#Biometric Accuracy
Explore tagged Tumblr posts
Text
Mobile fingerprinting services provide a level of convenience that many individuals and businesses need. Instead of having to visit a fingerprinting location, you can have a professional come directly to you. If you need a Livescan fingerprint in Laurel, Maryland, mobile services allow you to complete the fingerprinting process without leaving your home or office. This option is especially useful for busy professionals, parents, or anyone who needs a more flexible solution for fingerprinting.
0 notes
Text
Biometric Time Attendance Solutions
Biometric time attendance solutions offer an advanced method for tracking employee work hours by using unique biological traits such as fingerprints, facial recognition, or iris scans. These systems enhance security by ensuring that only the authenticated individual can clock in, preventing common issues like buddy punching or fraudulent time entries. Biometric systems are highly accurate, minimizing errors in attendance data. They also save time for employees and managers, as the process of clocking in is swift and requires minimal interaction. Additionally, biometric systems help in maintaining compliance with labor regulations and integrate seamlessly with payroll systems, improving overall workforce efficiency.
More info: https://ahalts.com/solutions/hr-services/outsourcing-time-attendance

#biometric time attendance#fingerprint time tracking#facial recognition attendance#iris scan attendance system#biometric employee tracking#time tracking accuracy#secure time attendance
0 notes
Text
Do you need a highly accurate and efficient method for capturing and verifying biometric data? Are you looking for a solution that eliminates errors associated with traditional ink-and-paper methods? A live scan is what you are looking for!
0 notes
Text

ENTERING THE S.H.I.E.L.D. DATABASE . . .
loading . . .
loading . . .
loading . . .
WELCOME TO THE S.H.I.E.L.D PERSONNEL DATABASE. CONTINUE?
﹥﹥ YES.
AGENT: Apollo ▇▇▇ ALIAS: Karma ABILITIES:
UMBRAL CONJURATION — Agent ▇▇▇ possesses the ability to manipulate both existing and created shadows. These shadow apparitions defy physical interference and cannot be affected by blade, bullet, or shield.
METAMORPHIC RECONFIGURATION — Wields the ability to alter minute aspects of corporeal identity—voice, facial structure, eye hue, gait, and in extreme circumstances, even the very composition of his fingertips to avoid biometric detection.
MNEMONIC INVASION — By touching two fingers to each temple, Agent ▇▇▇ may access the memoryscape of others, provided mutual trust exists between both parties. He is able to navigate their memories as if perusing through a gallery. (Ability used for intel confirmation.)
MARTIAL POLYMATH — Master of both armed and unarmed combat. Physical attributed exceed baseline human limitations—stamina, flexibility, reaction time. • Bladed weaponry (knives, daggers, short-range projectiles) • Firearms & precision shooting • Archery • Memorization & replication of any combat style after brief observation
OMNIPOTENCE — Agent ▇▇▇ exhibits flawless instinctual strategy and natural capacity for decision-making under extreme pressure. Should mission parameters shift, he adapts.
VOCAL & BEHAVIORAL MIMICRY — Able to replicate cadences, voices, and physical nuances with unsettling accuracy. (Ability used for infiltration, deception, & manipulation)
SUBLIME INFLUENCE — Agent ▇▇▇ commands attention with presence alone; influence is subtle, often imperceptible. Subjects frequently follow directives before realizing they've received them. (WARNING: Effects may bypass conscious resistance. Prolonged exposure can cause psychological disorientation or unintended compliance in teammates and targets alike.)

