#❛ DATA ;; SCANNING┊Q's
Text
About Mai, Devil Survivor's cut character
So, imagine one day you're looking for official images of your favs and you find some scans from the artbook. Cool. But then you also find something you didn't expect:

This character is on page 175 of the Devil Survivor: Official Material Collection. If you've played the game, you'll know she doesn't appear anywhere.
Her name is Mai.
She is still in the game, in a sense. There's leftover data of her at least in the vanilla version. You can see her battle menu image here at the Spriters Resource between Izuna's and Honda's. Meaning that she was supposed to fight.
And indeed, The Cutting Room Floor has something more to say about it:

She was a magic tank.
But the most important source of information I could find about Mai was the same artbook where I first found her, Devil Survivor: Official Material Collection. There is a translated version of this book, sadly I couldn't find it on the vast Internet, so instead I asked @nenilein to translate a relevant fragment from page 174. The people talking on this fragment are Suzuhito Yasuda (character designer) and Akiko Kotoh (chief designer).
Q: "Are there any characters you ended up cutting?
Yasuda: "There was a character who was supposed to contrast Shoji, the journalist. We had already decided her name would be "Mai" and she was going to be a girl who appears at the TV station. Since the her purpose was supposed to be working for you from the side of mass media during an arc concerning intel gathering about the government, we at first had planned to have her debute alongside Shoji, but the more we thought about it the less likely it looked like we could find a good way for the protagonist to get into the TV station, and it became less and less practical to have her in the game at all. In the end we ended up just cutting her."
Kotoh: "She was supposed to be a playable character, I remember, at least at the very start."
Yasuda: "Yeah, and also, while we didn't end up cutting them, a JSDF soldier and commander duo were also initially planned as playable. At the time we received mixed opinions about the fact that there was a bear stuck to the JSDF soldier's chest, but even even so I never expected that would lead to the character being retooled into an NPC.
Kotoh: "And here's another character who wasn't cut, but changed rather suddely, it's the police officer. Originally they were going to be wearing long sleeves, but then I realized the game was set in summer and it would look ridiculous, so we quickly changed it to short sleeves."
There you have it, along with some some other info about no-so-cut characters. By the way, that long-sleeved policeman is in the artbook too, just below Mai. He smol:

So, to recap, Mai was supposed to be a playable character, at least at first, who worked on TV (I forgot to mention it until now, but there's also some text next to her image that directly identifies her as an entertainer 芸能人), knew Shoji and helped you gathering information about the government. That's interesting, but I can see how she was cut.
There's still an arc about uncovering the government's plot in the game, even if doesn't seem as important as it might have originally been. There are plenty of characters who help you gather intel on it: Shoji, Atsuro, 10BIT, Izuna and Fushimi. Media as a form of mass control is an interesting bit to explore that she could've been involved with, but it would have been difficult to do so in a context with no electricity nor signal, and therefore, no radio, TV or Internet. The lines we got from Shoji about the government announcements was the most we could've got.
Lastly, I want to mention another thing I found on TCRF:
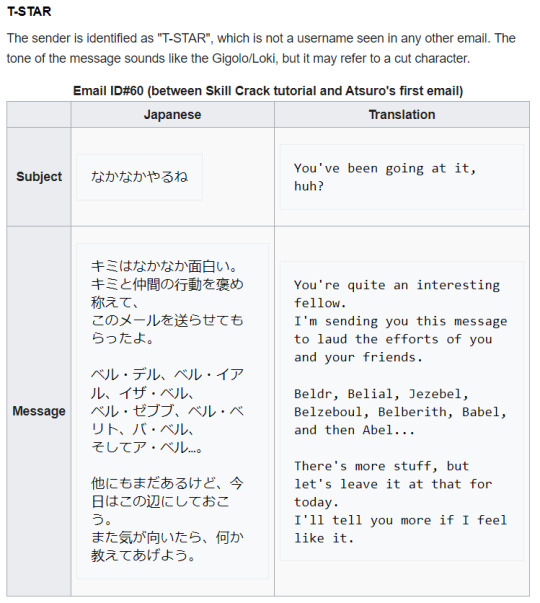
I'm hesitant to post this unused e-mail, since it could very well belong to Loki. Despite that, the handle T-STAR... Mai is most likely a TV star. Loki has somewhat of a connection to stars (the star Sirius has been called Lokabrenna, or Loki's torch, in Scandinavia), but I'm not sure if it's enough to justify that handle.
If Mai was the sender of this e-mail, however, that would mean that she knew not only about the government conspiracy (the cover-up of the demons, the UEM field, maybe about the angels...), but also about THE WAR OF BEL?? That's far from the role that was described by the staff, and that's why I'm more inclined to think that Loki, and not Mai, is the one who was supposed to send it.
Anyway, I hope you found all of this interesting. Mai may not have been in the game, but I think she's fun to think about and can easily become inspiration for roleplaying or fanfiction. That's why I wanted to compile all the info I could find about her on one post. Have fun with it.
26 notes
·
View notes
Note
Do Gallifreyans have some sort of Braille for the visually impaired? Do we have any idea how it'd look?
Do Gallifreyans use a Braille-like system for the visually impaired?
To begin with, it's important to note that blindness/visual impairment appears relatively rare on Gallifrey—only a few known Gallifreyans have completely lost their sight, and each has found their own way to adapt to it. This matters because eyes are very important on Gallifrey, as Gallifreyan technology often uses retina scans.
Unfortunately, there is no known documented equivalent to Earth's Braille on Gallifrey, so there is no real idea of how it might work.
... But never let that get in the way of some theories.
👆Theoretical Gallifreyan Braille Systems
In human terms, Braille is a tactile writing system that relies on touch. Gallifrey, with its five-dimensional tech, might push this concept further. Imagine a Braille that conveys letters and words through touch and dimensions beyond typical human perceptions.
Multi-Dimensional Touch: Gallifreyan Braille could utilise a form of tactile feedback that incorporates temporal and spatial dimensions. Each 'dot' could represent different states depending on temporal phase shifts. So, a single touch could convey layers of information about an object or concept, not just its name or description.
Sonic Enhancements: Gallifreyan Braille could integrate sonic feedback to help convey more complex information. Different frequencies or vibrations could be used to add layers of context or emotion to the tactile experience.
Holographic Projections: For a society that can manipulate light and space, why limit Braille to a static surface? Holographic projections that can be felt and manipulated in the air could be an everyday reality for the visually impaired Gallifreyans, allowing them to 'feel' the data as it floats before them.
Neuro-Sensory Integration: Taking it a step further, Gallifreyan Braille might directly interface with the nervous system, allowing a user to 'see' through touch by translating tactile information into visual-like perceptions in the brain. This method would bypass traditional sensory routes and offer a direct, immersive experience.
🏫 So ...
While Gallifreyans may not have a direct equivalent to Braille, we can certainly have lots of fun thinking about it. Of course, you may decide all these theories are rubbish—the floor is open!
Related:
Could a Time Lord be deaf or mute after regeneration?: Sensory impairments from regenerations and how society could perceive these people.
Factoid: How do Gallifreyans cope with extreme vision loss?
Do Time Lord-specific disabilities exist?: Types of disabilities specifically for Gallifreyans, both known and theoretical.
Hope that helped! 😃
More content ...
