#Biometrics Journal Reference
Explore tagged Tumblr posts
Text





Abstract
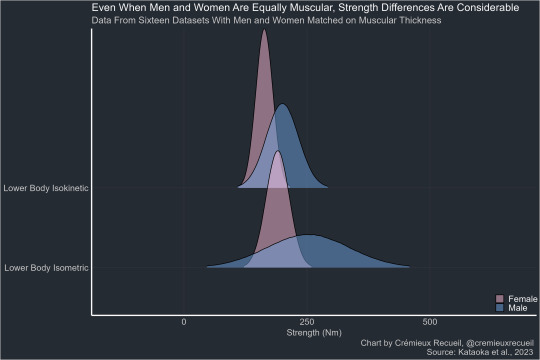
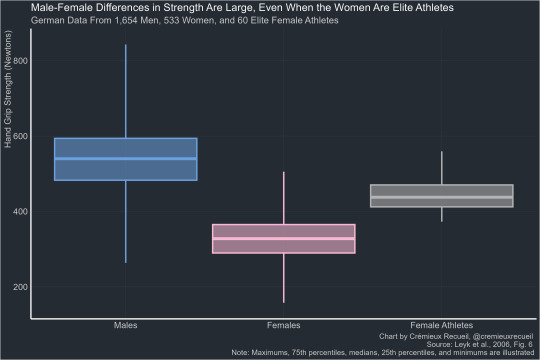
Hand-grip strength has been identified as one limiting factor for manual lifting and carrying loads. To obtain epidemiologically relevant hand-grip strength data for pre-employment screening, we determined maximal isometric hand-grip strength in 1,654 healthy men and 533 healthy women aged 20–25 years. Moreover, to assess the potential margins for improvement in hand-grip strength of women by training, we studied 60 highly trained elite female athletes from sports known to require high hand-grip forces (judo, handball). Maximal isometric hand-grip force was recorded over 15 s using a handheld hand-grip ergometer. Biometric parameters included lean body mass (LBM) and hand dimensions. Mean maximal hand-grip strength showed the expected clear difference between men (541 N) and women (329 N). Less expected was the gender related distribution of hand-grip strength: 90% of females produced less force than 95% of males. Though female athletes were significantly stronger (444 N) than their untrained female counterparts, this value corresponded to only the 25th percentile of the male subjects. Hand-grip strength was linearly correlated with LBM. Furthermore, both relative hand-grip strength parameters (F max/body weight and F max/LBM) did not show any correlation to hand dimensions. The present findings show that the differences in hand-grip strength of men and women are larger than previously reported. An appreciable difference still remains when using lean body mass as reference. The results of female national elite athletes even indicate that the strength level attainable by extremely high training will rarely surpass the 50th percentile of untrained or not specifically trained men.
#dimorphism#science#biological dimorphism#sex differences#biology#human biology#grip strength#lean body mass#body mass#body mass index#religion is a mental illness
15 notes
·
View notes
Text
Instagram Face: Why Everyone Is Starting to Look the Same?
Let’s play a game. Open Instagram. Scroll five selfies. I bet at least three of them look eerily similar: High cheekbones. Snatched jawline. Pouty lips. Smooth glassy skin. Catlike almond eyes. Perfectly arched brows.

Congrats! you’ve just spotted the “Instagram Face.” It’s beautiful. It’s flawless. It’s also... everywhere ;( But how did we get here? Why are different people, across cultures and continents, chasing the same face? Let’s filter this out 🧠
Filtered Reality, Literally
As Rettberg (2014) explains, filters don’t just tweak your lighting: they reshape your reality. Instagram and Snapchat filters nudge users toward aesthetic norms that the algorithm (and culture) favors: thinner noses, bigger eyes, and smoother skin. Over time, users internalize these enhancements as the new baseline.

You’re not just beautifying. You’re editing yourself into the algorithm’s idea of hot. And when millions of people do the same thing? Boom: beauty homogenization.
From FaceTune to Facelift
Enter Coy-Dibley’s (2016) idea of digitized dysmorphia - where people become obsessed with their filtered face to the point they want to look like it IRL. Think: fillers, buccal fat removal, and the rise of “Snapchat dysmorphia.”
TikTok’s “Bold Glamour” filter sparked a wave of creators saying, “Why don’t I look like this in real life?” You don’t... because no one does.
youtube
If Everyone’s Hot, Then Who’s Boring?
The "Instagram Face" creates an illusion of diversity while reinforcing a singular, Westernized beauty ideal. Coy-Dibley (2016) and Rettberg (2017) both point out how platforms offer a “menu” of desirable traits, but the defaults tend to align with whiteness, thinness, and femininity. It’s not just aesthetic - it’s political. Filters erase features, flatten cultural identity, and promote beauty colonialism in digital form.
Software Literacy: Know Your Filter
If we don’t understand how filters shape our self-image, we can’t resist them. This is where software literacy and digital citizenship come in. Choi & Cristol (2021) argue that being a good digital citizen means being critical of the tools we use - especially the ones that quietly train us to hate our unfiltered selves.

Final Thought
Instagram Face didn’t just “happen.” It was built, coded, tested, and normalized. And while filters can be fun and creative, they’re also ideological machines, shaping how we see beauty - and ourselves.
So next time you reach for that beauty filter, ask yourself: Are you enhancing… or erasing?
Seen any wild “Instagram Face” trends lately? Or have a favorite creator who keeps it beautifully unfiltered? Drop it in the tags. Let’s celebrate faces that aren’t factory settings.
References
Choi, M., & Cristol, D. (2021). Digital citizenship with intersectionality lens: Towards participatory democracy driven digital citizenship education. Theory Into Practice, 60(4), 361–370. https://doi.org/10.1080/00405841.2021.1987094
Coy-Dibley, I. (2016). ‘Digitized dysmorphia of the female body: The re/disfigurement of the image’. Continuum: Journal of Media & Cultural Studies, 30(2), 126–138. https://doi.org/10.1080/10304312.2016.1141868
Rettberg, J. W. (2014). Seeing Ourselves Through Technology: How We Use Selfies, Blogs and Wearable Devices to See and Shape Ourselves. Palgrave Macmillan.
Rettberg, J. W. (2017). Biometric citizens. In A. T. Kenney, M. D. Witmer, & A. J. Tinkcom (Eds.), Theories of the Mobile Internet (pp. 123–138). Routledge.
2 notes
·
View notes
Text
[8]Augmented Beauty – Are AR Filters Changing How We See Ourselves?
Snapchat and Instagram filters have turned self-presentation into augmented reality. A single swipe can smooth skin, reshape features, and create a “perfect” version of yourself. But what happens when that filtered self becomes more desirable than reality?
These effects aren’t just playful enhancements—they’re reshaping beauty standards, self-esteem, and even cosmetic trends. If we see ourselves more often through a digital lens, how do we separate real identity from algorithmic perfection?

Snapchat & The Rise of Filtered Beauty
Snapchat was the first platform to introduce real-time beauty filters, subtly refining facial features while making users look “better.” What started as fun became an expectation—the filtered self replaced the real one. Studies found that many users, particularly young women, felt pressure to match their digital appearance, leading to Snapchat Dysmorphia, where people seek cosmetic procedures to look like their filtered selfies (Baker, 2022).
This isn’t just about beauty preferences—filters gamify self-perception, reinforcing what the algorithm deems attractive. The more polished a face looks, the more engagement it gets, creating a cycle where digital perfection becomes the standard.

