#Apache Thrift
Explore tagged Tumblr posts
Text
The Ins and Outs of the Used Construction Equipment Market: A Witty Dive
Welcome to the wild world of used construction equipment, where bulldozers have more stories to tell than a seasoned detective and excavators have seen more dirt than your garden shovel. In this blog, we're going to take a jaunty stroll through the bustling market of pre-loved machinery, exploring its quirks, challenges, and triumphs. So, buckle up and let's dig in!

The Scoop on the Market:
Picture this: a dynamic sector where giant machines find new homes faster than you can say "Jackhammer." With a market size valued at a whopping USD 115.32 billion in 2022, the used construction equipment market isn't just big; it's colossal. And guess what? It's only getting bigger, poised to reach a staggering USD 191.55 billion by 2031. Talk about growth spurts!
What Drives the Madness:
Why the craze, you ask? Well, imagine scoring a perfectly functional crane at a fraction of the cost. It's like finding a vintage treasure in a thrift store, but with more steel and hydraulic fluid. Plus, with emerging economies clamoring for shiny new infrastructure, the demand for used equipment is skyrocketing faster than a faulty elevator.
Regional Rumbles:
North America leads the charge, waving its flag of developed infrastructure and construction galore. But don't count Europe out; it's hot on America's heels with its well-oiled building sector. And let's not forget the underdog, Asia Pacific, rising like a phoenix with its urbanization frenzy and tech-savvy construction wizards.
The Dance of Equipment Types:
Excavators and loaders take center stage, stealing the limelight with their versatility and charm. But hold onto your hard hats; cranes are waltzing their way to the top as the fastest-growing segment. It's a battle of the titans, and everyone's invited to the spectacle.
The Game of Applications:
From infrastructure development to residential and commercial construction, there's a piece of the pie for everyone. Earthmoving equipment reigns supreme, digging its claws into every construction project like an eager puppy in a pile of dirt. And with technology playing cupid, the marriage between construction and innovation is a match made in heaven.
For More Information:
https://www.skyquestt.com/report/used-construction-equipment-market
The Nitty-Gritty of Regional Insights:
North America flaunts its construction prowess, Europe brings its A-game with a dash of environmental consciousness, and Asia Pacific is the new kid on the block, ready to shake things up. It's a global dance-off, and every region's got its own moves.
The Heroes and Villains:
In this epic saga, our heroes Caterpillar, Komatsu, and Volvo Construction Equipment fight tooth and nail for market supremacy. But watch out for the villainous depreciation and maintenance costs lurking in the shadows, ready to spoil the party.
The Rising Stars:
Rental and used equipment are the rising stars of the show, offering budget-friendly alternatives in a world of shiny new toys. And with technological advancements turning used machinery into high-tech marvels, it's a win-win for buyers and sellers alike.
Conclusion:
So there you have it, folks, a whirlwind tour of the used construction equipment market, where every machine has a story to tell and every deal is a dance of supply and demand. Whether you're a seasoned veteran or a wide-eyed rookie, there's never a dull moment in this bustling marketplace. So, grab your hard hat, roll up your sleeves, and join the fray. After all, in the world of construction, the only way to go is up!
About Us-
SkyQuest Technology Group is a Global Market Intelligence, Innovation Management & Commercialization organization that connects innovation to new markets, networks & collaborators for achieving Sustainable Development Goals.
Contact Us-
SkyQuest Technology Consulting Pvt. Ltd.
1 Apache Way,
Westford,
Massachusetts 01886
USA (+1) 617–230–0741
Email- [email protected]
Website: https://www.skyquestt.com
0 notes
Link
0 notes
Text
If you did not already know
Apache Thrift The Apache Thrift software framework, for scalable cross-language services development, combines a software stack with a code generation engine to build services that work efficiently and seamlessly between C++, Java, Python, PHP, Ruby, Erlang, Perl, Haskell, C#, Cocoa, JavaScript, Node.js, Smalltalk, OCaml and Delphi and other languages. … IBN-Net Convolutional neural networks (CNNs) have achieved great successes in many computer vision problems. Unlike existing works that designed CNN architectures to improve performance on a single task of a single domain and not generalizable, we present IBN-Net, a novel convolutional architecture, which remarkably enhances a CNN’s modeling ability on one domain (e.g. Cityscapes) as well as its generalization capacity on another domain (e.g. GTA5) without finetuning. IBN-Net carefully integrates Instance Normalization (IN) and Batch Normalization (BN) as building blocks, and can be wrapped into many advanced deep networks to improve their performances. This work has three key contributions. (1) By delving into IN and BN, we disclose that IN learns features that are invariant to appearance changes, such as colors, styles, and virtuality/reality, while BN is essential for preserving content related information. (2) IBN-Net can be applied to many advanced deep architectures, such as DenseNet, ResNet, ResNeXt, and SENet, and consistently improve their performance without increasing computational cost. (3) When applying the trained networks to new domains, e.g. from GTA5 to Cityscapes, IBN-Net achieves comparable improvements as domain adaptation methods, even without using data from the target domain. With IBN-Net, we won the 1st place on the WAD 2018 Challenge Drivable Area track, with an mIoU of 86.18%. … UNet++ In this paper, we present UNet++, a new, more powerful architecture for medical image segmentation. Our architecture is essentially a deeply-supervised encoder-decoder network where the encoder and decoder sub-networks are connected through a series of nested, dense skip pathways. The re-designed skip pathways aim at reducing the semantic gap between the feature maps of the encoder and decoder sub-networks. We argue that the optimizer would deal with an easier learning task when the feature maps from the decoder and encoder networks are semantically similar. We have evaluated UNet++ in comparison with U-Net and wide U-Net architectures across multiple medical image segmentation tasks: nodule segmentation in the low-dose CT scans of chest, nuclei segmentation in the microscopy images, liver segmentation in abdominal CT scans, and polyp segmentation in colonoscopy videos. Our experiments demonstrate that UNet++ with deep supervision achieves an average IoU gain of 3.9 and 3.4 points over U-Net and wide U-Net, respectively. … Alpha Model-Agnostic Meta-Learning (Alpha MAML) Model-agnostic meta-learning (MAML) is a meta-learning technique to train a model on a multitude of learning tasks in a way that primes the model for few-shot learning of new tasks. The MAML algorithm performs well on few-shot learning problems in classification, regression, and fine-tuning of policy gradients in reinforcement learning, but comes with the need for costly hyperparameter tuning for training stability. We address this shortcoming by introducing an extension to MAML, called Alpha Model-agnostic meta-learning, to incorporate an online hyperparameter adaptation scheme that eliminates the need to tune meta-learning and learning rates. Our results with the Omniglot database demonstrate a substantial reduction in the need to tune MAML training hyperparameters and improvement to training stability with less sensitivity to hyperparameter choice. … https://analytixon.com/2023/01/27/if-you-did-not-already-know-1950/?utm_source=dlvr.it&utm_medium=tumblr
0 notes
Text


Spotted this old Apache in town today while the wife and I were out thrifting. Looks pretty solid. I don't know much about Chevys, but this pickup has to be mid 50's, yes?
