#Affiliate network software
Explore tagged Tumblr posts
Text
Best affiliate software for saas with a free demo
In today's fast-paced business landscape, the power to control, monitor, and make informed decisions in real time can be a game-changer. Imagine having the ability to track leads, manage payments, analyze traffic, and more, all in real time. This is where our innovative software steps in, offering you a comprehensive solution to streamline your operations seamlessly.
Real-Time Capabilities: Stay Ahead of the Curve
Our software empowers you with real-time capabilities that extend beyond traditional management tools. From tracking your business's performance to evaluating leads and monitoring traffic, every bit of information is at your fingertips instantly. By harnessing the power of real-time data, you gain a competitive edge by making prompt and accurate decisions to propel your business forward.
Image: A dynamic dashboard displaying real-time analytics.
Making Informed Decisions for Business Growth
The ability to access crucial data in real time enables you to make informed decisions that drive business growth. Whether it's identifying potential leads, optimizing payment processes, or analyzing website traffic patterns, our software provides you with the insights needed to enhance your strategies proactively. With a holistic view of your operations in real time, you can adapt swiftly to market changes and seize new opportunities as they arise.
Affordable Network Management Software Tailored to Your Needs
Apart from its real-time capabilities, our software offers the distinct advantage of affordability. We understand the diverse needs of businesses, which is why we provide network management solutions that are not only powerful but also cost-effective. Our affordable pricing model ensures that you get access to cutting-edge technology without breaking the bank. Empowering your business with the tools it needs should be accessible to all, and our software makes that a reality.
Image: An illustration showcasing the seamless integration of our software with existing networks.
Embrace the Future of Business Management
In a digital age where agility and efficiency are paramount, our software stands out as a beacon of innovation. By unleashing the potential of real-time control and affordable network management, we pave the way for businesses to thrive in a dynamic environment. Take the reins of your operations, harness the power of instant insights, and witness the transformative impact on your business performance.
Experience the difference with our software - where real-time meets affordability to unlock a world of possibilities for your business.
Image: A visual representation of business success through effective network management.
Embrace innovation, seize opportunities, and steer your business toward a brighter future with our cutting-edge software. The time to take control in real-time is now. Let's embark on this transformative journey together!
In conclusion, our software offers a revolutionary approach to business management with real-time capabilities and affordability at its core. Make the switch today and elevate your business to new heights!
Note: The website's name and business type are provided for context purposes only and are not part of the blog post content.
If you want to know more about the Affiliate software, please click on the Affiliate software.

#Affiliate network software#Software affiliate network#Affiliate network tracking software#Affiliate network programs#Affiliate network website#List of all affiliate networks#Affiliate network management software#Best affiliate network software#Free affiliate network software#Affiliate network tool
0 notes
Text
Unlocking the Power of Affiliate Network Software for Business Success: A Journey into the Unknown

In today's fast-paced business environment, entrepreneurs need efficient tools to scale their operations. Multi-Level Marketing (MLM) software has emerged as a game-changer in this regard. It streamlines operations, enhances growth opportunities, and provides valuable insights. In fact, companies using MLM software have reported up to a 30% increase in sales due to better tracking and engagement. Let’s explore the essential features of MLM software and how a thoughtful development process can lead to significant business growth.
Understanding MLM Software
MLM software is specifically designed to ease the management of multi-level marketing structures. This software simplifies various aspects, such as recruitment, sales tracking, and commission management. For example, a direct selling company might find it challenging to manage three levels of sales agents, especially when they have different commission rates. MLM software automates these complicated calculations, personalizing support for each agent and allowing the company to focus on broader growth strategies.
This software is crucial for achieving higher profitability while ensuring transparency and accountability. It helps track sales, manage commissions, and communicate effectively across different levels of the organization.
If you want to try our software, please click on the Affiliate network software.

#Software affiliate network#affiliate network tracking software#affiliate network programs#affiliate network website#list of all affiliate networks#affiliate network management software#best affiliate network software#free#affiliate network tool#Network Marketing#MLM#Multi-level marketing#Direct selling#Affordable#Budget#Cheap#Free demo#Binary#MAtrix#Unilevel#Step up plan
0 notes
Text
Best affiliate marketing companies software for saas with a free demo
Quite possibly the most rewarding method for making automated revenue is member advertising. Basically, it permits organizations to publicize their items through a member in return for a commission. Contrasted with conventional promoting, this altogether increments crowd go after less expense and hazard.