image credit & inspired by : @rosebudshifter <3
why is my surname redacted ??? you'll find out very soon (aka whenever i have the time to make an intro </3)
. . . back to the circus 🎪
#© moonyskarma#marvel reality𑁤#jtscircusevent ���#shiftblr#shifting blog#reality shifting#shifting antis dni#reality shifting community#shifting motivation#loassblog#loassumption#loa tumblr#loablr#loa blog#master manifestor#law of assumption#shifting community#shifting journey#shifting consciousness#reality shifter#shifters#anti shifters dni#shifting realities#shifting reality#loa success
80 notes
·
View notes
Text
Scan the online brochures of companies who sell workplace monitoring tech and you’d think the average American worker was a renegade poised to take their employer down at the next opportunity. “Nearly half of US employees admit to time theft!” “Biometric readers for enhanced accuracy!” “Offer staff benefits in a controlled way with Vending Machine Access!”
A new wave of return-to-office mandates has arrived since the New Year, including at JP Morgan Chase, leading advertising agency WPP, and Amazon—not to mention President Trump’s late January directive to the heads of federal agencies to “terminate remote work arrangements and require employees to return to work in-person … on a full-time basis.” Five years on from the pandemic, when the world showed how effectively many roles could be performed remotely or flexibly, what’s caused the sudden change of heart?
“There’s two things happening,” says global industry analyst Josh Bersin, who is based in California. “The economy is actually slowing down, so companies are hiring less. So there is a trend toward productivity in general, and then AI has forced virtually every company to reallocate resources toward AI projects.
“The expectation amongst CEOs is that’s going to eliminate a lot of jobs. A lot of these back-to-work mandates are due to frustration that both of those initiatives are hard to measure or hard to do when we don’t know what people are doing at home.”
The question is, what exactly are we returning to?
Take any consumer tech buzzword of the 21st century and chances are it’s already being widely used across the US to monitor time, attendance and, in some cases, the productivity of workers, in sectors such as manufacturing, retail, and fast food chains: RFID badges, GPS time clock apps, NFC apps, QR code clocking-in, Apple Watch badges, and palm, face, eye, voice, and finger scanners. Biometric scanners have long been sold to companies as a way to avoid hourly workers “buddy punching” for each other at the start and end of shifts—so-called “time theft.” A return-to-office mandate and its enforcement opens the door for similar scenarios for salaried staff.
Track and Trace
The latest, deluxe end point of these time and attendance tchotchkes and apps is something like Austin-headquartered HID’s OmniKey platform. Designed for factories, hospitals, universities and offices, this is essentially an all-encompassing RFID log-in and security system for employees, via smart cards, smartphone wallets, and wearables. These will not only monitor turnstile entrances, exits, and floor access by way of elevators but also parking, the use of meeting rooms, the cafeteria, printers, lockers, and yes, vending machine access.
These technologies, and more sophisticated worker location- and behavior-tracking systems, are expanding from blue-collar jobs to pink-collar industries and even white-collar office settings. Depending on the survey, approximately 70 to 80 percent of large US employers now use some form of employee monitoring, and the likes of PwC have explicitly told workers that managers will be tracking their location to enforce a three-day office week policy.
“Several of these earlier technologies, like RFID sensors and low-tech barcode scanners, have been used in manufacturing, in warehouses, or in other settings for some time,” says Wolfie Christl, a researcher of workplace surveillance for Cracked Labs, a nonprofit based in Vienna, Austria. “We’re moving toward the use of all kinds of sensor data, and this kind of technology is certainly now moving into the offices. However, I think for many of these, it’s questionable whether they really make sense there.”
What’s new, at least to the recent pandemic age of hybrid working, is the extent to which workers can now be tracked inside office buildings. Cracked Labs published a frankly terrifying 25-page case study report in November 2024 showing how systems of wireless networking, motion sensors, and Bluetooth beacons, whether intentionally or as a byproduct of their capabilities, can provide “behavioral monitoring and profiling” in office settings.
The project breaks the tech down into two categories: The first is technology that tracks desk presence and room occupancy, and the second monitors the indoor location, movement, and behavior of the people working inside the building.
To start with desk and room occupancy, Spacewell offers a mix of motion sensors installed under desks, in ceilings, and at doorways in “office spaces” and heat sensors and low-resolution visual sensors to show which desks and rooms are being used. Both real-time and trend data are available to managers via its “live data floorplan,” and the sensors also capture temperature, environmental, light intensity, and humidity data.
The Swiss-headquartered Locatee, meanwhile, uses existing badge and device data via Wi-Fi and LAN to continuously monitor clocking in and clocking out, time spent by workers at desks and on specific floors, and the number of hours and days spent by employees at the office per week. While the software displays aggregate rather than individual personal employee data to company executives, the Cracked Labs report points out that Locatee offers a segmented team analytics report which “reveals data on small groups.”
As more companies return to the office, the interest in this idea of “optimized” working spaces is growing fast. According to S&S Insider’s early 2025 analysis, the connected office was worth $43 billion in 2023 and will grow to $122.5 billion by 2032. Alongside this, IndustryARC predicts there will be a $4.5 billion employee-monitoring-technology market, mostly in North America, by 2026—the only issue being that the crossover between the two is blurry at best.
At the end of January, Logitech showed off its millimeter-wave radar Spot sensors, which are designed to allow employers to monitor whether rooms are being used and which rooms in the building are used the most. A Logitech rep told The Verge that the peel-and-stick devices, which also monitor VOCs, temperature, and humidity, could theoretically estimate the general placement of people in a meeting room.
As Christl explains, because of the functionality that these types of sensor-based systems offer, there is the very real possibility of a creep from legitimate applications, such as managing energy use, worker health and safety, and ensuring sufficient office resources into more intrusive purposes.
“For me, the main issue is that if companies use highly sensitive data like tracking the location of employees’ devices and smartphones indoors or even use motion detectors indoors,” he says, “then there must be totally reliable safeguards that this data is not being used for any other purposes.”
Big Brother Is Watching
This warning becomes even more pressing where workers’ indoor location, movement, and behavior are concerned. Cisco’s Spaces cloud platform has digitized 11 billion square feet of enterprise locations, producing 24.7 trillion location data points. The Spaces system is used by more than 8,800 businesses worldwide and is deployed by the likes of InterContinental Hotels Group, WeWork, the NHS Foundation, and San Jose State University, according to Cisco’s website.
While it has applications for retailers, restaurants, hotels, and event venues, many of its features are designed to function in office environments, including meeting room management and occupancy monitoring. Spaces is designed as a comprehensive, all-seeing eye into how employees (and customers and visitors, depending on the setting) and their connected devices, equipment, or “assets” move through physical spaces.
Cisco has achieved this by using its existing wireless infrastructure and combining data from Wi-Fi access points with Bluetooth tracking. Spaces offers employers both real-time views and historical data dashboards. The use cases? Everything from meeting-room scheduling and optimizing cleaning schedules to more invasive dashboards on employees’ entry and exit times, the duration of staff workdays, visit durations by floor, and other “behavior metrics.” This includes those related to performance, a feature pitched at manufacturing sites.
Some of these analytics use aggregate data, but Cracked Labs details how Spaces goes beyond this into personal data, with device usernames and identifiers that make it possible to single out individuals. While the ability to protect privacy by using MAC randomization is there, Cisco emphasizes that this makes indoor movement analytics “unreliable” and other applications impossible—leaving companies to make that decision themselves.
Management even has the ability to send employees nudge-style alerts based on their location in the building. An IBM application, based on Cisco’s underlying technology, offers to spot anomalies in occupancy patterns and send notifications to workers or their managers based on what it finds. Cisco’s Spaces can also incorporate video footage from Cisco security cameras and WebEx video conferencing hardware into the overall system of indoor movement monitoring; another example of function creep from security to employee tracking in the workplace.
“Cisco is simply everywhere. As soon as employers start to repurpose data that is being collected from networking or IT infrastructure, this quickly becomes very dangerous, from my perspective.” says Christl. “With this kind of indoor location tracking technology based on its Wi-Fi networks, I think that a vendor as major as Cisco has a responsibility to ensure it doesn’t suggest or market solutions that are really irresponsible to employers.
“I would consider any productivity and performance tracking very problematic when based on this kind of intrusive behavioral data.” WIRED approached Cisco for comment but didn’t receive a response before publication.
Cisco isn't alone in this, though. Similar to Spaces, Juniper’s Mist offers an indoor tracking system that uses both Wi-Fi networks and Bluetooth beacons to locate people, connected devices, and Bluetooth tagged badges on a real-time map, with the option of up to 13 months of historical data on worker behavior.
Juniper’s offering, for workplaces including offices, hospitals, manufacturing sites, and retailers, is so precise that it is able to provide records of employees’ device names, together with the exact enter and exit times and duration of visits between “zones” in offices—including one labeled “break area/kitchen” in a demo. Yikes.
For each of these systems, a range of different applications is functionally possible, and some which raise labor-law concerns. “A worst-case scenario would be that management wants to fire someone and then starts looking into historical records trying to find some misconduct,” says Christl. "If it’s necessary to investigate employees, then there should be a procedure where, for example, a worker representative is looking into the fine-grained behavioral data together with management. This would be another safeguard to prevent misuse.”
Above and Beyond?
If warehouse-style tracking has the potential for management overkill in office settings, it makes even less sense in service and health care jobs, and American unions are now pushing for more access to data and quotas used in disciplinary action. Elizabeth Anderson, professor of public philosophy at the University of Michigan and the author of Private Government: How Employers Rule Our Lives, describes how black-box algorithm-driven management and monitoring affects not just the day-to-day of nursing staff but also their sense of work and value.
“Surveillance and this idea of time theft, it’s all connected to this idea of wasting time,” she explains. “Essentially all relational work is considered inefficient. In a memory care unit, for example, the system will say how long to give a patient breakfast, how many minutes to get them dressed, and so forth.
“Maybe an Alzheimer’s patient is frightened, so a nurse has to spend some time calming them down, or perhaps they have lost some ability overnight. That’s not one of the discrete physical tasks that can be measured. Most of the job is helping that person cope with declining faculties; it takes time for that, for people to read your emotions and respond appropriately. What you get is massive moral injury with this notion of efficiency.”