→📫Got a question? | 📚Complete list of Q+A and factoids
→😆Jokes |🩻Biology |🗨️Language |🕰️Throwbacks |🤓Facts
→🫀Gallifreyan Anatomy and Physiology Guide (pending)
→⚕️Gallifreyan Emergency Medicine Guides
→📝Source list (WIP)
→📜Masterpost
If you're finding your happy place in this part of the internet, feel free to buy a coffee to help keep our exhausted human conscious. She works full-time in medicine and is so very tired 😴
#doctor who#gil#gallifrey institute for learning#dr who#dw eu#gallifrey#dw meta#gallifreyans#ask answered#whoniverse#gil biology#gallifreyan biology#time lord biology#visual impairment#blindness
22 notes
·
View notes
Text
NASA Transmits Hip-Hop Song to Deep Space for First Time
Gerelle Q. Dodson in a news post for NASA:
The stars above and on Earth aligned as an inspirational message and lyrics from the song "The Rain (Supa Dupa Fly)" by hip-hop artist Missy Elliott were beamed to Venus via NASA's DSN (Deep Space Network). The agency's Jet Propulsion Laboratory in Southern California sent the transmission at 10:05 a.m. PDT on Friday, July 12.
As the largest and most sensitive telecommunication service of NASA's Space Communications and Navigation (SCaN) program, DSN has an array of giant radio antennas that allow missions to track, send commands, and receive scientific data from spacecraft venturing to the Moon and beyond. To date, the system has transmitted only one other song into space, making the transmission of Elliott's song a first for hip-hop and NASA.
Now do Wu-Tang. For the children. ... who are in outer space.
8 notes
·
View notes
Text
The Misfits fanzine is currently in the first stages of development!

The theme is… For the love of Misfits! It will be a free-to-read e-zine that celebrates the 15th anniversary of the show and the fans' love for it. But we need help with suggestions on what should be included in the zine. With this zine being about the fans' love of the show, we don't want to limit the collaborators to just visual art and writing.
This is where you come in! What would you like to be a part of the zine?
There are plans for fanart and fanfiction, along with a questionnaire about fans' favourite seasons, episodes, characters, ships, etc.; the data will be included in the zine.
We don't want to limit the fandom's writers to just fanfiction, so if collaborators wish, think pieces, character analysis, plot deep dives, and mini-essays are also possible. (But there will be a word limit! Same with any fanfiction.)
The same goes for artists! It doesn't just have to be digital art; it can be any form of media that you can photograph or scan into a good-quality photo that's uploaded as a PNG or JPEG file.
Other possible ideas:
-If the community's roleplayers want to contribute, we can work something out, such as conducting a Q&A in character.
-If there is demand, we can do a cosplay page.
-We want to celebrate the many original character creators and self-shippers in the fandom. We could do an introduction page or something similar.
-And, of course, playlist makers! (But they will be limited to 74 minutes per playlist. Think of it being a CD mix.)
Do you have any suggestions or input? Leave a comment on this post, reblog it with your input or even send it to this blog's inbox!
It will lean toward a general audience; ship work is allowed, but it shouldn't be the main focus. The rating will be Mature. Anything that goes in the show goes here!
Applications for collaborators will open by July 10th and close by July 22nd; we will also be reaching out to not just the Tumblr community.
The current goal is for collaborators to start their pieces by August 1st and be done by November 1st.
All finished work must be new and not currently posted anywhere online! Work can be posted to the collaborator's social media shortly after the zine is published.
This is a volunteer-based fan project, and no profit will be made or distributed.

Currently run by @fulfillingbineeds, if you want to be more than just a collaborator and work behind the scenes, let me know!
3 notes
·
View notes
Text
https://mediamonarchy.com/wp-content/uploads/2024/04/20240402_MorningMonarchy.mp3
Download MP3
Swipe-fee settlements, palm payments and apocalyptic eclipse colliders + this day in history w/Coronavirus comet drives command teams to Cheyenne Mountain and our song of the day by K-Rino on your #MorningMonarchy for April 2, 2024.
Notes/Links:
Fans bid farewell to giant moving Gundam in Yokohama
https://japantoday.com/category/national/update1-fans-bid-farewell-to-giant-moving-gundam-in-yokohama
US-59 south of Sallisaw at the Kerr Reservoir is completely shut down at this time due to a barge that has struck the bridge. Troopers are diverting traffic away from the area. The bridge is going to be shut down until inspections of the bridge can be made.
https://vxtwitter.com/OHPDPS/status/1774163632303079885
Video: Another bridge struck by a barge. U.S. 59 Bridge in Sallisaw Oklahoma; Dayton Holland and her family captured this video as they were fishing near the bridge.
https://vxtwitter.com/HighImpactFlix/status/1774167830792941737
Family Dollar, Dollar Tree to close about 1,000 stores
https://www.fox5ny.com/news/dollar-tree-closing-stores-family-dollar-march-13-2024
Here ye here ye: SWIFT planning launch of new central bank digital currency platform in 12-24 months
https://www.reuters.com/business/finance/swift-planning-launch-new-central-bank-digital-currency-platform-12-24-months-2024-03-25/
Visa and Mastercard’s swipe-fee settlement could lead to a rewards fallout
https://sherwoodmedia.com/snacks/business/visa-and-mastercards-swipe-fee-settlement-could-lead-to-a-rewards-fallout/
Video: Visa, Mastercard settle swipe fee lawsuit, agree to reduce rates and halt increases until 2030 (Audio)
https://www.youtube.com/watch?v=tOMBnFcd_vU
FBI agent says he hassles people ‘every day, all day long’ their Facebook posts
https://reason.com/2024/03/29/fbi-agent-says-he-hassles-people-every-day-all-day-long-over-facebook-posts/
Facebook Used “Man-in-the-Middle” Approach To Snoop on Users’ Encrypted Traffic in Secret Project
https://reclaimthenet.org/facebook-used-man-in-the-middle-approach-to-snoop-on-users-encrypted-traffic-in-secret-project
Feds subpoena YouTube viewers for certain videos
https://www.pcworld.com/article/2278729/feds-demanded-id-of-youtube-users-who-watched-certain-videos.html
Elon Musk announces more changes to X – after claims user numbers have plummeted
https://news.sky.com/story/elon-musk-announces-more-changes-to-x-following-claims-user-numbers-have-plummeted-13103101
AT&T Says Data From 73 Million Current and Former Account Holders Leaked on Dark Web; Data from roughly 7.6 million current account holders and 65.4 million former account holders were released on the dark web, AT&T said.
https://www.theepochtimes.com/us/att-says-leaked-data-set-impacts-about-73-million-current-former-account-holders-5618644
AT&T is investigating a leak that put millions of customers’ data on the dark web
https://www.cnbc.com/2024/03/30/att-investigating-breach-that-put-customer-data-on-dark-web.html
Room 641A
https://en.wikipedia.org/wiki/Room_641A
Updates to Discord’s Policies
https://search.brave.com/news?q=Updates%20to%20Discord%E2%80%99s%20Policies
Video Game Publisher Take-Two Interactive to Acquire ‘Borderlands’ Maker Gearbox for $460M
https://www.hollywoodreporter.com/business/business-news/take-two-interactive-borderlands-maker-gearbox-deal-1235861917/
Experts Warn of ‘Digital Enslavement’ as Amazon Pushes Palm-Scan Payment Service; Amazon has rolled out tech to facilitate palm-scanning payments, drawing criticism from experts on privacy and social surveillance and control.
https://www.theepochtimes.com/business/experts-warn-of-digital-enslavement-as-amazon-pushes-palm-scan-payment-service-5618084
Video: Amazon Launches Sign-Up App For Its Palm Payment Service (Audio)
https://www.youtube.com/shorts/XgHM6yDnNTs
Image: Perspective is everything –
Soyjack: Looking at the night sky makes me realize how puny and insignificant I am. //
Based Chad: I am the result of 14 billion yea...