So, making an effective partner showcasing program requires technique, and utilizing offshoot promoting programming is a major one. Here are the absolute best partner promoting stages to assist you with kicking off, regulate, and extend your offshoot showcasing drives.
1. Refersion 2. Post Affiliate Pro 3. Tapfiliate 4. LeadDyno 5. Everflow 6. Affiliatly 7. TUNE 8. PartnerStack 9. iDevAffiliate 10. FlexOffers
Read More...

#Affiliate marketing management software#Affiliate marketing management system#Affiliate marketing systems software#Affiliate marketing manager software#Network Marketing#Affordable software
0 notes
Text
MLM Integrated E-Commerce: A High-Yield Collaboration for Business Profitability

In today’s business world, combining Multi-Level Marketing (MLM) with E-Commerce is emerging as a powerful strategy for maximizing profitability. This collaboration merges the personal, relationship-driven aspects of MLM with the scalability and convenience of E-commerce, creating a high-yield business model.
Understanding MLM and E-Commerce
MLM relies on direct selling through a network of distributors, who earn commissions from their sales and the sales of their recruits. The structure allows for exponential growth as new distributors join and expand the network.
Ecommerce, on the other hand, refers to selling products or services online, providing businesses with access to a vast customer base and streamlined, low-cost operations. The rapid rise of digital commerce has made it a vital tool for modern businesses.
Benefits of MLM and Ecommerce Integration
1. Expanded Sales Reach
Combining MLM with Ecommerce allows businesses to reach a global audience. Distributors can sell products online and recruit new members from different regions, extending their influence far beyond local markets.
2. Lower Costs
Ecommerce reduces overhead expenses, eliminating the need for physical storefronts and streamlining inventory management and shipping. This allows MLM businesses to operate with lower costs while increasing profitability.
3. Automation
Ecommerce platforms provide tools to automate marketing and sales processes, such as lead generation, customer follow-ups, and personalized campaigns. MLM distributors can use these tools to increase efficiency and focus on recruiting and selling.
4. Customer Retention
MLM’s focus on building personal relationships aligns well with Ecommerce’s ability to create loyalty programs and offer subscription services. This encourages repeat purchases and fosters customer loyalty, driving long-term profitability.
Synergies for Profitability
Integrating MLM with Ecommerce enhances scalability and global reach. Distributors can manage larger networks with minimal infrastructure while using Ecommerce tools to increase sales and conversions. The ease of entry for new participants, combined with low overhead costs, makes this model particularly attractive for entrepreneurs.
Challenges of Integration
Despite the advantages, there are challenges. MLM's reputation has often been scrutinized due to concerns about unethical practices. Ensuring transparency and ethical operations is critical to avoiding skepticism. Additionally, balancing recruitment with product sales can be difficult. MLM companies must prioritize sales over recruitment to avoid legal and reputational risks.
Regulatory compliance is another issue, as Ecommerce introduces complexities, especially when operating across borders. Ensuring the business adheres to both MLM and ecommerce regulations is essential for sustainability.
Future Trends As social commerce and influencer marketing continue to rise, MLM E-Commerce integration is poised to benefit from these trends. Personal recommendations from influencers align perfectly with MLM’s word-of-mouth model. Additionally, advancements in AI and big data analytics will allow distributors to optimize their sales strategies, enhancing customer targeting and increasing conversion rates.
Conclusion
MLM integrated with e-commerce offers businesses the opportunity to scale globally, reduce costs, and drive higher sales and conversions. This collaboration is an effective way to increase profitability while leveraging the strengths of both models. However, success requires addressing challenges related to reputation, compliance, and network management. The future looks bright for businesses that embrace this high-yield collaboration.
#mlm#mlm software#mlm business#networkmarketing#affiliate marketing#mlmbusiness#multilevelmarketing#mlm companies#ecommerce integration#ecommercebusiness#mlmecomemerceintegration#ecommerce#network marketing business#networkmarketingsoftware
0 notes
Text
#MLM Resources#Affiliate MLM Sofftware#Free affiliate tracking software#Best and Free demo#Affordable#Direct selling#Network marketing
0 notes
Text
#MLM Software cheap#MLM Software demo#Affiliate Marketing#Network Marketing#Direct Selling Software#Affordable MLM software#USA#UK#Brazil
0 notes
Text
#Affiliate marketing management software#Affiliate marketing management system#Affiliate marketing systems software#Affiliate marketing manager software#Network Marketing#Direct selling#Affordable software#MLM#Free demo#Best affiliate white label#Multi level marketing
0 notes
Text
My Open-Source Tolkien Studies Data Sets
One of the best parts of being an independent scholar is that I get to be generous with my research. I am not counting on it for a job, and frankly, between teaching at a small rural school and running the Silmarillion Writers' Guild, I will likely never be able to do all that I want to do with the data that I collect and so love the idea that someone might do something with it.
