#Avg Antivirus Customer Support UK
Explore tagged Tumblr posts
Link
Resolve the issue is not an easy task for users and when the situation is out of control, then you have to get connected to the technical experts of AVG Antivirus Support Help Number.
#Avg Contact Number#Avg Antivirus Customer Support UK#AVG Antivirus support#AVG Antivirus Help Number UK
1 note
·
View note
Video
youtube
AVG Retail Registration +1866 321 3111
#AVG Retail Registration#AVG Retail Activation#Avg.com/retail#security system#Antivirus#Toll free num#avg support number#avg customer service#avg customer care number uk
1 note
·
View note
Text
Avast mobile security

Avast mobile security software#
Avast mobile security windows#
A day later, he changed his annual pay to $1 and pledged his board director's compensation of $100,000 to charity. Ondřej Vlček assumed the role of CEO and co-owner of Avast Plc in July 2019. Avast had its IPO on the London Stock Exchange in May 2018, which valued it at £2.4bn and was one of the UK's biggest technology listings. Shortly afterwards it was disclosed that someone may have created a malicious version of CCleaner with a backdoor for hackers. In July 2017, Avast acquired UK-based Piriform for an undisclosed sum.
Avast mobile security software#
AVG was a large IT security company that sold software for desktops and mobile devices. In July 2016, Avast reached an agreement to buy AVG for $1.3 billion. By 2015, Avast had the largest share of the market for antivirus software. Additionally, in 2014 Avast's online support forum was compromised, exposing 400,000 names, passwords and email addresses. Later that year, Avast acquired mobile app developer Inmite in order to build Avast's mobile apps. In 2014, CVC Capital bought an interest in Avast for an undisclosed sum. At the time, the company had 350 employees. By 2013, Avast had 200 million users in 38 countries and had been translated into 43 languages. In 2012, Avast fired its outsourced tech support service iYogi, after it was discovered that iYogi was using misleading sales tactics to persuade customers to buy unnecessary services. The following December, Avast filed for an initial public offering, but withdrew its application the following July, citing changes in market conditions. In 2010, Alwil changed its name to Avast, adopting the name of the software, and raised $100 million in venture capital investments. Former Symantec executive Vince Steckler was appointed CEO of Avast in 2009. As a result of the freemium model, the number of users of the software grew to one million by 2004 and 20 million by 2006. īy 2001, Alwil was experiencing financial difficulties, when it converted to a freemium model, offering a base Avast software product at no cost. Alwil rebuffed acquisition offers by McAfee, who was licensing the Avast antivirus engine. However, by the late 1990s, the company was struggling financially. In the 1990s security researchers at the Virus Bulletin, an IT security testing organization, gave the Avast software an award in every category tested, increasing the popularity of the software.
Avast mobile security windows#
In 1995, Avast employee Ondřej Vlček wrote the first antivirus program for the Windows 95 operating system. The new regime severed ties with the Soviet Union and reverted the country's economic system to a market economy. The cooperative was changed to a joint partnership in 1991, two years after the velvet revolution caused a regime change in Czechoslovakia. The cooperative was originally called Alwil and only the software was named Avast. Afterwards, he asked Eduard Kucera to join him in cofounding Avast as a cooperative. At the institute, Pavel Baudiš discovered the Vienna virus on a floppy disk and developed the first program to remove it. They studied math and computer science, because the Communist Party of Czechoslovakia would require them to join the communist party to study physics. The founders met each other at the Research Institute for Mathematical Machines in Czechoslovakia. The company's main product is the Avast Antivirus along with tools such as the Avast Secure Browser and the Avast SecureLine VPN.Īvast produces Avast Online Security, which is its main extension, but it also has extensions like Avast SafePrice and Avast Passwords.Īvast was founded by Eduard Kučera and Pavel Baudiš in 1988. It is dual-listed on the Prague Stock Exchange and on the London Stock Exchange and is a constituent of the FTSE 100 Index. At the time, AVG was the third-ranked antivirus product. In July 2016, Avast acquired competitor AVG Technologies for $1.3 billion. It had been a private company since 2010 and had its IPO in May 2018. Īvast was founded by Pavel Baudiš and Eduard Kučera in 1988 as a cooperative. In August 2021, Avast's board of directors agreed to an offer of US$8 billion. In July 2021, NortonLifeLock, an American cybersecurity company, announced that it is in talks to merge with Avast Software. The company has approximately 1,700 employees across its 25 offices worldwide. Avast has more than 435 million monthly active users and the second largest market share among anti-malware application vendors worldwide as of April 2020. is a Czech multinational cybersecurity software company headquartered in Prague, Czech Republic that researches and develops computer security software, machine learning and artificial intelligence. Avast founders Eduard Kučera (left) and Pavel Baudiš (right) in 2016 with their spouses, who run the non-profit Avast Foundation for community developmentĪvast Software s.r.o.

0 notes
Text
How to protect your small business from data breaches
Cyberattack vs. data breach: what’s the difference?
A cyberattack is simply a digital attack on computer systems, networks, devices, and/or applications. The objective is usually to disable computer systems or steal data. Attackers can use a variety of tools and techniques to achieve their goals, including phishing emails, ransomware, viruses, and denial-of-service attacks. A data breach is one potential consequence of a successful cyberattack. The types of data they are looking for could be passwords, email addresses, personal information, or financial information.