48 notes
·
View notes
Text

buncha interesting books at thrift
#thrift books#books#used books#thrift store#linux#unix#computer book#8086#sed#awk#microcomputer#apache#hacks
6 notes
·
View notes
Text
A neat thing happened to me today. I was looking around the thrift store and found a huge bag of embroidery thread but a lady's basket was in the way. I said Excuse Me, and she moved, I said Thank You.... In Apache. I’ve been listening to my dad’s mom in the phone and it’s something I picked up. I’ve been wanting to learn more from her tbh.
The older lady in front of me squinted and I was half scared she’d think I said something offensive to her in another language. Her eyes lit up suddenly, smiled and said “ Are you Mescarelo? I'm from Ruidoso!”
“ No, Coyotero. I live in Los Alamos.”
So that whole time in the store we were talking about our families, where they live, who are our grandmothers or aunts, and if we have any links as distant relatives. We don’t, at least none that we know of. I was a bit suspicious of all her questions since a lot of older ladies like her act as matchmakers, and yeah..she wasted no time whipping out her phone to show me her grandsons. Her very single and available grandsons. XD Why are all the grannies like this?
I found out she does quilting and has really beautiful work, that’s something I’ve never tried to do, and I mentioned needle felting and she has heard of it but thinks it looks too complicated. It can be, it depends. I showed her a photo of something I made and she thought it was cute, she suggested I do some southwestern animals. That’s actually a good idea, I've never really seen that done before. We exchanged emails - I don’t have social media -, and I went on my way to another thrift store before going home to start dinner. No idea what I want to make though. I’m lazy. I honestly could go for chili dogs.
7 notes
·
View notes
Text
If you did not already know
Apache Thrift The Apache Thrift software framework, for scalable cross-language services development, combines a software stack with a code generation engine to build services that work efficiently and seamlessly between C++, Java, Python, PHP, Ruby, Erlang, Perl, Haskell, C#, Cocoa, JavaScript, Node.js, Smalltalk, OCaml and Delphi and other languages. … IBN-Net Convolutional neural networks (CNNs) have achieved great successes in many computer vision problems. Unlike existing works that designed CNN architectures to improve performance on a single task of a single domain and not generalizable, we present IBN-Net, a novel convolutional architecture, which remarkably enhances a CNN’s modeling ability on one domain (e.g. Cityscapes) as well as its generalization capacity on another domain (e.g. GTA5) without finetuning. IBN-Net carefully integrates Instance Normalization (IN) and Batch Normalization (BN) as building blocks, and can be wrapped into many advanced deep networks to improve their performances. This work has three key contributions. (1) By delving into IN and BN, we disclose that IN learns features that are invariant to appearance changes, such as colors, styles, and virtuality/reality, while BN is essential for preserving content related information. (2) IBN-Net can be applied to many advanced deep architectures, such as DenseNet, ResNet, ResNeXt, and SENet, and consistently improve their performance without increasing computational cost. (3) When applying the trained networks to new domains, e.g. from GTA5 to Cityscapes, IBN-Net achieves comparable improvements as domain adaptation methods, even without using data from the target domain. With IBN-Net, we won the 1st place on the WAD 2018 Challenge Drivable Area track, with an mIoU of 86.18%. … UNet++ In this paper, we present UNet++, a new, more powerful architecture for medical image segmentation. Our architecture is essentially a deeply-supervised encoder-decoder network where the encoder and decoder sub-networks are connected through a series of nested, dense skip pathways. The re-designed skip pathways aim at reducing the semantic gap between the feature maps of the encoder and decoder sub-networks. We argue that the optimizer would deal with an easier learning task when the feature maps from the decoder and encoder networks are semantically similar. We have evaluated UNet++ in comparison with U-Net and wide U-Net architectures across multiple medical image segmentation tasks: nodule segmentation in the low-dose CT scans of chest, nuclei segmentation in the microscopy images, liver segmentation in abdominal CT scans, and polyp segmentation in colonoscopy videos. Our experiments demonstrate that UNet++ with deep supervision achieves an average IoU gain of 3.9 and 3.4 points over U-Net and wide U-Net, respectively. … Alpha Model-Agnostic Meta-Learning (Alpha MAML) Model-agnostic meta-learning (MAML) is a meta-learning technique to train a model on a multitude of learning tasks in a way that primes the model for few-shot learning of new tasks. The MAML algorithm performs well on few-shot learning problems in classification, regression, and fine-tuning of policy gradients in reinforcement learning, but comes with the need for costly hyperparameter tuning for training stability. We address this shortcoming by introducing an extension to MAML, called Alpha Model-agnostic meta-learning, to incorporate an online hyperparameter adaptation scheme that eliminates the need to tune meta-learning and learning rates. Our results with the Omniglot database demonstrate a substantial reduction in the need to tune MAML training hyperparameters and improvement to training stability with less sensitivity to hyperparameter choice. … https://analytixon.com/2023/01/27/if-you-did-not-already-know-1950/?utm_source=dlvr.it&utm_medium=tumblr
0 notes
Text
