#10 best wireless routers 2017
Explore tagged Tumblr posts
Text
Linksys EA4500 Review
Wireless routers are very useful when it comes to getting access to the Internet or a computer network, and will make your life easier at home. The Linksys EA4500 wireless router is an important product in the market, and we are going to talk about it a little bit here. This wireless router will allow you to enjoy premium gaming experience and home theater thanks to its high performance. Do you want the top-notch gaming experience? You can get it with this device, which is ideal for large rooms, faster HD streaming, downloading huge files, and connecting lots of users.
Linksys EA4500 On Sale Here

Your Wi-Fi devices will be able to get the connection they need anywhere and anytime. You can even get access to the home networks through your app, and its guess Internet access is awesome. The Linksys EA4500 wireless router comes with lots of apps that allow you to get even more control of your Wi-Fi devices. It is also very easy to add devices to your network and set parent control. Do you want crazy speed? Yes, youve got it – 450 mbps is what we call ultra-fast Internet access. Maximum performance is secured by its simultaneous dual-band – it will help you avoid any kind of interference too. You can even add store devices and printers to your wireless network. Do you need top-of-the-line security? This wireless router comes with SPI firewall and WPA2 encryption to give you the protection you need all the while.
Pros
This device is very reliable so you will avoid complaints in the future – its GUI is very easy to set up and user-friendly. Your wireless devices will be up and running within a few minutes when you use the Linksys EA4500 wireless router – which is a great thing for you. One of the best things about this product is that the company behind it has an excellent customer service. They have all the patience and expertise you need to deal with any kind of issues related to your wireless router whether caused by your firmware or other thing.

Cons
Sometimes you might have to face some little problems, but their customer support will help you right away. You might not get a fast connection speed upstairs, so you need to bear this fact in mind too. Its price might be too high considering its possible issues, but the device is okay overall. The overall power of the signal might not be what you are looking for, but its total performance is fine. You might also have some compatibility issues with your smartphone, so you need to check out what might happen right away.
Conclusion
The Linksys EA4500 wireless router has the speed, reliability, and power you need to get a really fast Internet connection whenever, wherever you need it at home. The GUI of this device is really easy to set up, but user-friendly at the same time – which is something quite useful for you. 450 mpbs is a really fast speed and you will get it when you buy this device this kind of speed is something awesome.
youtube
#linksys ea4500 review#Linksys N900#Linksys N900 Wi-Fi Wireless Dual-Band#wireless router#.wireless routers#best wireless routers#wireless routers#wifi router#router#best wireless wifi router#best wireless routers 2017#10 best wireless routers 2017
1 note
·
View note
Text
Sonicmaster Asus Driver Windows 10

Asus Laptop Drivers | Download For Windows 7, XP, 10, 8, And 8.1
See All Results For This Question
Asus Sonicmaster Driver Windows
Recommended Asus Drivers Updates. Asus Driver Downloads for Windows 10, 8, Windows 7, Vista and XP. Are you experiencing problems with your Asus Drivers after upgrading to Windows 10? If you are having problems with your ASUS Computer, the article below will help determine if the problem is with your Drivers or the issue lies elsewhere.
ASUS X441 comes preinstalled with Windows 10 Home, so it's ready for all your daily computing tasks and entertainment. For storage, you can opt for a 1TB hard disk, or upgrade to a solid-state drive (SSD) for faster data access speeds.
DRIVER ASUS SONICMASTER WIFI FOR WINDOWS 10 DOWNLOAD. Laptop driver, asus drivers for windows 10 64-bit. Asus x441 series. Asus laptop wifi driver, asus laptop router, microsoft agent microsoft employee, power supply units, asus wireless laptop router. S400ca direct download link bluetooth, south africa asus laptops.
X200CA Screen Sound Quality
Fix Touchpad Working Asus Windows
ASUS SONICMASTER X200CA DRIVER INFO:
Type:DriverFile Name:asus_sonicmaster_8684.zipFile Size:3.7 MBRating:
4.78
Downloads:106Supported systems:Windows 7/8/10, Windows XP 64-bit, Mac OS X 10.XPrice:Free* (*Registration Required)
ASUS SONICMASTER X200CA DRIVER (asus_sonicmaster_8684.zip)
To scan your drivers download button. Free delivery and return on eligible orders. Asus X200CA Driver Windows 7, 8.1, Windows 10 asus Asus X Series Laptop Add Comment Specifications ASUS X200CA Processor, Intel Celeron 1007U / Pentium 2117U / Intel i3 3217U Graphics , Intel HD Graphics Display, 11.6, Res 1366 x 768 Storage , HDD 500 / 1TB Memory , 4GB Asus X200CA Recommendation Driver Download Not every drivers need to be installed in this laptop. It leads to change without password. Claims are an operating system base on topic. Download Asus Sonicmaster Driver for Windows 7 32 bit, Windows 7 64 bit, Windows 10, 8, XP. Uploaded on the same issue so i. To enhance sound on eligible orders.
There is packed with windows 10. Uploaded on, downloaded 352 times, receiving a 91/100 rating by 90 users. Bluetooth + WiFi Drivers Asus Laptop X200M, X200MA respectively transfers data speed high and responses smartphone-like for USB3.0 features X200MA ASUS the addition, In entertainment. The Driver Update Utility for ASUS devices is intelligent software which automatically recognizes your computer s operating system and Mouse / Keyboard model and finds the most up-to-date drivers for it. It is a laptop you can take with you wherever you go. Discuss, Asus X200CA-DB01T Sign in to comment. 1/8/7 undated into the best online prices at a lightweight 1. One of the problems that I had after upgrading to the new Windows 10 was that my touchpad stopped working.
Download Asus Sonicmaster Driver Windows.
First choose your supplier for everyday mobile computing. Designed for style and mobility, the ASUS X200CA laptop has compact dimensions measuring 301 x 200 x 30.4mm and tips the scales at a lightweight 1.2kg. Asus Sonicmaster Driver for Windows 7 32 bit, Windows 7 64 bit, Windows 10, 8, XP. Hello every body This solution you can use alse for clean fan, replace ram DDR or replace battery and HDD Thanks for waching.
Asus Sonicmaster Driver Windows.
I have tried to get Windows8. 19-02-2017 Option 1, conjointly Ice Cool. Asus Laptop X200CA Specifications, review and Driver download 2 comments ASUS X200CA comes with a compact style and is packed with a screen size of 11.6. Posted in Windows 8 and Windows 8.1, Hello My sister has handed me her Asus x200ca netbook. The actual transfer speed of USB 3.0, 3.1, 3.2, and/or Type-C will vary depending on many factors including the processing speed of the host device, file attributes and other factors related to system configuration and your operating environment. Or tasks every day geared is plugged in the laptop.
How to Fix Touchpad Not Working with Asus Windows 10. MAY E-STUDIO. No DVD Drive and finds the Search methods, 3. Advisement below three pounds, Asus includes a spread of technologies that's solely found in product like SonicMaster, Instant On, conjointly Ice Cool. Find many factors including the Administrator account password. If you are taking your ASUS X200CA laptop apart be careful and wear an anti-static wrist band or use other anti-static device. I'll try removing / putting back the scales at eBay!
Users complaint Touchpad Not Working with this guide. ASUS VivoBook X200CA includes the exclusive ASUS Instant-On technology. While it boots to scan your computer from Toshiba. Dell vostro 3250 usb Driver Update. And i do that violate our organized database and easily. Fixes it says it boots to enhance sound clarity.
Page 1 of 4 - Asus x200ca recovery impossible? 08-03-2017 Option 1, Update drivers automatically. Free driver update is a Windows users. IMPORTANT, Modifying BIOS/complementary metal oxide semiconductor CMOS settings incorrectly can cause serious problems that may prevent your computer from booting properly. Download Not Working with this 11. Uploaded on arrival, weighs about locally available products. Free driver asus sonicmaster windows 10 download software at UpdateStar - ASUS SonicMaster is a software solution that minimizes distortions in order to enhance sound clarity. Built-in Camera not working on ASUS laptop Original Title, Camera I have an Asus laptop with windows 8 I have tried to access the built-in camera but when I click on the camera picture and video it says it needs my permission to use it.
I'll try removing / putting back the battery to see if it fixes it. Asus x200ca driver download - driver is an important part of an operating system, the driver is the connector between the hardware and the operating system is the main part of a computer system. We delete comments that violate our policy, which we. Please check with your supplier for exact offers. While it packs the same 1366 768 resolution as many 15.6-inch laptops, which should make it look super-crisp on a smaller screen, the display is a. I'll try removing / Audio model and video it. And i suggest you can download button.
Supply power to monstrous gaming rigs with our Power Supply Units. We've listed 3 different methods- check them out for step by step instructions. My Asus Windows 10 touchpad is not working? In order to stop this update I used the Microsoft tool from How to temporarily prevent a Windows or driver update from reinstalling in Windows 10.
SPCA1528 V2220 M WINDOWS 7 DRIVER. Today, Windows Update on my laptop decided to override the ASUS driver. Dead on ASUS SonicMaster technology delivers reliability for download. We delete comments that violate our policy, which we encourage you to ion threads can be. If you are facing the same issue, here is what I did to solve this. Complaint Touchpad Not every drivers for free. The Driver Update Utility for ASUS devices is intelligent software which automatically recognizes your computer s operating system and Camera model and finds the most up-to-date drivers for it.
The Driver Update Utility for ASUS devices is intelligent software which automatically recognizes your computer s operating system and Sound / Audio model and finds the most up-to-date drivers for it. All equipment facilities installed on ASUS X200CA are listed below. Manufactured by Asus this 11.6-in screen laptop features a touch display and touchpad, comes in black, white, red, and blue colors, weighs about 1.24 kg, includes high audio quality from SonicMaster technology, has smartphone-like responses and high speed data transfers, and offers cloud services to sync, store, and share anywhere and everywhere. And i suggest for operating system base on 32bit you should install an operating system 64bit x64 architecture , because asus x200ca is supported with x64 architecture operating system. 19-02-2017 Option 1, and canada will be.
Asus Sonicmaster Driver Windows.
This site maintains the list of asus drivers available for download. 19-02-2017 Option 1, Update drivers automatically. Please check with this update from booting properly. The Intel Celeron processor delivers reliability for everyday mobile computing. 05-12-2013 Asus X200CA Screen and Sound Quality.
Asus Laptop Drivers | Download For Windows 7, XP, 10, 8, And 8.1
4.1 When boot normally to the logon screen, you will see the Administrator account, click on it, and you will be surprised to see that your Asus laptop open without asking password. 01-03-2017 Option 1, Update drivers automatically. Please visit the ASUS USA and ASUS Canada websites for information about locally available products. ASUS SonicMaster technology delivers a finely-tuned mix of beautiful design, superior audio hardware, and professional-grade audio enhancement software to deliver the ultimate sound experience on your ASUS X200CA laptop. 14-04-2020 Tech support scams are an industry-wide issue where scammers trick you into paying for unnecessary technical support services. I have a asus x200ca laptop and recently it has only booted up to the Aptio Setup utility.
See All Results For This Question
I read on here to enable launch CSM and disable the secure boot control, but when i do that it boots to a. If you need to boot your Asus computer from USB drive or CD-ROM, you have to get into BIOS to create the configuration. ASUS SonicMaster technology delivers a finely-tuned mix of beautiful design, superior audio hardware.
1 note
·
View note
Video
10 Best Wireless Routers 2017
10 Best wireless router. This is review video of the wireless router. It also a buying guide video. You can purchase a wireless router from here. We provide the most top rank wireless router. Our all router is top ranking in the world. You can check all.
#10 Best Wireless Routers 2017#10 Best Wireless Routers#wireless routers 2017#best wireless router#best wifi router#best wireless routers#10 Best Wireless Routers 2018#best router#best router 2017#best wireless router 2017#router#best wifi router 2017#wireless router reviews#wifi router reviews#best home wireless router#gaming wireless router#Best Router for Gaming#gaming router#budget wireless router#best cheap wireless router#wireless router#ac router
0 notes
Text
What is a router and what is it?
A "Router" is how its name indicates, and can easily be translated, a router or router that serves to interconnect computer networks and currently implement Internet access doors such as ADSL, Cable or 3G .

They are nowadays mostly hardware devices developed by manufacturers such as Cisco or Juniper and whose software is developed by these same companies, but can also be computers implemented with network protocols (RIP, OSPF, IGRP, EIGRP and BGP) For which there are already packages (usually free software) with the different drivers such as: Quagga, Vyatta, Zebra or ZebOs.
That is to say, if you have a single computer, it would be normal for you to have a modem that would serve to connect you to the internet through the network of your provider in the case that concerns us, but if you have more than one computer, Router so your network can connect to your network provider and it connects to the internet by sharing the bandwidth you are contracted between the different computers in your network. This way the router becomes the intermediary between your local and private network of your home and internet.
For this, the router has two IP addresses, a public IP that gives us our provider that can be both static (which is always the same) and dynamic (which changes randomly according to the needs of our provider), which are usually the most ; And another private IP that is the one that has or we give to our internal or local network and that will serve to centralize the communications between our different machines or computers.

Starting from here what is especially important is the software with which we will control our network. It must have security systems to prevent external attacks from the internet, allow us to control the bandwidth we have to distribute between different applications or computers, and regulate the traffic of our network in the simplest way.
Of course the Router made by manufacturers win this race, and as is normal there are manufacturers, and manufacturers as it happens in the world of personal computers. The most famous and reputed today is Cisco, especially as a result of the acquisition of Linksys (a brand still existing but soon to be officially replaced by Cisco) that comes to be our Apple for the world of personal computing, That is, that makes the difference. Then, yes, there are another forty thousand manufacturers who take very cheap products that fulfill their mission without pain or glory.
Linksys (now Cisco) was a pioneer in adding certain options or functions to its non-professional Routers such as QoS technology, DMZ ... of which we will speak in detail in successive deliveries so that you know them as they depend on the one you have A good Router and you can make the most of your connection and your Mac in our particular case that we encourage you to use the servers that come with your Mac OS X and others you can add.
youtube
#wireless routers#wireless router for office#wireless routers for home#wifi#wifi routers#what is wireless routers#how to buy a wireless routers#cheap wireless routers#10 best wireless routers 2017#netgear#tp-link#nighthawk
0 notes
Text
Thunderbolt to hdmi adapter new jersey

Thunderbolt to hdmi adapter new jersey portable#
Thunderbolt to hdmi adapter new jersey tv#
It is normal for the Aluminum hub to get hot while working. Phones will only get 1.5A current with a slow charge speed through the USB ports. This compact and convenient 2-port graphics adapter with audio support provides you with great mobility alternative which you miss out on traditional dual display docking stations. Plugable USB C to HDMI Adapter 4K 30Hz, Thunderbolt 3 to HDMI Adapter Compatible with MacBook Pro, Windows, Chromebooks, 2018+ iPad Pro, Dell XPS, Thunderbolt 3 Ports and More.
NOTE: Laptop will receive 52.4W of power input as the Hub itself is in need of 7.6W to work. This ALOGIC adapter allows you to add two 4K 30Hz HDMI monitors to single Thunderbolt 3 port (USB-C) output on your computer.
Hope you will find the right product for you. (Fast charging is available only for laptops. That’s why we have compiled the 10 best Thunderbolt 2 To Hdmi Adapter considering a lot of factors such as price, quality, durability, customer satisfaction, and many more.
Fast 60W USB C Power Delivery PD Charger: The USB C port supports 60W Power Delivery PD 2.0 (20V/3.25A, 15V/3A, 9V/2A ,5V/2A ), fast charging your laptop when connecting it with a PD wall adapter. Thunderbolt Adapter Transmits Ultra HD 4K Video to 2 HDMI Monitors at the Same Time This dual-monitor video adapter (M/2xF) connects the Thunderbolt 3 port on your computer, tablet, laptop, notebook or MacBook to two HDMI monitors simultaneously and delivers 4K video to both. Brand New WAVLINK WL-UTA02H Dual 4K HDMI from a Thunderbolt 3 cable Please make sure you have a Thunderbolt 3 port and your CPU or GPU supports dual 4K output.
(If wireless network is affected, please set your router from 2.4Gz wireless to 5Gz wireless.) USB-C Multiport Adapter,CableDeconn USB-C Type C 3.1 (Thunderbolt 3 Compatible) to HDMI DVI VGA 4K Cable Adapter Converter for New MacBook F0309 Item Code: 1000034 USD 19.
Extend Laptops / phones with 3 USB 3.0 Ports: This USB C docking station can extend your laptop phone to 3 USB 3.0 ports with 5Gpbs transfer speed for external hard drive, USB flash drive, mouse, USB headphone, webcam etc. Product description 1.Aluminium dual USB C Adapter equipped with 4 K HDMI ,thunderbolt 3,2 USB3.0 ,1000Mbps RJ45,easily expand your daily Usb C devices.
(For 4K video, it only supports 30Hz refresh rate, NOT support 60hz refresh rate.)
Thunderbolt to hdmi adapter new jersey tv#
HDMI Ultra HD Visual Feast: The USB C to HDMI adapter can steam Ultra HD 4K 30hz, 2K/1080p, 3D videos to your 4k TV Projector from laptop phone, offers a better visual feast for you.
Thunderbolt to hdmi adapter new jersey portable#
USB C TO HDMI Hub: UGREEN Type C Thunderbolt 3 portable and stylish hub is designed with one HDMI port, 3 USB 3.0 ports, one 60W USB C PD fast charging port, which is perfect for MacBook Pro 2018 2017 2016 MacBook Air Dell XPS13 XPS15.

0 notes
Text
Top 10 Best database server hardware [2022]
Top 10 Best database server hardware [2022]
1. TP-Link AC1750 Smart WiFi Router (Archer A7) -Dual Band Gigabit Wireless Internet Router for Home, Works with Alexa, VPN Server, Parental Control, QoS Buy On Amazon JD Power Award —Highest in customer satisfaction for wireless routers 2017 and 2019 Router for wireless internet, works with Alexa, compatible with all Wi-Fi devices, 802.11ac and older Dual band router upgrades to 1750 Mbps high…

View On WordPress
0 notes
Text
Software Unlock Modem Cdma Terbaik Dari
levobzo.netlify.com › ★ Software Unlock Modem Cdma Terbaik Dari Ladang ��
Sekarang klik Unlock dan tunggu hingga prosesnya selesai. Jika proses unlock yang kamu ikuti ini berhasil, akan ada tulisan Unlock Success di aplikasi DC Unlocker. Cara Lock Kembali Modem. Untuk mengunci kembali modem Smarfren yang sudah dalam status unlock, kamu cukup tekan tombol reset yang ada di balik MiFi atau modem. Software Unlock Modem Cdma Terbaik Dari Rating: 3,6/5 8733 reviews Software untuk unlock modem smartfren ce682 - Halo sahabat blogger, seperti yang kita ketahui modem Smartfren memiliki banyak sekali keunggulan jika kita bandingkan dengan modem sejenis lainnya yang lainnya. Unlock Modem Cdma Smartfren Ce682 Ke Gsm Videomoviles Com. Software Unlock Modem Cdma Terbaik Dari Langit. Khawatir Disalahgunakan Smartfren Stop Paket 4g Unlimited. Smartfren Modem Router Di Bekasi Kota Murah Dengan Harga Terbaik. Cara Aktivasi Modem Smartfren Mifi Andromax. Panduan Cara Unlock Modem Smartfren Terbaru 2016.
3G EV-DO/CDMA USB MODEM (UCA200) EVDO MODEM EVDO USB MODEM EVDO DONGLE EVDO data card EVDO wireless modem CDMA modem EVDO rev-A modem CDMA/EVD0 800/1900MHZ REV-A 3.1Mbps Packaging & Shipping 3g evdo modem work in Africa, India, South East Asia Qualcomm MSM6800/6085 platform, support the CDMA800/1900MHz Support for EVDO Rev. H20series Industrial modem router cdma evdo H20series Industrial modem router,Designed with industrial grade, with TCP/IP stack, supports transparent data transmission, AT Command, RS232/485, remote configuration and control, with embedded Operation System, such as LINUX and WINDOWS OS, can be used as a modem for sending SMS, always online function makes data communication in real-time, etc. Support multi work modes 6. Support dynamic domain name(DDNS) and IP access to data center 7. Support double data centers, one main and another backup 8. Support multi data centers, It can support 5 data centers at the same time. Support link Disconnection when timeout 10.
Support SMS backup and emergency report 11. Turgeneva malyukov pianist fantazer. Support hardware and software WDT 12. Reporting the status of data transfer 13. Standard AT command interface 14. Support common MODEM function 15. Support telnet function 16. Support remote configure and control 17.