Threats
The following statistics paint a vivid picture of the threats to SMB data:
52% of small businesses experienced cybersecurity breaches in the past year.
Cybersecurity breaches cost UK businesses approximately £30 billion in 2016.
60% of small firms don’t know the source of the most disruptive cybersecurity breach or attack in the last twelve months.
Across the globe, just under 5 million records a day are compromised through a data breach.
On average, it takes 120 days for a business to discover a data breach.
In summary, data breaches are common, often go undetected at first, and can cost businesses – who don’t know how to protect themselves – thousands.
What is a data breach?
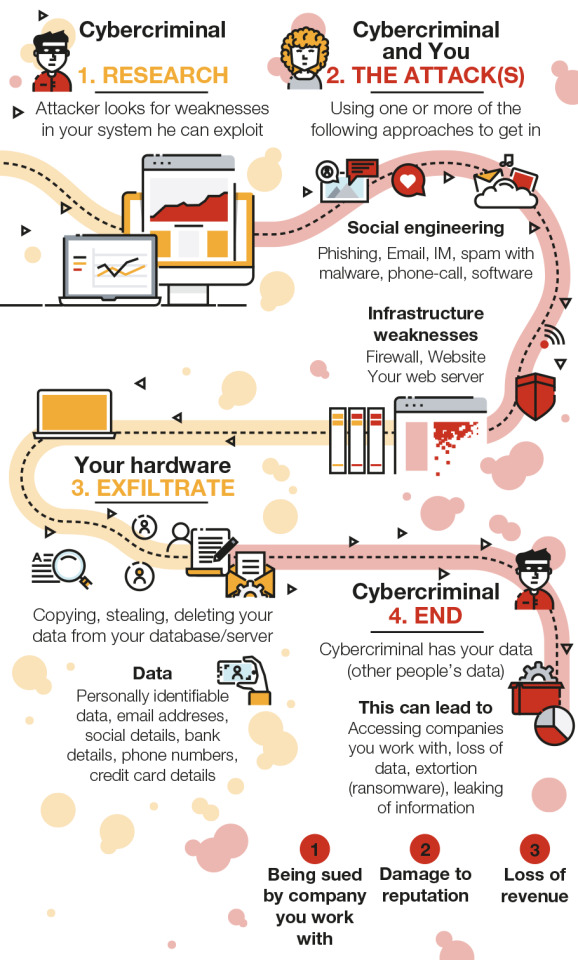
What can SMBs do to protect themselves?
Putting a cost-effective cybersecurity strategy in place can help to better protect you further down the line.
Strategy Step 1: Understand the elements of proper data protection
The first step in creating a cybersecurity strategy is to truly understand what is meant by ‘data protection’. Think of it in terms of the CIA acronym:
Confidentiality
Integrity
Availability.
This means your data needs to be kept confidential. It should only be available to people with relevant privileges. Your data should maintain its integrity and be in the format the user requires it to be (and not to have been materially altered by the system capturing, storing, or transmitting it.) Finally, your data should be available whenever the person with those relevant privileges is requesting it.
Strategy Step 2: Assess
The first step in assessing your customers’ potential vulnerabilities is to identify all the physical and virtual computing devices within the organization. Together with your client, make a list that includes all of them:
• Workstations and laptops• Network file servers• Network application servers• Corporate firewalls and switches• Multi-function printers• Mobile devices.
This infrastructure assessment should distinguish between cloud and on-premise systems and devices. This makes it easier for you to determine all possible storage locations for data. The number one threat to devices is a hybrid ransomware attack. For people, it’s targeted social engineering.
Now, categorize all business data and divide it into three locations: cloud,on-premise systems, and devices. For example:
• Cloud On-premise systems Devices• Cloud email and applications• Cloud storage• Websites and social media• Databases• Company-wide file sharing and storage• Intellectual property• Presentations• Company memos• Statistics and reports.
Read our white paper on the three essential components of managed security services.
Strategy Step 3: Identify relevant security measures
Once you’ve assessed what data is important to your business, where it resides, and who has access to it, you can determine the relevant security measures you should adopt. These may include:
Purchasing tools (for example, AVG antivirus Subscription for small businesses).
Redesigning your security protocols.
A wholesale change in your business’s attitude towards data security.
Training for all members of staff.
Data protection must be discussed and supported at every level within your business. It is as critical for senior executives as it is for junior team members, all of whom will have access to sensitive data of some kind. Take the time to review what data they may handle, and put the relevant measures in place.
Steps for protecting data

There are plenty of good security measures all businesses can apply today that will help prevent or reduce the chances of data loss, breach, or theft. These tools and solutions come in many shapes and sizes, but all have a role to play in protecting your sensitive and private data.
1: The basics
Install firewalls
Install AVG antivirus Subscription
Install encryption software.
2: Staff awareness
Use strong passwords.
Consistently communicate the importance of staff caution when clicking on links or attachments.
Provide training and education for staff on how to be security-aware.
Highlight the responsibility of every staff member.
Let all staff know how to report concerns or suspicions.
3: Starters and leavers process
Identify the specific data, devices, and access privileges new starters need.
Adopt a controlled exit policy for leavers, including group password resetting.
Review returned devices, wipe or securely destroy data where necessary.
4: Maintenance, upgrades, and planning
Back up your data regularly.
Scan network and devices frequently for necessary upgrades and/or action any security updates from trusted software providers as they pop up on your computer (for example AVG Driver Updater).
Force password changes regularly.