Who Controls Beauty? The Algorithm Decides
Filters aren’t neutral. Research shows that many AR effects lighten skin, shrink noses, and enlarge eyes—reinforcing Eurocentric beauty ideals (Coy-Dibley, 2016). Snapchat’s early beauty lenses, for example, made darker skin appear washed out, proving that even code carries cultural bias.
Platforms claim these filters enhance self-expression, but who is really being enhanced, and who is erased? Algorithms prioritize conventionally attractive faces because they get more engagement, creating a system where beauty is no longer personal—it’s dictated by data.
More Than A Filter: The Biometric Surveillance Issue
Every time you use a face-altering filter, your facial data is mapped and stored. While platforms say this is for user experience, it’s also used for facial recognition and AI training (Rettberg, 2017).
This raises major privacy concerns. If we normalize scanning and modifying our faces, we also normalize a future where facial tracking is the default—for advertising, policing, and surveillance. The question isn’t just how we see ourselves, but who else is watching.
Can We See Ourselves Beyond the Filter?
Filters are more than playful effects—they reshape self-perception, reinforce biased beauty norms, and normalize biometric surveillance. As AR tools become more advanced, the gap between digital perfection and reality widens, fueling body dissatisfaction and algorithm-driven beauty expectations.
Social media platforms must take responsibility by ensuring transparency in AR design, reducing racial and gender biases in filters, and limiting biometric data collection. However, individual users also play a role. Recognizing that filtered beauty is artificially constructed is the first step in reclaiming control over self-image.
True beauty should not be dictated by an algorithm that optimizes faces for engagement. Instead of conforming to digitally altered ideals, we should challenge the idea that perfection must be enhanced, corrected, or filtered at all.

References
Baker, J. (2020). Making-up on mobile: The pretty filters and ugly implications of Snapchat. Fashion, Style & Popular Culture, 7(2+3), 207–221. https://doi.org/10.1386/fspc_00015_1
Coy-Dibley, I. (2016). Digitized Dysmorphia: The Effect of Social Media on Perceptions of the Female Body. Journal of Gender Studies, 25(4), 423-437.
Rettberg, J. (2014). Filtered Reality: The Rise of Digital Self-Presentation and Biometric Tracking. New Media & Society, 16(3), 479-497.
Rettberg, J. (2017). Biometric Citizens: The Role of Facial Recognition in Digital Identity Construction. Surveillance & Society, 15(5), 627-643.
1 note
·
View note
Text
AR Abuse – When Your Face Doesn’t Belong to You
AR filters are effects that use augmented reality (AR) technology to insert virtual elements into the real world, creating a transformed but still realistic image (Azuma, 1997, p. 355). Initially, AR filters were developed for entertainment purposes, but today, they have become a tool to collect biometric data without the user knowing. When the face becomes a form of data that can be analyzed, stored and exploited, we must ask: Do we own our own digital identity?
👤Facial Recognition - When Privacy Is No Longer Yours
According to Baker (2020), Snapchat filters are not only a beauty tool but also collect biometric data to improve facial recognition. Instagram, TikTok and many other applications also use this technology to track facial features over time. The constant use of filters by users is not just for entertainment, but also inadvertently turns them into "trainers" of AI, helping the system to recognize faces more accurately.
🔹 Facial data is being collected without clear transparency.
🔹 Facial recognition is no longer a technology serving humans, but can be used for surveillance.
🔹 When the face becomes a form of "biometric password", can you protect it?
Rettberg (2017) argues that selfies today are not just a personal moment, but also data for machines to analyze. The use of this technology in facial recognition makes people gradually become "biometric citizens", where personal identity is digitized and can be abused. When AI can identify and track a person based on their face alone, do we have privacy?
🎭Deepfakes, Fake Identities, and the Growing Danger
In addition to data collection, AR filters have also played a role in the development of deepfakes - a technology that creates fake images and voices that are so realistic that they are difficult to distinguish. Improvements in facial recognition and artificial intelligence have not only improved security, but also made identity forgery easier than ever.
🔹 Deepfakes can create extremely realistic fake images and videos, posing enormous security threats (Verdoliva, 2020).
🔹 Cybercriminals can exploit facial data to commit fraud.
🔹 When your image is controlled by AI, are you still yourself in the digital space?
This poses a big challenge: Can we trust what we see in the digital age? As deepfakes proliferate, the line between real and fake is blurring. Without strong safeguards, personal identity can become a tool for manipulation, fraud, and even human rights violations. This is no longer a technology issue, but a crisis of trust and privacy.
The most important question remains: Are we trading control of our own identity for a beauty filter?

What do you think about facial recognition technology becoming more and more ingrained in our lives? Is it a step forward or a threat? Share your views below! ⬇️
References
Azuma, R. T. (1997). A Survey of Augmented Reality. Presence: Teleoperators and Virtual Environments, 6(4), 355–385. https://doi.org/10.1162/pres.1997.6.4.355
Barker, J. (2020). Making-up on mobile: The pretty filters and ugly implications of snapchat. Fashion, Style & Popular Culture, 7(2), 207–221. https://doi.org/10.1386/fspc_00015_1
Rettberg, J. W. (2017). Biometric Citizens: Adapting Our Selfies to Machine Vision. Springer EBooks, 89���96. https://doi.org/10.1007/978-3-319-45270-8_10
Verdoliva, L. (2020). Media Forensics and DeepFakes: An Overview. IEEE Journal of Selected Topics in Signal Processing, 14(5), 910–932. https://doi.org/10.1109/jstsp.2020.3002101
0 notes
Text
The Future of Filters: Beyond Beauty Enhancements

Filters are developing into more than merely instruments for altering eye color or smoothing skin. Digital filters of the future are heading toward an immersive, interactive experience that combines augmented reality (AR) with daily life. Although filters were originally used to improve appearance, they now include fun, interactive effects that may change settings, produce animations, and even incorporate 3D into videos. These technologies are already being used by platforms such as Instagram, Snapchat, and TikTok, and as augmented reality develops, we should expect to see increasingly more imaginative and customized filter experiences.
It is anticipated that filters will advance in sophistication to better accommodate different faces and settings, enabling users to produce one-of-a-kind, highly customized content. The virtual and real worlds could be blended together by using filters that represent events, mood, or weather. In order to allow customers to digitally "try on" apparel, accessories, and even home décor before making a purchase, businesses are also experimenting with filters for virtual shopping experiences."
But there are also moral concerns with this advancement. Filters have come under fire for encouraging unattainable beauty standards and having a detrimental impact on mental health. There might be more pressure on the industry to make filter usage more transparent, possibly by including minor clues that show when an image has been altered. Additionally, consumers might be encouraged to embrace more natural content or utilize these tools more thoughtfully as filters become more immersive.
Filters of the future combine responsibility, innovation, and technology. With AR developments, filters could become more widely used outside of social media, fostering new forms of digital interaction and promoting safer online norms and behaviors.
Reference list
Arena, F, Collotta, M, Pau, G & Termine, F 2022, ‘An Overview of Augmented Reality’, Computers, vol. 11, no. 2, p. 28, viewed <https://www.mdpi.com/2073-431X/11/2/28/htm>.
Barker, J 2020, ‘Making-up on mobile: The pretty filters and ugly implications of snapchat’, Fashion, Style & Popular Culture, vol. 7, no. 2, pp. 207–221, viewed <https://intellectdiscover.com/content/journals/10.1386/fspc_00015_1>.
Coy-Dibley, I 2016, ‘“Digitized Dysmorphia” of the female body: the re/disfigurement of the image’, Palgrave Communications, vol. 2, no. 1, viewed <https://www.nature.com/articles/palcomms201640>.
Jill Walker Rettberg 2017, ‘Biometric Citizens: Adapting Our Selfies to Machine Vision’, Springer eBooks, pp. 89–96.
0 notes
Text
Lupine Publishers-Biometrics and Biostatistics Journal
Model Selection in Regression: Application to Tumours in Childhood by Annah Managa

We give a chronological review of the major model selection methods that have been proposed from circa 1960. These model selection procedures include Residual mean square error (MSE), coefficient of multiple determination (R2), adjusted coefficient of multiple determination (Adj R2), Estimate of Error Variance (S2), Stepwise methods, Mallow’s Cp, Akaike information criterion (AIC), Schwarz criterion (BIC). Some of these methods are applied to a problem of developing a model for predicting tumors in childhood using log-linear models. The theoretical review will discuss the problem of model selection in a general setting. The application will be applied to log-linear models in particular.
https://lupinepublishers.com/biostatistics-biometrics-journal/fulltext/model-selection-in-regression-application-to-tumours-in-childhood.ID.000101.php
For more Lupine Publishers Open Access Journals Please visit our website https://www.lupinepublishers.com/
For more Biostatistics & Biometrics Articles Please Click Here: https://lupinepublishers.com/biostatistics-biometrics-journal/
#Biometrics Open Access Journal#Biostatistics and Biometrics Open Access Journal#Biometrics Journal Reference#Journal of Biometrics
1 note
·
View note
Text
ANALYSIS of Face Cages
Denada Permatasari. 1 September 2017.