Application Performance Monitoring (APM) can be defined as the process of discovering, tracing, and performing diagnoses on cloud software applications in production. These tools enable better analysis of network topologies with improved metrics and user experiences. Pinpoint is an open-source Application Performance Management(APM) with trusted millions of users around the world. Pinpoint, inspired by Google Dapper is written in Java, PHP, and Python programming languages. This project was started in July 2012 and later released to the public in January 2015. Since then, it has served as the best solution to analyze the structure as well as the interconnection between components across distributed applications. Features of Pinpoint APM Offers Cloud and server Monitoring. Distributed transaction tracing to trace messages across distributed applications Overview of the application topology – traces transactions between all components to identify potentially problematic issues. Lightweight – has a minimal performance impact on the system. Provides code-level visibility to easily identify points of failure and bottlenecks Software as a Service. Offers the ability to add a new functionality without code modifications by using the bytecode instrumentation technique Automatically detection of the application topology that helps understand the configurations of an application Real-time monitoring – observe active threads in real-time. Horizontal scalability to support large-scale server group Transaction code-level visibility – response patterns and request counts. This guide aims to help you deploy Pinpoint APM (Application Performance Management) in Docker Containers. Pinpoint APM Supported Modules Below is a list of modules supported by Pinpoint APM (Application Performance Management): ActiveMQ, RabbitMQ, Kafka, RocketMQ Arcus, Memcached, Redis(Jedis, Lettuce), CASSANDRA, MongoDB, Hbase, Elasticsearch MySQL, Oracle, MSSQL(jtds), CUBRID, POSTGRESQL, MARIA Apache HTTP Client 3.x/4.x, JDK HttpConnector, GoogleHttpClient, OkHttpClient, NingAsyncHttpClient, Akka-http, Apache CXF JDK 7 and above Apache Tomcat 6/7/8/9, Jetty 8/9, JBoss EAP 6/7, Resin 4, Websphere 6/7/8, Vertx 3.3/3.4/3.5, Weblogic 10/11g/12c, Undertow Spring, Spring Boot (Embedded Tomcat, Jetty, Undertow), Spring asynchronous communication Thrift Client, Thrift Service, DUBBO PROVIDER, DUBBO CONSUMER, GRPC iBATIS, MyBatis log4j, Logback, log4j2 DBCP, DBCP2, HIKARICP, DRUID gson, Jackson, Json Lib, Fastjson Deploy Pinpoint APM (Application Performance Management) in Docker Containers Deploying the PInpoint APM docker container can be achieved using the below steps: Step 1 – Install Docker and Docker-Compose on Linux. Pinpoint APM requires a Docker version 18.02.0 and above. The latest available version of Docker can be installed with the aid of the guide below: How To Install Docker CE on Linux Systems Once installed, ensure that the service is started and enabled as below. sudo systemctl start docker && sudo systemctl enable docker Check the status of the service. $ systemctl status docker ● docker.service - Docker Application Container Engine Loaded: loaded (/usr/lib/systemd/system/docker.service; enabled; vendor preset: disabled) Active: active (running) since Wed 2022-01-19 02:51:04 EST; 1min 4s ago Docs: https://docs.docker.com Main PID: 34147 (dockerd) Tasks: 8 Memory: 31.3M CGroup: /system.slice/docker.service └─34147 /usr/bin/dockerd -H fd:// --containerd=/run/containerd/containerd.sock Verify the installed Docker version. $ docker version Client: Docker Engine - Community Version: 20.10.12 API version: 1.41 Go version: go1.16.12 Git commit: e91ed57 Built: Mon Dec 13 11:45:22 2021 OS/Arch: linux/amd64 Context: default Experimental: true
..... Now proceed and install Docker-compose using the dedicated guide below: How To Install Docker Compose on Linux Add your system user to the Docker group to be able to run docker commands without sudo sudo usermod -aG docker $USER newgrp docker Step 2 – Deploy the Pinpoint APM (Application Performance Management) The Pinpoint docker container can be deployed by pulling the official docker image as below. Ensure that git is installed on your system before you proceed. git clone https://github.com/naver/pinpoint-docker.git Once the image has been pulled, navigate into the directory. cd pinpoint-docker Now we will run the Pinpoint container that will have the following containers joined to the same network: The Pinpoint-Web Server Pinpoint-Agent Pinpoint-Collector Pinpoint-QuickStart(a sample application, 1.8.1+) Pinpoint-Mysql(to support certain feature) This may take several minutes to download all necessary images. Pinpoint-Flink(to support certain feature) Pinpoint-Hbase Pinpoint-Zookeeper All these components and their configurations are defined in the docker-compose YAML file that can be viewed below. cat docker-compose.yml Now start the container as below. docker-compose pull docker-compose up -d Sample output: ....... [+] Running 14/14 ⠿ Network pinpoint-docker_pinpoint Created 0.3s ⠿ Volume "pinpoint-docker_mysql_data" Created 0.0s ⠿ Volume "pinpoint-docker_data-volume" Created 0.0s ⠿ Container pinpoint-docker-zoo3-1 Started 3.7s ⠿ Container pinpoint-docker-zoo1-1 Started 3.0s ⠿ Container pinpoint-docker-zoo2-1 Started 3.4s ⠿ Container pinpoint-mysql Sta... 3.8s ⠿ Container pinpoint-flink-jobmanager Started 3.4s ⠿ Container pinpoint-hbase Sta... 4.0s ⠿ Container pinpoint-flink-taskmanager Started 5.4s ⠿ Container pinpoint-collector Started 6.5s ⠿ Container pinpoint-web Start... 5.6s ⠿ Container pinpoint-agent Sta... 7.9s ⠿ Container pinpoint-quickstart Started 9.1s Once the process is complete, check the status of the containers. $ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES cb17fe18e96d pinpointdocker/pinpoint-quickstart "catalina.sh run" 54 seconds ago Up 44 seconds 0.0.0.0:8000->8080/tcp, :::8000->8080/tcp pinpoint-quickstart 732e5d6c2e9b pinpointdocker/pinpoint-agent:2.3.3 "/usr/local/bin/conf…" 54 seconds ago Up 46 seconds pinpoint-agent 4ece1d8294f9 pinpointdocker/pinpoint-web:2.3.3 "sh /pinpoint/script…" 55 seconds ago Up 48 seconds 0.0.0.0:8079->8079/tcp, :::8079->8079/tcp, 0.0.0.0:9997->9997/tcp, :::9997->9997/tcp pinpoint-web 79f3bd0e9638 pinpointdocker/pinpoint-collector:2.3.3 "sh /pinpoint/script…" 55 seconds ago Up 47 seconds 0.0.0.0:9991-9996->9991-9996/tcp, :::9991-9996->9991-9996/tcp, 0.0.0.0:9995-9996->9995-9996/udp,