Because I do love making sets of data. Everything from the mind-numbing copy/paste data entry to learning new spreadsheet formulas is enjoyable to me. I'm an introvert in a very extraverted profession, and after a day of being all on for my students, turning everything into numbers is like a cup of tea under a warm blanket with a Golden Retriever at my feet.
So please use these data sets if they interest you. Play with them. Write about and share what you notice. Expand and build on them. Publish using them. If you use my data or work, credit Dawn Walls-Thumma and link to my website, dawnfelagund.com, if possible. I'd also love if you'd let me know if you share anything using them.
Consolidated Timelines. I made this back in 2013. I was trying to arrange all of Tolkien's timelines side by side. I did some weird things with numbers that I'm not sure I fully understand now, but maybe you can make sense of this or maybe you just want everything Tolkien said about timelines in one handy document. (Make a copy of the Consolidated Timelines.)
Fanfiction Archive Timeline. Made for the 2023 Fan Studies Network North America conference, this timeline-on-a-spreadsheet shows archives in the Tolkien and Harry Potter fandoms, multifandom archives, and social networks and when they came online, were active, became inactive, and went offline, along with data about affiliated communities, software, and rescue efforts. I update this timeline annually with that year's data and will continue to add new archives when I have enough data to do so. (Make a copy of the Fanfiction Archive Timeline spreadsheet.)
References to Sources in the Works of J.R.R. Tolkien. In this document, I record each time a narrator's source is mentioned or alluded to. Ideally, this will one day include The Hobbit and The Lord of the Rings as well! For now, it is just The Silmarillion for the selfish reason that I'm predominantly a Silmarillion researcher. (Make a copy of the References to Sources.)
Silmarillion Characters. A list of all of the characters in The Silmarillion, demographic data about them, the number of times they are mentioned, various aliases, and which "books" of The Silmarillion they appear in. The latter part is a work-in-progress. (Make a copy of Silmarillion Characters.)
Silmarillion Death Scenes (spreadsheet | document). For last year's Tolkien at UVM and Oxonmoot conferences, I collected every death scene in the Quenta Silmarillion and recorded various details about character demographics, cause of death, and grief and mourning rituals. (Make a copy of the spreadsheet. Make a copy of the document.)
The Silmarillion: Who Speaks? This is my newest project, which I hope to complete by the end of the year, documenting which characters get to speak actual words, the number of words they speak, and demographics about the speaking characters. Eventually, I would like to include as well characters who are mentioned as having spoken without being given actual dialogue, but one step at a time. Again, this is a work-in-progress. I have just started working on it. Come back in 2025 and, hopefully, there will be interesting stuff to see.
112 notes
·
View notes
Note
I am willing to give you or anyone else on tumblr the skills and advice the helped me get my dream job
the idea of working for TEK a few months ago would just be a fantasy
my background in education is English. I learned what I know now on my own and only by random chance.
This is why I am so critical of the linux commumity on tumblr.
They're tagging themselves as -official when they can't provide casual end user support.
They're entirely too horny to be in this sphere. Computers and linux should not be about how much you want to fuck/be fucked by X
it will deter end users
This is very cool that you will help other tumblr users with this stuff; i may actually take you up on this at some point :3
(my tone here is /g, /pos, /nm, /lh)
I do, however, kind of disagree with the other points. I think that for any other social media it's correct, twt or fb does not have the culture to make these sorts of parody accounts viable or not-counter-productive to increasing the linux market share. But I don't think that tumblr is the same.
I think that tumblr does. I think the tumblr community has always been this somewhat ephemeral yet perpetual inside joke culture where almost every user is in-the-know, and new users to the joke are able generally able to catch on quickly to it due to their general understanding of they way tumblr communities operate.