Create an Emergency Response Plan in case of theft, breach, or loss.
Many businesses decide to invest in cybersecurity solutions offered by companies such as AVG Antivirus Subscription Business who provides all-in-one protection including firewalls, server security, and email protection backed up with technical support. Compare the AVG Business options here.
Suspecting a breach
As the statistics at the top of this page show, SMBs often aren’t immediately aware when a breach has occurred. Here are some warning signs to look out for:
Your network performance decreases suddenly and dramatically.
You can’t perform routine updates.
Your AVG antivirus Subscription software is disabled and you can’t re-enable it.
You are locked out of accounts.
The longer a breach goes undetected, the more information the criminals can steal and the more damage they can inflict. You must act fast to:
Confirm if your network has been compromised.
Contain the damage as much as possible.
Under GDPR, organisations operating in Europe must report a personal data breach to the relevant authority within 72 hours.
If the incident concerns data held on a mobile device, you may need to consider whether you can (or should) wipe or disable the device remotely. A step such as this might provoke staff disapproval – especially if the device is the property of an employee. If you’re unable to provide a separate work phone, writing a Bring Your Own Device (BYOD) policy is always recommended.
If you do have a BYOD policy, it should include a backup schedule to ensure your business data and your employees’ personal data (photos, contacts, etc) is protected. Read our article: Tips on implementing a Bring Your Own Device policy.
Once the mobile device is wiped, if you do have a backup, you can restore this after the data breach is resolved. And while a simple backup might not be the ideal solution, it will go some way to putting you back in the position you were in prior to the breach or theft. Don’t underestimate its importance.
Key action points for preventing a data breach at your small business:
Make sure you understand the confidentiality, integrity and availability of your business data.
Assess the infrastructure of your network – devices, cloud locations, etc – and who has access.
Take relevant security measures: ensure you have up-to-date AVG Antivirus Subscription for small businesses, redesign your security policies and protocols and train your staff.
Know the signs of a breach – dramatic changes in network performance, can’t perform routine updates, you are locked out of accounts, etc – so that you can confirm and report it as soon as possible.
from WordPress https://quicksolvo939231001.wordpress.com/2020/06/30/how-to-protect-your-small-business-from-data-breaches/
0 notes
Photo

Antivirus247help is a trusted organization for any technical support for antivirus and its updates. Experienced executives are always available on antivirus customer support phone number +1-844-284-4811 to help you. You can contact us for online technical support in case of not finding a genuine support. #antivirus, #technicalsupport, #virus, #support, #help, #tollfree, #avast, ##Norton, #avg, #quickheal, #McAfee, #Avira, #BitDefender, #system, #systemsecurity, #Kaspersky, #Webroot, #ESET, #AVG, #k7, #Guardian, #COMODO, #Vipre, #eScan, #usa, #US, #Canada, #Australia, #UK
0 notes
Link
Antivirus has been vital to use, as it protects the system from harms, but it's tech issue create an issue and to resolve that; must contact us 0800-014-8298.
#Antivirus Support Number UK#Antivirus Technical Team Support UK#Antivirus Customer Support UK#Antivirus Solution UK#Antivirus Support Contact Number UK#Antivirus Customer Care UK#Antivirus Customer Support Number UK#Kaspersky Antivirus Contact Number UK#antivirus#Kaspersky Antivirus Technical Support UK#kaspersky antivirus#antivirus support#antivirus support number#PC Support#AVG Antivirus Support#Avast Antivirus Support#Avira Antivirus Support#Bullguard Antivirus Support#Kaspersky Antivirus Support#antivirus customer service
0 notes
Text
How to Fix AVG Free Antivirus Error

For any problem with your AVG antivirus please get in touch with our tech support agents who are available at 0808-101-2159 AVG Customer Care Number UK. Our technicians have great knowledge about antivirus working and functionality and hence it becomes easy for them to handle any complicated issue in an easy manner. In addition, these technicians are working round the clock, so it becomes easy for you to call them whenever you want to.
#AVG Help Desk Number UK#AVG Customer Support Number UK#AVG Toll Free Number UK#AVG Antivirus Technical Support Number UK#AVG Technical Helpline Number UK#AVG Installation Support Number UK#AVG Setup Support Number UK#AVG Refund Support Number UK#AVG Online Chat Support UK#AVG Tech Support Number UK
0 notes
Text
AVG Technical Support Number UK
PCs and laptops are vulnerable to viruses, malware and ransom ware. To protect them we need an antivirus to be installed, AVG is a reliable antivirus but still it has technical loop holes and we have to solve them to make our computer work smoothly with speed. If you are unable to resolve such technical issues yourselves then contact our skillful technicians at AVG Contact Number UK 0808-281-8685. Our technician will give you instant technical support to prevent your device. Our service is fast, reliable and effective.
#AVG Help number UK#AVG Support helpline number UK#AVG customer service contact number UK#AVG Antivirus Help Number UK
0 notes
Text
How to protect your small business from data breaches
Cyberattack vs. data breach: what’s the difference?
A cyberattack is simply a digital attack on computer systems, networks, devices, and/or applications. The objective is usually to disable computer systems or steal data. Attackers can use a variety of tools and techniques to achieve their goals, including phishing emails, ransomware, viruses, and denial-of-service attacks. A data breach is one potential consequence of a successful cyberattack. The types of data they are looking for could be passwords, email addresses, personal information, or financial information.
