#AVG Installation Support Number UK
Explore tagged Tumblr posts
Link

#AVG Customer Service Number UK#AVG Help Desk Number UK#AVG Customer Support Number UK#AVG Technical Helpline Number UK#AVG Refund Support Number UK#AVG Installation Support Number UK
0 notes
Text
What do I fix 'AVG updating issue'?
For any computer security setup, anti-virus is a crucial part that will protect your system from malware, spyware, and virus. AVG supports to keep a network secure and safe from cyber threats and makes your company and employees able to access the internet safely and securely. It not only detects the malware, ransom-ware and virus but also removes them from your system.
It is more important to update anti-virus utilities that software as it is only as good as its latest update. Having a recent update of AVG will spot new threats and dangers from the Web. If you want to know more about AVG then contact at AVG Support Number UK.
AVG offers an automatic option for the update that can be updated without any issue. But, sometimes it refuses to update on your device. Or, an error appears on your screen ‘AVG fails to update’ when you start the process of updating. It creates big trouble for you as it stops working with the older version.
Causes of failure update of AVG are listed below:
Third-party Software: If your device has more than one anti-virus software programs installed at the same time then the security programs interact with your system on a basic level. In that case, make sure that your device has only one anti-virus tool on your system.
Malware Problem: Update failure also causes if malware has trapped your system. It restricts the updating process in order to remain undetected. For this, it is advisable to remove it from your device. Then re-install AVG software and try to update it again.
Software Problem: Sometimes, the problem is with the AVG software program itself instead of anything external. In that case, uninstall the AVG Antivirus completely from your device by clicking on the link, ‘Uninstall a program’ that is available in Control Panel. After that, reinstall it using an updated version from the official website of AVG.
Device Problem: AVG update failure also happens due to your device setting as the device is not permitted to access the new program due to security purposes. In that case, the user needs to change the device setting and allows it to make changes with the latest version.
Apart from these reasons, the intermittent or unstable Internet connection can also restrict AVG antivirus software to apply the latest update. For that, it is recommended to check the internet connection and try to update again.
Also, you will need to delete some temporary files that are used during the update. Let’s talk about some steps to delete them:
Double click on the AVG icon that is available on your desktop.
Then, open the ‘Options’ to go to ‘Advanced Settings.
Now, navigate to the option ‘Manage’ that you will find in the ‘Update branch’.
Select the option ‘Delete temporary update files’.
And at last, try to update AVG.
After executing these processes, the update failure issue will be easily resolved. In case, the problem still persists, it is advisable to take the support of AVG Helpline Number UK.
Source Url: http://avg-support.over-blog.com/2019/06/what-do-i-fix-avg-updating-issue.html
#AVG Support Number UK#AVG Help Number UK#AVG Contact Number UK#avg internet security serial key#avg internet security#AVG Login Error
1 note
·
View note
Text
Pvsyst Keygen Free Download
PVsyst is able to import meteo data from many different sources, as well as personal data. 'There are so many several solar PV system simulation programs in the market for commercial and free version. PVsyst is the most accurate program in Market with accepted by Institute of Finance Corporation, a member of World Bank Group. Where is the keygen? (PVSyst) Free Download. General features G rid-connected systems Download PVsyst 6.35 (March 24, 2015) Link to. https://csfox933.tumblr.com/post/654148191600672768/usb-dect-driver. Jul 05, 2018 Trusted Windows (PC) download PVsyst 6.40. Virus-free and 100% clean download. Get PVsyst alternative downloads.
Sample Results From Member Downloads
Download NameDate AddedSpeedPvsyst 513-Dec-20202,164 KB/sPvsyst 5 Download13-Dec-20202,856 KB/sPvsyst 5 Crack12-Dec-20202,869 KB/sPvsyst 5 Unlock Key09-Dec-20202,897 KB/sPvsyst 5 Torrent09-Dec-20202,549 KB/sPvsyst.5.Complete.rar07-Dec-20202,132 KB/s(FULL) Pvsyst 504-Dec-20202,142 KB/s
To create more accurate search results for Pvsyst 5 try to exclude using commonly used keywords such as: crack, download, serial, keygen, torrent, warez, etc. Simplifying your search should return more download results. Many downloads like Pvsyst 5 may also include a crack, serial number, unlock code, cd key or keygen (key generator). If this is the case it is usually found in the full download archive itself.
Welcome To FileFixation.com
FileFixation.com is a new file sharing web service which gives you access to literally hundreds of thousands of direct downloads including software, games, movies, tv shows, mp3 albums, ebooks and more! Our downloads database is updated daily to provide the latest download releases on offer. To celebrate our launch we are offering unlimited full download access for FREE! This is a limited offer and will soon expire and revert back to the normal member price. We now have 431,315 downloads in the member section. Take the FileFixation tour now for more detailed information!
What is a Crack?
The word 'crack' in this context means the action of removing the copy protection from commercial software. A crack is a set of instructions or patch used to remove copy protection from a piece of software or to unlock features from a demo or time-limited trial. There are crack groups who work together in order to crack software, games, etc. If you search for Pvsyst 5 Crack, you will often see the word 'crack' amongst the results which means it is the full version of the product.
What is a Serial?
Pvsyst Keygen Free Download Microsoft Office 2010
The word 'serial' means a unique number which identifies the license of the software as being valid. All retail software uses a serial number or key of some form. The installation often requires the user to enter a valid serial number to proceed. A serial can also be referred to as a 'CD Key'. When you search for Pvsyst 5 Serial for example, you may find the word 'serial' amongst the results. This usually means your software download includes a serial number of some sort.
What is a Keygen?
The word 'keygen' means a small program that can generate a cd key, activation number, license code, serial number, or registration number for a piece of software. KeyGen is a shortened word for Key Generator. A keygen is made available through crack groups free to download. When writing a keygen, the author will identify the algorithm used in creating a valid cd key. Once the algorithm is identified they can then incorporate this into the keygen. If you search a download site for Pvsyst 5 Keygen, this often means your download includes a keygen.
Popular Download Searches
Pvsyst 5, Avg 8.5 Full, Production Bundle, AutoCAD Architecture Uk, Agisoft Photoscan Professional 1.3.2.4164 Multilin, Canon Resetter 1980, Envie 4.5, Digital Paint, Japanese Mom And Son, Glee Project, Cheat Engine 6.5.1, Winrar 4.1.0.0, Networks Magic 5, Batbabe The Dark Nightie 2009 DVDrip Xvid Fico, We Have Always Lived In The Castle 2019 720p Web, Kaiser Chiefs, Chocolatier Montre Ravel Repliquemontre Me, Apple Mobiles And IPhone 4, Sony Vegas Movie Studio Hd Platinum 10.0,
( Home | Signup | Take A Tour | FAQ | Testimonials | Support | Terms & Conditions | Legal & Content Removal ) Design and Layout © 2020 FileFixation. All rights reserved.