This kind of monitoring extends to service workers, including servers in restaurants and cleaning staff, according to a 2023 Cracked Labs’ report into retail and hospitality. Software developed by Oracle is used to, among other applications, rate and rank servers based on speed, sales, timekeeping around breaks, and how many tips they receive. Similar Oracle software that monitors mobile workers such as housekeepers and cleaners in hotels uses a timer for app-based micromanagement—for instance, “you have two minutes for this room, and there are four tasks.”
As Christl explains, this simply doesn’t work in practice. “People have to struggle to combine what they really do with this kind of rigid, digital system. And it’s not easy to standardize work like talking to patients and other kinds of affective work, like how friendly you are as a waiter. This is a major problem. These systems cannot represent the work that is being done accurately.”
But can knowledge work done in offices ever be effectively measured and assessed either? In an episode of his podcast in January, host Ezra Klein battled his own feelings about having many of his best creative ideas at a café down the street from where he lives rather than in The New York Times’ Manhattan offices. Anderson agrees that creativity often has to find its own path.
“Say there’s a webcam tracking your eyes to make sure you’re looking at the screen,” she says. “We know that daydreaming a little can actually help people come up with creative ideas. Just letting your mind wander is incredibly useful for productivity overall, but that requires some time looking around or out the window. The software connected to your camera is saying you’re off-duty—that you’re wasting time. Nobody’s mind can keep concentrated for the whole work day, but you don’t even want that from a productivity point of view.”
Even for roles where it might make more methodological sense to track discrete physical tasks, there can be negative consequences of nonstop monitoring. Anderson points to a scene in Erik Gandini’s 2023 documentary After Work that shows an Amazon delivery driver who is monitored, via camera, for their driving, delivery quotas, and even getting dinged for using Spotify in the van.
“It’s very tightly regulated and super, super intrusive, and it’s all based on distrust as the starting point,” she says. “What these tech bros don’t understand is that if you install surveillance technology, which is all about distrusting the workers, there is a deep feature of human psychology that is reciprocity. If you don’t trust me, I’m not going to trust you. You think an employee who doesn’t trust the boss is going to be working with the same enthusiasm? I don’t think so.”
Trust Issues
The fixes, then, might be in the leadership itself, not more data dashboards. “Our research shows that excessive monitoring in the workplace can damage trust, have a negative impact on morale, and cause stress and anxiety,” says Hayfa Mohdzaini, senior policy and practice adviser for technology at the CIPD, the UK’s professional body for HR, learning, and development. “Employers might achieve better productivity by investing in line manager training and ensuring employees feel supported with reasonable expectations around office attendance and manageable workloads.”
A 2023 Pew Research study found that 56 percent of US workers were opposed to the use of AI to keep track of when employees were at their desks, and 61 percent were against tracking employees’ movements while they work.
This dropped to just 51 percent of workers who were opposed to recording work done on company computers, through the use of a kind of corporate “spyware” often accepted by staff in the private sector. As Josh Bersin puts it, “Yes, the company can read your emails” with platforms such as Teramind, even including “sentiment analysis” of employee messages.
Snooping on files, emails, and digital chats takes on new significance when it comes to government workers, though. New reporting from WIRED, based on conversations with employees at 13 federal agencies, reveals the extent to Elon Musk’s DOGE team’s surveillance: software including Google’s Gemini AI chatbot, a Dynatrace extension, and security tool Splunk have been added to government computers in recent weeks, and some people have felt they can’t speak freely on recorded and transcribed Microsoft Teams calls. Various agencies already use Everfox software and Dtex’s Intercept system, which generates individual risk scores for workers based on websites and files accessed.
Alongside mass layoffs and furloughs over the past four weeks, the so-called Department of Government Efficiency has also, according to CBS News and NPR reports, gone into multiple agencies in February with the theater and bombast of full X-ray security screenings replacing entry badges at Washington, DC, headquarters. That’s alongside managers telling staff that their logging in and out of devices, swiping in and out of workspaces, and all of their digital work chats will be “closely monitored” going forward.
“Maybe they’re trying to make a big deal out of it to scare people right now,” says Bersin. “The federal government is using back-to-work as an excuse to lay off a bunch of people.”
DOGE staff have reportedly even added keylogger software to government computers to track everything employees type, with staff concerned that anyone using keywords related to progressive thinking or "disloyalty” to Trump could be targeted—not to mention the security risks it introduces for those working on sensitive projects. As one worker told NPR, it feels “Soviet-style” and “Orwellian” with “nonstop monitoring.” Anderson describes the overall DOGE playbook as a series of “deeply intrusive invasions of privacy.”
Alternate Realities
But what protections are out there for employees? Certain states, such as New York and Illinois, do offer strong privacy protections against, for example, unnecessary biometric tracking in the private sector, and California’s Consumer Privacy Act covers workers as well as consumers. Overall, though, the lack of federal-level labor law in this area makes the US something of an alternate reality to what is legal in the UK and Europe.
The Electronic Communications Privacy Act in the US allows employee monitoring for legitimate business reasons and with the worker’s consent. In Europe, Algorithm Watch has made country analyses for workplace surveillance in the UK, Italy, Sweden, and Poland. To take one high-profile example of the stark difference: In early 2024, Serco was ordered by the UK's privacy watchdog, the Information Commissioner’s Office (ICO), to stop using face recognition and fingerprint scanning systems, designed by Shopworks, to track the time and attendance of 2,000 staff across 38 leisure centers around the country. This new guidance led to more companies reviewing or cutting the technology altogether, including Virgin Active, which pulled similar biometric employee monitoring systems from 30-plus sites.
Despite a lack of comprehensive privacy rights in the US, though, worker protest, union organizing, and media coverage can provide a firewall against some office surveillance schemes. Unions such as the Service Employees International Union are pushing for laws to protect workers from black-box algorithms dictating the pace of output.
In December, Boeing scrapped a pilot of employee monitoring at offices in Missouri and Washington, which was based on a system of infrared motion sensors and VuSensor cameras installed in ceilings, made by Ohio-based Avuity. The U-turn came after a Boeing employee leaked an internal PowerPoint presentation on the occupancy- and headcount-tracking technology to The Seattle Times. In a matter of weeks, Boeing confirmed that managers would remove all the sensors that had been installed to date.
Under-desk sensors, in particular, have received high-profile backlash, perhaps because they are such an obvious piece of surveillance hardware rather than simply software designed to record work done on company machines. In the fall of 2022, students at Northeastern University hacked and removed under-desk sensors produced by EnOcean, offering “presence detection” and “people counting,” that had been installed in the school’s Interdisciplinary Science & Engineering Complex. The university provost eventually informed students that the department had planned to use the sensors with the Spaceti platform to optimize desk usage.
OccupEye (now owned by FM: Systems), another type of under-desk heat and motion sensor, received a similar reaction from staff at Barclays Bank and The Telegraph newspaper in London, with employees protesting and, in some cases, physically removing the devices that tracked the time they spent away from their desks.
Despite the fallout, Barclays later faced a $1.1 billion fine from the ICO when it was found to have deployed Sapience’s employee monitoring software in its offices, with the ability to single out and track individual employees. Perhaps unsurprisingly in the current climate, that same software company now offers “lightweight device-level technology” to monitor return-to-office policy compliance, with a dashboard breaking employee location down by office versus remote for specific departments and teams.
According to Elizabeth Anderson’s latest book Hijacked, while workplace surveillance culture and the obsession with measuring employee efficiency might feel relatively new, it can actually be traced back to the invention of the “work ethic” by the Puritans in the 16th and 17th centuries.
“They thought you should be working super hard; you shouldn’t be idling around when you should be in work,” she says. “You can see some elements there that can be developed into a pretty hostile stance toward workers. The Puritans were obsessed with not wasting time. It was about gaining assurance of salvation through your behavior. With the Industrial Revolution, the ‘no wasting time’ became a profit-maximizing strategy. Now you’re at work 24/7 because they can get you on email.”
Some key components of the original work ethic, though, have been skewed or lost over time. The Puritans also had strict constraints on what duties employers had toward their workers: paying a living wage and providing safe and healthy working conditions.
“You couldn’t just rule them tyrannically, or so they said. You had to treat them as your fellow Christians, with dignity and respect. In many ways the original work ethic was an ethic which uplifted workers.”
6 notes
·
View notes
Text
Biometric Attendance Management System | Only 1 SGD Per Month
A Biometric Attendance Management System is a modern, secure, and highly efficient method for tracking employee attendance using biometric data such as fingerprints, facial recognition, or iris scans. Unlike traditional attendance systems that rely on manual entries or swipe cards, a Biometric Attendance Management System ensures accuracy, eliminates time theft, and prevents proxy attendance. Businesses of all sizes, from small startups to large corporations, are now shifting towards biometric solutions to maintain transparency and improve workforce management.
One of the most attractive offerings in the market today is the Biometric Attendance Management System | Only 1 SGD Per Month plan. This cost-effective solution makes advanced attendance tracking accessible to businesses with limited budgets, especially in competitive markets like Singapore. At just 1 SGD monthly, companies can enjoy premium biometric services without compromising on quality. It includes features like real-time attendance tracking, automated reports, integration with payroll, and secure cloud-based data storage.
Implementing a Biometric Attendance Management System significantly reduces administrative workload. HR teams no longer need to manually check timesheets or address attendance discrepancies. The system automatically records accurate timestamps every time an employee checks in or out. This not only improves operational efficiency but also boosts employee accountability and punctuality. With biometric authentication, the risk of buddy punching or attendance fraud is virtually eliminated.
Additionally, opting for a Biometric Attendance Management System | Only 1 SGD Per Month ensures businesses remain compliant with labor laws and company policies by maintaining accurate and tamper-proof attendance records. These records can be easily accessed for audits, employee evaluations, and payroll calculations, ensuring smooth administrative operations. The affordable pricing makes it a valuable investment, providing a high return through increased productivity and reduced payroll errors.
In conclusion, integrating a Biometric Attendance Management System into your business operations is a smart, future-ready decision. With an affordable plan of Only 1 SGD Per Month, companies can benefit from precise attendance management, enhanced security, and seamless integration with existing HR systems. This modern solution not only streamlines workforce management but also fosters a culture of discipline and reliability in the workplace.

