's deserved, isn't it?
Starscream! If it turns out that you are behind the... what is rickrolling?
No idea!
I take it it is an Autobot... thing. Anyway, regardless. If you have had a part in it...
I'll find out who it was and make it stop. It was probably Swindle.
Excellent.
21 notes
·
View notes
Text
“Stop Internet Censorship” Master List
The following is a master list for all of the major Internet Censorship and Surveillance Bills between 2022 to 2023, with the most major bills that are currently active posted below. They will each link to the Tumblr posts that I have made in the past related to them, with all of the relevant information associated.
This was made because I feel people need to get a sense for just how interconnected they really are, how much Congress and third parties are trying to desperately gain full control and access to our information and silencing anything they don’t want to see and hear, and having a centralized hub of information for them will make it easier for people to find them.
The Major Bills:
EARN IT Act: 2022 version of EARN IT Act
2023 version of EARN IT Act (No text yet, but it’s pretending to be about preventing child abuse online this time)
Enigma2Me Post on EARN IT Act
fullhalalalchemist Post on EARN IT
Condemnation of the EARN IT Act 2020 Coalition Letter
STOP EARN IT Act LINKTREE
Engadget: EARN IT Act reintroduced for the Third Time
------
Kids Online Safety Act: Current Draft of 2023 KOSA bill
Enigma2Me Post on Kids Online Safety Act
STOP KOSA LinkTree
------
RESTRICT Act: Read Bill Here.
Enigma2Me Post On RESTRICT Act
LoganGalbraith’s Post on RESTRICT Act
Truthout Article 4/02/2023: Restrict Act Critics Call the Far-Reaching “TikTok Ban” Bill a “Patriot Act 2.0”
------
STOP CSAM Act:
Electronic Frontier Foundation: Take Action on STOP CSAM/EARN IT
TechDirt Post Against STOP CSAM Act
------
So if you’ve seen the above, you’re probably asking: What can we do about it?
1) Spread the Word online!
Twitter Hashtags
For Earn It: #EARNITAct, #STOPTheEARNITAct, #NoEarnItAct
For KOSA: #KOSA, #KidsOnlineSafetyAct, STOPKOSA
For RESTRICTAct: #RESTRICTAct, #STOPRESTRICTAct
2) PLEASE call your Senators.
Find your 2 senators numbers here. Fax them, email them. Tell them they MUST oppose this bill. Calmly make it clear to them that if they support this bill, then you will vote for someone else who doesn’t go along with this blatant act of authoritarian intent.
3) CONTACT any major human rights and cybersecurity related organizations and let them know about this bill. Get this out to any local news groups that you can.
The following Google Doc contains a list of every major organization we could think of to contact, and will be updated as we find more allies in the fight against censorship and surveillance.
ANTI-CENSORSHIP MASTER LIST
Also Contact the organizations on these 2020 letters to get them to publicly speak out against the EARN IT Act like they did back then.
But for those who want to have official organizations to work with (and who usually have petitions except TechDirt), the following usually are up to date on info:
Electronic Frontier Foundation
Fight For the Future
Techdirt
#RESTRICT Act#EARN IT Act#Stop Kids Online Safety Act#stop internet censorship#stop restrict act#stop earn it act#FUCK BLUMENTHAL#fuck surveillance#fuck censorship#archive post#archive
652 notes
·
View notes