:::9995-9996->9995-9996/udp pinpoint-collector 4c4b5954a92f pinpointdocker/pinpoint-flink:2.3.3 "/docker-bin/docker-…" 55 seconds ago Up 49 seconds 6123/tcp, 0.0.0.0:6121-6122->6121-6122/tcp, :::6121-6122->6121-6122/tcp, 0.0.0.0:19994->19994/tcp, :::19994->19994/tcp, 8081/tcp pinpoint-flink-taskmanager 86ca75331b14 pinpointdocker/pinpoint-flink:2.3.3 "/docker-bin/docker-…" 55 seconds ago Up 51 seconds 6123/tcp, 0.0.0.0:8081->8081/tcp, :::8081->8081/tcp pinpoint-flink-jobmanager e88a13155ce8 pinpointdocker/pinpoint-hbase:2.3.3 "/bin/sh -c '/usr/lo…" 55 seconds ago Up 50 seconds 0.0.0.0:16010->16010/tcp, :::16010->16010/tcp, 0.0.0.0:16030->16030/tcp, :::16030->16030/tcp, 0.0.0.0:60000->60000/tcp, :::60000->60000/tcp, 0.0.0.0:60020->60020/tcp, :::60020->60020/tcp pinpoint-hbase 4a2b7dc72e95 zookeeper:3.4 "/docker-entrypoint.…" 56 seconds ago Up 52 seconds 2888/tcp, 3888/tcp, 0.0.0.0:49154->2181/tcp, :::49154->2181/tcp pinpoint-docker-zoo2-1 3ae74b297e0f zookeeper:3.4 "/docker-entrypoint.…" 56 seconds ago Up 52 seconds 2888/tcp, 3888/tcp, 0.0.0.0:49155->2181/tcp, :::49155->2181/tcp pinpoint-docker-zoo3-1 06a09c0e7760 zookeeper:3.4 "/docker-entrypoint.…" 56 seconds ago Up 52 seconds 2888/tcp, 3888/tcp, 0.0.0.0:49153->2181/tcp, :::49153->2181/tcp pinpoint-docker-zoo1-1 91464a430c48 pinpointdocker/pinpoint-mysql:2.3.3 "docker-entrypoint.s…" 56 seconds ago Up 52 seconds 0.0.0.0:3306->3306/tcp, :::3306->3306/tcp, 33060/tcp pinpoint-mysql Access the Pinpoint APM (Application Performance Management) Web UI The Pinpoint Web run on the default port 8079 and can be accessed using the URL��http://IP_address:8079. You will be granted the below page. Select the desired application to analyze. For this case, we will analyze our deployed Quickapp. Select the application and proceed. Here, click on inspector to view the detailed metrics. Here select the app-in-docker You can also make settings to Pinpoint such as setting user groups, alarms, themes e.t.c. Under administration, you can view agent statistics for your application Manage your applications under the agent management tab To set an alarm, you first need to have a user group created. you also need to create a pinpoint user and add them to the user group as below. With the user group, an alarm for your application can be created, a rule and notification methods to the group members added as shown. Now you will have your alarm configured as below. You can also switch to the dark theme which appears as below. View the Apache Flink Task manager page using the URL http://IP_address:8081. Voila! We have triumphantly deployed Pinpoint APM (Application Performance Management) in Docker Containers. Now you can discover, trace, and perform diagnoses on your applications.
0 notes
Text
Iconsole application

#Iconsole application code
There are several maven plugins for this, but I will be using protoc-jar-maven-plugin, that wraps protoc executable as a jar so it can run in any OS and compile your.
#Iconsole application code
Automatically, by adding protoc code generation to your maven project build.If you wish to proceed with this method read protoc installation guide here Manually, by downloading protoc in your machine and running it.proto files targeting the desired output language. Ok, protobuf contracts created, now, to generate code (java classes) from this contract, we need to use protoc executable to compile. Open IntelliJ IDEA CE and choose to create a new project.For this example I'll be using OpenJDK 15, IntelliJ IDEA CE and Maven as build tool to do so. That said, let us start by creating the Java console application. The ideal for big and complex projects is to have a separate repository as a neutral ground for projects. proto file will be a common resource in C# and Java but for simplicity sake, I'll recreate it in both projects repository. Well Known Types here or Google Common Types here. There are other scalar types, you can read the documentation here. You have to copy these types definitions file from google repository and paste it in your project whatever the language you are using. Date and Money types are a "Google Common Type", differently than "Well Known Type" you are not able to use it only by importing.Timestamp type is a " Well Known Type" introduced in proto3, you can use these types by importing in the first lines of proto file.First follow instructions of the README file of the Java project repository: If you just want to read some code and figure it out on your own, I've setup these two applications repository. A C# console application that will read the hard coded customer file generated by Java console application, and display the data in console.proto specification to generate a file with a hard coded customer A Java console application that will use the customer.In this example we will be creating two projects: Protobuf is similar to Apache Thrift used by Facebook, Ion by Amazon or Microsoft Bonds Protocol. Protocol buffers can serve as basis for a remote procedure call (RPC) which are widely used for inter-machine communication, most commonly used with gRPC. A program from any language supported is able to generate source code from that description in order to create or parse a stream of bytes that represents the structured data. This protocol involves a specific interface description language to describe the data structure defined in a. Protobuf messages are serialized into a binary wire format which is very compact and boosts performance. It was designed by Google early 2001 (but only publicly released in 2008) to be smaller and faster than XML. Protocol Buffers (protobuf) is a method of serializing structured data which is particulary useful to communication between services or storing data.

0 notes
Link
#BigData#DataLake#Hadoop#HDFS#Hive#Kubernetes#NoSQL#SQL#Большиеданные#контейнеризация#обработкаданных
0 notes
Text
What is the current choice for doing RPC in Python
XML-RPC is part of the Python standard library:
Python 2: xmlrpclib and SimpleXMLRPCServer
Python 3: xmlrpc (both client and server)
Apache Thrift is a cross-language RPC option developed at Facebook. Works over sockets, function signatures are defined in text files in a language-independent way.
0 notes
Text
We typically deliver a message and accumulate a proper away response without cleaning a web page. However, earlier, allowing real-time functionality modified right proper into a big mission for app developers after the present way HTTP extended polling and AJAP, the network of developers has the long run placed a choice to develop real-time packages.