Fig 1. Zach Blas’ Face Cages, exhibited at the Institute of Contemporary Arts Singapore, Gallery 1. 29 July - 22 October 2017.
I visited Gallery 1 at B1 on LASALLE College of the Arts, Singapore and I was immediately drawn to Zach Blas’ Face Cages exhibition.
The exhibit contains four 113.7 x 64 cm screens displayed in portrait mode, with each screen presenting a twelve-minute video of people wearing different masks. The screens have the distance of 93 cm between them. At the front of the screens there are the original masks that were worn by the subjects, not remakes. The plain black background behind the screens and the contrasting white lights illuminating the masks gives off a very polished and technologically-savvy vibes of the exhibition, even when the placement of the exhibition is not at the front of center of the gallery.
The face masks are 3D-printed with stainless steel as their material, and the polygonal patterns are from the subjects' own biometric data from facial recognition scans. They are symmetrical and express a progression from barely a mask until a mask so wide it goes beyond the just the face. The material's strength and durability is a symbol of oppression that is everlasting, while the progression shows the growth of imprisonment that steadily gets worse overtime.
Face Cages is the title of the series and I think the title is self-explanatory. At first glance, I understood immediately what the series is about. It's about not being able to express our true selves, and that we are trapped within our own selves. But after further study I found out that the artwork carries a more nuanced meaning.
First, I learned that the artist who made them, Zach Blas, is a gay man. The rest of the subjects also belong to the LGBT community. Aside from Blas, they are also racial minorities (non-Caucasian). The fact that the subjects wearing the masks are minorities of minorities makes this series a bold political statement: "We, (referring to Blas et al. as representatives) the minority, suffer greatly."
To give this series even further context, "Zach Blas is an artist and writer whose practice confronts technologies of surveillance, security and control with minoritarian politics." (Blas) The masks do not fit the subject's faces and in doing so, it is an "endurance performance" as it is very painful to wear them. I can confidently say that this is an analogy of the minority struggle, in which they suffer until they can't anymore (implying rebellion and or suicide).
From the start of the 2010s, especially up until the mid-2010s, the LGBT discourse is reaching its all-time high, with notable moments such as the USA legalising same-sex marriage country-wide in June 2015 and the suicide of Leelah Alcorn, a transgender teen, in December 2014, just to name a few. This series rightly belongs to the Contemporary Art genre, which has all the hallmarks of the genre: identity politics and incorporated technology (Kleiner 942).
Taking into account of today's social and political context, this series is a plea for attention, a "dramatization of the abstract violence of the biometric diagram." (Blas) When I read that, I disagreed with the description as 'violence' is a strong and specific word, but upon more research I discovered that it is about literal violence; countries all over the world are implementing a nationwide biometric face scan for identification purposes, and people whose faces aren't recognised will receive penalty and years in prison. (Blas)
At this point I realised that Face Cages is a literal title, not a metaphorical one. The revelation drives home at the gravity of systemic discrimination and violence inherent in a so-called 'objective' algorithm that runs biometric scans, and that this invisible brutality is happening right under my nose. After viewing Face Cages and having knowledge of its context, I am grateful and impressed at Blas' courage for speaking up through his art, to give the oppressed minorities a voice that can, and should be heard.
References
Blas, Zach. “Biography”. <www.zachblas.info/biography/>
Kleiner, Fred S. Gardner’s Art through the Ages. 14th edition. Wadsworth Publishing, 2012. Print.
Blas, Zach. “Face Cages”. <http://www.zachblas.info/works/face-cages/>
Blas, Zach. “Escaping the Face: Biometric Facial Recognition and the Facial Weaponization Suite”. Journal of the New Media Caucus. CAA Conference 2013 (2003). <http://median.newmediacaucus.org/caa-conference-edition-2013/escaping-the-face-biometric-facial-recognition-and-the-facial-weaponization-suite/>
#zach blas#face cages#lgbt#oppression#minority#queer#biometric#identity#algorithm#essay#analysis#art#exhibition#lasalle#2017#malphigus#malphiguswrites
2 notes
·
View notes
Text
Views of nature as well as natural light (Duffield et
The core benefits of the spirituality in the care delivery revolve around the elements of prayer, meditations and religious counsel provided in the facility (Yong, Kim, Park, Seo, & Swinton, 2011). These benefits include the increasing feeling of optimism and hope, decreased fear, and anxiety in addition to decreased depression and faster recovery from cases of depression.Journal of nursing management,18(8), 901-913. The assertion is that the access to these attributes of the healthcare environment reduces the amounts of job stress endured by nurses..The Journal of Continuing Education in Nursing,42(6), 280-288. (2011).Sherry Roberts is the author of this paper.The use of technological innovation in the reduction of extraneous noise via the replacement of the overhead paging system with a call system that will route the request to a mobile phone is critical to this reduction. S., . Effects of work environments on nurse and patient outcomes. (2012)., King, M. (2008). K. The patient outcomes are additionally promoted via the coordination of wellness encompassing the adoption of staff productivity through assessment of their health via the use of biometrics, stress management, satisfaction, productivity as well as absenteeism. Patient safety, satisfaction, and quality of hospital care: cross sectional surveys of nurses and patients in 12 countries in Europe and the United States., Seo, I., &
Aisbett, K.International journal of arts and commerce,3(9), 101-119. The hospital environment should be one that assists in the prevention of patient falls; the hospital acquired infections as well as some types of medical efforts (Kalisch, Tschannen & Lee, 2012).Evidence Based Design for healthcare facilities, 45-80. There additionally should be the use of a multilingual signage to address the cultural diversity at the facility., Roche, M.Daykin, N.Yong, J. (2011)., McKee, M. Effects of a spirituality training program on the spiritual and psychosocial well-being of hospital middle manager nurses in Korea.Question TwoThe health facility design, arts, and spirituality have additionally been found to be a major contributor to the patients' healing processes., O'Brien-Pallas, L., & Lee, K. (2014).Com in urgent custom research papers., Kim, J. The medical healers model adopted refers to the program that emphasizes on the holistic practices as well as noninvasive means that will assist the patient to reduce their stress, lessen their pain, promote their sleeping patterns and heal on the four levels.Journal of nursing care quality,27(1), 6-12. Nursing staffing, nursing workload, the work environment and patient outcomes. (2012). J. Access to the serene landscaped gardens that are nestled throughout the facility for meditation along with reflection offer both the workforce and patients at the facility with an environment that offers them an opportunity to assess their wellbeing and focus on the positive attributes (Daykin, Byrne, Soteriou & O'Connor, 2008).
A senior editor at MeldaResearch., & O'Connor, S.Architecture, Arts, Spirituality, Healing and Health. Bmj, 344, e1717. These technological innovations have allowed for the provision of quiet nurse call systems that enhance patient-nurse communication in addition to providing a more peaceful environment (Aiken, et al. (2010).The provision of the quiet nurse call platforms fitted with the latest technological features promotes the satisfaction at the facility as they allow the elimination of the noisy overhead paging that adversely affects the nurse response and patient access to timely services as the facility. It is attained through the creation of centers of care via the branding of their facilities furthermore relating the dots between the diagnostic and treatment processes (Rousek & Hallbeck, 2011).Duffield, C., Soteriou, T. M. O. Wayfinding in healthcare facilities: contributions from environmental psychology.Iyendo, T. Such interventions that reduced the level of stress suffered by nurses and thus better satisfaction rates include shorter shifts, access to sophisticated technologies, reduced workloads that led to better service delivery and thus superior patient satisfaction., Finegan, J. The furniture and surfaces have been made to feature rounded corners, non-textured surfaces as well as clean lines that are meant to offer pathogens and dust fewer places to hide (Daykin, Byrne, Soteriou & O'Connor, 2008).Journal of the Royal Society for the Promotion of Health,128(2), 85-94., Park, J. & Tishelman, C., & Swinton, J. Further, interventions based on the post-fall review encompassing the assessment of the possible reasons leading to the specific instances of a fall and remediating the contributing factors, patient and staff education, footwear advice have been interventions that successfully addressed the issue of falls.Rousek, J.Question ThreeIn the case of design, spirituality, artistic programs in of nosocomial infection control, fall prevention and wayfinding in healthcare, the assertion is that the perfect hospital environment should not only promote rest and healing.Kalisch, B.On the issue of promoting the wayfinding program at the facility, the assertion is that the program should be composed of the physical elements, communications as well as human interactions (Devlin, 2014).Technological interventions have also been central to the promotion of positive patients' outcomes with the core issues promoting the use of technologies in the facility encompassing the enhanced precision and safety in care delivery., Kerr, M.
Healing environments. There has been the provision of private rooms for the overnight patients and workstations between every two rooms to ensure the medical team can stay close the patient for better monitoring and access to patient records. Further, there is the use of a visual reminder that prompts the healthcare providers to adopt good hygiene which is central to the prevention of the secondary infections at the facility (Purdy, et al. Missed nursing care, staffing, and patient falls. The visual arts have been demonstrated to China LED bulb Manufacturers exhibit positive impact on the healthcare environment in an assortment of ways that include the presentation of opportunities for nonverbal communication and improving specific patient outcomes in oncology, diagnostic, cardiac and long-term care (Iyendo & Alibaba, 2014).).In preventing the in-hospital falls, it there has been the emphasis on the designing the location of the bathroom such that they are along the headwall allowing the unassisted patients to have something to hold on to while making their way to the bathroom (Daykin, Byrne, Soteriou & O'Connor, 2008).
1 note
·
View note
Text
Top Guidelines Of Marvel