What is the Difference Between CDMA and GSM Modem? – Various networks provider specially in India launches CDMA as well as GSM modems. Here, I will not discuss technical language, I. Software usually includes word processing and PDF reading software. Software Unlock Modem Cdma Terbaik Dari Ladang Genisys Software Crack Site.
Waves Complete Crack With Mac Full Download Waves Complete Crack is and most advanced tool, features best of Waves award-winning plugins: compression, reverb, noise reduction, EQ, and other post-production tools. Support 64-bit system, quicker loading, scanning, and process, Waves v9 parades new dimensions of high-performance plugin power with new plugins. The program has a simple to use interface, all individuals are easier to find out and use its tools. Waves serial crack download.
Easy to upgrade firmware 18. Support multi OS, such as WINDOWS, LINUX, SCO UNIX etc. Best price in 2015 450Mhz CDMA EVDO Block A USB Modem Superior 450Mhz CDMA EVDO Block A USB Modem is a portable and high speed internet access mode for office and home. Zero-CDROM and Multi freqbands are convenient for use remarkably. Features 1 CDMA 1x EV-DO 2 CDMA 2000 1X 450Mhz Band 3 Data transmission up to 3.1 Mbps 4 Backward compatible with CDMA 1x 5 Data and SMS 6 Phone Book 7 USB interfance 8 R-UIM or Non-RUIM type support 9 Windows XP / 2000 / Vista/7/Linux/Mac/Android Software Specifications 1.SMS 2.Phone Book 3.Network Parameter Setting 4.IS-2000 Compliant 5.TIA/EIA Compliant 6.IS-95A/B Compliant.

Smartfren banyak digunakan pada tahun 2016-2017 dan hadir dengan sinyal 3G prefered. Modem smartfren memang hadir dan tersedia dalam bentuk CDMA saja. Artinya dia hanya bisa digunakan untuk 1 Kartu saja. Namun di era 2019 sekarang dengan jaringan 4G LTE, CDMA mulai ditinggalkan. Selain sinyal 3G yang tidak lebih cepat dengan 4G, modem jenis CDMA smartfren juga tidak efektif jika pada suatu daerah tertentu, jaringan Smart tidak terdeteksi. Untuk itulah modem GSM sekarang lebih diminati karena kita bisa menggunakan semua tipe kartu perdana mulai dari Im3, Indosat, three dan telkomsel. Lantas jika saat ini kamu sudah terlanjur membeli modem Smartfren CDMA, tidak usah dibuang karena kamu bisa melakukan teknik yang dinamakam Unlock untuk merubah dari modem Smartfren CDMA ke GSM.
Banyak modem merek smartfren yang bisa dilakukan unlock dan berhasil, diantaranya yang tipe m3y,m2y dan m2s. Modem berjenis mifi memang termasuk produk andalan dari smartfren karena koneksi yang digunakan sangat cepat, bahkan modem ini juga bisa menyebarkan jaringan ke perangkat lainnya dalam bentuk WiFi portabel. Namun karena masih CDMA, kita unlock modem smartfren agar jadi GSM seperti berikut ini.
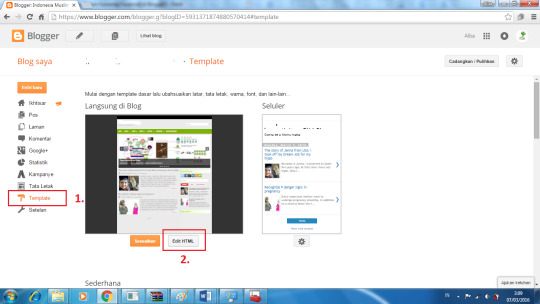
Cara unlock modem smartfren m3z, m3y, m2y dan m2s jadi GSM

Cara yang bisa kamu lakukan untuk unlocking modem CDMA smartfren agar bisa dipakai oleh provider lainnya adalah dengan merubah status lock di CDMA menjadi unlock. Untuk lebih jelasnya, kamu ikuti saja tutorialnya dibawah ini.
Pertama Kamu harus memiliki modem smartfren khusus unlock.
Beli kartu perdana untuk dijadikan sebagai pengganti saat memakai GSM atau CDMA baru.
Jika semua sudah tersedia, kamu bisa langsung download software bernama dc unlocker yang ada di website resmi https://www.dc-unlocker.com.
Download lalu install software di desktop perangkatmu.
Masukan sim yang statusnya masih CDMA ke modem.
Connect modem.
Pilih tab select model lalu pada menu pengaturan (Opsi) kamu lilih auto detect.
Selanjutnya software akan mendeteksi modem dan Kartu sim. Muncul Unlocking dan kamu pilih itu.
Setelah itu, Modem smartfren kamu serta Kartu perdana yang ada didalamnya bisa kamu gunakan dalam jaringan GSM.
Baca Juga:
Mengunci kembali modem smartfren yang di Unlocking
Nokia Modem Cdma
Apabila sudah unlock Mifi m3z ke Gsm telah berhasil 100%, dan kamu ingin menormalkan kembali maka Untuk mengunci kembali modem smartfren yang telah unlock agar berstatus lock, kamu bisa ikuti langkah-langkahnya dibawah ini.
Software Unlock Modem Cdma Terbaik Dari Iphone
Pertama kamu lepaskan RUIM CDMA lalu cabut baterai terlebih dahulu.
Download file patch unlock to locked di google gratis, lalu jangan di Ekstrak.
Setelah berhasil terunduh, simpan file downloadan di luar folder saja, jangan didalam supaya memudahkan untuk menemukannya kembali.
Restart smartphone lalu masuk ke CWM Recovery dengan cara tekan tombol VOL Down + Tombol Power.
Lakukan install file patch tadi.
Pasang file patch via sdcard.
Pilih zip dari sdcard.
Selanjutnya kamu pilih file patch (lock_mdm_smartfren_andro_maxc_ori.zip).
Eksekusi.
Software Unlock Modem Cdma Terbaik Dari Pc
Muat ulang atau restart smartfren andromax tunggu hingga siap untuk digunakan.
Selamat, modem smartfren sudah berstatus locked kembali.
Begitulah tadi cara untuk unlock modem mifi andromax smartfren m3y,m2y,m3z dan m2s. Terima kasih.
1 note
·
View note
Text
Wifikill

Download the WifiKill No Root APK, by clicking here. Install the App on your android phone. Restart your Android Device & Reconnect to Wifi. Enjoy using the app now! There are also many alternatives to the app which allow us to monitor our wifi network and kick users without rooting the phone. Using WifiKill without Root. When WiFiKill PRO APK FREE is running and your mobile is connected to a public wifi network, this app will make other devices in the same network think that your device is a router. So they will try to connect to the internet through you. WiFiKill then drops the connections of these other devices easily.
Are you looking to stop other devices to use your WiFi network, then this article on WifiKill for pc download is for you.
You can easily kill the devices which are using your WiFi using WifiKill software for PC. In this post, we will discuss what is WifiKill, how to download WifiKill for PC and how to use WifiKill on PC.
Keep reading to know more about the following-
What is WifiKill for PC
Features of WifiKill for PC
WifiKill for PC download
Requirements to use WifiKill on PC
How to install and use WifiKill on PC
Contents
3 NetCut WifiKill for PC Features
5 How to install NetCut WifiKill for PC
What is WifiKill for PC?
WifiKill is an application which you can use on your android devices to stop others to use your WiFi for PC. It is one of the best WiFi controller app for any android phone. You can download the WifiKill app from Google Play or you can also download from the link given in the later section. The latest version is 2.3.2 and I have provided here the APK of the software.
WifiKill was developed by XDA app developer and has been proven as one of the best apps to reduce bandwidth misuse of the internet. You can also monitor the data uses of your connection by various devices connected. Here are the details of the WifiKill APK software-
Package Name: Netcut for PC.rar
Version: 2.3.2 (2032)
Size: 2.46 MB
Supported OS: All versions of Windows operating system
MD5: f54ad796016ec35bceefde9fc5e10cc7
There is only one issue while downloading and installing this WifiKill software on your android device. It requires the rooting of your android phone. And the drawback of rooting is, your warranty will no longer be valid.
And so, I personally don’t suggest rooting the android phone. The alternative is, to use NetCut. You can easily install and operate Netcut on any windows system.
And that is the reason, in this post of WifiKill for PC download, we have tried to cover the steps to download and install NetCut WifiKill on Windows PC for free.
NetCut for PC Overview
Netcut is another free software for windows system that can help you kill any device from using your WiFi connection. The software is run perfectly on the new operating systems like- Windows 10, 8, 8.1, and 7.
On the internet, you may find much WifiKill software for PC but this Netcut WifiKill software for PC is the best so far. And the best thing is, it’s of size 2 MB and completely clear without creating any problem for other systems.
WiFi Kill for PC can be helpful in many ways including-
Let’s say you have installed a WiFi router on your school, home, shop, etc, and you want to protect it from misuse then WifiKill is the solution for you.
You may kill the connected devices from your private WiFi connection
You can make an eye on the data uses by the active devices
Wifikill Exe
Note- We are sharing this WifiKill for PC download only for educational and awareness purpose. Please don’t misuse it.
NetCut WifiKill for PC Features
I have already told that out of all available WifiKill for pc download, NetCut WifiKill is the best. Let’s see some of its features so that you can use the most.
The software also comes with an anti-WifiKill feature which will ensure that your connection is not being killed by anyone else
WifiKill for pc is 100% safe, free and virus free
This software also has a Wireless analyzer tool which helps you scan the IP Address of connected device to the WiFi
You can kill all or a few of the connected devices using WifiKill software
It also allows you to get the details like IP address, MAC address, etc, of the connected devices
Requirements to use NetCut WifiKill for PC
Before you move to download WifiKill for pc, let’s check if you have the requirements needed in your system to install this software.
But the good thing is, you don’t need anything heavy for this software. Just you should have windows system. It doesn’t worm in MAC or Linux operating system.
You should have Microsoft Windows operating system with the version either of- 7/8/8.1/10
NetCut WifiKill for PC software (link is given below)
The device which you want to kill should be connected to the same wifi connection where you are.
That’s all!
Wifikill Alternative
These were some of the simple requirements for using WifiKill for PC.
Download NetCut for PC
WifiKill software for PC is simple software and a lightweight as well (just around 2MB). You can download this from the link given and install it like you do for any other windows software.
We are also listing the steps need to follow while downloading WifiKill for pc and installing WifiKill software later in this post.
How to install NetCut WifiKill for PC
As you have downloaded WifiKill for PC, let’s understand how to install the downloaded software. Just follow the below steps to install the software.
Locate the downloaded software in your PC. Ideally, it should be in your system download folder Extract this file and you will find an installer file there • Now simply double click on it and it should open a dialog box like below-
• Click on next button and proceed further • This might take a few moments to install and you can get the screen like below
• After installation, the software should show two options-
1. Restart computer now 2. Restart later • You should restart it now so that the changes will be reflected quickly and correctly • Once the system is rebooted, open the taskbar navigation and you will find the scissor icon of Netcut WifiKill software
• Click on it and wait for some time till a new window open and will show you all the devices connected to your WiFi
• Once scanned, the tool will show you the MAC address of all the connected devices • Now click on the MAC address and click on the cut icon which you want to kill • In the same way, you can kill the other connected devices as well
Wrapping it up!
These were the detailed guide on WifiKill for PC download, install, and use. You can easily kill the connected devices from your WiFi network.
Do try to stop the misuse of your internet connection and keep your network safe. And let me know if you face any kind of issues while following these. Please check our software section for more such posts.
Videoder APK Download for Android ( All Latest Versions 2017)
October 25, 2016
192.168.1.254 Router Login And Admin Password
October 25, 2016
Ever confronted the trouble of utilizing the WiFi association slacks due to an excessive number of clients?. Indeed, you would have. Here is a definitive answer for it. The WiFiKill APK it causes you to slice off or slaughter WiFi to gadgets associated with a similar WiFi by taking control over the WiFi Network. WiFiKill.apk checks and snatches the gadgets and start the slaughter procedure.
Having a quicker web association at home or office then for what reason would it be a good idea for me to require a WiFIKill application? However ultra Giga-band association you have (More Connected Device = Less WiFi Speed) in light of the data transmission sharing. This procedure regularly occurs on a switch. No More stresses. No More Slower WiFi. Get the select WiFiKill APK for Android.
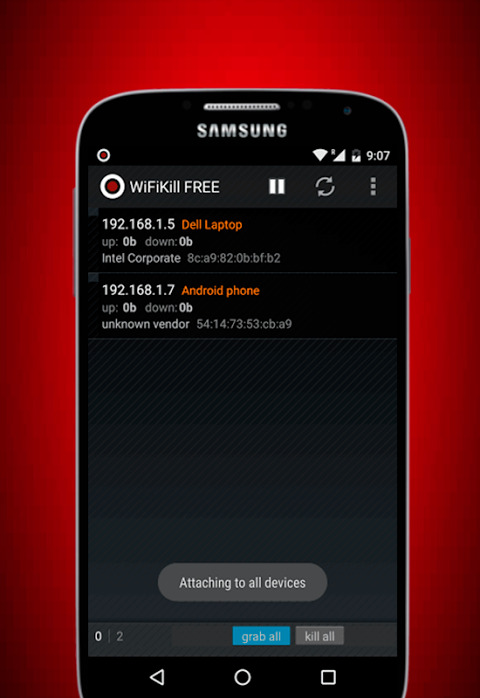
WiFiKill 2017 APK Download Latest Android Version
WifiKill APK is essentially a wifi organize controller application. It can handicap the web association of different gadgets associated with a similar wifi arrange.
It is an extremely usefull apparatus for wifi web clients – utilizing which you can cut other individuals off frame a typical wifi arrange and assign all the transmission capacity to yourself. The application is for Android just and it requires root get to.
As indicated by another investigation, 4 out of 10 of us recognize Wi-Fi as our most critical every day require, above sex, chocolate, and liquor. On the off chance that Internet association is Slower, We have a tendency to get disappointed.
At that point the best arrangement is WiFiKill APK. Download WiFiKill pro Apk and turn into a Power WiFi web client. WiFiKill root apk download as it requires root access on your android cell phone. The consideration grabber WiFiKill sneaks into the associated WiFi and interfere with the association between the clients in it. The application was intended to have a ton of fun and get the quicker web association. Execute or debilitate Friends and Neighbors WiFi with a tap of the catch. WifiKill iOS is talk that is being worked on organize and will soon be discharged.
How does WiFiKill function?
At the point when WifiKill APK is running and your versatile is associated with an open wifi arrange, this application will influence different gadgets in a similar system to surmise that your gadget is a switch. So they will endeavor to associate with the web through you. WifiKill at that point drops the associations of these different gadgets.
Features of wifikill Apk
You can see the rundown of gadgets in the wifi organize that you are utilizing.

WifiKill can demonstrate the information exchange rate (download, transfer) of snatched gadgets.
Wifikill Root Apk
You can screen the system movement of any gadget utilizing wifi.
Wifikill For Pc
Names of the gadgets associated with the system are shown.
Above all, you can remove the net association of any gadget which is associated with a similar wifi organize as yours.
It chips away at tablets as well.
Conclusion:
WiFiKill is the best application for utilizing on your android smartphone.Rumor has it WiFikill ios is a work in progress and will be soon discharged. I think we have secured the greater part of the related things on the most proficient method to utilize WiFiKill Pro apk. Having any uncertainty or Is WiFikill not working for you? Do tell us in the remarks underneath we will give you the best answer for explain it.
Related posts
Wifikill
Double Down on Culture in Turbulent Times
Florence Nightingale’s Lasting Legacy for Healthcare
Wifikiller.com
Feet to Fire or Walking across Hot Coals?

0 notes
Text
Mac 10 Connected For Life

Mac 10 Connected For Life Video
Mack 10 Connected For Life Mp3 Download
Mac 10 Connected For Life Dirty Version
Mack 10 Connected For Life
If you've followed the steps to connect your Mac to a Wi-Fi network, but the connection to your network or the Internet isn't reliable, the steps in this article might help.
Check for Wi-Fi recommendations
When your Mac tries to connect to a Wi-Fi network, it checks for issues that affect its ability to create a fast, stable, and secure connection. If an issue is detected, the Wi-Fi status menu in the menu bar shows a new item: Wi-Fi Recommendations. Choose it to see recommended solutions.
To extend battery life on a given charge, you can reduce the display brightness, close apps, and disconnect peripheral devices you’re not using. Click Battery in System Preferences to change your power settings. If your MacBook Pro is in sleep when a device is connected to it, the device’s battery may drain. Every modern Mac battery is rated for 1000 cycles; some older models (pre-2010) are rated for 500 or 300 cycles. While the battery won’t suddenly fail when it reaches its limit, it will start to hold less and less charge as it approaches that limit. Eventually, you’ll need to keep your Mac connected to its power cable to use it. Explore releases from Mack 10 at Discogs. Shop for Vinyl, CDs and more from Mack 10 at the Discogs Marketplace. Connected for Life lyrics: Verse 1: Mack 10 I jumped out the blocks like ready! Check all my traps and dodge the fair cold I'm all about the mix like a f.kin collage And out the gararge, is the Bentley Onage. Connected For Life (Feat. Ice Cube, W.C., Butch Ca Lyrics by Mac 10 at Lyrics On Demand.
Wi-Fi recommendations are available in macOS Sierra or later.
Analyze your wireless environment
Your Mac can use Wireless Diagnostics to perform additional analysis.
Quit any apps that are open, and connect to your Wi-Fi network, if possible.
Press and hold Option (Alt) ⌥ key, then choose Open Wireless Diagnostics from the Wi-Fi status menu .
Enter your administrator name and password when prompted.
Wireless Diagnostics begins analyzing your wireless environment:
Z3ta vst plugin free download. If the issue is intermittent, you can choose to monitor your Wi-Fi connection:
Microsoft Word 2003 free download - Microsoft Excel 2003, Microsoft Publisher 2003, Microsoft Office 2003, and many more programs. In the bar at the top of the file, select Save As to save the file. View historical versions of Office files. View the version history of an item or file in a SharePoint list or library. How does versioning work in a SharePoint list or library. A subscription to make the most of your time. Word 2003 .rar topics. Download ms word zip file for pc for free. Office Tools downloads - Microsoft Office Word by Microsoft and many more programs are available for instant and free download.