WebSockets WebSockets are upgraded HTTP connections that preserve until the consumer or the server kills the connection through the WebSocket connection. It’s miles viable to perform duplex communication that is an extravagant way to say communication is viable from and to the server the clients the use of this single connection this as an opportunity lowers the amount of network overhead needed to enlarge the real-time apps with the use of WebSockets because of the that there may be non-prevent polling of HTTP endpoints needed.
📷
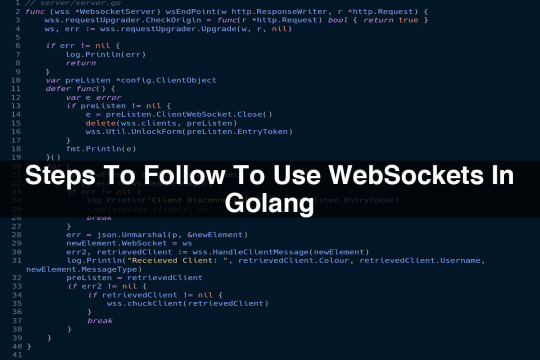
Build a WebSockets in Golang
Step-1: Setting up a handshakeAt first, you need to form an HTTP handler using a WebSocket endpoint: Next, run the WebSocket structure. The consumer typically sends the number one handshake request when the server authenticated a Web Socket request, it has to reply with a response of a handshake.Step-2: Transferring statistics framesOnce you whole the handshake, your software program can have a look at and write to and from the Specification of the WebSockets describes a specific frame format that is finished amongst a server and consumer.Step-3: Closing a handshakeWhen one of the customer sports activities sends a near to border along with a reputation because of the payload, a handshake is closed spontaneously, the third-party sends to the frame can also deliver a close to motive with the payload in case the consumer initiates the closing, the server needs to deliver an equal close to frame in turn.
List of WebSockets in Golang libraries
1. STDLIBThis Web Socket library belongs to the equal vintage library. It applies a server and consumer for the Web Socket protocol you don’t need to install it and it includes reliable documentation. However, on the other hand, it doesn’t have some talents that can be located in a single in each of a kind WebSocket libraries. In the STDLIB (x/internet/WebSocket) package deal, Golang WebSocket packages don’t permit clients to use I/O buffers yet again amongst connections.2. GorillaIn the Gorilla toolkit, the WebSocket package deal talents as an examined and whole software program of the WebSocket protocol and a regular package deal API this Web Socket package deal is easy to use and nicely documented and you can discover its documentation on the reliable web page of Gorilla.
3. GOB WASThis is a small WebSocket package that includes a strong list of talents, like a low-diploma API that lets in the growth of the unusual place, custom packet dealing with and a zero-reproduction upgrade GOBWAS doesn’t need intermediate allocations within the route of I/O. Moreover, its talented high-diploma helpers and wrappers at the end of the API within the WsUtil package, allowing developers to begin speedy without analyzing the protocol’s internals.4. GOWebsocketsThis Golang device offers an in-depth arrays. It allows for putting request headers, compressing information, and controlling concurrency. It assists proxies and subprotocols for transmitting and getting binary information and text.
Conclusion This instructional has covered some of the fundamentals of WebSockets and to grow a clean WebSocket based complete app in Golang extraordinary tool besides the tool, someone in each kind of possible packages permits developers to grow strong streaming solutions they include package RPC, gRPC, Apache Thrift, and go-socket. The supply of well-documented equipment like WebSocket’s and the non-save you development of streaming technology makes it smooth for builders to build up real-time apps.
0 notes
Text
BIG DATA SERVICES

Coding Brains is the top software service provider company supporting clients capitalize on the transformational potential of Big Data.
Utilizing our business domain expertise, we assist clients in integrating Big Data into their over all IT architecture and implement the Big Data Solution to take your business to a whole new level. With the belief that companies will rely on Big Data for business decision making, our team has focused on the delivery and deployment of Big Data solutions to assist corporations with strategic decision making.
Our Services related to Big Data analytics support in analyzing the information to give you smart insights into new opportunities. Our data scientists consist of a unique approach to develop services that analyze each piece of information before making any critical business decision. Big Data Analytics Consulting & Strategy support you to opt for an appropriate technology that complements your data warehouse.
APACHE HADOOP
With the utilization of Apache Hadoop consulting, we help Business verticals to leverage the advantage of a large amount of information by organizing it in an appropriate way to gain smarter insights. We have a team of professionals who gain upper hand in Big Data technology and expert in offering integrated services across the Hadoop ecosystem of HDFS, Map Reduce, Sqoop, Oozie, and Flume.
APACHE HIVE
At Coding Brains, Our Hive development and integration services are designed to enable SQL developers to write Hive Query Language statements that are similar to standard SQL ones. Our objective to bring the familiarity of relational technology to big data processing utilizing HQL and other structures and processes of relational databases.
APACHE MAHOUT
We offer solutions related to Apache Mahout designed to make business intelligence apps. Our team specializes in developing scalable applications that meet user expectations. Focused on deriving smarter insights, we have expertise in Apache Mahout and proficiency in implementing Machine Learning algorithms.
APACHE PIG
Coding Brains offers services in Apache Pig, an open- source platform and a high-level data analysis language that is utilized to examine large data sets. Our Big Data Professionals use Pig to execute Hadoop jobs in MapReduce and Apache Spark. We help simplify the implementation of technology and navigate the complexities.
APACHE ZOOKEEPER
Our team delivers high-end services in Apache ZooKeeper, an open-source project dealing with managing configuration information, naming, as well as group solutions that are deployed on the Hadoop cluster to administer the infrastructure.
APACHE KAFKA
As a leading IT Company, We provide comprehensive services in Apache Kafka, a streaming platform. Our Big Data team expert in developing enterprise-grade streaming apps as well as for streaming data pipelines that present the opportunity to exploit information in context-rich scenarios to drive business results.
NOSQL DATABASE
Our services provide elements such as quality, responsiveness, and consistency to deliver development solutions for exceptional results. We understand your business-critical requirement and deliver NoSQL technologies that are most appropriate for your apps. We support enterprises to seize new market opportunities and strategically respond to threats by empowering better client experiences.