IMO, it's a somewhat quick pipeline of:
\> find first "x-official" blog -> assume it's real -> see them horny posting about xenia -> infer that RH corporate would probably not approve of such a blog
I can appreciate that it might be intimidating to seek out help as a new linux user, and especially a new linux & tumblr user, but looking through these blogs, you do see them helping out people ^^. heck, my last post was helping someone getting wayland working on an nvidia system.
The main goal of these blogs is not to be a legitimate CS service to general end-users. they aren't affiliated with the software their blog is named after, so in many cases they *cant*. The goal is instead to foster a community around linux, creating a general network of blogs of the various FOSS projects that they enjoy.
I think that final sentiment, of these blogs detering end users, is most likely counter to their actual effect on end users who are considering switching to linux.
We all know a lot of tumblr is 20 or 30 something year olds who have just stuck around since ~2012ish, and new users to tumblr join with pre-existing knowledge of the culture and platform. Almost anyone coming across these blogs are going to be people who can see the "in" joke, and acclimate. I do highly doubt that a random facebook mom who's son convinced her to install mint on her old laptop would find tumblr, find a -official blog, scroll through said blog, and be detered from using mint.
The other side of this is that any tumblr users who come across these blogs, be it with an inkling of desire to switch to linux or not, will see a vibrant and active community that fits very well into the tumblr community. They remember, or have heard of, the amtrac & OSHA blogs, and are therefore probably aware that this is a pre-existing meme on here.
In all likelyhood, this will probably further incentivize them to make the switch, as they would be more attracted to a community of their peers over a community of redditors telling them to read the arch wiki repeatedly
I can, on the other hand, definitely see that for people who have difficulties with parsing tone, and especially sarcasm, would have trouble with this. TBH, I have these difficulties (hence when I was speaking to you yesterday I used the /unjerk indicator, as I couldn't tell what the tone of the conversation was), and so it took me a little while of being in this weird "I'm 99% sure these *aren't* official, but what if?". I have been there forI think that maybe being more transparent with the fact that the blogs are parodies is probably important. I'm guilty of this, and after i post this, i'll add it to my bio.
#i use arch btw#they should switch to xenia#tux is so mid#penguins of madagascar was better#linuxposting#linux#distros#ask#mipseb
49 notes
·
View notes
Text
#Best CRM for MLM software#mlm hybrid marketing plan#MLM software programs cheap#Direct selling#Network marekting#Affiliate marekting#MLM business#10 to 20 mlm software
0 notes
Text
Unraveling the Potential of MLM Software for Business Growth: A Closer Look at Our Development Process
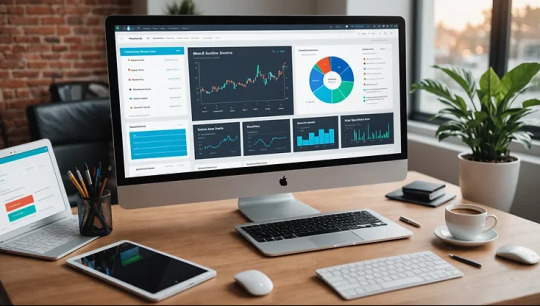
In today's fast-paced business environment, entrepreneurs need efficient tools to scale their operations. Multi-Level Marketing (MLM) software has emerged as a game-changer in this regard. It streamlines operations, enhances growth opportunities, and provides valuable insights. In fact, companies using MLM software have reported up to a 30% increase in sales due to better tracking and engagement. Let’s explore the essential features of MLM software and how a thoughtful development process can lead to significant business growth.
Understanding MLM Software
MLM software is specifically designed to ease the management of multi-level marketing structures. This software simplifies various aspects, such as recruitment, sales tracking, and commission management. For example, a direct selling company might find it challenging to manage three levels of sales agents, especially when they have different commission rates. MLM software automates these complicated calculations, personalizing support for each agent and allowing the company to focus on broader growth strategies.
This software is crucial for achieving higher profitability while ensuring transparency and accountability. It helps track sales, manage commissions, and communicate effectively across different levels of the organization.
If you want to try our software, please click on the MLM software developers.

#Affordable MLM software developers#MLM developers#Affiliate marketing#Direct selling#Network Marketing#Free demo#Services#Binary#Matrix#Unilevel
0 notes
Text

An Introduction to Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
What is cybersecurity?
Cybersecurity is all about securing technology and processes - making sure that the software, hardware, and networks that run the world do exactly what they need to do and can't be abused by bad actors.