Threats
The following statistics paint a vivid picture of the threats to SMB data:
52% of small businesses experienced cybersecurity breaches in the past year.
Cybersecurity breaches cost UK businesses approximately £30 billion in 2016.
60% of small firms don’t know the source of the most disruptive cybersecurity breach or attack in the last twelve months.
Across the globe, just under 5 million records a day are compromised through a data breach.
On average, it takes 120 days for a business to discover a data breach.
In summary, data breaches are common, often go undetected at first, and can cost businesses – who don’t know how to protect themselves - thousands.
What is a data breach?
What can SMBs do to protect themselves?
Putting a cost-effective cybersecurity strategy in place can help to better protect you further down the line.
Strategy Step 1: Understand the elements of proper data protection
The first step in creating a cybersecurity strategy is to truly understand what is meant by ‘data protection’. Think of it in terms of the CIA acronym:
Confidentiality
Integrity
Availability.
This means your data needs to be kept confidential. It should only be available to people with relevant privileges. Your data should maintain its integrity and be in the format the user requires it to be (and not to have been materially altered by the system capturing, storing, or transmitting it.) Finally, your data should be available whenever the person with those relevant privileges is requesting it.
Strategy Step 2: Assess
The first step in assessing your customers’ potential vulnerabilities is to identify all the physical and virtual computing devices within the organization. Together with your client, make a list that includes all of them:
• Workstations and laptops• Network file servers• Network application servers• Corporate firewalls and switches• Multi-function printers• Mobile devices.
This infrastructure assessment should distinguish between cloud and on-premise systems and devices. This makes it easier for you to determine all possible storage locations for data. The number one threat to devices is a hybrid ransomware attack. For people, it’s targeted social engineering.
Now, categorize all business data and divide it into three locations: cloud,on-premise systems, and devices. For example:
• Cloud On-premise systems Devices• Cloud email and applications• Cloud storage• Websites and social media• Databases• Company-wide file sharing and storage• Intellectual property• Presentations• Company memos• Statistics and reports.
Read our white paper on the three essential components of managed security services.
Strategy Step 3: Identify relevant security measures
Once you’ve assessed what data is important to your business, where it resides, and who has access to it, you can determine the relevant security measures you should adopt. These may include:
Purchasing tools (for example, AVG antivirus Subscription for small businesses).
Redesigning your security protocols.
A wholesale change in your business’s attitude towards data security.
Training for all members of staff.
Data protection must be discussed and supported at every level within your business. It is as critical for senior executives as it is for junior team members, all of whom will have access to sensitive data of some kind. Take the time to review what data they may handle, and put the relevant measures in place.
Steps for protecting data
There are plenty of good security measures all businesses can apply today that will help prevent or reduce the chances of data loss, breach, or theft. These tools and solutions come in many shapes and sizes, but all have a role to play in protecting your sensitive and private data.
1: The basics
Install firewalls
Install AVG antivirus Subscription
Install encryption software.
2: Staff awareness
Use strong passwords.
Consistently communicate the importance of staff caution when clicking on links or attachments.
Provide training and education for staff on how to be security-aware.
Highlight the responsibility of every staff member.
Let all staff know how to report concerns or suspicions.
3: Starters and leavers process
Identify the specific data, devices, and access privileges new starters need.
Adopt a controlled exit policy for leavers, including group password resetting.
Review returned devices, wipe or securely destroy data where necessary.
4: Maintenance, upgrades, and planning
Back up your data regularly.
Scan network and devices frequently for necessary upgrades and/or action any security updates from trusted software providers as they pop up on your computer (for example AVG Driver Updater).
Force password changes regularly.
Create an Emergency Response Plan in case of theft, breach, or loss.
Many businesses decide to invest in cybersecurity solutions offered by companies such as AVG Antivirus Subscription Business who provides all-in-one protection including firewalls, server security, and email protection backed up with technical support. Compare the AVG Business options here.
Suspecting a breach
As the statistics at the top of this page show, SMBs often aren’t immediately aware when a breach has occurred. Here are some warning signs to look out for:
Your network performance decreases suddenly and dramatically.
You can’t perform routine updates.
Your AVG antivirus Subscription software is disabled and you can’t re-enable it.
You are locked out of accounts.
The longer a breach goes undetected, the more information the criminals can steal and the more damage they can inflict. You must act fast to:
Confirm if your network has been compromised.
Contain the damage as much as possible.
Under GDPR, organisations operating in Europe must report a personal data breach to the relevant authority within 72 hours.
If the incident concerns data held on a mobile device, you may need to consider whether you can (or should) wipe or disable the device remotely. A step such as this might provoke staff disapproval - especially if the device is the property of an employee. If you’re unable to provide a separate work phone, writing a Bring Your Own Device (BYOD) policy is always recommended.
If you do have a BYOD policy, it should include a backup schedule to ensure your business data and your employees’ personal data (photos, contacts, etc) is protected. Read our article: Tips on implementing a Bring Your Own Device policy.
Once the mobile device is wiped, if you do have a backup, you can restore this after the data breach is resolved. And while a simple backup might not be the ideal solution, it will go some way to putting you back in the position you were in prior to the breach or theft. Don’t underestimate its importance.
Key action points for preventing a data breach at your small business:
Make sure you understand the confidentiality, integrity and availability of your business data.
Assess the infrastructure of your network - devices, cloud locations, etc - and who has access.