The supplies to up grade the gears to twenty five may be received through actively playing Yet another freshly extra attribute termed "Best Planet Boss" which displays the past entire world bosses (Thanos as well as the Black Get) wearing their costumes for the Avengers Infinity War. By getting tier 3, figures get a 6th Lively skill, which calls for charging to 100% so as to use. Players can buy extra upgrades, equipment, comedian playing cards, and consumables via retailers. Gamers can rank up devoid of getting additional practical experience with Rank-Up Tickets. The group think that it's the Ultimates Doing the job to solve the challenge of the scale collapsing. If they get there at the Ultimates HQ - The Triskellion, They are really confronted from the defense techniques drones and also a skeptical Black Panther who believes They can be from Yet another dimension. Following overpowering Black Panther and assuring him of their identification they progress on to satisfy Blue Marvel who's focusing on the device to seal the dimension rifts. Blue Marvel apologizes with the hostile stability drones and Black Panther informs them the implies to shut them down lies within the lab at the guts of your Triskelion. Arriving in the lab They're attacked by The usa Chavez who again believes the heroes are from A different dimension. They control to influence her but quickly come to understand that the Triskelion has gone in comprehensive lock down. The heroes rescue Jemma from Goal. Jemma tells them that they took their analysis in Proportions. Shortly thereafter, in seeking to Track down MODOK, the heroes come upon alternate Proportions of varied heroes and villains and recognize that Purpose has created a tool to mail people today between dimensions. The Marvel brand had been made use of over the years, but solidified as the business's only brand name within a number of many years. "[a hundred thirty] Joe afterwards elaborated that when each movie's Imaginative group "come up with conceptually what we want to do" for a film, then We are going to request questions about whether This is able to interfere which has a storyline in One more movie. Or, what is going on on in that movie, can we pull a number of that into this movie? Which is wherever you start on the lookout for the interconnectedness, however it's important early on that the idea be made within a bubble because It's important to safeguard The theory, it needs to be pushed by storytelling. Kevin's ... often while in the mindset of "let us just make this Film now and be concerned about the next Motion picture when it will come."[128] Look at Image · Marvel @marvelapp Apr 29 “Our principal query right now is how do we enhance the caliber of research so that the influence we’re obtaining as functions is really precious?” In November 2013, Feige stated that "in a really perfect environment" releases each and every year would come with one particular movie dependant on an existing character and one showcasing a whole new character, stating It truly is "a good rhythm" in that structure. Although marvel fight , as evident by the 2013 releases of Iron Gentleman 3 and Thor: The Dark Earth, he said it's "definitely a little something to goal for".[thirteen] Feige expanded on this in July 2014, expressing, "I don't realize that we will keep to [that model] every year, but we're performing that in 2014 and 2015, so I feel it would be exciting to carry on that kind of thing".[fourteen] In February 2014, Feige said that Marvel Studios would like to mimic the "rhythm" that the comedian publications have produced, by having the figures surface in their own movies, then come together, much like "a huge celebration or crossover collection,"[fifteen] with Avengers films acting as "big, large linchpins". The player may have a maximum of 5 teams arrange. There are also workforce bonuses, for specified sets of character crew combinations. People are unlocked and rated up by getting Biometrics, which can be found in specified missions plus the Video game retail outlet. People can get well improve options at bigger concentrations and may be leveled up as a result of character XP. Gamers can easily personalize heroes to their Engage in design as a result of updates, like upgrading expertise, equipment, and equipping ISO-eight. In August 2016, Marvel announced that Marvel's Runaways had received a pilot get from Hulu,[85] eventually receiving a ten episode purchase the following Could.[86] That July, Loeb confirmed the series would occur inside the MCU saying, "It all life in a similar globe, the way it's related and where by It is really connected and what it should be linked to stays to become noticed. - Make a choice from numerous Uniforms to boost your character’s powers and perfect your hero's glance. With our marvel future fight hack, you might recruit and unlock every one of the playable people in the game. Quite possibly the most basic way I could place it really is Marvel won't come to the filmmakers and say, "This is what the following Film is." They come to the filmmakers and say, "Exactly what is the up coming movie?" That's very much the process. This post could contain content discouraged through the handbook of fashion for video clip video game subjects. Make sure you support by eliminating articles which include lists of minutiae or an in depth description of tips on how to Participate in a game, and rewriting the short article within an encyclopedic type. (December 2018) I downloaded the mod, but Not any figures unlocked And no crystals either. You should convey to how to address this issue?
A Review Of Marvel Future Fight
In April 2017, in addition to his announcement that he was returning to write and direct Guardians in the Galaxy Vol. three, James Gunn disclosed he can be dealing with Marvel "that will help style in which these tales go, and ensure the future in the Marvel Cosmic Universe is as Distinctive and reliable and magical as what We've got produced to this point". Your not too long ago viewed things and featured tips › Check out or edit your searching historical past Almost all of Marvel's fictional figures function in only one truth often called the Marvel Universe, with most areas mirroring real-lifetime destinations; a lot of key people are based in New York City.[3] Now, its time to search out many of the available superheroes to face collectively to stop the villains from destroying the planet. Marvel Future Fights Mod APK September 2018 do i just tap on my hero group 5 time for the 5X and Def to operate and my cellphone is not really rooted and want to know if this get the job done also my account is auto login to google? Check out photo · Marvel @marvelapp Apr 24 Replying to @steffenbogeholm If you select an iPad task, it will eventually perform comprehensive-display on the iPad itself but Provide you use of the swipe location so for the end consumer there isn't any variation :) When the studio employed Kenneth Branagh and Joe Johnston to immediate Thor and Captain The us: The very first Avenger, respectively, it created guaranteed both administrators ended up open to the thought of a shared universe and which include Avengers established-up scenes inside their movies.[six] Joe Russo said, "That is the thrilling component of [incorporating references to your much larger universe]. 'What can we put in place to the future?' You might be consistently pitching out Thoughts that not simply impact your movie, but could possibly have a ripple influence that affects other movies ... It is a Bizarre sort of tapestry of writers and directors Performing collectively to generate this universe that is form of organic. In August 2011, Marvel introduced a number of direct-to-video clip shorter films referred to as Marvel 1-Shots,[117] the identify derived from your label utilized by Marvel Comics for his or her one particular-shot comics.[118] Co-producer Brad Winderbaum mentioned, "It is a fun technique to experiment with new people and ideas, but far more importantly it's a way for us to broaden the Marvel Cinematic Universe and notify stories that live outside the house the plot of our characteristics."[117] Every single brief movie is designed to be considered a self-contained story that provides far more backstory for people or activities released while in the films. 1Apkmod is completely dedicated towards Modding of Video games, Android Purposes and lots of much more things. marvel game at 1Apkmod offer the best at school Doing work mods of each of the video games. Subscribe to our E-newsletter for modern updates. Dont know the place to tap 5x. Ive attempted tapping everywhere you go. As an alternative to a video are you able to publish screenshots on exactly where to faucet? A few of these have been published in larger sized-format black and white Journals, less than its Curtis Magazines imprint. @deanblacc who developed his own pixel artwork iOS game in his spare time! Go seize it! twitter.com/AdvOfKidd/stat… … As Marvel Future Fight Mod APK Latest Version Download of DC Comics, this man definitely knew many of the product sales figures and was in the most beneficial situation to inform this tidbit to Goodman. … Needless to say, Goodman would wish to be playing golf using this type of fellow and be in his superior graces. … Sol worked carefully with Impartial Information' major management more than the a long time and might have gotten this story straight from the horse's mouth. Loeb talked further on the topic in July 2016, reiterating The problem of scheduling by declaring "if I'm taking pictures a tv series and that is intending to go on over a 6-month or eight-thirty day period interval, how am I gonna get [a television collection actor] to have the ability to go be inside of a Motion picture?" He noted that This might not be as much of a problem if people were being building really minimal cameo appearances, but explained that Marvel was not thinking about cameos and easter eggs just for the sake of lover provider, which could detract in the story getting explained to; "As I often get reported by you folks for stating #ItsAllConnected, our feeling would be that the connection isn't just whether somebody is going for walks into a Film or walking from a tv present.
1 note
·
View note
Video
Austin Biometrics and Biostatistics by Austin Publishing Group
Via Flickr: Austin Biometrics and Biostatistics is a peer-reviewed, open access journal published by Austin Publishers. It provides easy access to high quality Manuscripts covering wide aspects of science of biostatistics that encompasses the design of biological experiments in various related fields like medicine, pharmacy, agriculture and fishery where the collection, summarization, and analysis of data, interpretations of data and inference. This journal also focuses upon the combination of biology and statistics, commonly referred as Biometry or Biometrics. Austin Publishing Group is a successful host of more than hundred peer reviewed, open access journals in various fields of science and technology with intent to bridge the gap between academia and research access. Austin Biometrics and Biostatistics accepts original research articles, review articles, case reports, mini reviews, rapid communication, opinions and editorials on all the related aspects of biometrics and biostatistics.
6 notes
·
View notes
Text
Just tell me what I need to know when you find out!
Each state in the U.S. has their own individual laws as to when a company must report a data breach. In addition, there are federal laws and EU laws that likewise dictate when companies need to disclose.
On September 1, 2018, Colorado will enact the toughest law yet, giving companies 30 days to provide notice of a breach involving personal information belonging to Colorado residents. Most states mandate 45 or 60 days.
According to The Wall Street Journal, "Colorado also expanded the definition of personal information to include biometric data, driver’s license numbers, passwords and other items. In other state laws, personal information is often limited to a first name or initial and last name in combination with an identifier, such as a Social Security number."
Just this week, Air Canada discovered a breach and responded within days of discovering it. You can see their response below to the people who they believe were affected. It timely and clearly explains:
What happened;
The steps the company took to limit the breach; and,
What they need their customers do to further protect themselves.
Your system will be breached. It is not a matter of IF, it will be a matter of WHEN. To prepare your company needs to create the protocols to MONITOR your systems and develop the PLANS to respond. This includes creating the TEAM and creating SIMULATED responses.
In 2017, a data breach compromised the personal information of 147.9 million Equifax customers. The company was not prepared for the breach and failed in their response, leaving peoples personal data exposed.
if the law in your state or for your industry is unclear, company's in the U.S. should use the European Union’s General Data Protection Regulation (GDPR), which went into effect in May, as guidance which requires companies to disclose a breach within 72 hours of discovering it. Companies, both large and small, should now put the plans in place and prepare for the next attack.
AIR CANADA EMAIL RE. DATA BREACH 28 AUGUST 2018 We recently detected unusual log‑in behaviour with Air Canada’s mobile App between Aug. 22‑24, 2018. We immediately took action to block these attempts and implemented additional protocols to protect against further unauthorized attempts. As an additional security precaution, we have locked all Air Canada mobile App accounts to protect our customers’ data. Am I affected? As a result of our analysis, we are confident your account was not affected by these unauthorized attempts. As an additional security precaution however, we have locked all Air Canada mobile App accounts to further protect customer data. To reactivate your Air Canada mobile App account, please see the instructions below or follow the prompts the next time you log into your Air Canada mobile App. Your privacy and the protection of your data are extremely important to Air Canada. Our security is multi‑layered, and we work with leading industry experts to continuously improve our practices as technology and security procedures evolve. Reset your password Please reset your password to resume using Air Canada’s mobile App and mobile products with confidence. Your new password must be a minimum of 10 characters. Here are some helpful tips in creating your new password: • Minimum of 10 characters which must contain at least 1 uppercase letter, 1 number, 1 symbol/special character, 1 lowercase letter • Do not use your old password • Do not use your name or something easily associated with you • Do not use your Air Canada mobile App password with other accounts You can reset your password by following the prompts when you next log‑in to your Air Canada mobile App, or you may reset your password now or you may also go to https://services.aircanada.com/portal-web/mobile/profile?action=resetpwd&locale=en For more information We regret any inconvenience this has caused. If you have questions, please refer to additional information posted on aircanada.com Sincerely,
Catherine Dyer Senior Vice President, Chief Information Officer Air Canada
2 notes
·
View notes
Text
Given the amount of surveillance, can social activism prevail in China?