For more details Visit us: https://exigasoftware.com.sg/biometric-attendance-management-system/
Email: [email protected]
2 notes
·
View notes
Text
Voice Authentication and Compliance: Meeting KYC, GDPR, and HIPAA Standards
Voice authentication is transforming the way businesses verify identity for their consumer base. It’s fast, secure, and convenient. But for businesses in regulated industries, voice technology must also comply with global privacy laws.

Why Voice Authentication Needs Compliance
Voice is biometric data. Like a fingerprint, it’s unique to each user. That makes it powerful but also sensitive. Businesses using voice authentication must ensure that it complies with standards like KYC, GDPR, and HIPAA.
Failing to meet these requirements can result in legal issues. It can also erode customer trust. That’s why compliance isn’t optional. It’s essential for secure and ethical use.
KYC: Know Your Customer Regulations
KYC is vital for banks, fintech firms, and financial services. It helps prevent fraud, money laundering, and identity theft. Voice authentication helps verify users in real time. It confirms their identity with speed and accuracy.
But voice data must be stored securely. Businesses must ensure encryption and limited access. Only authorized personnel should handle this data. Consent must also be collected before using voice for KYC.
GDPR: Protecting Data Privacy in the EU
GDPR governs how personal data is handled in the European Union. Voiceprints fall under “biometric data,” a special category of personal information. Businesses must get explicit user consent before collecting voice data.
They must also explain how the data will be used. Users should be allowed to withdraw consent anytime. Under GDPR, companies must also ensure data is deleted when no longer needed.
HIPAA: Safeguarding Health Information in the US
In the healthcare industry, HIPAA protects patient information, including voice recordings. If voice authentication is used to access health data, it must follow HIPAA rules.
This means ensuring voice data is encrypted and audit logs are maintained. Staff must be trained in how to handle and protect this information. Failing to do so can lead to costly penalties.
Best Practices for Voice Authentication Compliance
Always obtain explicit consent from users
Use strong encryption for storing voiceprints
Limit access to voice data within the organization
Keep audit logs of authentication events
Comply with data retention and deletion policies
The Bottom Line
Voice authentication boosts security and improves user experience. However, if this process does not comply with the privacy laws, it poses major risks. By aligning voice authentication with KYC, GDPR, and HIPAA, it ensures legal safety for the business and builds user trust. Businesses that prioritize privacy stand to win in the long run.
4 notes
·
View notes
Text
The Strategic Role of Check-in Kiosks in Military Airport Terminals

Military airport terminals operate under heightened security and efficiency demands compared to their commercial counterparts. These facilities not only handle routine transport of service members but also play crucial roles in logistics, emergency deployments, and diplomatic missions. In such high-stakes environments, even minor inefficiencies or security lapses can have significant consequences.
To meet these challenges, many military terminals are turning to check-in kiosk technology—automated, self-service systems that streamline passenger processing and improve terminal security. These kiosks, equipped with advanced features such as biometric scanning, real-time data synchronization, and user-friendly interfaces, are reshaping the operational landscape of military air travel. In this blog, we explore how kiosk technology enhances security, boosts efficiency, improves user experience, and supports long-term cost-effectiveness and emergency readiness in military airport terminals.
Enhancing Security Protocols with Check-in Kiosks
Security is paramount in military environments, and check-in kiosks significantly contribute to strengthening existing protocols. These kiosks do more than expedite the check-in process—they integrate seamlessly with military-grade security systems to ensure rigorous identity verification and real-time data updates.
Biometric Integration for Identity Verification
One of the standout features of military check-in kiosks is biometric integration. Fingerprint scans, iris recognition, and facial recognition ensure that only authorized personnel gain access to secured areas. These systems eliminate the risks associated with lost or forged ID cards and allow for multi-factor authentication, which is critical in sensitive operations.
Biometric data is instantly matched against military personnel databases and watchlists, providing a higher level of accuracy and preventing unauthorized access. The process is not only secure but also faster and less intrusive than traditional methods, offering a seamless experience for users.
Real-Time Data Synchronization with Security Networks
Check-in kiosks in military terminals are linked to centralized security networks, allowing for real-time synchronization of data. When a service member checks in, their identity, assignment, and travel itinerary are cross-verified with military systems to detect inconsistencies or threats.
This instant communication enhances threat detection and tracking capabilities, allowing security personnel to respond swiftly to anomalies. Furthermore, in the event of a security breach, kiosks provide critical logs and timestamps to aid investigation and resolution.