View On WordPress
#alternative news#cyber space war#K-Rino#media monarchy#Morning Monarchy#mp3#podcast#Songs Of The Day#This Day In History
2 notes
·
View notes
Text
I’ve Just Got That Face
“You do NOT have Autism, you’re an Introvert.”
Such comforting words, coming from a cousin I probably held as a baby.
It’s truly the first time I’ve had to confront blatant, in-your-face ableism. And she insisted on this even after I’d told her I’ve been professionally diagnosed and can show her my scores on two of the primary tests used by those professionals to diagnose ASD. Incidentally I also took the Aspie Quiz during that round but I didn’t include it in my post because it’s so granular that the post would have ended up being thousands of words and nobody ain’t got time for that. The RAADS and CAT-Q were enough to prove my point. I’ll cover the Aspie Quiz at a later date.
Which did absolutely nothing to convince my cousin.
Given my problems in talking face to face with people, I stumbled and stuttered through whatever it was I said to her in answer. Honestly it just hit me so hard, getting outright negation from a member of the family. She wasn’t just going to ignore it like everybody else, she outright denied it.
My relationship to my family is complicated. As they’re really the only people I have extended contact with on anything like a regular basis, I mask like Tony Stark in the Hulkbuster suit. But this particular cousin I rarely see, really only at Thanksgiving / Christmas. So since I realized she likely hadn’t heard about it I mentioned I’d been diagnosed as Autistic. And got the above reaction.
There was an argument, which I am bad at. I have real problems talking face to face with people if the conversation is not predictable. I used to be a window clerk when I was working for the Postal service, and that was easy enough since it’s largely scripted. People are there to get stuff done, they’re not going to be sitting around arguing at you, so to speak. But realtime, fraught communications? Can’t think past my nose. So it didn’t go well.
But this was my first encounter with actual ableism directed specifically at me.
To be fair, she did come apologize to me afterward, when I was gathering up my stuff to leave. I actually got on my Tumblr here and read her the scores. I need to scan in my diagnosis letter as well, so likely will do that this weekend. But I did after the fact show her the actual scores from actual ASD diagnosing questionnaires.
No idea if it will change any minds, but ya know, I believe in data.
What she said, it doesn’t change what I am. I can’t un-be Autistic. If all it took was her unbelief to correct 53 years of failed relationships, perpetual misunderstanding, endless alienation, and all the botched interactions... well, she’d be the richest woman in the United States, I reckon.
But if I didn’t have autism, I wouldn’t have the universe in my head. I wouldn’t have the graceful turning of rotating habitats, the deadly glow of supernova remnants, the deceptive serenity of Neptune’s racing depths, or any of the characters that have come out of my hands all these years. All these imaginary people that have kept me company in this empty life.
So yeah. Thanksgiving in the South, y’all. One hell of a good meal, it’s the conversation afterward that’ll ruin your day.
11 notes
·
View notes
Note
re: deviantart, they recently 1) started scanning art to compare against minted NFTs, which sounds great except... people minted NFTs of existing works by living artists, who then had their posts on DA flagged for 'infringing' on NFTs made of THEIR art without their consent-- just the general NFT clusterfucking, and then very recently 2) opted everyone's art into AI training data, both internal and external (at first you had to opt out on every piece of artwork for GENERAL AI training AND send DA a form to opt out of DA's AI training specifically-- they made it easier, but still), 2) stepped back when people raised hell and changed it so everyone is default opted OUT, but they're still letting people scrape the site for AI training
they (DA management) also said some DUMB as fuck shit while discussing the opt-in to AI training thing (q: what about deceased artists? a: idk whatever not our problem), before they eventually rolled it back anyway
tldr, they've made a series of poor decisions and only very loud vocal outrage has changed their course

You're alright hun! I appreciate all the info i can get! Jeez, sounds like deviantart has been pretty sucky over the last few years. Guess I'll have to find someplace else to post sexy art pieces sksksk
2 notes
·
View notes
Text
Enhancing Vehicle Safety with QR Codes: Kavach QR’s Innovative Solutions
Enhancing Vehicle Safety with QR Codes: Kavach QR’s Innovative Solutions
As vehicles become more advanced, ensuring their safety and security has never been more critical. QR technology is leading the charge in this evolution, offering innovative solutions that protect both drivers and vehicles. Kavach QR is at the forefront of integrating these technologies into everyday driving experiences, providing essential tools like emergency QR stickers, digital shields for vehicles, and more. This guest post explores how QR codes are revolutionizing vehicle safety and security.
QR Codes for Cars: A New Standard in Vehicle Safety
QR codes, or Quick Response codes, are two-dimensional barcodes that can store a wealth of information in a small, scannable space. When applied to vehicles, these codes can be scanned to instantly access important details such as the vehicle identification number (VIN), insurance information, service history, and emergency contacts.
Why QR Codes Are Essential for Modern Vehicles
Instant Access to Information: Whether during routine checks or emergencies, QR codes allow quick retrieval of crucial vehicle data, helping to expedite decision-making processes.
Simplified Vehicle Management: QR codes streamline how vehicle information is managed, making it easier for owners, mechanics, and emergency responders to access and update records.
Emergency QR Stickers: Lifesaving Technology on the Road
One of the most critical uses of QR codes in vehicles is the emergency QR sticker. These stickers are strategically placed on the vehicle to provide first responders with immediate access to vital information in case of an accident.
The Importance of Emergency QR Stickers
In an emergency, every second counts. Emergency QR stickers can store essential information, such as medical conditions, allergies, and emergency contact numbers. When first responders scan these stickers, they gain instant access to this life-saving information, ensuring that the correct care is administered without delay.
For example, if a driver is incapacitated following a collision, an emergency QR sticker could inform paramedics of any severe allergies, guiding them to avoid specific medications that could cause harm.
Digital Shield for Vehicles: Enhancing Security with QR Technology
A digital shield for vehicles is a groundbreaking concept that uses QR codes to protect vehicles from theft and unauthorized access. This digital shield leverages the secure storage and quick access capabilities of QR codes to offer enhanced security.
How the Digital Shield Works
A digital shield involves embedding a QR code with encrypted information that only authorized individuals can access. This data might include ownership verification, service records, and security protocols. When the QR code is scanned, it confirms the legitimacy of the vehicle and its owner, making it more difficult for unauthorized persons to tamper with or steal the vehicle.
Advantages of a Digital Shield
Theft Prevention: By securing sensitive vehicle information within a QR code, the digital shield helps deter theft and unauthorized use.
Streamlined Verification: Whether during traffic stops or service visits, the digital shield allows for quick and secure verification of the vehicle’s details.
QR Scanners: The Gateway to Vehicle Information
QR scanners are devices or smartphone applications that read and decode the information stored within QR codes. These tools are essential for accessing the data embedded in vehicle QR codes.