These days, surveillance is widely accepted as a societal phenomenon that governments, businesses, and communities use for diverse purposes. It provides instruments for protection and detection; thus, it plays an indispensable role in cybersecurity but is also a source of privacy and freedom concerns. Surveillance can be said to ingrain into people's daily lives, as it made use of numerous technologies around us physically or virtually to monitor and record daily activities. Moreover, it is divisive because it affects a wide range of concepts such as privacy and freedom for individuals, the conduct of economic and social activity in communities, and the state's legal, political, and military underpinnings (Wang & Tucker 2017, p. 145).
Surveillance in China

From now, China already boasts the most fabulous surveillance network globally, with over half of all surveillance cameras in use. According to research by ChinaFile, a publication of the Asia Society's Center on US-China Relations, government procurement orders for surveillance technologies such as facial recognition cameras and maintenance services surged about 1,900% between 2010 and 2019 (McGregor 2020).
Besides that, in 2018, China's ruling Communist Party's official mouthpiece, People's Daily, stated on English-language Twitter that the country's facial recognition system could scan the faces of the country's 1.4 billion residents in less than a second (Davies 2021).
In Tibet and Xinjiang, ubiquitous checkpoints and surveillance cameras equipped with the most up-to-date iris scanners and facial recognition technologies obstruct the indigenous population's ability to go about their daily lives. People in Xinjiang are also reportedly compelled to download a spyware program to track their online activities and have a QR code carrying their personal information etched on any blades they purchase (Velghe 2019).
As the IoT technology grows exponentially, the relevant authorities have the power to analyze more significant amounts of data by using the updated surveillance and feedback mechanism to act preemptively on incidents and social unrest (Velghe 2019). Back in 2021, the government was able to follow the precise movements of 17 million people in Beijing using the signal from their phones. In addition, complex closed-circuit television (CCTV) networks with millions of panoramic cameras cover much of the public space in cities. The government even asserts that they could monitor 100% of public streets in Beijing due to at least 30 million cameras and 4,000 police officers (Velghe 2019).
youtube
Video taken from Wall Street Journal (2017)
Thus, would social activism still be able to prevail in China?