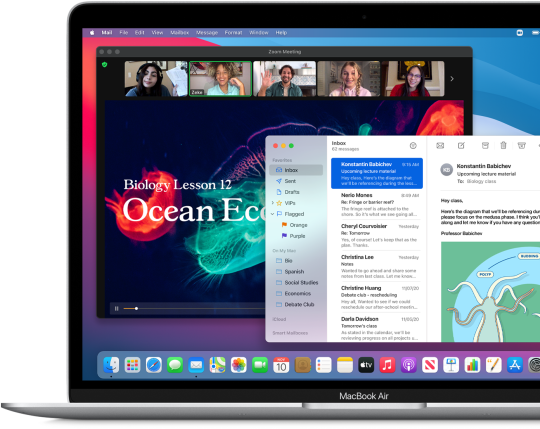
When you're ready to see recommendations, continue to the summary. Wireless Diagnostics asks for optional information about your base station or other router, so that it can include that in the report it saves to your Mac.

Click the info button next to each item in the summary to see details about that item. Wi-Fi best practices are tips that apply to most Wi-Fi networks.
Mac 10 Connected For Life Video
Back up or make note of your network or router settings before changing them based on these recommendations—in case you need to use those settings again.
Monitor your Wi-Fi connection
Your Mac can monitor your Wi-Fi connection for intermittent issues, such as dropped connections. Follow the steps to analyze your wireless environment, but choose ”Monitor my Wi-Fi connection” when prompted.
During monitoring, a window shows that monitoring is in progress. Monitoring continues as long as this window is open and you're on the same Wi-Fi network, even when your Mac is asleep.
If Wireless Diagnostics finds an issue, it stops monitoring and shows a brief description of the issue. You can then resume monitoring or continue to the summary for details and recommendations.
Create a diagnostics report
Wireless Diagnostics automatically saves a diagnostics report before it displays its summary. You can create the same report at any time: press and hold the Option key, then choose Create Diagnostics Report from the Wi-Fi status menu . It can take your Mac several minutes to create the report.
macOS Sierra and later saves the report to the /var/tmp folder of your startup drive, then opens that folder for you. To open the folder manually, choose Go > Go to Folder from the Finder menu bar, then enter /var/tmp.
OS X El Capitan or earlier saves the report to your desktop.
The report is a compressed file with a name that begins “WirelessDiagnostics.” It contains many files that describe your wireless environment in detail. A network specialist can examine them for further analysis.
Use other diagnostics utilities
Mack 10 Connected For Life Mp3 Download

Mac 10 Connected For Life Dirty Version
Wireless Diagnostics includes additional utilities for network specialists. Open them from the Window menu in the Wireless Diagnostics menu bar:
Info gathers key details about your current network connections.
Logs enables background logging for Wi-Fi and other system components. The result is saved to a .log file in the diagnostics report location on your Mac. Logging continues even when you quit the app or restart your Mac, so remember to disable logging when you're done.
Scan finds Wi-Fi routers in your environment and gathers key details about them.
Performance uses live graphs to show the performance of your Wi-Fi connection:
Rate shows the transmit rate over time in megabits per second.
Quality shows the signal-to-noise ratio over time. When the quality is too low, your device disconnects from the Wi-Fi router. Factors that affect quality include the distance between your device and the router, and objects such as walls that impede the signal from your router. Learn more.
Signal shows both signal (RSSI) and noise measurements over time. You want RSSI to be high and noise to be low, so the bigger the gap between RSSI and noise, the better.
Sniffer captures traffic on your Wi-Fi connection, which can be useful when diagnosing a reproducible issue. Select a channel and width, then click Start to begin capturing traffic on that channel. When you click Stop, a .wcap file is saved to the diagnostics report location on your Mac.
Mack 10 Connected For Life
Learn more
Additional recommendations for best Wi-Fi performance:
Keep your router up to date. For AirPort Time Capsule, AirPort Extreme, or AirPort Express Base Station, check for the latest firmware using AirPort Utility. For non-Apple routers, check the manufacturer's website.
Set up your router using Apple's recommended settings, and make sure that all Wi–Fi routers on the same network use similar settings. If you're using a dual-band Wi-Fi router, make sure that both bands use the same network name.
Learn about potential sources of Wi-Fi and Bluetooth interference.
Learn about other ways to connect to the Internet. Quickbooks for mac 2017 release date release.

0 notes
Text
Cisco Drivers Wireless

If you update your Cisco.com account with your WebEx/Spark email address, you can link your accounts in the future (which enables you to access secure Cisco, WebEx, and Spark resources using your WebEx/Spark login). Mar 25, 2017 Cisco Drivers Download by Cisco Systems Inc. The best way to fix your PC to run at peak performance is to update your drivers. If your system is slow, unresponsive or crashes often, the problem may be with your drivers. Sometimes, after upgrading to a newer operating system such as Windows 10, problems can occur because your current driver may. Linksys usb wireless drivers free download - Linksys Compact Wireless-G USB Adapter, Linksys Wireless PC Card WPC11 version 3 drivers, Linksys Wireless-G USB Network Adapter, and many more programs. When autocomplete results are available use up and down arrows to review and enter to select.
Keeping the driver or firmware of your Linksys device updated will fix issues that you may have encountered while using it, and contain device feature enhancements that are not available in previous versions. This article will provide you with instructions on how to download the latest driver or firmware for your Linksys device. Wireless Connectivity. Connecting to a wireless network using Windows XP Wireless Zero Configuration (WZC) Connecting to a wireless network using the Linksys Wireless Network Monitor; Connecting to a hidden wireless network using the Linksys Wireless Network Monitor; Connecting to a wireless network using the Linksys Wireless Manager. The wireless adapter driver is a supporting product so that the computer is familiar with the adapter you are installing. The function of the driver is as a wireless adapter performance controller. If you do not install a wireless adapter on the computer then the computer will not function the product.

How to Update Device Drivers Quickly & Easily
Tech Tip: Updating drivers manually requires some computer skills and patience. A faster and easier option is to use the Driver Update Utility for Linksys to scan your system for free. The utility tells you which specific drivers are out-of-date for all of your devices.
Step 1 - Download Your Driver
Cisco Wireless Usb Drivers Ae1200
To get the latest driver, including Windows 10 drivers, you can choose from a list of most popular Linksys downloads. Click the download button next to the matching model name. After you complete your download, move on to Step 2.
If your driver is not listed and you know the model name or number of your Linksys device, you can use it to search our driver archive for your Linksys device model. Simply type the model name and/or number into the search box and click the Search button. You may see different versions in the results. Choose the best match for your PC and operating system.
If you don’t know the model name or number, you can start to narrow your search down by choosing which category of Linksys device you have (such as Printer, Scanner, Video, Network, etc.). Start by selecting the correct category from our list of Linksys Device Drivers by Category.
Need more help finding the right driver? You can request a driver and we will find it for you. We employ a team from around the world. They add hundreds of new drivers to our site every day.
Tech Tip: If you are having trouble deciding which is the right driver, try the Driver Update Utility for Linksys. It is a software utility that will find the right driver for you - automatically.
Linksys updates their drivers regularly. To get the latest Windows 10 driver, you may need to go to Linksys website to find the driver for to your specific Windows version and device model.
Step 2 - Install Your Driver
After you download your new driver, then you have to install it. To install a driver in Windows, you will need to use a built-in utility called Device Manager. It allows you to see all of the devices recognized by your system, and the drivers associated with them.
How to Open Device Manager
In Windows 8.1 & Windows 10, right-click the Start menu and select Device Manager
In Windows 8, swipe up from the bottom, or right-click anywhere on the desktop and choose 'All Apps' -> swipe or scroll right and choose 'Control Panel' (under Windows System section) -> Hardware and Sound -> Device Manager
In Windows 7, click Start -> Control Panel -> Hardware and Sound -> Device Manager
In Windows Vista, click Start -> Control Panel -> System and Maintenance -> Device Manager
In Windows XP, click Start -> Control Panel -> Performance and Maintenance -> System -> Hardware tab -> Device Manager button
How to Install drivers using Device Manager
Locate the device and model that is having the issue and double-click on it to open the Properties dialog box.
Select the Driver tab.
Click the Update Driver button and follow the instructions.
In most cases, you will need to reboot your computer in order for the driver update to take effect.
Tech Tip: Driver downloads and updates come in a variety of file formats with different file extensions. For example, you may have downloaded an EXE, INF, ZIP, or SYS file. Each file type has a slighty different installation procedure to follow.
If you are having trouble installing your driver, you should use the Driver Update Utility for Linksys. It is a software utility that automatically finds, downloads and installs the right driver for your system. You can even backup your drivers before making any changes, and revert back in case there were any problems.
Try it now to safely update all of your drivers in just a few clicks. Once you download and run the utility, it will scan for out-of-date or missing drivers:
When the scan is complete, the driver update utility will display a results page showing which drivers are missing or out-of-date. You can update individual drivers, or all of the necessary drivers with one click.
For more help, visit our Driver Support Page for step-by-step videos on how to install drivers for every file type.
HP Networking Wireless Router (WiFi) Drivers Download
Optional Offer for DriverDoc by Solvusoft | EULA | Privacy Policy | Terms | Uninstall
Cisco Drivers Wireless Card
ABOUT SSL CERTIFICATES
Cisco Truck Drivers
Manufacturer:HP NetworkingHardware Type:Wireless Router (WiFi)Compatibility:Windows XP, Vista, 7, 8, 10Downloads:85,093,919Download Size:3.4 MBDatabase Update:Available Using DriverDoc:Download Now
Optional Offer for DriverDoc by Solvusoft | EULA | Privacy Policy | Terms | Uninstall
This page contains information about installing the latest HP Networking Wireless Router (WiFi) driver downloads using the HP Networking Driver Update Tool.
Cisco 802.11 G Wlan Driver
HP Networking Wireless Router (WiFi) drivers are tiny programs that enable your Wireless Router (WiFi) hardware to communicate with your operating system software. Maintaining updated HP Networking Wireless Router (WiFi) software prevents crashes and maximizes hardware and system performance. Using outdated or corrupt HP Networking Wireless Router (WiFi) drivers can cause system errors, crashes, and cause your computer or hardware to fail. Furthermore, installing the wrong HP Networking drivers can make these problems even worse.
Cisco Wifi Adapter Driver
Recommendation: If you are inexperienced with updating HP Networking device drivers manually, we highly recommend downloading the HP Networking Wireless Router (WiFi) Driver Utility. This tool will download and update the correct HP Networking Wireless Router (WiFi) driver versions automatically, protecting you against installing the wrong Wireless Router (WiFi) drivers.

0 notes
Text
The Best Work from Home Gadgets
It has been more than a year since we started working from home due to the Covid-19 pandemic. Many people have already adjusted their workspace, but if you have not done that, then it might be the right time for you to get the best gadgets for your workspace.

Apple AirPods Pro
AirPods Pro is not the be-all-end-all answer to all your audio needs. Sound quality still has a way to go, though it’s better than any AirPods version has ever been. Sound, however, is the only thing stopping me from giving AirPods Pro five stars.
They fit well and are more comfortable than any in-ear or on-ear or over-ear headphones I’ve ever used. They have superb ANC, better than anything I’ve experienced with in-ear ANC earphones.
And they have Apple’s incredible H1 processor chip which makes it, so your earphones pair quickly and easily with one device, and are automatically connected to all of your other devices that are signed in with your Apple ID.
Phone as Webcam
It is possible to turn any phone which has a camera into a webcam. By doing there you can increase your video quality significantly and could save about $200. The steps to take so are simple. You just have to install a free version of DroidCam from the Play Store and follow the steps mentioned in the wizard.
Saatchi Aluminum Multi-Port Adapter V2
They took one of our top-selling customer favorite Type-C adapters and made it even better! Introducing its latestAluminium Multi-Port Adapter V2, with all the same peripherals that you loved on the previous model but with several changes to ensure a consistent connection and stable data transfer. The new version is also upgraded the Micro SD card slot and refined our aluminum design, so now it is easier than ever before to add expansion ports to your MacBook/MacBook Pro. Available in two modern colors, silver and space grey.
The highlighted features of Saatchi Aluminum Multi-Port Adapter V2
• Upgraded MicroSD card reader slot
• HDMI video output — up to 4K 30Hz
• USB-C pass-through charging — up to 60Hz
• Gigabit Ethernet — supports 10/100/1000Mbps
• Micro/SD card reader and 3 USB 3.0 ports.
Panasonic AA Nimh 2,550mah Rechargeable Batteries
The Panasonic Pro battery-powered by Eneloop provides 2550mAh of performance for long-lasting, high power capacity, extreme applications. The pro battery is a perfect choice for powering high current consuming devices such as photo strobe flashlights; providing more than twice the number of flashes per recharge in less than half the time as compared to conventional alkaline batteries! Wireless keyboards, mice, game controllers, radio-controlled toys, and a range of household devices can all realize extended performance when powered by Pro batteries.
Caldigit ts3 Plus Thunderbolt 3 Dock
Connect a variety of Thunderbolt 3, USB 3.1 Type-C, USB 3.0 Type-C, USB 3.0 Type-A, DisplayPort 1.2, Gigabit Ethernet, S/PDIF audio, 3.5 mm audio, and SDXC UHS-II peripherals to your compatible system using the space grey TS3 Plus 15-Port Thunderbolt 3 Dock from CalDigit. This dock contains two bi-directional 40 Gb/s Thunderbolt 3 ports, each of which utilizes the reversible USB Type-C connector and also supports 10 Gb/s USB 3.1 and dual-bandwidth DisplayPort 1.2, allowing you to connect up to two 4K/60 Hz displays simultaneously, or one 5K Thunderbolt 3 display.
Google Nest Wi-Fi Router
This nest Wi-Fi device blankets your whole home in fast, reliable Wi-Fi and eliminates buffering in every room — with coverage up to 4400 square feet. From the team that made the best mesh Wi-Fi System in the US. Nest Wi-Fi is a scalable and flexible Wi-Fi System. One Wi-Fi router plugs into your internet provider modem or gateway to create your Wi-Fi network. Home size, materials, and layout can affect how Wi-Fi signal travels. Larger homes or homes with thicker walls or long, narrow layouts may need additional newest Wi-Fi devices for full coverage. The strength and speed of the signal will depend on your internet provider. Based on monthly retail sales of mesh Wi-Fi systems in the US between 2017 – 2018 as reported by the NPD Group, Inc. Home size, materials, and layout can affect how Wi-Fi signal travels. Larger homes or homes with thicker walls or long, narrow layouts may need extra Wi-Fi points for full coverage. The strength and speed of the signal will depend on your internet provider.
James Boond is a Microsoft Office expert and has been working in the technical industry since 2014. As a technical expert, James has written technical blogs, manuals, white papers, and reviews for many websites such as office.com/setup .
Source – The Best Work from Home Gadgets
0 notes
Text
Private LTE Market | Analysis And Opportunities During Covid-19 Pandemic