Types of QR Scanners
Smartphone Scanners: Most modern smartphones are equipped with built-in QR code scanning capabilities, allowing users to scan codes directly through their camera apps.
Handheld QR Scanners: These are portable devices commonly used in professional settings where frequent and accurate scanning is required.
Integrated Vehicle Systems: Some advanced vehicles feature integrated QR scanners within their systems, providing seamless access to critical vehicle data.
Best Practices for Using QR Scanners
Proper Alignment: Hold the scanner steady and align it correctly with the QR code for accurate reading.
Adequate Lighting: Ensure the QR code is well-lit to facilitate accurate scanning.
Regular Software Updates: Keep the QR scanner software updated to ensure compatibility with the latest QR code formats.
Understanding QR Codes: The Foundation of Vehicle Safety
QR codes are highly durable and versatile, making them ideal for use in vehicles. They can store a wide range of information, from basic identification details to comprehensive medical records, making them essential in emergencies.
Why QR Codes Are Effective for Vehicles
Durability: QR codes are designed to withstand harsh conditions, ensuring they remain functional over time.
Versatility: They can store detailed information that is easily accessible with a quick scan, making them invaluable tools for vehicle safety and management.
QR Code Readers: Decoding Critical Information
QR code readers are the applications or devices that decode the information contained within QR codes. These readers are crucial for utilizing the full potential of QR technology in vehicles.
Choosing the Right QR Code Reader
When selecting a QR code reader, consider the following:
Compatibility: Ensure the reader works with your device, whether it’s a smartphone, tablet, or specialized scanner.
Ease of Use: Look for readers with an intuitive interface that simplifies the scanning process.
Advanced Features: Some QR code readers offer batch scanning or cloud storage, which can be useful for managing multiple codes efficiently.
Implementing QR Codes on Your Vehicle
Adding QR codes to your vehicle is a straightforward process that can significantly enhance its safety and functionality. Here’s how you can implement them effectively:
Steps to Implement QR Codes
Create the QR Code: Design a QR code that includes essential information such as the VIN, insurance details, and emergency contacts.
Print and Apply the QR Code: Use durable, weather-resistant materials to ensure the QR code remains legible over time.
Strategically Place the QR Code: Position the QR code in accessible yet secure locations, such as the windshield, dashboard, or inside the driver’s door.
Maintaining QR Codes on Your Vehicle
Regular Inspection: Periodically check the QR codes to ensure they are clean and readable.
Update Information: If your contact details or vehicle information changes, update the QR code to reflect these updates.
Replace Damaged Codes: If a QR code becomes worn or damaged, replace it to ensure it remains functional.
Kavach QR: Leading the Way in Vehicle Safety and Security
Kavach QR is at the forefront of integrating QR technology into vehicle safety and security systems. Their innovative products, such as emergency QR stickers and digital shields, provide comprehensive protection for vehicle owners, ensuring that both the vehicle and its occupants are secure.
Why Choose Kavach QR?
Innovation: Kavach QR is known for its cutting-edge solutions that seamlessly integrate QR technology into vehicle safety.
Durability: Kavach QR products are built to last, designed to withstand harsh environmental conditions while maintaining functionality.
Ease of Use: Kavach QR’s solutions are user-friendly, making them easy to implement and maintain, whether for personal vehicles or commercial fleets.
Conclusion
QR codes are revolutionizing the automotive industry by offering innovative solutions that enhance vehicle safety and security. From emergency QR stickers to digital shields, these technologies provide a practical and effective way to protect both drivers and their vehicles. As QR technology continues to advance, its role in the automotive world will only expand, making it an essential feature for modern vehicles.
FAQs
1. How do QR codes improve vehicle security?
QR codes improve vehicle security by storing and providing quick access to essential information that can verify a vehicle’s ownership and status, making it more difficult for unauthorized individuals to tamper with or steal the vehicle.
2. What are emergency QR stickers?
Emergency QR stickers are strategically placed on vehicles to provide first responders with immediate access to vital information, such as medical conditions and emergency contacts, in the event of an accident.
3. Can QR codes be used on older vehicles?
Yes, QR codes can be implemented on any vehicle, regardless of its age or model. They are versatile and can be customized to fit various vehicle types.
4. How does a digital shield protect vehicles?
A digital shield uses QR codes embedded with encrypted data to prevent unauthorized access and theft. It ensures that only authorized individuals can access sensitive vehicle information.
5. What should I include in a vehicle’s QR code?
A vehicle’s QR code should include essential details such as the VIN, insurance information, emergency contacts, and any relevant medical information to assist in emergencies.
0 notes
Text
Enhancing Vehicle Safety with QR Codes: Kavach QR’s Innovative Solutions
Enhancing Vehicle Safety with QR Codes: Kavach QR’s Innovative Solutions
As vehicles become more advanced, ensuring their safety and security has never been more critical. QR technology is leading the charge in this evolution, offering innovative solutions that protect both drivers and vehicles. Kavach QR is at the forefront of integrating these technologies into everyday driving experiences, providing essential tools like emergency QR stickers, digital shields for vehicles, and more. This guest post explores how QR codes are revolutionizing vehicle safety and security.
QR Codes for Cars: A New Standard in Vehicle Safety
QR codes, or Quick Response codes, are two-dimensional barcodes that can store a wealth of information in a small, scannable space. When applied to vehicles, these codes can be scanned to instantly access important details such as the vehicle identification number (VIN), insurance information, service history, and emergency contacts.
Why QR Codes Are Essential for Modern Vehicles
Instant Access to Information: Whether during routine checks or emergencies, QR codes allow quick retrieval of crucial vehicle data, helping to expedite decision-making processes.
Simplified Vehicle Management: QR codes streamline how vehicle information is managed, making it easier for owners, mechanics, and emergency responders to access and update records.
Emergency QR Stickers: Lifesaving Technology on the Road
One of the most critical uses of QR codes in vehicles is the emergency QR sticker. These stickers are strategically placed on the vehicle to provide first responders with immediate access to vital information in case of an accident.
The Importance of Emergency QR Stickers
In an emergency, every second counts. Emergency QR stickers can store essential information, such as medical conditions, allergies, and emergency contact numbers. When first responders scan these stickers, they gain instant access to this life-saving information, ensuring that the correct care is administered without delay.
For example, if a driver is incapacitated following a collision, an emergency QR sticker could inform paramedics of any severe allergies, guiding them to avoid specific medications that could cause harm.
Digital Shield for Vehicles: Enhancing Security with QR Technology
A digital shield for vehicles is a groundbreaking concept that uses QR codes to protect vehicles from theft and unauthorized access. This digital shield leverages the secure storage and quick access capabilities of QR codes to offer enhanced security.
How the Digital Shield Works
A digital shield involves embedding a QR code with encrypted information that only authorized individuals can access. This data might include ownership verification, service records, and security protocols. When the QR code is scanned, it confirms the legitimacy of the vehicle and its owner, making it more difficult for unauthorized persons to tamper with or steal the vehicle.
Advantages of a Digital Shield
Theft Prevention: By securing sensitive vehicle information within a QR code, the digital shield helps deter theft and unauthorized use.
Streamlined Verification: Whether during traffic stops or service visits, the digital shield allows for quick and secure verification of the vehicle’s details.
QR Scanners: The Gateway to Vehicle Information
QR scanners are devices or smartphone applications that read and decode the information stored within QR codes. These tools are essential for accessing the data embedded in vehicle QR codes.