In my perspective, social activism is primarily impossible for people in China to conduct nor prevail. It is an implausible claim; however, China's surveillance status has been increasing continuously. In 2018, the government continued to collect biometrics such as DNA and voice samples on a large scale. They have utilized them for automated surveillance, developed a nationwide reward and punishment system known as the "social credit system," and developed and implemented "big data" policing programs to prevent protest. For instance, several Chinese women came out in 2018, inspired by the global #MeToo movement, to expose those they said had sexually assaulted them. However, soon the subsequent public uproar was tempered by government censorship, as the dissent and expression had to be restricted globally (Human Rights Watch 2019).

These technologies mentioned above are being implemented without appropriate privacy safeguards, either in law or in practice. Furthermore, most people are unaware that their data is being collected, processed, or kept (Human Rights Watch 2019).
Since President Xi Jinping took office in 2012, China has tightened its existing constrained cyberspace rules dramatically. It refers to the ruling allowing jail time for spreading “rumors” on the Internet, a cybersecurity law that promotes state control and data access, combats unauthorized VPN connections and emphasizes the concept of “Internet sovereignty” (Qiang 2019, p. 53).
Based on the study conducted by Qin, Stromberg & Wu (2018), it has been highlighted that Beijing's political leaders can successfully monitor corrupt officials and foresee uprisings in distant places via social media. As a result, the use of social media for monitoring and propaganda is expected to strengthen government power and stability.
In conclusion
From the government's perspective, social media is beneficial for monitoring protests, local politicians and disseminating propaganda. Strict control will reduce the value of social media for surveillance and propaganda reasons (Qin, Stromberg & Wu 2018). With the help of China's social credit system, it allows the state to assess an individual's perceived "danger" to it in real-time by monitoring their social connections, usage of social media, and physical activity. They help shape and "score" the citizens' economic and social conduct (Clarkesep 2018). Hence, the citizens do not have the freedom to conduct any social activism about anything, as they would get detained and penalized once trying to spread any sensitive content.
Not only that, digitally-powered totalitarianism has emerged to the reality, as it can be seen obviously in Xinjiang, the westernmost province of China (Clarkesep 2018). Around 25 million Xinjiang people, Uighur Muslims, were forced to provide the state with detailed biometric data, such as fingerprints, voice recordings, facial scans, DNA, and blood type, as the surveillance and censorship mechanisms (Palfrey 2020).

Reference List
Clarkesep, M 2018, 'How China Is Gaining Political Influence Through Social Management', Grist, 10 September, viewed 20 November 2021, <https://psmag.com/social-justice/china-is-using-social-management-to-watch-us>.
Davies, D 2021, 'Facial Recognition And Beyond: Journalist Ventures Inside China's 'Surveillance State", Fresh Air, 5 January, viewed 20 November 2021, <https://www.npr.org/2021/01/05/953515627/facial-recognition-and-beyond-journalist-ventures-inside-chinas-surveillance-sta>.
Human Rights Watch 2019, World Report 2019: Rights Trends in China, viewed 20 November 2021, <https://www.hrw.org/world-report/2019/country-chapters/china-and-tibet#>.
McGregor, G 2020, 'The world's largest surveillance system is growing—and so is the backlash', Fortune, 3 November, viewed 20 November 2021, <https://fortune.com/2020/11/03/china-surveillance-system-backlash-worlds-largest/>.
Palfrey, J 2020, 'The Ever-Increasing Surveillance State', Walsh School of Foreign Service, 2 March, viewed 20 November 2021, <https://gjia.georgetown.edu/2020/03/02/the-ever-increasing-surveillance-state/>.
Qiang, X 2019, 'The Road to Digital Unfreedom: President Xi's Surveillance State', Journal of Democracy, vol. 30, no. 1, pp. 53-67, viewed 20 November 2021, <https://www.journalofdemocracy.org/articles/the-road-to-digital-unfreedom-president-xis-surveillance-state/>.
Qin, B, Stromberg, D & Wu, Y 2018, 'E-autocracy: Surveillance and propaganda in Chinese social media', VOX, CEPR Policy Portal, 25 May, viewed 20 November 2021, <https://voxeu.org/article/e-autocracy-surveillance-and-propaganda-chinese-social-media>.
Velghe, P 2019, 'The Internet of Things, Surveillance, and Social Management in the PRC', OpenEdition Journals, pp. 85-89, viewed 20 November 2021, <https://doi.org/10.4000/chinaperspectives.8874>.
Wall Street Journal 2017, Life Inside China's Total Surveillance State, 21 December, viewed 20 November 2021, <https://www.youtube.com/watch?v=OQ5LnY21Hgc&ab_channel=WallStreetJournal>.
#MDA20009#Digital Communities#Week11#China#social activism#surveillance#yeah <3#mission accomplished
0 notes
Photo