The CIA triad is a concept used to explain the three goals of cybersecurity. The pieces are:
Confidentiality: ensuring that information is kept secret, so it can only be viewed by the people who are allowed to do so. This involves encrypting data, requiring authentication before viewing data, and more.
Integrity: ensuring that information is trustworthy and cannot be tampered with. For example, this involves making sure that no one changes the contents of the file you're trying to download or intercepts your text messages.
Availability: ensuring that the services you need are there when you need them. Blocking every single person from accessing a piece of valuable information would be secure, but completely unusable, so we have to think about availability. This can also mean blocking DDoS attacks or fixing flaws in software that cause crashes or service issues.
What are some specializations within cybersecurity? What do cybersecurity professionals do?
incident response
digital forensics (often combined with incident response in the acronym DFIR)
reverse engineering
cryptography
governance/compliance/risk management
penetration testing/ethical hacking
vulnerability research/bug bounty
threat intelligence
cloud security
industrial/IoT security, often called Operational Technology (OT)
security engineering/writing code for cybersecurity tools (this is what I do!)
and more!
Where do cybersecurity professionals work?
I view the industry in three big chunks: vendors, everyday companies (for lack of a better term), and government. It's more complicated than that, but it helps.
Vendors make and sell security tools or services to other companies. Some examples are Crowdstrike, Cisco, Microsoft, Palo Alto, EY, etc. Vendors can be giant multinational corporations or small startups. Security tools can include software and hardware, while services can include consulting, technical support, or incident response or digital forensics services. Some companies are Managed Security Service Providers (MSSPs), which means that they serve as the security team for many other (often small) businesses.
Everyday companies include everyone from giant companies like Coca-Cola to the mom and pop shop down the street. Every company is a tech company now, and someone has to be in charge of securing things. Some businesses will have their own internal security teams that respond to incidents. Many companies buy tools provided by vendors like the ones above, and someone has to manage them. Small companies with small tech departments might dump all cybersecurity responsibilities on the IT team (or outsource things to a MSSP), or larger ones may have a dedicated security staff.
Government cybersecurity work can involve a lot of things, from securing the local water supply to working for the big three letter agencies. In the U.S. at least, there are also a lot of government contractors, who are their own individual companies but the vast majority of what they do is for the government. MITRE is one example, and the federal research labs and some university-affiliated labs are an extension of this. Government work and military contractor work are where geopolitics and ethics come into play most clearly, so just… be mindful.
What do academics in cybersecurity research?
A wide variety of things! You can get a good idea by browsing the papers from the ACM's Computer and Communications Security Conference. Some of the big research areas that I'm aware of are:
cryptography & post-quantum cryptography
machine learning model security & alignment
formal proofs of a program & programming language security
security & privacy
security of network protocols
vulnerability research & developing new attack vectors
Cybersecurity seems niche at first, but it actually covers a huge range of topics all across technology and policy. It's vital to running the world today, and I'm obviously biased but I think it's a fascinating topic to learn about. I'll be posting a new cybersecurity masterpost each day this week as a part of the #StudyblrMasterpostJam, so keep an eye out for tomorrow's post! In the meantime, check out the tag and see what other folks are posting about :D
#studyblrmasterpostjam#studyblr#cybersecurity#masterpost#ref#I love that this challenge is just a reason for people to talk about their passions and I'm so excited to read what everyone posts!
40 notes
·
View notes
Text
semi related but reading about affiliate networks for rogue antivirus software is really funny. pyramid scheme for malware sellers
7 notes
·
View notes
Text
Top 6 Cryptocurrency Exchange Clone Scripts you should know in 2025
In thi Article about Top 6 Cryptocurrency Exchange Clone Scripts you should know in 2025, Read it out.

What is Cryptocurrency Exchange
To purchase, sell, or trade cryptocurrencies like Bitcoin, Ethereum, and Litecoin, you go to an online marketplace called a cryptocurrency exchange. Cryptocurrency exchanges work much like stock exchanges, except instead of issuing or trading stocks, you trade digital currencies.
In simple terms, it’s where Buyers and sellers meet to exchange cryptocurrencies. You can buy cryptocurrency with ordinary money (such as dollars or euros) or swap one cryptocurrency for another. Some exchanges allow you to store your crypto in secure wallets held on the platform.