Increasing Operational Efficiency in Terminal Management
Military terminals operate around tight schedules and high throughput. By automating check-in procedures, kiosks alleviate common bottlenecks and enhance operational efficiency.
Automated Boarding Pass and ID Issuance
Traditional check-in desks involve manual data entry and document verification, which can slow down the boarding process. In contrast, automated kiosks issue boarding passes and temporary access credentials within seconds, drastically reducing processing time.
Kiosks can print, scan, and digitally store documentation, minimizing the likelihood of human error. This not only improves accuracy but also enhances compliance with standardized military travel protocols.
Reduced Staff Workload and Resource Allocation
By handling repetitive check-in tasks, kiosks free up human resources for more critical responsibilities. Personnel previously tied to desk duties can be reassigned to areas such as tactical operations, logistics support, or passenger assistance.
This optimized resource allocation ensures that the terminal functions more smoothly, even during peak hours or large-scale deployments. It also reduces the risk of operational delays, contributing to overall mission readiness.
Improving User Experience for Military Personnel and Visitors
Ease of use is crucial in high-pressure environments. Military check-in kiosks are designed with user-centric interfaces, ensuring accessibility for all users, including service members, dependents, and visitors.
Multilingual Support and Accessibility Features
Military airports cater to diverse users from various linguistic and cultural backgrounds. Kiosks equipped with multilingual options ensure that language barriers do not impede check-in or access.
Moreover, features such as voice commands, screen magnification, and wheelchair-accessible interfaces make these kiosks usable for individuals with disabilities. This commitment to inclusivity aligns with military values and enhances the overall user experience.
24/7 Availability and Minimizing Congestion
Unlike staffed check-in counters, kiosks offer uninterrupted service around the clock. This is especially beneficial in military operations where flights and deployments can occur at odd hours or on short notice.
By distributing the check-in load across multiple kiosks, these systems minimize terminal congestion, allowing for smoother passenger flow and reduced wait times. This is particularly valuable during mobilizations, drills, or emergency evacuations.
Cost-Effectiveness and Long-Term Savings
Implementing kiosk systems in military terminals requires upfront investment, but the long-term financial benefits make a compelling case for adoption.
Reduction in Manual Processing Costs
Kiosks reduce the need for manual data entry, paper forms, and physical staffing, all of which incur recurring costs. Digital processes streamline administrative workflows and lower the chances of clerical errors, which can be costly and time-consuming to fix.
In addition, kiosks help reduce the environmental footprint of military operations by minimizing paper use—a growing priority in defense logistics.
Scalability to Meet Future Demands
Modern kiosk systems are built with modular and scalable designs, allowing for future upgrades without major overhauls. As military travel protocols evolve, new software features or hardware modules (e.g., upgraded biometric sensors or contactless payment capabilities) can be easily integrated.
This future-proofing makes kiosk systems a strategic investment, capable of adapting to shifting operational needs and technological advancements.

Supporting Emergency and Contingency Operations
Military terminals must remain operational under all circumstances, including crises. Kiosks offer resilience and flexibility during emergencies, supporting both evacuation and redeployment efforts.
Rapid Reconfiguration for Emergency Protocols
In the event of a crisis—whether it’s a natural disaster, base lockdown, or global conflict—check-in kiosks can be rapidly reprogrammed to follow new protocols. For example, they can be configured to prioritize certain personnel categories, enable emergency passes, or facilitate health screenings during pandemics.
This capability allows terminals to maintain order and operational continuity, even in high-stress environments.
Reliable Communication Channels for Critical Updates
During emergencies, timely and accurate communication is essential. Kiosks can function as broadcast hubs, displaying critical alerts, evacuation routes, or mission updates directly on the screen.
Some systems can also send automated SMS or email updates to personnel, ensuring that everyone receives the necessary information regardless of their physical location within the terminal. This functionality is invaluable during fast-moving operations where traditional communication lines may be overloaded or unavailable.
Conclusion
Check-in kiosks are no longer just a convenience feature—they are a strategic asset in military airport terminals. From strengthening security with biometric authentication and real-time data sync, to improving operational efficiency and delivering a seamless user experience, kiosks represent a significant leap forward in military logistics technology.
They not only reduce costs and optimize personnel usage, but also enhance readiness and resilience during emergencies. With scalable architectures and support for the latest security features, kiosk systems are well-positioned to meet the future demands of military air transport.
For defense organizations aiming to modernize their infrastructure and improve mission efficiency, adopting kiosk technology is not just an option—it’s a mission-critical necessity.
#kiosk#technology#software#business#development#programming#productivity#airport#check in kiosk#tech#techtrends#selfservicekiosk#kioskmachine#innovation#kiosks#panashi#techinnovation#digitaltransformation
2 notes
·
View notes
Text
BREAKING NEWS: Revolutionary AI Scheduling Model Disrupts Multi-Billion Dollar Industries
IndustriesMay 14, 2025 – In a groundbreaking development set to redefine time management across education, fitness, and the arts, researchers from the Zurich Institute of Technology (ZIT) have unveiled an artificial intelligence model capable of autonomously optimizing human schedules with an accuracy rate exceeding 98.7%.Dubbed "ChronoPilot," the new system leverages deep contextual learning to interpret not only user preferences but also emotional states, productivity trends, and even regional weather forecasts to dynamically tailor personal and group schedules. In early trials, the system outperformed existing scheduling platforms by over 400% in efficiency and conflict resolution.The implications span vast sectors. Educational institutions using class scheduling software like Lunacal’s platform for class bookings have already reported dramatic improvements in attendance and engagement. In the fitness industry, where applications such as gym booking software are crucial, ChronoPilot’s integration led to a 37% rise in client retention during a 90-day pilot. Music academies leveraging music lesson scheduling tools observed a 52% reduction in missed appointments.ZIT’s Secret Weapon: Sentient Sync ProtocolWhat truly sets ChronoPilot apart is its proprietary Sentient Sync Protocol (SSP) — a neural time-mapping engine that mimics human anticipation. SSP doesn’t just block out time; it predicts the best time for each task based on thousands of variables, including circadian rhythms, cognitive load history, and even micro-fluctuations in vocal tone during user interactions.Dr. Lena Marwick, lead AI architect at ZIT, explained, “We’re no longer asking users to fit into rigid schedules. ChronoPilot adapts to them, moment by moment.”Global Trials, Unprecedented ResultsThe AI was tested across 1.2 million scheduling interactions in 11 countries, across five major time zones. In one compelling instance, a public school in Osaka integrated ChronoPilot into its digital classroom system. Within three weeks, student punctuality improved by 48%, and feedback indicated a 63% increase in perceived classroom coherence.Meanwhile, a UK-based national gym chain used ChronoPilot to coordinate personal training sessions across 87 locations. Instructors reported a 41% decrease in downtime, and an average boost of 18% in customer satisfaction scores.ChronoPilot vs. The Old GuardWhile current scheduling tools rely heavily on manual input or rigid templates, ChronoPilot learns from passive inputs — browsing behavior, sleep app data, voice command history — with the user’s consent. This passive data synergy allows it to preemptively adjust schedules without user intervention.Analysts say the AI’s capabilities pose an existential threat to legacy scheduling systems and even to calendar giants like Google Calendar and Microsoft Outlook. “It’s not just a calendar anymore,” says Gideon Lark, senior analyst at MetaMetrics. “It’s a lifestyle orchestrator.”Privacy Concerns and Ethical DebateNot everyone is celebrating. Digital rights watchdogs have raised concerns about the volume and sensitivity of data ChronoPilot processes. The AI can access everything from location logs to biometric signals. While ZIT asserts the system uses end-to-end encryption and offers opt-out data controls, some critics remain wary."We’re trading convenience for surveillance,” warns Aria Salim, director of the Tech Privacy Initiative. “There must be enforceable limits on how such AI models evolve, especially as they begin to predict and possibly influence human behavior.”ZIT has responded by publishing a white paper detailing its privacy protocols and inviting third-party audits. Still, the debate over AI autonomy and human agency continues to intensify.
2 notes
·
View notes
Text
Building a Mobile-First CRM: UX Considerations for Developers
As teams become increasingly mobile and remote, CRMs must function seamlessly on smartphones and tablets. A mobile-first CRM isn’t just a responsive design — it’s a rethinking of how users interact with features in real-time, on the go.