Take relevant security measures: ensure you have up-to-date AVG Antivirus Subscription for small businesses, redesign your security policies and protocols and train your staff.
Know the signs of a breach - dramatic changes in network performance, can’t perform routine updates, you are locked out of accounts, etc - so that you can confirm and report it as soon as possible.
via Blogger https://ift.tt/3g9ozG8
0 notes
Text
Steps to follow after AVG installation
If you want to protect your Windows, Macs and Android devices, then your first answer should be AVG Antivirus. This software is specifically developed to provide the user with such excellent attributes as it an ideal choice for them over time.
This software could be downloaded from the official website for free. This antivirus program provides outstanding affordability and flexibility with its amazing and devastating features. This software is an excellent and ideal match for personal computer users.
Today, it is extremely important to protect your PC from viruses and hacking in the internet prominent world that we work in. AVG brings free as well as a paid version to protect your device from virus, rootkits, spyware, and threats.
More and more users around the world prefer to use free AVG editions to ensure the safety of their personal computers. To enjoy the benefits of AVG, it is essential to install it on your PC. The AVG Installation process is very user-friendly and simple.
With a few clicks, the installation process is completed. The free AVG provides for free upgrades and convenient access to the latest attributes with its official websites. In this blog, we will discuss the installation process and the post-installation process of AVG.
Before installation, make sure that, your device does not have third-party software. If available then, remove the existing software with the help of AVG Removal Tool.
To install AVG software, follow these steps:
Go to AVG official website and find download section and then click the ‘Free Download’ box.
After downloading the software, click on the run box to start the installation. You can also find the downloading file in your download folder and then double click the application.
When the installation begins, choose the language whichever you want to choose and then select ‘Next’.
After that, read the license agreement of software and then understand the terms and click ‘Accept’ to continue the installation process.
Then, a license box appears automatically in which you need to fill your license number. Just click ‘next’ to proceed.
Further, select the custom install option, switch with default path and then click next to continue along with installation.
In the next installation component, you may either deselect the ‘Additional installed Languages’ or can just click next to proceed.
Click on ‘Finish’ to get the installation done.
These steps will make you easy to install the AVG on your device. Hold on, now you need to set up the features, update and configure the software.
Follow these steps for Post Installation Setup:
After installation is completed, the AVG menu will appear and provide you the options of scanning the system. We have to click the select option that is available on the top right corner and then click on ‘Advanced Settings’.
Here, you will need to select the ‘Virus Vault’ that appears on the left corner under the ‘Update’. Increase the size of the vault to 20% and after you are finished, press ‘Apply’ that is available on the bottom right corner.
After that, click on ‘Update’ on the left side of the application and then deselect ‘Start Memory and process scan further a successful update’. Again, click on ‘Apply’ box in the right corner when you have done.
Click on ‘Identity Protection’ on the left corner and choose the ‘Automatically quarantine detected threats’ box. Press ‘Apply’ from the same, right corner.
Now, finally, click on the ‘Appearance’ option that is available on the top left corner. Deselect both ‘AVG Advisor notifications’ and ‘Boot time improvement’ and then click on Apply.
Now, you have installed and completely configured the AVG Antivirus to protect your PC from threats that may attack from outside and maintains maximum efficiency and speed of the system.
If you have any queries against AVG or if you are facing any problem while installing or updating antivirus, then directly connected with the experts with just a call on AVG Support Number UK. The team will help you to figure out the reason for that issue and provide proper guidance to troubleshoot the issue.
Source URL: https://medium.com/@ellietaylor706/steps-to-follow-after-avg-installation-d36959f6dfcd
#install avg free for windows 7#avg antivirus not installing#avg not installing on windows 10#AVG Technical Number UK#AVG Toll free number UK#AVG Support Number UK
0 notes
Text
Call phone number UK when you need assistance
If you live or perhaps reside in great britain and its nearby environs, you can easily contact AVG. how is that? Via the avg phone number UK, it is possible to contact the company and also communicate all you could wish for or perhaps want. Specialized expertise is among the benefits a person stand to acquire where building success out out of these companies is concerned. Remember to find true worth in these solutions. That is a very important factor you need to be considering. You need to constantly make the right decisions. When such decisions are created you never, arrive at struggle. It's important for you to hold the right number to these specialists. That will help you receive all the help you'll need. There are times when you could be facing several issues with the software and its protection. If you have such problems, you need to contact avg customer service. Whenever you contact them, you get to benefit from everything they have to offer. That is one thing you should never get lightly. It is crucial that the right degree of technical experience is put set up. This will provide you with all you need and that's important. AVG antivirus will always have removal of malicious viruses from your devices. There are many ways that infections get into your devices. This means you need to have these sorted out as you can. Remember, there'll always be a way out there for you to possess total independence from this kind of viruses. AVG ensures of that. Using the finest speak support system, it is possible to communicate with personnel as if you are just standing just before them. That is a benefit you need to itch to possess. Most online companies do not have this kind of unique advantages. That doesn’t suggest you should negotiate with something that isn’t up to the proper standard for you personally. With avg help number UK, you may always have a great time. When you phone avg help number UK, you are able to have the right guidance regarding these types of apps and systems. With the right information obtained, nothing could be taken for granted. You'll have every decision met because it is required or necessitated. With all the tips and advice you're given, you can have all problems handled yourself down the road. The complex experiences that these call center agents have to offer you'll amaze you. Remember, there'll always be a reason to call avg client service. Make sure you are getting the right help you need whenever you call. That isn’t always good for you to face challenges. However, any time these difficulties come you will need some help to take care of them. So make sure of in which. With avg help number UK, you will always have a good time. For more information check out bestsupportnumbers.co.uk/support-for-avg.