There are two main types:
Centralized exchanges (CEX)
Decentralized exchanges (DEX)
What is Cryptocurrency Exchange Clone Script
The Cryptocurrency Exchange Clone Script is a ready-made program that simulates the technical features and functionality of popular cryptocurrency exchanges such as Binance, Coinbase, Kraken, or Bitfinex. Compared to developing from scratch, the clone scripts significantly ease and shorten the time required to set up a cryptocurrency exchange network for an aspiring entrepreneur and firms.
These sort of scripts are somewhat equipped with all the basic features to run a cryptocurrency exchange, like user account management, wallet integration, order book, trading engine, liquidity management, and options for secure payment gateways. The whole idea of a clone script is to give you something out-of-the-box that can be customized, thus allowing you to skip the whole painful development process but still be able to modify the script to suit your needs.
Top 6 Cryptocurrency Exchange Clone Scripts
There are many clone scripts for cryptocurrency exchange development, but here are the top 6 of the cryptocurrency exchange clone script.
Binance clone script
Coinbase Clone Script
Kucoin Clone Script
Paxful Clone Script
WazirX clone script
FTX Clone Script
Binance clone script
A Binance clone script is a Pre-made software that is almost ready for use to create your own cryptocurrency exchange platform, along the way simulating Binance, one of the largest and most popular exchanges in the world. This “clone” is a reapplication of some of the features and functionality of Binance, but it can allow for some level of customization depending upon your particular brand and need.
Key Features:
User Registration and Login
Multi-Currency Support
Trading Engine
Multi-Layer Security
Admin Dashboard
Wallet Integration
KYC/AML Compliance
Liquidity Management
Mobile Compatibility
Referral and Affiliate Program
Trading Fees and Commission Management
Live Market Charts and Trading Tools
Coinbase clone script:
The Coinbase clone script is a ready-made solution that allows you to set up a cryptocurrency exchange platform exhibiting features and functionalities similar to the world’s most popular and user-friendly crypto exchange, Coinbase. These scripts are bundled with all the necessary features to run an exchange while still offering ample customization to cater to your branding and business requirements.
Key Features:
User Registration and Account Management
Fiat and Crypto Support
Secure Wallet Integration
Quick Buy/Sell Functionality
Multiple Payment Methods
P2P Trading
Admin Dashboard
Launchpad Functionality
Staking Feature
KYC/AML Compliance
API Integration
Kucoin Clone Script
A KuCoin clone script is a ready-made software solution replicating all functional attributes and operational features of the KuCoin, which can also be customized according to your brand name and business requirement specifications. Fast and feasible for launching your crypto exchange, the idea is to save yourself from the headaches of developing everything from scratch.
Key Features:
Spot trading
Margin trading
Future trading
Crypto derivatives
Advanced security transactions
Escrow protection
User registration
Wallet integration
Advanced analytics
Currency converter
Paxful clone script
A Paxful clone script is a ready-Made platform for opening a peer-to-peer cryptocurrency exchange for users to trade Bitcoin and other cryptocurrencies directly among themselves without any intermediaries. The script replicates the core features of Paxful operated using its server; you can customize it to your brand and business needs.
Key Features:
Secured Escrow Service
Multi Payment Processing
BUY/SELL Ad posting
Real-Time Data
Referrals & Gift Card options
Multi Language Support
Online/Offline Trading
Cold/Offline Wallet Support
FTX Clone Script
An FTX clone script is a ready-made software solution that will allow you to set up your own cryptocurrency exchange like FTX, which was formerly one of the largest crypto exchanges globally before going under in 2022. This script mimics the core features of FTX, such as spot trading, derivatives, margin trading, token offering, etc., so that you can fast-track the launch and operations of your own exchange with customizable branding and features.
Key Features:
Derivatives Trading
Leveraged Tokens
Spot Trading
User-Friendly Interface
KYC/AML Compliance
Staking Functionality
WazirX clone script
A WazirX Clone Script is a pre-made software solution for the creation of your cryptocurrency exchange platform akin to WazirX, one of the top cryptocurrency exchanges in India. The clone script replicating the essential elements, functionality, and WazirX’s user experience enables you to swiftly put together a fully fledged cryptocurrency exchange that would accept a number of digital assets and trading features.