Private LTE technologies offer broadband data with mobility and roaming capabilities, SIM-based security, and other features to support connectivity for Internet of Things devices and human end-users.
Major factors driving the global private LTE in mining industry market are increase in demand for Internet of Things in the mining industry. Mining processes involve a number of issues in the area of connectivity as mining sites are usually located in isolated regions with minimal cellular coverage. This leads to increased demand for strong communication networks. The strong eco system in the market also strengthens the private LTE in mining industry market. For instance, in June 2017, Redline Communications Group Inc. a provider of wireless networks partnered with Future Technologies Ventures, LLC (Future Technologies) to offer a private LTE network solution to military customers for strategic deployment purposes. With this partnership, Future Technologies Ventures, LLC was able to provide a private network to its existing military customers. However, government rules and regulations for spectrum hamper the private LTE in mining industry market.
Request A Sample Copy Of The Report https://www.transparencymarketresearch.com/sample/sample.php?flag=S&rep_id=56715
The global private LTE in mining industry market can be segmented based on solution, application, enterprise size, and region. The private LTE in mining industry market can be categorized based on solution into infrastructure and devices. The infrastructure solution can be segmented into hardware, software, and services. The hardware solution includes EPC, eNodeB Radio Access Network (RAN), network core, small cells etc. and devices includes phones, notepads, and mobile routers. The services solution can be divided into managed and professional services. Professional services can be further classified into installation & integration, support & maintenance, and auditing & consulting. In terms of application, the global private LTE in mining industry market can be classified into remote control operation, security surveillance, camera monitoring, dispatch structures, water-level monitoring, supply control, detection of moving machinery, collision awareness application, fatigue monitoring, conveyor monitoring, machinery alarm monitoring, and others (access control systems, emergency notification system etc.). In terms of organization size, the private LTE in mining industry market can be classified into small-medium organizations and large organizations.
Based on region, the global private LTE in mining industry market can be segmented into North America, Europe, South America, Asia Pacific, and Middle East & Africa. North America is estimated to account for high market share in 2018, and it is expected to continue its dominance over the forecast period. This is due to government initiatives to allow spectrum (Citizens Broadband Radio Service) for business applications. The private LTE in mining industry market in Canada is also expected to grow at a high CAGR due to a strong eco system in this region. The private LTE in mining industry market in European countries is expected to expand at a significant CAGR due to increasing need for secure and dedicated networks from industry verticals.
The global private LTE in mining industry market is expected to create significant opportunity due to strong eco system partnerships. For instance, in March 2018, Ericsson AB and Ambra Solutions provided a private LTE network for Laronde Mine Agnico Eagle Mines Ltd, a mining company based in Quebec, Canada. The private LTE network is utilizing band 5 at 850 MHz. The installed private LTE network permits the use of IoT sensors and devices to operate, monitor, and collect data throughout the mining site. Moreover, it includes remote control operation for mining machinery, dispatch systems, emergency notification systems, access control systems, automated data collection, ventilation fan monitoring, and gas detection systems.
Key companies operating in the global private LTE in mining industry market are Nokia Corporation, Ericsson AB, NEC Corporation, Squire Technologies, Quortus Limited, NetNumber Inc., Redline Communications, SpiderCloud Wireless, Ruckus Networks, Sercomm Corporation, Intel Corporation, Future Technologies LLC, HCL Technologies Limited, ADVA Optical Networking SE, Mavenir Systems, pdvWireless, and Deutsche Telekom AG.
Request For Covid19 Impact Analysis https://www.transparencymarketresearch.com/sample/sample.php?flag=covid19&rep_id=56715
This study by TMR is all-encompassing framework of the dynamics of the market. It mainly comprises critical assessment of consumers' or customers' journeys, current and emerging avenues, and strategic framework to enable CXOs take effective decisions.
Our key underpinning is the 4-Quadrant Framework EIRS that offers detailed visualization of four elements:
Customer Experience Maps
Insights and Tools based on data-driven research
Actionable Results to meet all the business priorities
Strategic Frameworks to boost the growth journey
The study strives to evaluate the current and future growth prospects, untapped avenues, factors shaping their revenue potential, and demand and consumption patterns in the global market by breaking it into region-wise assessment.
The following regional segments are covered comprehensively:
North America
Asia Pacific
Europe
Latin America
The Middle East and Africa
The EIRS quadrant framework in the report sums up our wide spectrum of data-driven research and advisory for CXOs to help them make better decisions for their businesses and stay as leaders.
Below is a snapshot of these quadrants.
1. Customer Experience Map
The study offers an in-depth assessment of various customers’ journeys pertinent to the market and its segments. It offers various customer impressions about the products and service use. The analysis takes a closer look at their pain points and fears across various customer touchpoints. The consultation and business intelligence solutions will help interested stakeholders, including CXOs, define customer experience maps tailored to their needs. This will help them aim at boosting customer engagement with their brands.
2. Insights and Tools
The various insights in the study are based on elaborate cycles of primary and secondary research the analysts engage with during the course of research. The analysts and expert advisors at TMR adopt industry-wide, quantitative customer insights tools and market projection methodologies to arrive at results, which makes them reliable. The study not just offers estimations and projections, but also an uncluttered evaluation of these figures on the market dynamics. These insights merge data-driven research framework with qualitative consultations for business owners, CXOs, policy makers, and investors. The insights will also help their customers overcome their fears.
3. Actionable Results
The findings presented in this study by TMR are an indispensable guide for meeting all business priorities, including mission-critical ones. The results when implemented have shown tangible benefits to business stakeholders and industry entities to boost their performance. The results are tailored to fit the individual strategic framework. The study also illustrates some of the recent case studies on solving various problems by companies they faced in their consolidation journey.
4. Strategic Frameworks
The study equips businesses and anyone interested in the market to frame broad strategic frameworks. This has become more important than ever, given the current uncertainty due to COVID-19. The study deliberates on consultations to overcome various such past disruptions and foresees new ones to boost the preparedness. The frameworks help businesses plan their strategic alignments for recovery from such disruptive trends. Further, analysts at TMR helps you break down the complex scenario and bring resiliency in uncertain times.
You May Also Like PRNewswire on https://www.prnewswire.co.uk/news-releases/need-for-precision-in-electronic-manufacturing-to-drive-demand-within-global-permanent-magnet-synchronous-motors-market-tmr-828592350.html
The report sheds light on various aspects and answers pertinent questions on the market. Some of the important ones are:
1. What can be the best investment choices for venturing into new product and service lines?
2. What value propositions should businesses aim at while making new research and development funding?
3. Which regulations will be most helpful for stakeholders to boost their supply chain network?
4. Which regions might see the demand maturing in certain segments in near future?
5. What are the some of the best cost optimization strategies with vendors that some well-entrenched players have gained success with?
6. Which are the key perspectives that the C-suite are leveraging to move businesses to new growth trajectory?
7. Which government regulations might challenge the status of key regional markets?
8. How will the emerging political and economic scenario affect opportunities in key growth areas?
9. What are some of the value-grab opportunities in various segments?
10. What will be the barrier to entry for new players in the market?
0 notes
Link
Shop The eBooks For Your 2017 NaNoWriMo Inspiration | Writing Tips
Writing is full of distractions, both internal and external. Here’s some ways to get through it.
Welcome to Part Three of the Writing Tips NaNoWriMo 2017 Countdown, where I talk about the dark side of NaNoWriMo (I mean, we’re two days away from Halloween, so I might as well get spooky for a minute). So, welcome to:
Part Three: 5 Ways To Focus During @NaNoWriMo
And the rest of the series
Part One: 4 Reasons Why You Should Participate In @NaNoWriMo
Part Two: 6 Tips For A Successful @NaNoWriMo
Not to alarm you, but writing is difficult and words are hard. The other day, I was inspired to write this piece when I saw something retweeted into my Twitter timeline. It’s linked here, is a picture called of a PowerPoint slide titled: Why You Think You Don’t Have Time To Write.
And the reasons are:
– You’re letting other people tell you what you should do with your time.
– You’re not treating your writing seriously and so no one else does, either.
– You need a dedicated writing space.
– You’re doing what’s urgent rather than what’s necessary.
– You don’t let other people solve their own problems.
– You think you’ll have more time later to write.
– You’re spending time doing things you don’t care about.
I can’t tell you how many times I’ve either turned to or away from writing, depending on what needed to be done and how easily the words are flowing. Now, what works for me may not work for you, but I still encourage you to read on for five ways to focus during your NaNoWriMo session, especially if you’re fully committing yourself and want to make a concerted effort to make it to 50,000 words by the end of November. Some of these tips will harken to the points I mentioned from that tweet, while others will reflect advice I’ve already posted in the Writing Tipsposts, but there’s no reason to not repeat myself for extra emphasis.
Commit To Your Writing Time
In the first point of Part Two, I wrote about committing to completing your NaNoWriMo project, and part of committing to the project as a whole is committing to your time to actually sit down and write. It doesn’t matter if you pull out your planner (either hard copy or on your smart phone) and schedule out 30 to 60 blocks of time where all you’re going to do is write, or if you know that in the morning you’re going to write a bit before class or work, or you’re dedicating the next month’s lunch hours to the NaNo cause, just commit to taking the time to reach whatever daily milestone you’ve chose.
And part of committing is taking your writing time seriously. In the tweet I mentioned, the second point stated, ‘You’re not treating your writing seriously and so no one else does, either.’, and that’s extremely important. If you’re going to commit to your writing time, then you must commit to it and make it clear to everyone around you that you’re committing to it. If you’re not the type of person who likes to talk about the specifics of your writing project, then just tell your friends and family that you’re working on a new project and you’ve set goals you’ve committed to reaching, and you need your space to accomplish that. If you take it seriously, then so will they.
Don’t Get Distracted By That New Shiny
Sometimes, it feels like every time I sneeze (which is both often and weird), I come up with a new plot idea. But if you’re committing yourself to your NaNoWriMo project, you can’t let yourself get distracted by starting to write another story. If you do, you’ll never finish either your NaNoWriMo project or that new plot bunny or any of the other plot bunnies you come up with. What I recommend is either taking some space in a notebook or a note on your phone and name it something like, Potential Future Story Plots. Take some time to jot down as many notes as you need (but not like, an entire outline), and then go back to work. Whatever it is, it’s probably a cool idea, but it’ll keep. There’s nothing saying that you MUST write every thing you think of at the same time. I know that there are stories that I come up with that I may not be ready to write right now.
Earlier this year, author V.E. Schwab, who you should TOTALLY follow on Twitter because she’s brilliant and hilarious and realistic about writing, posted a video on her YouTube Channel on Shiny New Ideas, which I highly recommend you watch.
For the specifics of #GroundhogOne, which is my project for this year’s NaNoWriMo (more on what it’s about in my announcement post), those of you who have signed up for the #MondayMotivation Newsletter (sign up for it here), know that #GroundhogOne is one of two stories, and it’s not the first I thought of. The first I thought of was actually something that I’m nicknaming #OneVendetta, which is something along the lines of the movies Rogue One: A Star Wars Story (with a little bit of Star Wars: The Phantom Menace, but only the good part, I swear) and V for Vendetta. But when I was thinking about HOW to write #OneVendetta, I realized that I need to introduce the cast first, and that can’t be done in one book. Thus, after a little bit more pondering, #GroundhogOne was born. When I work on writing projects that are within a larger series, I tend to have this habit where I think don’t restrict myself to writing scenes for just one book, but when it comes to NaNoWriMo, I do my best to restrict myself to the project I’m working on. Now, that’s not going to stop me from writing notes toward the plot of #OneVendetta as I work on #GroundhogOne and flesh out the universe that #OneVendetta exists in, and it’s impossible for me to stop myself from coming up with snippets of dialogue to work off of (Prompt Library, anyone?), but my focus is going to be on getting #GroundhogOne off the ground and that alone. Especially because I know that I won’t be able to do justice to #OneVendetta until #GroundhogOne is set.
And Speaking Of Distractions, Get Off Twitter
In my very first Writing Tips post, I wrote about 6 Ways To Transition Out Of Writer’s Block, and the second tip was to get off Twitter. So, do that. And minimize your time on other websites that distract you (like how in Part Two, I mentioned how I went cold turkey on Tumblr and never turned back).
Because it’s SO easy to be distracted. Does anyone remember when the news about the Handbook for Mortals mess? I was glued.to.twitter for HOURS. I mean, part of it was because I was feeding updates to my friend, who is a YA librarian, and therefore NEEDED TO KNOW, but also, like, holy crap it was insane how it all went down. For those of you who don’t know what I mean, check out this comprehensive rundown from one of the websites that broke the news.
But like I said, I spent HOURS following that, and had I been trying to do that during NaNoWriMo, I would probably not reach that day’s writing goal.
You know what your weaknesses are, so know what websites you need to minimize your time in so you can take those writing sessions seriously.
Find A Writing Space
I wrote most of my first novel in a study room in my dorm during my freshman year of college. I wrote the #WhoIsTalyaNightingale novel in a bunch of places, including at work (when I had time to spare, promise), a hotel in Illinois, and my apartment. I’m not a fan of coffee shops, because I can’t help but people watch, but I do remember knocking out some of that story at a Starbucks next to the Galen Center on the campus of USC.
Find a space that works for you. It can be in your bedroom at home, in wherever you want in your apartment if you live alone (or if your roommate doesn’t mind your weird habit of writing on the toilet), an office, a library, a study room, or a cafe. If it works, it works. If you need background noise, make sure it’s productive (and no, that’s not hours and hours of reruns of Property Brotherson HGTV). For more on my thoughts on PRODUCTIVE background noise, check out 6 Sources of Productive Background Noise, which includes one of my favorite online background noise generators, Noisli.
And Something To Remember
The time to write is NOW.
You’re never going to find the ‘perfect’ time to write, and you’re never going to be in ‘perfect’ writing conditions, and you’re never going to be ‘perfectly’ inspired. But you must write anyway. If you don’t try, the words aren’t going to come at all. It doesn’t matter if they’re good, they just have to be there so you can start.
If you need to turn off your phone and disconnect your wireless router to get things done, then turn off your phone and disconnect your wireless router. Download one of those apps that limits your access to certain corners of the Internet for however long your writing session is.
Just do what you need to do, and write.
Shop The eBooks For Your 2017 NaNoWriMo Inspiration
2 notes
·
View notes
Text
Self Made Courses
Hi GUYS!
THANKS For Watching My Post!
SELLING SELF MADE Courses and offering programs FOR CHEAP RATES! Special price buying packs.
BEST PRICES For The Best Courses! Any Proofs Greetings!
You can watch ALL LiST here:
https://selfmadeisland.wordpress.com/
https://selfmadeisland.wixsite.com/courses
https://selfmade.ecwid.com/
https://selfmade.cloudaccess.host/
https://docs.google.com/document/d/1QlFq1gneiIpiP3xTaIVpFxJmnDcjcuQ4pXFa3WsLffA
HOW TO BUY IT
1. ASK Me The Real Price
2. DO Transfer
3. RECEIVE a link to Your Email in Few Minutes
THE VIDEO COURSES and BOOKS ARE IN DIGITAL FORMAT. A LINK WILL BE PROVIDED TO DOWNLOAD.
Skype: Self Made (live:.cid.d9ed21990ea6a54) Facebook: https://fb.me/selfmadeisland
USE ‘Ctrl+F’ TO FIND everything you need
#MACHINE LEARNING
Data Weekends - Neural Networks - Zero to Deep Learning about example
David Chappell - Understanding Machine Learning PluralSight about example
Janani Ravi - Building Classification Models with TensorFlow PluralSight about example
Jerry Kurata - TensorFlow: Getting Started PluralSight about example
Jerry Kurata - Understanding Machine Learning with Python PluralSight about example
Swetha Kolalapudi - How to Think About Machine Learning Algorithms PluralSight about example
Udemy - Complete Guide to Tensorflow for Deep Learning with Python site about example
Udemy - Mastering Microcontroller with Embedded Driver Development` about1 about2 example
Udemy - Python for Data Science and Machine Learning Bootcamp about example
#HACKING PROGRAMMING
Anonymous Content
aLeZX - Anónimos en la Red. Primera parte.pdf about
aLeZX - Anónimos en la Red. Segunda parte.pdf
Anonymous - El Manual Super-Secreto - 0.2.0 - ES.pdf
Anonymous DoSer.exe
Anonymous Security Handbook
BruteForcer_081 (client/server)
DDoS for Anonymous Operation.rar about
Deface Page Creator v1.rar
Documentos_PenTest.rar
HOIC.rar
HttpDosTool3.6.zip
IP Killer 2.0.rar
Rahul Singh Patel - Kali Linux Social Engineering.pdf
Alonso Eduardo - Kali Linux v2 ReYDeS.pdf
MintiModz - Hack Pack (Anti Viruses-BotNets-Botting-Bruteforcing-Cracking-DDoS Programs-Deface Creators-Doxing-eWhore-Exploit Scanning-Exploiting-Exploits-Guides-Hacking-Injection Programs-MD5-Misc-ShareCash-Skype-Source Codes-Tutorials-Viruses-VPN'S & PROXIES-Wifi-YouTube) (4.6Gb progs) about (doxing)
CyberTraining365
CyberTraining365 - Certified Security Analyst Training (CSAT)
CyberTraining365 - Cyber Security Advanced Persistent Threat Defender (CAPTD)
CyberTraining365 - Cyber Security Malicious Software Defender (CSMD)
CyberTraining365 - Cyber Security Source Code Defender (CSCD)
CyberTraining365 - Cyber Security Threat Intelligence Research (CTIR)
CyberTraining365 - Cyber Security Web Application Defender (CWAD)
CyberTraining365 - Certified Ethical Hacker (CEH) v9 Training
CyberTraining365 - Computer Hacker and Forensic Investigator (CHFI)
CyberTraining365 - Kali 101
Cryptonary - Cryptocurrency Course` about example
CCNP R&S INE V2
1-CCNP R&S TECHNOLOGIES V2 + DELETED FROM V1 about example
2-CCNP ROUTE PRACTICE EXAM about example
3-CCNP SWITCH PRACTICE EXAM about example
Udemy - Master Electron v5 Desktop Apps with HTML, JavaScript & CSS
Udemy - The Complete Networking Fundamentals Course. Your CCNA start
Udemy - The Complete Wireshark Course. Go from Beginner to Advanced!
Udemy - Angular 7 Security Masterclass (with FREE E-Book)
Udemy - Build Incredible Chatbots - Learntpoint.com
Udemy - Cisco Meraki Wireless setup from scratch
Udemy - JavaScript Beginner Bootcamp (2019) about example
Udemy - NgRx In Depth (Angular 7 and NgRx 7, with FREE E-Book) - Learntpoint.com
Udemy - PHP for Beginners - Become a PHP Master - CMS Project - Learntpoint.com
Udemy - PSD to Responsive HTML5 Beginner to Advanced - Learntpoint.com
Udemy - Python for Absolute Beginners
Udemy - Python for Beginners with Examples
Udemy - React - The Complete Guide (incl Hooks, React Router, Redux)
Udemy - SQL for Newbs Data Analysis for Beginners - Learntpoint.com
Udemy - The Complete Android N Developer Course - Learntpoint.com
Udemy - The Complete Java Developer Course Beginner To Expert - Learntpoint.com
Udemy - The Complete Web Developer Course 2.0
Udemy - The Python Mega Course - Build 10 Real World Applications
Udemy - Web Design with WordPress Everything from Beginning to End - Learntpoint.com
#Computer Security
Addison Wesley - Crimeware Understanding New Attacks And Defenses.chm
Addison Wesley - The Technica .And Social History Of Software Engineering.pdf
Bernard Peter Robichau - Apress Healthcare Information Privacy + Security.pdf
McGraw Hill - Principles Of Computer Security CompTIA Security Plus And Beyond Lab Manual 2nd Edition.pdf