0 notes
Text
How to protect your small business from data breaches
Cyberattack vs. data breach: what’s the difference?
A cyberattack is simply a digital attack on computer systems, networks, devices, and/or applications. The objective is usually to disable computer systems or steal data. Attackers can use a variety of tools and techniques to achieve their goals, including phishing emails, ransomware, viruses, and denial-of-service attacks. A data breach is one potential consequence of a successful cyberattack. The types of data they are looking for could be passwords, email addresses, personal information, or financial information.
Threats
The following statistics paint a vivid picture of the threats to SMB data:
52% of small businesses experienced cybersecurity breaches in the past year.
Cybersecurity breaches cost UK businesses approximately £30 billion in 2016.
60% of small firms don’t know the source of the most disruptive cybersecurity breach or attack in the last twelve months.
Across the globe, just under 5 million records a day are compromised through a data breach.
On average, it takes 120 days for a business to discover a data breach.
In summary, data breaches are common, often go undetected at first, and can cost businesses – who don’t know how to protect themselves - thousands.
What is a data breach?
What can SMBs do to protect themselves?
Putting a cost-effective cybersecurity strategy in place can help to better protect you further down the line.
Strategy Step 1: Understand the elements of proper data protection
The first step in creating a cybersecurity strategy is to truly understand what is meant by ‘data protection’. Think of it in terms of the CIA acronym:
Confidentiality
Integrity
Availability.
This means your data needs to be kept confidential. It should only be available to people with relevant privileges. Your data should maintain its integrity and be in the format the user requires it to be (and not to have been materially altered by the system capturing, storing, or transmitting it.) Finally, your data should be available whenever the person with those relevant privileges is requesting it.
Strategy Step 2: Assess
The first step in assessing your customers’ potential vulnerabilities is to identify all the physical and virtual computing devices within the organization. Together with your client, make a list that includes all of them:
• Workstations and laptops• Network file servers• Network application servers• Corporate firewalls and switches• Multi-function printers• Mobile devices.
This infrastructure assessment should distinguish between cloud and on-premise systems and devices. This makes it easier for you to determine all possible storage locations for data. The number one threat to devices is a hybrid ransomware attack. For people, it’s targeted social engineering.
Now, categorize all business data and divide it into three locations: cloud,on-premise systems, and devices. For example:
• Cloud On-premise systems Devices• Cloud email and applications• Cloud storage• Websites and social media• Databases• Company-wide file sharing and storage• Intellectual property• Presentations• Company memos• Statistics and reports.
Read our white paper on the three essential components of managed security services.
Strategy Step 3: Identify relevant security measures
Once you’ve assessed what data is important to your business, where it resides, and who has access to it, you can determine the relevant security measures you should adopt. These may include:
Purchasing tools (for example, AVG antivirus Subscription for small businesses).
Redesigning your security protocols.
A wholesale change in your business’s attitude towards data security.
Training for all members of staff.
Data protection must be discussed and supported at every level within your business. It is as critical for senior executives as it is for junior team members, all of whom will have access to sensitive data of some kind. Take the time to review what data they may handle, and put the relevant measures in place.
Steps for protecting data
There are plenty of good security measures all businesses can apply today that will help prevent or reduce the chances of data loss, breach, or theft. These tools and solutions come in many shapes and sizes, but all have a role to play in protecting your sensitive and private data.
1: The basics
Install firewalls
Install AVG antivirus Subscription
Install encryption software.
2: Staff awareness
Use strong passwords.
Consistently communicate the importance of staff caution when clicking on links or attachments.
Provide training and education for staff on how to be security-aware.
Highlight the responsibility of every staff member.
Let all staff know how to report concerns or suspicions.
3: Starters and leavers process
Identify the specific data, devices, and access privileges new starters need.
Adopt a controlled exit policy for leavers, including group password resetting.
Review returned devices, wipe or securely destroy data where necessary.
4: Maintenance, upgrades, and planning
Back up your data regularly.
Scan network and devices frequently for necessary upgrades and/or action any security updates from trusted software providers as they pop up on your computer (for example AVG Driver Updater).
Force password changes regularly.
Create an Emergency Response Plan in case of theft, breach, or loss.
Many businesses decide to invest in cybersecurity solutions offered by companies such as AVG Antivirus Subscription Business who provides all-in-one protection including firewalls, server security, and email protection backed up with technical support. Compare the AVG Business options here.
Suspecting a breach
As the statistics at the top of this page show, SMBs often aren’t immediately aware when a breach has occurred. Here are some warning signs to look out for:
Your network performance decreases suddenly and dramatically.
You can’t perform routine updates.
Your AVG antivirus Subscription software is disabled and you can’t re-enable it.
You are locked out of accounts.
The longer a breach goes undetected, the more information the criminals can steal and the more damage they can inflict. You must act fast to:
Confirm if your network has been compromised.
Contain the damage as much as possible.
Under GDPR, organisations operating in Europe must report a personal data breach to the relevant authority within 72 hours.
If the incident concerns data held on a mobile device, you may need to consider whether you can (or should) wipe or disable the device remotely. A step such as this might provoke staff disapproval - especially if the device is the property of an employee. If you’re unable to provide a separate work phone, writing a Bring Your Own Device (BYOD) policy is always recommended.