Types of QR Scanners
Smartphone Scanners: Most modern smartphones are equipped with built-in QR code scanning capabilities, allowing users to scan codes directly through their camera apps.
Handheld QR Scanners: These are portable devices commonly used in professional settings where frequent and accurate scanning is required.
Integrated Vehicle Systems: Some advanced vehicles feature integrated QR scanners within their systems, providing seamless access to critical vehicle data.
Best Practices for Using QR Scanners
Proper Alignment: Hold the scanner steady and align it correctly with the QR code for accurate reading.
Adequate Lighting: Ensure the QR code is well-lit to facilitate accurate scanning.
Regular Software Updates: Keep the QR scanner software updated to ensure compatibility with the latest QR code formats.
Understanding QR Codes: The Foundation of Vehicle Safety
QR codes are highly durable and versatile, making them ideal for use in vehicles. They can store a wide range of information, from basic identification details to comprehensive medical records, making them essential in emergencies.
Why QR Codes Are Effective for Vehicles
Durability: QR codes are designed to withstand harsh conditions, ensuring they remain functional over time.
Versatility: They can store detailed information that is easily accessible with a quick scan, making them invaluable tools for vehicle safety and management.
QR Code Readers: Decoding Critical Information
QR code readers are the applications or devices that decode the information contained within QR codes. These readers are crucial for utilizing the full potential of QR technology in vehicles.
Choosing the Right QR Code Reader
When selecting a QR code reader, consider the following:
Compatibility: Ensure the reader works with your device, whether it’s a smartphone, tablet, or specialized scanner.
Ease of Use: Look for readers with an intuitive interface that simplifies the scanning process.
Advanced Features: Some QR code readers offer batch scanning or cloud storage, which can be useful for managing multiple codes efficiently.
Implementing QR Codes on Your Vehicle
Adding QR codes to your vehicle is a straightforward process that can significantly enhance its safety and functionality. Here’s how you can implement them effectively:
Steps to Implement QR Codes
Create the QR Code: Design a QR code that includes essential information such as the VIN, insurance details, and emergency contacts.
Print and Apply the QR Code: Use durable, weather-resistant materials to ensure the QR code remains legible over time.
Strategically Place the QR Code: Position the QR code in accessible yet secure locations, such as the windshield, dashboard, or inside the driver’s door.
Maintaining QR Codes on Your Vehicle
Regular Inspection: Periodically check the QR codes to ensure they are clean and readable.
Update Information: If your contact details or vehicle information changes, update the QR code to reflect these updates.
Replace Damaged Codes: If a QR code becomes worn or damaged, replace it to ensure it remains functional.
Kavach QR: Leading the Way in Vehicle Safety and Security
Kavach QR is at the forefront of integrating QR technology into vehicle safety and security systems. Their innovative products, such as emergency QR stickers and digital shields, provide comprehensive protection for vehicle owners, ensuring that both the vehicle and its occupants are secure.
Why Choose Kavach QR?
Innovation: Kavach QR is known for its cutting-edge solutions that seamlessly integrate QR technology into vehicle safety.
Durability: Kavach QR products are built to last, designed to withstand harsh environmental conditions while maintaining functionality.
Ease of Use: Kavach QR’s solutions are user-friendly, making them easy to implement and maintain, whether for personal vehicles or commercial fleets.
Conclusion
QR codes are revolutionizing the automotive industry by offering innovative solutions that enhance vehicle safety and security. From emergency QR stickers to digital shields, these technologies provide a practical and effective way to protect both drivers and their vehicles. As QR technology continues to advance, its role in the automotive world will only expand, making it an essential feature for modern vehicles.
FAQs
1. How do QR codes improve vehicle security?
QR codes improve vehicle security by storing and providing quick access to essential information that can verify a vehicle’s ownership and status, making it more difficult for unauthorized individuals to tamper with or steal the vehicle.
2. What are emergency QR stickers?
Emergency QR stickers are strategically placed on vehicles to provide first responders with immediate access to vital information, such as medical conditions and emergency contacts, in the event of an accident.
3. Can QR codes be used on older vehicles?
Yes, QR codes can be implemented on any vehicle, regardless of its age or model. They are versatile and can be customized to fit various vehicle types.
4. How does a digital shield protect vehicles?
A digital shield uses QR codes embedded with encrypted data to prevent unauthorized access and theft. It ensures that only authorized individuals can access sensitive vehicle information.
5. What should I include in a vehicle’s QR code?
A vehicle’s QR code should include essential details such as the VIN, insurance information, emergency contacts, and any relevant medical information to assist in emergencies.
0 notes
Text
FlexiFile Converter
FlexiFile Converter

Drag & Drop files here or click to select
Convert to
...
FlexiFile Converter is your free online straightforward service to quickly, easily, and conveniently convert files to any format you choose. By using the convert options of our tool, you can efficiently get all the kinds of files that you want in the desired format when converting documents, images, spreadsheets, and presentations.
To be precise, this online tool is a free PDF Converter, Free JPEG Converter, Free PNG Converter, Free DOC converter, Free Mp3 Converter and a free DOCX converter, enabling a wide range of file format support. The tool generates quality file conversions of manageable sizes that fit your requirements.
FlexiFile converter has to and fro conversion properties. For instance, when you use it to convert a PNG file to PDF, and download the file, you can use it to convert the downloaded file back to PNG while maintaining the same quality output. It is attributed as a Free PDF Converter since it easily converts the other supported files to PDF.
Why Choose Free Online FlexiFile Converter?
Versatile File Conversions: From word documents like DOC and DOCX to Excel sheets like XLS and XLSX, images inclusive of JPG, PNG and Mp3 music files with many others can be converted to file formats of your choice.
User-Friendly Interface: This also means that our operational platform can easily navigate so that you can upload and convert files easily. It takes a few seconds to convert your file and prepare a download link for your file.
Secure and Confidential: We value your privacy and ensure to safeguard your documents and other materials uploaded. For the protection of data, it handles every file that is uploaded and converted privately and securely.
Customization Options: Add headers, footers, and watermarks to the output PDF and other settings such as orientation and margins of the output PDF.
Free of Charge: Our service does not cost anything, reflecting its name well. As as a free PDF converter, free Mp3 converter, free JPG converter, free Word document converter, etc, you shall be able to convert as much as you wish with no extra charges or regressive subscription.
Download Link: Once you convert your files, you will immediately get a download link to access your conversion.
How to Use the Free Online FlexiFile Converter
Upload Your File: You can use Choose File by clicking the upload button to select the file you want to convert. You can upload files in batches and convert them at once.
Choose Conversion Formats: Using the drop down button, choose the type of format you want your uploaded file to be converted to.
Convert and Download: Click the ‘convert’ button to initiate the conversion process. After the conversion process, ensure to download the new converted file.
Supported File Formats
Documents: DOC, DOCX, TXT, RTF, ODT
Spreadsheets: XLS, XLSX, CSV, ODS
Images: JPG, PNG, GIF, BMP, TIFF
Presentations: PPT, PPTX, ODP
Music: Mp4, Mp3
Actions After Downloading
After completing the conversion process it provides a downloading link.
Once the page is refreshed, any converted file is immediately deleted from our servers.
Related Tool
Website Budget Estimator
Do you want us to create a website for you but cannot estimate a budget? Click here.