APACHE SPARK
Our expert team of professionals provides Apache Spark solutions to companies worldwide providing high-performance advantages and versatility. In order to stay ahead and gain the business benefit, we offer processing and analysis to support the Big Data apps utilizing options like machine learning, streaming analytics and more.
APACHE THRIFT
We support enterprises to deal with the complex situation where polyglot systems make the overall administration complicated. Exploiting Apache Thrift, we enable diverse modules of a system to cross-communicate flawlessly and integrate various aspects of the IT infrastructure.
Contact Us
0 notes
Link
0 notes
Text
How can I install Apache Cassandra 4.0 on CentOS 8 | Rocky Linux 8 machine?. Apache Cassandra is a free and open-source NoSQL database management system designed to be distributed and highly available. Cassandra can handle large amounts of data across many commodity servers without any single point of failure. This guide will walk you through the installation of Cassandra on CentOS 8 | Rocky Linux 8. After installation is done, we’ll proceed to do configurations and tuning of Cassandra to work with machines having minimal resources available. Features of Cassandra Cassandra provides the Cassandra Query Language (CQL), an SQL-like language, to create and update database schema and access data. CQL allows users to organize data within a cluster of Cassandra nodes using: Keyspace: defines how a dataset is replicated, for example in which datacenters and how many copies. Keyspaces contain tables. Table: defines the typed schema for a collection of partitions. Cassandra tables have flexible addition of new columns to tables with zero downtime. Tables contain partitions, which contain partitions, which contain columns. Partition: defines the mandatory part of the primary key all rows in Cassandra must have. All performant queries supply the partition key in the query. Row: contains a collection of columns identified by a unique primary key made up of the partition key and optionally additional clustering keys. Column: A single datum with a type which belong to a row. Cassandra has support for the following client drivers: Java Python Ruby C# / .NET Nodejs PHP C++ Scala Clojure Erlang Go Haskell Rust Perl Elixir Dart Install Apache Cassandra 4.0 on CentOS 8 | Rocky Linux 8 Java is required for running Cassandra on CentOS 8 | Rocky Linux 8. As of this writing, required version of Java is 8. If you want to use cqlsh, you need the latest version of Python 2.7. Step 1: Install Java 8 and Python and cqlsh Install Python3 Pip and OpenJDK 8 on your CentOS / Rocky Linux 8: sudo yum install python3 python3-pip java-1.8.0-openjdk java-1.8.0-openjdk-devel Install cqsh using pip3 Python package manager: sudo pip3 install cqlsh tox Ensure the install is successful: .... Collecting importlib-metadata; python_version < "3.8" (from click->geomet=0.1->cassandra-driver->cqlsh) Downloading https://files.pythonhosted.org/packages/71/c2/cb1855f0b2a0ae9ccc9b69f150a7aebd4a8d815bd951e74621c4154c52a8/importlib_metadata-4.8.1-py3-none-any.whl Collecting zipp>=0.5 (from importlib-metadata; python_version < "3.8"->click->geomet=0.1->cassandra-driver->cqlsh) Downloading https://files.pythonhosted.org/packages/bd/df/d4a4974a3e3957fd1c1fa3082366d7fff6e428ddb55f074bf64876f8e8ad/zipp-3.6.0-py3-none-any.whl Collecting typing-extensions>=3.6.4; python_version < "3.8" (from importlib-metadata; python_version < "3.8"->click->geomet=0.1->cassandra-driver->cqlsh) Downloading https://files.pythonhosted.org/packages/74/60/18783336cc7fcdd95dae91d73477830aa53f5d3181ae4fe20491d7fc3199/typing_extensions-3.10.0.2-py3-none-any.whl Installing collected packages: thrift, cql, zipp, typing-extensions, importlib-metadata, click, geomet, cassandra-driver, cqlsh Running setup.py install for thrift ... done Running setup.py install for cql ... done Successfully installed cassandra-driver-3.25.0 click-8.0.3 cql-1.4.0 cqlsh-6.0.0 geomet-0.2.1.post1 importlib-metadata-4.8.1 thrift-0.15.0 typing-extensions-3.10.0.2 zipp-3.6.0 Confirm the installation of Java and cqlsh. $ java -version openjdk version "1.8.0_312" OpenJDK Runtime Environment (build 1.8.0_312-b07) OpenJDK 64-Bit Server VM (build 25.312-b07, mixed mode) $ cqlsh --version cqlsh 6.0.0 Step 2: Install Apache Cassandra 4.0 on CentOS 8 | Rocky Linux 8 Now that Java and Python are installed. Let’s now add Cassandra repository to our CentOS / Rocky system. sudo tee /etc/yum.repos.d/cassandra.repo
0 notes
Text
300+ TOP CASSANDRA Interview Questions and Answers
CASSANDRA Interview Questions for freshers experienced :-
1. What is Cassandra? Cassandra is an open source data storage system developed at Facebook for inbox search and designed for storing and managing large amounts of data across commodity servers. It can server as both Real time data store system for online applications Also as a read intensive database for business intelligence system OR Apache Cassandra is an open source, distributed and decentralized/distributed storage system (database), for managing very large amounts of structured data spread out across the world. It provides highly available service with no single point of failure.It was developed at Facebook for inbox search and it was open-sourced by Facebook in July 2008. 2. What was the design goal of Cassandra? The design goal of Cassandra is to handle big data workloads across multiple nodes without any single point of failure. 3. What is NoSQLDatabase? NoSQL database (sometimes called as Not Only SQL) is a database that provides a mechanism to store and retrieve data other than the tabular relations used in relational databases. These databases are schema-free, support easy replication, have simple API, eventually consistent, and can handle huge amounts of data. 4. Cassandra is written in which language? Java 5. How many types of NoSQL databases? Document Stores (MongoDB, Couchbase) Key-Value Stores (Redis, Volgemort) Column Stores (Cassandra) Graph Stores (Neo4j, Giraph) 6. What do you understand by composite type? Composite Type is a cool feature of Hector and Cassandra.It allow to define a key or a column name with a concatenation of data of different type.With CassanraUnit, you can use CompositeType in 2 places : row key column name 7. What is mandatory while creating a table in Cassandra? While creating a table primary key is mandatory, it is made up of one or more columns of a table. 8. What is the relationship between Apache Hadoop, HBase, Hive and Cassandra? Apache Hadoop, File Storage, Grid Compute processing via Map Reduce. Apache Hive, SQL like interface ontop of hadoop. Apache Hbase, Column Family Storage built like BigTable Apache Cassandra, Column Family Storage build like BigTable with Dynamo topology and consistency. 9. List out some key features of Apache Cassandra? It is scalable, fault-tolerant, and consistent. It is a column-oriented database. Its distribution design is based on Amazon’s Dynamo and its data model on Google’s Bigtable. Created at Facebook, it differs sharply from relational database management systems. Cassandra implements a Dynamo-style replication model with no single point of failure, but adds a more powerful “column family” data model. Cassandra is being used by some of the biggest companies such as Facebook, Twitter, Cisco, Rackspace, ebay, Twitter, Netflix, and more. 10. What do you understand by Data Replication in Cassandra? Database replication is the frequent electronic copying data from a database in one computer or server to a database in another so that all users share the same level of information. Cassandra stores replicas on multiple nodes to ensure reliability and fault tolerance. A replication strategy determines the nodes where replicas are placed. The total number of replicas across the cluster is referred to as the replication factor. A replication factor of 1 means that there is only one copy of each row on one node. A replication factor of 2 means two copies of each row, where each copy is on a different node. All replicas are equally important; there is no primary or master replica. As a general rule, the replication factor should not exceed the number of nodes in the cluster. However, you can increase the replication factor and then add the desired number of nodes later.