Are Dogs' Nose Prints Really Unique and Unchanging?
Are dogs' nose prints distinctive enough to be used for identification?
September 22, 2021
Jessica Schrader
Up to now, there has been little proof to show that a dog's nose prints are distinctive enough to allow the identification of individual dogs.
Evidence that the canine nose print is unique to specific dogs is actually an extrapolation of data collected on cattle.
A new study shows that a dog's nose print is well-established by 2 months of age and is unchanging over the first year of life.
I was somewhat surprised when I read a recent article by a team of Korean investigators, headed by Hyeong In Choi of Seoul National University, in the scientific journal Animals. My surprise came from the fact that the authors stated that, "The objective of this paper is to focus on the canine nose pattern (nose print) by studying if it can be used similarly to the human fingerprint as a unique biometric marker for each individual dog."
As a scientist and dog owner residing in Canada, I knew that the Canadian Kennel Club has been accepting dog nose prints as proof of identity since 1938. A few places in the United States have also adopted dog nose printing as a common way of identifying lost dogs as well. The stated belief is that nose printing is a more reliable way of matching identity, since a dog tag on a collar can be lost, and microchips can malfunction or become dislodged, making them useless for determining the dog's identity. The argument is that the nose print serves as a unique biometric marker for individual dogs.
Fingerprints Versus Nose Prints
The most familiar biometric marker of identity for most people is fingerprints. The uniqueness of fingerprints and their usefulness for identifying people was first established by Francis Galton, an eminent 19th-century scientist whose life and careerspanned the reign of Queen Victoria. He made significant contributions to the study of psychology and statistics, but also did important work in establishing the forensic usefulness of fingerprints, and establishing the first system for classifying them. Galton claimed that fingerprints were unique and that no two individuals have the same fingerprint patterns. (Recently it has been determined that the actual probability of finding two identical fingerprints is one in 64 billion, even including twins. Given the fact that the population of the entire world amounts to under 8 billion, that makes it highly unlikely that any two people alive today will have the same fingerprint.)
Of course dogs don't have fingerprints. However, the substitute biometric marker for fingerprints in dogs is their nose print. It has been supposed that just as the pattern of every person's fingerprints is unique, each dog's rhinarium (the section of bare skin at the tip of a dog's nose) has a distinguishing design of dimples, dots, and ridges that, when combined with the shape of his nostril openings, is believed to make a mark that is distinctive enough to conclusively identify one dog among all others.
Is There Any Scientific Proof?
So what is the evidence for this assertion that every dog's nose print is unique? This turned out to be one of those puzzling situations. I did a fairly extensive literature search to try to find out what the evidence was for the uniqueness of canine nose prints. I found several veterinary texts which asserted that canine nose prints were unique enough to be able to be used for identification, but none of them provided any references to actual scientific data on dogs. In fact, most of them referred to articles using nose prints to identify cattle. There is a lot of literature on the bovine nose print suggesting uniqueness and invariance, but the only report I could find on dogs was a three-paragraph short note in the journal Veterinary Quarterly in 1994, which stated that in the course of developing a computer program to recognize canine nose prints an unspecified number of Doberman pinschers were tested and their nose prints were found to be unique. On the basis of that literature search, I can only conclude that the assertions about dog nose prints are extrapolations based on the data collected mainly on cattle. Given that fact, it then made sense why the Korean team collected their new data.
The New Data
This contemporary study used a very small number of dogs, namely two litters of beagles for a total of 10 dogs. The researchers were asking two questions: if the canine nose pattern is properly formed by two months of age and if this nose pattern remains unchanged throughout the first year of the dog's life. Obviously, given such a small sample, the assumption of the uniqueness of an individual's nose pattern could not be definitively tested, however by using dogs in the same litter the chance for similar patterns might be increased.
The findings were quite clear. By 2 months of age, the nose print pattern was established, and monthly testing over the first year of their life showed no changes in the pattern. Furthermore, the investigators were able to show that a computer program could be used to identify nose prints. This result suggests that if a database could be established for dogs' nose prints, then the canine equivalent of the Automated Fingerprint Identification System (AFIS) used by police forces to identify potential criminal suspects by their fingerprints, might be useful to locate and identify lost dogs.
A Unique Canine Keepsake
Even in the absence of such a database, it is a fun project to collect your dog's nose print, perhaps to frame it as a unique keepsake of your pet. The process is really quite simple and only requires a roll of paper towels, some food coloring, and a pad of paper. First blot your dog's nose with a paper towel to dry it out a bit. Then dip a piece of paper toweling into some food coloring and dab it onto your dog's nose. Gently press the pad of paper to your dog's nose, curving it around or rolling it in a smooth motion from one side to the other to ensure that you get the impression of the entire nose. You'll probably require a few attempts before you get a clear picture of what you want (especially if you have a squirmy dog). Once you get your clear print, immediately clean your dog's nose. You now have a frameable memento that may well be completely unique to your pet.
0 notes
Video
youtube

buy research papers
About me
113 Great Research Paper Topics
113 Great Research Paper Topics That is the simplest approach to forestall cross-contamination, whether or not you employ an air dryer or a paper towel to dry your hands, she added. Get a month's limitless entry to THE content on-line. Just register and complete your profession abstract. Where attainable we will impute lacking values, however where that's not attainable we have excluded schools. In addition, some faculties did not meet our threshold for a legitimate variety of respondents to the scholar survey in 2019. We have additionally excluded personal for-profit colleges. We additionally accept US service academies supplied that they are able to provide the necessary information. There are two explanation why a college might not be included in the ranking. Reputation – the whole votes acquired for educating excellence in theTHEAcademic Reputation survey, which is performed in partnership with Elsevier. We use only votes provided by teachers associated with US institutions. You probably already know that you could’t simply copy and paste it into your project, or type it in, with out additionally providing credit to the original writer. Looking for a full visible of a web page of references? Scroll down and take a peek at our APA format essay instance in the direction of the bottom of this page. You’ll see a list of references and you'll acquire a way of how they appear. First and foremost, use abbreviations sparingly. However, simply figuring out a webpage is perceived as lower high quality doesn’t give perception as to what aspects of a web page are disliked by a consumer. Additionally, it’s attainable that the person is misremembering elements of the webpage or being dishonest of their assessment. Using each can probably determine patterns amongst the biometric measures and the questionnaire, which might strengthen the validity of the outcomes. The information from the coed survey have been rebalanced by gender to mirror the actual gender ratio on the college. We additionally look extra typically at pupil range – both racial and ethnic diversity (three%), and the inclusion of students with lower household earnings (2%). For the previous, we use IPEDS data on range. For the latter, we have a look at the proportion of scholars who obtain Pell Grants , as reported in IPEDS. We used the total instructing votes from our 2017 and 2018 status surveys. We will be reviewing our methodology for subsequent 12 months to discover a suitable substitute for this measure for future rankings. TheWall Street Journal/Times Higher EducationCollege Ranking is a pioneering ranking of US faculties and universities that places pupil success and studying at its heart. Data driven insights help determine whether students are doing their own work, enabling you to uphold your institution’s commitment to educational excellence. More so, the attention monitoring knowledge has the potential to determine patterns amongst websites of lower or greater high quality. Moreso, analysis on the connection between visual design and perceived usability (Stojmenovic, Pilgrim, & Lindgaard, 2014) has revealed a optimistic correlation between the 2. As users’ rankings of visible quality increase, their ratings of perceived usability follows a similar development. Although this analysis spans numerous domains, the reliance on self-report measures to gauge ideas like visible design and net high quality is prevalent throughout a lot of the literature. Every quote or piece of out of doors data included in the paper should be referenced and have an entry. Did you find the right quote or piece of data to include in your project? It’s always a nice feeling after we find that magical piece of knowledge or data to include in our writing. We cite based on the 8th version of MLA, sixth version of APA, and sixteenth edition of Chicago . If an analogous paper exists elsewhere, notify the editor in the cover letter. A assertion to the editor that the paper is original. Check section 17, which is APA writing format for numbers. The impact of web site quality dimensions on buyer satisfaction in the B2C e-commerce context. Comparing the effects of web site high quality on customer preliminary purchase and continued buy at e-commerce web sites. We know from earlier research that the standard of websites mediates many aspects of e-commerce, and provides insight as to how shoppers view the webpages generally. This metric takes into consideration spending on both undergraduate and graduate programmes, which is consistent with the way in which that the relevant spend knowledge is available in IPEDS. The Department of Education requires colleges to report key statistics such as this to IPEDS, making it a comprehensive source for education information. Students and their households must know that their college has the best resources to provide the amenities, tuition and help which are needed to succeed at college. These longitudinal data were what we used in our value-added model, and we're not able to substitute it with the brand new values revealed. This 12 months we are reusing last year’s scores from the worth-added metric.
0 notes
Photo