Key Features:
Escrow protection
KYC approval
Trading bots
User-friendly interface
Stunning User Dashboard
SMS Integration
Multiple Payment Methods
Multiple Language Support
Benefits of Using Cryptocurrency Exchange Clone Scripts
The use of a cryptocurrency exchange cloning script entails great advantages, particularly if one is keen on starting an exchange without having to do the full development from scratch. Below, I have listed the primary advantages of using cryptocurrency exchange cloning scripts:
Cost-Effective
Quick and Profitable Launch
Proven Model
Customizable Features
Scalability
Multi-Currency and Multi-Language Support
Low Development Cost
Continuous Support and Updates
Why Choose BlockchainX for Cryptocurrency Exchange clone script
In the opinion of an entrepreneur set to develop a secure, scalable, and feature-loaded cryptocurrency exchange clone script, BlockchainX is the best bet. Since BlockchainX provides a full-fledged solution that replicates the features of flagship cryptocurrency exchanges such as Binance, Coinbase, and WazirX, the entrepreneur gets all the additional features required practically out of the box. With the addition of certain basic offerings such as spot trading, margin trading, and peer-to-peer (P2P) capabilities along with more advanced ones like liquidity management and derivatives trading, BlockchainX provides a holistic set of solutions to carve out an exchange rightly fitted for newbies and pros alike.
Conclusion:
In conclusion, the Top 6 Cryptocurrency Exchange Clone Scripts in 2025 are high-powered and feature-rich solutions which any enterprising spirit would find indispensable if they were to enter the crypto market very quickly and efficiently. Whether it be a Binance clone, Coinbase clone, or WazirX clone-these scripts offer dynamic functionalities that enhance trading engines, wallets, KYC/AML compliance, and various security attributes.
Choosing the right clone script, such as those provided by BlockchainX or other reputable providers, will give you a strong foundation for success in the dynamic world of cryptocurrency exchanges.
#cryptocurrency#cryptocurrency exchange script#exchange clone script#binance clone script#clone script development#blockchainx
2 notes
·
View notes
Text
As the Biden administration comes to a close, the White House released a 40-page executive order on Thursday aimed at shoring up federal cybersecurity protections and placing guardrails on the US government’s use of AI. WIRED also spoke with outgoing US ambassador for cyberspace and digital policy, Nathaniel Fick, about the urgency that the Trump administration not cow to Russia and China in the global race for technical dominance. Outgoing FCC chair Jessica Rosenworcel details to WIRED the threats facing US telecoms, at least nine of which were recently breached by China’s Salt Typhoon hackers. Meanwhile, US officials are still scrambling to get a handle on multiple espionage campaigns and other data breaches, with new revelations this week that a breach of AT&T disclosed last summer compromised FBI call and text logs that could reveal the identity of anonymous sources.
Huione Guarantee, the massive online marketplace that researchers say provides an array of services to online scammers, is expanding its offerings to include a messaging app, stablecoin, and crypto exchange and has facilitated a whopping $24 billion in transactions, according to new research. New findings indicate that GitHub’s efforts to crack down on the use of deepfake porn software are falling short. And WIRED did a deep dive into the opaque world of predictive travel surveillance and the companies and governments that are pumping data about international travelers into AI tools meant to detect people who might be a “threat.”
But wait, there's more! Each week, we round up the security and privacy news we didn’t cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
US Names One of the Chinese Hackers Allegedly Behind Massive Salt Typhoon Intrusions
China spies, the US spies, everybody spies. Mutual espionage is a geopolitical game played by virtually every nation in the world. So when the US government singles out a single hacker for espionage-focused intrusions, naming him and targeting him with sanctions, he must have spied aggressively—or effectively—enough to have made powerful people very angry.
The US Treasury on Friday imposed sanctions on Yin Kecheng, a 39-year old Chinese man accused of being involved in both the breach of nine US telecommunications companies carried out by the Chinese hacker group known as Salt Typhoon, as well as another recent breach of the US Treasury. In a statement about the news, Treasury alleges that Yin is affiliated with China’s Ministry of State Security and has been a “cyber actor” for over a decade. It also imposed sanctions on Sichuan Juxinhe Network Technology, a company that Treasury says is also associated with Salt Typhoon.
Salt Typhoon’s breach of US telecoms gave Chinese hackers enormous access to the real-time texts and phone calls of Americans, and was reportedly used to spy on president-elect Donald Trump and vice president-elect JD Vance, among other targets. FBI director Christopher Wray has called the telecom breaches China’s "most significant cyberespionage campaign in history.”