CASSANDRA Interview Questions 11. What do you understand by Node in Cassandra? Node is the place where data is stored. 12. What do you understand by Data center in Cassandra? Data center is a collection of related nodes. 13. What do you understand by Cluster in Cassandra? Cluster is a component that contains one or more data centers. 14. What do you understand by Commit log in Cassandra? Commit log is a crash-recovery mechanism in Cassandra. Every write operation is written to the commit log. 15. What do you understand by Mem-table in Cassandra? Mem-table is a memory-resident data structure. After commit log, the data will be written to the mem-table. Sometimes, for a single-column family, there will be multiple mem-tables. 16. What do you understand by SSTabl in Cassandra? SSTable is a disk file to which the data is flushed from the mem-table when its contents reach a threshold value. 17. What do you understand by Bloom filter in Cassandra? Bloom filter are nothing but quick, nondeterministic, algorithms for testing whether an element is a member of a set. It is a special kind of cache. Bloom filters are accessed after every query. 18. What do you understand by CQL? User can access Cassandra through its nodes using Cassandra Query Language (CQL. CQL treats the database (Keyspace) as a container of tables. Programmers use cqlsh: a prompt to work with CQL or separate application language drivers. 19. What do you understand by Column Family? Column family is a container for an ordered collection of rows. Each row, in turn, is an ordered collection of columns. 20. What is the use of "void close()" method? This method is used to close the current session instance. 21. What is the use of "ResultSet execute(Statement statement)" method? This method is used to execute a query. It requires a statement object. 22. Which command is used to start the cqlsh prompt? Cqlsh 23. What is the use of "cqlsh --version" command? This command will provides the version of the cqlsh you are using. 24. What are the collection data types provided by CQL? List : A list is a collection of one or more ordered elements. Map : A map is a collection of key-value pairs. Set : A set is a collection of one or more elements. 25. What is Cassandra database used for? Apache Cassandra is a second-generation distributed database originally open-sourced by Facebook. Its write-optimized shared-nothing architecture results in excellent performance and scalability. The Cassandra storage cluster and S3 archival layer are designed to expand horizontally to any arbitrary size with linear cost.Cassandra’s memory footprint is more dependent on the number of column families than on the size of the data set. Cassandra scales pretty well horizontally for storage and IO, but not for memory footprint, which is tied to your schema and your cache settings regardless of the size of your cluster. some of the important link about casandara is available-here. 26. What is the syntax to create keyspace in Cassandra? Syntax for creating keyspace in Cassandra is CREATE KEYSPACE WITH 27. What is a keyspace in Cassandra? In Cassandra, a keyspace is a namespace that determines data replication on nodes. A cluster consist of one keyspace per node. 28. What is cqlsh? cqlsh is a Python-based command-line client for cassandra. 29. Does Cassandra works on Windows? Yes, Cassandra works pretty well on windows. Right now we have linux and windows compatible versions available. 30. What do you understand by Consistency in Cassandra? Consistency means to synchronize and how up-to-date a row of Cassandra data is on all of its replicas. 31. Explain Zero Consistency? In this write operations will be handled in the background, asynchronously. It is the fastest way to write data, and the one that is used to offer the least confidence that operations will succeed. 32. What do you understand by Thrift? Thrift is the name of the RPC client used to communicate with the Cassandra server. 33. What do you understand by Kundera? Kundera is an object-relational mapping (ORM) implementation for Cassandra written using Java annotations. 34. JMX stands for? Java Management Extension 35. How does Cassandra write? Cassandra performs the write function by applying two commits-first it writes to a commit log on disk and then commits to an in-memory structured known as memtable. Once the two commits are successful, the write is achieved. Writes are written in the table structure as SSTable (sorted string table). Cassandra offers speedier write performance. 36. When to use Cassandra? Being a part of NoSQL family Cassandra offers solution for problem where your requirement is to have very heavy write system and you want to have quite responsive reporting system on top of that stored data. Consider use case of Web analytic where log data is stored for each request and you want to built analytical platform around it to count hits by hour, by browser, by IP, etc in real time manner. 37. When should you not use Cassandra? OR When to use RDBMS instead of Cassandra? Cassandra is based on NoSQL database and does not provide ACID and relational data property. If you have strong requirement of ACID property (for example Financial data), Cassandra would not be a fit in that case. Obviously, you can make work out of it, however you will end up writing lots of application code to handle ACID property and will loose on time to market badly. Also managing that kind of system with Cassandra would be complex and tedious for you. 38. What are secondary indexes? Secondary indexes are indexes built over column values. In other words, let’s say you have a user table, which contains a user’s email. The primary index would be the user ID, so if you wanted to access a particular user’s email, you could look them up by their ID. However, to solve the inverse query given an email, fetch the user ID requires a secondary index. 39. When to use secondary indexes? You want to query on a column that isn't the primary key and isn't part of a composite key. The column you want to be querying on has few unique values (what I mean by this is, say you have a column Town, that is a good choice for secondary indexing because lots of people will be form the same town, date of birth however will not be such a good choice). 40. When to avoid secondary indexes? Try not using secondary indexes on columns contain a high count of unique values and that will produce few results. 41. I have a row or key cache hit rate of 0.XX123456789 reported by JMX. Is that XX% or 0.XX% ? XX% 42. What happens to existing data in my cluster when I add new nodes? When a new nodes joins a cluster, it will automatically contact the other nodes in the cluster and copy the right data to itself. 43. What are "Seed Nodes" in Cassandra? A seed node in Cassandra is a node that is contacted by other nodes when they first start up and join the cluster. A cluster can have multiple seed nodes. Seed node helps the process of bootstrapping for a new node joining a cluster. Its recommended to use the 2 seed node per data center. 