Saturday, April 4, 2015
Free Keygens Downloads
Solar System Design Software (PVSyst) Free Download
Download PVsyst 6.35(March 24, 2015)
Link to previous PVsyst6 versions
Management of the project
For a given project (a defined site and meteo), you can construct several variations for your system (“calculation versions”).
System design board
The system design is based on a quick and simple procedure:
Specify the desired power or available area
Choose the inverter from the internal database
Pvsyst Keygen Free Download Camtasia
… and PVsyst will propose an array/system configuration, that allows you to conduct a preliminary simulation.
System sizing: Visual tool
Pvsyst Software Free Training
A specific tool gathers all constraints for the sizing of the system:
Pvsyst Keygen Free Download Windows 7

For the number of modules in a series: the upper diagram shows the I/V curve of the PV array, together with the MPPT range, voltage, power, and current limits of the inverter.
Pvsyst 6
For the inverter sizing: the second graph displays the annual distribution of the array power, with the array and inverter nominal power
The optimal sizing of the inverter is based on the acceptable overload loss throughout the year. It usually leads to over-size the power ratio (array nominal power by respect to the inverter nom. AC power), by a factor of 1.25.
After a good system sizing, you can define different losses like far and near shadings using a full 3D editor for the definition of the environmental and near shading conditions.
Specialized tools are also provided for the evaluation of the wiring losses (and other losses like the module quality), the mismatch between modules, soiling, thermal behavior according to the mechanical mounting, system unavailability, etc.
Simulation and results report
The simulation calculates the distribution of energies throughout the year.
Main results:
1. The total energy production (MWh/y) is essential for the evaluation of the PV system's profitability.
2. The Performance Ratio (PR (%)) describes the quality of the system itself.
3. The specific energy (kWh/kWp) is an indicator of production based on the available irradiation (location and orientation).
Shows the main energies and gains/losses involved in the simulation,
Powerful tool for a quick analysis of the system's behavior, and potential improvements in the design.
0 notes
Text
How to protect your small business from data breaches
Cyberattack vs. data breach: what’s the difference?
A cyberattack is simply a digital attack on computer systems, networks, devices, and/or applications. The objective is usually to disable computer systems or steal data. Attackers can use a variety of tools and techniques to achieve their goals, including phishing emails, ransomware, viruses, and denial-of-service attacks. A data breach is one potential consequence of a successful cyberattack. The types of data they are looking for could be passwords, email addresses, personal information, or financial information.
Threats
The following statistics paint a vivid picture of the threats to SMB data:
52% of small businesses experienced cybersecurity breaches in the past year.
Cybersecurity breaches cost UK businesses approximately £30 billion in 2016.
60% of small firms don’t know the source of the most disruptive cybersecurity breach or attack in the last twelve months.
Across the globe, just under 5 million records a day are compromised through a data breach.
On average, it takes 120 days for a business to discover a data breach.
In summary, data breaches are common, often go undetected at first, and can cost businesses – who don’t know how to protect themselves – thousands.
What is a data breach?
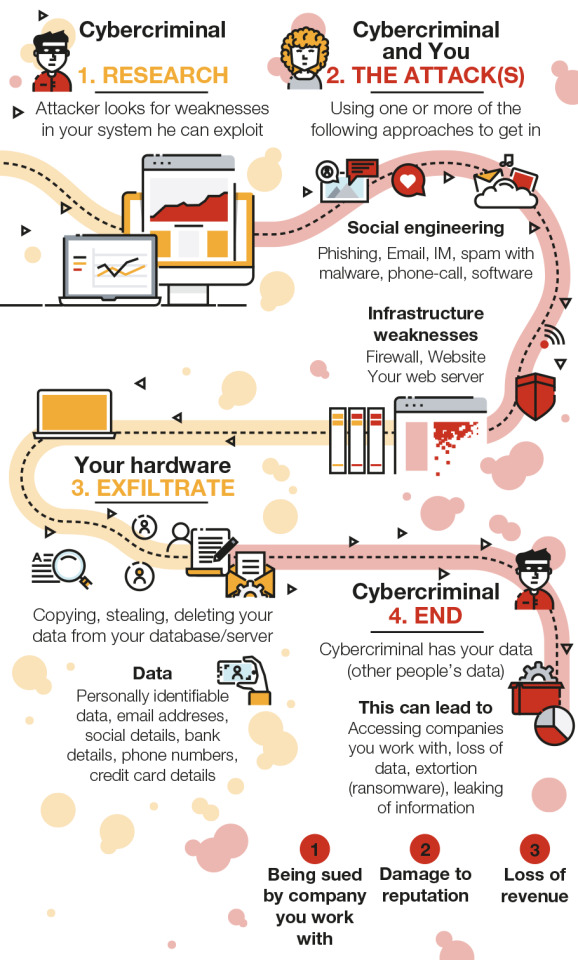
What can SMBs do to protect themselves?
Putting a cost-effective cybersecurity strategy in place can help to better protect you further down the line.
Strategy Step 1: Understand the elements of proper data protection
The first step in creating a cybersecurity strategy is to truly understand what is meant by ‘data protection’. Think of it in terms of the CIA acronym:
Confidentiality
Integrity
Availability.
This means your data needs to be kept confidential. It should only be available to people with relevant privileges. Your data should maintain its integrity and be in the format the user requires it to be (and not to have been materially altered by the system capturing, storing, or transmitting it.) Finally, your data should be available whenever the person with those relevant privileges is requesting it.
Strategy Step 2: Assess
The first step in assessing your customers’ potential vulnerabilities is to identify all the physical and virtual computing devices within the organization. Together with your client, make a list that includes all of them:
• Workstations and laptops• Network file servers• Network application servers• Corporate firewalls and switches• Multi-function printers• Mobile devices.
This infrastructure assessment should distinguish between cloud and on-premise systems and devices. This makes it easier for you to determine all possible storage locations for data. The number one threat to devices is a hybrid ransomware attack. For people, it’s targeted social engineering.
Now, categorize all business data and divide it into three locations: cloud,on-premise systems, and devices. For example:
• Cloud On-premise systems Devices• Cloud email and applications• Cloud storage• Websites and social media• Databases• Company-wide file sharing and storage• Intellectual property• Presentations• Company memos• Statistics and reports.
Read our white paper on the three essential components of managed security services.
Strategy Step 3: Identify relevant security measures
Once you’ve assessed what data is important to your business, where it resides, and who has access to it, you can determine the relevant security measures you should adopt. These may include:
Purchasing tools (for example, AVG antivirus Subscription for small businesses).
Redesigning your security protocols.
A wholesale change in your business’s attitude towards data security.
Training for all members of staff.