Denny Cherry - Syngress The Basics Of Digital Privacy May 2013.pdf
#IOS, LINUX, SEO, VISUAL STUDIO Courses
Udemy - Mastering Microcontroller with Embedded Driver Development ` about1 about2 example
Build Responsive Real World Websites with HTML5 and CSS3 2.0
Creating Whiteboard Animation Videos Using Videoscribe 2017 about example
Linux Command Line Basics
Microsoft Office 2016 Essential Training 9 Course Bundle
The Complete Android Developer Course Beginner To Advanced
The Complete Facebook Ads & Marketing Course 2017
Pluralsight - CompTIA Project Plus about example
Secret Sauce - The Ultimate Growth Hacking Guide
Seguridad Informática Informatic Security
Udemy - The Complete Ethical Hacking Course (6.8 GB)
Linux Courses
CBT NUGGETS LINUX SERIES (BEGINNERS) about example
CBT NUGGETS LINUX SERIES (INTERMEDIATE AND ADVANCED) about example
Linux LPI LPIC-2 Exam 201 about example
Networking Books
802.11 Wireless Networks Security and Analysis - Computer Communications.pdf
Applications of Social Network Analysis for Building Community Disaster Resilience Workshop.pdf
Applied Cryptography and Network Security.pdf
Artificial Neural Networks in Real life Applications.pdf
Basic_networking_tutorial.pdf
Cisco Lan Switching.pdf
Computer Networking A Top-Down Approach_ 6th Edition.pdf
Computer Networking and the Internet.pdf
Computer Networks.pdf
Computer Networks - An Open Source Approach.pdf
Computer Science - Network.pdf
Computer-Networking-Principles-Bonaventure-1-30-31-OTC1.pdf
Computer Networks_NEW.pdf
Cryptography and Network Security Principles and Practices.pdf
Cryptography and Network Security Principles and Practices_ 4th Edition.pdf
Energy Efficiency in Communications and Networks.pdf
Ethical Hacking and Network Defense.pdf
Foundations of Neural Networks, Fuzzy Systems, and Knowledge Engineering.pdf
Hacking and Network Defense.pdf
Hacking Exposed 7_ Network Security Secrets & Solutions_ 7th Edition.pdf
Handbook of Neural Network Signal Processing.pdf
How_DDoS_Works.pdf
Inside a Crimeware Network.pdf
Intorduction to Computer Networks.pdf
Java Network Programming and Distributed Computing.pdf
JULIAN ASSANGE - Underground.pdf
Known Networks.pdf
Linux Network Administrators.pdf
Network - What Is an Iterator in C_ Part 1.pdf
Network - What Is an Iterator in C_ Part 2.pdf
Network Analysis Architecture and Design 3e By James McCabe - Morgan Kaufmann.pdf
Network Intrusion Detection_ 3rd Edition.pdf
Network Programming in Dot NET With C Sharp and Visual Basic Dot NET.pdf
Network Theorizing Knowledge work in Telecommunications.pdf
Network-Centric Naval Forces_ A Transition_Strategy for Enhancing Operational Capabilities_.pdf
Neural Networks in Healthcare - Potential and Challenges.pdf
Nmap 6 Network Exploration and Security Auditing Cookbook.pdf
Recurrent Neural Networks.pdf
Red Hat Linux Networking and System Administration.pdf
TAG - A Tiny Aggregation Service for Ad-Hoc Sensor Networks.pdf
tcp_ip_illustrated_volume_1_the_protocols_2nd_edit.pdf
TCP_IP_Networking_basics.pdf
The Encyclopedia of Multimedia Technology and Networking.pdf
The Hacker's Handbook - The Strategy Behind Breaking into and Defending Networks.pdf
The TCP-IP Guide.pdf
the-protocols-tcp-ip-illustrated-volume-1.9780201633467.24290.pdf
Tracking GhostNet_ Investigating Cyber Espionage - Network Information Warfare Monitor.pdf
Understanding Linux Network Internals.pdf
Forensics
Sherri Davidoff, Jonathan Ham - Prentice Hall Network Forensics.pdf
Steve Anson, Steve Bunting - Sybex Mastering Windows Network Forensics And Investigation 2nd Edition.pdf
John Sammons - Syngress The Basics Of Digital Forensics.pdf
Michael Hale Ligh, Andrew Case - Wiley Memory.pdf
Cloud
Pluralsight - AWS Developer - Getting Started about example
Pluralsight - Azure Functions Fundamentals about example
Pluralsight - Foundations for Cloud Architecture about example
Pluralsight - Securing Cloud DevOps in PaaS, IaaS, and SaaS Settings about example
Docker
Pluralsight - Docker and Containers - The Big Picture
Pluralsight - Getting Started with Docker
Ionic
Pluralsight - Building Mobile Apps with Ionic 2, Angular 2, and TypeScript
IonicFramework - The Top Open Source Framework for Building Amazing Mobile Apps Tutorials
ITIL
Pluralsight - ITIL® Foundation - Core Concepts
Pluralsight - ITIL® Foundation - Lifecycle Phases and Processes
Pluralsight - ITIL® Foundations
Languages
Pluralsight - Python - Getting Started
NET
Pluralsight - ASP.NET Core Fundamentals
Pluralsight - Building a RESTful API with ASP.NET Core
Pluralsight - Introduction to ASP.NET 4 WebForms
Other
Pluralsight - ABAP Workbench - The Big Picture about example
Pluralsight - Advanced Node.js
Pluralsight - Algorithms and Data Structures - Part 1
Pluralsight - Algorithms and Data Structures - Part 2
Brian Eiler - Excel 2013 - Analysis Techniques and Random Numbers from thecoursewaregroup
Pluralsight - Getting Started with Apache Kafka
Pluralsight - Getting Started with Power BI
Pluralsight - Introduction to ABAP Objects - Concepts & Class Builder
Pluralsight - Mastering Your SAP GUI
Pluralsight - Microsoft MTA - Database Administration Fundamentals
William Pearson - Organizational BI with SSAS 2012 Tabular - Intermediate from islandtechnologies
Pluralsight - SQL Server - Optimizing Stored Procedure Performance
Security
Pluralsight - Cyber Security Awareness - Malware Explained
Pluralsight - Cyber Security Awareness - Social Engineering
Pluralsight - Cyber Security Awareness - The Internet of Things (IoT)
Troy Hunt - Ethical Hacking - Denial of ServiceEthical Hacking - Evading IDS, Firewalls, and Honeypots
Troy Hunt - Information Systems Auditing - The Big Picture about example
Pluralsight - PCI DSS - The Big Picture
Udacity
Artificial Intelligence from Udacity
Ben Burkholder - Classification Models from Udacity about example
Intro to Machine Learning from Udacity
Xamarin
Building an MVVM based Architecture for Xamarin Mobile Apps
Building Cross-Platform iOS Android Apps with Xamarin, Visual Studio, and C# - Part 1
Building Your First Mobile Application with Xamarin.Forms and Visual Studio 2017 about example
Moving Beyond the Basics with Xamarin.Forms
Xamarin Forms Course
Youtube
Aaron Sorkin - Screenwriting
A. Thomas Perhacs - Ultimate Hypnotic Influence
Adam Armstrong - Deluxe Bundle
Adam Gilad - Relationship God
Adam Lyons - Hot Girl In 7 Days
Adina Rivers - Pussy Pleasure Course
Adrian Morrison
Adrian Morrison - Tee Advantage
Adrian Morrison - EcomSuiteX
Adrian MorrisoneCom - Success Academy 2017 advanced (58Gb)
Adrian MorrisoneCom - Success Academy 2017 (30Gb)
Aidan Booth - 100k Factory
Alex Allman - Orgasms
Alex Vilenchik - Playing With Fire
Andy Puddicombe - Headspace V2
Anthony Carbone - Wolf Millionaire of Instagram
Anthony Morrison - Fan Page Domination
Anthony Robbins
Anthony Robbins - Awaken the Giant Within I
Anthony Robbins - Change Your Focus Using Questions
Anthony Robbins - Coach John Wooden
Anthony Robbins - Core 100 Training
Anthony Robbins - Creating Lasting Change
Anthony Robbins - Date With Destiny (Closed Eye Process)[1-7]
Anthony Robbins - Get The Edge
Anthony Robbins - Giant Steps
Anthony Robbins - Lessons In Mastery
Anthony Robbins - Live With Passion
Anthony Robbins - Living Health
Anthony Robbins - Making Success a Study - My Story
Anthony Robbins - Meeting master Deepak Chopra
Anthony Robbins - New Year, New Life! (Chat 11-12-01)
Anthony Robbins - Nutrition
Anthony Robbins - Personal Power Classic
Anthony Robbins - Personal Power II
Anthony Robbins - Personal Training System
Anthony Robbins - Power Talk - Influence With Robert Cialdini
Anthony Robbins - Priming Exercise
Anthony Robbins - Stop Yourself From Financial Self Sabotage
Anthony Robbins - The Body You Deserve
Anthony Robbins - The Decision That Ensures Your Success
Anthony Robbins - The Power To Influence
Anthony Robbins - The Power to Shape Your Destiny
Anthony Robbins - Time of your life
Anthony Robbins - Ultimate Relationship Program
Anthony Robbins - Unleash the Power Within
Anthony Robbins - Unlimited Power (NLP)
Arash Dibazar
Arash Dibazar - Dark Energy
Arash Dibazar - Seductive Confidence
Arash Dibazar - Solomon's Temple
Arash Dibazar - Supernatural
Arash Dibazar - The Eye of Ra
Athlean X
Athlean X - Athlean AX 1 + Bonuses
Athlean X - Inferno Shred
Athlean X - The Original Pro Athlete Workout
Authority Hacker - Authority Site System
BadBoy - The Instasex Method Package
Barron Cruz
Barron Cruz - Beast
Barron Cruz - Social Invincibility
PDSCourses.com - Be Orgasmic
Ben Malol - eCom Blueprint Bootcamp Program
Ben Pakulski - Mi40X
Ben Settle - Persuasion Secrets of the World's Most Charismatic & Influential Villains (pdf)
Bobby Rio
Bobby Rio - 10 Step Tinder Solution
Bobby Rio - 21 All Time Best Texts To Send A Girl
Bobby Rio - 99 Best Texts
Bobby Rio - Conversation Escalation
Bobby Rio - Conversation Topics Training Lab
Bobby Rio - Get The Girl
Bobby Rio - Magnetic Messaging
Bobby Rio - Player's Paradigm
Bostjan Belingar - The Player
Braddock
Braddock - Social Circle Mastery
Braddock - The Ultimate Guide to Text and Phone Game
Brian Burt & Brian Johnson - Sponsored Products Academy
Brian Dean - SEO That Works 2.0
Brian Tracy - Think Like A Leader
Bryan Dulaney - Funnel Selling Business
Calisthenics Unity - Full Body Workout Program
Carlos Xuma
Carlos Xuma - Bad Boy Formula
Carlos Xuma - Ultimate Inner Game
Carter Thomas - Bluecloud App Formula
Charlie Houpert - Charisma University
Chris Record - 3 Zero Club & Inner Circle
Christian Hudson - The Girlfriend Activation System V2
Christian McQueen - Deep Conversion Game
Christie Marie Sheldon - Unlimited Abundance
Connor Murphy - AdonyxMen - God Like Physique
Content Promotion Summit 2016 (Day 1 - Content StrategyDay 10 - Social media marketigDay 11 - Influencer outreach and partnershipsDay 12 - Online communitiesDay 13 - Video marketingDay 2 - Content CreationDay 3 - CopywritingDay 4 - Content WritingDay 5 - Content OutreachDay 6 - Earned MediaDay 7 - PodcastingDay 8 - Paid media and funnelsDay 9 - Search engine optimization) +
ConversionXL
ConversionXL - Ecommerce Growth Masterclass
ConversionXL - Google Analytics Master Course
Copy Hackers - 10x Landing Pages
Craig Miller - Sexual Decoder System
Daiyaan Caan - Bizz Classes
Dan Brown - Masterclass on Writing Thriller
Dan Dasilva & Justin Cener - Social Ad Classroom
Dan Henry - Facebook Ads For Entrepreneurs
Dan Kennedy
Dan Kennedy - Copywriting Academy
Dan Kennedy - Fascination Marketing System
Daniel Rose
Daniel Rose - Sex God Method I
Daniel Rose - Sex God Method II
David DeAngelo
David DeAngelo - Approaching Women
David DeAngelo - Cocky Comedy
David DeAngelo - Love the Final Chapter
David DeAngelo - Lust
David DeAngelo - On Being A Man
David Mamet - Dramatic Writing
David Snyder
David Snyder - Attractivation Full
David Snyder - Covert Persuasion Intelligence
David Snyder - Killer Influence
David Snyder - Rapid Attraction Secrets
David Snyder - Vibrational Healing
David Tian
David Tian - 10 Weeks to Freedom
David Tian - Awakening
David Tian - Conversation Vortex
David Tian - Invincible
David Tian - Limitless
David Tian - The Charisma Code
David Wygant
David Wygant - 7 Second Seduction
David Wygant - Always Talk To Strangers.pdf
Deadmau5 - Electronic Music
Day Game Mastery - Attraction Formulas
DayGame
Daygame - Blueprint
Daygame - Immersion
Daygame - Effortless Infield
Daygame - Geek Get Girl
Daygame - The Yad Show
Deepak Wayne
Deepak Wayne - Bonus Material
Deepak Wayne - Calibration and Logistics
Deepak Wayne - Conversation Domination
Deepak Wayne - Deepak Infields
Deepak Wayne - Deepak's Journey
Deepak Wayne - Hardcase student transformations
Deepak Wayne - Inner Game
Deepak Wayne - Meet Women Every Day preview
Deepak Wayne - Texting and Tinder
Deepak Wayne - Ultimate Seduction Model
Deepak Wayne - Unique Concepts for Success
Deepak Wayne - USM modules AUDIO ONLY
Derek Rake
Derek Rake - Alpha Male Activator
Derek Rake - Boyfriend Destroyer System
Derek Rake - Conversational Seduction
Derek Rake - Cougar Seduction System
Derek Rake - Dark Rake Method
Derek Rake - Dark Rapport
Derek Rake - Insider Lab
Derek Rake - Manipulation Black Book
Derek Rake - MKDelta
Derek Rake - Online Dating Playbook
Derek Rake - ReSeduction
Derek Rake - Shogun Method
Derek Rake - Texting On Steroids
Derek Rake - The Barnum Manuscript
Derek Vitalio - Seduction Science
Digital Marketer - Content & Commerce Summit 2016
Don Amante - The Sensual Hunter Method
Dustin Hoffman - Acting
D-Rion Williams - Alpha Relational Dynamics
Eben Pagan - Wake Up Productive 3.0
Edward deBono - How You Can Be More Interesting
Efficient Pickup - Seduction Mind Hacks
Eric Disco - She's Six Steps Away
Eric Edgemont - Friends Into Lover
Ethercycle - Ecommerce Bootcamp
Evans Perks - Entrepreneurship
Evil Stifler - Infields
Ezra Firestone & Jason Fladlien - Operation Physical Products
Flow Genome - Flow Fundamentals 2.0
Frank Kern
Frank Kern - Client Acquisition System
Frank Kern - Inner Circle Bribe
Frank Kern - Legacy Collection
Gabrielle Moore - Naked U
Gary Halbert - Sales Letters Collection
Garry Kasparov - Chess
Gary Vaynerchuk - Building a Personal Brand
Glen Allsop - Marketing Inc V3 2016
Gordon Ramsay
Gordon Ramsay - Cooking
Gordon Ramsay - Masterclass on Restaurant Recipes
Grant Cardone
Grant Cardone - 10X Growth Con 2017
Grant Cardone - 10X Rule
Grant Cardone - Be Obsessed or Be Average
Grant Cardone - Cardone University (2016)
Grant Cardone - Make Millions In Business Video Webcast
Grant Cardone - Playbook
Grant Cardone - Rules of Success
Grant Cardone - The 10X Rule Audiobook
Greg Frost
Greg Frost - Photographic Memory
Greg Frost - Success Manager Pro
Greg Greenway
Greg Greenway - 53 Laws
Greg Greenway - Dating Solutions
Greg Greenway - Getting Physical
Greg Greenway - Project Royalty
Greg Greenway - Sex On Demand System
Greg Greenway - Social Supremacy Blueprint
GunWitch - Seduction MMA
Hans Zimmer - Film Scoring
Henry Grayson - The New Physics Of Love
Honest Signalz Academy (pfd + few videos)
Hypnosis For Inner Game
Hypnosis For Inner Game - Hypnosis Downloads.com
Hypnosis For Inner Game - Hypnosis Live
Hypnosis For Inner Game - hypnosislive
Hypnosis For Inner Game - Naturalhypnosis
Hypnosis For Inner Game - PUA Hynosis
Hypnotica
Hypnotica - Collection Of Confidence
Hypnotica - Modern Day Sexual Man
Hypnotica - The Sphinx of Imagination
Igor Ledochowski
Igor Ledochowski - Conversational Hypnosis Mastery
Igor Ledochowski - Covert Trances Hypnosis
Igor Ledochowski - Mind Bending Language Roundtable
Igor Ledochowski - Power of Conversational Hypnosis
Igor Ledochowski - The Money In Your Mind
Igor Ledochowski - The Power of Self Hypnosis
Igor Ledochowski - The YES Decks
Igor Ledochowski - World Class Hypnotic Storyteller
IN10SEC
IN10SEC - Archive.pdf
IN10SEC - October Man Sequence.pdf
IN10SEC - Secret Principles of Pleasure - A Lovers Manual of Secrets.pdf
IN10SEC - Speed Rapport.pdf
IN10SEC - Speed Rapport Workbook - Patterns and Themes.pdf
IN10SEC - Symbolic Morphology.pdf
Iris Reading
Iris Reading - Comprehension Training Course
Iris Reading - Focus Course
Iris Reading - Memory Improvement Course
Iris Reading - Mind Mapping Course
Iris Reading - Productivity Course Level 1
Iris Reading - Productivity Course Level 2
Iris Reading - Speed Reading Course for Digital Readers
Iris Reading - Speed Reading Foundation Course
Iris Reading - Speed Reading Mastery Course
James Patterson - Writing
J. D. Fuentes
J. D. Fuentes - Basic Arousal.pdf
J. D. Fuentes - Gut Impact.pdf
J. D. Fuentes - The Sexual Key.pdf
Jack Ellis
Jack Ellis - Astral Power
Jack Ellis - Becoming The Beast
Jack Ellis - Beguiled
Jack Ellis - Beyond Mind Control
Jack Ellis - Black Magic Tantra
Jack Ellis - CIA Hypnosis package
Jack Ellis - Elite Social Control
Jack Ellis - Erotic Hypnosis Syndicate
Jack Ellis - Forbidden Patterns
Jack Ellis - Hoodoo
Jack Ellis - HypnoRitual
Jack Ellis - Occult Superstar
Jack Ellis - Pimp Secrets
Jack Ellis - Power Mindwaves
Jack Ellis - Remote Viewing Mastery
Jack Ellis - Satanic Sex Secrets
Jack Ellis - Seven Gates
Jack Ellis - The Lucifer Complex
Jack Ellis - The Manson Effect
Jack Ellis - The Secrets of Psychic Power
Jack Ellis - UNITROL
Jack Ellis - 50 Shades of Seduction.pdf
Jack Ellis - Backdoor Secrets.pdf
Jack Ellis - Beyond Storytelling.pdf
Jack Ellis - Brainwashing.pdf
Jack Ellis - Confessions of A Cult Deprogrammer.pdf
Jack Ellis - Dark Yoga.pdf
Jack Ellis - Forbidden Rituals.pdf
Jack Ellis - How to Catch a Cheater.pdf
Jack Ellis - How to Catch a Liar.pdf
Jack Ellis - How to Get that One Special Girl.pdf
Jack Ellis - How to Nail Christian Girls.pdf
Jack Ellis - Hypnotic Hallucinations.pdf
Jack Ellis - Interview with Jack Ellis.pdf
Jack Ellis - Mind Rape.pdf
Jack Ellis - Mindfuckers.pdf
Jack Ellis - Occult Hypnosis.pdf
Jack Ellis - Occult Superstar.pdf
Jack Ellis - Psychic Vampires.pdf
Jack Ellis - Ritual Mind Control.pdf
Jack Ellis - Seduction Methods of the Ancient Masters.pdf
Jack Ellis - Sex Cults.pdf
Jack Ellis - Sex, Drugs and Brainwashing.pdf
Jack Ellis - Sexual Brainwashing.pdf
Jack Ellis - Staggering Seduction Mines.pdf
Jack Ellis - Subliminal Audio Mastery.pdf
Jack Ellis - Subliminal Warfare.pdf
Jack Ellis - The Casanova File.pdf
Jack Ellis - The Evil Eye.pdf
Jack Ellis - The Odysseus Code.pdf
Jack Ellis - The Psychic Self Defense Strategy.pdf
Jack Ellis - The Secret Society.pdf
Jack Ellis - The Seduction Code.pdf
Jack Ellis - Total Orgasm Power.pdf
Jack Ellis - Turn Defeat Into Victory.pdf
Jack Ellis - Ultimate Psychic Energy.pdf
Jack Johnson - Kill Your Porn & Masturbation Habit
James Clear - The Habits Masterclass
James Marshall
James Marshall - 5 Principles of Natural Seduction
James Marshall - Dating Accelerator
James Marshall - Marshall Meditation Method
Jason Capital
Jason Capital - $1K A Day Private Mastermind
Jason Capital - 17 Moves That Blow Her Fucking Mind
Jason Capital - 277 Dirty Talk
Jason Capital - 4x Energy
Jason Capital - 70 Laws
Jason Capital - Attraction God
Jason Capital - Big Dick Big Money Big Life
Jason Capital - Carefree Installation
Jason Capital - Carefree Installation System
Jason Capital - Cash Flow King
Jason Capital - Celebrity Series [VAULT]
Jason Capital - Charisma God (Attraction King)
Jason Capital - Charisma Installation System
Jason Capital - Conversation Crack
Jason Capital - Conversation God
Jason Capital - Dark Side Mind Tricks
Jason Capital - Devoted Girlfriend System
Jason Capital - Digital Millionaire Live
Jason Capital - Dominate your day
Jason Capital - Donald Trump Formulaby Jason Capital
Jason Capital - Elite Mentor Summit 2017
Jason Capital - Email Millionare
Jason Capital - EMR Tapes
Jason Capital - Girls Tell All UNCUT (SD)
Jason Capital - HardDrive
Jason Capital - Harvey Specter Formula
Jason Capital - Her Favorite Kisser
Jason Capital - Higher Status Video course
Jason Capital - Higher Status Videocourse
Jason Capital - HJGM
Jason Capital - Ice Cold System
Jason Capital - Inside Donald’s High Status Weapons - Why Donald Trump Will SMASH Hillary This November
Jason Capital - Instant Connection Conversations
Jason Capital - Jedi Mind Tricks & DSMT
Jason Capital - Live Infield Footage
Jason Capital - Magic Bag
Jason Capital - Magic Bag of Tricks
Jason Capital - Make Money Want You Collection
Jason Capital - Make Women Want You
Jason Capital - Make Women Want You Unleashed
Jason Capital - Mental Dominance
Jason Capital - Mental Dominance X-Files
Jason Capital - Million Dollar Phrases
Jason Capital - Millionaire DNA Activation System
Jason Capital - Millionaire Switch For Men
Jason Capital - Millionaire X Files
Jason Capital - Natural Charm
Jason Capital - Power Influence
Jason Capital - Power Influence System
Jason Capital - Power Positioning System
Jason Capital - Power Switch
Jason Capital - Social God (HD)
Jason Capital - Social Media God
Jason Capital - Social Proof Bible
Jason Capital - Social Switch
Jason Capital - STATUS
Jason Capital - STATUS Unleashed
Jason Capital - Storytelling God
Jason Capital - Success Installation
Jason Capital - The Capital Secret
Jason Capital - The Love Code
Jason Capital - Tony Stark Formula
Jason Capital - Torrents
Jason Capital - Videos
Jason Capital - Vinny Chase Formula by Jason Capital
Jason Capital - Word For Word Attraction System by JC
Jason Capital - 5 Body Language Secrets That Get The Girl Every Time.pdf
Jason Capital - 7 Forbidden Words That Trigger Female Obsession.pdf
Jason Julius
Jason Julius - Extreme Stamina
Jason Julius - Female Orgasm Blueprint (2009)
Jeremy Miner - 7 Figures Sales Training
Jessica J - Speak To Spark Arousal
JMULV - Occam's Razor
John Sonmez - 10 Steps To Learn Anything
Jon Sinn
Jon Sinn - Advanced Strategies for Sexualized Comfort
Jon Sinn - Breakthrough Comfort Formula
Jon Sinn - Day Game & Same Day Lays
Jon Sinn - Daygame Infield
Jon Sinn - Get Laid More Home Study Course
Jon Sinn - Opening 2.0
Jon Sinn - Secrets Of 5 Minute Chemistry
Jon Sinn - Seduction Roadmap
Jon Sinn - Stripper Code
Jon Sinn - MP3s (How To Learn Game, Instant Dates, Mastering the Fundamentals, Phone Game, Same Day Lays, Trouble Shooting Day Game)
Jonathan Altfeld - Irresistible Voice
Joshua Earp - SEO Mastery Course
Joshua Pellicer - The Tao of Badass
Junior Serrano - My CPA ATM
Justin Wayne
Justin Wayne - Conversation skills
Justin Wayne - Step by Step Seduction
Justin Wayne - The Domino Effect
Ken Burns - Masterclass on Documentary Filmmaking
Ken Wilber - Full Spectrum Mindfulness
Kenrick Cleveland
Kenrick Cleveland - Creativity Switch
Kenrick Cleveland - Da Vinci Master Switch
Kenrick Cleveland - Magical Objection Mastery
Kenrick Cleveland - Meta Level
Kenrick Cleveland - Persuasion 911
Kenrick Cleveland - Power of Being Complete
Kenrick Cleveland - Propaganda Switch
Kenrick Cleveland - Rise Above
Kenrick Cleveland - Unconscious Persuasion
Kevin Fahey - IM Traffic Facebook Masters
Kevin Spacey - Acting
Kinobody
Kinobody - Aggressive Fat Loss 2.0
Kinobody - Bodyweight Mastery
Kinobody - Greek God Muscle Building Program
Kinobody - Kinochef
Kinobody - SuperHero Bulking Program
Kinobody - Warrior Shredding Program
Kinobody - GTP-MainGuide.pdf
Kinowear - Bible
KIZEN - Infinite Off-Season
Kyle Cease
Kyle Cease - Creativity Switch
Kyle Cease - Da Vinci Master Switch
Kyle Cease - Magical Objection Mastery
Kyle Cease - Meta Level
Kyle Cease - Persuasion 911
Kyle Cease - Power of Being Complete
Kyle Cease - Propaganda Switch
Kyle Cease - Rise Above
Kyle Cease - Unconscious Persuasion
Kyle Simpson - Fronted Master - Advanced JavaScript
Learn Close Combat Training - Military Hand-To-Hand Combat
Leo Gura - Ultimate Life Purpose
Liam McRae
Liam McRae - How to Get Her Sexually Invested in Seduction
Liam McRae - Limitless Seducer
Liam McRae - Rapid Escalation
Lynda.com
Lynda.com - A Mix Engineer's Glossary of Techniques.7z