Frequently Asked Questions (FAQs)
Q: What is a FlexiFile Converter?A: It is a tool supporting multiple file formats and conversions. It can work as:
Free PDF Converter
Free JPG Converter
Free MP3 Converter
Free DOC Converter
Free MOBI Converter
Q: Is Free Online FlexiFile Converter a free tool?A: Yes, our tool is completely free to use, and you can scan as many documents as you want. Using the software is free, and you don’t have to pay any charges or subscribe to anything. Q: How safe are my files while the conversion is on?A: Absolutely. Secure processing is what we employ to make sure your files are safe and your data secure.Q: How many weeks or months does the conversion process take?A: The time taken to convert files depends on the size and type of the file, but most of the conversions usually take a few seconds.Q: Is it possible to convert several files for will at once?A: Definitely, you can convert several files at once because the tool includes a batch conversion option.Q: In which file formats can I convert the files to PDF?A: The free PDF converter enables conversion of most file types to PDF, spreadsheets to PDF, images to PDF, and presentations to PDF.Q: How is the quality of the file conversions?A: Our sources indicate FlexiFile Converter generates quality conversions that satisfy your needs.Q: Does FlexiFile convert music files?A: Yes, as a free mp3 converter, FlexiFile supports mp4 music files when importing and converts them to mp3 audio files.Related Content: What is a Website Budget Estimator?
Read the full article
0 notes
Text
What is Information Technology Security?
Information technology (IT) security is a major problem for people, companies, and organizations in today’s digital environment. The risk of cyber threats and data breaches rises as technology develops and more data is kept online. Protecting sensitive data from unauthorized access, use, disclosure, disruption, alteration, or destruction requires strong IT security.
What is Information Technology Security?

types of threats. These threats can be intentional, such as hacking and viruses, or unintentional, like hardware failures and natural disasters.
Key Components of IT Security
1. Confidentiality: Protecting sensitive information from unauthorized access.
2. Integrity: Ensuring data accuracy and completeness.
3. Availability: Guaranteeing access to data and systems when needed.
4. Authentication: Verifying user identities and access rights.
5. Authorization: Controlling user access to resources and data.
Types of IT Security Threats
1. Malware: Viruses, worms, trojans, and ransomware.
2. Phishing: Social engineering attacks via email or phone.
3. Denial of Service (DoS): Overwhelming systems with traffic.
4. SQL Injection: Exploiting vulnerabilities in databases.
5. Insider Threats: Authorized personnel misusing access.
Best Practices for IT Security*
1. Implement Firewalls and Antivirus Software
2. Use Strong Passwords and Multi-Factor Authentication
3. Regularly Update Software and Systems
4. Conduct Security Audits and Risk Assessments
5. Educate Users on Security Awareness
Understanding IT Security
Information technology security is the collection of tactics, procedures, and tools used to protect information networks. This wide area of study covers safeguarding data, networks, and computer systems from dangers like malware, phishing, and hacking. Ensuring the confidentiality, integrity, and availability of data requires IT security.
Information technology security is a vital aspect of protecting digital information and systems from various threats. By understanding the components, types of threats, and best practices, individuals and organizations can take proactive measures to safeguard their sensitive data and prevent cyber attacks.
Here are some FAQs on Information Technology (IT) Security:
Q:1 What is Information Technology (IT) Security?
A: IT Security refers to the practices, technologies, and processes designed to protect digital information, computer systems, and electronic data from unauthorized access, use, disclosure, disruption, modification, or destruction.
Q:2Why is IT Security important?
A: IT Security is crucial to protect sensitive information, prevent financial loss, maintain confidentiality, integrity, and availability of data, and ensure business continuity.
Q:3 What are common IT Security threats?
A: Common threats include malware, phishing, ransomware, viruses, Trojan horses, spyware, adware, SQL injection, cross-site scripting (XSS), and denial-of-service (DoS) attacks.
Q:4 What is a firewall, and how does it work?
A: A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
Q:5 What is encryption, and how does it work?
A: Encryption is the process of converting plaintext into unreadable ciphertext to protect data confidentiality, integrity, and authenticity.
Q:6 What is the difference between a virus and a worm?
A: A virus requires human interaction to spread, while a worm can spread automatically without human intervention.
Q:7What is phishing, and how can I avoid it?
A: Phishing is a social engineering attack that tricks users into revealing sensitive information. Avoid suspicious emails, verify sender identities, and never click on unfamiliar links.
Q:8 What is two-factor authentication (2FA), and how does it work?
A: 2FA adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone or a biometric scan, in addition to a password.
Q:8 How often should I update my software and operating system?
A: Regularly, as updates often include security patches and bug fixes to protect against known vulnerabilities.
Q:8 What is a vulnerability, and how is it different from a threat?
A: A vulnerability is a weakness in a system or software, while a threat is an exploit or attack that takes advantage of a vulnerability.
Q:9 What is the role of an IT Security professional?
A: IT Security professionals design, implement, and maintain security measures to protect computer systems, networks, and data from cyber threats.
By understanding these fundamental concepts and best practices, you can better protect yourself and your organization from cyber threats and maintain the confidentiality, integrity, and availability of your digital information.
#digitalmarketing#marketing#socialmediamarketing#socialmedia#business#seo#branding#marketingdigital#onlinemarketing#entrepreneur#instagram#advertising#contentmarketing#marketingstrategy#digitalmarketingagency
0 notes
Note
Followup on my hypothetical question of whether or not the CIA could find me from my connection to a renegade Time Lord:
Let's say that renegade has somehow managed to evade permanent punishment on Gallifrey for 2000+ years. (random large amount of time from a human perspective) If I've known this renegade for a few months, let's say somewhere around 4-7, how long would it take for the CIA to hypothetically find me?
How long would it take the Celestial Intervention Agency to find someone?
Considering the advanced capabilities of the CIA and the resources at their disposal, it wouldn't take them long to find you. Here's a rough estimate:
Initial Investigation: Within the first few days to a week, the CIA would gather preliminary data and begin scanning for temporal anomalies and symbiotic links.
Targeted Search: If you've been in contact with the renegade for 4-7 months, they could pinpoint your location within a few weeks using their advanced tracking technology and intelligence networks.
Direct Intervention: Depending on the priority level assigned to the renegade, the CIA could deploy agents to your location within a month or two of initiating the search, especially if they have reason to believe the renegade is using you to evade capture.
If the renegade is highly skilled at evading detection and has taken extensive measures to hide their presence, it might extend the timeframe slightly. However, the CIA's persistence and advanced technology would eventually overcome these obstacles.
⚠️ Please Note
Given that the CIA has mastery over time travel, the concept of timeframes is quite funny. The CIA can travel to any point in time to track you, which means they might have already found you before you even asked this question.
🏫 So ...
They already have.
Related:
What technology can the Celestial Intervention Agency use to track someone?: Limited overview on CIA tracking technology.
Does Gallifrey have anyone they've had friendly interactions with?: History of historical alliances Gallifrey have made.
What does the Gallifreyan political and social environment look like?: Overview of the general structure of Gallifreyan society and politics.
Hope that helped! 😃
Any purple text is educated guesswork or theoretical.
More content ...