Data protection must be discussed and supported at every level within your business. It is as critical for senior executives as it is for junior team members, all of whom will have access to sensitive data of some kind. Take the time to review what data they may handle, and put the relevant measures in place.
Steps for protecting data

There are plenty of good security measures all businesses can apply today that will help prevent or reduce the chances of data loss, breach, or theft. These tools and solutions come in many shapes and sizes, but all have a role to play in protecting your sensitive and private data.
1: The basics
Install firewalls
Install AVG antivirus Subscription
Install encryption software.
2: Staff awareness
Use strong passwords.
Consistently communicate the importance of staff caution when clicking on links or attachments.
Provide training and education for staff on how to be security-aware.
Highlight the responsibility of every staff member.
Let all staff know how to report concerns or suspicions.
3: Starters and leavers process
Identify the specific data, devices, and access privileges new starters need.
Adopt a controlled exit policy for leavers, including group password resetting.
Review returned devices, wipe or securely destroy data where necessary.
4: Maintenance, upgrades, and planning
Back up your data regularly.
Scan network and devices frequently for necessary upgrades and/or action any security updates from trusted software providers as they pop up on your computer (for example AVG Driver Updater).
Force password changes regularly.
Create an Emergency Response Plan in case of theft, breach, or loss.
Many businesses decide to invest in cybersecurity solutions offered by companies such as AVG Antivirus Subscription Business who provides all-in-one protection including firewalls, server security, and email protection backed up with technical support. Compare the AVG Business options here.
Suspecting a breach
As the statistics at the top of this page show, SMBs often aren’t immediately aware when a breach has occurred. Here are some warning signs to look out for:
Your network performance decreases suddenly and dramatically.
You can’t perform routine updates.
Your AVG antivirus Subscription software is disabled and you can’t re-enable it.
You are locked out of accounts.
The longer a breach goes undetected, the more information the criminals can steal and the more damage they can inflict. You must act fast to:
Confirm if your network has been compromised.
Contain the damage as much as possible.
Under GDPR, organisations operating in Europe must report a personal data breach to the relevant authority within 72 hours.
If the incident concerns data held on a mobile device, you may need to consider whether you can (or should) wipe or disable the device remotely. A step such as this might provoke staff disapproval – especially if the device is the property of an employee. If you’re unable to provide a separate work phone, writing a Bring Your Own Device (BYOD) policy is always recommended.
If you do have a BYOD policy, it should include a backup schedule to ensure your business data and your employees’ personal data (photos, contacts, etc) is protected. Read our article: Tips on implementing a Bring Your Own Device policy.
Once the mobile device is wiped, if you do have a backup, you can restore this after the data breach is resolved. And while a simple backup might not be the ideal solution, it will go some way to putting you back in the position you were in prior to the breach or theft. Don’t underestimate its importance.
Key action points for preventing a data breach at your small business:
Make sure you understand the confidentiality, integrity and availability of your business data.
Assess the infrastructure of your network – devices, cloud locations, etc – and who has access.
Take relevant security measures: ensure you have up-to-date AVG Antivirus Subscription for small businesses, redesign your security policies and protocols and train your staff.
Know the signs of a breach – dramatic changes in network performance, can’t perform routine updates, you are locked out of accounts, etc – so that you can confirm and report it as soon as possible.
from WordPress https://quicksolvo939231001.wordpress.com/2020/06/30/how-to-protect-your-small-business-from-data-breaches/
0 notes
Text
Review Of Sony Xperia 10 : Easy To Hold, Hard To Use
Most importantly, they lack a selling point, but their super high display is certainly one of them. With it, you can watch a series of original aspect ratio movies (no black bars). You can also take photos and footage at 21:9 using your phone's camera app.
When you're living with Xperia 10, its slim scale makes it more comfortable than most other big screen devices. Most smartphones today cannot be used with one hand or anything smaller than a jacket pocket.
Sony found a way to achieve this, but the rest of the phone failed to support its most impressive features.
For the biggest criminals, its buttons are barely lifted from the frame, making them almost impossible to feel or press. The hardware is slow and the camera is miserable. After a few weeks of use, the glossy paint around the camera will break. If you want to watch a 21:9 movie, make sure you use headphones because the single bottom emission speaker is weak. It is easy and expected for a small tolerant cheap mobile phone. But when $300 can provide you with a great phone, such as the Moto G7, Sony's mistakes are obvious and cannot be ignored.
The 21:9 display is arguably the most compelling feature. The 6-inch Xperia 10 and 6.5-inch Xperia 10 Plus are equipped with a 1080p LCD display that extends to the bottom edge of the phone. Sony's phone uses a thicker baffle at the top to mount the camera and headphones instead of looking for a gap or punching the camera. It is similar to last year's Sony Xperia XZ3, except that Sony managed to remove its logo from the bottom chin bezel and replace it with more screens.
The phone in this price range looks good, but this high phone actually needs a bottom bezel to balance it. I can appreciate Sony's efforts to extend the display all the way to the bottom, but when I tried to stretch my thumb to the bottom of this huge screen, the ergonomic design of the easy-to-grip design was thrown out of the window. Whether I'm heading to the necessary navigation buttons, typing a message, or doing anything that requires me to touch the bottom of the screen, I will remind the form to select features for each turn. With a few exceptions to the fingerprint sensor, it is mounted on the side of the phone. It is slightly sunken and can be used as a guide for your fingers.
Sony seems to want ease of use to be a problem for some people, trying to mitigate it with some software features. The first one lets you capture the screen to "one-hand mode" by double-clicking the home button. This will shrink the screen to something that is easier to use with one hand. It works, but it seems ridiculous in practice.
Another consideration is the Side Sense user interface. It is a translucent vertical bar on the right side of the screen. When you click twice, a pop-up menu will appear, giving you access to all applications, notification trays, and various hardware features in most thumb ranges. In both solutions, this is a better solution, but it still feels like a solution to the problem of its big screen creation.
It's easier to use SONY's usability tips
The Xperia 10 lineup comes with Android 9 Pie, which enables new gesture-based navigation by default, but you can switch to button navigation (I will do so soon). If you are from a Samsung phone or Google Pixel, Sony's world will be a bit different, but everything is here. Sony has made its own version of the basic app, but later turned to Google's stock app, I don't want to argue. When installing the phone for the first time, it provides a bunch of UK media software, including Booking.com, Amazon, AVG Virus Protection, Facebook and other apps, but fortunately, you don't have to install any one.
Despite its high (or super wide, depending on how it works in your hands) screen, using apps and playing games is mostly not a problem with Xperia 10. Most applications work fine and automatically adjust to a 21:9 aspect ratio. However, one of my favorite games I played on the subway, Alto's Odyssey, cut its menu due to its aspect ratio. Whether it affects the app you like and the app you like, but it's likely that the app or game you're using will make the display slightly darker.