Here are key UX considerations developers should prioritize when building mobile-first CRM solutions:
1. Simplified Navigation
Use a bottom-tab or collapsible hamburger menu for easy one-hand use
Prioritize the most-used features on the home screen
Limit user interactions to 2–3 taps to access critical tasks
Avoid overloading the interface with too many options
2. Offline Access and Sync
Allow users to access records even without internet connectivity
Auto-sync changes once the device goes online
Use local caching for smooth experience during field operations
Maintain data accuracy across devices
3. Touch-Optimized Interactions
Design larger touch targets for forms, buttons, and menus
Use swipe gestures for actions like delete, archive, or assign
Minimize typing by offering dropdowns, toggles, and voice input
Focus on finger-friendly UI patterns over mouse-based ones
4. Performance and Speed
Optimize loading times with lazy loading and minimal animation
Compress images and minimize API payloads
Use skeleton loaders to improve perceived speed
Reduce background processes that drain battery
5. Context-Aware Functionality
Trigger location-based reminders or check-ins for sales reps
Show recently accessed contacts or tasks upon app launch
Personalize dashboards based on time of day or past activity
Custom CRM apps can dynamically adapt to user context
6. Data Entry Efficiency
Pre-fill forms with known user data
Add barcode/QR code scanning for quick product or ticket lookup
Use camera access for attachments and visual records
Minimize scrolling with accordion or segmented layouts
7. Notifications and Alerts
Send real-time push notifications for leads, meetings, and updates
Group notifications logically to avoid spamming users
Allow users to customize alert preferences within settings
Deliver actionable alerts with quick action buttons
8. Security on Mobile Devices
Require biometric or PIN login on app launch
Encrypt stored data and use secure authentication APIs
Set auto-logout for idle sessions
Mobile CRM security must match or exceed desktop-grade protection
#MobileFirstCRM#UXDesign#CRMDevelopment#UserExperience#MobileUX#CRMApps#SalesOnTheGo#CRMDesign#CustomCRM#TouchUI
2 notes
·
View notes
Text
Precision is crucial when it comes to fingerprinting services. The accuracy of Livescan fingerprint in Laurel, Maryland ensures that background checks and identity verifications are both correct and reliable. Livescan technology allows for the digital capture of fingerprints, providing a much more precise method than traditional ink-based techniques. This accuracy is vital in various situations such as job screenings, security clearances, and legal matters. The precision of your fingerprints directly impacts the speed and reliability of the entire process.
0 notes
Text
G Witch Onscreen Text: Episode 2
This is part 3 in an ongoing series where I try and document and discuss all of the text that appears on screens and monitors throughout the show! Just because I can!
<<Click here to go back to Episode 1!
(Once I have a masterpost set up I will link it here!) Let us Begin! Below the Cut!

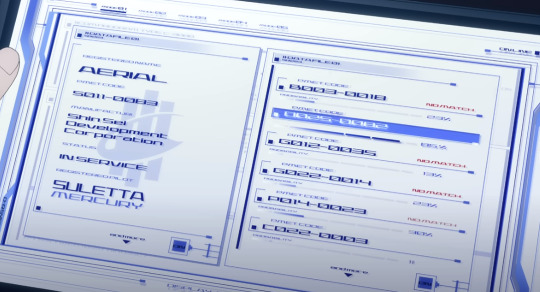
TEXT: (Lefthand side) Registered Name: AERIAL PMET CODE: 5011-0083 MANUFACTUR(ER): SHIN-SEI DEVELOPMENT CORPORATION STATUS: IN SERVICE REGISTERED PILOT: SULETTA MERCURY
At the beginning of the episode, Rouji has Haro run a program that compares Aerial's permet code and registered statistics against other registered Mobile Suits to try and find a match, and measures the probability of the two being the same type of MS. There is no direct match to any other MS by Permet Code, but the system states there's an 85% probability that it's a match for a Mobile Suit with permet code 0025-0082.
We never see the specific name of this MS, but considering that Shaddiq names "Ochs Earth" as the company that made it and proceeds to call Aerial, "...the Witch's Mobile Suit," I think it's reasonable to assume that 0025-0082 was the Permet Code for Lfrith-03.

TEXT: ALERT ACCESS CONTROL [???] [----OF ENTRY A---]
Unfortunately due to the small text of the Alert message, the fact that it scrolls, and it's brief time onscreen, its hard to make out specifically what it says. My best assumption from what we have is that it's a warning currently barring anyone from entry into the 13th Tactical Testing Sector.

TEXT: (Suletta's Asticassia ID) PILOTING DEPARTMENT ID No: LP-041 SULETTA MERCURY BIRTHPLACE: MERCURY HOUSE: NO DATA PC-CRIMINAL RECORD: NO DATA PC-BIOMETRIC SYSTEM: REGISTERED
(Below) WE ARE RESPONSIBLE UNDER COMPANY REGULATIONS FOR THE PROCESSING OF PERSONAL DATA
UNDER THESE REGULATIONS, WE ARE ALSO RESPONSIBLE FOR DATA HANDLING SUCH AS TRANSMISSION TO RECIPIENTS AND THIRD PARTIES.
PLEASE REFER TO THE FOLLOWING DOCUMENTS FOR DETAILS.
As Suletta is being questioned, we get a brief glimpse at the investigation report the interrogator was looking at before the screen cuts to black when it hits the table. Nothing super interesting here, but Suletta doesn't have a registered criminal record! Yippeeee!

TEXT: CAM: 05 MONITORING CAMERA FACILITY MANAGEMENT COMPANY
Not much to say here, this camera lets us know where Suletta is currently being held. (The Facility Management Company)
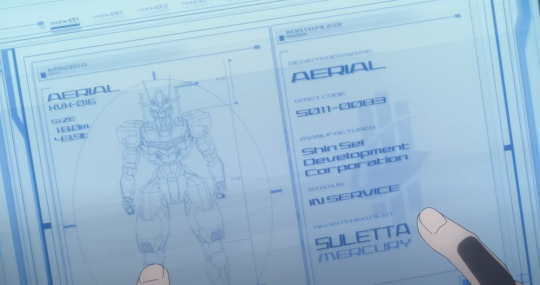
TEXT: (Lefthand Side) AERIAL XVX - 016 SIZE: 18.0m 48.9t
No point discussing the info on the right, we've already seen it, but this gives us a look at Aerial's height and weight.

TEXT: (Top Right) COM DELLING REMBRAN BENERIT GROUP
I only included this to point out that wow the display system devs made some poor choices with the UI here. Dark Blue text on Dark Backgrounds? You'd think the text would automatically lighten but I guess we'll have to wait for Ver 6.0 for that update.
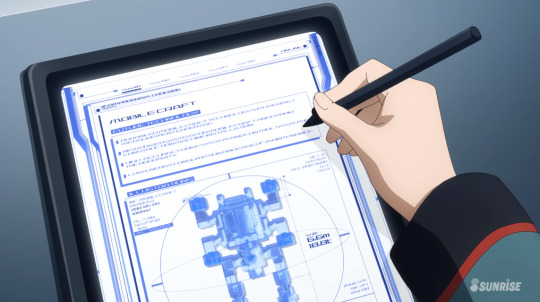
TEXT (Top half) MOBILE CRAFT FUTURE TECHNOLOGY
ADVANCED MOBILE CRAFT TECHNOLOGY WITH PERMET MEASUREMENT EXPERTISE NEW POWER SYSTEM FOR MOBILE CRAFT AND HYBRID CONSTRUCTION MACHINE INSTALLATION HIGH ACCURACY DRIVE SYSTEM AND CONTROL SYSTEM IN MICROGRAVITY LOW ENERGY CONSUMPTION AND EASE OF MAINTENNANCE
No need to discuss the bottom half, its just the height and weight of the MC which we already know. I think it's funny how many classes this school seems to have on the new and improved Mobile Craft from Future Technology. I should probably buy one too. I love you Mobile Craft.