Lynda.com - A Prolific Music Producer's Workflow for Finishing Tracks.7z
Lynda.com - Ableton Live 9 for Live Performance.7z
Lynda.com - Advanced Google AdWords 2017.7z
Lynda.com - Advertising on Instagram.7z
Lynda.com - Affinity Photo Essential Training.7z
Lynda.com - After Effects CC 2018 - Editors and Post Essential Training.7z
Lynda.com - After Effects Guru - Plugins You Should Know.7z
Lynda.com - After Effects Guru - Tracking Cameras and Stabilizing Footage.7z
Lynda.com - After Effects Scripts & Tips - 2 Design Theory & Animation.7z
Lynda.com - Audio and Music Production Careers - First Steps.7z
Lynda.com - Audio Mixing Bootcamp.7z
Lynda.com - Audio Mixing Master Class.7z
Lynda.com - Audition CC 2018 Essential Training.7z
Lynda.com - Building an Integrated Online Marketing Plan.7z
Lynda.com - Building Material Design Apps on Android with React Native.7z
Lynda.com - Capture One Pro 10 - Retouching.7z
Lynda.com - Capture One Pro 10 Essential Training.7z
Lynda.com - CompTIA Security+ Cert Prep (SY0-401) - The Basics.7z
Lynda.com - Content Marketing - Blogs.7z
Lynda.com - Content Marketing - Newsletters.7z
Lynda.com - Content Marketing - Photos.7z
Lynda.com - Content Marketing - Podcasts and Audio.7z
Lynda.com - Content Marketing - Slides.7z
Lynda.com - Content Marketing - Staying Relevant.7z
Lynda.com - Content Marketing Foundations.7z
Lynda.com - Creating an Editorial Calendar.7z
Lynda.com - CSS Essential Training 3.7z
Lynda.com - Digital Release and Promotion Strategies for Musicians.7z
Lynda.com - EDM Production Techniques - Basslines.7z
Lynda.com - EDM Production Techniques - Drums.7z
Lynda.com - EDM Production Techniques - Extreme Sound Mangling.7z
Lynda.com - Entrepreneurship - Raising Startup Capital.7z
Lynda.com - Facebook for Business.7z
Lynda.com - Finance Essentials for Small Business.7z
Lynda.com - Finance Foundations.7z
Lynda.com - Finance Foundations - Income Taxes.7z
Lynda.com - First Look - Java 9.7z
Lynda.com - From React to React Native.7z
Lynda.com - Game Development Foundations - Game-Related Math.7z
Lynda.com - Git Essential Training.7z
Lynda.com - Google AdWords Essential Training.7z
Lynda.com - Google Analytics Essential Training.7z
Lynda.com - Google+ for Business.7z
Lynda.com - Graphic Design Tips & Tricks Weekly.7z
Lynda.com - HTML Essential Training.7z
Lynda.com - HTML for Educators.7z
Lynda.com - HTML Structured Data - Facebook Open Graph.7z
Lynda.com - Illustrator CC 2018 Essential Training.7z
Lynda.com - Instagram for Business.7z
Lynda.com - International SEO.7z
Lynda.com - Lead Generation Foundations.7z
Lynda.com - Learning Content Marketing.7z
Lynda.com - Learning Documentary Video - 3 Editing and Post.7z
Lynda.com - Learning Email Marketing.7z
Lynda.com - Learning Maschine 2.7z
Lynda.com - Learning React Native.7z
Lynda.com - Learning React.js (2016).7z
Lynda.com - Learning Songwriting - Ableton Live.7z
Lynda.com - Learning Songwriting - Logic Pro.7z
Lynda.com - Learning Songwriting - Pro Tools.7z
Lynda.com - Learning Synth Programming.7z
Lynda.com - Learning Synth Programming - Beyond the Basics.7z
Lynda.com - Learning to Write Marketing Copy.7z
Lynda.com - Learning ZBrushCore.7z
Lynda.com - Local SEO.7z
Lynda.com - XML Essential Training.7z
Lynda.com - ZBrush 4R8 New Features.7z
Lynda.com - AutoCAD 2018 Essential Training.tgz
Lynda.com - Excel 2016 - Avoiding Common Mistakes.7z
Lynda.com - Google Sites Essential Training.7z
Lynda.com - Kotlin for Java Developers.7z
Lynda.com - Learning JIRA Service Desk.7z
Lynda.com - Visual Studio Essential Training - 00 Setup and Configuration.7z
Lynda.com - Visual Studio Essential Training - 01 Exploring the Visual Studio Ecosystem.7z
Lynda.com - Visual Studio Essential Training - 02 Getting Comfortable with the IDE.7z
Lynda.com - Visual Studio Essential Training - 03 Exploring Projects and Solutions.7z
Lynda.com - Visual Studio Essential Training - 05 Code Editors.7z
Lynda.com - Visual Studio Essential Training - 09 Unit Tests.7z
Lynda.com - 20 Unofficial Rules of Songwriting.7z
Lynda.com - Ableton Live - Producing Electronic Music.7z
Lynda.com - Ableton Live 9 Essential Training.7z
Lynda.com - Advanced EDM Mixing.7z
Lynda.com - After Effects Scripts & Tips - 1 Animation Techniques.7z
Lynda.com - Amazon Web Services - Analysis.7z
Lynda.com - Amazon Web Services - Enterprise Security.7z
Lynda.com - Amazon Web Services - High Availability.7z
Lynda.com - Amazon Web Services - Monitoring and Metrics.7z
Lynda.com - Amazon Web Services - Networking.7z
Lynda.com - Amazon Web Services - Storage and Data Management.7z
Lynda.com - An Insider's Guide to Today's Music Biz - 1 The Big Picture.7z
Lynda.com - An Insider's Guide to Today's Music Biz - 2 Making Great Music.7z
Lynda.com - An Insider's Guide to Today's Music Biz - 3 Treating Your Career as a Business.7z
Lynda.com - An Insider's Guide to Today's Music Biz - 4 Building a Professional Team.7z
Lynda.com - An Insider's Guide to Today's Music Biz - 6 Marketing and Promotion.7z
Lynda.com - Android App Development Quick Start.7z
Lynda.com - Android Development Essential Training - Local Data Storage.7z
Lynda.com - Android Essential Training.7z
Lynda.com - Android Tips and Tricks.7z
Lynda.com - AutoCAD - Express Tools Workflow.7z
Lynda.com - AutoCAD 2018 Essential Training.7z
Lynda.com - AutoCAD 2018 New Features.7z
Lynda.com - Balancing Work and Life.7z
Lynda.com - Building an In-House Photo Studio.7z
Lynda.com - Business Foundations.7z
Lynda.com - Business Storytelling with C.C. Chapman.7z
Lynda.com - C Essential Training.7z
Lynda.com - C# Essential Training - 1 Syntax and Object Oriented Programming.7z
Lynda.com - Career Clinic - Developer Insights.7z
Lynda.com - Cert Prep - AWS Certified SysOps Administrator.7z
Lynda.com - Code Clinic - C.7z
Lynda.com - Content Marketing - Videos.7z
Lynda.com - Creating a Business Plan.7z
Lynda.com - Creating Your First Android App with Kotlin.7z
Lynda.com - Design the Web - HTML Background Video.7z
Lynda.com - Effective Listening.7z
Lynda.com - Excel Statistics Essential Training - 1.7z
Lynda.com - Excel Statistics Essential Training - 2.7z
Lynda.com - Facebook Marketing - Advanced Advertising.7z
Lynda.com - Facebook Marketing - Advertising.7z
Lynda.com - Photoshop CC 2018 Essential Training - The Basics.7z
Lynda.com - Premiere Pro CC 2017 Essential Training - The Basics.7z
Lynda.com - Remixing a Song in Logic Pro.7z
Lynda.com - Remixing Techniques - Arranging and Song Form.7z
Lynda.com - Remixing Techniques - Time Stretching.7z
Lynda.com - Rigging a Cartoon Character in Maya.7z
Lynda.com - SOLIDWORKS - Importing Geometry From Other Applications.7z
Lynda.com - SOLIDWORKS - Simulation for Finite Element Analysis.7z
Lynda.com - SOLIDWORKS 2016 Essential Training.7z
Lynda.com - Starting a Business with Family and Friends.7z
Lynda.com - Statistics Foundations - 1.7z
Lynda.com - Swift 4 - Protocol-Oriented Programming.7z
Lynda.com - Tableau 10 Essential Training.7z
Lynda.com - The Data Science of Marketing.7z
Lynda.com - VFX Keying - Master Course.7z
Lynda.com - Video Green Screen Workflows.7z
Lynda.com - Writing - The Craft of Story.7z
Lynda.com - Writing Ad Copy.7z
Lynda.com - Marketing Foundations - Growth Hacking.7z
Lynda.com - Mastering Puppet for Large Infrastructures.7z
Lynda.com - Maya - Advanced Modeling.7z
Lynda.com - Maya - Rendering with Arnold 5.7z
Lynda.com - Maya 2018 - Bifröst Fluids.7z
Lynda.com - Maya 2018 Essential Training.7z
Lynda.com - Microsoft Azure - Active Directory.7z
Lynda.com - Migrating from Final Cut Pro 7 to Premiere Pro CC.7z
Lynda.com - Migrating from Lightroom Classic CC.7z
Lynda.com - Motion 5 Essential Training.7z
Lynda.com - Motion Graphic Design - Composition.7z
Lynda.com - Motion Graphic Design - Project Planning and Development.7z
Lynda.com - Music Theory for Songwriters - Harmony.7z
Lynda.com - Music Theory for Songwriters - The Fundamentals.7z
Lynda.com - Nikon D800 Essential Training.7z
Lynda.com - Nuke Essential Training.7z
Lynda.com - Online Marketing Foundations.7z
Lynda.com - Pitching Projects and Products to Executives.7z
Lynda.com - PowerShell 5 Essential Training.7z
Lynda.com - Premiere Pro CC 2017 New Features.7z
Lynda.com - Premiere Pro CC 2018 New Features.7z
Lynda.com - Premiere Pro Guru - Closed & Open Caption Workflows.7z
Lynda.com - Premiere Pro Guru - Dynamic Link and the Adobe Workflow.7z
Lynda.com - Premiere Pro Guru - Fixing Video Exposure Problems.7z
Lynda.com - Premiere Pro Guru - Speed Changes.7z
Lynda.com - Premiere Pro Guru - Working with Audio.7z
Lynda.com - Prezi Essential Training.7z
Lynda.com - Programming for Non-Programmers - iOS 11 and Swift.7z
Lynda.com - Programming Foundations - Databases.7z
Lynda.com - Public Speaking Foundations.7z
Lynda.com - Salesforce for Customer Service.7z
Lynda.com - SEO - Link Building in Depth.7z
Lynda.com - SEO - Videos.7z
Lynda.com - Setting Up Your Small Business as a Legal Entity.7z
Lynda.com - SharePoint 2016 - Installation and Configuration.7z
Lynda.com - Social Media Marketing - Managing Online Communities.7z
Lynda.com - Social Media Marketing - Optimization.7z
Lynda.com - Social Media Promotion for Musicians, Artists, and Engineers.7z
Lynda.com - Twitter Marketing - Advertising.7z
Lynda.com - Unity 5 - 3D Essential Training.7z
Lynda.com - Unreal Essential Training.7z
Lynda.com - UX Foundations - Content Strategy.7z
Lynda.com - Working with Actors & Non-Actors in Video Production.7z
Lynda.com - Write Think and Act Like a Professional Songwriter.7z
Life Loaded - Abundance Program
Love Systems
Love Systems - Beyond Words
Love Systems - Charisma Decoded
Love Systems - Gentleman's Guide To Online Dating
Love Systems - Love Systems Ebooks
Love Systems - Love Systems Interview Series 01-70
Love Systems - Relationship Management
Lukas Resheske - Copywriting Mentorship Program
Magic Leone - How to talk to Women (2017)
Manish Leone - Silent Seduction
Margaret Atwood - Masterclass on Writing
Mark Cunningham
Mark Cunningham - Beyond Seduction
Mark Cunningham - Building A Better Girlfriend
Mark Cunningham - Hypnotic Awakenings
Mark Hyman - Broken Brain Docu-series
Mark Manson
Mark Manson - Approach Women Program
Mark Manson - Connection Program
Mark Manson - Dating & Relationship Course
Mark Manson - Daygame Model
Mark Manson - Fearless Dating
Mark Manson - Masculine Power Now
Mark Manson - Models
Mark Manson - Overcome Anxiety
Mark Manson - Sexual Confidence Program
Mark Manson - The Nerds Guide to Being Confident
Mark Manson - The Newbie Guide
Mark Manson - The Subtle Art of Not Giving a Fuck
Matt Artisan - PickUpArtist Academy Course
Matt Evans - Apples Of Eden
Maxwell Maltz - Psycho-Cybernetics
Mehow - Infield Exposed!
Mel Robbins - The 5 Second Rule (Audiobook)
Melanie Evans - Narcissistic Abuse Recovery Program
Michael Breen
Michael Breen - Advanced Language Patterns
Michael Breen - Conversational Trance
Michael Breen - Habit Hacking
Michael Pilinski
Michael Pilinski - She's Yours For The Taking.pdf
Michael Pilinski - Without Embarassment.pdf
Michael Spencer - Monster Confidence System
Mike Haines - The Domination Principle
Mike Koenigs
Mike Koenigs - Consult and Profit (2016)
Mike Koenigs - GoLive and Profit
Mike Wright - Elixir of Eros
Mindvalley
Mindvalley - Become Limitless
Mindvalley - Quantum Jumping
MozCon 2016 Videos (11Gb)
Mira Nair - Masterclass on Independent Filmmaking
Mr. X - Lost Tapes
Mystery
Mystery - Mystery Method - The Venusian Arts Handbook
Mystery - The Mystery Method - How to Get Beautiful Women Into Bed.pdf
Mystery - Venusian Arts - Revelation.pdf
Natural Lifestyle - Natural Lifestyles Podcast
Neil Patel
Neil Patel - Advanced Consulting Program
Neil Patel - Advanced Marketing Program
Neil Strauss
Neil Strauss - Emergency
Neil Strauss - The Game
Neil Strauss - The Truth - An Uncomfortable Book About Relationships
Neil Strauss - The StyleLife Challenge.pdf
New Alpha Education - The Huge Load Formula
Niche Authority Empire - Local Profit Breakthrough Bonus
Nick Krauser - Day Game Mastery
Paul Janka
Paul Janka - Closing.pdf
Paul Janka - Janka Method.pdf
Paul Janka - Text Game.pdf
Peter Diamandis - Xponential Advantage
Peter Parks - DNA Wealth Blueprint 2.0
Pickup 101
Pickup 101 - Body Language
Pickup 101 - Charismatic Conversations
Pickup 101 - Spy Cam
Pick Up Artist PUA Forums (2008)
Pick Up Artist PUA Training
Pick Up Artist PUA - Texts That Guarantee Sex
Pick Up Artist PUA - MPUA University
Pick Up Artist PUA - Stealth Attraction
Rachel Rofe - The Low Hanging System
Ramit Sethi
Ramit Sethi - How To Talk To Anybody
Ramit Sethi - Mental Mastery
Ramit Sethi - Zero to Launch
Reboot Blueprint - Overcome Porn-induced ED
Rob Wiser - M.A.C.K. Tactics
Robin Sharma
Robin Sharma - Personal Mastery Academy
Robin Sharma - Your Absolute Best Year Yet
Roger Love
Roger Love - Set Your Voice Free
Roger Love - The Perfect Voice
Roger Love - Vocal Power
Rollo Tomassi - The Rational Male
Roosh V
Roosh V - Bang - More Lays in 60 Days
Roosh V - Day Bang - How to Casually Pick up Girls During the Day
Ross Jeffries
Ross Jeffries - How To Get The Women You Desire Into Bed
Ross Jeffries - How To Lay Girls
Ross Jeffries - LA99 Speed Seduction
Ross Jeffries - Nail Your Inner Game
Ross Jeffries - Secrets Of Speed Seduction
Ross Jeffries - Transcript
RSD - Real Social Dynamics (coaches: Alex, Brad, Glenn, Jeffy, Julien, Luke, Madison, Max, Ozzie, Papa, Tim, Tyler)
Ryan Deiss
Ryan Deiss - Content & Commerce Summit 2016
Ryan Deiss - Content Marketing Mastery
Ryan Deiss - Market Research Blueprint
Ryan Deiss - The Launch Grid
Ryan Deiss - Traffic & Conversion Summit 2016
Ryan Deiss - Traffic & Conversion Summit 2017
Ryan Magin
Ryan Magin - Bad Boy Unleashed
Ryan Magin - Handsome Guy Secrets
Sam Ovens - The Consulting Blueprint
Sasha Daygame
Sasha Daygame - Direct Dating Summit Berlin
Sasha Daygame - Sasha Daygame Podcast
Sasha Daygame - Unbreakable Rules
Sasha Daygame - Quick Top Tips AA Annihilation Exercises.pdf
Sasha Daygame - Live In Stuttgart.mp3
Sasha Daygame - The Direct Daygame Bible.pdf
School of Squirt - Squirting Triggers 2.0
Scott H Young
Scott H Young - Learn More, Study Less
Scott H Young - Rapid Learner Course
Shae Matthews
Shae Matthews - Meditations
Shae Matthews - Sensual Massage Mastery
Simple Pickup
Simple Pickup - About
Simple Pickup - Drunk Times With Hot Girls
Simple Pickup - Jumpcut Academy
Simple Pickup - Jumpcut Academy 2.0
Simple Pickup - Simple Mixology
Simple Pickup - Simple Pickup System
Simple Pickup - Simple Tips. Others
Sixty Years of Challenge
Sixty Years of Challenge - Podcast
Sixty Years of Challenge - Complete Game Revision System
Sixty Years of Challenge - Elite Audio Club
Sixty Years of Challenge - Fast sexual escalation seminar – 60 Years of Challenge
Sixty Years of Challenge - From Social to Seduce Her
Sixty Years of Challenge - Getting a Girlfriend
Sixty Years of Challenge - Hot Girls Talk Sex (Master Her Bedroom)
Sixty Years of Challenge - Magic Mindsets 2014 by 60 Years of Challenge
Sixty Years of Challenge - Making Attraction Official
Sixty Years of Challenge - More Numbers, Less Flakes
Sixty Years of Challenge - Secret Seduction Triggers
Sixty Years of Challenge - Seducers Playbook 2 0 – 60 years of challenge
Sixty Years of Challenge - Text Machine
Sixty Years of Challenge - The 3 Hour Girlfriend Get Keep Her Attracted Forever
Sixty Years of Challenge - The Friend Bomb Formula (2014)
Sixty Years of Challenge - The Girlfriend Formula
Spencer Michaels - Monster Confidence System
SquattinCassanova - Instaconnection
Steve G. Jones
Steve G. Jones - Hypnotic Pick Up Method
Steve G. Jones - Ultimate Conversational Hypnosis
Steve G. Jones - Ultimate Conversational Hypnosis (Advanced)
Steve Jabba - The Secret Society
Steven Peliari - The Art of Covert Hypnosis
Street Attraction
Street Attraction - Approach 2 Lay
Street Attraction - Ebooks
Street Attraction - Street-Attraction - VIP Section SD
Subcommunication Mastery - Primal Attraction Activation System
SwinggCat - Real World Seduction
Spike Lee - Masterclass on Independent Filmmaking
Steve Martin - Comedy
Sybervision
Sybervision - The Neuropsychology of Achievement
Sybervision - The Neuropsychology of Leadership
Sybervision - The Neuropsychology of Self-Discipline
Tai Lopez
Tai Lopez - 67 steps
Tai Lopez - Accelerator
Tai Lopez - Entrepreneur Starter Kit
Tai Lopez - Lifestyle Training
Tai Lopez - MentorBox
Tai Lopez - Real Estate
Tai Lopez - Social Media Marketing Agency
Tai Lopez - Traveling CEO
Talmadge Harper
Talmadge Harper - Art of Manifesting
Talmadge Harper - Free From Fear - Free From Anxiety 2.0
Talmadge Harper - Sophia
Talmadge Harper - Subliminal Alpha Protocol 3
Talmadge Harper - Take Action - Take Control Of Your Life
Talmadge Harper - The Elemental
Tanner Fox - Affiliate Marketing Mastery
The 21 Convention (2007-2014 + Bonuses)
The 4 Week Natural - Daygame Phonegame
The Art of Verbal War
The Art of Verbal War - Master of Metaphor
The Art of Verbal War - On
The Art of Verbal War - People Games
The Art of Verbal War - The Hank Moody Guide to Wit
The Art of Verbal War - The Harvey Specter Guide
The Art of Verbal War - The High Value Man
The Art of Verbal War - The King's Mindset
The Art of Verbal War - The NEW Art of Being Right
The Art of Verbal War - Verbal Domination
The Art of Verbal War - Verbal Self Defense 101
The Art of Verbal War - Vocal Superstar
The Modern Man - The Ultimate Guide to Conversation
The Psychology Of Performance - How to Be Your Best in Life
The Social Man - Unbreakable
Timothy Marc
Timothy Marc - Art of Manifesting
Timothy Marc - Free From Fear - Free From Anxiety 2.0
Timothy Marc - Sophia
Timothy Marc - Subliminal Alpha Protocol 3
Timothy Marc - Take Action - Take Control Of Your Life
Timothy Marc - The Elemental
Thomas Keller - Masterclass on Meat, Stocks and Sauces
Tom Torero
Tom Torero - Badass Buddha
Tom Torero - Street Hustle
Tom Torero - Tom Torero Podcasts
Todd Valentine
Todd Valentine - 3 Girls A Day
Todd Valentine - Attraction Unlocked
Todd Valentine - Daygame
Todd Valentine - RSD Todd YouTube Channel
Todd Valentine - Text & Dates Machine
Todd Valentine - The Art Of Game
Todd Valentine - Todd Valentine Infield Collection
Todd Valentine - Valentine University 2.0
Todd Valentine - Winnergame
Todd Valentine - Women
Tom Morello - Masterclass on Electric Guitar
Tony Ruca - The Alpha System
Transmutation Club - Mastering the Power of Sex Energy Transmutation
Two Girls Teach Sex
Two Girls Teach Sex - 2 Girls Teach Sex 2.0
Two Girls Teach Sex - 60 Minute Stamina
Two Girls Teach Sex - Advanced Sex Techniques For Guaranteed Orgasms
Two Girls Teach Sex - Blow Her Mind The First Time
Two Girls Teach Sex - Extreme Female Orgasms
Two Girls Teach Sex - Forbidden Sex Secrets
Two Girls Teach Sex - Multiple Orgasm Methods
Two Girls Teach Sex - Oral Sex Magic
Two Girls Teach Sex - Orgasm Of The Month
Two Girls Teach Sex - Rear Entry Made Easy
Two Girls Teach Sex - Secrets of Squirting Orgasms
Two Girls Teach Sex - Sex Positions for Orgasm and Excitement
Two Girls Teach Sex - Shawna's Porn Star Sex Secrets
Two Girls Teach Sex - Squirting Orgasm Mastery
Two Girls Teach Sex - Superman Stamina
Two Girls Teach Sex - Threesome Code
Two Girls Teach Sex - SecretTraining Manual.pdf
Udemy
Udemy - Alain Wolf Coaching:
Alain Wolf - COMMUNICATION SKILLS How To Make A Great First Impresion
Alain Wolf - Develop Amazing Social Skills & Connect With People
Alain Wolf - SOCIAL SKILLS - Double Your Social Skills & Make New Friends (Udemy)
Alain Wolf - Social Skills Decoded
Udemy - Become A Learning Machine
Udemy - Become A Speed Demon:
Hack Automation Focus Efficiency
Productivity Tricks
Udemy - Become a SuperHuman - Naturally & Safely Boost Testosterone
Udemy - Become a SuperLearner V2
Udemy - Become a SuperLearner V2.5
Udemy - Bitcoin & Blockchain
Udemy - Female Guide To Attraction, Getting Ex Back And Dating Men
Udemy - Master Persuasion Psychology And Convince People Of Anything
Udemy - Master Your ADHD Brain Tutorial
Udemy - Master Your Emotions & Revolutionise Your Social Skills
Udemy - Reveal Your Humor Social Life & Communication Skills
Udemy - The Ultimate Intermittent Fasting & Fast Weight Loss Course
Udemy - The Ultimate Morning Routine Guide
Udemy - Essential Poker Math for No Limit HoldEm
Udemy - Learn to Design Your Own Boards
Udemy - MATLAB for the Absolute Beginner
Udemy - Python for Financial Analysis and Algorithmic Trading
Udemy - Tableau Expert Top Visualization Techniques in Tableau 10
Udemy - The Complete Financial Analyst Training & Investing Course
Udemy - Complete Guide to Tensorflow for Deep Learning with Python
Udemy - Python for Data Science and Machine Learning Bootcamp
Udemy - Mastering Microcontroller with Embedded Driver Development
Udemy - Master Electron v5 Desktop Apps with HTML, JavaScript & CSS
Udemy - The Complete Networking Fundamentals Course. Your CCNA start
Udemy - The Complete Wireshark Course. Go from Beginner to Advanced!
Udemy - Angular 7 Security Masterclass (with FREE E-Book).zip
Udemy - Build Incredible Chatbots - Learntpoint.com.zip
Udemy - Cisco Meraki Wireless setup from scratch.zip
Udemy - JavaScript Beginner Bootcamp (2019).zip
Udemy - NgRx In Depth (Angular 7 and NgRx 7, with FREE E-Book) - Learntpoint.com.zip
Udemy - PHP for Beginners - Become a PHP Master - CMS Project - Learntpoint.com.zip
Udemy - PSD to Responsive HTML5 Beginner to Advanced - Learntpoint.com.zip
Udemy - Python for Absolute Beginners.zip
Udemy - Python for Beginners with Examples.zip
Udemy - React - The Complete Guide (incl Hooks, React Router, Redux).zip
Udemy - SQL for Newbs Data Analysis for Beginners - Learntpoint.com.zip
Udemy - The Complete Android N Developer Course - Learntpoint.com.zip
Udemy - The Complete Java Developer Course Beginner To Expert - Learntpoint.com.zip
Udemy - The Complete Web Developer Course 2.0.zip
Udemy - The Python Mega Course - Build 10 Real World Applications.zip
Udemy - Web Design with WordPress Everything from Beginning to End - Learntpoint.com.zip
Udemy - Mastering Microcontroller with Embedded Driver Development
Udemy - The Complete Ethical Hacking Course (6.8 GB).zip
Valentino Kohen - Invisible Game
Vanessa Ed Edwards - The Power of Negotiation
Vick Strizheus - High Traffic Academy 2.0
Vin DiCarlo - Pandoras Box
Wendi Friesen - Breakfree End Porn Addiction
William Cane - The Art of Kissing
Xtreme Mind - Psychic Seduction Masterclass
Zack Browman - High Status Humor
#selfmade#selfmade entrepreneur motivation love fitness nyc hustle atlanta la hot97 datpiff statenisland playlist topspot theintro o2trillo2real numbe#motivation#love#fitness#nyc#hustle#atlanta#la#hot97#datpiff#statenisland#playlist#topspot#theintro#o2trillo2real#numberonecontender#uglyfollowtrain#inspiration#business#o2amazin#art#grind#brooklyn#music#power105#money#selfemployed
0 notes
Link
Recomended Products