Worse than these display problems is that its hardware can't stay in good shape. The Snapdragon 636 processor in the Xperia 10 Plus is significantly faster than the Xperia 10 Snapdragon 630, although they don't work in a small number of common applications, and the UI animation will be intermittent even without any action. Its fingerprint sensor is one of the best designed features on mobile phones, and fingerprint recognition is very slow. I often need to reapply my fingers to read correctly.
SonyRepair, is a phone repair and game console repair website offering repair services at an affordable prices. Sony Repair is one of the topmost repair service providers in the UK.
For more details, visit the website http://www.sonyrepair.com
0 notes
Text
How to protect your small business from data breaches
Cyberattack vs. data breach: what’s the difference?
A cyberattack is simply a digital attack on computer systems, networks, devices, and/or applications. The objective is usually to disable computer systems or steal data. Attackers can use a variety of tools and techniques to achieve their goals, including phishing emails, ransomware, viruses, and denial-of-service attacks. A data breach is one potential consequence of a successful cyberattack. The types of data they are looking for could be passwords, email addresses, personal information, or financial information.
Threats
The following statistics paint a vivid picture of the threats to SMB data:
52% of small businesses experienced cybersecurity breaches in the past year.
Cybersecurity breaches cost UK businesses approximately £30 billion in 2016.
60% of small firms don’t know the source of the most disruptive cybersecurity breach or attack in the last twelve months.
Across the globe, just under 5 million records a day are compromised through a data breach.
On average, it takes 120 days for a business to discover a data breach.
In summary, data breaches are common, often go undetected at first, and can cost businesses – who don’t know how to protect themselves - thousands.
What is a data breach?
What can SMBs do to protect themselves?
Putting a cost-effective cybersecurity strategy in place can help to better protect you further down the line.
Strategy Step 1: Understand the elements of proper data protection
The first step in creating a cybersecurity strategy is to truly understand what is meant by ‘data protection’. Think of it in terms of the CIA acronym:
Confidentiality
Integrity
Availability.
This means your data needs to be kept confidential. It should only be available to people with relevant privileges. Your data should maintain its integrity and be in the format the user requires it to be (and not to have been materially altered by the system capturing, storing, or transmitting it.) Finally, your data should be available whenever the person with those relevant privileges is requesting it.
Strategy Step 2: Assess
The first step in assessing your customers’ potential vulnerabilities is to identify all the physical and virtual computing devices within the organization. Together with your client, make a list that includes all of them:
• Workstations and laptops• Network file servers• Network application servers• Corporate firewalls and switches• Multi-function printers• Mobile devices.
This infrastructure assessment should distinguish between cloud and on-premise systems and devices. This makes it easier for you to determine all possible storage locations for data. The number one threat to devices is a hybrid ransomware attack. For people, it’s targeted social engineering.
Now, categorize all business data and divide it into three locations: cloud,on-premise systems, and devices. For example:
• Cloud On-premise systems Devices• Cloud email and applications• Cloud storage• Websites and social media• Databases• Company-wide file sharing and storage• Intellectual property• Presentations• Company memos• Statistics and reports.
Read our white paper on the three essential components of managed security services.
Strategy Step 3: Identify relevant security measures
Once you’ve assessed what data is important to your business, where it resides, and who has access to it, you can determine the relevant security measures you should adopt. These may include:
Purchasing tools (for example, AVG antivirus Subscription for small businesses).
Redesigning your security protocols.
A wholesale change in your business’s attitude towards data security.
Training for all members of staff.
Data protection must be discussed and supported at every level within your business. It is as critical for senior executives as it is for junior team members, all of whom will have access to sensitive data of some kind. Take the time to review what data they may handle, and put the relevant measures in place.
Steps for protecting data
There are plenty of good security measures all businesses can apply today that will help prevent or reduce the chances of data loss, breach, or theft. These tools and solutions come in many shapes and sizes, but all have a role to play in protecting your sensitive and private data.
1: The basics
Install firewalls
Install AVG antivirus Subscription
Install encryption software.
2: Staff awareness
Use strong passwords.
Consistently communicate the importance of staff caution when clicking on links or attachments.
Provide training and education for staff on how to be security-aware.
Highlight the responsibility of every staff member.
Let all staff know how to report concerns or suspicions.
3: Starters and leavers process
Identify the specific data, devices, and access privileges new starters need.
Adopt a controlled exit policy for leavers, including group password resetting.
Review returned devices, wipe or securely destroy data where necessary.
4: Maintenance, upgrades, and planning
Back up your data regularly.
Scan network and devices frequently for necessary upgrades and/or action any security updates from trusted software providers as they pop up on your computer (for example AVG Driver Updater).
Force password changes regularly.
Create an Emergency Response Plan in case of theft, breach, or loss.
Many businesses decide to invest in cybersecurity solutions offered by companies such as AVG Antivirus Subscription Business who provides all-in-one protection including firewalls, server security, and email protection backed up with technical support. Compare the AVG Business options here.
Suspecting a breach
As the statistics at the top of this page show, SMBs often aren’t immediately aware when a breach has occurred. Here are some warning signs to look out for:
Your network performance decreases suddenly and dramatically.
You can’t perform routine updates.
Your AVG antivirus Subscription software is disabled and you can’t re-enable it.
You are locked out of accounts.
The longer a breach goes undetected, the more information the criminals can steal and the more damage they can inflict. You must act fast to:
Confirm if your network has been compromised.
Contain the damage as much as possible.
Under GDPR, organisations operating in Europe must report a personal data breach to the relevant authority within 72 hours.
If the incident concerns data held on a mobile device, you may need to consider whether you can (or should) wipe or disable the device remotely. A step such as this might provoke staff disapproval - especially if the device is the property of an employee. If you’re unable to provide a separate work phone, writing a Bring Your Own Device (BYOD) policy is always recommended.
If you do have a BYOD policy, it should include a backup schedule to ensure your business data and your employees’ personal data (photos, contacts, etc) is protected. Read our article: Tips on implementing a Bring Your Own Device policy.
Once the mobile device is wiped, if you do have a backup, you can restore this after the data breach is resolved. And while a simple backup might not be the ideal solution, it will go some way to putting you back in the position you were in prior to the breach or theft. Don’t underestimate its importance.
Key action points for preventing a data breach at your small business:
Make sure you understand the confidentiality, integrity and availability of your business data.
Assess the infrastructure of your network - devices, cloud locations, etc - and who has access.
Take relevant security measures: ensure you have up-to-date AVG Antivirus Subscription for small businesses, redesign your security policies and protocols and train your staff.