TEXT: (Left Image) The Shin Sei Development Corporation was established in A.S. 89. Our business began with the development of integrated operating systems for mobile suits and medical devices. We have been involved in MS development and have supported welfare engineering throughout our company history.
(Right Image) Ranking: D Sales Ranking (within group companies): 151th (out of) Total 157 companies [Mobile Suit Development] Number of clients: Over 300 companies Yearly patents: Over 200
We get a lot of information about Shin Sei in this scene where Martin looks at the Company History tab on their official website. The most interesting thing being that they were founded in A.S. 89. The Vanadis Incident occured in A.S. 101, and the show proper takes place in A.S. 122, so at some point between 101 and 122, Prospera worked her way up through Shin Sei, eventually becoming its CEO.
Given that Suletta had to have been born around A.S. 105, and that in Cradle Planet, we learn that Prospera had been working within Shin Sei when Suletta was around 6, that places A.S. 111 as the earliest she was involved.
We also learn in Cradle Planet, that when Suletta is around 11, Prospera has recently been promoted within the company, and now has many people working under her. That would be around A.S. 116. When Suletta is 16, that's when Prospera tells her that she's going to school, which would be around A.S. 121, and I think it's safe to assume that she had already become president by then.
SO!! TL;DR!! It's most likely that Prospera became the president of Shin Sei at SOME point between A.S 116 and A.S 121. I'd put it somewhere in the middle, around A.S 119. (Can't wait to find out that they probably just outright state this somewhere and I did all this for nothing....)
ADDENDUM

GOD DAMNIT. I WATCHED ALL OF CRADLE PLANET TO MATH THAT SHIT OUT. WHATEVER. I CAME TO THE SAME CONCLUSION SO I WIN.

The text is too small to make out, but we DO get a small glimpse at the letter Delling sent to Miorine about unenrolling her from the school. It probably just literally says what the body guard reads out.
I think it says something that Delling doesn't even like, text his daughter. He sends an email through the official Benerit Group email account to her bodyguard who reads it for her. What a cowardly man.

TEXT: (Left) FLUSH (Right) EMERGENCY CALL UNLOCK LOCK
YES the toilet text is important to document stop fucking looking at me like that.

TEXT: NEXT STAGE TOUCH SCREEN TO CONTINUE
I'll leave the explanation of the symbolism of this scene as an exercise for the reader. [Sultry Wink]

TEXT (Above) THIS ELECTRONIC SIGNATURE IS PROOF THAT IT WAS SIGNED BY A REPRESENTATIVE OF THE BENERIT GROUP.
No way to tell what Delling is signing here, but we do get a brief look at his handwriting. It turns out his cursive is really bad, actually!
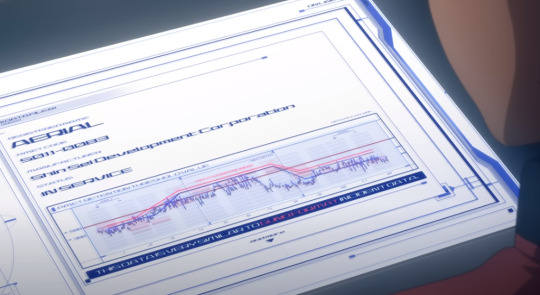
At the Shin Sei inquiry, Shaddiq shares this graph titled "PMET RETENTION THRESHOLD VALUE", stating that during the duel, Aerial's Permet Influx Values exceeded the standards set by Cathedra.
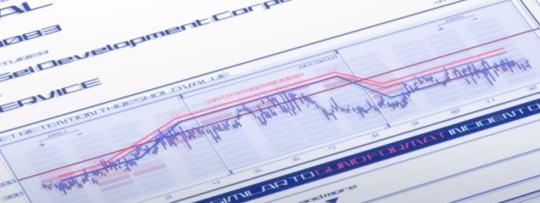
This graph can be tough to parse, so let me explain it as best I can. The blue line represents Aerial's Permet Retention during the duel. The solid dark line represents the permet retention limit imposed by cathedra on mobile suits. (At around 500) As we can see, while Aerial began the duel underneath that limit, it exceeded it for a moment (presumably when Suletta took over for Miorine and the GUND bits were activated.)
The red line above that is labelled DATA STORM INCIDENT, which is representative of the minimum Permet Retention a Gundam expresses when it is interfacing with a Data Storm. The text on the bottom reads, THIS DATA IS VERY SIMILAR TO GUND FORMAT INCIDENT DATA.
But the key thing to take note of here is that Aerial's chart just BARELY doesn't exceed the DATA STORM INCIDENT graph, meaning that, despite it exceeding Cathedra's standards, it CANNOT be directly proven that Aerial was interfacing with a Data Storm. This is actually what Prospera brings up as her main counterpoint to the accusation.

So the graph is entirely consistent with Prospera's main argument. While she can't prove that Aerial isn't a gundam, nobody else can prove that it is.
Huaaaahh!! Alright!! This one was very DENSE. If you made it all the way through, thank you very much!! As a reward, have some little gay people




[I sprinkle these stills on the ground like bird seed.]
There was definitely a lot of really interesting info in this episode, and while not a lot of it was particularly new, I think it's really a testament to the dedication of keeping things wholly consistent in this world, even for the smallest of things that no normal person watching would even bother noticing.
Also, on the Shin Sei Website, did you notice that they accidentally put 151th instead of 151st?
You can't win em all!
Click here to go to Episode 3! >>
Click here to go to the Masterpost!
36 notes
·
View notes
Text
How Questionnaires and Technology Are Revolutionizing Fraud Prevention