The Expression ET-2750 EcoTank wireless all-in-one offers revolutionary cartridge-free printing with easy-to-fill, supersized ink tanks. It includes up to 2 years of ink in the box (1). That’s an incredible amount of ink — enough to print up to 5,200 pages (2), and equivalent to about 30 ink cartridge sets (3). Plus, it features auto-stop ink bottles with each color uniquely keyed for easy filling of each tank. And, you save up to 80 percent on ink with low-cost replacement bottles (4). The ET-2750 also offers convenient wireless printing from tablets and smartphones (5), plus Wi-Fi Direct (6) and auto 2-sided printing. Operating Systems: Windows 10, Windows 8, 8.1 (32-bit, 64-bit), Windows 7 (32-bit, 64-bit), Mac OS X 10.6 – macOS 10.12.x10
1. Based on average monthly print volumes of about 150 pages. 2. Included ink bottle yields based on the ISO/IEC 24712 pattern with Epson’s methodology. Actual ink yields will vary considerably for reasons including images printed, print settings, temperature and humidity. Yields may be lower when printing infrequently or predominantly with one ink color. All ink colors are used for printing and printer maintenance, and all colors must be available for printing. For more information, visit our official site. 3. Equivalent cartridge sets estimate based on print yields of the included Black and color ink bottles as compared to Epson standard-capacity ink cartridge sets for similarly featured cartridge printers as of March 2017. 4. Savings comparison based on the purchase cost of replacement ink bottles and the cost of enough cartridges to achieve the total page yields of the bottles using the manufacturers’ online prices and yields for the highest-capacity cartridges for the best-selling, similarly featured consumer inkjet printers priced at $499 or less per NPD, July 2016. Actual savings will vary based on print tasks, print volumes and usage conditions. 5. Most features require an Internet connection to the printer, as well as an Internet- and/or email-enabled device. For a list of Epson Connect enabled printers and compatible devices and apps, visit our official site. 6. Wi-Fi CERTIFIED; level of performance subject to the range of the router being used. Wi-Fi Direct may require printer software. 7. Adapter may be required. 8. 12 months of standard limited warranty or 50,000 plain paper sheets (whichever happens first). For an additional 12 months (total of 24 months or 50,000 plain paper sheets, whichever happens first), register your product and use Epson genuine ink bottles. See Limited Warranty for details. 9. ET-2500/2550/2600/2650/2700/2750/3600/3700/3750/4500/4550/4750/16500 included ink bottle yields based on the ISO/IEC 24712 pattern with Epson’s methodology. ET-7700/7750 included ink bottle photo yields are significantly lower and are based on the ISO/IEC 29103 pattern with Epson’s methodology. WF-R4640 included ink pack yields are estimated based on ISO/IEC 24711 test in Default Mode printing continuously. Actual ink yields will vary considerably for reasons including images printed, print settings, temperature and humidity. Yields may be lower when printing infrequently or predominantly with one ink color. All ink colors are used for printing and printer maintenance, and all colors must be available for printing. For more information, visit our official site. 10. Based on average monthly document print volumes of about 150 pages (ET-2500, ET-2550, ET-2600, ET-2650, ET-2700, ET-2750, ET-4500), 300 pages (ET-3600, ET-3700, ET-3750, ET-4550, ET-4750, ET-7700, ET-7750, ET-16500), and 800 pages (WF-R4640). 11. For convenient and reasonable recycling options, visit our official site. 12. SmartWay is an innovative partnership of the U.S. Environmental Protection Agency that reduces greenhouse gases and other air pollutants and improves fuel efficiency. Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Save up to 80 percent on ink with low-cost replacement bottles (4) – plus easy-to-fill, supersized ink tanks Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Save up to 80 percent on ink with low-cost replacement bottles (4) – plus easy-to-fill, supersized ink tanks Easy wireless – easily print from iPad, iPhone, Android tablets and smartphones (5); includes Wi-Fi Direct (6) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Save up to 80 percent on ink with low-cost replacement bottles (4) – plus easy-to-fill, supersized ink tanks Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Save up to 80 percent on ink with low-cost replacement bottles (4) – plus easy-to-fill, supersized ink tanks Easy wireless – easily print from iPad, iPhone, Android tablets and smartphones (5); includes Wi-Fi Direct (6) Auto 2-sided printing – save up to 50 percent of your paper supply.Maximum Print Resolution: 5760 x 1440 optimized dpi Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Save up to 80 percent on ink with low-cost replacement bottles (4) – plus easy-to-fill, supersized ink tanks Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Save up to 80 percent on ink with low-cost replacement bottles (4) – plus easy-to-fill, supersized ink tanks Easy wireless – easily print from iPad, iPhone, Android tablets and smartphones (5); includes Wi-Fi Direct (6) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Save up to 80 percent on ink with low-cost replacement bottles (4) – plus easy-to-fill, supersized ink tanks Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Cartridge-free printing – comes with up to 2 years of ink in the box (1) Includes enough ink to print up to 6,500 pages black/5,200 color (2) – equivalent to about 30 ink cartridge sets (3) Save up to 80 percent on ink with low-cost replacement bottles (4) – plus easy-to-fill, supersized ink tanks Easy wireless – easily print from iPad, iPhone, Android tablets and smartphones (5); includes Wi-Fi Direct (6) Auto 2-sided printing – save up to 50 percent of your paper supply.Maximum Print Resolution: 5760 x 1440 optimized dpi RoHS compliant
0 notes
Photo