→📫Got a question? | 📚Complete list of Q+A and factoids
→😆Jokes |🩻Biology |🗨️Language |🕰️Throwbacks |🤓Facts
→🫀Gallifreyan Anatomy and Physiology Guide (pending)
→⚕️Gallifreyan Emergency Medicine Guides
→📝Source list (WIP)
→📜Masterpost
If you're finding your happy place in this part of the internet, feel free to buy a coffee to help keep our exhausted human conscious. She works full-time in medicine and is so very tired😴
#gil#gallifrey institute for learning#dr who#dw eu#ask answered#whoniverse#doctor who#gallifreyan culture#celestial intervention agency
11 notes
·
View notes
Text
Our Local Experience at KFSH&RC Jeddah Branch with SPECT/CT Perfusion Imaging
Introduction
Pulmonary embolism is the third most common acute cardiovascular disease after myocardial infarction and stroke and results in thousands of deaths each year because it often goes undetected [1]. Diagnostic tests for thromboembolic disease include the D-dimer assay and lower limb ultrasonography, both have high specificity but low sensitivity, ventilation-perfusion scintigraphy and Computed Tomographic Pulmonary Embolism (CTPE) [2]. Planar V/Q scan has inherent limitations related to the overlap of anatomic segments resulting in underestimation of the extent of perfusion loss. The medial basal segment of the right lower lobe is often not visualized on planar scans [3]. Added to these factors is use of probabilistic reporting criteria, and a relatively high indeterminate rate, both caused significant dissatisfaction among referring physicians. It is unsurprising that CT Pulmonary Angiography (CTPA), with its binary reporting approach become the preferred imaging test to assess Pulmonary Embolism (PE) in many institutions (Figure 1A, B &C) [4]. SPECT/CT perfusion imaging can integrate anatomic information with the functional information ones. A potential for a single imaging procedure to yield a high sensitivity and specificity method for the detection of PE. The absence of contrast-related risks, the equal sensitivity and specificity in addition to its lower radiation dose compared to CTPA, are all supporting data for its use to rule out acute and or acute on top of chronic PEs. We aim in our study to assess the trend of using Perfusion SPECT/CT at KFSH&RC Jeddah compared to the standard CTPE. Compared to the 31 scans performed in 2016, 112 studies (361% increase) were completed in 2021.
Read More About This Article: https://crimsonpublishers.com/fsar/fulltext/FSAR.000639.php
Read More Crimson Publishers Google Scholar Articles: https://scholar.google.com/citations?view_op=view_citation&hl=en&user=BcljX0IAAAAJ&cstart=20&pagesize=80&authuser=1&cit crimsonpublishers ation_for_view=BcljX0IAAAAJ:_Ybze24A_UAC
0 notes
Text
What types of machine learning algorithms are used in solving some popular real-world problems
Machine learning (ML) algorithms are used in various real-world applications to solve complex problems. Here are some of the popular types of machine learning algorithms and the real-world problems they address:

1. Supervised Learning Algorithms
These algorithms learn from labeled data and make predictions based on that data.
a. Linear Regression
Use Case: Predicting house prices.
Description: This algorithm predicts a continuous value. For example, given historical data on house prices, linear regression can predict the price of a new house based on its features (e.g., size, location, number of bedrooms).
b. Logistic Regression
Use Case: Spam detection in emails.
Description: This algorithm predicts a binary outcome (e.g., spam or not spam). Logistic regression is used to classify emails into spam or non-spam based on features like word frequency and sender information.
c. Decision Trees
Use Case: Customer segmentation.
Description: Decision trees split the data into subsets based on feature values, creating a tree-like model. This can be used to segment customers based on their purchasing behavior to target them with personalized marketing.
d. Support Vector Machines (SVM)
Use Case: Image classification.
Description: SVMs find the hyperplane that best separates different classes in the data. For instance, they can be used to classify images of cats and dogs based on pixel values.
2. Unsupervised Learning Algorithms
These algorithms find hidden patterns or intrinsic structures in input data without labeled responses.
a. K-Means Clustering
Use Case: Market basket analysis.
Description: K-means clustering groups similar data points together. Retailers use it to understand customer purchase behavior and group similar items together for better inventory management.
b. Principal Component Analysis (PCA)
Use Case: Facial recognition.
Description: PCA reduces the dimensionality of the data, making it easier to analyze. It’s used in facial recognition systems to identify the key features of faces for accurate identification.
3. Reinforcement Learning Algorithms
These algorithms learn by interacting with an environment and receiving feedback in the form of rewards or penalties.
a. Q-Learning
Use Case: Game playing.
Description: Q-learning is a model-free reinforcement learning algorithm. It’s used in developing AI agents that play games (e.g., AlphaGo), where the agent learns the best actions to take to maximize its score.
b. Deep Q-Networks (DQN)
Use Case: Autonomous driving.
Description: DQNs combine Q-learning with deep neural networks. They are used in self-driving cars to navigate and make decisions in complex environments.
4. Neural Networks and Deep Learning
These algorithms are inspired by the structure and function of the human brain.
a. Convolutional Neural Networks (CNNs)
Use Case: Medical image analysis.
Description: CNNs are designed for processing structured grid data like images. They are used in medical diagnostics to analyze X-rays, MRI scans, and other medical images for detecting diseases.
b. Recurrent Neural Networks (RNNs)
Use Case: Language translation.
Description: RNNs are used for sequential data. They are employed in natural language processing tasks such as translating text from one language to another (e.g., Google Translate).
5. Ensemble Learning Algorithms
These algorithms combine multiple models to improve performance.
a. Random Forest
Use Case: Fraud detection.
Description: Random forests combine multiple decision trees to improve accuracy. They are used in banking and finance to detect fraudulent transactions based on transaction patterns.
b. Gradient Boosting Machines (GBMs)
Use Case: Predictive maintenance.
Description: GBMs build models sequentially to correct errors made by previous models. They are used in predictive maintenance to forecast equipment failures and schedule timely maintenance.
Conclusion
Machine learning algorithms are crucial in solving a wide range of real-world problems, from predicting prices and detecting fraud to diagnosing diseases and enabling self-driving cars. The choice of algorithm depends on the nature of the problem, the type of data available, and the specific requirements of the application.
0 notes
Text
Revolutionizing Quality Control: CMM Inspection Services and 3D Scanning in Chicago

In the heart of the Midwest, Chicago stands as a bustling hub of industry and innovation. Among the many technological advancements that have taken root in this vibrant city, Coordinate Measuring Machine (CMM) inspection services and 3D scanning technologies are at the forefront. These cutting-edge techniques are revolutionizing the way manufacturers ensure quality, accuracy, and efficiency in their production processes. This article delves into the significance of CMM inspection services and 3D scanning in Chicago, highlighting the benefits and applications of these transformative technologies.
The Importance of CMM Inspection Services
CMM inspection services are essential for maintaining the highest standards of precision in manufacturing. A CMM is a device that measures the geometry of physical objects by sensing discrete points on the surface of the object with a probe. These machines are capable of delivering highly accurate measurements that are critical in industries where precision is paramount, such as aerospace, automotive, and medical device manufacturing.
Ensuring Precision and Accuracy
One of the primary advantages of CMM inspection services is their unparalleled precision and accuracy. Traditional measurement methods often leave room for human error, but CMMs utilize advanced software and hardware to eliminate this issue. The machine's probes can reach tight tolerances and measure complex geometries that would be impossible to assess accurately by hand. This level of precision ensures that every component meets stringent quality standards, reducing the likelihood of defects and enhancing overall product reliability.