Fraud has become a significant challenge across industries, from finance to healthcare. As criminals become more sophisticated, organizations must adopt advanced methods to detect and prevent fraudulent activities. One powerful combination proving effective is the integration of questionnaires and technology in fraud prevention strategies.
The Role of Questionnaires in Fraud Detection
Questionnaires serve as an essential tool in gathering crucial information from individuals, be it customers, employees, or vendors. Structured questionnaires can help organizations assess risks, verify identities, and detect inconsistencies in responses. By incorporating behavioral and psychological cues, they can reveal red flags indicating potential fraudulent intent.
Technology Enhancing Questionnaires for Accuracy
Modern technology amplifies the effectiveness of questionnaires in fraud prevention. Artificial intelligence (AI) and machine learning (ML) analyze response patterns, detect anomalies, and flag inconsistencies in real-time. Natural Language Processing (NLP) helps identify deceptive answers, while automated data cross-referencing ensures accuracy. Additionally, biometric verification and blockchain technology enhance security by confirming identities and preventing document forgery.
Real-World Applications
Many industries leverage digital questionnaires and AI-driven analytics to prevent fraud. Banks use them to assess loan applicants' credibility, insurance companies detect false claims, and e-commerce platforms verify users to prevent identity theft. Government agencies also employ AI-powered questionnaires in immigration and border security to detect fraudulent intent.
The Future of Fraud Prevention
With fraudsters constantly evolving their tactics, the future lies in adaptive questionnaires powered by AI, where questions change dynamically based on responses. Coupled with real-time data analytics and blockchain verification, this approach will further strengthen fraud detection and prevention.
In conclusion, the synergy between questionnaires and technology is a game-changer in fraud prevention. By leveraging advanced analytics and AI-driven insights, organizations can stay ahead of fraudsters, ensuring security and trust in their operations.
Book a free demo: online panel management platform
fraud detection and reporting tool
2 notes
·
View notes
Text
Employer Health Testing Solutions by My Care Labs
My Care Labs offers comprehensive employer health testing solutions designed to support workplace safety, compliance, and productivity. Our services are tailored to meet the unique needs of businesses across various industries, ensuring a healthier workforce and minimizing disruptions due to illness.
We provide on-site and off-site testing services, including COVID-19 testing (RT-PCR and rapid antigen), drug and alcohol screening, biometric screenings, and general wellness checks. Our mobile testing units and quick turnaround lab capabilities ensure minimal downtime and seamless integration with your company's schedule.
Our employer health testing programs help businesses comply with OSHA and other regulatory requirements, reduce absenteeism, and improve overall employee well-being. We work closely with HR and occupational health departments to develop custom protocols that align with your organization's health policies.
What sets My Care Labs apart is our commitment to accuracy, confidentiality, and convenience. We use CLIA-certified laboratories and HIPAA-compliant systems to ensure data security and reliable results. Test results are typically available within 24 hours, helping employers make informed decisions swiftly.
Additionally, we offer digital platforms for easy scheduling, result tracking, and analytics reporting. Our dedicated support team is always available to assist with coordination, compliance documentation, and answering employee questions.
By partnering with My Care Labs, employers gain access to scalable, cost-effective health testing solutions that promote a culture of health and responsibility in the workplace. Whether for pre-employment screening, routine wellness checks, or managing outbreaks, My Care Labs is your trusted partner in occupational health.
For more information visit :
1 note
·
View note
Text
🤖 Facial Recognition Software: How It Works
Facial recognition technology is everywhere—from unlocking phones to biometric attendance systems. But how does it work? Here’s a quick breakdown:
1️⃣ Detection: The software locates faces in images or videos using advanced computer vision, even in complex settings. 2️⃣ Analysis: Key facial features are mapped (e.g., eye distance, chin shape) and converted into a unique "faceprint," similar to a fingerprint. 3️⃣ Recognition: The faceprint is compared to a database for verification or classification, ensuring accuracy with confidence scores.

2 notes
·
View notes
Text
Automated Armor Suit Fitting System (AASF System)

The Automated Armor Suit Fitting System (AASF System) represents the latest advancement in the seamless integration of advanced full-body armor suits onto cadets. Designed for efficiency and precision, the AASF System eliminates the need for manual fitting, ensuring a perfect fit for each cadet in minimal time. This system underscores a pragmatic approach to uniformity and control, reflecting the reality of modern military training environments.
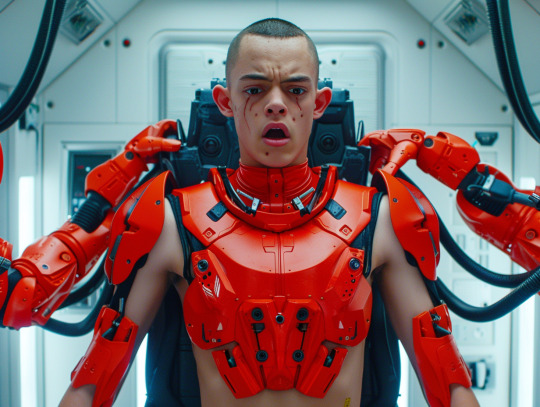
Design and Features
Robotic Chamber: The AASF System consists of a fully automated robotic chamber equipped with high-precision actuators and sensors. The chamber is designed to accommodate a wide range of body sizes and shapes, ensuring each cadet receives a tailored fit.
3D Scanning Technology: The system employs advanced 3D scanning technology to capture the cadet’s exact body dimensions. This data is used to adjust the armor suit in real-time, ensuring a snug and secure fit that maximizes protection and mobility.
Robotic Servo Arms: The fitting process utilizes robotic servo arms to install the suits onto the conscripts' bodies. These arms handle the suit components with precision, attaching each part securely while the conscript remains passive. This automation ensures consistency and accuracy, reducing the risk of human error.
Precision Fitting: Using a combination of hydraulic and pneumatic systems, the chamber adjusts the suit’s various components—torso, limbs, helmet, and integrated chastity/underwear/diaper component—to fit the cadet’s body perfectly. The process ensures that all joints and seals are aligned correctly, minimizing potential points of failure or discomfort.
Biometric Integration: The system integrates biometric monitoring to track the cadet’s vital signs during the fitting process. This includes heart rate, respiration, and stress levels, ensuring the process is conducted safely and efficiently.
Automated Fastening: Once the suit components are in place, the AASF System employs automated fastening mechanisms to secure the suit. This includes the activation of locking mechanisms, sealing of joints, and integration of the internal waste management system.
Calibration and Adjustment: The system performs final calibration and adjustment checks, ensuring that all suit functions—such as the servos, waste management, and communication systems—are operational and correctly configured. This stage also includes a diagnostic check to identify and rectify any potential issues.

Fitting Procedure
Initial Positioning: Cadets enter the fitting chamber nude except for their Standard Chastity/Underwear/Diaper Component. The chamber’s docking mechanism arm clasps them from behind, fixing them in place securely. This initial docking provides the first point of stabilization.
Boot Installation: Robotic servo arms install the boots onto the cadets' feet. These boots are the foundation of the armor, providing additional strap points to stabilize the cadets during the subsequent steps.
Torso Protector: The next step involves the application of the torso protector. The servo arms carefully align and attach the torso segment, ensuring it fits snugly and securely around the cadet’s upper body.
Hips and Legs Armor: Following the torso protector, the hips and legs armor components are attached. These segments are aligned with the boots and torso protector, creating a seamless protective layer over the cadet’s lower body.

Arm Armor: The servo arms then attach the arm segments, ensuring each piece aligns with the torso protector and the shoulder joints. This step includes both the upper arm and forearm components.
Gauntlet-Style Gloves: The final armor components to be attached are the gauntlet-style gloves. These gloves are carefully aligned with the forearm segments, completing the protective suit.
Helmet: Although not specified in the initial sequence, the helmet is typically the final piece, providing comprehensive protection and integrating with the suit’s communication and sensory systems.
Final Checks and Adjustments: The system performs a series of checks to ensure all components are securely fastened and properly aligned. The cadet's biometrics are continuously monitored, and any necessary adjustments are made to ensure comfort and functionality.

Psychological Component
The AASF System is designed not only for physical integration but also for psychological conditioning. The process of being fitted by robotic servo arms, without any active participation, instills a sense of helplessness in the conscripts. This experience reinforces their acceptance of being encased in the suits, effectively making them acknowledge and adapt to their place within the system. The feeling of being physically and psychologically enveloped by the suit contributes to a deeper integration into the regimented environment of the academy.

4 notes
·
View notes