44. What are "Coordinator Nodes" in Cassandra? Coordinator Nodes: Its a node which receive the request from client and send the request to the actual node depending upon the token. So all the nodes acts as coordinator node,because every node can receive a request and proxy that request. 45. What are the befefits of NoSQL over relational database? NoSQL overcome the weaknesses that the relational data model does not address well, which are as follows: Huge volume of sructured, semi-structured, and unstructured data Flexible data model(schema) that is easy to change Scalability and performance for web-scale applications Lower cost Impedance mismatch between the relational data model and object-oriented programming Built-in replication Support for agile software development 46. What ports does Cassandra use? By default, Cassandra uses 7000 for cluster communication, 9160 for clients (Thrift), and 8080 for JMX. These are all editable in the configuration file or bin/cassandra.in.sh (for JVM options. All ports are TCP. 47. What do you understand by High availability? A high availability system is the one that is ready to serve any request at any time. High avaliability is usually achieved by adding redundancies. So, if one part fails, the other part of the system can serve the request. To a client, it seems as if everything worked fine. 48. How Cassandra provide High availability feature? Cassandra is a robust software. Nodes joining and leaving are automatically taken care of. With proper settings, Cassandra can be made failure resistant. That means that if some of the servers fail, the data loss will be zero. So, you can just deploy Cassandra over cheap commodity hardware or a cloud environment, where hardware or infrastructure failures may occur. 49. Who uses Cassandra? Cassandra is in wide use around the world, and usage is growing all the time. Companies like Netflix, eBay, Twitter, Reddit, and Ooyala all use Cassandra to power pieces of their architecture, and it is critical to the day-to-da operations of those organizations. to date, the largest publicly known Cassandra cluster by machine count has over 300TB of data spanning 400 machines. Because of Cassandra's ability to handle high-volume data, it works well for a myriad of applications. This means that it's well suited to handling projects from the high-speed world of advertising technology in real time to the high-volume world of big-data analytics and everything in between. It is important to know your use case before moving forward to ensure things like proper deployment and good schema design. 50. When to use secondary indexes? You want to query on a column that isn't the primary key and isn't part of a composite key. The column you want to be querying on has few unique values (what I mean by this is, say you have a column Town, that is a good choice for secondary indexing because lots of people will be form the same town, date of birth however will not be such a good choice). 51. When to avoid secondary indexes? Try not using secondary indexes on columns contain a high count of unique values and that will produce few results. 52. What do you understand by Snitches? A snitch determines which data centers and racks nodes belong to. They inform Cassandra about the network topology so that requests are routed efficiently and allows Cassandra to distribute replicas by grouping machines into data centers and racks. Specifically, the replication strategy places the replicas based on the information provided by the new snitch. All nodes must return to the same rack and data center. Cassandra does its best not to have more than one replica on the same rack. 53. What is Hector? Hector is an open source project written in Java using the MIT license. It was one of the early Cassandra clients and is used in production at Outbrain. It wraps Thrift and offers JMX, connection pooling, and failover. 54. What do you understand by NoSQL CAP theorem? Consistency: means that data is the same across the cluster, so you can read or write to/from any node and get the same data. Availability: means the ability to access the cluster even if a node in the cluster goes down. Partition: Tolerance means that the cluster continues to function even if there is a "partition" (communications break) between two nodes (both nodes are up, but can't communicate). In order to get both availability and partition tolerance, you have to give up consistency. Consider if you have two nodes, X and Y, in a master-master setup. Now, there is a break between network comms in X and Y, so they can't synch updates. At this point you can either: A) Allow the nodes to get out of sync (giving up consistency), or B) Consider the cluster to be "down" (giving up availability) All the combinations available are: CA - data is consistent between all nodes - as long as all nodes are online - and you can read/write from any node and be sure that the data is the same, but if you ever develop a partition between nodes, the data will be out of sync (and won't re-sync once the partition is resolved). CP - data is consistent between all nodes, and maintains partition tolerance (preventing data desync) by becoming unavailable when a node goes down. AP - nodes remain online even if they can't communicate with each other and will resync data once the partition is resolved, but you aren't guaranteed that all nodes will have the same data (either during or after the partition) 55. What is Keyspace in Cassandra? Before doing any work with the tables in Cassandra, we have to create a container for them, otherwise known as a keyspace. One of the main uses for keyspaces is defining a replication mechanism for a group of tables. Example: CREATE KEYSPACE used_cars WITH replication = { 'class': 'SimpleStrategy', 'replication_factor' : 1}; 56. Explain Cassandra data model? The Cassandra data model has 4 main concepts which are cluster, keyspace, column, column family. Clusters contain many nodes(machines) and can contain multiple keyspaces. A keyspace is a namespace to group multiple column families, typically one per application. A column contains a name, value and timestamp. A column family contains multiple columns referenced by a row keys. 57. Can you add or remove Column Families in a working Cluster? Yes, but keeping in mind the following processes. Do not forget to clear the commitlog with ‘nodetool drain’ Turn off Cassandra to check that there is no data left in commitlog Delete the sstable files for the removed CFs 58. What is Replication Factor in Cassandra? ReplicationFactor is the measure of number of data copies existing. It is important to increase the replication factor to log into the cluster. 59. Can we change Replication Factor on a live cluster? Yes, but it will require running repair to alter the replica count of existing data. 60. How to iterate all rows in ColumnFamily? Using get_range_slices. You can start iteration with the empty string and after each iteration, the last key read serves as the start key for next iteration. CASSANDRA Questions and Answers pdf Download Read the full article
0 notes