Know the signs of a breach - dramatic changes in network performance, can’t perform routine updates, you are locked out of accounts, etc - so that you can confirm and report it as soon as possible.
via Blogger https://ift.tt/3g9ozG8
0 notes
Text
AVG Helpline Number UK 0800-014-8298 AVG Support Number UK

The AVG antivirus use to protect the desktop from the virus and better the performance. This protection software is easy to install and use. It shows the complete device connected to your network. The AVG security helps you to identify the dangerous site. You can remove the virus from the desktop without losing any data. We provide the latest version of AVG antivirus to secure the device from the malware and threats. If you are facing any issue in the AVG security software then you can call on our AVG Toll Free Number and get the reliable solution.
#AVG Customer Care number UK#AVG Phone Number UK#AVG Support Help Number UK#AVG Support Helpline Number UK#AVG Contact Number UK
0 notes
Text
How to Fix AVG Free Antivirus Error

For any problem with your AVG antivirus please get in touch with our tech support agents who are available at 0808-101-2159 AVG Customer Care Number UK. Our technicians have great knowledge about antivirus working and functionality and hence it becomes easy for them to handle any complicated issue in an easy manner. In addition, these technicians are working round the clock, so it becomes easy for you to call them whenever you want to.
#AVG Help Desk Number UK#AVG Customer Support Number UK#AVG Toll Free Number UK#AVG Antivirus Technical Support Number UK#AVG Technical Helpline Number UK#AVG Installation Support Number UK#AVG Setup Support Number UK#AVG Refund Support Number UK#AVG Online Chat Support UK#AVG Tech Support Number UK
0 notes
Text
Steps to follow after AVG installation
If you want to protect your Windows, Macs and Android devices, then your first answer should be AVG Antivirus. This software is specifically developed to provide the user with such excellent attributes as it an ideal choice for them over time.
This software could be downloaded from the official website for free. This antivirus program provides outstanding affordability and flexibility with its amazing and devastating features. This software is an excellent and ideal match for personal computer users.
Today, it is extremely important to protect your PC from viruses and hacking in the internet prominent world that we work in. AVG brings free as well as a paid version to protect your device from virus, rootkits, spyware, and threats.
More and more users around the world prefer to use free AVG editions to ensure the safety of their personal computers. To enjoy the benefits of AVG, it is essential to install it on your PC. The AVG Installation process is very user-friendly and simple.
With a few clicks, the installation process is completed. The free AVG provides for free upgrades and convenient access to the latest attributes with its official websites. In this blog, we will discuss the installation process and the post-installation process of AVG.
Before installation, make sure that, your device does not have third-party software. If available then, remove the existing software with the help of AVG Removal Tool.
To install AVG software, follow these steps:
Go to AVG official website and find download section and then click the ‘Free Download’ box.
After downloading the software, click on the run box to start the installation. You can also find the downloading file in your download folder and then double click the application.
When the installation begins, choose the language whichever you want to choose and then select ‘Next’.
After that, read the license agreement of software and then understand the terms and click ‘Accept’ to continue the installation process.
Then, a license box appears automatically in which you need to fill your license number. Just click ‘next’ to proceed.
Further, select the custom install option, switch with default path and then click next to continue along with installation.
In the next installation component, you may either deselect the ‘Additional installed Languages’ or can just click next to proceed.
Click on ‘Finish’ to get the installation done.
These steps will make you easy to install the AVG on your device. Hold on, now you need to set up the features, update and configure the software.
Follow these steps for Post Installation Setup:
After installation is completed, the AVG menu will appear and provide you the options of scanning the system. We have to click the select option that is available on the top right corner and then click on ‘Advanced Settings’.
Here, you will need to select the ‘Virus Vault’ that appears on the left corner under the ‘Update’. Increase the size of the vault to 20% and after you are finished, press ‘Apply’ that is available on the bottom right corner.
After that, click on ‘Update’ on the left side of the application and then deselect ‘Start Memory and process scan further a successful update’. Again, click on ‘Apply’ box in the right corner when you have done.
Click on ‘Identity Protection’ on the left corner and choose the ‘Automatically quarantine detected threats’ box. Press ‘Apply’ from the same, right corner.
Now, finally, click on the ‘Appearance’ option that is available on the top left corner. Deselect both ‘AVG Advisor notifications’ and ‘Boot time improvement’ and then click on Apply.
Now, you have installed and completely configured the AVG Antivirus to protect your PC from threats that may attack from outside and maintains maximum efficiency and speed of the system.
If you have any queries against AVG or if you are facing any problem while installing or updating antivirus, then directly connected with the experts with just a call on AVG Support Number UK. The team will help you to figure out the reason for that issue and provide proper guidance to troubleshoot the issue.
Source URL: https://medium.com/@ellietaylor706/steps-to-follow-after-avg-installation-d36959f6dfcd
#install avg free for windows 7#avg antivirus not installing#avg not installing on windows 10#AVG Technical Number UK#AVG Toll free number UK#AVG Support Number UK
0 notes
Text
What is the Use of AVG PC Tune Up?
Are you fed up of your slow PC? As you keep your computer, its hard disk start filling up with unwanted files and programs and then it will ultimately become slow. The more programs you will use, the slower it will become with time. This is not only the case with old computers, even new computer system sometime work slower than our expectation. The solution for this problem is one and i.e. AVG PC TuneUp. Call our experts on AVG Support Number to download and install this tool.

AVG PC TuneUp is a tool that will keep your system clean and remove all unwanted leftover files. This tool automatically remove temporary file in Office 2016, snagIt, Windows 10 and more. It will also clear out all unnecessary Windows cache and logs, duplicate photos, docs and other files. Moreover, it also clean up hidden browser traces from the latest IE, Edge, Chrome and Firefox. Once all this is cleared out, your system will automatically become fast no matter whether it’s a new one or an old PC. Take help from our experts on 24 X7 AVG Phone Number @ 0808-169-1988 (Toll- Free) in UK to understand the correct usage of this tool and its features. They will tell you everything from A to Z about this AVG utility.