If you do have a BYOD policy, it should include a backup schedule to ensure your business data and your employees’ personal data (photos, contacts, etc) is protected. Read our article: Tips on implementing a Bring Your Own Device policy.
Once the mobile device is wiped, if you do have a backup, you can restore this after the data breach is resolved. And while a simple backup might not be the ideal solution, it will go some way to putting you back in the position you were in prior to the breach or theft. Don’t underestimate its importance.
Key action points for preventing a data breach at your small business:
Make sure you understand the confidentiality, integrity and availability of your business data.
Assess the infrastructure of your network - devices, cloud locations, etc - and who has access.
Take relevant security measures: ensure you have up-to-date AVG Antivirus Subscription for small businesses, redesign your security policies and protocols and train your staff.
Know the signs of a breach - dramatic changes in network performance, can’t perform routine updates, you are locked out of accounts, etc - so that you can confirm and report it as soon as possible.
via Blogger https://ift.tt/2ZkcOpL
0 notes
Link
The AVG Support is also having chat support at all days and at all times. This would enable customer to have easy assistance without any waiting time. Such assistance is provided through remote service at AVG Helpline Number UK.
#AVG Support UK#AVG Help Number UK#AVG Support Number UK#AVG Helpline Number UK#AVG Contact Number UK
0 notes
Text
AVG customer care phone number
If you want to free yourself from regular tension due to AVG antivirus then it’s time to make a call at 0808-101-2159 AVG Support Number UK. You will be able to communicate with best technicians from all over the world and get solution for your problem from them. This is a 24 hour service; hence you don’t have to wait for anything. You can make us a call at your convenient time.
#AVG Help Desk Number UK#AVG Customer Support Number UK#AVG Antivirus Technical Support Number UK#AVG Technical Helpline Number UK#AVG Online Chat Support UK#AVG Tech Support Number UK
0 notes
Text
How to protect your small business from data breaches
Cyberattack vs. data breach: what’s the difference?
A cyberattack is simply a digital attack on computer systems, networks, devices, and/or applications. The objective is usually to disable computer systems or steal data. Attackers can use a variety of tools and techniques to achieve their goals, including phishing emails, ransomware, viruses, and denial-of-service attacks. A data breach is one potential consequence of a successful cyberattack. The types of data they are looking for could be passwords, email addresses, personal information, or financial information.
Threats
The following statistics paint a vivid picture of the threats to SMB data:
52% of small businesses experienced cybersecurity breaches in the past year.
Cybersecurity breaches cost UK businesses approximately £30 billion in 2016.
60% of small firms don’t know the source of the most disruptive cybersecurity breach or attack in the last twelve months.
Across the globe, just under 5 million records a day are compromised through a data breach.
On average, it takes 120 days for a business to discover a data breach.
In summary, data breaches are common, often go undetected at first, and can cost businesses – who don’t know how to protect themselves - thousands.
What is a data breach?
What can SMBs do to protect themselves?
Putting a cost-effective cybersecurity strategy in place can help to better protect you further down the line.
Strategy Step 1: Understand the elements of proper data protection
The first step in creating a cybersecurity strategy is to truly understand what is meant by ‘data protection’. Think of it in terms of the CIA acronym:
Confidentiality
Integrity
Availability.
This means your data needs to be kept confidential. It should only be available to people with relevant privileges. Your data should maintain its integrity and be in the format the user requires it to be (and not to have been materially altered by the system capturing, storing, or transmitting it.) Finally, your data should be available whenever the person with those relevant privileges is requesting it.
Strategy Step 2: Assess
The first step in assessing your customers’ potential vulnerabilities is to identify all the physical and virtual computing devices within the organization. Together with your client, make a list that includes all of them:
• Workstations and laptops• Network file servers• Network application servers• Corporate firewalls and switches• Multi-function printers• Mobile devices.
This infrastructure assessment should distinguish between cloud and on-premise systems and devices. This makes it easier for you to determine all possible storage locations for data. The number one threat to devices is a hybrid ransomware attack. For people, it’s targeted social engineering.
Now, categorize all business data and divide it into three locations: cloud,on-premise systems, and devices. For example:
• Cloud On-premise systems Devices• Cloud email and applications• Cloud storage• Websites and social media• Databases• Company-wide file sharing and storage• Intellectual property• Presentations• Company memos• Statistics and reports.
Read our white paper on the three essential components of managed security services.
Strategy Step 3: Identify relevant security measures
Once you’ve assessed what data is important to your business, where it resides, and who has access to it, you can determine the relevant security measures you should adopt. These may include:
Purchasing tools (for example, AVG antivirus Subscription for small businesses).
Redesigning your security protocols.
A wholesale change in your business’s attitude towards data security.
Training for all members of staff.
Data protection must be discussed and supported at every level within your business. It is as critical for senior executives as it is for junior team members, all of whom will have access to sensitive data of some kind. Take the time to review what data they may handle, and put the relevant measures in place.
Steps for protecting data
There are plenty of good security measures all businesses can apply today that will help prevent or reduce the chances of data loss, breach, or theft. These tools and solutions come in many shapes and sizes, but all have a role to play in protecting your sensitive and private data.
1: The basics
Install firewalls
Install AVG antivirus Subscription
Install encryption software.
2: Staff awareness
Use strong passwords.