China’s Silk Typhoon Hackers Targeted Sanctions and Intelligence in Treasury Breach
As the Treasury hits back at China’s spy operations, it’s also still working to determine the scope of the intrusion some of those same hackers carried out inside its network. An internal Treasury report obtained by Bloomberg found that hackers had penetrated at least 400 of the agency’s PCs and stolen more than 3,000 files in a recent breach. The espionage-focused intrusion appears to have gone after sanctions and law-enforcement related information, the report found, as well as other intelligence materials. Despite that vast access, the intruders didn’t gain access to Treasury’s emails or classified portions of its network, the report states, nor did they leave behind malware that would suggest an attempt at maintaining longer-term access.
FBI Uninstalls Chinese PlugX Malware From Thousands of Machines
The Justice Department revealed this week that the FBI carried out an operation to delete a specimen of malware known as PlugX from 4,200 computers around the world. The malware, which was typically transmitted to computers via infected USB drives, has persisted for at least a decade and been used at times by Chinese state-sponsored hacker groups to target Chinese dissidents. In July of last year, cybersecurity firm Sekoia and French law enforcement took over the command-and-control server behind the malware. This week, the FBI obtained a court order that allowed the bureau to send a self-destruct command to the software on infected machines.
Victims of “PowerSchool” Edtech Data Breach Say “All” of Their Student and Teacher Info Was Stolen
After news earlier this week of a cyberattack in December that breached the US education technology platform PowerSchool, school districts targeted in the intrusion told TechCrunch on Thursday that attackers gained access to “all” stored student and teacher data in their accounts. PowerSchool is used by more than 60 million K-12 students in the US. Hackers gained access to the information by stealing login credentials that gave them access to the company’s customer support portal. The attack has not yet been publicly linked to a specific perpetrator. PowerSchool has not yet disclosed the exact number of victim schools nor whether all of its customers were affected.
3 notes
·
View notes
Text
High-Ticket Affiliate Programs: A Comprehensive Guide for 2025
High-ticket affiliate marketing represents a strategic approach to generating substantial commissions through the promotion of premium products and services.
Unlike traditional affiliate marketing that focuses on high-volume, low-commission items, high-ticket affiliate programs offer significantly larger earnings per sale, often ranging from $500 to several thousand dollars per transaction.
The primary advantage of pursuing high-ticket affiliate programs lies in their potential for generating meaningful income with fewer sales. For instance, promoting a $2,000 product with a 40% commission yields $800 per sale, equivalent to selling eighty $10 products at a 10% commission rate.
Top High-Ticket Affiliate Programs for Serious Marketers
When evaluating high-ticket affiliate marketing opportunities, several programs stand out for their exceptional earning potential and professional support structures:
Digital Education Platforms
Commission rates: 30-50% per sale
Average product value: $1,000-$3,000
Comprehensive training materials included
Enterprise Software Solutions
Commission rates: 20-40% per sale
Average product value: $2,500-$10,000
Recurring commission opportunities
Enterprise Software Solutions
Commission rates: 15-30% per sale
Average booking value: $5,000-$15,000
Exclusive partnership opportunities
Essential Steps to Start High-Ticket Affiliate Marketing Successfully
Success in high-ticket affiliate marketing requires a strategic approach:
Market Research and Selection Begin by identifying your target audience and understanding their specific needs. High-ticket products require a more sophisticated approach to market analysis, focusing on demographics with substantial purchasing power.
Platform Development Establish a professional online presence through:
A professionally designed website
Authoritative content development
Strategic social media positioning
Relationship Building Develop strong relationships with:
Program vendors
Industry influencers
Potential customers through value-driven content
Advanced Strategies for Promoting High-Ticket Affiliate Products
To maximize success in high-ticket affiliate marketing, implement these advanced strategies:
Content Marketing Excellence Create comprehensive content that demonstrates expertise and builds trust. This includes:
Detailed product reviews
Case studies
Expert interviews
Educational webinars
Email Marketing Automation Develop sophisticated email sequences that:
Nurture potential customers
Provide valuable insights
Build credibility over time
Guide prospects through the decision-making process
Personal Brand Development Establish yourself as an authority in your chosen niche by:
Speaking at industry events
Publishing thought leadership content
Participating in professional networks
Showcasing successful case studies
Success in high-ticket affiliate marketing stems from building genuine relationships and providing substantial value to your audience. Focus on understanding your target market's needs and consistently delivering solutions that address their specific challenges. Remember that while the commission potential is significant, the responsibility to provide accurate, valuable information to your audience is paramount.
2 notes
·
View notes