0 notes
Text
Lighterbit Hyip Review : We Provide Best Investment For Your Business

About Lighterbit
Welcome to the site of Lighterbit LTD ! speculation stage is a result of watchful arrangement and productive work of specialists in the field of crypto, exceptionally gainful exchange digital forms of money and web-based promoting. Utilizing current strategies for working together and an individual way to deal with every customer, they offer a one of a kind speculation model to individuals who need to utilize Bitcoin as a strategy for installment, as well as a solid wellspring of stable pay. LIGHTER BIT LTD business utilizes just current mining hardware and exchanges and no more steady markets, which limits the danger of monetary misfortune to clients and promises them a steady salary accumulated each logbook day. LIGHTER BIT LTD is situated in London - 52 Gray's Inn Square, London, United Kingdom, WC1R 5JP. Enlisted Company No. 11336173. Acquire 2% Daily For 75 days. Put resources into one of our Investment Plans and Start Earning cash Daily. Withdrawl your Funds Daily into bitcoin Wallet, Ethereum Wallet, Perfect Money Account litecoin account advcash record or Payeer Account. Withdrawal Requests are Processed from 20 Minutes to 1 Business Day. They acknowledge Bitcoin, Ethereum, Perfect Money , advcash , litecoin and Payeer for Deposits and Withdrawals. Click Here To Visit Website Basic Information Min Investment $10.00 Min Withdraw Avg. Refer Rate 5 Level Refer System 5% - 3% - 1% - 0.5% - 0.2% Payment Type Instant Company Type Hyip Web I.P 158.69.100.46 Company Address UK Company No 11336173 Payment Accepted Payeer, Bitcoin, Bitcoin Cash, Links Homepage Investment Plan Of Lighterbit INVESTMENT PACKAGE 2% DAILY FOR 75 DAYS Minimum Deposit :$10.00 Maximum Deposit :$100000.00 Principal Return: Included Complete Review Of Lighterbit LIGHTER BIT LTD is situated in London - 52 Gray's Inn Square, London, United Kingdom, WC1R 5JP. Enlisted Company No. 11336173. Acquire 2% Daily For 75 days. Put resources into one of our Investment Plans and Start Earning cash Daily. Withdrawl your Funds Daily into bitcoin Wallet, Ethereum Wallet, Perfect Money Account litecoin account advcash record or Payeer Account. Withdrawal Requests are Processed from 20 Minutes to 1 Business Day. We acknowledge Bitcoin, Ethereum, Perfect Money , advcash , litecoin and Payeer for Deposits and Withdrawals. The Income of our Company to Pay our Investors are Originated from the Bitcoin Trading we do each day, purchasing Bitcoin in the fall of cost and Selling Bitcoin on high. Your Funds are Managed by Specialists in International Financial Market. Put resources into the Best Digital Currency Investment Company in the World. Cryptographic money trading,digital cash, bitcoin wallets, bitcoin cost, bitcoin advertise. Gain Bitcoin Forever. Some Uniques Features Of Lighterbit Referral Commission They HAVE 5 LEVEL REFERRAL COMMISSION 5% LEVEL-1 3% LEVEL-2 1% LEVEL-3 0.5% LEVEL-4 0.2% LEVEL- Corporation Opportunities Ensured accomplice expenses and an abnormal state of dynamic wage in the organization. DDOS PROTECTION LIGHTER BIT LTD site has the best and largest amount of assurance from any sort of assaults by DDOSGurard COMODO EV-SSL SECURITY Lighterbit Comodo EV - SSL Certificate ensures the security of your exchanges. Uk Registered Company LIGHTER BIT LTD has been legitimately enrolled in United Kingdom. Our Company Number is #11336173. Fast Payment Withdrawals Each withdrawal demands are forms inside 24 hours to your E-Currency account. Least pull back sum is $0.01, most extreme has no restriction. Great Customer Support On the off chance that you have any inquiry, the help administration will react rapidly. 24/7 Customer Support Lighterbit provides 24/7 customer support through Live Chat and e-mail. Company support representatives are always available to answer any questions. Need More Hyip Review Just Click Here Disclaimer: Not all the websites Which listed in Top List are 100% safe to use or investment. We do not promote any of those. Due diligence is your own responsibility. You should never make an investment in an online program with money you aren’t prepared to lose. Make sure to research the website. So Please take care of your investments. and be on the safe site and avoid much losing online. Read the full article
0 notes
Text
How to protect your small business from data breaches
Cyberattack vs. data breach: what’s the difference?
A cyberattack is simply a digital attack on computer systems, networks, devices, and/or applications. The objective is usually to disable computer systems or steal data. Attackers can use a variety of tools and techniques to achieve their goals, including phishing emails, ransomware, viruses, and denial-of-service attacks. A data breach is one potential consequence of a successful cyberattack. The types of data they are looking for could be passwords, email addresses, personal information, or financial information.
Threats
The following statistics paint a vivid picture of the threats to SMB data:
52% of small businesses experienced cybersecurity breaches in the past year.
Cybersecurity breaches cost UK businesses approximately £30 billion in 2016.
60% of small firms don’t know the source of the most disruptive cybersecurity breach or attack in the last twelve months.
Across the globe, just under 5 million records a day are compromised through a data breach.
On average, it takes 120 days for a business to discover a data breach.
In summary, data breaches are common, often go undetected at first, and can cost businesses – who don’t know how to protect themselves - thousands.
What is a data breach?
What can SMBs do to protect themselves?
Putting a cost-effective cybersecurity strategy in place can help to better protect you further down the line.
Strategy Step 1: Understand the elements of proper data protection
The first step in creating a cybersecurity strategy is to truly understand what is meant by ‘data protection’. Think of it in terms of the CIA acronym:
Confidentiality
Integrity
Availability.
This means your data needs to be kept confidential. It should only be available to people with relevant privileges. Your data should maintain its integrity and be in the format the user requires it to be (and not to have been materially altered by the system capturing, storing, or transmitting it.) Finally, your data should be available whenever the person with those relevant privileges is requesting it.
Strategy Step 2: Assess
The first step in assessing your customers’ potential vulnerabilities is to identify all the physical and virtual computing devices within the organization. Together with your client, make a list that includes all of them:
• Workstations and laptops• Network file servers• Network application servers• Corporate firewalls and switches• Multi-function printers• Mobile devices.
This infrastructure assessment should distinguish between cloud and on-premise systems and devices. This makes it easier for you to determine all possible storage locations for data. The number one threat to devices is a hybrid ransomware attack. For people, it’s targeted social engineering.
Now, categorize all business data and divide it into three locations: cloud,on-premise systems, and devices. For example:
• Cloud On-premise systems Devices• Cloud email and applications• Cloud storage• Websites and social media• Databases• Company-wide file sharing and storage• Intellectual property• Presentations• Company memos• Statistics and reports.
Read our white paper on the three essential components of managed security services.
Strategy Step 3: Identify relevant security measures
Once you’ve assessed what data is important to your business, where it resides, and who has access to it, you can determine the relevant security measures you should adopt. These may include:
Purchasing tools (for example, AVG antivirus Subscription for small businesses).
Redesigning your security protocols.
A wholesale change in your business’s attitude towards data security.
Training for all members of staff.
Data protection must be discussed and supported at every level within your business. It is as critical for senior executives as it is for junior team members, all of whom will have access to sensitive data of some kind. Take the time to review what data they may handle, and put the relevant measures in place.
Steps for protecting data
There are plenty of good security measures all businesses can apply today that will help prevent or reduce the chances of data loss, breach, or theft. These tools and solutions come in many shapes and sizes, but all have a role to play in protecting your sensitive and private data.
1: The basics
Install firewalls
Install AVG antivirus Subscription
Install encryption software.
2: Staff awareness
Use strong passwords.
Consistently communicate the importance of staff caution when clicking on links or attachments.
Provide training and education for staff on how to be security-aware.
Highlight the responsibility of every staff member.