Enhancing Quality Control
Quality control is a critical aspect of manufacturing, and CMM inspection services play a pivotal role in this process. By providing detailed measurements and analyses, CMMs help manufacturers identify deviations from design specifications early in the production cycle. This proactive approach enables swift corrective actions, preventing costly rework or scrap and ensuring that final products conform to exacting standards.
Reducing Production Costs
While the initial investment in CMM technology can be significant, the long-term cost savings are substantial. By minimizing defects and improving product quality, manufacturers can reduce waste and avoid the expense associated with recalls or warranty claims. Additionally, the efficiency of CMM inspection services translates to faster production times, ultimately leading to increased profitability.
The Role of 3D Scanning in Modern Manufacturing
Alongside CMM inspection services, 3D scanning has emerged as a powerful tool in the arsenal of modern manufacturing. 3D scanning Chicago are leveraging this technology to provide comprehensive solutions for a variety of applications, from reverse engineering to quality assurance.
Capturing Complex Geometries
3D scanning is a non-contact method that captures the complete geometry of an object, creating a digital representation that can be analyzed and manipulated. This capability is particularly valuable when dealing with complex or freeform shapes that are difficult to measure using traditional methods. The high-resolution data obtained from 3D scanning can be used to create accurate CAD models, which are essential for design, analysis, and manufacturing.
Facilitating Reverse Engineering
One of the most significant applications of 3D scanning is reverse engineering. When original design documentation is unavailable or outdated, 3D scanning provides a means to recreate accurate digital models of existing parts. This process involves scanning the physical object to capture its dimensions and features, then using specialized software to generate a precise 3D model. This model can then be used to produce new parts, modify existing designs, or integrate with other components.
Streamlining Quality Assurance
In quality assurance, 3D scanning companies in Chicago offer unparalleled capabilities. By comparing scanned data with CAD models, manufacturers can quickly identify discrepancies and ensure that parts meet specifications. This level of scrutiny is invaluable for maintaining consistency and quality in production runs. Additionally, 3D scanning allows for the inspection of large assemblies and complex structures that would be impractical to assess using traditional methods.
Integration of CMM Inspection Services and 3D Scanning
The synergy between CMM inspection services and 3D scanning is transforming the landscape of quality control in manufacturing. By integrating these technologies, companies can achieve a level of precision and efficiency that was previously unattainable.
Comprehensive Measurement Solutions
Combining CMM and 3D scanning technologies provides a comprehensive measurement solution that leverages the strengths of both methods. While CMMs excel in delivering highly precise point measurements, 3D scanners capture complete surface data. Together, these technologies offer a robust approach to dimensional inspection, ensuring that every aspect of a component is accurately assessed.
Enhanced Data Analysis
The integration of CMM and 3D scanning data enhances the analysis process. Advanced software tools can merge the datasets to provide a holistic view of the part, allowing for detailed inspections and comparisons. This integrated approach enables manufacturers to detect even the smallest deviations and make informed decisions to maintain quality.
Increased Flexibility and Efficiency
By incorporating both CMM inspection services and 3D scanning, manufacturers gain increased flexibility in their quality control processes. They can choose the most appropriate method for each application, whether it's the high precision of CMMs for critical dimensions or the comprehensive coverage of 3D scanning for complex geometries. This flexibility leads to more efficient workflows and improved overall productivity.
The Future of Manufacturing in Chicago
As Chicago continues to be a leader in technological innovation, the adoption of CMM inspection services and 3D scanning is set to grow. The city's thriving manufacturing sector stands to benefit immensely from these advancements, driving increased competitiveness and economic growth.
Investment in Advanced Technologies
Chicago's manufacturing companies are investing heavily in advanced technologies to stay ahead in a competitive market. By embracing CMM inspection services and 3D scanning, these companies are positioning themselves at the forefront of quality control and precision manufacturing. This investment not only enhances their capabilities but also attracts new business opportunities and fosters growth.
Training and Workforce Development
To fully capitalize on the benefits of CMM and 3D scanning companies, there is a growing emphasis on training and workforce development. Educational institutions and industry associations in Chicago are collaborating to provide specialized training programs that equip workers with the skills needed to operate and manage these advanced systems. This focus on education ensures a steady pipeline of qualified professionals who can drive innovation and maintain high standards of quality in manufacturing.
Collaboration and Innovation
The integration of CMM inspection services and 3D scanning is fostering collaboration and innovation across Chicago's manufacturing ecosystem. Companies are working together to develop new applications and improve existing processes, leveraging the combined power of these technologies to solve complex challenges. This spirit of collaboration is propelling the industry forward, creating a dynamic environment where creativity and technological advancement thrive.
Conclusion
CMM inspection services and 3D scanning are revolutionizing the manufacturing landscape in Chicago. These technologies provide unparalleled precision, efficiency, and flexibility, enabling manufacturers to maintain the highest standards of quality and competitiveness. As Chicago continues to invest in advanced technologies and workforce development, the city's manufacturing sector is poised for sustained growth and innovation. By embracing the transformative potential of CMM and 3D scanning, Chicago is setting a new standard for excellence in manufacturing, solidifying its position as a leader in the global marketplace.
0 notes
Text

Practical AI Applications for Addressing ESG Challenges
In today's rapidly evolving business landscape, integrating sustainable practices is more than just a trend; it's a necessity. Environmental, social, and governance (ESG) challenges are at the forefront of this transformation, with AI emerging as a powerful tool to address these issues.
Understanding ESG and AI
ESG covers three key areas: Environmental (sustainability efforts), Social (improving equity and engagement), and Governance (ethical practices). AI offers innovative solutions to address these challenges through data and advanced algorithms.
Case Studies of AI in ESG
Environmental Impact:
IBM Watson has been used by various organizations to predict and mitigate climate risks. In one notable case, IBM's AI helped a major European utility company optimize its renewable energy production, leading to a 15% increase in efficiency and a significant reduction in carbon emissions.
Social Equity:
AI-driven platforms like Pymetrics are revolutionizing hiring processes by using neuroscience-backed games to match candidates with roles without bias. This approach has been instrumental for companies like Unilever, which reported a 16% increase in diversity among hires.
Governance:
Accenture implemented an AI-powered compliance monitoring system for a global financial institution. This system scans through thousands of transactions daily, identifying potential regulatory breaches and ensuring higher levels of transparency and accountability.
Statistics Highlighting AI's Impact on ESG
According to a recent study, AI can potentially boost global GDP by up to 26% by 2030 while also reducing greenhouse gas emissions by 4% annually.
The World Economic Forum reports that AI could eliminate 75 million jobs by 2022 but create 133 million new roles focused on sustainable development and equitable growth.
FAQs
Q: How does AI contribute to environmental sustainability?
A: AI optimizes resource use, predicts environmental risks, and enhances renewable energy production, significantly reducing carbon footprints.
Q: Can AI ensure unbiased hiring?
A: Yes, AI platforms like Pymetrics use objective assessments to match candidates with roles, promoting diversity and inclusion.
Q: What role does AI play in corporate governance?
A: AI ensures compliance by monitoring transactions and identifying potential regulatory breaches, enhancing transparency and accountability.
Conclusion
AI is essential in the evolving ESG landscape, helping businesses tackle environmental, social, and governance challenges to promote sustainability.
For more insights on how AI can transform your ESG strategies, explore the discussions and case studies from the World ESG and Climate Summit.
0 notes