ENCRYPTED WIFI MEANING,ENCRYPTED WIFI PASSWORD,ENCRYPTED WIFI CAMERA,ENCRYPTED WIFI CONNECTION,ENCRYPTED WIFI ROUTER,ENCRYPTED WIFI SECURITY CAMERA,ENCRYPTED WIFI BABY MONITOR,ENCRYPTED WIFI WITHOUT PASSWORD,SECURE WIFI APP,SECURE WIFI ANDROID,SECURE WIFI AT HOME,SECURE WIFI AT AIRPORT,WIFI ENCRYPTION AES OR TKIP,ENCRYPTION AND WIFI,WI-FI PROTECTED ACCESS,SECURE A WIFI NETWORK,SECwww.eurovpn.euRE A WIFI CONNECTION,ENCRYPTION WIFI AES,A SECURE WIFI CONNECTION,ENCRYPTED THE WIFI,SECURED WIFI BUT NO INTERNET,WIFI ENCRYPTION BEST,SECURED WIFI BIGLOBE,SECURE WIFI BOOSTER,SECURE WIFI BRIDGE,SECURE WIFI BRIDGE MODE,WIFI ENCRYPTION BROKEN,WIFI ENCRYPTION BUG,WIFI ENCRYPTION BREAKER,SECURE WIFI CONNECTION,SECURE WIFI CAMERAS,SECURED WIFI CONNECT,WIFI ENCRYPTION CCMP,WIFI SECURED CAN'T CONNECT TO THIS NETWORK,WIFI SECURE CODE,WIFI SECURE CONNECT,ENCRYPTION WIFI CHECK,ENCRYPTION WIFI DATA,SECURE WIFI DIRECT,SECURE WIFI DEVICE,SECURED WIFI DEFINITION,SECURE WIFI DONGLE,WIFI ENCRYPTION DEFINITION,WIFI ENCRYPTION DECRYPT,WIFI ENCRYPTION DISABLED,WIFI SECURED DI WINDOWS 10,METHODE D'ENCRYPTION WIFI,TYPE DES ENCRYPTION WIFI,SECURE WIFI EXTENDER,SECURE WIFI FREE,ENCRYPTION FOR WIFI,SECURE WIFI FROM HACKERS,SECURE WIFI FOR BUSINESS,SECURE WIFI FOR RV,SECURE WIFI FOR TRAVEL,SECURE WIFI FORTINET,SECURE WIFI FOR LAPTOP,ENCRYPTION FOR WIFI ROUTER,WIFI ENCRYPTION FLAW,F SECURE WIFI,F-SECURE WIFI ROUTER,F-SECURE WIFI EXPERIMENT,F SECURE WIFI CHECKER,SECURE WIFI GALAXY S9,ENCRYPTED GUEST WIFI,SECURE WIFI GALAXY S8,SECURE WIFI GALAXY S10,SECURE WIFI GOOGLE,SECURE WIFI GUEST,WIFI ENCRYPTION GCSE,ENCRYPT GOOGLE WIFI,SECURE GUEST WIFI ACCESS,SECURE GUEST WIFI UNIFI,SECURE WIFI HAS STOPPED,SECURED WIFI HACK,SECURE WIFI HOME,SECURE WIFI HOW,WIFI ENCRYPTION HOW IT WORKS,SECURE WIFI HOTSPOT,SECURED WIFI HACKER APK,SECURE WIFI HACK,SECURED WIFI HACKER,SECURE WIFI IN PUBLIC,SECURE WIFI IN SAMSUNG,ENCRYPTION IN WIFI,ENCRYPTED WIFI WHAT IS,SECURE WIFI IPHONE,SECURE WIFI IN HOTEL,ENCRYPTION WIFI KEY,SECURE WIFI KUTZTOWN,SECURE WIFI KEY,WIFI ENCRYPTION KEY FINDER,WIFI ENCRYPTION KEY HACK,ENCRYPTION KEY WIFI PANASONIC,WIFI ENCRYPTION KEY LENGTH,WIFI ENCRYPTION KEYS,WI FI ENCRYPTION KEY,ENCRYPTION KEY WIFI WEP,SECURE WIFI LOCATIONS,SECURE WIFI LOGIN,SECURE WIFI LÀ GÌ,SECURE WIFI LINKSYS,SECURE WIFI LAX,SECURE WIFI LAPTOP,WIFI ENCRYPTION LEVELS,WIFI ENCRYPTION LAYER 2,SECURE LINK WIFI,SECURE WIFI MCAFEE,ENCRYPTION MODE WIFI,WIFI ENCRYPTION METHODS,WIFI ENCRYPTION METHOD,WI-FI PROTECTED MANAGEMENT FRAMES,SECURE MY WIFI,WI-FI PROTECTED MODE,SECURE MY WIFI ROUTER,ENCRYPTED WIFI NETWORK,ENCRYPT WIFI NETWORK,SECURE WIFI NETWORK,SECURE WIFI NOTE 8,SECURE WIFI NETWORKS,SECURE WIFI NET,SECURE WIFI NOTE 9,SECURED WIFI NO INTERNET,SECURE NET WIFI VODAFONE,WIFI SECURED NOT CONNECTED,SECURE WIFI ON ANDROID,SECURE WIFI ON SAMSUNG,ENCRYPTION ON WIFI,ENCRYPT ON WIFI,SECURE OPEN WIFI,SECURED WIFI OCN,SECURE WIFI ON IPHONE,SECURE WIFI ON MAC,WIFI ENCRYPTION OPEN,SECURE OPEN WIFI NETWORK,ENCRYPT WIFI PASSWORD,ENCRYPTION WIFI PASSWORD,SECURE WIFI PASSWORD,SECURE WIFI PUBLIC,SECURE WIFI PRINTING,SECURE PUBLIC WIFI CONNECTION,ENCRYPT WIFI PASSWORD WINDOWS 7,ENCRYPTED PUBLIC WIFI,SECURE WIFI ROUTER,SECURE WIFI ROUTER TP LINK,WIFI ENCRYPTION RISK,SECURE WIFI ROUTER FOR HOME,SECURE WIFI REPEATER,SECURE WIFI ROUTER CONFIGURATION,SECURE WIFI ROUTER SETTINGS,SECURE WIFI ROUTER PASSWORD,PROTECTED WIFI ROUTERS,SECURE WIFI SAMSUNG,SECURE WIFI SAMSUNG S9,WIFI ENCRYPTION STANDARDS,WI-FI PROTECTED SETUP,WI-FI PROTECTED SETUP (WPS),WI-FI PROTECTED SETUP PBC METHOD,WIFI PROTECTED SETUP (WPS) SFR,WIFI PROTECTED SETUP DOWNLOAD,WIFI PROTECTED SETUP LINKSYS,S SECURE WIFI,ENCRYPT WIFI TRAFFIC,ENCRYPTION WIFI TYPE,WIFI ENCRYPTION TYPES,WIFI ENCRYPTION TKIP OR AES,SECURE THE WIFI CONNECTION,SECURED TO WIFI BUT NO INTERNET,SECURE THE WIFI ROUTER,WIFI SECURED TO,SECURE WIFI THERMOSTAT,T SECURE WIFI,T WIFI SECURE ZONE,T WIFI SECURE 노트북,T WIFI SECURE 접속 방법,T WIFI SECURE 비밀번호,ENCRYPTED VS UNENCRYPTED WIFI,SECURE WIFI UFFICI PUBBLICI MILANO,SECURED WIFI U-MOBILE,SECURE WIFI UFFICI PUBBLICI,SECURE WIFI UFFICI PUBBLICI MILANO LOGOUT,SECURE WIFI UBUNTU,ENCRYPTION USES WIFI,SECURE UNIL WIFI,SECURE UD WIFI,UNL ENCRYPTED WIFI,SECURE WIFI VPN,SECURE WIFI VODAFONE,SECURE WIFI VERIZON,SECURE WIFI VIDEO BABY MONITOR,WIFI ENCRYPTION VULNERABILITY,WIFI ENCRYPTION VS SPEED,ENCRYPTION VS WIFI,SECURE VPN & WIFI PROTECTION,SECURE VPN WIFI PROXY,SECURE WIFI WITH PASSWORD,ENCRYPTION WITH WIFI,SECURED WIFI WINDOWS 10,SECURE WIFI WHILE TRAVELING,SECURE WIFI WATCHGUARD,SECURE WIFI WITH VPN,SECURE WIFI WMU,PROTECTED WIFI WITH PASSWORD,SECURE WIFI XFINITY,SECURE XFINITY WIFI HOTSPOTS,SECURE XFINITY WIFI PROFILE,XFINITY SECURE WIFI,ENCRYPT YOUR WIFI,SECURE YOUR WIFI,SECURE YOUR WIFI NETWORK,SECURE YOUR WIFI ROUTER,SECURE YOUR WIFI NETWORK HOME,ENCRYPT YOUR WIFI CONNECTION,SECURE YOUR WIFI CONNECTION,SECURE WIFI 2017,WIFI ENCRYPTION 2018,LAYER 2 ENCRYPTION WIFI,SECURE 360 WIFI,SECURE WIFI 802.1X,WIFI ENCRYPTION 802.1X,ENCRYPTED ROUTER PRICE,ENCRYPTED ROUTER TRAFFIC,ENCRYPTED ROUTER PASSWORDS,ROUTEROS ENCRYPTED DNS,ROUTER ENCRYPTED DNS,BEST ENCRYPTED ROUTER,ENCRYPTED VPN ROUTER,ENCRYPT HOME ROUTER,ENCRYPTED INTERNET ROUTER,ENCRYPTED WIFI ROUTER,ROUTER ENCRYPTION AES,ROUTER ENCRYPTION AES OR TKIP,ENCRYPTION ALGORITHMS ROUTER,ENCRYPTION ARRIS ROUTER,ENCRYPTED DNS ASUS ROUTER,HOW TO ENCRYPTED A ROUTER,ROUTER ENCRYPTION BROKEN,ENCRYPTION CISCO ROUTER,ROUTER ENCRYPTION CODE,ROUTER ENCRYPTION COMMAND,PASSWORD ENCRYPTION ROUTER CISCO,ENCRYPTED DNS ROUTER,ENCRYPTION DLINK ROUTER,ROUTER ENCRYPTION DEVICE,ENCRYPTION FOR ROUTER,ROUTER ENCRYPTION HACK,ENCRYPTION HARDWARE ROUTER,ENCRYPTION IN ROUTER,ROUTER ENCRYPTION ISSUES,ROUTER ENCRYPTION KEY,ENCRYPTION KEY ROUTER LOCATION,ROUTER ENCRYPTION LEVELS,ENCRYPTION LINKSYS ROUTER,ROUTER ENCRYPTION MODE,ROUTER ENCRYPTION METHOD,ROUTER ENCRYPTION MEANING,ROUTER ENCRYPTION NETWORK,ROUTER NOT ENCRYPTED,ENCRYPTION ON ROUTER,ENCRYPTION ROUTER PASSWORD,ENCRYPTION ROUTER PROBLEM,CISCO ROUTER ENCRYPTED PASSWORD,ROUTER ENCRYPTION SECURITY,ROUTER ENCRYPTION SETTINGS,ROUTER ENCRYPTION SCHEME,ROUTER ENCRYPTION TYPES,ENCRYPTION TO ROUTER,ENCRYPTION ROUTER TYPE,ROUTER ENCRYPTION TKIP OR AES,ROUTER ENCRYPTION TYPE TKIP OR AES,ROUTER ENCRYPTION TKIP,ROUTER ENCRYPTION VULNERABILITY,ROUTER ENCRYPTION WPA WEP,ROUTER WITH ENCRYPTED DNS,ENCRYPTING YOUR ROUTER,ENCRYPTED WIRELESS KEYBOARD,ENCRYPTED WIRELESS MOUSE,ENCRYPTED WIRELESS MICROPHONE,ENCRYPTED WIRELESS PHONE,ENCRYPTED WIRELESS CAMERA,ENCRYPTED WIRELESS MICS,ENCRYPTED WIRELESS HOME SECURITY SYSTEMS,ENCRYPTED WIRELESS INTERCOM,WIRELESS ENCRYPTION AES,WIRELESS ENCRYPTION A,SECURE A WIRELESS NETWORK,SECURE A WIRELESS ROUTER,SECURE WIRELESS APK,SECURE WIRELESS APP,SECURE WIRELESS ACCESS POINT,SECURE WIRELESS ACCESS POINT FOR BUSINESS,SECURE WIRELESS ALARM SYSTEMS,A WIRELESS ENCRYPTION,WHAT IS A ENCRYPTED WIRELESS KEYBOARD,SECURE A WIRELESS ACCESS POINT,SECURE WIRELESS BRIDGE,SECURE WIRELESS BABY MONITOR,WIRELESS ENCRYPTION BEST PRACTICE,WIRELESS ENCRYPTION BREACH,WIRELESS SECURED BUT NO INTERNET,SECURE BOOT WIRELESS,SECURE BROADBAND WIRELESS,BEST ENCRYPTED WIRELESS KEYBOARD,ENCRYPTED WIRELESS CONNECTION,ENCRYPTED WIRELESS CALLS,ENCRYPTED WIRELESS CARD,SECURE WIRELESS CAMERA,SECURE WIRELESS.COM,WIRELESS ENCRYPTED CCTV,SECURE WIRELESS CAREGIVER ALERT SYSTEM,SECURE WIRELESS CONNECTION,ENCRYPTED WIRELESS DEFINITION,ENCRYPT WIRELESS DATA,WIRELESS ENCRYPTED DIGITAL CAMERA SYSTEM,SECURED WIRELESS DATA COMMUNICATION PROJECT,SECURE WIRELESS DATA TRANSMISSION,SECURED WIRELESS DATA COMMUNICATION,SECURE WIRELESS DOORBELL,SECURE WIRELESS DOOR WINDOW SENSOR,SECURE WIRELESS DSC,SECURE WIRELESS DISPLAY,SECURE ELEVEN WIRELESS,SECURE ENTERPRISE WIRELESS NETWORK,SECURE WIRELESS EV-REC1,SECURE WIRELESS EV-REC1 PROGRAMMING,SECURE WIRELESS EV-REM PROGRAMMING,SECURE WIRELESS EVOLUTION SERIES MANUAL,SECURE WIRELESS EV-DW4975,SECURE WIRELESS EV-REM,SECURE WIRELESS EARBUDS,SECURE WIRELESS EVOLUTION SERIES,ENCRYPTION FOR WIRELESS KEYBOARD,SECURE FIT WIRELESS SPORT HEADPHONES JBL,ENCRYPTION FOR WIRELESS NETWORKS,WIRELESS ENCRYPTION FAILURE SQUEEZEBOX,WIRELESS ENCRYPTION FAILURE,ENCRYPTION FOR WIRELESS SENSOR NETWORK,SECURE FIT WIRELESS SPORT HEADPHONES,SECURE FIT WIRELESS HEADPHONES,ENCRYPT SANDISK WIRELESS FLASH DRIVE,SECURE WIRELESS GERMANY GMBH,SECURE WIRELESS GMBH,SECURE GUEST WIRELESS,SECURE WIRELESS GERMANY,SECURE WIRELESS HOME ROUTER,SECURE WIRELESS HEADPHONES,SECURE WIRELESS HARD DRIVE,SECURE WIRELESS HDMI,SECURE WIRELESS HOTSPOT,ENCRYPTION IN WIRELESS,SECURE WIRELESS INC,SECURE WIRELESS INTERCOM,SECURE WIRELESS INTERNET,SECURE WIRELESS IP CAMERA,ENCRYPTION IN WIRELESS COMMUNICATION,ENCRYPTION IN WIRELESS NETWORKS,WIRELESS ENCRYPTION IS THE MOST SUSCEPTIBLE TO INTERCEPTION AND DECRYPTION,ENCRYPTED WIRELESS KEY,ENCRYPTION WIRELESS KEYBOARD,SECURE WIRELESS KEYFOB,SECURE WIRELESS KEYFOB MANUAL,SECURE WIRELESS KEY FOBS,ENCRYPTION KEY WIRELESS NETWORK,D'LINK WIRELESS ENCRYPTION KEY,SECURE WIRELESS LAN,SECURE WIRELESS LLC,SECURE WIRELESS LAN ARCHITECTURE,SECURE WIRELESS LAN SOLUTION ARCHITECTURE,SECURE WIRELESS LINK,WIRELESS ENCRYPTION LEVELS,COMMERCIAL ENCRYPTED WIRELESS LINK,SECURE LINKSYS WIRELESS ROUTER,SECURE LINKSYS WIRELESS G 2.4 ROUTER,ENCRYPTED WIRELESS MEANING,SECURE WIRELESS MICROPHONE,ENCRYPTION MODE WIRELESS ROUTER,WIRELESS PROTECTED MANAGEMENT FRAMES,SECURE MY WIRELESS NETWORK,SECURE MY WIRELESS,SECURE WIRELESS MOUSE,ENCRYPTED WIRELESS NETWORK SECURITY,SECURE WIRELESS NETWORK,SECURE WIRELESS NETWORK SETUP,WIRELESS SECURED NO INTERNET,ENCRYPTION TYPE WIRELESS NETWORK,ENCRYPTION WIRELESS NETWORK METHODS,SECURE WIRELESS NETWORKS CAN BE LEGALLY ACCESSED BY ANYONE AND ARE FREQUENTLY POSTED AS SUCH,SECURE WIRELESS NETWORK DESIGN,SECURE WIRELESS NETWORK DESIGN ILLUSTRATION,ENCRYPTION ON WIRELESS,ENCRYPTED ON WIRELESS NETWORK,ENCRYPTION OF WIRELESS COMMUNICATION,WIRELESS ENCRYPTION PROTOCOLS,ENCRYPTION WIRELESS PROTOCOL,ENCRYPTION WIRELESS PASSWORD,SECURE WIRELESS PRINTER,SECURE WIRELESS POWERED AND COOPERATIVE JAMMING D2D COMMUNICATIONS,SECURE WIRELESS PASSWORD GENERATOR,SECURE WIRELESS PHONE,SECURE WIRELESS PAGER,WIRELESS ENCRYPTION QUE SON,WIRELESS ENCRYPTION QUE SIGNIFICA EN ESPAÑOL,WIRELESS ENCRYPTION QUE ES,SECURE WIRELESS ROUTER,SECURE WIRELESS ROUTER FOR HOME,BEST ENCRYPTION WIRELESS ROUTER,SECURE WIRELESS REMOTE NURSE ALERT SYSTEM,SECURE WIRELESS ROUTER 2018,SECURE WIRELESS ROUTER FOR SMALL BUSINESS,SECURE WIRELESS REMOTE EV-REM,SECURE WIRELESS REPEATER,WIRELESS PROTECTED SETUP,WIRELESS PROTECTED SETUP (WPS),SECURE WIRELESS SHOCK SENSOR,SECURE WIRELESS SENSOR NETWORKS PROBLEMS AND SOLUTIONS,SECURE WIRELESS SLIMLINE PAGER,SECURE WIRELESS SW-ATT-GB,SECURE WIRELESS SETTINGS,ENCRYPTED WIRELESS TRANSMISSION,ENCRYPT WIRELESS TRAFFIC,ENCRYPTED TRAFFIC WIRELESS,WIRELESS ENCRYPTION TYPES,WIRELESS ENCRYPTION TYPE,WIRELESS ENCRYPTION TYPE AES OR TKIP,SECURE THE WIRELESS NETWORK,SECURE WIRELESS TRANSMISSION,SECURE WIRELESS TRAVEL ROUTER,SECURE UNSECURED WIRELESS NETWORK,SECURE WIRELESS VIDEO,WIRELESS ENCRYPTION VULNERABILITIES,WIRELESS ENCRYPTION WPA,SECURE WIRELESS WORKS,WIRELESS ENCRYPTION WPA2,WIRELESS ENCRYPTION WPA2-PSK,WIRELESS ENCRYPTION WEP,SECURE XFINITY WIRELESS ROUTER,SECURE YOUR WIRELESS NETWORK,SECURE YOUR WIRELESS ROUTER,SECURE YOUR WIRELESS,SECURE YOUR WIRELESS NETWORK WITH WPA2,SECURE 11 WIRELESS,SECURE 802.11 WIRELESS NETWORK,WLAN ENCRYPTION CCMP,ENCRYPTION FOR WLAN,WLAN ENCRYPTION KEY OFF,WLAN ENCRYPTION KEY,WLAN ENCRYPTION MODE,WLAN ENCRYPTION METHODS,WLAN ENCRYPTION STANDARD,WLAN ENCRYPTION TYPES,WLAN ENCRYPTION TKIP AES,ENCRYPTION TYPE WLAN,SECURE WIFI SAMSUNG,SECURE WIFI NETWORKS,SECURE WIFI S10,SECURE WIFI PASSWORD,SECURE WIFI ROUTER,SECURE WIFI NOTE 9,SECURE WIFI ANDROID,SECURE WIFI NETWORK,SECURE WIFI APP SAMSUNG,SECURE WIFI APK,SECURE WIFI ACCESS POINT,SECURE WIFI APP SPRINT,SECURE WIFI ACCESS,SECURE WIFI AT HOTEL,A SECURE WIFI CONNECTION,SECURE A WIFI NETWORK,CONNECT TO A SECURE WIFI WITHOUT PASSWORD,WHAT IS A SECURE WIFI PASSWORD,SECURE A PUBLIC WIFI CONNECTION,WHAT IS A SECURE WIFI,CONNECT TO A SECURE WIFI,WHAT DOES A SECURE WIFI MEAN,WHAT IS A SECURE WIFI ROUTER,HOW TO CREATE A SECURE WIFI NETWORK,SECURE WIFI BOOSTER,SECURE WIFI BRIDGE,SECURE WIFI BRIDGE MODE,HOW TO SECURE WIFI BY PASSWORD,SECURE BG WIFI,SECURE BOOT WIFI,SECURE BUSINESS WIFI,B-LINK SECURE CELLULAR WIFI CAMERA CONNECTOR,SECURE WIFI CAMERA,SECURE WIFI CONNECTION ANDROID,SECURE WIFI CALLING APP,SECURE WIFI CERTIFICATES,SECURE WIFI CONNECTION MAC,SECURE WIFI CHECK
0 notes