Let all staff know how to report concerns or suspicions.
3: Starters and leavers process
Identify the specific data, devices, and access privileges new starters need.
Adopt a controlled exit policy for leavers, including group password resetting.
Review returned devices, wipe or securely destroy data where necessary.
4: Maintenance, upgrades, and planning
Back up your data regularly.
Scan network and devices frequently for necessary upgrades and/or action any security updates from trusted software providers as they pop up on your computer (for example AVG Driver Updater).
Force password changes regularly.
Create an Emergency Response Plan in case of theft, breach, or loss.
Many businesses decide to invest in cybersecurity solutions offered by companies such as AVG Antivirus Subscription Business who provides all-in-one protection including firewalls, server security, and email protection backed up with technical support. Compare the AVG Business options here.
Suspecting a breach
As the statistics at the top of this page show, SMBs often aren’t immediately aware when a breach has occurred. Here are some warning signs to look out for:
Your network performance decreases suddenly and dramatically.
You can’t perform routine updates.
Your AVG antivirus Subscription software is disabled and you can’t re-enable it.
You are locked out of accounts.
The longer a breach goes undetected, the more information the criminals can steal and the more damage they can inflict. You must act fast to:
Confirm if your network has been compromised.
Contain the damage as much as possible.
Under GDPR, organisations operating in Europe must report a personal data breach to the relevant authority within 72 hours.
If the incident concerns data held on a mobile device, you may need to consider whether you can (or should) wipe or disable the device remotely. A step such as this might provoke staff disapproval - especially if the device is the property of an employee. If you’re unable to provide a separate work phone, writing a Bring Your Own Device (BYOD) policy is always recommended.
If you do have a BYOD policy, it should include a backup schedule to ensure your business data and your employees’ personal data (photos, contacts, etc) is protected. Read our article: Tips on implementing a Bring Your Own Device policy.
Once the mobile device is wiped, if you do have a backup, you can restore this after the data breach is resolved. And while a simple backup might not be the ideal solution, it will go some way to putting you back in the position you were in prior to the breach or theft. Don’t underestimate its importance.
Key action points for preventing a data breach at your small business:
Make sure you understand the confidentiality, integrity and availability of your business data.
Assess the infrastructure of your network - devices, cloud locations, etc - and who has access.
Take relevant security measures: ensure you have up-to-date AVG Antivirus Subscription for small businesses, redesign your security policies and protocols and train your staff.
Know the signs of a breach - dramatic changes in network performance, can’t perform routine updates, you are locked out of accounts, etc - so that you can confirm and report it as soon as possible.
via Blogger https://ift.tt/2ZkcOpL
0 notes
Text
avg.com Login

avg.com Login
avg.com Login-Having trouble with AVG Activate Enter Code online ? We are here to fix your AVG Activation and installation issues online by Live Chat or Call.
Welcome to avg.com Login Website
Support for AVG Antivirus
Call USA/Canada Toll Free
Instant Support 1–844–833–0610
UK technical support- 020–3890–3474
Installs in moments. Protects forever.
This antivirus program is so light and easy to install, you and your family will be protected in just moments. It’ll then keep protecting you day and night, automatically updating itself against the latest threats to help keep you and your family safe.
Install AVG-Download and Install your AVG Online
Where to seek out AVG License Key? The AVG security package is simple to setup & install. Simply find alpha-numeric code that is written on the backside of the retail card. Here may be a sample Product Key to let you understand: xxxxx-xxxxx-xxxxx-xxxxx-xxxxx-xxxxx
Start Setup to Activate and Install Your Product.
Support For AVG Retail Enrollment
AVG Retail Help — Here you can find the Step by Step guide for AVG Activate, download and complete installation from www.avg.com/retail online. We are independent technical support services provider, if in any case you are facing problem while activate or install AVG product. You just need to fill the form above and our expert will get in touch directly to short out the issues.
If you need help to activate, download & install AVG Retail security on www.avg.com/retail? If you required an AVG activation code easily with you subsequently you must have security retail card which is very well-liked means to install AVG then there should be an individual activation code & internet link avg.com/retail in your acquire confirmation e-mail or in the products box. Now you need follow the activation link by instruction supplied or if you’ve a CD of the security merchandise then add it in to your CD or DVD drive and wait approximately for it to auto start and should isn’t automatically open then personally go in to your CD/DVD drive and run the setup or installation file.
The best way to Install AVG Security Online and Enroll, AVG Retail Enrollment from avg.com/retail is an easiest method to Activate AVG and setup because CD and DVD’s may be harm in transportation and also majority of the most recent computing devices not comes along with CD/DVD drives. So, it’s really becoming difficult for computer users to install Antivirus utilizing CD’S, but with the help of retail card you can readily finish Activation and setup by simply following a straightforward net address on-line.
How To Download and Install AVG
You can download AVG products from here or visit www.avg.com/retail or avg.com/retail
To get it register put the unique code or retail key code.
If you have AVG account then Log in or if you are new to AVG create your account to register AVG retail key code.
In the setup window of your avg account , you will see the avg file to download
Run the downloaded file to start the installation process.
Follow the instruction on your screen.
When prompted, eneter your AVG license number. The License number is sent automatically to your email once purchased.
Complete the installation and restart your computer
Related or other useful links
www.avg.com/retail :- TO download and Install the AVG Retail Unique code
www.avg.com/register :- TO download and Install the AVG Online Purchase
www.avg.com/download :- To Download and Install the AVG Softwares
www.avg.com/myaccount :- To Login to AVG Account to manage, dowload or Setup an account
www.avg.com/support :- To get 24*7 AVG Technical Support ( Toll free 1–844–296–4279 USA & Canada)
www.avg.com/lost :- To retrieve the AVG Purchase License key.
Tip: If you need to retrieve the license number for your AVG product, visit http://www.avg.com/lost, and fill in the form. Your license information will be sent to your email.
0 notes
Text
How do I completely remove avg from my computer?
Sometimes, the things become out of the reach to resolve them out. Therefore, it is essential to get them completely out of the place. When we talk about Antivirus solutions, we know that they are really commendable as doing a great job in removing various malwares and viruses out of your system’s reach. But there is also a time, when they starts acting weird and are the reason behind some technical issues. So there is an urgent to remove them completely. AVG Antivirus is renowned to be the most responsible antivirus solution and is highly enamored. But the thing is, everything has its limit and so does in the case of AVG. Sometimes, its users get so much disturbed that they only find a way how can they get rid of this disturbing antivirus solution. But they are in a shortage of way, how can they accomplish this task. Follow the steps suggested below and resolve out your issue within a short time period:
• You have to press Windows and X key simultaneously and then select Programs and Features from the menu that displays.
• Thereafter, Right-click AVG in the list of programs and choose Uninstall to open up the AVG uninstall wizard.