Consistently communicate the importance of staff caution when clicking on links or attachments.
Provide training and education for staff on how to be security-aware.
Highlight the responsibility of every staff member.
Let all staff know how to report concerns or suspicions.
3: Starters and leavers process
Identify the specific data, devices, and access privileges new starters need.
Adopt a controlled exit policy for leavers, including group password resetting.
Review returned devices, wipe or securely destroy data where necessary.
4: Maintenance, upgrades, and planning
Back up your data regularly.
Scan network and devices frequently for necessary upgrades and/or action any security updates from trusted software providers as they pop up on your computer (for example AVG Driver Updater).
Force password changes regularly.
Create an Emergency Response Plan in case of theft, breach, or loss.
Many businesses decide to invest in cybersecurity solutions offered by companies such as AVG Antivirus Subscription Business who provides all-in-one protection including firewalls, server security, and email protection backed up with technical support. Compare the AVG Business options here.
Suspecting a breach
As the statistics at the top of this page show, SMBs often aren’t immediately aware when a breach has occurred. Here are some warning signs to look out for:
Your network performance decreases suddenly and dramatically.
You can’t perform routine updates.
Your AVG antivirus Subscription software is disabled and you can’t re-enable it.
You are locked out of accounts.
The longer a breach goes undetected, the more information the criminals can steal and the more damage they can inflict. You must act fast to:
Confirm if your network has been compromised.
Contain the damage as much as possible.
Under GDPR, organisations operating in Europe must report a personal data breach to the relevant authority within 72 hours.
If the incident concerns data held on a mobile device, you may need to consider whether you can (or should) wipe or disable the device remotely. A step such as this might provoke staff disapproval - especially if the device is the property of an employee. If you’re unable to provide a separate work phone, writing a Bring Your Own Device (BYOD) policy is always recommended.
If you do have a BYOD policy, it should include a backup schedule to ensure your business data and your employees’ personal data (photos, contacts, etc) is protected. Read our article: Tips on implementing a Bring Your Own Device policy.
Once the mobile device is wiped, if you do have a backup, you can restore this after the data breach is resolved. And while a simple backup might not be the ideal solution, it will go some way to putting you back in the position you were in prior to the breach or theft. Don’t underestimate its importance.
Key action points for preventing a data breach at your small business:
Make sure you understand the confidentiality, integrity and availability of your business data.
Assess the infrastructure of your network - devices, cloud locations, etc - and who has access.
Take relevant security measures: ensure you have up-to-date AVG Antivirus Subscription for small businesses, redesign your security policies and protocols and train your staff.
Know the signs of a breach - dramatic changes in network performance, can’t perform routine updates, you are locked out of accounts, etc - so that you can confirm and report it as soon as possible.
from Blogger http://quicksolvocom.blogspot.com/2020/06/how-to-protect-your-small-business-from.html
0 notes
Text
www.avg.com/download

https://www.install-avg.com/Login/
www.avg.com/download-Having trouble with AVG Activate Enter Code online ? We are here to fix your AVG Activation and installation issues online by Live Chat or Call.
Welcome to
www.avg.com/download
Website
Support for AVG Antivirus
Call USA/Canada Toll Free
Instant Support 1–844–833–0610
UK technical support- 020–3890–3474
Installs in moments. Protects forever.
This antivirus program is so light and easy to install, you and your family will be protected in just moments. It’ll then keep protecting you day and night, automatically updating itself against the latest threats to help keep you and your family safe.
Install AVG-Download and Install your AVG Online
Where to seek out AVG License Key? The AVG security package is simple to setup & install. Simply find alpha-numeric code that is written on the backside of the retail card. Here may be a sample Product Key to let you understand: xxxxx-xxxxx-xxxxx-xxxxx-xxxxx-xxxxx
Start Setup to Activate and Install Your Product.
avg.com/retail
Register www.avg.com/retail and Install AVG Security on-line
Today life is not possible without Internet every person use internet these days no matter what’s the age of person. They are accessing internet for gather information, stock update, playing games, watching movies, making money and many more.
When you surfing on internet virus automatically download in your device and sometime you connect infected device in your system then virus is enter in your device. When virus enter in your device you are facing too much problem and computer doing very unusual activity, you lose your important data and many other problem. If you want your computer virus free you have to buy one good antivirus for your device. AVG antivirus is the best protector for your device from all type of virus, threat, malware. AVG is the World best antivirus these days. AVG antivirus is user friendly and is easy to install and download. AVG provide the best support for their customers they are working 24/7. We have best certified experts to solve your problem.
avg.com/retail gives best support to their customers. AVG antivirus detect virus, malware from your computer automatically and you can also schedule a daily or weekly scan of your device. When you start your computer its start automatically and remove the virus this software just show you the popup, virus is detect in your computer and already removed.
Continual Updates can be done on the website avg.com/retail
Most Basic Problems you face
Our Labs set the standards to be followed for the compliance of commercial security products.
Software Installation Problems
Unable to Access Some Application After Installation
AVG Antivirus Not Working
Can’t Uninstall AVG
Discrepancy in PC Performance After Installation
Conflicts your Registry
Update/ Upgrade Issues
Compatibility Problems of AVG with other Programs
Activate avg Product
Manage avg Setup
If you face any problem during installing, downloading or any other problem you can call us any time.
If you face any problem during AVG setup, installing, downloading or any other problem please call +1–844–833–0610.
0 notes