Don’t panic, no one is going to jail… yet…
It’s here, the Protection of Personal Information Act (POPI Act or POPIA) commenced on 1 July 2020. It was originally due to take effect from 1 April 2020 (an amusing date, but I digress), however, thanks to the appearance of an invisible enemy, namely CV-19, the roll-out was delayed. (So maybe it was an appropriate date, a case of ‘Just kidding!’?)
Now that the Act is in place, parties will be given a one-year transition period to comply. That sounds like a lot of time, but the roll-out of a comprehensive POPIA compliance plan can take between six months and two years to complete.
So, what is it, I hear you ask querulously?
https://bit.ly/3fX3b7p
Well, for those of you who have just come out of hibernation, POPIA refers to South Africa’s Protection of Personal Information Act, whose aim is the control and Processing of Personal Information.
When we talk Personal Information, that broadly means any information relating to an identifiable, living natural person or juristic person; a body recognised by the law as being entitled to rights and duties in the same way as a natural or human person, the common example being a company, CCs etc. and includes, but is not limited to information around contact details: email, telephone, physical address, location; demographic information: age, sex, race, birth date, ethnicity, sexual orientation; the employment, financial, educational, criminal and medical history of the person/entity, including blood type and other biometric information.
Also, of interest, included in the POPI Act is the capture of personal opinions, views or preferences and opinions of and about the person (yeah, that Twitter comment and or rant on FaceBook…), as well as private correspondence etc.
However, POPIA, unlike the GDPR, (that’s General Data Protection Regulation) does not apply extraterritorially, that is, it only pertains to organisations in South Africa. In essence, if you reside in South Africa or you process personal information within the country, then you need to comply with POPIA. (Although, if you are GDPR compliant, chances are you’re already pretty much POPIA-compliant). In addition, the processing of some personal information is excluded. For example, if you are processing purely for personal reason, then POPIA won’t apply to you.
Some instances where POPIA does not apply, include:
purely household or personal activity
some state functions including criminal prosecutions, national security etc.
journalism under a code of ethics
judiciary functions
https://bit.ly/3fX3b7p
While both GDPR and POPIA enforce the law for managing and storing personal information (as well the guidelines for alerting third parties if there are safety violations) there are variances, as the safety regulations differ a little.
GDPR: “The controller and the processor shall implement appropriate technical and organisational measures to ensure a level of security and appropriate to risks represented by the processing and the nature of the personal data to be protected.”
POPIA: “A responsible party must secure the integrity and confidentiality of personal information in its possession or under its control by taking appropriate, reasonable technical and organisational measures.”
Also, penalties differ. Under the GDPR, a fine of up to four percent of annual global turnover or €20-million, whichever is greater, can be leveraged. Try paying that as a South African company!
With the POPIA Act, being non-compliant, the responsible party could run the risk of a penalty of a fine and/or imprisonment of up to 12 months, or under certain conditions, imprisonment of up to 10 years.
While this really has the overtones of George Orwell’s ‘1984’, there is an upside: The Act is also aimed at providing rights to people when it comes to unwanted electronic communications. That’s gotta be good, right? The POPIA legislation essentially deems your personal information to be “precious goods” and therefore aims to grant you, as the owner of your personal information, certain rights of protection and the ability to exercise control over information that is gathered.
You see, included in the Act, are guidelines about direct marketing. This means that you can’t just send any unsolicited messages willy-nilly, or emails to consumers without them opting in.
Marketing is one of the business departments that will be most affected by POPIA, meaning you have to be fully clued up on what POPIA entails and how it’ll affect your day-to-day job.
Think ‘consent’ and you basically have POPIA compliance. People must opt-in to receiving your communication, and you’re only permitted to send them the kind of data they have opted-in to receiving. For example, you cannot send a monthly newsletter to a user who only wants to obtain information linked to their individual investment portfolio. By the same token, users need to be able to opt-out easily from any further communication.
https://bit.ly/3fX3b7p
In addition, when asking people for their personal information you must reveal why you need this information, how it will be used and whether it will be passed on to third parties.
While some limitations on direct marketing are imposed by POPIA, (emails, cold calling and SMSes) there are various other ways in which you can market your products to prospects without concerns related to violating the Act.
For example, social media marketing. As explained by Deloitte, if an individual interacted with you, or is following your company on social media, they already anticipate hearing from you, so any related communication within this format or platform, is not considered unsolicited.
It is important to note that the POPI Act is not only applicable on forms that are filled in manually, but also any cookies on websites used for analytics, advertising and any chat boxes or pop-ups. All compliant websites have a clear user opt-in, acknowledging that they have given consent to the website (the business presented in the website) to collect, process and store their gathered information.
The Act will also affect the way you notify stakeholders; if a security or privacy breach has occurred, and personal information is compromised, you will have to notify third parties as soon as possible.
While the possibilities to implement POPIA are many, it’s important to take the right one for your organisation over this 12-month period.
So, what to do, to prevent that awful sound of a prison cell door thudding shut behind you? (Only kidding, they close like any other door.)
Seems there are benefits to complying with the Act. According to POPIA.biz, consumer studies show that in 90% of cases, people feel safer about doing business with companies that are transparent about how they use your info, increasing customer confidence in the organisation. Wouldn’t you be happier if you knew how it was being stored, and why? Companies who take these measures are likely to have a more reliable database, which in itself, has numerous upsides.
https://bit.ly/3fX3b7p
With POPIA compliance, it’s not a case of ‘one size fits all’, as every organisation needs to implement different measures. For example, an SME’s requirements are very different to that of a medium or large-sized organisation.
Every organisation or company, no matter what size has some person who holds the role of Information Officer by default. (Some call them ‘Know all’, other times they have a clearly defined role and official title.) This is the person responsible for ensuring that your organisation complies with POPIA.
So, that person who always jumps on the bandwagon ensuring you follow policies etc, may be the ideal Information Officer. If that’s you, then you need to ask if you are happy with that responsibility, do you want to continue to be the Information Officer? If you’re not, then the question is: Who should be?
Ultimately, compliance accountability rests with a responsible party, which could be a public or private concern or any other person who, individually, or in combination with others, defines the objective of, and method for processing personal information within the company. As a rule, the elected party or person/s must be resident in South Africa or, the processing should occur within South Africa (subject to certain exclusions).
Also, further actioning is dependent on the foundations already laid to protect personal information, and, while some companies may have many procedures in place, others may be entirely new to this exercise.
Managing information is the crux of the process. You’ll have to categorise any consumer data that you hold and identify and determine whether it can be construed as ‘personal information’. So too, any ‘records’ and ‘sensitive’ information you might have, you’ll have to identify, as different criteria exist for handling personal information and non-personal information.
Broadly, processing info includes anything that can be done with the Personal Information, including collection, usage, storage, dissemination, modification or destruction (whether such processing is automated or not).
The POPI Act involves capturing the minimum required data, certifying accuracy, and removing data that is no longer required. The Act includes the following guidelines: ensure that the info you collect is needed for a specific purpose and apply practical security measures to safeguard it. Also, make sure it’s accurate, relevant and up to date and don’t be overzealous, only hold as much as you need for as long as you need it; no reason to hoard here. If the subject asks, they must be allowed access to the information and to see it upon request.
https://bit.ly/3fX3b7p
In brief, what you need to do:
Appoint an information officer: If the organisation does not already have one, the first step to compliance would be to appoint an information officer, in line with the requirements set out in POPIA.
Clarity of definition: Make sure everyone in the company, from the top down, understands what data privacy legislation entails and what is required of them, to ensure effective compliance.
Conduct self-audits: When staff are informed, conduct self-assessments and audits throughout the organisation, within each business unit. It is important to understand what, how, by whom information is collected. Also, what it is used for, how it is stored and processed and how it is retained and destroyed. Most importantly, whether it was collected with the requisite consent? After this, the company will be better able to identify gaps and produce a clear gap analysis and risk assessment report.
Develop a compliance protocol: An appropriate gap analysis will help pinpoint processes and policies to be put in place, which may include:
updates to employment contracts
updates to supplier agreements
changes to marketing practices (opt-in and opt-out best practice) and more.
Implement: Once implemented, the compliance framework should be monitored and maintained and ensure proper implementation of new policies and procedures through in-depth training, awareness campaigns, annual re-training and compliance audits.
In a nutshell, POPIA is a code of conduct for all businesses. While companies will be affected by the Act, it will impact specifically on those that deal with a large amount of personal information — think banks, insurance companies, medical aids, etc. That’s not to say that if you are a smaller concern that you will be able to dodge the Act, as all companies need to have systems in place to deal with personal information.
When in doubt, find out!
Disclaimer: While listed sources have been referenced, we cannot be held responsible for incorrect information being unwittingly relayed. Please consult the government website www.gov.za for confirmation, or for any queries.
https://bit.ly/3fX3b7p
0 notes