• Then follow the procedure available on your screen to complete the installation.
• At last, Restart your system.
If you are still left with some of the AVG components and are in an urgent need to uninstall them immediately, then connect the technical customer support team available at AVG Help Number UK 0808-101-2159 toll free and you get instant solutions on the go. The technical team here is so skilled and determined to every task they are being assigned to.
#AVG helpline phone number UK#AVG customer service number UK#AVG tech support number UK#AVG technical helpline number UK
0 notes
Text
How to protect your small business from data breaches
Cyberattack vs. data breach: what’s the difference?
A cyberattack is simply a digital attack on computer systems, networks, devices, and/or applications. The objective is usually to disable computer systems or steal data. Attackers can use a variety of tools and techniques to achieve their goals, including phishing emails, ransomware, viruses, and denial-of-service attacks. A data breach is one potential consequence of a successful cyberattack. The types of data they are looking for could be passwords, email addresses, personal information, or financial information.
Threats
The following statistics paint a vivid picture of the threats to SMB data:
52% of small businesses experienced cybersecurity breaches in the past year.
Cybersecurity breaches cost UK businesses approximately £30 billion in 2016.
60% of small firms don’t know the source of the most disruptive cybersecurity breach or attack in the last twelve months.
Across the globe, just under 5 million records a day are compromised through a data breach.
On average, it takes 120 days for a business to discover a data breach.
In summary, data breaches are common, often go undetected at first, and can cost businesses – who don’t know how to protect themselves - thousands.
What is a data breach?
What can SMBs do to protect themselves?
Putting a cost-effective cybersecurity strategy in place can help to better protect you further down the line.
Strategy Step 1: Understand the elements of proper data protection
The first step in creating a cybersecurity strategy is to truly understand what is meant by ‘data protection’. Think of it in terms of the CIA acronym:
Confidentiality
Integrity
Availability.
This means your data needs to be kept confidential. It should only be available to people with relevant privileges. Your data should maintain its integrity and be in the format the user requires it to be (and not to have been materially altered by the system capturing, storing, or transmitting it.) Finally, your data should be available whenever the person with those relevant privileges is requesting it.
Strategy Step 2: Assess
The first step in assessing your customers’ potential vulnerabilities is to identify all the physical and virtual computing devices within the organization. Together with your client, make a list that includes all of them:
• Workstations and laptops• Network file servers• Network application servers• Corporate firewalls and switches• Multi-function printers• Mobile devices.
This infrastructure assessment should distinguish between cloud and on-premise systems and devices. This makes it easier for you to determine all possible storage locations for data. The number one threat to devices is a hybrid ransomware attack. For people, it’s targeted social engineering.
Now, categorize all business data and divide it into three locations: cloud,on-premise systems, and devices. For example:
• Cloud On-premise systems Devices• Cloud email and applications• Cloud storage• Websites and social media• Databases• Company-wide file sharing and storage• Intellectual property• Presentations• Company memos• Statistics and reports.
Read our white paper on the three essential components of managed security services.
Strategy Step 3: Identify relevant security measures
Once you’ve assessed what data is important to your business, where it resides, and who has access to it, you can determine the relevant security measures you should adopt. These may include:
Purchasing tools (for example, AVG antivirus Subscription for small businesses).
Redesigning your security protocols.
A wholesale change in your business’s attitude towards data security.
Training for all members of staff.
Data protection must be discussed and supported at every level within your business. It is as critical for senior executives as it is for junior team members, all of whom will have access to sensitive data of some kind. Take the time to review what data they may handle, and put the relevant measures in place.
Steps for protecting data
There are plenty of good security measures all businesses can apply today that will help prevent or reduce the chances of data loss, breach, or theft. These tools and solutions come in many shapes and sizes, but all have a role to play in protecting your sensitive and private data.
1: The basics
Install firewalls
Install AVG antivirus Subscription
Install encryption software.
2: Staff awareness
Use strong passwords.
Consistently communicate the importance of staff caution when clicking on links or attachments.
Provide training and education for staff on how to be security-aware.
Highlight the responsibility of every staff member.
Let all staff know how to report concerns or suspicions.
3: Starters and leavers process
Identify the specific data, devices, and access privileges new starters need.
Adopt a controlled exit policy for leavers, including group password resetting.
Review returned devices, wipe or securely destroy data where necessary.
4: Maintenance, upgrades, and planning
Back up your data regularly.
Scan network and devices frequently for necessary upgrades and/or action any security updates from trusted software providers as they pop up on your computer (for example AVG Driver Updater).
Force password changes regularly.
Create an Emergency Response Plan in case of theft, breach, or loss.
Many businesses decide to invest in cybersecurity solutions offered by companies such as AVG Antivirus Subscription Business who provides all-in-one protection including firewalls, server security, and email protection backed up with technical support. Compare the AVG Business options here.
Suspecting a breach
As the statistics at the top of this page show, SMBs often aren’t immediately aware when a breach has occurred. Here are some warning signs to look out for:
Your network performance decreases suddenly and dramatically.
You can’t perform routine updates.
Your AVG antivirus Subscription software is disabled and you can’t re-enable it.
You are locked out of accounts.
The longer a breach goes undetected, the more information the criminals can steal and the more damage they can inflict. You must act fast to:
Confirm if your network has been compromised.
Contain the damage as much as possible.
Under GDPR, organisations operating in Europe must report a personal data breach to the relevant authority within 72 hours.
If the incident concerns data held on a mobile device, you may need to consider whether you can (or should) wipe or disable the device remotely. A step such as this might provoke staff disapproval - especially if the device is the property of an employee. If you’re unable to provide a separate work phone, writing a Bring Your Own Device (BYOD) policy is always recommended.
If you do have a BYOD policy, it should include a backup schedule to ensure your business data and your employees’ personal data (photos, contacts, etc) is protected. Read our article: Tips on implementing a Bring Your Own Device policy.
Once the mobile device is wiped, if you do have a backup, you can restore this after the data breach is resolved. And while a simple backup might not be the ideal solution, it will go some way to putting you back in the position you were in prior to the breach or theft. Don’t underestimate its importance.
Key action points for preventing a data breach at your small business:
Make sure you understand the confidentiality, integrity and availability of your business data.
Assess the infrastructure of your network - devices, cloud locations, etc - and who has access.
Take relevant security measures: ensure you have up-to-date AVG Antivirus Subscription for small businesses, redesign your security policies and protocols and train your staff.
Know the signs of a breach - dramatic changes in network performance, can’t perform routine updates, you are locked out of accounts, etc - so that you can confirm and report it as soon as possible.
from Blogger http://quicksolvocom.blogspot.com/2020/06/how-to-protect-your-small-business-from.html
0 notes
Link

Get quick support for AVG products or AVG internet security by technical help for virus removal, upgrades, installation or any kind of technical issues or errors.
0 notes